Problem Description
This KB article addresses the following NRPE error:
CHECK_NRPE: Error - Could Not Complete SSL Handshake
The NRPE client may also log messages similar to the following in SYSLOG:
Dec 11 09:08:14 centos19 xinetd[2567]: FAIL: nrpe address from=2001:44b8:3132:25:be5f:f4ff:fefd:7d97
Dec 11 09:08:53 centos19 xinetd[2578]: FAIL: nrpe address from=10.25.254.5
Assumed Knowledge
The following KB article contains an explanation of how NRPE works and may need to be referenced to completely understand the problem and solution that is provided here:
NRPE — Agent and Plugin Explained
Troubleshooting The Error
This is probably the most common of all error messages and one of the first you will experience when new to NRPE. There are a few different causes of this, though the most likely one is that the Nagios XI server’s IP address is not defined as being allowed to communicate with NRPE. This can be defined in one of two locations, depending if you are using xinetd as the daemon to run NRPE or if NRPE has it’s own dedicated daemon. To identified which one is being used, execute the following command on the remote host:
ls -la /etc/xinetd.d/nrpe
If you get output like this, xinetd is being used and you should follow the XINETD steps below:
-rw-r--r--. 1 root root 483 Feb 22 12:23 /etc/xinetd.d/nrpe
If you get output like this, NRPE has it’s own Daemon and you should follow the nrpe.cfg steps below:
ls: cannot access /etc/xinetd.d/nrpe: No such file or directory
XINETD
If you use xinetd for controlling the NRPE daemon (most people do), then you need to add the Nagios server’s IP address to the xinetd NRPE configuration file /etc/xinetd.d/nrpe. Edit the file by executing the following command:
vi /etc/xinetd.d/nrpe
In this file you will find the line:
only_from = 127.0.0.1
This list is a space-delimited list. Change it to:
only_from = 127.0.0.1 <Nagios XI server ip>
With the increasing popularity of IPv6 you may also want to add the local IPv6 ::1 address to the list of only_from addresses, for example:
only_from = 127.0.0.1 ::1 <Nagios XI server ip>
You can also define the only_from directive over multiple lines by using += for each consecutive line, for example:
only_from = 127.0.0.1
only_from += ::1
only_from += <Nagios XI server ip>
Remember to change <Nagios XI server ip> to your actual Nagios XI server IP address. One thing to note is that 127.0.0.1 should remain as it allows you to troubleshoot NRPE issues locally (and so does ::1). After you have made the following changes, restart the xinetd service on the remote host (this example may be different to your operating system distribution):
service xinetd restart
NRPE.CFG
If you use a dedicated daemon for NRPE, then you need to add the Nagios server’s IP address to the nrpe.cfg configuration file /usr/local/nagios/etc/nrpe.cfg. Edit the file by executing the following command:
vi /usr/local/nagios/etc/nrpe.cfg
In this file you will find the line:
allowed_hosts=127.0.0.1
This list is a comma-delimited list. Change it to:
allowed_hosts=127.0.0.1,<Nagios XI server ip>
Remember to change <Nagios XI server ip> to your actual Nagios XI server IP address. One thing to note is that 127.0.0.1 should remain as it allows you to troubleshoot NRPE issues locally. After you have made the following changes, restart the xinetd service on the remote host (this example may be different to your operating system distribution):
service nrpe restart
SSL Not Compiled In:
Another cause of SSL issues is that NRPE was not compiled with ssl enabled. To recompile NRPE with ssl support, browse to your NRPE source directory (usually in /tmp/nrpe-2.15 if you followed the compiling NRPE from source document) and re-compile using the —enable-ssl flag:
cd /tmp/nrpe-2.14
./configure --enable-ssl
make all
make install
Understand that if you installed from a corporate build or from a package repo, you may have either uninstall the current NRPE package and install from source. You may need to pursue support on the specific distribution’s forums or through Nagios support. The following link has detailed instructions on compiling NRPE from source:
https://support.nagios.com/kb/article.php?id=515
Xinetd Per Source Limit:
This cause is rare, but worth mentioning. If you use your remote host’s NRPE server as a NRPE node proxy (sending all checks for the network segment to a single NRPE enabled server behind a firewall), or if you are doing a large number of NRPE checks in relatively short time period on one remote host, you may hit the maximum connection limit of NRPE. This is technically an xinetd setting and can be uncapped by editing the file /etc/xinetd.d/nrpeon your remote host:
nano /etc/xinetd.d/nrpe
Add the following line to the file inside the closing «}«:
per_source = UNLIMITED
instances = UNLIMITED
And then restart XINETD with the following command (this example may be different to your operating system distribution):
service xinetd restart
Final Thoughts
For any support related questions please visit the Nagios Support Forums at:
http://support.nagios.com/forum/
I have NRPE daemon process running under xinetd on amazon ec2 instance and nagios server on my local machine.
The check_nrpe -H [amazon public IP] gives this error:
CHECK_NRPE: Error - Could not complete SSL handshake.
Both Nrpe are same versions. Both are compiled with this option:
./configure --with-ssl=/usr/bin/openssl --with-ssl-lib=/usr/lib/i386-linux-gnu/
«allowed host» entry contains my local IP address.
What could be the possible reason of this error now??
Harikrishnan
9,4729 gold badges86 silver badges127 bronze badges
asked Dec 11, 2013 at 13:23
Dushyant GuptaDushyant Gupta
5071 gold badge5 silver badges24 bronze badges
3
If you are running nrpe as a service, make sure you have this line in your nrpe.cfg on the client side:
# example 192. IP, yours will probably differ
allowed_hosts=127.0.0.1,192.168.1.100
You say that is done, however, if you are running nrpe under xinetd, make sure to edit the only_from directive in the file /etc/xinetd.d/nrpe.
Don’t forget to restart the xinetd service:
service xinetd restart
answered Nov 7, 2014 at 3:20
0
To check if you have access to it at all attempt a simple telnet on the address:port, a ping or traceroute to see where it is blocking.
telnet IP port
ping IP
traceroute -p $port IP
Also check on the target server that the nrpe daemon is working properly.
netstat -at | grep nrpe
You also need to check the versions of OpenSSL installed on both servers, as I have seen this break checks on occasion with the SSL handshake!
answered Jan 7, 2014 at 20:43
check your /var/sys/system.log . In my case, it turned out my monitored IP was set to something else than the one I set in nrpe.cfg file. I don’t know the cause of this change, though.
answered Nov 9, 2014 at 9:24
ÖzgürÖzgür
7,9992 gold badges68 silver badges66 bronze badges
1
@jgritty was right.
you should edit nrpe.cfg and nrpe config files to allow your master nagios server’s access:
vim /usr/local/nagios/etc/nrpe.cf
allowed_hosts=127.0.0.1,172.16.16.150
and
vim /etc/xinetd.d/nrpe
only_from= 127.0.0.1 172.16.16.150
icebat
4,6564 gold badges22 silver badges36 bronze badges
answered Feb 16, 2016 at 7:40
NOZUONOHIGHNOZUONOHIGH
1,7821 gold badge20 silver badges20 bronze badges
1
That’s somewhat of a catch-all error message for NRPE. Check your firewall rules and make sure that port is open. Also try disabling SELinux and seeing if that lets the connection through. It’s likely not an SSL issue, but just an issue with the connection being refused.
answered Dec 13, 2013 at 14:12
Michael GuthrieMichael Guthrie
5121 gold badge4 silver badges11 bronze badges
It looks like you are running your Nagios server in a virtual machine on a host-only network. If this is so, this would stop any external access. Ensure that you have a NAT or Bridged Network available.
answered Mar 14, 2016 at 20:17
So many answers, none of them hit the reason why I ran into this issue.
It turns out that nagios has terrible cross-version support and this was caused by me having a version 2 «client» (machine being monitored) and a version 3 «server» (monitoring machine).
Once I upgraded the client to version 3, the problem went away and I could do a check_nrpe -H [client IP] without issues.
Note that I am not sure if client/server are the right terms with nagios, as in the case of an NRPE call, the server is really the machine being called, but I digress.
answered May 12, 2019 at 17:38
dovetalkdovetalk
1,9851 gold badge13 silver badges21 bronze badges
1
Make sure that you have restarted the Nagios Client Plugin as well.
answered Apr 15, 2016 at 18:13
I’m running nrpe using the xinetd service.
Make sure also (in addition to the above basic steps) that your nagios user is authenticating properly. In my case:
Jun 6 15:05:52 gse2 xinetd[33237]: **Unknown user: nagios**<br>[file=/etc/xinetd.d/nrpe] [line=9]
Jun 6 15:05:52 gse2 xinetd[33237]: Error parsing attribute user - DISABLING
SERVICE [file=/etc/xinetd.d/nrpe] [line=9]
Jun 6 15:05:52 gse2 xinetd[33237]: **Unknown group: nagios**<br>[file=/etc/xinetd.d/nrpe] [line=10]
Jun 6 15:05:52 gse2 xinetd[33237]: Error parsing attribute group - DISABLING
SERVICE [file=/etc/xinetd.d/nrpe] [line=10]
Jun 6 15:05:52 gse2 xinetd[33237]: Service nrpe missing attribute user - DISABLING
Was showing in the /var/log messages.
It escaped me at first, but then I did a check on ypbind service and found it was not started.
After starting ypbind, nagios user and group was authenticating properly, the error went away.
answered Jun 6, 2016 at 19:13
some edge cases restarting nagios-nrpe-server doesn’t help, due to the fact that process was not killed or it was not properly restarted.
just kill it manually then, and start.
answered Jul 9, 2016 at 16:19
SSL handshake error msg.Beside the allow_host you should assign.
your nagios server is in a local lan with C type ip address such as 192.168.xxxx
when the target monitored server feedback the ssl msg to your local nagios server,the message should first comes to your public IP of your line,the message cannot across the public IP into your nagios server which ip is an internal one.
you need NAT to guide the SSL message from target server to inner nagios server.
Or you better use «GET» method which just get monitor message from the nagios client side,such as SNMP to fulfill the remote monitor of local resource of linux servers.
SSL need feedback in double direction.
Best Regards
answered Sep 28, 2016 at 3:54
RickyRicky
293 bronze badges
For me setting the following in /etc/nagios/nrpe.cfg on Client worked:
dont_blame_nrpe=1
It’s and ubuntu 16.04 machine.
For other possible problems, I recommend looking at nrpe logs. Here is good article for configuring logs.
answered Mar 8, 2017 at 6:37
Mayank JaiswalMayank Jaiswal
11.9k7 gold badges39 silver badges41 bronze badges
If you are running Debian 9 then there is a known issue regarding this problem, caused by OpenSSL dropping support for the method NRPE uses to initiate anonymous SSL connections.
The issue seems to be fixed but the fix hasn’t made it into the official packages, yet.
Currently there seems to be no secure work-around.
answered Jun 28, 2017 at 15:26
Florian BruckerFlorian Brucker
9,1213 gold badges47 silver badges75 bronze badges
check configuration in /etc/xinetd.d/nrpe and verify the server IP. If it is showing only_from = 127.0.0.1 change it with Server IP .
answered Oct 23, 2018 at 8:39
decimaldecimal
3124 silver badges8 bronze badges
11 января 2013 г.
Nagios
NRPE
Мониторинг
FreeBSD
Debian
Linux
Вслед за статьей Вызов удаленных команд для Nagios с помощью NRPE решил записать решение на самую популярную проблему с NRPE, когда вы вызываете удаленную команду (в моем примере: плагин на FreeBSD, агент на Debian), то вам возвращается нечто такое CHECK_NRPE: Error receiving data from daemon
Эта ошибка, на деле, означает несколько проблем, а точнее их 5.
В Nagios Support FAQ есть замечательный топик Debugging «CHECK_NRPE: Error — Could not complete SSL handshake» errors объясняющий возможные проблемы, но не дающий конкретных решений.
Давайте разберем их:
Different versions. Make sure you are using the same version of the check_nrpe plugin and the NRPE daemon. Newer versions of NRPE are usually not backward compatible with older versions.
1
Если у вас установлены разные версии NRPE на серверах, то стоит для начала сделать их одинаковыми. Софт во FreeBSD-портах обычно свежее черем пакеты в Debian, поэтому доустанавливаем NRPE-агент в Debian вручную. Входим на страницу загрузки NRPE2 и качаем архив с NRPE (в моем случае это был nrpe-2.13):
wget -O nrpe-2.13.tar.gz http://downloads.sourceforge.net/project/nagios/nrpe-2.x/nrpe-2.13/nrpe-2.13.tar.gz tar -xzf nrpe-2.13.tar.gz cd nrpe-2.13 # Нам нужна поддержка SSL sudo apt-get install libssl-dev # Смотрим где храняться headers от libssl (в моем случае это "/usr/lib/i386-linux-gnu") dpkg -L libssl-dev | grep libssl.a # Собираем и устанавливаем ./configure --with-ssl=`which openssl` --with-ssl-lib=/usr/lib/i386-linux-gnu make sudo make install # Останавливаем агента, подменяем бинарник, запускаем агента sudo /etc/init.d/nagios-nrpe-server stop sudo cp /usr/local/nagios/bin/nrpe /usr/sbin/nrpe sudo /etc/init.d/nagios-nrpe-server startSSL is disabled. Make sure both the NRPE daemon and the check_nrpe plugin were compiled with SSL support and that neither are being run without SSL support (using command line switches).
2
Это возникает, когда вы установили один из NRPE без поддержки SSL. В Debian он собирается по умолчанию с SSL, значит у вас проблема с портом во FreeBSD, при установке надо было выбрать поддержку SSL, теперь его переустановим:
cd /usr/ports/net-mgmt/nrpe2 make config # Выбираем SSL [*] SSL Enable SSL support (disables plain-text server) make deinstall clean && make distclean && make install cleanУзнать собран ли NRPE-агент с поддержкой SSL или без, можно при запуске агента:
$ nrpe2 | head -n8 NRPE - Nagios Remote Plugin Executor Copyright (c) 1999-2008 Ethan Galstad (nagios@nagios.org) Version: 2.13 Last Modified: 11-11-2011 License: GPL v2 with exemptions (-l for more info) TCP Wrappers AvailableПосле переустановки порта (обратите внимание на предпоследнюю строку):
$ nrpe2 | head -n8 NRPE - Nagios Remote Plugin Executor Copyright (c) 1999-2008 Ethan Galstad (nagios@nagios.org) Version: 2.13 Last Modified: 11-11-2011 License: GPL v2 with exemptions (-l for more info) >>> SSL/TLS Available: Anonymous DH Mode, OpenSSL 0.9.6 or higher required TCP Wrappers AvailableIncorrect file permissions. Make sure the NRPE config file (nrpe.cfg) is readable by the user (i.e. nagios) that executes the NRPE binary from inetd/xinetd.
3
Нехватает прав у пользователя nagios (так как везде, именно под ним запускается NRPE), проверяем:
# В Debian sudo -u nagios /usr/lib/nagios/plugins/check_nrpe # Во FreeBSD sudo -u nagios /usr/local/libexec/nagios/check_nrpe2Проверьте также права на конфигурационные файлы.
Pseudo-random device files are not readable. Greg Haygood noted the following… «After wringing my hair out and digging around with truss, I figured out the problem on my Solaris 8 boxen. The files /devices/pseudo/random* (linked through /dev/*random, and provided by Sun patch 112438) were not readable by the nagios user I use to launch NRPE. Making the character devices world-readable solved it.»
4
Не встречался с такой проблемой, но для этого предусмотрен параметр в конфигурационном файле nrpe.cfg (надо его расскоментировать):
#allow_weak_random_seed=1Unallowed address. If you’re running the NRPE daemon under xinetd, make sure that you have a line in the xinetd config file that say «only_from = xxx.xxx.xxx.xxx», where xxx.xxx.xxx.xxx is the IP address that you’re connected to the NRPE daemon from.
5
Скорее всего вы забыли указать allowed_hosts в конфигурационном файле nrpe.cfg и внешние хосты просто не уполномочены обращаться к NRPE-агенту, укажите нужные IP-адреса через запятую и без пробелов:
allowed_hosts=127.0.0.1,203.0.113.41,203.0.113.42Сам я под xinetd не запускал агента, меня устроил standalone-режим. Но именно 5-ая проблема самая распространенная в сети, но и сама простая.
Какие были у меня проблемы?
У меня самого было только две проблемы (разные версии NRPE и плагин без поддержки SSL). Вначале была ошибка:
/usr/local/libexec/nagios/check_nrpe2 -H <REMOTE_SERVER_ADDRESS> -c <COMMAND> CHECK_NRPE: Error receiving data from daemonА после того как я обновил (решение проблемы под номером 1) версии NRPE-агента (на Debian) до версии плагина (на FreeBSD), с которого запускал, то появилась следующая ошибка в /var/log/syslog (на Remote Host, Debian):
[nrpe] Error: Could not complete SSL handshakeЕё я решил переустановив плагин на FreeBSD, как рассказывал в решении проблемы номер 2.
И совет напоследок, если не работает, начните с чтения лога /var/log/syslog или /var/log/messages, потому что nrpe будет писать именно туда:
tail -f /var/log/syslog tail -f /var/log/messagesУдачи!
I ran up a fresh Arch system today and I was able to replicate this. I don’t have an answer however I’m providing the information here to help the dev’s.
What I did notice is that when trying to compile 3.0.1, the «make all» step fails.
The «make all» step did not fail on the maint branch and was able to do a full install. However I also experienced the «CHECK_NRPE: Error — Could not complete SSL handshake.» error and NRPE does not work.
Here are the full steps for 3.0.1:
[root@arch01 ~]# pacman --noconfirm -S autoconf gcc glibc libmcrypt make libmcrypt openssl wget
warning: autoconf-2.69-4 is up to date -- reinstalling
warning: gcc-6.3.1-2 is up to date -- reinstalling
warning: glibc-2.25-1 is up to date -- reinstalling
warning: make-4.2.1-2 is up to date -- reinstalling
warning: skipping target: libmcrypt
warning: openssl-1.1.0.e-1 is up to date -- reinstalling
resolving dependencies...
looking for conflicting packages...
Packages (7) autoconf-2.69-4 gcc-6.3.1-2 glibc-2.25-1 libmcrypt-2.5.8-4 make-4.2.1-2
openssl-1.1.0.e-1 wget-1.19.1-2
Total Download Size: 0.64 MiB
Total Installed Size: 159.89 MiB
Net Upgrade Size: 2.79 MiB
:: Proceed with installation? [Y/n]
:: Retrieving packages...
libmcrypt-2.5.8-4-x86_64 71.3 KiB 285K/s 00:00 [###################################] 100%
wget-1.19.1-2-x86_64 583.8 KiB 881K/s 00:01 [###################################] 100%
(7/7) checking keys in keyring [###################################] 100%
(7/7) checking package integrity [###################################] 100%
(7/7) loading package files [###################################] 100%
(7/7) checking for file conflicts [###################################] 100%
(7/7) checking available disk space [###################################] 100%
:: Processing package changes...
(1/7) reinstalling glibc [###################################] 100%
Generating locales...
en_US.UTF-8... done
Generation complete.
(2/7) reinstalling autoconf [###################################] 100%
(3/7) reinstalling gcc [###################################] 100%
(4/7) installing libmcrypt [###################################] 100%
(5/7) reinstalling make [###################################] 100%
(6/7) reinstalling openssl [###################################] 100%
(7/7) installing wget [###################################] 100%
Optional dependencies for wget
ca-certificates: HTTPS downloads [installed]
:: Running post-transaction hooks...
(1/3) Creating temporary files...
(2/3) Arming ConditionNeedsUpdate...
(3/3) Updating the info directory file...
[root@arch01 ~]# cd /tmp
[root@arch01 tmp]# wget --no-check-certificate -O nrpe.tar.gz https://github.com/NagiosEnterprises/nrpe/archive/nrpe-3.0.1.tar.gz
--2017-05-04 10:38:36-- https://github.com/NagiosEnterprises/nrpe/archive/nrpe-3.0.1.tar.gz
Loaded CA certificate '/etc/ssl/certs/ca-certificates.crt'
Resolving github.com... 192.30.255.113, 192.30.255.112
Connecting to github.com|192.30.255.113|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://codeload.github.com/NagiosEnterprises/nrpe/tar.gz/nrpe-3.0.1 [following]
--2017-05-04 10:38:38-- https://codeload.github.com/NagiosEnterprises/nrpe/tar.gz/nrpe-3.0.1
Resolving codeload.github.com... 192.30.253.120, 192.30.253.121
Connecting to codeload.github.com|192.30.253.120|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [application/x-gzip]
Saving to: ‘nrpe.tar.gz’
nrpe.tar.gz [ <=> ] 502.08K 288KB/s in 1.7s
2017-05-04 10:38:40 (288 KB/s) - ‘nrpe.tar.gz’ saved [514135]
[root@arch01 tmp]# tar xzf nrpe.tar.gz
[root@arch01 tmp]# cd /tmp/nrpe-nrpe-3.0.1/
[root@arch01 nrpe-nrpe-3.0.1]# ./configure --enable-command-args
checking for a BSD-compatible install... /usr/bin/install -c
checking what the operating system is ... linux
checking what the distribution type is ... archlinux
checking what init system is being used ... systemd
checking what inetd is being used ... systemd
checking for which paths to use ... default
checking for which init file to use ... default-service
checking for which inetd files to use ... default-socket
checking for gcc... gcc
checking whether the C compiler works... yes
checking for C compiler default output file name... a.out
checking for suffix of executables...
checking whether we are cross compiling... no
checking for suffix of object files... o
checking whether we are using the GNU C compiler... yes
checking whether gcc accepts -g... yes
checking for gcc option to accept ISO C89... none needed
checking whether make sets $(MAKE)... yes
checking how to run the C preprocessor... gcc -E
checking for grep that handles long lines and -e... /usr/bin/grep
checking for egrep... /usr/bin/grep -E
checking for ANSI C header files... yes
checking whether time.h and sys/time.h may both be included... yes
checking for sys/wait.h that is POSIX.1 compatible... yes
checking for sys/types.h... yes
checking for sys/stat.h... yes
checking for stdlib.h... yes
checking for string.h... yes
checking for memory.h... yes
checking for strings.h... yes
checking for inttypes.h... yes
checking for stdint.h... yes
checking for unistd.h... yes
checking ctype.h usability... yes
checking ctype.h presence... yes
checking for ctype.h... yes
checking dirent.h usability... yes
checking dirent.h presence... yes
checking for dirent.h... yes
checking errno.h usability... yes
checking errno.h presence... yes
checking for errno.h... yes
checking fcntl.h usability... yes
checking fcntl.h presence... yes
checking for fcntl.h... yes
checking getopt.h usability... yes
checking getopt.h presence... yes
checking for getopt.h... yes
checking grp.h usability... yes
checking grp.h presence... yes
checking for grp.h... yes
checking for inttypes.h... (cached) yes
checking netdb.h usability... yes
checking netdb.h presence... yes
checking for netdb.h... yes
checking pwd.h usability... yes
checking pwd.h presence... yes
checking for pwd.h... yes
checking signal.h usability... yes
checking signal.h presence... yes
checking for signal.h... yes
checking for stdint.h... (cached) yes
checking for strings.h... (cached) yes
checking for string.h... (cached) yes
checking syslog.h usability... yes
checking syslog.h presence... yes
checking for syslog.h... yes
checking tcpd.h usability... no
checking tcpd.h presence... no
checking for tcpd.h... no
checking for unistd.h... (cached) yes
checking arpa/inet.h usability... yes
checking arpa/inet.h presence... yes
checking for arpa/inet.h... yes
checking netinet/in.h usability... yes
checking netinet/in.h presence... yes
checking for netinet/in.h... yes
checking socket.h usability... no
checking socket.h presence... no
checking for socket.h... no
checking for sys/types.h... (cached) yes
checking sys/time.h usability... yes
checking sys/time.h presence... yes
checking for sys/time.h... yes
checking sys/resource.h usability... yes
checking sys/resource.h presence... yes
checking for sys/resource.h... yes
checking for sys/wait.h... (cached) yes
checking sys/socket.h usability... yes
checking sys/socket.h presence... yes
checking for sys/socket.h... yes
checking for sys/stat.h... (cached) yes
checking paths.h usability... yes
checking paths.h presence... yes
checking for paths.h... yes
checking for an ANSI C-conforming const... yes
checking whether struct tm is in sys/time.h or time.h... time.h
checking for mode_t... yes
checking for pid_t... yes
checking for size_t... yes
checking return type of signal handlers... void
checking for uid_t in sys/types.h... yes
checking type of array argument to getgroups... gid_t
checking size of int... 4
checking size of short... 2
checking size of long... 8
checking for uint32_t... yes
checking for u_int32_t... yes
checking for int32_t... yes
checking for struct sockaddr_storage... yes
checking for seteuid... yes
checking for va_copy... yes
checking for vsnprintf... yes
checking for snprintf... yes
checking for asprintf... yes
checking for vasprintf... yes
checking for C99 vsnprintf... yes
checking for getopt_long... yes
checking for main in -lnsl... yes
checking for socket in -lsocket... no
checking for main in -lwrap... no
checking for strdup... yes
checking for strstr... yes
checking for strtoul... yes
checking for strtok_r... yes
checking for initgroups... yes
checking for closesocket... no
checking for sigaction... yes
checking for socklen_t... yes
checking for type of socket size... size_t
checking for Kerberos include files... found Kerberos include files in /usr/include/krb5
checking for pkg-config... pkg-config
checking whether compiling and linking against SSL works... yes
checking for openssl... /sbin/openssl
*** Generating DH Parameters for SSL/TLS ***
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
................................................................................................+..........................................................................................................................................................+.........................................................................................+................................................................................................................................................................................................+.......................................................................................................................................................+.....................................................................................................................................+.......................................................................................................................................................................................................................................................................................+.......................................................................................................................+.............................................................................................+...............................................................................+.......................+.....+............................+......................+............................................................................+................+..................................+..........................................................................................................................................................................................................................................+.........................................................................................................................................................................................................................................+...........+.........+......................+...........................................................+................+....+...................................................................................................+..........................................................................................................................................................+.................................+....+..................................................................................................................................................................................................................................................................+...........................................................................................................................+....................................................................+..............................................................................................+.......+.........................................................................................................................................+...........................................................+....................................................................................................................................................................................+.........................................................................................................................+......................................................................................................................................................................................+........................................................................................................................+.........................................................+...................................................................................................................................+...........................+.......................................................+........................................................+...........+....................................................................................+..........................................................................................+.............................................+.........................................................................................................................................+...............................................+..................................................................................................................................+...................................+............................................................................................................................................................................+..............................+..........................................................................................................................................+......................................................................................................................................................................+..........................................................................................................................................................................................................................................................................................+........................................................................................................................................................................+............................................................................................................+.....................+...............................................................................................................................................................................................................................................................................................................+...........................................+...................................................+.....+...........................................................................+.....................................................................................................................................................................................+..........................+.....+.................................+................+......................+......................+................................................................................................................+....................................................................................................................................................................................+........+...........................................+........................+.......................................................................+......................+.................................................................................................................+..........................................................................................................................................+..................................+....................................+............................................+...+.........................+..........................................+...........................................................................................................................................................................................................................................................................................................................................................................+...........................................................+.............................................................................................................+.............................................................................................................+..................................................................................................................................................................................................+.........................................................................+.......................................+..........................+.............................................+............................................+.........+.................................................+............................+..+............................................................+..........................................................................................................................................................................................................................................................................................+.................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................+................................................................................................................+......................................................................................................................................................................+.......................+................................................................+..........................................................................................................................................................................................+..............................................................................................................................................................................................................+.............................................................................................................................................................................................+.......................................................................+...................................................................................................................................................................+.....................................................................................................................................................+..............................................................................................................................................................................................................................................................................................................................................................+................................................................................+.............................+...............................................................................................................................................................................................................+.......................................................................................+...........+.....................+...........................................+................................................................................+..................+.................................................................................................................................+..............................................................................+.............................................................................................................................................................................+.+...............................+.............................+.............................................................+...............................................+.+...................................................................................................................................................................................................................................................+...............................+.................................................................................................+.............+.................+....+..........................................+....................+...............+..................................+...............................................................................................+.....................++*++*
checking for perl... /usr/bin/perl
configure: creating ./config.status
config.status: creating Makefile
config.status: creating src/Makefile
config.status: creating nrpe.spec
config.status: creating uninstall
config.status: creating sample-config/nrpe.cfg
config.status: creating startup/bsd-init
config.status: creating startup/debian-init
config.status: creating startup/default-init
config.status: creating startup/default-inetd
config.status: creating startup/default-service
config.status: creating startup/default-socket
config.status: creating startup/default-socket-svc
config.status: creating startup/default-xinetd
config.status: creating startup/mac-init.plist
config.status: creating startup/mac-inetd.plist
config.status: creating startup/newbsd-init
config.status: creating startup/openbsd-init
config.status: creating startup/openrc-conf
config.status: creating startup/openrc-init
config.status: creating startup/solaris-init.xml
config.status: creating startup/solaris-inetd.xml
config.status: creating startup/tmpfile.conf
config.status: creating startup/upstart-init
config.status: creating startup/rh-upstart-init
config.status: creating include/common.h
config.status: creating include/config.h
*** Configuration summary for nrpe 3.0.1 09-08-2016 ***:
General Options:
-------------------------
NRPE port: 5666
NRPE user: nagios
NRPE group: nagios
Nagios user: nagios
Nagios group: nagios
Review the options above for accuracy. If they look okay,
type 'make all' to compile the NRPE daemon and client
or type 'make' to get a list of make options.
[root@arch01 nrpe-nrpe-3.0.1]# make all
cd ./src/; make
make[1]: Entering directory '/tmp/nrpe-nrpe-3.0.1/src'
gcc -g -O2 -I/usr/include/krb5 -DHAVE_CONFIG_H -I ../include -I ./../include -o nrpe ./nrpe.c ./utils.c ./acl.c -lssl -lcrypto -lnsl
./nrpe.c: In function ‘init_ssl’:
./nrpe.c:264:33: warning: implicit declaration of function ‘RAND_status’ [-Wimplicit-function-declaration]
if (allow_weak_random_seed && (RAND_status() == 0)) {
^~~~~~~~~~~
./nrpe.c:265:7: warning: implicit declaration of function ‘RAND_file_name’ [-Wimplicit-function-declaration]
if (RAND_file_name(seedfile, sizeof(seedfile) - 1))
^~~~~~~~~~~~~~
./nrpe.c:266:8: warning: implicit declaration of function ‘RAND_load_file’ [-Wimplicit-function-declaration]
if (RAND_load_file(seedfile, -1))
^~~~~~~~~~~~~~
./nrpe.c:267:5: warning: implicit declaration of function ‘RAND_write_file’ [-Wimplicit-function-declaration]
RAND_write_file(seedfile);
^~~~~~~~~~~~~~~
./nrpe.c:277:5: warning: implicit declaration of function ‘RAND_seed’ [-Wimplicit-function-declaration]
RAND_seed(seedfile, sizeof(seedfile));
^~~~~~~~~
./nrpe.c:283:10: warning: implicit declaration of function ‘SSLv2_server_method’ [-Wimplicit-function-declaration]
meth = SSLv2_server_method();
^~~~~~~~~~~~~~~~~~~
./nrpe.c:283:8: warning: assignment makes pointer from integer without a cast [-Wint-conversion]
meth = SSLv2_server_method();
^
./nrpe.c:290:3: warning: ‘TLSv1_server_method’ is deprecated [-Wdeprecated-declarations]
meth = TLSv1_server_method();
^~~~
In file included from /usr/include/openssl/ct.h:13:0,
from /usr/include/openssl/ssl.h:61,
from ../include/common.h:27,
from ./nrpe.c:28:
/usr/include/openssl/ssl.h:1597:1: note: declared here
DEPRECATEDIN_1_1_0(__owur const SSL_METHOD *TLSv1_server_method(void)) /* TLSv1.0 */
^
./nrpe.c:293:3: warning: ‘TLSv1_1_server_method’ is deprecated [-Wdeprecated-declarations]
meth = TLSv1_1_server_method();
^~~~
In file included from /usr/include/openssl/ct.h:13:0,
from /usr/include/openssl/ssl.h:61,
from ../include/common.h:27,
from ./nrpe.c:28:
/usr/include/openssl/ssl.h:1603:1: note: declared here
DEPRECATEDIN_1_1_0(__owur const SSL_METHOD *TLSv1_1_server_method(void)) /* TLSv1.1 */
^
./nrpe.c:296:3: warning: ‘TLSv1_2_server_method’ is deprecated [-Wdeprecated-declarations]
meth = TLSv1_2_server_method();
^~~~
In file included from /usr/include/openssl/ct.h:13:0,
from /usr/include/openssl/ssl.h:61,
from ../include/common.h:27,
from ./nrpe.c:28:
/usr/include/openssl/ssl.h:1609:1: note: declared here
DEPRECATEDIN_1_1_0(__owur const SSL_METHOD *TLSv1_2_server_method(void)) /* TLSv1.2 */
^
./nrpe.c:317:16: warning: implicit declaration of function ‘ERR_get_error’ [-Wimplicit-function-declaration]
while ((x = ERR_get_error()) != 0)
^~~~~~~~~~~~~
./nrpe.c:319:27: warning: implicit declaration of function ‘ERR_error_string’ [-Wimplicit-function-declaration]
sslprm.cert_file, ERR_error_string(x, NULL));
^~~~~~~~~~~~~~~~
./nrpe.c: In function ‘verify_callback’:
./nrpe.c:617:44: error: dereferencing pointer to incomplete type ‘X509_STORE_CTX {aka struct x509_store_ctx_st}’
X509_NAME_oneline(X509_get_issuer_name(ctx->current_cert), issuer, 256);
^~
./nrpe.c: In function ‘handle_conn_ssl’:
./nrpe.c:1752:16: warning: implicit declaration of function ‘ERR_get_error_line_data’ [-Wimplicit-function-declaration]
while ((x = ERR_get_error_line_data(NULL, NULL, NULL, NULL)) != 0) {
^~~~~~~~~~~~~~~~~~~~~~~
./nrpe.c:1754:22: warning: implicit declaration of function ‘ERR_reason_error_string’ [-Wimplicit-function-declaration]
remote_host, ERR_reason_error_string(x));
^~~~~~~~~~~~~~~~~~~~~~~
./nrpe.c:1790:26: error: dereferencing pointer to incomplete type ‘X509 {aka struct x509_st}’
remote_host, peer->valid ? "a " : "an in");
^~
make[1]: *** [Makefile:48: nrpe] Error 1
make[1]: Leaving directory '/tmp/nrpe-nrpe-3.0.1/src'
make: *** [Makefile:66: all] Error 2
Here are the full steps for the maint branch:
[root@arch01 ~]# wget https://github.com/NagiosEnterprises/nrpe/archive/maint.zip
--2017-05-04 10:43:54-- https://github.com/NagiosEnterprises/nrpe/archive/maint.zip
Loaded CA certificate '/etc/ssl/certs/ca-certificates.crt'
Resolving github.com... 192.30.255.112, 192.30.255.113
Connecting to github.com|192.30.255.112|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://codeload.github.com/NagiosEnterprises/nrpe/zip/maint [following]
--2017-05-04 10:43:55-- https://codeload.github.com/NagiosEnterprises/nrpe/zip/maint
Resolving codeload.github.com... 192.30.253.121, 192.30.253.120
Connecting to codeload.github.com|192.30.253.121|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [application/zip]
Saving to: ‘maint.zip’
maint.zip [ <=> ] 518.09K 305KB/s in 1.7s
2017-05-04 10:43:58 (305 KB/s) - ‘maint.zip’ saved [530525]
[root@arch01 ~]# mv maint.zip /tmp/
[root@arch01 ~]# cd /tmp
[root@arch01 tmp]# pacman -S unzip
resolving dependencies...
looking for conflicting packages...
Packages (1) unzip-6.0-12
Total Download Size: 0.12 MiB
Total Installed Size: 0.31 MiB
:: Proceed with installation? [Y/n] y
:: Retrieving packages...
unzip-6.0-12-x86_64 126.0 KiB 398K/s 00:00 [########################################] 100%
(1/1) checking keys in keyring [########################################] 100%
(1/1) checking package integrity [########################################] 100%
(1/1) loading package files [########################################] 100%
(1/1) checking for file conflicts [########################################] 100%
(1/1) checking available disk space [########################################] 100%
:: Processing package changes...
(1/1) installing unzip [########################################] 100%
:: Running post-transaction hooks...
(1/1) Arming ConditionNeedsUpdate...
[root@arch01 tmp]# unzip maint.zip
Archive: maint.zip
e89e8323666d0d729030ba7e56003600f0a69a86
creating: nrpe-maint/
inflating: nrpe-maint/.gitignore
inflating: nrpe-maint/Changelog
inflating: nrpe-maint/LEGAL
inflating: nrpe-maint/LICENSE
inflating: nrpe-maint/Makefile.in
inflating: nrpe-maint/README.SSL.md
inflating: nrpe-maint/README.md
inflating: nrpe-maint/SECURITY.md
inflating: nrpe-maint/THANKS
inflating: nrpe-maint/aclocal.m4
creating: nrpe-maint/build-aux/
inflating: nrpe-maint/build-aux/config.guess
inflating: nrpe-maint/build-aux/config.sub
inflating: nrpe-maint/build-aux/custom_help.m4
inflating: nrpe-maint/build-aux/install-sh
inflating: nrpe-maint/configure
inflating: nrpe-maint/configure.ac
creating: nrpe-maint/contrib/
inflating: nrpe-maint/contrib/README.nrpe_check_control
inflating: nrpe-maint/contrib/nrpe_check_control.c
creating: nrpe-maint/docs/
inflating: nrpe-maint/docs/NRPE.odt
inflating: nrpe-maint/docs/NRPE.pdf
creating: nrpe-maint/include/
inflating: nrpe-maint/include/acl.h
inflating: nrpe-maint/include/common.h.in
inflating: nrpe-maint/include/config.h.in
inflating: nrpe-maint/include/nrpe.h
inflating: nrpe-maint/include/utils.h
creating: nrpe-maint/macros/
extracting: nrpe-maint/macros/.gitignore
inflating: nrpe-maint/macros/LICENSE
inflating: nrpe-maint/macros/README.md
inflating: nrpe-maint/macros/add_group_user
inflating: nrpe-maint/macros/ax_nagios_get_distrib
inflating: nrpe-maint/macros/ax_nagios_get_files
inflating: nrpe-maint/macros/ax_nagios_get_inetd
inflating: nrpe-maint/macros/ax_nagios_get_init
inflating: nrpe-maint/macros/ax_nagios_get_os
inflating: nrpe-maint/macros/ax_nagios_get_paths
inflating: nrpe-maint/macros/ax_nagios_get_ssl
inflating: nrpe-maint/nrpe.spec.in
inflating: nrpe-maint/paths.in
creating: nrpe-maint/sample-config/
inflating: nrpe-maint/sample-config/nrpe.cfg.in
creating: nrpe-maint/src/
inflating: nrpe-maint/src/Makefile.in
inflating: nrpe-maint/src/acl.c
inflating: nrpe-maint/src/check_nrpe.c
inflating: nrpe-maint/src/nrpe.c
inflating: nrpe-maint/src/snprintf.c
inflating: nrpe-maint/src/utils.c
creating: nrpe-maint/startup/
inflating: nrpe-maint/startup/bsd-init.in
inflating: nrpe-maint/startup/debian-init.in
inflating: nrpe-maint/startup/default-inetd.in
inflating: nrpe-maint/startup/default-init.in
inflating: nrpe-maint/startup/default-service.in
inflating: nrpe-maint/startup/default-socket-svc.in
inflating: nrpe-maint/startup/default-socket.in
inflating: nrpe-maint/startup/default-xinetd.in
inflating: nrpe-maint/startup/mac-inetd.plist.in
inflating: nrpe-maint/startup/mac-init.plist.in
inflating: nrpe-maint/startup/newbsd-init.in
inflating: nrpe-maint/startup/openbsd-init.in
inflating: nrpe-maint/startup/openrc-conf.in
inflating: nrpe-maint/startup/openrc-init.in
inflating: nrpe-maint/startup/rh-upstart-init.in
inflating: nrpe-maint/startup/solaris-inetd.xml.in
inflating: nrpe-maint/startup/solaris-init.xml.in
inflating: nrpe-maint/startup/tmpfile.conf.in
inflating: nrpe-maint/startup/upstart-init.in
inflating: nrpe-maint/uninstall.in
inflating: nrpe-maint/update-cfg.pl
inflating: nrpe-maint/update-version
[root@arch01 tmp]# cd nrpe-maint/
[root@arch01 nrpe-maint]# ./configure --enable-command-args
checking for a BSD-compatible install... /usr/bin/install -c
checking what the operating system is ... linux
checking what the distribution type is ... archlinux
checking what init system is being used ... systemd
checking what inetd is being used ... systemd
checking for which paths to use ... default
checking for which init file to use ... default-service
checking for which inetd files to use ... default-socket
checking for gcc... gcc
checking whether the C compiler works... yes
checking for C compiler default output file name... a.out
checking for suffix of executables...
checking whether we are cross compiling... no
checking for suffix of object files... o
checking whether we are using the GNU C compiler... yes
checking whether gcc accepts -g... yes
checking for gcc option to accept ISO C89... none needed
checking whether make sets $(MAKE)... yes
checking how to run the C preprocessor... gcc -E
checking for grep that handles long lines and -e... /usr/bin/grep
checking for egrep... /usr/bin/grep -E
checking for ANSI C header files... yes
checking whether time.h and sys/time.h may both be included... yes
checking for sys/wait.h that is POSIX.1 compatible... yes
checking for sys/types.h... yes
checking for sys/stat.h... yes
checking for stdlib.h... yes
checking for string.h... yes
checking for memory.h... yes
checking for strings.h... yes
checking for inttypes.h... yes
checking for stdint.h... yes
checking for unistd.h... yes
checking ctype.h usability... yes
checking ctype.h presence... yes
checking for ctype.h... yes
checking dirent.h usability... yes
checking dirent.h presence... yes
checking for dirent.h... yes
checking errno.h usability... yes
checking errno.h presence... yes
checking for errno.h... yes
checking fcntl.h usability... yes
checking fcntl.h presence... yes
checking for fcntl.h... yes
checking getopt.h usability... yes
checking getopt.h presence... yes
checking for getopt.h... yes
checking grp.h usability... yes
checking grp.h presence... yes
checking for grp.h... yes
checking for inttypes.h... (cached) yes
checking netdb.h usability... yes
checking netdb.h presence... yes
checking for netdb.h... yes
checking pwd.h usability... yes
checking pwd.h presence... yes
checking for pwd.h... yes
checking signal.h usability... yes
checking signal.h presence... yes
checking for signal.h... yes
checking for stdint.h... (cached) yes
checking for strings.h... (cached) yes
checking for string.h... (cached) yes
checking syslog.h usability... yes
checking syslog.h presence... yes
checking for syslog.h... yes
checking tcpd.h usability... no
checking tcpd.h presence... no
checking for tcpd.h... no
checking for unistd.h... (cached) yes
checking arpa/inet.h usability... yes
checking arpa/inet.h presence... yes
checking for arpa/inet.h... yes
checking netinet/in.h usability... yes
checking netinet/in.h presence... yes
checking for netinet/in.h... yes
checking socket.h usability... no
checking socket.h presence... no
checking for socket.h... no
checking for sys/types.h... (cached) yes
checking sys/time.h usability... yes
checking sys/time.h presence... yes
checking for sys/time.h... yes
checking sys/resource.h usability... yes
checking sys/resource.h presence... yes
checking for sys/resource.h... yes
checking for sys/wait.h... (cached) yes
checking sys/socket.h usability... yes
checking sys/socket.h presence... yes
checking for sys/socket.h... yes
checking for sys/stat.h... (cached) yes
checking paths.h usability... yes
checking paths.h presence... yes
checking for paths.h... yes
checking for an ANSI C-conforming const... yes
checking whether struct tm is in sys/time.h or time.h... time.h
checking for mode_t... yes
checking for pid_t... yes
checking for size_t... yes
checking return type of signal handlers... void
checking for uid_t in sys/types.h... yes
checking type of array argument to getgroups... gid_t
checking size of int... 4
checking size of short... 2
checking size of long... 8
checking for uint32_t... yes
checking for u_int32_t... yes
checking for int32_t... yes
checking for struct sockaddr_storage... yes
checking for seteuid... yes
checking for va_copy... yes
checking for vsnprintf... yes
checking for snprintf... yes
checking for asprintf... yes
checking for vasprintf... yes
checking for C99 vsnprintf... yes
checking for getopt_long... yes
checking for main in -lnsl... yes
checking for socket in -lsocket... no
checking for main in -lwrap... no
checking for strdup... yes
checking for strstr... yes
checking for strtoul... yes
checking for strtok_r... yes
checking for initgroups... yes
checking for closesocket... no
checking for sigaction... yes
checking for scandir... yes
checking for socklen_t... yes
checking for type of socket size... size_t
need_dh = |yes|
checking for Kerberos include files... found Kerberos include files in /usr/include/krb5
checking for pkg-config... pkg-config
checking whether compiling and linking against SSL works... yes
checking for openssl... /sbin/openssl
*** Generating DH Parameters for SSL/TLS ***
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
.......................................................................................................+...........................................................+.......................................+.............................+.........................................................................................................................+................................................................................................................................................+.......................................................................................+...........................................................................................................+.+.............................................................+..........................................................................+............................................+................................................+..................................................................................................................................+...................................................................................................................................+............................+.....................................................................................................................+..+................................................................................................................................................................+...................................................+.....................................................................................................................................................................................................................................................................+......................................................................................................................................................................................................+............................................................................................................+................+...............................................................................+...........................................................................+.+.................................................+............................................+.......................................................................................+......................................................................................................................................................+........................................+..................................................................+...................................+...............+...............................................................................+..................................................................++*++*
checking for perl... /usr/bin/perl
configure: creating ./config.status
config.status: creating Makefile
config.status: creating src/Makefile
config.status: creating nrpe.spec
config.status: creating uninstall
config.status: creating sample-config/nrpe.cfg
config.status: creating startup/bsd-init
config.status: creating startup/debian-init
config.status: creating startup/default-init
config.status: creating startup/default-inetd
config.status: creating startup/default-service
config.status: creating startup/default-socket
config.status: creating startup/default-socket-svc
config.status: creating startup/default-xinetd
config.status: creating startup/mac-init.plist
config.status: creating startup/mac-inetd.plist
config.status: creating startup/newbsd-init
config.status: creating startup/openbsd-init
config.status: creating startup/openrc-conf
config.status: creating startup/openrc-init
config.status: creating startup/solaris-init.xml
config.status: creating startup/solaris-inetd.xml
config.status: creating startup/tmpfile.conf
config.status: creating startup/upstart-init
config.status: creating startup/rh-upstart-init
config.status: creating include/common.h
config.status: creating include/config.h
*** Configuration summary for nrpe 3.1.0 2017-04-19 ***:
General Options:
-------------------------
NRPE port: 5666
NRPE user: nagios
NRPE group: nagios
Nagios user: nagios
Nagios group: nagios
Review the options above for accuracy. If they look okay,
type 'make all' to compile the NRPE daemon and client
or type 'make' to get a list of make options.
[root@arch01 nrpe-maint]# make all
cd ./src/; make
make[1]: Entering directory '/tmp/nrpe-maint/src'
gcc -g -O2 -I/usr/include/krb5 -DHAVE_CONFIG_H -I ../include -I ./../include -o nrpe ./nrpe.c ./utils.c ./acl.c -lssl -lcrypto -lnsl
./acl.c: In function ‘add_ipv4_to_acl’:
./acl.c:144:4: warning: implicit declaration of function ‘logit’ [-Wimplicit-function-declaration]
logit(LOG_INFO, "add_ipv4_to_acl: checking ip-address >%s<", ipv4);
^~~~~
gcc -g -O2 -I/usr/include/krb5 -DHAVE_CONFIG_H -I ../include -I ./../include -o check_nrpe ./check_nrpe.c ./utils.c -lssl -lcrypto -lnsl
make[1]: Leaving directory '/tmp/nrpe-maint/src'
*** Compile finished ***
You can now continue with the installation or upgrade process.
Read the PDF documentation (docs/NRPE.pdf) for information on the next
steps you should take to complete the installation or upgrade.
[root@arch01 nrpe-maint]# make install-groups-users
groupadd -r nagios
useradd -r -g nagios nagios
[root@arch01 nrpe-maint]# make install
cd ./src/; make install
make[1]: Entering directory '/tmp/nrpe-maint/src'
make install-plugin
make[2]: Entering directory '/tmp/nrpe-maint/src'
/usr/bin/install -c -m 755 -d /usr/local/nagios/bin
/usr/bin/install -c -m 755 ../uninstall /usr/local/nagios/bin/nrpe-uninstall
/usr/bin/install -c -m 775 -o nagios -g nagios -d /usr/local/nagios/libexec
/usr/bin/install -c -m 775 -o nagios -g nagios -d /usr/local/nagios/libexec
/usr/bin/install -c -m 775 -o nagios -g nagios check_nrpe /usr/local/nagios/libexec
make[2]: Leaving directory '/tmp/nrpe-maint/src'
make install-daemon
make[2]: Entering directory '/tmp/nrpe-maint/src'
/usr/bin/install -c -m 755 -d /usr/local/nagios/bin
/usr/bin/install -c -m 755 ../uninstall /usr/local/nagios/bin/nrpe-uninstall
/usr/bin/install -c -m 755 nrpe /usr/local/nagios/bin
/usr/bin/install -c -m 755 -o nagios -g nagios -d /usr/local/nagios/var
/usr/bin/install -c -m 755 -d /usr/lib/tmpfiles.d
/usr/bin/install -c -m 644 ../startup/tmpfile.conf /usr/lib/tmpfiles.d/nrpe.conf
make[2]: Leaving directory '/tmp/nrpe-maint/src'
make[1]: Leaving directory '/tmp/nrpe-maint/src'
[root@arch01 nrpe-maint]# vi /etc/services
[root@arch01 nrpe-maint]# echo >> /etc/services
[root@arch01 nrpe-maint]# echo '# Nagios services' >> /etc/services
[root@arch01 nrpe-maint]# echo 'nrpe 5666/tcp' >> /etc/services
[root@arch01 nrpe-maint]# make install-init
/usr/bin/install -c -m 644 startup/default-service /usr/lib/systemd/system/nrpe.service
[root@arch01 nrpe-maint]# systemctl enable nrpe.service
Created symlink /etc/systemd/system/multi-user.target.wants/nrpe.service → /usr/lib/systemd/system/nrpe.service.
[root@arch01 nrpe-maint]# make install-config
/usr/bin/install -c -m 775 -o nagios -g nagios -d /usr/local/nagios/etc
/usr/bin/install -c -m 644 -o nagios -g nagios sample-config/nrpe.cfg /usr/local/nagios/etc
[root@arch01 nrpe-maint]# sed -i '/^allowed_hosts=/s/$/,10.25.5.2/' /usr/local/nagios/etc/nrpe.cfg
[root@arch01 nrpe-maint]# sed -i '/^allowed_hosts=/s/$/,10.25.0.0/16/' /usr/local/nagios/etc/nrpe.cfg
[root@arch01 nrpe-maint]# systemctl start nrpe.service
[root@arch01 nrpe-maint]# systemctl status nrpe.service
● nrpe.service - Nagios Remote Plugin Executor
Loaded: loaded (/usr/lib/systemd/system/nrpe.service; enabled; vendor preset: disabled)
Active: active (running) since Thu 2017-05-04 10:52:06 UTC; 11s ago
Docs: http://www.nagios.org/documentation
Process: 8879 ExecStopPost=/bin/rm -f /usr/local/nagios/var/nrpe.pid (code=exited, status=0/SUCCESS)
Main PID: 8883 (nrpe)
Tasks: 1 (limit: 19660)
CGroup: /system.slice/nrpe.service
└─8883 /usr/local/nagios/bin/nrpe -c /usr/local/nagios/etc/nrpe.cfg -f
May 04 10:52:06 arch01 systemd[1]: Stopped Nagios Remote Plugin Executor.
May 04 10:52:06 arch01 systemd[1]: Started Nagios Remote Plugin Executor.
May 04 10:52:06 arch01 nrpe[8883]: add_ipv4_to_acl: Error, ip-address >::1< incorrect length
May 04 10:52:06 arch01 nrpe[8883]: Starting up daemon
May 04 10:52:06 arch01 nrpe[8883]: Server listening on 0.0.0.0 port 5666.
May 04 10:52:06 arch01 nrpe[8883]: Server listening on :: port 5666.
May 04 10:52:06 arch01 nrpe[8883]: Warning: Daemon is configured to accept command arguments from clients!
May 04 10:52:06 arch01 nrpe[8883]: Listening for connections on port 5666
May 04 10:52:06 arch01 nrpe[8883]: Allowing connections from: 127.0.0.1,::1,10.25.0.0/16
May 04 10:52:09 arch01 nrpe[8888]: Error: Could not complete SSL handshake with 10.25.5.2: 1
[root@arch01 nrpe-maint]# /bin/openssl version
OpenSSL 1.1.0e 16 Feb 2017
After upgrading the operating system of a monitoring server, the nagios-nrpe-plugin package (and therefore the check_nrpe plugin) was also updated. The current NRPE version on Ubuntu 20.04 (Focal) is 4.0.0:
root@focal:~# dpkg -l|grep nrpe
ii nagios-nrpe-plugin 4.0.0-2ubuntu1 amd64 Nagios Remote Plugin Executor Plugin
ii nagios-nrpe-server 4.0.0-2ubuntu1 amd64 Nagios Remote Plugin Executor Server
Shortly after the upgrade Windows hosts, which are monitored using NSClient++ (nscp), started to alert. It seems that the communication between check_nrpe and NSClient++ stopped working:
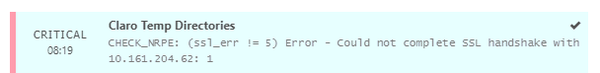
This can also be confirmed on the command line:
root@focal:~# /usr/lib/nagios/plugins/check_nrpe -H 10.10.22.23
CHECK_NRPE: (ssl_err != 5) Error — Could not complete SSL handshake with 10.10.22.23: 1
Even forcing the older NRPE protocol (v2) results in the same error:
root@focal:~# /usr/lib/nagios/plugins/check_nrpe -H 10.10.22.23 -2
CHECK_NRPE: (ssl_err != 5) Error — Could not complete SSL handshake with 10.10.22.23: 1
Communication still works with check_nrpe 2.15
The communication however still works with the old check_nrpe version (2.15), which was restored as nrpe2:
root@focal:~# /usr/lib/nagios/plugins/check_nrpe2 —help | head
NRPE Plugin for Nagios
Copyright (c) 1999-2008 Ethan Galstad (nagios@nagios.org)
Version: 2.15
Last Modified: 09-06-2013
License: GPL v2 with exemptions (-l for more info)
SSL/TLS Available: Anonymous DH Mode, OpenSSL 0.9.6 or higher required
Usage: check_nrpe -H <host> [ -b <bindaddr> ] [-4] [-6] [-n] [-u] [-p <port>] [-t <timeout>] [-c <command>] [-a <arglist…>]
root@focal:~# /usr/lib/nagios/plugins/check_nrpe2 -H 10.10.22.23
I (0.4.4.19 2015-12-08) seem to be doing fine…
So what did change in between?
NRPE was revived
NRPE itself staid at version 2.15 for many many years. This introduced a lot of weaknesses and security concerns. In 2018 NRPE was finally picked up again by Nagios Enterprises and until this year, 2021, new NRPE versions were released.
The major changes between the NRPE 2.x and the newer NRPE 3.x and 4.x concern the TLS/SSL settings. This also added a newer DH (Diffie-Hellman) key with a larger key size. From the README:
Running ./configure will now create a 2048-bit DH key instead of the old 512-bit key.
But how does that affect NSClient++?
NSClient++ uses smaller DH key
Thanks to this excellent blog post by Milan Kozak, one can find out that NSClient++ actually uses a smaller DH key. This can be seen inside the NSClient++ installation path, in the «security» folder:
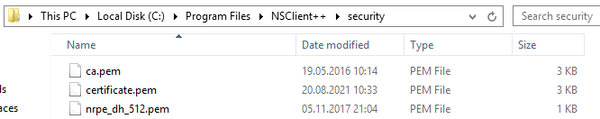
NSClient++ itself uses an internal nrpe_dh_512.pem DH key, obviously still referring to the old NRPE version.
To be able to communicate with the newer check_nrpe version, a new DH key with a size of 2048 bytes (same as the check_nrpe plugin itself) needs to be created.
Create new DH key and configure NSClient++
The new DH key can easily be created on the monitoring server using the openssl command:
root@focal:~# openssl dhparam -C 2048 2> /dev/null|sed -n ‘/BEGIN/,/END/p’
——BEGIN DH PARAMETERS——
MIIBXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXwIBAg==
——END DH PARAMETERS——
Note: This command might take a few minutes. On a busy machine this will be generated faster.
The final output can be copied (including the BEGIN and END lines) and saved into a new file on the Windows server: C:Program FilesNSClient++securitynrpe_dh_2048.pem.
Now the configuration of NSClient++ (usually C:Program FilesNSClient++nsclient.ini) needs to be adjusted. Inside the NRPE server settings, add the parameter for the dh key:
; Section for NRPE (NRPEServer.dll) (check_nrpe) protocol options.
[/settings/NRPE/server]
; ENABLE SSL ENCRYPTION — This option controls if SSL should be enabled
use ssl = 1
; COMMAND ALLOW NASTY META CHARS — This option determines whether or not that we will allow clients to specify nasty (as in |`&><‘»[]{}) characters in arguments.
allow nasty characters = 1
; COMMAND ARGUMENT PROCESSING — This option determines whether or not that we will allow clients to specify arguments to commands that are executed.
allow arguments = 1
; PORT NUMBER — Port to use for NRPE.
port = 5666
; EXTENDED RESPONSE — Send more than 1 return packet to allow response to go beyond payload (requires modified client, if legacy is true this defaults to false).
extended response = 1
; # DH KEY
dh = ${certificate-path}/nrpe_dh_2048.pem
The ${certificate-path} variable is an internal NSClient++ variable which points to the security folder.
Now restart the NSClient++ service in services.msc:
Again Kudos to Milan Kozak for finding and sharing this solution!
Invalid packet version received from server
As soon as NSClient++ was re-configured to use the larger DH key and the service restarted, the check_nrpe plugin was able to communicate with this Windows host again.
However another warning started to show up:
root@focal:~# /usr/lib/nagios/plugins/check_nrpe -H 10.10.22.23
CHECK_NRPE: Invalid packet version received from server.
I (0.5.2.35 2018-01-28) seem to be doing fine…
The newer check_nrpe plugin uses the newer NRPE v3 protocol — but it seems that the NSClient++ agent answers with the older NRPE v2 protocol. To handle this, simply tell the check_nrpe plugin to use the older v2 protocol using the optional -2 parameter:
root@focal:~# /usr/lib/nagios/plugins/check_nrpe -H 10.10.22.23 -2
I (0.5.2.35 2018-01-28) seem to be doing fine…
Add a comment
Show form to leave a comment
Comments (newest first)
No comments yet.

