I came across this problem today, and found this possible solution for you (fixed it for me);
When you connect to a powered-on server using VMWare converter, the tool attempts to interrogate the target server using a number of methods, including attempting to try to connect to any existing VMWare converter agents on that target system. The default port for VMWare converter agent is 9090. If VMWare converter can connect to the machine, but gets no answer on port 9090, it should then proceed to ask you if you want it to automatically deploy the converter agent onto the target system for you,
In my case, something else on the target server was already using port 9090, and this confused VMWare converter into giving the error you described. Your two choices are to either temporarily disable the software using 9090, or manually install the converter agent, choosing a different port during the installation wizard. If you decided on this latter option, be sure to specify the port to connect to when you attempt the VMWare conversion again, by using the format (eg server01:9091)
Hope this helps!
—
Mark Lomas
Hi all,
I’m trying to migrate a physical Windows Server 2003 SP2 Server to our vCenter but the Target selection fails with Unexpected EOF.
I’ve tried to disable SSL according to Disabling SSL encryption on VMware Converter Standalone 5.x and 6.0 (2020517) | VMware KB but it was already disabled.
Products used:
OS: Windows Server 2003 SP2
vCenter Converter Standalone 5.0.1
vSphere Client Version 6.5.0.10000
Logfile excerpts:
First Logfile:
2017-10-18T10:43:35.437+02:00 [02680 verbose ‘wizardController’] Trying connection to VC server ‘X’ with user ‘administrator@domain.intern’
2017-10-18T10:43:35.437+02:00 [02680 verbose ‘wizardController’] Getting VIM connection to X…
2017-10-18T10:43:35.468+02:00 [02680 info ‘wizardController’] Connecting to host X on port 443
2017-10-18T10:43:35.468+02:00 [02680 info ‘wizardController’] localVersion is: vim.version.version7
2017-10-18T10:43:35.484+02:00 [02656 error ‘Default’] SSLStreamImpl::DoClientHandshake (03fda008) SSL_connect failed with Unexpected EOF
2017-10-18T10:43:35.484+02:00 [02656 error ‘HttpConnectionPool’] [ConnectComplete] Connect error SSL Exception: Unexpected EOF
2017-10-18T10:43:35.484+02:00 [02680 error ‘wizardController’] GetVimConnection has error while trying to connect (3), Error: SSL Exception: Unexpected EOF
—>
2017-10-18T10:43:35.484+02:00 [02680 error ‘Default’] SSL Exception: Unexpected EOF
2017-10-18T10:43:54.484+02:00 [02636 info ‘ConverterSession’] Converter data provider created.
2nd Logfile:
2017-10-18T10:42:00.703+02:00 [01668 info ‘Default’] [user,890] Successfully authenticated user Administrator
2017-10-18T10:42:14.890+02:00 [02664 info ‘Default’] [user,890] Successfully authenticated user Administrator
2017-10-18T10:42:16.062+02:00 [02664 error ‘Default’] Found dangling SSL error: [0] error:00000001:lib(0):func(0):reason(1)
2017-10-18T10:43:54.484+02:00 [02660 info ‘Default’] [diagnosticManager,370] Generating Converter.Server log bundle.
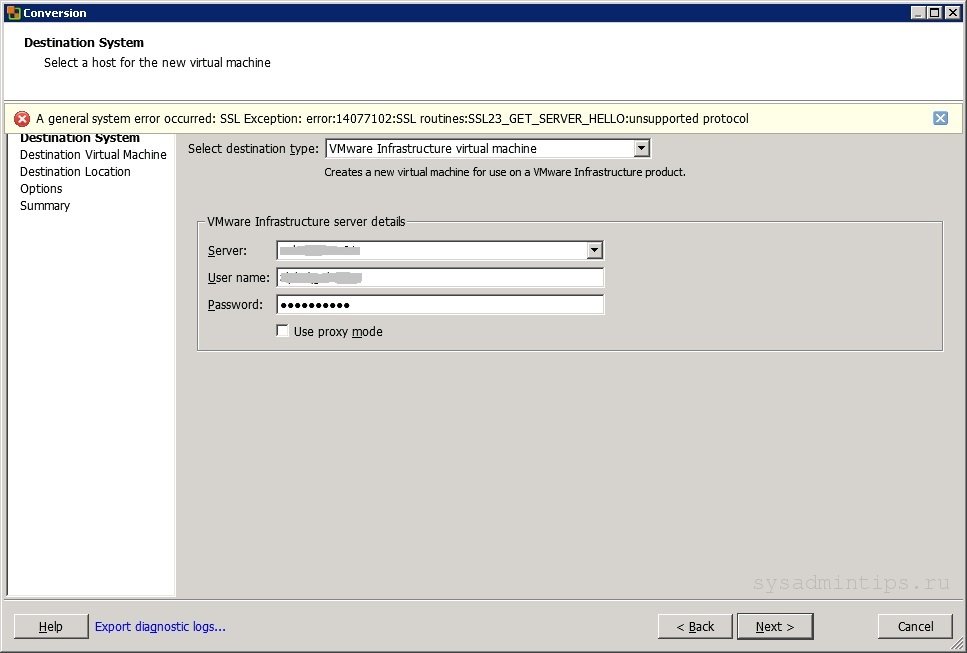
Недавно столкнулись с такой проблемой, что при попытке конвертировать физический сервер в виртуальную инфраструктуру VMware vSphere с помощью VMware vCenter Converter Standalone возникла ошибка:
SSL Exception: error:14077102:SSL routines:SSL23_GET_SERVER_HELLO:unsupported protocol
Ошибка появлялась в момент подключения к vCenter:
Изменение параметра SSL в файле converter-worker.xml, описанного в статье VMware Knowledge Base, ни к чему не приводило, ошибка 14077102 оставалась.
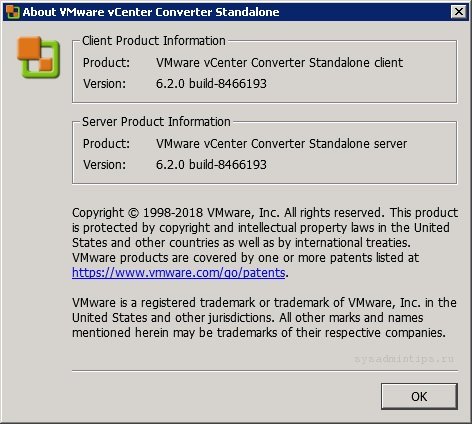
Примечание. Коротко об используемых версиях программного обеспечения:
- VMware vCenter Converter Standalone – 6.2.0, build 8466193;
- VMware vCenter – 5.5.0, 2646482;
- ОС конвертируемого сервера – Windows Server 2012 R2;
- ОС сервера с установленным конвертером – Windows Server 2008 R2.
Никакие манипуляции с переустановкой конвертера на другой сервер также не увенчались успехом.
Решение по устранению ошибки SSL 14077102
В нашем окружении помог только обходной путь в виде отката версии конвертера на 6.1.1.
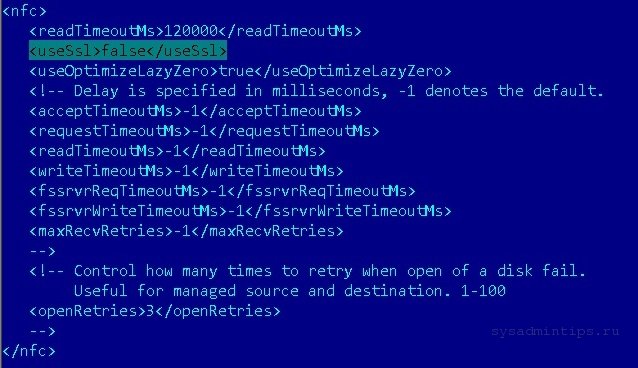
После установки старой версии параметр useSsl в файле converter-worker.xml был переведен в состояние false, согласно статьи выше из базы знаний производителя:
После редактирования файла не забывайте перезапустить службу VMware vCenter Converter Standalone Worker. Надеемся, что это статья сэкономит кому-то час-два рабочего времени.
Видео от вендора по отключению использования SSL в конвертере:
Disabling SSL encryption on VMware Converter Standalone 5.x
- 5214
Comments
This was referenced
Mar 23, 2020
barhom
referenced
this issue
in openwrt/openwrt
Mar 25, 2020
This version includes bug and security fixes, including medium-severity CVE-2019-1551, affecting RSA1024, RSA1536, DSA1024 & DH512 on x86_64. Signed-off-by: Eneas U de Queiroz <cotequeiroz@gmail.com>
Bubu
mentioned this issue
Mar 26, 2020
nginx-hg-mirror
pushed a commit
to nginx/nginx
that referenced
this issue
Aug 10, 2021
A new behaviour was introduced in OpenSSL 1.1.1e, when a peer does not send
close_notify before closing the connection. Previously, it was to return
SSL_ERROR_SYSCALL with errno 0, known since at least OpenSSL 0.9.7, and is
handled gracefully in nginx. Now it returns SSL_ERROR_SSL with a distinct
reason SSL_R_UNEXPECTED_EOF_WHILE_READING ("unexpected eof while reading").
This leads to critical errors seen in nginx within various routines such as
SSL_do_handshake(), SSL_read(), SSL_shutdown(). The behaviour was restored
in OpenSSL 1.1.1f, but presents in OpenSSL 3.0 by default.
Use of the SSL_OP_IGNORE_UNEXPECTED_EOF option added in OpenSSL 3.0 allows
to set a compatible behaviour to return SSL_ERROR_ZERO_RETURN:
https://git.openssl.org/?p=openssl.git;a=commitdiff;h=09b90e0
See for additional details: openssl/openssl#11381
diogoaos
pushed a commit
to diogoaos/nginx
that referenced
this issue
Nov 4, 2021
A new behaviour was introduced in OpenSSL 1.1.1e, when a peer does not send
close_notify before closing the connection. Previously, it was to return
SSL_ERROR_SYSCALL with errno 0, known since at least OpenSSL 0.9.7, and is
handled gracefully in nginx. Now it returns SSL_ERROR_SSL with a distinct
reason SSL_R_UNEXPECTED_EOF_WHILE_READING ("unexpected eof while reading").
This leads to critical errors seen in nginx within various routines such as
SSL_do_handshake(), SSL_read(), SSL_shutdown(). The behaviour was restored
in OpenSSL 1.1.1f, but presents in OpenSSL 3.0 by default.
Use of the SSL_OP_IGNORE_UNEXPECTED_EOF option added in OpenSSL 3.0 allows
to set a compatible behaviour to return SSL_ERROR_ZERO_RETURN:
https://git.openssl.org/?p=openssl.git;a=commitdiff;h=09b90e0
See for additional details: openssl/openssl#11381
nginx-hg-mirror
pushed a commit
to nginx/nginx
that referenced
this issue
Nov 16, 2021
A new behaviour was introduced in OpenSSL 1.1.1e, when a peer does not send
close_notify before closing the connection. Previously, it was to return
SSL_ERROR_SYSCALL with errno 0, known since at least OpenSSL 0.9.7, and is
handled gracefully in nginx. Now it returns SSL_ERROR_SSL with a distinct
reason SSL_R_UNEXPECTED_EOF_WHILE_READING ("unexpected eof while reading").
This leads to critical errors seen in nginx within various routines such as
SSL_do_handshake(), SSL_read(), SSL_shutdown(). The behaviour was restored
in OpenSSL 1.1.1f, but presents in OpenSSL 3.0 by default.
Use of the SSL_OP_IGNORE_UNEXPECTED_EOF option added in OpenSSL 3.0 allows
to set a compatible behaviour to return SSL_ERROR_ZERO_RETURN:
https://git.openssl.org/?p=openssl.git;a=commitdiff;h=09b90e0
See for additional details: openssl/openssl#11381
nginx-hg-mirror
pushed a commit
to nginx/unit
that referenced
this issue
May 12, 2022
A new behaviour was introduced in OpenSSL 1.1.1e, when a peer does not send
close_notify before closing the connection. Previously, it was to return
SSL_ERROR_SYSCALL with errno 0, known since at least OpenSSL 0.9.7, and is
handled gracefully in unitd. Now it returns SSL_ERROR_SSL with a distinct
reason SSL_R_UNEXPECTED_EOF_WHILE_READING ("unexpected eof while reading").
This leads to critical errors seen in nginx within various routines such as
SSL_do_handshake(), SSL_read(), SSL_shutdown(). The behaviour was restored
in OpenSSL 1.1.1f, but presents in OpenSSL 3.0 by default.
Use of the SSL_OP_IGNORE_UNEXPECTED_EOF option added in OpenSSL 3.0 allows
setting a compatible behaviour to return SSL_ERROR_ZERO_RETURN:
https://git.openssl.org/?p=openssl.git;a=commitdiff;h=09b90e0
See for additional details: openssl/openssl#11381
sebres
pushed a commit
to sebres/nginx
that referenced
this issue
May 23, 2022
A new behaviour was introduced in OpenSSL 1.1.1e, when a peer does not send
close_notify before closing the connection. Previously, it was to return
SSL_ERROR_SYSCALL with errno 0, known since at least OpenSSL 0.9.7, and is
handled gracefully in nginx. Now it returns SSL_ERROR_SSL with a distinct
reason SSL_R_UNEXPECTED_EOF_WHILE_READING ("unexpected eof while reading").
This leads to critical errors seen in nginx within various routines such as
SSL_do_handshake(), SSL_read(), SSL_shutdown(). The behaviour was restored
in OpenSSL 1.1.1f, but presents in OpenSSL 3.0 by default.
Use of the SSL_OP_IGNORE_UNEXPECTED_EOF option added in OpenSSL 3.0 allows
to set a compatible behaviour to return SSL_ERROR_ZERO_RETURN:
https://git.openssl.org/?p=openssl.git;a=commitdiff;h=09b90e0
See for additional details: openssl/openssl#11381
I have an issue with connecting to a specific site using Python requests and get this error:
HTTPSConnectionPool(host=’XXXXXXXXX’, port=443): Max retries exceeded with url: / (Caused by SSLError(SSLError(«bad handshake: SysCallError(-1, ‘Unexpected EOF’)»,),))
How can I work around this? (setting verify=False does not make a difference) I’m suspecting the server who’s at fault here as it get an overall rating of F @ ssllabs when I run their test
I am fairly new with Python and requests
my code:
import requests
try:
site = requests.get('https://XXXXXXXXXX', verify=True)
print(site)
except requests.exceptions.RequestException as e:
print(e)
pass
asked Nov 6, 2017 at 17:49
2
Faced with the same error my troubles went away after doing pip install ndg-httpsclient. yum install python-ndg_httpsclient or apt-get install python-ndg-httpsclient (or apt-get install python3-ndg-httpsclient) probably works too.
answered Dec 14, 2017 at 15:14
brynbryn
3,1051 gold badge16 silver badges15 bronze badges
2
The root cause might be this open bug in the requests library: «Session.verify=False ignored when REQUESTS_CA_BUNDLE environment variable is set».
We’ve seen similar issues start all of a sudden on a specific host. It turned out that the env variable was set there recently, which started causing requests to spawn with session.verify not False despite being initialized to False. Once we removed the REQUESTS_CA_BUNDLE environment variable the errors stopped.
answered Jul 22, 2020 at 9:34
2
Set verify = False, it will help:
import requests
try:
site = requests.get('https://XXXXXXXXXX', verify=False)
print(site)
except requests.exceptions.RequestException as e:
print(e)
pass
or try with urllib:
import requests
import urllib.request
import ssl
# Ignore SSL certificate errors
ctx = ssl.create_default_context()
ctx.check_hostname = False
ctx.verify_mode = ssl.CERT_NONE
try:
site =urllib.request.urlopen(url, context=ctx)
print(site.read().decode())
except requests.exceptions.RequestException as e:
print(e)
pass
answered Jul 22, 2020 at 9:39
Roshin RaphelRoshin Raphel
2,5153 gold badges19 silver badges37 bronze badges
I have a brand new Ubuntu 22.04 install with mail system setup broadly as per:
and I get the following errors:
Jun 1 08:07:48 ocean postfix/submission/smtpd[21217]: warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
Jun 1 08:07:51 ocean postfix/submission/smtpd[21222]: warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
Jun 1 08:19:32 ocean postfix/submission/smtpd[21340]: warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
Jun 1 08:41:54 ocean postfix/smtps/smtpd[22197]: warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
185 of them in the last 24 hours and the system isn’t live yet.
To pick one and give some more context:
Jun 1 08:52:58 ocean named[1814]: client @0x7fb35c3fe258 127.0.0.1#59947 (78.211.104.172.in-addr.arpa): query: 78.211.104.172.in-addr.arpa IN PTR +E(0) (127.0.0.1)
Jun 1 08:52:58 ocean named[1814]: client @0x7fb35c3fe258 127.0.0.1#59065 (cloud-scanner-c5ca2208.internet-research-project.net): query: cloud-scanner-c5ca2208.internet-research-project.net IN A +E(0) (127.0.0.1)
Jun 1 08:52:59 ocean postfix/smtpd[22291]: connect from cloud-scanner-c5ca2208.internet-research-project.net[172.104.211.78]
Jun 1 08:52:59 ocean postfix/smtpd[22291]: SSL_accept error from cloud-scanner-c5ca2208.internet-research-project.net[172.104.211.78]: -1
Jun 1 08:52:59 ocean postfix/smtpd[22291]: warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
Jun 1 08:52:59 ocean postfix/smtpd[22291]: lost connection after STARTTLS from cloud-scanner-c5ca2208.internet-research-project.net[172.104.211.78]
Jun 1 08:52:59 ocean postfix/smtpd[22291]: disconnect from cloud-scanner-c5ca2208.internet-research-project.net[172.104.211.78] ehlo=1 starttls=0/1 commands=1/2
Only reference on google I can find is a bug report, with very limited info here:
https://www.mail-archive.com/debian-bugs-dist@lists.debian.org/msg1854063.html
Any help or guidance appreciated.
Thanks
Kevin
asked Jun 1, 2022 at 8:48
Kevin WKevin W
731 gold badge1 silver badge5 bronze badges
1
Well, I had a similar error, but it was related to the postfix message size limit.
I’ve postfix/dovecot/amavis/clamav running on ubuntu 22.04
Problem: Mail with large attachments
Logfile: /var/log/syslog
warning: TLS library problem: error:0A000126:SSL routines::unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
Logfile: /var/log/mail.err
mail dovecot: auth: Error: auth client 0 disconnected with 1 pending requests: EOF
Solution:
- check your limit by «postconf | grep message_size_limit»
- Increase to 50MB by «postconf -e message_size_limit=52428800»
answered Dec 19, 2022 at 19:47
1