Содержание
- An error in computer data is called
- 2. ___________ is the main memory of the computer.
- 3. Which of the following is correct for operating system?
- 4. .VXD represents
- 5. Which group does PIF editor belong?
- 6. Combo box in a dialog box is
- 7. RTF is _____________
- 8. Which of the following better define UNIX?
- 9. Choose the network for the computers that are within 100 to 300 metres :
- 10. Which of the following is sequence storage device?
- 11. An assembler is a
- 12. Who is the father of computer?
- 13. Which of the following is used to manufacture fourth generation computer?
- 14. Choose the result of the expression.
- 15. Can two methods have same name in Java?
- 16. A class that inherits a base class containing virtual function is called
- 17. Which of the following is the scope resolution operator?
- 18. In C++, a function contained within a class is called
- 19. Binary overloaded operators are passed by __________ arguments
- 20. CPU stands for
- 21. ___________ is a single integrated circuit.
- 22. e-commerce is an application of _____________
- 23. Virus is a ___________
- 24. For what logic gate, the output is complement of the input?
- 25. __________ uses the structured programming approach.
- 26. Which of the following has the single bus structure?
- 27 . _________ is the heart of computer.
- 28 . Which of the following languages is frequently used to design web pages?
- 29. Which of the following is the fastest printer?
- 30. Which of the following is a virus?
- 31. A byte consists of
- 32. A 16 bit computer word consists of _________ bytes.
- 33. Memory addresses are calculated by an algorithm which is widely known as
- 34. A microprocessor consists of
- 35. Secondary memory device is
- 36. The computer memory which is empty is
- 37. A half byte is known as
- 38. An error in computer data is called ___________
- 39. Which of the following performs the OR, XOR & AND functions?
- 40. Which of the following is correct for Logic Gate?
- 41. Nibble contains
- 42. The means of storing a large amount of data outside the main memory is
- 43. A binary object which can have a value of 0 or 1 is called.
- 44. The smallest unit in the computer which represents information is
- 45. The octat number 110 in hexadecimal system is written as
- 46. The binary number 110011 in octal system is represented as
- 47. The decimal equivalent of hexadecimal number A2C is
- 48. ____________ is currently the smallest and least costly computer.
- 49. A special storage register associated with the arithmetic logic unit (ALU) is
- 50. Minicomputer manufactured today are more powerful than ____________
- ANSWER :
- What are Error-Detecting Codes?
- Features of Error Detecting Codes
- Error Detection Techniques
- Parity Check
- Checksum
- Cyclic Redundancy Check (CRC)
- Error Detection and Correction in Data link Layer
- Errors
- Types of Errors
- Error Control
- Error Detection Techniques
- Parity Check
- Checksum
- Cyclic Redundancy Check (CRC)
- Error Correction Techniques
An error in computer data is called
a.) An operating environment
b.) An operating system
c.) An interface
d.) Hardware
2. ___________ is the main memory of the computer.
a.) ERAM
b.) ROM
c.) RAM
d.) EPROM
3. Which of the following is correct for operating system?
a.) OS helps other programs run
b.) OS recovers lost data
c.) OS helps in resource management
d.) None
4. .VXD represents
a.) Picture file
b.) Text file
c.) Device drivers
d.) Image file
5. Which group does PIF editor belong?
a.) Games
b.) Accessories
c.) Main
d.) None
6. Combo box in a dialog box is
a.) A combination of text box and list box
b.) A list box
c.) A combination of list box and check box
d.) None
7. RTF is _____________
a.) Rich text format
b.) Rich text fonts
c.) Real time fonts
d.) Real time files
8. Which of the following better define UNIX?
a.) Real time sharing system
b.) Batch processing operating system
c.) Time sharing operating system
d.) Memory sharing operating system
9. Choose the network for the computers that are within 100 to 300 metres :
a.) LAN
b.) WAN
c.) WWW
d.) None
10. Which of the following is sequence storage device?
a.) Magnetic tape
b.) Paper tape
c.) Magnetic disk
d.) a.) and b.)
11. An assembler is a
a.) Program
b.) Hardware
c.) Language
d.) Error
12. Who is the father of computer?
a.) Charles Babbage
b.) Bill gates
c.) Steve jobs
d.) Hollerith
13. Which of the following is used to manufacture fourth generation computer?
a.) Vacuum Tubes
b.) IC-chips
c.) Transistors
d.) Micro processors
14. Choose the result of the expression.
15. Can two methods have same name in Java?
16. A class that inherits a base class containing virtual function is called
a.) Derived
b.) Polymorphic
c.) Virtual
d.) Base
17. Which of the following is the scope resolution operator?
18. In C++, a function contained within a class is called
a.) A member function
b.) An operator
c.) A class function
d.) A method
19. Binary overloaded operators are passed by __________ arguments
a.) Two
b.) One
c.) Three
d.) Four
20. CPU stands for
a.) Central programming unit
b.) Central program unit
c.) Central processing unit
d.) None
21. ___________ is a single integrated circuit.
a.) Chip
b.) CPU
c.) Gate
d.) Motherboard
22. e-commerce is an application of _____________
a.) LAN
b.) WAN
c.) Internet
d.) Intranet
23. Virus is a ___________
a.) Software
b.) Hardware
c.) Chip
d.) Device driver
24. For what logic gate, the output is complement of the input?
25. __________ uses the structured programming approach.
a.) c
b.) Java
c.) Basic
d.) Visual basic
26. Which of the following has the single bus structure?
a.) Parallel systems
b.) Super computer
c.) Mainframes
d.) Mini and micro computers
27 . _________ is the heart of computer.
a.) CPU
b.) Memory
c.) I/O unit
d.) Disks
28 . Which of the following languages is frequently used to design web pages?
a.) Java
b.) C
c.) Cobol
d.) Pascal
29. Which of the following is the fastest printer?
a.) Laser
b.) Int jet
c.) Dot-matrix
d.) Plotter
30. Which of the following is a virus?
a.) Worm
b.) Trojan horse
c.) File Infector
d.) All of the above
31. A byte consists of
a.) 2 bits
b.) 4 bits
c.) 8 bits
d.) 10 bits
32. A 16 bit computer word consists of _________ bytes.
33. Memory addresses are calculated by an algorithm which is widely known as
a.) Searching
b.) Sorting
c.) Hashing
d.) None
34. A microprocessor consists of
a.) Hardware and software
b.) Memory and CPU
c.) ALU and control unit
d.) None of the above
35. Secondary memory device is
a.) ALU
b.) CPU
c.) Floppy disk
d.) Mouse
36. The computer memory which is empty is
a.) RAM
b.) ROM
c.) Floppy disk
d.) Mouse
37. A half byte is known as
a.) Bit
b.) Data
c.) Nibble
d.) None
38. An error in computer data is called ___________
a.) Bit
b.) Bug
c.) Byte
d.) Chip
39. Which of the following performs the OR, XOR & AND functions?
a.) Memory
b.) Register Unit
c.) ALU
d.) Control unit
40. Which of the following is correct for Logic Gate?
a.) Makes logical decisions
b.) Allows current only in one direction
c.) Allows current in both the direction
d.) Is based on ordinary algebra
41. Nibble contains
a.) 16 bits
b.) 8 bits
c.) 32 bits
d.) 4 bits
42. The means of storing a large amount of data outside the main memory is
a.) Accumulator
b.) Primary store
c.) Auxiliary store
d.) Secondary store
43. A binary object which can have a value of 0 or 1 is called.
a.) Byte
b.) Bit
c.) Decimal
d.) Octal
44. The smallest unit in the computer which represents information is
a.) Byte
b.) Bit
c.) Character
d.) Digit
45. The octat number 110 in hexadecimal system is written as
46. The binary number 110011 in octal system is represented as
47. The decimal equivalent of hexadecimal number A2C is
a.) 2814
b.) 2674
c.) 2604
d.) 2786
48. ____________ is currently the smallest and least costly computer.
a.) Microcomputer
b.) Supercomputer
c.) Mainframes
d.) None of the above
49. A special storage register associated with the arithmetic logic unit (ALU) is
a.) CPU
b.) Accumulator
c.) Primary store
d.) Auxiliary store
50. Minicomputer manufactured today are more powerful than ____________
a.) Mainframes
b.) Supercomputer
c.) Microcomputer
d.) None of the above
ANSWER :
1. b
2. c
3. a
4. c
5. c
6. a
7. a
8. c
9. b
10. d
11. a
12. a
13. b
14. a
15. b
16. b
17. a
18. a
19. a
20. c
21. a
22. c
23. a
24. a
25. b
26. d
27. a
28. a
29. a
30. d
31. c
32. a
33. c
34. c
35. c
36. b
37. c
38. b
39. c
40. b
41. d
42. c
43. b
44. b
45. a
46. a
47. c
48. a
49. b
50. a
Источник
What are Error-Detecting Codes?
Error-detecting codes are a sequence of numbers generated by specific procedures for detecting errors in data that has been transmitted over computer networks.
When bits are transmitted over the computer network, they are subject to get corrupted due to interference and network problems. The corrupted bits leads to spurious data being received by the receiver and are called errors.
Error – detecting codes ensures messages to be encoded before they are sent over noisy channels. The encoding is done in a manner so that the decoder at the receiving end can detect whether there are errors in the incoming signal with high probability of success.
Features of Error Detecting Codes
Error detecting codes are adopted when backward error correction techniques are used for reliable data transmission. In this method, the receiver sends a feedback message to the sender to inform whether an error-free message has been received or not. If there are errors, then the sender retransmits the message.
Error-detecting codes are usually block codes, where the message is divided into fixed-sized blocks of bits, to which redundant bits are added for error detection.
Error detection involves checking whether any error has occurred or not. The number of error bits and the type of error does not matter.
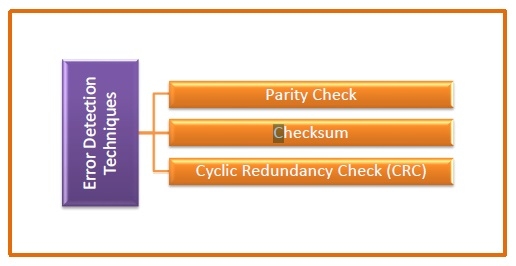
Error Detection Techniques
There are three main techniques for detecting errors
Parity Check
Parity check is done by adding an extra bit, called parity bit to the data to make number of 1s either even in case of even parity, or odd in case of odd parity.
While creating a frame, the sender counts the number of 1s in it and adds the parity bit in following way
In case of even parity: If number of 1s is even then parity bit value is 0. If number of 1s is odd then parity bit value is 1.
In case of odd parity: If number of 1s is odd then parity bit value is 0. If number of 1s is even then parity bit value is 1.
On receiving a frame, the receiver counts the number of 1s in it. In case of even parity check, if the count of 1s is even, the frame is accepted, otherwise it is rejected. Similar rule is adopted for odd parity check.
Parity check is suitable for single bit error detection only.
Checksum
In this error detection scheme, the following procedure is applied
Data is divided into fixed sized frames or segments.
The sender adds the segments using 1’s complement arithmetic to get the sum. It then complements the sum to get the checksum and sends it along with the data frames.
The receiver adds the incoming segments along with the checksum using 1’s complement arithmetic to get the sum and then complements it.
If the result is zero, the received frames are accepted; otherwise they are discarded.
Cyclic Redundancy Check (CRC)
Cyclic Redundancy Check (CRC) involves binary division of the data bits being sent by a predetermined divisor agreed upon by the communicating system. The divisor is generated using polynomials.
Here, the sender performs binary division of the data segment by the divisor. It then appends the remainder called CRC bits to the end of data segment. This makes the resulting data unit exactly divisible by the divisor.
The receiver divides the incoming data unit by the divisor. If there is no remainder, the data unit is assumed to be correct and is accepted. Otherwise, it is understood that the data is corrupted and is therefore rejected.
Источник
Error Detection and Correction in Data link Layer
Data-link layer uses error control techniques to ensure that frames, i.e. bit streams of data, are transmitted from the source to the destination with a certain extent of accuracy.
Errors
When bits are transmitted over the computer network, they are subject to get corrupted due to interference and network problems. The corrupted bits leads to spurious data being received by the destination and are called errors.
Types of Errors
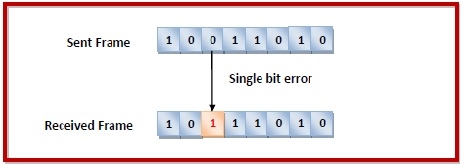
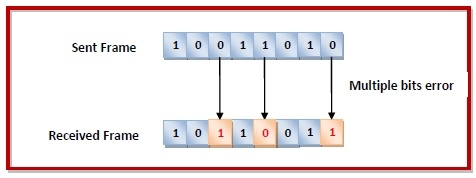
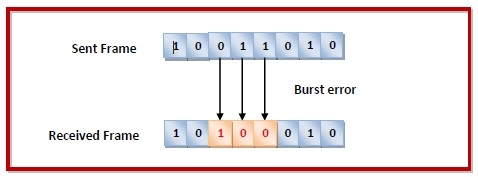
Errors can be of three types, namely single bit errors, multiple bit errors, and burst errors.
Single bit error − In the received frame, only one bit has been corrupted, i.e. either changed from 0 to 1 or from 1 to 0.
Multiple bits error − In the received frame, more than one bits are corrupted.
Burst error − In the received frame, more than one consecutive bits are corrupted.
Error Control
Error control can be done in two ways
Error detection − Error detection involves checking whether any error has occurred or not. The number of error bits and the type of error does not matter.
Error correction − Error correction involves ascertaining the exact number of bits that has been corrupted and the location of the corrupted bits.
For both error detection and error correction, the sender needs to send some additional bits along with the data bits. The receiver performs necessary checks based upon the additional redundant bits. If it finds that the data is free from errors, it removes the redundant bits before passing the message to the upper layers.
Error Detection Techniques
There are three main techniques for detecting errors in frames: Parity Check, Checksum and Cyclic Redundancy Check (CRC).
Parity Check
The parity check is done by adding an extra bit, called parity bit to the data to make a number of 1s either even in case of even parity or odd in case of odd parity.
While creating a frame, the sender counts the number of 1s in it and adds the parity bit in the following way
In case of even parity: If a number of 1s is even then parity bit value is 0. If the number of 1s is odd then parity bit value is 1.
In case of odd parity: If a number of 1s is odd then parity bit value is 0. If a number of 1s is even then parity bit value is 1.
On receiving a frame, the receiver counts the number of 1s in it. In case of even parity check, if the count of 1s is even, the frame is accepted, otherwise, it is rejected. A similar rule is adopted for odd parity check.
The parity check is suitable for single bit error detection only.
Checksum
In this error detection scheme, the following procedure is applied
Data is divided into fixed sized frames or segments.
The sender adds the segments using 1’s complement arithmetic to get the sum. It then complements the sum to get the checksum and sends it along with the data frames.
The receiver adds the incoming segments along with the checksum using 1’s complement arithmetic to get the sum and then complements it.
If the result is zero, the received frames are accepted; otherwise, they are discarded.
Cyclic Redundancy Check (CRC)
Cyclic Redundancy Check (CRC) involves binary division of the data bits being sent by a predetermined divisor agreed upon by the communicating system. The divisor is generated using polynomials.
Here, the sender performs binary division of the data segment by the divisor. It then appends the remainder called CRC bits to the end of the data segment. This makes the resulting data unit exactly divisible by the divisor.
The receiver divides the incoming data unit by the divisor. If there is no remainder, the data unit is assumed to be correct and is accepted. Otherwise, it is understood that the data is corrupted and is therefore rejected.
Error Correction Techniques
Error correction techniques find out the exact number of bits that have been corrupted and as well as their locations. There are two principle ways
Backward Error Correction (Retransmission) − If the receiver detects an error in the incoming frame, it requests the sender to retransmit the frame. It is a relatively simple technique. But it can be efficiently used only where retransmitting is not expensive as in fiber optics and the time for retransmission is low relative to the requirements of the application.
Forward Error Correction − If the receiver detects some error in the incoming frame, it executes error-correcting code that generates the actual frame. This saves bandwidth required for retransmission. It is inevitable in real-time systems. However, if there are too many errors, the frames need to be retransmitted.
The four main error correction codes are
- Hamming Codes
- Binary Convolution Code
- Reed – Solomon Code
- Low-Density Parity-Check Code
Источник
► MCQ Exam ON : Computer Fundamentals
An error in computer data is called
| 1) |
A) Chip |
|
| 2) |
B) Bug |
|
| 3) |
C) CPU |
|
| 4) |
D) Storage device |
|
| 5) | NULL |
Complaint Here As Incorrect Question / Answer
171 .
An error in computer data is called
172 .
Which of the following translate back from machine code something resembling the source language
| A. | Compiler | B. | Decompiler |
| C. | Interpreter | D. | Assembler |
173 .
Who developed a mechanical device in the 17th century that could add, subtract, multiply, divide and find square roots?
| A. | Pascal | B. | Napier |
| C. | Leibnitz | D. | Babbage |
174 .
A six — digit card field used for postal ZIP codes is defined as
| A. | An alphanumeric field |
| B. | A numeric field |
| C. | A letter field |
| D. | A alphabetic field |
175 .
A hand-held device for optically reading bar codes on goods, labels & shelves is
| A. | Wand | B. | Light pen |
| C. | Mouse | D. | Touch tablet |
Home >
GK > Computer knowledge
1. Windows is ______________
a.) An operating environment
b.) An operating system
c.) An interface
d.) Hardware
2. ___________ is the main memory of the computer.
a.) ERAM
b.) ROM
c.) RAM
d.) EPROM
3. Which of the following is correct for operating system?
a.) OS helps other programs run
b.) OS recovers lost data
c.) OS helps in resource management
d.) None
4. .VXD represents
a.) Picture file
b.) Text file
c.) Device drivers
d.) Image file
5. Which group does PIF editor belong?
a.) Games
b.) Accessories
c.) Main
d.) None
6. Combo box in a dialog box is
a.) A combination of text box and list box
b.) A list box
c.) A combination of list box and check box
d.) None
7. RTF is _____________
a.) Rich text format
b.) Rich text fonts
c.) Real time fonts
d.) Real time files
8. Which of the following better define UNIX?
a.) Real time sharing system
b.) Batch processing operating system
c.) Time sharing operating system
d.) Memory sharing operating system
9. Choose the network for the computers that are within 100 to 300 metres :
a.) LAN
b.) WAN
c.) WWW
d.) None
10. Which of the following is sequence storage device?
a.) Magnetic tape
b.) Paper tape
c.) Magnetic disk
d.) a.) and b.)
11. An assembler is a
a.) Program
b.) Hardware
c.) Language
d.) Error
12. Who is the father of computer?
a.) Charles Babbage
b.) Bill gates
c.) Steve jobs
d.) Hollerith
13. Which of the following is used to manufacture fourth generation computer?
a.) Vacuum Tubes
b.) IC-chips
c.) Transistors
d.) Micro processors
14. Choose the result of the expression.
a.) 1
b.) 2
c.) 3
d.) 4
15. Can two methods have same name in Java?
a.) Yes
b.) No
16. A class that inherits a base class containing virtual function is called
a.) Derived
b.) Polymorphic
c.) Virtual
d.) Base
17. Which of the following is the scope resolution operator?
a.) ::
b.) ;
c.) <<
d.) >>
18. In C++, a function contained within a class is called
a.) A member function
b.) An operator
c.) A class function
d.) A method
19. Binary overloaded operators are passed by __________ arguments
a.) Two
b.) One
c.) Three
d.) Four
20. CPU stands for
a.) Central programming unit
b.) Central program unit
c.) Central processing unit
d.) None
21. ___________ is a single integrated circuit.
a.) Chip
b.) CPU
c.) Gate
d.) Motherboard
22. e-commerce is an application of _____________
a.) LAN
b.) WAN
c.) Internet
d.) Intranet
23. Virus is a ___________
a.) Software
b.) Hardware
c.) Chip
d.) Device driver
24. For what logic gate, the output is complement of the input?
a.) NOT
b.) AND
c.) OR
d.) XOR
25. __________ uses the structured programming approach.
a.) c
b.) Java
c.) Basic
d.) Visual basic
26. Which of the following has the single bus structure?
a.) Parallel systems
b.) Super computer
c.) Mainframes
d.) Mini and micro computers
27 . _________ is the heart of computer.
a.) CPU
b.) Memory
c.) I/O unit
d.) Disks
28 . Which of the following languages is frequently used to design web pages?
a.) Java
b.) C
c.) Cobol
d.) Pascal
29. Which of the following is the fastest printer?
a.) Laser
b.) Int jet
c.) Dot-matrix
d.) Plotter
30. Which of the following is a virus?
a.) Worm
b.) Trojan horse
c.) File Infector
d.) All of the above
31. A byte consists of
a.) 2 bits
b.) 4 bits
c.) 8 bits
d.) 10 bits
32. A 16 bit computer word consists of _________ bytes.
a.) 16
b.) 64
c.) 32
d.) 54
33. Memory addresses are calculated by an algorithm which is widely known as
a.) Searching
b.) Sorting
c.) Hashing
d.) None
34. A microprocessor consists of
a.) Hardware and software
b.) Memory and CPU
c.) ALU and control unit
d.) None of the above
35. Secondary memory device is
a.) ALU
b.) CPU
c.) Floppy disk
d.) Mouse
36. The computer memory which is empty is
a.) RAM
b.) ROM
c.) Floppy disk
d.) Mouse
37. A half byte is known as
a.) Bit
b.) Data
c.) Nibble
d.) None
38. An error in computer data is called ___________
a.) Bit
b.) Bug
c.) Byte
d.) Chip
39. Which of the following performs the OR, XOR & AND functions?
a.) Memory
b.) Register Unit
c.) ALU
d.) Control unit
40. Which of the following is correct for Logic Gate?
a.) Makes logical decisions
b.) Allows current only in one direction
c.) Allows current in both the direction
d.) Is based on ordinary algebra
41. Nibble contains
a.) 16 bits
b.) 8 bits
c.) 32 bits
d.) 4 bits
42. The means of storing a large amount of data outside the main memory is
a.) Accumulator
b.) Primary store
c.) Auxiliary store
d.) Secondary store
43. A binary object which can have a value of 0 or 1 is called.
a.) Byte
b.) Bit
c.) Decimal
d.) Octal
44. The smallest unit in the computer which represents information is
a.) Byte
b.) Bit
c.) Character
d.) Digit
45. The octat number 110 in hexadecimal system is written as
a.) 49
b.) 52
c.) 63
d.) 73
46. The binary number 110011 in octal system is represented as
a.) 63
b.) 36
c.) 51
d.) 45
47. The decimal equivalent of hexadecimal number A2C is
a.) 2814
b.) 2674
c.) 2604
d.) 2786
48. ____________ is currently the smallest and least costly computer.
a.) Microcomputer
b.) Supercomputer
c.) Mainframes
d.) None of the above
49. A special storage register associated with the arithmetic logic unit (ALU)
is
a.) CPU
b.) Accumulator
c.) Primary store
d.) Auxiliary store
50. Minicomputer manufactured today are more powerful than ____________
a.) Mainframes
b.) Supercomputer
c.) Microcomputer
d.) None of the above
ANSWER :
1. b
2. c
3. a
4. c
5. c
6. a
7. a
8. c
9. b
10. d
11. a
12. a
13. b
14. a
15. b
16. b
17. a
18. a
19. a
20. c
21. a
22. c
23. a
24. a
25. b
26. d
27. a
28. a
29. a
30. d
31. c
32. a
33. c
34. c
35. c
36. b
37. c
38. b
39. c
40. b
41. d
42. c
43. b
44. b
45. a
46. a
47. c
48. a
49. b
50. a