Environment
- Red Hat Enterprise Linux 6.4
- ca-certificates-2010.63-3.el6_1.5.noarch
- curl-7.19.7-35.el6.x86_64
Issue
-
Getting an error «curl: (60) Peer certificate cannot be authenticated with known CA certificates» when trying to curl a site that has a VALID SSL certificate
[root@example.com ~]# curl -v https://example.com * About to connect() to example.com port 443 (#0) * Trying 192.168.0.254... connected * Connected to example.com (192.168.0.254) port 443 (#0) * Initializing NSS with certpath: sql:/etc/pki/nssdb * CAfile: /etc/pki/tls/certs/ca-bundle.crt CApath: none * Certificate is signed by an untrusted issuer: 'CN=Go Daddy Secure Certificate Authority - G2,OU=http://www.example.com/repository/,O="example.com, Inc.",L=Scottsdale,ST=Arizona,C=US' * NSS error -8172 * Closing connection #0 * Peer certificate cannot be authenticated with known CA certificates curl: (60) Peer certificate cannot be authenticated with known CA certificates More details here: http://www.example.com/docs/sslcerts.html curl performs SSL certificate verification by default, using a "bundle" of Certificate Authority (CA) public keys (CA certs). If the default bundle file isn't adequate, you can specify an alternate file using the --cacert option. If this HTTPS server uses a certificate signed by a CA represented in the bundle, the certificate verification probably failed due to a problem with the certificate (it might be expired, or the name might not match the domain name in the URL). If you'd like to turn off curl's verification of the certificate, use the -k (or --insecure) option. -
It works after manually updating the certificate.
[root@example.com certs]# curl http://www.example.com/ca/cacert.pem -o /etc/pki/tls/certs/ca-bundle.crt % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 223k 100 223k 0 0 222k 0 0:00:01 0:00:01 --:--:-- 265k [root@example.com certs]# curl -v https://example.com * About to connect() to example.com port 443 (#0) * Trying 192.168.0.254... connected * Connected to example.com (192.168.0.254) port 443 (#0) * Initializing NSS with certpath: sql:/etc/pki/nssdb * CAfile: /etc/pki/tls/certs/ca-bundle.crt CApath: none * SSL connection using SSL_RSA_WITH_RC4_128_SHA * Server certificate: * subject: CN=www.example.com,OU=Domain Control Validated * start date: Sep 06 18:00:03 2013 GMT * expire date: Sep 06 18:00:03 2014 GMT * common name: www.example.com * issuer: CN=Secure Certificate Authority - G2,OU=http://www.example.com/repository/,O="example.com, Inc.",L=Scottsdale,ST=Arizona,C=US > GET / HTTP/1.1 > User-Agent: curl/7.19.7 (x86_64-redhat-linux-gnu) libcurl/7.19.7 NSS/3.14.0.0 zlib/1.2.3 libidn/1.18 libssh2/1.4.2 > Host: example.com > Accept: */* > < HTTP/1.1 200 OK < Date: Mon, 16 Sep 2013 19:49:10 GMT < Server: Apache < X-Powered-By: PHP/5.3.3 < Content-Length: 0 < Connection: close < Content-Type: text/html; charset=UTF-8 < * Closing connection #0
Resolution
- Update the
ca-certificatespackage to the version provided in RHEA-2013:1596 (ca-certificates-2013.1.94-65.0.el6) or a newer version
Root Cause
- This was addressed in bugzilla: Rebase RHEL 6 to ca-certificates from NSS 3.15
-
Product(s)
- Red Hat Enterprise Linux
-
Component
- ca-certificates
-
Category
- Troubleshoot
-
Tags
- certificates
- rhel
- rhel_6
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.
I am getting the below error while making ssl connection with self signed certificate.
«Peer certificate cannot be authenticated with known CA certificates»
It is working fine with CA signed certificate.
I am setting the below using curl_easy_setopt().
curl_easy_setopt(MyContext, CURLOPT_CAPATH, CA_CERTIFICATE_PATH)
curl_easy_setopt(MyContext, CURLOPT_SSL_VERIFYPEER,TRUE);
The curl version:
libcurl-7.19.7-26
Openssl version is:
0_9_8u
Please let me know how to solve this issue.
neuron
1,8271 gold badge13 silver badges28 bronze badges
asked Feb 4, 2013 at 8:25
By default CURL will generally verify the SSL certificate to see if its valid and issued by an accepted CA. To do this, curl uses a bundled set of CA certificates.
If you’d like to turn off curl’s verification of the certificate, use the -k (or —insecure) option. Here’s an example:
curl --noproxy -k * -D - https://127.0.0.1:443/some-secure-endpoint
answered May 10, 2013 at 15:37
Mark BonanoMark Bonano
6,1622 gold badges15 silver badges12 bronze badges
Security issue: This answer disables a security feature. Do not use this in production!
For php it is possible to switch off curl’s verification of the certificate (see warning below) e.g. for curl_exec
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, FALSE);
http://php.net/manual/en/function.curl-setopt.php
(evaluate the security risk yourself, in my case it was on a partner company’s server and the file required contained no secure information — just happened to be on a secure server)
PiTheNumber
22.4k17 gold badges105 silver badges176 bronze badges
answered Jan 27, 2016 at 13:56
zzapperzzapper
4,6635 gold badges47 silver badges45 bronze badges
1
We fixed a similar issue on CentOS 6 by updating curl to the latest version available in the standard repositories and installing the newest ca-certificates bundle:
yum update curl
yum install ca-certificates
answered Oct 26, 2016 at 15:11
ArthArth
12.6k5 gold badges37 silver badges69 bronze badges
2
libcurl performs peer SSL certificate verification by default. This is done
by using CA cert bundle that the SSL library can use to make sure the peer’s
server certificate is valid.
If you communicate with HTTPS or FTPS servers using certificates that are
signed by CAs present in the bundle, you can be sure that the remote server
really is the one it claims to be.
Until 7.18.0, curl bundled a severely outdated ca bundle file that was
installed by default. These days, the curl archives include no ca certs at
all. You need to get them elsewhere. See below for example.
For more to know about Peer SSL Certificate Verification visit http://curl.haxx.se/docs/sslcerts.html
answered Feb 22, 2013 at 10:02
Though this error happened in the case of using git clone rather than with using curl, I’ve recently stumbled across an identical error message:
Peer certificate cannot be authenticated with known CA certificates
Similar to Arth’s findings, something that worked for CentOS 6 (in order to successfully use HTTPS URLs with git clone for related GitLab repositories) involved updating the trusted certificates on the server (i.e., the server that is using HTTPS), using the following steps:
sudo yum install ca-certificatessudo update-ca-trust enablesudo cp /path/to/your_new_cert.crt /etc/pki/ca-trust/source/anchors/sudo update-ca-trust extract
Perhaps the same certificate steps can be applied for the case of curl (or other similar scenarios) for users on CentOS in the future.
answered Dec 20, 2016 at 17:34
summeasummea
7,2904 gold badges31 silver badges48 bronze badges
Security issue: This answer disables a security feature. Do not use this in production!
In ‘C’
curl_easy_setopt(curl_handle, CURLOPT_SSL_VERIFYPEER, 0);
worked for me
PiTheNumber
22.4k17 gold badges105 silver badges176 bronze badges
answered Jan 12, 2018 at 12:44
As we checked and observed/ Found in Centos 8 .
Due to Proxy issue your packages not allowing you to get accessible to update or download any packages.
try to add sslverify=0 in file /etc/dnf/dnf.conf
Its worked for me.
Also make sure you must have proper internet acess on your server.
cigien
56.7k11 gold badges69 silver badges107 bronze badges
answered May 2, 2022 at 11:38
‘cURL error 60 SSL certificate problem’ occurs when we make a cURL call to third party services.
Here at Bobcares, we have seen several such cURL command related errors as part of our Server Management Services for web hosts and online service providers.
Today we’ll take a look at the causes for this error and see the fix.
What causes ‘cURL error 60 SSL certificate problem’ error to occur
Digital certificates are mainly used in transferring sensitive content. These digital certificates are issued by certificate authorities or CA.
When a cURL receives a server CA that is not signed by one of the trusted certificates in the installed CA certificate store, then it will lead to an error: “failed to verify the legitimacy of the server” during the SSL handshake. As a result, SSL will then refuse the communication with the server leading to an SSL error.
In short, this error occurs because cURL makes sure to verify and make a secure connection request using a self-signed certificate. But when it doesn’t find any valid certificate then it throws this error message.
How we fix the error ‘cURL error 60 SSL certificate problem’
Now let’s see how our Support Engineers resolve this error message.
1. Re-download the cURL CA-Bundle from the cURL site to fix this error. Here are the steps for it.
- First, download the “cacert.pem” from the link: http://curl.haxx.se/docs/caextract.html
- Next copy the complete page and save it as “cacert.pem”
- Now, open the php.ini file and add the following line in it.
curl.cainfo = “[pathtofile]cacert.pem”
In, case, if the php.ini file doesn’t have the curl.cainfo line, then just add it to the end of the file. Then add the file path where cacert.pem file is saved. - Finally, restart the web server or on Windows, restart the application pool and try the request again.
2. If the insecure certificate is a self-signed, known-trusted certificate, then load the certificate to your local trusted certificate location for your OS.
[Need any further assistance in fixing curl errors? – We are here to help you.]
Conclusion
In short, this error occurs when cURL doesn’t find any valid certificate to communicate over https. Today, we saw how our Support Engineers fix this error.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
Published: Aug 24, 2019
— Updated: Mar 16, 2022
In this guide, we are going to solve the “cURL error 60: Peer’s Certificate issuer is not recognized” issue. We may face this at the time to downloading file using wget or curl method. We may also face at the moment to generating or updating Let’s Encrypt SSL certificate.
The error looks like:
curl: (60) Peer's Certificate issuer is not recognized.
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.The Solution
Let’s install the ca-certificates package by using this command:
yum install ca-certificatesWe have to enable dynamic CA configuration feature. Let’s do this by this command:
update-ca-trust force-enableRestart your webserver to check if the error was solved or not.
// Apache
sudo systemctl restart httpd
// Nginx
sudo systemctl restart nginxIf the error not solved yet, then follow these steps:
- Add your cert.pem file to
/etc/pki/ca-trust/source/anchors/. - If you don’t have cert.pem file, you can convert cert.crt to cert.pem using OpenSSL:
openssl x509 -in cert.crt -inform der -outform pem -out cert.pem. - Last update ca-trust using this command:
update-ca-trust extract.
Now restart your webserver and check.
Note: You can also upload cert.pem file to any location and can set a Symbolic link like this:
sudo ln -s /etc/ssl/your-cert.pem /etc/pki/ca-trust/source/anchors/your-cert.pemYou don’t want to fix this permanently, you may follow these two methods:
Method 1: Skip Certificate Check
You can simply add --no-check-certificate in your command. Here’s an example:
wget --no-check-certificate https://wordpress.org/latest.zipMethod 2: Temporary Turned off SSL
To install any package, you can temporary turned off SSL check. Open yum configuration file:
sudo vi /etc/yum.confJust add this line:
sslverify=falseThe article is over. Thanks for reading. ?
Most Related:
- SSL: CERTIFICATE_VERIFY_FAILED with Let’s Encrypt
- PHP cURL Error Code 60 : SSL Certificate Problem
This document (7002146) is provided subject to the disclaimer at the end of this document.
Environment
SUSE Linux Enterprise Server 10
SUSE Linux Enterprise Desktop 10
Situation
While trying to register a client against a SMT server, the following error is experienced:
linux-client:~ # suse_register -a email=$EMAIL -a regcode-sles=$REGCODE Execute curl command failed with '60': curl: (60) SSL certificate problem, verify that the CA cert is OK. Details: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed More details here: cURL - Details on Server SSL Certificates curl performs SSL certificate verification by default, using a "bundle" of Certificate Authority (CA) public keys (CA certs). The default bundle is named curl-ca-bundle.crt; you can specify an alternate file using the --cacert option. If this HTTPS server uses a certificate signed by a CA represented in the bundle, the certificate verification probably failed due to a problem with the certificate (it might be expired, or the name might not match the domain name in the URL). If you'd like to turn off curl's verification of the certificate, use the -k (or --insecure) option.
Resolution
This issue may be encountered if:
- Time and date of server and client differ
- The certificate got created on the server and time was adjusted afterwards so the certificate becomes invalid
- A server certificate was configured in the vhost setup for SMT but the public part of the CA in /srv/www/htdocs/smt.crt does not match the certificate
- The paths for the SSL directories in /etc/smt.d/vhost-ssl.conf do not match
- The common server certificate expired
Additional Information
How to address
Cause: Time and date of server differ
Use NTP (Network Time Protocol) to synchronize the time between server and client. To accomplish this use the YaST2 NTP module to setup a NTP client.
In case there is no local NTP server available, look up the public IP of a NTP server close to your location. Please note that it might take some time for the clients to synchronize with the server. Depending on the firewall configuration, the ports to communicate with an external NTP server might need to be adjusted.
Also check time and date settings of suse_register returns the following error:
[info] SEND DATA to URI: https://smt.office.domain/center/regsvc?command=listproducts&lang=en-US&version=1.0:
[error] ERROR: Peer certificate cannot be authenticated with known CA certificates: (60)
[error] (2)
Cause: Certificate was created before time was adjusted
Using the command
openssl x509 -in <certificate file> -text
it is possible to check the validity of a certificate. The important part of the output is:
linux:/srv/www/htdocs # openssl x509 -in smt.crt -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
b0:4a:85:14:d2:33:86:c8
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=DE, CN=YaST Default CA (linux)/emailAddress=postmaster@domain.site
Validity
Not Before: Nov 19 11:52:58 2008 GMT
Not After : Nov 17 11:52:58 2018 GMT
Subject: C=DE, CN=YaST Default CA (linux)/emailAddress=postmaster@domain.site
Subject Public Key Info:
Check the Validity section in the output of the openssl command if it matches.
Also, use Yast | Security and Users | CA Managment to check the validity period of the server certificates, as the above command only checks the validity period of the CA.
Cause: Server certificate does not match CA
SMT stores a copy of the public part of the CA as smt.crt in /srv/www/htdocs. This copy is downloaded and used by the client to verify the SMT server.
In case a existing certificate was used to configure the Apache2 host, it might happen that the CA copy and certificate do not match.
Copy the appropriate part of the CA to /srv/www/htdocs/smt.crt and import it on the client using clientsetup4smt.sh.
Cause: Paths for SSL directories in /etc/smt.d/vhost-ssl.conf do not match
SMT stores a apache vhost-ssl.conf file in /etc/smt.d/. If the paths for the SSL certificates in this configuration file do not match the current paths (YaST-CA.pem in /etc/ssl/certs/ and servercert.pem and serverkey.pem in /etc/ssl/servercerts/ the suse_register command will compare the imported CA with a different certificate and fail.
In order to correct this either adjust the paths in /etc/smt.d/vhost-ssl-conf or restore the file from the latest smt RPM.
Cause: The common server certificate expired
Recreate the server certificate. Please see TID 000017336 — Howto recreate SMT11 CA and server certificate for details. Attention: only the server certificate has to be recreated, not the CA!
Cause: Network environment uses a proxy server
The command «./clientSetup4SMT.sh —host SMT-FQDN» returns:
Do you accept this certificate? [y/n] y
Client setup finished.
Start the registration now? [y/n] y
/usr/bin/suse_register -i -L /root/.suse_register.log
There are no enabled services defined.
Use ‘zypper addservice’ or ‘zypper modifyservice’ commands to add or enable services.
There are no enabled repositories defined.
Use ‘zypper addrepo’ or ‘zypper modifyrepo’ commands to add or enable repositories.
ERROR: HTTP/1.1 200 Connection established
Accept-Ranges: none
Connection: Keep-Alive
(2)
ERROR: Peer certificate cannot be authenticated with known CA certificates: (60)
(2)
ERROR: Peer certificate cannot be authenticated with known CA certificates: (60)
(2)
This issue may be experienced if the proxy is not properly configured on the system. Please use the YaST2 proxy module to configure the proxy settings and if necessary add an exclude for the SMT server.
Disclaimer
This Support Knowledgebase provides a valuable tool for SUSE customers and parties interested in our products and solutions to acquire information, ideas and learn from one another. Materials are provided for informational, personal or non-commercial use within your organization and are presented «AS IS» WITHOUT WARRANTY OF ANY KIND.
- Document ID:7002146
- Creation Date:
10-Dec-2008 - Modified Date:30-Dec-2021
-
- SUSE Linux Enterprise Desktop
- SUSE Linux Enterprise Server
< Back to Support Search
For questions or concerns with the SUSE Knowledgebase please contact: tidfeedback[at]suse.com
Steps to reproduce
- https://server.dom/index.php/settings/admin/logging
- see log entries: «GuzzleHttpExceptionRequestException: cURL error 60: Peer’s Certificate issuer is not recognized.»
- under /index.php/settings/apps i can’t find a list of external Apps
Expected behaviour
Nextcloud should load list of installable apps from external site (apps.nextcloud.com?!)
Actual behaviour
No app list and a log entry: GuzzleHttpExceptionRequestException: cURL error 60: Peer's Certificate issuer is not recognized.
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 104: GuzzleHttpExceptionRequestException wrapException(Object(GuzzleHttpMessageRequest), Object(GuzzleHttpRingExceptionRingException))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 132: GuzzleHttpRequestFsm->__invoke(Object(GuzzleHttpTransaction))
/opt/appl/www/3rdparty/react/promise/src/FulfilledPromise.php - line 25: GuzzleHttpRequestFsm->GuzzleHttp{closure}(Array)
/opt/appl/www/3rdparty/guzzlehttp/ringphp/src/Future/CompletedFutureValue.php - line 55: ReactPromiseFulfilledPromise->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Message/FutureResponse.php - line 43: GuzzleHttpRingFutureCompletedFutureValue->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 135: GuzzleHttpMessageFutureResponse proxy(Object(GuzzleHttpRingFutureCompletedFutureArray), Object(Closure))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 132: GuzzleHttpRequestFsm->__invoke(Object(GuzzleHttpTransaction))
/opt/appl/www/3rdparty/react/promise/src/FulfilledPromise.php - line 25: GuzzleHttpRequestFsm->GuzzleHttp{closure}(Array)
/opt/appl/www/3rdparty/guzzlehttp/ringphp/src/Future/CompletedFutureValue.php - line 55: ReactPromiseFulfilledPromise->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Message/FutureResponse.php - line 43: GuzzleHttpRingFutureCompletedFutureValue->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 135: GuzzleHttpMessageFutureResponse proxy(Object(GuzzleHttpRingFutureCompletedFutureArray), Object(Closure))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Client.php - line 165: GuzzleHttpRequestFsm->__invoke(Object(GuzzleHttpTransaction))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Client.php - line 125: GuzzleHttpClient->send(Object(GuzzleHttpMessageRequest))
/opt/appl/www/lib/private/Http/Client/Client.php - line 137: GuzzleHttpClient->get('http //www.next...', Array)
/opt/appl/www/settings/Controller/CheckSetupController.php - line 124: OCHttpClientClient->get('http //www.next...')
/opt/appl/www/settings/Controller/CheckSetupController.php - line 107: OCSettingsControllerCheckSetupController->isSiteReachable('www.nextcloud.c...')
/opt/appl/www/settings/Controller/CheckSetupController.php - line 363: OCSettingsControllerCheckSetupController->isInternetConnectionWorking()
[internal function] OCSettingsControllerCheckSetupController->check()
/opt/appl/www/lib/private/AppFramework/Http/Dispatcher.php - line 160: call_user_func_array(Array, Array)
/opt/appl/www/lib/private/AppFramework/Http/Dispatcher.php - line 90: OCAppFrameworkHttpDispatcher->executeController(Object(OCSettingsControllerCheckSetupController), 'check')
/opt/appl/www/lib/private/AppFramework/App.php - line 114: OCAppFrameworkHttpDispatcher->dispatch(Object(OCSettingsControllerCheckSetupController), 'check')
/opt/appl/www/lib/private/AppFramework/Routing/RouteActionHandler.php - line 47: OCAppFrameworkApp main('CheckSetupContr...', 'check', Object(OCAppFrameworkDependencyInjectionDIContainer), Array)
[internal function] OCAppFrameworkRoutingRouteActionHandler->__invoke(Array)
/opt/appl/www/lib/private/Route/Router.php - line 299: call_user_func(Object(OCAppFrameworkRoutingRouteActionHandler), Array)
/opt/appl/www/lib/base.php - line 1010: OCRouteRouter->match('/settings/ajax/...')
/opt/appl/www/index.php - line 40: OC handleRequest()
{main}
Server configuration
I have to talk a bit about our network configuration. We are forced to use an SSL-offloading proxy (the one that is configured). I searched around to proper configure the environment to accept the certificate from the proxy. I installed the certificate systemwide. With it curl -v https://google.com establishes a proper connection. php-curl is also enabled for nextcloud.
So I can’t figure out where the issue is located..
We also have to configure an Active Directory User (format: ADDOMusername ) to authenticate. But I guess this is not the reason for this issue.
Operating system: RHEL 7.2
Web server: apache
Database: mysql
PHP version: 5.6
Nextcloud version: 11.0.2 (stable)
Updated from an older Nextcloud/ownCloud or fresh install: very long update list from owncloud 5
Where did you install Nextcloud from: manually unzipping it.
Signing status:
Signing status
No errors have been found.
List of activated apps:
- comments: 1.1.0
- dav: 1.1.1
- federatedfilesharing: 1.1.1
- federation: 1.1.1
- files: 1.6.1
- files_sharing: 1.1.1
- files_texteditor: 2.2
- files_trashbin: 1.1.0
- files_versions: 1.4.0
- files_videoplayer: 1.0.0
- firstrunwizard: 2.0
- logreader: 2.0.0
- lookup_server_connector: 1.0.0
- nextcloud_announcements: 1.0
- notifications: 1.0.1
- passman: 2.1.2
- password_policy: 1.1.0
- provisioning_api: 1.1.0
- serverinfo: 1.1.1
- templateeditor: 0.2
- theming: 1.1.1
- twofactor_backupcodes: 1.0.0
- updatenotification: 1.1.1
- workflowengine: 1.1.1
Nextcloud configuration:
Config report
{
"system": {
"passwordsalt": "***REMOVED SENSITIVE VALUE***",
"datadirectory": "/opt/appl/data",
"dbtype": "mysql",
"version": "11.0.2.7",
"dbname": "ownclouddb",
"dbhost": "localhost",
"dbtableprefix": "oc_",
"dbuser": "***REMOVED SENSITIVE VALUE***",
"dbpassword": "***REMOVED SENSITIVE VALUE***",
"installed": true,
"loglevel": 1,
"logfile": "/opt/appl/serverlogs/owncloud.log",
"updatechecker": false,
"knowledgebaseenabled": false,
"appstoreenabled": false,
"instanceid": "5108f7036f849",
"maintenance": false,
"theme": "",
"trusted_domains": [
"nc.our.dom"
],
"secret": "***REMOVED SENSITIVE VALUE***",
"share_folder": "/Shared",
"mail_smtpmode": "smtp",
"mail_domain": "our.dom",
"overwritehost": "nc.our.dom",
"overwriteprotocol": "https",
"overwritewebroot": "",
"appstore.experimental.enabled": true,
"mail_from_address": "owncloud-no-reply",
"mail_smtphost": "smtp.our.dom",
"mail_smtpport": "25",
"memcache.local": "\OC\Memcache\APCu",
"enable_avatars": true,
"proxy": "proxy.our.dom:8080",
"proxyuserpwd": "ADDOM\user:PW-with-special-chars",
"auth.bruteforce.protection.enabled": false,
"singleuser": false
},
"apps": {
"activity": {
"enabled": "no",
"installed_version": "2.4.1",
"types": "filesystem"
},
"admin_dependencies_chk": {
"enabled": "no",
"installed_version": "0.02",
"ocsid": "166041",
"types": ""
},
"admin_migrate": {
"enabled": "no",
"installed_version": "0.1",
"types": ""
},
"backgroundjob": {
"lastjob": "94298"
},
"calendar": {
"enabled": "no",
"installed_version": "0.4.1n",
"types": ""
},
"comments": {
"enabled": "yes",
"installed_version": "1.1.0",
"types": "logging"
},
"configreport": {
"enabled": "no",
"installed_version": "0.1.1",
"types": "filesystem"
},
"contacts": {
"enabled": "no",
"installed_version": "0.2",
"types": ""
},
"core": {
"backgroundjobs_mode": "cron",
"backgroundjobs_step": "queued_tasks",
"backgroundjobs_task": "OC_Cache_FileGlobal-gc",
"global_cache_gc_lastrun": "1461431848",
"incoming_server2server_share_enabled": "no",
"installedat": "1345803025.5034",
"lastcron": "1500366602",
"lastupdateResult": "[]",
"lastupdatedat": "1500366314",
"oc.integritycheck.checker": "[]",
"outgoing_server2server_share_enabled": "no",
"previewsCleanedUp": "1",
"public_caldav": "/apps/calendar/share.php",
"public_calendar": "/apps/calendar/share.php",
"public_files": "files_sharing/public.php",
"public_gallery": "/apps/gallery/sharing.php",
"public_webdav": "dav/appinfo/v1/publicwebdav.php",
"remote_ampache": "/apps/media/remote.php",
"remote_caldav": "dav/appinfo/v1/caldav.php",
"remote_calendar": "dav/appinfo/v1/caldav.php",
"remote_carddav": "dav/appinfo/v1/carddav.php",
"remote_contacts": "dav/appinfo/v1/carddav.php",
"remote_core.css": "/core/minimizer.php",
"remote_core.js": "/core/minimizer.php",
"remote_dav": "dav/appinfo/v2/remote.php",
"remote_files": "dav/appinfo/v1/webdav.php",
"remote_filesync": "files/appinfo/filesync.php",
"remote_webdav": "dav/appinfo/v1/webdav.php",
"repairlegacystoragesdone": "yes",
"shareapi_allow_mail_notification": "yes",
"shareapi_allow_public_notification": "yes",
"shareapi_default_expire_date": "yes",
"shareapi_exclude_groups": "no",
"shareapi_expire_after_n_days": "10",
"umgmt_show_last_login": "true",
"vendor": "nextcloud"
},
"dav": {
"OCA\DAV\Migration\ValueFixInsert_ran": "true",
"enabled": "yes",
"installed_version": "1.1.1",
"types": "filesystem"
},
"federatedfilesharing": {
"enabled": "yes",
"installed_version": "1.1.1",
"types": ""
},
"federation": {
"autoAddServers": "0",
"enabled": "yes",
"installed_version": "1.1.1",
"types": "authentication"
},
"files": {
"backgroundwatcher_previous_file": "13466",
"backgroundwatcher_previous_folder": "20484",
"cronjob_scan_files": "1000",
"default_quota": "8 GB",
"enabled": "yes",
"installed_version": "1.6.1",
"types": "filesystem"
},
"files_archive": {
"enabled": "no",
"installed_version": "0.2",
"types": "filesystem"
},
"files_imageviewer": {
"enabled": "no",
"installed_version": "1.0",
"types": ""
},
"files_odfviewer": {
"enabled": "no",
"installed_version": "0.1",
"types": ""
},
"files_pdfviewer": {
"enabled": "no",
"installed_version": "0.2",
"types": ""
},
"files_retention": {
"enabled": "no",
"installed_version": "1.0.1",
"types": "filesystem"
},
"files_sharing": {
"enabled": "yes",
"incoming_server2server_share_enabled": "yes",
"installed_version": "1.1.1",
"outgoing_server2server_share_enabled": "yes",
"types": "filesystem"
},
"files_texteditor": {
"enabled": "yes",
"installed_version": "2.2",
"types": ""
},
"files_trashbin": {
"enabled": "yes",
"installed_version": "1.1.0",
"types": "filesystem"
},
"files_versions": {
"enabled": "yes",
"installed_version": "1.4.0",
"types": "filesystem"
},
"files_videoplayer": {
"enabled": "yes",
"installed_version": "1.0.0",
"types": ""
},
"firstrunwizard": {
"enabled": "yes",
"installed_version": "2.0",
"types": "logging"
},
"gallery": {
"enabled": "no",
"installed_version": "0.5.0n",
"types": ""
},
"logreader": {
"enabled": "yes",
"installed_version": "2.0.0",
"ocsid": "170871",
"types": ""
},
"lookup_server_connector": {
"enabled": "yes",
"installed_version": "1.0.0",
"types": "authentication"
},
"media": {
"enabled": "no",
"installed_version": "0.4",
"types": ""
},
"nextcloud_announcements": {
"enabled": "yes",
"installed_version": "1.0",
"types": "logging"
},
"notifications": {
"enabled": "yes",
"installed_version": "1.0.1",
"types": "logging"
},
"passman": {
"enabled": "["mwo-linux"]",
"installed_version": "2.1.2",
"types": ""
},
"password_policy": {
"enabled": "yes",
"installed_version": "1.1.0",
"types": ""
},
"provisioning_api": {
"enabled": "yes",
"installed_version": "1.1.0",
"types": "prevent_group_restriction"
},
"serverinfo": {
"enabled": "["admin"]",
"installed_version": "1.1.1",
"types": ""
},
"sharebymail": {
"enabled": "no",
"installed_version": "1.0.1",
"types": "filesystem"
},
"storagecharts2": {
"enabled": "no",
"installed_version": "2.6.0",
"types": ""
},
"survey_client": {
"enabled": "no",
"installed_version": "0.1.5",
"types": ""
},
"systemtags": {
"enabled": "no",
"installed_version": "0.2",
"types": "logging"
},
"templateeditor": {
"enabled": "yes",
"installed_version": "0.2",
"types": ""
},
"theming": {
"backgroundMime": "image/jpeg",
"cachebuster": "10",
"color": "#E2002A",
"enabled": "yes",
"installed_version": "1.1.1",
"logoMime": "image/svg+xml",
"name": "",
"slogan": "",
"types": "logging",
"url": ""
},
"twofactor_backupcodes": {
"enabled": "yes",
"installed_version": "1.0.0",
"types": ""
},
"updatenotification": {
"enabled": "yes",
"installed_version": "1.1.1",
"types": ""
},
"updater": {
"enabled": "no",
"installed_version": "0.6",
"types": ""
},
"user_migrate": {
"enabled": "no",
"installed_version": "0.1",
"types": ""
},
"workflowengine": {
"enabled": "yes",
"installed_version": "1.1.1",
"types": "filesystem"
}
}
}
Are you using external storage, if yes which one: no
Are you using encryption: no
Are you using an external user-backend, if yes which one: no
Client configuration
Browser: Firefox
Operating system: Kubuntu 16.04
Logs
Nextcloud log (data/nextcloud.log)
Nextcloud log
Error | internet_connection_check | GuzzleHttpExceptionRequestException: cURL error 60: Peer's Certificate issuer is not recognized. | 2017-07-18T11:11:17+0200
-- | -- | -- | --
Error | internet_connection_check | GuzzleHttpExceptionRequestException: cURL error 60: Peer's Certificate issuer is not recognized. | 2017-07-18T11:11:17+0200
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 104: GuzzleHttpExceptionRequestException wrapException(Object(GuzzleHttpMessageRequest), Object(GuzzleHttpRingExceptionRingException))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 132: GuzzleHttpRequestFsm->__invoke(Object(GuzzleHttpTransaction))
/opt/appl/www/3rdparty/react/promise/src/FulfilledPromise.php - line 25: GuzzleHttpRequestFsm->GuzzleHttp{closure}(Array)
/opt/appl/www/3rdparty/guzzlehttp/ringphp/src/Future/CompletedFutureValue.php - line 55: ReactPromiseFulfilledPromise->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Message/FutureResponse.php - line 43: GuzzleHttpRingFutureCompletedFutureValue->then(Object(Closure), NULL, NULL)
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/RequestFsm.php - line 135: GuzzleHttpMessageFutureResponse proxy(Object(GuzzleHttpRingFutureCompletedFutureArray), Object(Closure))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Client.php - line 165: GuzzleHttpRequestFsm->__invoke(Object(GuzzleHttpTransaction))
/opt/appl/www/3rdparty/guzzlehttp/guzzle/src/Client.php - line 125: GuzzleHttpClient->send(Object(GuzzleHttpMessageRequest))
/opt/appl/www/lib/private/Http/Client/Client.php - line 137: GuzzleHttpClient->get('https //www.goo...', Array)
/opt/appl/www/settings/Controller/CheckSetupController.php - line 125: OCHttpClientClient->get('https //www.goo...')
/opt/appl/www/settings/Controller/CheckSetupController.php - line 107: OCSettingsControllerCheckSetupController->isSiteReachable('www.google.com')
/opt/appl/www/settings/Controller/CheckSetupController.php - line 363: OCSettingsControllerCheckSetupController->isInternetConnectionWorking()
[internal function] OCSettingsControllerCheckSetupController->check()
/opt/appl/www/lib/private/AppFramework/Http/Dispatcher.php - line 160: call_user_func_array(Array, Array)
/opt/appl/www/lib/private/AppFramework/Http/Dispatcher.php - line 90: OCAppFrameworkHttpDispatcher->executeController(Object(OCSettingsControllerCheckSetupController), 'check')
/opt/appl/www/lib/private/AppFramework/App.php - line 114: OCAppFrameworkHttpDispatcher->dispatch(Object(OCSettingsControllerCheckSetupController), 'check')
/opt/appl/www/lib/private/AppFramework/Routing/RouteActionHandler.php - line 47: OCAppFrameworkApp main('CheckSetupContr...', 'check', Object(OCAppFrameworkDependencyInjectionDIContainer), Array)
[internal function] OCAppFrameworkRoutingRouteActionHandler->__invoke(Array)
/opt/appl/www/lib/private/Route/Router.php - line 299: call_user_func(Object(OCAppFrameworkRoutingRouteActionHandler), Array)
/opt/appl/www/lib/base.php - line 1010: OCRouteRouter->match('/settings/ajax/...')
/opt/appl/www/index.php - line 40: OC handleRequest()
{main}
Summary
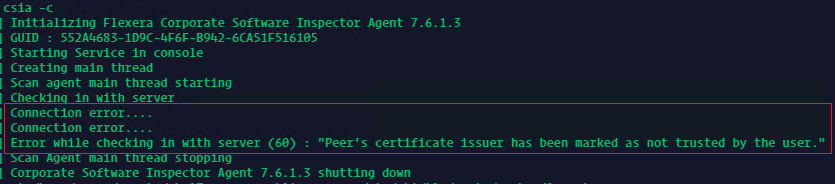
While running an ongoing terminal scan with the SVM Agent for Linux, the latter returns the following:
«error while checking in with server (60) … connection error»
This error is related to the server SSL certificate which in this case had not yet been imported in the ‘trusted certificates list’ of the Linux server system. The error message says the following:
«Peer’s certificate issuer had been marked as not trusted by the user»
Symptoms
While running a scan with the Software Vulnerability Manager Agent for Red Hat Linux, the latter returns:
«Error while checking in with server (60)» message and «connection error» known as ‘curl 60’.
You might see this error in the «sync.log» log file of your RHEL/CentOS SVM server, printed out with the following message:
«There was a problem with the curl request. Error no 60: Peer certificate cannot be authenticated with known CA certificates»
Cause
The error indicates that the ‘Certification Authorities’ list on the Redhat machine does not include a reference to the SSL certificate which your server instance is using to authorize SSL connections.
You should copy the public-key copy of your certificate to your Redhat machine and import it to the list of trusted certification authorities (ca-bundle.crt)
Resolution
1. Open Internet Explorer on a Windows host and type in the browser the name of your server (https://).
2. Once connected, click on the lock icon on the right side of the address bar, click ‘View Certificates’.
3. Click on Details TAB.
4. Click ‘Copy to File’ > Next > ‘Base-64 encoded x.509 (.CER)’ > Next > Save (e.g. rhel7-server-public.CER).
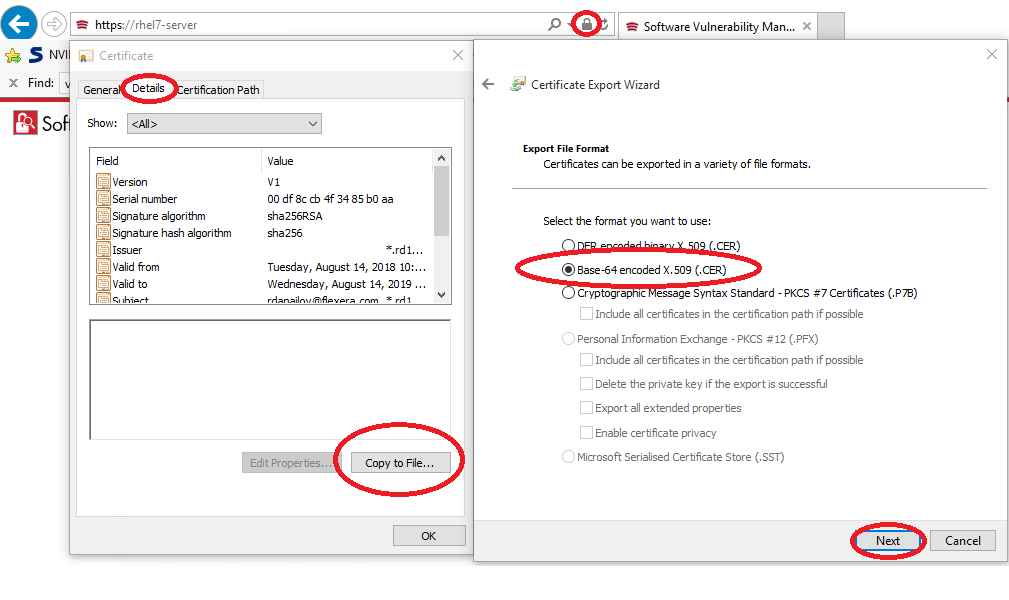
6. Run this command to import the certificate in the trusted CA’s list:
cat rhel7-server-public.CER >> /etc/pki/tls/certs/ca-bundle.crt
After you performed these actions, you should be able to run an error-free scan with the SVM Agent.