Server crashes machine
Every single time I run the server it crashes the machine. It seems to be clashing with something. At the moment it’s unusable.
I’ve turned everything off possible and I managed to get it to run. However when I turn the server off and then restart the server, it crashes. Octane and Blender run fine it is just the server application that has the issue.
I’ve tried all the version with the same result.
I’m running a stock HP z820 workstation and a GTX680.
Has anyone had the same problem!
- j-mation
- Licensed Customer
- Posts: 2
- Joined: Tue Feb 25, 2014 1:19 am
Re: Server crashes machine
by JimStar » Tue Mar 04, 2014 6:45 am
Check that TCP port 5130 is not used by some other software. It may be the reason why OctaneServer exits right after start — if this port is already in use…
-
JimStar - OctaneRender Team
- Posts: 3749
- Joined: Thu Jul 28, 2011 8:19 pm
- Location: Auckland, New Zealand
Re: Server crashes machine
by mib2berlin » Tue Mar 04, 2014 6:55 am
It is may interesting if you start server from a command shell CMD to get error messages.
Cheers, mib.
Opensuse Leap 42.3/64 i5-3570K 16 GB
GTX 760 4 GB Driver: 430.31
Octane 3.08 Blender Octane
- mib2berlin
- Licensed Customer
- Posts: 1194
- Joined: Wed Jan 27, 2010 7:18 pm
- Location: Germany
Re: Server crashes machine
by j-mation » Tue Mar 04, 2014 11:00 pm
I seem to be out of luck. I’ve check the port 5130 and it is not in use.
Running from the command line is of no use as it crashes the machine as soon as it runs.
I’ll try another machine.
- j-mation
- Licensed Customer
- Posts: 2
- Joined: Tue Feb 25, 2014 1:19 am
Re: Server crashes machine
by cjardin » Fri May 09, 2014 4:02 am
I am having the exact same issue.. New machine, fresh install, dedicated rendering rig, windows 8.1, TITAN Black Superclocked.
Gives a message that it can’t bind to 5130 «No Error»
Verified nothing is running on port 5130..
- cjardin
- Licensed Customer
- Posts: 1
- Joined: Fri May 09, 2014 2:40 am
Re: Server crashes machine
by bkjernis » Mon Oct 20, 2014 5:38 pm
Iam getting the message «error binding socket on TCP port 5130; no error,» when I start the server. How do I rectify this problem? In blender should octane automatically render when the render mode is set to octane and I hit render? Thanks
- bkjernis
- Licensed Customer
- Posts: 30
- Joined: Wed Sep 15, 2010 11:06 pm
Re: Server crashes machine
by bkjernis » Tue Oct 21, 2014 12:20 am
I put all my license information in the right pallet but I am not able to render a simple cube with a rgb material. Is there a tutorial for blender to show how one goes about getting the render engine to work in blender?
- bkjernis
- Licensed Customer
- Posts: 30
- Joined: Wed Sep 15, 2010 11:06 pm
Re: Server crashes machine
by mib2berlin » Tue Oct 21, 2014 12:34 am
Hi, you need internet access to start render the first time and you need a real network card.
A wifi card does not work.
Please put your system specs in your post or better put it in your signature.
If the server start without error > http://render.otoy.com/manuals/Blender/?page_id=16
Cheers, mib
Opensuse Leap 42.3/64 i5-3570K 16 GB
GTX 760 4 GB Driver: 430.31
Octane 3.08 Blender Octane
- mib2berlin
- Licensed Customer
- Posts: 1194
- Joined: Wed Jan 27, 2010 7:18 pm
- Location: Germany
Return to Blender
Who is online
Users browsing this forum: No registered users and 3 guests
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and
privacy statement. We’ll occasionally send you account related emails.
Already on GitHub?
Sign in
to your account
Closed
phantom0929 opened this issue
Feb 10, 2017
· 8 comments
Comments
syslog-ng
Module loaded and initialized successfully; module=’syslogformat’
Error binding socket; addr=’AF_INET(0.0.0.0:1234)’, error=’Address already in use (98)’
Error initializing message pipeline;
Version of syslog-ng
3.5.6
output of syslog-ng —version
syslog-ng 3.5.6
Installer-Version: 3.5.6
Revision: 3.5.6-2+b1 [@416d315] (Debian/unstable)
Compile-Date: Oct 1 2014 18:23:11
Available-Modules: afprog,linux-kmsg-format,csvparser,afamqp,afsql,afstomp,cryptofuncs,afsocket,afuser,afsocket-notls,afmongodb,afsmtp,redis,json-plugin,dbparser,confgen,affile,system-source,afsocket-tls,tfgeoip,syslogformat,basicfuncs
Enable-Debug: off
Enable-GProf: off
Enable-Memtrace: off
Enable-IPv6: on
Enable-Spoof-Source: on
Enable-TCP-Wrapper: on
Enable-Linux-Caps: on
Enable-Pcre: on
Platform
Debian 8.7
Issue
Trying to setup syslog-ng host to recieve log mesages from client s by listening on port 1234 via tcp
Failure
Module loaded and initialized successfully; module=’syslogformat’
Error binding socket; addr=’AF_INET(0.0.0.0:1234)’, error=’Address already in use (98)’
Error initializing message pipeline;
Steps to reproduce
Configuration
@Version: 3.5.6
@include «scl.conf»
options {
time-reap(30);
mark-freq(10);
keep-hostname(yes);
};
source s_local { system(); internal(); };
source s_network { syslog(ip(0.0.0.0) transport(«tcp») port(1234) ); };
destination d_logs {
file(
"/var/log/syslog-ng/logs.txt"
owner("root")
group("root")
perm(0777)
); };
log { source(s_local); source(s_network); destination(d_logs); };
log { source(s_network); destination(d_logs); };
Hi,
This usually happens if you have another syslog-ng or other process running that already bound to the interface.
Check that there are no other syslog-ng processes running.
Same issue here. I changed port number with random numbers e.g. : 1999, 1313, 6767 and so on! but for each number syslog-ng make same error :
Error binding socket; addr='AF_INET(0.0.0.0:XXXX)', error='Address already in use (98)'
Any suggestion?
syslog-ng —version
syslog-ng 3 (3.13.2)
Config version: 3.13
Installer-Version: 3.13.2
Revision: 3.13.2-1
Compile-Date: Dec 5 2017 13:31:27
Module-Directory: /usr/lib/syslog-ng/3.13
Module-Path: /usr/lib/syslog-ng/3.13
Available-Modules: pseudofile,afuser,system-source,date,confgen,basicfuncs,redis,afstomp,sdjournal,cef,tags-parser,kvformat,syslogformat,dbparser,afsql,afmongodb,appmodel,afsocket,affile,json-plugin,geoip-plugin,cryptofuncs,csvparser,afsmtp,disk-buffer,linux-kmsg-format,afamqp,afprog,xml
Enable-Debug: off
Enable-GProf: off
Enable-Memtrace: off
Enable-IPv6: on
Enable-Spoof-Source: on
Enable-TCP-Wrapper: on
Enable-Linux-Caps: on
Enable-Systemd: on
#global options.
options { chain_hostnames(off); flush_lines(0); use_dns(no); use_fqdn(no);
owner(«root»); group(«root»); perm(0640); stats_freq(0);
bad_hostname(«^gconfd$»); chain_hostnames(off); flush_lines(0); stats_ freq(43200);
};
source siem_s {
syslog(ip(192.168.250.94) port(64500)
transport(«tls»)
tls( key-file(«/etc/CA/serverkey.pem»)
cert-file(«/etc/CA/serverreq.pem»)
ca-dir(«/etc/CA»)) ); };
destination correlator_internal {
pipe(«/var/zzz/fifo/XXX.fifo»
template(«$SOURCEIP|$FACILITY|$PRIORITY|$LEVEL|$TAG|$YEAR-$MONTH-$DAY|$HO UR:$MIN:$SEC|$PROGRAM| $MSGn») template-escape(no));
log { source(siem_s);destination(correlator_internal); };
Maybe you are opening that socket twice somehow? You should define a source
once and then reference it from other parts of the config.
You could always do an strace on syslog-ng starting up, and check all the
bind () calls to see if it calls bind multiple times for the same port
number.
Bazsi
…
Thanks for your response. No any twice bind in my configuration and other include confs.
how should I trace on syslog-ng starting up?
Logs:
«Apr 22 11:23:16 Corallator syslog-ng[9103]: Configuration reload request received, reloading configuration;
Apr 22 11:23:16 Corallator syslog-ng[9103]: Configuration reload finished;
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection accepted; fd=’25’, client=’AF_INET(192.168.250.65:37565)’, local=’AF_INET(0.0.0.0:514)’
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection accepted; fd=’26’, client=’AF_INET(192.168.250.65:41083)’, local=’AF_INET(0.0.0.0:514)’
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection closed; fd=’25’, client=’AF_INET(192.168.250.65:37565)’, local=’AF_INET(0.0.0.0:514)’
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection closed; fd=’26’, client=’AF_INET(192.168.250.65:41083)’, local=’AF_INET(0.0.0.0:514)’
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection accepted; fd=’25’, client=’AF_INET(192.168.250.65:41237)’, local=’AF_INET(0.0.0.0:514)’
Apr 22 11:23:17 Corallator syslog-ng[9103]: Syslog connection closed; fd=’25’, client=’AF_INET(192.168.250.65:41237)’, local=’AF_INET(0.0.0.0:514)’
«
You should start the syslog-ng from console with the same set of arguments as before (expect if you do not have the -F I would advise to include), and put all of those after the strace command.
An example: strace syslog-ng- F.
Also based on your logs, I would suggest the following steps:
Start up syslog-ng from «clean» environment:
- stop all of the syslog-ng instance/service (no reload and such)
- check if there is syslog-ng running
- check if the port in the configuration are used by any process
The above should be a ground zero, when you start looking for issue. If the issue does not come up in with the above method, maybe it connected to reload.
Start syslog-ng to investigate:
- start syslog-ng from console manually with debug logs (
-Fdev) - start syslog-ng with strace
I ran strace syslog-ng -f /etc/syslog-ng/syslog-ng.conf -F
log file :
strace.log
Thanks a lot Kokan & bazsi
Have you checked if there are a process using that port; because from the strace you sent it looks syslog-ng tries only bind it to once (not the current instance of syslog-ng using that port).
$ less ~/Downloads/strace.log |grep bind
bind(5, {sa_family=AF_LOCAL, sun_path="/var/lib/syslog-ng/syslog-ng.ctl"}, 35) = 0
bind(12, {sa_family=AF_INET, sin_port=htons(5140), sin_addr=inet_addr("0.0.0.0")}, 16) = -1 EADDRINUSE (Address already in use)
write(2, "[2018-04-22T12:12:24.882353] Err"..., 117[2018-04-22T12:12:24.882353] Error binding socket; addr='AF_INET(0.0.0.0:5140)', error='Address already in use (98)'
Some process must be binding that address. You should check which process is using that address and port. You could check it via netstat -tunap command, please run it as root, so the netstat could lookup all the process. You have to check for the 5140 port, which process is listening there.
Thanks a million for your time. I’ll try to fix this issue. Close the issue.
Best regards.
Здравствуйте товарищи!
Имеется Nport IA-5250 в режиме TCP Client, через RS485 подключён ПК с сервером
Имеются Nport IA-5150 2шт и Nport 5232 в режимах TCP Server, через RS485 подключены опрашиваемые контроллеры
Всё работает уже давно.
Потребовалось подключить Nport 5130 RU, все настройки сети и порта проверены и идентичны работающим Nport’ам, но связи с контроллером нет
То есть связка ПК(RS485)-> Nport IA5250 -> Nport 5130RU -> контроллер(RS485) — не работает.
А если: ПК(Ethernet) ->Nport 5130RU -> контроллер(RS485) — то работает
Но что интересно, связка ПК(RS485)-> Nport 5130RU -> Nport 5130RU -> контроллер(RS485) — работает.
Стали разбираться и выяснилось, что через telnet все Nport’ы (кроме 5130) отвечают (см. «здоровая моха», где 0.109-ПК, 10.155 — Nport IA5150)
А Nport 5130 RU порт открывает, но говорить не хочет (см. «больная моха», где 250.100-ПК, 250.34-Nport 5130RU)
Прошу обратить внимание, после открытия соединения здоровой моксы IA5150 (стоки 2908-2909) идёт отчистка буфера от ПК (2910 и 2912) и от Nport (2913 и 2918), далее идёт запрос-ответ (2921-2950) и т.д. до закрытия порта. И чему равны Seq и Ack в связке запрос-ответ.
А вот 5130 так же открывает порт (строки 1056-1057), так же от ПК прилетает запрос на очистку буфера (1058 и 1060), но от 5130 приходит только один пакет (1061). После чего автоматически общения не происходит. Строки 1624 и 1625 — это запрос-ответ по нажатию клавиши Enter и окне telnet, обратите внимание на Seq и Ack в этой связке.
Пробовал прошивки для 5130 версии 3.5, 3.8, 3.8.1, 3.9, везде ведёт себя одинаково (разве что в 3.9 нет строки типа 1059, что и исправлено в этой прошивке)
Вопрос: как исправить данную проблему?
I’ve gone through many posts and forums and I’m new to socket programming. Major parts of my code are similar to
BIND ERROR : Address already in use
but then i changed my code so that i include «setsockopt» function like so:
const char* port="5555";
int opt=1;
portno=atoi(port);
//parameters for server address
serv_addr.sin_family=AF_INET;
serv_addr.sin_port=htons(portno);
serv_addr.sin_addr.s_addr=INADDR_ANY;
//bind the socket to the address
setsockopt(sockfd,SOL_SOCKET,SO_REUSEADDR,(const char *)&opt,sizeof(int));
if(bind(sockfd,(struct sockaddr*)&serv_addr,sizeof(serv_addr))<0)
{close(sockfd);
error("error in binding port!");
}
But still i get the error. I have to close the terminal and restart it in order to use the port again. I want to use a hardcoded port (like i mentioned in the code above)
Thanks a lot in advance
asked Feb 9, 2012 at 8:53
3
Check to see if the port is in use. Either telnet to that port or use netstat -a. It should be in use (as the error indicates) and kill the appropriate process. Perhaps using ps to find the process.
answered Feb 9, 2012 at 8:59
Ed HealEd Heal
58.6k17 gold badges87 silver badges125 bronze badges
1
A port number can only be used by one application at a time. That means you can not start the same program twice expecting both to bind to the same port.
The SO_REUSEADDR is for when the socket bound to an address has already been closed, the same address (ip-address/port pair) can be used again directly.
answered Feb 9, 2012 at 8:59
6
I am trying to set up an FTP server on one of my devices that runs DietPi and I selected proFTPD as a server.
I have installed the software and followed some set-up information I found here. But then I noticed that the service was not running. After trying to find it in via ps aux | grep proftpd I did not succeed.
After issuing: systemclt status proftpd.service I got the following:
● proftpd.service - LSB: Starts ProFTPD daemon
Loaded: loaded (/etc/init.d/proftpd; generated)
Active: failed (Result: exit-code) since Tue 2021-04-13 22:58:49 BST; 9s ago
Docs: man:systemd-sysv-generator(8)
Process: 26998 ExecStart=/etc/init.d/proftpd start (code=exited, status=1/FAILURE)
Apr 13 22:58:48 DietPi systemd[1]: Starting LSB: Starts ProFTPD daemon...
Apr 13 22:58:49 DietPi proftpd[26998]: Starting ftp server: proftpd2021-04-13 22:58:49,163 DietPi proftpd[2700
5]: mod_ctrls/0.9.5: error: unable to bind to local socket: Address already in use
Apr 13 22:58:49 DietPi proftpd[26998]: 2021-04-13 22:58:49,242 DietPi proftpd[27005]: error: unable to stat()
/var/log/proftpd: No such file or directory
Apr 13 22:58:49 DietPi proftpd[26998]: 2021-04-13 22:58:49,244 DietPi proftpd[27005]: mod_ctrls/0.9.5: unable
to open ControlsLog '/var/log/proftpd/controls.log': No such file or directory
Apr 13 22:58:49 DietPi proftpd[26998]: 2021-04-13 22:58:49,246 DietPi proftpd[27005]: fatal: ControlsLog: unab
le to open '/var/log/proftpd/controls.log': No such file or directory on line 68 of '/etc/proftpd/proftpd.conf'
Apr 13 22:58:49 DietPi proftpd[26998]: failed!
Apr 13 22:58:49 DietPi systemd[1]: proftpd.service: Control process exited, code=exited, s
tatus=1/FAILURE
Apr 13 22:58:49 DietPi systemd[1]: proftpd.service: Failed with result 'exit-code'.
Apr 13 22:58:49 DietPi systemd[1]: Failed to start LSB: Starts ProFTPD daemon.
So I dug a little bit here and turns out that no other process runs or binds on port 21. So, what could be the issue of the service failing here?
Furthermore, by issuing sudo lsof -i tcp:21 I do not get any response.
Also, via nmap I get the following:
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
No 21/tcp port here.
Debug via proftpd -nd10 on the cl:
roftpd -nd10
2021-04-14 08:13:45,498 DietPi proftpd[951]: using PCRE 8.39 2016-06-14
2021-04-14 08:13:45,508 DietPi proftpd[951]: using TCP receive buffer size of 131072 bytes
2021-04-14 08:13:45,510 DietPi proftpd[951]: using TCP send buffer size of 16384 bytes
2021-04-14 08:13:45,513 DietPi proftpd[951]: testing Unix domain socket using S_ISFIFO
2021-04-14 08:13:45,517 DietPi proftpd[951]: testing Unix domain socket using S_ISSOCK
2021-04-14 08:13:45,519 DietPi proftpd[951]: using S_ISSOCK macro for Unix domain socket detection
2021-04-14 08:13:45,528 DietPi proftpd[951]: mod_ctrls/0.9.5: error: unable to bind to local socket: Address already in use
2021-04-14 08:13:45,532 DietPi proftpd[951]: using 'UTF-8' as local charset for UTF-8 conversion
2021-04-14 08:13:45,535 DietPi proftpd[951]: ROOT PRIVS at mod_core.c:376
2021-04-14 08:13:45,537 DietPi proftpd[951]: RELINQUISH PRIVS at mod_core.c:378
2021-04-14 08:13:45,541 DietPi proftpd[951]: ROOT PRIVS at mod_core.c:385
2021-04-14 08:13:45,544 DietPi proftpd[951]: ROOT PRIVS at parser.c:1187
2021-04-14 08:13:45,549 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_ctrls_admin.c'
2021-04-14 08:13:45,554 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_ctrls_admin' (from '/usr/lib/proftpd/mod_ctrls_admin.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,558 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_tls.c'
2021-04-14 08:13:45,562 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_tls' (from '/usr/lib/proftpd/mod_tls.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,565 DietPi proftpd[951]: mod_tls/2.7: using OpenSSL 1.1.1d 10 Sep 2019
2021-04-14 08:13:45,587 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_radius.c'
2021-04-14 08:13:45,591 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_radius' (from '/usr/lib/proftpd/mod_radius.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,594 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_quotatab.c'
2021-04-14 08:13:45,599 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_quotatab' (from '/usr/lib/proftpd/mod_quotatab.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,602 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_quotatab_file.c'
2021-04-14 08:13:45,607 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_quotatab_file' (from '/usr/lib/proftpd/mod_quotatab_file.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,609 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_quotatab_radius.c'
2021-04-14 08:13:45,612 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_quotatab_radius' (from '/usr/lib/proftpd/mod_quotatab_radius.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,617 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_wrap.c'
2021-04-14 08:13:45,625 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_wrap' (from '/usr/lib/proftpd/mod_wrap.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,628 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_rewrite.c'
2021-04-14 08:13:45,633 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_rewrite' (from '/usr/lib/proftpd/mod_rewrite.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,636 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_load.c'
2021-04-14 08:13:45,639 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_load' (from '/usr/lib/proftpd/mod_load.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,643 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_ban.c'
2021-04-14 08:13:45,648 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_ban' (from '/usr/lib/proftpd/mod_ban.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,651 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_wrap2.c'
2021-04-14 08:13:45,656 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_wrap2' (from '/usr/lib/proftpd/mod_wrap2.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,660 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_wrap2_file.c'
2021-04-14 08:13:45,664 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_wrap2_file' (from '/usr/lib/proftpd/mod_wrap2_file.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,668 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_dynmasq.c'
2021-04-14 08:13:45,673 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_dynmasq' (from '/usr/lib/proftpd/mod_dynmasq.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,675 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_exec.c'
2021-04-14 08:13:45,681 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_exec' (from '/usr/lib/proftpd/mod_exec.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,683 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_shaper.c'
2021-04-14 08:13:45,688 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_shaper' (from '/usr/lib/proftpd/mod_shaper.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,692 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_ratio.c'
2021-04-14 08:13:45,696 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_ratio' (from '/usr/lib/proftpd/mod_ratio.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,699 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_site_misc.c'
2021-04-14 08:13:45,704 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_site_misc' (from '/usr/lib/proftpd/mod_site_misc.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,706 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_sftp.c'
2021-04-14 08:13:45,722 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_sftp' (from '/usr/lib/proftpd/mod_sftp.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,725 DietPi proftpd[951]: mod_sftp/1.0.0: using OpenSSL 1.1.1d 10 Sep 2019
2021-04-14 08:13:45,737 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_sftp_pam.c'
2021-04-14 08:13:45,741 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_sftp_pam' (from '/usr/lib/proftpd/mod_sftp_pam.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,744 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_facl.c'
2021-04-14 08:13:45,749 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_facl' (from '/usr/lib/proftpd/mod_facl.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,752 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_unique_id.c'
2021-04-14 08:13:45,757 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_unique_id' (from '/usr/lib/proftpd/mod_unique_id.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,762 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_copy.c'
2021-04-14 08:13:45,768 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_copy' (from '/usr/lib/proftpd/mod_copy.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,773 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_deflate.c'
2021-04-14 08:13:45,787 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_deflate' (from '/usr/lib/proftpd/mod_deflate.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,789 DietPi proftpd[951]: mod_deflate/0.5.7: using zlib 1.2.11
2021-04-14 08:13:45,792 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_ifversion.c'
2021-04-14 08:13:45,798 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_ifversion' (from '/usr/lib/proftpd/mod_ifversion.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,800 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_memcache.c'
2021-04-14 08:13:45,805 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_memcache' (from '/usr/lib/proftpd/mod_memcache.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,809 DietPi proftpd[951]: mod_memcache/0.1: using libmemcached-1.0.18
2021-04-14 08:13:45,812 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_tls_memcache.c'
2021-04-14 08:13:45,815 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_tls_memcache' (from '/usr/lib/proftpd/mod_tls_memcache.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,815 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_readme.c'
2021-04-14 08:13:45,823 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_readme' (from '/usr/lib/proftpd/mod_readme.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,825 DietPi proftpd[951]: mod_dso/0.5: loading 'mod_ifsession.c'
2021-04-14 08:13:45,831 DietPi proftpd[951]: mod_dso/0.5: loaded module 'mod_ifsession' (from '/usr/lib/proftpd/mod_ifsession.so', last modified on Tue Mar 10 23:03:08 2020)
2021-04-14 08:13:45,835 DietPi proftpd[951]: RELINQUISH PRIVS at parser.c:1190
2021-04-14 08:13:45,838 DietPi proftpd[951]: RELINQUISH PRIVS at mod_core.c:388
2021-04-14 08:13:45,844 DietPi proftpd[951]: DenyFilter: compiling regex '*.*/'
2021-04-14 08:13:45,857 DietPi proftpd[951]: retrieved UID 1000 for user 'dietpi'
2021-04-14 08:13:45,862 DietPi proftpd[951]: retrieved GID 1000 for group 'dietpi'
2021-04-14 08:13:45,866 DietPi proftpd[951]: <IfModule>: using 'mod_quotatab.c' section at line 53
2021-04-14 08:13:45,868 DietPi proftpd[951]: <IfModule>: using 'mod_ratio.c' section at line 57
2021-04-14 08:13:45,871 DietPi proftpd[951]: <IfModule>: using 'mod_delay.c' section at line 61
2021-04-14 08:13:45,873 DietPi proftpd[951]: <IfModule>: using 'mod_ctrls.c' section at line 65
2021-04-14 08:13:45,874 DietPi proftpd[951]: ROOT PRIVS at mod_ctrls.c:114
2021-04-14 08:13:45,877 DietPi proftpd[951]: RELINQUISH PRIVS at mod_ctrls.c:117
2021-04-14 08:13:45,878 DietPi proftpd[951]: <IfModule>: using 'mod_ctrls_admin.c' section at line 73
2021-04-14 08:13:45,879 DietPi proftpd[951]: ROOT PRIVS at mod_core.c:376
2021-04-14 08:13:45,879 DietPi proftpd[951]: RELINQUISH PRIVS at mod_core.c:378
2021-04-14 08:13:45,879 DietPi proftpd[951]: ROOT PRIVS at mod_core.c:385
2021-04-14 08:13:45,879 DietPi proftpd[951]: processing configuration directory '/etc/proftpd/conf.d/'
2021-04-14 08:13:45,880 DietPi proftpd[951]: RELINQUISH PRIVS at mod_core.c:388
2021-04-14 08:13:45,907 DietPi proftpd[951]: UseReverseDNS off, returning IP address instead of DNS name
2021-04-14 08:13:45,907 DietPi proftpd[951] 127.0.0.1:
2021-04-14 08:13:45,907 DietPi proftpd[951] 127.0.0.1: Config for DietPi FTP:
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: IdentLookups
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: DeferWelcome
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: MultilineRFC2228
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: DefaultServer
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: ShowSymlinks
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: AllowRetrieveRestart
2021-04-14 08:13:45,908 DietPi proftpd[951] 127.0.0.1: AllowStoreRestart
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: TimeoutNoTransfer
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: TimeoutStalled
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: TimeoutIdle
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: DisplayLogin
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: DisplayChdir
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: ListOptions
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: DenyFilter
2021-04-14 08:13:45,909 DietPi proftpd[951] 127.0.0.1: DefaultRoot
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: RootLogin
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: UserID
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: UserName
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: GroupID
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: GroupName
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: Umask
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: DirUmask
2021-04-14 08:13:45,910 DietPi proftpd[951] 127.0.0.1: AllowOverwrite
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: TransferLog
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: SystemLog
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: WtmpLog
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: QuotaEngine
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: Ratios
2021-04-14 08:13:45,911 DietPi proftpd[951] 127.0.0.1: DelayEngine
2021-04-14 08:13:45,912 DietPi proftpd[951] 127.0.0.1: mod_facl/0.6: registered 'facl' FS
2021-04-14 08:13:45,921 DietPi proftpd[951] 127.0.0.1: mod_tls/2.7: generating initial TLS session ticket key
2021-04-14 08:13:45,924 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at mod_tls.c:4815
2021-04-14 08:13:45,927 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at mod_tls.c:4818
2021-04-14 08:13:45,930 DietPi proftpd[951] 127.0.0.1: mod_tls/2.7: scheduling new TLS session ticket key every 3600 secs
2021-04-14 08:13:45,935 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: binding to text domain 'proftpd' using locale path '/usr/share/locale'
2021-04-14 08:13:45,936 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: using locale files in '/usr/share/locale'
2021-04-14 08:13:45,939 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'ko_KR': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,943 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'bg_BG': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,945 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'ja_JP': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,948 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'en_US': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,951 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'fr_FR': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,954 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'es_ES': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,958 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'zh_TW': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,960 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'zh_CN': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,964 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'it_IT': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,968 DietPi proftpd[951] 127.0.0.1: mod_lang/1.1: skipping possible language 'ru_RU': not supported by setlocale(3); see `locale -a'
2021-04-14 08:13:45,971 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at mod_log.c:2151
2021-04-14 08:13:45,974 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at mod_log.c:2154
2021-04-14 08:13:45,976 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at mod_rlimit.c:555
2021-04-14 08:13:45,978 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at mod_rlimit.c:558
2021-04-14 08:13:45,980 DietPi proftpd[951] 127.0.0.1: set core resource limits for daemon
2021-04-14 08:13:45,981 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at mod_auth_unix.c:1338
2021-04-14 08:13:45,986 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at mod_auth_unix.c:1341
2021-04-14 08:13:45,989 DietPi proftpd[951] 127.0.0.1: retrieved group ID: 1000
2021-04-14 08:13:45,991 DietPi proftpd[951] 127.0.0.1: setting group ID: 1000
2021-04-14 08:13:45,993 DietPi proftpd[951] 127.0.0.1: SETUP PRIVS at main.c:2594
2021-04-14 08:13:45,994 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at main.c:1862
2021-04-14 08:13:45,995 DietPi proftpd[951] 127.0.0.1: deleting existing scoreboard '/run/proftpd.scoreboard'
2021-04-14 08:13:45,996 DietPi proftpd[951] 127.0.0.1: opening scoreboard '/run/proftpd.scoreboard'
2021-04-14 08:13:45,998 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at main.c:1889
2021-04-14 08:13:46,002 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at mod_ctrls_admin.c:1632
2021-04-14 08:13:46,002 DietPi proftpd[951] 127.0.0.1: opening scoreboard '/run/proftpd.scoreboard'
2021-04-14 08:13:46,005 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at mod_ctrls_admin.c:1634
2021-04-14 08:13:46,007 DietPi proftpd[951] 127.0.0.1: ROOT PRIVS at inet.c:409
2021-04-14 08:13:46,008 DietPi proftpd[951] 127.0.0.1: RELINQUISH PRIVS at inet.c:459
2021-04-14 08:13:46,009 DietPi proftpd[951] 127.0.0.1: Failed binding to ::, port 21: Address already in use
2021-04-14 08:13:46,011 DietPi proftpd[951] 127.0.0.1: Check the ServerType directive to ensure you are configured correctly
2021-04-14 08:13:46,011 DietPi proftpd[951] 127.0.0.1: Check to see if inetd/xinetd, or another proftpd instance, is already using ::, port 21
2021-04-14 08:13:46,011 DietPi proftpd[951] 127.0.0.1: Unable to start proftpd; check logs for more details
Debug via strace proftpd | grep -E "SOCKET|sock"
getpeername(0, 0xbe8a6c1c, [16]) = -1 ENOTSOCK (Socket operation on non-socket)
socket(AF_UNIX, SOCK_DGRAM, 0) = 3
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 3
connect(3, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 3
connect(3, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_INET, SOCK_STREAM, IPPROTO_TCP) = 4
getsockopt(4, SOL_SOCKET, SO_RCVBUF, [131072], [4]) = 0
getsockopt(4, SOL_SOCKET, SO_SNDBUF, [16384], [4]) = 0
socket(AF_UNIX, SOCK_STREAM, 0) = 4
bind(4, {sa_family=AF_UNIX, sun_path="/run/test.sock"}, 110) = 0
unlink("/run/test.sock") = 0
socket(AF_UNIX, SOCK_STREAM, 0) = 4
bind(4, {sa_family=AF_UNIX, sun_path="/run/proftpd.sock"}, 110) = -1 EADDRINUSE (Address already in use)
write(2, "2021-04-14 11:08:40,739 DietPiHo"..., 1292021-04-14 11:08:40,739 DietPi proftpd[2682]: mod_ctrls/0.9.5: error: unable to bind to local socket: Address already in use
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 6
connect(6, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 6
connect(6, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 5
connect(5, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 5
connect(5, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 4
connect(4, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_UNIX, SOCK_STREAM|SOCK_CLOEXEC|SOCK_NONBLOCK, 0) = 4
connect(4, {sa_family=AF_UNIX, sun_path="/var/run/nscd/socket"}, 110) = -1 ENOENT (No such file or directory)
socket(AF_NETLINK, SOCK_RAW|SOCK_CLOEXEC, NETLINK_ROUTE) = 4
getsockname(4, {sa_family=AF_NETLINK, nl_pid=2682, nl_groups=00000000}, [12]) = 0
socket(AF_INET, SOCK_DGRAM|SOCK_CLOEXEC, IPPROTO_IP) = 4
getsockname(4, {sa_family=AF_INET, sin_port=htons(44402), sin_addr=inet_addr("127.0.0.1")}, [28->16]) = 0
getsockname(4, {sa_family=AF_INET, sin_port=htons(40796), sin_addr=inet_addr("127.0.0.1")}, [28->16]) = 0
socket(AF_INET, SOCK_DGRAM|SOCK_CLOEXEC|SOCK_NONBLOCK, IPPROTO_IP) = 4
Содержание
- MySQL: Can’t start server: Bind on TCP/IP port: Address already in use resolved
- Tcp server bind error
- Introduction¶
- socket Function¶
- AF_ xxx Versus PF_ xxx¶
- connect Function¶
- Example: nonexistent host on the local subnet *¶
- Example: no server process running *¶
- Example: destination not reachable on the Internet *¶
- bind Function¶
- Wildcard Address and INADDR_ANY *¶
- Binding a non-wildcard IP address *¶
- listen Function¶
- Connection queues *¶
- Packet exchanges during conenction establishment *¶
- The backlog argument *¶
- SYN Flooding *¶
- accept Function¶
- Example: Value-Result Arguments¶
- fork and exec Functions¶
- Concurrent Servers¶
- Reference count of sockets *¶
- Visualizing the sockets and connection *¶
- close Function¶
- Descriptor Reference Counts¶
- getsockname and getpeername Functions¶
- Example: Obtaining the Address Family of a Socket¶
MySQL: Can’t start server: Bind on TCP/IP port: Address already in use resolved
180523 20:18:12 mysqld_safe mysqld from pid file /var/run/mysqld/mysqld.pid ended
180523 20:21:33 mysqld_safe Logging to ‘/var/log/mysqld.log’.
180523 20:21:33 mysqld_safe Starting mysqld daemon with databases from /DBdata/mysql
2018-05-23 20:21:33 0 [Warning] TIMESTAMP with implicit DEFAULT value is deprecated. Please use –explicit_defaults_for_timestamp server option (see documentation for more details).
2018-05-23 20:21:33 0 [Note] /usr/sbin/mysqld (mysqld 5.6.40) starting as process 18548 …
2018-05-23 20:21:33 18548 [Warning] Buffered warning: Changed limits: max_open_files: 1024 (requested 5000)
2018-05-23 20:21:33 18548 [Warning] Buffered warning: Changed limits: table_open_cache: 431 (requested 2000)
2018-05-23 20:21:33 18548 [Note] Plugin ‘FEDERATED’ is disabled.
2018-05-23 20:21:33 18548 [Note] InnoDB: Using atomics to ref count buffer pool pages
2018-05-23 20:21:33 18548 [Note] InnoDB: The InnoDB memory heap is disabled
2018-05-23 20:21:33 18548 [Note] InnoDB: Mutexes and rw_locks use GCC atomic builtins
2018-05-23 20:21:33 18548 [Note] InnoDB: Memory barrier is not used
2018-05-23 20:21:33 18548 [Note] InnoDB: Compressed tables use zlib 1.2.3
2018-05-23 20:21:33 18548 [Note] InnoDB: Using Linux native AIO
2018-05-23 20:21:33 18548 [Note] InnoDB: Using CPU crc32 instructions
2018-05-23 20:21:33 18548 [Note] InnoDB: Initializing buffer pool, size = 128.0M
2018-05-23 20:21:33 18548 [Note] InnoDB: Completed initialization of buffer pool
2018-05-23 20:21:33 18548 [Note] InnoDB: Highest supported file format is Barracuda.
2018-05-23 20:21:33 18548 [Note] InnoDB: 128 rollback segment(s) are active.
2018-05-23 20:21:33 18548 [Note] InnoDB: Waiting for purge to start
2018-05-23 20:21:33 18548 [Note] InnoDB: 5.6.40 started; log sequence number 1602387
2018-05-23 20:21:33 18548 [Note] Server hostname (bind-address): ‘*’; port: 3306
2018-05-23 20:21:33 18548 [Note] IPv6 is available.
2018-05-23 20:21:33 18548 [Note] – ‘::’ resolves to ‘::’;
2018-05-23 20:21:33 18548 [Note] Server socket created on IP: ‘::’.
2018-05-23 20:21:33 18548 [ERROR] Can’t start server: Bind on TCP/IP port: Address already in use
2018-05-23 20:21:33 18548 [ERROR] Do you already have another mysqld server running on port: 3306 ?
2018-05-23 20:21:33 18548 [ERROR] Aborting
Finally, we checked the mysql TCP/IP port[3306]:
]# lsof -i TCP:3306
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
mysqld 17915 mysql 10u IPv6 55522 0t0 TCP *:mysql (LISTEN)
Источник
Tcp server bind error
In C, we cannot represent a constant structure on the right-hand side of an assignment. UNP
Introduction¶
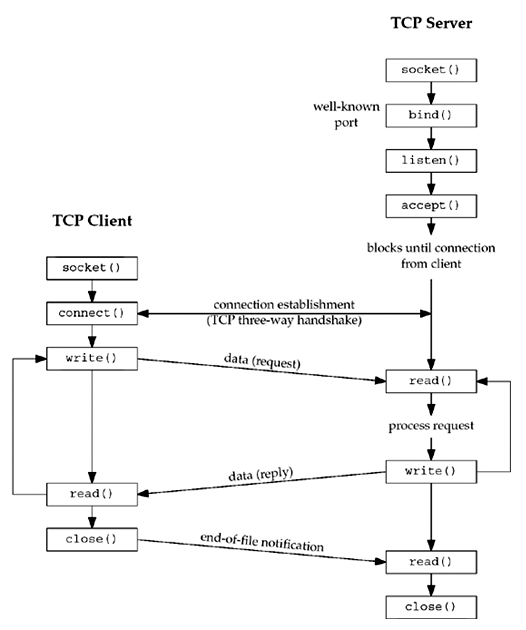
This chapter describes the elementary socket functions required to write a complete TCP client and server, along with concurrent servers, a common Unix technique for providing concurrency when numerous clients are connected to the same server at the same time. Each client connection causes the server to fork a new process just for that client. In this chapter, we consider only the one-process-per-client model using fork .
The figure below shows a timeline of the typical scenario that takes place between a TCP client and server. First, the server is started, then sometime later, a client is started that connects to the server. We assume that the client sends a request to the server, the server processes the request, and the server sends a reply back to the client. This continues until the client closes its end of the connection, which sends an end-of-file notification to the server. The server then closes its end of the connection and either terminates or waits for a new client connection.
socket Function¶
To perform network I/O, the first thing a process must do is call the socket function, specifying the type of communication protocol desired (TCP using IPv4, UDP using IPv6, Unix domain stream protocol, etc.).
family specifies the protocol family and is one of the constants in the table below. This argument is often referred to as domain instead of family.
| family | Description |
|---|---|
| AF_INET | IPv4 protocols |
| AF_INET6 | IPv6 protocols |
| AF_LOCAL | Unix domain protocols (Chapter 15) |
| AF_ROUTE | Routing sockets (Chapter 18) |
| AF_KEY | Key socket (Chapter 19) |
The socket type is one of the constants shown in table below:
| type | Description |
|---|---|
| SOCK_STREAM | stream socket |
| SOCK_DGRAM | datagram socket |
| SOCK_SEQPACKET | sequenced packet socket |
| SOCK_RAW | raw socket |
The protocol argument to the socket function should be set to the specific protocol type found in the table below, or 0 to select the system’s default for the given combination of family and type.
| protocol | Description |
|---|---|
| IPPROTO_TCP | TCP transport protocol |
| IPPROTO_UDP | UDP transport protocol |
| IPPROTO_SCTP | SCTP transport protocol |
Not all combinations of socket family and type are valid. The table below shows the valid combinations, along with the actual protocols that are valid for each pair. The boxes marked «Yes» are valid but do not have handy acronyms. The blank boxes are not supported.
| AF_INET | AF_INET6 | AF_LOCAL | AF_ROUTE | AF_KEY |
| SOCK_STREAM | TCP/SCTP | TCP/SCTP | Yes | |
| SOCK_DGRAM | UDP | UDP | Yes | |
| SOCK_SEQPACKET | SCTP | SCTP | Yes | |
| SOCK_RAW | IPv4 | IPv6 | Yes | Yes |
- You may also encounter the corresponding PF_ xxx constant as the first argument to socket. This is discussed in the next section in this Chapter.
- You may encounter AF_UNIX (the historical Unix name) instead of AF_LOCAL (the POSIX name). This is discussed in Chapter 15.
- Linux supports a new socket type, SOCK_PACKET , that provides access to the datalink, similar to BPF and DLPI (Section 2.2). This is discussed in Chapter 29
- The key socket, AF_KEY , is newer than the others. It provides support for cryptographic security. Similar to the way that a routing socket ( AF_ROUTE ) is an interface to the kernel’s routing table, the key socket is an interface into the kernel’s key table. This is discussed in Chapter 19.
On success, the socket function returns a small non-negative integer value, similar to a file descriptor. We call this a socket descriptor, or a sockfd. To obtain this socket descriptor, all we have specified is a protocol family (IPv4, IPv6, or Unix) and the socket type (stream, datagram, or raw). We have not yet specified either the local protocol address or the foreign protocol address.
AF_ xxx Versus PF_ xxx¶
The » AF_ » prefix stands for «address family» and the » PF_ » prefix stands for «protocol family.» Historically, the intent was that a single protocol family might support multiple address families and that the PF_ value was used to create the socket and the AF_ value was used in socket address structures. But in actuality, a protocol family supporting multiple address families has never been supported and the header defines the PF_ value for a given protocol to be equal to the AF_ value for that protocol. While there is no guarantee that this equality between the two will always be true, should anyone change this for existing protocols, lots of existing code would break.
To conform to existing coding practice, we use only the AF_ constants in this text, although you may encounter the PF_ value, mainly in calls to socket .
connect Function¶
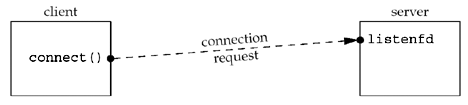
The connect function is used by a TCP client to establish a connection with a TCP server.
- sockfd is a socket descriptor returned by the socket function.
- The servaddr and addrlen arguments are a pointer to a socket address structure (which contains the IP address and port number of the server) and its size. (Section 3.3)
The client does not have to call bind before calling connect : the kernel will choose both an ephemeral port and the source IP address if necessary.
In the case of a TCP socket, the connect function initiates TCP’s three-way handshake (Section 2.6). The function returns only when the connection is established or an error occurs. There are several different error returns possible:
- If the client TCP receives no response to its SYN segment, ETIMEDOUT is returned.
- For example, in 4.4BSD, the client sends one SYN when connect is called, sends another SYN 6 seconds later, and sends another SYN 24 seconds later. If no response is received after a total of 75 seconds, the error is returned.
- Some systems provide administrative control over this timeout.
- If the server’s response to the client’s SYN is a reset (RST), this indicates that no process is waiting for connections on the server host at the port specified (the server process is probably not running). This is a hard error and the error ECONNREFUSED is returned to the client as soon as the RST is received. An RST is a type of TCP segment that is sent by TCP when something is wrong. Three conditions that generate an RST are:
- When a SYN arrives for a port that has no listening server.
- When TCP wants to abort an existing connection.
- When TCP receives a segment for a connection that does not exist.
- If the client’s SYN elicits an ICMP «destination unreachable» from some intermediate router, this is considered a soft error. The client kernel saves the message but keeps sending SYNs with the same time between each SYN as in the first scenario. If no response is received after some fixed amount of time (75 seconds for 4.4BSD), the saved ICMP error is returned to the process as either EHOSTUNREACH or ENETUNREACH . It is also possible that the remote system is not reachable by any route in the local system’s forwarding table, or that the connect call returns without waiting at all. Note that network unreachables are considered obsolete, and applications should just treat ENETUNREACH and EHOSTUNREACH as the same error.
Example: nonexistent host on the local subnet *¶
We run the client daytimetcpcli (Figure 1.5) and specify an IP address that is on the local subnet (192.168.1/24) but the host ID (100) is nonexistent. When the client host sends out ARP requests (asking for that host to respond with its hardware address), it will never receive an ARP reply.
We only get the error after the connect times out. Notice that our err_sys function prints the human-readable string associated with the ETIMEDOUT error.
Example: no server process running *¶
We specify a host (a local router) that is not running a daytime server:
The server responds immediately with an RST.
Example: destination not reachable on the Internet *¶
Our final example specifies an IP address that is not reachable on the Internet. If we watch the packets with tcpdump , we see that a router six hops away returns an ICMP host unreachable error.
As with the ETIMEDOUT error, connect returns the EHOSTUNREACH error only after waiting its specified amount of time.
In terms of the TCP state transition diagram (Figure 2.4):
- connect moves from the CLOSED state (the state in which a socket begins when it is created by the socket function) to the SYN_SENT state, and then, on success, to the ESTABLISHED state.
- If connect fails, the socket is no longer usable and must be closed. We cannot call connect again on the socket.
In Figure 11.10, we will see that when we call connect in a loop, trying each IP address for a given host until one works, each time connect fails, we must close the socket descriptor and call socket again.
bind Function¶
The bind function assigns a local protocol address to a socket. The protocol address is the combination of either a 32-bit IPv4 address or a 128-bit IPv6 address, along with a 16-bit TCP or UDP port number.
- The second argument myaddr is a pointer to a protocol-specific addres
- The third argument addrlen is the size of this address structure.
With TCP, calling bind lets us specify a port number, an IP address, both, or neither.
Servers bind their well-known port when they start. (Figure 1.9) If a TCP client or server does not do this, the kernel chooses an ephemeral port for the socket when either connect or listen is called.
- It is normal for a TCP client to let the kernel choose an ephemeral port, unless the application requires a reserved port (Figure 2.10)
- However, it is rare for a TCP server to let the kernel choose an ephemeral port, since servers are known by their well-known port.
Exceptions to this rule are Remote Procedure Call (RPC) servers. They normally let the kernel choose an ephemeral port for their listening socket since this port is then registered with the RPC port mapper. Clients have to contact the port mapper to obtain the ephemeral port before they can connect to the server. This also applies to RPC servers using UDP.
A process can bind a specific IP address to its socket. The IP address must belong to an interface on the host.
- For a TCP client, this assigns the source IP address that will be used for IP datagrams sent on the socket. Normally, a TCP client does not bind an IP address to its socket. The kernel chooses the source IP address when the socket is connected, based on the outgoing interface that is used, which in turn is based on the route required to reach the server
- For a TCP server, this restricts the socket to receive incoming client connections destined only to that IP address. If a TCP server does not bind an IP address to its socket, the kernel uses the destination IP address of the client’s SYN as the server’s source IP address.
As mentioned, calling bind lets us specify the IP address, the port, both, or neither. The following table summarizes the values to which we set sin_addr and sin_port , or sin6_addr and sin6_port , depending on the desired result.
| IP address | Port | Result |
|---|---|---|
| Wildcard | Kernel chooses IP address and port | |
| Wildcard | nonzero | Kernel chooses IP address, process specifies port |
| Local IP address | Process specifies IP address, kernel chooses port | |
| Local IP address | nonzero | Process specifies IP address and port |
- If we specify a port number of 0, the kernel chooses an ephemeral port when bind is called.
- If we specify a wildcard IP address, the kernel does not choose the local IP address until either the socket is connected (TCP) or a datagram is sent on the socket (UDP).
Wildcard Address and INADDR_ANY *¶
With IPv4, the wildcard address is specified by the constant INADDR_ANY , whose value is normally 0. This tells the kernel to choose the IP address. Figure 1.9 has the assignment:
While this works with IPv4, where an IP address is a 32-bit value that can be represented as a simple numeric constant (0 in this case), we cannot use this technique with IPv6, since the 128-bit IPv6 address is stored in a structure. In C we cannot represent a constant structure on the right-hand side of an assignment. To solve this problem, we write:
The system allocates and initializes the in6addr_any variable to the constant IN6ADDR_ANY_INIT . The header contains the extern declaration for in6addr_any .
The value of INADDR_ANY (0) is the same in either network or host byte order, so the use of htonl is not really required. But, since all the INADDR_ constants defined by the header are defined in host byte order, we should use htonl with any of these constants.
If we tell the kernel to choose an ephemeral port number for our socket (by specifying a 0 for port number), bind does not return the chosen value. It cannot return this value since the second argument to bind has the const qualifier. To obtain the value of the ephemeral port assigned by the kernel, we must call getsockname to return the protocol address.
Binding a non-wildcard IP address *¶
A common example of a process binding a non-wildcard IP address to a socket is a host that provides Web servers to multiple organizations:
- First, each organization has its own domain name, such as www.organization.com.
- Next, each organization’s domain name maps into a different IP address, but typically on the same subnet.
For example, if the subnet is 198.69.10, the first organization’s IP address could be 198.69.10.128, the next 198.69.10.129, and so on. All these IP addresses are then aliased onto a single network interface (using the alias option of the ifconfig command on 4.4BSD, for example) so that the IP layer will accept incoming datagrams destined for any of the aliased addresses. Finally, one copy of the HTTP server is started for each organization and each copy bind s only the IP address for that organization.
An alternative technique is to run a single server that binds the wildcard address. When a connection arrives, the server calls getsockname to obtain the destination IP address from the client, which in our discussion above could be 198.69.10.128, 198.69.10.129, and so on. The server then handles the client request based on the IP address to which the connection was issued.
One advantage in binding a non-wildcard IP address is that the demultiplexing of a given destination IP address to a given server process is then done by the kernel.
We must be careful to distinguish between the interface on which a packet arrives versus the destination IP address of that packet. In Section 8.8, we will talk about the weak end system model and the strong end system model. Most implementations employ the former, meaning it is okay for a packet to arrive with a destination IP address that identifies an interface other than the interface on which the packet arrives. (This assumes a multihomed host.) Binding a non-wildcard IP address restricts the datagrams that will be delivered to the socket based only on the destination IP address. It says nothing about the arriving interface, unless the host employs the strong end system model.
A common error from bind is EADDRINUSE («Address already in use»), which is detailed in Section 7.5 when discussing the SO_REUSEADDR and SO_REUSEPORT socket options.
listen Function¶
The listen function is called only by a TCP server and it performs two actions:
- The listen function converts an unconnected socket into a passive socket, indicating that the kernel should accept incoming connection requests directed to this socket. In terms of the TCP state transition diagram (Figure 2.4), the call to listen moves the socket from the CLOSED state to the LISTEN state.
- When a socket is created by the socket function (and before calling listen ), it is assumed to be an active socket, that is, a client socket that will issue a connect .
- The second argument backlog to this function specifies the maximum number of connections the kernel should queue for this socket.
This function is normally called after both the socket and bind functions and must be called before calling the accept function.
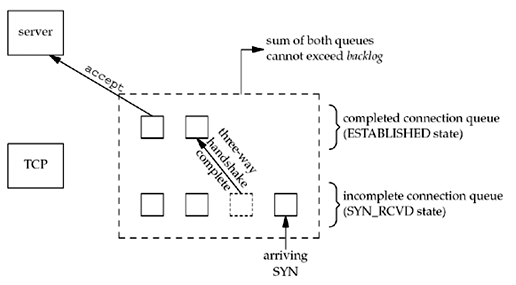
Connection queues *¶
To understand the backlog argument, we must realize that for a given listening socket, the kernel maintains two queues:
- An incomplete connection queue, which contains an entry for each SYN that has arrived from a client for which the server is awaiting completion of the TCP three-way handshake. These sockets are in the SYN_RCVD state (Figure 2.4).
- A completed connection queue, which contains an entry for each client with whom the TCP three-way handshake has completed. These sockets are in the ESTABLISHED state (Figure 2.4).
These two queues are depicted in the figure below:
When an entry is created on the incomplete queue, the parameters from the listen socket are copied over to the newly created connection. The connection creation mechanism is completely automatic; the server process is not involved.
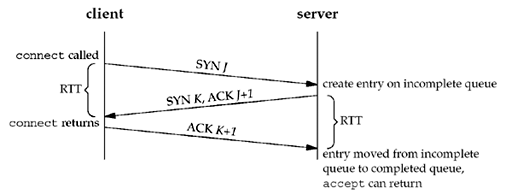
Packet exchanges during conenction establishment *¶
The following figure depicts the packets exchanged during the connection establishment with these two queues:
- When a SYN arrives from a client, TCP creates a new entry on the incomplete queue and then responds with the second segment of the three-way handshake: the server’s SYN with an ACK of the client’s SYN (Section 2.6).
- This entry will remain on the incomplete queue, until:
- The third segment of the three-way handshake arrives (the client’s ACK of the server’s SYN), or
- The entry times out. (Berkeley-derived implementations have a timeout of 75 seconds for these incomplete entries.)
- If the three-way handshake completes normally, the entry moves from the incomplete queue to the end of the completed queue.
- When the process calls accept :
- The first entry on the completed queue is returned to the process, or
- If the queue is empty, the process is put to sleep until an entry is placed onto the completed queue.
The backlog argument *¶
Several points to consider when handling the two queues:
- Sum of both queues. The backlog argument to the listen function has historically specified the maximum value for the sum of both queues.
- Multiplied by 1.5. Berkeley-derived implementations add a fudge factor to the backlog: It is multiplied by 1.5.
- If the backlog specifies the maximum number of completed connections the kernel will queue for a socket, then the reason for the fudge factor is to take into account incomplete connections on the queue.
- Do not specify value of 0 for backlog, as different implementations interpret this differently (Figure 4.10). If you do not want any clients connecting to your listening socket, close the listening socket.
- One RTT. If the three-way handshake completes normally (no lost segments and no retransmissions), an entry remains on the incomplete connection queue for one RTT.
- Configurable maximum value. Many current systems allow the administrator to modify the maximum value for the backlog. Historically, sample code always shows a backlog of 5 (which is adequate today).
- What value should the application specify for the backlog (5 is often inadequate)? There is no easy answer to this.
- HTTP servers now specify a larger value, but if the value specified is a constant in the source code, to increase the constant requires recompiling the server.
- Another method is to allow a command-line option or an environment variable to override the default. It is always acceptable to specify a value that is larger than supported by the kernel, as the kernel should silently truncate the value to the maximum value that it supports, without returning an error. The following example is the wrapper function for listen which allows the environment variable LISTENQ to override the value specified by the caller:
- Fixed number of connections. Historically the reason for queuing a fixed number of connections is to handle the case of the server process being busy between successive calls to accept . This implies that of the two queues, the completed queue should normally have more entries than the incomplete queue. Again, busy Web servers have shown that this is false. The reason for specifying a large backlog is because the incomplete connection queue can grow as client SYNs arrive, waiting for completion of the three-way handshake.
- No RST sent if queues are full. If the queues are full when a client SYN arrives, TCP ignores the arriving SYN; it does not send an RST. This is because the condition is considered temporary, and the client TCP will retransmit its SYN, hopefully finding room on the queue in the near future. If the server TCP immediately responded with an RST, the client’s connect would return an error, forcing the application to handle this condition instead of letting TCP’s normal retransmission take over. Also, the client could not differentiate between an RST in response to a SYN meaning «there is no server at this port» versus «there is a server at this port but its queues are full.»
- Data queued in the socket’s receive buffer. Data that arrives after the three-way handshake completes, but before the server calls accept , should be queued by the server TCP, up to the size of the connected socket’s receive buffer.
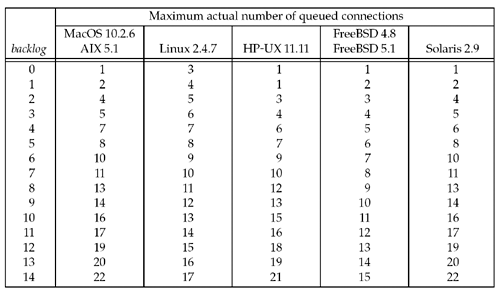
The following figure shows actual number of queued connections for values of backlog:
SYN Flooding *¶
SYN flooding is a type of attack (the attacker writes a program to send SYNs at a high rate to the victim) that attempts to fill the incomplete connection queue for one or more TCP ports. Additionally, the source IP address of each SYN is set to a random number (called IP spoofing) so that the server’s SYN/ACK goes nowhere.This also prevents the server from knowing the real IP address of the attacker. By filling the incomplete queue with bogus SYNs, legitimate SYNs are not queued, providing a denial of service to legitimate clients.
The listen ‘s backlog argument should specify the maximum number of completed connections for a given socket that the kernel will queue. The purpose ofto limit completed connections is to stop the kernel from accepting new connection requests for a given socket when the application is not accepting them. If a system implements this interpretation, then the application need not specify huge backlog values just because the server handles lots of client requests or to provide protection against SYN flooding. The kernel handles lots of incomplete connections, regardless of whether they are legitimate or from a hacker. But even with this interpretation, scenarios do occur where the traditional value of 5 is inadequate.
accept Function¶
accept is called by a TCP server to return the next completed connection from the front of the completed connection queue (Figure 4.7). If the completed connection queue is empty, the process is put to sleep (assuming the default of a blocking socket).
The cliaddr and addrlen arguments are used to return the protocol address of the connected peer process (the client). addrlen is a value-result argument (Section 3.3):
- Before the call, we set the integer value referenced by *addrlen to the size of the socket address structure pointed to by cliaddr;
- On return, this integer value contains the actual number of bytes stored by the kernel in the socket address structure.
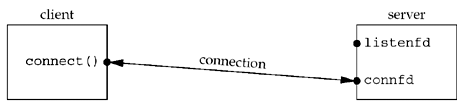
If successful, accept returns a new descriptor automatically created by the kernel. This new descriptor refers to the TCP connection with the client.
- The listening socket is the first argument (sockfd) to accept (the descriptor created by socket and used as the first argument to both bind and listen ).
- The connected socket is the return value from accept the connected socket.
It is important to differentiate between these two sockets:
- A given server normally creates only one listening socket, which then exists for the lifetime of the server.
- The kernel creates one connected socket for each client connection that is accepted (for which the TCP three-way handshake completes).
- When the server is finished serving a given client, the connected socket is closed.
This function returns up to three values:
- An integer return code that is either a new socket descriptor or an error indication,
- The protocol address of the client process (through the cliaddr pointer),
- The size of this address (through the addrlen pointer).
If we are not interested in having the protocol address of the client returned, we set both cliaddr and addrlen to null pointers. See intro/daytimetcpsrv.c.
Example: Value-Result Arguments¶
The following code shows how to handle the value-result argument to accept by modifying the code from intro/daytimetcpsrv.c to print the IP address and port of the client:
This program does the following:
- New declarations. Two new variables are defined:
- len will be a value-result variable.
- cliaddr will contain the client’s protocol address.
- Accept connection and print client’s address.
- Initialize len to the size of the socket address structure
- Pass a pointer to the cliaddr structure and a pointer to len as the second and third arguments to accept.
- Call inet_ntop (Section 3.7) to convert the 32-bit IP address in the socket address structure to a dotted-decimal ASCII string and call ntohs (Section 3.4) to convert the 16-bit port number from network byte order to host byte order.
Run this new server and then run our client on the same host, connecting to our server twice in a row:
We first specify the server’s IP address as the loopback address (127.0.0.1) and then as its own IP address (192.168.1.20). Here is the corresponding server output:
Since our daytime client (Figure 1.5) does not call bind , the kernel chooses the source IP address based on the outgoing interface that is used (Section 4.4).
- In the first case, the kernel sets the source IP address to the loopback address;
- In the second case, it sets the address to the IP address of the Ethernet interface.
We can also see in this example that the ephemeral port chosen by the Solaris kernel is 43388, and then 43389
The pound sign (#) as the shell prompt indicates that our server must run with superuser privileges to bind the reserved port of 13. If we do not have superuser privileges, the call to bind will fail:
fork and exec Functions¶
Concurrent Servers¶
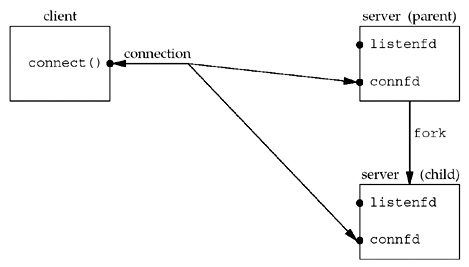
The server described in intro/daytimetcpsrv1.c is an iterative server. But when a client request can take longer to service, we do not want to tie up a single server with one client; we want to handle multiple clients at the same time. The simplest way to write a concurrent server under Unix is to fork a child process to handle each client.
The following code shows the outline for a typical concurrent server:
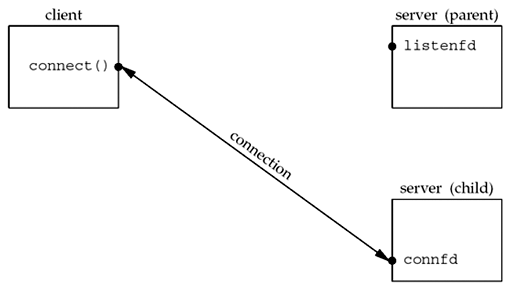
- When a connection is established, accept returns, the server calls fork, and the child process services the client (on connfd , the connected socket) and the parent process waits for another connection (on listenfd , the listening socket). The parent closes the connected socket since the child handles the new client.
- We assume that the function doit does whatever is required to service the client. When this function returns, we explicitly close the connected socket in the child. This is not required since the next statement calls exit , and part of process termination is to close all open descriptors by the kernel. Whether to include this explicit call to close or not is a matter of personal programming taste.
Reference count of sockets *¶
Calling close on a TCP socket causes a FIN to be sent, followed by the normal TCP connection termination sequence. Why doesn’t the close of connfd by the parent terminate its connection with the client? To understand what’s happening, we must understand that every file or socket has a reference count. The reference count is maintained in the file table entry. This is a count of the number of descriptors that are currently open that refer to this file or socket. In the above code:
- After socket returns, the file table entry associated with listenfd has a reference count of 1.
- After accept returns, the file table entry associated with connfd has a reference count of 1.
- But, after fork returns, both descriptors are shared (duplicated) between the parent and child, so the file table entries associated with both sockets now have a reference count of 2. Therefore, when the parent closes connfd , it just decrements the reference count from 2 to 1 and that is all.
- The actual cleanup and de-allocation of the socket does not happen until the reference count reaches 0. This will occur at some time later when the child closes connfd .
Visualizing the sockets and connection *¶
The following figures visualize the sockets and connection in the code above:
Before call to accept returns, the server is blocked in the call to accept and the connection request arrives from the client:
Ater return from accept , the connection is accepted by the kernel and a new socket connfd is created (this is a connected socket and data can now be read and written across the connection):
After fork returns, both descriptors, listenfd and connfd , are shared (duplicated) between the parent and child:
After the parent closes the connected socket and the child closes the listening socket:
This is the desired final state of the sockets. The child is handling the connection with the client and the parent can call accept again on the listening socket, to handle the next client connection.
close Function¶
The normal Unix close function is also used to close a socket and terminate a TCP connection.
The default action of close with a TCP socket is to mark the socket as closed and return to the process immediately. The socket descriptor is no longer usable by the process: It cannot be used as an argument to read or write . But, TCP will try to send any data that is already queued to be sent to the other end, and after this occurs, the normal TCP connection termination sequence takes place.
SO_LINGER socket option (detailed in Section 7.5) lets us change this default action with a TCP socket.
Descriptor Reference Counts¶
As mentioned in end of Section 4.8, when the parent process in our concurrent server closes the connected socket, this just decrements the reference count for the descriptor. Since the reference count was still greater than 0, this call to close did not initiate TCP’s four-packet connection termination sequence. This is the behavior we want with our concurrent server with the connected socket that is shared between the parent and child.
If we really want to send a FIN on a TCP connection, the shutdown function can be used (Section 6.6) instead of close .
Be aware if the parent does not call close for each connected socket returned by accept :
- The parent will eventually run out of descriptors (there is usually a limit to the number of descriptors that any process can have open at any time)
- None of the client connections will be terminated. When the child closes the connected socket, its reference count will go from 2 to 1 and it will remain at 1 since the parent never close s the connected socket. This will prevent TCP’s connection termination sequence from occurring, and the connection will remain open.
getsockname and getpeername Functions¶
- getsockname returns the local protocol address associated with a socket.
- getpeername returns the foreign protocol address associated with a socket.
The addrlen argument for both functions is value-result argument: both functions fill in the socket address structure pointed to by localaddr or peeraddr.
The term «name» in the function name is misleading. These two functions return the protocol address associated with one of the two ends of a network connection, which for IPV4 and IPV6 is the combination of an IP address and port number. These functions have nothing to do with domain names.
These two functions are required for the following reasons:
- After connect successfully returns in a TCP client that does not call bind , getsockname returns the local IP address and local port number assigned to the connection by the kernel.
- After calling bind with a port number of 0 (telling the kernel to choose the local port number), getsockname returns the local port number that was assigned.
- getsockname can be called to obtain the address family of a socket.
- In a TCP server that bind s the wildcard IP address (intro/daytimetcpsrv.c), once a connection is established with a client ( accept returns successfully), the server can call getsockname to obtain the local IP address assigned to the connection. The socket descriptor argument to getsockname must be that of the connected socket, and not the listening socket.
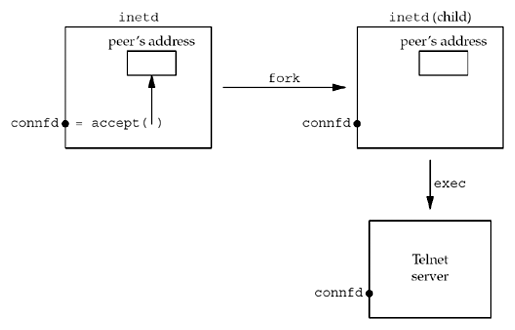
- When a server is exec ed by the process that calls accept , the only way the server can obtain the identity of the client is to call getpeername . For example, inetd fork s and exec s a TCP server (follwing figure):
- inetd calls accept , which return two values: the connected socket descriptor ( connfd , return value of the function) and the «peer’s address» (an Internet socket address structure) that contains the IP address and port number of the client.
- fork is called and a child of inetd is created, with a copy of the parent’s memory image, so the socket address structure is available to the child, as is the connected socket descriptor (since the descriptors are shared between the parent and child).
- When the child exec s the real server (e.g. Telnet server that we show), the memory image of the child is replaced with the new program file for the Telnet server (the socket address structure containing the peer’s address is lost), and the connected socket descriptor remains open across the exec . One of the first function calls performed by the Telnet server is getpeername to obtain the IP address and port number of the client.
In this example, the Telnet server must know the value of connfd when it starts. There are two common ways to do this.
- The process calling exec pass it as a command-line argument to the newly exec ed program.
- A convention can be established that a certain descriptor is always set to the connected socket before calling exec .
The second one is what inetd does, always setting descriptors 0, 1, and 2 to be the connected socket.
Example: Obtaining the Address Family of a Socket¶
The sockfd_to_family function shown in the code below returns the address family of a socket.
This program does the following:
- Allocate room for largest socket address structure. Since we do not know what type of socket address structure to allocate, we use a sockaddr_storage value, since it can hold any socket address structure supported by the system.
- Call getsockname . We call getsockname and return the address family. The POSIX specification allows a call to getsockname on an unbound socket.
Источник
ошибка привязки порта «Адрес уже используется» Программирование TCP-сокета в unix
Я просмотрел много сообщений и форумов, и я новичок в программировании сокетов. Основные части моего кода похожи на
BIND ERROR: адрес уже используется
но затем я изменил свой код, чтобы включить функцию «setsockopt» следующим образом:
const char* port="5555";
int opt=1;
portno=atoi(port);
//parameters for server address
serv_addr.sin_family=AF_INET;
serv_addr.sin_port=htons(portno);
serv_addr.sin_addr.s_addr=INADDR_ANY;
//bind the socket to the address
setsockopt(sockfd,SOL_SOCKET,SO_REUSEADDR,(const char *)&opt,sizeof(int));
if(bind(sockfd,(struct sockaddr*)&serv_addr,sizeof(serv_addr))<0)
{close(sockfd);
error("error in binding port!");
}
Но все же я получаю сообщение об ошибке. Мне нужно закрыть терминал и перезапустить его, чтобы снова использовать порт. Я хочу использовать жестко запрограммированный порт (как я уже упоминал в коде выше)
Thanks a lot in advance
2 ответы
Проверьте, используется ли порт. Либо telnet в этот порт или использовать netstat -a. Он должен быть использован (как указывает ошибка) и убить соответствующий процесс. Возможно, используя ps найти процесс.
Создан 09 фев.
Номер порта может использоваться одновременно только одним приложением. Это означает, что вы не можете запускать одну и ту же программу дважды, ожидая, что обе будут привязаны к одному и тому же порту.
Компания SO_REUSEADDR когда сокет, привязанный к адресу, уже был закрыт, тот же адрес (пара IP-адрес / порт) можно снова использовать напрямую.
Создан 09 фев.
Не тот ответ, который вы ищете? Просмотрите другие вопросы с метками
c
sockets
unix
tcp
or задайте свой вопрос.