Our VMware View Client disconnects after 8-10 hours without any notification. The error ‘Error reading from tunnel HTTP socket: An existing connection was forcibiliy closed by the remote host’ is displayed.
After clicking on the ‘OK’ button (only button available), the session disconnects. If you reconnect, you are good to go for another 8-10 hours.
I checked the ‘Automatically logoff after disconnect’ setting on the pool, it is set to 240 minutes.
The session timeout in the Global Settings are set to 9999999 minutes.
Client debug log:
2014-10-02T20:41:47.900+02:00 DEBUG (0F9C-0D54) <vchanRecvThread> [pcoip_mfw] pcoip_vchan_recv FAILED result -514
2014-10-02T20:41:47.900+02:00 DEBUG (0F9C-0D48) <vchanRecvThread2> [pcoip_mfw] pcoip_vchan_recv FAILED result -514
2014-10-02T20:41:47.978+02:00 DEBUG (0F9C-0B4C) <2892> [pcoip_mfw] pcoip disconnected
2014-10-02T20:41:48.088+02:00 DEBUG (0F9C-0D54) <vchanRecvThread> [ViewMMDevRedir] {MultimediaRedirChannel}: SessionId=108871520 — Closed/Disconnected
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0D54) <vchanRecvThread> [ViewMMDevRedir] {MultimediaRedirChannel}: Client side — After Channel Close notification
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0D54) <vchanRecvThread> [pcoip_mfw] channelThread STOP for channel MultimediaRedirChannel
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] DataMgrClient::ProcessEnvMsg — Processing PMsgChannelClose
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] States: Env=STOn. AIn=STOff. WCam=STOff
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] DataMgrClient::ProcessEnvMsg — Finished PMsgChannelClose
2014-10-02T20:41:48.135+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] States: Env=STChannelClose. AIn=STOff. WCam=STOff
2014-10-02T20:41:49.478+02:00 DEBUG (0F9C-0FA0) <4000> [vmware-remotemks] Unloaded virtual channel plugin vdp_rdpvcbridge @ C:Program Files (x86)VMwareVMware Horizon View Clientvdp_rdpvcbridge.dll
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0FA0) <4000> [vmware-remotemks] pcoip_vchan_plugin_client_exit(): unloaded
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0FA0) <4000> [ViewMMDevRedir] pcoip_vchan_plugin_client_exit — Unloading Pcoip Client Plugin Channel=MultimediaRedirChannel
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0FA0) <4000> [ViewMMDevRedir] {MultimediaRedirChannel}: Closing channel
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] stop of virtual channel MultimediaRedirChannel
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0FA0) <4000> [ViewMMDevRedir] {MultimediaRedirChannel}: Client side — After Channel Close notification
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] DataMgrClient::ProcessEnvMsg — Processing PMsgChannelClose
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] States: Env=STChannelClose. AIn=STOff. WCam=STOff
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] DataMgrClient::ProcessEnvMsg — Finished PMsgChannelClose
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] States: Env=STChannelClose. AIn=STOff. WCam=STOff
2014-10-02T20:41:49.541+02:00 DEBUG (0F9C-0A40) <2624> [ViewMMDevRedir] Thread exited. Name=DataMgrIntf. Id=2624
2014-10-02T20:41:49.572+02:00 DEBUG (0F9C-0A58) <2648> [ViewMMDevRedir] Thread exited. Name=DataMgrClient(Reg). Id=2648
2014-10-02T20:41:49.572+02:00 DEBUG (0F9C-0FA0) <4000> [ViewMMDevRedir] {MultimediaRedirChannel}: Client side deleted
2014-10-02T20:41:49.572+02:00 DEBUG (0F9C-0A5C) <2652> [ViewMMDevRedir] Thread exited. Name=VChanServiceThread — Client. Id=2652
2014-10-02T20:41:49.572+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] remove of pcoip_mfw MultimediaRedirChannel
2014-10-02T20:41:49.572+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] remove of pcoip_channel MultimediaRedirChannel
2014-10-02T20:41:49.822+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] stop of virtual channel Smart Card Virtual Channel
2014-10-02T20:41:49.822+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] remove of pcoip_mfw Smart Card Virtual Channel
2014-10-02T20:41:49.822+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] remove of pcoip_channel Smart Card Virtual Channel
2014-10-02T20:41:49.885+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] pcoip_mfw exit called
2014-10-02T20:41:49.900+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] service: Stop
2014-10-02T20:41:49.900+02:00 DEBUG (0F9C-0FE8) <NodeManagerWatcher> [pcoip_mfw] Closed outgoing SharedMemory channel to machine L-DY8QM3J, user L-DY8QM3JCUSTOMER
2014-10-02T20:41:50.760+02:00 DEBUG (0F9C-0FA0) <4000> [pcoip_mfw] DllMain — DLL_PROCESS_DETACH by «C:Program Files (x86)VMwareVMware Horizon View Clientvmware-remotemks.exe»
Security Server log:
2014-10-06T10:50:56.475+02:00 INFO (0820-0B54) <Thread-39> [g] (Request1963) User USERNAME connected to the Secure Gateway Server — session ID: FB20_***_4323
2014-10-06T10:50:56.477+02:00 WARN (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Old client detected: ChunkVersion = 0, latest = 1
2014-10-06T18:49:34.574+02:00 WARN (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel error: Stream closed
2014-10-06T19:49:39.539+02:00 INFO (0820-0A3C) <SessionHandler> [ay] (FB20_***_4323) User USERNAME Secure Gateway Server session ended — session ID: FB20_***_4323
2014-10-06T19:49:39.544+02:00 INFO (0820-0DD0) <Tunnel#1662> [ay] (FB20_***_4323) User USERNAME Secure Gateway Server session ended — session ID: FB20_***_4323
Security Server debug log:
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [q] (ad70_***_e26a) doCapStatus: capID = ad70_***_e26a, locationID = LOCATION-ID, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, clientVersion = 8.0, lite = false, newAllowed = true
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [q] (ad70_***_e26a) Found 0 existing connected sessions for: cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [q] (ad70_***_e26a) This session unknown or not yet connected.
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [bx] (ad70_***_e26a) getInstance: capID = NONE, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID, seh = com.vmware.vdi.ice.server.ay@3740dfc9
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [ay] (ad70_***_e26a) Created new session capID: FB20_***_4323
2014-10-06T10:50:56.216+02:00 DEBUG (0820-0A34) <MsgWorker#8> [bx] (ad70_***_e26a) Created new session for: capID = FB20_***_4323, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID
2014-10-06T10:50:56.475+02:00 DEBUG (0820-0B54) <Thread-39> [g] (Request1963) Tunnel (re)connection for capID = FB20_***_4323
2014-10-06T10:50:56.475+02:00 INFO (0820-0B54) <Thread-39> [g] (Request1963) User USERNAME connected to the Secure Gateway Server — session ID: FB20_***_4323
2014-10-06T10:50:56.476+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel reader starting.
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [bx] (FB20_***_4323) Tunnel registered: session = (ServerSession capID = FB20_***_4323, type = NORMAL, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID), connected = Mon Oct 06 10:50:56 CEST 2014
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Observed chunk version: 0
2014-10-06T10:50:56.477+02:00 WARN (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Old client detected: ChunkVersion = 0, latest = 1
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session.onMessage(INIT)
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Client capabilities: C-BASE
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Not initialising plugins, client not capable.
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session.onMessage(START)
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Starting session for capID FB20_***_4323
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Broker authenticated session started (local authentication): userDN=cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session authentication completed: userID = USERNAME
2014-10-06T10:50:56.477+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session will time out after: 599999927s, at Mon Oct 10 21:29:43 CEST 2033
2014-10-06T10:51:04.305+02:00 DEBUG (0820-0A38) <MsgWorker#9> [q] (FB20_***_4323) Raising channel directly
2014-10-06T10:51:04.305+02:00 DEBUG (0820-0A38) <MsgWorker#9> [al] (FB20_***_4323) Raising port *:-1 for IPADDRESS:4172(1) keepalives called Port1
2014-10-06T10:51:04.306+02:00 DEBUG (0820-0A38) <MsgWorker#9> [cs] (FB20_***_4323) Queuing request FB208BB6_A112_498E_BA33_2B2787194323-0
2014-10-06T10:51:04.350+02:00 DEBUG (0820-0A1C) <MsgWorker#2> [q] (FB20_***_4323) Raising channel directly
2014-10-06T10:51:04.350+02:00 DEBUG (0820-0A1C) <MsgWorker#2> [al] (FB20_***_4323) Raising port *:-1 for IPADDRESS:32111(0) keepalives called Port2
2014-10-06T10:51:04.360+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session.onMessage(LISTEN_RP)
2014-10-06T10:51:12.632+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) Session.onMessage(RAISE_RQ)
2014-10-06T10:51:12.632+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) createServerConveyor: graceConnection = null
2014-10-06T10:51:12.632+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [aa] (FB20_***_4323) Connecting directly to IPADDRESS:32111
2014-10-06T10:51:12.632+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [aa] (FB20_***_4323) Onbound connection will have SO_KEEPALIVE set.
2014-10-06T10:51:12.732+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [bm] (FB20_***_4323) Connected to /IPADDRESS:32111
2014-10-06T10:51:12.732+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [al] (FB20_***_4323) User USERNAME starting channel 1 connecting to target IPADDRESS:32111 session FB20_***_4323
2014-10-06T18:49:34.574+02:00 WARN (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel error: Stream closed
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel error: java.io.IOException: Stream closed com.vmware.vdi.ob.tunnelservice.ca.run(SourceFile:896)
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [bx] (FB20_***_4323) Tunnel reported as disconnected
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ay] (FB20_***_4323) User USERNAME disconnected from the Secure Gateway Server — session ID: FB20_***_4323
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) lostConnection done
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel waiting for a reconnection…
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [aa] (FB20_***_4323) Conveyor 1 IOException. Remote address is /IPADDRESS:32111: An existing connection was forcibly closed by the remote host
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [bm] (FB20_***_4323) Socket channel closed
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [ca] (FB20_***_4323) Data being sent while tunnel is disconnected.
2014-10-06T18:49:34.574+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [al] (FB20_***_4323) Message: Channel 1 stopped
2014-10-06T19:49:39.533+02:00 DEBUG (0820-0A3C) <SessionHandler> [bx] (FB20_***_4323) Session FB20_***_4323 disconnected too long (threshold = Mon Oct 06 18:49:39 CEST 2014, disconnected at = Mon Oct 06 18:49:34 CEST 2014)
2014-10-06T19:49:39.533+02:00 DEBUG (0820-0A3C) <SessionHandler> [ay] (FB20_***_4323) Session has been disconnected too long — terminating: (ServerSession capID = FB20_***_4323, type = NORMAL, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID)
2014-10-06T19:49:39.536+02:00 DEBUG (0820-0A3C) <SessionHandler> [ay] (FB20_***_4323) Terminating session: (ServerSession capID = FB20_***_4323, type = NORMAL, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID)
2014-10-06T19:49:39.537+02:00 DEBUG (0820-0A3C) <SessionHandler> [cs] (FB20_***_4323) Queuing request FB208BB6_A112_498E_BA33_2B2787194323-2
2014-10-06T19:49:39.539+02:00 DEBUG (0820-0A3C) <SessionHandler> [bx] (FB20_***_4323) Terminating sesson.
2014-10-06T19:49:39.539+02:00 INFO (0820-0A3C) <SessionHandler> [ay] (FB20_***_4323) User USERNAME Secure Gateway Server session ended — session ID: FB20_***_4323
2014-10-06T19:49:39.539+02:00 DEBUG (0820-0A3C) <SessionHandler> [ay] (FB20_***_4323) Session removed: FB20_***_4323
2014-10-06T19:49:39.539+02:00 DEBUG (0820-0A3C) <SessionHandler> [bx] (FB20_***_4323) Session stop: Listeners stopped
2014-10-06T19:49:39.539+02:00 DEBUG (0820-0A3C) <SessionHandler> [bx] (FB20_***_4323) Session stop: Conveyors stopped
2014-10-06T19:49:39.542+02:00 DEBUG (0820-0A3C) <SessionHandler> [al] (FB20_***_4323) Stop server-side conveyor state.
2014-10-06T19:49:39.543+02:00 DEBUG (0820-0A3C) <SessionHandler> [ca] (FB20_***_4323) Tunnel.stop()
2014-10-06T19:49:39.544+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [ab] (FB20_***_4323) Closing selector
2014-10-06T19:49:39.544+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel waiting for reconnection has been interrupted…
2014-10-06T19:49:39.544+02:00 DEBUG (0820-0E1C) <PooledIO#1662> [ab] (FB20_***_4323) Thread stopping.
2014-10-06T19:49:39.544+02:00 INFO (0820-0DD0) <Tunnel#1662> [ay] (FB20_***_4323) User USERNAME Secure Gateway Server session ended — session ID: FB20_***_4323
2014-10-06T19:49:39.544+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [bx] (FB20_***_4323) Session.emergencyStop
2014-10-06T19:49:39.545+02:00 DEBUG (0820-0DD0) <Tunnel#1662> [ca] (FB20_***_4323) Tunnel thread finished
2014-10-06T19:49:39.545+02:00 DEBUG (0820-0A3C) <SessionHandler> [bx] (FB20_***_4323) Tunnel closed.
2014-10-07T11:36:09.176+02:00 DEBUG (0820-0B44) <Thread-35> [g] (Request2125) Tunnel (re)connection for capID = FB20_***_4323
2014-10-07T11:36:09.176+02:00 WARN (0820-0B44) <Thread-35> [g] (Request2125) Session not found: FB20_***_4323
2014-10-07T12:00:31.885+02:00 DEBUG (0820-0A20) <MsgWorker#3> [q] (50eb_***_6667) doCapStatus: capID = 50eb_***_6667, locationID = LOCATION-ID2, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, clientVersion = 9.0, lite = false, newAllowed = true
2014-10-07T12:00:31.885+02:00 DEBUG (0820-0A20) <MsgWorker#3> [q] (50eb_***_6667) Found 0 existing connected sessions for: cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int
2014-10-07T12:00:31.885+02:00 DEBUG (0820-0A20) <MsgWorker#3> [bx] (50eb_***_6667) getInstance: capID = NONE, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID2, seh = com.vmware.vdi.ice.server.ay@3740dfc9
2014-10-07T12:00:31.885+02:00 DEBUG (0820-0A20) <MsgWorker#3> [bx] (50eb_***_6667) Created new session for: capID = 3E51_***_552C, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID2
2014-10-07T12:00:32.111+02:00 INFO (0820-0B58) <Thread-40> [g] (Request2129) User USERNAME connected to the Secure Gateway Server — session ID: 3E51_***_552C
2014-10-07T12:00:32.115+02:00 DEBUG (0820-026C) <Tunnel#1804> [bx] (3E51_***_552C) Tunnel registered: session = (ServerSession capID = 3E51_***_552C, type = NORMAL, userID = USERNAME, userDN = cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int, locationID = LOCATION-ID2), connected = Tue Oct 07 12:00:32 CEST 2014
2014-10-07T12:00:32.166+02:00 DEBUG (0820-026C) <Tunnel#1804> [al] (3E51_***_552C) Broker authenticated session started (local authentication): userDN=cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int
2014-10-07T12:00:32.166+02:00 DEBUG (0820-026C) <Tunnel#1804> [al] (3E51_***_552C) Session authentication completed: userID = USERNAME
2014-10-07T12:00:41.337+02:00 DEBUG (0820-026C) <Tunnel#1804> [al] (3E51_***_552C) User USERNAME starting channel 1 connecting to target IPADDRESS:32111 session 3E51_***_552C
2014-10-07T14:20:19.630+02:00 DEBUG (0820-0A38) <MsgWorker#9> [ay] (3E51_***_552C) User USERNAME disconnected from the Secure Gateway Server — session ID: 3E51_***_552C
2014-10-07T14:20:19.646+02:00 INFO (0820-026C) <Tunnel#1804> [ay] (3E51_***_552C) User USERNAME Secure Gateway Server session ended — session ID: 3E51_***_552C
Connection Server log
2014-10-06T00:01:40.428+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] SHUTDOWN:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;
2014-10-06T00:02:37.007+02:00 INFO (0ABC-1408) <TP-Processor5> [LoginBean] User USERNAME has successfully authenticated to View Administrator
2014-10-06T00:12:23.761+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] STARTUP:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;
2014-10-06T00:13:46.769+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] SHUTDOWN:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;
2014-10-06T00:14:34.533+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] STARTUP:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;
2014-10-06T00:47:54.292+02:00 INFO (0ABC-13F4) <ContainerBackgroundProcessor[StandardEngine[Catalina]]> [LoginSessionTimeoutListener] User USERNAME has logged out of View Administrator
2014-10-06T10:50:42.965+02:00 INFO (0ABC-00E8) <TP-Processor19> [AuthorizationFilter] (SESSION:ad70_***_e26a) User DOMAINUSERNAME has successfully authenticated to VDM
2014-10-06T10:50:42.974+02:00 INFO (0ABC-00E8) <TP-Processor19> [Audit] (SESSION:ad70_***_e26a) BROKER_LOGON:USER:DOMAINUSERNAME;USERSID:USER-SID;USERDN:CN=USER-SID,CN=ForeignSecurityPrincipals,DC=vdi,DC=vmware,DC=int;
2014-10-06T10:50:48.983+02:00 WARN (0ABC-00E8) <TP-Processor19> [RadiusAuthSessionState] (SESSION:ad70_***_e26a) Received timeout (for accounting)
2014-10-06T10:50:54.988+02:00 WARN (0ABC-00E8) <TP-Processor19> [RadiusAuthSessionState] (SESSION:ad70_***_e26a) Received timeout (for accounting)
2014-10-06T10:50:54.988+02:00 WARN (0ABC-00E8) <TP-Processor19> [RadiusAuthSessionState] (SESSION:ad70_***_e26a) RADIUS start accounting failed for user USERNAME, with accounting session id2191
2014-10-06T10:51:03.630+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] PENDING:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T10:51:19.406+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] CONNECTED:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T10:51:19.407+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [DesktopTracker] User DOMAINUSERNAME connected to machine COMPUTERNAME for desktop pool1 — session allocated at 6 oktober 2014 10:51:17 CEST, connected after 0 mins 1 secs
2014-10-06T19:49:38.555+02:00 INFO (0ABC-0E48) <SwiftMQ-SessionPool-3> [Audit] BROKER_LOGOFF:USER:DOMAINUSERNAME;USERSID:USER-SID;USERDN:CN=USER-SID,CN=ForeignSecurityPrincipals,DC=vdi,DC=vmware,DC=int;
2014-10-06T19:49:38.556+02:00 INFO (0ABC-0E48) <SwiftMQ-SessionPool-3> [UserSessionTracker] User USER:DOMAINUSERNAME;USERSID:USER-SID;USERDN:CN=USER-SID,CN=ForeignSecurityPrincipals,DC=vdi,DC=vmware,DC=int; has logged out of VDM
2014-10-06T19:50:39.021+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] DISCONNECTED:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T19:50:39.021+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [DesktopTracker] User DOMAINUSERNAME disconnected from machine COMPUTERNAME for desktop pool1 — session allocated at 6 oktober 2014 10:51:17 CEST, connected for 539 mins 19 secs
2014-10-06T23:50:40.763+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] ENDED:Server:cn=SERVER-CN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T23:50:40.763+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [DesktopTracker] User DOMAINUSERNAME logged off from machine COMPUTERNAME for desktop pool1 — session allocated at 6 oktober 2014 10:51:17 CEST, connected for 779 mins 20 secs
Connection Server debug log:
2014-10-06T19:49:38.554+02:00 DEBUG (0ABC-0E48) <SwiftMQ-SessionPool-3> [UserSessionTracker] Successfully unbound UserSessionTracker (userId=USER-SID, sessionId=ad70_***_e26a)
2014-10-06T19:49:38.555+02:00 INFO (0ABC-0E48) <SwiftMQ-SessionPool-3> [Audit] BROKER_LOGOFF:USER:DOMAINUSERNAME;USERSID:USER-SID;USERDN:CN=USER-SID,CN=ForeignSecurityPrincipals,DC=vdi,DC=vmware,DC=int;
2014-10-06T19:49:38.555+02:00 DEBUG (0ABC-0E48) <SwiftMQ-SessionPool-3> [EventLogger] Info_Event:[BROKER_USERLOGGEDOUT] «User DOMAINUSERNAME has logged out»: Source=net.propero.modules.properOps.UserSessionTracker, Time=Mon Oct 06 19:49:38 CEST 2014, Severity=AUDIT_SUCCESS, Node=SECURITYSERVER.DOMAIN.COM, TotalUsers=20, UserSID=USER-SID, BrokerSessionId=ad70_***_e26a, Module=Broker, UserDisplayName=DOMAINUSERNAME, Acknowledged=true
2014-10-06T19:49:38.556+02:00 INFO (0ABC-0E48) <SwiftMQ-SessionPool-3> [UserSessionTracker] User USER:DOMAINUSERNAME;USERSID:USER-SID;USERDN:CN=USER-SID,CN=ForeignSecurityPrincipals,DC=vdi,DC=vmware,DC=int; has logged out of VDM
2014-10-06T19:49:38.556+02:00 DEBUG (0ABC-0E48) <SwiftMQ-SessionPool-3> [ManagementFilter] Invalidating session (time out = 1sec): ad707289_79ff_4627_9726_76ee37cee26a
2014-10-06T19:50:20.202+02:00 DEBUG (0ABC-13F4) <ContainerBackgroundProcessor[StandardEngine[Catalina]]> [RadiusAuthSessionState] RADIUS unbound, username: USERNAME
2014-10-06T19:50:20.202+02:00 DEBUG (0ABC-13F4) <ContainerBackgroundProcessor[StandardEngine[Catalina]]> [RadiusAuthSessionState] Session closed for user USERNAME, duration 32377 seconds
2014-10-06T19:50:39.021+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] DISCONNECTED:Server:cn=SERVERCN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T19:50:39.021+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [DesktopTracker] User DOMAINUSERNAME disconnected from machine VDZAN0148 for desktop pool1 — session allocated at 6 oktober 2014 10:51:17 CEST, connected for 539 mins 19 secs
2014-10-06T19:50:39.022+02:00 DEBUG (0ABC-09F0) <1e4a17c8-2713-47e8-b5b7-26060dd315c9> [DesktopTracker] onEvent: DISCONNECTED — UserName:USERNAME;DomainName:DOMAIN;UserDn:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;UserSid:USER-SID;GroupSids:null;BrokerUserSid:USER-SID;ConnectionId:FB20_***_4323;Protocol:PCOIP;ClientName:;ClientAddress:;ServerDn:cn=SERVERCN,ou=servers,dc=vdi,dc=vmware,dc=int;ServerPoolDn:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;ServerDnsName:COMPUTERNAME.DOMAIN.COM;DynamicIpAddress:IPADDRESS;ManagedObjectId:null;Id:1e4a17c8-2713-47e8-b5b7-26060dd315c9;State:Disconnected;SessionGuid:9485-***-586a;PreviousSessionGuid:null;LoggedInAsDomain:DOMAIN;LoggedInAsUser:USERNAME
6 hours after the error occured, the system will logoff the user (as configured)
2014-10-06T23:50:40.763+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [Audit] ENDED:Server:cn=SERVERCN,ou=servers,dc=vdi,dc=vmware,dc=int;Pool:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;DNS:COMPUTERNAME.DOMAIN.COM;IP:IPADDRESS;USER:DOMAINUSERNAME;USERDN:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;BROKERUSERSID:USER-SID;
2014-10-06T23:50:40.763+02:00 INFO (0ABC-0DD0) <DesktopControlJMS> [DesktopTracker] User DOMAINUSERNAME logged off from machine COMPUTERNAME for desktop pool1 — session allocated at 6 oktober 2014 10:51:17 CEST, connected for 779 mins 20 secs
2014-10-06T23:50:40.764+02:00 DEBUG (0ABC-0F74) <c074cfd4-7412-4b6a-b133-8d162f8c064b> [DesktopTracker] onEvent: ENDED — UserName:USERNAME;DomainName:DOMAIN;UserDn:cn=USER-SID,cn=foreignsecurityprincipals,dc=vdi,dc=vmware,dc=int;UserSid:USER-SID;GroupSids:null;BrokerUserSid:USER-SID;ConnectionId:FB20_***_4323;Protocol:PCOIP;ClientName:;ClientAddress:;ServerDn:cn=SERVERCN,ou=servers,dc=vdi,dc=vmware,dc=int;ServerPoolDn:cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int;ServerDnsName:COMPUTERNAME.DOMAIN.COM;DynamicIpAddress:IPADDRESS;ManagedObjectId:null;Id:c074cfd4-7412-4b6a-b133-8d162f8c064b;State:Disconnected;SessionGuid:9485-***-586a;PreviousSessionGuid:null;LoggedInAsDomain:DOMAIN;LoggedInAsUser:USERNAME
2014-10-06T23:50:40.766+02:00 DEBUG (0ABC-0F74) <c074cfd4-7412-4b6a-b133-8d162f8c064b> [VirtualCenterDriver] onMachineEvent: cn=SERVERCN,ou=servers,dc=vdi,dc=vmware,dc=int in pool: cn=pool1,ou=server groups,dc=vdi,dc=vmware,dc=int
Does anyone has an explanation?
We already tried to uninstall the VMware Tools and the VMware View Agent.
Yeah, that’s what I tought too, but since there’s no config changes related to this (upgrade), and connection drops before I even get to choose what desktop I want to connect to, I’m not so sure that this is a PCoIP isolated problem.
Does the client communicate over PCoIP when it authenticates and requests the list of available desktops? Isn’t that done over SSL? I tought the PCoIP tunnel was initiated when the client connected to a spesific desktop.
—
And just testet with an iPad -> Works just fine. Can logon, and connect to desktops successfully.
So, again, not certain that this is a PCoIP problem.
In the client log in Windows, I get this:
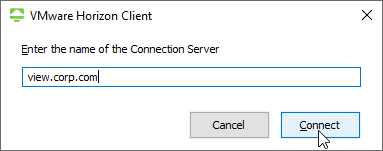
BrokerItem::Connect : [User] Enter ConnectToServer:view.XXXXX.no.
2014-07-02 10:19:08.083+01:00 DEBUG (1628) [WinCDK] SSLSettings::SSLSettings : SSL 2.0: Disabled
2014-07-02 10:19:08.083+01:00 DEBUG (1628) [WinCDK] SSLSettings::IsProtocolDisabled : SSL 3.0: Enabled
2014-07-02 10:19:08.083+01:00 DEBUG (1628) [WinCDK] SSLSettings::IsProtocolDisabled : TLS 1.0: Enabled
2014-07-02 10:19:08.083+01:00 DEBUG (1628) [WinCDK] SSLSettings::IsProtocolDisabled : TLS 1.1: Enabled
2014-07-02 10:19:08.084+01:00 DEBUG (1628) [WinCDK] SSLSettings::IsProtocolDisabled : TLS 1.2: Disabled
2014-07-02 10:19:08.084+01:00 DEBUG (1628) [WinCDK] SSLSettings::GetCipherControlString : SSL cipher control string from registry: AES:!aNULL:!eNULL:!EXPORT:@STRENGTH
2014-07-02 10:19:08.084+01:00 DEBUG (1628) [WinCDK] SSLSettings::GetSSLSettings : Cipher String from client: AES:!aNULL:!eNULL:!EXPORT:@STRENGTH
2014-07-02 10:19:08.175+01:00 INFO (1628) [WinCDK] BrokerItem::Connect : [User] Exit ConnectToServer:view.XXXXXX.no.
2014-07-02 10:19:08.175+01:00 INFO (1628) [libcdk] TUNNEL INTERRUPTED: Could not establish tunnel connection
—
Running the 2.3 client on another machines throws this message:
Error reading from tunnel HTTP Socket: An established connection was aborted by software in your host machine.
Message was edited by: Oivind Ekeberg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had an issue with my View 5.3 replica server. Users were complaining that the server was taking along time to authenticate BUT once logged in, everything seemed to work normally. On my replica server, I do not have the PCoIP gateway checked, I do have the HTTP secure tunnel checked though. When I rebooted my replica server, all users connected via that replica got a message «Error reading from tunnel HTTP socket: Connection reset by peer». I was under the impression that if the PCoIP wasn’t checked, it was just nailing up the connection then getting out of the way. I thought I confirmed this with wireshark in the past but this doesn’t seem to be the case. Can anyone elaborate on what I am missing here?
Thanks in advance.
- replica
- server
- view
-
All forum topics -
Previous Topic -
Next Topic
3 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think that would impact RDP connections. The below is taken from the help menu.
«This setting enables a secure tunnel on this Connection Server instance and its paired security servers.
When the setting is enabled, View Clients connect to desktops through the secure tunnel, which carries RDP and other data over HTTPS. PCoIP and HTML Access connections use separate secure gateways.
In general, check all secure gateway settings, or check none.»
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All of my View clients are using PCoIP so RDP wouldn’t come into play here. Maybe my setup is somehow the issue. I have 3 View servers, one security, one connection, and one replica. The replica does NOT have the box for PCoIP secure gateway checked. The other 2 servers do because they are actually using it. I did this so internal connections would go to the replica using the HTTPS gateway, rather than funneling them all through the security gateway. Since my main view connection server has it checked, is that what is causing this? The replica server traffic, last time I checked, looks to nail it up and get out of the way BUT maybe something else is going on as well?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the tunnel setting is enabled then supporting clients will always establish a tunnel connection on authentication to the CS, if this goes down and on reconnection it is told that the connection is no longer valid (which will happen after your replica comes back up) then the client will terminate. This is expected behaviour, even if you don’t have an RDP session going through it. Note that ancillary connections such as USB and MMR data will go through the tunnel even if you are using PCoIP since they have their own TCP transport. If you do not want clients to be disconnected when restarting a connection sever, neither the PSG nor the tunnel can be enabled.
Edit: just a note to say the raw «connection reset by peer» message isn’t great, this bad message may be a client bug as I’m fairly sure the older wswc client used to explicitly say that the authentication failed for a reconnection.
Open
Issue created Nov 15, 2019 by
openconnect 8.02 can’t connect to Cisco RV340 VPN SSL — Failed to read from SSL socket: Success
I try to connect to a VPN SSL on our Cisco RV340 Router.
I also downloaded the official Cisco Anyconnect Client and I am ablt to connect with the same settings I am using for the connection with openconnect.
I am using the following openconnect version:
openconnect -V
OpenConnect version v8.02-1build1
Using GnuTLS. Features present: TPMv2, PKCS#11, RSA software token, HOTP software token, TOTP software token, Yubikey OATH, System keys, DTLS, ESP
Supported protocols: anyconnect (default), nc, gpMy System is a Ubuntu 19.10
uname -a
Linux XPS-15-9570 5.3.0-19-generic #20-Ubuntu SMP Fri Oct 18 09:04:39 UTC 2019 x86_64 x86_64 x86_64 GNU/LinuxWhen I try to connect I always get the error
Failed to read from SSL socket: Success.
Error fetching HTTPS
Failed to obtain WebVPN cookieHere is the complete output. Confidential data is masked
openconnect -b -vvvvv --dump-http-traffic --user=XXXX https://myserver.com:8443
POST https://myserver.com:8443/
Attempting to connect to server myserver.com:8443
Connected to myserver.com:8443
SSL negotiation with myserver.com
Server certificate verify failed: signer not found
Certificate from VPN server "myserver.com" failed verification.
Reason: signer not found
To trust this server in future, perhaps add this to your command line:
--servercert pin-sha256:jOfIpq4BtLnaNQ9/I3hyRsZiVvutHo4rcsRCipmlm7Y=
Enter 'yes' to accept, 'no' to abort; anything else to view: yes
Connected to HTTPS on myserver.com
> POST / HTTP/1.1
> Host: myserver.com:8443
> User-Agent: Open AnyConnect VPN Agent v8.02-1build1
> Accept: */*
> Accept-Encoding: identity
> X-Transcend-Version: 1
> X-Aggregate-Auth: 1
> X-AnyConnect-Platform: linux-64
> X-Support-HTTP-Auth: true
> X-Pad: 000000000000000000000000000000000000
> Content-Type: application/x-www-form-urlencoded
> Content-Length: 220
>
> <?xml version="1.0" encoding="UTF-8"?>
> <config-auth client="vpn" type="init"><version who="vpn">v8.02-1build1</version><device-id>linux-64</device-id><group-access>https://myserver.com:8443</group-access></config-auth>
Got HTTP response: HTTP/1.1 303 See Other
Content-Type: text/html
Content-Length: 0
Location: https://myserver.com:8443/webvpn.html
Set-Cookie: webvpncontext=00000@SSLContext; path=/
Connection: Keep-Alive
HTTP body length: (0)
GET https://myserver.com:8443/
Attempting to connect to server myserver.com:8443
Connected to myserver.com:8443
SSL negotiation with myserver.com
Server certificate verify failed: signer not found
Connected to HTTPS on myserver.com
> GET / HTTP/1.1
> Host: myserver.com:8443
> User-Agent: Open AnyConnect VPN Agent v8.02-1build1
> Cookie: webvpncontext=00000@SSLContext
> Accept: */*
> Accept-Encoding: identity
> X-Transcend-Version: 1
> X-Support-HTTP-Auth: true
>
Got HTTP response: HTTP/1.1 200 OK
Cache-Control: max-age=0
Content-Type: text/html
Set-Cookie: webvpn=; expires=Thu, 01 Jan 1970 22:00:00 GMT; path=/
Set-Cookie: webvpncontext=00000@SSLContext; path=/
X-Transcend-Version: 1
Content-Length: 472
Connection: Keep-Alive
HTTP body length: (472)
< <?xml version="1.0" encoding="UTF-8"?>
< <auth id="main">
< <title>Default Customization</title>
< <message>Please enter your username and password.</message>
< <form method="post" action="webvpn.html">
< <input type="text" label="USERNAME:" name="username" value="" />
< <input type="password" label="PASSWORD:" name="password" value="" />
< <input type="submit" name="Login" value="Login" />
< <input type="reset" name="Clear" value="Clear" />
< </form>
< </auth>
Please enter your username and password.
PASSWORD:
POST https://myserver.com:8443/webvpn.html
> POST /webvpn.html HTTP/1.1
> Host: myserver.com:8443
> User-Agent: Open AnyConnect VPN Agent v8.02-1build1
> Cookie: webvpncontext=00000@SSLContext
> Accept: */*
> Accept-Encoding: identity
> X-Transcend-Version: 1
> X-Support-HTTP-Auth: true
> X-Pad: 0000000000000000000000000000000
> Content-Type: application/x-www-form-urlencoded
> Content-Length: 33
>
> username=XXXX&password=YYYY
Failed to read from SSL socket: Success.
Error fetching HTTPS response
Failed to obtain WebVPN cookieWhat can I do to use openconnect to connect with my Cisco RV340?
Thanks for your help.
Navigation
This article applies to all versions of Horizon Client for Windows, including versions 2212 and 5.5.4.
- Change Log
- Horizon Client Versions
- Windows 10 / Windows 11 Support
- Install – Horizon Client Manual
- Install – Horizon Client Silent
- Launch Horizon Client
- Shortcuts and Favorites
- Support information
- Certificate Validation
- Client Device Redirection
- Client Drive Redirection
- Serial Port Redirection
- Scanner Redirection
- Scanner Redirection Caveats
- Client Printers
- File Type Association
- Session Collaboration
- Performance Tracker
- HTML Blast
- Thin Clients
- Repurposed PCs
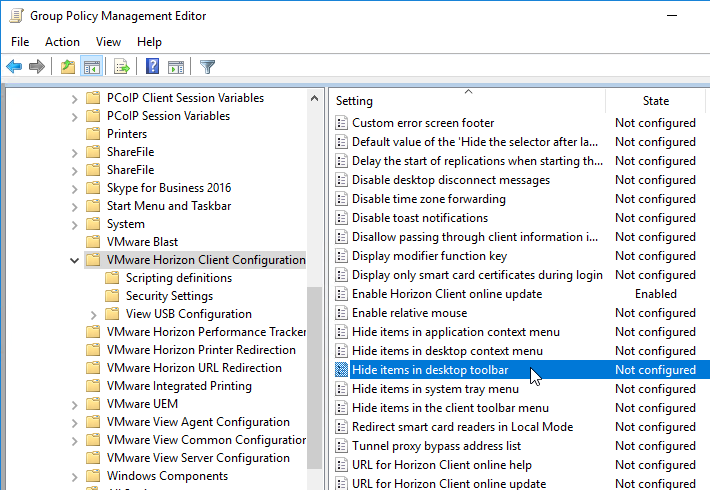
- Horizon Client GPO – Security Settings
💡 = Recently Updated
Change Log
- 2023 Jan 15 – Install Horizon Client – updated for Horizon Client 2212
- 2022 Oct 22 – Install Horizon Client – updated for Horizon Client 2209
- 2022 July 21 – Install Horizon Client – updated for Horizon Client 2206
- 2022 Apr 6 – Install Horizon Client – updated for Horizon Client 2203
- 2022 Mar 16 – Install Horizon Client – updated for Horizon Client 2111.1
- 2022 Mar 11 – Install Horizon Client – updated for Horizon Client 5.5.4
- 2021 Jan 19 – Install Horizon Client – updated for Horizon Client 5.5.3
- 2021 Dec 6 – Install Horizon Client – updated for Horizon Client 2111
- 2021 July 16 – Install Horizon Client – updated for Horizon Client 2106
Horizon Client Versions
Starting August 2020, the client versioning changed to a YYMM format. Horizon Client 2212 is the latest release.
- Horizon 8.x no longer supports Horizon Client 5.x and older.
- Features, like ThinPrint, were removed from Horizon Client 2006 and newer, so don’t use the 2xxx (8.x) clients with Horizon 7.13 and older.
- Microsoft Teams optimization features depend on Horizon Client version and Horizon Agent version. See VMware Knowledgebase Article 86475 MS Teams Optimization Feature Compatibility Matrix for Horizon 7 and Horizon 8 Recent Releases.
- Windows 21H2 and Windows 11 are supported with Horizon Client 2111.
- Horizon Client 2006 and newer no longer support Windows 7, Windows 8.1, or Windows 10 1809.
The Software Updates feature of Horizon Client 5.5 will not upgrade to Horizon Client 2006 or newer. Instead, you must manually download Horizon Client 2006 or newer and install it.
Horizon Client 5.5.3 and newer resolve security vulnerabilities.
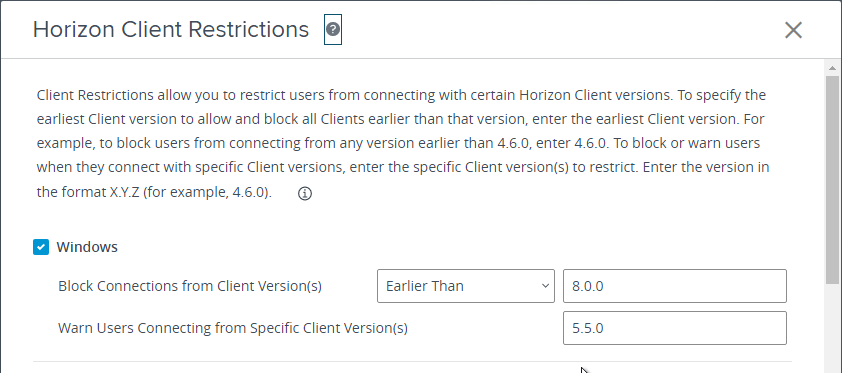
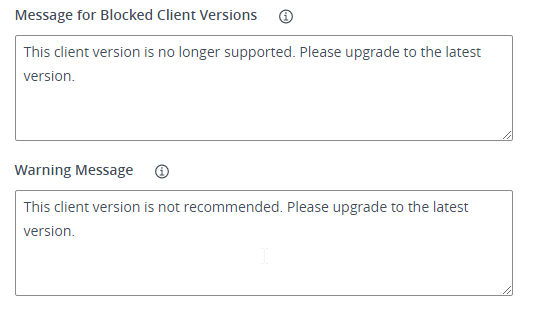
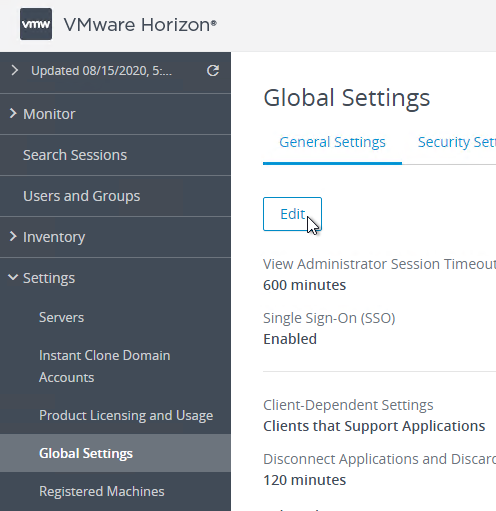
Connection Server can be configured to prevent older clients from connecting. Find it in the Global Settings node in Horizon Console.
Windows 10 / Windows 11 Support
- Windows 10 22H2 and Windows 11 22H2 are supported with Horizon Client 2209 (8.7) and newer.
- Windows 10 21H2 and Windows 11 are supported with Horizon Client 2111 (8.4) and newer.
- Windows 10 21H1 is supported with Horizon Client 2103 (8.2) and newer.
- Windows 10 20H2 is supported with Horizon Client 2012 (8.1) and newer.
- Windows 10 2004 is supported with Horizon Client 2006 (8.0) and newer
- Windows 10 1909 is supported with Horizon Client 5.3 and newer
- Windows 10 1803 is supported with Horizon Client 4.8 and newer
Manual Installation of Horizon Client
The Horizon Clients can be downloaded from http://www.vmware.com/go/viewclients.
- Logon to the client machine as an administrator. Administrative rights are required for the Horizon Client installation. You can also push the client silently as described in the next section.
- Open a browser and enter the name of your Horizon Connection Server in the address bar (e.g. https://view.corp.local). Use https://.
- Click the Install VMware Horizon Client link. If the Horizon Clients are installed on the Connection Server, the client will download immediately. Or, you’ll be taken to vmware.com to download the client.
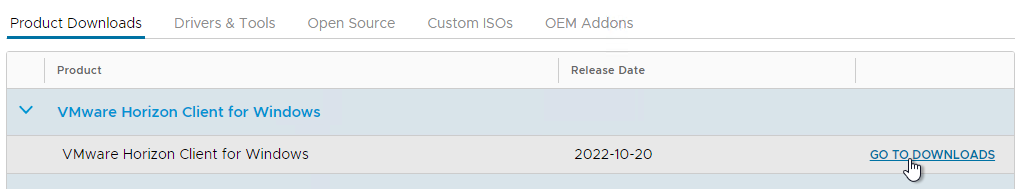
- If you are redirected to the Clients download page (https://customerconnect.vmware.com/en/downloads/info/slug/desktop_end_user_computing/vmware_horizon_clients/horizon_8), then find the VMware Horizon Client for Windows, and click Go to Downloads. Note: if you are running Horizon 7, then use the Change Version drop-down to select Horizon 7 (5.0) instead of Horizon 8.
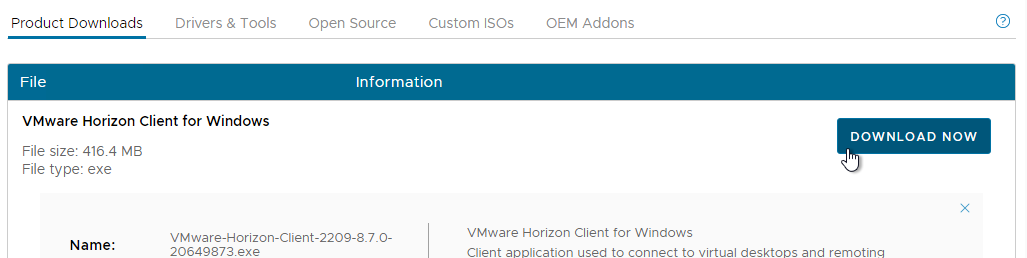
- Then click Download Now.
- On the client machine, run the downloaded VMware-Horizon-Client-2212-8.8.0.exe or VMware-Horizon-Client-5.5.4.exe.
- If you want to use the URL Content Redirection feature in Horizon 7 and newer, run the installer with the following switch:
/v URL_FILTERING_ENABLED=1. - If you want the UNC Path Redirection feature in 2209 (8.7) and newer, then you run the Client installer with the following switches:
/v ENABLE_UNC_REDIRECTION=1. You can combine the two switches.
- If you want to use the URL Content Redirection feature in Horizon 7 and newer, run the installer with the following switch:
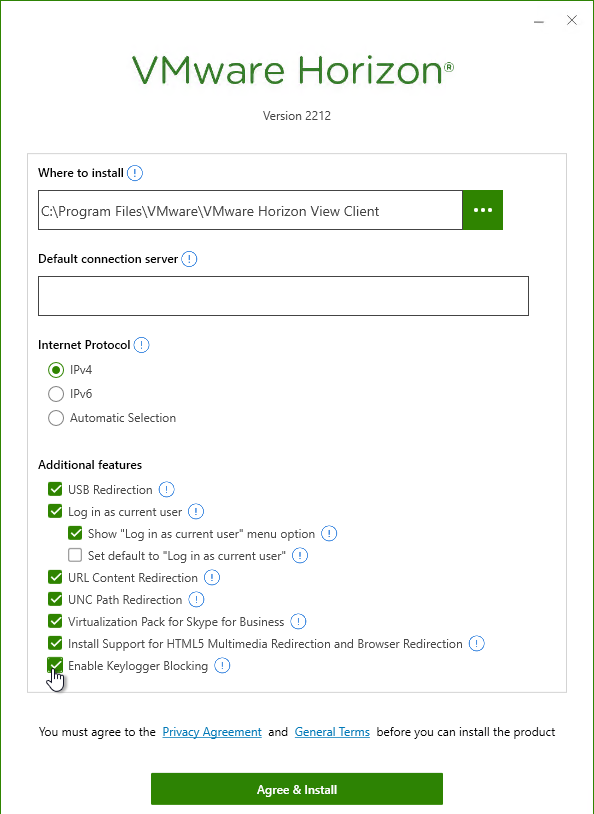
- Click Agree & Install. Or you can click Customize Installation. Horizon Client 2203 and newer has an option to Enable Keylogger Blocking, but only in Custom installation.
- If you selected Customize Installation, you can enter a Default connection server, install Teams Optimization, etc.
- Horizon Client 2203 and newer has an option to Enable Keylogger Blocking, but only in Custom installation.
- Click Agree & Install when done.
- In the Success page, click Finish.
- Click Restart Now when prompted to restart.
- Note: Horizon Client 2106 and newer have an updated user interface.
Verify URL Redirection
- To verify that URL Content Redirection is installed, verify the presence of the file C:Program FilesVMwareVMware Horizon View Clientvmware-url-protocol-launch-helper.exe.
- There’s also an IE add-on.
- URL Content Redirection is configured using group policy.
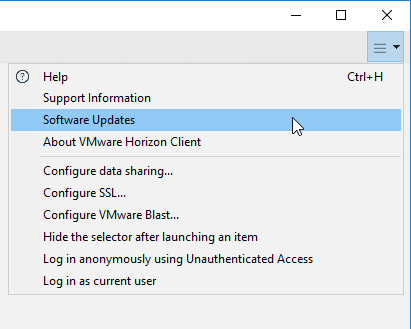
Software Updates
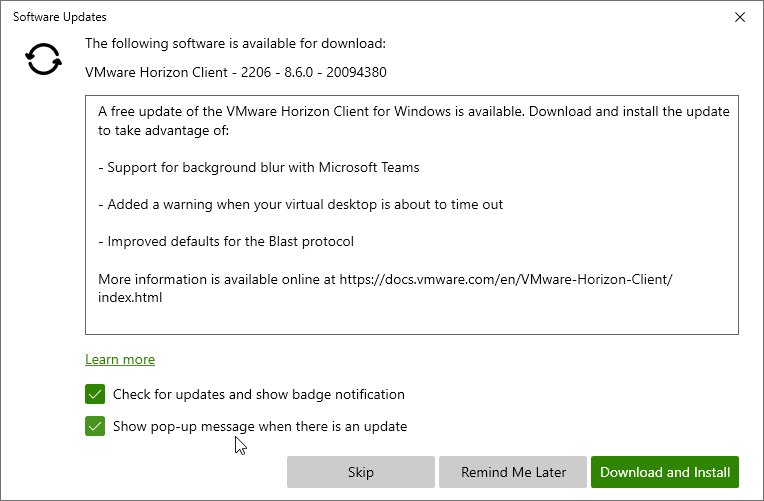
- In the Horizon Client, click the hamburger icon on the top right, and click Software Updates. It will be green if there is an update available. Note: Horizon Client 5.5 will not offer an upgrade to Horizon Client 2006 or newer.
- There is an option to Show pop-up message when there is an update.
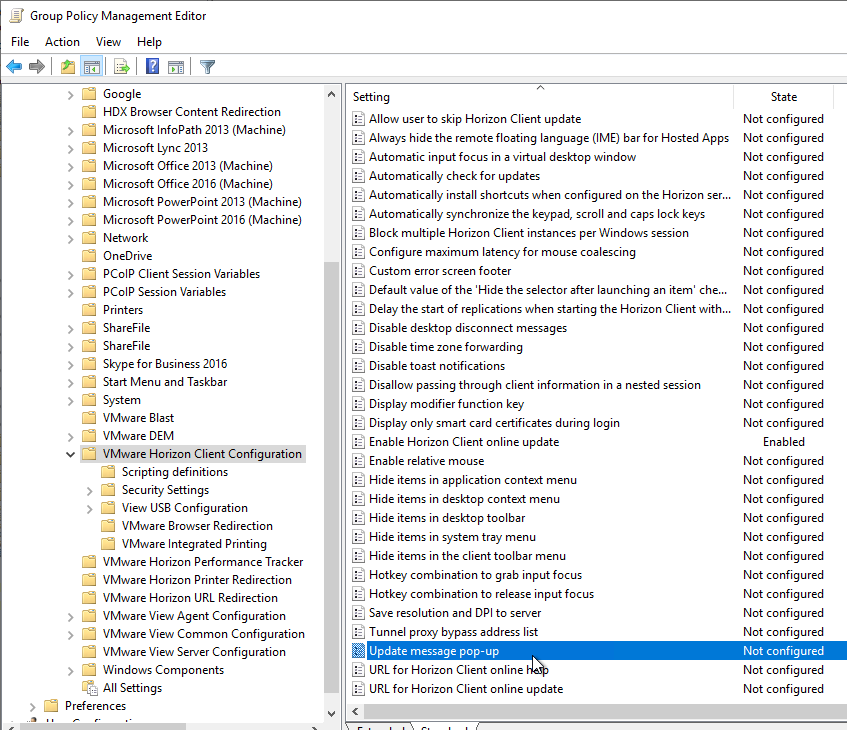
- The Horizon GPO Templates for Horizon Client have GPO settings to control the pop-up message. The settings are Update message pop-up and Allow user to skip Horizon Client update.
Install – Horizon Client Silent
Installing Horizon Client From the Command Line at VMware Docs has instructions on how to install the Horizon Client silently. Common methods for installing the client silently include: SCCM and Active Directory Group Policy Computer Startup Script.
Launch Horizon Client
To launch a View Desktop or application manually:
- From the Start Menu run VMware Horizon Client.
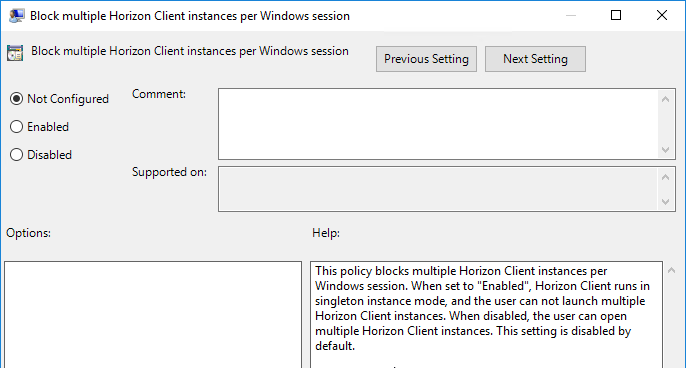
- Horizon Client 4.7 and newer has a GPO setting to prevent the Client from being launched multiple times.
- Install the Horizon GPO templates if you haven’t already.
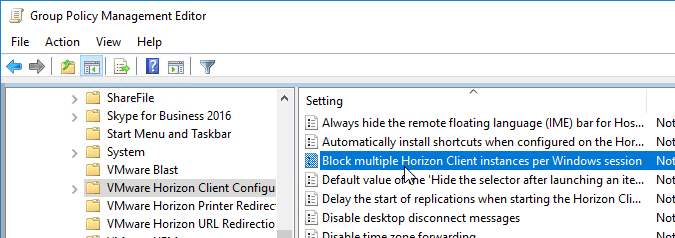
- Create or edit a GPO that is linked to an OU containing the Horizon Client machines. These are the end-user PCs, not the virtual desktops.
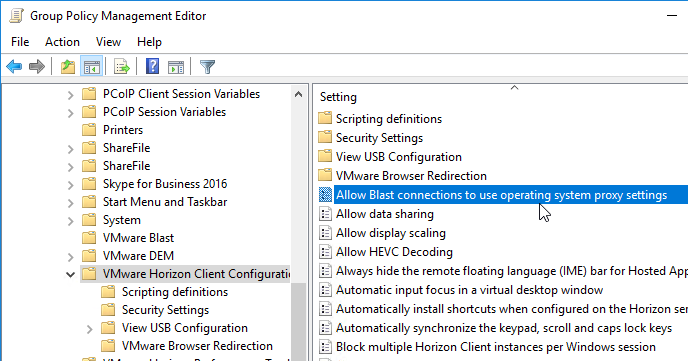
- The Block multiple Horizon Client instances per Windows session setting is at Computer Configuration | Policies | Administrative Templates | VMware Horizon Client Configuration.
- To change SSL certificate verification:
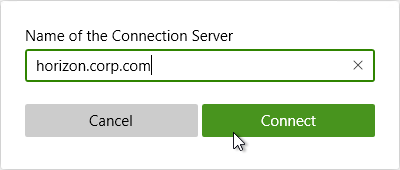
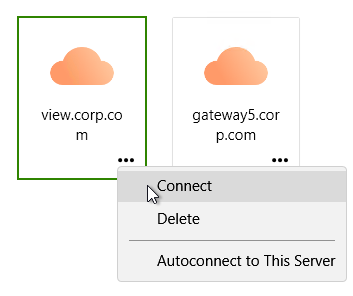
- If there is no server in the list, then use the New Server button on the top left or click Add Server on the top right.
- Enter the load balanced FQDN for the Connection Server and click Connect.
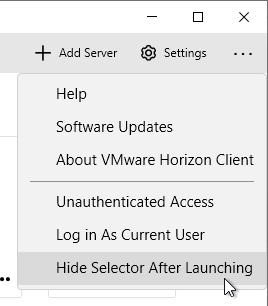
- You can click the Options menu to Hide the selector after launching an item.
- If you want to perform pass-through authentication, click the hamburger icon, and select Log in as current user. This option is only available if selected during installation, the client machine was rebooted, and is not prohibited using group policy. Also, the Connection Server must allow Log on as current user.
- Horizon 7.2 and newer have Recursive Unlock, which is enabled by default. See Using the Log In as Current User Feature Available with Windows-Based Horizon Client at VMware Docs.
- If you have apps published to an Unauthenticated User, click the hamburger icon, and select Unauthenticated access or Log in anonymously using Unauthenticated Access.
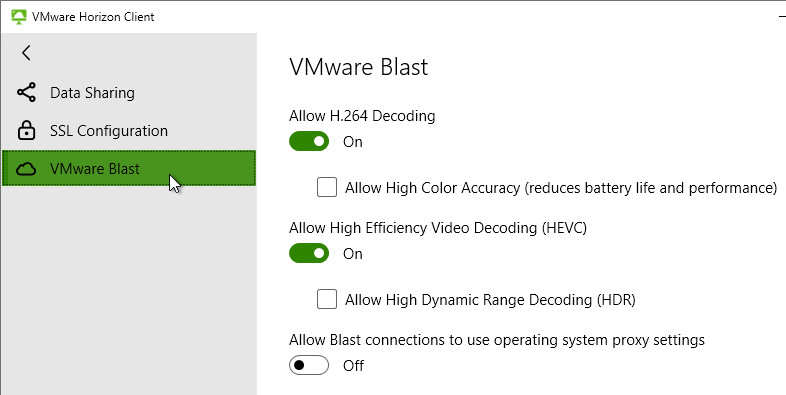
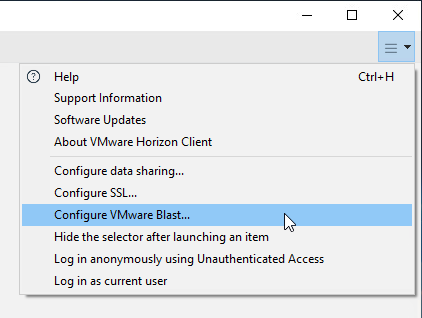
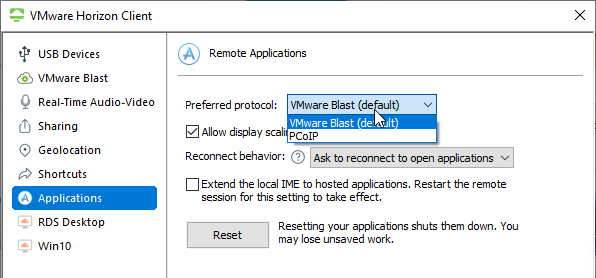
- Before connecting to the server, click Settings and then switch to the VMware Blast page. Or click the hamburger icon and then click Configure VMware Blast.
- In Horizon Client 4.8 and newer, network condition is determined automatically and no longer configurable in the client.
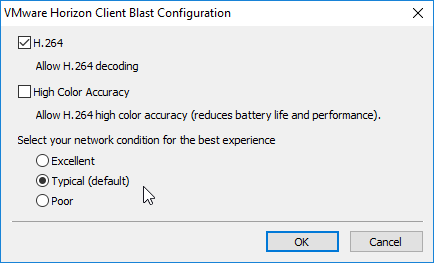
- If your Horizon Client is older than 4.8, then adjust the network condition and click OK. This affects TCP vs UDP for Blast connectivity. Excellent = TCP only. Typical = UDP if the ports are open. Poor = UDP plus packet duplication, which is best for 20% packet loss networks. More info in the Technical White Paper VMware Blast Extreme Display Protocol in Horizon 7.
- If your Horizon Client is older than 4.8, then adjust the network condition and click OK. This affects TCP vs UDP for Blast connectivity. Excellent = TCP only. Typical = UDP if the ports are open. Poor = UDP plus packet duplication, which is best for 20% packet loss networks. More info in the Technical White Paper VMware Blast Extreme Display Protocol in Horizon 7.
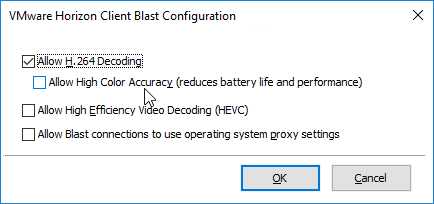
- You can optionally enable Allow High Color Accuracy.
- In Horizon Client 2106 and Horizon Agent 2106 and newer, High Efficiency Video Decoding (HEVC) is enabled by default.
- Horizon Client 5.2 and newer have an option to Allow Blast connections to use operating system proxy settings, which is deselected by default. You can configure a client-side group policy to enable proxy. Or users can manually enable it.
- Double-click the server.
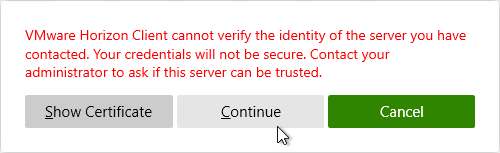
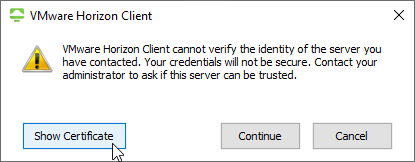
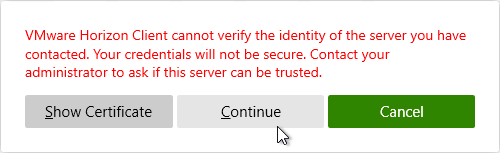
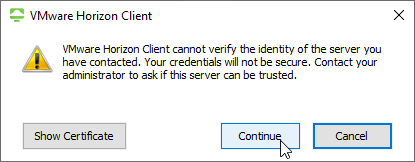
- If the certificate is not trusted, click Show Certificate, and then click Continue. To disable this prompt, see Certificate Validation below.
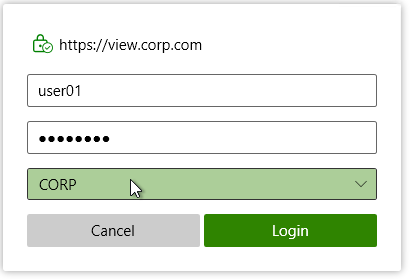
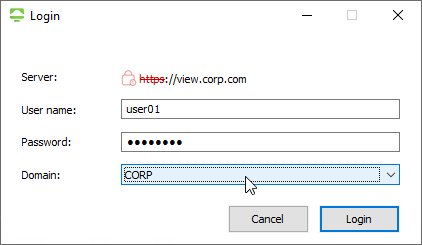
- Enter your username and password, and then click Login.
- If you see too many domains in the Domain list:
- You can filter them by running the
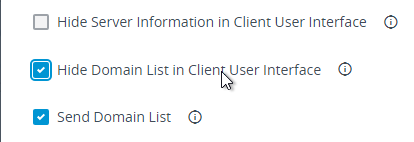
vdmadmin -Ncommand. See Configuring Domain Filters Using the ‑N Option at VMware Docs. - Horizon 7.1 and newer have an option to Hide domain list in client user interface. If you enable this in Global Settings, then users must enter UPN, or DomainUsername. This is the same place you can configure Horizon to send the Domain List to the client.
- You can filter them by running the
- If any of your published applications or desktops are configured with a Category Folder, click Yes when asked for shortcuts to appear in your Start Menu or desktop.
- Horizon Client 5.1 and newer have an interesting command line switch -installShortcutsThenQuit that connects to a Connection Server, creates the shortcuts on Start Menu and Desktop, and then quits. Here is sample syntax:
vmware-view.exe -serverURL serverurl -loginAsCurrentUser true -installShortcutsThenQuit
- Horizon Client 5.1 and newer have an interesting command line switch -installShortcutsThenQuit that connects to a Connection Server, creates the shortcuts on Start Menu and Desktop, and then quits. Here is sample syntax:
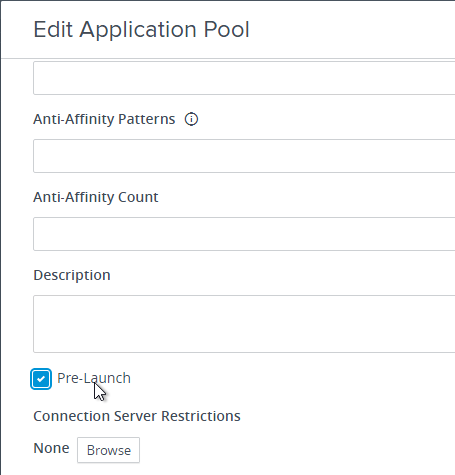
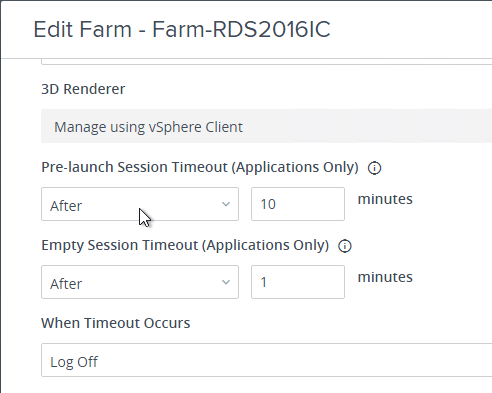
- If any of your published application icons have Pre-launch enabled, then a session will be started on one of the Horizon Agents that hosts the icon. All it does is create a session; the icon that Pre-launch was enabled on is not launched until the user double-clicks the icon. When the user launches any icon published from the Horizon Agent, it will launch quickly.
- After the user closes the Horizon Client, the Pre-launch session remains disconnected for the duration specified in the RDS Farm.
- After the user closes the Horizon Client, the Pre-launch session remains disconnected for the duration specified in the RDS Farm.
- If you have a bunch of icons, click one of the icons and then start typing in the name of the icon and it will highlight.
- If the pool settings allow it, you can right-click an icon and then select a protocol. VMware Blast is the recommended protocol.
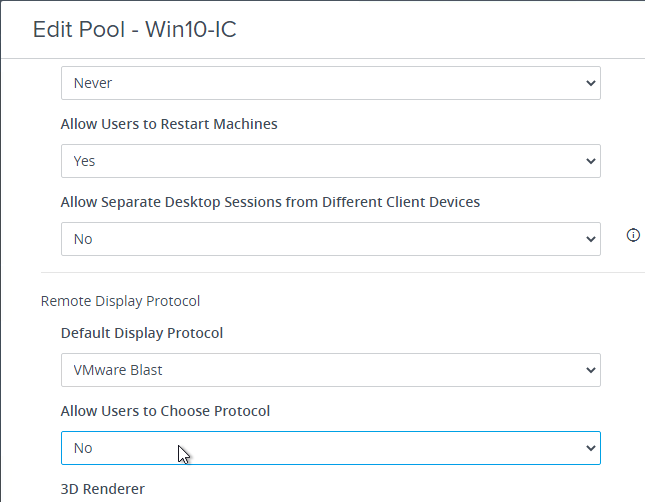
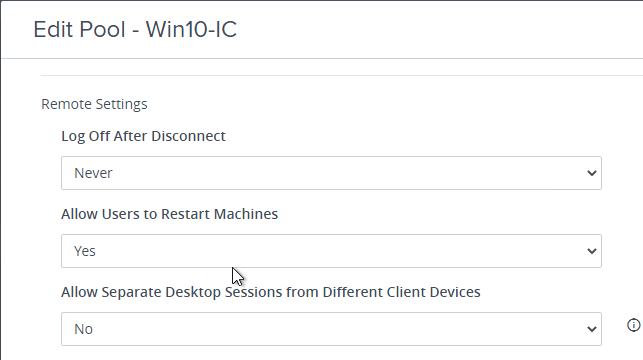
- When editing a pool, you can force users to use a particular protocol by setting Allow Users to Choose Protocol = No.
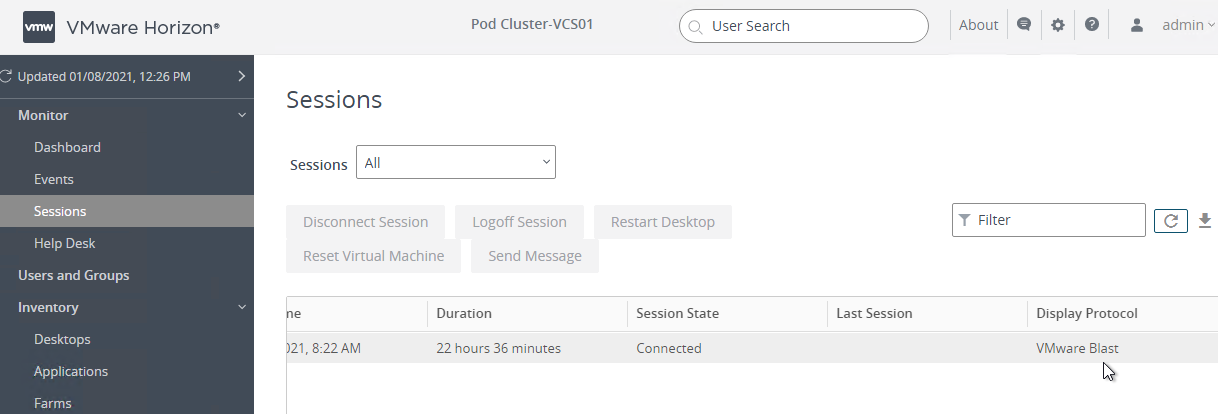
- In Horizon Console, at Monitor > Sessions, if you scroll to the right, you can see which Protocol the clients are using.
- When editing a pool, you can force users to use a particular protocol by setting Allow Users to Choose Protocol = No.
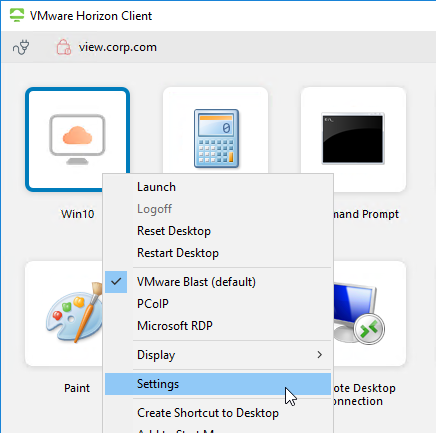
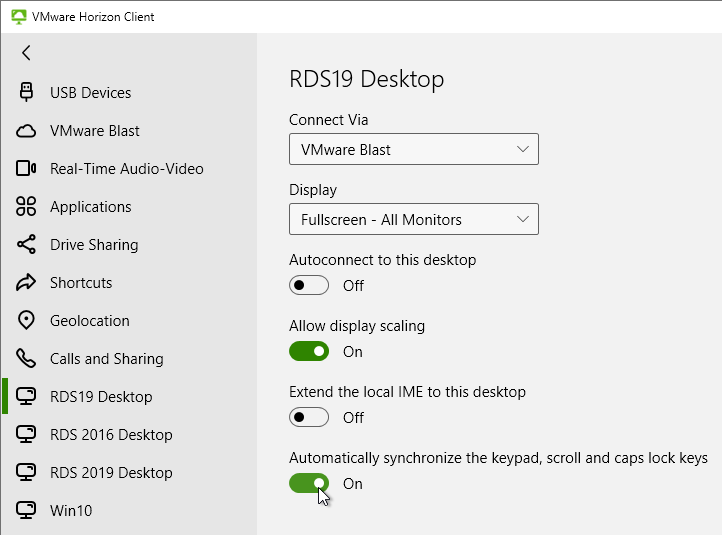
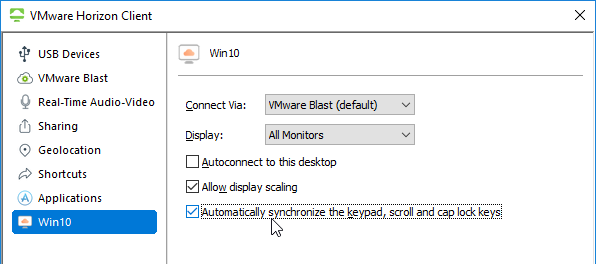
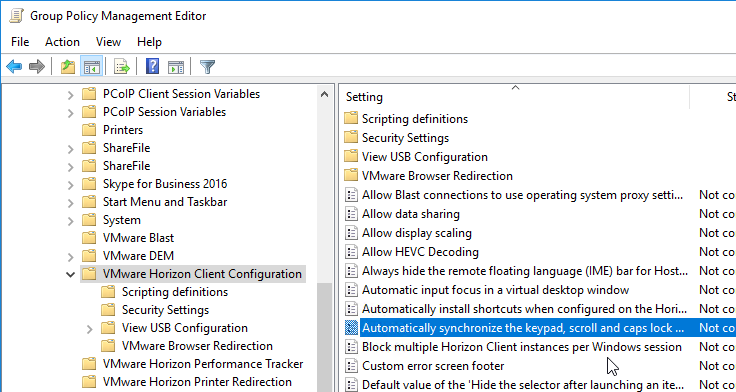
- You can synchronize num lock and cap lock status.
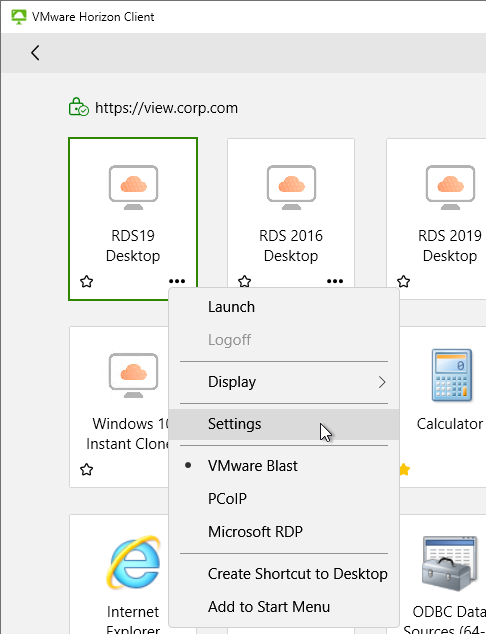
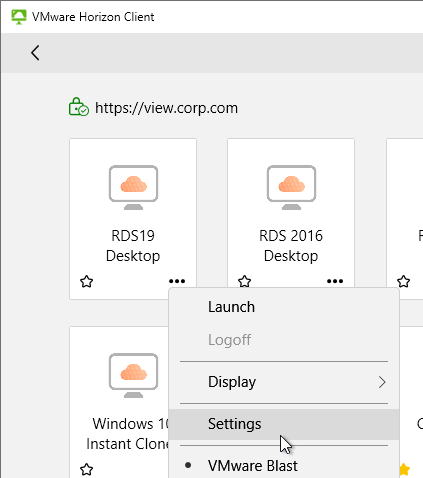
- Right-click a desktop icon and click Settings.
- The left side of the screen shows all published desktops. On the right, enable the option to Automatically synchronize the keypad, scroll, and cap lock keys.
- You can also automatically enable this setting by configuring a client-side group policy setting.
- Right-click a desktop icon and click Settings.
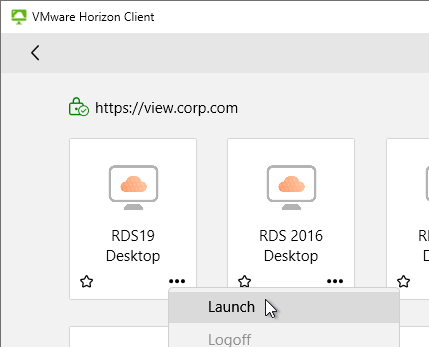
- Either double-click an icon, or right-click an icon, and click Launch.
- When connecting, you might be prompted to access your local files.
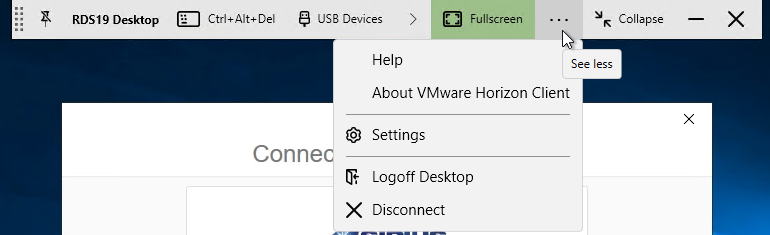
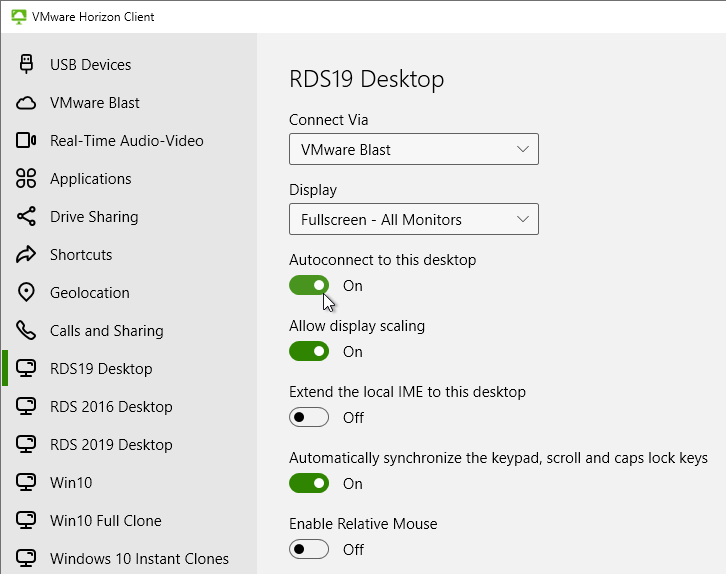
- If you are connected to a remote desktop, you can use the menu at the top of the screen, click the three dots, and then click Settings.. An interesting option is Autoconnect to this Desktop. This setting is stored on the Horizon Connection Server in LDAP and there doesn’t appear to be any way to automate enabling it.
- In Horizon Client 4.4 and newer, administrators can enable a Desktop Pool Setting that allows users to Restart the remote desktop gracefully.
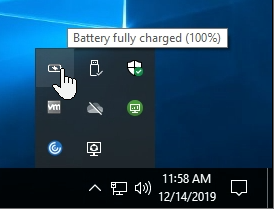
- Horizon can show the client’s battery status in the remote desktop. The user will have to click the up arrow in the system tray to see the battery icon. The battery icon is shown in both single-user Virtual Desktops and multi-user RDS Desktops.
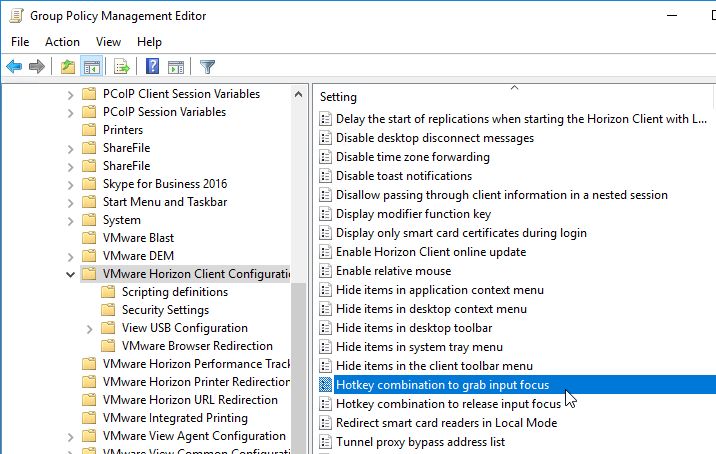
- There are client-side group policy settings to define a hotkey combination for grabbing and releasing input focus.
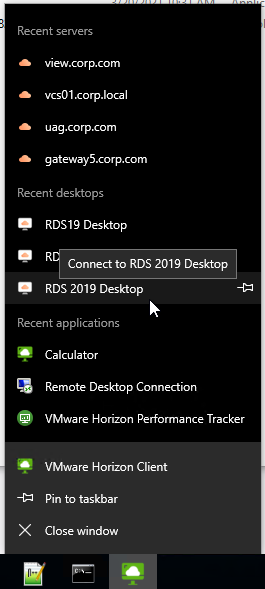
- The Horizon Client also has a taskbar jump list showing recently launched applications and desktops.
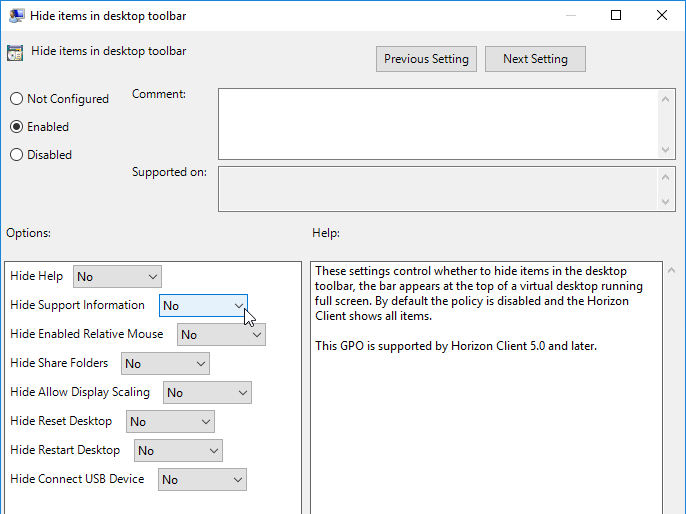
- Some of the menu items in Horizon Client can be hidden by configuring Group Policy using the Horizon GPO Templates.
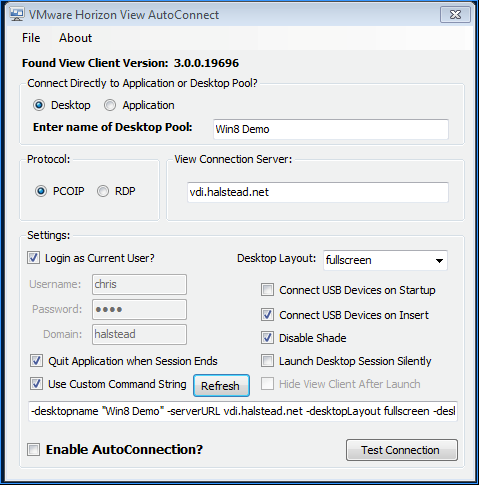
VMware Fling View Auto-Connection Utility: The View Auto-Connection Utility allows you to connect the VMware View Client automatically into a View desktop or an application pool when the system starts up.
Shortcuts and Favorites
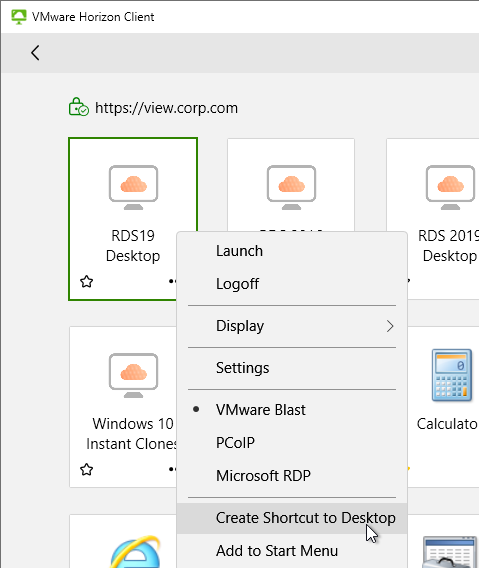
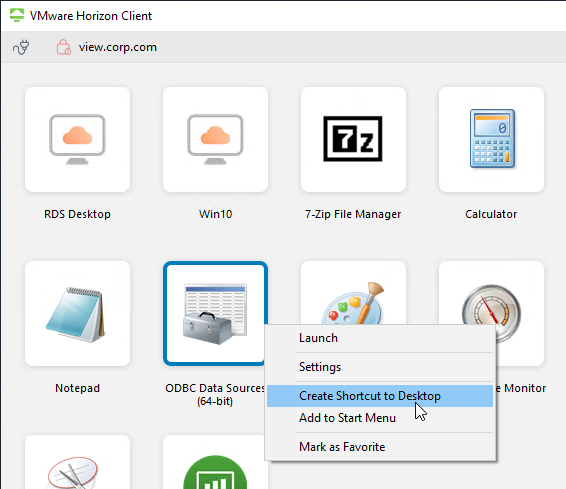
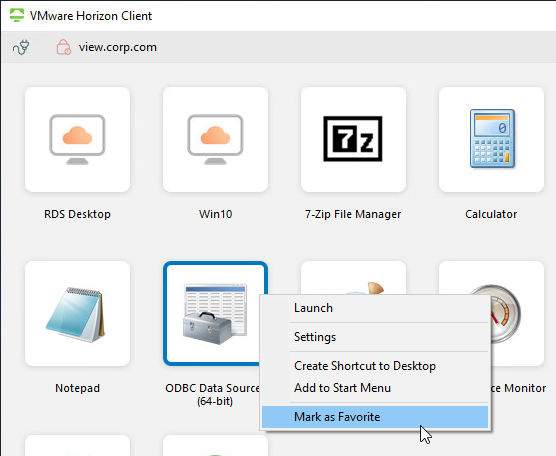
In the Horizon Client, once you are connected to a server, you can right-click an icon and click Create Shortcut to Desktop or Add to Start Menu.
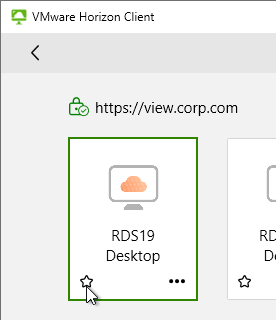
In the Horizon Client, each desktop/app icon has a star icon you can click, or right-click an icon and Mark as Favorite. Favorites are stored in the LDAP database on the Horizon Connection Server.
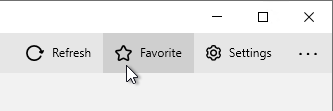
- On the top right of the Horizon Client, you can switch to the Favorite view so that only icons selected as Favorites are displayed.
- Or switch back to the All View by deselecting the Favorite button.
Support information
- In Horizon Client 2106 and newer, in the menu is About VMware Horizon Client.
- Or on the Question Mark menu is Support Information.
- Or on the Question Mark menu is Support Information.
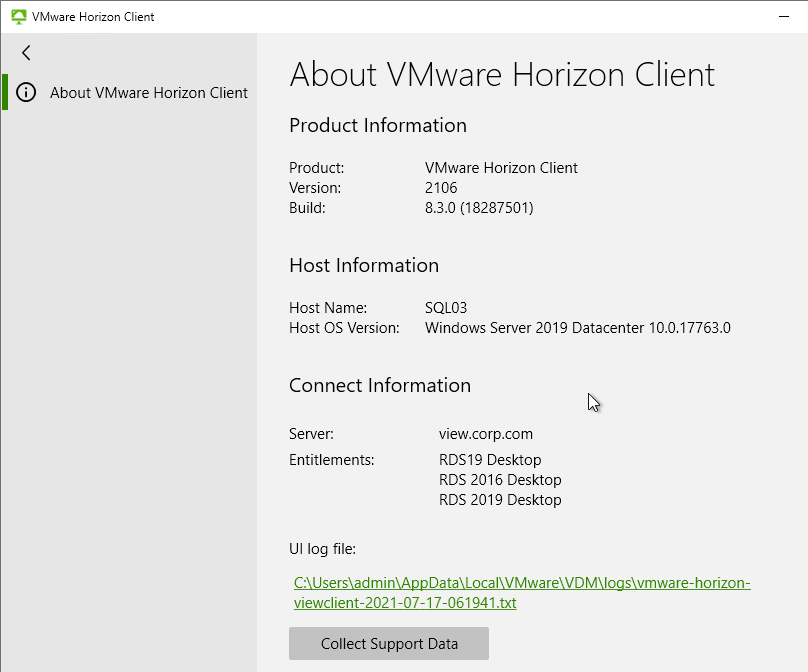
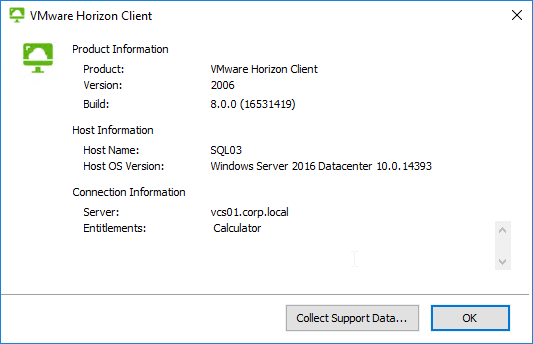
- Users can click this to find the client name, client operating system, Horizon Client version, the Horizon Connection Server name, and entitled desktops.
Certificate Validation
When you connect to a Horizon Connection Server, and if the certificate is not trusted or valid, then the user is prompted to accept the certificate. You can disable this prompt for any client machine that can be controlled using group policy.
- Copy the Horizon .admx files to PolicyDefinitions if you haven’t already.
- Create a GPO that is linked to an OU containing the Horizon Client machines. These are the end-user PCs, not the virtual desktops.
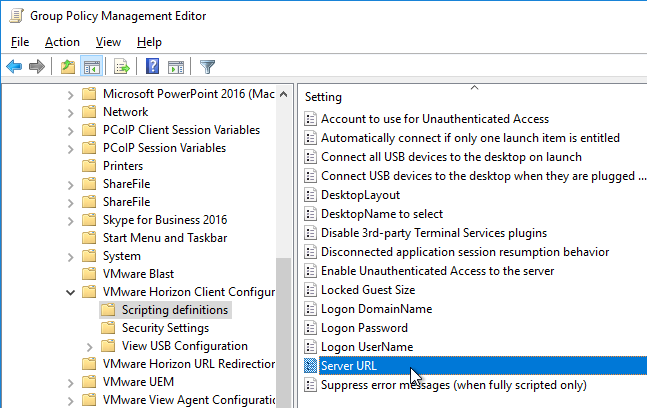
- Edit the GPO.
- Go to Computer Configuration | Policies | Administrative Templates | VMware Horizon Client Configuration | Scripting Definitions.
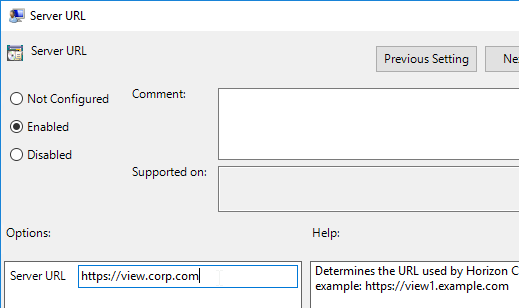
- On the right, double-click Server URL.
- Set the URL to your Horizon View URL, and click OK.
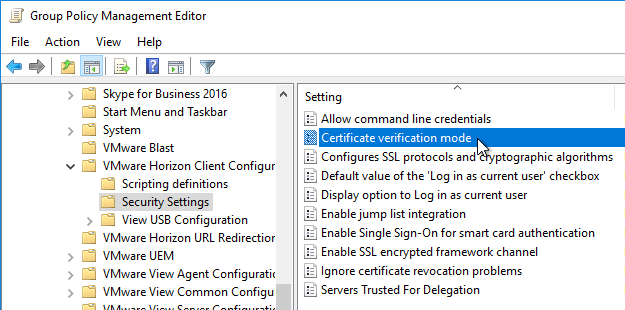
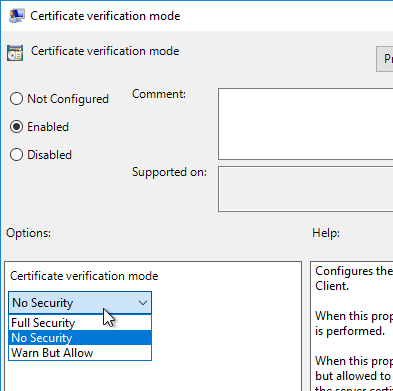
- On the left, click Security Settings. On the right, open the setting Certificate verification mode.
- Enable the setting and make your choice. No Security will disable the certificate prompt. Then click OK.
Device Redirection
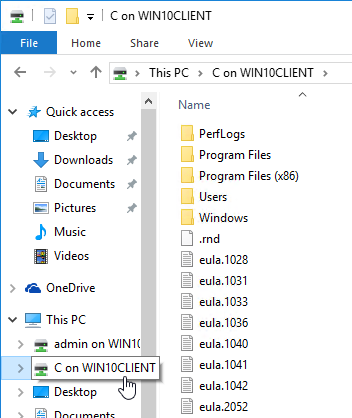
Client Drive Redirection
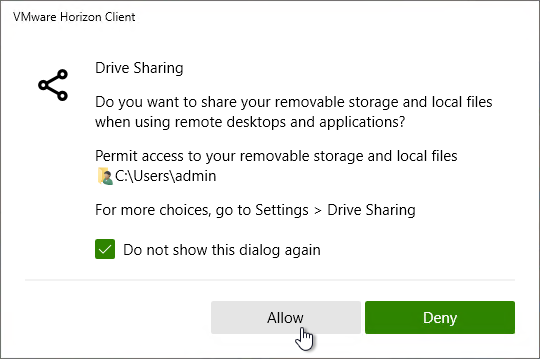
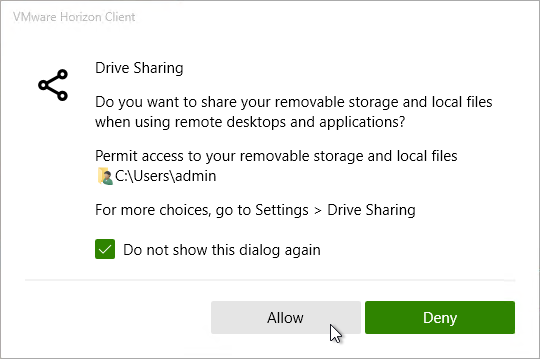
- When you connect to a Horizon Agent that has Client Drive Redirection enabled, you are prompted to allow file redirection.
- By default, only the user’s local profile is redirected.
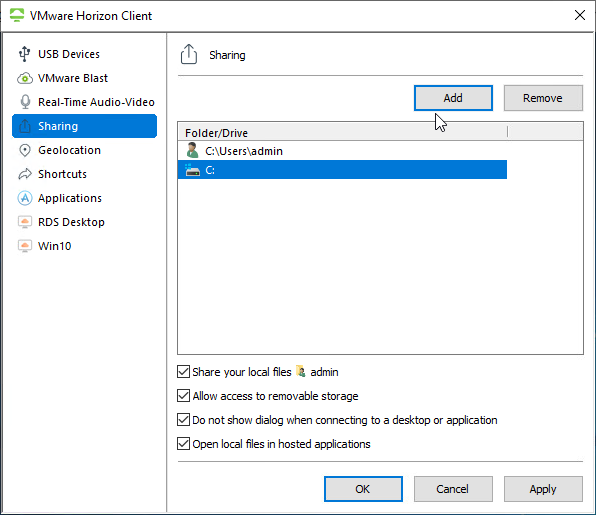
- You can redirect more folders or drives by opening Settings, or click the Options menu, and click Share Folders.
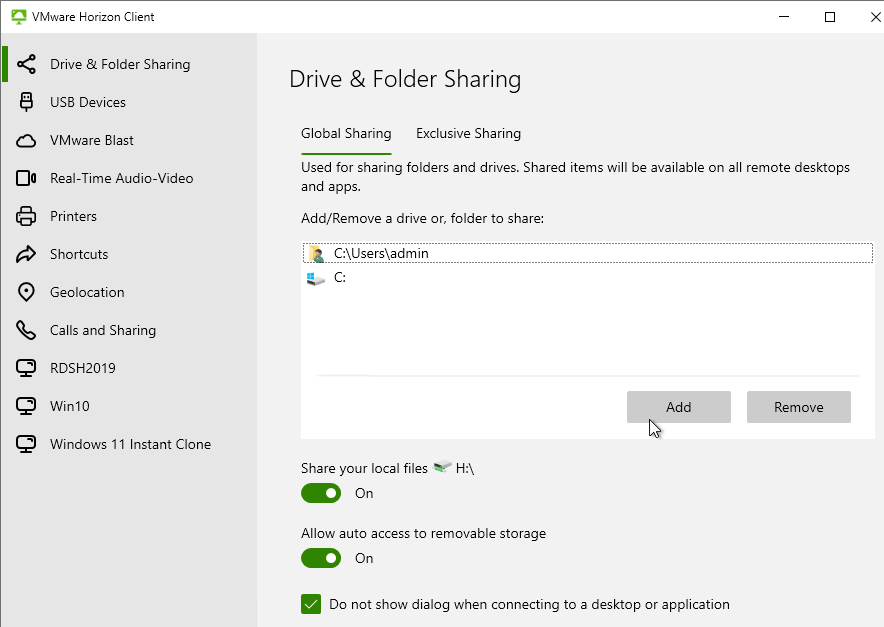
- In the Drive & Folder Sharing tab (or Sharing tab), on the Global Sharing sub-tab, add drives or folders.
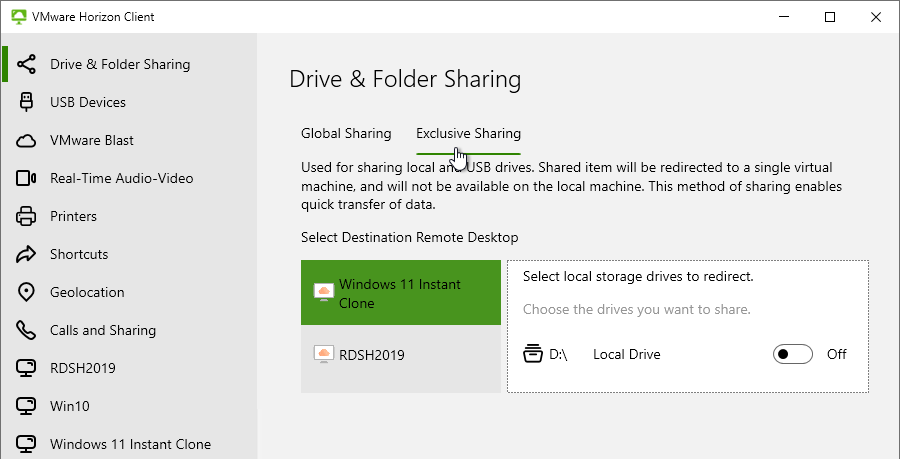
- Horizon Client 2206 and newer with Horizon Agent 2206 and newer have an Exclusive Sharing tab that lets you share a client drive exclusively with the remote desktop for faster file transfer performance. The Storage Drive Redirection feature is installed by default on Horizon Agent 2206 and newer.
- Horizon Client 2206 and newer with Horizon Agent 2206 and newer have an Exclusive Sharing tab that lets you share a client drive exclusively with the remote desktop for faster file transfer performance. The Storage Drive Redirection feature is installed by default on Horizon Agent 2206 and newer.
- The folders or drives you added are now visible within Explorer in the Horizon Desktop.
- Client Drive Redirection also works in published applications.
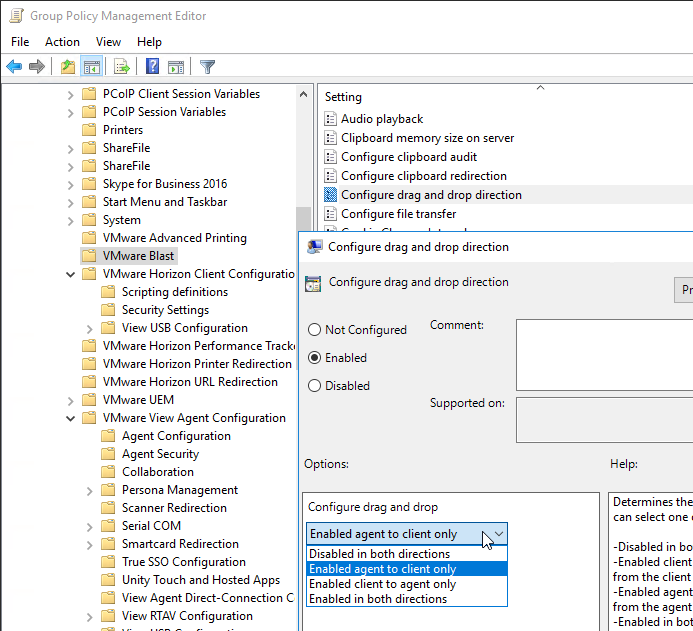
- Horizon Agent 7.7 and newer with Horizon Client 4.10 and newer let you drag files from the local machine into the remote machine. This is drag only. You can’t copy/paste. If you drag the file onto a remote application, then then application opens the file.
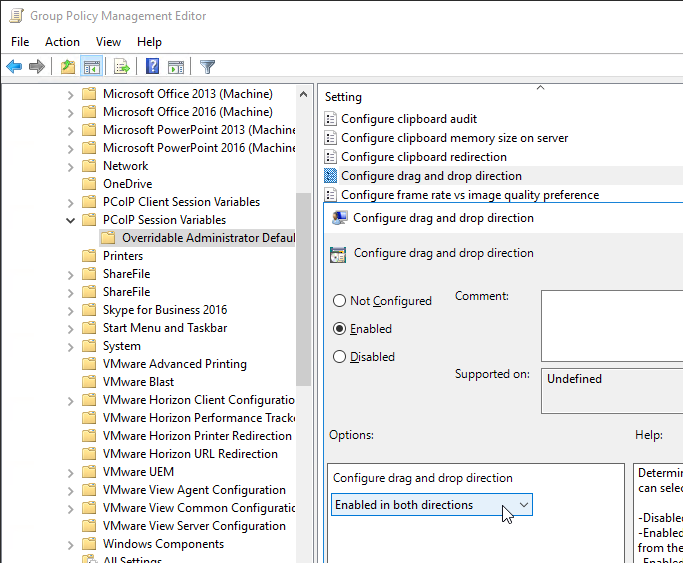
- This feature can be disabled and/or controlled in a GPO that applies to the Horizon Agent. Make sure the Horizon 7.7 or newer GPO templates are installed. In the Computer half of the GPO, go to Administrative Templates > VMware Blast and edit the setting Configure drag and drop direction.
- The Configure drag and drop direction setting is also configurable for PCoIP under the Computer-half node named PCoIP Session Variables > Overridable Administrative Defaults.
- This feature can be disabled and/or controlled in a GPO that applies to the Horizon Agent. Make sure the Horizon 7.7 or newer GPO templates are installed. In the Computer half of the GPO, go to Administrative Templates > VMware Blast and edit the setting Configure drag and drop direction.
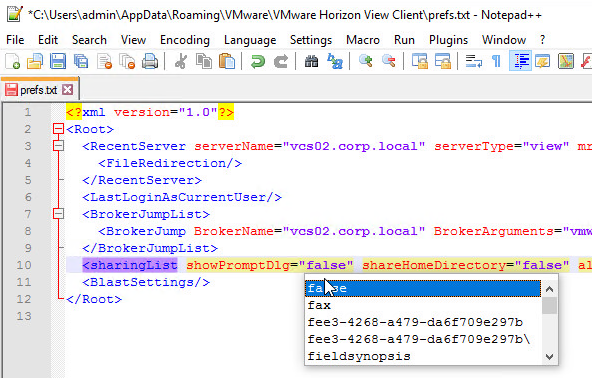
- The client drive redirection prompt configuration is stored in %appdata%VMwareVMware Horizon View Clientprefs.txt. You can edit this file to disable the prompt. See Rob Beekmans Customizing the VMware Horizon Client sharing pop-up for more info.
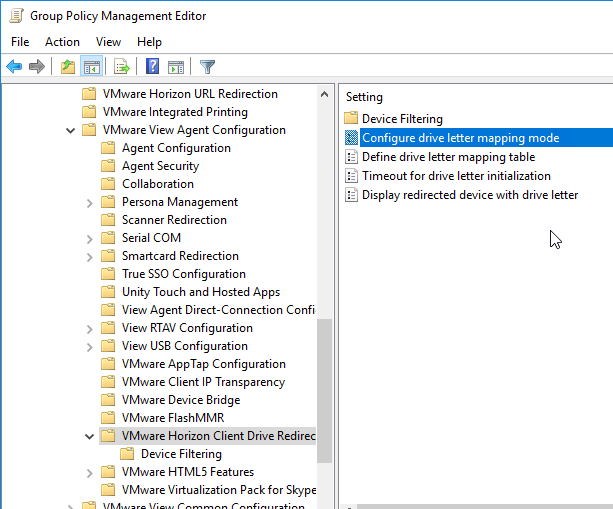
- Horizon has some GPO settings for Client Drive Redirection that let you control drive letters for client drives in the remote session. Install the Horizon GPO Templates if you haven’t already. Edit a GPO that applies to the Horizon Agents. Then find the settings under VMware View Agent Configuration > VMware Horizon Client Drive Redirection.
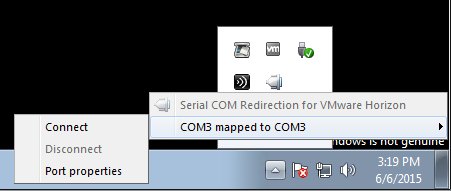
Serial Port Redirection
- If you connect to a Horizon Agent that has Serial Port Redirection enabled, then a new icon will appear in the system tray.
- Right-click the icon to map the remote COM port to the local COM port.
Scanner Redirection
From VMware Blogs Scanner Redirection in Horizon with View: we have added scanner redirection to Horizon with View for use with both VDI desktops and Remote Desktop Session Host (RDSH) applications and desktops. The new scanner redirection functionality in View works by capturing the entire image at the client with the scanning device, compressing the image, and sending that compressed image to the guest in the data center, where the image is presented by a “virtual scanner device” to the application that requested the image capture. The scanner redirection functionality supports both TWAIN and WIA scanning modes and allows images to be captured from both scanners and other imaging devices (such as webcams).
The scanner redirection functionality requires the Horizon Agent version 6.0.2 or later, and the Windows Horizon Client 3.2 or later.
When you install the Horizon Agent component, be sure to select the scanner redirection feature if you want to use it; it is disabled by default. If you are installing the feature onto a server-based OS (Windows Server 2008 R2 or Windows Server 2012 R2) for either VDI desktops or RDSH desktops or applications, then be sure that the Desktop Experience feature (a Microsoft operating system feature) is installed on the server OS first. (This is a prerequisite for installing scanners in a server-based OS.)
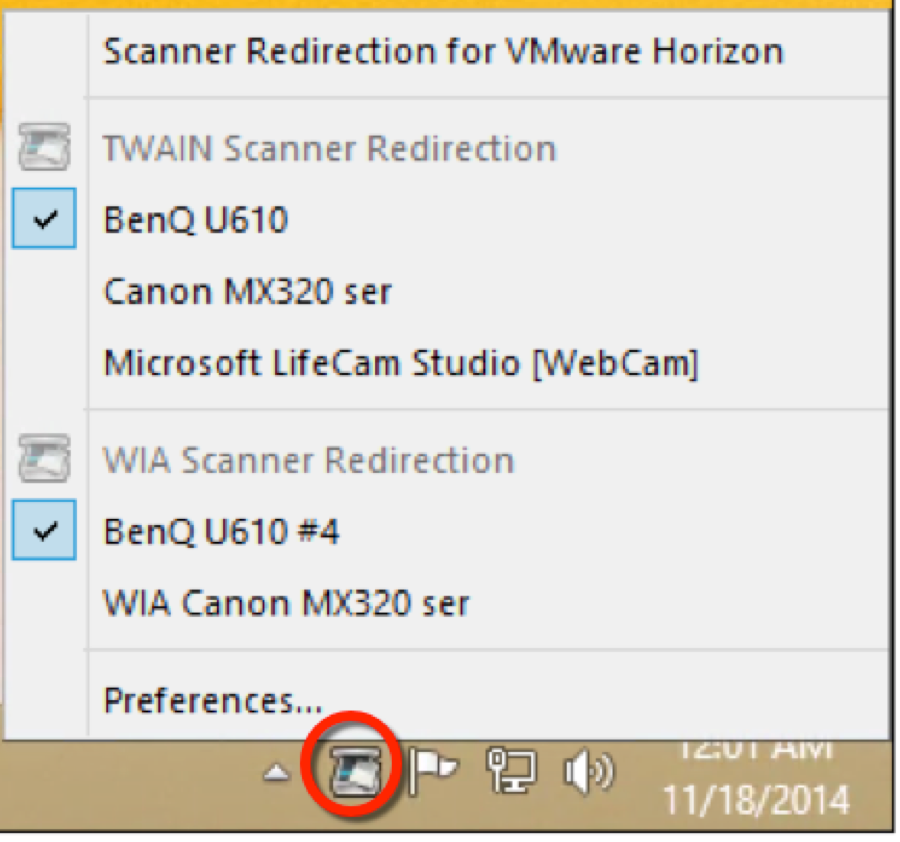
After a user makes a connection from a compatible Windows Horizon Client to the new Horizon Agent, a new tool-tray application icon appears. The user clicks the icon to reveal the compatible image acquisition devices available for scanning.
The default mode of operation is, however, that “it should just work,” and the seamless hosted application should be able to acquire an image without needing manual intervention. The user may need to adjust the preferences if more than one imaging device is connected to the client machine, and the user wants to select a specific scanner, or if the user wants to adjust the scan resolution, and so on.
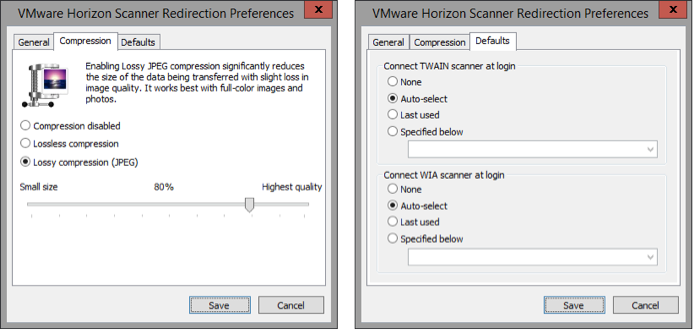
Scanner Redirection Preferences, available by clicking Preferences from the tool-tray icon, allows further configuration of the scanning process, for example, adjusting the default compression applied to the scanning. This can greatly reduce the bandwidth needed to transmit the image (the compression is applied on the client side before the image is transmitted to the guest), but, of course, the more an image is compressed, the lower the image quality. In addition, in the Scanner Redirection Preferences, options are available to adjust the default image capture device (for example, automatic mode, last-used, or an absolute specified device).
These preferences can also be adjusted by way of Group Policy options in the guest OS. A new GPO file (available in the Horizon with View GPO Bundle) allows this configuration. See Configuring Scanner Redirection in Setting Up Desktop and Application Pools in View for more information
Scanner Redirection Caveats
From VMware Communities:
- Scanner redirection does not create a device on your virtual desktop that matches the name of the actual scanner. It creates a generic scanner in Device Manager called VMWare Virtual WIA Scanner (or VMWare Virtual TWAIN Scanner I am assuming). For us this stinks because the image capture software our client uses (Vertex by Jack Henry), has a prepopulated list of scanners you can select. So if we plug in a Canon-CR50 and select Canon CR50/80 in the application, it does not recognize that this scanner is attached to the virtual desktop.
- There is a tick box option in the scanner preferences dialog box titled “Use vendor defined names for TWAIN scanners”. This should solve the issue you mention, and we added it specifically to cover the problematic use case you mention.
- This only applies to TWAIN scans, WIA can’t use the vendor name.
- You must install a TWAIN or WIA driver on your thin client. If you can’t find a TWAIN or WIA driver, you are out of luck. For teller check image scanners, we have found no TWAIN or WIA drivers for the TellerScan TS-230, TS-240, or the Canon CR-55. We have found a TWAIN driver for the Canon CR-50 (from the Canon Europe site no less), but issue #1 above means we are out of luck.
Client Printers
Horizon 7.7 and newer with Horizon Client 4.10 and newer have a new VMware Integrated Printing (aka VMware Advanced Printing) feature that replaces the older ThinPrint technology. ThinPrint is no longer available in Horizon Agent 2006 and newer.
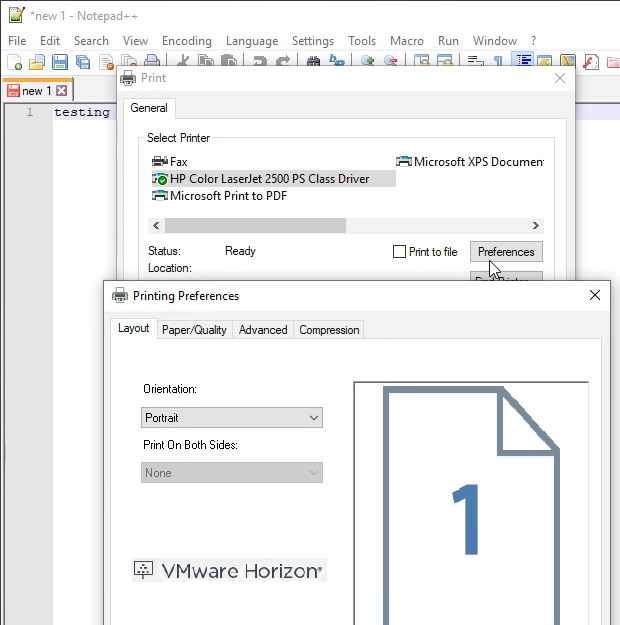
When printing from an application, if you highlight a printer and click Preferences, the VMware Horizon icon on the Layout tab shows you that this printer is using VMware Integrated Printing.
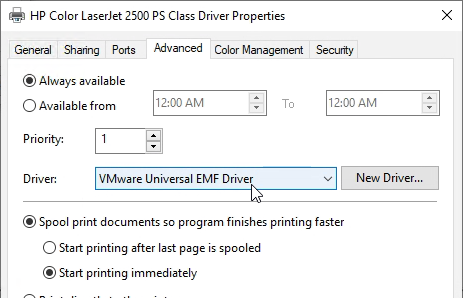
If you open the client printer Properties as an administrator, on the Advanced tab, you will see the VMware Universal EMF Driver.
If older ThinPrint:
File Type Association
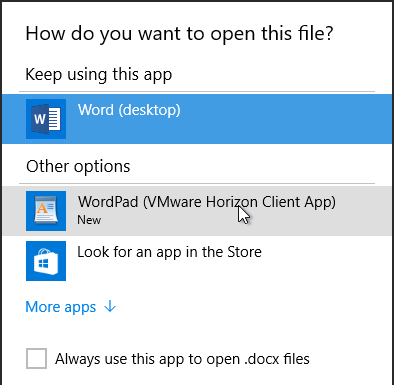
Some published applications might have file types associated with them. When you double-click a file with the configured extension, you might be prompted to open the file using the remote application.
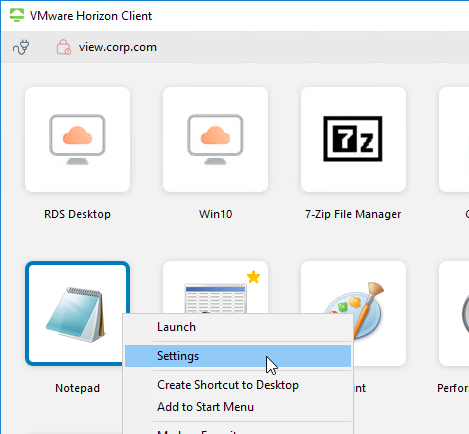
In Horizon Client, if you right-click an icon and click Settings:
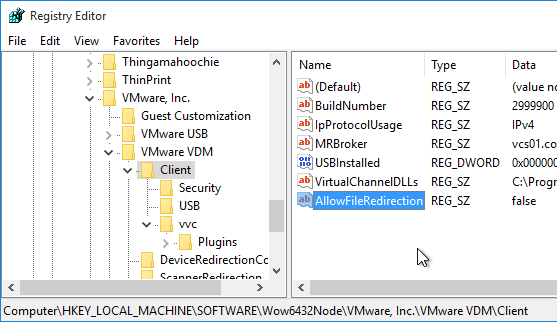
It’s also configurable in the client-side registry at HKEY_LOCAL_MACHINESOFTWAREWow6432NodeVMware, Inc.VMware VDMClient by creating a String value at named AllowFileRedirection and setting it to false. See VMware Communities for more information.
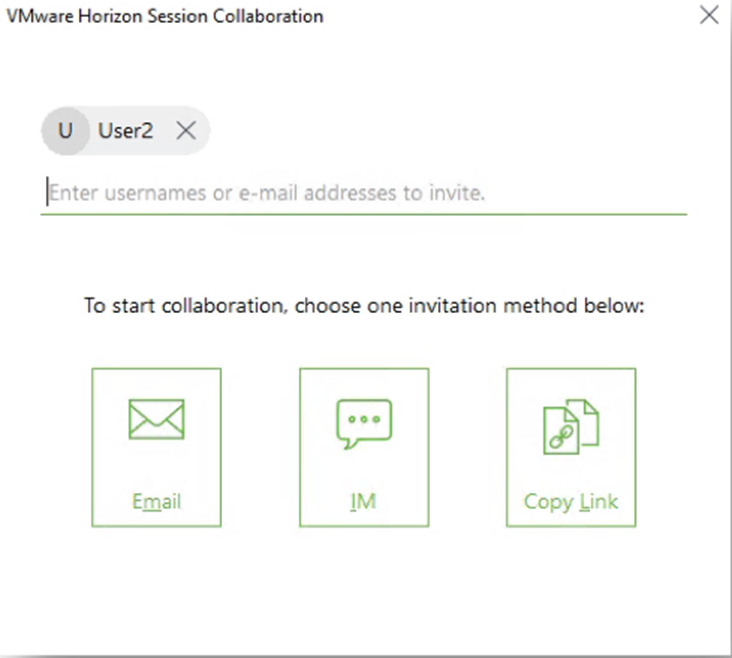
Session Collaboration
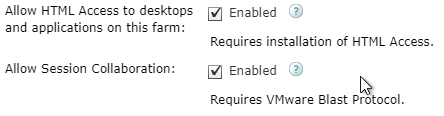
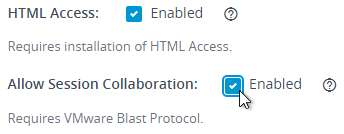
Horizon 7.4 and newer have an Allow Session Collaboration checkbox in Pool Settings and RDS Farm Settings.
This setting enables a VMware Horizon Collaboration icon in the system tray of the remote desktop, which lets you invite users to collaborate.
The invite is a URL that you can run (or click) on the collaborator’s machine that has Horizon Client 4.7 or newer installed.
To give control to the collaborator, double-click the green icon to open the Session Collaboration window. Or open the icon in the system tray.
Performance Tracker
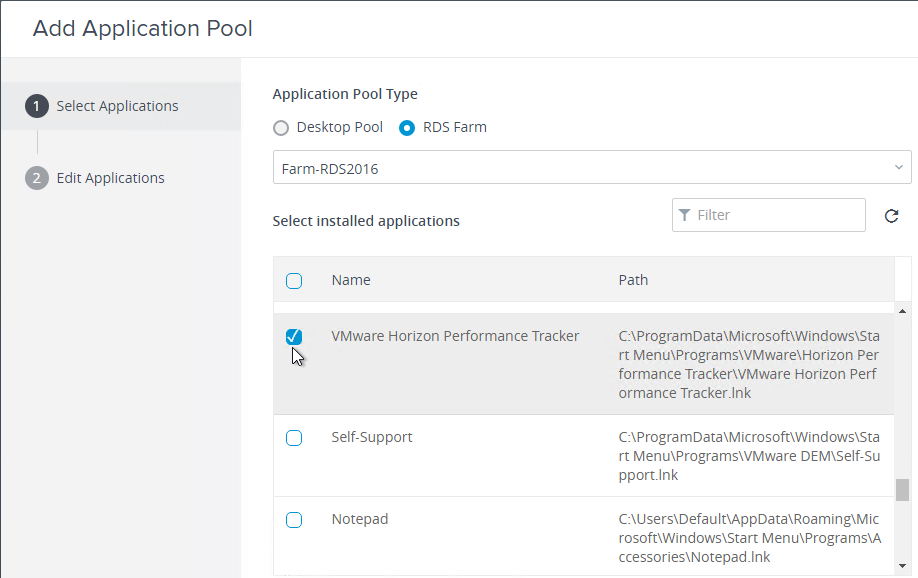
Horizon Agent 7.5 and newer have an optional component called Performance Tracker.
When installing Horizon Agent, the last option is Horizon Performance Tracker. It is deselected by default.
After it’s installed in an RDS farm, you can publish the Performance Tracker as an Application Pool
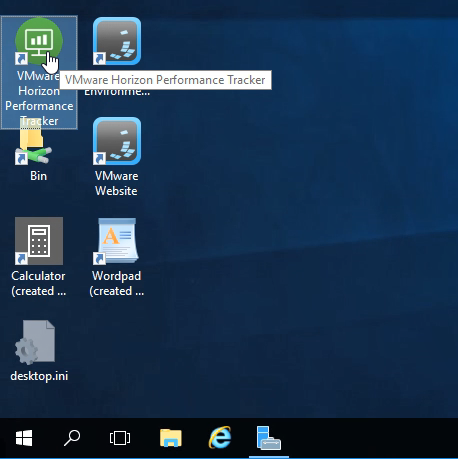
Or connect to a Desktop and launch it from the Desktop icon.
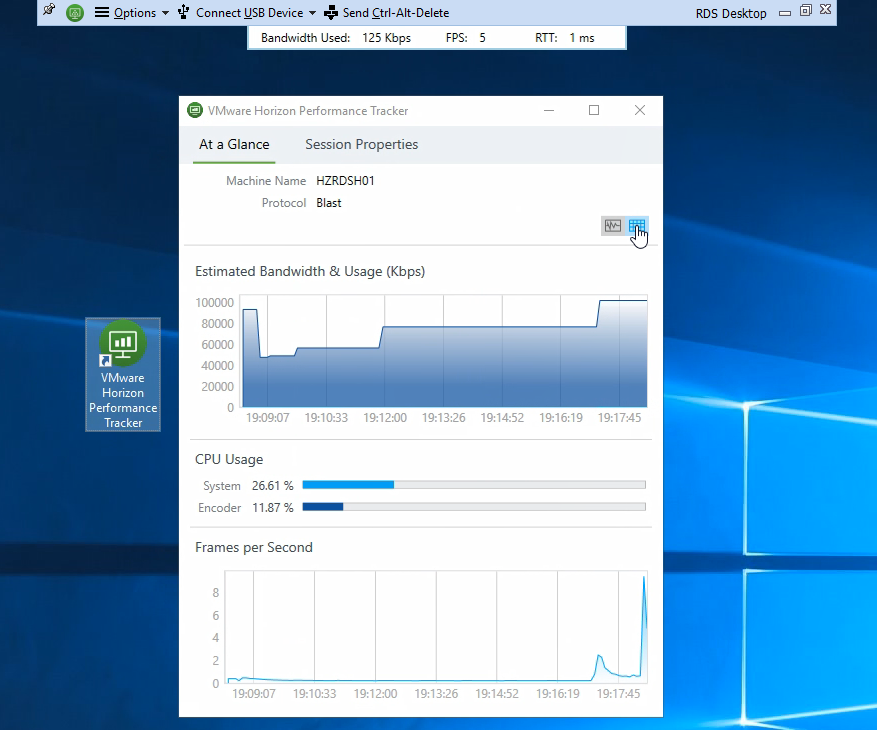
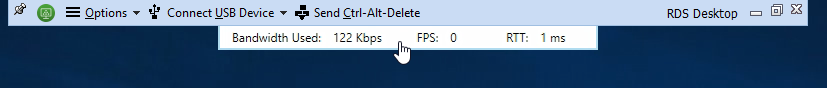
It can display protocol performance information in graphical or tabular form. The overview UI also shows the name of the Horizon Agent machine.
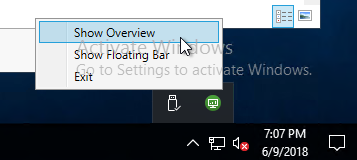
There’s also a Floating Bar option.
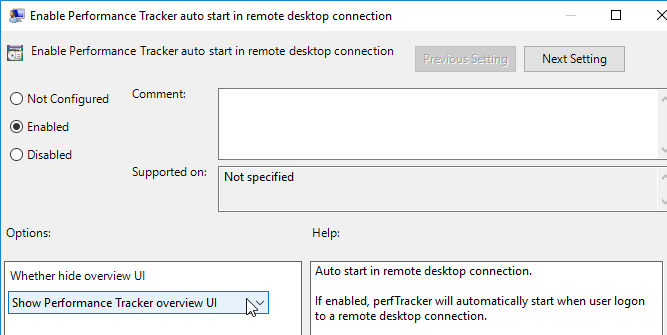
Performance Tracker can be configured to launch automatically:
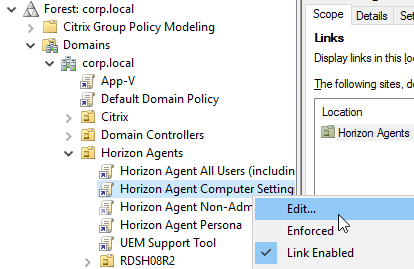
- Install the Horizon GPO templates if you haven’t already.
- Edit a GPO that applies to the Horizon Agents. These are Computer settings.
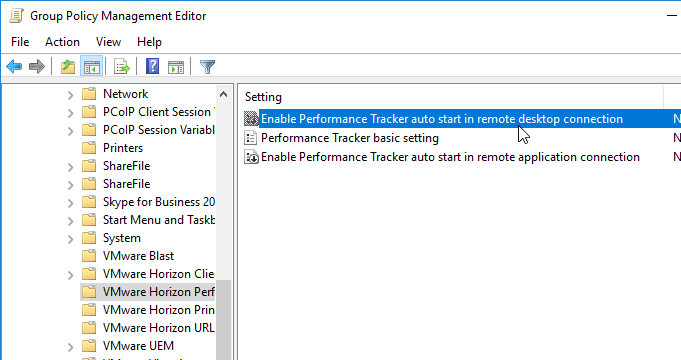
- Go to Computer Configuration | Policies | Administrative Templates | VMware Horizon Performance Tracker.
- On the right, you’ll see two options for auto starting the Performance Tracker.
- Both settings let you Show or Hide the overview UI.
- If Hide is selected, then users can open the Tracker from the systray icon.
HTML Blast
From the Horizon Connection Server webpage, you can click the VMware Horizon View HTML Access link to launch a desktop or application inside your browser. While Internet Explorer 9 is supported, some functionality, like clipboard and audio, is only available in Internet Explorer 10 and newer, Chrome and Firefox.
In Horizon 6.2 and later, you can launch applications as well as desktops from HTML Blast.
If you click the star icon then you can Mark the icon as a Favorite. Favorites are stored in the LDAP database on the Horizon Connection Server.
Applications and desktops are launched within the browser window. You can click the vertical lines on the left to switch to a different application or desktop.
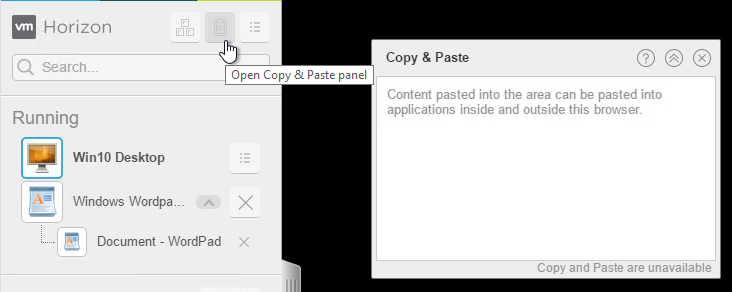
You can open the Copy & Paste panel to copy between the local machine and the remote machine.
Thin Clients
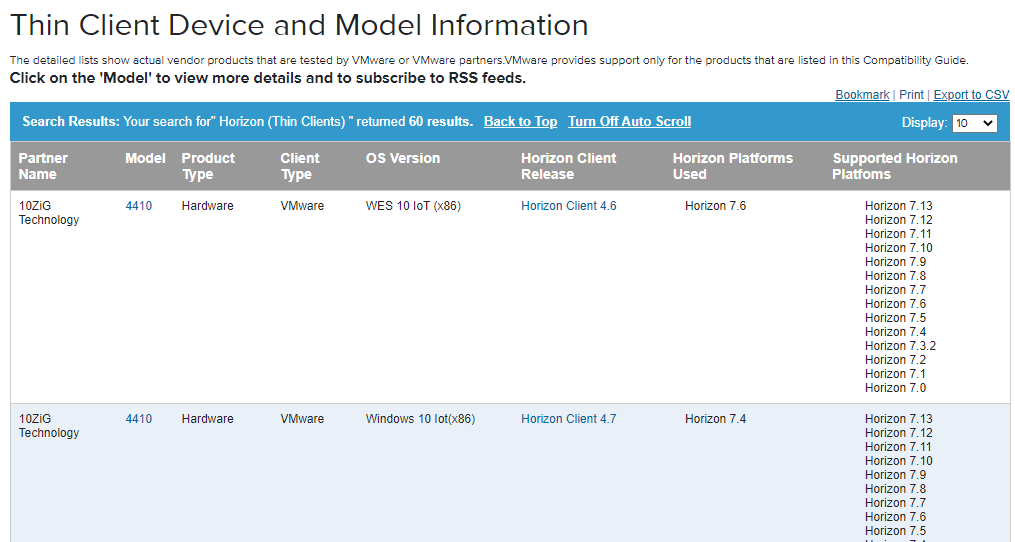
VMware View Thin Client Compatibility Guide – Thin Client Device and Model Information. It shows thin client models and the version of Horizon View that is supported with the model.
Repurposed PCs
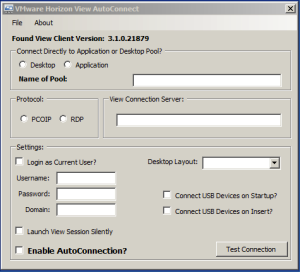
From Chris Halstead VMware Horizon View AutoConnection Utility: I decided to write an app in .NET that is essentially a wrapper for the View Client. It creates the command line variables based on what the user configures in the GUI and automatically connects to the specified desktop or application pool. All of the user configured information is stored in the registry under the current user hive.
The application silently and automatically connects into either a desktop or application pool each time a user logs in by placing it in the startup folder.
Once you have tested your connection, you are ready to enable AutoConnection. You enable AutoConnection by checking the “Enable AutoConnection” box. A common use case would be to place the .exe in the Windows startup folder so that every time a user logs in it will automatically connect to the Virtual Desktop.
This will run the application with the GUI hidden and will automatically connect to the specified pool. The application will minimize to the system tray and a balloon will indicate the connection process is occurring.
Horizon Client Group Policy – Security Settings
The Horizon GPO Bundle includes policy templates for the Horizon Client. See https://www.carlstalhood.com/horizon-group-policy-and-profiles/#viewtemplates to install the ADMX files.
Here are some security GPO settings recommended (VMware Horizon with View Security Hardening Overview) by VMware:
| GPO Setting |
|
Computer Config | Policies | Administrative Templates | VMware Horizon Client Configuration | Scripting definitions Disable 3rd-party Terminal Server plugins = enabled |
|
Computer Config | Policies | Administrative Templates | VMware Horizon Client Configuration | Security Settings Allow command line credentials = disabled Certificate verification mode = enabled, Full Security Default value of the ‘Log in as current user’ checkbox = disabled Display option to Log in as current user = disabled Servers Trusted for Delegation = enabled |
Recommend Projects
-
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.
Getting error while updating Webdriver in Protractor.
Tried with proxy setting:
npm config set proxy http:Proxy:port
npm config set http_proxy http:Proxy:port
npm config set https_proxy https:Proxy:port
System info:
Protractor version:5.2.0
npm version:3.10.10
mvn version: 3.5.2
Error:
tunneling socket could not be established, cause=read ECONNRESET
C:WindowsSystem32>webdriver-manager update
events.js:160
throw er; // Unhandled 'error' event
^
Error: tunneling socket could not be established, cause=read ECONNRESET
at ClientRequest.onError (C:Usersa655086AppDataRoamingnpmnode_modules
protractornode_modulestunnel-agentindex.js:177:17)
at ClientRequest.g (events.js:292:16)
at emitOne (events.js:96:13)
at ClientRequest.emit (events.js:188:7)
at TLSSocket.socketErrorListener (_http_client.js:310:9)
at emitOne (events.js:96:13)
at TLSSocket.emit (events.js:188:7)
at emitErrorNT (net.js:1277:8)
at _combinedTickCallback (internal/process/next_tick.js:80:11)
at process._tickCallback (internal/process/next_tick.js:104:9)
C:WindowsSystem32>
HaC
87214 silver badges24 bronze badges
asked Nov 22, 2017 at 12:51
4
Looks like duplicate of this. In your attempts mentioned in the OP, I don’t see :// after http. Also note that even for https-proxy the protocol is http and not https. If you are not behind any proxy, you need to unset them as mentioned in the linked answer
npm config set proxy http://proxyhost:proxyport
npm config set https-proxy http://proxyhost:proxyport
answered Nov 22, 2017 at 21:06
nileshnilesh
14k7 gold badges64 silver badges78 bronze badges
1
The issue got resolved by running cmd as administrator using below command
npm config set proxy false
npm cache clean
then restarting cntlm services
Webdriver-manager update
answered Nov 26, 2017 at 6:26