Не знаю как вы, но лично я в своем телефоне ничему не удивляюсь. Обрывочные сообщения в заметках, забавные (и не очень) фотографии в Галерее и приложения, которые нужно было удалить год назад. С такими неожиданностями встречаются многие пользователи гаджетов. Но они незначительны по сравнению с Календарем, который неожиданно напоминает о событиях, которые никто не добавлял. Мы расскажем, что за вирус создает напоминания в Календаре на Андроиде, и как удалить его.
Как себя проявляет вирус-спамер в Календаре
На самом деле, программа, провоцирующая создание новых событий, прячется не в самом гаджете. Скажем больше, спам, попадающий в Календарь, создается не вирусами, а людьми, которые просто получили полный адрес вашей электронной почты. Злоумышленники (или горе-рекламодатели) отправляют приглашение на вашу почту, которая автоматически синхронизируется с Календарем.
Последний, в свою очередь, отображает приглашения в виде событий за день и несколько часов до установленной даты. Все бы ничего, но эти сообщения сопровождаются звуковым уведомлением, а также всплывающим окном. Потому мы попытаемся разобраться, как избавиться от спам-рассылки или хотя бы минимизировать проблемы от нее.
Как от него избавиться
Следуя логике, решить проблему можно несколькими способами:
- Лишить спамеров возможности указывать вашу почту. Но это практически нереально, так как почта используется для регистрации практически во всех сервисах. Да и вирусы постоянно копируют все найденные адреса.
- Разорвать связь между почтой и Календарем. Следуя терминологии, для этого нужно выключить синхронизацию.
- Избавиться от того, что создает проблему, то есть от Календаря.
Последняя идея немного рисковая, учитывая, что сегодня сервис Google по умолчанию используется во многих приложениях.
Отключение синхронизации с Gmail
Итак, рассмотрим наиболее безопасный вариант, который рекомендуют, в том числе и специалисты Google (ограничить возможности рассылок они почему-то не решились).
При отключении синхронизации с Gmail все спам-рассылки продолжат приходить на почту, но при этом они не будут высвечиваться в событиях на телефоне. Алгоритм действий:
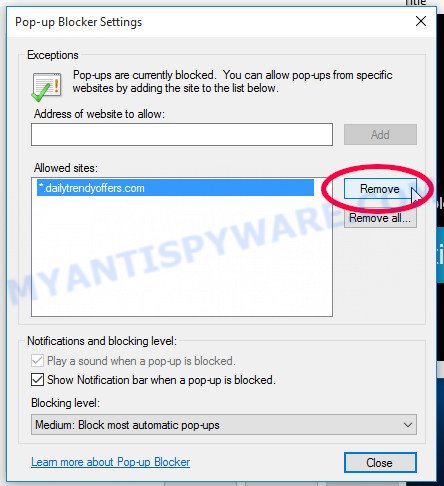
- Найдите приложение Google Календарь на телефоне. Порой для этого достаточно кликнуть по дате в шторке уведомлений.
- Кликните по трем горизонтальным линиям в левом верхнем углу.
- Прокрутите открывшееся меню вниз, пока не увидите кнопку «Настройки». Кликните по ней.
- Выберите раздел «Мероприятия из Gmail».
- Отключите единственный пункт в открывшемся разделе.
Готово. Теперь проблема со спамом должна исчезнуть.
Удаление Google Календаря
Этот вариант несет за собой серьезные последствия, да и мы не видим в нем смысла. Предыдущий способ обычно покрывает все требования пользователей. Однако, если вам нужно удалить (а точнее отключить) сам Google Календарь, то это можно сделать следующим способом:
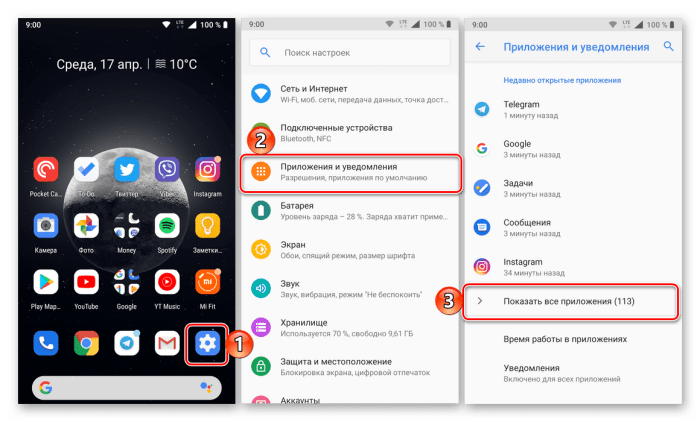
- Откройте настройки. Скорее всего, это значок шестеренки или тумблеров в шторке уведомлений.
- Перейдите в раздел «Приложения».
- Найдите в этом разделе приложение «Google Календарь» и откройте страницу о нем.
- Нажмите на кнопку «Отключить» или «Удалить» (при ее наличии).
Готово. Также не забудьте выключить автозапуск для приложения. Теперь останется найти только альтернативный Календарь. Учтите, что после этого вы не сможете добавлять события в Календарь через Google-ассистента.
Если даже после двух вышеперечисленных способов приходят странные спам-сообщения, значит, на вашем устройстве действительно завелся вирус. В таком случае рекомендуем установить антивирус (например, Dr. Web Cureit) и запустить полную проверку гаджета.
Благодарим за прочтение.
Часто смартфоны и планшеты под управлением операционной системы Андроид подвергаются атакам разных вирусов и спама. Для борьбы с вредоносным ПО рекомендуется использовать лучшие приложения антивирусы. Чтобы избавиться от спама в Гугл Календаре, а также в любых других сторонних программах-календарях, которые в процессе своей работы синхронизируются с Google, необходимо просто изменить некоторые настройки. После этого вы навсегда забудете об этой распространенной проблеме.
Каким образом спам проникает в Календарь от Гугл?
Компания Google давно ведет активную борьбу со спамом и всплывающей рекламой на Андроид телефонах. Для этого уже было внедрено множество разработок. Но, совершенствуя методы борьбы со спамным контентом, сами спамеры успешно модернизируют и свои продукты.
На всех устройствах Андроид спам появляется в Календаре из-за синхронизации с почтовой службой Gmail. При таком раскладе рассылки на те или иные мероприятия отправляются на наши смартфоны в формате приглашений, а не как обычные письма. Таким образом, они сразу попадают в приложение Календарь, легко обходя почтовый сервис Gmail, который мог бы распознать и убрать спамные уведомления.
Как можно избавиться от спама в Календаре?
Календарь Гугл наделен двумя специальными опциями. По умолчанию они предоставляют возможность любому, кому известен адрес вашей электронной почты, отправить вам спамное приглашение. Одна из таких опций отключается непосредственно на мобильном устройстве в настройках работы приложения «Календарь», а другая в онлайн-версии сервиса.
Благодаря простым настройкам, каждый владелец Андроид может избавиться от спамных приглашений и уведомлений. Например, одно из часто встречающихся — «Вам денежный перевод». Для гарантированного результата рекомендуется использовать функционал веб-версии Гугл Календаря.
-
- Откройте официальный сайт по этой ссылке и авторизуйтесь под данными свой учетной записи Google. После входа вверху экрана нажмите на значок шестеренки, чтобы оказаться в «Настройках» сервиса.
-
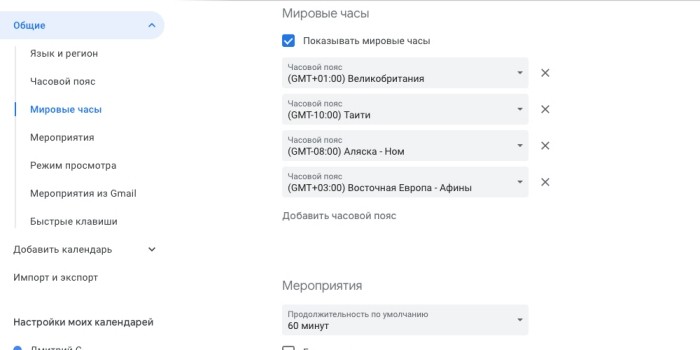
- Перейдите в раздел «Общие», а в нем выберите пункт под названием «Мероприятия».
-
- Здесь в поле «Автоматически добавлять приглашения» выберите функцию «Нет, показывать только приглашения, на которые уже отправлен ответ».
-
- Теперь в разделе «Общие» откройте пункт «Мероприятия из Gmail». Напротив опции «Автоматически добавлять мероприятия из Gmail в мой календарь» уберите отметку.
На этом все. Задав такие параметры, спам больше не будет появляться в Гугл Календаре вашего Андроид.
Looks like no one’s replied in a while. To start the conversation again, simply
ask a new question.
Starting a week ago, I am getting several messages a day added as entries to the calendar, such as «Your phone might not be protected! Click to protect it!», «Click now to protect your priceless data!», or «Your phone data might leak! Secure it by clicking now», that seem to be malware. This has never happened to me in the past. What would have triggered the messages? Is there actually anything to fix on the phone? How could I stop receiving those messages? Thanks for your help
iPhone 12,
iOS 14
Posted on Jan 7, 2021 10:11 AM
The warnings are a scam
You picked up a spam calendar, possibly by saying yes to a website offering notifications.
First open Calendar. Tap Calendars, uncheck the one you don’t recognise.
Then in Settings, Calendars, Accounts delete any rogue accounts .
Posted on Jan 7, 2021 10:29 AM
Similar questions
-
Messages from calendar
I have been getting some messages from my calendar, saying my iPhone is being hacked and my phone have been infected and also my iOS has been damaged… how can i solve this problem?
91
1
-
Message that my phone been attacked
I have been receiving messages that my phone been attacked, and that very soon all my data will be lost.Giving me some links to open,but have not opened them.What made me question these messages is that they come through my calendar.But now I keep on receiving alerts and calendar invites which are random.
How can I stop this?
38
1
-
I keep getting messages on my IPhone Calendar staying my phone may have been hacked.
I keep getting messages on my IPhone Calendar staying my phone may have been hacked.
114
1
iphone 12 calendar messages
CLICK-NOW-ON-THIS.ONLINE — это вирус, который показывает всплывающую рекламу в браузере.
- Показывает CLICK-NOW-ON-THIS.ONLINE нежелательную всплывающую рекламу.
- CLICK-NOW-ON-THIS.ONLINE перенаправляет щелчки в браузере на вредоносные веб сайты.
- CLICK-NOW-ON-THIS.ONLINE показывается регулярно, даже если закрываешь браузер.
- CLICK-NOW-ON-THIS.ONLINE появляется в строке ввода браузера при выборе новой вкладки.
- CLICK-NOW-ON-THIS.ONLINE меняет настройки поиска в браузере.
- CLICK-NOW-ON-THIS.ONLINE меняет ярлыки браузера на рабочем столе и в меню, чтобы вместе с запуском браузера показывалась реклама.
Как происходит заражение рекламным вирусом CLICK-NOW-ON-THIS.ONLINE?
Мой братишка — заядлый геймер. Что ни зайду в гости — он постоянно во что-то рубится. Иногда я думаю, что ест, спит и справляет нужду — тоже возле компьютера. Играет просто во все, что движется. Онлайн, оффлайн…
В общем, скачивает он порядочное количество всякого интернет мусора, не обращая внимание на содержимое и безопасность установочного процесса. Все, что он инсталлирует — он инсталлирует по-умолчанию. Так же быстрее! Короче, я не был удивлен, когда вчера он пожаловался мне, что подцепил очередной рекламный вирус — CLICK-NOW-ON-THIS.ONLINE.
Сейчас очень популярно стало дополнять инсталяционные пакеты всяческим мусорным софтом, которое, вообще говоря, вам вовсе и не нужно. Более того, иногда оно даже потенциально опасно. Одним из примеров такого нежелательного программного обеспечения и служит рекламный вирус CLICK-NOW-ON-THIS.ONLINE. Звучит просто как имя сайта. Но на самом деле данный зловред начинает заваливать вас назойливой рекламой с момента заражения вашего компьютера.
Как избежать заражения вирусом CLICK-NOW-ON-THIS.ONLINE или иным зловредом?
Прежде всего никогда не устанавливайте новое программное обеспечение по-умолчанию. Всегда обращайте внимание на опции установки. Внимательно смотрите, не предлагается ли установить дополнительно и ненужное вам программное обеспечение. От его установки лучше отказаться. Помните: потратьте сейчас на минуту больше своего времени, и вы избежите геморроя по расчистке своего компьютера в будущем!
«Ну а что делать, если я уже заразился вирусом?», — спросите вы.
Без паники, пару методов я набросал. Как всегда: ручками, и машиной. Угадайте, какой предпочитаю я?
Инструкция по ручному удалению рекламного вируса CLICK-NOW-ON-THIS.ONLINE
Для того, чтобы самостоятельно избавиться от рекламы CLICK-NOW-ON-THIS.ONLINE, вам необходимо последовательно выполнить все шаги, которые я привожу ниже:
- Поискать «CLICK-NOW-ON-THIS.ONLINE» в списке установленных программ и удалить ее.
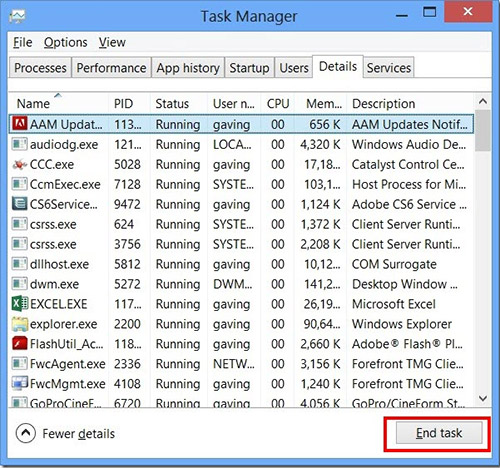
- Открыть Диспетчер задач и закрыть программы, у которых в описании или имени есть слова «CLICK-NOW-ON-THIS.ONLINE». Заметьте, из какой папки происходит запуск этой программы. Удалите эти папки.
- Запретить вредные службы с помощью консоли services.msc.
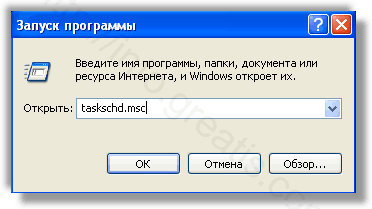
- Удалить ‘Назначенные задания’, относящиеся к CLICK-NOW-ON-THIS.ONLINE, с помощью консоли taskschd.msc.
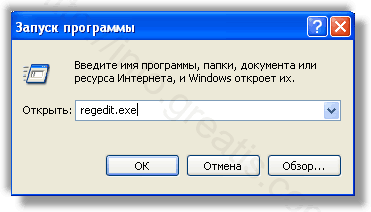
- С помощью редактора реестра regedit.exe поискать ключи с названием или содержащим «CLICK-NOW-ON-THIS.ONLINE» в реестре.
- Проверить ярлыки для запуска браузеров на предмет наличия в конце командной строки дополнительных адресов Web сайтов и убедиться, что они указывают на подлинный браузер.
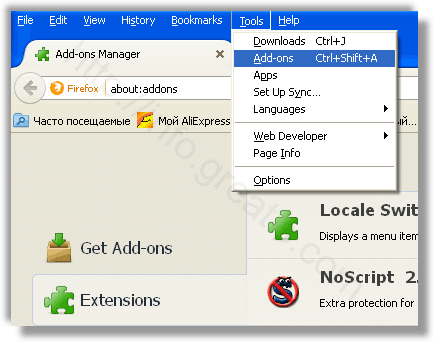
- Проверить плагины всех установленных браузеров Internet Explorer, Chrome, Firefox и т.д.
- Проверить настройки поиска, домашней страницы. При необходимости сбросить настройки в начальное положение.
- Проверить настройки DNS вашей сети. Рекомендую обратиться к документации, предоставленной вашим провайдером.
- Очистить корзину, временные файлы, кэш браузеров.
И все же автоматика лучше!
Если ручной метод — не для вас, и хочется более легкий путь, существует множество специализированного ПО, которое сделает всю работу за вас. Я рекомендую воспользоваться UnHackMe от Greatis Software, выполнив все по пошаговой инструкции.
Шаг 1. Установите UnHackMe. (1 минута)
Шаг 2. Запустите поиск вредоносных программ в UnHackMe. (1 минута)
Шаг 3. Удалите вредоносные программы. (3 минуты)
UnHackMe выполнит все указанные шаги, проверяя по своей базе, всего за одну минуту.
При этом UnHackMe скорее всего найдет и другие вредоносные программы, а не только редиректор на CLICK-NOW-ON-THIS.ONLINE.
При ручном удалении могут возникнуть проблемы с удалением открытых файлов. Закрываемые процессы могут немедленно запускаться вновь, либо могут сделать это после перезагрузки. Часто возникают ситуации, когда недостаточно прав для удалении ключа реестра или файла.
UnHackMe легко со всем справится и выполнит всю трудную работу во время перезагрузки.
И это еще не все. Если после удаления редиректа на CLICK-NOW-ON-THIS.ONLINE какие то проблемы остались, то в UnHackMe есть ручной режим, в котором можно самостоятельно определять вредоносные программы в списке всех программ.
Итак, приступим:
Шаг 1. Установите UnHackMe (1 минута).
- Скачали софт, желательно последней версии. И не надо искать на всяких развалах, вполне возможно там вы нарветесь на пиратскую версию с вшитым очередным мусором. Оно вам надо? Идите на сайт производителя, тем более там есть бесплатный триал. Запустите установку программы.
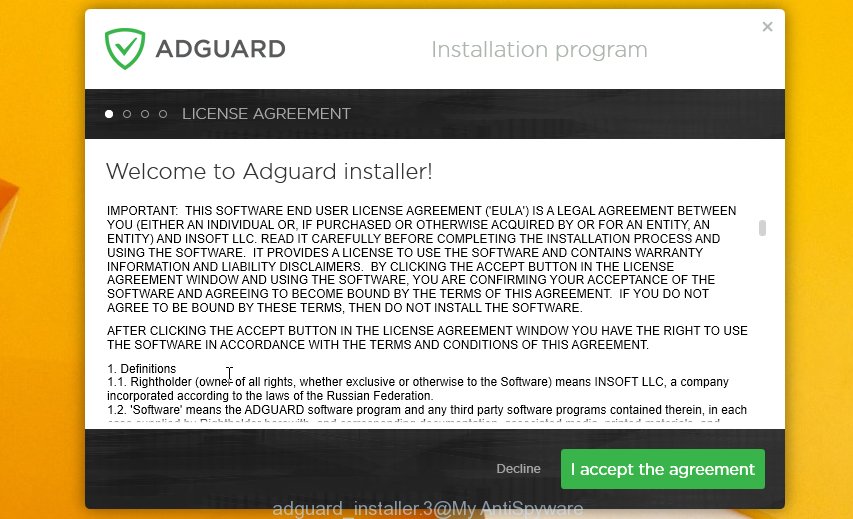
- Затем следует принять лицензионное соглашение.
- И наконец указать папку для установки. На этом процесс инсталляции можно считать завершенным.
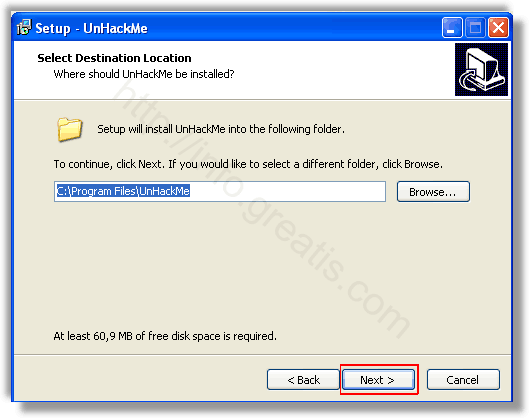
Шаг 2. Запустите поиск вредоносных программ в UnHackMe (1 минута).
- Итак, запускаем UnHackMe, и сразу стартуем тестирование, можно использовать быстрое, за 1 минуту. Но если время есть — рекомендую расширенное онлайн тестирование с использованием VirusTotal — это повысит вероятность обнаружения не только вируса CLICK-NOW-ON-THIS.ONLINE, но и остальной нечисти.
- Мы увидим как начался процесс сканирования.
Шаг 3. Удалите вредоносные программы (3 минуты).
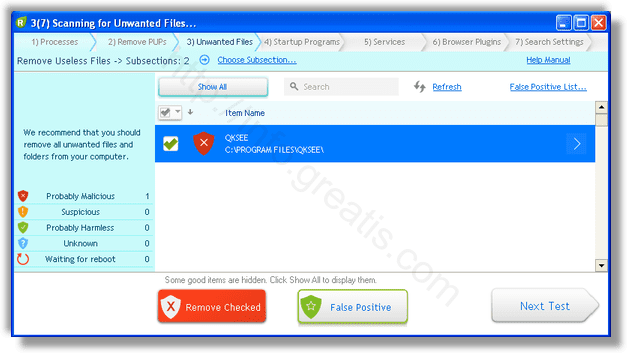
- Обнаруживаем что-то на очередном этапе. UnHackMe отличается тем, что показывает вообще все, и очень плохое, и подозрительное, и даже хорошее. Не будьте обезьяной с гранатой! Не уверены в объектах из разряда ‘подозрительный’ или ‘нейтральный’ — не трогайте их. А вот в опасное лучше поверить. Итак, нашли опасный элемент, он будет подсвечен красным. Что делаем, как думаете? Правильно — убить! Ну или в английской версии — Remove Checked. В общем, жмем красную кнопку.
- После этого вам возможно будет предложено подтверждение. И приглашение закрыть все браузеры. Стоит прислушаться, это поможет.
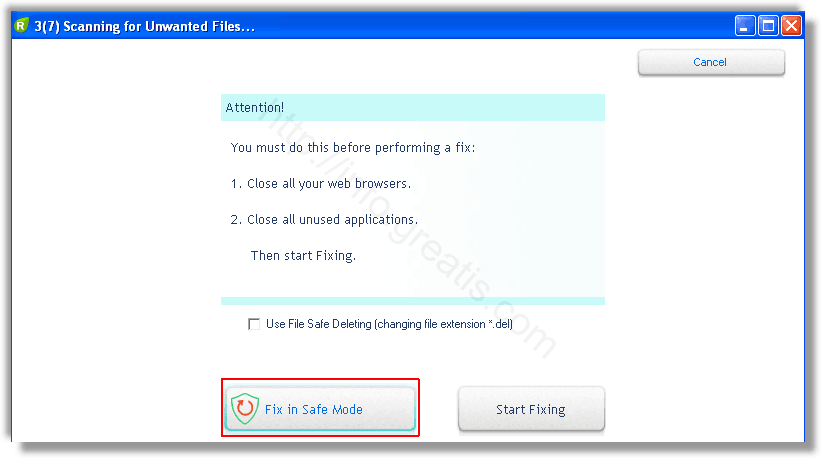
- В случае, если понадобится удалить файл, или каталог, пожалуй лучше использовать опцию удаления в безопасном режиме. Да, понадобится перезагрузка, но это быстрее, чем начинать все сначала, поверьте.
- Ну и в конце вы увидите результаты сканирования и лечения.
Итак, как вы наверное заметили, автоматизированное лечение значительно быстрее и проще! Лично у меня избавление от вируса CLICK-NOW-ON-THIS.ONLINE заняло 5 минут! Поэтому я настоятельно рекомендую использовать UnHackMe для лечения вашего компьютера от любых нежелательных программ!
[ratings]
What is Micmitosas.top?
Micmitosas.top domain is part of a redirect chain. Redirect chain is a sequence of URLs starting from the first – initial URL, ending with the last – final destination URL. Attackers may use long redirect chains to hide malicious content. Most malicious redirects are conditional. It means that redirection only occurs when a certain condition is met. For example, search traffic redirects only occur when someone clicks from Google’s search results.
In some cases, unsuspecting users are taken to a rogue web page containing a pretend CAPTCHA examine, clicking which serves unwanted ads which are disguised to look as if they come from the working system and never from a web browser. In other cases, users are redirected to pages containing malware.
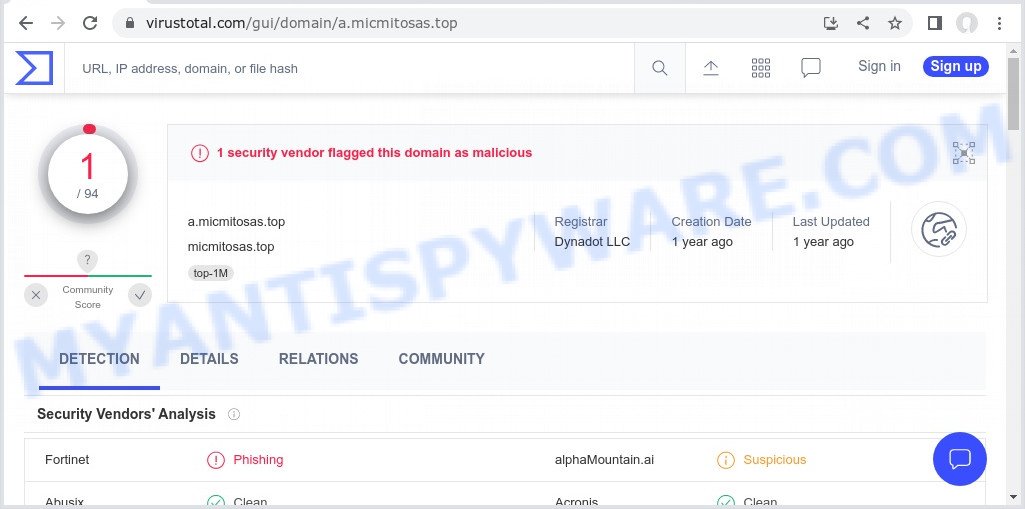
VirusTotal flagged Micmitosas.top as malicious:
QUICK LINKS
- What is Micmitosas.top?
- Protection
- Removal
Micmitosas.top redirect in detail
Micmitosas.top is not the final redirect destination. Depending on the browser and the IP, the visitor gets redirected further. In most cases, malicious redirects occur when users browse high-risk websites, when users click on a malicious link from spam calendar events, push notifications and spam emails. In addition, they can be redirected to the first – initial URL by malicious advertisements (malvertising) and Adware. Adware is a form of malicious software designed to display unwanted ads, redirect search queries to sponsored websites, and collect user data for marketing purposes. Adware can display banner ads, full-screen advertisements, pop-ups, videos, or other forms of online advertising. These annoying advertisements consume PC resources and slow down the system.
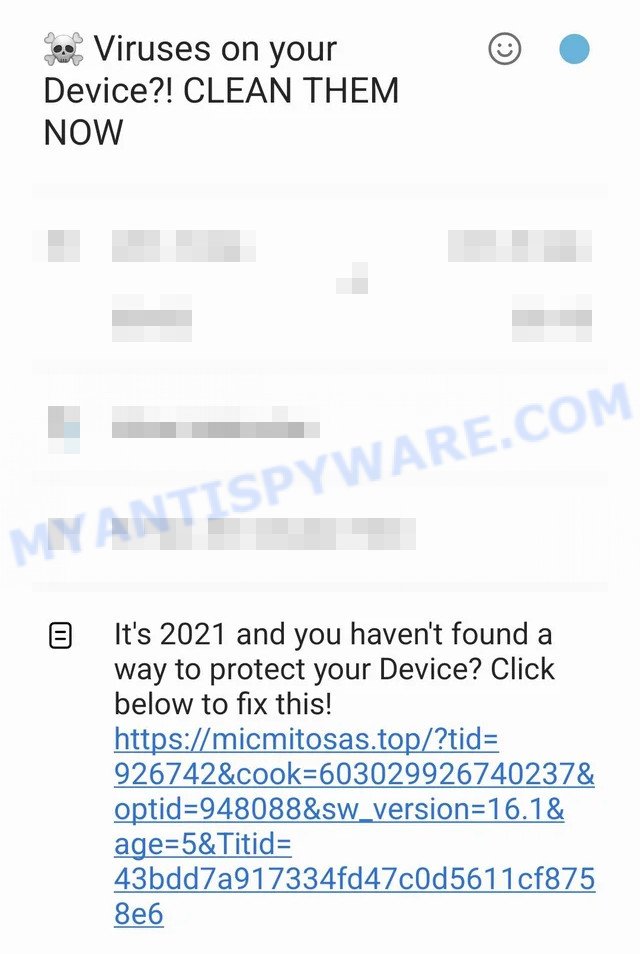
An example of micmitosas.top spam calendar event on android:
Adware is often harmless, but sometimes adware can also be spyware. Spyware can steal personal information (passwords, credit card numbers, and other confidential information) that can be used for identity theft. Therefore, it is very important to get rid of adware immediately.
Attackers often use adware to redirect users to various diet pills scams, fake dating websites, pornographic content, fake virus alerts that trick users to buy or install applications that are not needed, work-at-home schemes and other questionable content. Below are some examples of such sites:
In summary, malicious redirects can trick users into making security mistakes or giving away sensitive information, exploit vulnerabilities on their computer and install malicious software.
Threat Summary
| Name | Micmitosas.top |
| Type | redirect chain, redirects |
| Example URLs | https://micmitosas.top/?tid=926742&cook=…&optid=948088&sw_version=16.1&age=8&Titid=… |
| Calendar Spam Events | “⚠ YOUR Device can be infected with A VIRUS ⚠ Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS”, “☠️ Viruses on your Device?! CLEAN THEM NOW It’s 2021 and you haven’t found a way to protect your Device? Click below to fix this!”, “⚠ Android Virus Protection Expired ?! Renew for 2021 We have all heard stories about people who got exposed to malware and expose their data at risk. Don’t be silly, protect yourself now by clicking below!”, “🛑 Your Phone is not Protected ?! Click To Protect it!It’s 2021 and you haven’t found a way to protect your Device? Click below to fix this!”, “🛡️ Click NOW to Protect your Priceless Data!Your identity and other important information can be easily stolen online without the right protection. VPN can effectively avoid that from happening. Click below to avail of that needed protection.”, “⚠ Viruses Alert – Check Protection NOWHackers and practically anyone who want it can check where you live by breaking into your device. Protect your self by clicking below.”, “⚠ Hackers may try to steal your data! Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS”, “⚠ You May Be Exposed Online Click To Fix!Hackers can check where you live by checking your device’s IP while you are at home. Protect yourself by installing a VPN. Protect your self by clicking below.” |
| Symptoms |
|
| Removal | Micmitosas.top removal guide |
Examples of malicious and scam sites
We have reported several other scam and malicious sites in the past. Examples: Pornographic Spyware Alert, You’ve made the 5-billionth search, Windows Defender – Security Warning, Cleaner Update for Android is Recommended.
Users never visit sites like Micmitosas.top themselves. Typically, users are redirected to them after they click on misleading ads, visit torrent, illegal movie streaming and similar websites. Sometimes, users are redirected to the sites due to installed browser hijackers, adware or other unwanted software.
How does Adware get on your computer
A large number of spyware, adware programs, browser toolbars, hijackers, and PUPs are installed when installing freeware and peer-2-peer file sharing software. Therefore, when installing freeware, you need to be careful not to accidentally install additional software. It is important that you pay attention to the EULA (End User License Agreements) and select the Custom, Manual or Advanced setup mode as it will typically disclose what bundled apps will also be installed.
How can you protect against malicious redirects?
There are a number of methods that you can use to protect against malicious redirects and Adware. It is better to use them together, this will provide stronger protection.
- Use an ad blocker. Ad blockers allow you to browse sites without ads, thus eliminating the possibility of clicking on something malicious and preventing it from being downloaded to the machine.
- Pay for premium versions of popular services. The easiest way to avoid adware is to pay for the service you use. Many Internet services make it possible to use them without ads if you purchase a premium subscription. This helps ensure that malicious adware cannot reach you.
- Buy devices from trusted companies with built-in security. There have already been many cases where people who bought inexpensive Android devices found that adware was already installed on their devices. Cheap Android devices do not receive security updates and are therefore particularly susceptible to infection and should be avoided.
- Use an antivirus. Most antivirus programs can block malicious adware. Some malicious adware can block antiviruses, in which case a more aggressive method should be used, which is to use adware removal software. This software can detect and remove adware that has a negative impact on the device.
How to remove Micmitosas.top pop-up redirect (Adware removal instructions)
We can help you remove Micmitosas.top from your browsers without the need to contact an IT technician. Just follow the removal instructions below. If you find it difficult to get rid scam pop-ups on your browser, feel free to contact us for help in the comments section below. Some steps will require you to restart your computer or exit this web page. So, read this guide carefully and then bookmark this page or open it on your smartphone for future reference.
To remove Micmitosas.top, follow the steps below:
- Remove spam notifications
- Check the list of installed software
- Remove Micmitosas.top pop-ups from Google Chrome
- Remove Micmitosas.top from Mozilla Firefox
- Remove Micmitosas.top pop-ups from Internet Explorer
- Automatic Removal of Adware
- Stop Micmitosas.top pop-ups
The step-by-step guide will help you manually remove Micmitosas.top pop-ups from your computer. If you have little experience in using computers, we advise that you use free adware removers listed below.
Remove spam notifications
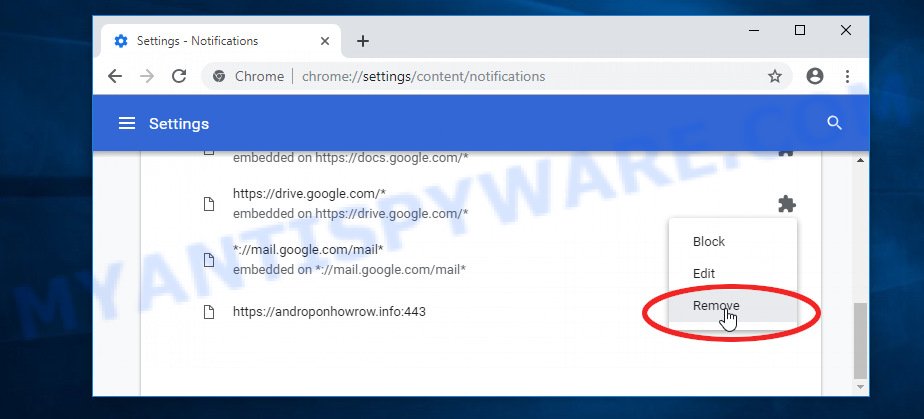
If you are receiving spam notifications, then you have previously clicked the “Allow” button. Below we will teach you how to turn them off.
Google Chrome:
- Click on ‘three dots menu’ button at the top-right corner of the Google Chrome window.
- Select ‘Settings’, scroll down to the bottom and click ‘Advanced’.
- At the ‘Privacy and Security’ section click ‘Site settings’.
- Click on ‘Notifications’.
- Locate a malicious site and click the three vertical dots button next to it, then click on ‘Remove’.
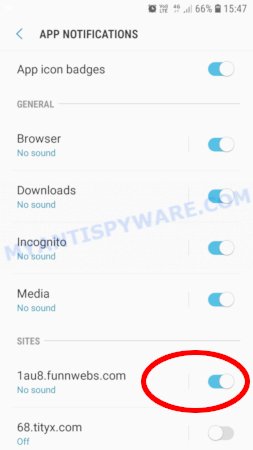
Android:
- Open Chrome.
- Tap on the Menu button (three dots) on the top right corner of the screen.
- In the menu tap ‘Settings’, scroll down to ‘Advanced’.
- In the ‘Site Settings’, tap on ‘Notifications’, locate a scam URL and tap on it.
- Tap the ‘Clean & Reset’ button and confirm.
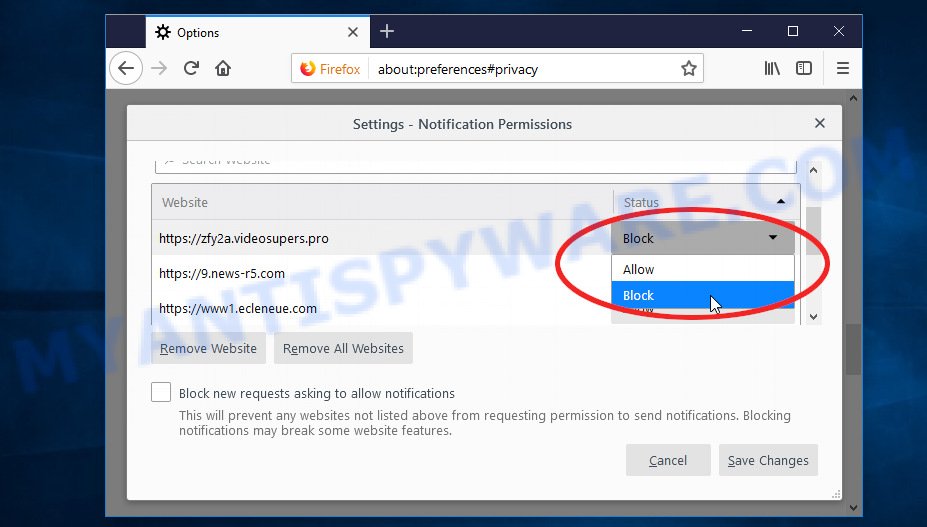
Mozilla Firefox:
- In the top right corner, click the Firefox menu (three bars).
- In the drop-down menu select ‘Options’. In the left side select ‘Privacy & Security’.
- Scroll down to ‘Permissions’ section and click ‘Settings…’ button next to ‘Notifications’.
- Find suspicious URLs, click the drop-down menu and select ‘Block’.
- Click ‘Save Changes’ button.
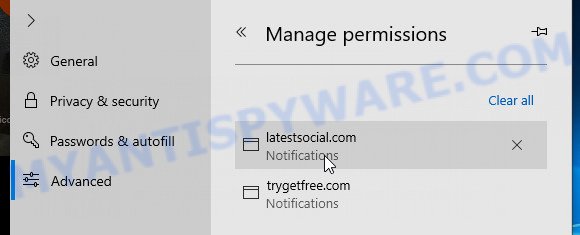
Edge:
- Click the More button (three dots) in the top-right corner of the window.
- Scroll down, locate and click ‘Settings’. In the left side select ‘Advanced’.
- In the ‘Website permissions’ section click ‘Manage permissions’.
- Disable the on switch for scam domains.
Internet Explorer:
- Click the Gear button on the top-right corner of the browser.
- Select ‘Internet options’.
- Click on the ‘Privacy’ tab and select ‘Settings’ in the pop-up blockers section.
- Locate a scam site and click the ‘Remove’ button to delete the site.
Safari:
- Go to ‘Preferences’ in the Safari menu.
- Select the ‘Websites’ tab and then select ‘Notifications’ section on the left panel.
- Find a scam site and select it, click the ‘Deny’ button.
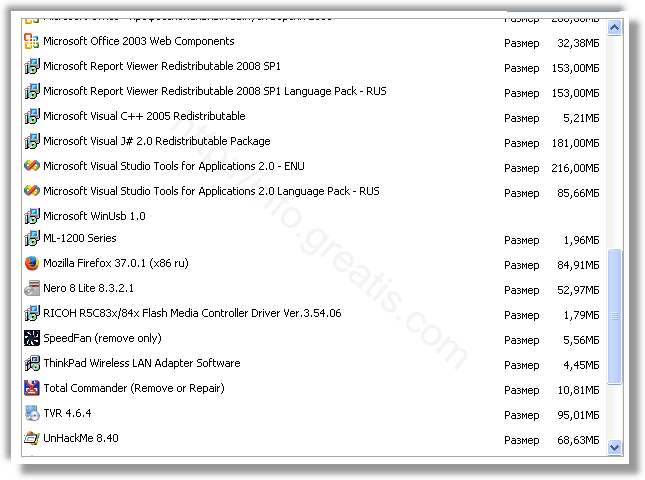
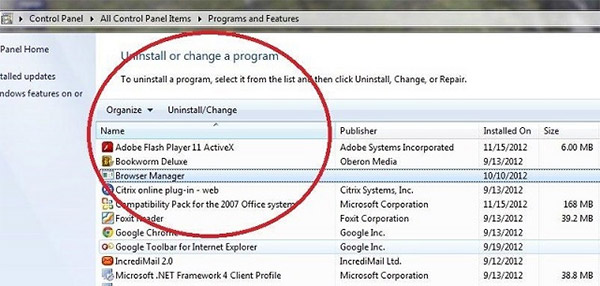
Check the list of installed software
The adware removal process is generally the same in all versions of Windows from 11 to XP. First you need to check the list of installed software on your computer and remove all unused, unknown and suspicious software.
|
|
|
|
Remove Micmitosas.top pop-ups from Google Chrome
This step will show you how to restore your original Chrome browser settings. This can remove rogue pop-ups and fix some browsing issues, especially after adware infection. However, your topics, bookmarks, history, passwords, and web form autofill data will not be deleted.
- First start the Google Chrome and click Menu button (small button in the form of three dots).
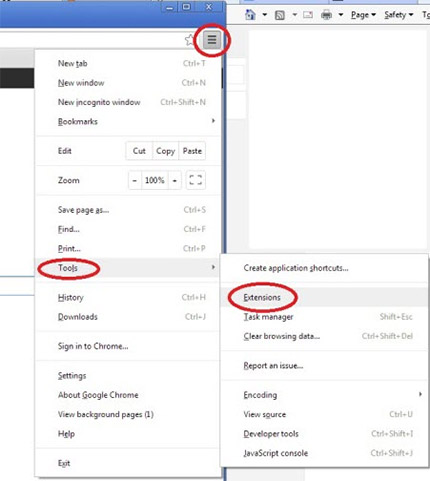
- It will show the Google Chrome main menu. Choose More Tools, then press Extensions.
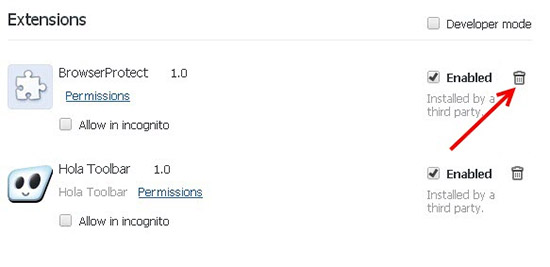
- You will see the list of installed add-ons. If the list has the extension labeled with “Installed by enterprise policy” or “Installed by your administrator”, then complete the following guide: Remove Chrome extensions installed by enterprise policy.
- Now open the Chrome menu once again, click the “Settings” menu.
- You will see the Google Chrome’s settings page. Scroll down and click “Advanced” link.
- Scroll down again and click the “Reset” button.
- The Chrome will display the reset profile settings page as shown on the image above.
- Next press the “Reset” button.
- Once this process is done, your web browser’s home page, newtab and search engine by default will be restored to their original defaults.
- To learn more, read the blog post How to reset Chrome settings to default.
Remove Micmitosas.top from Mozilla Firefox
Resetting Mozilla Firefox will remove redirects to Micmitosas.top, fix changed settings, disable malicious extensions, and restore security settings altered by adware. However, your saved passwords and bookmarks will not be changed, deleted or cleared.
First, start the Mozilla Firefox. Next, click the button in the form of three horizontal stripes (). It will open the drop-down menu. Next, press the Help button (
).
In the Help menu click the “Troubleshooting Information”. In the upper-right corner of the “Troubleshooting Information” page click on “Refresh Firefox” button like below.
Confirm your action, click the “Refresh Firefox”.
Remove Micmitosas.top pop-ups from Internet Explorer
Resetting Internet Explorer is great if your browser is hijacked or you have unwanted add-ons or toolbars in your web browser installed by malware.
First, launch the Microsoft Internet Explorer, then click ‘gear’ icon . It will show the Tools drop-down menu on the right part of the internet browser, then click the “Internet Options” as shown on the image below.
In the “Internet Options” screen, select the “Advanced” tab, then click the “Reset” button. The Internet Explorer will display the “Reset Internet Explorer settings” dialog box. Further, click the “Delete personal settings” check box to select it. Next, click the “Reset” button as shown in the following example.
When the process is complete, click the “Close” button. Close Internet Explorer and restart your computer for the changes to take effect. This step will help you restore your browser settings to their default state.
Automatic Removal of Adware
The guide above is tedious and may not always help you remove adware and rogue pop-ups completely. Here I will tell you the automatic way to completely remove adware from your PC. Zemana, MalwareBytes, and Hitman Pro are anti-malware utilities that can find and remove all kinds of malware, including adware that causes scam pop-ups.
Remove Micmitosas.top redirect with MalwareBytes
We recommend using the MalwareBytes AntiMalware that are completely clean your PC of the adware software. The free utility is an advanced malicious software removal application developed by (c) Malwarebytes lab. This program uses the world’s most popular anti malware technology. It’s able to help you remove intrusive Micmitosas.top pop ups from your web browsers, PUPs, malware, hijackers, toolbars, ransomware and other security threats from your PC for free.
- Visit the page linked below to download the latest version of MalwareBytes for Microsoft Windows. Save it directly to your Desktop.
- When the download is done, close all software and windows on your computer. Open a directory in which you saved it. Double-click on the icon that’s named MBsetup.
- Choose “Personal computer” option and click Install button. Follow the prompts.
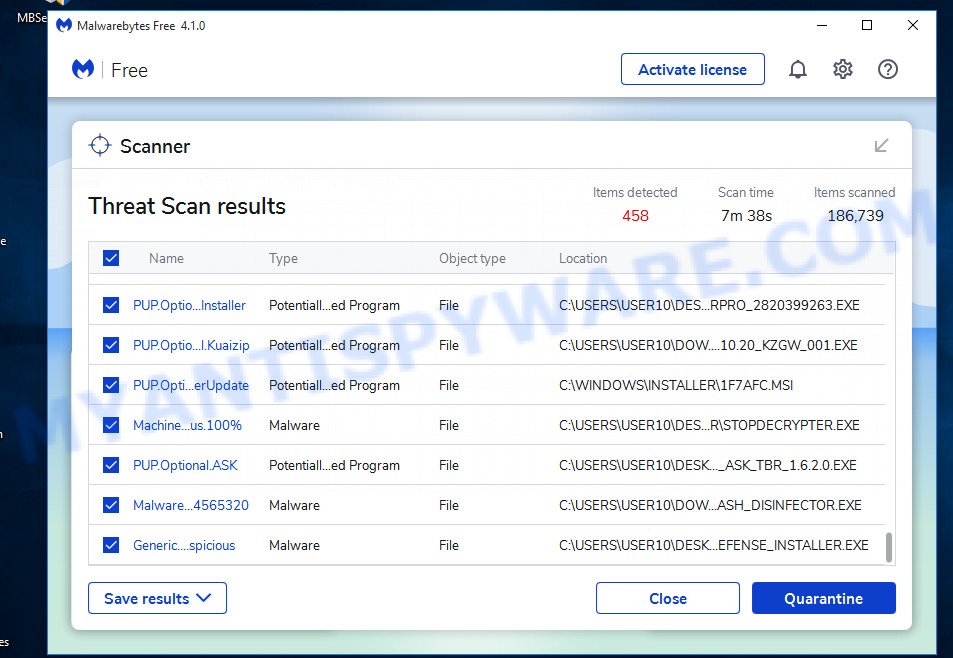
- Once setup is finished, press the “Scan” button to perform a system scan for adware and other malware. A system scan can take anywhere from 5 to 30 minutes, depending on your personal computer. While the MalwareBytes Anti Malware utility is scanning, you can see how many objects it has identified as being infected by malware.
- After MalwareBytes completes the scan, it will open you the results. In order to remove all threats, simply click “Quarantine”. After finished, you can be prompted to restart your PC system.
The following video demonstrates how to use MalwareBytes to remove browser hijackers, adware and other malware.
Remove Micmitosas.top pop-ups with Zemana
Zemana Anti Malware is a free malware removal tool for Windows that allows you to find and remove adware and other unwanted programs such as PUPs, malicious internet browser add-ons, browser toolbars.
- First, visit the page linked below, then click the ‘Download’ button in order to download the latest version of Zemana.
Zemana AntiMalware
159024 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019 - Once you have downloaded the install file, make sure to double click on the Zemana.AntiMalware.Setup. This would start Zemana installation on your computer.
- Select installation language and press ‘OK’ button.
- On the next screen ‘Setup Wizard’ simply click the ‘Next’ button and follow the prompts.
- Finally, once the install is finished, Zemana Anti-Malware will open automatically. Else, if does not then double-click on the Zemana icon on your desktop.
- Now that you have successfully install Zemana, let’s see How to use Zemana to remove Micmitosas.top pop-ups from your computer.
- After you have opened the Zemana AntiMalware, you will see a window as shown on the image below, just press ‘Scan’ button to perform a system scan with this tool for the adware.
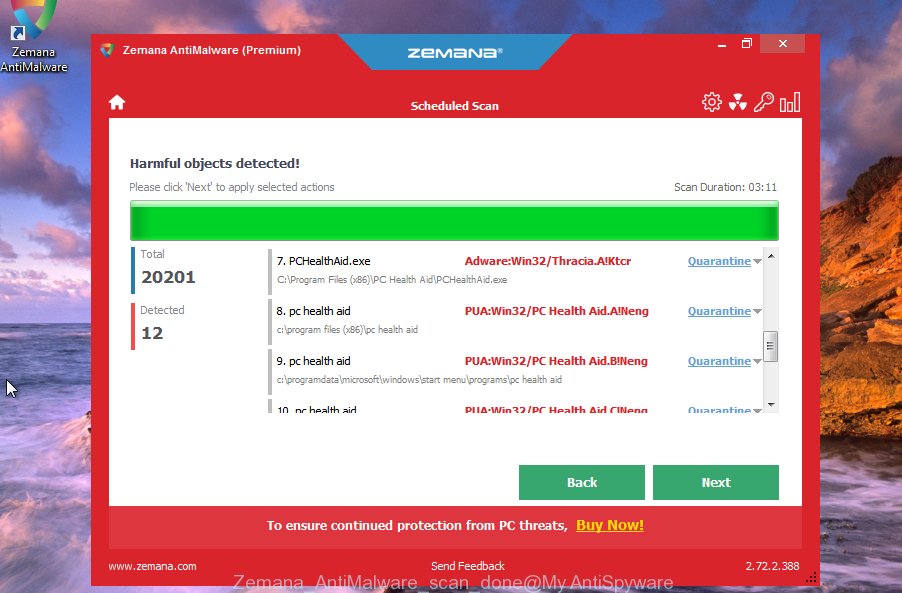
- Now pay attention to the screen while Zemana Anti-Malware scans your PC.
- After the scan is finished, Zemana will show a screen that contains a list of malicious software that has been detected. In order to remove all items, simply click ‘Next’ button.
- Zemana may require a restart computer in order to complete the malware removal process.
- If you want to permanently delete adware from your personal computer, then click ‘Quarantine’ icon, select all malicious software, adware, potentially unwanted applications and other items and press Delete.
- Reboot your computer to complete the removal process.
Remove Micmitosas.top pop-ups from browsers with HitmanPro
HitmanPro is a free removal tool. It removes potentially unwanted applications, adware, browser hijackers, and unwanted web browser extensions. It will detect and remove adware causing Micmitosas.top pop-ups. Hitman Pro uses very small PC resources and is portable program. What’s more, Hitman Pro adds another layer of malware protection.
First, click the following link, then click the ‘Download’ button in order to download the latest version of HitmanPro.
HitmanPro
11186 downloads
Author: Sophos
Category: Security tools
Update: June 28, 2018
When downloading is done, open the file location and double-click the Hitman Pro icon. It will launch the Hitman Pro utility. If the User Account Control prompt will ask you want to run the program, press Yes button to continue.
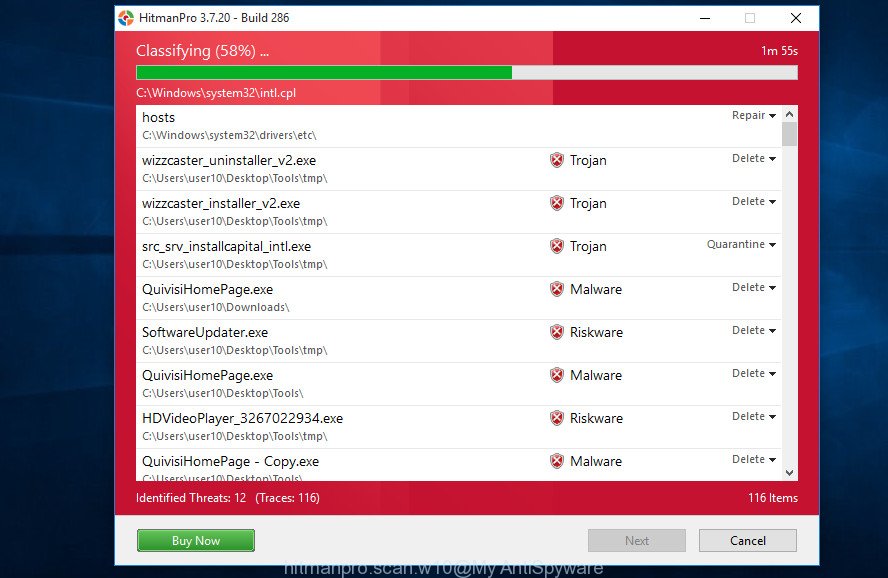
Next, press “Next” . Hitman Pro will scan through the whole computer for adware software, the scan can take anywhere from a few minutes to close to an hour. When a threat is found, the count of the security threats will change accordingly. Wait until the the scanning is finished.
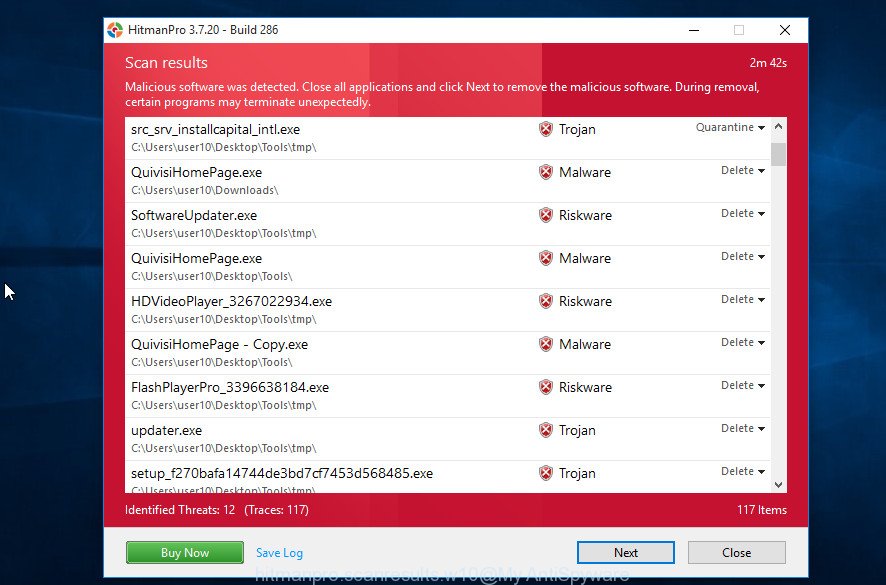
As the scanning ends, it will open the Scan Results like below.
Once you have selected what you want to remove from your PC press “Next” button. It will open a dialog box, click the “Activate free license” button. Hitman Pro will remove adware related to scam popups and move the selected threats to the Quarantine. Once the clean-up is finished, the tool may ask you to restart your device.
Stop Micmitosas.top pop-ups
Use an ad blocking program like AdGuard to stop unwanted ads, malvertisements, pop-ups and online trackers, avoid installing malware and adware browser add-ons that affect your PC performance and impact your PC security. Browse the World Wide Web anonymously and stay safe online!
Visit the following page to download AdGuard. Save it on your Windows desktop.
Adguard download
25500 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to launch it. The “Setup Wizard” window will show up on the computer screen as displayed on the image below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick tutorial as shown in the figure below.
Press “Skip” button to close the window and use the default settings, or click “Get Started” to see an quick guidance which will allow you get to know AdGuard better.
Each time, when you start your computer, AdGuard will start automatically and stop unwanted advertisements, block Micmitosas.top, as well as other malicious or misleading sites. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that is located on your desktop.
To sum up
We hope this article helped you learn more about the Micmitosas.top redirects and avoid the scammers. If you have questions or additional information for our readers, please leave a comment.
On iOS we have seen link shortener services pushing spam calendar files to victims’ devices.
We hope you already know that you shouldn’t click on just any URLs. You might be sent one in a message; somebody might insert one under a social media post or you could be provided with one on basically any website. Users or websites providing these links might use URL shortener services. These are used to shorten long URLs, hide original domain names, view analytics about the devices of visitors, or in some cases even monetize their clicks.
Monetization means that when someone clicks on such a link, an advertisement, such as the examples in Figure 1, will be displayed that will generate revenue for the person who generated the shortened URL. The problem is that some of these link shortener services use aggressive advertising techniques such as scareware ads: informing users their devices are infected with dangerous malware, directing users to download dodgy apps from the Google Play store or to participate in shady surveys, delivering adult content, offering to start premium SMS service subscriptions, enabling browser notifications, and making dubious offers to win prizes.
We’ve even seen link shortener services pushing “calendar” files to iOS devices and distributing Android malware – indeed, we discovered one piece of malware we named Android/FakeAdBlocker, which downloads and executes additional payloads (such as banking trojans, SMS trojans, and aggressive adware) received from its C&C server.
Below we describe the iOS calendar-event-creating downloads and how to recover from them, before spending most of the blogpost on a detailed analysis of the distribution of Android/FakeAdBlocker and, based on our telemetry, its alarming number of detections. This analysis is mainly focused on the functionality of the adware payload and, since it can create spam calendar events, we have included a brief guide detailing how to automatically remove them and uninstall Android/FakeAdBlocker from compromised devices.
Figure 1. Examples of shady aggressive advertisements
Distribution
Content displayed to the victim from monetized link shorteners can differ based on the running operating system. For instance, if a victim clicked on the same link on a Windows device and on a mobile device, a different website would be displayed on each device. Besides websites, they could also offer an iOS device user to download an ICS calendar file, or an Android device user to download an Android app. Figure 2 outlines options we have seen in the campaign analyzed here.
Figure 2. Malware distribution process
While some advertisements and Android applications served by these monetized shortened links are legitimate, we observed that the majority lead to shady or unwanted behavior.
iOS targets
On iOS devices, besides flooding victims with unwanted ads, these websites can create events in victims’ calendars by automatically downloading an ICS file. As the screenshots in Figure 3 show, victims must first tap the subscribe button to spam their calendars with these events. However, the calendar name “Click OK To Continue (sic)” is not revealing the true content of those calendar events and only misleads the victims into tapping the Subscribe and Done button.
These calendar events falsely inform victims that their devices are infected with malware, hoping to induce victims to click on the embedded links, which lead to more scareware advertisements.
Figure 3. Scam website requests user to subscribe to calendar events on iOS platform
Android targets
For victims on Android devices, the situation is more dangerous because these scam websites might initially provide the victim with a malicious app to download and afterwards proceed with visiting or downloading the actual expected content searched for by the user.
There are two scenarios for Android users that we observed during our research. In the first one, when the victim wants to download an Android application other than from Google Play, there is a request to enable browser notifications from that website, followed by a request to download an application called adBLOCK app.apk. This might create the illusion that this adBLOCK app will block displayed advertisements in the future, but the opposite is true. This app has nothing to do with the legitimate adBLOCK application available from the official source.
When the user taps on the download button, the browser is redirected to a different website where the user is apparently offered an ad-blocking app named adBLOCK, but ends up downloading Android/FakeAdBlocker. In other words, the victim’s tap or click is hijacked and used to download a malicious application. If the victim returns to the previous page and taps on the same download button, the correct legitimate file that the intended victim wanted is downloaded onto the device. You can watch one of the examples in the video below.
In the second Android scenario, when the victims want to proceed with downloading the requested file, they are shown a web page describing the steps to download and install an application with the name Your File Is Ready To Download.apk. This name is obviously misleading; the name of the app is trying to make the user think that what is being downloaded is the app or a file they wanted to access. You can see the demonstration in the video below.
In both cases, a scareware advertisement or the same Android/FakeAdBlocker trojan is delivered via a URL shortener service. Such services employ the Paid to click (PTC) business model and act as intermediaries between customers and advertisers. The advertiser pays for displaying ads on the PTC website, where part of that payment goes to the party that created the shortened link. As stated on one of these link shortening websites in the privacy policy section, these ads are via their advertising partners and they are not responsible for delivered content or visited websites.
One of the URL shortener services states in its terms of service that users should not create shortened links to transmit files that contain viruses, spyware, adware, trojans or other harmful code. To the contrary, we have observed that their ad partners are doing it.
Telemetry
Based on our detection data, Android/FakeAdBlocker was spotted for the first time in September 2019. Since then, we have been detecting it under various threat names. From the beginning of this year till July 1st, we have seen more than 150,000 instances of this threat being downloaded to Android devices.
Figure 4. ESET detection telemetry for Android/FakeAdBlocker
Figure 5. Top ten countries by proportion of Android/FakeAdBlocker detections (January 1st – July 1st 2021)
Android/FakeAdBlocker analysis
After downloading and installing Android/FakeAdBlocker, the user might realize that, as seen in Figure 6, it has a white blank icon and, in some cases, even has no app name.
Figure 6. App icon of Android/FakeAdBlocker
After its initial launch, this malware decodes a base64-encoded file with a .dat extension that is stored in the APK’s assets. This file contains C&C server information and its internal variables.
Figure 7. Decoded config file from APK assets
From its C&C server it will request another configuration file. This has a binary payload embedded, which is then extracted and dynamically loaded.
Figure 8. Android/FakeAdBlocker downloads an additional payload
For most of the examples we have observed, the this payload was responsible for displaying out-of-context ads. However, in hundreds of cases, different malicious payloads were downloaded and executed. Based on our telemetry, the C&C server returned different payloads based on the location of the device. The Cerberus banking trojan was downloaded to devices in Turkey, Poland, Spain, Greece and Italy. It was disguised as Chrome, Android Update, Adobe Flash Player, Update Android, or Google Guncelleme app (guencelleme is Turkish for “update” so the name of the app is Google Update). In Greece we have also seen the Ginp banking trojan being downloaded. The same malware family variant of SMS trojan was distributed in the Middle East. Besides these trojans, Bitdefender Labs also identified the TeaBot (also known as Anatsa) banking trojan being downloaded as a payload by Android/FakeAdBlocker. Payloads are downloaded to external media storage in the files subdirectory of the parent app package name using various app names. A list of payload APK names is included in the IoCs section.
The emerging fact that the C&C server can at any time distribute different malicious payloads makes this threat unpredictable. Since all aforementioned trojans have already been analyzed, we will continue with the analysis of the adware payload that was distributed to more than 99% of the victims. The adware payload bears many code similarities with the downloader so we are classifying both in the same Android/FakeAdBlocker malware family.
Although the payloads download in the background, the victim is informed about actions happening on the mobile device by the activity displayed saying file is being downloaded. Once everything is set up, the Android/FakeAdBlocker adware payload asks the victim for permission to draw over other apps, which will later result in it creating fake notifications to display advertisements in the foreground, and for permission to access the calendar.
Figure 9. Activity shown after start
Figure 10. Permission request to control what is displayed in foreground
Figure 11. Permission request to edit calendar events
After all permissions are enabled, the payload silently starts to create events in Google Calendar for upcoming months.
Figure 12. Scareware calendar events created by malware (above) and detail (below)
It creates eighteen events happening every day, each of them lasts 10 minutes. Their names and descriptions suggest that the victim’s smartphone is infected, user data is exposed online or that a virus protection app is expired. Descriptions of each event include a link that leads the victim to visit a scareware advertisement website. That website again claims the device has been infected and offers the user to download shady cleaner applications from Google Play.
Figure 13. Titles and descriptions of the events (left) and the reminder displayed by one of them (right)
All the event title names and their descriptions can be found the malware’s code. Here are all scareware event texts created by the malware, verbatim. If you find one of these in your Google Calendar, you are or were most likely a victim of this threat.
⚠ Hackers may try to steal your data!
Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS
⚠ YOUR Device can be infected with A VIRUS ⚠
Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS
☠️Severe Viruses have been found recently on Android devices
Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS
🛑 Your Phone is not Protected ?! Click To Protect it!
It’s 2021 and you haven’t found a way to protect your Device? Click below to fix this!
⚠ Android Virus Protection Expired ?! Renew for 2021
We have all heard stories about people who got exposed to malware and expose their data at risk. Don’t be silly, protect yourself now by clicking below!
⚠ You May Be Exposed Online Click To Fix!
Hackers can check where you live by checking your device’s IP while you are at home. Protect yourself by installing a VPN. Protect your self by clicking below.
✅ Clear Your Device from Malicious Attacks!
Your Device is not invincible from viruses. Make sure that it is free from infection and prevent future attacks. Click the link below to start scanning!
⚠ Viruses Alert – Check Protection NOW
Hackers and practically anyone who want it can check where you live by breaking into your device. Protect your self by clicking below.
☠️ Viruses on your Device?! CLEAN THEM NOW
It’s 2021 and you haven’t found a way to protect your Device? Click below to fix this!
🛡️ Click NOW to Protect your Priceless Data!
Your identity and other important information can be easily stolen online without the right protection. VPN can effectively avoid that from happening. Click below to avail of that needed protection.
⚠ You Are Exposed Online, Click To Fix!
Hackers can check where you live by checking your device’s IP while you are at home. Protect yourself by installing a VPN. Protect your self by clicking below.
🧹 Clean your Phone from potential threats, Click Now.
Going online exposes you to various risks including hacking and other fraudulent activities. VPN will protect you from these attacks. Make your online browsing secured by clicking the link below.
🛑 Your Phone is not Protected! Click To Protect it!
It’s 2021 and you haven’t found a way to protect your iPhone? Click below to fix this!
⚠ YOUR Device can be infected with A VIRUS ⚠
Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS
⚠ You May Be Exposed Online Click To Fix!
Hackers can check where you live by checking your device’s IP while you are at home. Protect yourself by installing a VPN. Protect your self by clicking below.
☠️Severe Viruses have been found recently on Android devices
Block ads, viruses and pop-ups on YouTube, Facebook, Google, and your favorite websites. CLICK THE LINK BELOW TO BLOCK ALL ADS
☠️ Viruses on your Device?! CLEAN THEM NOW
It’s 2021 and you haven’t found a way to protect your Device? Click below to fix this!
⚠ Android Virus Protection Expired ?! Renew for 2021
We have all heard stories about people who got exposed to malware and expose their data at risk. Don’t be silly, protect yourself now by clicking below!
Besides flooding the calendar with scam events, Android/FakeAdBlocker also randomly displays full screen advertisements within the mobile browser, pops up scareware notifications and adult advertisements, and displays a Messenger-like “bubble” in the foreground mimicking a received message with a scammy text next to it.
Figure 14. Examples of displayed scareware ads
Clicking on any of these would lead the user to a website with further scareware content that suggests that the victim install cleaners or virus removers from Google Play. We have already written about similar shady apps impersonating security software in 2018.
Uninstall process
To identify and remove Android/FakeAdBlocker, including its dynamically loaded adware payload, you need to first find it among your installed applications, by going to Settings -> Apps. Because the malware doesn’t have an icon or an app name (see Figure 15), it should be easy to spot. Once located, tap it once to select it and then tap on Uninstall button and confirm the request to remove the threat.
Figure 15. Manual uninstallation of malware
How to automatically remove spam events
Uninstalling Android/FakeAdBlocker will not remove the spam events it created in your calendar. You can remove them manually; however, it would be a tedious job. This task can also be done automatically, using an app. During our tests we successfully removed all these events using a free app available from the Google Play store called Calendar Cleanup. A problem with this app is that it removes only past events. Because of that, to remove upcoming events, temporarily change the current time and date in the settings of the device to be the day after the last spam event created by the malware. That would make all these events expired and Calendar Cleanup can then automatically remove them all.
It is important to state that this app removes all events, not just the ones created by the malware. Because of that, you should carefully select the targeted range of days.
Once the job is done, make sure to reset the current time and date.
Conclusion
Based on our telemetry, it appears that many users tend to download Android apps from outside of Google Play, which might lead them to download malicious apps delivered through aggressive advertising practices that are used to generate revenue for their authors. We identified and demonstrated this vector of distribution in the videos above. Android/FakeAdBlocker downloads malicious payloads provided by its operator’s C&C server; in most cases, after launch these hide themselves from user view, deliver unwanted scareware or adult content advertisements and create spam calendar events for upcoming months. Trusting these scareware ads might cost their victims money either by sending premium rate SMS messages, subscribing to unnecessary services, or downloading additional and often malicious applications. Besides these scenarios, we identified various Android banking trojans and SMS trojans being downloaded and executed.
IoCs
| Hash | Detection name |
|---|---|
| B0B027011102B8FD5EA5502D23D02058A1BFF1B9 | Android/FakeAdBlocker.A |
| E51634ED17D4010398A1B47B1CF3521C3EEC2030 | Android/FakeAdBlocker.B |
| 696BC1E536DDBD61C1A6D197AC239F11A2B0C851 | Android/FakeAdBlocker.C |
C&Cs
emanalyst[.]biz
mmunitedaw[.]info
ommunite[.]top
rycovernmen[.]club
ransociatelyf[.]info
schemics[.]club
omeoneha[.]online
sityinition[.]top
fceptthis[.]biz
oftongueid[.]online
honeiwillre[.]biz
eaconhop[.]online
ssedonthep[.]biz
fjobiwouldli[.]biz
offeranda[.]biz
File paths of downloaded payloads
/storage/emulated/0/Android/data/com.intensive.sound/files/Download/updateandroid.apk
/storage/emulated/0/Android/data/com.intensive.sound/files/Download/Chrome05.12.11.apk
/storage/emulated/0/Android/data/com.intensive.sound/files/Download/XXX_Player.apk
/storage/emulated/0/Android/data/com.confidential.pottery/files/Download/Google_Update.apk
/storage/emulated/0/Android/data/com.confidential.pottery/files/Download/System.apk
/storage/emulated/0/Android/data/com.confidential.pottery/files/Download/Android-Update.5.1.apk
/storage/emulated/0/Android/data/com.cold.toothbrush/files/Download/Android_Update.apk
/storage/emulated/0/Android/data/com.cold.toothbrush/files/Download/chromeUpdate.apk
/storage/emulated/0/Android/data/com.cold.toothbrush/files/Download/FreeDownloadVideo.apk
/storage/emulated/0/Android/data/com.anaconda.brave/files/Download/MediaPlayer.apk
/storage/emulated/0/Android/data/com.anaconda.brave/files/Download/GoogleChrome.apk
/storage/emulated/0/Android/data/com.dusty.bird/files/Download/Player.apk
MITRE ATT&CK techniques
This table was built using version 9 of the ATT&CK framework.
| Tactic | ID | Name | Description |
|---|---|---|---|
| Initial Access | T1476 | Deliver Malicious App via Other Means | Android/FakeAdBlocker can be downloaded from third-party websites. |
| T1444 | Masquerade as Legitimate Application | Android/FakeAdBlocker impersonates legitimate AdBlock app. | |
| Persistence | T1402 | Broadcast Receivers | Android/FakeAdBlocker listens for the BOOT_COMPLETED broadcast, ensuring that the app’s functionality will be activated every time the device starts. |
| T1541 | Foreground Persistence | Android/FakeAdBlocker displays transparent notifications and pop-up advertisements. | |
| Defense Evasion | T1407 | Download New Code at Runtime | Android/FakeAdBlocker downloads and executes an APK filefiles from a malicious adversary server. |
| T1406 | Obfuscated Files or Information | Android/FakeAdBlocker stores base64-encoded file in assets containing config file with C&C server. | |
| T1508 | Suppress Application Icon | Android/FakeAdBlocker’s icon is hidden from its victim’s view. | |
| Collection | T1435 | Access Calendar Entries | Android/FakeAdBlocker creates scareware events in calendar. |
| Command And Control | T1437 | Standard Application Layer Protocol | Android/FakeAdBlocker communicates with C&C via HTTPS. |
| Impact | T1472 | Generate Fraudulent Advertising Revenue | Android/FakeAdBlocker generates revenue by automatically displaying ads. |
Click NOW to Secure Your iPhone is a page-rerouting and ad-displaying application that security experts classify as a browser hijacker. What is typical for Click NOW to Secure Your iPhone is that it can display hundreds of sponsored ads, pop-ups and banners during a single browsing session and redirect user searches to pre-defined URLs.
The “Click NOW to Secure Your iPhone” Calendar Spam will display pop up ads and messages
Browser hijackers such as Click NOW to Secure Your iPhone can be very frustrating and they can also be rather scary to anyone who has never dealt with one of their representatives before. The unauthorized changes that these programs can impose on popular web browsers like Safari, Chrome or Firefox typically make most web users believe that a virus or some malware has infected their computer. The unwanted changes most commonly include a redesigned homepage or a different search engine, but there may be also some changes in the web browser’s toolbar section where some new redirect buttons and add-ons may appear. Many people are specifically annoyed by the auto-redirects that they start to experience the moment the browser hijacker gets installed in the system. They also report that any website they visit through the hijacked browser gets stuffed with ads of all shapes and sizes: pop-ups, banners, text links, box notifications and more.
Without a doubt, such activity can be distracting and, honestly, quite annoying. Luckily, you don’t have to deal with it every day because in the removal guide below we will show you how to remove the nagging ads and how to safely reverse all the changes that have been imposed on your web browser.
Additional Information
Is Click NOW to Secure Your iPhone a threat to your system’s security?
Due to the aforementioned web-browsing disturbance they create, it is often unclear what the purpose of programs like Click NOW to Secure Your iPhone is and why they mess with the settings of your browser. Many people simply assume that the browser hijacker is some sort of annoying redirect virus. But the truth is that hijackers are quite different than malicious programs like Trojans, Ransomware, Worms and other web viruses since, unlike them, they don’t seek to harm your machine in any way.
Instead, most programs of the browser hijacking type, including Click NOW to Secure Your iPhone, are interested in promoting certain paid ads and web links and generating pay-per-click revenue for their developers. This explains why they place changes in the web browser’s settings and start spamming the screen with ads and redirecting the user searches to some pre-defined URLs. In this way, the hijackers basically ensure that no matter what you do, you will always land on some ad or link that is sponsored and generates income for the developers.
In the long run, however, these ad-driven activities can transform into an unbearable web browsing disturbance. Besides, when being spammed with so many random messages on your screen, there is always a risk of clicking on something misleading which could land you dangerous viruses such as Ransomware, Trojans, Rootkits and more. That’s why it is safer not to click on anything that the browser hijacker displays and simply use the instructions in the removal guide below to uninstall the unwanted software. If you have never dealt with such an application before, a much faster and risk-free way to remove Click NOW to Secure Your iPhone is to use a professional removal tool and we highly recommend this method if you are afraid that you will mess things up.
SUMMARY:
| Name | Click NOW to Secure Your iPhone |
| Type | Browser Hijacker |
Remove Click NOW to Secure Your iPhone Calendar Spam
You are dealing with a browser hijacker that can restore itself. We are sending you to another page with a removal guide that gets regularly updated. It covers in-depth instructions on how to:
- Locate and clean up your phone’s calendar events if they are infected.
- Find browser extensions related to the threat and how to remove them.
- Ensure your passwords were not stolen or tampered with.
You can find the removal guide here.
About the author
Lidia is a web content creator with years of experience in the cyber-security sector. She helps readers with articles on malware removal and online security. Her strive for simplicity and well-researched information provides users with easy-to-follow It-related tips and step-by-step tutorials.
click-now-on-this.online всплывающих рекламных объявлений будут перенаправлены на потенциально нежелательных рекламных программ, установленных на вашем ПК. Adware программы запускает новый всплывающее в Internet Explorer, Google Chrome, Firefox и перенаправляет браузер на click-now-on-this.online объявление.
В click-now-on-this.online всплывающее окно может появиться внезапно или отображается, когда пользователь посещает определенный сайт или запускает определенное ключевое слово в тексте страницы. click-now-on-this.online всплывающее перенаправление(ы) возникают, когда например, рекламное объявлени поддержанная приложение устанавливается на ПК. Рекламное обманчиво программное обеспечение, предназначенное для отображения навязчивой рекламы на зараженном компьютере. Каком-то сайте, что предоставляют такие услуги, как бесплатные игры, бесплатные программы, панели инструментов и так далее, скорее всего, чтобы связать их бесплатными программами с рекламных доходов.
Скачать утилитучтобы удалить click-now-on-this.online
Используйте средство удаления вредоносных программ Spyhunter только для целей обнаружения. Узнайте больше о SpyHunter Spyware Detection Tool и шаги для удаления SpyHunter.
Стоп-браузер перенаправляет на click-now-on-this.online путем удаления Adware, ответственных за перенаправление в браузере. Рекламного использует обманчивое метод для установки на ПК, эта техника называется комплектации. Менеджеры загрузок, которые используют “эники-беники” известны как “оплата за установку” (ППИ) или “монетизации” установочными комплектами. Платить за установить менеджеры Закачек-это инструмент для развертывания рекламы для издателей рекламного платят за каждую новую установку рекламного.
Пользовательский интерфейс установка диспетчере загрузки не сразу раскрытие рекламного ПО настоящее время; она скрыта в человеческой психологии это названо темными узорами. Темный Рисунок-это техника, используемая для создания графического интерфейса пользователя с замечательным большим или кнопку «установить», и очень маленькая кнопка снижаться. Это заблуждение, эти менеджеры Закачек не хочу, чтобы вы обратили внимание на дополнительные сайты, которые тайно устанавливаются с начальным программного обеспечения, которые вы хотите скачать. Это самый распространенный способ для удаления, чтобы заразить компьютер и запустить браузер перенаправляет на click-now-on-this.online объявление.
Скачать утилитучтобы удалить click-now-on-this.online
Используйте средство удаления вредоносных программ Spyhunter только для целей обнаружения. Узнайте больше о SpyHunter Spyware Detection Tool и шаги для удаления SpyHunter.
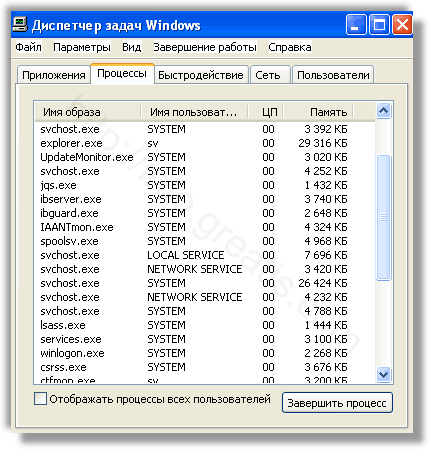
Шаг 1: Остановите все click-now-on-this.online процессы в диспетчере задач
- Нажмите и удерживайте Ctrl + Alt + Del, чтобы открыть диспетчер задач
- Перейдите на вкладку Подробности и конец всех связанных с ними процессов click-now-on-this.online (выберите процесс и нажмите кнопку завершить задачу)
Шаг 2: Удалите click-now-on-this.online сопутствующие программы
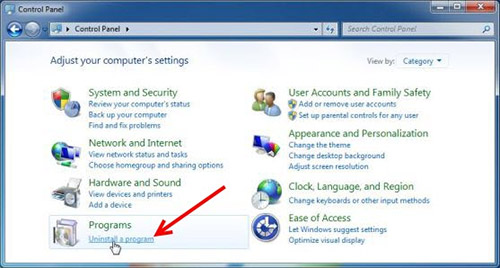
- Нажмите кнопку Пуск и откройте панель управления
- Выберите удалить программу в разделе программы
- Подозрительного программного обеспечения и нажмите кнопку Удалить/изменить
Шаг 3: Удалите вредоносные click-now-on-this.online записи в системе реестра
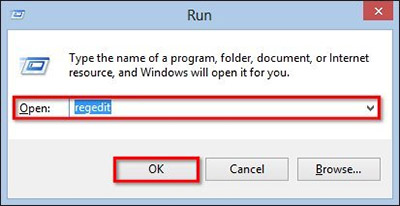
- Нажмите Win + R чтобы открыть выполнить, введите «regedit» и нажмите кнопку ОК
- Если контроль учетных записей пользователей, нажмите кнопку ОК
- Однажды в редакторе реестра, удалите все связанные записи click-now-on-this.online
Шаг 4: Устранить вредоносные файлы и папки, связанные с click-now-on-this.online
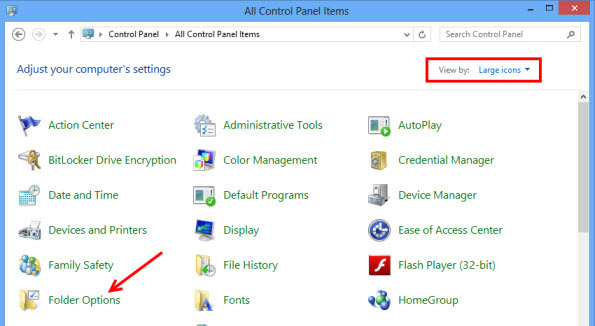
- Нажмите кнопку Пуск и откройте панель управления
- Нажмите Просмотр, выберите крупные значки и откройте свойства папки
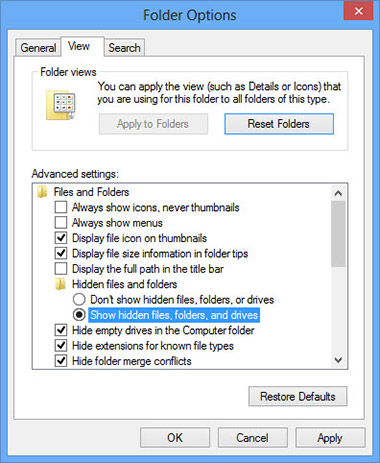
- Перейдите на вкладку Вид, проверить показывать скрытые файлы, папки или драйверы и нажмите кнопку ОК
- Удалить все click-now-on-this.online связанные файлы и папки
%AllUsersProfile%random.exe
%Temp%random.exe
%AllUsersProfile%Application Datarandom
Шаг 5: Удаление click-now-on-this.online из вашего браузера
Скачать утилитучтобы удалить click-now-on-this.online
Используйте средство удаления вредоносных программ Spyhunter только для целей обнаружения. Узнайте больше о SpyHunter Spyware Detection Tool и шаги для удаления SpyHunter.
Internet Explorer
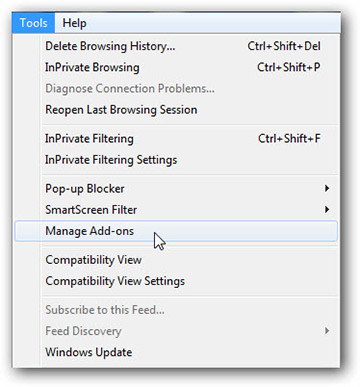
- Запуск Internet Explorer, нажмите на значок шестерни → Управление надстройками
- Выбрать раздел панели инструментов и расширения и отключите подозрительные расширения
Скачать утилитучтобы удалить click-now-on-this.online
Используйте средство удаления вредоносных программ Spyhunter только для целей обнаружения. Узнайте больше о SpyHunter Spyware Detection Tool и шаги для удаления SpyHunter.
Mozilla Firefox
- Откройте Mozilla, нажмите сочетание клавиш Ctrl + Shift + A и перейти к расширения
- Выберите и удалите все ненужные расширения
Скачать утилитучтобы удалить click-now-on-this.online
Используйте средство удаления вредоносных программ Spyhunter только для целей обнаружения. Узнайте больше о SpyHunter Spyware Detection Tool и шаги для удаления SpyHunter.
Google Chrome
- Откройте браузер, нажмите меню и выберите инструменты → расширения
- Выберите подозрительные надстройки и нажмите на значок корзины для его удаления
* SpyHunter сканера, опубликованные на этом сайте, предназначен для использования только в качестве средства обнаружения. более подробная информация о SpyHunter. Чтобы использовать функцию удаления, вам нужно будет приобрести полную версию SpyHunter. Если вы хотите удалить SpyHunter, нажмите здесь.
- What is PriceLess
- Download PriceLess WiperSoft Antispyware Malware Remediation Tool
- Remove PriceLess manually
- Remove PriceLess from Google Chrome
- Remove PriceLess from Mozilla Firefox
- Remove PriceLess from Internet Explorer
- Uninstall PriceLess from Windows 10
- Uninstall PriceLess from Windows 8/8.1
- Uninstall PriceLess from Windows 7
- Get Professional Support
- Read Comments
Threat’s profile 
Name of the threat:PriceLess
Command or file name:zI5Lu.exe
Threat type:Adware
Affected OS:Win32/Win64 (Windows XP, Vista/7, 8/8.1, Windows 10)
Affected browsers:Google Chrome, Mozilla Firefox, Internet Explorer, Safari
PriceLess — is a delusive browser extension, which is classified as PUP (Potentially Unwanted Program). It may be built in many internet browsers, for example Google Chrome, Internet Explorer, Mozilla Firefox. PriceLess shows a lot of commercials, like banners, pop-ups, targeted videos, coupons and deals. Those advertisements redirect user to potentially dangerous websites, where PC can be additionally infected. So we recommend you to remove PriceLess from computer.
PriceLess intrusion method
PriceLess installs on your PC along with free software. This method is called «bundled installation». Freeware offers you to install additional module (PriceLess). Then if you fail to decline the offer it starts hidden installation. PriceLess copies its file(s) to your hard disk. Its typical file name is zI5Lu.exe. Then it creates new startup key with name PriceLess and value zI5Lu.exe. You can also find it in your processes list with name zI5Lu.exe or PriceLess. Also, it can create folder with name PriceLess under C:Program Files or C:ProgramData. If you have further questions about PriceLess, please ask below. You can use programs to remove PriceLess from your browsers below.
Let our support team solve your problem with PriceLess and remove PriceLess right now!
Submit support ticket below and describe your problem with PriceLess. Support team will offer you solution in several minutes and give a step-by-step instruction on how to remove PriceLess. Trouble-free tech support with over 10 years experience removing malware.
Submit support ticket
Threat’s description and solution are developed by Security Stronghold security team.
Here you can also learn:
- Technical details of PriceLess threat.
- Manual PriceLess removal.
- Download PriceLess Removal Tool.
How to remove PriceLess manually
This problem can be solved manually by deleting all registry keys and files connected with PriceLess, removing it from startup list and unregistering all corresponding DLLs. Additionally missing DLL’s should be restored from distribution in case they are corrupted by PriceLess.
To get rid of PriceLess, you should:
- zI5Lu.exe
- CKJ.exe
- oh9H1tAs.exe
Warning: you should delete only those files which checksums are listed as malicious. There may be valid files with the same names in your system. We recommend you to use WiperSoft Antispyware Malware Remediation Tool for safe problem solution.
**Trial version of Wipersoft provides detection of computer viruses for FREE. To remove malware, you have to purchase the full version of Wipersoft.
- C:Documents and SettingsuserApplication datapriceless
no information
Warning: if value is listed for some registry entries, you should only clear these values and leave keys with such values untouched. We recommend you to use WiperSoft Antispyware Malware Remediation Tool for safe problem solution.
Uninstall PriceLess related programs from Control Panel
We recommend you to check list of installed programs and search for PriceLess entry or other unknown and suspicious programs. Below are instructions for different version if Windows. In some cases adware programs are protected by malicious service or process and it will not allow you to uninstall it. If PriceLess won’t uninstall or gives you error message that you do not have sufficient rights to do this perform below instructions in Safe Mode or Safe Mode with Networking or use WiperSoft Antispyware Malware Remediation Tool.
Windows 10
- Click on the Start menu and choose Settings
- Then click on System and choose Apps & Features in the left column
- Find PriceLess under in the list and click Uninstall button near it.
- Confirm by clicking Uninstall button in opened window if necessary.
Windows 8/8.1
- Right click on the bottom left corner of the screen (while on your desktop)
- In the menu choose Control Panel
- Click Uninstall a program under Programs and Features.
- Locate programs that can be connected with PriceLess or other related suspicious program.
- Click Uninstall button.
- Wait until uninstall process is complete.
Windows 7/Vista
- Click Start and choose Control Panel.
- Choose Programs and Features and Uninstall a program.
- In the list of installed programs find entries related to PriceLess
- Click Uninstall button.
Windows XP
- Click Start
- In the menu choose Control Panel
- Choose Add / Remove Programs.
- Find PriceLess related entries.
- Click Remove button.
Remove PriceLess related extensions from your browsers
PriceLess in some cases can be accompanied with browsers extension. We recommend you to use free option Toolbar Remover under Tools in Spyhunter Remediation Tool to remove unwanted browser extensions related to PriceLess. We recommend you to perform scan your PC with Removal Tool or Spyhunter Remediation Tool. To remove extenions from your browsers manually do the following:
- While in Internet Explorer click cogwheel icon in the top right corner
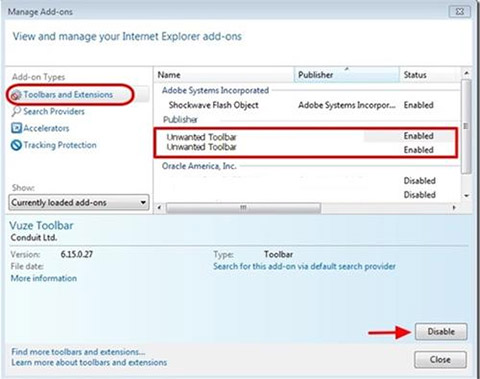
- In the menu choose the Manage Add-ons
- Select Toolbar and Extension tab.
- Choose add-on possibly related to PriceLess or other related adware BHO.
- Click Disable button.
Warning: This option will only disable unwanted plugin. For effective PriceLess removal use WiperSoft Antispyware Malware Remediation Tool.
- Start Google Chrome.
- In the address bar type chrome://extensions/
- In the list of add-ons find related to PriceLess and click recycle bin icon.
- Confirm PriceLess removal.
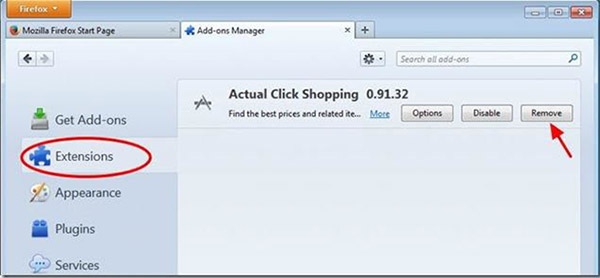
- Open Firefox
- In the address bar type about:addons
- Click Extensions tab.
- In the list of extension locate ones related to PriceLess.
- Click Remove button near it.
Protect computer and browsers from infection
Adware threats like PriceLess are very widespread and, unfortunately, many anti-virus programs fail to detect it. To protect your computer from future infection we recommend you to use WiperSoft Antispyware Malware Remediation Tool, it has active protection module and browser settings guard. It does not conflict with any anti-virus programs and creates additional shield against threats like PriceLess.
Next threat: Rcoupon »
« Back to catalog