LDAP: error code 49 — 80090308: LdapErr: DSID-0C0903A9, comment: AcceptSecurityContext error, data 52e, v1db1
I know «52e» code is when username is valid, but password is invalid. I am using the same user name and password in my apache studio, I was able to establish the connection succesfully to LDAP.
Here is my java code
String userName = "*******";
String password = "********";
String base ="DC=PSLTESTDOMAIN,DC=LOCAL";
String dn = "cn=" + userName + "," + base;
Hashtable env = new Hashtable();
env.put(Context.INITIAL_CONTEXT_FACTORY,"com.sun.jndi.ldap.LdapCtxFactory");
env.put(Context.PROVIDER_URL, "ldap://******");
env.put(Context.SECURITY_AUTHENTICATION, "simple");
env.put(Context.SECURITY_PRINCIPAL, dn);
env.put(Context.SECURITY_CREDENTIALS, password);
LDAPAuthenticationService ldap = new LDAPAuthenticationService();
// LdapContext ctx;
DirContext ctx = null;
try {
ctx = new InitialDirContext(env);
My error is on this line: ctx = new InitialDirContext(env);
I do not know what exactly is causing this error.
simbabque
53.5k8 gold badges77 silver badges133 bronze badges
asked Jul 14, 2015 at 15:59
0
For me the issue resolved when I set the principal section like this:
env.put(Context.SECURITY_PRINCIPAL, userId@domainWithoutProtocolAndPortNo);
answered Nov 9, 2016 at 15:45
VishalVishal
1,8332 gold badges19 silver badges22 bronze badges
4
In my case I have to use something like <username>@<domain> to successfully login.
sample_user@sample_domain
smonff
3,3513 gold badges39 silver badges46 bronze badges
answered Sep 24, 2018 at 7:50
Linh NguyenLinh Nguyen
2012 silver badges8 bronze badges
When you use Context.SECURITY_AUTHENTICATION as «simple», you need to supply the userPrincipalName attribute value (user@domain_base).
answered Oct 9, 2018 at 16:19
MAWMAW
8738 silver badges22 bronze badges
I had a similar issue when using AD on CAS , i.e. 52e error, In my case application accepts the Full Name when in the form of CN= instead of the actual username.
For example, if you had a user who’s full name is Ross Butler and their login username is rbutler —you would normally put something like, cn=rbutler,ou=Users,dc=domain,dc=com but ours failed everytime. By changing this to cn=Ross Butler,ou=Users,dc=domain,dc=com it passed!!
answered Jun 23, 2017 at 5:46
CountCount
1,3652 gold badges19 silver badges38 bronze badges
1
For me the issue is resolved by adding domain name in user name as follow:
string userName="yourUserName";
string password="passowrd";
string hostName="LdapServerHostName";
string domain="yourDomain";
System.DirectoryServices.AuthenticationTypes option = System.DirectoryServices.AuthenticationTypes.SecureSocketsLayer;
string userNameWithDomain = string.Format("{0}@{1}",userName , domain);
DirectoryEntry directoryOU = new DirectoryEntry("LDAP://" + hostName, userNameWithDomain, password, option);
answered Nov 23, 2018 at 7:14
if you debug and loook at ctx=null,maybe your username hava proble ,you shoud write like
«acadministrator»(double «») or «administrator@ac»
answered Jul 5, 2019 at 3:34
HaoSiHaoSi
211 bronze badge
0
For me the cause of the issue was that the format of username was incorrect. It was earlierly specified as «mydomainuser». I removed the domain part and the error was gone.
PS I was using ServerBind authentication.
answered Feb 24, 2021 at 14:02
1
LDAP is trying to authenticate with AD when sending a transaction to another server DB. This authentication fails because the user has recently changed her password, although this transaction was generated using the previous credentials. This authentication will keep failing until … unless you change the transaction status to Complete or Cancel in which case LDAP will stop sending these transactions.
answered Apr 13, 2017 at 20:40
For me issue is resolved by changing envs like this:
env.put("LDAP_BASEDN", base)
env.put(Context.SECURITY_PRINCIPAL,"user@domain")
answered Aug 28, 2019 at 7:52
1
Using domain Name may solve the problem (get domain name using powershell: $env:userdomain):
Hashtable<String, Object> env = new Hashtable<String, Object>();
String principalName = "domainName\userName";
env.put(Context.INITIAL_CONTEXT_FACTORY, "com.sun.jndi.ldap.LdapCtxFactory");
env.put(Context.PROVIDER_URL, "ldap://URL:389/OU=ou-xx,DC=fr,DC=XXXXXX,DC=com");
env.put(Context.SECURITY_AUTHENTICATION, "simple");
env.put(Context.SECURITY_PRINCIPAL, principalName);
env.put(Context.SECURITY_CREDENTIALS, "Your Password");
try {
DirContext authContext = new InitialDirContext(env);
// user is authenticated
System.out.println("USER IS AUTHETICATED");
} catch (AuthenticationException ex) {
// Authentication failed
System.out.println("AUTH FAILED : " + ex);
} catch (NamingException ex) {
ex.printStackTrace();
}
answered Feb 7, 2020 at 11:35
2
I’ve tested three diferent approaches and them all worked:
env.put(Context.SECURITY_PRINCIPAL, "user");
env.put(Context.SECURITY_PRINCIPAL, "user@domain.com");
env.put(Context.SECURITY_PRINCIPAL, "CN=user,OU=one,OU=two,DC=domain,DC=com");
If you use the last one, don’t forget to set all the OU’s where the user belongs to. Otherwise it won’t work.
answered Jan 27, 2022 at 15:57
In my case I misconfigured email credentials then I corrected
var passport = require('passport'),
WindowsStrategy = require('passport-windowsauth'),
User = require('mongoose').model('User');
module.exports = function () {
passport.use(new WindowsStrategy({ldap: {
url: 'ldap://corp.company.com:389/DC=corp,DC=company,DC=com',
base: 'DC=corp,DC=company,DC=com',
bindDN: 'myid@corp.company.com',
bindCredentials:'password',
tlsOptions: {
ca: [fs.readFileSync("./cert.pem")],
},
}, integrated: false},
function(profile, done) {
console.log('Windows');
console.log(profile);
User.findOrCreate({
username: profile.id
}, function(err, user) {
if (err) {
return done(err);
}
if (!user) {
return done(null, false, {
message: 'Unknown user'
});
}
if (!user.authenticate(password)) {
return done(null, false, {
message: 'Invalid password'
});
}
return done(null, user);
});
}));
};
answered May 12, 2022 at 13:50
KARTHIKEYAN.AKARTHIKEYAN.A
16.7k6 gold badges115 silver badges130 bronze badges
Please remove domain from the username «mydomainuser». please put «user» only. do not put domain and backslash .
You do not use ldaps://examplehost:8080(do not use s with ldaps coz cert is required), use ldap://examplehost:8080 then use non-TLS port number. it worked for me.
answered Jul 19, 2022 at 10:13
Last updated on: March 10th, 2021
vScope supports both Discovery of and integration with the Active Directory. If something goes wrong you will be prompted with an error message that can give you a hint of the cause to the issue.
The error messages might look something like this:
INVALID_CREDENTIALS: 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580
INVALID_CREDENTIALS: 80090308: LdapErr: DSID-0C090400, comment: AcceptSecurityContext error, data 775, v1db1
The code is listed after Data (in this case 52e and 775).
Here is a list of common error codes that might show up:
| Error code | Error | Description |
|---|---|---|
| 525 | User not found | Returned when an invalid username is supplied. |
| 52e | Invalid credentials | Returned when a valid username is supplied but an invalid password/credential is supplied. If this error is received, it will prevent most other errors from being displayed. |
| 530 | Not permitted to logon at this time | Returned when a valid username and password/credential are supplied during times when login is restricted. |
| 531 | Not permitted to logon from this workstation | Returned when a valid username and password/credential are supplied, but the user is restriced from using the workstation where the login was attempted. |
| 532 | Password expired | Returned when a valid username is supplied, and the supplied password is valid but expired. |
| 533 | Account disabled | Returned when a valid username and password/credential are supplied but the account has been disabled. |
| 701 | Account expired | Returned when a valid username and password/credential are supplied but the account has expired. |
| 773 | User must reset password | Returned when a valid username and password/credential are supplied, but the user must change their password immediately (before logging in for the first time, or after the password was reset by an administrator). |
| 775 | Account locked out | Returned when a valid username is supplied, but the account is locked out. Note that this error will be returned regardless of whether or not the password is invalid. |
Further reading
You can read more about integrating vScope with Active Directory on this Knowledge Base post.
Hi,
i am running Zimbra Release 8.6.0.GA.1153.UBUNTU14.64 UBUNTU14_64 FOSS edition, Patch 8.6.0_P6.
The user get authenticated against a Windows 2008R2 DC (LDAP Port 3268).
This works most time.
Sometime random user try to login and get immediatly «error in network service»
After waiting some time the login is working again.
in the mailbox.log i see
2016-05-11 08:20:57,051 INFO [qtp509886383-1216983:http://127.0.0.1:80/service/soap/AuthRequest] [name=mgloss@mydomain.hq;oip=10.58.0.91;ua=zclient/8.6.0_GA_1194;] SoapEngine — handler exception: authentication failed for [mgloss@mydomain.hq], external LDAP auth failed, LDAP error: — unable to ldap authenticate: 80090308: LdapErr: DSID-0C0903A9, comment: AcceptSecurityContext error, data 52e, v1db1
2016-05-11 08:20:57,051 INFO [qtp509886383-1216983:http://127.0.0.1:80/service/soap/AuthRequest] [name=mgloss@mydomain.hq;oip=10.58.0.91;ua=zclient/8.6.0_GA_1194;] soap — AuthRequest elapsed=5
2016-05-11 08:21:00,922 INFO [qtp509886383-1216982:http://127.0.0.1:80/service/soap/AuthRequest] [] misc — Access to IP 10.58.50.91suspended, for repeated failed login.
There are NO authentication errors before!
The interesting part is:
Code: Select all
zmprov gacf |grep -i InvalidLoginFilter
zimbraInvalidLoginFilterDelayInMinBetwnReqBeforeReinstating: 15
zimbraInvalidLoginFilterMaxFailedLogin: 10
zimbraInvalidLoginFilterMaxSizeOfFailedIpDb: 7000
zimbraInvalidLoginFilterReinstateIpTaskIntervalInMin: 5
so the question is:
what is the timerange for the 10 invalid logins?
How can it happen, after the first invalid login to hit the CSFE_SVC_ERROR ?
best regards
Thomas
- Remove From My Forums

LDAP authentication error: LDAP: error code 49 — 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 52e, vece
-
Question
-
Dear All,
We are developing a LDAP authentication against Active Directory, we met the follow errors, although the username and password are correct.
LDAP: error code 49 — 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 52e, vece
The user detail is: CN=Peter, Lia ,OU=DEV,OU=HK_U,OU=cita,OU=US,DC=achtest,DC=local
As you may saw, the last name of this user has a backslash, plus a space in CN, we guess it may be the problem, since other users don’t have this problem if the last name of users don’t have a backslash and a space.
However we don’t know how we can add a new user to duplicate this issue, since it’s not way to add a new user with space in the end of name, the Active Directory will auto trim the space when system save the new user to database.
My questions are:
1. Do you have this kind of experience? Any idea to resolve?
2. How we can add a new user with a space in the end of last name? and then we can replicate this issue again?
Thanks in advance!
Bright.
Всем привет.
Код: Выделить всё
# Модуль авторизации клиентов через Ldap #
$Self->{'Customer::AuthModule'} = 'Kernel::System::CustomerAuth::LDAP';
# Имя контроллера домена
$Self->{'Customer::AuthModule::LDAP::Host'} = 'dom1.k12.local';
# Параметры домена
$Self->{'Customer::AuthModule::LDAP::BaseDN'} = 'dc=k12,dc=local';
# Идентификатор пользователя в виде его доменного имени
$Self->{'Customer::AuthModule::LDAP::UID'} = 'sAMAccountName';
$Self->{'Customer::AuthModule::LDAP::GroupDN'} = 'dc=k12,dc=local';
$Self->{'Customer::AuthModule::LDAP::AccessAttr'} = 'sAMAccountName';
$Self->{'AuthModule::LDAP::UserSuffix'} = '@k12.local';
# Расположение учетной записи администратора домена пользователей и пароль
$Self->{'Customer::AuthModule::LDAP::SearchUserDN'} = 'cn=otrs,ou=otrs,ou=k12,dc=k12,dc=local';
$Self->{'Customer::AuthModule::LDAP::SearchUserPw'} = 'qwerty123';
# Параметры подключения по LDAP
$Self->{'Customer::AuthModule::LDAP::Params'} = {
port => 389,
timeout => 120,
async => 0,
version => 3,
};
# Пользовательский бэкенд LDAP #
$Self->{CustomerUser} = {
# Имя бэкенда
Name => 'Active Directory',
Module => 'Kernel::System::CustomerUser::LDAP',
Params => {
# Имя контроллера домена
Host => 'dom1.k12.local',
# Где расположены клиенты
BaseDN => 'dc=k12,dc=local',
SSCOPE => 'sub',
UserDN => 'cn=otrs,ou=otrs,ou=k12,dc=k12,dc=local',
UserPw => 'qwerty123',
# Фильтр
AlwaysFilter => '(&(objectcategory=person)(objectclass=user)(mail=*)(!(description=built-In))(!(userAccountControl:1.2.840.113556.1.4.803:=2)))',
SourceCharset => 'utf-8',
DestCharset => 'utf-8',
},
ReadOnly => 1,
CustomerKey => 'sAMAccountName',
CustomerID => 'mail',
CustomerUserListFields => ['givenname', 'sn', 'mail'],
CustomerUserSearchFields => ['displayName','sAMAccountName','givenName', 'sn', 'mail','description'],
CustomerUserSearchPrefix => '',
CustomerUserSearchSuffix => '*',
CustomerUserPostMasterSearchFields => ['displayName','sAMAccountName','givenName','sn','mail','description'],
CustomerUserNameFields => ['givenname', 'sn'],
CustomerUserExcludePrimaryCustomerID => 0,
CacheTTL => 120,
Map => [
[ 'UserSalutation', 'Title', 'title', 1, 0, 'var' ],
[ 'UserFirstname', 'Firstname', 'givenName', 1, 1, 'var' ],
[ 'UserLastname', 'Lastname', 'sn', 1, 1, 'var' ],
[ 'UserLogin', 'Login', 'sAMAccountName', 1, 1, 'var' ],
[ 'UserEmail', 'Email', 'mail', 1, 1, 'var' ],
[ 'UserCustomerID', 'CustomerID', 'mail', 0, 1, 'var' ],
[ 'UserPhone', 'Phone', 'telephoneNumber', 1, 0, 'var' ],
[ 'UserAddress', 'Address', 'postalAddress', 1, 0, 'var' ],
[ 'UserStreet', 'Street', 'streetAddress', 1, 0, 'var' ],
[ 'UserCity', 'City', 'l', 1, 0, 'var' ],
[ 'UserZip', 'ZIP', 'postalCode', 1, 0, 'var' ],
[ 'UserCountry', 'Country', 'co', 1, 0, 'var' ],
[ 'UserComment', 'Comment', 'wWWHomePage', 1, 0, 'var' ],
],
};Problem
Users are unable to log in. Nothing has changed in JIRA side.
The following appears in the atlassian-jira.log:
2017-10-25 14:13:07,009 ERROR [scheduler_Worker-3] [atlassian.crowd.directory.DbCachingDirectoryPoller] pollChanges Error occurred while refreshing the cache for directory [ 31064065 ].
com.atlassian.crowd.exception.OperationFailedException: Error looking up attributes for highestCommittedUSN
at com.atlassian.crowd.directory.MicrosoftActiveDirectory.fetchHighestCommittedUSN(MicrosoftActiveDirectory.java:847)
...
Caused by: org.springframework.ldap.AuthenticationException: [LDAP: error code 49 - 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580 ]; nested exception is javax.naming.AuthenticationException: [LDAP: error code 49 - 80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580 ]Cause
LDAP Error 49 data 52e means that the credentials of the user configured to bind LDAP directory with JIRA are incorrect, as described here: https://confluence.atlassian.com/kb/common-user-management-errors-820119309.html#CommonUserManagementErrors-ActiveDirectoryError49
This can happen when that user is either removed or has its password changed from LDAP side.
Resolution 1
Follow the steps outlined at Restore Passwords To Recover Admin User Rights. By doing so, you’ll be able to access the User Directory settings and change the «Username» field with a valid admin user or change the «Password» field with the new password, allowing JIRA to connect to LDAP.
As an alternative to Recovery Mode, you could utilize auth_fallback by following the guide: Bypass SAML authentication for Jira Data Center
Resolution 2
Alternatively, you can run the following query against your database to find out which one is the admin account that JIRA uses to connect to the LDAP:
SELECT * FROM cwd_directory_attribute WHERE attribute_name = 'ldap.userdn'; Note: The query may return multiple results in case you have more than one User Directory in your JIRA instance.
Re-adding the user back to the LDAP with the same password should resolve the issue.
Resolution 3
As JIRA storing LDAP Login credential in the database without encryption, you may also update those LDAP credential in your database:
lDAP Password Field
Select * from cwd_directory_attribute where attribute_name = 'ldap.password'LDAP User Name Field
SELECT * FROM cwd_directory_attribute WHERE attribute_name = 'ldap.userdn'; attribute_value is the fields which storing those data.
Always perform a backup before you perform edit/update query in the database. It is also highly recommended for you to perform this in a test instance before proceeding with production instance.
Issue
- Why below error is reported while trying to list the domain users after keystone integration with AD ?
[root@myvm ~(keystone_admin)]# openstack user list --domain TEST
ERROR: openstack An unexpected error prevented the server from fulfilling your request: {'info': '80090308: LdapErr: DSID-0C0903A9, comment: AcceptSecurityContext error, data 52e, v1db1', 'desc': 'Invalid credentials'} (Disable debug mode to suppress these details.) (HTTP 500) (Request-ID: req-ca7182e7-7f56-4542-9eb5-a68645e90353)
- Why I am not able to list the domain user in openstack setup ?
Environment
- Red Hat Enterprise Linux OpenStack Platform 7.
Subscriber exclusive content
A Red Hat subscription provides unlimited access to our knowledgebase, tools, and much more.
Current Customers and Partners
Log in for full access
Log In
Hello Gurus 
HDP 2.3.2
Ambari 2.1.2.1
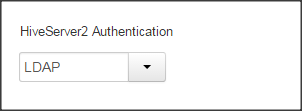
I’m trying to setup HiveServer2 with LDAP authentication.
It seems pretty straightforward:
I performed the following:
Changed HiveServer2 Authentication to LDAP
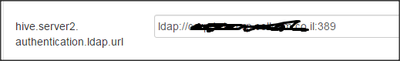
Then i setup my LDAP server url (as the Ambari requested):
Restarted the Hive but hiveserver2.log shows the following during it’s startup:
ERROR [HiveServer2-Handler-Pool: Thread-56]: transport.TSaslTransport (TSaslTransport.java:open(315)) — SASL negotiation failure
javax.security.sasl.SaslException: Error validating the login [Caused by javax.security.sasl.AuthenticationException: Error validating LDAP user [Caused by javax.naming.AuthenticationException: [LDAP: error code 49 — 80090308: LdapErr: DSID-0C0903A9, comment: AcceptSecurityContext error, data 52e, v1db1]]]
According to the error LDAP 49 — 52e the problem is with the credentials that were passed to the LDAP server.
I don’t find any field parameter in which i set the LDAP user & password for authentication…
Needless to say that the authentication acts as if it is set to NONE (which is a major problem….)
Any ideas ?
Thanks in advance
Adi J.