-
Question
-
Hi everyone,
Recently, all of our company window 7 PC are having issue downloading window update from wsus server.
When i check on one of the pc windowupdate.log, it has below error message:-
Report 80244019 — Automaticupdatewuapp failure content download error: download failed.
Any advise as to what i should troubleshoot? is it wsus server have problem? where should i navigate the problem?
Please help.
Thanks!
All replies
-
Hi,
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
net stop bits net stop wuauserv net stop appidsvc net stop cryptsvc Del "%ALLUSERSPROFILE%Application DataMicrosoftNetworkDownloader*.*" rmdir %systemroot%SoftwareDistribution /S /Q rmdir %systemroot%system32catroot2 /S /Q sc.exe sdset bits D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;PU) sc.exe sdset wuauserv D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;PU) cd /d %windir%system32 regsvr32.exe /s atl.dll regsvr32.exe /s urlmon.dll regsvr32.exe /s mshtml.dll regsvr32.exe /s shdocvw.dll regsvr32.exe /s browseui.dll regsvr32.exe /s jscript.dll regsvr32.exe /s vbscript.dll regsvr32.exe /s scrrun.dll regsvr32.exe /s msxml.dll regsvr32.exe /s msxml3.dll regsvr32.exe /s msxml6.dll regsvr32.exe /s actxprxy.dll regsvr32.exe /s softpub.dll regsvr32.exe /s wintrust.dll regsvr32.exe /s dssenh.dll regsvr32.exe /s rsaenh.dll regsvr32.exe /s gpkcsp.dll regsvr32.exe /s sccbase.dll regsvr32.exe /s slbcsp.dll regsvr32.exe /s cryptdlg.dll regsvr32.exe /s oleaut32.dll regsvr32.exe /s ole32.dll regsvr32.exe /s shell32.dll regsvr32.exe /s initpki.dll regsvr32.exe /s wuapi.dll regsvr32.exe /s wuaueng.dll regsvr32.exe /s wuaueng1.dll regsvr32.exe /s wucltui.dll regsvr32.exe /s wups.dll regsvr32.exe /s wups2.dll regsvr32.exe /s wuweb.dll regsvr32.exe /s qmgr.dll regsvr32.exe /s qmgrprxy.dll regsvr32.exe /s wucltux.dll regsvr32.exe /s muweb.dll regsvr32.exe /s wuwebv.dll netsh winsock reset netsh winsock reset proxy net start bits net start wuauserv net start appidsvc net start cryptsvc
thank you
-
Hi Min777,
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, «http://wsusserver.mydomain.local:8530«.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, «http://10.1.1.51:8530«.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.-
Edited by
Wednesday, December 25, 2019 2:04 AM
Paragraph format.
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
-
Hi,
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
net stop bits net stop wuauserv net stop appidsvc net stop cryptsvc Del "%ALLUSERSPROFILE%Application DataMicrosoftNetworkDownloader*.*" rmdir %systemroot%SoftwareDistribution /S /Q rmdir %systemroot%system32catroot2 /S /Q sc.exe sdset bits D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;PU) sc.exe sdset wuauserv D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;AU)(A;;CCLCSWRPWPDTLOCRRC;;;PU) cd /d %windir%system32 regsvr32.exe /s atl.dll regsvr32.exe /s urlmon.dll regsvr32.exe /s mshtml.dll regsvr32.exe /s shdocvw.dll regsvr32.exe /s browseui.dll regsvr32.exe /s jscript.dll regsvr32.exe /s vbscript.dll regsvr32.exe /s scrrun.dll regsvr32.exe /s msxml.dll regsvr32.exe /s msxml3.dll regsvr32.exe /s msxml6.dll regsvr32.exe /s actxprxy.dll regsvr32.exe /s softpub.dll regsvr32.exe /s wintrust.dll regsvr32.exe /s dssenh.dll regsvr32.exe /s rsaenh.dll regsvr32.exe /s gpkcsp.dll regsvr32.exe /s sccbase.dll regsvr32.exe /s slbcsp.dll regsvr32.exe /s cryptdlg.dll regsvr32.exe /s oleaut32.dll regsvr32.exe /s ole32.dll regsvr32.exe /s shell32.dll regsvr32.exe /s initpki.dll regsvr32.exe /s wuapi.dll regsvr32.exe /s wuaueng.dll regsvr32.exe /s wuaueng1.dll regsvr32.exe /s wucltui.dll regsvr32.exe /s wups.dll regsvr32.exe /s wups2.dll regsvr32.exe /s wuweb.dll regsvr32.exe /s qmgr.dll regsvr32.exe /s qmgrprxy.dll regsvr32.exe /s wucltux.dll regsvr32.exe /s muweb.dll regsvr32.exe /s wuwebv.dll netsh winsock reset netsh winsock reset proxy net start bits net start wuauserv net start appidsvc net start cryptsvc
thank you
Tried this before, and PC still having the same issue..
-
Hi Min777,
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, «http://wsusserver.mydomain.local:8530«.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, «http://10.1.1.51:8530«.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Hi, yes all pc is domain joined, and previously they have been able to download wsus update from wsus server through port 8531 without problem, just recently, only window 7 pc having problem..
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
any idea?
thanks!
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
-
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Hi Yic,
Yes, I checked mmc in the PC with problem, there’s SSL certificate in the trusted root certification authorities.
-
Hi Min,
Please determine if you have SSL enabled only for the web pages of the following WSUS administration sites:
- ClientWebService
- DssAuthWebService
- ServerSyncWebService
- SimpleAuthWebService
In addition, please do not enable SSL for other web pages and main sites.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
Hi Yic,
Thanks for your swift respond, did you mean to check the web pages in IIS of the WSUS Server?
If yes, then all web services in WSUS Server IIS, the SSL setting did not require SSL and client certificate is selected ignore.
Thanks!
-
Hi ,
Could you tell me please your version of WSUS?
thank you
-
Hi Min,
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
and:
- ApiRemoting30
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: «Enabling
SSL on Windows Server Update Services.«
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.Hope the above can help you.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. - ClientWebService
-
Hi ,
Could you tell me please your version of WSUS?
thank you
Hi Mooner09, it is version 6.3.9600
-
Hi Min,
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
and:
- ApiRemoting30
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: «Enabling
SSL on Windows Server Update Services.«
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.Hope the above can help you.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Hi Yic,
Not sure if this is the correct direction we heading, because other PC that is window 10 are not having any issue downloading the window update.
- ClientWebService
-
Hi Min,
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in
this thread.
Hope the above can help you.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.-
Edited by
Yic LvMicrosoft contingent staff
Monday, December 30, 2019 7:49 AM
Paragraph format.
-
Hi Min,
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in
this thread.
Hope the above can help you.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Hi Yic,
Thanks for the feedback,for item no3, how can i decline the problematic window update?
I selected the window update in wsus console, and when i click on the declide button, below alert appears.
here are the windowupdate.log captured.
2019-12-30 17:54:22:299 804 324c Report REPORT EVENT: {8E1D6878-9084-49A2-926D-335540327F28} 2019-12-30 17:54:03:244+0800 1
161 101 {ECAF8036-92F9-4F9F-8C20-CC4E381E9CDC} 202 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:299 804 2474 AU >>## RESUMED ## AU: Search for updates [CallId = {60B27BA6-FB23-4DE2-A63F-470DE896A211}]
2019-12-30 17:54:22:299 804 2474 AU # 5 updates detected
2019-12-30 17:54:22:299 804 324c Report REPORT EVENT: {84B570D6-A25B-4839-80F3-1D8E44326EC5} 2019-12-30 17:54:03:861+0800 1
161 101 {1B9EA75E-B216-4B3C-AF63-2A03FE2800FF} 200 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:300 804 2474 AU #########
2019-12-30 17:54:22:300 804 2474 AU ## END ## AU: Search for updates [CallId = {60B27BA6-FB23-4DE2-A63F-470DE896A211}]
2019-12-30 17:54:22:300 804 2474 AU #############
2019-12-30 17:54:22:300 804 2474 AU Featured notifications is disabled.
2019-12-30 17:54:22:301 804 2474 AU Successfully wrote event for AU health state:0
2019-12-30 17:54:22:303 804 2474 AU Successfully wrote event for AU health state:0
2019-12-30 17:54:22:305 804 1118 AU Getting featured update notifications. fIncludeDismissed = true
2019-12-30 17:54:22:305 804 1118 AU No featured updates available.
2019-12-30 17:54:22:306 804 324c Report WARNING: CWERReporter finishing event handling with error = 800700a1
2019-12-30 17:54:22:306 804 324c Report REPORT EVENT: {8E1D6878-9084-49A2-926D-335540327F28} 2019-12-30 17:54:03:244+0800 1
161 101 {ECAF8036-92F9-4F9F-8C20-CC4E381E9CDC} 202 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:306 804 324c Report REPORT EVENT: {84B570D6-A25B-4839-80F3-1D8E44326EC5} 2019-12-30 17:54:03:861+0800 1
161 101 {1B9EA75E-B216-4B3C-AF63-2A03FE2800FF} 200 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:312 804 324c Report WARNING: CWERReporter finishing event handling with error = 800700a1
2019-12-30 17:54:22:312 804 324c Report REPORT EVENT: {8E1D6878-9084-49A2-926D-335540327F28} 2019-12-30 17:54:03:244+0800 1
161 101 {ECAF8036-92F9-4F9F-8C20-CC4E381E9CDC} 202 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:312 804 324c Report REPORT EVENT: {84B570D6-A25B-4839-80F3-1D8E44326EC5} 2019-12-30 17:54:03:861+0800 1
161 101 {1B9EA75E-B216-4B3C-AF63-2A03FE2800FF} 200 80244019 AutomaticUpdatesWuApp Failure Content Download Error:
Download failed.
2019-12-30 17:54:22:319 804 324c Report WARNING: CWERReporter finishing event handling with error = 800700a1
2019-12-30 17:54:22:329 804 324c Report Uploading 32 events using cached cookie, reporting URL = http://dc04/ReportingWebService/ReportingWebService.asmx
2019-12-30 17:54:22:336 804 324c Report Reporter successfully uploaded 32 events.Kindly advise.
Thanks.!
-
I selected the window update in wsus console, and when i click on the declide button, below alert appears.
Please clicking «Yes» in the window will decline the update.
And than, you can then filter the «Approval» attribute to «Declined» in the update view of the WSUS console, find KB4525233, and re-approve.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
I selected the window update in wsus console, and when i click on the declide button, below alert appears.
Please clicking «Yes» in the window will decline the update.
And than, you can then filter the «Approval» attribute to «Declined» in the update view of the WSUS console, find KB4525233, and re-approve.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Hi Yic,
Thanks for your feedback, i tried declined the update then reapproved it, afterward in the client pc i tried redownload the window update, but it is still showing same error message.
Hmm,…any idea where i can check if the window update is re-download successfully?
Thanks.
-
you can import this update KB4525233 from Microsoft catalog
Click on USUS Updates and from Right side hits Import Updates
after that in IE catalog.update.microsoft.com search you update KB4525233 and click
Add and Import after that you will know exactly what uploaded successfullythank you
-
Hi Min,
Please consider running «regedit» on the WSUS server and navigating to the following location in the Registry Editor:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftUpdate ServicesServerSetup
Check if the address configured by «ContentDir» is canonical, don’t lack the necessary colons and slashes.
Then navigate to IIS-WSUS Administration-Content-Advanced Settings. Notice the value of ‘Physical Path’ and don’t lack the necessary colons and slashes.
If these values are inconsistent or abnormal, it may cause the update file to fail to download.
Reply back with the results would be happy to help.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. - HKEY_LOCAL_MACHINESOFTWAREMicrosoftUpdate ServicesServerSetup
-
Hi Yic,
I checked the mentioned path, it look tallied:-
Regedit of WSUS Server
IIS:-
-
Hi everyone,
any idea where i can further troubleshoot on this?
I’m able to download the .cab file from client PC through browser that it using port 80.
thanks!
-
I’m able to download the .cab file from client PC through browser that it using port 80.
On WSUS 6.2 and later (at least Windows Server 2012 ), port 8530 for HTTP and 8531 for HTTPS are used.
If the port number is changed to 80 after the WSUS configuration is completed, this may be the cause of the fault. If the conditions work, consider adjusting the port number of WSUS to 8530.
Hope the above can help you.
Regards,
Yic
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com. -
Hi Yic,
Thanks for your feedback.
The weird part is pc that are OS window 10 doesnt have this problem, and the OS window 10 PC cant telnet 8530 as well.
This means it shouldn’t be port number 80 problem right? because our OS Window 10 PC is able to download window update, in the wsus console it is showing 100% for all OS 10 pc.
Thanks for your help Yic, but look like we are going back to the starting point.
Содержание
- Warning cwerreporter finishing event handling with error 800700a1
- Asked by:
- Question
- All replies
- Warning cwerreporter finishing event handling with error 800700a1
- Вопрос
- Все ответы
Warning cwerreporter finishing event handling with error 800700a1
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:
Question
Recently, all of our company window 7 PC are having issue downloading window update from wsus server.
When i check on one of the pc windowupdate.log, it has below error message:-
Report 80244019 — Automaticupdatewuapp failure content download error: download failed.
Any advise as to what i should troubleshoot? is it wsus server have problem? where should i navigate the problem?
«Vote or mark as answer if you think useful» «Marquer comme réponse les réponses qui ont résolu votre problème»
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, » http: //wsusserver.mydomain.local:8530 «.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, » http://10.1.1.51:8530 «.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
- Edited by Yic Lv Microsoft contingent staff Wednesday, December 25, 2019 2:04 AM Paragraph format.
Followup the given steps in this guidance,
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
Tried this before, and PC still having the same issue..
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, » http: //wsusserver.mydomain.local:8530 «.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, » http://10.1.1.51:8530 «.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Hi, yes all pc is domain joined, and previously they have been able to download wsus update from wsus server through port 8531 without problem, just recently, only window 7 pc having problem..
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Followup the given steps in this guidance,
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Yes, I checked mmc in the PC with problem, there’s SSL certificate in the trusted root certification authorities.
Please determine if you have SSL enabled only for the web pages of the following WSUS administration sites:
- ClientWebService
- DssAuthWebService
- ServerSyncWebService
- SimpleAuthWebService
In addition, please do not enable SSL for other web pages and main sites.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Thanks for your swift respond, did you mean to check the web pages in IIS of the WSUS Server?
If yes, then all web services in WSUS Server IIS, the SSL setting did not require SSL and client certificate is selected ignore.
Could you tell me please your version of WSUS?
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: » Enabling SSL on Windows Server Update Services. «
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Could you tell me please your version of WSUS?
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: » Enabling SSL on Windows Server Update Services. «
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Not sure if this is the correct direction we heading, because other PC that is window 10 are not having any issue downloading the window update.
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in this thread .
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
- Edited by Yic Lv Microsoft contingent staff Monday, December 30, 2019 7:49 AM Paragraph format.
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in this thread .
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Thanks for the feedback,for item no3, how can i decline the problematic window update?
I selected the window update in wsus console, and when i click on the declide button, below alert appears.
Источник
Warning cwerreporter finishing event handling with error 800700a1
Вопрос
Recently, all of our company window 7 PC are having issue downloading window update from wsus server.
When i check on one of the pc windowupdate.log, it has below error message:-
Report 80244019 — Automaticupdatewuapp failure content download error: download failed.
Any advise as to what i should troubleshoot? is it wsus server have problem? where should i navigate the problem?
Все ответы
«Vote or mark as answer if you think useful» «Marquer comme réponse les réponses qui ont résolu votre problème»
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, » http: //wsusserver.mydomain.local:8530 «.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, » http://10.1.1.51:8530 «.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
- Изменено Yic Lv Microsoft contingent staff 25 декабря 2019 г. 2:04 Paragraph format.
Followup the given steps in this guidance,
Try do this on one workstation and you can see if after that downloads and update start working it’s mean workstation problem
Tried this before, and PC still having the same issue..
If your clients are located in a domain environment, the clients will receive the WSUS configuration information by receiving Group Policy, then check the configuration of the following Group Policy:
- Windows Components > Windows Update > [Specify intranet Microsoft update service location]
Please check if the intranet server you entered is the FDQN and port number of the WSUS server.
For example, » http: //wsusserver.mydomain.local:8530 «.
If your clients are in a workgroup environment, the clients will obtain the WSUS configuration information through the registry, then check the configuration of the following key values:
- [HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindowsWindowsUpdate]
Please check WUServer & WUStatusServer fill in the FQDN and port number of the WSUS server, or the IP and port number.
For example, » http://10.1.1.51:8530 «.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Hi, yes all pc is domain joined, and previously they have been able to download wsus update from wsus server through port 8531 without problem, just recently, only window 7 pc having problem..
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Followup the given steps in this guidance,
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
from Client PC (With Problem), i’m able to telnet wsus server with port 8531, but can’t access through web browser..
Has the certificate used for SSL connection encryption been added to the client’s «Trusted Root Certification Authorities» directory?
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Yes, I checked mmc in the PC with problem, there’s SSL certificate in the trusted root certification authorities.
Please determine if you have SSL enabled only for the web pages of the following WSUS administration sites:
- ClientWebService
- DssAuthWebService
- ServerSyncWebService
- SimpleAuthWebService
In addition, please do not enable SSL for other web pages and main sites.
Reply back with the results would be happy to help.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Thanks for your swift respond, did you mean to check the web pages in IIS of the WSUS Server?
If yes, then all web services in WSUS Server IIS, the SSL setting did not require SSL and client certificate is selected ignore.
Could you tell me please your version of WSUS?
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: » Enabling SSL on Windows Server Update Services. «
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Could you tell me please your version of WSUS?
Sorry I didn’t express clearly.
If you need to enable SSL access to your WSUS site, you need to enable SSL on those pages I mentioned:
- ClientWebService
DssAuthWebService
ServerSyncWebService
SimpleAuthWebService
The opening method can refer to the following snapshot:
If you have questions about how to enable SSL configuration, you can refer to the steps mentioned in this article: » Enabling SSL on Windows Server Update Services. «
* Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Not sure if this is the correct direction we heading, because other PC that is window 10 are not having any issue downloading the window update.
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in this thread .
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
- Изменено Yic Lv Microsoft contingent staff 30 декабря 2019 г. 7:49 Paragraph format.
The 0x80244019 error means a 404 error for HTTP, which happens when some resources cannot be found. If we first rule out issues that are not SSL, consider the following checks:
- On the Win7 client where 80244019 appears, you can find the location of the problem by retrieving 80244019 in WindowsUpdate.log.
- Usually, the context of these locations should include a record of obtaining some update files, but an error occurs because it is not available. Please consider checking that these mentioned files are actually stored in the content folder of the WSUS server.
- You can also try decline these problematic updates in the WSUS console and re-approve.
- There may also be problems caused by other reasons, refer to the explanation from Lawrence in this thread .
Hope the above can help you.
Please remember to mark as answers if they help.
If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com .
Thanks for the feedback,for item no3, how can i decline the problematic window update?
I selected the window update in wsus console, and when i click on the declide button, below alert appears.
Источник
ok all I need some help, I have googled the heck out of this. I recently had to reinstall my WSUS server and for some reason none of my clients will report to it? I have done everything that Microsoft has suggested and even a few things people form the web have said and still no luck. I have confirmed with the Client Diag tool they see the see the sever along with the web tool for downloading a file from that server and they all work fine. I have posted the windows update log from one of the clients here in hopes that someone will see what I’m missing. if you guys need any other logs from either the client or the server just let me know and I will post them as well. Thanks all
2014-04-22 17:24:05:185 964 1a0c Misc =========== Logging initialized (build: 7.6.7600.256, tz: -0700) ===========
2014-04-22 17:24:05:185 964 1a0c Misc = Process: C:Windowssystem32svchost.exe
2014-04-22 17:24:05:185 964 1a0c Misc = Module: c:windowssystem32wuaueng.dll
2014-04-22 17:24:05:185 964 1a0c Service *************
2014-04-22 17:24:05:185 964 1a0c Service ** START ** Service: Service startup
2014-04-22 17:24:05:185 964 1a0c Service *********
2014-04-22 17:24:05:189 964 1a0c Agent * WU client version 7.6.7600.256
2014-04-22 17:24:05:189 964 1a0c Agent * Base directory: C:WindowsSoftwareDistribution
2014-04-22 17:24:05:189 964 1a0c Agent * Access type: No proxy
2014-04-22 17:24:05:190 964 1a0c Agent * Network state: Connected
2014-04-22 17:24:50:221 964 1a0c Report CWERReporter::Init succeeded
2014-04-22 17:24:50:221 964 1a0c Agent *********** Agent: Initializing Windows Update Agent ***********
2014-04-22 17:24:50:222 964 1a0c Agent *********** Agent: Initializing global settings cache ***********
2014-04-22 17:24:50:222 964 1a0c Agent * WSUS server: <NULL>
2014-04-22 17:24:50:222 964 1a0c Agent * WSUS status server: <NULL>
2014-04-22 17:24:50:222 964 1a0c Agent * Target group: (Unassigned Computers)
2014-04-22 17:24:50:222 964 1a0c Agent * Windows Update access disabled: No
2014-04-22 17:24:50:222 964 1a0c DnldMgr Download manager restoring 0 downloads
2014-04-22 17:24:50:225 964 1a0c AU ########### AU: Initializing Automatic Updates ###########
2014-04-22 17:24:50:227 964 1a0c AU # Approval type: Scheduled (User preference)
2014-04-22 17:24:50:227 964 1a0c AU # Scheduled install day/time: Every day at 3:00
2014-04-22 17:24:50:227 964 1a0c AU # Auto-install minor updates: Yes (User preference)
2014-04-22 17:24:50:228 964 1a0c AU Setting AU scheduled install time to 2014-04-23 10:00:00
2014-04-22 17:24:50:566 964 1a0c Report *********** Report: Initializing static reporting data ***********
2014-04-22 17:24:50:566 964 1a0c Report * OS Version = 6.1.7601.1.0.65792
2014-04-22 17:24:50:566 964 1a0c Report * OS Product Type = 0x00000001
2014-04-22 17:24:50:593 964 1a0c Report * Computer Brand = TOSHIBA
2014-04-22 17:24:50:593 964 1a0c Report * Computer Model = Pottege0M750
2014-04-22 17:24:50:596 964 1a0c Report * Bios Revision = Version 1.00
2014-04-22 17:24:50:596 964 1a0c Report * Bios Name = v1.00
2014-04-22 17:24:50:596 964 1a0c Report * Bios Release Date = 2008-08-06T00:00:00
2014-04-22 17:24:50:596 964 1a0c Report * Locale ID = 1033
2014-04-22 17:24:50:602 964 1a0c AU Successfully wrote event for AU health state:1
2014-04-22 17:24:50:602 964 1a0c AU Initializing featured updates
2014-04-22 17:24:50:602 964 1a0c AU Found 0 cached featured updates
2014-04-22 17:24:50:603 964 1a0c AU Successfully wrote event for AU health state:1
2014-04-22 17:24:50:603 964 1a0c AU Successfully wrote event for AU health state:1
2014-04-22 17:24:50:603 964 1a0c AU AU finished delayed initialization
2014-04-22 17:24:53:570 964 1a0c Agent *********** Agent: Refreshing global settings cache ***********
2014-04-22 17:24:53:571 964 1a0c Agent * WSUS server: http://cu57531sv1cyprs Opens a new window (Changed)
2014-04-22 17:24:53:571 964 1a0c Agent * WSUS status server: http://cu57531sv1cyprs Opens a new window (Changed)
2014-04-22 17:24:53:571 964 1a0c Agent * Target group: (Unassigned Computers) (Unchanged)
2014-04-22 17:24:53:571 964 1a0c Agent * Windows Update access disabled: No (Unchanged)
2014-04-22 17:24:53:571 964 1a0c AU AU received policy change subscription event
2014-04-22 17:24:53:571 964 1a0c AU Sus server changed through policy.
2014-04-22 17:24:53:571 964 1a0c AU AU Options changed from policy.
2014-04-22 17:24:53:572 964 1a0c AU Successfully wrote event for AU health state:1
2014-04-22 17:24:53:572 964 1a0c AU ########### AU: Policy change processed ###########
2014-04-22 17:24:53:572 964 1a0c AU # Policy changed, AU refresh required = No
2014-04-22 17:24:53:572 964 1a0c AU # WSUS server: http://cu57531sv1cyprs Opens a new window
2014-04-22 17:24:53:572 964 1a0c AU # Detection frequency: 22
2014-04-22 17:24:53:572 964 1a0c AU # Approval type: Scheduled (Policy)
2014-04-22 17:24:53:572 964 1a0c AU # Scheduled install day/time: Every day at 13:00
2014-04-22 17:24:53:572 964 1a0c AU # Auto-install minor updates: Yes (Policy)
2014-04-22 17:24:53:572 964 1a0c AU # Will interact with non-admins (Non-admins are elevated (Policy))
2014-04-22 17:24:53:572 964 1a0c AU AU Refresh required….
2014-04-22 17:24:53:573 964 1a0c AU AU setting next detection timeout to 2014-04-23 00:24:53
2014-04-22 17:24:53:574 964 1a0c AU AU setting next featured software notification timeout to 2014-04-23 00:24:53
2014-04-22 17:24:53:574 964 1a0c AU Successfully wrote event for AU health state:0
2014-04-22 17:24:53:574 964 1a0c AU Triggering Online detection (non-interactive)
2014-04-22 17:24:53:574 964 1a0c AU #############
2014-04-22 17:24:53:574 964 1a0c AU ## START ## AU: Search for updates
2014-04-22 17:24:53:574 964 1a0c AU #########
2014-04-22 17:24:53:579 964 1a0c AU <<## SUBMITTED ## AU: Search for updates [CallId = {AE8D134B-E13A-48D3-A066-6F624C3D2AB4}]
2014-04-22 17:24:53:580 964 1200 Agent *************
2014-04-22 17:24:53:580 964 1200 Agent ** START ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:24:53:580 964 1200 Agent *********
2014-04-22 17:24:53:580 964 1200 Agent * Online = Yes; Ignore download priority = No
2014-04-22 17:24:53:580 964 1200 Agent * Criteria = «IsInstalled=0 and DeploymentAction=’Installation’ or IsPresent=1 and DeploymentAction=’Uninstallation’ or IsInstalled=1 and DeploymentAction=’Installation’ and RebootRequired=1 or IsInstalled=0 and DeploymentAction=’Uninstallation’ and RebootRequired=1»
2014-04-22 17:24:53:580 964 1200 Agent * ServiceID = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7} Managed
2014-04-22 17:24:53:580 964 1200 Agent * Search Scope = {Machine}
2014-04-22 17:24:53:580 964 1200 Setup Checking for agent SelfUpdate
2014-04-22 17:24:53:581 964 1200 Setup Client version: Core: 7.6.7600.256 Aux: 7.6.7600.256
2014-04-22 17:25:04:405 964 1200 Misc Validating signature for C:WindowsSoftwareDistributionSelfUpdatewuident.cab:
2014-04-22 17:25:04:415 964 1200 Misc Microsoft signed: Yes
2014-04-22 17:25:04:415 964 1200 Misc WARNING: Digital Signatures on file C:WindowsSoftwareDistributionSelfUpdatewuident.cab are not trusted: Error 0x800b0001
2014-04-22 17:25:04:416 964 1200 Setup WARNING: SelfUpdate check failed to download package information, error = 0x800B0001
2014-04-22 17:25:04:416 964 1200 Setup FATAL: SelfUpdate check failed, err = 0x800B0001
2014-04-22 17:25:04:416 964 1200 Agent * WARNING: Skipping scan, self-update check returned 0x800B0001
2014-04-22 17:25:04:417 964 1200 Agent * WARNING: Exit code = 0x800B0001
2014-04-22 17:25:04:417 964 1200 Agent *********
2014-04-22 17:25:04:417 964 1200 Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:25:04:417 964 1200 Agent *************
2014-04-22 17:25:04:417 964 1200 Agent WARNING: WU client failed Searching for update with error 0x800b0001
2014-04-22 17:25:04:418 964 1608 AU >>## RESUMED ## AU: Search for updates [CallId = {AE8D134B-E13A-48D3-A066-6F624C3D2AB4}]
2014-04-22 17:25:04:418 964 1608 AU # WARNING: Search callback failed, result = 0x800B0001
2014-04-22 17:25:04:418 964 1608 AU # WARNING: Failed to find updates with error code 800B0001
2014-04-22 17:25:04:418 964 1608 AU #########
2014-04-22 17:25:04:418 964 1608 AU ## END ## AU: Search for updates [CallId = {AE8D134B-E13A-48D3-A066-6F624C3D2AB4}]
2014-04-22 17:25:04:418 964 1608 AU #############
2014-04-22 17:25:04:418 964 1608 AU Need to show Unable to Detect notification
2014-04-22 17:25:04:420 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:04:421 964 1608 AU AU setting next detection timeout to 2014-04-23 05:25:04
2014-04-22 17:25:04:423 964 1608 AU Setting AU scheduled install time to 2014-04-23 20:00:00
2014-04-22 17:25:04:424 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:04:424 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:04:433 964 1200 Report CWERReporter finishing event handling. (00000000)
2014-04-22 17:25:09:413 964 1200 Report REPORT EVENT: {622C5DC3-4ADC-43AC-BCE2-7E5A4D019980} 2014-04-22 17:25:04:416-0700 1 148 101 {D67661EB-2423-451D-BF5D-13199E37DF28} 1 800b0001 SelfUpdate Failure Software Synchronization Windows Update Client failed to detect with error 0x800b0001.
2014-04-22 17:25:09:423 964 1200 Report CWERReporter::HandleEvents — WER report upload completed with status 0x8
2014-04-22 17:25:09:423 964 1200 Report WER Report sent: 7.6.7600.256 0x800b0001 D67661EB-2423-451D-BF5D-13199E37DF28 Scan 101 Managed
2014-04-22 17:25:09:423 964 1200 Report CWERReporter finishing event handling. (00000000)
2014-04-22 17:25:16:695 964 1648 AU Triggering AU detection through DetectNow API
2014-04-22 17:25:16:695 964 1648 AU Triggering Online detection (non-interactive)
2014-04-22 17:25:16:695 964 1a0c AU #############
2014-04-22 17:25:16:695 964 1a0c AU ## START ## AU: Search for updates
2014-04-22 17:25:16:695 964 1a0c AU #########
2014-04-22 17:25:16:696 964 1a0c AU <<## SUBMITTED ## AU: Search for updates [CallId = {CCA946E6-39B7-4E15-B6D1-2CA6BAAB289F}]
2014-04-22 17:25:16:696 964 1200 Agent *************
2014-04-22 17:25:16:696 964 1200 Agent ** START ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:25:16:696 964 1200 Agent *********
2014-04-22 17:25:16:696 964 1200 Agent * Online = Yes; Ignore download priority = No
2014-04-22 17:25:16:696 964 1200 Agent * Criteria = «IsInstalled=0 and DeploymentAction=’Installation’ or IsPresent=1 and DeploymentAction=’Uninstallation’ or IsInstalled=1 and DeploymentAction=’Installation’ and RebootRequired=1 or IsInstalled=0 and DeploymentAction=’Uninstallation’ and RebootRequired=1»
2014-04-22 17:25:16:696 964 1200 Agent * ServiceID = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7} Managed
2014-04-22 17:25:16:697 964 1200 Agent * Search Scope = {Machine}
2014-04-22 17:25:16:697 964 1200 Setup Checking for agent SelfUpdate
2014-04-22 17:25:16:697 964 1200 Setup Client version: Core: 7.6.7600.256 Aux: 7.6.7600.256
2014-04-22 17:25:17:212 964 1200 Misc Validating signature for C:WindowsSoftwareDistributionSelfUpdatewuident.cab:
2014-04-22 17:25:17:227 964 1200 Misc Microsoft signed: Yes
2014-04-22 17:25:17:228 964 1200 Misc WARNING: Digital Signatures on file C:WindowsSoftwareDistributionSelfUpdatewuident.cab are not trusted: Error 0x800b0001
2014-04-22 17:25:17:228 964 1200 Setup WARNING: SelfUpdate check failed to download package information, error = 0x800B0001
2014-04-22 17:25:17:228 964 1200 Setup FATAL: SelfUpdate check failed, err = 0x800B0001
2014-04-22 17:25:17:229 964 1200 Agent * WARNING: Skipping scan, self-update check returned 0x800B0001
2014-04-22 17:25:17:231 964 1200 Agent * WARNING: Exit code = 0x800B0001
2014-04-22 17:25:17:231 964 1200 Agent *********
2014-04-22 17:25:17:231 964 1200 Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:25:17:231 964 1200 Agent *************
2014-04-22 17:25:17:231 964 1200 Agent WARNING: WU client failed Searching for update with error 0x800b0001
2014-04-22 17:25:17:231 964 1608 AU >>## RESUMED ## AU: Search for updates [CallId = {CCA946E6-39B7-4E15-B6D1-2CA6BAAB289F}]
2014-04-22 17:25:17:232 964 1608 AU # WARNING: Search callback failed, result = 0x800B0001
2014-04-22 17:25:17:232 964 1608 AU # WARNING: Failed to find updates with error code 800B0001
2014-04-22 17:25:17:232 964 1608 AU #########
2014-04-22 17:25:17:232 964 1608 AU ## END ## AU: Search for updates [CallId = {CCA946E6-39B7-4E15-B6D1-2CA6BAAB289F}]
2014-04-22 17:25:17:232 964 1608 AU #############
2014-04-22 17:25:17:232 964 1608 AU Need to show Unable to Detect notification
2014-04-22 17:25:17:233 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:17:233 964 1608 AU AU setting next detection timeout to 2014-04-23 05:25:17
2014-04-22 17:25:17:233 964 1608 AU Setting AU scheduled install time to 2014-04-23 20:00:00
2014-04-22 17:25:17:234 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:17:235 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:20:500 964 1da4 AU Triggering AU detection through DetectNow API
2014-04-22 17:25:20:500 964 1da4 AU Triggering Online detection (interactive)
2014-04-22 17:25:20:501 964 1a0c AU #############
2014-04-22 17:25:20:501 964 1a0c AU ## START ## AU: Search for updates
2014-04-22 17:25:20:501 964 1a0c AU #########
2014-04-22 17:25:20:502 964 1a0c AU <<## SUBMITTED ## AU: Search for updates [CallId = {2C64103F-3D49-4DE3-AE71-44284A3BB9C1}]
2014-04-22 17:25:20:502 964 1200 Agent *************
2014-04-22 17:25:20:502 964 1200 Agent ** START ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:25:20:502 964 1200 Agent *********
2014-04-22 17:25:20:502 964 1200 Agent * Online = Yes; Ignore download priority = No
2014-04-22 17:25:20:502 964 1200 Agent * Criteria = «IsInstalled=0 and DeploymentAction=’Installation’ or IsPresent=1 and DeploymentAction=’Uninstallation’ or IsInstalled=1 and DeploymentAction=’Installation’ and RebootRequired=1 or IsInstalled=0 and DeploymentAction=’Uninstallation’ and RebootRequired=1»
2014-04-22 17:25:20:502 964 1200 Agent * ServiceID = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7} Managed
2014-04-22 17:25:20:502 964 1200 Agent * Search Scope = {Machine}
2014-04-22 17:25:20:502 964 1200 Setup Checking for agent SelfUpdate
2014-04-22 17:25:20:503 964 1200 Setup Client version: Core: 7.6.7600.256 Aux: 7.6.7600.256
2014-04-22 17:25:21:039 964 1200 Misc Validating signature for C:WindowsSoftwareDistributionSelfUpdatewuident.cab:
2014-04-22 17:25:21:051 964 1200 Misc Microsoft signed: Yes
2014-04-22 17:25:21:051 964 1200 Misc WARNING: Digital Signatures on file C:WindowsSoftwareDistributionSelfUpdatewuident.cab are not trusted: Error 0x800b0001
2014-04-22 17:25:21:051 964 1200 Setup WARNING: SelfUpdate check failed to download package information, error = 0x800B0001
2014-04-22 17:25:21:051 964 1200 Setup FATAL: SelfUpdate check failed, err = 0x800B0001
2014-04-22 17:25:21:052 964 1200 Agent * WARNING: Skipping scan, self-update check returned 0x800B0001
2014-04-22 17:25:21:052 964 1200 Agent * WARNING: Exit code = 0x800B0001
2014-04-22 17:25:21:052 964 1200 Agent *********
2014-04-22 17:25:21:052 964 1200 Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates]
2014-04-22 17:25:21:052 964 1200 Agent *************
2014-04-22 17:25:21:052 964 1200 Agent WARNING: WU client failed Searching for update with error 0x800b0001
2014-04-22 17:25:21:052 964 1608 AU >>## RESUMED ## AU: Search for updates [CallId = {2C64103F-3D49-4DE3-AE71-44284A3BB9C1}]
2014-04-22 17:25:21:052 964 1608 AU # WARNING: Search callback failed, result = 0x800B0001
2014-04-22 17:25:21:052 964 1608 AU # WARNING: Failed to find updates with error code 800B0001
2014-04-22 17:25:21:053 964 1608 AU #########
2014-04-22 17:25:21:053 964 1608 AU ## END ## AU: Search for updates [CallId = {2C64103F-3D49-4DE3-AE71-44284A3BB9C1}]
2014-04-22 17:25:21:053 964 1608 AU #############
2014-04-22 17:25:21:053 964 1608 AU Need to show Unable to Detect notification
2014-04-22 17:25:21:053 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:21:053 964 1608 AU AU setting next detection timeout to 2014-04-23 05:25:21
2014-04-22 17:25:21:053 964 1608 AU Setting AU scheduled install time to 2014-04-23 20:00:00
2014-04-22 17:25:21:053 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:21:054 964 1608 AU Successfully wrote event for AU health state:1
2014-04-22 17:25:22:228 964 1200 Report REPORT EVENT: {F99BD9C4-6A30-4F26-91DC-348AD3BED509} 2014-04-22 17:25:17:228-0700 1 148 101 {D67661EB-2423-451D-BF5D-13199E37DF28} 1 800b0001 SelfUpdate Failure Software Synchronization Windows Update Client failed to detect with error 0x800b0001.
2014-04-22 17:25:22:229 964 1200 Report REPORT EVENT: {C0AC6ABB-E093-4C67-8C09-BC5B37F79753} 2014-04-22 17:25:21:051-0700 1 148 101 {D67661EB-2423-451D-BF5D-13199E37DF28} 1 800b0001 SelfUpdate Failure Software Synchronization Windows Update Client failed to detect with error 0x800b0001.
2014-04-22 17:25:22:244 964 1200 Report CWERReporter::HandleEvents — WER report upload completed with status 0x8
2014-04-22 17:25:22:244 964 1200 Report WER Report sent: 7.6.7600.256 0x800b0001 D67661EB-2423-451D-BF5D-13199E37DF28 Scan 101 Managed
2014-04-22 17:25:22:261 964 1200 Report CWERReporter::HandleEvents — WER report upload completed with status 0x8
2014-04-22 17:25:22:261 964 1200 Report WER Report sent: 7.6.7600.256 0x800b0001 D67661EB-2423-451D-BF5D-13199E37DF28 Scan 101 Managed
2014-04-22 17:25:22:261 964 1200 Report CWERReporter finishing event handling. (00000000)
Эта статья объединяет известные мне способы починки агента WSUS.
Ранее, я уже писал, как сверить список компьютеров, которые есть в AD с теми, которые есть во WSUS. Если эти списки не совпадают, то у вас проблема и часть компьютеров не обновляется.
В самом простом случае, вы забыли сделать групповую политику, которая настраивает клиентские компьютеры и серверы на обновление со WSUS, или сконфигурировали ее так, что она не применяется. Ручная настройка параметров через gpedit.msc тоже допустима, но только для тех компьютеров, которые не входят в домен.
Итак, политика применяется, но все равно компьютер не обновляется. Что делать и как лечить?
Если у вас Windows Vista, Windows Server 2008, Windows 7 или Windows Server 2008 R2, то самым первым способом будет скачать с сайта Microsoft утилиту System Update Readiness Tool и запустить ее. Если это не поможет, то нижу приведены различные способы, которые могут помочь вам восстановить работоспособность.
На серверах Windows Server 2008 R2 и Windows Server 2008 стала проявляться следующая проблема. Windows Update показывает, что нужно обновить агента:
Install new Windows Update software
Мы пытаемся это сделать, но в результате получаем ошибку:
Error Code 80070005
В логе %systemroot%WindowsUpdate.log обнаружтваются следующие сообщения:
2012-06-20 14:04:12:198 912 698 Setup FATAL: WuSetupV.exe process ended prematurely, err = 0x80070005
2012-06-20 14:04:12:198 912 698 Setup WARNING: SelfUpdate install failed, error = 0x80070005
2012-06-20 14:04:17:166 912 b54 Report REPORT EVENT: {857B6F41-5A79-470E-9DCA-7749D23682E6} 2012-06-20 14:04:12:198+0300 1 182 101 {61CA813A-7585-442E-A66B-B0D15CE6BDC0} 1 80070005 SelfUpdate Failure Content Install Installation Failure: Windows failed to install the following update with error 0x80070005: Windows Update Setup Handler.
2012-06-20 14:04:17:182 912 b54 Report CWERReporter::HandleEvents — WER report upload completed with status 0x8
2012-06-20 14:04:17:182 912 b54 Report WER Report sent: 7.5.7601.17514 0x80070005 61CA813A-7585-442E-A66B-B0D15CE6BDC0 Install 101 Managed
2012-06-20 14:04:17:182 912 b54 Report CWERReporter finishing event handling. (00000000)
WARNING: WU client fails CClientCallRecorder::RemoveService with error 0x80248014
2012-06-21 12:06:26:649 3020 13ec Setup Performing SelfUpdate installation
2012-06-21 12:06:26:665 3020 13ec Setup WARNING: Failed to stop the WU service, error = 0x80070005
2012-06-21 12:06:26:665 3020 13ec Setup WuSetup has finished. Exit code is 0x00000005
2012-06-21 12:06:26:665 968 f84 Setup FATAL: WuSetupV.exe process ended prematurely, err = 0x80070005
2012-06-21 12:06:26:665 968 f84 Setup WARNING: SelfUpdate install failed, error = 0x80070005
Следует проверить разрешения в групповой политике для сервиса «Windows Updates”
Startup Mode: Automatic и разрешения:
Type Name Permission
Allow Everyone Read, Delete
Allow Everyone Change template, Start, Stop, Pause and continue
Если установка таких разрешений не принесет результата, попробуйте следующий вариант:
a) Поменять параметры для “Windows Updates» сервиса в «not defined» и для старта и разрешения
b) Удалить ключ в реестре:
HKLMSYSTEMCurrentControlSetServiceswuauservSecurity
После следующего обновления групповой политики проблема должна устраниться. gpupdate /force
Для простоты, для следующих способов, выкладываю все эти скрипты в уже готовом виде: Wsus-fix
1. Первый скрипт самый простой, и, на самом деле, даже не для лечения используется, а для того, чтобы принудительно запустить проверку на обновление, ну и, заодно, чистит папку, в которой накапливаются дистрибутивы уже установленных обновлений:
wsus_detect_manual.cmd
net stop wuauserv && net stop bits && net stop cryptsvc
del /f /s /q %windir%SoftwareDistributiondownload*.*
net start wuauserv && net start bits && net start cryptsvc
wuauclt.exe /detectnow exit
2. Второй скрипт нужен для того, чтобы “оживить” неработающий сервис WSUS. В нем идет чистка от старых обновлений, после чего папки SoftwareDistribution и Catroot2 переименовываются, что при перезапуске сервиса приведет к их пересозданию. Затем системные dll библиотеки перерегистрируются.
fix_wsus_service.cmd
net stop bits
net stop wuauserv
net stop cryptsvc
del /f /s /q %windir%SoftwareDistributiondownload*.*
ren %systemroot%System32Catroot2 Catroot2.old
ren %systemroot%SoftwareDistribution SoftwareDistribution.old
REM del /f /s /q %windir%SoftwareDistribution*.*
del /f /s /q %windir%windowsupdate.log
%windir%system32regsvr32.exe /U /s %windir%system32vbscript.dll
%windir%system32regsvr32.exe /U /s %windir%system32mshtml.dll
%windir%system32regsvr32.exe /U /s %windir%system32msjava.dll
%windir%system32regsvr32.exe /U /s %windir%system32msxml.dll
%windir%system32regsvr32.exe /U /s %windir%system32actxprxy.dll
%windir%system32regsvr32.exe /U /s %windir%system32shdocvw.dll
%windir%system32regsvr32.exe /U /s %windir%system32Mssip32.dll
%windir%system32regsvr32.exe /U /s %windir%system32wintrust.dll
%windir%system32regsvr32.exe /U /s %windir%system32initpki.dll
%windir%system32regsvr32.exe /U /s %windir%system32dssenh.dll
%windir%system32regsvr32.exe /U /s %windir%system32rsaenh.dll
%windir%system32regsvr32.exe /U /s %windir%system32gpkcsp.dll
%windir%system32regsvr32.exe /U /s %windir%system32sccbase.dll
%windir%system32regsvr32.exe /U /s %windir%system32slbcsp.dll
%windir%system32regsvr32.exe /U /s %windir%system32cryptdlg.dll
%windir%system32regsvr32.exe /U /s %windir%system32Urlmon.dll
%windir%system32regsvr32.exe /U /s %windir%system32Oleaut32.dll
%windir%system32regsvr32.exe /U /s %windir%system32msxml2.dll
%windir%system32regsvr32.exe /U /s %windir%system32Browseui.dll
%windir%system32regsvr32.exe /U /s %windir%system32shell32.dll
%windir%system32regsvr32.exe /U /s %windir%system32Mssip32.dll
%windir%system32regsvr32.exe /U /s %windir%system32atl.dll
%windir%system32regsvr32.exe /U /s %windir%system32jscript.dll
%windir%system32regsvr32.exe /U /s %windir%system32msxml3.dll
%windir%system32regsvr32.exe /U /s %windir%system32softpub.dll
%windir%system32regsvr32.exe /U /s %windir%system32wuapi.dll
%windir%system32regsvr32.exe /U /s %windir%system32wuaueng.dll
%windir%system32regsvr32.exe /U /s %windir%system32wuaueng1.dll
%windir%system32regsvr32.exe /U /s %windir%system32wucltui.dll
%windir%system32regsvr32.exe /U /s %windir%system32wups.dll
%windir%system32regsvr32.exe /U /s %windir%system32wups2.dll
%windir%system32regsvr32.exe /U /s %windir%system32wuweb.dll
%windir%system32regsvr32.exe /s %windir%system32vbscript.dll
%windir%system32regsvr32.exe /s %windir%system32mshtml.dll
%windir%system32regsvr32.exe /s %windir%system32msjava.dll
%windir%system32regsvr32.exe /s %windir%system32msxml.dll
%windir%system32regsvr32.exe /s %windir%system32actxprxy.dll
%windir%system32regsvr32.exe /s %windir%system32shdocvw.dll
%windir%system32regsvr32.exe /s %windir%system32Mssip32.dll
%windir%system32regsvr32.exe /s %windir%system32wintrust.dll
%windir%system32regsvr32.exe /s %windir%system32initpki.dll
%windir%system32regsvr32.exe /s %windir%system32dssenh.dll
%windir%system32regsvr32.exe /s %windir%system32rsaenh.dll
%windir%system32regsvr32.exe /s %windir%system32gpkcsp.dll
%windir%system32regsvr32.exe /s %windir%system32sccbase.dll
%windir%system32regsvr32.exe /s %windir%system32slbcsp.dll
%windir%system32regsvr32.exe /s %windir%system32cryptdlg.dll
%windir%system32regsvr32.exe /s %windir%system32Urlmon.dll
%windir%system32regsvr32.exe /s %windir%system32Oleaut32.dll
%windir%system32regsvr32.exe /s %windir%system32msxml2.dll
%windir%system32regsvr32.exe /s %windir%system32Browseui.dll
%windir%system32regsvr32.exe /s %windir%system32shell32.dll
%windir%system32regsvr32.exe /s %windir%system32Mssip32.dll
%windir%system32regsvr32.exe /s %windir%system32atl.dll
%windir%system32regsvr32.exe /s %windir%system32jscript.dll
%windir%system32regsvr32.exe /s %windir%system32msxml3.dll
%windir%system32regsvr32.exe /s %windir%system32softpub.dll
%windir%system32regsvr32.exe /s %windir%system32wuapi.dll
%windir%system32regsvr32.exe /s %windir%system32wuaueng.dll
%windir%system32regsvr32.exe /s %windir%system32wuaueng1.dll
%windir%system32regsvr32.exe /s %windir%system32wucltui.dll
%windir%system32regsvr32.exe /s %windir%system32wups.dll
%windir%system32regsvr32.exe /s %windir%system32wups2.dll
%windir%system32regsvr32.exe /s %windir%system32wuweb.dll
net start bits
net start wuauserv
net start cryptsvc
wuauclt /detectnow
exit
3. Этот скрипт применяется в тех случаях, когда компьютер был недавно клонирован, или в тех, когда регистрации в WSUS у компьютера так и не произошло. Он отличается от предыдущего только предпоследней строчкой, в которой производится обнуление авторизации с перегенерацией идентификатора. Приведу только эту строчку:
wsus_resetaut_detect_manual.cmd
wuauclt.exe /resetauthorization /detectnow
4. Если нужно просто обнулить авторизацию, то можно воспользоваться конструкцией из предыдущего скрипта. Практика показала, что еще лучше удалять лишние ключи из реестра, для чего мы используем следующий скрипт
AU_Clean_SID.cmd
@echo on
net stop wuauserv
REG DELETE «HKLMSOFTWAREMicrosoftWindowsCurrentVersionWindowsUpdate» /v AccountDomainSid /f
REG DELETE «HKLMSOFTWAREMicrosoftWindowsCurrentVersionWindowsUpdate» /v PingID /f
REG DELETE «HKLMSOFTWAREMicrosoftWindowsCurrentVersionWindowsUpdate» /v SusClientId /f
net start wuauserv
wuauclt /resetauthorization /detectnow
5. Иногда, для того, чтобы все заработало нужно переустановить агента WSUS. Вначале нужно скачать latest Windows Update Agent, ну а затем установить соответствующую редакцию
для x32 версий Windows
windowsupdateagent30-x86.exe /wuforce
для x64 версий Windows
windowsupdateagent30-x64.exe /wuforce
Если вы счастливый обладатель Itanium – догадаетесь сами 
После установки агента нужно обязательно перезагрузиться.
6. Для “лечения” ошибок 0x80070005, т.е. ошибок доступа может пригодиться нижеприведенный скрипт. Он восстанавливает доступы для администраторов и системы к реестру и системным папкам.
Для выполнения этого скрипта понадобится майкрософтовская утилита subinacl.exe. Она входит в resource kit для Windows Server 2003, но пользоваться той версией, что входит туда не стоит, т.к. там неприятные ошибки. Следует скачать subinacl.exe версии 5.2.3790.1180.
Restore_registry_and_system_permission.cmd
@echo off
REM Применять при ошибках 0x80070005 Windows Update
subinacl /subkeyreg HKEY_LOCAL_MACHINE /grant=administrators=f
subinacl /subkeyreg HKEY_CURRENT_USER /grant=administrators=f
subinacl /subkeyreg HKEY_CLASSES_ROOT /grant=administrators=f
subinacl /subdirectories %SystemDrive% /grant=administrators=f
subinacl /subkeyreg HKEY_LOCAL_MACHINE /grant=system=f
subinacl /subkeyreg HKEY_CURRENT_USER /grant=system=f
subinacl /subkeyreg HKEY_CLASSES_ROOT /grant=system=f
subinacl /subdirectories %SystemDrive% /grant=system=f
Скрипт был найден в статье базы знаний Microsoft
Все эти скрипты можно выполнять практически автоматически, в случае возникновения проблем. Если в результате проблема таки не решена, то приходится разбираться уже плотнее. И тут нам пригодится тот самый windowsupdate.log, который лежит в корне папки Windows. Если компьютер проблемный, то файл этот большого размера. Для простоты, желательно его удалить перед тем как запускать скрипты. Почти во всех скриптах предусмотрена команда его удаления, но не все так просто. Не смотря на остановку сервиса wuauserv, обычно, его продолжают держать открытые IE и т.п. Поэтому, есть хитрый способ. Запускаю
notepad.exe %windir%windowsupdate.log
Выделяю весь текст, удаляю его и сохраняю вместо старого файла (не забыть в диалоге сохранения поменять тип файла на *.*, а то по умолчанию – *.txt)
Итак, вернемся к логу, коды ошибок WSUS 3 могут помочь в разбирательстве.
Одна из распространенных проблем со wsus клиентом на серверах может заключаться в том, что сам сервис может подключаться к WSUS через прокси, а этого не нужно и наоборот. Манипулировать этим поведением можно с помощью команды proxycfg
Доступ без прокси: proxycfg –d
Доступ через прокси с опциональным указанием байпас листа: proxycfg –d
Проимпортировать пользовательские настройки: proxycfg –u
В новых версиях Windows используется другой способ — Настройка прокси для сервисов на Windows 7/Windows Server 2008
Стоит заметить, что есть случаи, когда заставить клиента обновляться со wsus так и не получается. У меня есть прецеденты с парочкой Windows Server 2003 R2, которые мне побороть так и не удалось. Поэтому я их обновляю через интернет 
Свежие операционные системы типа Windows 7, Windows 2008 иногда “заводятся” с трудом. Для таких случаев, эмпирическим путем, был найден алгоритм типа:
1. Обновляемся первый раз с сайта microsoft с обновлением агента
2. Потом обновляем агента уже локально
3. А потом все начинает работать
Надеюсь, что плоды наших трудов кому-нибудь помогут.
Для простоты, выкладываю все эти скрипты в уже готовом виде: Wsus-fix
Let’s see how you can FIX SCCM Task Sequence has failed with the error code 0x800700A1. You might encounter a prompt error message while performing Operating System Deployment with SCCM Task Sequence. The error 0x800700A1 translates “The specified path is invalid.”. This is often seen when you will perform the deployment in new machines.
Being an IT admin, we keep used to replacing an HDD on a machine and perform the deployment most of the time. In this scenario, the error code 0x800700A1 has been noticed as well.
0x800700A1 means BAD_PATHNAME. The reason you get this error is if the task sequence cannot find the path because the drive is RAW. In this case, it’s always recommended to format the disk partition before deploying Windows Image to help us avoid unwanted issues.
Issue Summary
This error occurs when attempting to run an operating system deployment task sequence and in a step, it attempted to copy the files to the local hard drive but cannot find the path as the drive is in RAW state.
Task Sequence Error: Task Sequence has failed with the error code 0x800700A1 in the task sequence step. For more information, contact your system administrator or helpdesk operator.
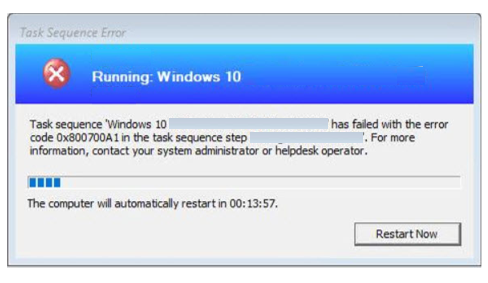
It’s always recommended to examine the SMSTS log for task sequence failure issues to help you get the inside about the failure prompt to troubleshoot the task sequence error. Most importantly, to be aware of the location of the SMSTS log during SCCM OSD process. More you can explore SCCM OSD Task Sequence Troubleshooting Steps by Step Ultimate Guide SMSTS.log.
Here are the highlights the Task sequence has failed with the error code 0x800700A1 from the SMSTS.log.
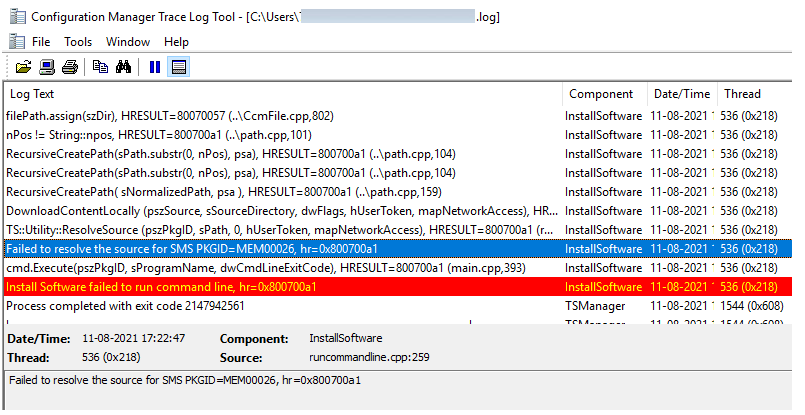
Failed to resolve the source for SMS PKGID=MEM00026, hr=0x800700a1 InstallSoftware 11-08-2021 17:22:47 536 (0x0218)
Install Software failed to run command line, hr=0x800700a1
Process completed with exit code 2147942561
The execution of the group (Install Operating System) has failed and the execution has been aborted. An action failed. Error 0x80004004
Failed to run the last action: Decrypt Drive. Result -2147024735. Execution of task sequence failed.
To fix this issue, The drive needs to be formatted before continuing with the task sequence. Let’s follow the steps below to format the hard drive –
If you’re already in the error windows screen Task sequence has failed with the error code 0x800700A1, Press F8 to launch the command prompt window or Restart the machine and boot with the same task sequence.
Important – Enable command support (F8) that is not recommended for production use. You can explore the available command prompt support option in Boot Image.
The diskpart command interpreter helps you manage your computer’s drives (disks, partitions, volumes, or virtual hard disks), Type the following commands in the command prompt –
Diskpart
List disk (Displays all the disks on the device)
Select disk 0
Clean (Wipes the disk)
Create partition primary (Creates windows partition)
Select partition 1
Format quick fs=NTFS (Format primary partition)
Assign letter C
ExitDisclaimer – The information provided on site is for general informational purposes only. All information on the site is provided in good faith, however, we make no representation or warranty of any kind, express or implied regarding the accuracy, adequacy, validity, reliability, availability, or completeness of any information on the website.
Once you are done with the above steps, Restart the target machine and reinitiate the task sequence deployment, It should continue without any errors.
About Author -> Jitesh has over 5 years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus area is Windows 10 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
Resources
- OSD Known Issues Troubleshooting Guide |SCCM |ConfigMgr
- ConfigMgr OSD Troubleshooting Known Issues Guide Part 2 | SCCM
- FIX: SCCM Task Sequence Failed to load class properties 0x80041002 (2147749890)
- SCCM Deployment Failed to Resolve Task Sequence Dependencies 0X80040102



