I recently clean installed Debian 9 on two machines, a desktop and a laptop. I had a problem updating the repositories on both machines. I did eventually get the desktop to update properly, but the laptop is still ‘broken’. Perhaps relevant to the problem is that I did a Net Install on both computers.
My laptop is an old Dell 1420 with an Intel Centrino CPU. Everything else works.
Here’s what I get when I ‘sudo apt-get update’ on my laptop:
Code: Select all
Hit:1 http://security.debian.org stretch/updates InRelease
Ign:2 http://ftp.us.debian.org/debian stretch InRelease
Hit:3 https://repo.skype.com/deb stable InRelease
Hit:4 http://ftp.us.debian.org/debian stretch-updates InRelease
Err:1 http://security.debian.org stretch/updates InRelease
The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 9D6D8F6BC857C906 NO_PUBKEY 8B48AD6246925553
Ign:5 http://ftp.us.debian.org/debian stretch/updates InRelease
Ign:7 http://ftp.us.debian.org/debian stretch/updates Release
Err:4 http://ftp.us.debian.org/debian stretch-updates InRelease
The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
Get:6 http://ftp.us.debian.org/debian stretch Release [118 kB]
Ign:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Ign:9 http://ftp.us.debian.org/debian stretch/updates/non-free Sources
Ign:10 http://ftp.us.debian.org/debian stretch/updates/contrib Sources
Get:11 http://ftp.us.debian.org/debian stretch Release.gpg [2,373 B]
Ign:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Ign:11 http://ftp.us.debian.org/debian stretch Release.gpg
Ign:9 http://ftp.us.debian.org/debian stretch/updates/non-free Sources
Ign:10 http://ftp.us.debian.org/debian stretch/updates/contrib Sources
Get:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Ign:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Get:13 http://ftp.us.debian.org/debian stretch/contrib Sources [44.7 kB]
Get:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages [7,095 kB]
Ign:9 http://ftp.us.debian.org/debian stretch/updates/non-free Sources
Ign:10 http://ftp.us.debian.org/debian stretch/updates/contrib Sources
Ign:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Hit:13 http://ftp.us.debian.org/debian stretch/contrib Sources
Hit:15 http://ftp.us.debian.org/debian stretch/main Sources
Hit:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Hit:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Hit:19 http://ftp.us.debian.org/debian stretch/main Translation-en
Ign:13 http://ftp.us.debian.org/debian stretch/contrib Sources
Ign:15 http://ftp.us.debian.org/debian stretch/main Sources
Ign:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Ign:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Ign:19 http://ftp.us.debian.org/debian stretch/main Translation-en
Hit:20 http://ftp.us.debian.org/debian stretch/main amd64 DEP-11 Metadata
Hit:21 http://ftp.us.debian.org/debian stretch/contrib amd64 Packages
Hit:22 http://ftp.us.debian.org/debian stretch/contrib Translation-en
Hit:23 http://ftp.us.debian.org/debian stretch/contrib amd64 DEP-11 Metadata
Ign:20 http://ftp.us.debian.org/debian stretch/main amd64 DEP-11 Metadata
Ign:21 http://ftp.us.debian.org/debian stretch/contrib amd64 Packages
Ign:22 http://ftp.us.debian.org/debian stretch/contrib Translation-en
Ign:23 http://ftp.us.debian.org/debian stretch/contrib amd64 DEP-11 Metadata
Hit:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages
Hit:25 http://ftp.us.debian.org/debian stretch/non-free Translation-en
Hit:26 http://ftp.us.debian.org/debian stretch/non-free amd64 DEP-11 Metadata
Ign:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages
Ign:25 http://ftp.us.debian.org/debian stretch/non-free Translation-en
Ign:26 http://ftp.us.debian.org/debian stretch/non-free amd64 DEP-11 Metadata
Ign:9 http://ftp.us.debian.org/debian stretch/updates/non-free Sources
Ign:10 http://ftp.us.debian.org/debian stretch/updates/contrib Sources
Ign:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
Ign:9 http://ftp.us.debian.org/debian stretch/updates/non-free Sources
Ign:10 http://ftp.us.debian.org/debian stretch/updates/contrib Sources
Err:8 http://ftp.us.debian.org/debian stretch/updates/main Sources
404 Not Found [IP: 64.50.233.100 80]
Hit:13 http://ftp.us.debian.org/debian stretch/contrib Sources
Hit:15 http://ftp.us.debian.org/debian stretch/main Sources
Hit:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Hit:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Hit:19 http://ftp.us.debian.org/debian stretch/main Translation-en
Hit:20 http://ftp.us.debian.org/debian stretch/main amd64 DEP-11 Metadata
Hit:21 http://ftp.us.debian.org/debian stretch/contrib amd64 Packages
Hit:22 http://ftp.us.debian.org/debian stretch/contrib Translation-en
Ign:13 http://ftp.us.debian.org/debian stretch/contrib Sources
Ign:15 http://ftp.us.debian.org/debian stretch/main Sources
Ign:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Ign:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Ign:19 http://ftp.us.debian.org/debian stretch/main Translation-en
Ign:20 http://ftp.us.debian.org/debian stretch/main amd64 DEP-11 Metadata
Ign:21 http://ftp.us.debian.org/debian stretch/contrib amd64 Packages
Ign:22 http://ftp.us.debian.org/debian stretch/contrib Translation-en
Hit:23 http://ftp.us.debian.org/debian stretch/contrib amd64 DEP-11 Metadata
Ign:23 http://ftp.us.debian.org/debian stretch/contrib amd64 DEP-11 Metadata
Get:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages [77.9 kB]
Hit:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages
Hit:25 http://ftp.us.debian.org/debian stretch/non-free Translation-en
Hit:26 http://ftp.us.debian.org/debian stretch/non-free amd64 DEP-11 Metadata
Hit:13 http://ftp.us.debian.org/debian stretch/contrib Sources
Ign:15 http://ftp.us.debian.org/debian stretch/main Sources
Ign:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Ign:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages
Ign:25 http://ftp.us.debian.org/debian stretch/non-free Translation-en
Ign:26 http://ftp.us.debian.org/debian stretch/non-free amd64 DEP-11 Metadata
Ign:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Err:19 http://ftp.us.debian.org/debian stretch/main Translation-en
BZ2_bzread: /var/lib/apt/lists/partial/ftp.us.debian.org_debian_dists_stretch_main_i18n_Translation-en.bz2 Read error (-5: DATA_ERROR_MAGIC)
Hit:21 http://ftp.us.debian.org/debian stretch/contrib amd64 Packages
Ign:22 http://ftp.us.debian.org/debian stretch/contrib Translation-en
Hit:23 http://ftp.us.debian.org/debian stretch/contrib amd64 DEP-11 Metadata
Ign:15 http://ftp.us.debian.org/debian stretch/main Sources
Ign:16 http://ftp.us.debian.org/debian stretch/non-free Sources
Hit:24 http://ftp.us.debian.org/debian stretch/non-free amd64 Packages
Ign:25 http://ftp.us.debian.org/debian stretch/non-free Translation-en
Hit:26 http://ftp.us.debian.org/debian stretch/non-free amd64 DEP-11 Metadata
Ign:17 http://ftp.us.debian.org/debian stretch/main amd64 Packages
Fetched 120 kB in 6s (17.4 kB/s)
Reading package lists... Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://security.debian.org stretch/updates InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 9D6D8F6BC857C906 NO_PUBKEY 8B48AD6246925553
W: The repository 'http://ftp.us.debian.org/debian stretch/updates Release' does not have a Release file.
N: Data from such a repository can't be authenticated and is therefore potentially dangerous to use.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://ftp.us.debian.org/debian stretch-updates InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
W: GPG error: http://ftp.us.debian.org/debian stretch Release: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010 NO_PUBKEY EF0F382A1A7B6500
W: The repository 'http://ftp.us.debian.org/debian stretch Release' is not signed.
N: Data from such a repository can't be authenticated and is therefore potentially dangerous to use.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: Failed to fetch http://ftp.us.debian.org/debian/dists/stretch-updates/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
W: Failed to fetch http://security.debian.org/dists/stretch/updates/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 9D6D8F6BC857C906 NO_PUBKEY 8B48AD6246925553
E: Failed to fetch http://ftp.us.debian.org/debian/dists/stretch/updates/main/source/Sources 404 Not Found [IP: 64.50.233.100 80]
E: Failed to fetch http://ftp.us.debian.org/debian/dists/stretch/main/i18n/Translation-en BZ2_bzread: /var/lib/apt/lists/partial/ftp.us.debian.org_debian_dists_stretch_main_i18n_Translation-en.bz2 Read error (-5: DATA_ERROR_MAGIC)
W: Some index files failed to download. They have been ignored, or old ones used instead.
Here’s what I’ve tried so far:
1. I read the ‘SecureApt’ material on the Debian Wiki. Based on that material, I searched for the missing keys, found them and put them in my gpg keyring. But that was wasted work, because I found that the same keys were already present in the ‘apt-key list’. So I did not export them to ‘apt-key’. It appears as though the keys are present and just not being recognized by the repo servers.
2. I checked the file sources.list multiple times and changed the entries to conform with what I found on the Debian Wiki. No joy.
Here’s my sources.list file contents:
Code: Select all
deb http://ftp.us.debian.org/debian/ stretch main contrib non-free
deb-src http://ftp.us.debian.org/debian/ stretch main contrib non-free
deb http://ftp.us.debian.org/debian/ stretch-updates main contrib non-free
deb-src http://ftp.us.debian.org/debian/ stretch-updates main contrib non-free
deb http://security.debian.org/ stretch/updates main contrib non-free
deb-src http://ftp.us.debian.org/debian/ stretch/updates main contrib non-free
3. I deleted the ‘lists’ subdirectory in /var/lib/apt/ and allowed the update process to reform the information.
4. I found the permissions for the file trusted.gpg were ‘0600’ and I set them to ‘0644’, thinking that maybe this was a permission issue.
Like I stated, I did solve this on my desktop machine (and old AMD dual core) but can’t figure out what I did that worked. I’ll take notes next time.
I am reluctant to uninstall and then reinstall the Debian Archrive Keyring.
Thanks in advance.
the server I work on is a Debian 9.13 OS and «mysql Ver 14.14 Distrib 5.7.34,».
I tried downloading package information from all configured sources with the following command:
sudo apt update
then I faced to the following error:
Hit:1 http://security.debian.org stretch/updates InRelease
Hit:2 http://packages.cloud.google.com/apt google-cloud-monitoring-stretch-all InRelease
Hit:3 http://packages.cloud.google.com/apt cloud-sdk-stretch InRelease
Hit:4 http://packages.cloud.google.com/apt google-compute-engine-stretch-stable InRelease
Ign:5 http://deb.debian.org/debian stretch InRelease
Hit:6 http://repo.mysql.com/apt/debian stretch InRelease
Hit:7 http://packages.cloud.google.com/apt google-cloud-packages-archive-keyring-stretch InRelease
Hit:8 http://deb.debian.org/debian stretch-updates InRelease
Hit:9 https://packages.cloud.google.com/apt google-cloud-logging-stretch-all InRelease
Hit:10 http://deb.debian.org/debian stretch-backports InRelease
Hit:11 http://deb.debian.org/debian stretch Release
Get:12 https://packages.sury.org/php stretch InRelease [6,839 B]
Err:6 http://repo.mysql.com/apt/debian stretch InRelease
The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
Err:12 https://packages.sury.org/php stretch InRelease
The following signatures were invalid: EXPKEYSIG B188E2B695BD4743 DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
Fetched 6,839 B in 1s (5,504 B/s)
Reading package lists... Done
Building dependency tree
Reading state information... Done
10 packages can be upgraded. Run 'apt list --upgradable' to see them.
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://repo.mysql.com/apt/debian stretch InRelease: The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://packages.sury.org/php stretch InRelease: The following signatures were invalid: EXPKEYSIG B188E2B695BD4743 DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
W: Failed to fetch http://repo.mysql.com/apt/debian/dists/stretch/InRelease The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
W: Failed to fetch https://packages.sury.org/php/dists/stretch/InRelease The following signatures were invalid: EXPKEYSIG B188E2B695BD4743 DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
W: Some index files failed to download. They have been ignored, or old ones used instead.
then for fixing the issue of expired signatures I did a long journey, and faced to some problems , so I thought maybe I did something wrong, so I explain the setps I followed in details.
after reseacrh I conculded to update expired keys as the following:
sudo apt-key list
then I saw this:
/etc/apt/trusted.gpg
--------------------
pub dsa1024 2003-02-03 [SCA] [expired: 2022-02-16]
A4A9 4068 76FC BD3C 4567 70C8 8C71 8D3B 5072 E1F5
uid [ expired] MySQL Release Engineering <mysql-build@oss.oracle.com>
pub rsa3072 2019-03-18 [SC] [expired: 2021-03-17]
1505 8500 A023 5D97 F5D1 0063 B188 E2B6 95BD 4743
uid [ expired] DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
/etc/apt/trusted.gpg.d/debian-archive-bullseye-automatic.gpg
------------------------------------------------------------
pub rsa4096 2021-01-17 [SC] [expires: 2029-01-15]
1F89 983E 0081 FDE0 18F3 CC96 73A4 F27B 8DD4 7936
uid [ unknown] Debian Archive Automatic Signing Key (11/bullseye) <ftpmaster@debian.org>
sub rsa4096 2021-01-17 [S] [expires: 2029-01-15]
/etc/apt/trusted.gpg.d/debian-archive-bullseye-security-automatic.gpg
---------------------------------------------------------------------
pub rsa4096 2021-01-17 [SC] [expires: 2029-01-15]
AC53 0D52 0F2F 3269 F5E9 8313 A484 4904 4AAD 5C5D
uid [ unknown] Debian Security Archive Automatic Signing Key (11/bullseye) <ftpmaster@debian.org>
sub rsa4096 2021-01-17 [S] [expires: 2029-01-15]
/etc/apt/trusted.gpg.d/debian-archive-bullseye-stable.gpg
---------------------------------------------------------
pub rsa4096 2021-02-13 [SC] [expires: 2029-02-11]
A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793
uid [ unknown] Debian Stable Release Key (11/bullseye) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-buster-automatic.gpg
----------------------------------------------------------
pub rsa4096 2019-04-14 [SC] [expires: 2027-04-12]
80D1 5823 B7FD 1561 F9F7 BCDD DC30 D7C2 3CBB ABEE
uid [ unknown] Debian Archive Automatic Signing Key (10/buster) <ftpmaster@debian.org>
sub rsa4096 2019-04-14 [S] [expires: 2027-04-12]
/etc/apt/trusted.gpg.d/debian-archive-buster-security-automatic.gpg
-------------------------------------------------------------------
pub rsa4096 2019-04-14 [SC] [expires: 2027-04-12]
5E61 B217 265D A980 7A23 C5FF 4DFA B270 CAA9 6DFA
uid [ unknown] Debian Security Archive Automatic Signing Key (10/buster) <ftpmaster@debian.org>
sub rsa4096 2019-04-14 [S] [expires: 2027-04-12]
/etc/apt/trusted.gpg.d/debian-archive-buster-stable.gpg
-------------------------------------------------------
pub rsa4096 2019-02-05 [SC] [expires: 2027-02-03]
6D33 866E DD8F FA41 C014 3AED DCC9 EFBF 77E1 1517
uid [ unknown] Debian Stable Release Key (10/buster) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg
----------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
126C 0D24 BD8A 2942 CC7D F8AC 7638 D044 2B90 D010
uid [ unknown] Debian Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg
-------------------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
D211 6914 1CEC D440 F2EB 8DDA 9D6D 8F6B C857 C906
uid [ unknown] Debian Security Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-stable.gpg
-------------------------------------------------------
pub rsa4096 2013-08-17 [SC] [expired: 2021-08-15]
75DD C3C4 A499 F1A1 8CB5 F3C8 CBF8 D6FD 518E 17E1
uid [ expired] Jessie Stable Release Key <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-stretch-automatic.gpg
-----------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
E1CF 20DD FFE4 B89E 8026 58F1 E0B1 1894 F66A EC98
uid [ unknown] Debian Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-security-automatic.gpg
--------------------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
6ED6 F5CB 5FA6 FB2F 460A E88E EDA0 D238 8AE2 2BA9
uid [ unknown] Debian Security Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-stable.gpg
--------------------------------------------------------
pub rsa4096 2017-05-20 [SC] [expires: 2025-05-18]
067E 3C45 6BAE 240A CEE8 8F6F EF0F 382A 1A7B 6500
uid [ unknown] Debian Stable Release Key (9/stretch) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/google-cloud-packages-archive-keyring.gpg
----------------------------------------------------------------
pub rsa2048 2021-03-01 [SC] [expires: 2023-03-02]
7F92 E05B 3109 3BEF 5A3C 2D38 FEEA 9169 307E A071
uid [ unknown] Rapture Automatic Signing Key (cloud-rapture-signing-key-2021-03-01-08_01_09.pub)
sub rsa2048 2021-03-01 [E]
pub rsa2048 2020-12-04 [SC] [expires: 2022-12-04]
59FE 0256 8272 69DC 8157 8F92 8B57 C5C2 836F 4BEB
uid [ unknown] gLinux Rapture Automatic Signing Key (//depot/google3/production/borg/cloud-rapture/keys/cloud-rapture-pubkeys/cloud-rapture-signing-key-2020-12-03-16_08_05.pub) <glinux-team@google.com>
sub rsa2048 2020-12-04 [E]
so as it is shown here the three key are expired:
pub dsa1024 2003-02-03 [SCA] [expired: 2022-02-16]
A4A9 4068 76FC BD3C 4567 70C8 8C71 8D3B 5072 E1F5
uid [ expired] MySQL Release Engineering <mysql-build@oss.oracle.com>
pub rsa3072 2019-03-18 [SC] [expired: 2021-03-17]
1505 8500 A023 5D97 F5D1 0063 B188 E2B6 95BD 4743
uid [ expired] DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
pub rsa4096 2013-08-17 [SC] [expired: 2021-08-15]
75DD C3C4 A499 F1A1 8CB5 F3C8 CBF8 D6FD 518E 17E1
uid [ expired] Jessie Stable Release Key <debian-release@lists.debian.org>
so I tried the following command:
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys A4A9406876FCBD3C456770C88C718D3B5072E1F5
result:
Executing: /tmp/apt-key-gpghome.8n1JFs3V5i/gpg.1.sh --keyserver keyserver.ubuntu.com --recv-keys A4A9406876FCBD3C456770C88C718D3B5072E1F5
gpg: failed to start the dirmngr '/usr/bin/dirmngr': No such file or directory
gpg: connecting dirmngr at '/tmp/apt-key-gpghome.8n1JFs3V5i/S.dirmngr' failed: No such file or directory
gpg: keyserver receive failed: No dirmngr
so after research, I did the following:
sudo apt install dirmngr --install-recommends
result:
Reading package lists... Done
Building dependency tree
Reading state information... Done
Suggested packages:
dbus-user-session libpam-systemd pinentry-gnome3 tor
The following NEW packages will be installed:
dirmngr
0 upgraded, 1 newly installed, 0 to remove and 10 not upgraded.
2 not fully installed or removed.
Need to get 597 kB of archives.
After this operation, 1,114 kB of additional disk space will be used.
Get:1 http://deb.debian.org/debian stretch/main amd64 dirmngr amd64 2.1.18-8~deb9u4 [597 kB]
Fetched 597 kB in 0s (7,412 kB/s)
Selecting previously unselected package dirmngr.
(Reading database ... 68920 files and directories currently installed.)
Preparing to unpack .../dirmngr_2.1.18-8~deb9u4_amd64.deb ...
Unpacking dirmngr (2.1.18-8~deb9u4) ...
Processing triggers for man-db (2.7.6.1-2) ...
Setting up dirmngr (2.1.18-8~deb9u4) ...
Setting up google-fluentd (1.8.7-1) ...
Conffile /etc/google-fluentd/google-fluentd.conf has been modified. Remain untouched.
Conffile /etc/google-fluentd/baseline/google-fluentd.conf has been modified. Remain untouched.
Job for google-fluentd.service failed because the control process exited with error code.
See "systemctl status google-fluentd.service" and "journalctl -xe" for details.
invoke-rc.d: initscript google-fluentd, action "start" failed.
● google-fluentd.service - LSB: data collector for Treasure Data
Loaded: loaded (/etc/init.d/google-fluentd; generated; vendor preset: enabled)
Active: failed (Result: exit-code) since Thu 2022-04-21 16:26:02 UTC; 9ms ago
Docs: man:systemd-sysv-generator(8)
Process: 21302 ExecStart=/etc/init.d/google-fluentd start (code=exited, status=1/FAILURE)
Apr 21 16:26:02 marketing-vm systemd[1]: Starting LSB: data collector for Treasure Data...
Apr 21 16:26:02 marketing-vm google-fluentd[21302]: Starting google-fluentd 1.8.7: Disabled via metadata ... (warning).
Apr 21 16:26:02 marketing-vm google-fluentd[21302]: google-fluentd ... failed!
Apr 21 16:26:02 marketing-vm systemd[1]: google-fluentd.service: Control process exited, code=exited status=1
Apr 21 16:26:02 marketing-vm systemd[1]: Failed to start LSB: data collector for Treasure Data.
Apr 21 16:26:02 marketing-vm systemd[1]: google-fluentd.service: Unit entered failed state.
Apr 21 16:26:02 marketing-vm systemd[1]: google-fluentd.service: Failed with result 'exit-code'.
dpkg: error processing package google-fluentd (--configure):
subprocess installed post-installation script returned error exit status 1
dpkg: dependency problems prevent configuration of google-fluentd-catch-all-config:
google-fluentd-catch-all-config depends on google-fluentd (>= 1.3.0); however:
Package google-fluentd is not configured yet.
dpkg: error processing package google-fluentd-catch-all-config (--configure):
dependency problems - leaving unconfigured
Errors were encountered while processing:
google-fluentd
google-fluentd-catch-all-config
E: Sub-process /usr/bin/dpkg returned an error code (1)
I ran the following command after research and the result after that:
admin@marketing-vm:~$ systemctl status google-fluentd.service
Failed to connect to bus: No such file or directory
how ever this returned an error but it seems that required dirmngr was installed succesfully and I assumed this is something related to google cloud server and I ingnored research about it. but if you know what should I do regarding it I will be appreciate it. but let’s continue as it is not my main issue
then I tried the following command again
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys A4A9406876FCBD3C456770C88C718D3B5072E1F5
result:
Executing: /tmp/apt-key-gpghome.q3eZMOsbBP/gpg.1.sh --keyserver keyserver.ubuntu.com --recv-keys A4A9406876FCBD3C456770C88C718D3B5072E1F5
gpg: key 8C718D3B5072E1F5: 4 duplicate signatures removed
gpg: key 8C718D3B5072E1F5: 60 signatures not checked due to missing keys
gpg: key 8C718D3B5072E1F5: "MySQL Release Engineering <mysql-build@oss.oracle.com>" 33 new signatures
gpg: Total number processed: 1
gpg: new signatures: 33
and
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 15058500A0235D97F5D10063B188E2B695BD4743
result:
Executing: /tmp/apt-key-gpghome.NYzCNLi5bV/gpg.1.sh --keyserver keyserver.ubuntu.com --recv-keys 15058500A0235D97F5D10063B188E2B695BD4743
gpg: key B188E2B695BD4743: 1 signature not checked due to a missing key
gpg: key B188E2B695BD4743: "DEB.SURY.ORG Automatic Signing Key <deb@sury.org>" 3 new signatures
gpg: Total number processed: 1
gpg: new signatures: 3
and
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 75DDC3C4A499F1A18CB5F3C8CBF8D6FD518E17E1
result:
Executing: /tmp/apt-key-gpghome.shHWXIw0ob/gpg.1.sh --keyserver keyserver.ubuntu.com --recv-keys 75DDC3C4A499F1A18CB5F3C8CBF8D6FD518E17E1
gpg: key CBF8D6FD518E17E1: 12 signatures not checked due to missing keys
gpg: key CBF8D6FD518E17E1: "Jessie Stable Release Key <debian-release@lists.debian.org>" 10 new signatures
gpg: Total number processed: 1
gpg: new signatures: 10
then when I ran sudo apt update I just saw only one remaining signature issue:
Hit:1 http://packages.cloud.google.com/apt google-cloud-monitoring-stretch-all InRelease
Ign:2 http://deb.debian.org/debian stretch InRelease
Hit:3 http://deb.debian.org/debian stretch-updates InRelease
Hit:4 http://deb.debian.org/debian stretch-backports InRelease
Hit:5 http://security.debian.org stretch/updates InRelease
Hit:6 http://packages.cloud.google.com/apt cloud-sdk-stretch InRelease
Hit:7 http://packages.cloud.google.com/apt google-compute-engine-stretch-stable InRelease
Hit:8 http://repo.mysql.com/apt/debian stretch InRelease
Hit:9 http://packages.cloud.google.com/apt google-cloud-packages-archive-keyring-stretch InRelease
Hit:10 http://deb.debian.org/debian stretch Release
Hit:11 https://packages.cloud.google.com/apt google-cloud-logging-stretch-all InRelease
Get:12 https://packages.sury.org/php stretch InRelease [6,839 B]
Err:8 http://repo.mysql.com/apt/debian stretch InRelease
The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
Get:14 https://packages.sury.org/php stretch/main amd64 Packages [356 kB]
Fetched 363 kB in 2s (149 kB/s)
Reading package lists... Done
Building dependency tree
Reading state information... Done
26 packages can be upgraded. Run 'apt list --upgradable' to see them.
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://repo.mysql.com/apt/debian stretch InRelease: The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
W: Failed to fetch http://repo.mysql.com/apt/debian/dists/stretch/InRelease The following signatures were invalid: EXPKEYSIG 8C718D3B5072E1F5 MySQL Release Engineering <mysql-build@oss.oracle.com>
W: Some index files failed to download. They have been ignored, or old ones used instead.
maybe I was wrong but I did the following based on the log again:
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 8C718D3B5072E1F5
result:
gpg: key 8C718D3B5072E1F5: 4 duplicate signatures removed
gpg: key 8C718D3B5072E1F5: 60 signatures not checked due to missing keys
gpg: key 8C718D3B5072E1F5: "MySQL Release Engineering <mysql-build@oss.oracle.com>" not changed
gpg: Total number processed: 1
gpg: unchanged: 1
so I searched about it and I followed the instructions on the following documentation:
https://dev.mysql.com/doc/refman/8.0/en/checking-gpg-signature.html
based on of what was recommened as here which was reported same issue:
https://ubuntuforums.org/showthread.php?t=2415997
as following:
sudo nano /home/admin/mysql_pubkey.asc
and I copy and paste the PGP PUBLIC KEY BLOCK mentioned in the documentation there. and saved it.
then:
gpg --import /home/admin/mysql_pubkey.asc
result:
gpg: /home/admin/.gnupg/trustdb.gpg: trustdb created
gpg: key 467B942D3A79BD29: public key "MySQL Release Engineering <mysql-build@os s.oracle.com>" imported
gpg: Total number processed: 1
gpg: imported: 1
then I copied the public key to txt file then I did this:
sudo apt-key add mysql_pubkey.txt
result:
OK
I do not know why the key 467B942D3A79BD29 is different from what document says which is 3A79BD29
. any way now when I run sudo apt-key list I see the following keys:
/etc/apt/trusted.gpg
--------------------
pub rsa3072 2019-03-18 [SC] [expires: 2024-02-16]
1505 8500 A023 5D97 F5D1 0063 B188 E2B6 95BD 4743
uid [ unknown] DEB.SURY.ORG Automatic Signing Key <deb@sury.org>
sub rsa3072 2019-03-18 [E] [expires: 2024-02-16]
pub rsa4096 2021-12-14 [SC] [expires: 2023-12-14]
859B E8D7 C586 F538 430B 19C2 467B 942D 3A79 BD29
uid [ unknown] MySQL Release Engineering <mysql-build@oss.oracle.com>
sub rsa4096 2021-12-14 [E] [expires: 2023-12-14]
/etc/apt/trusted.gpg.d/debian-archive-bullseye-automatic.gpg
------------------------------------------------------------
pub rsa4096 2021-01-17 [SC] [expires: 2029-01-15]
1F89 983E 0081 FDE0 18F3 CC96 73A4 F27B 8DD4 7936
uid [ unknown] Debian Archive Automatic Signing Key (11/bullseye) <ftpmaster@debian.org>
sub rsa4096 2021-01-17 [S] [expires: 2029-01-15]
/etc/apt/trusted.gpg.d/debian-archive-bullseye-security-automatic.gpg
---------------------------------------------------------------------
pub rsa4096 2021-01-17 [SC] [expires: 2029-01-15]
AC53 0D52 0F2F 3269 F5E9 8313 A484 4904 4AAD 5C5D
uid [ unknown] Debian Security Archive Automatic Signing Key (11/bullseye) <ftpmaster@debian.org>
sub rsa4096 2021-01-17 [S] [expires: 2029-01-15]
/etc/apt/trusted.gpg.d/debian-archive-bullseye-stable.gpg
---------------------------------------------------------
pub rsa4096 2021-02-13 [SC] [expires: 2029-02-11]
A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793
uid [ unknown] Debian Stable Release Key (11/bullseye) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-buster-automatic.gpg
----------------------------------------------------------
pub rsa4096 2019-04-14 [SC] [expires: 2027-04-12]
80D1 5823 B7FD 1561 F9F7 BCDD DC30 D7C2 3CBB ABEE
uid [ unknown] Debian Archive Automatic Signing Key (10/buster) <ftpmaster@debian.org>
sub rsa4096 2019-04-14 [S] [expires: 2027-04-12]
/etc/apt/trusted.gpg.d/debian-archive-buster-security-automatic.gpg
-------------------------------------------------------------------
pub rsa4096 2019-04-14 [SC] [expires: 2027-04-12]
5E61 B217 265D A980 7A23 C5FF 4DFA B270 CAA9 6DFA
uid [ unknown] Debian Security Archive Automatic Signing Key (10/buster) <ftpmaster@debian.org>
sub rsa4096 2019-04-14 [S] [expires: 2027-04-12]
/etc/apt/trusted.gpg.d/debian-archive-buster-stable.gpg
-------------------------------------------------------
pub rsa4096 2019-02-05 [SC] [expires: 2027-02-03]
6D33 866E DD8F FA41 C014 3AED DCC9 EFBF 77E1 1517
uid [ unknown] Debian Stable Release Key (10/buster) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg
----------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
126C 0D24 BD8A 2942 CC7D F8AC 7638 D044 2B90 D010
uid [ unknown] Debian Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg
-------------------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
D211 6914 1CEC D440 F2EB 8DDA 9D6D 8F6B C857 C906
uid [ unknown] Debian Security Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-stable.gpg
-------------------------------------------------------
pub rsa4096 2013-08-17 [SC] [expired: 2021-08-15]
75DD C3C4 A499 F1A1 8CB5 F3C8 CBF8 D6FD 518E 17E1
uid [ expired] Jessie Stable Release Key <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-stretch-automatic.gpg
-----------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
E1CF 20DD FFE4 B89E 8026 58F1 E0B1 1894 F66A EC98
uid [ unknown] Debian Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-security-automatic.gpg
--------------------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
6ED6 F5CB 5FA6 FB2F 460A E88E EDA0 D238 8AE2 2BA9
uid [ unknown] Debian Security Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-stable.gpg
--------------------------------------------------------
pub rsa4096 2017-05-20 [SC] [expires: 2025-05-18]
067E 3C45 6BAE 240A CEE8 8F6F EF0F 382A 1A7B 6500
uid [ unknown] Debian Stable Release Key (9/stretch) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/google-cloud-packages-archive-keyring.gpg
----------------------------------------------------------------
pub rsa2048 2021-03-01 [SC] [expires: 2023-03-02]
7F92 E05B 3109 3BEF 5A3C 2D38 FEEA 9169 307E A071
uid [ unknown] Rapture Automatic Signing Key (cloud-rapture-signing-key-2021-03-01-08_01_09.pub)
sub rsa2048 2021-03-01 [E]
pub rsa2048 2020-12-04 [SC] [expires: 2022-12-04]
59FE 0256 8272 69DC 8157 8F92 8B57 C5C2 836F 4BEB
uid [ unknown] gLinux Rapture Automatic Signing Key (//depot/google3/production/borg/cloud-rapture/keys/cloud-rapture-pubkeys/cloud-rapture-signing-key-2020-12-03-16_08_05.pub) <glinux-team@google.com>
sub rsa2048 2020-12-04 [E]
but still I face same result when I run sudo apt update
Hit:1 http://packages.cloud.google.com/apt google-cloud-monitoring-stretch-all InRelease
Ign:2 http://deb.debian.org/debian stretch InRelease
Hit:3 http://security.debian.org stretch/updates InRelease
Hit:4 http://packages.cloud.google.com/apt cloud-sdk-stretch InRelease
Hit:5 http://deb.debian.org/debian stretch-updates InRelease
Hit:6 http://packages.cloud.google.com/apt google-compute-engine-stretch-stable InRelease
Hit:7 http://deb.debian.org/debian stretch-backports InRelease
Hit:8 http://packages.cloud.google.com/apt google-cloud-packages-archive-keyring-stretch InRelease
Hit:9 http://deb.debian.org/debian stretch Release
Hit:10 http://repo.mysql.com/apt/debian stretch InRelease
Hit:11 https://packages.cloud.google.com/apt google-cloud-logging-stretch-all InRelease
Hit:12 https://packages.sury.org/php stretch InRelease
Err:10 http://repo.mysql.com/apt/debian stretch InRelease
The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8C718D3B5072E1F5
Reading package lists... Done
Building dependency tree
Reading state information... Done
26 packages can be upgraded. Run 'apt list --upgradable' to see them.
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://repo.mysql.com/apt/debian stretch InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8C718D3B5072E1F5
W: Failed to fetch http://repo.mysql.com/apt/debian/dists/stretch/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8C718D3B5072E1F5
W: Some index files failed to download. They have been ignored, or old ones used instead.
I also tried
gpg --delete-key 8C718D3B5072E1F5
result:
gpg (GnuPG) 2.1.18; Copyright (C) 2017 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: key "8C718D3B5072E1F5" not found: Not found
gpg: 8C718D3B5072E1F5: delete key failed: Not found
and
gpg --keyid-format=long --with-fingerprint --list-keys 8C718D3B5072E1F5
result:
gpg: error reading key: No public key
i will appreciate it if you can help me to solve this issue
I am trying to refresh repository indexes using Synsptic Package Manager and getting the following error.
An error occurred during the signature verification. The repository is
not updated and the previous index files will be used. GPG error:
http://deb.debian.org/debian buster InRelease: gpgv, gpgv2 or gpgv1
required for verification, but neither seems installedAn error occurred during the signature verification. The repository is
not updated and the previous index files will be used. GPG error:
http://security.debian.org/debian-security buster/updates InRelease:
gpgv, gpgv2 or gpgv1 required for verification, but neither seems
installedAn error occurred during the signature verification. The repository is
not updated and the previous index files will be used. GPG error:
http://deb.debian.org/debian buster-updates InRelease: gpgv, gpgv2 or
gpgv1 required for verification, but neither seems installedFailed to fetch http://deb.debian.org/debian/dists/buster/InRelease
gpgv, gpgv2 or gpgv1 required for verification, but neither seems
installedFailed to fetch
http://security.debian.org/debian-security/dists/buster/updates/InRelease
gpgv, gpgv2 or gpgv1 required for verification, but neither seems
installedFailed to fetch
http://deb.debian.org/debian/dists/buster-updates/InRelease gpgv,
gpgv2 or gpgv1 required for verification, but neither seems installedSome index files failed to download. They have been ignored, or old
ones used instead.
Even I have gpgv, gpgv2 and gpgv1 installed.
This error does not happen on sudo apt update but synaptic throws out this error.
I am new to debian and I do not understand how to resolve this. Please help me out.
I’m getting a lot of errors like this:
W: An error occurred during the signature verification.
The repository is not updated and the previous index files will be used.
GPG error: http://ftp.uk.debian.org/debian stretch-updates
InRelease: The following signatures couldn't be verified because the public key
is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
Tried to add the keys manually using:
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 8B48AD6246925553
and it says imported/processed but I still get the same errors.
agc
6,9151 gold badge20 silver badges51 bronze badges
asked Oct 20, 2017 at 5:58
1
I suggest these:
sudo apt-get clean
sudo mv /var/lib/apt/lists /tmp
sudo mkdir -p /var/lib/apt/lists/partial
sudo apt-get clean
sudo apt-get update
answered Oct 20, 2017 at 9:29
FargolKFargolK
1,5931 gold badge11 silver badges20 bronze badges
MySQL runs their own package repositories for community editions of MySQL. They support both yum and apt package managers, separated by sub-directories.
So far so good, but it seems that the previous GPG (to sign the packages) was replaced. This leads to errors when running apt-get update (or apt update):
root@debian:~# apt-get update
Hit:1 http://security.debian.org buster/updates InRelease
Hit:2 https://artifacts.elastic.co/packages/7.x/apt stable InRelease
Hit:3 http://httpredir.debian.org/debian buster InRelease
Get:4 http://repo.mysql.com/apt/debian buster InRelease [22.1 kB]
Hit:5 https://packages.sury.org/php buster InRelease
Err:4 http://repo.mysql.com/apt/debian buster InRelease
The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 467B942D3A79BD29
Reading package lists… Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://repo.mysql.com/apt/debian buster InRelease: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 467B942D3A79BD29
W: Failed to fetch http://repo.mysql.com/apt/debian/dists/buster/InRelease The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 467B942D3A79BD29
W: Some index files failed to download. They have been ignored, or old ones used instead.
When looking through the repository, no specific APT gpg key could be identified. These files usually end with a suffix of .gpg, .gnupg, .key or similar.
However there is one more intriguing file at the top-level directory of the repository: RPM-GPG-KEY-mysql-2022.
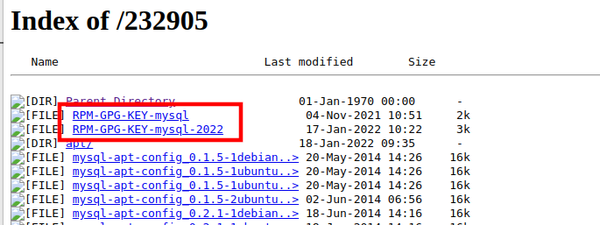
Why intriguing? Because the file starts with RPM, suggesting this key is only used for rpm packages (for the yum package manager).
Let’s import that file with apt-key:
root@debian:~# curl -s http://repo.mysql.com/RPM-GPG-KEY-mysql-2022 | apt-key add —
OK
It worked, so it is a GPG key. But is it the right key for the signed deb packages in the apt repositories?
root@debian:~# apt-get update
Hit:1 http://security.debian.org buster/updates InRelease
Hit:2 http://httpredir.debian.org/debian buster InRelease
Hit:3 https://artifacts.elastic.co/packages/7.x/apt stable InRelease
Get:4 http://repo.mysql.com/apt/debian buster InRelease [22.1 kB]
Hit:5 https://packages.sury.org/php buster InRelease
Get:6 http://repo.mysql.com/apt/debian buster/mysql-8.0 Sources [941 B]
Get:7 http://repo.mysql.com/apt/debian buster/mysql-apt-config amd64 Packages [567 B]
Get:8 http://repo.mysql.com/apt/debian buster/mysql-8.0 amd64 Packages [8,421 B]
Get:9 http://repo.mysql.com/apt/debian buster/mysql-tools amd64 Packages [7,070 B]
Hit:10 https://packagecloud.io/varnishcache/varnish60lts/debian buster InRelease
Fetched 39.1 kB in 1s (35.9 kB/s)
Reading package lists… Done
No errors! Although RPM-GPG-KEY-mysql-2022 sounds confusing, it is indeed the right key for the MySQL APT repository.
Add a comment
Show form to leave a comment
Comments (newest first)
Peter from wrote on Jun 18th, 2022:
Thanks for this post and making the command where it can be copied. This is like the 5th time I’ve ran into this and finally somebody posted a short, coherent fix.
Claude LaBadie from Canada wrote on May 6th, 2022:
Thank you so much for sharing this.
Would creating a better named symlink a good approach?
Comments
malept
added a commit
to electron/forge
that referenced
this issue
Feb 3, 2020
apo-mak
added a commit
to apo-mak/streisand
that referenced
this issue
Feb 4, 2020
apo-mak
added a commit
to apo-mak/streisand
that referenced
this issue
Feb 4, 2020
TriplEight
added a commit
to paritytech/scripts
that referenced
this issue
Feb 4, 2020
TriplEight
added a commit
to paritytech/scripts
that referenced
this issue
Feb 4, 2020
alimakki
added a commit
to StreisandEffect/streisand
that referenced
this issue
Feb 19, 2020
* add Update Yarn Debian key Update Yarn Debian key (see yarnpkg/yarn#7866) * create S.dirmngr S.gpg-agent Create a directory S.dirmngr and S.gpg-agent if it does not exist ( see #1630) * Update main.yml * Update yamllint-config.yml truthy: disable truthy value should be one of [false, true] but we use [no, yes] Co-authored-by: Ali Makki <alimakki@gmail.com>
juusokor
added a commit
to HSLdevcom/jore-graphql-import
that referenced
this issue
Feb 21, 2020
xini
mentioned this issue
Jan 25, 2023
GLStephen
added a commit
to prebid/Prebid.js
that referenced
this issue
Feb 1, 2023
Debian containers for yarn are having issues with key expirations. This change resolves that. Eventually the base images should be updated, but that timeline is unknown. There are a number of proposed solutions for the issue, but this one fixes ours. References to the issue: yarnpkg/yarn#7866 Similar in AWS Builds: yarnpkg/yarn#7866
patmmccann
pushed a commit
to prebid/Prebid.js
that referenced
this issue
Feb 2, 2023
Debian containers for yarn are having issues with key expirations. This change resolves that. Eventually the base images should be updated, but that timeline is unknown. There are a number of proposed solutions for the issue, but this one fixes ours. References to the issue: yarnpkg/yarn#7866 Similar in AWS Builds: yarnpkg/yarn#7866
Главная
»
Блог программиста
»
Ошибка при apt update An error occurred during the signature verification
22.03.2019 10:21
Просмотров: 3971
При использовании команды apt update на Debian 9 появилась следующая ошибка:
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://packages.sury.org/php stretch InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B188E2B695BD4743 W: Failed to fetch https://packages.sury.org/php/dists/stretch/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B188E2B695BD4743 W: Some index files failed to download. They have been ignored, or old ones used instead.
Она возникла из-за того, что DPA обновил signing key. Для решения этой проблемы необходимо обновить ключ APT signing key перед запуском обновления пакетов, скачать новый ключ можно из репозиториев:
$ sudo wget -O /etc/apt/trusted.gpg.d/php.gpg https://packages.sury.org/php/apt.gpg
Теперь apt update будет работать корректно.
Источник (EN)
Друзья! Приглашаем вас к обсуждению. Если у вас есть своё мнение, напишите нам в комментарии.
Поделиться
Skip to content
Update 21 March 2021: there’s been a recent uptick in traffic to this page – the current problem everyone is having is due to an expired key. Read more in this deb.sury.org github issue.
Solution (Debian 10.8 Buster):
(comments in various places suggest removing the old key is crucial)
sudo apt-key del B188E2B695BD4743 sudo wget -O /etc/apt/trusted.gpg.d/php.gpg https://packages.sury.org/php/apt.gpg
Useful command worth noting:
apt-key list
Original April 2019 blog post:
If you’re running Debian and using:
deb https://packages.sury.org/php/ stretch main
(it might be in /etc/apt/sources.list.d/php.list rather than the usual sources.list)
… you may see this error:
Err:5 https://packages.sury.org/php stretch InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B188E2B695BD4743 Reading package lists... Done W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://packages.sury.org/php stretch InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B188E2B695BD4743 W: Failed to fetch https://packages.sury.org/php/dists/stretch/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B188E2B695BD4743 W: Some index files failed to download. They have been ignored, or old ones used instead.
This isn’t widely blogged yet, however the best source of info is the Issue queue for the deb.sury.org GitHub repository – it turns out that in mid-March, the key for each repository on sury.org was regenerated due to a compromised server.
Here’s the command to download the new one, after which apt will work as expected.
sudo wget -O /etc/apt/trusted.gpg.d/php.gpg https://packages.sury.org/php/apt.gpg

