- Remove From My Forums
-
Question
-
Hi,
I wanted to issue user certificate from CA and got error:
Error Constructing or Publishing Certificate The certificate validity period will be shorter than the User Certificate Template specifies, because the template validity period is longer than the maximum certificate validity period allowed by the CA. Consider
renewing the CA certificate, reducing the template validity period, or increasing the registry validity periodWe use online ent CA, how to solve this issue? Will it help if I change «ValidityPeriodUnits» in registry?
thanks
aurimas
Answers
-
Yes, that is why you got the error. Three things determine the validity period of an issued certificate:
1. The validity period of the CA’s certificate
2. The ValidityPeriodUnits and ValidityPeriod reg keys
3. The template itself
If the CA certificate is due to expire next month, then no certificates can be issued that are valid longer than one month. So, in your case your CA’s certificate expires in less than one year, so no certificate can be issued with a validity period
greater than 2012.02.01.In order to resolve this, you need to renew the CA’s certificate:
Creating a Certificate Renewal Strategy
http://technet.microsoft.com/en-us/library/cc772847(WS.10).aspxThanks!
-
Proposed as answer by
Monday, May 9, 2011 3:02 PM
-
Marked as answer by
Bruce-Liu
Tuesday, May 17, 2011 10:50 AM
-
Proposed as answer by
Issue
When requesting a certificate via the browser, at the point you try to issue the certificate (via certsrv.msc) you receive the error:
Error Constructing or Publishing Certificate
When looking through the Events for Active Directoty Certificate Services you see the error:
Active Directory Certificate Services denied request 8 because The request subject name is invalid or too long. 0x80094001 (-2146877439).
Solution
To enable the parsing of request attributes for subject information, the following command must be run. This allows for enrollment through web enrollment pages. Once done restart the certification authority service (net stop certsvc && net start certsvc).
certutil -setreg caCRLFlags +CRLF_ALLOW_REQUEST_ATTRIBUTE_SUBJECT
Additional
A useful command to check the request attributes can be found below:
C:UsersAdministrator>certutil -view -restrict “Disposition>=30,Disposition<=31”
!! Output Omitted !!
Request Attributes: ”
challenge: provePequalsNP
country: UK
state: HANTS
locality: STOKE
org: IT
orgunit: IT
email: [email protected]
commonname: bob
CertificateUsage: 1.3.6.1.5.5.7.3.2
UserAgentString: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.4 (KHTML, like Gecko) Chrome/22.0.1229.94 Safari/537.4
- Author
- Recent Posts
Rick Donato is a Network Automation Architect/Evangelist and the founder of Packet Coders.
Want to become a Windows expert?
Here is our hand-picked selection of the best courses you can find online:
Windows Server 2019 Administration course
Windows 10 Troubleshooting course
and our recommended certification practice exams:
AlphaPrep Practice Tests — Free Trial
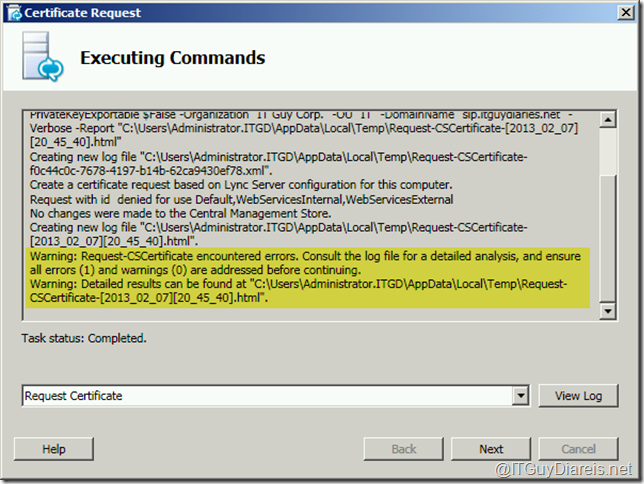
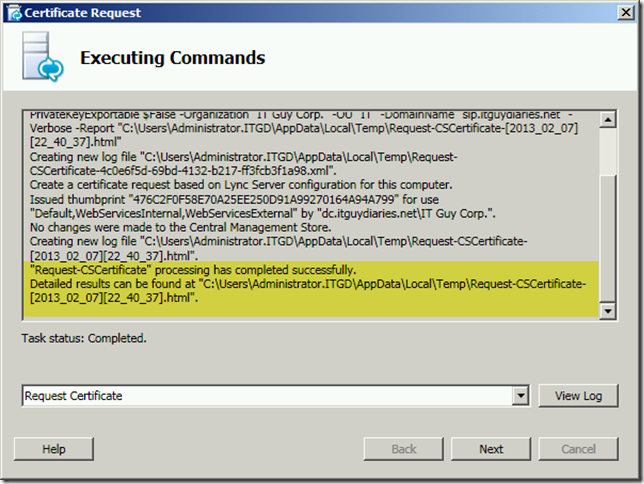
Recently, I was working on installing Lync Server 2010 for testing purposes , all was going smoothly till I reached the certificate request and assignment step . When I ran the certificate request wizard I was able to complete the request but with a warning as shown below :
When I checked the log file I got the following “Error:Error Constructing or Publishing Certificate”
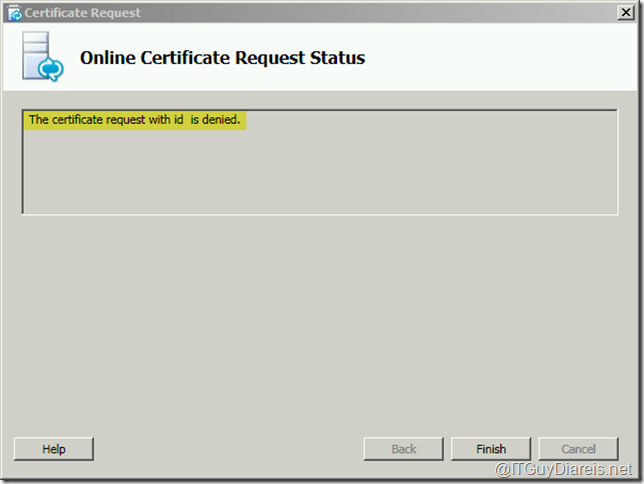
Additionally , I got the following when clicked next at the certificate request wizard
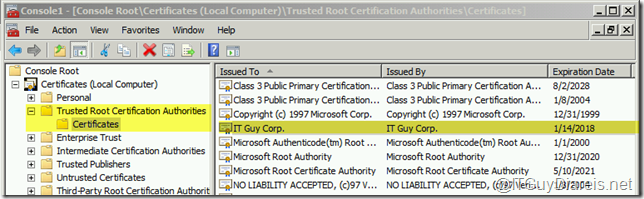
I verified the existence of the root CA certificate at the Trusted Root Certification Authorities container on the Lync Server ,as below :
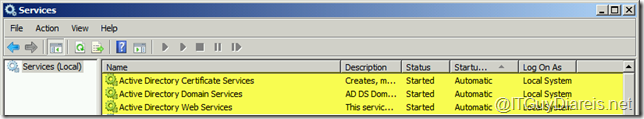
At this stage I went to check my Certificate Authority server s follow :
-
Checked the services at Services snap-in : Both Active Directory Domain Services and Active Directory Certificate Services were started
-
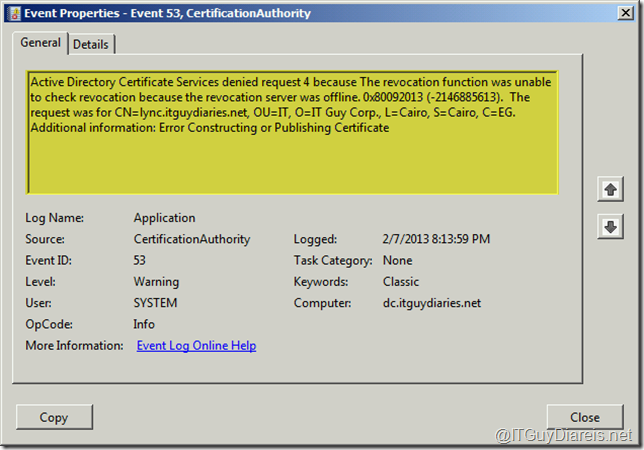
Upon checking for Active Directory Certificate Services events using Event Viewer I found that an event with ID 53 is present identifying the cause of the certificate generation failure
Hence , although the services were up and running all required was to do a restart for both Directory Domain Services and Active Directory Certificate Services ( Thanks to the restartable Active Directory Domain Services ) and voilà , the certificate request completed successfully without any warnings or errors
Tried to request a new Certificate from the Enterprise Certificate Authority and received the following error:
Your Certificate Request was denied.
Error Constructing or Publishing Certificate.
The solution is to restart the Certificate Authority service as it looked like it had got itself into a bind. Now you will be able to get create your certificate.
Leave a Reply
Enter your comment here…
Fill in your details below or click an icon to log in:
Email (required) (Address never made public)
Name (required)
Website
You are commenting using your WordPress.com account.
( Log Out /
Change )
You are commenting using your Twitter account.
( Log Out /
Change )
You are commenting using your Facebook account.
( Log Out /
Change )
Cancel
Connecting to %s
Notify me of new comments via email.
Notify me of new posts via email.
When adding a new Skype for Business server to an existing topology, I came across the following error statement whilst trying to request a certificate from the internal certificate authority:
Command execution failed: Error Constructing or Publishing Certificate. The certificate validity period will be shorter than the “template name” certificate template specifies, because the template validity period is longer than the maximum certificate validity period allowed by the CA. Consider renewing the CA Certificate, reducing the template validity period, or increasing the registry validity period.
A screen shot of the error
The problem is down to a configuration issue with the certificate authority used for the request. I decided to perform some due diligence checking against what was currently configured. First checking the certificate template used, I could establish that the validity period of the template was 3 years.
Next, I decided I would double check the root certificate had not expired, as you can see from the screen shot, it is within it’s validity period
Next on the list of advices from the error was to check the registry validity period on the certificate authority server. You can check the values by browsing to the following locations using the registry editor:
HKLM:SYSTEMCurrentControlSetServicesCertSvcConfiguration”CA NAME”
The two entries you need to be concerned with are:
- ValidityPeriod – This should be set to Years
- ValidityPeriodUnits – This will be the number of units in the period set by the Validity Period (in my case: 2 Years)
By default, the registry validity period is set to two years.
As we can see, there is a discrepancy in the certificate template specifying a 3 year validity period, whilst the registry on the CA server has set a maximum of 2 years.
Changing the registry validity period to a higher or same value as the template is the recommended resolution to this error. Change the ValidityPeriodUnits value to a higher number e.g. 10
The restart the certificate authority services for the changes to take effect.
If you are not confortable with the registry editor method, you can alternatively use CERTUTIL to achieve this.
Open Command Prompt as an elevated administrator and type:
certutil –getreg CAValidityPeriod
and
certutil –getreg CAValidityPeriodUnits
These commands will output the current configured values:
To change the value of the validity period type the following command:
certutil –setreg CAValidityPeriodUnits 10
(where 10 is the number of units you want to set)
Again, restart the certificate authority service for these changes to take effect.
Once changed you will be able to request your Skype for Business certificates once more.
Mark is an Independent Microsoft Teams Consultant with over 15 years experience in Microsoft Technology. Mark is the founder of Commsverse, a dedicated Microsoft Teams conference and former MVP. You can follow him on twitter @UnifiedVale
- Remove From My Forums
-
Question
-
HI! Help plz!!!
Windows server 2008 r2
Log— <Event xmlns=»http://schemas.microsoft.com/win/2004/08/events/event«>
— <System>
<Provider Name=»Microsoft-Windows-CertificationAuthority« Guid=»{6A71D062-9AFE-4F35-AD08-52134F85DFB9}« EventSourceName=»CertSvc« />
<EventID Qualifiers=»33370«>53</EventID>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime=»2009-09-19T11:35:34.000000000Z« />
<EventRecordID>3046</EventRecordID>
<Execution ProcessID=»0« ThreadID=»0« />
<Channel>Application</Channel>
<Computer>VM.Ldsoft.com</Computer>
<Security UserID=»S-1-5-18« />
</System>
— <EventData Name=»MSG_DN_CERT_DENIED_WITH_INFO«>
<Data Name=»RequestId«>3</Data>
<Data Name=»Reason«>The certificate has invalid policy. 0x800b0113 (-2146762477)</Data>
<Data Name=»SubjectName«>CN=Osgood, OU=Service Accounts, DC=Ldsoft, DC=com</Data>
<Data Name=»AdditionalInformation«>Error Constructing or Publishing Certificate Invalid Issuance Policies: 1.3.6.1.4.1.311.21.8.4441183.15224949.6701450.1097412.9014876.64.1.401</Data>
</EventData>
</Event>
Answers
-
-
Marked as answer by
Tuesday, September 22, 2009 12:29 PM
-
Marked as answer by