Installing a Secure Sockets Layer (SSL) certificate on your WordPress site enables it to use HTTPS to ensure secure connections. Unfortunately, there are a variety of things that can go wrong in the process of confirming a valid SSL certificate and making a connection between your site’s server and a visitor’s browser.
If you’ve encountered an “SSL Handshake Failed” error message and are confused as to what it means, you’re not alone. It’s a common error that doesn’t tell you much on its own. While this can be a frustrating experience, the good news is that there are simple steps you can take to resolve the issue.
In this post, we’ll explain what the SSL Handshake Failed error is and what causes it. Then we’ll provide you with several methods you can use to fix it.
Let’s get started!
An Introduction to the SSL Handshake
Before we dig deeper into what causes a TLS or SSL handshake failure, it’s helpful to understand what the TLS/SSL handshake is. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols used to authenticate data transfers between servers and external systems such as browsers.
SSL certificates are needed in order to secure your website using HTTPS. We won’t get too in-depth about the difference between TLS vs SSL since it’s a minor one. The terms are often used interchangeably, so for simplicity’s sake, we’ll use “SSL” to refer to both.
With that out of the way, an SSL handshake is the first step in the process of establishing an HTTPS connection. To authenticate and establish the connection, the user’s browser and the website’s server must go through a series of checks (the handshake), which establish the HTTPS connection parameters.
Let us explain: the client (typically the browser) sends a request for a secure connection to the server. After the request is sent, the server sends a public key to your computer and checks that key against a list of certificates. The computer then generates a key and encrypts it, using the public key sent from the server.
To make a long story short, without the SSL handshake, a secure connection won’t be made. This can pose a significant security risk. Plus, there are a lot of moving parts involved in the process.
That means there are many different opportunities for something to go wrong and cause a handshake failure, or even lead to the “your connection is not private” error, causing visitors to leave.
Confronted with the ‘SSL Handshake Failed’ error? 🤝 Get a grip on how to solve it with these 5 methods ⤵️Click to Tweet
Understanding What Causes SSL Handshake Failures
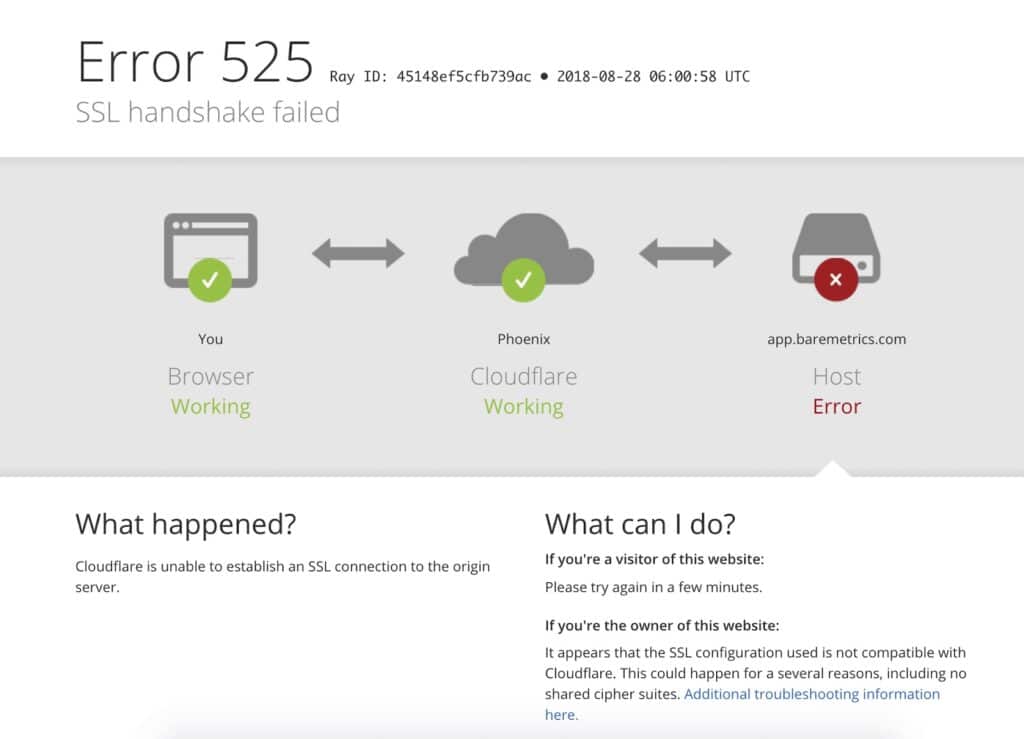
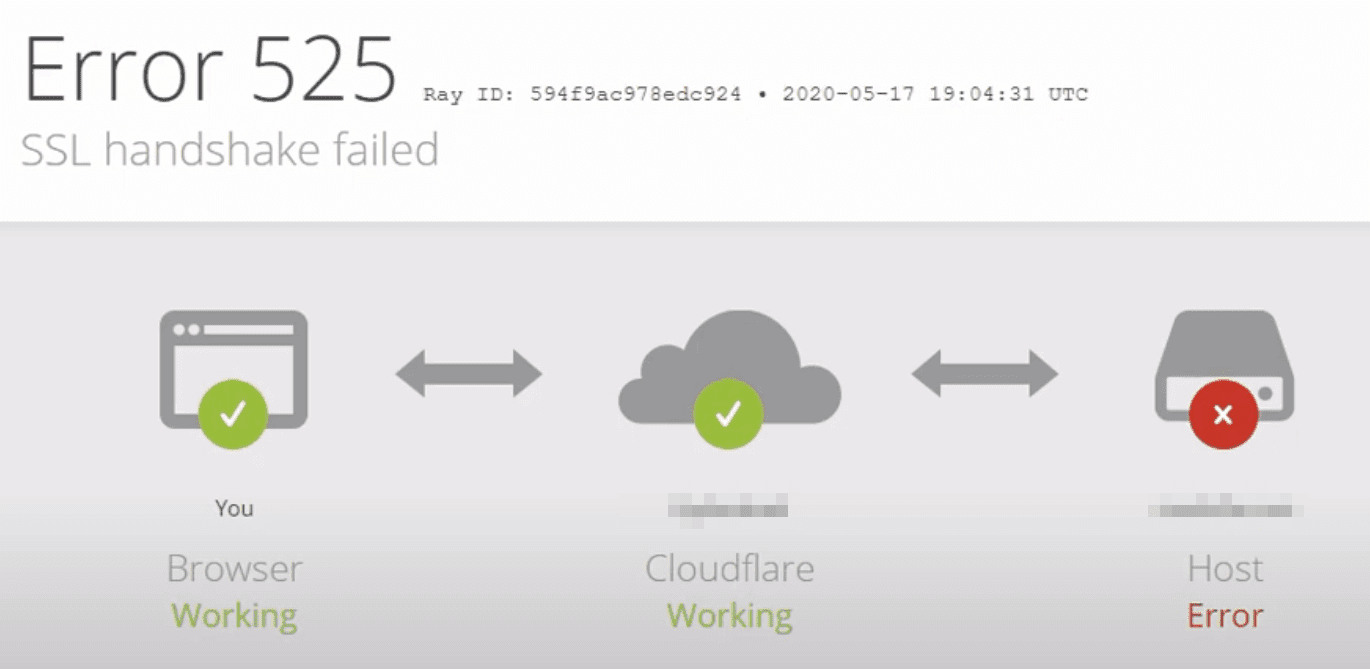
An SSL Handshake Failure or Error 525 means that the server and browser were unable to establish a secure connection. This can happen for a variety of reasons.
Generally, an Error 525 means that the SSL handshake between a domain using Cloudflare and the origin web server failed:
However, it’s also important to understand that SSL errors can happen on the client-side or the server-side. Common causes of SSL errors on the client-side include:
- The wrong date or time on the client device.
- An error with the browser configuration.
- A connection that is being intercepted by a third party.
Some server-side causes include:
- A cipher suite mismatch.
- A protocol used by the client that isn’t supported by the server.
- A certificate that is incomplete, invalid, or expired.
Typically, if the SSL handshake fails, the issue can be attributed to something wrong with the website or server and their SSL configurations.
How to Fix the SSL Handshake Failed Error (5 Methods)
There are several potential causes behind the “SSL Handshake Failed” error. So there’s no simple answer when it comes to how you should fix it.
Fortunately, there are a handful of methods you can use to begin exploring potential issues and resolving them one by one. Let’s take a look at five strategies you can use to try and fix the SSL Handshake Failed error.
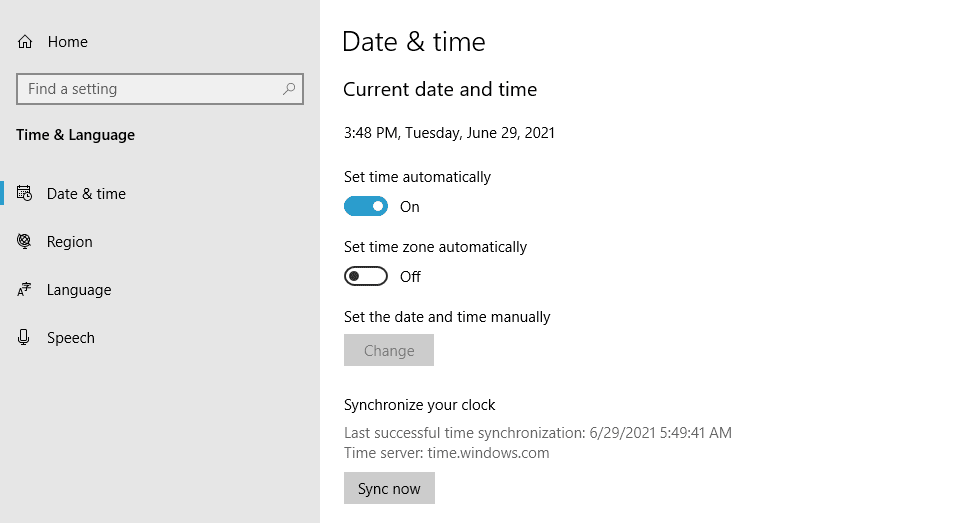
1. Update Your System Date and Time
Let’s start with one of the more unlikely causes, but one that is incredibly easy to correct if it is the problem: your computer’s clock.
If your system is using the wrong date and time, that may interrupt the SSL handshake. When the system clock is different than the actual time, for example, if it’s set too far into the future, it can interfere with the SSL certificate verification.
Your computer’s clock might have been set incorrectly due to human error or simply due to a glitch in your settings. Whatever the reason, it’s a good idea to check and make sure your system time is correct, and update it if it’s not.
Of course, if your clock is showing the correct information, it’s safe to assume that this isn’t the source of the “SSL Handshake Failed” issue.
2. Check to See If Your SSL Certificate Is Valid
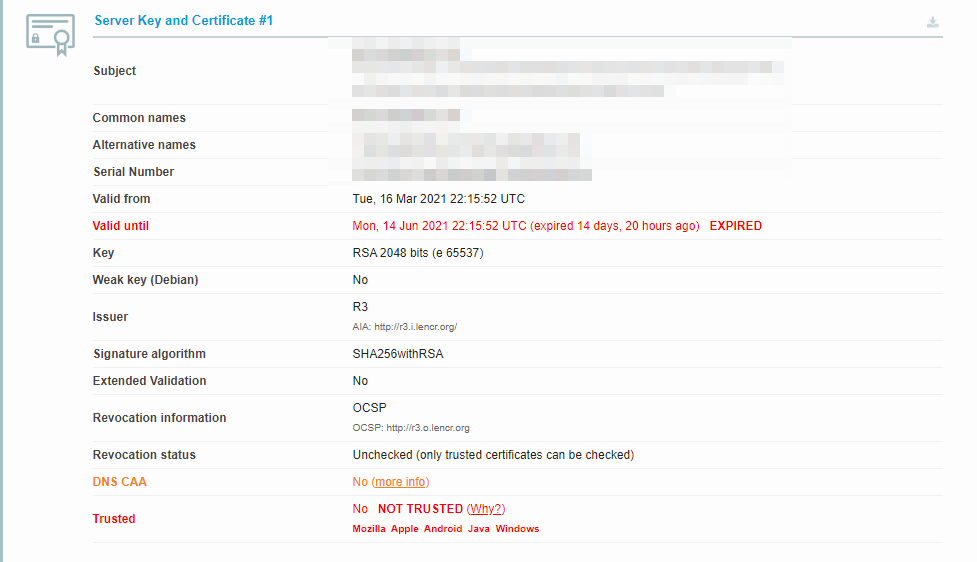
Expiration dates are placed on SSL certificates, to help make sure their validation information remains accurate. Generally, the validity of these certificates lasts for anywhere between six months and two years.
If an SSL certificate is revoked or expired, the browser will detect this and be unable to complete the SSL handshake. If it’s been more than a year or so since you installed an SSL certificate on your website, it might be time to reissue it.
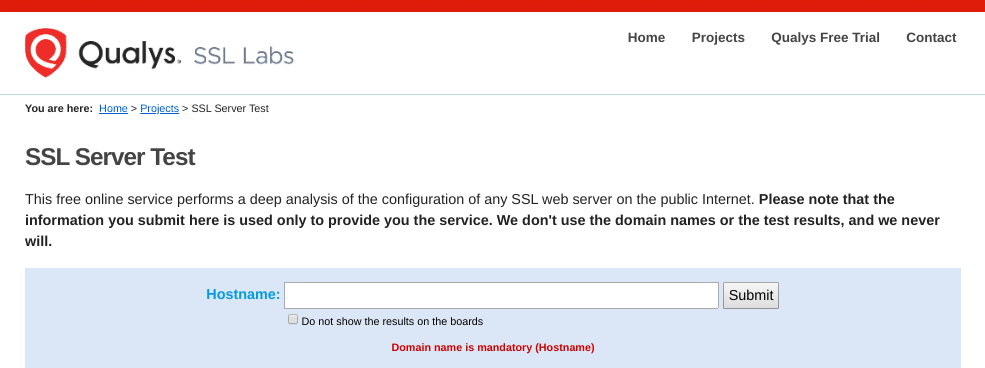
To view the status of your SSL certificate, you can use an SSL certificate checker tool such as the one offered by Qualys:
This tool is both reliable and free to use. All you need to do is input your domain name into the Hostname field, and then click on Submit. Once the checker is done analyzing your site’s SSL configuration, it will present you with some results:
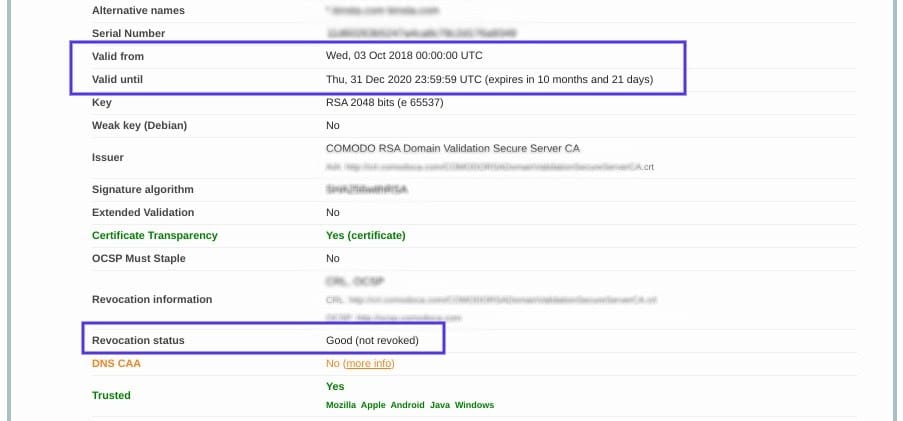
On this page, you can find out if your certificate is still valid and see if it has been revoked for any reason.
In either case, updating your SSL certificate should resolve the handshake error (and is vital for keeping your site and your WooCommerce store secure).
3. Configure Your Browser for the Latest SSL/TLS Protocol Support
Sometimes the best way to determine the root cause of an issue is by process of elimination. As we mentioned earlier, the SSL handshake failure can often occur due to a browser misconfiguration.
The quickest way to determine whether a particular browser is the problem is to try switching to a different one. This can at least help narrow down the problem. You may also try disabling any plugins and resetting your browser back to its default settings.
Another potential browser-related issue is a protocol mismatch. For example, if the server only supports TLS 1.2, but the browser is only configured for TLS 1.0 or TLS 1.1, there’s no mutually-supported protocol available. This will inevitably lead to an SSL handshake failure.
How you can check to see if this problem is occurring varies based on the browser you’re using. As an example, we’ll look at how the process works in Chrome. First, open your browser and go to Settings > Advanced. This will expand a number of menu options.
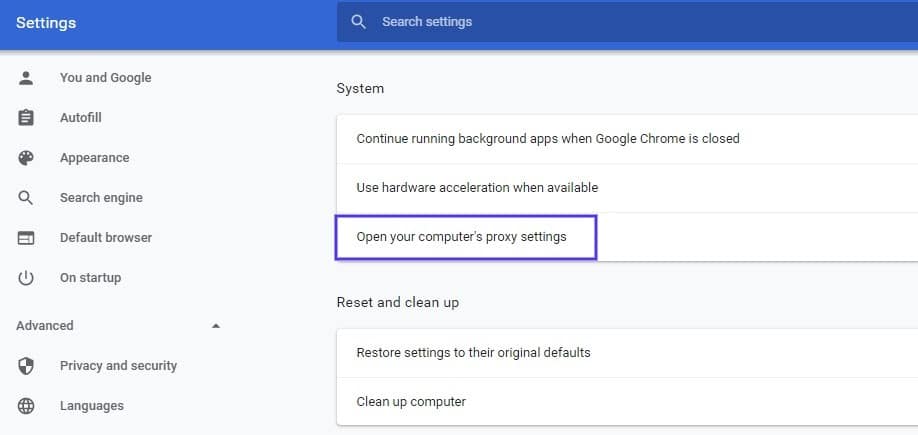
Under the System section, click on Open your computer’s proxy settings:
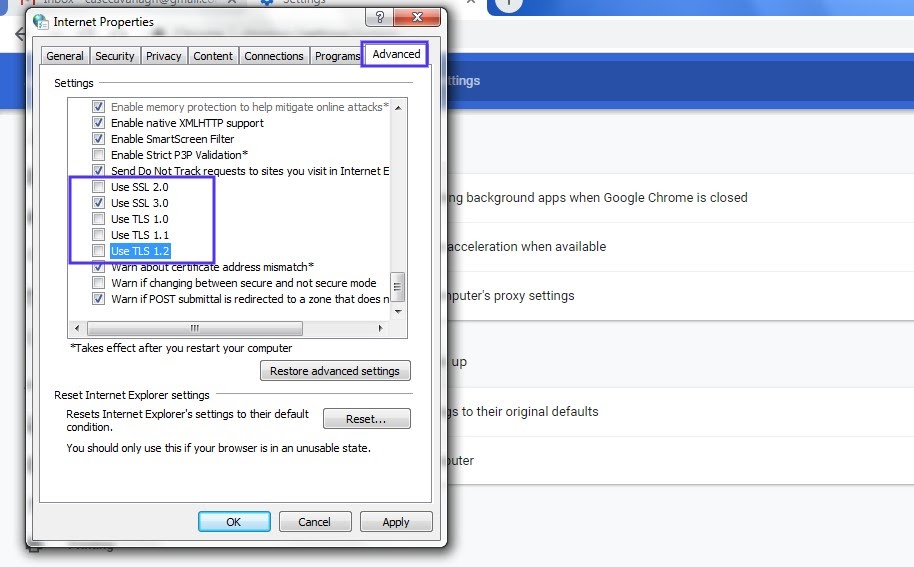
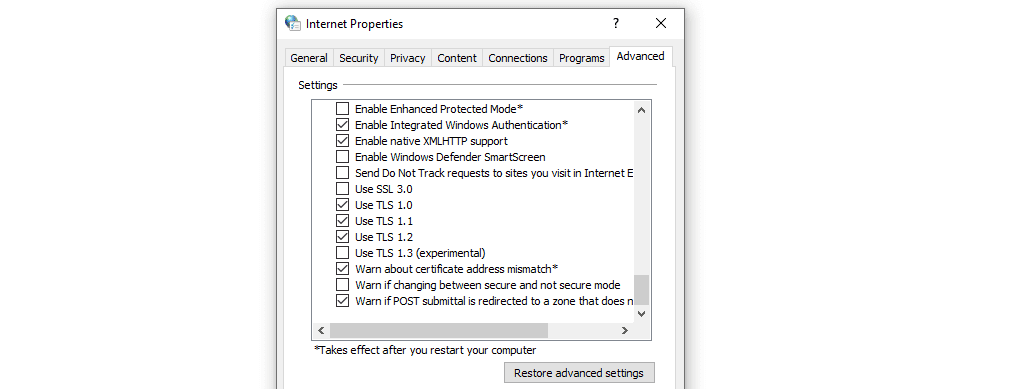
This will open up a new window. Next, select the Advanced tab. Under the Security section, check to see if the box next to Use TLS 1.2 is selected. If not, check that option:
It’s also recommended that you uncheck the boxes for SSL 2.0 and SSL 3.0.
The same applies to TLS 1.0 and TLS 1.1 since they are being phased out. When you’re done, click on the OK button, and check to see if the handshake error has been resolved.
Note that if you’re using Apple Safari or Mac OS there isn’t an option to enable or disable SSL protocols. TLS 1.2 is automatically enabled by default. If you’re using Linux, you can refer to the Red Hat guide on TLS hardening.
4. Verify That Your Server Is Properly Configured to Support SNI
It’s also possible that the SSL handshake failure is being caused by improper Server Name Indication (SNI) configuration. The SNI is what enables a web server to securely host several TLS certificates for one IP address.
Each website on a server has its own certificate. However, if the server isn’t SNI-enabled, that can result in an SSL handshake failure, because the server may not know which certificate to present.
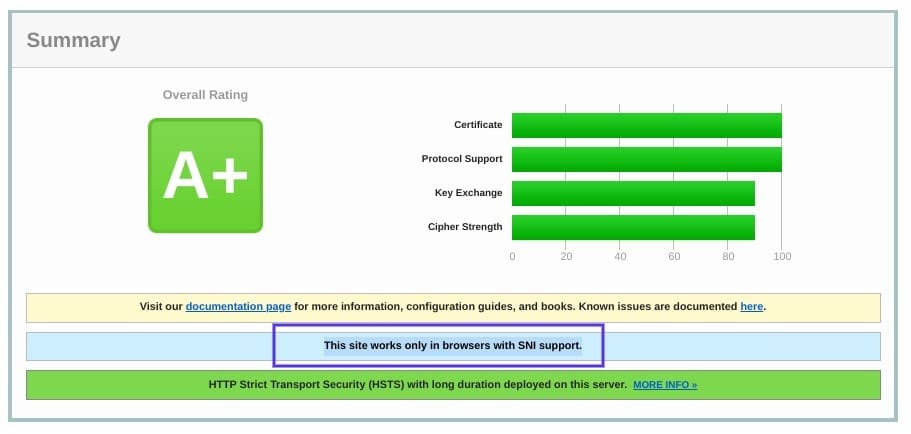
There are a few ways to check and see whether a site requires SNI. One option is to use Qualys’ SSL Server Test, which we discussed in the previous section. Input your site’s domain name, and then click on the Submit button.
On the results page, look for a message that reads “This site works only in browsers with SNI support”:
Another approach for detecting if a server is using SNI is to browse the server names in the ‘ClientHello’ message. This is a more technical process, but it can offer a lot of information.
It involves checking the extended hello header for a ‘server_name’ field, to see if the correct certifications are presented.
If you’re familiar with using tools such as the OpenSSL toolkit and Wireshark, you might find this method preferable. You can use openssl s_client with and without the -servername option:
# without SNI
$ openssl s_client -connect host:port
# use SNI
$ openssl s_client -connect host:port -servername hostIf you get two different certificates with the same name, it means that the SNI is supported and properly configured.
However, if the output in the returned certificates is different, or the call without SNI cannot establish an SSL connection, it indicates that SNI is required but not correctly configured. Resolving this issue may require switching to a dedicated IP address.
5. Make Sure the Cipher Suites Match
If you still haven’t been able to identify the cause of the SSL handshake failure, it might be due to a cipher suite mismatch. In case you’re unfamiliar with the term, ‘cipher suites’ refer to a set of algorithms, including ones for key exchange, bulk encryption, and message authentication code, that can be used for securing SSL and TLS network connections.
If the cipher suites that a server uses don’t support or match what’s used by Cloudflare, that can result in an “SSL Handshake Failed” error.
When it comes to figuring out whether there is a cipher suite mismatch, Qualys’ SSL Server Test proves yet again to be a useful tool.
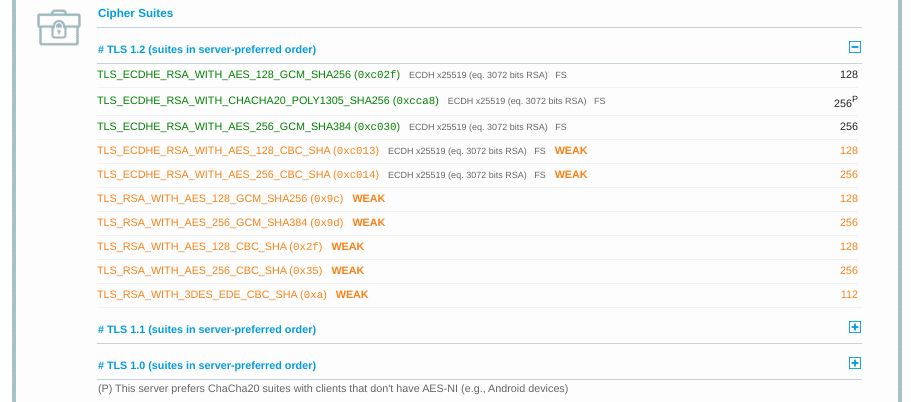
When you input your domain and click on Submit, you’ll see a summary analysis page. You can find the cipher information under the Cipher Suites section:
You can use this page to discover which ciphers and protocols the server supports. You’ll want to look out for any that display the ‘weak’ status. In addition, this section also details the specific algorithms for the cipher suites.
To correct this issue, you can compare the results against what your browser supports by using the Qualys SSL/TLS Capabilities of Your Browser tool. For more extensive information and guidance about cipher suites, we also recommend checking out the ComodoSSLStore guide.
Confused by the ‘SSL Handshake Failed’ error message? This guide explains what it is and, most importantly, 5 ways to fix it 🙌Click to Tweet
Summary
One of the most perplexing yet common types of SSL-related problems is the “SSL Handshake Failed” error. Dealing with this error can be stressful since it has many potential causes, including both client- and server-side issues.
However, there are some reliable solutions you can use to identify the problem and resolve it. Here are five ways you can use to fix the SSL Handshake Failed error:
- Update your system date and time.
- Check to see if your SSL certificate is valid (and reissue it if necessary).
- Configure your browser to support the latest TLS/SSL versions.
- Verify that your server is properly configured to support SNI.
- Make sure the cipher suites match.
Get all your applications, databases and WordPress sites online and under one roof. Our feature-packed, high-performance cloud platform includes:
- Easy setup and management in the MyKinsta dashboard
- 24/7 expert support
- The best Google Cloud Platform hardware and network, powered by Kubernetes for maximum scalability
- An enterprise-level Cloudflare integration for speed and security
- Global audience reach with up to 35 data centers and 275 PoPs worldwide
Test it yourself with $20 off your first month of Application Hosting or Database Hosting. Explore our plans or talk to sales to find your best fit.
Installing a Secure Sockets Layer (SSL) certificate on your WordPress site enables it to use HTTPS to ensure secure connections. Unfortunately, there are a variety of things that can go wrong in the process of confirming a valid SSL certificate and making a connection between your site’s server and a visitor’s browser.
If you’ve encountered an “SSL Handshake Failed” error message and are confused as to what it means, you’re not alone. It’s a common error that doesn’t tell you much on its own. While this can be a frustrating experience, the good news is that there are simple steps you can take to resolve the issue.
In this post, we’ll explain what the SSL Handshake Failed error is and what causes it. Then we’ll provide you with several methods you can use to fix it.
Let’s get started!
An Introduction to the SSL Handshake
Before we dig deeper into what causes a TLS or SSL handshake failure, it’s helpful to understand what the TLS/SSL handshake is. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols used to authenticate data transfers between servers and external systems such as browsers.
SSL certificates are needed in order to secure your website using HTTPS. We won’t get too in-depth about the difference between TLS vs SSL since it’s a minor one. The terms are often used interchangeably, so for simplicity’s sake, we’ll use “SSL” to refer to both.
With that out of the way, an SSL handshake is the first step in the process of establishing an HTTPS connection. To authenticate and establish the connection, the user’s browser and the website’s server must go through a series of checks (the handshake), which establish the HTTPS connection parameters.
Let us explain: the client (typically the browser) sends a request for a secure connection to the server. After the request is sent, the server sends a public key to your computer and checks that key against a list of certificates. The computer then generates a key and encrypts it, using the public key sent from the server.
To make a long story short, without the SSL handshake, a secure connection won’t be made. This can pose a significant security risk. Plus, there are a lot of moving parts involved in the process.
That means there are many different opportunities for something to go wrong and cause a handshake failure, or even lead to the “your connection is not private” error, causing visitors to leave.
Confronted with the ‘SSL Handshake Failed’ error? 🤝 Get a grip on how to solve it with these 5 methods ⤵️Click to Tweet
Understanding What Causes SSL Handshake Failures
An SSL Handshake Failure or Error 525 means that the server and browser were unable to establish a secure connection. This can happen for a variety of reasons.
Generally, an Error 525 means that the SSL handshake between a domain using Cloudflare and the origin web server failed:
However, it’s also important to understand that SSL errors can happen on the client-side or the server-side. Common causes of SSL errors on the client-side include:
- The wrong date or time on the client device.
- An error with the browser configuration.
- A connection that is being intercepted by a third party.
Some server-side causes include:
- A cipher suite mismatch.
- A protocol used by the client that isn’t supported by the server.
- A certificate that is incomplete, invalid, or expired.
Typically, if the SSL handshake fails, the issue can be attributed to something wrong with the website or server and their SSL configurations.
How to Fix the SSL Handshake Failed Error (5 Methods)
There are several potential causes behind the “SSL Handshake Failed” error. So there’s no simple answer when it comes to how you should fix it.
Fortunately, there are a handful of methods you can use to begin exploring potential issues and resolving them one by one. Let’s take a look at five strategies you can use to try and fix the SSL Handshake Failed error.
1. Update Your System Date and Time
Let’s start with one of the more unlikely causes, but one that is incredibly easy to correct if it is the problem: your computer’s clock.
If your system is using the wrong date and time, that may interrupt the SSL handshake. When the system clock is different than the actual time, for example, if it’s set too far into the future, it can interfere with the SSL certificate verification.
Your computer’s clock might have been set incorrectly due to human error or simply due to a glitch in your settings. Whatever the reason, it’s a good idea to check and make sure your system time is correct, and update it if it’s not.
Of course, if your clock is showing the correct information, it’s safe to assume that this isn’t the source of the “SSL Handshake Failed” issue.
2. Check to See If Your SSL Certificate Is Valid
Expiration dates are placed on SSL certificates, to help make sure their validation information remains accurate. Generally, the validity of these certificates lasts for anywhere between six months and two years.
If an SSL certificate is revoked or expired, the browser will detect this and be unable to complete the SSL handshake. If it’s been more than a year or so since you installed an SSL certificate on your website, it might be time to reissue it.
To view the status of your SSL certificate, you can use an SSL certificate checker tool such as the one offered by Qualys:
This tool is both reliable and free to use. All you need to do is input your domain name into the Hostname field, and then click on Submit. Once the checker is done analyzing your site’s SSL configuration, it will present you with some results:
On this page, you can find out if your certificate is still valid and see if it has been revoked for any reason.
In either case, updating your SSL certificate should resolve the handshake error (and is vital for keeping your site and your WooCommerce store secure).
3. Configure Your Browser for the Latest SSL/TLS Protocol Support
Sometimes the best way to determine the root cause of an issue is by process of elimination. As we mentioned earlier, the SSL handshake failure can often occur due to a browser misconfiguration.
The quickest way to determine whether a particular browser is the problem is to try switching to a different one. This can at least help narrow down the problem. You may also try disabling any plugins and resetting your browser back to its default settings.
Another potential browser-related issue is a protocol mismatch. For example, if the server only supports TLS 1.2, but the browser is only configured for TLS 1.0 or TLS 1.1, there’s no mutually-supported protocol available. This will inevitably lead to an SSL handshake failure.
How you can check to see if this problem is occurring varies based on the browser you’re using. As an example, we’ll look at how the process works in Chrome. First, open your browser and go to Settings > Advanced. This will expand a number of menu options.
Under the System section, click on Open your computer’s proxy settings:
This will open up a new window. Next, select the Advanced tab. Under the Security section, check to see if the box next to Use TLS 1.2 is selected. If not, check that option:
It’s also recommended that you uncheck the boxes for SSL 2.0 and SSL 3.0.
The same applies to TLS 1.0 and TLS 1.1 since they are being phased out. When you’re done, click on the OK button, and check to see if the handshake error has been resolved.
Note that if you’re using Apple Safari or Mac OS there isn’t an option to enable or disable SSL protocols. TLS 1.2 is automatically enabled by default. If you’re using Linux, you can refer to the Red Hat guide on TLS hardening.
4. Verify That Your Server Is Properly Configured to Support SNI
It’s also possible that the SSL handshake failure is being caused by improper Server Name Indication (SNI) configuration. The SNI is what enables a web server to securely host several TLS certificates for one IP address.
Each website on a server has its own certificate. However, if the server isn’t SNI-enabled, that can result in an SSL handshake failure, because the server may not know which certificate to present.
There are a few ways to check and see whether a site requires SNI. One option is to use Qualys’ SSL Server Test, which we discussed in the previous section. Input your site’s domain name, and then click on the Submit button.
On the results page, look for a message that reads “This site works only in browsers with SNI support”:
Another approach for detecting if a server is using SNI is to browse the server names in the ‘ClientHello’ message. This is a more technical process, but it can offer a lot of information.
It involves checking the extended hello header for a ‘server_name’ field, to see if the correct certifications are presented.
If you’re familiar with using tools such as the OpenSSL toolkit and Wireshark, you might find this method preferable. You can use openssl s_client with and without the -servername option:
# without SNI
$ openssl s_client -connect host:port
# use SNI
$ openssl s_client -connect host:port -servername hostIf you get two different certificates with the same name, it means that the SNI is supported and properly configured.
However, if the output in the returned certificates is different, or the call without SNI cannot establish an SSL connection, it indicates that SNI is required but not correctly configured. Resolving this issue may require switching to a dedicated IP address.
5. Make Sure the Cipher Suites Match
If you still haven’t been able to identify the cause of the SSL handshake failure, it might be due to a cipher suite mismatch. In case you’re unfamiliar with the term, ‘cipher suites’ refer to a set of algorithms, including ones for key exchange, bulk encryption, and message authentication code, that can be used for securing SSL and TLS network connections.
If the cipher suites that a server uses don’t support or match what’s used by Cloudflare, that can result in an “SSL Handshake Failed” error.
When it comes to figuring out whether there is a cipher suite mismatch, Qualys’ SSL Server Test proves yet again to be a useful tool.
When you input your domain and click on Submit, you’ll see a summary analysis page. You can find the cipher information under the Cipher Suites section:
You can use this page to discover which ciphers and protocols the server supports. You’ll want to look out for any that display the ‘weak’ status. In addition, this section also details the specific algorithms for the cipher suites.
To correct this issue, you can compare the results against what your browser supports by using the Qualys SSL/TLS Capabilities of Your Browser tool. For more extensive information and guidance about cipher suites, we also recommend checking out the ComodoSSLStore guide.
Confused by the ‘SSL Handshake Failed’ error message? This guide explains what it is and, most importantly, 5 ways to fix it 🙌Click to Tweet
Summary
One of the most perplexing yet common types of SSL-related problems is the “SSL Handshake Failed” error. Dealing with this error can be stressful since it has many potential causes, including both client- and server-side issues.
However, there are some reliable solutions you can use to identify the problem and resolve it. Here are five ways you can use to fix the SSL Handshake Failed error:
- Update your system date and time.
- Check to see if your SSL certificate is valid (and reissue it if necessary).
- Configure your browser to support the latest TLS/SSL versions.
- Verify that your server is properly configured to support SNI.
- Make sure the cipher suites match.
Get all your applications, databases and WordPress sites online and under one roof. Our feature-packed, high-performance cloud platform includes:
- Easy setup and management in the MyKinsta dashboard
- 24/7 expert support
- The best Google Cloud Platform hardware and network, powered by Kubernetes for maximum scalability
- An enterprise-level Cloudflare integration for speed and security
- Global audience reach with up to 35 data centers and 275 PoPs worldwide
Test it yourself with $20 off your first month of Application Hosting or Database Hosting. Explore our plans or talk to sales to find your best fit.
BNAME.RU » Код ошибки HTTP 525 SSL Handshake Failed Cloudflare
Ошибка 525: не удалось установить соединение SSL.
Ошибки 525 часто возникают из-за проблем с конфигурацией исходного веб-сервера. Ошибка 525 возникает, когда выполняются эти два условия:
- Связывание SSL между Cloudflare и исходным веб-сервером не удается, и
- Полный или полный (строгий) SSL устанавливается на вкладке «Обзор» вашего приложения Cloudflare SSL / TLS.
Как устранить ошибку 525 SSL handshake failed?
Обратитесь к своему хостинг-провайдеру, чтобы исключить следующие распространенные причины на вашем исходном веб-сервере:
- Не установлен действующий сертификат SSL
- Порт 443 (или другой настраиваемый безопасный порт) не открыт
- Нет поддержки SNI
- Наборы шифров, принятые Cloudflare, не совпадают с наборами шифров, поддерживаемыми исходным веб-сервером.
Если 525 ошибок возникают периодически, просмотрите журналы ошибок исходного веб-сервера, чтобы определить причину. Настройте Apache для регистрации ошибок mod_ssl. Кроме того, nginx включает ошибки SSL в свой стандартный журнал ошибок, но может потребовать повышения уровня журнала.
Are you looking forward to resolving Error 525 SSL handshake failed?
The error indicates that the SSL handshake between Cloudflare and the origin web server failed.
This problem happens mainly because of an invalid SSL certificate, closed port 445, etc.
At Bobcares, we often get requests from our customers to fix the Error 525 SSL handshake failed as part of our Server Management Services.
Today, let’s have a look for the reason of this error. We’ll also see how our Support Engineers fix this error.
Why Error 525 SSL handshake failed?
The error 525 essentially means the SSL handshake between Cloudflare and the origin web server failed. This inturn causes the error to pop up while accessing the website.
Again, this error occurs on the domain using Cloudflare Full or Full (Strict) SSL mode.
The most common causes of this error are:
- No valid SSL certificate installed on the website
- The website is not listening on port 443.
- The SNI is not supported by the website(sometimes not configured to SNI)
- The cipher suites that Cloudflare uses do not match what the origin accepts
While accessing the website the error appears as:
The major reasons and fixes of this error
At Bobcares, where we have more than a decade of expertise in managing servers, we see many customers face problems with error 525 SSL handshake failed.
Now, let’s see the major reasons for this error and how our Support Engineers fix it.
Invalid certificate
One of the major reasons for this error is due to the website not having a valid SSL certificate.
Therefore, when a customer reports the error, we check for the SSL certificate expiry date. If expired, we install the valid SSL certificate for the domain. Also, we double-check if the website uses the correct certificate.
Port 443
Recently, one of the customers approached us with the same error. On further analyzing, we could trace that the issue was due to closed SSL secure port 443.
We have checked that whether the port 443 was listening or not, by applying the command follows.
netstat -nltp | grep : 443We could see that the port was not listening and it was closed. So that we opened the SSL port and that fixed the problem.
SNI
Also, another major cause of the error is the improper configuration of SNI.
Server Name Indication (SNI) allows the server to safely host multiple TLS Certificates for multiple sites, all under a single IP address.
Here, we check and make sure whether the SNI is properly configured on the website. If the SNI is not supported or configured will cause this error to pop up.
If the server is not having SNI, then the website should need a dedicated IP address to avoid this error.
Cipher suites
Similarly, Cipher Suites also can be a cause for the 525 error.
A cipher suite is a set of algorithms that help secure a network connection that uses Transport Layer Security (TLS) or its now-deprecated predecessor Secure Socket Layer (SSL). The set of algorithms that cipher suites usually include: a key exchange algorithm, a bulk encryption algorithm, and a message authentication code (MAC) algorithm.
In certain cases, the cipher suites that the origin server uses do not match with Cloudflare. The cipher suites 115 that Cloudflare accepts 29 and the cipher suites that the origin server supports do not match. Thus, to fix the error, we always ensure that the version of Open SSL supports the cipher suites that Cloudflare support.
[Need assistance to fix Cloudflare error? We’ll help you.]
Conclusion
In short, Error 525 SSL handshake failed to occur mainly due to invalid SSL certificate, closed 443 port, SNI problem, and so on. Today, we have discussed this error in detail and saw how our Support Engineers fix this error for our customers.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
I switched with my Domain to Cloudflare and now I’m trying to use CloudFlare’s SSL Feature.
I already own a SSL cert from StartSSL so I would be possible to set the settings to ‘Full (Strict)’ but I don’t want to so I turned it to ‘Full’.
Now I’m getting 525 Errors, after a ‘Retry for a live Version’ everything is okay.
But I’m getting this Error everytime.
Has anyone an idea ?
Thank you
Picture of my Error
asked Dec 5, 2015 at 9:32
Change Cloudflare SSL/TLS encryption mode in to Flexible. it worked for me.
answered Jan 7, 2020 at 14:04
1
A 525 error indicates that CloudFlare was unable to contact your origin server and create a SSL connection with it.
This can be due to:
- Your servers not having matching or compatible SSL Ciphers
- Your website may not have a certificate installed properly
- Your website may not have a dedicated IP OR is not configured to use SNI
Attempt to contact your hosting provider for assistance to ensure that your SSL certificate is setup correctly. If you are using a control panel, a quick google search can help you find a install guide for that said control panel.
answered Dec 6, 2015 at 8:07
1
Visit SSL/TLS tab in Cloudflare. Then:
- Switch Your SSL/TLS encryption mode to Flexible.
- Make sure to switch On «Always Use HTTPS» under «Edge Certificate» tab.
This will transfer all your request from Http to Https automatically. And if you’ll implement custom SSL certificate on your hosting server then this 525 error will automatically disappear without changing anything on Cloudflare.
answered Mar 14, 2021 at 17:48
Amar KumarAmar Kumar
2,2242 gold badges23 silver badges33 bronze badges
1
Got the same problem a few days ago.
Our DevOps contacted support and found out that Cloudflare changed certificate type or smth in that way. Asked to return everything back.
That helped.
answered Nov 12, 2019 at 10:07
muinhmuinh
4866 silver badges14 bronze badges
1
I went through the same problem today and found that (at least in my case) it was the lack of TLS v1.3
I had just made a server using nginx + php-fpm and a self signed ssl to use below CloudFlare proxy.
When I switched from the production server to this new one, it gave error 525.
I gave the command: curl -I https://your_server_public_ip/ and it returned the error:
error: 1408F10B: SSL routines: ssl3_get_record: wrong version number
This error is described in the CloudFlare community at:
https://community.cloudflare.com/t/community-tip-fixing-error-525-ssl-handshake-failed/44256
There they advise turning off TLS v1.3 on the CloudFlare panel, but I decided to try installing it.
Using nginx is so easy that I don’t know why to have it shut down.
Only add TLSv1.3 like this-> ssl_protocols TLSv1.2 TLSv1.3; in your nginx/snippets/ssl-params.conf file (default Ubuntu 20 and 18) that will work and you still use the latest and most secure protocols.
answered Jun 17, 2020 at 23:33
Felipe LimaFelipe Lima
4231 gold badge9 silver badges18 bronze badges
TROUBLESHOOTING 525 SSL HANDSHAKE ERROR
Error 525 indicates that the SSL handshake between Cloudflare and the origin web server failed. This only occurs when the domain is using Cloudflare Full or Full (Strict) SSL mode. This is typically caused by a configuration issue in the origin web server, when this happens, you’ll see “Error 525: SSL handshake failed”
Quick Fix Ideas
- If you are a site visitor, report the problem to the site owner. Neither this Community nor Cloudflare Support can assist you. Cloudflare Support only works with the verified owner of the domain.
- Make sure you have a valid SSL certificate installed on your origin server.
- Check with your hosting provider to make sure they’re listening on port 443.
- Check to make sure your origin server is properly configured for SNI 1.2k.
- The cipher suites 289 that Cloudflare accepts 242 and the cipher suites that the origin server supports do not match. Review the cipher suites your server is using to ensure they match what is supported by Cloudflare. A cipher suite is a set of algorithms that help secure a network connection that uses Transport Layer Security (TLS) or its now-deprecated predecessor Secure Socket Layer (SSL). The set of algorithms that cipher suites usually include: a key exchange algorithm, a bulk encryption algorithm, and a message authentication code (MAC) algorithm.
- If you are the site owner and you’re only seeing errors intermittently, this suggests the TCP connection between Cloudflare and your origin is being reset during the SSL handshake causing the error. Ask your hosting provider/system administrator to check if there are any server issues. Reviewing your webserver access/error logs would be a good place to locate this information.
- Note that Apache must be configured 279 to log mod_ssl errors and Nginx includes these errors in its standard error log, but it may be necessary to increase the log level.
- Pause 110 Cloudflare or update your local hosts file to point directly at your server IP to test that your server is presenting an SSL certificate. If you do not have a certificate installed on your server you can generate one using our Origin CA 275 certificates. This is a free certificate for the purpose of encrypting the connection between Cloudflare and your web server so that you do not need to purchase a certificate.
- If you cURL to the origin on port 443 and receive the error
error:1408F10B:SSL routines:ssl3_get_record:wrong version number, disable TLS 1.3 on the Edge Certificates tab of the SSL/TLS app on the Cloudflare dashboard.
Setting up a Secure Sockets Layer (SSL) certificate for your website has never been easier. You can generate certificates for free, and many hosting providers will even set them up for you. However, if you don’t configure your certificate properly, you may encounter errors such as “SSL handshake failed”.
The “SSL handshake failed” error shows up when your browser and the server can’t establish a secure connection. This article will explain what an SSL handshake is and what to do if you fail to establish one.
Let’s get to it!
What Is an SSL Handshake?
As you may know, an SSL certificate validates your website’s “identity”. It does that using a cryptographic key that your browser checks to make sure the certificate is valid. Once you establish a connection, your browser can decrypt the content that the server sends it.
This process is called a “handshake”. Here’s how it works in more detail:
- You visit a website with an SSL certificate and your browser sends a request for data.
- The server sends the browser an encrypted public key.
- Your browser checks that key and sends its encrypted key back to the server.
- The server decrypts the key and sends encrypted content back to your browser.
- Your browser decrypts the content (hence completing the handshake).
All of this happens in seconds. SSL certificates and the HTTPS protocol enable your website to transmit data securely, without negatively impacting performance. That makes an SSL certificate vital for any website. However, like any element of your site, it can occasionally create unique problems.
What Causes the “SSL Handshake Failed” Error
The “SSL handshake failed” error tells you precisely what the problem is. It shows up when your browser fails to establish a connection with a website that has an SSL certificate:
In this example from a website using Cloudflare, you can see that the “SSL handshake failed” error corresponds to the “525” code. Thus, the error can stem from both server- and client-side problems.
The most common causes of the “SSL handshake failed” error include:
- Your local device has the wrong date or time
- The browser doesn’t support the latest SSL protocol
- Your SSL certificate is invalid
- There’s a problem with your Server Name Identification (SNI) configuration
- There’s an issue with your Content Delivery Network (CDN), such as Cloudflare
That list includes two local issues, two that are related to your website’s server, and one that’s specific to a third-party service. In the next sections, we’ll explore how to tackle each of them.
How to Fix the “SSL Handshake Failed” Error (5 Ways)
Here, we’re going to start by showing you how to fix the client-side issues that can cause the “SSL handshake failed” error. Those solutions are pretty simple. In case they don’t work, however, we’ll then move on to more technical solutions you can try.
1. Update Your Local Device’s Date and Time
When your browser tries to establish an SSL handshake, it verifies the certificate against your computer’s date and time. It does this to verify that the SSL certificate is still valid.
If your local device’s date and time are off, that can lead to errors during the verification process (i.e., no handshake). Fortunately, this is an issue with a simple fix.
On a Windows device, open the Start menu and type in Date & Time settings. Select the option that appears, and a new window will pop up. Enable the setting Set time automatically, and ensure that your time zone is correct:
Verify that your date is now correct, and then try to reload the website.
Here’s how to fix your date and time on other Operating Systems (OSs):
- macOS
- iOS
- Android
If fixing the date and time on your local device doesn’t do the trick, you can move on to the next fix.
2. Ensure That Your Browser Supports the Latest TLS Protocol
In some cases, you may run into the “SSL handshake failed” error due to problems with your browser. The most common issue is that your browser doesn’t support the Transport Layer Security (TLS) protocol that your certificate uses.
To put it simply, both SSL and TLS are authentication protocols, and your certificate may use either one. Modern browsers support both protocols, but their older versions might not.
The easiest way to determine whether your browser is causing the issue is to use another one. If the “SSL handshake failed” error doesn’t appear in other browsers, the original one may be the problem.
To fix this issue in Windows, open the Start menu and type in Internet Options. Select the option that appears and go to the Advanced tab. Scroll down the list of settings until you find the options that correspond to SSL and TLS settings:
Ideally, you should un-check the box for SSL 3 and 2 (if you see those options). You only need to check the boxes for TLS 1, 1.1, and 1.2.
Then save the changes to your internet options and try re-accessing the website. Note that if you’re using macOS or iOS, TLS 1.2 should be enabled by default.
3. Make Sure Your SSL Certificate Is Valid
SSL certificates have expiration dates. That’s a built-in function that forces you to renew the certificate at some point, and validate your domain ownership.
If your SSL certificate expires, your browser won’t be able to establish a handshake. Depending on who your SSL certificate provider is, you’ll probably receive notifications well before it expires so you can renew it.
Even so, it doesn’t hurt to check if you’re not sure about your certificate’s expiration date. You can use a tool such as SSL Server Test to do so:
The service will return a lot of information about your website’s SSL certificate. If the certificate expired, you’ll see when its validity ran out:
In this case, you’ll need to re-issue and install the SSL certificate on your website. Depending on who your hosting provider is, they might be able to help with that process.
4. Check Your Server’s Server Name Identification (SNI) Configuration
If you’re using a shared server to host your website, you can run into issues with multiple SSL certificates. Hosting providers use proper Server Name Identification (SNI) configuration to ensure that when visitors try to access your site, they get the correct SSL certificate (and not one from another property).
Generally speaking, most reputable hosting providers won’t present any issues with SNI configuration. Additionally, if you’re not using a shared server, you can move on to the next fix.
If you want to be 100% sure that your hosting provider isn’t presenting any issues with SNI configuration, you can contact its support for help. On a shared server, you won’t be able to access this configuration directly. If this turns out to be the problem, you may want to consider upgrading to a more robust hosting plan.
5. Pause Cloudflare to Test Your SSL Certificate
If you’re using Cloudflare, the “SSL handshake failed” error can be due to a problem with its connection to your website. The easiest way to test this is by temporarily disabling it.
Fortunately, Cloudflare offers a “pausing” feature you can use to disable the service at any time. Once you do this, we recommend clearing your browser’s cache before trying to access your website again.
If the SSL handshake error is gone, you’ll want to contact Cloudflare to see what the problem might be. While you wait for a response, keep the CDN disabled so other users can also access your website. On the other hand, if the SSL error persists, that means it’s probably due to an error with your server’s configuration (see above).
Conclusion
The “SSL handshake failed” error is relatively easy to fix, as long as you’re aware of what its potential causes are. The error might be due to an issue with your local device’s settings, your server’s configuration, or your CDN.
Here’s what you might need to do to fix the “SSL handshake failed” error:
- Update your local device’s date and time.
- Ensure that your browser supports the latest TLS protocol.
- Make sure your SSL certificate is valid.
- Check your server’s SNI configuration.
- Pause Cloudflare to test your SSL certificate.
Do you have any questions about how to fix the “SSL handshake failed” error? Let’s talk about them in the comments section below!
Featured Image via vladwel / shutterstock.com