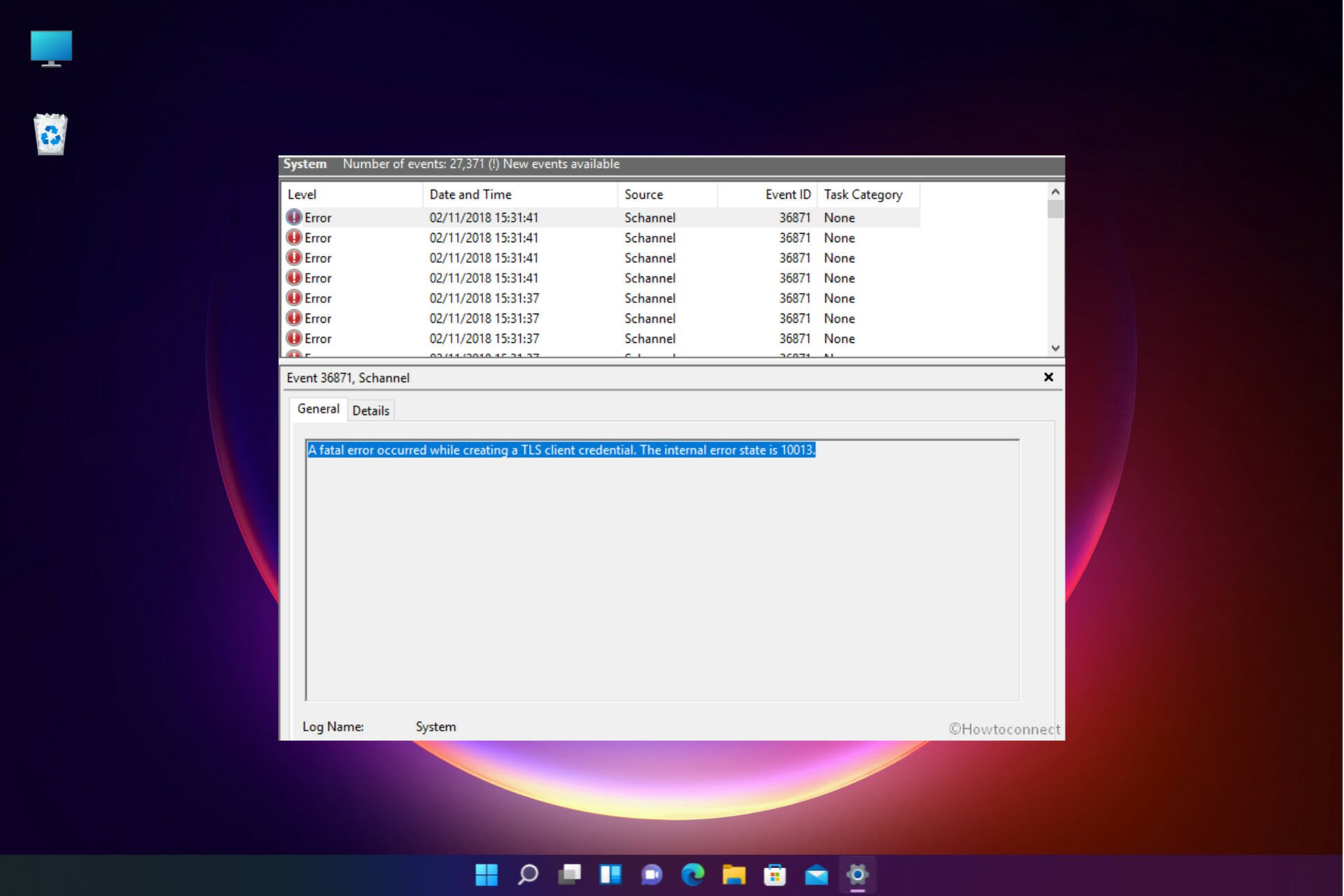
Recently deployed a Windows 2016 Standard Server, with Active Directory and Exchange 2016.
We have disabled SSL 1.0, 2.0 and 3.0 for both Server and Client, and have disabled TLS 1.0 and TLS 1.1.
We are repeatedly getting the following entry in our system log. What is causing this, and how can I fix it.
asked Nov 2, 2018 at 15:52
4
Basically we had to enable TLS 1.2 for .NET 4.x. Making this registry changed worked for me, and stopped the event log filling up with the Schannel error.
More information on the answer can be found here
Linked Info Summary
Enable TLS 1.2 at the system (SCHANNEL) level:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
(equivalent keys are probably also available for other TLS versions)
Tell .NET Framework to use the system TLS versions:
Windows Registry Editor Version 5.00
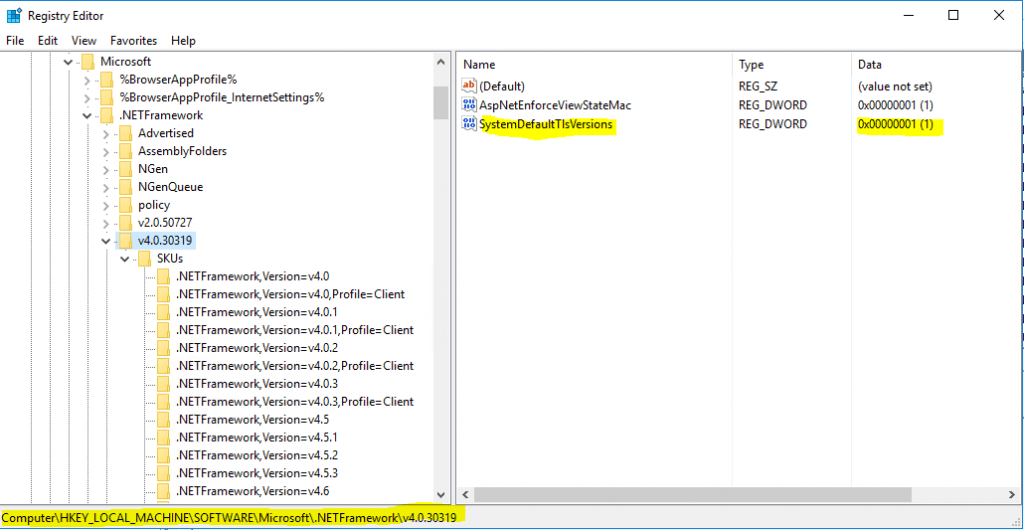
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319]
"SystemDefaultTlsVersions"=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv4.0.30319]
"SystemDefaultTlsVersions"=dword:00000001
This may not be desirable for edge cases where .NET Framework 4.x applications need to have different protocols enabled and disabled than the OS does.
TylerH
20.5k62 gold badges75 silver badges97 bronze badges
answered Dec 5, 2018 at 15:36
neildtneildt
4,96310 gold badges55 silver badges99 bronze badges
6
After none of the methods I could find anywhere helped me:
I opened the Event Viewer and searched when this error started to show so often. I used filter set to Error from Schannel source. In my case, this error was happening every now and then but then, on certain date, it started to show every few seconds! I went to Settings -> Apps & features and searched if anything new was installed on this date – and bingo! It was PrivadoVPN. After uninstalling PrivadoVPN, the error stopped to show!
P.S. I’m not saying that specifically PrivadoVPN is problematic. Mybe it is something with my configuration… Just suggesting the method I used to find the root cause of the error in my case.
answered Mar 10, 2022 at 3:34
After making no changes to a production server we began receiving this error. After trying several different things and thinking that perhaps there were DNS issues, restarting IIS fixed the issue (restarting only the site did not fix the issue). It likely won’t work for everyone but if we tried that first it would have saved a lot of time.
answered Jan 20, 2021 at 18:04
Matt LMatt L
411 silver badge5 bronze badges
In my case, the Windows 2016 server where this was happening was hardened for security compliance. As a result, only specific cipher suites were allowed. This was causing an incompatibility when making HTTPS connections to highly secure endpoints (like Apple Push Notifications API aka APNS)
To fix the issue, I downloaded IIS Crypto and clicked on the Cipher Suites button on the left, to display the list of enabled/disabled cipher suites, and then clicked the «Best Practices» button and rebooted the server. Problem fixed.
answered Jul 21, 2021 at 12:10
blizzblizz
4,0725 gold badges34 silver badges57 bronze badges
I encountered this while rebuilding a server that was moving from Server 2012R2 to DataCenter 2019. It was making me crazy because I could debug it from Visual Studio just fine but IIS immediately returned a 500 error.
In my case, we have several .NET 3.5 and .NET 4.5 applications commingled on the same server and when I created the application for one of the 4.5 applications I had pointed it to the 2.0 App Pool.
Repointing it to the 4.0 App Pool resolved the issue.
answered Oct 7, 2022 at 20:51
I found this here: https://port135.com/schannel-the-internal-error-state-is-10013-solved/
«Correct file permissions
Correct the permissions on the c:ProgramDataMicrosoftCryptoRSAMachineKeys folder:
Everyone Access: Special Applies to ‘This folder only’
Network Service Access: Read & Execute Applies to ‘This folder, subfolders and files’
Administrators Access: Full Control Applies to ‘This folder, subfolder and files’
System Access: Full control Applies to ‘This folder, subfolder and Files’
IUSR Access: Full Control Applies to ‘This folder, subfolder and files’
The internal error state is 10013
After these changes, restart the server. The 10013 errors should disappear.»
answered Nov 16, 2020 at 23:21
2
- Remove From My Forums
-
Question
-
Recently deployed a Windows 2016 Standard Server, with Active Directory and Exchange 2016.
We have disabled SSL 1.0, 2.0 and 3.0 for both Server and Client, and have disabled TLS 1.0 and TLS 1.1.
We are repeatedly getting the following entry in our system log. What is causing this, and how can I fix it.
Answers
-
The issue and solution isn’t about exchange server, its a .Net Framework issue. Although the article is about Exchange Server its the part about configuring .Net that you need.
In short you need to make registry change:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001This change is for any version of .Net 4
If you need to the same with earlier versions of .Net it is:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001The registry change enables TLS 1.2 for .Net
-
Proposed as answer by
Friday, November 8, 2019 7:05 PM
-
Marked as answer by
Hamid Sadeghpour SalehMVP
Friday, January 31, 2020 12:19 PM
-
Proposed as answer by
If you are getting A fatal error occurred while creating a TLS client credential error in the Event Viewer, you can troubleshoot the problem with the help of this guide. This error occurs on Windows 11 as well as Windows 10. However, the solutions are the same irrespective of the operating system.

The entire error message says:
A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
This error appears on your computer when you do not have the TLS 1.0 and TLS 1.1 enabled. Although some programs may not require when you have TLS 1.2 or TLS 1.3, some old programs might need them for connecting to the internet. If it happens, you can get rid of this error with the help of these solutions.
To fix A fatal error occurred while creating a TLS client credential, The internal error state is 10013 while creating a TLS client credential error, follow these steps:
- Enable TLS 1.0/1.1 using Internet Properties
- Change values in the Registry
To learn more about these steps, continue reading.
1] Enable TLS 1.0/1.1 using Internet Properties
As said earlier, you need to enable or turn on TLS 1.0 and TLS 1.1 on your computer in order to fix this issue. As these are not enabled by default on Windows 11 and Windows 10, you need to do that manually. For that, you can get the help of the Internet Properties panel. In order to enable TLS 1.0/1.1 on Windows 11/10, do the following:
- Search for internet properties in the Taskbar search box.
- Click on the individual search result.
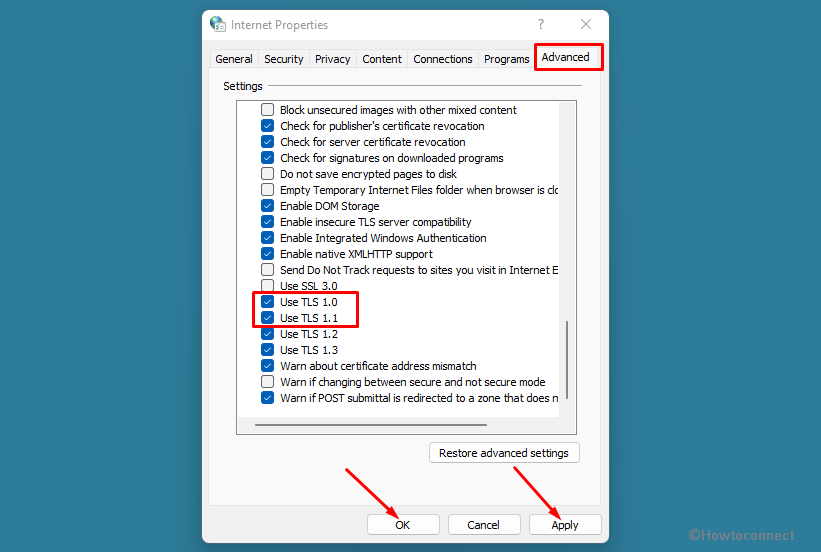
- Switch to the Advanced tab.
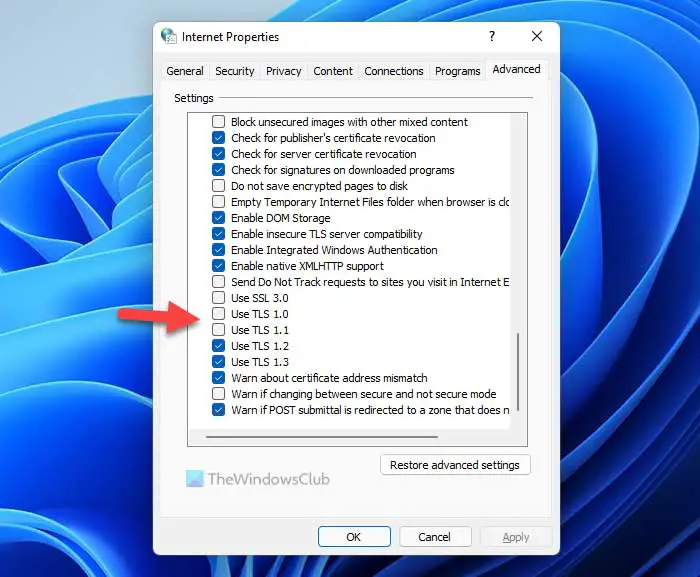
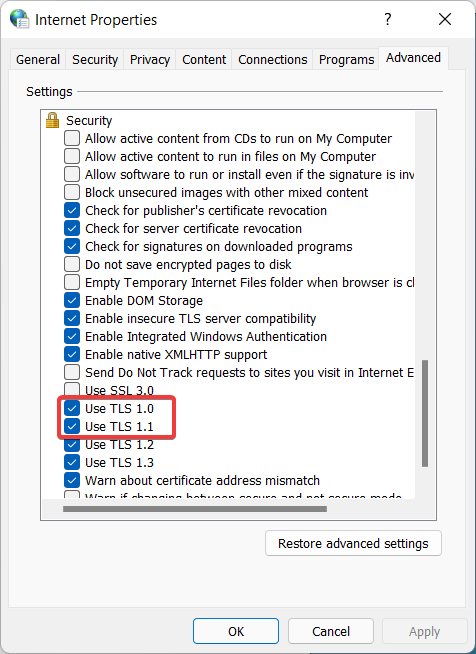
- Find the TLS 1.0 and TLS 1.1.
- Tick both checkboxes.
- Click the OK button.
You may need to restart your computer to get the job done. Once done, you won’t find the aforementioned error message. To verify that, you can open the Event Viewer and check if the problem is resolved or not.
However, this needs to be a temporary measure only, as it is not very secure to use TLS 1.10 and TLS 1.1 for long.
2] Change values in the Registry
If you get the above-mentioned error, a simple change in the Registry file could fix the issue. However, you may need to create some keys and REG_DWORD values as well. Whether it is Windows 11, Windows 10, or any other older version, you can do the following:
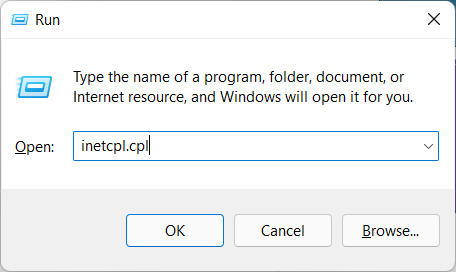
Press Win+R to open the Run prompt.
Type regedit > click the OK button > click the Yes option.
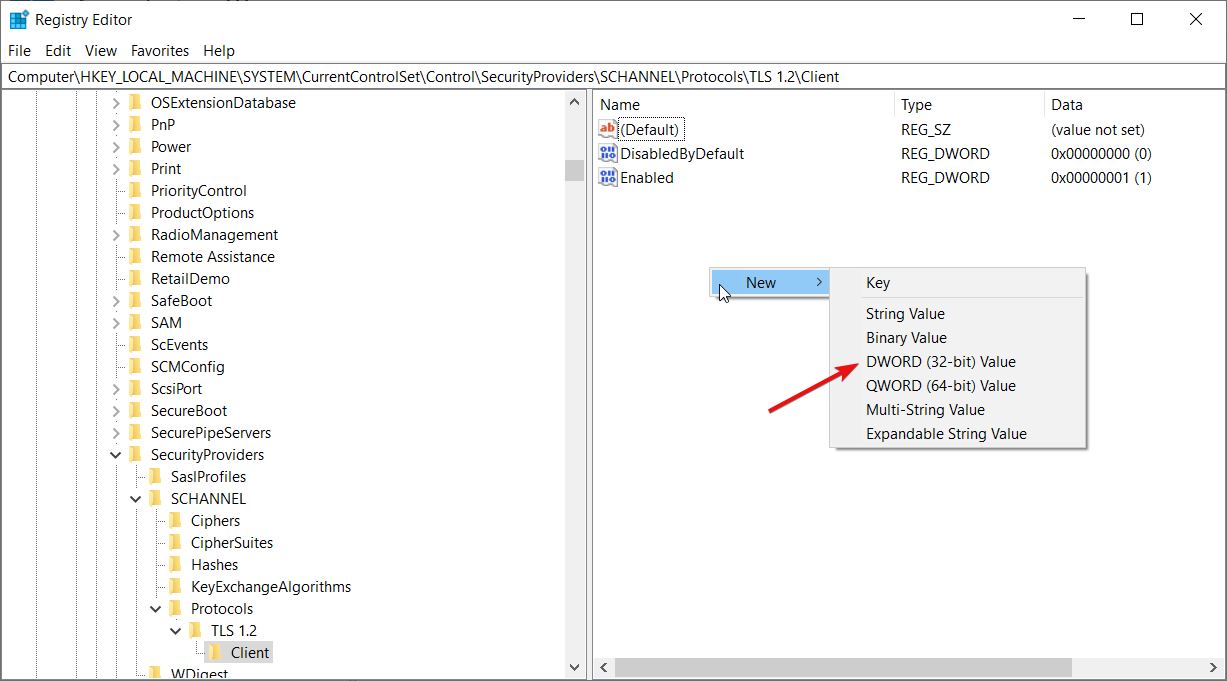
Navigate to this path:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols
Right-click on Protocols > New > Key and name it as TLS 1.2.
Right-click on TLS 1.2 > New > Key and name it as Client.
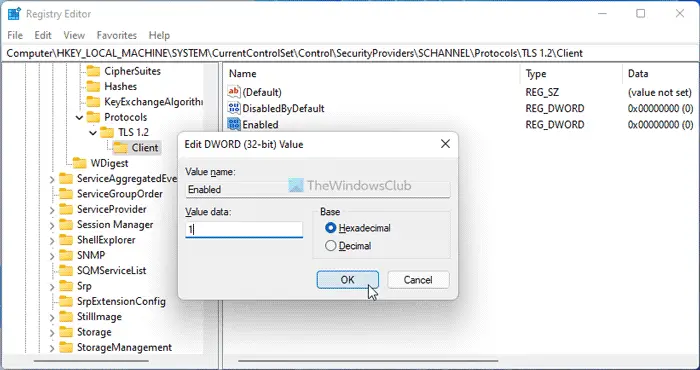
Right-click on Client > New > DWORD (32-bit) Value.
Set the name as DisabledByDefault.
Right-click on Client > New > DWORD (32-bit) Value.
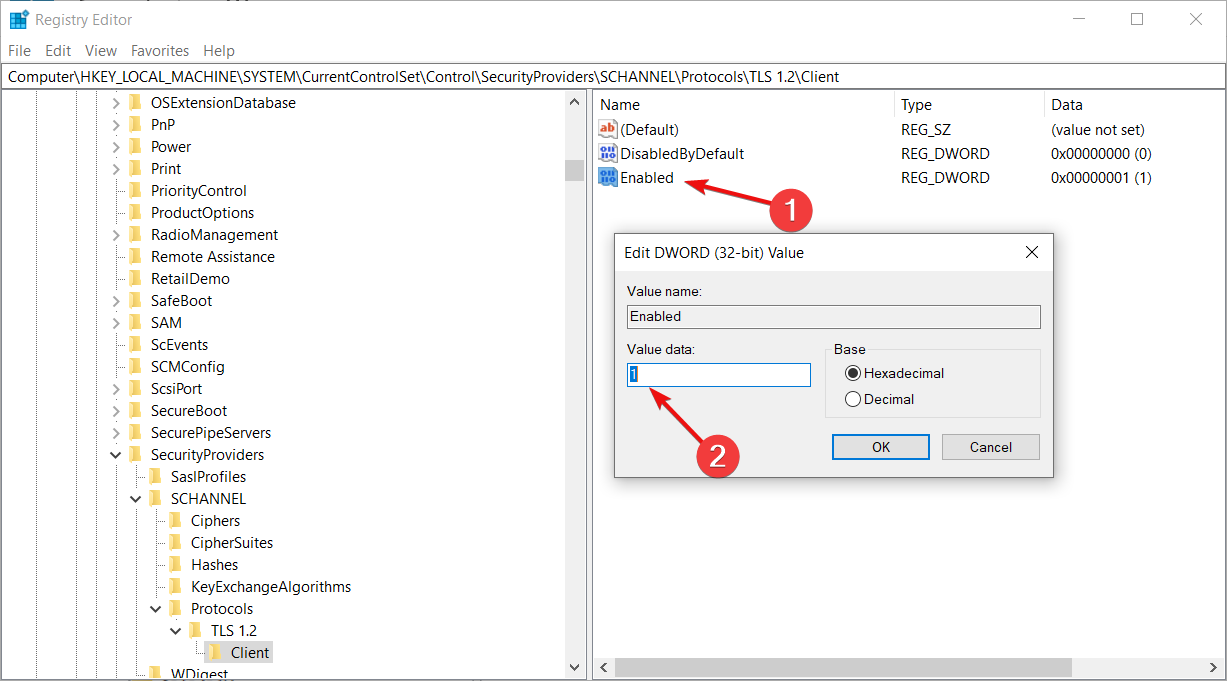
Set the name as Enabled.
Double-click on it to set the Value data as 1.
Click the OK button.
Finally, restart your computer. Once done, your computer won’t show such error messages in the Event Viewer anymore.
How do you check if TLS 1.2 is enabled?
The easiest way to check if TLS 1.2 is enabled or not on Windows 11/10 PC. You can use the Internet Properties panel. For that, press Win+R to open the Run prompt, type inetcpl.cpl, and hit the Enter button. Then, switch to the Advanced tab and navigate to the Security section. Now, check if the Use TLS 1.2 checkbox is enabled or not. If ticked, TLS 1.2 is turned on.
How do you check if TLS 1.0 is enabled on server?
To check if TLS 1.0 is enabled on the server or not, you can use the same steps as above. Having said that, you can search for internet properties in the Taskbar search box and click on the individual search box. Go to the Advanced tab and check if the Use TLS 1.0 checkbox is enabled or not.
That’s all! Hope this guide helped.
Read: How to disable TLS 1.0 in Windows 11/10.
A fatal error occurred while creating a TLS client credential. The internal error state is 10013″. The Windows tool prompts this message repeatedly and disturbs continuing ongoing tasks.
The fatal error occurred while creating a TLS client credential commonly appears when you launch a program, browse the web, or connect to a network. The reason is a disagreement between client and server on a mutual cipher to use to establish a secure connection. However, you can fix the internal error state is 10013 in Windows 11 or 10 simply using the methods in the upcoming parts of this post –
Here is how to Fix A fatal error occurred while creating a TLS client credential. The internal error state is 10013 Windows 11/10 –
For Windows 10 or 11 –
Way-1: Enable TLS 1.0 and 1.1 Protocols
- Press – Windows+R.
- Type – ncpa.cpl.
- Click OK or hit Enter.
- Once the Internet properties window opens up, click on the Advanced tab.
- Scroll down and check both Use TLS 1.0 and Use TLS 1.1.
- Click Apply and then OK.
- Reboot the device and check if the error A fatal error occurred while creating a TLS client credential still appears.
Way-2: Registry tweak to fix The internal error state is 10013
- Click – Search.
- Type – regedit. See – 9 Ways to Open Registry Editor in Windows 10.
- Hit – Enter.
- On User Account Control prompt, select – Yes.
- On the Registry Editor, navigate to the location –
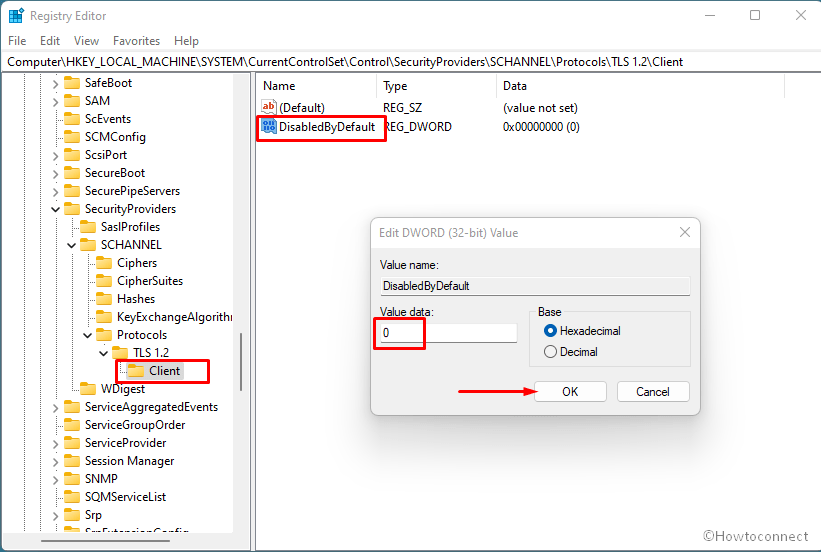
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client
- Go to right pane, right click and select New => DWORD (32-bit) Value.
- Name the value DisabledByDefault.
- Double click on this value and enter Value data 0.
- Click – OK.
- Similarly, create one more value named, Enabled. and put value data 1 for this.
- Close the registry editor and restart the PC.
For Windows Server
Way-3: Enable deprecated Transport Layer Security protocols
- Click on IIS Crypto GUI and download the tool.
- Double click on IISCrypto.exe and launch the app.
- By default, it opens with the Schannel tab.
- Check TLS 1.0 and TLS 1.1 in both the Server protocols and Client protocols sections.
- Click on – Apply. These are the deprecated protocols.
Way-4: Solve A fatal error occurred while creating a TLS client credential by running a PowerShell Script
You can also enable TLS 1.2 using a script. Simply follow the steps –
- Download TLS1.2_enable.
- Unpack the file by extracting the file.
- Right-click on the TLS1.2_enable.ps1 and select Run with PowerShell.
- Alternatively, launch PowerShell ISE.
- Copy the following script –
New-Item 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been enabled.'
- Paste the script in PowerShell ISE.
- Press – Enter.
- Restart the Windows Server.
- Now open Start Event Viewer. Go to Windows Logs and click – System.
- You will no longer find The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.”
Methods list:
Way-1: Enable TLS 1.0 and 1.1 Protocols
Way-2: Registry tweak to fix The internal error state is 10013
Way-3: Enable deprecated Transport Layer Security protocols
Way-4: Run a PowerShell Script
That’s all!!
Repair any Windows problems such as Blue/Black Screen, DLL, Exe, application, Regisrty error and quickly recover system from issues using Reimage.
- Updated on November 16, 2022
- Windows Server
The monitoring software triggers you with the error Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013. In this article, you will learn why this is happening, and the solution for a fatal error occurred while creating a TLS client credential.
Table of contents
- A fatal error occurred while creating a TLS client credential
- Check Transport Layer Security protocols
- Transport Layer Security protocols status
- Solution for a fatal error occurred while creating a TLS client credential
- Conclusion
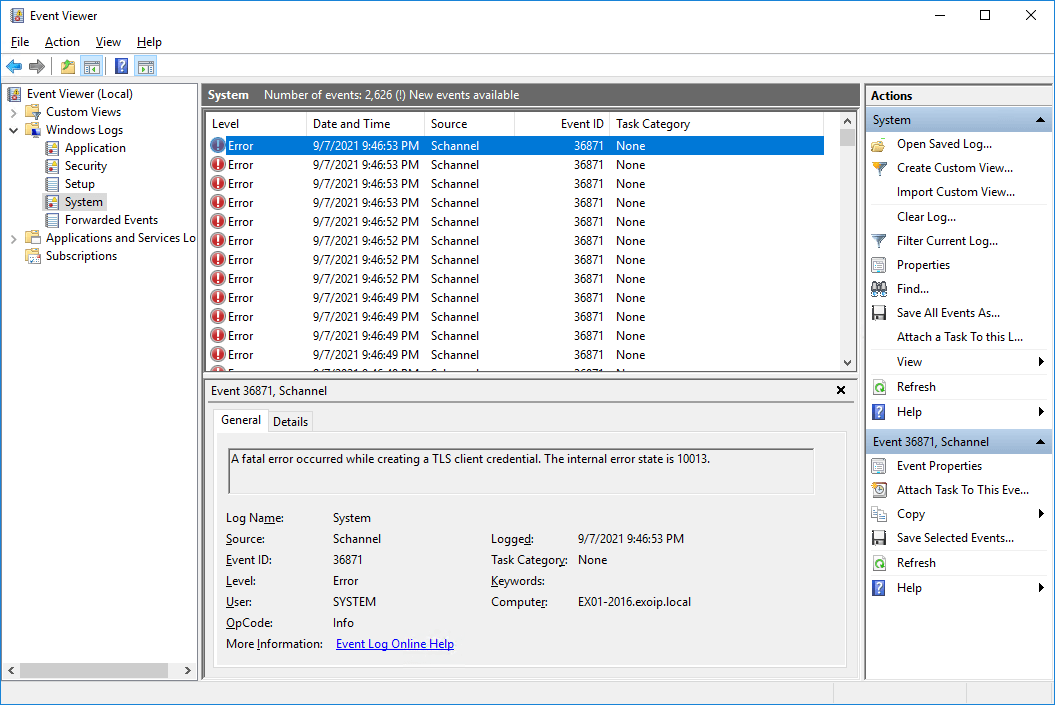
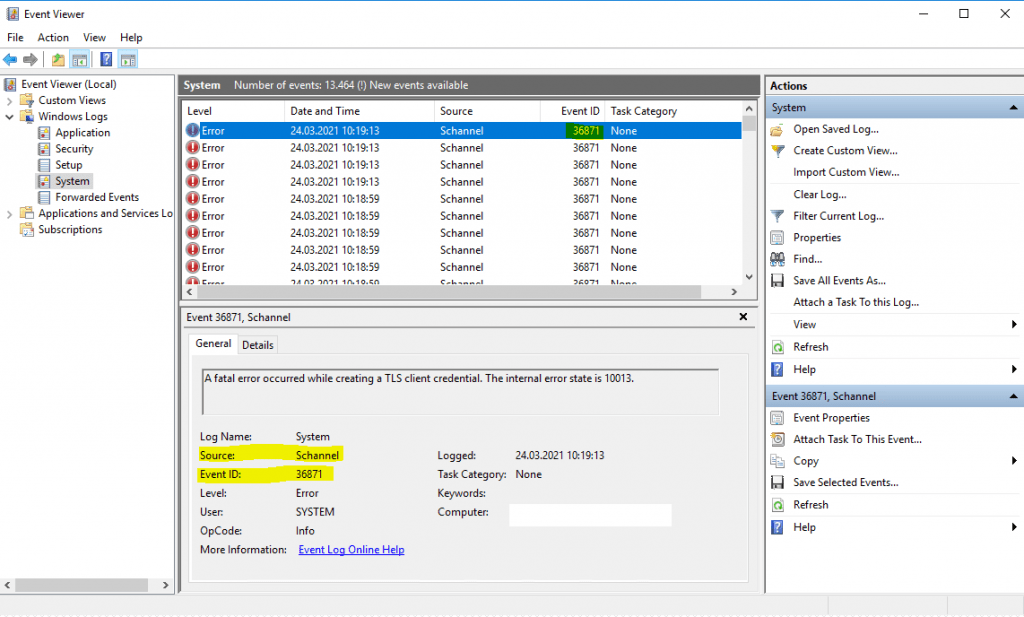
Sign in to the Windows Server and start Event Viewer. Navigate to Windows Logs > System. You will see error Event ID 36871. A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
Why do we get this error, and what is the solution for a fatal error occurred while creating a TLS client credential. The internal error state is 10013?
Check Transport Layer Security protocols
Schannel is a Security Support Provider (SSP) that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) Internet standard authentication protocols.
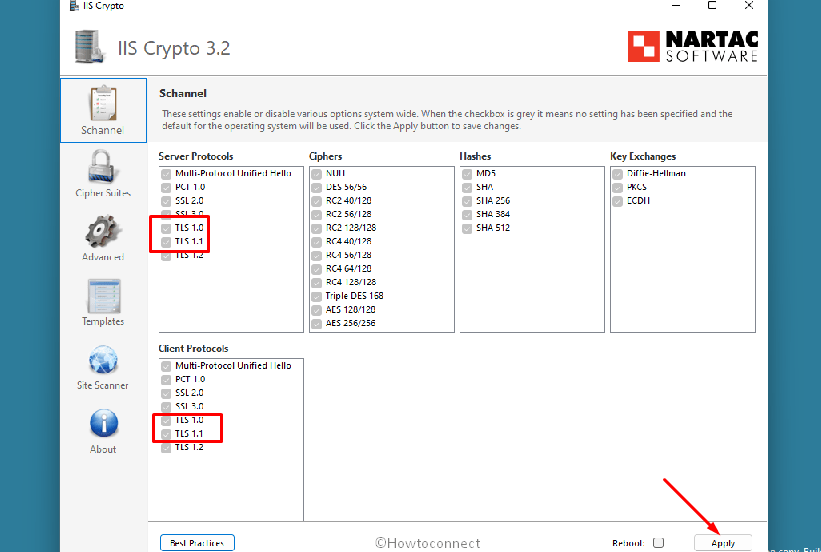
Download IIS Crypto GUI by Nartac Software. After the application is downloaded, start the application.
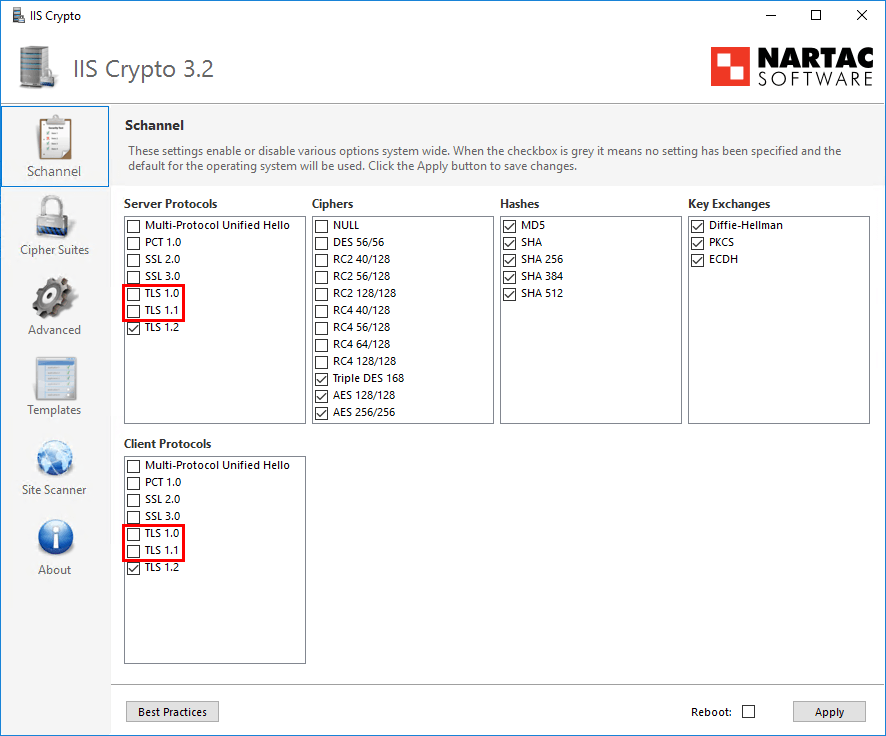
We see that Server Protocols and Client Protocols TLS 1.0 and TLS 1.1 are unchecked.
If we click on Best Practices, it will enable Server Protocols and Client Protocols TLS 1.0 and TLS 1.1. After a reboot, the event error will not show up. When doing that, we fix the problem, but we enable the deprecated protocols. That’s what we do not want.
So how do we keep TLS 1.0 and TLS 1.1 unchecked (disabled) without a fatal error TLS client credential 10013 from showing up?
Transport Layer Security protocols status
See a list of the security protocols and when they are published, including the current status.
Note: Only TLS 1.3 and TLS 1.2 are approved. The protocol TLS 1.3 is only available to enable in Windows Server 2022 or newer.
| Protocol | Published | Status |
|---|---|---|
| SSL 2.0 | 1995 | Deprecated in 2011 |
| SSL 3.0 | 1996 | Deprecated in 2015 |
| TLS 1.0 | 1999 | Deprecated in 2020 |
| TLS 1.1 | 2006 | Deprecated in 2020 |
| TLS 1.2 | 2008 | Approved |
| TLS 1.3 | 2018 | Approved |
Solution for a fatal error occurred while creating a TLS client credential
Now that we gathered all the information, we are going to enable TLS 1.2 on the system by running the script. After a reboot, we will check the Event Viewer. It should not show any errors.
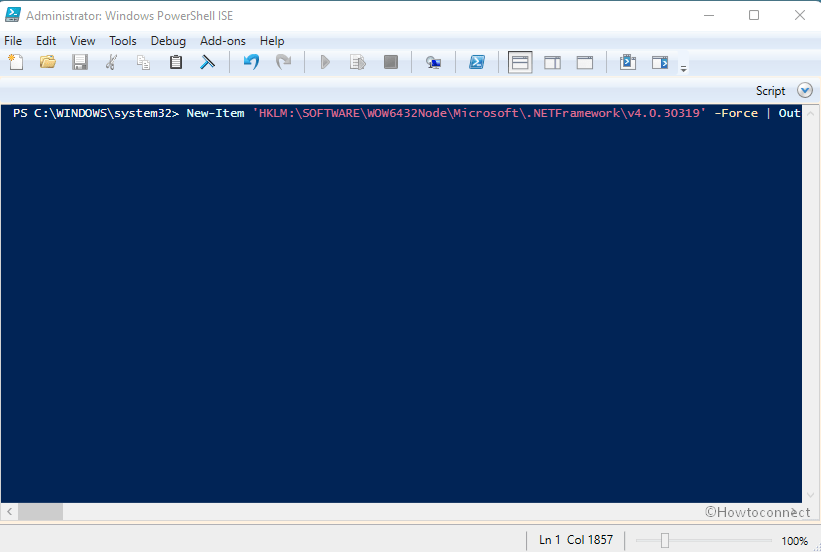
Run PowerShell as administrator. Download Enable-TLS1.2.ps1 PowerShell script and run it from PowerShell. Another way is to copy the below PowerShell script.
If (-Not (Test-Path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319')) {
New-Item 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:SOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319')) {
New-Item 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -Name 'SystemDefaultTlsVersions' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:SOFTWAREMicrosoft.NETFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server')) {
New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client')) {
New-Item 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Name 'Enabled' -Value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 has been enabled. You must restart the Windows Server for the changes to take effect.' -ForegroundColor CyanPaste the script in PowerShell ISE and run the script.
Reboot the Windows Server.
Start Event Viewer. Expand Windows Logs and click System. The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.” doesn’t show up anymore.
Did it work for you?
Conclusion
You learned why you get a fatal error occurred while creating a TLS client credential. The internal error state is 10013. The solution to this problem is configuring TLS 1.2 on the Windows Server. After that, you don’t see the Event ID 36871 errors in Event Viewer.
Did you enjoy this article? You may also like How to Enable TLS 1.2 on Windows Server. Don’t forget to follow us and share this article.
ALI TAJRAN is a passionate IT Architect, IT Consultant, and Microsoft Certified Trainer. He started Information Technology at a very young age, and his goal is to teach and inspire others. Read more »
If you have disabled the deprecated server and client protocols TLS 1.0 and TLS 1.1 on your Windows Server as further down for security reasons.
And after that you will see a bunch of error messages as in the title of this post like this.
You have to add the following registry DWORD value like follows.
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319
“SystemDefaultTlsVersions”=dword:00000001This registry key has a value of type DWORD. A value of 1 causes your app to allow the operating system to choose the protocol. A value of 0 causes your app to use protocols picked by the .NET Framework.
If your app targets .NET Framework 4.7 or later versions, this key defaults to a value of 1. That’s a secure default that we recommend. If your app targets .NET Framework 4.6.1 or earlier versions, the key defaults to 0. In that case, you should explicitly set its value to 1.
To ensure .NET Framework applications remain secure, the TLS version should not be hardcoded. .NET Framework applications should use the TLS version the operating system (OS) supports.
So in case of our error messages, .NET Framework was trying to use one of the disabled TLS 1.0 or TLS 1.1 client protocols. Now after setting SystemDefaultTlsVersions to 1, the operating system is now choosing the right and available protocol instead the .NET Framework itself.
This change is for any version of .NET 4 and 64 Bit Applications.
For versions before .NET 4 you need to add the value in HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727
After a reboot the error messages should stay out and disappear.
For 32 Bit Applications and .Net 4 and above you need to add the value in HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319 resp. v2.0.50727 for versions before .Net 4.
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
The following .REG file sets the registry keys and their variants to their most safe values:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001
Links
by Milan Stanojevic
Milan has been enthusiastic about technology ever since his childhood days, and this led him to take interest in all PC-related technologies. He’s a PC enthusiast and he… read more
Updated on February 6, 2023
- Many users are encountering the Fatal error while creating a TLS client credential and it doesn’t offer too much information.
- During the runtime of an application, a fatal error occurs when the program can’t continue with its execution.
- This is because your application is not able to connect to the database, as a result of which it cannot proceed further.
XINSTALL BY CLICKING THE DOWNLOAD FILE
- Download Restoro PC Repair Tool that comes with Patented Technologies (patent available here).
- Click Start Scan to find Windows 11 issues that could be causing PC problems.
- Click Repair All to fix issues affecting your computer’s security and performance
- Restoro has been downloaded by 0 readers this month.
With the launch of the Windows 11 operating system, it is rare for users to face problems while launching programs on their computers.
However, with programs linked to a server, users often encounter the Fatal error occurred while creating a TLS client credentials on their system.
Error messages are usually not very explanatory, especially when they are cryptic. But what is even more frustrating is when the error doesn’t give a hint as to what the problem is.
This guide has been created to help you fix the fatal error that occurred while creating a TLS client credential error without losing your files, documents, and other data.
What is the TLS client credential?
The Transport Layer Security (TLS) is a protocol designed to provide secure communication over the Internet with end-to-end encryption, proof of integrity, and identity verification.
When a TLS connection is established, the server provides a certificate to the client. The client then validates the server’s identity by checking for an Internet security protocol known as Client TLS.
If the certificate doesn’t correspond to the protocol, you get the message Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
Why does the error occur while creating a TLS client credential?
The reason behind this error is that the program is a client that needs a connection to a server. Though the internet would be working well, the client would not be able to decipher the code sent by the server.
This indicates an issue with the protocols. The statement of the error also points toward the TLS encryption protocol.
Some PC issues are hard to tackle, especially when it comes to corrupted repositories or missing Windows files. If you are having troubles fixing an error, your system may be partially broken.
We recommend installing Restoro, a tool that will scan your machine and identify what the fault is.
Click here to download and start repairing.
There is a need to decrypt some information that has been encrypted. The challenge is not knowing how to get the data back into a format where it can be read.
You may also encounter the Event ID 36871: A Fatal Error Occurred While Creating An SSL (client or server) Credential. The internal error state is 10011.
However, you don’t have to mistake it with the issue we’re dealing with here because it is a whole different issue that has to do with the email server.
There is also the Event ID 36871: A fatal error occurred while creating a TLS client credential RDP that is triggered because you can’t access the remote desktop from Windows Server 2012.
Many times, this information is stored in the system registry on a Windows computer. Some of the possible workarounds that you can try to fix this error are mentioned below.
What can I do if a fatal error occurs while creating a TLS client credential?
1. Enable the TLS 1.0 and 1.1 Protocols
- Press Windows + R keys and type in inetcpl.cpl into the Run dialog window, then hit Enter.
- In the Internet Properties window, click on the Advanced tab.
- From here, check both Use TLS 1.0 and Use TLS 1.1.
- Then, click Apply and OK.
- Reboot the device and see if the error persists.
Enabling TLS 1.0 and 1.1 protocols should fix the issue. However, if it does not work for you, move on to the next resolution.
2. Run the Registry Editor
- Press Windows + R keys, type regedit, and hit Enter.
- On the User Account Control prompt, click Yes.
- In the Registry Editor, navigate to the following location:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client - Go to the right pane, right-click on a free space, and hit New, then DWORD (32-bit) Value.
- Name the value DisabledByDefault.
- Double-click the value and in the window that pops up, enter 0 for Value Data, then select OK.
- In the same way, create another value called Enabled and set the Value data to 1.
- Finally, exit the Registry Editor and reboot your PC.
Windows registry is a vital tool that helps you make changes to your computer’s settings. The registry editor’s role is to modify data such as file paths, windows titles, or other OS-critical settings.
- How do I enable or disable TLS in Windows Server?
- How to fix the TLS error on Windows 11
- Fix: TLS security settings are not set to the defaults
The methods used in this guide should be enough to fix a fatal error occurred while creating a TLS client credential. The internal error state is 10013 issue.
TLS can be a pretty buggy sometimes and if you don’t really need it you can disable it all together to stop it from creating any issues.
If you found this tutorial helpful, do let us know in the comments section below. We would love to hear from you.
Still having issues? Fix them with this tool:
SPONSORED
If the advices above haven’t solved your issue, your PC may experience deeper Windows problems. We recommend downloading this PC Repair tool (rated Great on TrustPilot.com) to easily address them. After installation, simply click the Start Scan button and then press on Repair All.
Newsletter
So, today we are going to go over another annoying error we most often see in Windows 10 event logs. The error in question is «A fatal error occurred while creating a TLS client credential. The internal error state is 10013» with an EventID of 10013. This error seems to be caused by the disabling of certain client side ciphers and TSL versions, or some sort of corruption from installed updates.
As we know, SSL 1.0, SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 are insecure and no longer recommended to be used. Despite Microsoft stating its version of TLS 1.0 is free of any known security vulnerabilities, they still recommend migrating existing applications to use new versions of TLS such as 1.2 or ideally 1.3.
However, Microsoft Windows is a funny thing. It relies heavily on RPC(Remote Procedure Call). It even uses RPC to carry out local functions. This makes Windows robust, but can often have unintended consequences such as this error.
To fix this issue we need to do two things:
1. Edit Registry to Fix TLS version used by .Net Framework by adding the following registry values to the registry by using regedit. Navigate to the proper keys, and change or create them. See below:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv4.0.30319]
«SystemDefaultTlsVersions»=dword:00000001Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv2.0.50727]
«SystemDefaultTlsVersions»=dword:00000001
Those registry keys will enable TLS 1.2 for use by applications that use .Net Framework.
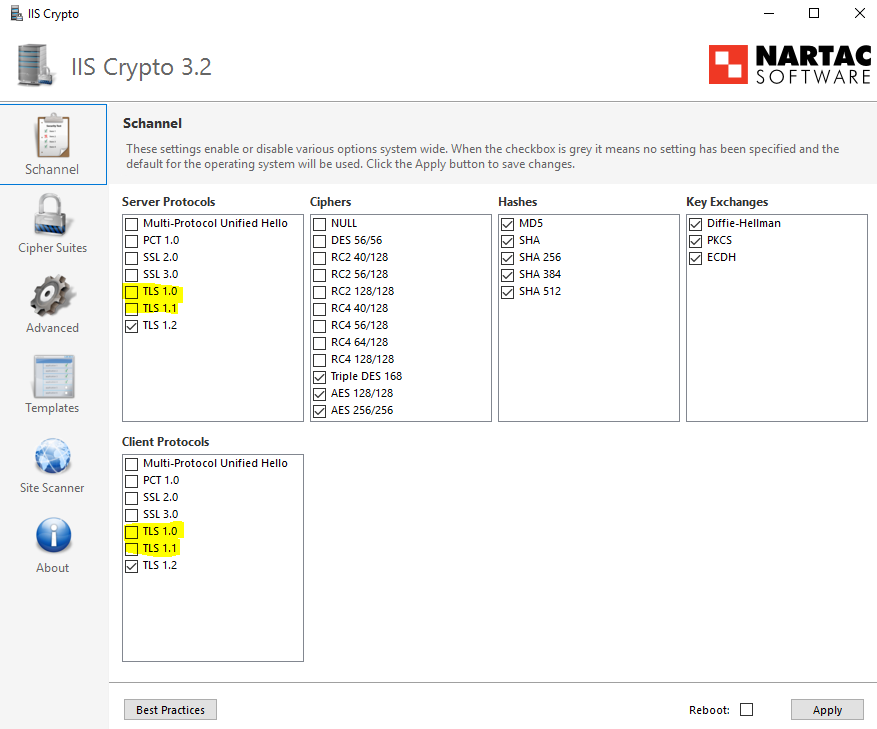
2. Use the ISS Crypto Application by Nartac software to set security suites to the «Best Practices» setting and then restarting the computer. See Screenshot below
After using the ISS Crypto application to set the system to «Best Practices» which is really the Microsoft Windows Default Settings, adding the registry enteries above for .Net Framework, and restarting the computer, the TLS Event ID 10013 error should stop.
Before anyone asks, yes it shows TLS 1.0 being enabled, however, TLS 1.2 is backwards compatible with previous versions. So in essence what these changes do is allow TLS 1.2 and 1.3 in Windows to respond and handle requests for older versions so the event viewer doesn’t flood your log with errors.
I hope this article helps anyone out there dealing with these errors. Until next time!
Disclaimer: I am not responsible for anything that may happen to your PC when changing settings or changing registry values. If you choose to make changes, you do so at your own risk.. You are solely responsible for any damage to your computer , data, or other hardware due to user error, inadequate cooling, too high of voltages, incorrect software settings, and any other factors. Please remember to back up your computer before attempting this. If overclocking, Do not Overclock on the stock AMD or Intel CPU Heatsink and fans. Use Aftermarket cooling heat sinks of sufficient TDP or water cooling to ensure best chance of not having premature hardware failure. As always, remember to backup your data before attempting any change. I am not responsible for data loss or damage of any kind.