How do I troubleshoot 403 errors from CloudFront?
Last updated: 2022-06-09
I’m using Amazon CloudFront to serve content. My users are receiving an HTTP 403 errors with the messages “The request could not be satisfied” or “Access Denied.” How can I troubleshoot this?
Resolution
An alternate CNAME is incorrectly configured
To use an alternate CNAME instead of the default CloudFront URL:
- Add the CNAME in your CloudFront distribution configuration.
- Create a CNAME record in your DNS to point the CNAME to CloudFront distribution URL.
If you create the DNS record but don’t add the CNAME in your CloudFront distribution configuration, then the request returns a 403 error. For instructions on configuring a custom CNAME, see Using custom URLs by adding alternate domain names (CNAMEs).
AWS WAF is configured on CloudFront distribution or at the origin
CloudFront can’t distinguish between an HTTP status code 403 that’s returned by your origin and one that’s returned by AWS WAF when a request is blocked.
To find the source of the 403 status code, check your AWS WAF web access control list (ACL) rule for a blocked request. For more information, see Testing web ACLs.
A custom origin is returning the 403 error
A 403 error might be caused by an AWS WAF or custom firewall configuration made at the origin. To troubleshoot, make the request directly to the origin. If you can replicate the error without CloudFront, then the origin is causing the 403 error.
If the error is caused by the custom origin, then check the origin logs to identify what might be causing the error.
An Amazon S3 origin returning 403 error
The error is caused by a signed URL or signed cookies configuration
Did this article help?
Do you need billing or technical support?
AWS support for Internet Explorer ends on 07/31/2022. Supported browsers are Chrome, Firefox, Edge, and Safari.
Learn more »
Last updated: 2023-01-20
Amazon CloudFront is returning the error message «403 Error — The request could not be satisfied. Request Blocked.»
Short description
The error message «403 Error — The request could not be satisfied. Request Blocked.» is an error from the client. This error can occur due to the default actions of AWS WAF rules associated with the CloudFront distribution. The following settings might cause a Request Blocked error:
- When the default action is set to Allow, the request matches a rule that has Action set to Block.
- When the default action is set to Block, the request matches the conditions of a rule that has Action set to Block.
-or- - When the default action is set to Block, the request doesn’t match the conditions of any rule that has Action set to Allow.
For information on troubleshooting other types of 403 errors, see How do I troubleshoot 403 errors from CloudFront?
Resolution
To resolve the Request Blocked error:
- Open the CloudFront console.
- Choose the ID for the distribution that you want to update.
- Choose the General tab.
- Under Settings, in the AWS WAF web ACL list, choose the web access control list (web ACL) associated with your distribution.
- In the AWS WAF console, choose Web ACLs.
- On the Web ACLs page, for AWS Region, choose Global (CloudFront).
- Choose the web ACLs that require review. Check that the AWS WAF default action is set on the web ACL.
- To resolve the Request Blocked error when the default action is Allow, review the requests. Be sure that they don’t match the conditions for any AWS WAF rules with Action set to Block.
If valid requests match the conditions for a rule that blocks requests, then update the rule to allow the requests. - To resolve the Request Blocked error when the default action is Block, review the requests. Be sure that they match the conditions for any AWS WAF rules with Action set to Allow.
If valid requests don’t match any existing rules that allow requests, then create a rule that allows the requests.
Note: For more troubleshooting, use the
AWS WAF console to review a sample of requests that match the rule that might cause the Request Blocked error. For more information, see
Testing and tuning your AWS WAF protections.
Did this article help?
Do you need billing or technical support?
AWS support for Internet Explorer ends on 07/31/2022. Supported browsers are Chrome, Firefox, Edge, and Safari.
Learn more »
How do I resolve «403 ERROR — The request could not be satisfied. Bad Request» in CloudFront?
Last updated: 2023-01-19
Amazon CloudFront is returning the error message «403 ERROR — The request could not be satisfied. Bad Request.»
Short description
The error message «403 ERROR — The request could not be satisfied. Bad Request.» is from the client. This error can occur due to one of the following reasons:
- The request is initiated over HTTP, but the CloudFront distribution is configured to allow only HTTPS requests. To resolve this issue, follow the steps in the Allow HTTP requests Resolution section.
- The requested alternate domain name (CNAME) isn’t associated with the CloudFront distribution. To resolve this issue, follow the steps in the Associate a CNAME with a distribution Resolution section.
Note: This resolution is for troubleshooting the error when you own the application or website that uses CloudFront to serve content to end users. If you receive this error when trying to view an application or access a website, then contact the provider or website owner for assistance.
For information on troubleshooting other types of 403 errors, see How do I troubleshoot 403 errors from CloudFront?
Resolution
Allow HTTP requests
Follow these steps:
- Open the Amazon CloudFront console.
- Choose the distribution that’s returning the Bad Request error.
- Choose the Behaviors tab.
- Choose the behavior that matches the request. Then, choose Edit.
- For Viewer Protocol Policy, choose either HTTP and HTTPS or Redirect HTTP to HTTPS.
Note: HTTP and HTTPS allows connections on both HTTP and HTTPS. Redirect HTTP to HTTPS automatically redirects HTTP requests to HTTPS. - Choose Save Changes.
Associate a CNAME with a distribution
Follow these steps:
- Open the Amazon CloudFront console.
- Choose the distribution that’s returning the Bad Request error.
- Choose the General tab.
- Under Settings, choose Edit.
- For Alternate Domain Names (CNAMEs), select Add Item.
- Enter the CNAME that you want to associate with the CloudFront distribution.
- Under Custom SSL certificate, choose the certificate that covers the domain. For more information, see How do I configure my CloudFront distribution to use an SSL/TLS certificate?
Note: An SSL certificate is required to associate a CNAME with a distribution. For more information see, Requirements for using alternate domain names. - Choose Save changes.
Did this article help?
Do you need billing or technical support?
AWS support for Internet Explorer ends on 07/31/2022. Supported browsers are Chrome, Firefox, Edge, and Safari.
Learn more »
Если AWS CloudFront выдает сообщение об ошибке 403 Error — запрос не может быть удовлетворен. Запрос заблокирован, тогда не волнуйтесь. Это можно исправить в кратчайшие сроки.
Здесь, в этом блоге, мы обсудим способ исправления этой ошибки сразу после того, как поговорим о том, что вызвало эту проблему в первую очередь. Давайте начнем!
Что вызывает ошибку 403, запрос не может быть удовлетворен, запрос заблокирован?
Причин возникновения проблемы может быть несколько. Здесь мы упомянули популярные из них:
- Разрешение заблокировано. Если у вас нет необходимых разрешений для доступа к содержимому на сервере, вы можете получить эту ошибку в CloudFront.
- Неправильно настроен сертификат SSL/TLS. Если в вашей раздаче CloudFront есть сертификат SSL/TLS, но он настроен неправильно, вы можете столкнуться с этой проблемой.
- Ошибки конфигурации. Если CloudFront настроен на блокировку запросов с IP-адреса, вы можете получить ошибку 403.
- Имя домена не связано — если запрошенное альтернативное имя домена не связано с раздачей CloudFront, вы можете получить эту ошибку.
- Действие и правило не согласованы — если для действия по умолчанию установлено значение «Разрешить», но сделанный запрос соответствует правилу, для которого установлено значение «Блокировать». Если для действия установлено значение «Блокировать», но для правила установлено значение «Разрешить».
Как я могу исправить запрос об ошибках 403, который не может быть удовлетворен?
1. Измените правила AWS WAF, если для действия по умолчанию установлено значение «Разрешить».
- Войдите в Консоль управления AWS. Перейдите в консоль CloudFront.
- Выберите идентификатор распространения, который вы хотите изменить или обновить.
- Перейдите на вкладку Общие.
- В разделе «Настройки» найдите AWS WAF и выберите список управления веб-доступом, относящийся к дистрибутиву.
- На странице AWS WAF & Shield выберите Web ACL на левой панели. Теперь для региона AWS выберите Global (CloudFront) на странице Web ACL.
- Перейдите к веб-спискам контроля доступа, которые необходимо просмотреть, на правой панели.
- Перейдите на вкладку «Правила» и в разделе «Действие веб-списка управления доступом по умолчанию» для запросов, которые не соответствуют ни одному из заголовков правил, убедитесь, что для параметра «Действие» установлено значение «Разрешить».
- Теперь проверьте, что запрос, который возвращается с ошибкой блокировки запроса, соответствует правилу, в котором действие установлено на блокировку.
- Чтобы это исправить, необходимо проверить, не соответствует ли сделанный запрос условиям для правил AWS WAF, для которых для параметра «Действие» установлено значение « Блокировать». Нажмите на запрос, который был заблокирован, и в разделе Если запрос соответствует заявлению, проверьте его.
- Если допустимые запросы соответствуют предварительным требованиям для правила, которое блокирует запросы, измените правило, чтобы разрешить запросы. Для этого нажмите кнопку «Изменить».
- На следующей странице прокрутите, чтобы найти Действие. Поставьте галочку рядом с Разрешить и нажмите Сохранить.
2. Измените правила AWS WAF, если для действия по умолчанию установлено значение «Блокировать».
- Выполните указанные выше действия (1–6), чтобы перейти на вкладку «Правила» в консоли AWS WAF.
- В разделе «Действие веб-списка управления доступом по умолчанию» для запросов, которые не соответствуют ни одному из правил, если для параметра «Действие» установлено значение «Блокировать», проверьте запрос, чтобы убедиться, что он соответствует условиям для всех правил AWS WAF с параметром «Действие», для которого установлено значение «Разрешить».
- Вы можете создать правило, если допустимый запрос не связан с какими-либо текущими правилами, для которых действие установлено на Разрешить. Для этого нажмите «Добавить правила», затем в раскрывающемся списке выберите «Добавить мои собственные правила и группы правил».
- На следующей странице перейдите в раздел Заявление. В поле «Проверить» выберите «Заголовок».
- Заполните данные для имени поля заголовка, типа соответствия и строки для сопоставления.
- Выберите действие, чтобы разрешить. Нажмите Добавить правило, чтобы подтвердить изменения.
Таким образом, вы можете исправить ошибку 403: запрос не может быть удовлетворен в CloudFront. Выполните все шаги и сообщите нам, сработало ли это для вас, в разделе комментариев ниже.
When restricting access to S3 content using a bucket policy that inspects the incoming Referer: header, you need to do a little bit of custom configuration to «outsmart» CloudFront.
It’s important to understand that CloudFront is designed to be a well-behaved cache. By «well-behaved,» I mean that CloudFront is designed to never return a response that differs from what the origin server would have returned. I’m sure you can see that is an important factor.
Let’s say I have a web server (not S3) behind CloudFront, and my web site is designed so that it returns different content based on an inspection of the Referer: header… or any other http request header, like User-Agent: for example. Depending on your browser, I might return different content. How would CloudFront know this, so that it would avoid serving a user the wrong version of a certain page?
The answer is, it wouldn’t be able to tell — it can’t know this. So, CloudFront’s solution is not to forward most request headers to my server at all. What my web server can’t see, it can’t react to, so the content I return cannot vary based on headers I don’t receive, which prevents CloudFront from caching and returning the wrong response, based on those headers. Web caches have an obligation to avoid returning the wrong cached content for a given page.
«But wait,» you object. «My site depends on the value from a certain header in order to determine how to respond.» Right, that makes sense… so we have to tell CloudFront this:
Instead of caching my pages based on just the requested path, I need you to also forward the Referer: or User-Agent: or one of several other headers as sent by the browser, and cache the response for use on other requests that include not only the same path, but also the same values for the extra header(s) that you forward to me.
However, when the origin server is S3, CloudFront doesn’t support forwarding most request headers, on the assumption that since static content is unlikely to vary, these headers would just cause it to cache multiple identical responses unnecessarily.
Your solution is not to tell CloudFront that you’re using S3 as the origin. Instead, configure your distribution to use a «custom» origin, and give it the hostname of the bucket to use as the origin server hostname.
Then, you can configure CloudFront to forward the Referer: header to the origin, and your S3 bucket policy that denies/allows requests based on that header will work as expected.
Well, almost as expected. This will lower your cache hit ratio somewhat, since now the cached pages will be cached based on path + referring page. It an S3 object is referenced by more than one of your site’s pages, CloudFront will cache a copy for each unique request. It sounds like a limitation, but really, it’s only an artifact of proper cache behavior — whatever gets forwarded to the back-end, almost all of it, must be used to determine whether that particular response is usable for servicing future requests.
See http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/distribution-web-values-specify.html#DownloadDistValuesForwardHeaders for configuring CloudFront to whitelist specific headers to send to your origin server.
Important: don’t forward any headers you don’t need, since every variant request reduces your hit rate further. Particularly when using S3 as the back-end for a custom origin, do not forward the Host: header, because that is probably not going to do what you expect. Select the Referer: header here, and test. S3 should begin to see the header and react accordingly.
Note that when you removed your bucket policy for testing, CloudFront would have continued to serve the cached error page unless you flushed your cache by sending an invalidation request, which causes CloudFront to purge all cached pages matching the path pattern you specify, over the course of about 15 minutes. The easiest thing to do when experimenting is to just create a new CloudFront distribution with the new configuration, since there is no charge for the distributions themselves.
When viewing the response headers from CloudFront, note the X-Cache: (hit/miss) and Age: (how long ago this particular page was cached) responses. These are also useful in troubleshooting.
Update: @alexjs has made an important observation: instead of doing this using the bucket policy and forwarding the Referer: header to S3 for analysis — which will hurt your cache ratio to an extent that varies with the spread of resources over referring pages — you can use the new AWS Web Application Firewall service, which allows you to impose filtering rules against incoming requests to CloudFront, to allow or block requests based on string matching in request headers.
For this, you’d need to connect the distribution to S3 as as S3 origin (the normal configuration, contrary to what I proposed, in the solution above, with a «custom» origin) and use the built-in capability of CloudFront to authenticate back-end requests to S3 (so the bucket contents aren’t directly accessible if requested from S3 directly by a malicious actor).
See https://www.alexjs.eu/preventing-hotlinking-using-cloudfront-waf-and-referer-checking/ for more on this option.
I have uploaded a react app to AWS S3 and am using static website hosting. I then linked a cloudfront distribution to the s3 bucket.
I am able to navigate to the site and it functions properly except when I navigate to a new page my-domain/new-page. At first it succeeds but if I try and load the page directly or refresh I get a 403 forbidden error.
asked Sep 29, 2017 at 23:08
Using react with S3 and CloudFront, I had this or a similar issue where loading the initial index page and then linking to other pages worked just fine (push state changes), but if I refreshed the page or linked directly to the page, it came up as «Access Denied,» status 403.
The solution I found was to add custom error pages for 403 and 404 errors to the CloudFront configuration.
S3 responds 403 when an object doesn’t exist as would be the case with pages in client side routing.
answered Mar 16, 2018 at 1:02
KokaubeamKokaubeam
6266 silver badges8 bronze badges
5
I have noticed this happens when you change the object and look for the object immediately. To resolve this issue, we used to cache the object for 5 mins, so CloudFront will serve cached version when available.
This also relates if you are changing the object and applying the ACL along with the object. Ensure you have public read as policy for the bucket, so you can reduce outage time.
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"AddPerm",
"Effect":"Allow",
"Principal": "*",
"Action":["s3:GetObject"],
"Resource":["arn:aws:s3:::examplebucket/*"]
}
]
}
Enabling cache in CloudFront also solves the issue.
Hope it helps.
answered Sep 30, 2017 at 1:04
KannaiyanKannaiyan
12.3k2 gold badges43 silver badges80 bronze badges
I have uploaded a react app to AWS S3 and am using static website hosting. I then linked a cloudfront distribution to the s3 bucket.
I am able to navigate to the site and it functions properly except when I navigate to a new page my-domain/new-page. At first it succeeds but if I try and load the page directly or refresh I get a 403 forbidden error.
asked Sep 29, 2017 at 23:08
Using react with S3 and CloudFront, I had this or a similar issue where loading the initial index page and then linking to other pages worked just fine (push state changes), but if I refreshed the page or linked directly to the page, it came up as «Access Denied,» status 403.
The solution I found was to add custom error pages for 403 and 404 errors to the CloudFront configuration.
S3 responds 403 when an object doesn’t exist as would be the case with pages in client side routing.
answered Mar 16, 2018 at 1:02
KokaubeamKokaubeam
6266 silver badges8 bronze badges
5
I have noticed this happens when you change the object and look for the object immediately. To resolve this issue, we used to cache the object for 5 mins, so CloudFront will serve cached version when available.
This also relates if you are changing the object and applying the ACL along with the object. Ensure you have public read as policy for the bucket, so you can reduce outage time.
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"AddPerm",
"Effect":"Allow",
"Principal": "*",
"Action":["s3:GetObject"],
"Resource":["arn:aws:s3:::examplebucket/*"]
}
]
}
Enabling cache in CloudFront also solves the issue.
Hope it helps.
answered Sep 30, 2017 at 1:04
KannaiyanKannaiyan
12.3k2 gold badges43 silver badges80 bronze badges
Improve Article
Save Article
Improve Article
Save Article
Sometimes users of Amazon Cloudfront get a 403 Access Denied error when using an Amazon S3 website endpoint as an origin in Amazon CloudFront distribution. So, in this article, we will work through resolving this error.
To resolve the Access Denied Error follow the below steps:
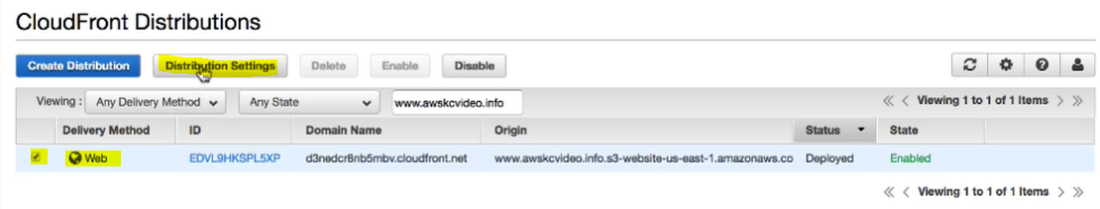
Step 1: After signing in to the AWS management console navigate to Amazon CloudFront.
Step 2: Choose the distribution and then choose distribution settings.
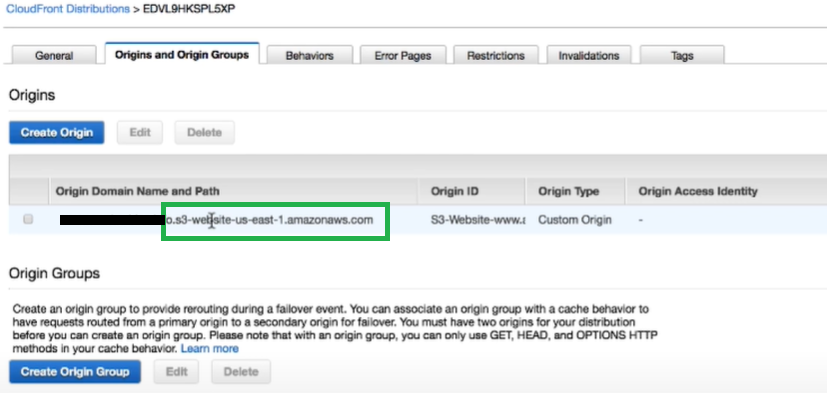
Step 3: Now choose the origin view.
Step 4: Now review the domain name format to confirm the S3 endpoint type, configure it as the origin. If the endpoint isn’t formatted off bucket name “.S3-website-region.amazonaws.com”, then make sure the following requirements are met.
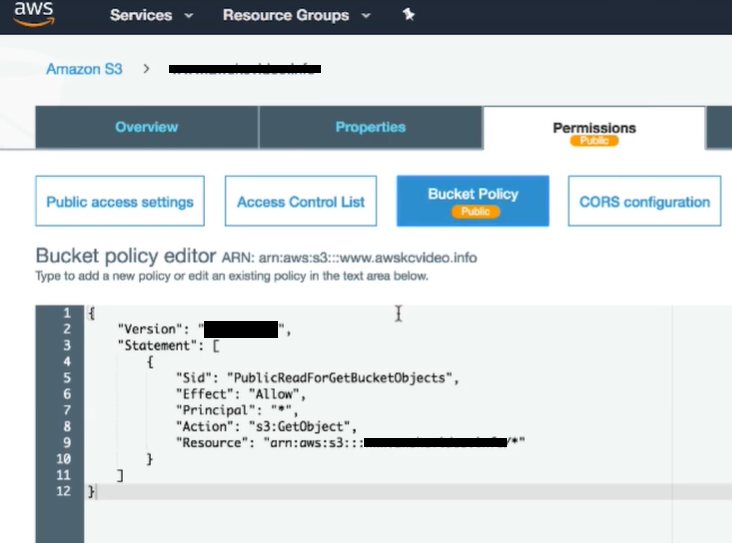
- First, navigate the S3 console to confirm if the objects are publicly accessible to the bucket policy or the ACL. Review the bucket policy to confirm that it does not contain a derived statement, which affects the get object action.
- If the public read is given through a bucket policy, then make sure the bucket owner owns the object.
- Search for the object which resulted in an HTTP 403 error in the console to make sure that it exists. If the requested object does not exist, and the bucket doesn’t allow public S3 list bucket access, then the request receives an HTTP 403 error rather than an HTTP 404 error.
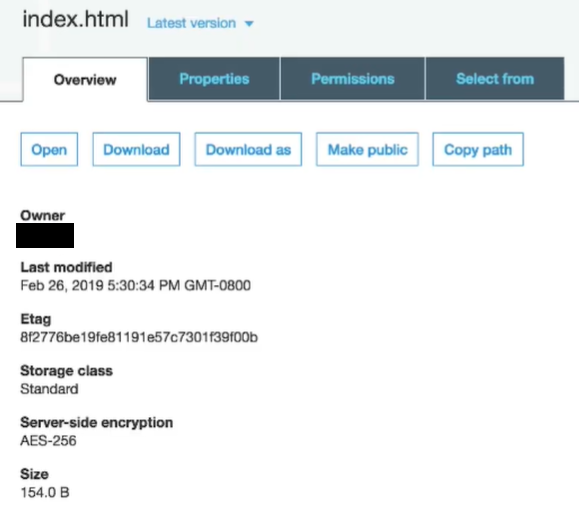
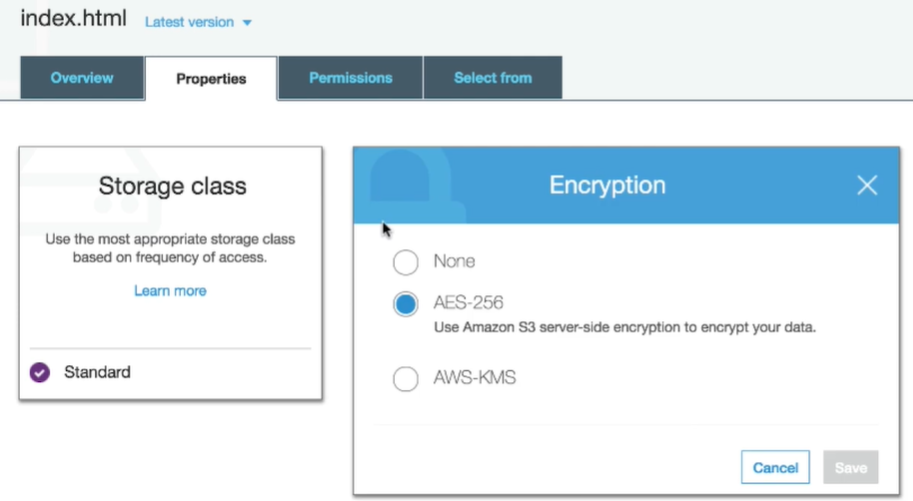
- Open the object in the asterisk console, and confirm that it is not encrypted with AWS-KMS.
Something is causing your files to be requested from CloudFront before they are present in the bucket. The default configuration of CloudFront causes this to be negatively-cached for up to 5 minutes.
By default, when your origin returns an HTTP 4xx or 5xx status code, CloudFront caches these error responses for five minutes and then submits the next request for the object to your origin to see whether the problem that caused the error has been resolved and the requested object is now available.
— http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/custom-error-pages.html
If the browser, or anything else, tries to download the file from that particular CloudFront edge (or any edge, if the request happens to also go through the regional edge — CloudFront now has two edge layers) before the upload into S3 is complete, S3 will return an error, and CloudFront — at that edge location — will cache that error and remember, for the next 5 minutes, not to bother trying again.
This timer is configurable.
You can specify the error-caching duration—the Error Caching Minimum TTL—for each 4xx and 5xx status code that CloudFront caches. For a procedure, see Configuring Error Response Behavior.
— http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/custom-error-pages.html
Set the value to 0 for any error codes, like 403, where you want to disable the error cache.
The content in this answer is adapted from my original post on Stack Overflow.