Comments
t57ser
pushed a commit
to t57ser/electron
that referenced
this issue
Oct 27, 2021
Fixes: electron#31212
Signed-off-by: Juan Cruz Viotti <jv@jviotti.com>
t57ser
pushed a commit
to t57ser/electron
that referenced
this issue
Oct 27, 2021
Fixes: electron#31212
Signed-off-by: Juan Cruz Viotti <jv@jviotti.com>
t57ser
pushed a commit
to t57ser/electron
that referenced
this issue
Oct 29, 2021
Fixes: electron#31212
Signed-off-by: Juan Cruz Viotti <jv@jviotti.com>
pmer
mentioned this issue
Feb 11, 2022
3 tasks
Коллеги, добрый день!
Нужна помощь с обновлением сертификата.
Обнаружил, что после бэкапа и рестарта зимбы ldap не запустился. Я отключил проверку и запустил zimbra.
[zimbra@mail ~]$ zmlocalconfig -e ldap_starttls_supported=0
при попытке обновления сертификата он всегда ругается как я понимаю на потерянную цепочку в сертификате.
zimbra@vm-mail:~/ssl/letsencrypt$ /opt/zimbra/bin/zmcertmgr verifycrt comm privkey.pem cert.pem chain.pem
** Verifying 'cert.pem' against 'privkey.pem'
Certificate 'cert.pem' and private key 'privkey.pem' match.
** Verifying 'cert.pem' against 'chain.pem'
ERROR: Unable to validate certificate chain: cert.pem: C = US, O = Let's Encrypt, CN = R3
error 2 at 1 depth lookup:unable to get issuer certificate
Я перечитал кучу форумов, обновил certbot, по этой статье https://habr.com/ru/post/580092/ проверил, что ISRG root в доверенных
awk -v cmd='openssl x509 -noout -subject' ' /BEGIN/{close(cmd)};{print | cmd}' < /etc/ssl/certs/ca-certificates.crt | grep "ISRG Root X1"
subject= /C=US/O=Internet Security Research Group/CN=ISRG Root X1
Но при любой попытке обновить сертификат вручную или скриптом для обновлений сертификата получаю verification failed
obtain-and-deploy-letsencrypt-cert.sh: info: start nginx
obtain-and-deploy-letsencrypt-cert.sh: info: assemble cert files
obtain-and-deploy-letsencrypt-cert.sh: info: test and deploy certificates
obtain-and-deploy-letsencrypt-cert.sh: error: Verification of the issued certificate failed.
или если вручную, то
zimbra@vm-mail:~/ssl/letsencrypt$ /opt/zimbra/bin/zmcertmgr verifycrt comm privkey.pem cert.pem chain.pem
** Verifying 'cert.pem' against 'privkey.pem'
Certificate 'cert.pem' and private key 'privkey.pem' match.
** Verifying 'cert.pem' against 'chain.pem'
ERROR: Unable to validate certificate chain: cert.pem: C = US, O = Let's Encrypt, CN = R3
error 2 at 1 depth lookup:unable to get issuer certificate
прошу помощи в решении проблемы!
I followed this guide and I now have a fully working zimbra with up to date certificates.
Replace with your domain
Then:
cp /etc/letsencrypt/live//privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
wget -O /tmp/ISRG-X1.pem
https://letsencrypt.org/certs/isrgrootx1.pem
wget -O /tmp/R3.pem
https://letsencrypt.org/certs/lets-encrypt-r3.pem
The files in /etc/letsencrypt/live/ are symbolic links to files in /etc/letsencrypt/archive/.
Check which files they point at (cert.pem, chain.pem, …)
Then perform this, but replace the part with correct one.
cat /tmp/R3.pem > /etc/letsencrypt/archive//chain.pem
cat /tmp/ISRG-X1.pem >> /etc/letsencrypt/archive//chain.pem
As zimbra (su — zimbra) user perform
/opt/zimbra/bin/zmcertmgr verifycrt comm /opt/zimbra/ssl/zimbra/commercial/commercial.key /etc/letsencrypt/live//cert.pem /etc/letsencrypt/live//chain.pem
If it runs successfully perform deploy. If it gives you file permissions error temporarily do this:
chmod o+rx /etc/letsencrypt/archive
chmod o+rx /etc/letsencrypt/live
And verify the cert again.
You can run certbot-zimbra deploy, or the below one:
I ran certbot_zimbra.sh and selected to use the cert that I already had from the failed previous attempt.
Afterwards remove the extra permissions (as root)
chmod o-rx /etc/letsencrypt/archive
chmod o-rx /etc/letsencrypt/live
Restart zimbra:
zmcontrol restart`
I had to restart the full server to stop issues when I was sending test emails. So something requires a reboot of the system to be fully recognised.
Cheers
Spart
I try to create a DoT Gateway with nginx. However, i get every time when i try to connect via Android private DNS a status 500 response.
My Nginx config looks like this:
stream {
log_format basic '$remote_addr [$time_local] $protocol $status $bytes_sent $bytes_received $session_time $upstream_addr';
upstream dns {
server 8.8.8.8:53;
}
server {
listen 853 ssl;
access_log /var/log/nginx/dot-access.log basic;
error_log /var/log/nginx/dot-error.log;
ssl_certificate /etc/letsencrypt/live/my.domain.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/my.domain.com/privkey.pem;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_session_timeout 4h;
ssl_handshake_timeout 10s;
proxy_pass dns;
}
}
I have tried to solve the error with https://medium.com/@nykolas.z/troubleshooting-dns-over-tls-e7ca570b6337 and https://www.aaflalo.me/2019/03/dns-over-tls/. A test request with https://getdnsapi.net/query/ works fine and i get "status": GETDNS_RESPSTATUS_GOOD. In in /var/log/nginx/dot-access.log i see
185.49.141.27 [01/Oct/2021:11:59:57 +0200] TCP 200 56 130 0.210 8.8.8.8:53
However, if i enter «my.domain.com» in Android private DNS settings, i get the error message «Connection not possible» and in /var/log/nginx/dot-access.log
84.33.44.28 [01/Oct/2021:11:55:01 +0200] TCP 500 0 0 0.131 -
For me, this means that this setup basically works, however not with Android Private DNS. Anyone with ideas?
Время прочтения
3 мин
Просмотры 13K
Как многие знают, вчера закончился сертификат Let’s Encrypt DST Root CA X3, использовавшийся, в том числе и для почтовых серверов Zimbra.
Я прождал до последнего и столкнулся с несколькими проблемами после его истечения, например перестала отправляться почта из системы обработки заявок OTRS и почтового клиента Spark. После некоторой возни было найдено решение по обновлению сертификата с новым корневым CA.
Моя конфигурация — Centos 7.9 и Zimbra 8.8.11
Инструкция по обновлению
Устанавливаем новый certbot
sudo yum install epel-release
sudo yum install snapd
sudo systemctl enable --now snapd.socket
sudo snap install core
sudo rebootПосле перезагрузки Zimbra отказалась запускаться, сославшись на некорректный сертификат, но на всякий случай, я приведу команды в таком порядке, как будто она работает.
Если вы впервые получаете сертификат, замените 3 строку на это:
certbot certonly --standalone --preferred-chain "ISRG Root X1"mail.example.com в 6 строке необходимо заменить на доменное имя вашего почтового сервера
letsencryptCA в 7 строке — файл, содержащий новый корневой сертификат. Вы должны создать его сами и скопировать туда этот текст:
-----BEGIN CERTIFICATE-----
MIIFazCCA1OgAwIBAgIRAIIQz7DSQONZRGPgu2OCiwAwDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
cmNoIEdyb3VwMRUwEwYDVQQDEwxJU1JHIFJvb3QgWDEwHhcNMTUwNjA0MTEwNDM4
WhcNMzUwNjA0MTEwNDM4WjBPMQswCQYDVQQGEwJVUzEpMCcGA1UEChMgSW50ZXJu
ZXQgU2VjdXJpdHkgUmVzZWFyY2ggR3JvdXAxFTATBgNVBAMTDElTUkcgUm9vdCBY
MTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK3oJHP0FDfzm54rVygc
h77ct984kIxuPOZXoHj3dcKi/vVqbvYATyjb3miGbESTtrFj/RQSa78f0uoxmyF+
0TM8ukj13Xnfs7j/EvEhmkvBioZxaUpmZmyPfjxwv60pIgbz5MDmgK7iS4+3mX6U
A5/TR5d8mUgjU+g4rk8Kb4Mu0UlXjIB0ttov0DiNewNwIRt18jA8+o+u3dpjq+sW
T8KOEUt+zwvo/7V3LvSye0rgTBIlDHCNAymg4VMk7BPZ7hm/ELNKjD+Jo2FR3qyH
B5T0Y3HsLuJvW5iB4YlcNHlsdu87kGJ55tukmi8mxdAQ4Q7e2RCOFvu396j3x+UC
B5iPNgiV5+I3lg02dZ77DnKxHZu8A/lJBdiB3QW0KtZB6awBdpUKD9jf1b0SHzUv
KBds0pjBqAlkd25HN7rOrFleaJ1/ctaJxQZBKT5ZPt0m9STJEadao0xAH0ahmbWn
OlFuhjuefXKnEgV4We0+UXgVCwOPjdAvBbI+e0ocS3MFEvzG6uBQE3xDk3SzynTn
jh8BCNAw1FtxNrQHusEwMFxIt4I7mKZ9YIqioymCzLq9gwQbooMDQaHWBfEbwrbw
qHyGO0aoSCqI3Haadr8faqU9GY/rOPNk3sgrDQoo//fb4hVC1CLQJ13hef4Y53CI
rU7m2Ys6xt0nUW7/vGT1M0NPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNV
HRMBAf8EBTADAQH/MB0GA1UdDgQWBBR5tFnme7bl5AFzgAiIyBpY9umbbjANBgkq
hkiG9w0BAQsFAAOCAgEAVR9YqbyyqFDQDLHYGmkgJykIrGF1XIpu+ILlaS/V9lZL
ubhzEFnTIZd+50xx+7LSYK05qAvqFyFWhfFQDlnrzuBZ6brJFe+GnY+EgPbk6ZGQ
3BebYhtF8GaV0nxvwuo77x/Py9auJ/GpsMiu/X1+mvoiBOv/2X/qkSsisRcOj/KK
NFtY2PwByVS5uCbMiogziUwthDyC3+6WVwW6LLv3xLfHTjuCvjHIInNzktHCgKQ5
ORAzI4JMPJ+GslWYHb4phowim57iaztXOoJwTdwJx4nLCgdNbOhdjsnvzqvHu7Ur
TkXWStAmzOVyyghqpZXjFaH3pO3JLF+l+/+sKAIuvtd7u+Nxe5AW0wdeRlN8NwdC
jNPElpzVmbUq4JUagEiuTDkHzsxHpFKVK7q4+63SM1N95R1NbdWhscdCb+ZAJzVc
oyi3B43njTOQ5yOf+1CceWxG1bQVs5ZufpsMljq4Ui0/1lvh+wjChP4kqKOJ2qxq
4RgqsahDYVvTH9w7jXbyLeiNdd8XM2w9U/t7y0Ff/9yi0GE44Za4rF2LN9d11TPA
mRGunUHBcnWEvgJBQl9nJEiU0Zsnvgc/ubhPgXRR4Xq37Z0j4r7g1SgEEzwxA57d
emyPxgcYxn/eR44/KJ4EBs+lVDR3veyJm+kXQ99b21/+jh5Xos1AnX5iItreGCc=
-----END CERTIFICATE-----Обратите внимание, что корневой сертификат, в результате команды в 7 строке, добавляется именно в конец полученного вами файла chain.pem
Все команды в этой части выполняются от имени пользователя root:
su - zimbra -c "/opt/zimbra/bin/zmproxyctl stop"
su - zimbra -c "/opt/zimbra/bin/zmmailboxdctl stop"
certbot renew --standalone --force-renewal --preferred-chain "ISRG Root X1"
rm -f /opt/zimbra/ssl/letsencrypt/*
rm -f /opt/zimbra/ssl/zimbra/commercial/commercial.key
cp /etc/letsencrypt/live/mail.example.com/* /opt/zimbra/ssl/letsencrypt/
cat letsencryptCA >> /opt/zimbra/ssl/letsencrypt/chain.pem
cp /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
chown zimbra:zimbra /opt/zimbra/ssl/letsencrypt/*
chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
cd /opt/zimbra/ssl/letsencrypt
su zimbraВ этот момент мы переключаемся на пользователя zimbra и выполняем следующее:
zmcertmgr verifycrt comm privkey.pem cert.pem chain.pem
zmcertmgr deploycrt comm cert.pem chain.pem
zmcontrol restartЕсли всё пройдет без ошибок, то вы получите свежий сертификат и работающую почтовую систему.
Источники информации:
-
https://snapcraft.io/docs/installing-snapd
-
https://certbot.eff.org/instructions
-
https://wiki.zimbra.com/wiki/Installing_a_LetsEncrypt_SSL_Certificate
-
https://letsencrypt.org/certificates/
Since last night, I have issue with all of of my AdGuard Home server with DNS over TLS enabled (port 853). All client unable to connect it using DNS over TLS although it work flawlessly since last year.
I also tried @Freek sg.adhole.org DNS over TLS project which is use similar configuration. The issue still persist.
All of my client can use dns.google and 1dot1dot1dot1.cloudflare-dns.com without any issue.
This is the log from Stubby, DNS over TLS client for Windows 10, when using @Freek sg.adhole.org. The log from my AdGuard Home also similar with this.
[20:07:18.737563] STUBBY: Stubby version: Stubby 0.3.0
[20:07:18.779579] STUBBY: Read config from file C:Program FilesStubbystubby.yml
[20:07:18.781562] STUBBY: DNSSEC Validation is OFF
[20:07:18.781562] STUBBY: Transport list is:
[20:07:18.781562] STUBBY: - TLS
[20:07:18.782565] STUBBY: Privacy Usage Profile is Strict (Authentication required)
[20:07:18.782565] STUBBY: (NOTE a Strict Profile only applies when TLS is the ONLY transport!!)
[20:07:18.782565] STUBBY: Starting DAEMON....
[20:07:20.060514] STUBBY: --- SETUP(TLS): : Adding Windows certificates from system root store to CA store
[20:07:20.072514] STUBBY: --- SETUP(TLS): : Completed adding Windows certificates to CA store successfully
[20:07:20.073492] STUBBY: 210.16.120.48 : Conn opened: TLS - Strict Profile
[20:07:20.186965] STUBBY: 210.16.120.48 : Verify failed : TLS - *Failure* - (10) "certificate has expired"
[20:07:20.187843] STUBBY: 210.16.120.48 : Conn closed: TLS - *Failure*
[20:07:20.187843] STUBBY: *FAILURE* no valid transports or upstreams available!
[20:07:20.187843] STUBBY: 210.16.120.48 : Conn closed: TLS - *Failure*
[20:07:20.188839] STUBBY: *FAILURE* no valid transports or upstreams available!
[20:07:20.188839] STUBBY: 210.16.120.48 : Conn closed: TLS - Resps= 0, Timeouts = 0, Curr_auth = Failed, Keepalive(ms)= 0
[20:07:20.188839] STUBBY: 210.16.120.48 : Upstream : TLS - Resps= 0, Timeouts = 0, Best_auth = Failed
[20:07:20.189840] STUBBY: 210.16.120.48 : Upstream : TLS - Conns= 0, Conn_fails= 1, Conn_shuts= 0, Backoffs = 0
[20:07:23.943510] STUBBY: *FAILURE* no valid transports or upstreams available!
Could not schedule query: None of the configured upstreams could be used to send queries on the specified transports
[20:07:29.922561] STUBBY: *FAILURE* no valid transports or upstreams available!
Could not schedule query: None of the configured upstreams could be used to send queries on the specified transports
[20:07:33.940687] STUBBY: *FAILURE* no valid transports or upstreams available!
Could not schedule query: None of the configured upstreams could be used to send queries on the specified transports
I am not sure this is LetsEncrypt SSL issue or AdGuard Home issue. Do you also have any issue with your AdGuard Home & DNS over TLS configuration?
⭕ A simple uptime dashboard using UptimeRobot API https://upy.duo.ovh
⭕ Currently using VPS from BuyVM, GreenCloudVPS, Gullo’s, Hetzner, HostHatch, InceptionHosting, LetBox, MaxKVM, MrVM, VirMach.
На чтение 10 мин Просмотров 2.1к. Опубликовано 13 октября, 2021 Обновлено 22 января, 2022
Вчера мы установили почтовый сервер Zimbra 9 на Centos 8, настроили сетевое оборудование — прокинули необходимые порты. Сегодня устанавливаем letsencrypt сертификат.
Содержание
- Устанавливаем репозиторий EPEL на Centos
- Устанавливаем snapd
- Если ранее стояли версии certbot-auto и прочих Certbot OS пакетов — удаляем
- Установка Cerbot
- Выпускаем сертификаты
- Устанавливаем сертификат
- Перевыпуск сертификата
- Тестируем сертификат Let’s Encrypt на почтовом сервере Zimbra
Устанавливаем репозиторий EPEL на Centos
Устанавливаем репозиторий EPEL на Centos 8
# sudo dnf install epel-release
# sudo dnf upgradeУстанавливаем репозиторий EPEL на Centos 7
# yum install epel-releaseУстанавливаем snapd
# sudo yum install snapd
# sudo systemctl enable --now snapd.socket
# sudo ln -s /var/lib/snapd/snap /snapПерегружаем сервер
# rebootУбедимся, что ваша версия snapd актуальна
# snap install core
# snap refresh coreЕсли ранее стояли версии certbot-auto и прочих Certbot OS пакетов — удаляем
На Ubuntu:
# sudo apt-get remove certbotНа Centos:
# dnf remove certbotили
# yum remove certbotУстановка Cerbot
# sudo snap install --classic certbot
# sudo ln -s /snap/bin/certbot /usr/bin/certbot 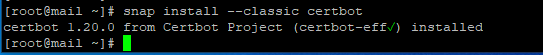
Выпускаем сертификаты
Обязательно запрашивайте сертификат с --preferred-chain "ISRG Root X1" опцией. Если у вас уже есть сертификат, но вы не использовали эту опцию, вам необходимо выполнить принудительное обновление с --force-renewal --preferred-chain "ISRG Root X1" опциями.
# certbot certonly --standalone --preferred-chain "ISRG Root X1"Попросит указать e-mail адрес
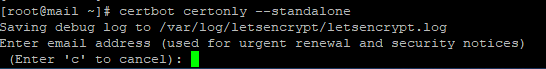
Вписываем, нажимаем ENTER
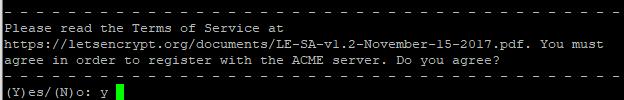
Далее на следующий вопрос — отвечаем Y:
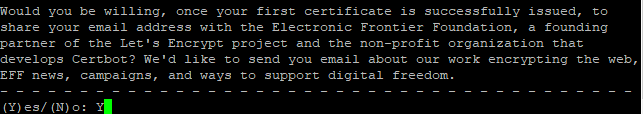
На следующий вопрос — так же отвечаем Y:
Далее нужно указать доменное имя сервера, в моем случае mail.inter-connect.ru:
Все прошло штатно:
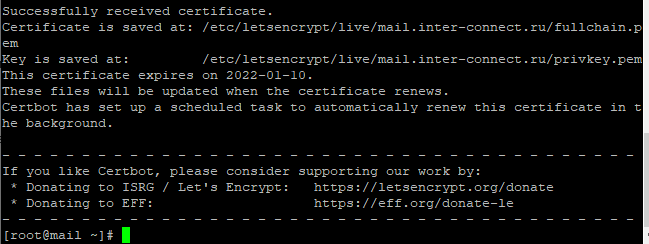
Сертификат + открытый ключ + цепочка выпущен
Устанавливаем сертификат
Делаем под root:
Создаем папку для сертификатов и даем права на нее. Переносим созданные сертификаты
# mkdir /opt/zimbra/ssl/letsencrypt/
# chown zimbra:zimbra /opt/zimbra/ssl/letsencrypt/
# cp /etc/letsencrypt/live/mail.inter-connect.ru/* /opt/zimbra/ssl/letsencrypt
# chown zimbra:zimbra /opt/zimbra/ssl/letsencrypt/*
# cp /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
# chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
# wget -O /tmp/ISRG-X1.pem https://letsencrypt.org/certs/isrgrootx1.pem.txt
# cat /tmp/ISRG-X1.pem >> /opt/zimbra/ssl/letsencrypt/chain.pem
Под учетной записью zimbra
# su zimbraОстанавливаем службы почтового сервера:
$ sudo su - zimbra -c "zmproxyctl stop"
Stopping proxy...done.
$ sudo su - zimbra -c "zmmailboxdctl stop"
Stopping mailboxd...done.# cd ~
# /opt/zimbra/bin/zmcertmgr verifycrt comm /opt/zimbra/ssl/zimbra/commercial/commercial.key /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
# /opt/zimbra/bin/zmcertmgr deploycrt comm /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pemесли все ок — должно быть
[zimbra@mail ~]$ /opt/zimbra/bin/zmcertmgr deploycrt comm /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/zimbra/commercial** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/zimbra/commercial/commercial.key'
Certificate '/opt/zimbra/ssl/letsencrypt/cert.pem' and private key '/opt/zimbra/ssl/zimbra/commercial/commercial.key' match.
** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/letsencrypt/chain.pem'
Valid certificate chain: /opt/zimbra/ssl/letsencrypt/cert.pem: OK
** Copying '/opt/zimbra/ssl/letsencrypt/cert.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Copying '/opt/zimbra/ssl/letsencrypt/chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt'
** Appending ca chain '/opt/zimbra/ssl/letsencrypt/chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Importing cert '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt' as 'zcs-user-commercial_ca' into cacerts '/opt/zimbra/common/lib/jvm/java/lib/security/cacerts'
** NOTE: restart mailboxd to use the imported certificate.
** Saving config key 'zimbraSSLCertificate' via zmprov modifyServer mail.inter-connect.ru...ok
** Saving config key 'zimbraSSLPrivateKey' via zmprov modifyServer mail.inter-connect.ru...ok
** Installing imapd certificate '/opt/zimbra/conf/imapd.crt' and key '/opt/zimbra/conf/imapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/imapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/imapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/conf/imapd.keystore'
** Installing ldap certificate '/opt/zimbra/conf/slapd.crt' and key '/opt/zimbra/conf/slapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/slapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/slapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/mailboxd/etc/keystore'
** Installing mta certificate '/opt/zimbra/conf/smtpd.crt' and key '/opt/zimbra/conf/smtpd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/smtpd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/smtpd.key'
** Installing proxy certificate '/opt/zimbra/conf/nginx.crt' and key '/opt/zimbra/conf/nginx.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/nginx.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/nginx.key'
** NOTE: restart services to use the new certificates.
** Cleaning up 3 files from '/opt/zimbra/conf/ca'
** Removing /opt/zimbra/conf/ca/ca.key
** Removing /opt/zimbra/conf/ca/ca.pem
** Removing /opt/zimbra/conf/ca/740bf472.0
** Copying CA to /opt/zimbra/conf/ca
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.key' to '/opt/zimbra/conf/ca/ca.key'
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.pem' to '/opt/zimbra/conf/ca/ca.pem'
** Creating CA hash symlink '740bf472.0' -> 'ca.pem'
** Creating /opt/zimbra/conf/ca/commercial_ca_1.crt
** Creating CA hash symlink '8d33f237.0' -> 'commercial_ca_1.crt'
** Creating /opt/zimbra/conf/ca/commercial_ca_2.crt
** Creating CA hash symlink '4042bcee.0' -> 'commercial_ca_2.crt'
перезапускаем остановленные ранее службы
$ sudo su - zimbra -c "zmcontrol restart"Перевыпуск сертификата
Фактически, перевыпуск сертификата мало чем отличается от выпуска нового.
Вводим команду:
certbot certonly --standalone --preferred-chain "ISRG Root X1"Необходимо будет ввести доменное имя почтового сервера — в моем случае mail.inter-connect.ru
На вопрос — выпустить новый сертификат или перевыпустить — отвечаем цифрой 2 — нажимаем enter
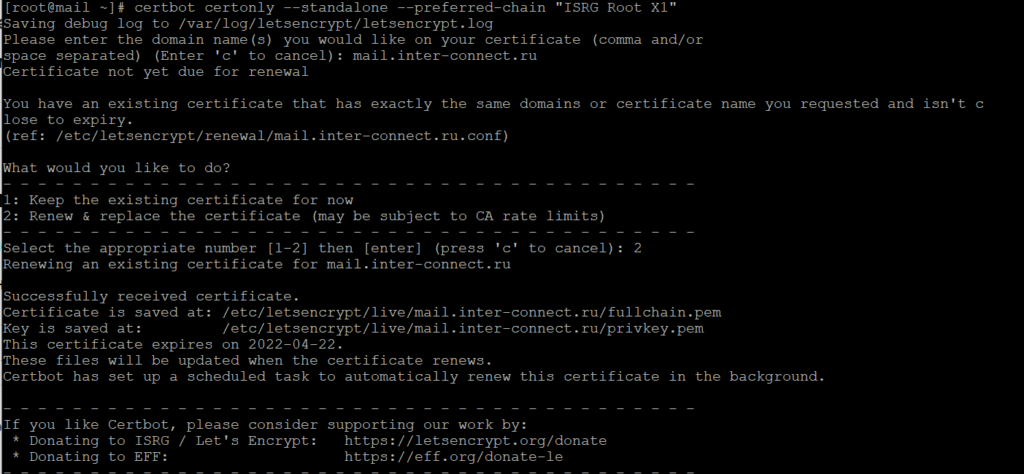
Далее, как и после выпуска нового, выполняем следующие команды под root:
# cp /etc/letsencrypt/live/mail.inter-connect.ru/* /opt/zimbra/ssl/letsencrypt
# chown zimbra:zimbra /opt/zimbra/ssl/letsencrypt/*
# cp /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
# chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
# wget -O /tmp/ISRG-X1.pem https://letsencrypt.org/certs/isrgrootx1.pem.txt
# cat /tmp/ISRG-X1.pem >> /opt/zimbra/ssl/letsencrypt/chain.pem
Под учетной записью zimbra — останавливаем службы почтового сервера:
# su zimbra
$ zmproxyctl stop
Stopping proxy...done.
$ zmmailboxdctl stop
Stopping mailboxd...done.
Далее выполняем команды:
$ cd ~
$ /opt/zimbra/bin/zmcertmgr verifycrt comm /opt/zimbra/ssl/zimbra/commercial/commercial.key /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
$ /opt/zimbra/bin/zmcertmgr deploycrt comm /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
Если Вы все правильно сделали, долно быть следующее:
[zimbra@mail ~]$ /opt/zimbra/bin/zmcertmgr deploycrt comm /opt/zimbra/ssl/letsencrypt/cert.pem /opt/zimbra/ssl/letsencrypt/chain.pem
** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/zimbra/commercial** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/zimbra/commercial/commercial.key'
Certificate '/opt/zimbra/ssl/letsencrypt/cert.pem' and private key '/opt/zimbra/ssl/zimbra/commercial/commercial.key' match.
** Verifying '/opt/zimbra/ssl/letsencrypt/cert.pem' against '/opt/zimbra/ssl/letsencrypt/chain.pem'
Valid certificate chain: /opt/zimbra/ssl/letsencrypt/cert.pem: OK
** Copying '/opt/zimbra/ssl/letsencrypt/cert.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Copying '/opt/zimbra/ssl/letsencrypt/chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt'
** Appending ca chain '/opt/zimbra/ssl/letsencrypt/chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Importing cert '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt' as 'zcs-user-commercial_ca' into cacerts '/opt/zimbra/common/lib/jvm/java/lib/security/cacerts'
** NOTE: restart mailboxd to use the imported certificate.
** Saving config key 'zimbraSSLCertificate' via zmprov modifyServer mail.inter-connect.ru...ok
** Saving config key 'zimbraSSLPrivateKey' via zmprov modifyServer mail.inter-connect.ru...ok
** Installing imapd certificate '/opt/zimbra/conf/imapd.crt' and key '/opt/zimbra/conf/imapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/imapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/imapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/conf/imapd.keystore'
** Installing ldap certificate '/opt/zimbra/conf/slapd.crt' and key '/opt/zimbra/conf/slapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/slapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/slapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/mailboxd/etc/keystore'
** Installing mta certificate '/opt/zimbra/conf/smtpd.crt' and key '/opt/zimbra/conf/smtpd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/smtpd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/smtpd.key'
** Installing proxy certificate '/opt/zimbra/conf/nginx.crt' and key '/opt/zimbra/conf/nginx.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/nginx.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/nginx.key'
** NOTE: restart services to use the new certificates.
** Cleaning up 3 files from '/opt/zimbra/conf/ca'
** Removing /opt/zimbra/conf/ca/ca.key
** Removing /opt/zimbra/conf/ca/ca.pem
** Removing /opt/zimbra/conf/ca/740bf472.0
** Copying CA to /opt/zimbra/conf/ca
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.key' to '/opt/zimbra/conf/ca/ca.key'
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.pem' to '/opt/zimbra/conf/ca/ca.pem'
** Creating CA hash symlink '740bf472.0' -> 'ca.pem'
** Creating /opt/zimbra/conf/ca/commercial_ca_1.crt
** Creating CA hash symlink '8d33f237.0' -> 'commercial_ca_1.crt'
** Creating /opt/zimbra/conf/ca/commercial_ca_2.crt
** Creating CA hash symlink '4042bcee.0' -> 'commercial_ca_2.crt'
Перезапускаем службы почтового сервера zimbra:
$ zmcontrol restart
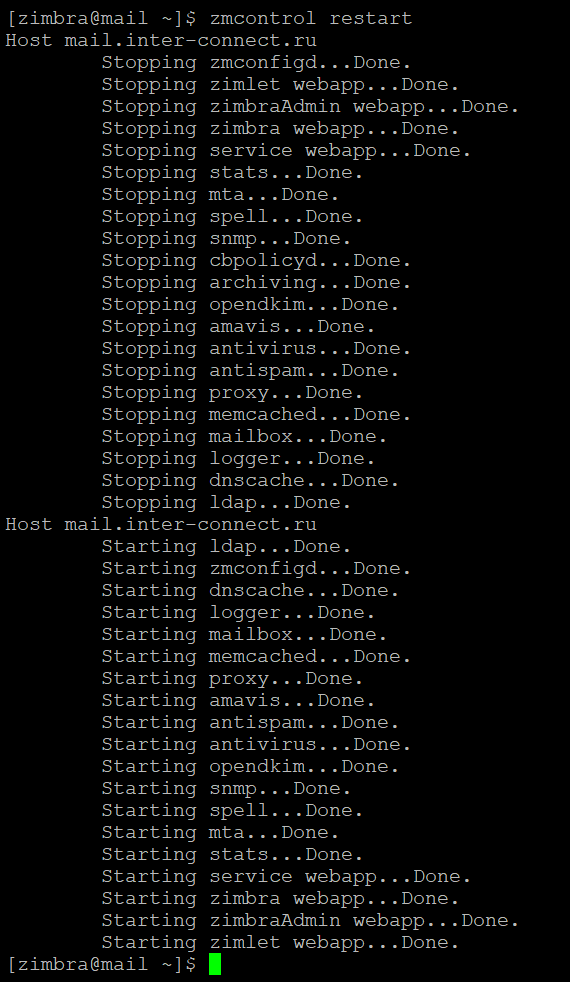
Тестируем сертификат Let’s Encrypt на почтовом сервере Zimbra
Заходим на наш сервер: https://ваш_домен.ru
Видим:
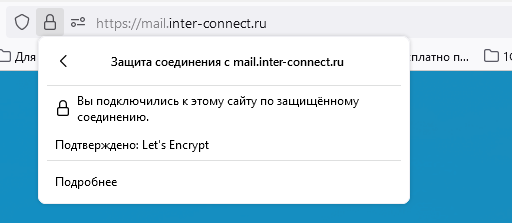
Результат работы — сертификат установлен.
Recommend Projects
-
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.
