Содержание
- Troubleshooting SSL related issues (Server Certificate)
- Tools Used in this Troubleshooter:
- Overview
- Scenarios
- Scenario 1
- Scenario 2
- Scenario 3
- Scenario 4
- Scenario 5
- Scenario 6
- Troubleshooting SSL related issues (Server Certificate)
- Tools Used in this Troubleshooter:
- Overview
- Scenarios
- Scenario 1
- Scenario 2
- Scenario 3
- Scenario 4
- Scenario 5
- Scenario 6
Tools Used in this Troubleshooter:
This material is provided for informational purposes only. Microsoft makes no warranties, express or implied.
Overview
This document will help you in troubleshooting SSL issues related to IIS only. Client Certificates troubleshooting will not be covered in this document. Server Certificates are meant for Server Authentication and we will be dealing only with Server Certificates in this document.
If the Client certificates section is set to «Require» and then you run into issues, then please don’t refer this document. This is meant for troubleshooting SSL Server certificates issue only.
It is important to know that every certificate comprises of a public key (used for encryption) and a private key (used for decryption). The private key is known only to the server.
The default port for https is 443.
I am under the assumption the reader is well-versed in SSL Handshake and the Server Authentication process during the SSL handshake.
Description of the Secure Sockets Layer (SSL) Handshake:
Description of the Server Authentication Process during the SSL Handshake:
Scenarios
The following error message is seen while browsing the website over https:
The first thing that has to be checked is whether the website is accessible over http. If it is not, there likely is a separate issue not covered here. You will need to have the website working on http first before continuing with this troubleshooter.
Now let’s assume the website is accessible over http and we get the above error when trying to browse over https. The problem is seen because the SSL handshake failed and hence the error message was seen. There could be many reasons. We will follow a step-by-step approach to solve this problem.
Scenario 1
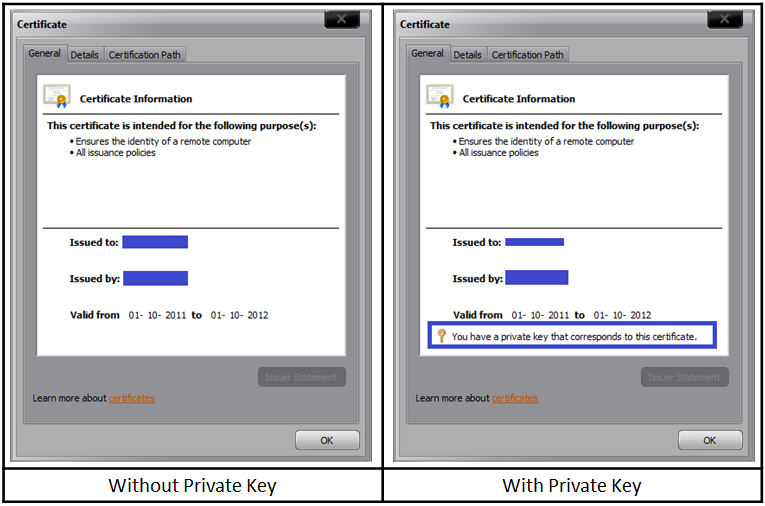
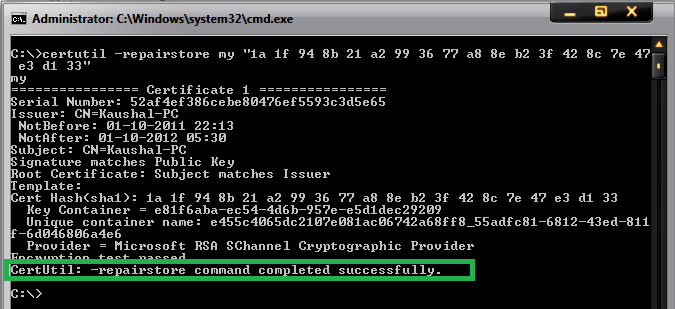
Check if the server certificate has the private key corresponding to it. Refer the below picture:
If private key is missing, then you need to get a certificate containing the private key, which is essentially a .PFX file. There is a command that we could try to run in order to associate the private key with the certificate:
If the association is successful, then you would see the following window:
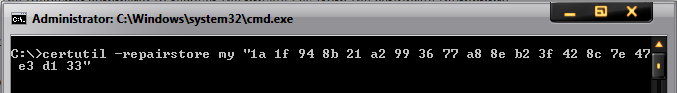
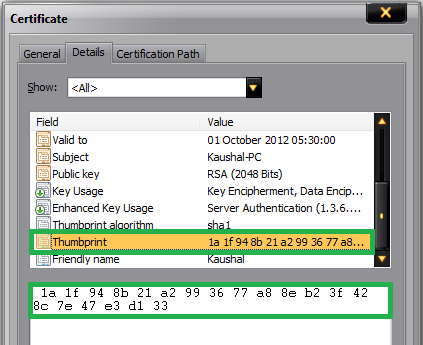
Note: 1a 1f 94 8b 21 a2 99 36 77 a8 8e b2 3f 42 8c 7e 47 e3 d1 33 is the thumbprint of the certificate. Open the certificate and click on the details tab. Scroll down to find the thumbprint section. Select the thumbprint section and click on the text below. Do a «Ctrl+A» and then «Ctrl+C» to select and copy it. Below is a snapshot for your reference:
Note: This command doesn’t succeed always. If this fails, then you need to get a certificate containing the private key from the CA. The file extension for a certificate containing private key is .pfx.
Scenario 2
We went pass the first hurdle and now we have a server certificate containing the private key installed on the website. However, we still get the same error as above. The website is still not accessible over https.
The SSLDiag tool comes in handy here.
Windows Server 2003:
Download X64 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=5329 )
Download X86 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=674 )
For IIS 7 and IIS 7.5, use vijaysk’s SSL Diagnostics tool. Below is the link:
Install the tool and run it on the server. If you have a certificate containing private key and still not able to access the website, then you may want to run this tool or check the system event logs for SChannel related warnings/errors.
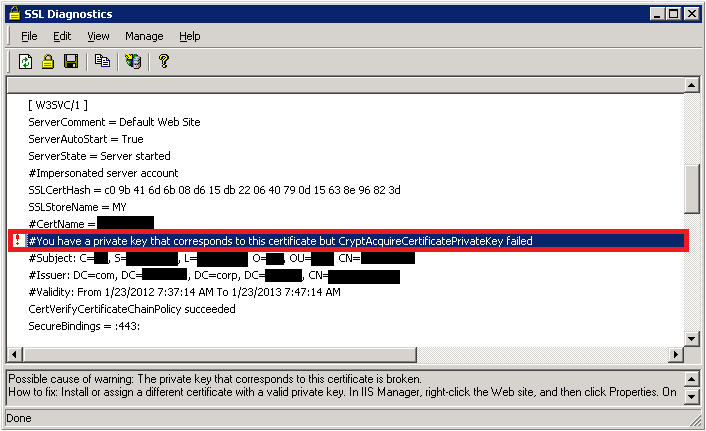
While running the SSLDiag tool you may get the following error:
You have a private key that corresponds to this certificate but CryptAcquireCertificatePrivateKey failed
There will also be a SChannel warning in the system event logs as shown below:
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| Description: A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x80090016. |
This event/error indicates that there was a problem acquiring certificate’s private key. So let’s try the below steps one by one:
Firstly, verify the permissions on the machinekeys folder as per the KB Article: https://support.microsoft.com/kb/278381. All the private keys are stored within the machinekeys folder, so we need to ensure that we have necessary permissions.
If the permissions are in place and if the issue is still not fixed. Then it must be a problem with the certificate. It may have been corrupted (You may see an error code of 0x8009001a in the SChannel event log).
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x8009001a. |
We will test if the website works with a test certificate. Take a back-up of the existing certificate and then replace it with a self-signed certificate. Try accessing the website via https. If it works then the certificate used earlier was corrupted and it has to be replaced with a new working certificate.
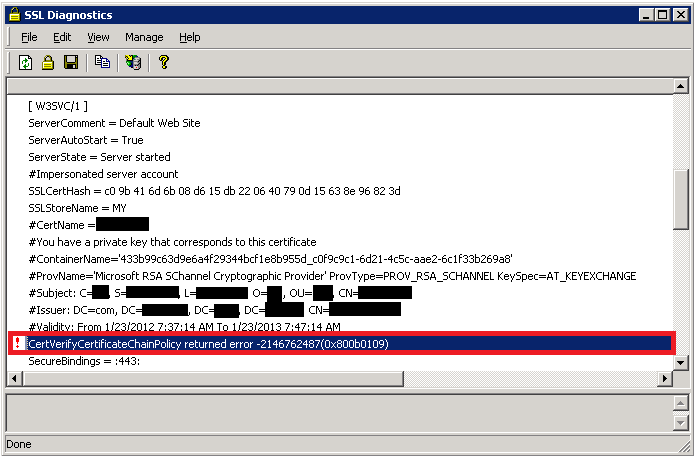
Sometimes the problem may not be with the certificate but with the issuer. You may see the following error in SSLDiag:
CertVerifyCertificateChainPolicy will fail with CERT_E_UNTRUSTEDROOT (0x800b0109), if the root CA certificate is not trusted root.
To fix this add the CA’s certificate to the «Trusted Root CA» store under My computer account on the server.
You may also get the following error:
CertVerifyCertificateChainPolicy returned error -2146762480(0x800b0110).
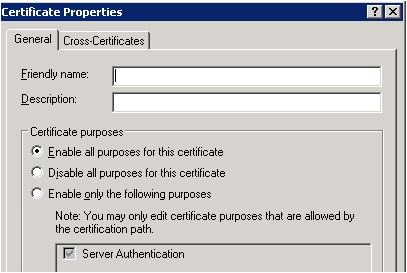
If the above error is received then we need to check the usage type of the certificate. Open the certificate, click on the «Details» tab and then click on «Edit Properties…» button. Under General tab make sure «Enable all purposes for this certificate» is selected and most importantly «Server Authentication» should be present in the list.
Scenario 3
The first 2 steps check the integrity of the certificate. Once we have confirmed that there are no issues with the certificate, a big problem is solved. But, what if the website is still not accessible over https. Check the HTTPS bindings of the website and determine what port and IP it is listening on. You could run the following command to ensure no other process is listening on the SSL port used by the website.
If there is another process listening on that port then check why that process is consuming that port. Try changing the IP-Port combination to check if the website is accessible or not.
Scenario 4
By now we are sure that we have a proper working certificate installed on the website and there is no other process using the SSL port for this website. However, I still get «Page cannot be displayed» error while accessing over https. When a client connects and initiates an SSL negotiation, HTTP.sys looks in its SSL configuration for the «IP:Port» pair to which the client connected. The HTTP.sys SSL configuration must include a certificate hash and the name of the certificate store before the SSL negotiation will succeed. The problem may be with the HTTP.SYS SSL Listener.
The Certificate hash registered with HTTP.SYS may be NULL or it may contain invalid GUID. Execute the following from a command prompt:
httpcfg is part of Windows Support tools and is present on the installation disk. You could download it from here as well: https://www.microsoft.com/download/en/details.aspx?id=7911
Below is a sample of a working and non-working scenario:
Working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
Non-working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | c09b416d6b 8d615db22 64079d15638e96823d |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
The Hash value seen above is the Thumbprint of your SSL certificate. Notice, that the Guid is all zero in a non-working scenario. You may see the Hash either having some value or blank. Even if we remove the certificate from the web site, and then run «httpcfg query ssl», the website will still list Guid as all 0’s. If you see the GUID as «<0000. 000>, then there is a problem.
We need to remove this entry by running the command:
Delete any entries in the IP Listen list.
To determine whether any IP addresses are listed, open a command prompt, and then run the following command:
If the IP Listen list is empty, the command returns the following string:
If the command returns a list of IP addresses, remove each IP address in the list by using the following command:
restart IIS after this via command «net stop http /y»
Scenario 5
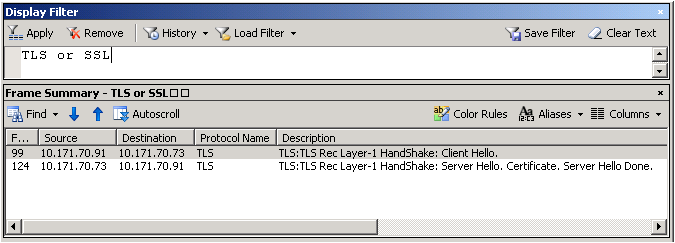
After all this if you are still unable to browse the website on https, then capture a network trace either from the client or server. Filter the trace by «SSL or TLS» to look at SSL traffic.
Below is a network trace snapshot of a non-working scenario:
Well, this is definitely now how you look at a network trace. You need to expand the frame details and see what protocol and cipher was chosen by the server. Select «Server Hello» from the description to get those details.
In the non-working scenario, the client was configured to use TLS 1.1 and TLS 1.2 only. However, the web server was IIS 6, which can support until TLS 1.0 and hence the handshake failed.
Do check the registry keys to determine what protocols are enabled or disabled. Here’s the path:
The «Enabled» DWORD should be set to «1». If «0» then the protocol is disabled.
For example, SSL 2.0 is disabled by default.
Scenario 6
If everything has been verified and if you are still running into issues accessing the website over https, then it most likely is some update which is causing the SSL handshake to fail.
Microsoft has released an update to the implementation of SSL in Windows:
There is potential for this update to impact customers using Internet Explorer, or using an application that uses Internet Explorer to perform HTTPS requests.
There were actually two changes made to address information disclosure vulnerability in SSL 3.0 / TLS 1.0. The MS12-006 update implements a new behavior in schannel.dll, which sends an extra record while using a common SSL chained-block cipher, when clients request that behavior. The other change was in Wininet.dll, part of the December Cumulative Update for Internet Explorer (MS11-099), so that IE will request the new behavior.
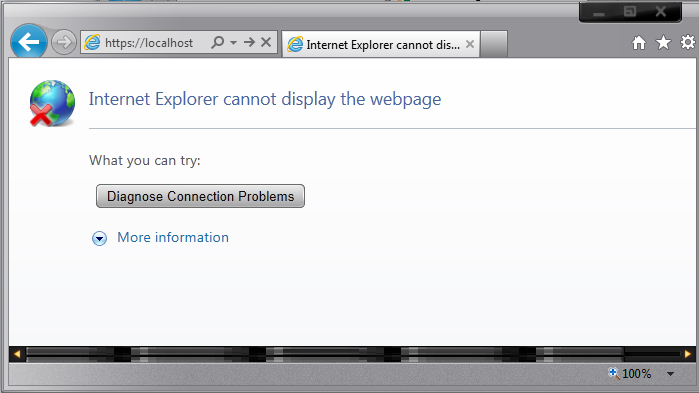
If a problem exists, it may manifest as a failure to connect to a server, or an incomplete request. Internet Explorer 9 is able to display an «Internet Explorer cannot display the webpage» error. Prior versions of IE may simply display a blank page.
Fiddler does not use the extra record when it captures and forwards HTTPS requests to the server. Therefore, if Fiddler is used to capture HTTPS traffic, the requests will succeed.
Registry keys
As documented in https://support.microsoft.com/kb/2643584, there is a SendExtraRecord registry value, which can:
- Globally disable the new SSL behavior
- Globally enable it, or
- (Default) enable it for SChannel clients that opt in to the new behavior.
Источник
Tools Used in this Troubleshooter:
This material is provided for informational purposes only. Microsoft makes no warranties, express or implied.
Overview
This document will help you in troubleshooting SSL issues related to IIS only. Client Certificates troubleshooting will not be covered in this document. Server Certificates are meant for Server Authentication and we will be dealing only with Server Certificates in this document.
If the Client certificates section is set to «Require» and then you run into issues, then please don’t refer this document. This is meant for troubleshooting SSL Server certificates issue only.
It is important to know that every certificate comprises of a public key (used for encryption) and a private key (used for decryption). The private key is known only to the server.
The default port for https is 443.
I am under the assumption the reader is well-versed in SSL Handshake and the Server Authentication process during the SSL handshake.
Description of the Secure Sockets Layer (SSL) Handshake:
Description of the Server Authentication Process during the SSL Handshake:
Scenarios
The following error message is seen while browsing the website over https:
The first thing that has to be checked is whether the website is accessible over http. If it is not, there likely is a separate issue not covered here. You will need to have the website working on http first before continuing with this troubleshooter.
Now let’s assume the website is accessible over http and we get the above error when trying to browse over https. The problem is seen because the SSL handshake failed and hence the error message was seen. There could be many reasons. We will follow a step-by-step approach to solve this problem.
Scenario 1
Check if the server certificate has the private key corresponding to it. Refer the below picture:
If private key is missing, then you need to get a certificate containing the private key, which is essentially a .PFX file. There is a command that we could try to run in order to associate the private key with the certificate:
If the association is successful, then you would see the following window:
Note: 1a 1f 94 8b 21 a2 99 36 77 a8 8e b2 3f 42 8c 7e 47 e3 d1 33 is the thumbprint of the certificate. Open the certificate and click on the details tab. Scroll down to find the thumbprint section. Select the thumbprint section and click on the text below. Do a «Ctrl+A» and then «Ctrl+C» to select and copy it. Below is a snapshot for your reference:
Note: This command doesn’t succeed always. If this fails, then you need to get a certificate containing the private key from the CA. The file extension for a certificate containing private key is .pfx.
Scenario 2
We went pass the first hurdle and now we have a server certificate containing the private key installed on the website. However, we still get the same error as above. The website is still not accessible over https.
The SSLDiag tool comes in handy here.
Windows Server 2003:
Download X64 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=5329 )
Download X86 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=674 )
For IIS 7 and IIS 7.5, use vijaysk’s SSL Diagnostics tool. Below is the link:
Install the tool and run it on the server. If you have a certificate containing private key and still not able to access the website, then you may want to run this tool or check the system event logs for SChannel related warnings/errors.
While running the SSLDiag tool you may get the following error:
You have a private key that corresponds to this certificate but CryptAcquireCertificatePrivateKey failed
There will also be a SChannel warning in the system event logs as shown below:
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| Description: A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x80090016. |
This event/error indicates that there was a problem acquiring certificate’s private key. So let’s try the below steps one by one:
Firstly, verify the permissions on the machinekeys folder as per the KB Article: https://support.microsoft.com/kb/278381. All the private keys are stored within the machinekeys folder, so we need to ensure that we have necessary permissions.
If the permissions are in place and if the issue is still not fixed. Then it must be a problem with the certificate. It may have been corrupted (You may see an error code of 0x8009001a in the SChannel event log).
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x8009001a. |
We will test if the website works with a test certificate. Take a back-up of the existing certificate and then replace it with a self-signed certificate. Try accessing the website via https. If it works then the certificate used earlier was corrupted and it has to be replaced with a new working certificate.
Sometimes the problem may not be with the certificate but with the issuer. You may see the following error in SSLDiag:
CertVerifyCertificateChainPolicy will fail with CERT_E_UNTRUSTEDROOT (0x800b0109), if the root CA certificate is not trusted root.
To fix this add the CA’s certificate to the «Trusted Root CA» store under My computer account on the server.
You may also get the following error:
CertVerifyCertificateChainPolicy returned error -2146762480(0x800b0110).
If the above error is received then we need to check the usage type of the certificate. Open the certificate, click on the «Details» tab and then click on «Edit Properties…» button. Under General tab make sure «Enable all purposes for this certificate» is selected and most importantly «Server Authentication» should be present in the list.
Scenario 3
The first 2 steps check the integrity of the certificate. Once we have confirmed that there are no issues with the certificate, a big problem is solved. But, what if the website is still not accessible over https. Check the HTTPS bindings of the website and determine what port and IP it is listening on. You could run the following command to ensure no other process is listening on the SSL port used by the website.
If there is another process listening on that port then check why that process is consuming that port. Try changing the IP-Port combination to check if the website is accessible or not.
Scenario 4
By now we are sure that we have a proper working certificate installed on the website and there is no other process using the SSL port for this website. However, I still get «Page cannot be displayed» error while accessing over https. When a client connects and initiates an SSL negotiation, HTTP.sys looks in its SSL configuration for the «IP:Port» pair to which the client connected. The HTTP.sys SSL configuration must include a certificate hash and the name of the certificate store before the SSL negotiation will succeed. The problem may be with the HTTP.SYS SSL Listener.
The Certificate hash registered with HTTP.SYS may be NULL or it may contain invalid GUID. Execute the following from a command prompt:
httpcfg is part of Windows Support tools and is present on the installation disk. You could download it from here as well: https://www.microsoft.com/download/en/details.aspx?id=7911
Below is a sample of a working and non-working scenario:
Working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
Non-working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | c09b416d6b 8d615db22 64079d15638e96823d |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
The Hash value seen above is the Thumbprint of your SSL certificate. Notice, that the Guid is all zero in a non-working scenario. You may see the Hash either having some value or blank. Even if we remove the certificate from the web site, and then run «httpcfg query ssl», the website will still list Guid as all 0’s. If you see the GUID as «<0000. 000>, then there is a problem.
We need to remove this entry by running the command:
Delete any entries in the IP Listen list.
To determine whether any IP addresses are listed, open a command prompt, and then run the following command:
If the IP Listen list is empty, the command returns the following string:
If the command returns a list of IP addresses, remove each IP address in the list by using the following command:
restart IIS after this via command «net stop http /y»
Scenario 5
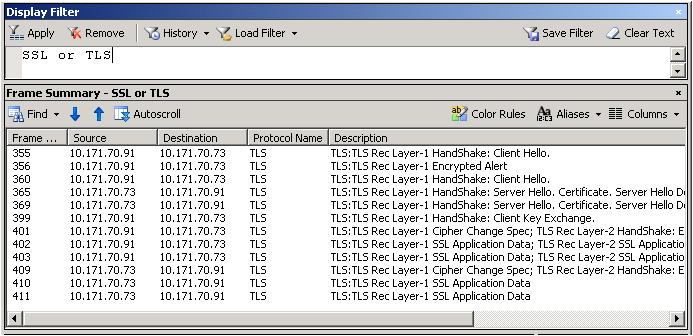
After all this if you are still unable to browse the website on https, then capture a network trace either from the client or server. Filter the trace by «SSL or TLS» to look at SSL traffic.
Below is a network trace snapshot of a non-working scenario:
Well, this is definitely now how you look at a network trace. You need to expand the frame details and see what protocol and cipher was chosen by the server. Select «Server Hello» from the description to get those details.
In the non-working scenario, the client was configured to use TLS 1.1 and TLS 1.2 only. However, the web server was IIS 6, which can support until TLS 1.0 and hence the handshake failed.
Do check the registry keys to determine what protocols are enabled or disabled. Here’s the path:
The «Enabled» DWORD should be set to «1». If «0» then the protocol is disabled.
For example, SSL 2.0 is disabled by default.
Scenario 6
If everything has been verified and if you are still running into issues accessing the website over https, then it most likely is some update which is causing the SSL handshake to fail.
Microsoft has released an update to the implementation of SSL in Windows:
There is potential for this update to impact customers using Internet Explorer, or using an application that uses Internet Explorer to perform HTTPS requests.
There were actually two changes made to address information disclosure vulnerability in SSL 3.0 / TLS 1.0. The MS12-006 update implements a new behavior in schannel.dll, which sends an extra record while using a common SSL chained-block cipher, when clients request that behavior. The other change was in Wininet.dll, part of the December Cumulative Update for Internet Explorer (MS11-099), so that IE will request the new behavior.
If a problem exists, it may manifest as a failure to connect to a server, or an incomplete request. Internet Explorer 9 is able to display an «Internet Explorer cannot display the webpage» error. Prior versions of IE may simply display a blank page.
Fiddler does not use the extra record when it captures and forwards HTTPS requests to the server. Therefore, if Fiddler is used to capture HTTPS traffic, the requests will succeed.
Registry keys
As documented in https://support.microsoft.com/kb/2643584, there is a SendExtraRecord registry value, which can:
- Globally disable the new SSL behavior
- Globally enable it, or
- (Default) enable it for SChannel clients that opt in to the new behavior.
Источник
Содержание
- 1С и Linux
- суббота, 15 декабря 2018 г.
- Доступ zakupki.gov.ru Not Secure
- Troubleshooting SSL related issues (Server Certificate)
- Tools Used in this Troubleshooter:
- Overview
- Scenarios
- Scenario 1
- Scenario 2
- Scenario 3
- Scenario 4
- Scenario 5
- Scenario 6
1С и Linux
Пишу для себя, чтобы не забыть как делал. 95 % рабочее. На комментарии отвечаю, когда увижу.
суббота, 15 декабря 2018 г.
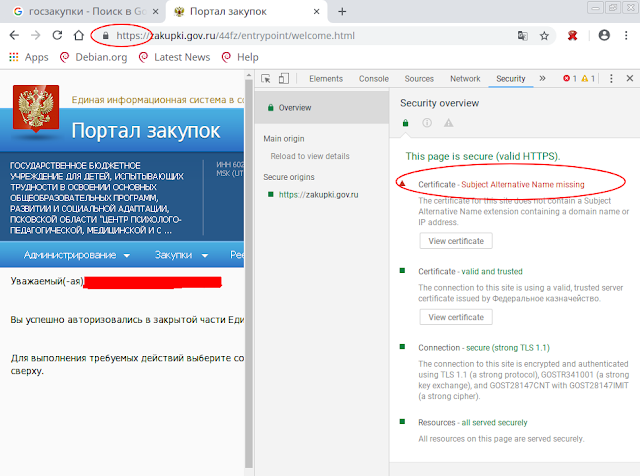
Доступ zakupki.gov.ru Not Secure
]# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -v -nosave -savecert /tmp/t.p7b
[root@test-x64-centos7
]# /opt/cprocsp/bin/amd64/certmgr -list -file /tmp/t.p7b
=============================================================================
1——-
Issuer : E=uc_fk@roskazna.ru, S=г. Москва, INN=007710568760, OGRN=1047797019830, STREET=»улица Ильинка, дом 7″, L=Москва, C=RU, O=Федеральное казначейство, CN=Федеральное казначейство
Subject : INN=007710568760, OGRN=1047797019830, STREET=»ул. Проспект Мира, 105″, E=777@roskazna.ru, C=RU, S=г. Москва, L=Москва, O=Федеральное казначейство, CN=zakupki.gov.ru
Serial : 0x6F064FA71C24CD7E2CE6FAAEA927D8C7EC69A35F
SHA1 Hash : c369b560ce239beddb2fc12b4884dee1cfc923aa
SubjKeyID : 10c6d12e7cd886d022bcdfea4cbe10e32acf82bc
Signature Algorithm : ГОСТ Р 34.11/34.10-2001
PublicKey Algorithm : ГОСТ Р 34.10-2001 (512 bits)
Public key : 04 40 1b ce 0b 15 6a 4a 57 e0 1b d8 39 ee 86 83
32 70 ea db fd f5 39 c1 e6 de 3c c8 be 10 81 03
5d da 0b 3b 09 7a d3 0d 46 33 58 11 3b 20 94 99
fe 04 fe 8e e6 bc 32 53 ff 2e 71 10 8e e2 12 a1
52 cf
Not valid before : 21/12/2017 06:06:33 UTC
Not valid after : 21/03/2019 06:06:33 UTC
PrivateKey Link : No
Subject Alt Names
UPN : ▒㌴ (2.5.4.12)
URL : 0
CDP : http://crl.roskazna.ru/crl/ucfk.crl
CDP : http://crl.fsfk.local/crl/ucfk.crl
Extended Key Usage : 1.3.6.1.5.5.7.3.1
.
При наличии расширения Subject Alt Names RFC требует сверять имя сервера с ним, а не с полем CN. Поэтому CN=zakupki.gov.ru отброшен, а в Subject Alt Names хрень.
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [05.10.18 11:35]
Но мы сделали параметр для отключения требований RFC6125, который может подвергнуть систему опасности для атак с подменой сертификатов:
[root@test-x64-centos7
]# /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
[root@test-x64-centos7
]# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HDEContext expired: OK if file is completely downloaded
Reply status: HTTP/1.1 200 OK
1 connections, 586 bytes in 0.186 seconds;
Total: SYS: 0,020 sec USR: 0,140 sec UTC: 0,230 sec
[ErrorCode: 0x00000000]
# /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 25072019
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,010 sec
[ErrorCode: 0x00000000]
L K, [15.12.18 14:12]
[В ответ на Andrey]
root@astra:
# /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
root@astra:
# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HSECPKG_ATTR_PACKAGE_INFO not supported.
Error 0x800b010f (CERT_E_CN_NO_MATCH) returned by CertVerifyCertificateChainPolicy!
An error occurred in running the program.
/dailybuildsbranches/CSP_4_0/CSPbuild/CSP/samples/csptest/WebClient.c:764:Error authenticating server credentials!
Error number 0x800b010f (2148204815).
CN-имя сертификата не совпадает с полученным значением.
Total: SYS: 0,070 sec USR: 0,290 sec UTC: 1,720 sec
[ErrorCode: 0x800b010f]
# /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 25072019
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,010 sec
[ErrorCode: 0x00000000]
Какой релиз КриптоПро нужно ставить?
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [12.12.18 18:12]
Вышел финальный релиз КриптоПро CSP 4.0 R4 (сборка 4.0.9963 Abel):
https://www.cryptopro.ru/forum2/default.aspx?g=posts&m=97735#post97735
На дистрибутив получено положительное заключение, скоро будет сертификат.
В тестовых целях её можно установить из нашего репозитория:
https://www.cryptopro.ru/forum2/default.aspx?g=posts&t=12507
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [15.12.18 23:07]
[В ответ на L K]
В любом случае лучше ставить последний, на который сейчас получаем сертификат — 4.0.9963 Abel. В 9944 в этой команде должна помочь замена long на bool и 1 на true.
Проблема решилась установкой КриптоПро версии 4.0.9963 и действиями как написал Андрей, за что ему огромное спасибо.
$ /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9019 KC2 Release Ver:4.0.9963 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 26834115
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,020 sec
[ErrorCode: 0x00000000]
$ sudo /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
$ sudo /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HSECPKG_ATTR_PACKAGE_INFO not supported.
DContext expired: OK if file is completely downloaded
Reply status: HTTP/1.1 200 OK
1 connections, 589 bytes in 1.221 seconds;
Total: SYS: 0,040 sec USR: 0,320 sec UTC: 1,300 sec
[ErrorCode: 0x00000000]
Для 4.0.9944
user@astra:
$ /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 20066515
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,030 sec
[ErrorCode: 0x00000000]
user@astra:
$ sudo /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add bool Rfc6125_NotStrict_ServerName_Check true
user@astra:
Источник
Tools Used in this Troubleshooter:
This material is provided for informational purposes only. Microsoft makes no warranties, express or implied.
Overview
This document will help you in troubleshooting SSL issues related to IIS only. Client Certificates troubleshooting will not be covered in this document. Server Certificates are meant for Server Authentication and we will be dealing only with Server Certificates in this document.
If the Client certificates section is set to «Require» and then you run into issues, then please don’t refer this document. This is meant for troubleshooting SSL Server certificates issue only.
It is important to know that every certificate comprises of a public key (used for encryption) and a private key (used for decryption). The private key is known only to the server.
The default port for https is 443.
I am under the assumption the reader is well-versed in SSL Handshake and the Server Authentication process during the SSL handshake.
Description of the Secure Sockets Layer (SSL) Handshake:
Description of the Server Authentication Process during the SSL Handshake:
Scenarios
The following error message is seen while browsing the website over https:
The first thing that has to be checked is whether the website is accessible over http. If it is not, there likely is a separate issue not covered here. You will need to have the website working on http first before continuing with this troubleshooter.
Now let’s assume the website is accessible over http and we get the above error when trying to browse over https. The problem is seen because the SSL handshake failed and hence the error message was seen. There could be many reasons. We will follow a step-by-step approach to solve this problem.
Scenario 1
Check if the server certificate has the private key corresponding to it. Refer the below picture:
If private key is missing, then you need to get a certificate containing the private key, which is essentially a .PFX file. There is a command that we could try to run in order to associate the private key with the certificate:
If the association is successful, then you would see the following window:
Note: 1a 1f 94 8b 21 a2 99 36 77 a8 8e b2 3f 42 8c 7e 47 e3 d1 33 is the thumbprint of the certificate. Open the certificate and click on the details tab. Scroll down to find the thumbprint section. Select the thumbprint section and click on the text below. Do a «Ctrl+A» and then «Ctrl+C» to select and copy it. Below is a snapshot for your reference:
Note: This command doesn’t succeed always. If this fails, then you need to get a certificate containing the private key from the CA. The file extension for a certificate containing private key is .pfx.
Scenario 2
We went pass the first hurdle and now we have a server certificate containing the private key installed on the website. However, we still get the same error as above. The website is still not accessible over https.
The SSLDiag tool comes in handy here.
Windows Server 2003:
Download X64 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=5329 )
Download X86 ( https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=674 )
For IIS 7 and IIS 7.5, use vijaysk’s SSL Diagnostics tool. Below is the link:
Install the tool and run it on the server. If you have a certificate containing private key and still not able to access the website, then you may want to run this tool or check the system event logs for SChannel related warnings/errors.
While running the SSLDiag tool you may get the following error:
You have a private key that corresponds to this certificate but CryptAcquireCertificatePrivateKey failed
There will also be a SChannel warning in the system event logs as shown below:
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| Description: A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x80090016. |
This event/error indicates that there was a problem acquiring certificate’s private key. So let’s try the below steps one by one:
Firstly, verify the permissions on the machinekeys folder as per the KB Article: https://support.microsoft.com/kb/278381. All the private keys are stored within the machinekeys folder, so we need to ensure that we have necessary permissions.
If the permissions are in place and if the issue is still not fixed. Then it must be a problem with the certificate. It may have been corrupted (You may see an error code of 0x8009001a in the SChannel event log).
| Event Type: Error |
|---|
| Event Source: Schannel |
| Event Category: None |
| Event ID: 36870 |
| Date: 2/11/2012 |
| Time: 12:44:55 AM |
| User: N/A |
| Computer: |
| A fatal error occurred when attempting to access the SSL server credential private key. The error code returned from the cryptographic module is 0x8009001a. |
We will test if the website works with a test certificate. Take a back-up of the existing certificate and then replace it with a self-signed certificate. Try accessing the website via https. If it works then the certificate used earlier was corrupted and it has to be replaced with a new working certificate.
Sometimes the problem may not be with the certificate but with the issuer. You may see the following error in SSLDiag:
CertVerifyCertificateChainPolicy will fail with CERT_E_UNTRUSTEDROOT (0x800b0109), if the root CA certificate is not trusted root.
To fix this add the CA’s certificate to the «Trusted Root CA» store under My computer account on the server.
You may also get the following error:
CertVerifyCertificateChainPolicy returned error -2146762480(0x800b0110).
If the above error is received then we need to check the usage type of the certificate. Open the certificate, click on the «Details» tab and then click on «Edit Properties…» button. Under General tab make sure «Enable all purposes for this certificate» is selected and most importantly «Server Authentication» should be present in the list.
Scenario 3
The first 2 steps check the integrity of the certificate. Once we have confirmed that there are no issues with the certificate, a big problem is solved. But, what if the website is still not accessible over https. Check the HTTPS bindings of the website and determine what port and IP it is listening on. You could run the following command to ensure no other process is listening on the SSL port used by the website.
If there is another process listening on that port then check why that process is consuming that port. Try changing the IP-Port combination to check if the website is accessible or not.
Scenario 4
By now we are sure that we have a proper working certificate installed on the website and there is no other process using the SSL port for this website. However, I still get «Page cannot be displayed» error while accessing over https. When a client connects and initiates an SSL negotiation, HTTP.sys looks in its SSL configuration for the «IP:Port» pair to which the client connected. The HTTP.sys SSL configuration must include a certificate hash and the name of the certificate store before the SSL negotiation will succeed. The problem may be with the HTTP.SYS SSL Listener.
The Certificate hash registered with HTTP.SYS may be NULL or it may contain invalid GUID. Execute the following from a command prompt:
httpcfg is part of Windows Support tools and is present on the installation disk. You could download it from here as well: https://www.microsoft.com/download/en/details.aspx?id=7911
Below is a sample of a working and non-working scenario:
Working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
Non-working scenario:
| Configuration | Setting |
|---|---|
| IP | 0.0.0.0:443 |
| Hash | c09b416d6b 8d615db22 64079d15638e96823d |
| Guid | |
| CertStoreName | MY |
| CertCheckMode | |
| RevocationFreshnessTime | |
| UrlRetrievalTimeout | |
| SslCtlIdentifier | |
| SslCtlStoreName | |
| Flags |
The Hash value seen above is the Thumbprint of your SSL certificate. Notice, that the Guid is all zero in a non-working scenario. You may see the Hash either having some value or blank. Even if we remove the certificate from the web site, and then run «httpcfg query ssl», the website will still list Guid as all 0’s. If you see the GUID as «<0000. 000>, then there is a problem.
We need to remove this entry by running the command:
Delete any entries in the IP Listen list.
To determine whether any IP addresses are listed, open a command prompt, and then run the following command:
If the IP Listen list is empty, the command returns the following string:
If the command returns a list of IP addresses, remove each IP address in the list by using the following command:
restart IIS after this via command «net stop http /y»
Scenario 5
After all this if you are still unable to browse the website on https, then capture a network trace either from the client or server. Filter the trace by «SSL or TLS» to look at SSL traffic.
Below is a network trace snapshot of a non-working scenario:
Well, this is definitely now how you look at a network trace. You need to expand the frame details and see what protocol and cipher was chosen by the server. Select «Server Hello» from the description to get those details.
In the non-working scenario, the client was configured to use TLS 1.1 and TLS 1.2 only. However, the web server was IIS 6, which can support until TLS 1.0 and hence the handshake failed.
Do check the registry keys to determine what protocols are enabled or disabled. Here’s the path:
The «Enabled» DWORD should be set to «1». If «0» then the protocol is disabled.
For example, SSL 2.0 is disabled by default.
Scenario 6
If everything has been verified and if you are still running into issues accessing the website over https, then it most likely is some update which is causing the SSL handshake to fail.
Microsoft has released an update to the implementation of SSL in Windows:
There is potential for this update to impact customers using Internet Explorer, or using an application that uses Internet Explorer to perform HTTPS requests.
There were actually two changes made to address information disclosure vulnerability in SSL 3.0 / TLS 1.0. The MS12-006 update implements a new behavior in schannel.dll, which sends an extra record while using a common SSL chained-block cipher, when clients request that behavior. The other change was in Wininet.dll, part of the December Cumulative Update for Internet Explorer (MS11-099), so that IE will request the new behavior.
If a problem exists, it may manifest as a failure to connect to a server, or an incomplete request. Internet Explorer 9 is able to display an «Internet Explorer cannot display the webpage» error. Prior versions of IE may simply display a blank page.
Fiddler does not use the extra record when it captures and forwards HTTPS requests to the server. Therefore, if Fiddler is used to capture HTTPS traffic, the requests will succeed.
Registry keys
As documented in https://support.microsoft.com/kb/2643584, there is a SendExtraRecord registry value, which can:
- Globally disable the new SSL behavior
- Globally enable it, or
- (Default) enable it for SChannel clients that opt in to the new behavior.
Источник
|
Boris7772 |
|
|
Статус: Новичок Группы: Участники
|
Добрый день, Пытаюсь настроить взаимодейтсвие с ФинЦЕРТ через stunnel установил согласно регламенту ФинЦЕРТ сертификаты из архива: http://cbr.ru/StaticHtml/File/14408/ASOI_docs.zip Приложил лог с ошибкой и конфигурацию stunnel. Использую stunnel из CSP 4.0.9963 Конфигурация stunnel [portal] Лог с проблемой: Цитата: 2020.11.24 12:30:44 LOG3[1123:140439079679744]: Error 0x8009030e returned by VerifyCertChain 2020.11.24 12:30:54 LOG3[1123:140439079679744]: Error 0x8009030e returned by VerifyCertChain Подскажите, пожалуйста, с чем связана данная проблема и как ее можно решить? Отредактировано пользователем 24 ноября 2020 г. 18:01:23(UTC) |
 |
|
|
Михаил Селезнёв |
|
|
Статус: Сотрудник Группы: Участники Сказал «Спасибо»: 3 раз |
Добрый день! |
 |
|
|
Boris7772 |
|
|
Статус: Новичок Группы: Участники
|
Автор: Михаил Селезнёв Добрый день! Что-то не удалось загрузить файлы нормально, опубликовал лог и конфигурацию в посте |
 |
|
|
Nikolay Batischev |
|
|
Статус: Сотрудник Группы: Участники Сказал «Спасибо»: 3 раз |
Добрый день! |
 |
|
|
Boris7772 |
|
|
Статус: Новичок Группы: Участники
|
Автор: Nikolay Batischev Добрый день! Установил этот параметр в 0, ошибка ушла спасибо, запросы к сервису стали отбиваться с 421 статусом, это я так понимаю уже внешняя проблема? Лог при этом следующий: Отредактировано пользователем 24 ноября 2020 г. 18:29:32(UTC) |
 |
|
| Пользователи, просматривающие эту тему |
|
Guest |
Быстрый переход
Вы не можете создавать новые темы в этом форуме.
Вы не можете отвечать в этом форуме.
Вы не можете удалять Ваши сообщения в этом форуме.
Вы не можете редактировать Ваши сообщения в этом форуме.
Вы не можете создавать опросы в этом форуме.
Вы не можете голосовать в этом форуме.
|
Иван Бахтин |
|
|
Статус: Участник Группы: Участники Сказал(а) «Спасибо»: 5 раз |
Здравствуйте! Установленный сертификат: Настройки stunnel.conf: Вывод log stunnel: Так же хочу сказать, что проверил сертификаты на совпадение (т.е. установленный у меня и передаваемый с сервера ГИС ЖКХ) утилитой /opt/cprocsp/bin/amd64/csptest, сертификаты совпадают. Подскажите, пожалуйста, где я допустил ошибку и как её исправить? |
 |
|
|
two_oceans |
|
|
Статус: Эксперт Группы: Участники Сказал(а) «Спасибо»: 110 раз |
Добрый день. 2) в строке CAFile по идее должен быть не сам сертификат сервера, а список сертификатов УЦ, выдавшего сертификат серверу. В случае тестового УЦ КриптоПро это обычно 2 сертификата от корневого и промежуточного УЦ. Обычно это выглядит как: Код: заголовки могут немного отличаться смотря какая версия stunnel и openssl Отредактировано пользователем 5 апреля 2022 г. 7:27:39(UTC) |
 |
|
|
|
Иван Бахтин
оставлено 05.04.2022(UTC) |
|
Иван Бахтин |
|
|
Статус: Участник Группы: Участники Сказал(а) «Спасибо»: 5 раз |
Автор: two_oceans Добрый день. 2) в строке CAFile по идее должен быть не сам сертификат сервера, а список сертификатов УЦ, выдавшего сертификат серверу. В случае тестового УЦ КриптоПро это обычно 2 сертификата от корневого и промежуточного УЦ. Обычно это выглядит как: Код: заголовки могут немного отличаться смотря какая версия stunnel и openssl Большое спасибо! С verify=0 запросы проходят. Очень надеюсь, что на боевом сервере с verify=2 всё будет работать. |
 |
|
| Пользователи, просматривающие эту тему |
|
Guest |
Быстрый переход
Вы не можете создавать новые темы в этом форуме.
Вы не можете отвечать в этом форуме.
Вы не можете удалять Ваши сообщения в этом форуме.
Вы не можете редактировать Ваши сообщения в этом форуме.
Вы не можете создавать опросы в этом форуме.
Вы не можете голосовать в этом форуме.
Всем доброго дня.
Недавно ко мне обратился знакомый с вопросом по реализации шифрованного по алгоритму ГОСТ TLS-канала для работы с веб-сервисами некоторых БКИ.
Немного помыслив, вспомнил, что есть такая замечательная штука как stunnel, которая может TLS как в режиме сервера, так и в режиме клиента. Плюс к этому компания КриптоПро сделала форк stunnel с оптимизацией под российские криптоалгоритмы. В итоге родился небольшой гайд по реализации простого и бюджетного варианта, которым и хочу поделиться с вами.
В качестве примера приводится настройка stunnel в качестве TLS клиента:
1) к серверу НБКИ без авторизации пользователя;
2) к тестовому УЦ КриптоПро с авторизацией пользователя по сертификату.
В данном материале использовались OC Debian 8.3 x86 и КриптоПро CSP 4.0.9708 (Nechaev) от 01.03.2016 (stunnel включен).
1. Установка Крипто-Про CSP и stunnel
Скачиваем архив CSP с сайта КриптоПро и распаковываем
tar zxvf linux-ia32_deb.tgz
cd linux-ia32_debУстановливаем минимально необходимый набор пакетов
sudo apt-get install lsb-core
sudo dpkg -i lsb-cprocsp-base_4.0.0-4_all.deb
sudo dpkg -i lsb-cprocsp-rdr_4.0.0-4_i386.deb
sudo dpkg -i lsb-cprocsp-capilite_4.0.0-4_i386.deb
sudo dpkg -i lsb-cprocsp-kc1_4.0.0-4_i386.deb
sudo dpkg -i cprocsp-stunnel_4.0.0-4_i386.deb2. Импорт корневых сертификатов
Импортируем корневые сертификаты КриптоПро в локальное хранилище сертификатов.
Нам понадобятся два сертификата:
— корневой сертификат УЦ Крипто-Про. Данным сертификатом подписан сертификат веб-сервера НБКИ;
— корневой сертификат тестового УЦ КриптоПро. Данным сертификатом подписан сертификат веб-сервера тестового УЦ КриптоПро и тестовый сертификат нашего пользователя.
/opt/cprocsp/bin/ia32/certmgr -inst -file <home>/cert/ca_cryptopro_4aad6f_der.cer -store ROOT
/opt/cprocsp/bin/ia32/certmgr -inst -file <home>/cert/ca_test_cryptopro_4487da_der.cer -store ROOTПосле импортирования полезно просмотреть список установленных корневых сертификатов
/opt/cprocsp/bin/ia32/certmgr -list -store ROOT3. Копирование ключевого контейнера пользователя
Наверное, это самая запутанная и самая важная часть данного руководства.
Сначала немного теории «на пальцах».
В протоколе TLS предусмотрена односторонняя и двусторонняя аутентификация. Под односторонней чаще всего понимается аутентификация веб-сервера, когда сервер доказывает клиенту что действительно владеет закрытым ключом предъявленного цифрового сертификата. Под двусторонней аутентификацией сервер и клиент доказывают это друг другу.
В КриптоПро ключевая информация (ключи шифрования) хранятся в контейнере (с точки зрения файловой системы — это каталог с несколькими файлами). В качестве носителя может выступать (чаще всего) дискета, флешка, токен, ветка реестра (Windows) или каталог (Linux). И если клиент или сервер проходят взаимную аутентификацию (доказывают владение ключами), то они должны иметь не только цифровой сертификат с открытым ключом, но и сам контейнер с ключами.
Опустим процесс создания тестового ключа в тестовом УЦ КриптоПро и начем с того момента, что у нас есть ключевой контейнер с именем «test» на флешке.
Монтируем флешку
sudo mount /dev/sdb1 /media/sdb1/
Копируем контейнер с флешки на HDD
Есть два способа: ручной и с помощью утилиты. Я скопировал вручную
cp -r /media/sdb1/test.000/ /var/opt/cprocsp/keys/stunnel/Проверим сертификат в контейнере
certmgr -list -cont '\.HDIMAGEtest'Проверим работоспособность ключей
csptest -keyset -check -cont '\.HDIMAGEtest'Экспортируем сертификат пользователя в файл (он еще понадобится)
certmgr -export -dest test_user_7a8110.cer -cont '\.HDIMAGEtest'Делаем привязку данного сертификата пользователя к нашему контейнеру
certmgr -inst -file test_user_7a8110.cer -cont '\.HDIMAGEtest'Проверяем локальное хранилище сертификатов пользователя
certmgr -list -store MyПроверяем локальное хранилище сертификатов пользователя
PrivateKey Link : Yes
Container : HDIMAGE\test.0002EF8Создаем файл конфигурации с нужными нам настройками для stunnel
sudo mkdir /etc/stunnel
sudo vim /etc/stunnel/stunnel.confСодержимое файла конфигурации:
setgid = stunnel
setuid = stunnel
pid=/var/opt/cprocsp/tmp/stunnel_cli.pid
output=/var/opt/cprocsp/tmp/stunnel_cli.log
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
debug = 3
client = yes
[stunnel.nbki]
accept = <IP address>:8181
connect = icrs.nbki.ru:443
verify=2
[stunnel.test_uc]
accept = <IP address>:8282
connect = www.cryptopro.ru:5555
client = /etc/stunnel/test_user_7a8110.cer
verify=2Запускаем процесс
/opt/cprocsp/sbin/amd64/stunnel_thread /etc/stunnel/stunnel.confПроверяем результат
5. Автоматический запуск Stunnel
Когда все заработало должным образом, то было бы неплохо автоматизировать запуск stunnel при загрузке ОС.
Создаем скрипт запуска. Также будут доступны команды управления start, stop, restart.
Пример команды для перезагрузки stunnel:
sudo service stunnel_thread restartСоздаем скрипт
sudo vim /etc/init.d/stunnel_threadи помещаем в него следующий текст:
#!/bin/sh
### BEGIN INIT INFO
# Provides: stunnel
# Default-Start: 3 5
# Default-Stop: 0 1 6
# Required-Start: $remote_fs $syslog
# Required-Stop: $remote_fs $syslog
# Short-Description: Start daemon at boot time
# Description: Enable stunnel by daemon.
### END INIT INFO
PATH_DAEMON=/opt/cprocsp/sbin/ia32
DAEMON=stunnel_thread
CONFIG=/etc/stunnel/stunnel.conf
test -x $PATH_DAEMON/$DAEMON || exit 0
case "$1" in
start)
$PATH_DAEMON/$DAEMON $CONFIG
;;
stop)
pkill -f $DAEMON
;;
restart)
pkill -f $DAEMON
sleep 3
$PATH_DAEMON/$DAEMON $CONFIG
;;
*)
echo "Usage: $0 {start|stop|restart}"
exit 1
;;
esac
exit 0Добавляем в автозагрузку
sudo update-rc.d stunnel_thread defaults6. Troubleshooting
Частые ошибки, с которыми я столкнулся и можете столкнуться вы.
1) Не открывается сайт через stunnel
Что нужно сделать:
— проверить адрес и порт в конфиге
— в браузере открывать не только сам адрес stunnel, а полный путь.
Пример: не 10.0.0.123:8181, а 10.0.0.123:8181/se/login
2) Следующие ошибки в логе
Error 0x40 ((unknown)) returned by CertVerifyCertificateChainPolicy!и/или
Error 0x40 when validate certificate
Ошибка возникает из-за того, что stunnel не может проверить сертификат по списку отзыва CRL. Проблему можно решить тремя вариантами (но с разной эффективностью):
— периодически вручную импортировать актуальный CRL с помощью certmgr;
— отключить проверку сертификатов в TLS в файле настроек CSP
/etc/opt/cprocsp/config.ini— в файле настроек CSP (написан выше) указать корректный путь к библиотеке curl.
"libcurl.so" = "/usr/lib/i386-linux-gnu/libcurl.so.4"7. Ссылки
Тестовый Удостоверяющий Центр КриптоПро
КриптоПро CSP
КриптоПро Stunnel
Официальные мануалы по КриптоПро Stunnel
Ключевые слова для поисковых систем: настройка БКИ, автоматизированый обмен с бюро кредитных историй, автоматическое получение отчетов с бюро кредитных историй, КриптоПро и БКИ, обмен с бюро кредитных историй, шифрование трафика криптопро, криптопро на linux
- Remove From My Forums
-
Question
-
I was using SSL Diagnostics to troubleshoot client cert problem, and I got this:
CertVerifyCertificateChainPolicy=»0x1″
CertGetCertificateChain_dwFlags=»0x40000000″
CERT_CHAIN_PARA.dwUrlRetrievalTimeout=»0 ms»
CERT_CHAIN_PARA.fCheckRevocationFreshnessTime=»FALSE»
CERT_CHAIN_PARA.dwRevocationFreshnessTime=»0 sec»
CERT_CHAIN_POLICY_STATUS.dwError=»0x800b010f»
CERT_CHAIN_POLICY_STATUS.lChainIndex=»0″
CERT_CHAIN_POLICY_STATUS.lElementIndex=»1″I want to know what CERT_CHAIN_POLICY_STATUS.dwError=»0x800b010f» means. Microsoft documentation gives out the error in string only, rather long ones too. Does anyone know how to interpret the error code in hex?
Answers
-
It stands for CERT_E_CN_NO_MATCH (from winerror.h). The explain text for this error is «The certificate’s CN name does not match the passed value». It literally means the target server name does not match the CN name in the certificate used in authentication. You can choose to ignore this error when calling CertVerifyCertificateChainPolicy (which may or may not be a good idea depending what is app is built for) by setting pPolicyPara->pvExtraPolicyPara->fdwChecks with SECURITY_FLAG_IGNORE_CERT_CN_INVALID.
http://msdn.microsoft.com/en-us/library/aa377163.aspx
Hope this helps.
Thanks!
GK
-
Marked as answer by
Tuesday, May 25, 2010 4:33 PM
-
Marked as answer by
- Remove From My Forums
-
Question
-
Hi there,
I have an application set up for deployment, but it seems installation is not starting on client.
After a few minutes from deployment I can see the state under «Unknown» tab with a state on the machine like «Client checks validated» (don’t now what it’s called in English exactly).
Will the installation start at a later time or will I wait forever? Is there a way to push installation a bit if there should be a waiting time?
Thanks for any help,
Melampous
Answers
-
BGB has nothing to do with installing applications. That component is used when you force an update of policies using the console. That’s not really needed. The client will check for policies every 60min (default) automatically. It also takes a while until
the state is sent to the site. Nothing is happening in real time.
Torsten Meringer | http://www.mssccmfaq.de
-
Marked as answer by
Saturday, May 3, 2014 6:54 PM
-
Marked as answer by
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [05.10.18 11:28]
[В ответ на Дмитрий Давидович]
У них кривой сертификат сервера.
Диагностировать можно так:
[root@test-x64-centos7 ~]# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -v -nosave -savecert /tmp/t.p7b
[root@test-x64-centos7 ~]# /opt/cprocsp/bin/amd64/certmgr -list -file /tmp/t.p7b
=============================================================================
1——-
Issuer : E=uc_fk@roskazna.ru, S=г. Москва, INN=007710568760, OGRN=1047797019830, STREET=»улица Ильинка, дом 7″, L=Москва, C=RU, O=Федеральное казначейство, CN=Федеральное казначейство
Subject : INN=007710568760, OGRN=1047797019830, STREET=»ул. Проспект Мира, 105″, E=777@roskazna.ru, C=RU, S=г. Москва, L=Москва, O=Федеральное казначейство, CN=zakupki.gov.ru
Serial : 0x6F064FA71C24CD7E2CE6FAAEA927D8C7EC69A35F
SHA1 Hash : c369b560ce239beddb2fc12b4884dee1cfc923aa
SubjKeyID : 10c6d12e7cd886d022bcdfea4cbe10e32acf82bc
Signature Algorithm : ГОСТ Р 34.11/34.10-2001
PublicKey Algorithm : ГОСТ Р 34.10-2001 (512 bits)
Public key : 04 40 1b ce 0b 15 6a 4a 57 e0 1b d8 39 ee 86 83
32 70 ea db fd f5 39 c1 e6 de 3c c8 be 10 81 03
5d da 0b 3b 09 7a d3 0d 46 33 58 11 3b 20 94 99
fe 04 fe 8e e6 bc 32 53 ff 2e 71 10 8e e2 12 a1
52 cf
Not valid before : 21/12/2017 06:06:33 UTC
Not valid after : 21/03/2019 06:06:33 UTC
PrivateKey Link : No
Subject Alt Names
UPN : ▒㌴ (2.5.4.12)
URL : 0
CDP : http://crl.roskazna.ru/crl/ucfk.crl
CDP : http://crl.fsfk.local/crl/ucfk.crl
Extended Key Usage : 1.3.6.1.5.5.7.3.1
…
При наличии расширения Subject Alt Names RFC требует сверять имя сервера с ним, а не с полем CN. Поэтому CN=zakupki.gov.ru отброшен, а в Subject Alt Names хрень.
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [05.10.18 11:35]
Но мы сделали параметр для отключения требований RFC6125, который может подвергнуть систему опасности для атак с подменой сертификатов:
[root@test-x64-centos7 ~]# /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
[root@test-x64-centos7 ~]# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HDEContext expired: OK if file is completely downloaded
Reply status: HTTP/1.1 200 OK
1 connections, 586 bytes in 0.186 seconds;
Total: SYS: 0,020 sec USR: 0,140 sec UTC: 0,230 sec
[ErrorCode: 0x00000000]
# /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 25072019
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,010 sec
[ErrorCode: 0x00000000]
L K, [15.12.18 14:12]
[В ответ на Andrey]
root@astra:~# /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
root@astra:~# /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HSECPKG_ATTR_PACKAGE_INFO not supported.
Error 0x800b010f (CERT_E_CN_NO_MATCH) returned by CertVerifyCertificateChainPolicy!
An error occurred in running the program.
/dailybuildsbranches/CSP_4_0/CSPbuild/CSP/samples/csptest/WebClient.c:764:Error authenticating server credentials!
Error number 0x800b010f (2148204815).
CN-имя сертификата не совпадает с полученным значением.
Total: SYS: 0,070 sec USR: 0,290 sec UTC: 1,720 sec
[ErrorCode: 0x800b010f]
# /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 25072019
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,010 sec
[ErrorCode: 0x00000000]
Какой релиз КриптоПро нужно ставить?
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [12.12.18 18:12]
Вышел финальный релиз КриптоПро CSP 4.0 R4 (сборка 4.0.9963 Abel):
https://www.cryptopro.ru/forum2/default.aspx?g=posts&m=97735#post97735
На дистрибутив получено положительное заключение, скоро будет сертификат.
В тестовых целях её можно установить из нашего репозитория:
https://www.cryptopro.ru/forum2/default.aspx?g=posts&t=12507
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Andrey, [15.12.18 23:07]
[В ответ на L K]
В любом случае лучше ставить последний, на который сейчас получаем сертификат — 4.0.9963 Abel. В 9944 в этой команде должна помочь замена long на bool и 1 на true.
ХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХХ
Проблема решилась установкой КриптоПро версии 4.0.9963 и действиями как написал Андрей, за что ему огромное спасибо.
user@astra:~$ /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9019 KC2 Release Ver:4.0.9963 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 26834115
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,020 sec
[ErrorCode: 0x00000000]
user@astra:~$ sudo /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add long Rfc6125_NotStrict_ServerName_Check 1
user@astra:~$ sudo /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HSECPKG_ATTR_PACKAGE_INFO not supported.
DContext expired: OK if file is completely downloaded
Reply status: HTTP/1.1 200 OK
1 connections, 589 bytes in 1.221 seconds;
Total: SYS: 0,040 sec USR: 0,320 sec UTC: 1,300 sec
[ErrorCode: 0x00000000]
Для 4.0.9944
user@astra:~$ /opt/cprocsp/bin/amd64/csptest -keyset -verifycontext
CSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:READY:AVX.
AcquireContext: OK. HCRYPTPROV: 20066515
GetProvParam(PP_NAME): Crypto-Pro GOST R 34.10-2012 KC2 CSP
Total: SYS: 0,000 sec USR: 0,000 sec UTC: 0,030 sec
[ErrorCode: 0x00000000]
user@astra:~$ sudo /opt/cprocsp/sbin/amd64/cpconfig -ini ‘configparameters’ -add bool Rfc6125_NotStrict_ServerName_Check true
user@astra:~$ sudo /opt/cprocsp/bin/amd64/csptestf -tlsc -server zakupki.gov.ru -nosave
HSECPKG_ATTR_PACKAGE_INFO not supported.
DContext expired: OK if file is completely downloaded
Reply status: HTTP/1.1 200 OK
1 connections, 589 bytes in 0.388 seconds;
Total: SYS: 0,050 sec USR: 0,200 sec UTC: 0,450 sec
[ErrorCode: 0x00000000]















 1 пользователь поблагодарил two_oceans за этот пост.
1 пользователь поблагодарил two_oceans за этот пост.