auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /data/data/com.termux/files/usr/opt/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 10.23.132.10
rhosts => 10.23.132.10
msf5 auxiliary(scanner/smb/smb_ms17_010) > exploit
[-] 10.23.132.10:445 — An SMB Login Error occurred while connecting to the IPC$ tree.
[] 10.23.132.10:445 — Scanned 1 of 1 hosts (100% complete)
[] Auxiliary module execution completed
This page contains detailed information about how to use the auxiliary/scanner/smb/smb_ms17_010 metasploit module. For list of all metasploit modules, visit the Metasploit Module Library.
- Module Overview
- Module Ranking and Traits
- Basic Usage
- Required Options
- Knowledge Base
- Vulnerable Application
- Verification Steps
- Options
- Msfconsole Usage
- Module Options
- Advanced Options
- Auxiliary Actions
- Evasion Options
- Error Messages
- Related Pull Requests
- References
- See Also
- Authors
- Version
Module Overview
Name: MS17-010 SMB RCE Detection
Module: auxiliary/scanner/smb/smb_ms17_010
Source code: modules/auxiliary/scanner/smb/smb_ms17_010.rb
Disclosure date: —
Last modification time: 2021-06-29 16:18:28 +0000
Supported architecture(s): —
Supported platform(s): —
Target service / protocol: microsoft-ds, netbios-ssn
Target network port(s): 139, 445
List of CVEs: CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, CVE-2017-0147, CVE-2017-0148
This module is also known as DOUBLEPULSAR or ETERNALBLUE.
Uses information disclosure to determine if MS17-010 has
been patched or not. Specifically, it connects to the IPC$
tree and attempts a transaction on FID 0. If the status
returned is «STATUS_INSUFF_SERVER_RESOURCES», the machine
does not have the MS17-010 patch. If the machine is missing
the MS17-010 patch, the module will check for an existing
DoublePulsar (ring 0 shellcode/malware) infection. This
module does not require valid SMB credentials in default
server configurations. It can log on as the user «» and
connect to IPC$.
Module Ranking and Traits
Module Ranking:
- normal: The exploit is otherwise reliable, but depends on a specific version and can’t (or doesn’t) reliably autodetect. More information about ranking can be found here.
Basic Usage
This module is a scanner module, and is capable of testing against multiple hosts.
msf > use auxiliary/scanner/smb/smb_ms17_010
msf auxiliary(smb_ms17_010) > show options
... show and set options ...
msf auxiliary(smb_ms17_010) > set RHOSTS ip-range
msf auxiliary(smb_ms17_010) > exploit
Other examples of setting the RHOSTS option:
Example 1:
msf auxiliary(smb_ms17_010) > set RHOSTS 192.168.1.3-192.168.1.200
Example 2:
msf auxiliary(smb_ms17_010) > set RHOSTS 192.168.1.1/24
Example 3:
msf auxiliary(smb_ms17_010) > set RHOSTS file:/tmp/ip_list.txt
Required Options
- RHOSTS: The target host(s), range CIDR identifier, or hosts file with syntax ‘file:<path>’
Knowledge Base
MS17-010 fixes RCE in SMBv1, but seems to also have inadvertently added a remote, uncredentialed
patch check information disclosure.
This module can determine if MS17-010 has been patched or not. Specifically, it connects to the
IPC$ tree and attempts a PeekNamedPipe transaction on FID 0.
If the status returned is «STATUS_INSUFF_SERVER_RESOURCES», the machine does not have the MS17-010
patch. After the patch, Win10 returns «STATUS_ACCESS_DENIED» and other Windows versions
«STATUS_INVALID_HANDLE». In case none of these are detected, the module says it was not able to
detect the patch level.
This module does not require valid SMB credentials in default server configurations. It can log on
as the user «» and connect to IPC$.
Vulnerable Application
To use smb_ms17_010, make sure you are able to connect to a SMB service that supports SMBv1.
Verification Steps
The following demonstrates a basic scenario of an unpatched system.
msf > use auxiliary/scanner/smb/smb_ms17_010
msf auxiliary(smb_ms17_010) > set RHOSTS 192.168.1.104
RHOSTS => 192.168.1.104
msf auxiliary(smb_ms17_010) > run
[*] 192.168.1.104:445 - Connected to \192.168.1.104IPC$ with TID = 2048
[*] 192.168.1.104:445 - Received STATUS_INSUFF_SERVER_RESOURCES with FID = 0
[!] 192.168.1.104:445 - Host is likely VULNERABLE to MS17-010!
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
If you run the same scan on the system after patching, you should see the following:
msf auxiliary(smb_ms17_010) > run
[*] 192.168.1.104:445 - Connected to \192.168.1.104IPC$ with TID = 2052
[*] 192.168.1.104:445 - Received STATUS_ACCESS_DENIED with FID = 0
[+] 192.168.1.104:445 - Host does NOT appear vulnerable.
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Options
By default, the smb_ms17_010 module only requires the RHOSTS option to run. In a default configuration,
you will not need valid credentials to connect to the IPC$ share. But, if you have them, it can’t hurt.
The SMBUser option
If you are testing a specific user, use this option.
set SMBUser [user name]
The SMBPass option
If you are testing a specific password, use this option.
set SMBPass [password]
Go back to menu.
Msfconsole Usage
Here is how the scanner/smb/smb_ms17_010 auxiliary module looks in the msfconsole:
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > show info
Name: MS17-010 SMB RCE Detection
Module: auxiliary/scanner/smb/smb_ms17_010
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
Sean Dillon <[email protected]>
Luke Jennings
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /opt/metasploit-framework/embedded/framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
Description:
Uses information disclosure to determine if MS17-010 has been
patched or not. Specifically, it connects to the IPC$ tree and
attempts a transaction on FID 0. If the status returned is
"STATUS_INSUFF_SERVER_RESOURCES", the machine does not have the
MS17-010 patch. If the machine is missing the MS17-010 patch, the
module will check for an existing DoublePulsar (ring 0
shellcode/malware) infection. This module does not require valid SMB
credentials in default server configurations. It can log on as the
user "" and connect to IPC$.
References:
https://nvd.nist.gov/vuln/detail/CVE-2017-0143
https://nvd.nist.gov/vuln/detail/CVE-2017-0144
https://nvd.nist.gov/vuln/detail/CVE-2017-0145
https://nvd.nist.gov/vuln/detail/CVE-2017-0146
https://nvd.nist.gov/vuln/detail/CVE-2017-0147
https://nvd.nist.gov/vuln/detail/CVE-2017-0148
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2017/MS17-010
https://zerosum0x0.blogspot.com/2017/04/doublepulsar-initial-smb-backdoor-ring.html
https://github.com/countercept/doublepulsar-detection-script
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Also known as:
DOUBLEPULSAR
ETERNALBLUE
Module Options
This is a complete list of options available in the scanner/smb/smb_ms17_010 auxiliary module:
msf6 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /opt/metasploit-framework/embedded/framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
Advanced Options
Here is a complete list of advanced options supported by the scanner/smb/smb_ms17_010 auxiliary module:
msf6 auxiliary(scanner/smb/smb_ms17_010) > show advanced
Module advanced options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
ConnectTimeout 10 yes Maximum number of seconds to establish a TCP connection
DCERPC::ReadTimeout 10 yes The number of seconds to wait for DCERPC responses
NTLM::SendLM true yes Always send the LANMAN response (except when NTLMv2_session is specified)
NTLM::SendNTLM true yes Activate the 'Negotiate NTLM key' flag, indicating the use of NTLM responses
NTLM::SendSPN true yes Send an avp of type SPN in the ntlmv2 client blob, this allows authentication on Windows 7+/Server 2008 R2+ when SPN is required
NTLM::UseLMKey false yes Activate the 'Negotiate Lan Manager Key' flag, using the LM key when the LM response is sent
NTLM::UseNTLM2_session true yes Activate the 'Negotiate NTLM2 key' flag, forcing the use of a NTLMv2_session
NTLM::UseNTLMv2 true yes Use NTLMv2 instead of NTLM2_session when 'Negotiate NTLM2' key is true
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
SMB::AlwaysEncrypt true yes Enforces encryption even if the server does not require it (SMB3.x only). Note that when it is set to false, the SMB client will still encrypt the communication if the server requires it
SMB::ChunkSize 500 yes The chunk size for SMB segments, bigger values will increase speed but break NT 4.0 and SMB signing
SMB::Native_LM Windows 2000 5.0 yes The Native LM to send during authentication
SMB::Native_OS Windows 2000 2195 yes The Native OS to send during authentication
SMB::ProtocolVersion 1,2,3 yes One or a list of coma-separated SMB protocol versions to negotiate (e.g. "1" or "1,2" or "2,3,1")
SMB::VerifySignature false yes Enforces client-side verification of server response signatures
SMBDirect true no The target port is a raw SMB service (not NetBIOS)
SMBName *SMBSERVER yes The NetBIOS hostname (required for port 139 connections)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCipher no String for SSL cipher - "DHE-RSA-AES256-SHA" or "ADH"
SSLVerifyMode PEER no SSL verification method (Accepted: CLIENT_ONCE, FAIL_IF_NO_PEER_CERT, NONE, PEER)
SSLVersion Auto yes Specify the version of SSL/TLS to be used (Auto, TLS and SSL23 are auto-negotiate) (Accepted: Auto, TLS, SSL23, SSL3, TLS1, TLS1.1, TLS1.2)
ShowProgress true yes Display progress messages during a scan
ShowProgressPercent 10 yes The interval in percent that progress should be shown
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Auxiliary Actions
This is a list of all auxiliary actions that the scanner/smb/smb_ms17_010 module can do:
msf6 auxiliary(scanner/smb/smb_ms17_010) > show actions
Auxiliary actions:
Name Description
---- -----------
Evasion Options
Here is the full list of possible evasion options supported by the scanner/smb/smb_ms17_010 auxiliary module in order to evade defenses (e.g. Antivirus, EDR, Firewall, NIDS etc.):
msf6 auxiliary(scanner/smb/smb_ms17_010) > show evasion
Module evasion options:
Name Current Setting Required Description
---- --------------- -------- -----------
DCERPC::fake_bind_multi true no Use multi-context bind calls
DCERPC::fake_bind_multi_append 0 no Set the number of UUIDs to append the target
DCERPC::fake_bind_multi_prepend 0 no Set the number of UUIDs to prepend before the target
DCERPC::max_frag_size 4096 yes Set the DCERPC packet fragmentation size
DCERPC::smb_pipeio rw no Use a different delivery method for accessing named pipes (Accepted: rw, trans)
SMB::obscure_trans_pipe_level 0 yes Obscure PIPE string in TransNamedPipe (level 0-3)
SMB::pad_data_level 0 yes Place extra padding between headers and data (level 0-3)
SMB::pad_file_level 0 yes Obscure path names used in open/create (level 0-3)
SMB::pipe_evasion false yes Enable segmented read/writes for SMB Pipes
SMB::pipe_read_max_size 1024 yes Maximum buffer size for pipe reads
SMB::pipe_read_min_size 1 yes Minimum buffer size for pipe reads
SMB::pipe_write_max_size 1024 yes Maximum buffer size for pipe writes
SMB::pipe_write_min_size 1 yes Minimum buffer size for pipe writes
TCP::max_send_size 0 no Maxiumum tcp segment size. (0 = disable)
TCP::send_delay 0 no Delays inserted before every send. (0 = disable)
Go back to menu.
Error Messages
This module may fail with the following error messages:
- Host is likely INFECTED with DoublePulsar! — Arch: <ARCH>, XOR Key: 0x<XOR_KEY>
- Host does NOT appear vulnerable.
- Unable to properly detect if host is vulnerable.
- An SMB Login Error occurred while connecting to the IPC$ tree.
- ErrorClass
Check for the possible causes from the code snippets below found in the module source code. This can often times help in identifying the root cause of the problem.
Host is likely INFECTED with DoublePulsar! — Arch: <ARCH>, XOR Key: 0x<XOR_KEY>
Here is a relevant code snippet related to the «Host is likely INFECTED with DoublePulsar! — Arch: <ARCH>, XOR Key: 0x<XOR_KEY>» error message:
118: code, signature1, signature2 = do_smb_doublepulsar_probe(tree_id)
119:
120: if code == 0x51
121: xor_key = calculate_doublepulsar_xor_key(signature1).to_s(16).upcase
122: arch = calculate_doublepulsar_arch(signature2)
123: print_warning("Host is likely INFECTED with DoublePulsar! - Arch: #{arch}, XOR Key: 0x#{xor_key}")
124: report_vuln(
125: host: ip,
126: name: "MS17-010 DoublePulsar Infection",
127: refs: self.references,
128: info: "MultiPlexID += 0x10 on Trans2 request - Arch: #{arch}, XOR Key: 0x#{xor_key}"
Host does NOT appear vulnerable.
Here is a relevant code snippet related to the «Host does NOT appear vulnerable.» error message:
145: )
146: end
147: end
148: elsif status == "STATUS_ACCESS_DENIED" or status == "STATUS_INVALID_HANDLE"
149: # STATUS_ACCESS_DENIED (Windows 10) and STATUS_INVALID_HANDLE (others)
150: print_error("Host does NOT appear vulnerable.")
151: else
152: print_error("Unable to properly detect if host is vulnerable.")
153: end
154:
155: unless (fp_match = Recog::Nizer.match('smb.native_os', simple.client.peer_native_os)).nil?
Unable to properly detect if host is vulnerable.
Here is a relevant code snippet related to the «Unable to properly detect if host is vulnerable.» error message:
147: end
148: elsif status == "STATUS_ACCESS_DENIED" or status == "STATUS_INVALID_HANDLE"
149: # STATUS_ACCESS_DENIED (Windows 10) and STATUS_INVALID_HANDLE (others)
150: print_error("Host does NOT appear vulnerable.")
151: else
152: print_error("Unable to properly detect if host is vulnerable.")
153: end
154:
155: unless (fp_match = Recog::Nizer.match('smb.native_os', simple.client.peer_native_os)).nil?
156: report_host(
157: host: rhost,
An SMB Login Error occurred while connecting to the IPC$ tree.
Here is a relevant code snippet related to the «An SMB Login Error occurred while connecting to the IPC$ tree.» error message:
164:
165: rescue ::Interrupt
166: print_status("Exiting on interrupt.")
167: raise $!
168: rescue ::Rex::Proto::SMB::Exceptions::LoginError
169: print_error("An SMB Login Error occurred while connecting to the IPC$ tree.")
170: rescue ::Exception => e
171: print_error("#{e.class}: #{e.message}")
172: ensure
173: disconnect
174: end
ErrorClass
Here is a relevant code snippet related to the «ErrorClass» error message:
212: # convert packet to response struct
213: pkt = Rex::Proto::SMB::Constants::SMB_TRANS_RES_HDR_PKT.make_struct
214: pkt.from_s(bytes[4..-1])
215:
216: # convert error code to string
217: code = pkt['SMB'].v['ErrorClass']
218: smberr = Rex::Proto::SMB::Exceptions::ErrorCode.new
219:
220: return smberr.get_error(code)
221: end
222:
Go back to menu.
- #15217 Merged Pull Request: Combine eternalblue modules
- #14294 Merged Pull Request: Allow adding details to CheckCodes
- #13417 Merged Pull Request: SMBv3 integration with Framework
- #11878 Merged Pull Request: Add tab completion and MS17-010 support to analyze command
- #11873 Merged Pull Request: Add mixin to implement an exploit’s check method by invoking a scanner
- #10570 Merged Pull Request: AKA Metadata Refactor
- #9618 Merged Pull Request: Add mixin for smb pipe auditing
- #9299 Merged Pull Request: Add arch to smb_ms17_010 MS17-010 detection
- #8822 Merged Pull Request: Make DoublePulsar check optional for MS17-010 scanner
- #8716 Merged Pull Request: Print_Status -> Print_Good (And OCD bits ‘n bobs)
- #8629 Merged Pull Request: add ‘Also known as’, AKA ‘AKA’, to module references
- #8309 Merged Pull Request: Add arch to smb_ms17_010 DOUBLEPULSAR detection
- #8271 Merged Pull Request: Added DoublePulsar detection to MS17-010 scanner module
References
- CVE-2017-0143
- CVE-2017-0144
- CVE-2017-0145
- CVE-2017-0146
- CVE-2017-0147
- CVE-2017-0148
- MS17-010
- https://zerosum0x0.blogspot.com/2017/04/doublepulsar-initial-smb-backdoor-ring.html
- https://github.com/countercept/doublepulsar-detection-script
- https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
See Also
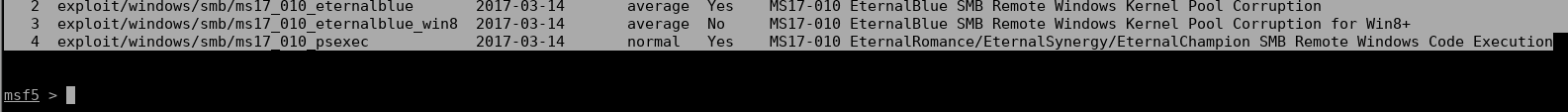
Check also the following modules related to this module:
- auxiliary/admin/smb/ms17_010_command
- exploit/windows/smb/ms17_010_eternalblue
- exploit/windows/smb/ms17_010_eternalblue_win8
- exploit/windows/smb/ms17_010_psexec
- exploit/windows/smb/smb_doublepulsar_rce
- auxiliary/scanner/smb/smb_enum_gpp
- auxiliary/scanner/smb/smb_enumshares
- auxiliary/scanner/smb/smb_enumusers
- auxiliary/scanner/smb/smb_enumusers_domain
- auxiliary/scanner/smb/smb_login
- auxiliary/scanner/smb/smb_lookupsid
- auxiliary/scanner/smb/smb_uninit_cred
- auxiliary/scanner/smb/smb_version
- auxiliary/scanner/smb/impacket/dcomexec
- auxiliary/scanner/smb/impacket/secretsdump
- auxiliary/scanner/smb/impacket/wmiexec
- auxiliary/scanner/smb/pipe_auditor
- auxiliary/scanner/smb/pipe_dcerpc_auditor
- auxiliary/scanner/smb/psexec_loggedin_users
- auxiliary/dos/smb/smb_loris
- auxiliary/fuzzers/smb/smb_create_pipe
- auxiliary/fuzzers/smb/smb_create_pipe_corrupt
- auxiliary/fuzzers/smb/smb_negotiate_corrupt
- auxiliary/fuzzers/smb/smb_ntlm1_login_corrupt
- auxiliary/fuzzers/smb/smb_tree_connect
- auxiliary/fuzzers/smb/smb_tree_connect_corrupt
- exploit/windows/smb/smb_delivery
- exploit/windows/smb/smb_relay
- exploit/windows/smb/smb_rras_erraticgopher
- exploit/windows/smb/smb_shadow
- post/linux/busybox/smb_share_root
- auxiliary/scanner/sap/sap_smb_relay
- auxiliary/admin/http/typo3_sa_2010_020
- exploit/windows/fileformat/office_ms17_11882
Related Nessus plugins:
- MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (WannaCry) (EternalRocks) (Petya)
- MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (WannaCry) (EternalRocks) (Petya) (uncredentialed check)
- SMB Server DOUBLEPULSAR Backdoor / Implant Detection (EternalRocks)
- Sean Dillon <[email protected]>
- Luke Jennings
Version
This page has been produced using Metasploit Framework version 6.1.28-dev. For more modules, visit the Metasploit Module Library.
Go back to menu.
-
Перейти на CTF площадку Игры Кодебай
Выполняйте задания по кибербезопасности в формате CTF и получайте бесценный опыт. Ознакомиться с подробным описанием можно тут.
-
B правой части каждого сообщения есть стрелки ⇧ и ⇩. Не стесняйтесь оценивать ответы. Чтобы автору вопроса закрыть свой тикет, надо выбрать лучший ответ. Просто нажмите значок ✔ в правой части сообщения.
-
#1
Ну что вопрос краток… Не знаю что случилось… РАньше работало, вот в этот счаствый день что то не так
При запуске
Код:
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhost 173.44.205.138
rhost => 173.44.205.138
msf5 auxiliary(scanner/smb/smb_ms17_010) > run
[-] 173.44.205.138:445 - An SMB Login Error occurred while connecting to the IPC$ tree.
[*] 173.44.205.138:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedНужно править что то в msf или искать это, и менять в файле, иль просто покажите актуальный лог и пас для него.) Или не в этом проблема?
-
#2
Та же беда , ждём товарищей по опытные)
-
#3
я так понимаю, более не уязвим
-
#5
не все, но уязвимость почти не актуальна. зайди в шодан, и вбей 445 порт, из 2 двух доступных сраниц будет уязвимо ноль.
речь идет об анонимном пользователе smb который отключен на стороне сервера
-
#6
не все, но уязвимость почти не актуальна. зайди в шодан, и вбей 445 порт, из 2 двух доступных сраниц будет уязвимо ноль.
речь идет об анонимном пользователе smb который отключен на стороне сервера
Да дело в том что это не в глобальной сети проверяю, в локалке, и странно что на пиратской 7 вдруг эту уязвимость пропатчили
-
#7
Да дело в том что это не в глобальной сети проверяю, в локалке, и странно что на пиратской 7 вдруг эту уязвимость пропатчили
хочешь сказать раньше работало, а сейчас не работает? обновления у жертвы включены? у меня сёма пиратка стоит с выключенными обновлениями, и она уязвима.
-
#8
хочешь сказать раньше работало, а сейчас не работает? обновления у жертвы включены? у меня сёма пиратка стоит с выключенными обновлениями, и она уязвима.
Раньше не проверял , конкретно на той машине, года 2 назад как вышла уязвимость работало, но опять же не на этой. Так что просто непонятно.
-
#9
Раньше не проверял , конкретно на той машине, года 2 назад как вышла уязвимость работало, но опять же не на этой. Так что просто непонятно.
ну значит более не уязвим. можно пробовать не использую auxiliary а сразу этерналблю. а лучше этерналблюДаблпульсар. если етерналблю не работает то может сработать даблпульсар как было в моем случаи. не знаю мужде ними разницу, но профит есть
-
#10
Ну что вопрос краток… Не знаю что случилось… РАньше работало, вот в этот счаствый день что то не так
При запускеКод:
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhost 173.44.205.138 rhost => 173.44.205.138 msf5 auxiliary(scanner/smb/smb_ms17_010) > run [-] 173.44.205.138:445 - An SMB Login Error occurred while connecting to the IPC$ tree. [*] 173.44.205.138:445 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completedНужно править что то в msf или искать это, и менять в файле, иль просто покажите актуальный лог и пас для него.) Или не в этом проблема?
А порт еще открыт, можешь достучаться? Можно попробовать бахнуть сразу эксплоитом, если цель неуязвима — сразу будет понятно.
-
2019-11-19 16_03_03-Working Clone Kali xfce — VMware Workstation.png
4,7 КБ
· Просмотры: 491
f22
Codeby Team
-
#11
Та же беда , ждём товарищей по опытные)
я так понимаю, более не уязвим
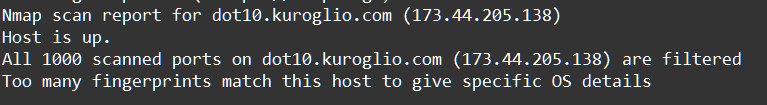
Друзья, откуда у вас вообще уверенность, что там Windows?
Ну банальный nmap покажет вам что и как
nmap -sV -O -A ${ip}
там конкретно видно и по открытым портам что винда
Там это где?
И какие порты открыты?
-
#12
Друзья, откуда у вас вообще уверенность, что там Windows?
Ну банальный nmap покажет вам что и как
nmap -sV -O -A ${ip}Посмотреть вложение 35043
Спасибо конечно, но что такое nmap вроде знаем) не на столько все плохо, там конкретно видно и по открытым портам что винда, и какая версия из заголовков
-
#13
Там это где?
И какие порты открыты?
445 и 135
В локальной сети
Скриншот сделать не могу, я сейчас не на месте. Но в базовом использовании nmap я уверен.
-
#14
Ты же понимаешь что этот порт не относится к данной уязвимости, это порт http и он открыт на тех же роутерах и вообще к чему ты это.
-
#15
Там это где?
И какие порты открыты?
Сорь,я держал в голове тему самой проблемы сканера уязвимости, не заметив что была упомянута цель. Так что я вел диалог не совсем поняв что вы собственно о ней. Моя проблема была не в этой цели, а в сканере в целом.
an smb login error occurred while connecting to the ipc$ tree about metasploit-framework HOT 3 CLOSED
Comments (3)
Hey @TGH75972 , Can you provide the steps to reproduce the bug and the msfconsole output?
That would be helpful in tracking down the issue. 🙂
github-actions commented on January 11, 2023
This issue has been left open with no activity for a while now.
We get a lot of issues, so we currently close issues after 60 days of inactivity. It’s been at least 30 days since the last update here.
If we missed this issue or if you want to keep it open, please reply here. You can also add the label «not stale» to keep this issue open!
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
github-actions commented on January 11, 2023
It’s been 60 days since anything happened on this issue, so we are going to close it.
Please keep in mind that I’m only a robot, so if I’ve closed this issue in error please feel free to reopen this issue or create a new one if you need anything else.
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
Related Issues (20)
- Why only android/meterpreter/reverse_https is slow and timing out ? HOT 1
- Write module for Lenovo Diagnostics Driver Exploit CVE-2022-3699 HOT 9
- Error running command download: Rex::TimeoutError Operation timed out.
- Msfvenom Error: Read-only file system @ rb_sysopen HOT 1
- Windows Secrets Dump Crashes With Kerberos HOT 1
- msfvenom hangs / takes long with some formats (csharp) HOT 1
- Can’t capture my android webcam (stdapi_webcam_start: Operation failed: 1) with meterpreter/reverse_tcp
- Post #write_file Does Not Return Failure Indicator On Unix HOT 1
- Integrate Creds to Modules (autofill) HOT 1
- Crack NetNTLM In crack_windows HOT 1
- Difference in store_loot db behavior when connected remotely
- Update smb_version to output host information when smb1 is disabled HOT 5
- Metasploit 6.2.31 Kali nethunter HOT 1
- get_env(«TEMP») gives wrong results HOT 4
- favorites enhancement HOT 2
- Exploit failed: NoMethodError undefined method `smtp_send_recv’ for # HOT 1
- does metasploit have a exploit that allows you to inject a script into any website the target visits and if not could someone link me a tutorial or tell me how without using a mitm attack HOT 1
- problem with setting up the metasploit database correctly. HOT 3
- meta HOT 1
- ldap_query fails on schema extraction when specifying base_dn as child DC
Recommend Projects
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
TensorFlow
An Open Source Machine Learning Framework for Everyone
Django
The Web framework for perfectionists with deadlines.
Laravel
A PHP framework for web artisans
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
Some thing interesting about web. New door for the world.
server
A server is a program made to process requests and deliver data to clients.
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
Visualization
Some thing interesting about visualization, use data art
Some thing interesting about game, make everyone happy.
Recommend Org
We are working to build community through open source technology. NB: members must have two-factor auth.
Microsoft
Open source projects and samples from Microsoft.
Источник
an smb login error occurred while connecting to the ipc$ tree #15979
Comments
TGH75972 commented Dec 19, 2021
an smb login error occurred while connecting to the ipc$ tree this issue is coming when i am using msfconsole and when i try to connect with an open port with a host then it comes , exploits like eternal blue and many other , and it gives me no session
The text was updated successfully, but these errors were encountered:
3V3RYONE commented Dec 22, 2021
Hey @TGH75972 , Can you provide the steps to reproduce the bug and the msfconsole output?
That would be helpful in tracking down the issue. 🙂
github-actions bot commented Jan 21, 2022
This issue has been left open with no activity for a while now.
We get a lot of issues, so we currently close issues after 60 days of inactivity. It’s been at least 30 days since the last update here.
If we missed this issue or if you want to keep it open, please reply here. You can also add the label «not stale» to keep this issue open!
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
github-actions bot commented Feb 21, 2022
It’s been 60 days since anything happened on this issue, so we are going to close it.
Please keep in mind that I’m only a robot, so if I’ve closed this issue in error please feel free to reopen this issue or create a new one if you need anything else.
As a friendly reminder: the best way to see this issue, or any other, fixed is to open a Pull Request.
Footer
© 2023 GitHub, Inc.
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
1337red
Penetration Testing, Social Engineering and Red Teaming – By @myexploit2600 & @5ub34x
MS17-010 – The Nuke
The Start
This is my 1st blog post for 1337red, so I wanted it to be good. Now I can happily talk for ages on security, but this, writing a blog, I felt stuck, so why?
Well, I have ideas, quite a few if honest, but nothing seems worthy of a post.
So in my typical, backwards, and slightly broken style, I’m just going to open on a subject which details a process, that I said I would never use. In fact, just to prove this, there is a recording of me saying this very statement Enemies of the West – Neil Lines – Bsides London in front of a few hundred people at 2017 Bsides London.
The calm before the storm
It is now possible to simply walk in to a client’s office, plug in your own laptop, gain an IP address and using the Metasploit Framework’s (MSF) ms17_010_eternalblue exploit, target a domain controller (DC) and gain access to accounts belonging to the Domain Admins (DA) or Enterprise Admins group.
If all goes to plan (and this is a very big if), there is no requirement for any other typical pentesting tools or techniques.
Oh wait, what, how can I be saying this
I’ll be honest, I hate this idea, I love tools, I love the chase of the DA, this is not something I like to rush. I like to earn it, but we can no longer bury our heads in the sand and I can no longer ignore MS17-010.
The back story, let’s be honest it’s no longer interesting. NSA had toys, Shadow Brokers found / stole / hacked the toys, then released the toys, and for a few days the world nearly stopped.
WANNACRY used the ETERNALBLUE exploit
» data-medium-file=»https://1337red.files.wordpress.com/2017/10/w1.png?w=300″ data-large-file=»https://1337red.files.wordpress.com/2017/10/w1.png?w=756″ src=»https://1337red.files.wordpress.com/2017/10/w1.png?w=615&h=357″ height=»357″ alt=»» width=»615″> WANNACRY used the ETERNALBLUE exploit The fallout of WANNACRY massively affected the NHS
» data-medium-file=»https://1337red.files.wordpress.com/2017/10/w2.png?w=300″ data-large-file=»https://1337red.files.wordpress.com/2017/10/w2.png?w=756″ src=»https://1337red.files.wordpress.com/2017/10/w2.png?w=599&h=340″ height=»340″ alt=»» width=»599″> The fallout of WANNACRY massively affected the NHS
Following this the MS17_010_eternalblue exploit was added to msf. Now anyone can use it (you could even teach your Nan to do this), but without a little respect, or understanding, you will most likely reboot your target. And let’s be honest everyone loves the pentester who bounces a DC, right?
So if you want to use a nuke, and potentially survive, this is the guide on how you could do it.
The Domain Controller
So what is a Domain Controller? Now I’m no MCSE, but what I can tell you is the DC is used to centrally manage and administrator (via active directory services) all domain joined machines in one central place. Think of it as the most important server in a windows environment. Typically, people have multiple DCs and these multiple servers replicate the contained data, this offers resilience and load balancing.
So how do you hunt out the DC
The simplest way to identify a potential DC is via the windows ipconfig / all command from your own laptop. Assuming you have gained an IP address via DHCP, you will have also been assigned an IP address for the local DNS server. The DNS server is typically configured on the same server as the DC.
Find the DNS service find the DC
I’m not going to get into the hows and whys of why is the DNS service typically installed on the DC in this post. To summarize, DNS is offered as a service during active directory creation. Download a trial copy of Windows server, install, start CMD and type DCPROMO and follow the prompts.
In my home lab, my DNS Server IP address is 192.168.56.200 and like most environments this DNS service sits on a DC. You can see an extract of the result of me running ipconfig / all on my lab machine below.
When I’m using Kali Linux, I tend to use Nmap to help me enumerate any potential DCs via port scanning techniques. To do this, I look for any devices that offer DNS as a service.
Domain Name System (DNS) uses TCP/UDP port 53. To enumerate all internal devices that have port TCP/53 enabled run the following command.
Below shows the full results of a typical Nmap scan of the suspected DC. The inclusion of the open ldap, kpasswd5, http-rpc-epmap, ldapssl and globalcatLDAP ports, are also typically connected to a DC server.
Once you have an IP list of all devices that support DNS you need to verify the operating system (OS) versions for each one.
As we are hunting for a DC we are only interested in windows based machines
To do this quickly, you can use MSF or Nmap. The following quick overview shows operating system enumeration using both of these tools.
MSF
Nmap
You can also use the -O (Enable OS detection) switch, the results of using this can be seen directly below.
Alternatively, you can use -A to also enable OS detection, again the results of using this switch can be seen directly below.
Personally I preference MSF smb_version because it’s quick to use and the results are simple to view
Once you have your list of potential targets, it’s time to narrow this list down to only include those that are missing the ms17_010 patch. To do this, you can use MSF smb_ms17_010 scanner.
Directly below details how to use the scanner.
From the above results you can see two potential hosts (Windows 7 Enterprise and Windows Server 2008 R2) which are potentially vulnerable to MS17-010.
And this is where you can easily start to go wrong
ms17_010_eternalblue is a 64bit exploit, and as such any 32bit machine you target with it, will very likely result in a crash, resulting in a system reboot.
Below details an example of this exploit crashing a 32bit copy of Windows 7 Enterprise.

» data-medium-file=»https://1337red.files.wordpress.com/2017/10/ms17.png?w=300″ data-large-file=»https://1337red.files.wordpress.com/2017/10/ms17.png?w=756″ src=»https://1337red.files.wordpress.com/2017/10/ms17.png?w=592&h=233″ height=»233″ alt=»» width=»592″> MSF starting to run MS17-010 exploit Impact of running MS17-010 exploit against 32BIT machine
» data-medium-file=»https://1337red.files.wordpress.com/2017/10/impact1.png?w=300″ data-large-file=»https://1337red.files.wordpress.com/2017/10/impact1.png?w=743″ src=»https://1337red.files.wordpress.com/2017/10/impact1.png?w=565&h=493″ height=»493″ alt=»» width=»565″> Impact of running MS17-010 exploit against 32BIT machine
Directly below you can see the response from the MSF console during running of the exploit.
If you have seen the above failed response before in MSF, you have most likely caused the target machine to reboot.
Windows 7 32bit
Windows 7 was released offering users a 32bit and 64bit version, the 32 bit was the most commonly installed, and as such, I personally would not target a windows 7 machine. You can see from the above enumeration, that it’s not clear if a machine is a 32bit or 64bit version, but server 2008 R2 was only released as a 64bit version OS.
So when running eternalblue against a server 2008 R2 target the associated risks, fall more in line with running any other exploit.
The following details the results of targeting the DC in my home lab.
As you can see it completes successfully against the server 2008 R2 and it results in CMD access to the device.
Where is the meterpreter?
If you look at the above configuration, no payload was configured, resulting in the default payload been used. Thats not meterpreter, so how do you get a meterpreter shell?
A nice trick were applicable is to opt for a x64 meterpreter reverse_tcp payload, as 64 bit processes tend to bypass AV ;0)
Then to interact with the session run the following command.
At this point it’s a good time to migrate to a process which will be more stable, to do this type the ps command. This will show you all the running processes. winlogin is a good option because as you can see below it is 64 bit process, it runs as system and migrating into the winlogin process will not cause any impact on any presently authenticated users.
To migrate into the winlogon.exe process simply type the correlating PID number as can be seen directly below.
So how do you verify you’re on a DC? The windows command systeminfo will reveal what the servers function is under the OS Configuration option, see directly below.
Or you can use the meterpreter enum_domain_tokens post script which also reveals if you’re on a DC or not, see below.
So we’re on a DC and at this point you may want to grab all the users password hashes. You could just run hashdump which you can see the result of directly below.
I won’t lie to you, hashdump is fine on a standard workstation, server, or laptop, but with a DC I have had experiences were it has caused the DC to reboot.
So a neat trick is to use the domain_hashdump post script, which is a lot safer to use.
To run the domain_hashdump script you need to background your meterpreter session, load domain_hashdump, target your chosen session and run.
And the results, see below.
Collate all of the hashes then in Kali Linux, either using gedit or nano (don’t mention vim to me) and paste the hashes in.
You can try your luck by simply running the hashes through John’s pot file see below.
Or you can use a word list such as Rocktastic, below I’m using a custom dictionary.
No password hashes left to crack (see FAQ)
I have cracked my lab DC hashes over and over, as such they are in the john pot file and it will no longer reveal the password unless you specify it to do so, to specify that it does reveal previously reversed passwords use the –show switch.
And finally, you’re on a DC so you can add an account, and assign it to the domain administrative group if you need to?
RDP to the DC using the added creds
» data-medium-file=»https://1337red.files.wordpress.com/2017/10/rdp1.png?w=280″ data-large-file=»https://1337red.files.wordpress.com/2017/10/rdp1.png?w=669″ src=»https://1337red.files.wordpress.com/2017/10/rdp1.png?w=442&h=453″ height=»453″ alt=»» width=»442″> RDP to the DC using the added creds
Below you can see the created myexploit account belongs to the domain administrators group.
Access to the DC and AD
» data-medium-file=»https://1337red.files.wordpress.com/2017/10/rdp2.png?w=300″ data-large-file=»https://1337red.files.wordpress.com/2017/10/rdp2.png?w=756″ src=»https://1337red.files.wordpress.com/2017/10/rdp2.png?w=618&h=524″ height=»524″ alt=»» width=»618″> Access to the DC and AD
This is the end
Where a DC is built on server 2008 R2 and it has not been patched with MS17-010, yes, you could most likely simply run ms17_010_eternalblue and get DA, but where is the fun in that?
Secondly, it is not a good result for a client, who will want to know that the whole domain has been fully reviewed, all that said and done, I wouldn’t rule out using ms17_010_eternalblue, but would only consider it after all other options have been fully tested.
Источник
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
## # auxiliary/scanner/smb/smb_ms_17_010
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::SMB::Client
include Msf::Exploit::Remote::SMB::Client::Authenticated
include Msf::Auxiliary::Scanner
include Msf::Auxiliary::Report
def initialize(info = {})
super(update_info(info,
'Name' => 'MS17-010 SMB RCE Detection',
'Description' => %q{
Uses information disclosure to determine if MS17-010 has been patched or not.
Specifically, it connects to the IPC$ tree and attempts a transaction on FID 0.
If the status returned is "STATUS_INSUFF_SERVER_RESOURCES", the machine does
not have the MS17-010 patch.
This module does not require valid SMB credentials in default server
configurations. It can log on as the user "" and connect to IPC$.
},
'Author' => [ 'Sean Dillon <[email protected]>' ],
'References' =>
[
[ 'CVE', '2017-0143'],
[ 'CVE', '2017-0144'],
[ 'CVE', '2017-0145'],
[ 'CVE', '2017-0146'],
[ 'CVE', '2017-0147'],
[ 'CVE', '2017-0148'],
[ 'MSB', 'MS17-010'],
[ 'URL', 'https://technet.microsoft.com/en-us/library/security/ms17-010.aspx']
],
'License' => MSF_LICENSE
))
end
def run_host(ip)
begin
status = do_smb_probe(ip)
if status == "STATUS_INSUFF_SERVER_RESOURCES"
print_warning("Host is likely VULNERABLE to MS17-010!")
report_vuln(
host: ip,
name: self.name,
refs: self.references,
info: 'STATUS_INSUFF_SERVER_RESOURCES for FID 0 against IPC$'
)
elsif status == "STATUS_ACCESS_DENIED" or status == "STATUS_INVALID_HANDLE"
# STATUS_ACCESS_DENIED (Windows 10) and STATUS_INVALID_HANDLE (others)
print_good("Host does NOT appear vulnerable.")
else
print_bad("Unable to properly detect if host is vulnerable.")
end
rescue ::Interrupt
print_status("Exiting on interrupt.")
raise $!
rescue ::Rex::Proto::SMB::Exceptions::LoginError
print_error("An SMB Login Error occurred while connecting to the IPC$ tree.")
rescue ::Exception => e
vprint_error("#{e.class}: #{e.message}")
ensure
disconnect
end
end
def do_smb_probe(ip)
connect
# logon as user
simple.login(datastore['SMBName'], datastore['SMBUser'], datastore['SMBPass'], datastore['SMBDomain'])
# connect to IPC$
ipc_share = "\\#{ip}\IPC$"
simple.connect(ipc_share)
tree_id = simple.shares[ipc_share]
print_status("Connected to #{ipc_share} with TID = #{tree_id}")
# request transaction with fid = 0
pkt = make_smb_trans_ms17_010(tree_id)
sock.put(pkt)
bytes = sock.get_once
# convert packet to response struct
pkt = Rex::Proto::SMB::Constants::SMB_TRANS_RES_HDR_PKT.make_struct
pkt.from_s(bytes[4..-1])
# convert error code to string
code = pkt['SMB'].v['ErrorClass']
smberr = Rex::Proto::SMB::Exceptions::ErrorCode.new
status = smberr.get_error(code)
print_status("Received #{status} with FID = 0")
status
end
def make_smb_trans_ms17_010(tree_id)
# make a raw transaction packet
pkt = Rex::Proto::SMB::Constants::SMB_TRANS_PKT.make_struct
simple.client.smb_defaults(pkt['Payload']['SMB'])
# opcode 0x23 = PeekNamedPipe, fid = 0
setup = "x23x00x00x00"
setup_count = 2 # 2 words
trans = "\PIPE\x00"
# calculate offsets to the SetupData payload
base_offset = pkt.to_s.length + (setup.length) - 4
param_offset = base_offset + trans.length
data_offset = param_offset # + 0
# packet baselines
pkt['Payload']['SMB'].v['Command'] = Rex::Proto::SMB::Constants::SMB_COM_TRANSACTION
pkt['Payload']['SMB'].v['Flags1'] = 0x18
pkt['Payload']['SMB'].v['Flags2'] = 0x2801 # 0xc803 would unicode
pkt['Payload']['SMB'].v['TreeID'] = tree_id
pkt['Payload']['SMB'].v['WordCount'] = 14 + setup_count
pkt['Payload'].v['ParamCountMax'] = 0xffff
pkt['Payload'].v['DataCountMax'] = 0xffff
pkt['Payload'].v['ParamOffset'] = param_offset
pkt['Payload'].v['DataOffset'] = data_offset
# actual magic: PeekNamedPipe FID=0, PIPE
pkt['Payload'].v['SetupCount'] = setup_count
pkt['Payload'].v['SetupData'] = setup
pkt['Payload'].v['Payload'] = trans
pkt.to_s
end
end
Update April 21, 2017 — There is an active pull request at Metasploit master which adds DoublePulsar infection detection to this module.
During the first Shadow Brokers leak, my colleagues at RiskSense and I reverse engineered and improved the EXTRABACON exploit, which I wrote a feature about for PenTest Magazine. Last Friday, Shadow Brokers leaked FuzzBunch, a Metasploit-like attack framework that hosts a number of Windows exploits not previously seen. Microsoft’s official response says these exploits were fixed up in MS17-010, released in mid-March.
Yet again I find myself tangled up in the latest Shadow Brokers leak. I actually wrote a scanner to detect MS17-010 about 2-3 weeks prior to the leak, judging by the date on my initial pull request to Metasploit master. William Vu, of Rapid7 (and whom coincidentally I met in person the day of the leak), added some improvements as well. It was pulled into the master branch on the day of the leak. This module can be used to scan a network range (RHOSTS) and detect if the patch is missing or not.
Module Information Page
https://rapid7.com/db/modules/auxiliary/scanner/smb/smb_ms17_010
Module Source Code
https://github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/scanner/smb/smb_ms17_010.rb
My scanner module connects to the IPC$ tree and attempts a PeekNamedPipe transaction on FID 0. If the status returned is «STATUS_INSUFF_SERVER_RESOURCES», the machine does not have the MS17-010 patch. After the patch, Win10 returns «STATUS_ACCESS_DENIED» and other Windows versions «STATUS_INVALID_HANDLE». In case none of these are detected, the module says it was not able to detect the patch level (I haven’t seen this in practice).
IPC$ is the «InterProcess Communication» share, which generally does not require valid SMB credentials in default server configurations. Thus this module can usually be done as an unauthed scan, as it can log on as the user «» and connect to IPC$.
This is the most important patch for Windows in almost a decade, as it fixes several remote vulnerabilities for which there are now public exploits (EternalBlue, EternalRomance, and EternalSynergy).
These are highly complex exploits, but the FuzzBunch framework essentially makes the process as easy as point and shoot. EternalRomance does a ridiculous amount of «grooming», aka remote heap feng shui. In the case of EternalBlue, it spawns numerous threads and simultaneously exploits SMBv1 and SMBv2, and seems to talk Cairo, an undocumented SMB LanMan alternative (only known because of the NT4 source code leaks). I haven’t gotten around to looking at EternalSynergy yet.
I am curious to learn more, but have too many side projects at the moment to spend my full efforts investigating further. And unlike EXTRABACON, I don’t see any «obvious» improvements other than I would like to see an open source version.
We have an iXSystems FreeNAS operating in our network, with SMB shared folders assigned to specific users. Those users were able to connect to write to the shared folders, from our laptops. Back then, our Windows 10 were only AAD-registered.
Now we have transitioned everybody to MDM (Intune) enrollment, joining all laptops to AAD in the process. New laptops allocated are provisioned with Windows Autopilot. I have been allocated one such new laptop. With this laptop I am not able to connect to
the shared folders despite keying in the correct credentials (even after password reset) in the Windows Explorer credential prompt.
On peeking at the server-side samba4 log, it appears my computer wants to access the IPC$ share (which there is nothing in FreeNAS to configure such a share).
[2020/07/06 19:15:27.580527, 2] ../../source3/auth/auth.c:316(auth_check_ntlm_password)
check_ntlm_password: authentication for user [user] -> [user]
-> [user] succeeded
[2020/07/06 19:15:27.592802, 1] ../../source3/smbd/smb2_tcon.c:234(smbd_smb2_tree_connect)
smbd_smb2_tree_connect: reject request to share [IPC$] as ‘NASuser’ without encryption or signing. Disconnecting.
From Windows client side event log
Log Name: Microsoft-Windows-SmbClient/Security
Source: Microsoft-Windows-SMBClient
Date: 6/7/2020 19:57:44
Event ID: 31010
Task Category: None
Level: Error
Keywords: (256)
User: N/A
Computer: AAD-LAPTOP
Description:
The SMB client failed to connect to the share.
Error: {Access Denied}
A process has requested access to an object, but has not been granted those access rights.
Path: NASIPC$
Event Xml:
<Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event»>
<System>
<Provider Name=»Microsoft-Windows-SMBClient» Guid=»{GUI}» />
<EventID>31010</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x200000000000100</Keywords>
<TimeCreated SystemTime=»2020-07-06T11:57:44.837154500Z» />
<EventRecordID>487</EventRecordID>
<Correlation />
<Execution ProcessID=»4″ ThreadID=»3536″ />
<Channel>Microsoft-Windows-SmbClient/Security</Channel>
<Computer>AAD-LAPTOP</Computer>
<Security />
</System>
<EventData>
<Data Name=»Reason»>12</Data>
<Data Name=»Status»>3221225506</Data>
<Data Name=»ShareNameLength»>10</Data>
<Data Name=»ShareName»>NASIPC$</Data>
<Data Name=»ObjectNameLength»>0</Data>
<Data Name=»ObjectName»>
</Data>
</EventData>
</Event>
Why does Windows need to access IPC$ when what I need is just the other shared folders?
(I cannot ascertain if the situation is moot and in working order for my older AAD-registered laptop since we’re usually working remotely from home now and rarely enter office.)
UPDATE
I should add that at home, this laptop never gets any credential prompt and outright fails when attempting to access my (Synology) home NAS folders. It only works if I pre-insert credentials in Credential Manager. I’m puzzled why there’s reversal in behaviour
with regards to my home NAS setup.
The melody of logic will always play out the truth. ~ Narumi Ayumu, Spiral
-
Edited by
Wednesday, July 8, 2020 12:17 PM
Recommend Projects
-
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.