i looked around a lot of similar question but none of this fixing my issue. We are upgrading to TLS 1.2 and am getting the below error which i got from Windows event log
An TLS 1.2 connection request was received from a remote client application,
but none of the cipher suites supported by the client application are supported by the server.
lantronix xport pro(Supporting TLS 1.2) Device making a call to the .net service deployed in Windows server 2012.
Client/Server Handshake is failing but am not able to figure out why. issue happens in the below line
stream.AuthenticateAsServer(_serverCertificate, false, SslProtocols.Ssl3| SslProtocols.Tls | SslProtocols.Tls11 | SslProtocols.Tls12, true);
Used Wireshark and Windows server 2012 R2 have only TLs 1.1 and 1.2 enabled using IIS Crypto
Client send TLS 1.2 Request with below Cipher suites
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
Cipher Suite: TLS_RSA_WITH_3DES_EDE_CBC_SHA (0x000a)
Cipher Suite: TLS_RSA_EXPORT1024_WITH_RC4_56_MD5 (0x0060)
Cipher Suite: TLS_RSA_EXPORT1024_WITH_RC4_56_SHA (0x0064)
Cipher Suite: TLS_RSA_EXPORT_WITH_RC4_40_MD5 (0x0003)
But server doesnt respond with Server Hello and finding the error message that none of the cipher supported by server.
I can see in IIS Crypto that AES_128_CBC_SHA in the crypto. But am not sure why it failing and almost stuck for days. Hope to get some clarity on what i can do further to troubleshoot this
My SSL requests failed when the client was Windows Server 2003, and the server (a win7 box) showed this error in the event log:
An TLS 1.0 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.
I spent days trying to fix it, trying about twenty different things. In the end, the real solution was to generate the SSL certificates again from scratch, this time forcing RSA and SHA1 (though SHA1 should be the default anyway). I used:
makecert -pe -r -ss my -sr localMachine -n “CN=[domain name or IP address]” -e 01/01/2099 -a sha1 -eku 1.3.6.1.5.5.7.3.1 -sky exchange -sp “Microsoft RSA SChannel Cryptographic Provider” -sy 12
Here is what all the switches mean:
-pe include private key
-r self-signed
-ss my put cert into “Personal” certificate store
-sr localMachine use local machine’s cert stores (not current user’s)
-n common name (external IP or domain name of server)
-e expiry date
-a sha1 use SHA1
-eku 1.3.6.1.5.5.7.3.1 enhanced key usage Object Identifier (OID) for “SSL server certificate”
-sky exchange cert is for key exchange
-sp “Microsoft RSA SChannel Cryptographic Provider” use RSA
-sy 12 CryptoAPI provider type
For some reason Win Server 2k3 couldn’t or wouldn’t use the right ciphers with a default makecert certificate.
Hope this helps someone.
I am running Ubuntu Server 20.04 and proftpd 1.36 and have an issue setting up TLS.
I have followed the guide in the config file, but I get a very odd error. That there is no supported cipher. And then the process breaks with a handshake error. The SSL clienthello message includes a lot of ciphers that is recognised, and that is on the machine.
TLS log:
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL sessions attempted: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL sessions established: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL sessions renegotiated: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL sessions resumed: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL sessions in cache: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL session cache hits: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL session cache misses: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL session cache timeouts: 0
2020-06-29 18:16:30,457 mod_tls/2.7[87378]: [stat]: SSL session cache size exceeded: 0
2020-06-29 18:16:35,242 mod_tls/2.7[87910]: TLSOption EnableDiags enabled, setting diagnostics callback
2020-06-29 18:16:35,245 mod_tls/2.7[87910]: error initializing OpenSSL context for this session
2020-06-29 18:16:35,247 mod_tls/2.7[87910]: TLS/TLS-C requested, starting TLS handshake
2020-06-29 18:16:35,247 mod_tls/2.7[87910]: [info] (unknown): before SSL initialization
2020-06-29 18:16:35,247 mod_tls/2.7[87910]: [info] accepting: before SSL initialization
2020-06-29 18:16:35,247 mod_tls/2.7[87910]: [info] accepting: before SSL initialization
2020-06-29 18:16:35,255 mod_tls/2.7[87910]: [msg] received protocol record message (5 bytes)
2020-06-29 18:16:35,255 mod_tls/2.7[87910]: [info] accepting: before SSL initialization
2020-06-29 18:16:35,255 mod_tls/2.7[87910]: [msg] received TLSv1.3 'ClientHello' Handshake message (368 bytes)
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [msg]
ClientHello:
client_version = TLS 1.2
random:
gmt_unix_time = Thu Oct 20 14:46:18 1904 (not guaranteed to be accurate)
random_bytes (28 bytes)
5820ebe66e5afa9ec7d9cfc5d69fd7b97698ba054091bd338c918587
session_id (0 bytes)
cipher_suites (58 bytes)
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
TLS_AES_128_GCM_SHA256
[unknown/unsupported]
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
[unknown/unsupported]
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
[unknown/unsupported]
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
[unknown/unsupported]
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
[unknown/unsupported]
TLS_RSA_WITH_AES_256_CBC_SHA
[unknown/unsupported]
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA
[unknown/unsupported]
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
[unknown/unsupported]
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
[unknown/unsupported]
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
[unknown/unsupported]
compression_methods (1 byte)
None
extensions (265 bytes)
extension_type = status_request (5 bytes)
extension_type = elliptic_curves (22 bytes)
extension_type = ec_point_formats (2 bytes)
extension_type = signature_algorithms (34 bytes)
extension_type = encrypt_then_mac (0 bytes)
extension_type = extended_master_secret (0 bytes)
extension_type = session_ticket (0 bytes)
extension_type = key_share (139 bytes)
extension_type = supported_versions (9 bytes)
extension_type = renegotiate (1 byte)
extension_type = psk_kex_modes (3 bytes)
extension_type = [unknown/unsupported] (2 bytes)
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [msg] sent protocol record message (5 bytes)
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [msg] sent TLSv1.2 fatal 'handshake_failure' Alert message (2 bytes)
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [info] writing: SSL/TLS alert fatal: handshake failure
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [info] accepting: error
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: unable to accept TLS connection: protocol error:
(1) error:1417A0C1:SSL routines:tls_post_process_client_hello:no shared cipher
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: unable to accept TLS connection: client does not support any cipher from 'TLSCipherSuite DEFAULT:!ADH:!EXPORT:!DES' (see `openssl ciphers DE>
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: TLS/TLS-C negotiation failed on control channel
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL sessions attempted: 1
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL sessions established: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL sessions renegotiated: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL sessions resumed: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL sessions in cache: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL session cache hits: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL session cache misses: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL session cache timeouts: 0
2020-06-29 18:16:35,256 mod_tls/2.7[87910]: [stat]: SSL session cache size exceeded: 0
Output of openssl
openssl ciphers -v 'DEFAULT:!ADH:!EXPORT:!DES'
TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD
TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD
TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD
ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD
ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD
DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD
ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD
ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD
DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD
ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384
ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384
DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256
ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256
ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256
DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256
ECDHE-ECDSA-AES256-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1
ECDHE-RSA-AES256-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1
DHE-RSA-AES256-SHA SSLv3 Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
ECDHE-ECDSA-AES128-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1
ECDHE-RSA-AES128-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1
DHE-RSA-AES128-SHA SSLv3 Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
RSA-PSK-AES256-GCM-SHA384 TLSv1.2 Kx=RSAPSK Au=RSA Enc=AESGCM(256) Mac=AEAD
DHE-PSK-AES256-GCM-SHA384 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(256) Mac=AEAD
RSA-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=RSAPSK Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
DHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=DHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
ECDHE-PSK-CHACHA20-POLY1305 TLSv1.2 Kx=ECDHEPSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD
PSK-AES256-GCM-SHA384 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(256) Mac=AEAD
PSK-CHACHA20-POLY1305 TLSv1.2 Kx=PSK Au=PSK Enc=CHACHA20/POLY1305(256) Mac=AEAD
RSA-PSK-AES128-GCM-SHA256 TLSv1.2 Kx=RSAPSK Au=RSA Enc=AESGCM(128) Mac=AEAD
DHE-PSK-AES128-GCM-SHA256 TLSv1.2 Kx=DHEPSK Au=PSK Enc=AESGCM(128) Mac=AEAD
AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD
PSK-AES128-GCM-SHA256 TLSv1.2 Kx=PSK Au=PSK Enc=AESGCM(128) Mac=AEAD
AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256
AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256
ECDHE-PSK-AES256-CBC-SHA384 TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(256) Mac=SHA384
ECDHE-PSK-AES256-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(256) Mac=SHA1
SRP-RSA-AES-256-CBC-SHA SSLv3 Kx=SRP Au=RSA Enc=AES(256) Mac=SHA1
SRP-AES-256-CBC-SHA SSLv3 Kx=SRP Au=SRP Enc=AES(256) Mac=SHA1
RSA-PSK-AES256-CBC-SHA384 TLSv1 Kx=RSAPSK Au=RSA Enc=AES(256) Mac=SHA384
DHE-PSK-AES256-CBC-SHA384 TLSv1 Kx=DHEPSK Au=PSK Enc=AES(256) Mac=SHA384
RSA-PSK-AES256-CBC-SHA SSLv3 Kx=RSAPSK Au=RSA Enc=AES(256) Mac=SHA1
DHE-PSK-AES256-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(256) Mac=SHA1
AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
PSK-AES256-CBC-SHA384 TLSv1 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA384
PSK-AES256-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(256) Mac=SHA1
ECDHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA256
ECDHE-PSK-AES128-CBC-SHA TLSv1 Kx=ECDHEPSK Au=PSK Enc=AES(128) Mac=SHA1
SRP-RSA-AES-128-CBC-SHA SSLv3 Kx=SRP Au=RSA Enc=AES(128) Mac=SHA1
SRP-AES-128-CBC-SHA SSLv3 Kx=SRP Au=SRP Enc=AES(128) Mac=SHA1
RSA-PSK-AES128-CBC-SHA256 TLSv1 Kx=RSAPSK Au=RSA Enc=AES(128) Mac=SHA256
DHE-PSK-AES128-CBC-SHA256 TLSv1 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA256
RSA-PSK-AES128-CBC-SHA SSLv3 Kx=RSAPSK Au=RSA Enc=AES(128) Mac=SHA1
DHE-PSK-AES128-CBC-SHA SSLv3 Kx=DHEPSK Au=PSK Enc=AES(128) Mac=SHA1
AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
PSK-AES128-CBC-SHA256 TLSv1 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA256
PSK-AES128-CBC-SHA SSLv3 Kx=PSK Au=PSK Enc=AES(128) Mac=SHA1
As you can see there is plenty of matching ciphers. So why do I get this error??
———— Bonus info———-
I have tried changing the Cipher to a single cipher, to every cipher, still same error.
I have tried changing the protocol, still same error.
Google has not helped me find a solution, all errors seems to be with actual missing certificates, or not related.
proftpd tls config for completions sake:
#
# Proftpd sample configuration for FTPS connections.
#
# Note that FTPS impose some limitations in NAT traversing.
# See http://www.castaglia.org/proftpd/doc/contrib/ProFTPD-mini-HOWTO-TLS.html
# for more information.
#
<IfModule mod_tls.c>
TLSEngine on
TLSLog /var/log/proftpd/tls.log
TLSProtocol SSLv23
#
# Server SSL certificate. You can generate a self-signed certificate using
# a command like:
#
# openssl req -x509 -newkey rsa:1024
# -keyout /etc/ssl/private/proftpd.key -out /etc/ssl/certs/proftpd.crt
# -nodes -days 365
#
# The proftpd.key file must be readable by root only. The other file can be
# readable by anyone.
#
# chmod 0600 /etc/ssl/private/proftpd.key
# chmod 0640 /etc/ssl/private/proftpd.key
#
TLSRSACertificateFile /etc/ssl/certs/proftpd.crt
TLSRSACertificateKeyFile /etc/ssl/private/proftpd.key
#
# CA the server trusts...
#TLSCACertificateFile /etc/ssl/certs/CA.pem
# ...or avoid CA cert and be verbose
TLSOptions NoCertRequest EnableDiags
# ... or the same with relaxed session use for some clients (e.g. FireFtp)
#TLSOptions NoCertRequest EnableDiags NoSessionReuseRequired
#
#
# Per default drop connection if client tries to start a renegotiate
# This is a fix for CVE-2009-3555 but could break some clients.
#
#TLSOptions AllowClientRenegotiations
#
# Authenticate clients that want to use FTP over TLS?
#
#TLSVerifyClient off
#
# Are clients required to use FTP over TLS when talking to this server?
#
TLSRequired auth
#
# Allow SSL/TLS renegotiations when the client requests them, but
# do not force the renegotations. Some clients do not support
# SSL/TLS renegotiations; when mod_tls forces a renegotiation, these
# clients will close the data connection, or there will be a timeout
# on an idle data connection.
#
#TLSRenegotiate required off
</IfModule>
In the System Event Viewer I get this error message
«An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.»
In the App Svc log I get
SSPI «The client and server cannot communicate, because they do not possess a common algorithm.»
I am on windows 7 running both the client and server on the same machine.
the server is a netTcpBinding with
<security mode=»Transport»>
<transport clientCredentialType=»Certificate» />
</security>
In Microsoft Message Analyzer I can see the TLS Client Handshake hello message go to the server the server responds with zero bytes and closes the connection, I assume because it doesn’t like the algorythms listed by the client.
Does anybody know how to parse the TLS client handshake message in Microsoft Message Analyzer?
Does the certificate in any way restrict what Algorithms are allowed? For example when I look at cert props I see MD5. Does that mean only MD5 can be used?
This was working last week. I think this started after Installing Visual Studio 2015. But it could have been a windows update. Not sure.
Any help would be appreciated.
Модератор: xM
Правила форума
Убедительная просьба юзать теги [code] при оформлении листингов.
Сообщения не оформленные должным образом имеют все шансы быть незамеченными.
-
ladserg
- рядовой
- Сообщения: 13
- Зарегистрирован: 2014-01-23 8:35:18
- Откуда: Россия
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Стоит exim, настроен, работает. TLS тоже работает. Но при попытке получить письмо с серверов Microsoft устанавливаются множественные конекты с их MTA, после чего некоторое время коннекты висят и затем отпадывают с выдачей ошибки.
Пример сообщений лога:
2018-01-23 16:32:23 [9336] SMTP connection from [104.47.42.74]:18608 I=[46.146.239.184]:25 (TCP/IP connection count = 1)
2018-01-23 16:45:05 [9377] TLS error on connection from mail-by2nam03on0074.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.74]:18608 I=[46.146.239.184]:25 (send): Error in the push function.
2018-01-23 16:45:05 [9377] TLS error on connection from mail-by2nam03on0074.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.74]:18608 I=[46.146.239.184]:25 (recv): The TLS connection was non-properly terminated.
2018-01-23 16:45:05 [9377] H=mail-by2nam03on0074.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.74]:18608 I=[46.146.239.184]:25 incomplete transaction (connection lost) from <account-security-noreply@accountprotection.microsoft.com> for **@***.***.**
2018-01-23 16:45:05 [9377] TLS error on connection from mail-by2nam03on0074.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.74]:18608 I=[46.146.239.184]:25 (send): The specified session has been invalidated for some reason.
2018-01-23 16:45:05 [9377] unexpected disconnection while reading SMTP command from mail-by2nam03on0074.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.74]:18608 I=[46.146.239.184]:25
Команда exiwhat во время попыток доставки следующее:
9336 daemon(4.89): -q30m, listening for SMTP on port 25 (IPv4) and for SMTPS on port 465 (IPv4) port 587 (IPv4)
12276 handling TLS incoming connection from mail-dm3nam03on0076.outbound.protection.outlook.com (NAM03-DM3-obe.outbound.protection.outlook.com) [104.47.41.76]:59392 I=[46.146.239.184]:25
12279 handling TLS incoming connection from mail-co1nam03on0058.outbound.protection.outlook.com (NAM03-CO1-obe.outbound.protection.outlook.com) [104.47.40.58]:61192 I=[46.146.239.184]:25
12280 handling TLS incoming connection from mail-by2nam03on0053.outbound.protection.outlook.com (NAM03-BY2-obe.outbound.protection.outlook.com) [104.47.42.53]:44626 I=[46.146.239.184]:25
12457 handling TLS incoming connection from mail-co1nam03on0069.outbound.protection.outlook.com (NAM03-CO1-obe.outbound.protection.outlook.com) [104.47.40.69]:39376 I=[46.146.239.184]:25
ОС — debian 9, на версии 7 и 8 проблема была та же (обновился с 7го релиза пытаясь решить проблему).
Вывод exim -bV:
Exim version 4.89 #1 built 28-Nov-2017 21:58:00
Copyright (c) University of Cambridge, 1995 — 2017
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 — 2017
Berkeley DB: Berkeley DB 5.3.28: (September 9, 2013)
Support for: crypteq iconv() IPv6 PAM Perl Expand_dlfunc GnuTLS move_frozen_messages Content_Scanning DKIM DNSSEC Event OCSP PRDR PROXY SOCKS TCP_Fast_Open
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch ldap ldapdn ldapm mysql nis nis0 passwd pgsql sqlite
Authenticators: cram_md5 cyrus_sasl dovecot plaintext spa tls
Routers: accept dnslookup ipliteral iplookup manualroute queryprogram redirect
Transports: appendfile/maildir/mailstore/mbx autoreply lmtp pipe smtp
Fixed never_users: 0
Configure owner: 0:0
Size of off_t: 8
2018-01-23 18:06:57 Warning: purging the environment.
Suggested action: use keep_environment.
Configuration file is /var/lib/exim4/config.autogenerated
С остальными серверами проблем не наблюдается, есть ошибки вида:
2018-01-23 16:33:55 [9336] SMTP connection from [149.202.123.238]:59164 I=[46.146.239.184]:25 (TCP/IP connection count = 3)
2018-01-23 16:33:58 [9474] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:59164 I=[46.146.239.184]:25 X=TLS1.2:DHE_RSA_AES_256_GCM_SHA384:256 CV=no F=<j@nicolatesla.ru> temporarily rejected RCPT <***@***>: greylisted.
2018-01-23 16:33:58 [9474] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:59164 I=[46.146.239.184]:25 (recv): The TLS connection was non-properly terminated.
2018-01-23 16:33:58 [9474] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:59164 I=[46.146.239.184]:25 incomplete transaction (connection lost) from <j@nicolatesla.ru>
2018-01-23 16:33:58 [9474] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:59164 I=[46.146.239.184]:25 (send): The specified session has been invalidated for some reason.
2018-01-23 16:33:58 [9474] unexpected disconnection while reading SMTP command from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:59164 I=[46.146.239.184]:25
2018-01-23 16:46:03 [9336] SMTP connection from [149.202.123.238]:44435 I=[46.146.239.184]:25 (TCP/IP connection count = 6)
2018-01-23 16:46:04 [9861] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:44435 I=[46.146.239.184]:25 X=TLS1.2:DHE_RSA_AES_256_GCM_SHA384:256 CV=no F=<gbj@nicolatesla.ru> temporarily rejected RCPT <***@***.***.**>: greylisted.
2018-01-23 16:46:04 [9861] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:44435 I=[46.146.239.184]:25 (recv): The TLS connection was non-properly terminated.
2018-01-23 16:46:04 [9861] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:44435 I=[46.146.239.184]:25 incomplete transaction (connection lost) from <gbj@nicolatesla.ru>
2018-01-23 16:46:04 [9861] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:44435 I=[46.146.239.184]:25 (send): The specified session has been invalidated for some reason.
2018-01-23 16:46:04 [9861] unexpected disconnection while reading SMTP command from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:44435 I=[46.146.239.184]:25
2018-01-23 17:11:35 [9336] SMTP connection from [149.202.123.238]:49703 I=[46.146.239.184]:25 (TCP/IP connection count = 7)
2018-01-23 17:11:39 [10604] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:49703 I=[46.146.239.184]:25 X=TLS1.2:DHE_RSA_AES_256_GCM_SHA384:256 CV=no F=<svvrfa@nicolatesla.ru> temporarily rejected RCPT <***@***.***.**>: greylisted.
2018-01-23 17:11:39 [10604] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:49703 I=[46.146.239.184]:25 (recv): The TLS connection was non-properly terminated.
2018-01-23 17:11:39 [10604] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:49703 I=[46.146.239.184]:25 incomplete transaction (connection lost) from <svvrfa@nicolatesla.ru>
2018-01-23 17:11:39 [10604] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:49703 I=[46.146.239.184]:25 (send): The specified session has been invalidated for some reason.
2018-01-23 17:11:39 [10604] unexpected disconnection while reading SMTP command from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:49703 I=[46.146.239.184]:25
2018-01-23 18:00:50 [9336] SMTP connection from [149.202.123.238]:46242 I=[46.146.239.184]:25 (TCP/IP connection count = 7)
2018-01-23 18:00:51 [12388] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:46242 I=[46.146.239.184]:25 X=TLS1.2:DHE_RSA_AES_256_GCM_SHA384:256 CV=no F=<yawabu@nicolatesla.ru> temporarily rejected RCPT <***@***.***.**>: greylisted.
2018-01-23 18:00:51 [12388] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:46242 I=[46.146.239.184]:25 (recv): The TLS connection was non-properly terminated.
2018-01-23 18:00:51 [12388] H=nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:46242 I=[46.146.239.184]:25 incomplete transaction (connection lost) from <yawabu@nicolatesla.ru>
2018-01-23 18:00:51 [12388] TLS error on connection from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:46242 I=[46.146.239.184]:25 (send): The specified session has been invalidated for some reason.
2018-01-23 18:00:51 [12388] unexpected disconnection while reading SMTP command from nicolatesla.ru (mail.nicolatesla.ru) [149.202.123.238]:46242 I=[46.146.239.184]:25
Но это как я понял результат работы greylist’а.
Ставил сертификат от Let’s Encrypt, проблема не изчезла. Если точнее — то ничего не изменилось.
Не могу понять в чем проблема, а получения этих писем нам требуется.
Может есть у кого какая идея или сталкивался кто с аналогичной проблемой?
-
Хостинг HostFood.ru
Услуги хостинговой компании Host-Food.ru
Хостинг HostFood.ru
Тарифы на хостинг в России, от 12 рублей: https://www.host-food.ru/tariffs/hosting/
Тарифы на виртуальные сервера (VPS/VDS/KVM) в РФ, от 189 руб.: https://www.host-food.ru/tariffs/virtualny-server-vps/
Выделенные сервера, Россия, Москва, от 2000 рублей (HP Proliant G5, Intel Xeon E5430 (2.66GHz, Quad-Core, 12Mb), 8Gb RAM, 2x300Gb SAS HDD, P400i, 512Mb, BBU):
https://www.host-food.ru/tariffs/vydelennyi-server-ds/
Недорогие домены в популярных зонах: https://www.host-food.ru/domains/
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
xM » 2018-01-24 13:35:01
Попробуйте для начала обновить у себя корневые сертификаты.
Для FreeBSD это делается так
-
ladserg
- рядовой
- Сообщения: 13
- Зарегистрирован: 2014-01-23 8:35:18
- Откуда: Россия
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
ladserg » 2018-01-24 14:47:54
xM писал(а):Попробуйте для начала обновить у себя корневые сертификаты.
Для FreeBSD это делается так
Спасибо за отклик. Проверил корневые сертификаты у себя. В дебиане это пакет ca-certificates, на всякий случай переустановил его:
Код: Выделить всё
apt-get install --reinstall ca-certificatesПодключил неподключенные:
Код: Выделить всё
dpkg-reconfigure ca-certificates
update-ca-certificates -f
c_rehash /etc/ssl/certs
Рестартанул exim. Проверил ssl соединение:
Код: Выделить всё
openssl s_client -connect mta.medlife.perm.ru:465 -tls1 -servername mta.medlife.perm.ruCONNECTED(00000003)
depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3
verify return:1
depth=1 C = US, O = Let’s Encrypt, CN = Let’s Encrypt Authority X3
verify return:1
depth=0 CN = mta.medlife.perm.ru
verify return:1
—
Certificate chain
0 s:/CN=mta.medlife.perm.ru
i:/C=US/O=Let’s Encrypt/CN=Let’s Encrypt Authority X3
1 s:/C=US/O=Let’s Encrypt/CN=Let’s Encrypt Authority X3
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
—
Server certificate
——BEGIN CERTIFICATE——
MIIFCTCCA/GgAwIBAgISA9KGM+pM6hoO5Vr11qAROOHDMA0GCSqGSIb3DQEBCwUA
MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD
ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xODAxMTkxMTEzMjlaFw0x
ODA0MTkxMTEzMjlaMB4xHDAaBgNVBAMTE210YS5tZWRsaWZlLnBlcm0ucnUwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC4VcgN1c5xf568S1B+9xvP5JX7
jTIVjAHBMy8gIiuHSdkmC+wrSXL4kY0mbQ3mF1ewtH+4akbE5SEybrm8WqyDxYhN
oCrDnyzMi/Dlo2JLpGLpFbLl2j3tPfqbo7UsomhUAZ+k0LNQAVzoIX0KtUrDiQTK
dqJNPcjrXunsxBGKWJW/LBx9/KCnmZWALmezvV1z2Q4F72oXjvaqfXcfcU6VuP2u
byFxCwaVQbSIfaYyPUooIZJnAyZLwlctIuFP57miY/xdJ+MbPkYzCUygkdlM6xnY
5GiszUMCiTaYh5UBAN9Na1LHofNh++Ets72hGbaNTCkutanyvRCn3Sp98tZhAgMB
AAGjggITMIICDzAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEG
CCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYEFGBJEfSpWaNg0rDMRAKC
wH/3CsQjMB8GA1UdIwQYMBaAFKhKamMEfd265tE5t6ZFZe/zqOyhMG8GCCsGAQUF
BwEBBGMwYTAuBggrBgEFBQcwAYYiaHR0cDovL29jc3AuaW50LXgzLmxldHNlbmNy
eXB0Lm9yZzAvBggrBgEFBQcwAoYjaHR0cDovL2NlcnQuaW50LXgzLmxldHNlbmNy
eXB0Lm9yZy8wHgYDVR0RBBcwFYITbXRhLm1lZGxpZmUucGVybS5ydTCB/gYDVR0g
BIH2MIHzMAgGBmeBDAECATCB5gYLKwYBBAGC3xMBAQEwgdYwJgYIKwYBBQUHAgEW
Gmh0dHA6Ly9jcHMubGV0c2VuY3J5cHQub3JnMIGrBggrBgEFBQcCAjCBngyBm1Ro
aXMgQ2VydGlmaWNhdGUgbWF5IG9ubHkgYmUgcmVsaWVkIHVwb24gYnkgUmVseWlu
ZyBQYXJ0aWVzIGFuZCBvbmx5IGluIGFjY29yZGFuY2Ugd2l0aCB0aGUgQ2VydGlm
aWNhdGUgUG9saWN5IGZvdW5kIGF0IGh0dHBzOi8vbGV0c2VuY3J5cHQub3JnL3Jl
cG9zaXRvcnkvMA0GCSqGSIb3DQEBCwUAA4IBAQCQPkqrjIs5uDazD+cPXew18tMv
63pJqRoqzx5Sj3Wtl3AlCkK7TyU0yN2Z0mTWFRmRKUoQkktu/PncwwR7gCpxO5Jv
DgHs6ulZH4vSyipL6+SrMQHJ7drE3DQRrDAC+aeB+T0zbxwO1i/8nYxArz6GN8eb
QlPouHerW32ftV6aFFrsKzu6H5JbfXqufCzduXrqx8iP8PekEtm5yTXLLY0V7soY
wh1jmm4PVV7d5oVOiQFg7hkWGWdL6iFJGEhUX1UPg/V30ytew58+pk2Eq8nwwKan
PDj/V4jjHKeybV0a7K3G09o7NXhkXWxoQmtIenrZQcMqP44yvuAJxahWZVR3
——END CERTIFICATE——
subject=/CN=mta.medlife.perm.ru
issuer=/C=US/O=Let’s Encrypt/CN=Let’s Encrypt Authority X3
—
No client certificate CA names sent
Server Temp Key: ECDH, P-256, 256 bits
—
SSL handshake has read 2993 bytes and written 268 bytes
Verification: OK
—
New, TLSv1.0, Cipher is ECDHE-RSA-AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1
Cipher : ECDHE-RSA-AES256-SHA
Session-ID: BF9624F0AE5BDFA317F7A6F624114F8EDDA0F5BA36EACAC451D51AADE944A563
Session-ID-ctx:
Master-Key: D3F861250549EECB0E4A5955F95BAEAB84658FA45751186483F8D630A07D4C9A76C6FE8574E0A8A623E542C9720AFAB1
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1516794076
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
—
220 mta.medlife.perm.ru ESMTP Exim 4.89 Wed, 24 Jan 2018 16:41:16 +0500
ehlo mta.medlife.perm.ru
250-mta.medlife.perm.ru Hello localhost [127.0.0.1]
250-SIZE 27262976
250-8BITMIME
250-PIPELINING
250 HELP
QUIT
DONE
Проверил STARTTLS:
Код: Выделить всё
swaks -a -tls -q HELO -s mta.medlife.perm.ru -au test -ap '<>'=== Trying mta.medlife.perm.ru:25…
=== Connected to mta.medlife.perm.ru.
<- 220 mta.medlife.perm.ru ESMTP Exim 4.89 Wed, 24 Jan 2018 16:44:04 +0500
-> EHLO mta.medlife.perm.ru
<- 250-mta.medlife.perm.ru Hello localhost [127.0.0.1]
<- 250-SIZE 27262976
<- 250-8BITMIME
<- 250-PIPELINING
<- 250-STARTTLS
<- 250 HELP
-> STARTTLS
<- 220 TLS go ahead
=== TLS started with cipher TLSv1.2:ECDHE-RSA-AES256-GCM-SHA384:256
=== TLS no local certificate set
=== TLS peer DN=»/CN=mta.medlife.perm.ru»
~> EHLO mta.medlife.perm.ru
<~ 250-mta.medlife.perm.ru Hello localhost [127.0.0.1]
<~ 250-SIZE 27262976
<~ 250-8BITMIME
<~ 250-PIPELINING
<~ 250 HELP
~> QUIT
<~ 221 mta.medlife.perm.ru closing connection
=== Connection closed with remote host.
И всё равно коннекты с *.outbound.protection.outlook.com висят подолгу, плодятся, затем отваливаются с вышеописанными ошибками
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
xM » 2018-01-24 17:24:09
У меня нет особенных идей. Разве что tcpdump посмотреть что там происходит.
Но, к слову, Microsoft’овская почта ещё та штука. К примеру, они умудряются в транзите повреждать тело подписанных DKIM сообщений, а шлют от другого имени хоста, нежели представляется в HELO. Ну и как не вспомнить историю, когда для всех «счастливых» пользователей Outlook/Hotmail пару недель не работал IMAP.
-
ladserg
- рядовой
- Сообщения: 13
- Зарегистрирован: 2014-01-23 8:35:18
- Откуда: Россия
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
ladserg » 2018-01-24 20:14:27
Кстати, а в EXIM есть возможность журналировать SMTP сеанс, в смысле какие команды и сообщения в сеансе посылаются? Судя по логам сама сессия начинается, происходит проверка SPF письма, конверт письма передаётся, и на сём сессия зависает. У меня есть подозрение что с шифрованием что то не так. При чём от гугла письма приходят.
Самое обидное, что в письмах этих шлётся код верификации для входа в кабинет с лицензиями и дистрибутивами.
Может подскажет кто, как заставить именно эти сервера без не стартовать TLS?
Отправлено спустя 10 минут 23 секунды:
Упс, кажется добился от них любви и ласки. Установил правило кое пропускает все проверки для их писем и письма стали ходить. Завтра поразбираюсь на каком правиле у меня виснет.
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
xM » 2018-01-24 20:31:25
Возможно у вас что-то в районе согласования шифров не проходит.
В любом случае, на дебаге должно быть видно всё в деталях. У Exim он подробный.
-
ladserg
- рядовой
- Сообщения: 13
- Зарегистрирован: 2014-01-23 8:35:18
- Откуда: Россия
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
ladserg » 2018-01-25 14:59:39
Нашел я правило, на коем подвисает коннект и валится сессия:
Код: Выделить всё
# Проверка существования адреса отправителя
warn
hosts = !+relay_from_hosts
!verify = sender/callout=3m,defer_ok
logwrite = [WARN][ACCC] Sender callout verify is invalid
H=$sender_helo_name[$sender_host_address] F=$sender_address T:$local_part@$domain
set acl_c_spamscore = ${eval:$acl_c_spamscore+20}
set acl_c_spamlog = $acl_c_spamlog Callout error;
Теперь осталось выяснить какое решение принять по этому поводу. Похоже ряд других почтовых серверов, чьи письма так же нужны, тоже не проходят проверку на существование почтового ящика.
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
xM » 2018-01-25 15:30:51
ladserg писал(а): !verify = sender/callout=3m,defer_ok
Это очень плохая практика. Рекомендую отказаться от callouts совершенно.
Отправлено спустя 1 минуту :
Чтобы долго не писать, вот вам статья где умный дядя всё по полочкам раскладывает
https://bsdly.blogspot.lt/2017/08/twent … s-are.html
-
ladserg
- рядовой
- Сообщения: 13
- Зарегистрирован: 2014-01-23 8:35:18
- Откуда: Россия
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
ladserg » 2018-01-25 16:28:37
xM писал(а):
ladserg писал(а): !verify = sender/callout=3m,defer_ok
Это очень плохая практика. Рекомендую отказаться от callouts совершенно.
Отправлено спустя 1 минуту :
Чтобы долго не писать, вот вам статья где умный дядя всё по полочкам раскладывает
https://bsdly.blogspot.lt/2017/08/twent … s-are.html
Понятно. Похоже я научился на собственной ошибке. За ссылку спасибо, хоть с англицким у меня плохо, но гугл-переводчик помог понять из статьи, что проверка сия не столь актуальна и может быть даже чревата. Вернее она стала чревата в моём случае.
Я правильно понял, что при обратной проверке на проверяемом сервере так же запускаются проверки на мою проверку, на которые мой сервер так же может запустить свои проверки?
-
xM
- ст. лейтенант
- Сообщения: 1316
- Зарегистрирован: 2009-01-15 23:57:41
- Откуда: Königsberg
- Контактная информация:
exim4: Проблемы с TLS при попытке получения писем с *.outbound.protection.outlook.com
Непрочитанное сообщение
xM » 2018-01-25 16:33:06
Да, грубо говоря, callout мало что даёт и, тем более гарантирует, создаёт нагрузку на обе системы, более того, если спамер использует несуществующий адрес в чужом домене, то callout с вашего сервера выглядит как попытка отправить туда спам, и, таким образом, вы можете попасть в spam trap с последующим баном вашего IP.
Отправлено спустя 38 секунд:
ladserg писал(а):
Я правильно понял, что при обратной проверке на проверяемом сервере так же запускаются проверки на мою проверку, на которые мой сервер так же может запустить свои проверки?
Смотря что там настроено, но, обычно, маловероятно.
In last blog, I introduced how SSL/TLS connections are established and how to verify the whole handshake process in network packet file. However capturing network packet is not always supported or possible for certain scenarios. Here in this blog, I will introduce 5 handy tools that can test different phases of SSL/TLS connection so that you can narrow down the cause of SSL/TLS connection issue and locate root cause.
curl
Suitable scenarios: TLS version mismatch, no supported CipherSuite, network connection between client and server.
curl is an open source tool available on Windows 10, Linux and Unix OS. It is a tool designed to transfer data and supports many protocols. HTTPS is one of them. It can also used to test TLS connection.
Examples:
1. Test connection with a given TLS version.
curl -v https://pingrds.redis.cache.windows.net:6380 —tlsv1.0
2. Test with a given CipherSuite and TLS version
curl -v https://pingrds.redis.cache.windows.net:6380 —ciphers ECDHE-RSA-NULL-SHA —tlsv1.2
Success connection example:
curl -v https://pingrds.redis.cache.windows.net:6380 --tlsv1.2
* Rebuilt URL to: https://pingrds.redis.cache.windows.net:6380/
* Trying 13.75.94.86...
* TCP_NODELAY set
* Connected to pingrds.redis.cache.windows.net (13.75.94.86) port 6380 (#0)
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 1/3)
* schannel: checking server certificate revocation
* schannel: sending initial handshake data: sending 202 bytes...
* schannel: sent initial handshake data: sent 202 bytes
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: failed to receive handshake, need more data
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: encrypted data got 4096
* schannel: encrypted data buffer: offset 4096 length 4096
* schannel: received incomplete message, need more data
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: encrypted data got 1024
* schannel: encrypted data buffer: offset 5120 length 5120
* schannel: received incomplete message, need more data
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: encrypted data got 496
* schannel: encrypted data buffer: offset 5616 length 6144
* schannel: sending next handshake data: sending 3791 bytes...
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: encrypted data got 51
* schannel: encrypted data buffer: offset 51 length 6144
* schannel: SSL/TLS handshake complete
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 3/3)
* schannel: stored credential handle in session cacheFail connection example due to either TLS version mismatch. Not supported ciphersuite returns similar error.
curl -v https://pingrds.redis.cache.windows.net:6380 --tlsv1.0
* Rebuilt URL to: https://pingrds.redis.cache.windows.net:6380/
* Trying 13.75.94.86...
* TCP_NODELAY set
* Connected to pingrds.redis.cache.windows.net (13.75.94.86) port 6380 (#0)
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 1/3)
* schannel: checking server certificate revocation
* schannel: sending initial handshake data: sending 144 bytes...
* schannel: sent initial handshake data: sent 144 bytes
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: failed to receive handshake, need more data
* schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step 2/3)
* schannel: failed to receive handshake, SSL/TLS connection failed
* Closing connection 0
* schannel: shutting down SSL/TLS connection with pingrds.redis.cache.windows.net port 6380
* Send failure: Connection was reset
* schannel: failed to send close msg: Failed sending data to the peer (bytes written: -1)
* schannel: clear security context handle
curl: (35) schannel: failed to receive handshake, SSL/TLS connection failedFailed due to network connectivity issue.
curl -v https://pingrds.redis.cache.windows.net:6380 --tlsv1.2
* Rebuilt URL to: https://pingrds.redis.cache.windows.net:6380/
* Trying 13.75.94.86...
* TCP_NODELAY set
* connect to 13.75.94.86 port 6380 failed: Timed out
* Failed to connect to pingrds.redis.cache.windows.net port 6380: Timed out
* Closing connection 0
curl: (7) Failed to connect to pingrds.redis.cache.windows.net port 6380: Timed outopenssl
Suitable scenarios: TLS version mismatch, no supported CipherSuite, network connection between client and server.
openSSL is an open source tool and its s_client acts as SSL client to test SSL connection with a remote server. This is helpful to isolate the cause of client.
- On majority Linux machines, OpenSSL is there already. On Windows, you can download it from this link: https://chocolatey.org/packages/openssl
- Run Open SSL
- Windows: open the installation directory, click /bin/, and then double-click openssl.exe.
- Mac and Linux: run openssl from a terminal.
- Issue s_client -help to find all options.
Command examples:
1. Test a particular TLS version:
s_client -host sdcstest.blob.core.windows.net -port 443 -tls1_1
2. Disable one TLS version
s_client -host sdcstest.blob.core.windows.net -port 443 -no_tls1_2
3. Test with a given ciphersuite:
s_client -host sdcstest.blob.core.windows.net -port 443 -cipher ECDHE-RSA-AES256-GCM-SHA384
4. Verify if remote server’s certificates are trusted.
Success connection example:
CONNECTED(000001A0)
depth=1 C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = *.blob.core.windows.net
verify return:1
---
Certificate chain
0 s:CN = *.blob.core.windows.net
i:C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02
1 s:C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02
i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root
---
Server certificate
-----BEGIN CERTIFICATE-----
MIINtDCCC5ygAwIBAgITfwAI6NfesKGuQGWPYQAAAAjo1zANBgkqhkiG9w0BAQsF
ADBPMQswCQYDVQQGEwJVUzEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9u
pK8hqxL0zc4NQLRTq9RNpdPwnNmGn5SZ4Nu5ktUgWokR97THzgs6a/ErHH2tigLF
jwkgB8UuV/hhu3vEa0jxstSBgbjQPgSNexAl7XwgawaucIF+wkRpPW2w0VTcDWtT
1bGtFCpewAo=
-----END CERTIFICATE-----
subject=CN = *.blob.core.windows.net
issuer=C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02
---
No client certificate CA names sent
Peer signing digest: MD5-SHA1
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 5399 bytes and written 293 bytes
Verification error: unable to get local issuer certificate
---
New, TLSv1.0, Cipher is ECDHE-RSA-AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.1
Cipher : ECDHE-RSA-AES256-SHA
Session-ID: B60B0000F51FFB7C9DDB4E58CD20DC20987C13CFD31386BE435D612CF5EFDBF9
Session-ID-ctx:
Master-Key: DA402F6E301B4E4981B7820CAF6E0AF3C633290E85E2998BFAB081788488D3807ABD3FF41FF48DA55DB56281C024C4F4
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1615557502
Timeout : 7200 (sec)
Verify return code: 20 (unable to get local issuer certificate)
Extended master secret: yesFail connection example due to TLS mismatch:
OpenSSL> s_client -host sdcstest.blob.core.windows.net -port 443 -tls1_3
CONNECTED(0000017C)
write:errno=10054
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 254 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
error in s_client
Fail connection example due to network connectivity:
OpenSSL> s_client -host sdcstest.blob.core.windows.net -port 7780
30688:error:0200274C:system library:connect:reason(1868):crypto/bio/b_sock2.c:110:
30688:error:2008A067:BIO routines:BIO_connect:connect error:crypto/bio/b_sock2.c:111:
connect:errno=0
error in s_client
Online tool
https://www.ssllabs.com/ssltest/
Suitable scenarios: TLS version mismatch, no supported CipherSuite.
This is a free online service performs a deep analysis of the configuration of any SSL web server on the public Internet. It can list all supported TLS versions and ciphers of a server. And auto detect if server works fine in different types of client, such as web browsers, mobile devices, etc.
Please note, this only works with public access website. For internal access website will need to run above curl or openssl from an internal environment. And it only supports domain name and does not work with IP address.
Web Browser:
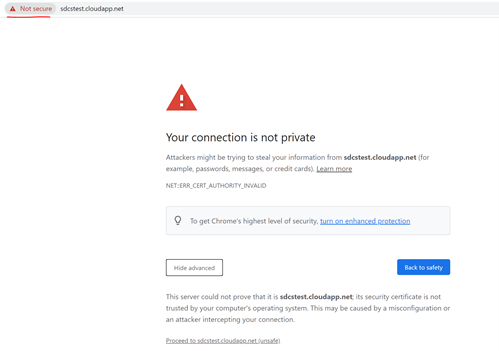
Suitable scenarios: Verify if server certificate chain is trusted on client.
Web Browser can be used to verify if remote server’s certificate is trusted or not locally:
- Access the url from web browser.
- It does not matter if the page can be load or not. Before loading anything from the remote sever, web browser tried to establish SSL connection.
- If you see below error returned, it means certificate is not trusted on current machine.
Certutil
Suitable scenarios: Verify if server certificate on client, verify client certificate on server.
Certutil is a tool available on windows. It is useful to verify a given certificate. For example verify server certificate from client end. If mutual authentication is implemented, this tool can also be used to verify client certificate on server.
The command auto verifies trusted certificate chain and certificate revocation list (CRL).
Command:
certutil -verify -urlfetch <client cert file path>
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certutil#-verify
Next blog, I will introduce solutions for common causes of SSL/TLS connection issues.