I try to start wifite on VMware (Kali) but doesnt work, is there a possibility to use the local network card (Intel(R) Dual Band Wireless-AC 3168) to let search the VM for available networks?
This is the error message i received:
root@kali:~# wifite
. .
.´ · . . · `. wifite 2.2.5
: : : (¯) : : : automated wireless auditor
`. · ` /¯ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯ ´
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[!] Conflicting processes: NetworkManager (PID 555), wpa_supplicant (PID 739), dhclient (PID 1454)
[!] If you have problems: kill -9 PID or re-run wifite with --kill)
[+] Checking airmon-ng...
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File "/usr/lib/python2.7/dist-packages/wifite/__main__.py", line 93, in entry_point
[!] wifite.start()
[!] File "/usr/lib/python2.7/dist-packages/wifite/__main__.py", line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File "/usr/lib/python2.7/dist-packages/wifite/config.py", line 129, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File "/usr/lib/python2.7/dist-packages/wifite/tools/airmon.py", line 299, in ask
[!] raise Exception('airmon-ng did not find any wireless interfaces')
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting*
I am new to Kali Linux and I have tried every method I know but every time I start up Wifite, this is the message that comes up, «Exception: airmon-ng did not find any wireless interfaces».
This the output after running Wifite:
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[+] Checking airmon-ng…
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File «/home/ /wifite2/wifite/main.py», line 93, in entry_point
[!] wifite.start()
[!] File «/home/ /wifite2/wifite/main.py», line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File «/home/ /wifite2/wifite/config.py», line 132, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File «/home/ /wifite2/wifite/tools/airmon.py», line 299, in ask
[!] raise Exception(‘airmon-ng did not find any wireless interfaces’)
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting
Anyone have any suggestions on how to fix this?
I am using ubuntu in vmware and for using airmon-ng, I already download it from terminal.
But when I run it it says
root@DESKTOP-SIVJTCS:/home/show# airmon-ng
PHY Interface Driver Chipset
so it doesnt show any interfaces name
then when i run ifconfig and finding my interface name
i run on terminal it says
root@DESKTOP-SIVJTCS:/home/show# airmon-ng start wifi0
PHY Interface Driver Chipset
at last when i run wifite it says
root@DESKTOP-SIVJTCS:/home/show# wifite
. .
.´ · . . · `. wifite2 2.5.2
: : : (¯) : : : a wireless auditor by @derv82
`. · ` /¯ ´ · .´ maintained by kimocoder
` /¯¯¯ ´ https://github.com/kimocoder/wifite2
[!] Warning: Recommended app bully was not found. install @ https://github.com/aanarchyy/bully
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app hashcat was not found. install @ https://hashcat.net/hashcat/
[!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[+] Checking airmon-ng...
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File "/usr/lib/python3/dist-packages/wifite/__main__.py", line 97, in entry_point
[!] wifite.start()
[!] File "/usr/lib/python3/dist-packages/wifite/__main__.py", line 50, in start
[!] Configuration.get_monitor_mode_interface()
[!] File "/usr/lib/python3/dist-packages/wifite/config.py", line 163, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File "/usr/lib/python3/dist-packages/wifite/tools/airmon.py", line 310, in ask
[!] raise Exception('airmon-ng did not find any wireless interfaces')
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting
-
Перейти на CTF площадку Игры Кодебай
Выполняйте задания по кибербезопасности в формате CTF и получайте бесценный опыт. Ознакомиться с подробным описанием можно тут.
-
B правой части каждого сообщения есть стрелки ⇧ и ⇩. Не стесняйтесь оценивать ответы. Чтобы автору вопроса закрыть свой тикет, надо выбрать лучший ответ. Просто нажмите значок ✔ в правой части сообщения.
-
#1
Приветствую всех! Увидел что на форуме могут помочь с Kali Linux и решил написать этот пост
Решил я воспользоваться инструментами Kali, включил Sub систему, которая работает на Винде 10, установил в Майкрософт сторе и все бы ничего…
Когда я воспользовался Wifite тот указал мне на ошибку:
Код:
[+] Checking airmon-ng...
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more infoЛогично что строка указывает что программа не может найти связь с сетью, походил я по сайту который шел дальше по строке, но он увы не помог моей проблеме, думаю фото ниже наглядно покажут что не так:
графы после введения команды airmon-ng пустуют, пробовал команду:
но увы, это не помогло, что я упустил или не сделал. Да, пожалуйста сразу тапком не кидайте, я просто человек который хотел немного побаловаться с Wifite////
-
#2
Можно предположить что Wi-Fi-адаптер не поддерживает monitor mode. Ну или Windows не совсем правильно пробрасывает адаптер в подсистему. Можно попробовать запустить LiveUSB с Kali и посмотреть будет ли в этом случае работать.
-
#3
Можно предположить что Wi-Fi-адаптер не поддерживает monitor mode. Ну или Windows не совсем правильно пробрасывает адаптер в подсистему. Можно попробовать запустить LiveUSB с Kali и посмотреть будет ли в этом случае работать.
идея хорошая, но я решил не возиться и скачать VirtualBox, с ним такая проблема отпадает
1: открыть терминал
[email protected]:~# wifite
. .
.´ · . . · `. wifite 2.2.5
: : : (¯) : : : automated wireless auditor
`. · ` /¯ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯ ´
[!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[!] Conflicting processes: NetworkManager (PID 506), dhclient (PID 564), wpa_supplicant (PID 1264)
[!] If you have problems: kill -9 PID or re-run wifite with --kill)
[+] Checking airmon-ng...
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File "/usr/lib/python2.7/dist-packages/wifite/__main__.py", line 93, in entry_point
[!] wifite.start()
[!] File "/usr/lib/python2.7/dist-packages/wifite/__main__.py", line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File "/usr/lib/python2.7/dist-packages/wifite/config.py", line 129, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File "/usr/lib/python2.7/dist-packages/wifite/tools/airmon.py", line 299, in ask
[!] raise Exception('airmon-ng did not find any wireless interfaces')
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting
2: ненормальный
Warning: Recommended app hcxdumptool was not found.3: Загрузите hcxdumptool
hcxtools v4.2.0 или выше
apt-get install libcurl4-openssl-dev libssl-dev zlib1g-dev libpcap-dev
git clone https://github.com/ZerBea/hcxtools
cd hcxtools
make
make installПримечание. Основная функция libcurl — подключаться и взаимодействовать с разными серверами, используя разные протоколы, т. Е. Инкапсулированный sockPHP поддерживает libcurl (позволяя вам подключаться и взаимодействовать с разными серверами, используя разные протоколы).
hcxdumptool v4.2.0 или выше
git clone https://github.com/ZerBea/hcxdumptool
cd hcxdumptool
make
make installhashcat v4.2.0 или выше
Версия hashcat в репозитории kali — 4.1, и также необходимо вручную установить более высокую версию hashcat.
wget https://hashcat.net/files/hashcat-4.2.1.7z
7z x hashcat-4.2.1.7z
service network-manager start
list / kill будет мешать процессу работы беспроводной сетевой карты
Использование: airmon-ng <check> [kill]
Перечислите все программы, которые могут мешать работе беспроводной сетевой карты. Если указан параметр kill, все программы будут остановлены.
airmon-ng check
Запустить WLAN
airmon-ng start wlan0
Airodump-ng wlan0mon
[email protected]:~# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
[email protected]:~# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
[email protected]:~# wifite
. .
.´ · . . · `. wifite 2.2.5
: : : (¯) : : : automated wireless auditor
`. · ` /¯ ´ · .´ https://github.com/derv82/wifite2
` /¯¯¯ ´
[!] Conflicting processes: NetworkManager (PID 5933), dhclient (PID 5948), wpa_supplicant (PID 6081)
[!] If you have problems: kill -9 PID or re-run wifite with --kill)
Interface PHY Driver Chipset
-----------------------------------------------------------------------
1. wlan0 phy0 mt7601u Ralink Technology, Corp. MT7601U
[+] enabling monitor mode on wlan0... enabled wlan0mon
NUM ESSID CH ENCR POWER WPS? CLIENT
--- ------------------------- --- ---- ----- ---- ------
1 (BC:5F:F6:4B:3D:D2) 12 WPA 99db no
2 TP-LINK_8393 11 WPA 62db no 1
3 TPGuest_8393 11 WPA 57db no
4 JCG Smart Wireless ... 8 WPA 28дБ нет
5 JCG-196998 8 WPA 28db no
6 ChinaNet-ZcJn 1 WPA 18db yes
7 TP-LINK_4128 11 WPA 17db no
8 ChinaNet-rL2d 7 WPA 17db yes
9 TP-LINK_92F6 6 WPA 16db no
10 (6C:59:40:15:57:C0) 6 WPA 14db no
11 HHP 1 WPA 13db no
12 Tenda_529690 8 WPA 12db no
13 ChinaNet-3Qj2 4 WPA 12db yes
[+] select target(s) (1-13) separated by commas, dashes or all: ^C
[!] Interrupted, Shutting down...
[!] Note: Leaving interface in Monitor Mode!
[!] To disable Monitor Mode when finished: airmon-ng stop wlan0mon
выберите цели (1-8), разделенные запятыми, тире или всеми: N (ваш выбор)
ОК: значение ключа будет отображаться как пароль.
apt install kali-linux-wireless
sudo apt install broadcom-sta-dkms
Затем я подключил USB WIFE, и все в порядке.
Вчера я также видел решение в китайской сети.
Первый шаг: введите airmon-ng check kill перед установкой режима прослушивания для завершения процесса
Шаг 2. Загрузите сетевую карту как прежде, чем airmon-ng запустит wlan0 (имя вашей сетевой карты)
Шаг 3. Он автоматически создаст интерфейс wlan0mon Запомните это имя интерфейса вместо предыдущего mon0
Шаг 4. Создание мониторинга airodump-ng wlan0mon
# wifite -h Просмотреть все параметры справки для wifite
Вот несколько вариантов, связанных с взломом wpa / wpa2
Взломать старый wep (в основном устранен, я все равно не видел) связанные варианты
О wps (новый протокол аутентификации, не напрямую проверяющий пароль, но использующий пин-код, для получения дополнительной информации, пожалуйста, гуглите сами), некоторые варианты взлома
0x03 Процесс использования wifite-скрипта следующий: вставьте заранее подготовленную карту беспроводной сети
использование:
wifite [-h] [—check CHECK] [—cracked] [—recrack] [—all][-i INTERFACE] [—mac] [—mon-iface MONITOR_INTERFACE][-c CHANNEL] [-e ESSID] [-b BSSID] [—showb] [—nodeauth][—power POWER] [—tx TX] [—quiet] [—wpa] [—wpat WPAT][—wpadt WPADT] [—strip] [—crack] [—dict DIC] [—aircrack][—pyrit] [—tshark] [—cowpatty] [—wep] [—pps PPS][—wept WEPT] [—chopchop] [—arpreplay] [—fragment][—caffelatte] [—p0841] [—hirte] [—nofakeauth][—wepca WEPCA] [—wepsave WEPSAVE] [—wps] [—pixie][—wpst WPST] [—wpsratio WPSRATIO] [—wpsretry WPSRETRY]
Подробное описание:
Необязательные параметры:
-h, —help показать это справочное сообщение и выйти
команда:
—check CHECK Проверить файл квитирования [файл] на наличие рукопожатия.
—cracked Отображает ранее взломанные точки доступа.
—recrack Включить взломанную сеть в цель.
Глобальный:
— все атаковать все цели.
-I ИНТЕРФЕЙС беспроводной интерфейс для захвата.
—mac Анонимный MAC-адрес.
—mon-iface MONITOR_INTERFACE Интерфейс уже находится в режиме мониторинга.
-C CHANNEL Цель сканирования канала.
-e ESSID Укажите конкретную точку доступа по ssid (имя).
-b BSSID Укажите конкретную точку доступа через bssid (mac).
—showb Показать целевой BSSID после сканирования.
—nodeauth Не отменять аутентификацию клиента при сканировании
-Power POWER атакует любую цель с силой сигнала> [pow].
—tx TX Установить уровень мощности TX адаптера.
—quiet Не печатать список точек доступа во время сканирования.
WPA:
—wpa только для сетей WPA (используйте —wps —wep).
—wpat WPAT Время (в секундах) ожидания завершения атаки WPA.
—wpadt WPADT Время ожидания между отправкой пакетов по умолчанию (в секундах).
—strip Используйте рукопожатие или пирит, чтобы пожать руку.
—crack Используйте файл словаря [dic] для взлома рукопожатия WPA.
—dict DIC DIC Специальный словарь, используемый в WPA.
—aircrack Используйте aircrack для подтверждения рукопожатия.
—pyrit Используйте pyrit для подтверждения рукопожатия.
—tshark Используйте tshark для подтверждения рукопожатия.
—cowpatty Используйте cowpatty для подтверждения рукопожатия.
WEP:
—wep Только для сети WEP.
—pps PPS Устанавливает количество пакетов, которые будут вводиться в секунду.
— WEPT WEPT ждать каждой атаки, 0 означает бесконечность.
-chopchop использует атаку chopchop.
—arpreplay Использовать атаку arpreplay.
—fragment Использовать атаки фрагментации.
-caffelatte использует атаку caffe-latte.
—p0841 Использовать атаку P0842.
— hirte Используйте hirte для атаки.
—nofakeauth Остановить атаку после неудачной аутентификации.
—wepca WEPCA Начать взламывать, когда количество IV превышает [n].
—wepsave WEPSAVE Сохраните копию файла .cap в этот каталог.
WPS:
—wps только для сетей WPS.
—pixie может использовать только атаку WPS PixieDust
—wpst WPST Максимальное время ожидания новой повторной попытки, прежде чем отказаться (0: никогда).
—wpsratio Минимальное соотношение успешных попыток ввода ПИН-кода / общего числа повторных попыток.
—wpsretry WPSRETRY Максимальное количество попыток одного и того же PIN-кода перед отказом.
wifite эффект и оценка:
Можно сказать, что этот инструмент очень всеобъемлющий, он поддерживает три типа зашифрованных беспроводных сетевых устройств: wpa, wep и wps. Можно сказать, что он очень всеобъемлющий! Сегодняшняя беспроводная связь — это в основном такие ситуации.
https://www.cnblogs.com/h2zZhou/p/9474181.html
Wifite
While the aircrack-ng suite is a well known name in the wireless hacking , the same can’t be said about Wifite. Living in the shade of the greatness of established aircrack-ng suite, Wifite has finally made a mark in a field where aircrack-ng failed. It made wifi hacking everyone’s piece of cake. While all its features are not independent (eg. it hacks WPS using reaver), it does what it promises, and puts hacking on autopilot. I’m listing some features, before I tell you how to use wifite (which I don’t think is necessary at all, as anyone who can understand simple English instructions given by Wifite can use it on his own).
Features Of Wifite
- Sorts targets by signal strength (in dB); cracks closest access points first
- Automatically de-authenticates clients of hidden networks to reveal SSIDs
- Numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- Customizable settings (timeouts, packets/sec, etc)
- «Anonymous» feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- All captured WPA handshakes are backed up to wifite.py’s current directory
- Smart WPA de-authentication; cycles between all clients and broadcast deauths
- Stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- Displays session summary at exit; shows any cracked keys
- All passwords saved to cracked.txt
- Built-in updater: ./wifite.py -upgrade
I find it worth mentioning here, that not only does it hack wifi the easy way, it also hack in the best possible way. For example, when you are hacking a WEP wifi using Wifite, it uses fakeauth and uses the ARP method to speed up data packets (I wrote a full length post about something which it does automatically!).
Hacking WEP network
If you’ve followed my previous posts on Hacking Wifi (WEP), you know there’s a lot of homework you have to do before you even start hacking. But not here. With Wifite, its as easy and simple as a single command.
wifite -wep
You might even have used the command
wifite
If you see any error at this stage move to the bottom of the page for troubleshooting tips. If your issue is not listed please comment. We reply within a day.
The -wep makes it clear to wifite that you want to hack WEP wifis only. It’ll scan the networks for you, and when you think it has scanned enough, you can tell it to stop by typing ctrl+c. It’ll then ask you which wifi to hack. In my case, I didn’t specify -wep so it shows all the wifis in range.
You can also select all and then go take a nap (or maybe go to sleep). When you wake up, you might be hacking all the wifi passwords in front of you. I typed one and it had gathered 7000 IVs (data packets) within 5 mins. Basically you can except it to hack the wifi in 10 mins approx. Notice how it automatically did the fake auth and ARP replay.
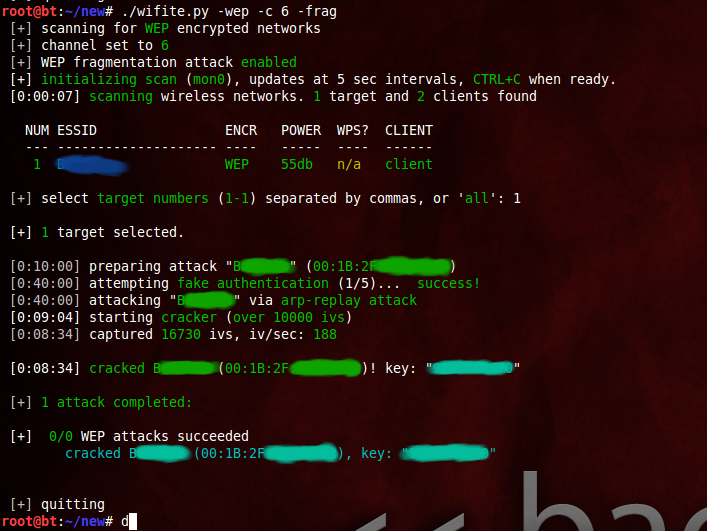
Here are a few more screenshots of the working of Wifite, from their official website (./wifite.py is not something that should bother you. You can stick with the simple wifite. Also, specifying the channel is optional so even the -c 6 was unnecessary. Notice that instead of ARP replay, the fragmentation attack was used, using -frag) —
Hacking WPS wasn’t fast (it took hours), but it was easy and didn’t require you to do anything but wait.
Note, the limitation that many reader on my blog are beginners forbid me from introducing too many attacks. I made a tutorial about ARP replay attack, and that too was detailed as hell. However, Wifite makes it possible for you to use any method that you want to use, by just naming it. As you saw in the screenshot above, the fragmentation attack was carried out just by typing -frag. Similarly, many other attacks can be played with. A good idea would be to execute the following-
wifite -help
This will tell you about the common usage commands, which will be very useful. Here is the list of WEP commands for different attacks-
WEP
-wep only target WEP networks [off]
-pps <num> set the number of packets per second to inject [600]
-wept <sec> sec to wait for each attack, 0 implies endless [600]
-chopchop use chopchop attack [on]
-arpreplay use arpreplay attack [on]
-fragment use fragmentation attack [on]
-caffelatte use caffe-latte attack [on]
-p0841 use -p0841 attack [on]
-hirte use hirte (cfrag) attack [on]
-nofakeauth stop attack if fake authentication fails [off]
-wepca <n> start cracking when number of ivs surpass n [10000]
-wepsave save a copy of .cap files to this directory [off]
As you can see, its the same thing as is there on the help screenshot. Play around with the attacks and see what you can do. Hacking WPA without WPS wouldn’t be that easy, and while I don’t usually do this, I’m providing a link to an external website for the tutorial . This is the best WPA cracking tutorial I’ve seen, and I can’t write a better one. It’s highly detailed, and I’m just hoping I don’t lose my audience to that website. Here is the tutorial — Cracking Wifi WPA/WPA2 passwords using pyrit cowpatty in Kali Linux
Troubleshooting
Wifite quits unexpectedly, sating «Scanning for wireless devices. No wireless interfaces were found. You need to plug in a wifi device or install drivers. Quitting.»
You are using Kali inside a virtual machine most probably. Virtual machine does not support internal wireless card. Either buy an external wireless card, or do a live boot / side boot with Windows. Anything other than Virtual machine in general.
Another attack automating script : Fluxion
Wifite is cool and all, but doesn’t do much against the invincible WPA-2 networks. Using a combination of evil-twin and man in the middle sort of attacks, fluxion tries to fool a client into giving you the key to the WPA-2 protected access point. Sounds interesting? Take a look.
Hacking WPA/WPA-2 without dictionary/bruteforce : Fluxion
Не робит wifite помогите)) (ПАМАГИТИ НЕ РАБОТАЕТ WIFITE0))
Модератор: Модераторы разделов
-
JobNakup
- Сообщения: 1
- ОС: WINDOWS 10/KALI LINUX

Не робит wifite помогите))
Shell
.´ · . . · `. wifite2 2.5.5
: : : (¯) : : : a wireless auditor by @derv82
`. · ` /¯ ´ · .´ maintained by kimocoder
` /¯¯¯ ´ https://github.com/kimocoder/wifite2
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[+] Checking airmon-ng...
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File "/usr/lib/python3/dist-packages/wifite/__main__.py", line 97, in entry_point
[!] wifite.start()
[!] File "/usr/lib/python3/dist-packages/wifite/__main__.py", line 51, in start
[!] Configuration.get_monitor_mode_interface()
[!] File "/usr/lib/python3/dist-packages/wifite/config.py", line 164, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File "/usr/lib/python3/dist-packages/wifite/tools/airmon.py", line 310, in ask
[!] raise Exception('airmon-ng did not find any wireless interfaces')
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting
Последний раз редактировалось Bizdelnick 01.09.2020 16:37, всего редактировалось 2 раза.
Причина: тег [sh]
-
Bizdelnick
- Модератор
- Сообщения: 19825
- Статус: nulla salus bello
- ОС: Debian GNU/Linux
Re: Не робит wifite помогите))
Сообщение
Bizdelnick » 01.09.2020 16:43
! Предупреждение от модератора Bizdelnick JobNakup, приведите, пожалуйста, подзаголовок темы в соответствие с пунктами 3.j и 3.k правил форума.
Пишите правильно:
| в консоли вку́пе (с чем-либо) в общем вообще |
в течение (часа) новичок нюанс по умолчанию |
приемлемо проблема пробовать трафик |
Hey ,
i cant find any Wifi spots , but here enaught in my city…
Any know how to fix it or why it happens ?
I exit this after 15mins
└─# wifite —wep
. .
.´ · . . · . wifite2 2.5.8 : : : (¯) : : : a wireless auditor by derv82 . · /¯ ´ · .´ maintained by kimocoder /¯¯¯ ´ https://github.com/kimocoder/wifite2
[+] option: targeting WEP-encrypted networks
[+] Using wlan0 already in monitor mode
[+] Scanning. Found 0 target(s), 0 client(s). Ctrl+C when ready ^C
[!] Error: No targets found. You may need to wait longer, or you may have issues with your wifi card
[!] Exiting
im noticing that the dauth stage in the WPA phase of the attack is not deauthorizing any users from my network. i was watching two devices and they never lost connection from the internet, never tried to reconnect, nothing. is there a quick fix for this? i have all the necessary software. im using an alfa awus1900, so its not that.
any input would be great.
I am pasting my terminal error in below :
root@localhost:~/wifite2# python3 Wifite.py
/root/wifite2/wifite/tools/ifconfig.py:21: SyntaxWarning: «is» with a literal. Did you mean «==»?
elif type(args) is ‘str’:
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[!] Error: Required app aircrack-ng was not found. install @ https://www.aircrack-ng.org/install.html
[!] Error: Required app iwconfig was not found. install @ apt-get install wireless-tools
[!] Error: Required app ifconfig was not found. install @ apt-get install net-tools
[!] Warning: Recommended app reaver was not found. install @ https://github.com/t6x/reaver-wps-fork-t6x
[!] Warning: Recommended app bully was not found. install @ https://github.com/aanarchyy/bully
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app tshark was not found. install @ apt-get install wireshark
[!] Warning: Recommended app hashcat was not found. install @ https://hashcat.net/hashcat/
[!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[!] Warning: Recommended app macchanger was not found. install @ apt-get install macchanger
[!] At least 1 Required app is missing. Wifite needs Required apps to run
root@localhost:~/wifite2#
If I run:
wifite --pmkid
Wifite will attempt to get the PMKID but nothing happens, then just fails to get it after it timeouts.
If I try using hcxdumptool I’m able to grab PMKID from networks all over, but I noticed it deauths devices when attempting to get PKMID from my own network.
hcxdumptool -o file.pcapng -i wlan0mon --enable_status 3
I’m wondering if it’s meant to deauth as I thought the PMKID attack was meant to be silent?
If it is, maybe wifite is struggle to send deauth packets.
Any help is appreciated.
user@RAZ0r ~ $ sudo wifite
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[!] Conflicting processes: NetworkManager (PID 1173), avahi-daemon (PID 1187), avahi-daemon (PID 1291), wpa_supplicant (PID 1429), dhclient (PID 1484)
[!] If you have problems: kill -9 PID or re-run wifite with —kill)
[+] Using mon0 already in monitor mode
[+] Scanning. Found 0 target(s), 0 client(s). Ctrl+C when ready
[!] Error: No targets found. You may need to wait longer, or you may have issues with your wifi card
[!] Exiting
if sudo airmon-ng check kill :
user@RAZ0r ~ $ sudo wifite
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[!] Conflicting processes: avahi-daemon (PID 9636), avahi-daemon (PID 9641)
[!] If you have problems: kill -9 PID or re-run wifite with —kill)
[+] Using mon0 already in monitor mode
[!] Error: No targets found. You may need to wait longer, or you may have issues with your wifi card
[!] Exiting
Help please!
I get operation not permitted when I try to put my alfa AWUS036ACH into monitor mode
I am pasting my terminal error in below :
root@localhost:~/wifite2# python3 Wifite.py
/root/wifite2/wifite/tools/ifconfig.py:21: SyntaxWarning: «is» with a literal. Did you mean «==»?
elif type(args) is ‘str’:
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[!] Error: Required app aircrack-ng was not found. install @ https://www.aircrack-ng.org/install.html
[!] Error: Required app iwconfig was not found. install @ apt-get install wireless-tools
[!] Error: Required app ifconfig was not found. install @ apt-get install net-tools
[!] Warning: Recommended app reaver was not found. install @ https://github.com/t6x/reaver-wps-fork-t6x
[!] Warning: Recommended app bully was not found. install @ https://github.com/aanarchyy/bully
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app tshark was not found. install @ apt-get install wireshark
[!] Warning: Recommended app hashcat was not found. install @ https://hashcat.net/hashcat/
[!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool
[!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools
[!] Warning: Recommended app macchanger was not found. install @ apt-get install macchanger
[!] At least 1 Required app is missing. Wifite needs Required apps to run
root@localhost:~/wifite2#
Hey 
I have gotten a little tired of not being able to set a time limit on the different attacks. It is wasting like 75% of the time on targets it is never going to break in to. Also why Pixiedust attack and PMKID got a short time limit to them.
Classic example:
WPS Pin attack: 51m, Pins: 1, ( 0% ) ( Timeouts: 49: Fails: 2 )
WPS pin attack: 2h21m, Pins: 1, ( 0% ) (Timeouts: 49: Fails: 2 )
How do I change the time limit? Google is no help and I suspect it is not possible :S
Thanks a lot for your hard work.
Deep respect.
Thanks
I ran
wifite —crack —dict /root/rockyou.txt
gives an error
crack attempt failed: passphrase not in dictionary
what can I do to fix it??
Please help I have been struggling for 3 weeks now
Hi! Yesterday I installed Kali, and I wanted to try cracking wi-fi passwords on different routers.
I could only get my router’s password, but others timed out. Any help is accepted!!
root@kali:~# wifite
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[+] Checking airmon-ng…
[!] airmon-ng did not find any wireless interfaces
[!] Make sure your wireless device is connected
[!] See http://www.aircrack-ng.org/doku.php?id=airmon-ng for more info
[!] Error: airmon-ng did not find any wireless interfaces
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File «/usr/lib/python2.7/dist-packages/wifite/main.py», line 93, in entry_point
[!] wifite.start()
[!] File «/usr/lib/python2.7/dist-packages/wifite/main.py», line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File «/usr/lib/python2.7/dist-packages/wifite/config.py», line 129, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File «/usr/lib/python2.7/dist-packages/wifite/tools/airmon.py», line 299, in ask
[!] raise Exception(‘airmon-ng did not find any wireless interfaces’)
[!] Exception: airmon-ng did not find any wireless interfaces
[!] Exiting
. .
.´ · . . · . wifite 2.2.5 : : : (¯) : : : automated wireless auditor . · /¯ ´ · .´ https://github.com/derv82/wifite2 /¯¯¯ ´
[!] Error: [WinError 2] 系统找不到指定的文件。
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File «D:PyCharm 6.28wifite2wifite_main_.py», line 93, in entry_point
[!] wifite.start()
[!] File «D:PyCharm 6.28wifite2wifite_main_.py», line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File «D:PyCharm 6.28wifite2wifiteconfig.py», line 132, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File «D:PyCharm 6.28wifite2wifitetoolsairmon.py», line 278, in ask
[!] Airmon.terminate_conflicting_processes()
[!] File «D:PyCharm 6.28wifite2wifitetoolsairmon.py», line 327, in terminate_conflicting_processes
[!] airmon_output = Process([‘airmon-ng’, ‘check’]).stdout()
[!] File «D:PyCharm 6.28wifite2wifiteutilprocess.py», line 89, in init
[!] self.pid = Popen(command, stdout=sout, stderr=serr, stdin=stdin, cwd=cwd, bufsize=bufsize)
[!] File «D:Python 3libsubprocess.py», line 775, in init
[!] restore_signals, start_new_session)
[!] File «D:Python 3libsubprocess.py», line 1178, in _execute_child
[!] startupinfo)
[!] FileNotFoundError: [WinError 2] 系统找不到指定的文件。
[!] Exiting
No clients are showing up when i know for a fact that my devices are connected. Monitor mode and packet injection are supported by my internal card. Any ideas?
Interface PHY Driver Chipset
- wlan0 phy0 wl Broadcom Limited BCM4331 802.11a/b/g/n (rev 02)
- wlan1 phy1 rtl8814au Realtek Semiconductor Corp.
[+] Select wireless interface (1-2): 2
[+] enabling monitor mode on wlan1… failed
failed
[!] Error: Cannot find any interfaces in Mode:Monitor
[!] Full stack trace below
[!] Traceback (most recent call last):
[!] File «/root/wifite2/wifite/main.py», line 93, in entry_point
[!] wifite.start()
[!] File «/root/wifite2/wifite/main.py», line 53, in start
[!] Configuration.get_monitor_mode_interface()
[!] File «/root/wifite2/wifite/config.py», line 130, in get_monitor_mode_interface
[!] cls.interface = Airmon.ask()
[!] File «/root/wifite2/wifite/tools/airmon.py», line 319, in ask
[!] iface.interface = Airmon.start(iface)
[!] File «/root/wifite2/wifite/tools/airmon.py», line 190, in start
[!] raise Exception(‘Cannot find any interfaces in Mode:Monitor’)
[!] Exception: Cannot find any interfaces in Mode:Monitor
[!] Exiting
What is the purple asterisk beside ESSID?
I ran wifite and left for a long time. However, when I returned. I saw that he was already stuck on “retrieving psk” for 6 hours. This is not the first time. This happens with some points. It looks like timeouts do not work when this command is executed. When I manually canceled CTRL + C, wifite continued to work as usual. Please fix it.
It seems that this happens when he cannot get the password via wps.
Hello everyone!
I have a problem with wifite tool using the WPS Pixie attack.
It just doesn’t work for some reason.
There’s output from terminal.
Traceback (most recent call last):
File "/usr/bin/wifite", line 3536, in <module>
engine.Start()
File "/usr/bin/wifite", line 1456, in Start
need_handshake = not wps_attack.RunAttack()
File "/usr/bin/wifite", line 3237, in RunAttack
if self.attack_wps_pixie():
File "/usr/bin/wifite", line 3372, in attack_wps_pixie
os.remove(self.RUN_CONFIG.temp + "out.out")
OSError: [Errno 2] No such file or directory: '/tmp/wifiteqeNT_X/out.out'
Hello,
wifite is a very cool tool. when running wifite you can choose which WifiNetworks to attack. Would it be possible to say «attack all, but these»? of course within the parameters give by commandline (like power for example).
another question:
for kali linux you should make a note on the startsite, that wifite is there wifite2 in reality, otherwise it can be confusing