- Remove From My Forums
-
Question
-
I have windows 2012 R2 Federation server but trying to add an ADFS proxy server (WAP) which runs on windows
2012 R2 server. I keep getting the above error. I have research and the certificate is right yet, i keep getting same error. The proxy server is not even in the DMZ, there is no firewall between them. any help?This is the complete error:
I have windows 2012 R2 Federation server but trying to add an ADFS proxy server (WAP) which runs on windows
2012 R2 server. I keep getting the above error. I have research and I the certificate is right yet i keep getting same error. I used net mon to monitor the traffic and i could not see any connection or attempt to communicate with the Federation server. The
proxy server is not even in the DMZ, there is no firewall between them. any help?Trying to run using Powershell got this error:
Install-WebApplicationProxy : The certificate that is specified by the CertificateThumbprint parameter could not be
found in the Local Computer Personal certificate store. Check the thumbprint value and ensure that the desired
certificate is installed in the Local Computer Personal certificate store.
At line:1 char:1
+ Install-WebApplicationProxy –CertificateThumbprint ‘1a2b3c4d5e6f1a2b3c4d5e6f1a2b …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Install-WebApplicationProxy], DisplayableArgumentException
+ FullyQualifiedErrorId : PrerequisiteTest,Microsoft.IdentityServer.Management.Proxy.Commands.InstallProxyCommand
Jose Chavez IT Manager
Answers
-
There are so many guides out there on how to install AD FS 3.0
I have setup a few farms now without issues, by doing some quick reading.
As Konnan has asked above — have you installed the ADFS Farm Server certificate onto your WAP server?
This article explains the certificate requirements for both the WAP and Farm Servers:
https://technet.microsoft.com/en-au/library/dn151311.aspx#BKMK_2-
Proposed as answer by
Friday, May 29, 2015 6:18 AM
-
Unproposed as answer by
Jose_ Chavez
Friday, May 29, 2015 4:12 PM -
Marked as answer by
Jose_ Chavez
Monday, June 1, 2015 8:49 PM
-
Proposed as answer by
-
Hi Jose,
I agree with others. Regarding installing and configuring the Web Application Proxy Server, the following articles can be referred to for more information.
Step 2: Plan the Web Application Proxy Server
https://technet.microsoft.com/en-in/library/dn383647.aspx
Install and Configure the Web Application Proxy Server
https://technet.microsoft.com/en-in/library/dn383662.aspx
Best regards,
Frank Shen
Please remember to mark the replies as answers if they help and unmark them if they provide no help. If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
-
Marked as answer by
Jose_ Chavez
Friday, May 29, 2015 4:12 PM
-
Marked as answer by
-
On your WAP server, which I suspect is brand new, do you have the root certificate in the Enterprise trust directory?
On your WAP server, do you have the ADFS certificate installed in the Personal directory? The one that you export from your ADFS server and install in the Personal directory before installing WAP? Does the certificate chain seems to be OK ?
Good luck !
Konnan
Understanding ADFS 3.0, the key to success
-
Proposed as answer by
Frank Shen5
Friday, May 29, 2015 6:18 AM -
Unproposed as answer by
Jose_ Chavez
Friday, May 29, 2015 4:12 PM -
Marked as answer by
Jose_ Chavez
Monday, June 1, 2015 8:49 PM
-
Proposed as answer by
Environment
- Windows 2012 R2 server on the LAN with the Active Directory Federation Service Role installed
- Windows 2012 R2 server in the DMZ with the Remote Access role and the Web Application Proxy (WAP) feature installed
Problem
Getting the following error running the Web Application Proxy Configuration Wizard
“An error occurred when attempting to establish a trust relationship with the federation service. Error: The request was aborted: Could not create SSL/TLS secure channel”
Event ID 393 was written to the event log
This is a relatively common error and is usually related to a problem with the certificates, ports, or permissions of the account used to run the wizard. A quick search of the web and you will find plenty of examples and solutions.
However, I have to admit, that after a lot of troubleshooting I was stumped. I opened a support ticket with the good folks at Microsoft Premier Support. After a 6 hour remote support session (with a great engineer), we found the problem.
A network trace from both the Proxy and the ADFS, and a seemingly unrelated Event ID 36874 on the ADFS server provided the clues as to the cause of the problem.
Cause
The template that the Windows 2012 R2 servers had been deployed which included server hardening – specifically with cipher, protocols, hashes and multiple subkeys with values disabled.
The hardened server registry for the Security Providers looked like this
The specific server hardened registry keys were as follows:
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersAES 128/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersAES 256/256]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersDES 56/56]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersNULL]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC2 128/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC2 40/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC2 56/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC4 128/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC4 40/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC4 56/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersRC4 64/128]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersTriple DES 168]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphersTriple DES 168/168]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesMD5]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA256]
- “Enabled”=dword:ffffffff
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA384]
- “Enabled”=dword:ffffffff
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA512]
- “Enabled”=dword:ffffffff
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsDiffie-Hellman]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsECDH]
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsPKCS]
- “Enabled”=dword:ffffffff
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsMulti-Protocol Unified HelloClient]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsMulti-Protocol Unified HelloServer]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsPCT 1.0Client]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsPCT 1.0Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Client]
- “DisabledByDefault”=dword:00000001
- “Enabled”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Client]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client]
- “Enabled”=dword:ffffffff
- “DisabledByDefault”=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server]
- “Enabled”=dword:ffffffff
- “DisabledByDefault”=dword:00000000
Solution
Removed the hardened SCHANNEL registry keys on both the ADFS & PROXY servers and rebooted.
The cleaned up registry look like this
Hi,
I have an existing ADFS farm on Server 2012 but I’m replacing it with a new farm with the same name on Server 2012 R2. There will be an ADFS server and a Web Application Proxy.
I’ve installed the first Federation server and can open
https://localhost/adfs/ls/IdpInitiatedSignon.aspx so all seems well.
I have exported the existing 3rd party certificate *.mydomain.com onto the ADFS server and the proxy and installed it in Personal container under computer certificates. I also exported/imported the Token-decrypting and Token-signing certificates onto
the ADFS server (though not onto the proxy as I don’t see how to do this — can’t see it in certmgr only in ADFS snapin which doesn’t seem to allow export)
I can ping both ways and I can telnet from the proxy to the ADFS server on 443 (though not the reverse direction) Windows firewalls are off and there is an any/any rule between the servers.
I am trying to run the proxy wizard but it fails with a couple of errors depending on what I use for the Federation Server Name (I’ve created the name as adfs.mydomain.com but TechNet says use the FQDN of the ADFS server, so I’m trying both)
An error occurred when attempting to establish a trust relationship with the federation service. Error: Forbidden (if I use adfs.mydomain.com as the Federation Server Name)
An error occurred when attempting to establish a trust relationship with the federation service. Error: The underlying connection was closed: An unexpected error occurred on a send. (if I use the hostname of the ADFS server)
I think the adfs.mydomain.com is the right one — can you confirm this and advise how I can fix this issue. The account I am using in the proxy wizard is the local admin password though have tried my own admin account too.
Have tried the links in
http://social.technet.microsoft.com/Forums/windowsserver/en-US/e04fe6fe-3415-45c2-a1ec-0c76be8ae3a5/web-application-proxy-configuration-error?forum=winserver8gen with no success
I’ve been following the main install link on
TechNet — not sure what I’ve done wrong.
Any assistance very welcome.
-
Edited by
Friday, March 14, 2014 8:12 PM
Hi mates. Today we’re going to cover how to investigate and fix WAP Trust error Service Unavailable when AD FS endpoint /adfs/proxy/establishTrust/ is not available.
Overview
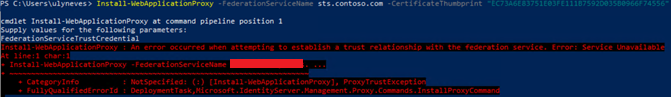
The endpoint /adfs/proxy/establishTrust/ is used by the WAP server to establish the trust during the post-install process. When this endpoint is not available, you might face error message below during a WAP trust configuration:
PowerShell Error message: cmdlet Install-WebApplicationProxy at command pipeline position 1
Supply values for the following parameters: FederationServiceTrustCredential
Install-WebApplicationProxy : An error occurred when attempting to establish a trust relationship with the federation service. Error: Service Unavailable
At line:1 char:1
+ Install-WebApplicationProxy -FederationServiceName fs.contoso. …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Install-WebApplicationProxy], ProxyTrustException
+ FullyQualifiedErrorId
DeploymentTask,Microsoft.IdentityServer.Management.Proxy.Commands.InstallProxyCommand
With AD FS tracing debug logs enabled, you might see event IDs 12, 57 and 104 on the WAP server as below:
WAP server: AD FS Tracing/Debug
Source: AD FS Tracing
Event ID: 12
Task Category: None
Level: Error
Keywords: ADFSConfiguration
Description:
Error: Exception: An error occurred when attempting to establish a trust relationship with the federation service. Error: Service Unavailable
StackTrace: at Microsoft.IdentityServer.Management.Proxy.Providers.ProxyTrustProvider.EstablishTrustWithSts(ICredentials credentials, String thumbprint) at Microsoft.IdentityServer.Deployment.Core.Tasks.ConfigurationTaskBase.Execute(IDeploymentContext context, IProgressReporter progressReporter)
Exception: The remote server returned an error: (503) Server Unavailable.
StackTrace: at System.Net.HttpWebRequest.GetResponse() at Microsoft.IdentityServer.Management.Proxy.Providers.ProxyTrustProvider.EstablishTrustWithSts(ICredentials credentials, String thumbprint)
AD FS server: AD FS Tracing/Debug
Source: AD FS Tracing
Event ID: 107
Task Category: None
Level: Error
Keywords: ADFSProxyConfiguration
Description:
ProxyConfigurationListener.OnGetContext: There were no registered handlers to handle the request to : ‘’.
Log Name: AD FS Tracing/Debug
Source: AD FS Tracing
Event ID: 54
Task Category: None
Level: Information
Keywords: ADFSSTS
Description:
Sending response at time: ‘2021-01-27 11:00:23’ with StatusCode: ‘503’ and StatusDescription: ‘Service Unavailable’.
Response headers set: {“Content-Type”:”text/html; charset=utf-8″}
Cause:
WAP trust is established by posting a client certificate to the AD FS “Proxy” endpoint. : /adfs/proxy/establishTrust/ and this endpoint should be accessible from WAP server.
Troubleshooting steps:
Checking AD FS Proxy Trust Endpoint status
Check if endpoint /adfs/Proxy/EstablishTrust/ is enabled on the primary AD FS running following command:
Get-AdfsEndpoint -AddressPath '/adfs/Proxy/EstablishTrust/'
If endpoint is disabled, you might see output below:
ClientCredentialType : Username-Password-Clear
Enabled : False
FullUrl : https://fs.contoso.com/adfs/proxy/EstablishTrust/
Proxy : False
Protocol : Web Application Proxy
SecurityMode : Transport
AddressPath : /adfs/proxy/EstablishTrust/
Version : default
Enabling endpoint /adfs/proxy/EstablishTrust/
Run commands below to enable the endpoint on the AD FS server. The AD FS service restart is required to take effect:
Enable-AdfsEndpoint -TargetAddressPath '/adfs/Proxy/EstablishTrust/' Restart-Service adfssrv
Run again the command Install-WebApplicationProxy to re-establish the trust as example below:
Note: Considering the federation service name is fs.contoso.com and the SSL certificate thumbprint is 3638de9b03a488341dfe32fc3ae5c480ee687793.
Install-WebApplicationProxy -FederationServiceName fs.contoso.com -CertificateThumbprint "3638de9b03a488341dfe32fc3ae5c480ee687793"
Summary
In this article, we covered how to investigate and fix WAP trust issues related to the endpoint ‘/adfs/Proxy/EstablishTrust/’.
I hope you have enjoyed reading this article and it helps you manage your AD FS environment.
Enjoyed the article? Like and share. 🙂
Note: I do not represent the organization I work for, all the opinions expressed here, are my own. This post is provided AS IS with no warranties or guarantees and confers no rights.
In case you have any suggestion or feedback, please leave a comment.
[ ]’s
Ulysses Neves
In the Tailspintoys environment the AD FS Proxy was offline for month. It was unable to contact the AD FS server on the internal network, and this allowed the short lived authentication certificate to expire. At this point the AD FS Proxy was «dead to me» as far as the AD FS server was concerned. The internal AD FS server was OK, the issue was just with the proxy.
Bummer….
How do we fix this? Actually before we dive into that, lets see what was going on first. Please note that this post is for AD FS 2012 R2 onwards. It does not aim to cover AD FS 2.0 or 2.1 at all.
This is an updated post from the original one back in April 2015. The original will remain as it is still relevant, and some folks may have linked or bookmarked it.
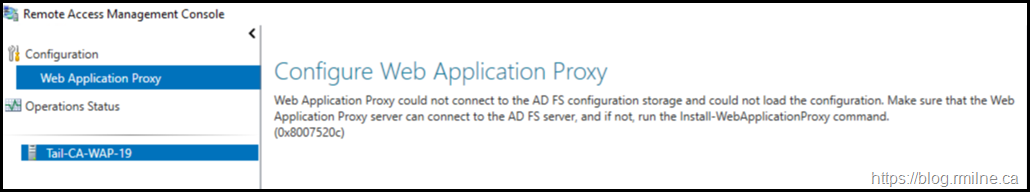
Starting Point – What The AD FS Proxy Saw In WAP Remote Management Console
On the WAP server, the Remote Access Management Console was not happy. It was reporting error code 0x8007520C.
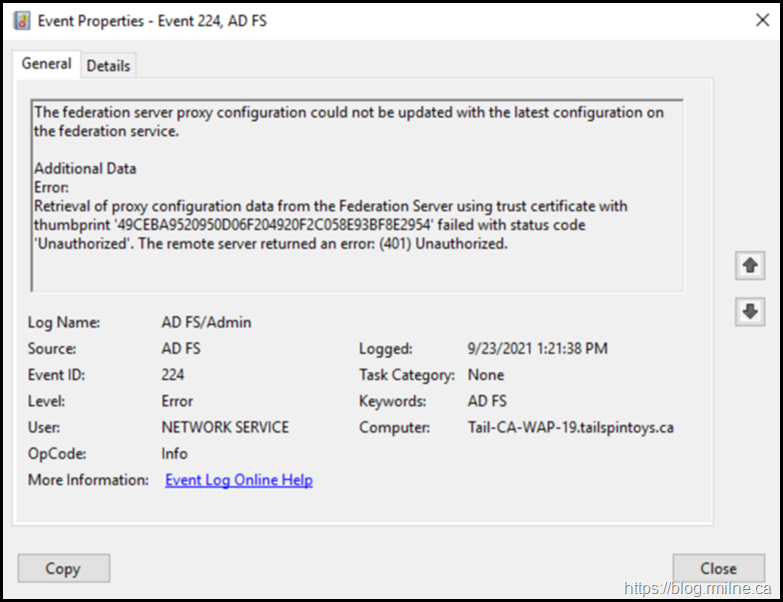
On the WAP server, EventID 244 was logged into the AD FS/Admin EventLog stating that it was unable to retrieve proxy configuration data from the Federation Service. The details in the event stated: System.Net.WebException: The remote server returned an error: (401) Unauthorized. This was EventID 422 as noted in the previous post.
There will also be errors present in the Microsoft-Windows-Web Application Proxy/Admin EventLog.
Starting Point – What AD FS Saw
On AD FS we can see what it really though about the AD FS proxy.
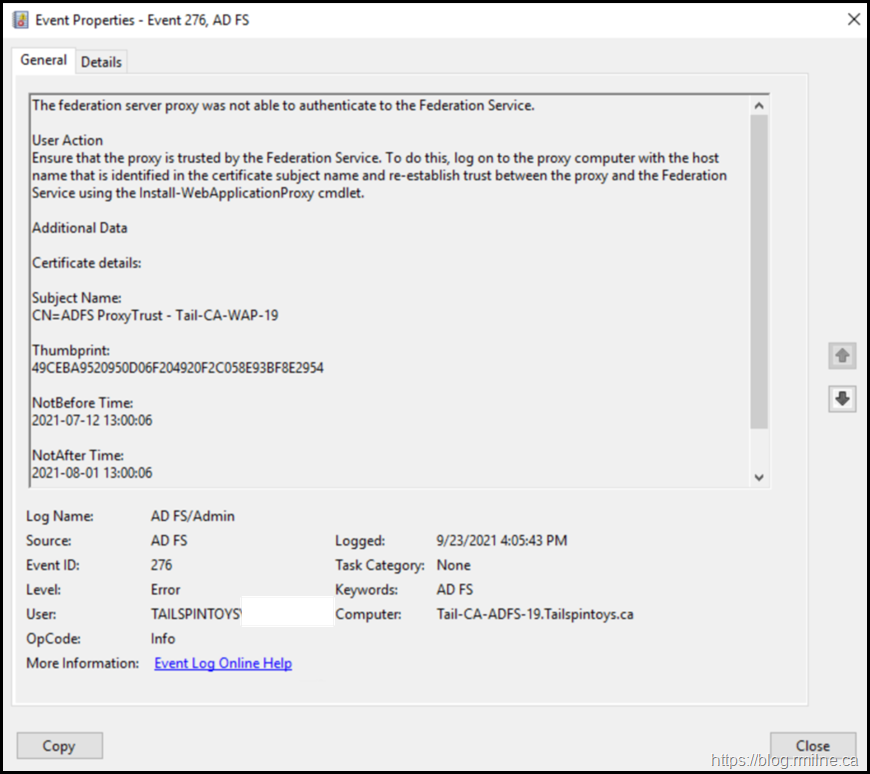
Since the federation server proxy could not renew its trust with the Federation Service, the recommended user action was: To ensure that the federation server proxy is trusted by the Federation Service. If the trust does not exist or has been revoked, establish a trust between the proxy and the Federation Service using the Federation Service Proxy Configuration Wizard by logging on to the proxy computer. This is detailed in EventID 276, which is again logged on the AD FS server.
The proxy trust certificate specified by thumpbrint has expired. Note that you can also see the calling IP listed at the bottom of the event message.
OK – so we need to re-establish the trust between the AD FS proxy and AD FS server. How do we go about doing that?
Re-Establish AD FS Proxy Trust Using Remote Access Management Console
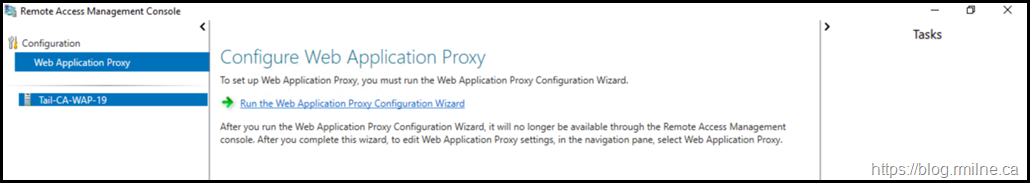
Interestingly enough there is no option presented initially in the GUI to re-configure the AD FS proxy.
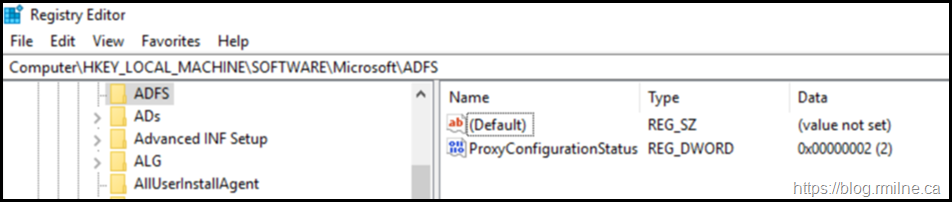
Currently it knows that the wizard was previously executed, and this fact is stored in the registry. As Georg discussed at MEC to allow the Remote Access GUI to re-run the wizard again, we need to edit the registry. The registry value that we need to change is:
HKLMSoftwareMicrosoftADFSProxyConfigurationStatus
We need to set the ProxyConfigurationStatus REG_DWORD to a value of 1 (meaning “not configured”) instead of 2 (“configured”). Once that change is made, re-open the GUI. No reboot is required.
After changing the ProxyConfigurationStatus to a value of 1, the Remote Access Manager should now allow you to re-run the configuration wizard.
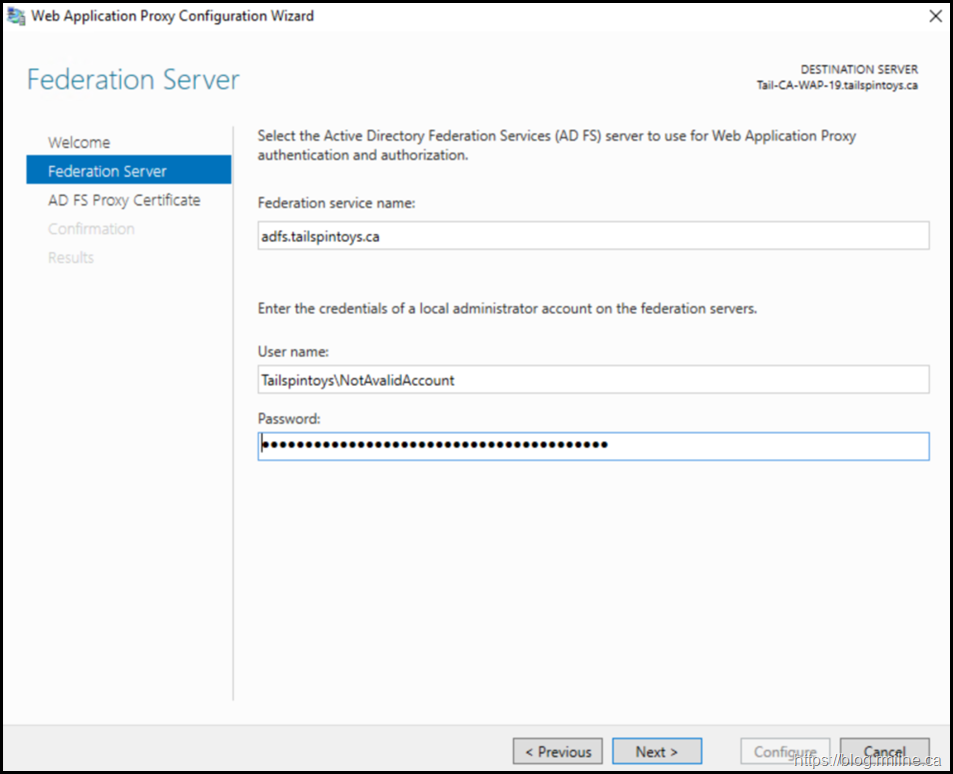
For full details on this process, please see this post. As a brief recap, we need to ensure that the federation service name is the AD FS endpoint that we defined when initially building the environment.
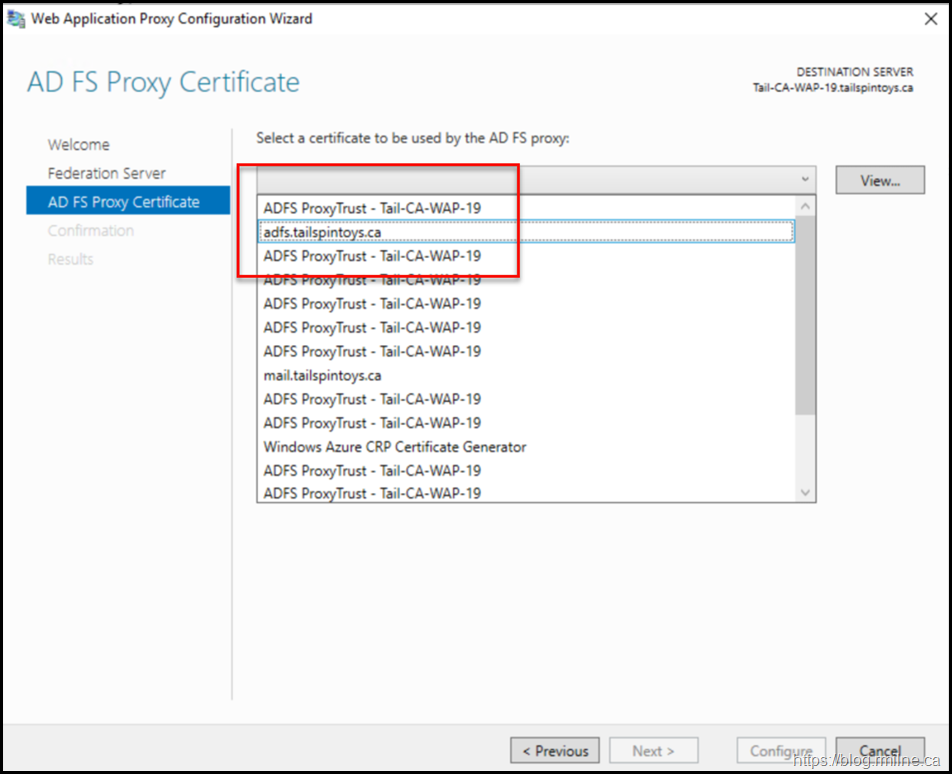
Since there may have been certificate replacement/renewal since the initial server was deployed, be careful to select the correct certificate:
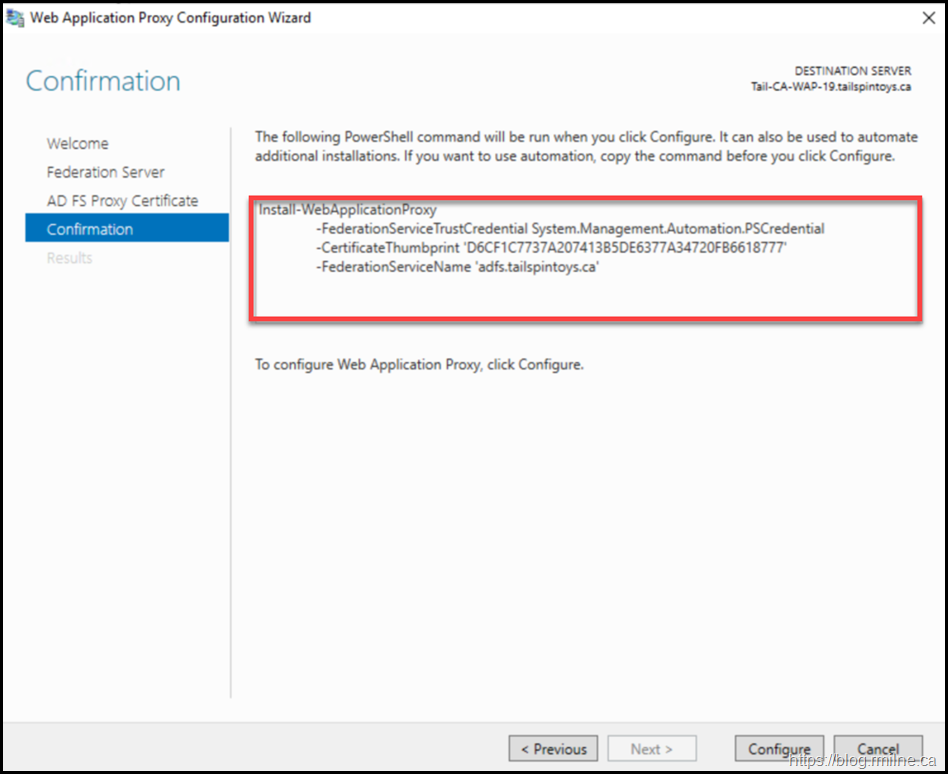
The summary screen indicates the PowerShell code that will be executed. This is also captured later in the post for reference.
And when complete, the trust is now re-established.
Now restart the AD FS service on the Proxy server, and check the AD FS event logs to ensure that they are all green ticky ticky!
Alternatively, this can be done from PowerShell, this is shown below. Typically this is what I normally use as it is faster, and does not require the registry modification.
Re-Establish AD FS Proxy Trust Using PowerShell
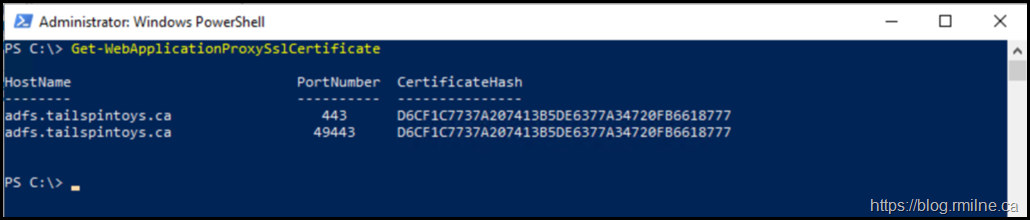
EventID 276 shown above, notes that we can run the Install-WebApplicationProxy cmdlet to re-establish trust between the AD FS server and the WAP. Docs discusses this in the Install and Configure the Web Application Proxy Server section. The certificate we want to use is already installed onto the server. In my case it has the thumbprint of D6CF1C7737A207413B5DE6377A34720FB6618777– note that yours *WILL* be different. To obtain your certificate thumbprint you can look at the certificate MMC or alternatively run:
Get-WebApplicationProxySslCertificate
In this lab, the command executed was:
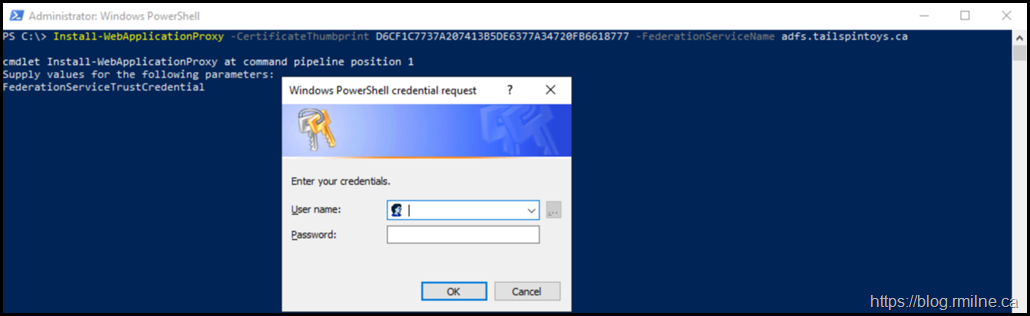
Install-WebApplicationProxy –CertificateThumbprint D6CF1C7737A207413B5DE6377A34720FB6618777 -FederationServiceName adfs.tailspintoys.ca
Note that the username and password were not specified, since the cmdlet knows it needs an account that has permission on the AD FS server and it prompts for this required information. This is the Tailspintoys administrator account as shown below:
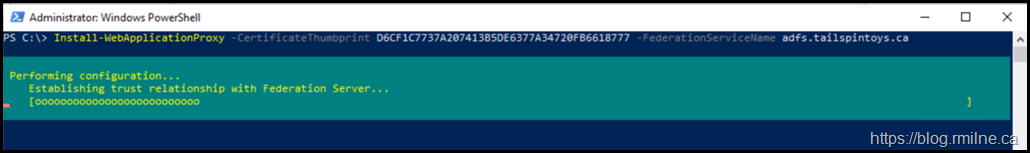
After providing the credentials, the cmdlet does it’s thang:
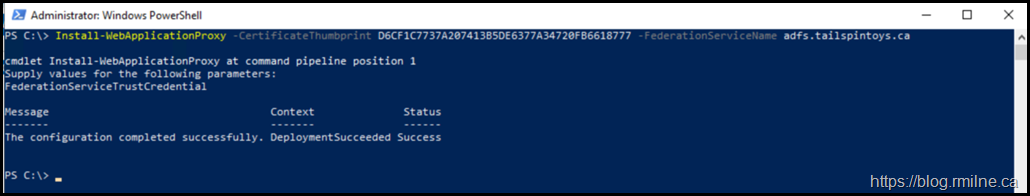
Finally finishing up with a Deployment Succeeded message.
Checking For Success
After the restarting the AD FS service on the proxy, success messages were then logged on both the AD FS server and the proxy.
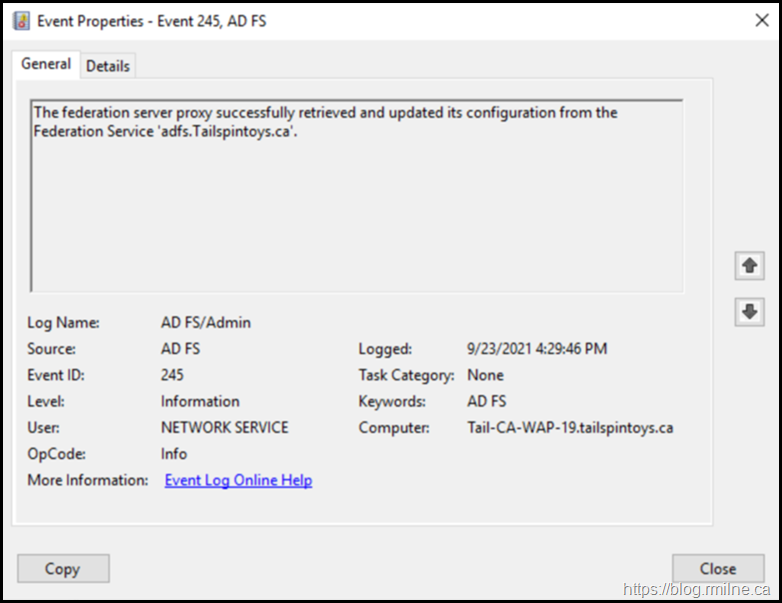
On the AD FS proxy EventID 245 noted that the proxy was able to successfully retrieve its configuration:
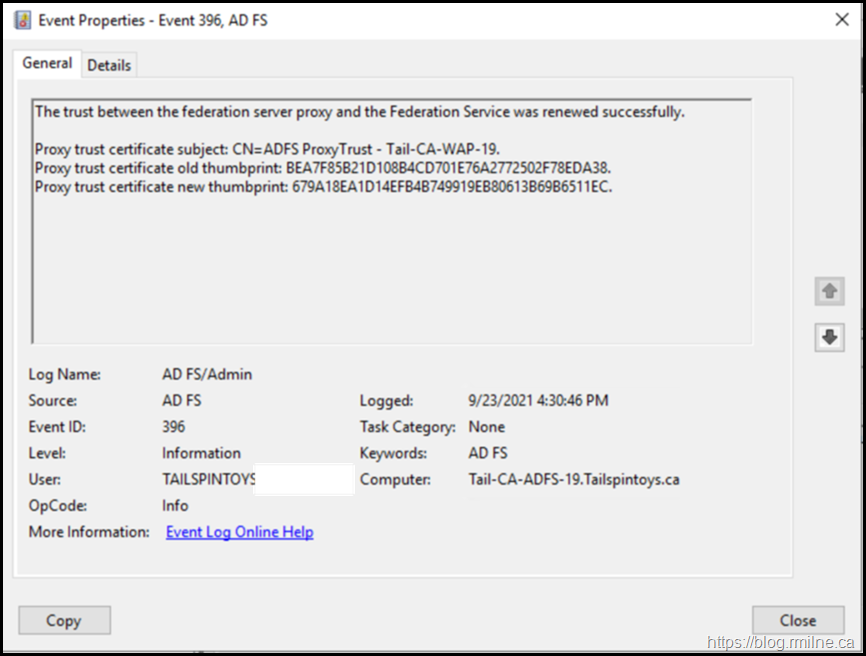
And on the AD FS server EventID 396 was logged stating that the trust between the proxy and AD FS server was renewed.
Clients were now able to successfully authenticate through the AD FS proxy from the Internet.
Good job. Time to go home for tea and medals!
Cheers,
Rhoderick
Issue Definition:
Proxy Trust Issues with AD FS 2012 R2 and Web Application Proxy
Infra Details:
2 X ADFS 2012 R2 servers
2 X Web Application proxy servers
Both ADFS and WAP servers were deployed with Load balancer (Citrix NetScaler).
AD FS Configuration database is on SQL Always On 2014
Observation:
- Host Entry in WAP servers are pointing to VIP >>> Internal LB of ADFS servers
- From a domain Joined machine when resolved the ADFS Federation service name, it was resolving to VIP >>> Internal LB
- Trust was established on WAP Server 01 but could see below Error event logged in the ADFS admin logs.
- Trust Wizard was not run on WAP Server 02
- There were no Error event Logged in AD FS servers.
Log Name: AD FS/Admin
Source: AD FS
Date: 8/23/2016 11:49:37 AM
Event ID: 422
Task Category: None
Level: Error
Keywords: AD FS
User: NETWORK SERVICE
Computer: WAP Server 01
Description:
Unable to retrieve proxy configuration data from the Federation Service.
Exception details:
System.Net.WebException: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel. —> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure.
Steps Taken:
- Checked the SSL bindings on ADFS/WAP servers – They were correct
- From an domain joined machine – Performed the below checks
- Tried accessing the IDP Page or the AD FS Sign in page – Status Success
- Performed another Test by making a host file entry pointing to ADFS servers individually – Status Success “Which confirmed that there is no issues with ADFS servers & Bindings”
- Pointed the host file entry to WAP server 01 IP Address and accessed the IDP page – Status Success
On WAP servers:
- Telnet from WAP to AD FS VIP >> Internal LB (ADFS Servers) on port 443 – Status Success
- Telnet from WAP to ADFS servers individually on port 443 – Status Success
- Tested IDP Page from WAP servers, working fine without any issues – With an Host file entry pointing to VIP >> Internal LB and with ADFS servers individually
- SSL certificate validation on WAP server – Certificate chain was not complete on both WAP servers “this the start of the clue”
- With an Host file Entry pointing to VIP >>> Internal LB of ADFS servers – Tried Establishing the trust on WAP Server 02, Status failed
with below error and Event ID 393 logged in ADFS admin logs
“An error occurred when attempting to establish a trust relationship with the federation service. Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel.
- Tried establishing the trust again by-passing the Load balancer by directly pointing to ADFS Server 01 in Host file. – Proxy Trust was established successfully
- On WAP Server 01 by passed the load balancer and pointed ADFS Server 01 in host file and restarted the WAP services, Error events related to SSL/TLS (Error Event ID 422) disappeared and could see the success event in the ADFS admin logs.
For Testing purpose made changes to host file in WAP Server 01 pointing to ADFS Server 02 and restarted the services, the web application proxy service cannot be started and Error Event ID 422 reappeared in ADFS admin logs “Unable to retrieve proxy configuration data from the Federation Service- The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel
- To isolate the issue further, Took a simultaneous network trace by Network Monitor from WAP Server 01 and ADFS Server 02 while restarting the WAP services.
- Analyzed the logs and here is what i found
“Client Helloà Server hello à Key Exchange à WAP server sends a ACK FIN to ADFS server and the session terminates. It appeared that certificate validation check was failed hence ACK FIN was sent to ADFS server”
- All these errors pin pointed to an incomplete Certificate chain on WAP servers,
- in order to fix the issue exported the intermediate and root certificate from ADFS server and imported to corresponding store in WAP servers.
- Post which Hard coded the host file to AD FS VIP IP >>> Internal LB of AD FS and restarted the services.
- The Proxy Trust Issues with AD FS 2012 R2 and Web Application Proxy has been resolved on both WAP servers.
I’m trying to install an ADFS proxy. In our intranet we have a ADFS 2.1 server running on Windows 2012 which is working fine. Now we’re trying to deploy a proxy to this one for internet access, using Windows 2012 R2’s Web Application Proxy.
I’m getting the following error on the proxy server, event ID 393:
Message : An error occurred while attempting to establish a trust
relationship with the Federation Server. An error occurred when
attempting to establish a trust relationship with the federation
service. Error: Forbidden Context : DeploymentTask Status : Error
I’m not getting any errors on the ADFS server.
I’ve tried with different credentials. The ADFS service account, a domain administrator who is a member of the local administrators group on the ADFs server, and the local administrator account on the ADFS server. Same error message.
Both port 80 and 443 is accessible from the proxy server to the internal ADFS server, and I can access the ADFS metadata endpoint from the proxy server. I’m using the same trusted SSL certificate (wildcard) on both machines.
Do you have any ideas that can help me troubleshoot this problem?
© Server Fault or respective owner
Related posts about active-directory
-
Can’t join OS X Mavericks to AD Domain
as seen on Server Fault
— Search for ‘Server Fault’
I’m attempting to join an OS X Mavericks (10.9) client to a Windows Server 2008 Active Directory domain, however the bind fails with this error in the OS X client’s system.log:
Oct 24 15:03:15 host.domain.com com.apple.preferences.users.remoteservice[5547]: -[ODCAddServerSheetController handleOtherActionError:…
>>> More -
Retrieve user details from Active Directory using SID
as seen on Server Fault
— Search for ‘Server Fault’
Hi,
How can I find a user in my AD when I have his/her SID.
I don’t want to rely on other attributes, since I am trying to detect changes to these.
Example:
I get a message about a change to user record containing:
Message: User Account Changed:
Target Account Name: test12
Target…
>>> More -
Retrieve user details from Active Directory using GUID
as seen on Server Fault
— Search for ‘Server Fault’
Hi,
How can I find a user in my AD when I have his/her GUID.
I don’t want to rely on other attributes, since I am trying to detect changes to these.
>>> More -
Retrieve user details from Active Directory using GUID [closed]
as seen on Super User
— Search for ‘Super User’
Hi,
How can I find a user in my AD when I have his/her GUID.
I don’t want to rely on other attributes, since I am trying to detect changes to these.
>>> More -
Office365 DirSync Active Directory Integration
as seen on Server Fault
— Search for ‘Server Fault’
I am preparing to deploy Office365 for my organization. We have an on premise Active Directory Domain Controller (Windows Server 2012 R2). We would like to leverage our Active Directory for: automatic user provisioning in Office365, and password synchronization, using the DirSync tool.
Our Active…
>>> More
Related posts about adfs
-
WIF, ADFS 2 and WCF–Part 3: ADFS Setup
as seen on Least Privilege
— Search for ‘Least Privilege’
In part
1 of this series I briefly gave an overview of the ADFS / WS-Trust infrastructure.
In part
2 we created a basic WCF service that uses ADFS for authentication. This part
will walk you through the steps to register the service in ADFS 2.
I could provide screenshots for all the wizard…
>>> More -
ADFS in Asp.Net
as seen on Stack Overflow
— Search for ‘Stack Overflow’
Hi All,
Suggest me with some informative links about working with ADFS in Asp.Net 3.5 and its related downloads.
>>> More -
ADFS 2.1 proxy trust establishment error
as seen on Server Fault
— Search for ‘Server Fault’
I’m trying to install an ADFS proxy. In our intranet we have a ADFS 2.1 server running on Windows 2012 which is working fine. Now we’re trying to deploy a proxy to this one for internet access, using Windows 2012 R2’s Web Application Proxy.
I’m getting the following error on the proxy server, event…
>>> More -
Bind ADFS 2.0 service to a specific IP address
as seen on Server Fault
— Search for ‘Server Fault’
I have one server with ADFS-2.0 and a few websites on it. One of the websites is Dynamics CRM which listens on a specific IP address on port 443.
Dynamics CRM provides a metadata file for configuration purposes which could be used to configure a relaying party trust with ADFS. It is accessible with…
>>> More -
How to install ADFS 3.0 in standalone mode?
as seen on Server Fault
— Search for ‘Server Fault’
I’ve installed Windows 2012 R2 and enabled the ADFS (3.0?) feature. After installation, it asks to configure ADFS, but this step requires a user account that is a domain administrator, as it wants to create certificate containers and SPN records.
In ADFS 2.0, you could install in standalone mode…
>>> More