Содержание
- Setup cURL in Windows
- Setup cURL in Windows
- cURL in Windows 10 version 1803 or higher
- Most Common Errors with Secure Websites
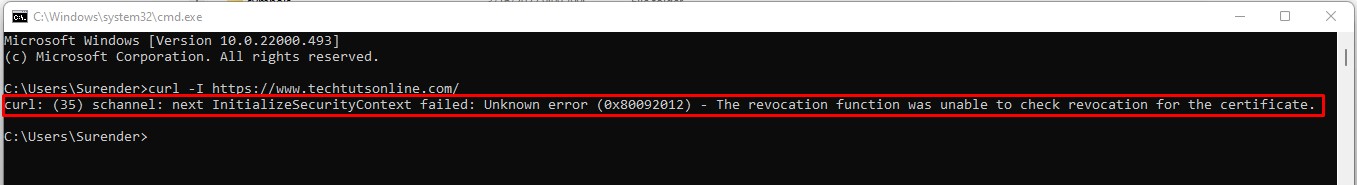
- curl: (35) schannel: next InitializeSecurityContext failed
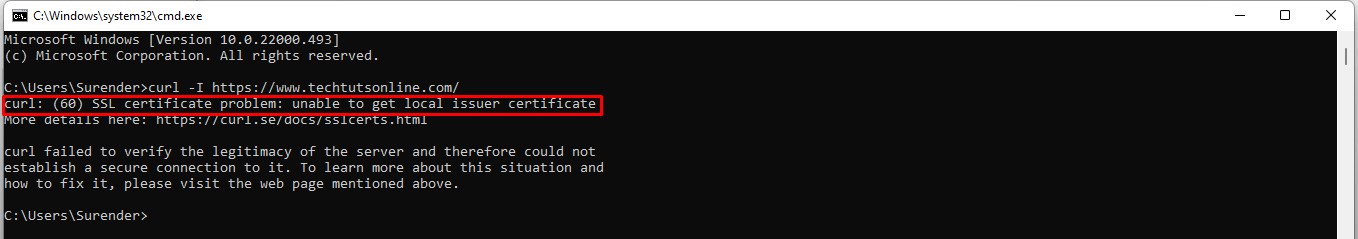
- curl: (60) SSL certificate problem
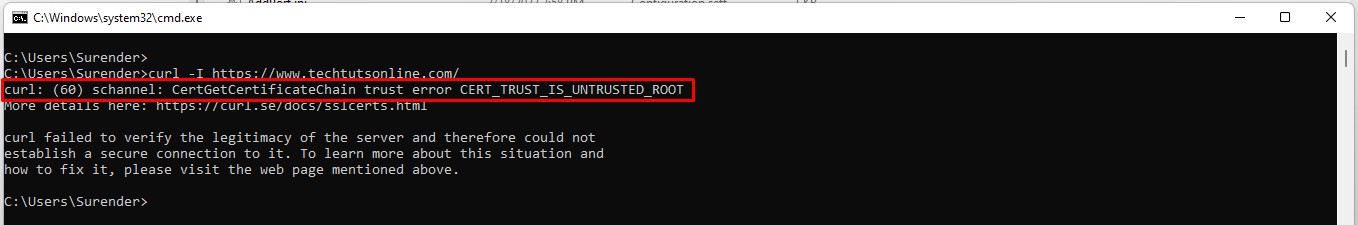
- curl: (60) schannel: CertGetCertificateChain trust error
- Setup the latest version of cURL in Windows
- Certificate Setup for cURL
- curl-library
- Man-in-the-middle proxies dont work with CURL + WinSSL #3727
- Comments
- I did this
- Also tested with custom proxy server instead of Fiddler
- curl version
- operating system
- These are configurations that I know don’t work and produces 0x80092012 error:
- These work without any errors with CURL + WinSSL and default revocation checks:
Setup cURL in Windows
Setup cURL in Windows
Table of Contents
cURL (client URL) is a command line tool that system admins and developers use to transfer data between server and client in the form of a URL. It supports several different protocols and has a variety of applications. I will not cover the details and applications of cRUL here. If you’re already on this page, I am assuming you know how to use it. Learn how to use curl in Windows if you are just getting started with it.
cURL in Windows 10 version 1803 or higher
Starting with Windows 10 (version 1803) or Server 2019, you will find curl.exe pre-installed in your %systemroot%System32 directory by default. This guide is useful if you are on an older Windows version or you want to use the latest curl version from official website, which supports more protocols than the built-in curl version. I will also cover how to fix some most common errors that you might face while using cURL in Windows.
Most Common Errors with Secure Websites
You will get a whole lot of different errors while using secure URLs with cURL. So if you’re getting any error among the below mentioned errors, you are on the right page.
curl: (35) schannel: next InitializeSecurityContext failed
If you get this error message, it indicates that curl was unable to check revocation for the certificate which is the default behavior when it comes to communication with secure websites. Even though you could easily circumvent this error by using the —ssl-no-revoke argument with curl command but it becomes tedious when you use curl command a lot. The following command shows how to bypass this error:
To learn how to get around this error once and for all – without having to specify the —ssl-no-revoke argument each time, see the Setup the latest version of cURL in Windows section.
curl: (60) SSL certificate problem
If you get this error, it means there is something wrong with root certificate that curl is using on your local system. To get around this error, you could use the —insecure (or -k for short) argument with curl command as shown in the following command:
Again, to learn how to get around this error once and for all, see the Setup the latest version of cURL in Windows section.
curl: (60) schannel: CertGetCertificateChain trust error
If you see this error, it means the root CA that curl is configured to use is untrusted. It may be using a self-signed certificate or the certificate is no longer valid. This error can also be bypassed by using the —insecure argument with curl command as shown in previous example.
Setup the latest version of cURL in Windows
Depending upon the edition of your Windows, you can download the latest version of cURL from the official website using the following links:
It will download a zip archive. There is no installer in this file so you will have to manually set the PATH environment for curl.exe binary. Once downloaded, you can extract the zip archive to any folder of your choice. I extracted mine inside D:WORKSOFTWAREcurl-7.81.0-win64 directory. Your directory should look like shown in the following screenshot:
Now to set the PATH environment variable, open RUN dialog (WinLogoKey+R), type “sysdm.cpl ,3” without quotes and press enter. This will open up advanced system properties page. Now follow the steps mentioned in the screenshot and click on OK thrice to save the changes.
When this is done, curl is ready to be used on your system. To confirm, you can open the command prompt and type curl —version command. If you see the curl version as shown in the following image, you’re all set to go to next step: 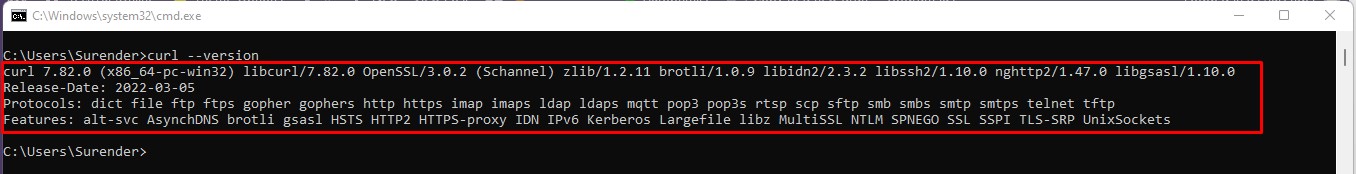
If you get an error that says ‘curl’ is not recognized as an internal or external command, operable program or batch file, it means something is wrong with the PATH environment variable you created. 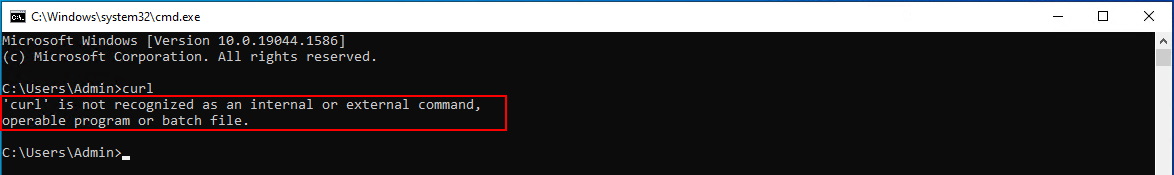
If you see this error, please follow the steps mentioned in this video to properly setup your PATH environment variable.
Certificate Setup for cURL
Now comes the most important part. At this point, when you try any secure URL with curl command, you will most probably get an error as we discussed in past sections. To permanently fix those SSL errors, you need to download the CA certificate file from official website and configure the curl on your system to use that certificate file. To do that, follow these steps:
- First of all, download the CA certificate file and copy it into the same directory where curl.exe file is available. To get the location of curl.exe, you could simply type where curl command in your command prompt.
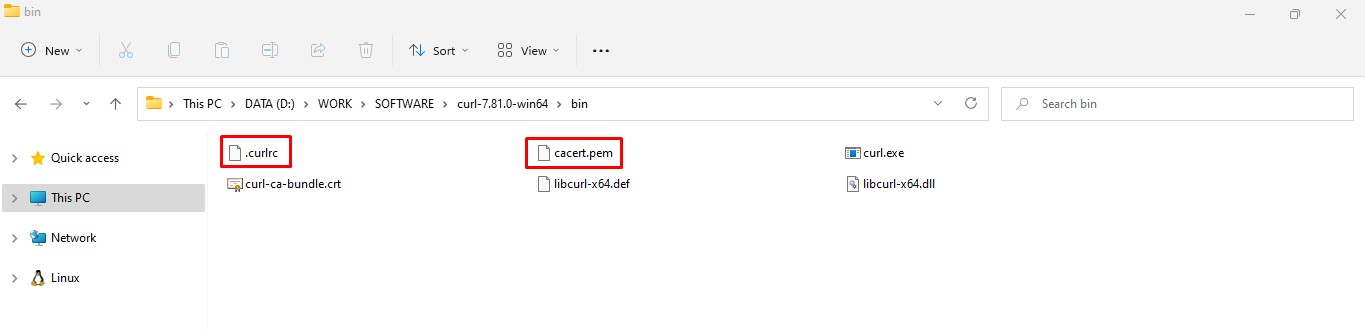
- Now create a new file named .curlrc in the same directory as that of curl.exe. In the end, your curl directory should look like shown in the following image:
- Now open the .curlrc file in notepad (or any other text editor) and set the complete path of root certificate file that you downloaded in first step. See the screenshot for reference:
Please remember to use the forward slash (/) while specifying directory path as shown below otherwise it won’t work:
[optional] If you’re using Windows 10 (version 1803) or higher, your system will most likely have curl.exe in %systemroot%System32 directory as well. When you will run curl command without explicitly specifying the complete path to curl.exe executable, your system will use the default executable located in %systemroot%System32. If this is true you will see curl.exe twice when you run where curl command. See the following image for reference:
If you see the same, you need to get rid of default curl.exe that comes with Windows. You can take the ownership of file, set the permissions and then rename the file with the help of following commands:
Make sure you run these commands in an elevated command prompt. See the following screenshot for reference: 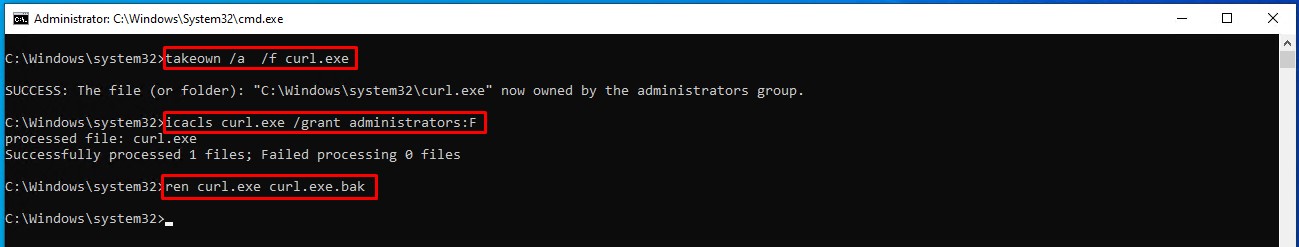
Источник
curl-library
I know people have had problems with this before and I did my googling about it, but I don’t really understand how to solve this problem because in my case it’s particularly weird. Consider this little snippet:
static void tryconnect(const char *address)
<
CURL *curl = curl_easy_init();
CURLcode res;
char buf[CURL_ERROR_SIZE];
curl_easy_setopt(curl, CURLOPT_URL, address);
curl_easy_setopt(curl, CURLOPT_CONNECT_ONLY, 1);
curl_easy_setopt(curl, CURLOPT_ERRORBUFFER, buf);
printf(«Trying %s «, address);
if(!(res = curl_easy_perform(curl))) <
printf(«OK!n»);
> else <
printf(«FAIL: %d %sn», res, buf);
>
int main(int argc, char *argv[])
<
curl_global_init(CURL_GLOBAL_DEFAULT);
tryconnect(«https://www.hollywood-mal.de/»); —> works!
tryconnect(«https://www.hollywood-mal.com/»); —> fails with schannel error
curl_global_cleanup();
return 0;
>
Why on earth does https://www.hollywood-mal.de/ work fine and https://www.hollywood-mal.com/ doesn’t work at all? I’m the owner of both domains and they are hosted by the very same company with the very same settings, yet one works, and the other one doesn’t. Of course, in a browser both work fine, but with curl only the *.de one works, the *.com one fails.
This is the output:
Trying https://www.hollywood-mal.de/ OK!
Trying https://www.hollywood-mal.com/ FAIL: 35 schannel: next InitializeSecurityContext failed: Unknown error (0x80092013) — Die Sperrfunktion konnte die Sperrung nicht ГјberprГјfen, da der Sperrserver offline war. (NB: In English the error is probably «schannel: next InitializeSecurityContext failed: Unknown error (0x80092013) — The revocation function was unable to check revocation because the revocation server was offline.»)
How can I solve this please? Some people seem to be suggesting to use the OpenSSL backend instead of schannel but is this really the only way to go? Isn’t this possible with in-house Windows solutions?
Источник
Man-in-the-middle proxies dont work with CURL + WinSSL #3727
We have users that use company wide man-in-the-middle proxies for internal security. However client software with libCURL + WinSSL reports following error in their environments:
schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) — The revocation function was unable to check revocation for the certificate.
All other Windows software work fine. It is also reproducable with Fiddler acting as decrypting proxy — as discussed in this issue #264
While solution was implemented:
curl_easy_setopt(m_curl, CURLOPT_SSL_OPTIONS, CURLSSLOPT_NO_REVOKE);
I would argue that this is not enough, especially as it makes CURL + WinSSL software act different from other Windows based software and reduces security.
I did this
- Run Fiddler
- set CURL_SSL_BACKEND=Schannel
- curl https://google.com -x 127.0.0.1:8888
(Got 0x80092012 error) - curl https://google.com -x 127.0.0.1:8888 —ssl-no-revoke
(Succeeded as expected) - curl https://revoked.badssl.com/ —ssl-no-revoke
(Succeeded, but there should be option to not allow this)
Also tested with custom proxy server instead of Fiddler
- Self signed Root CA certificate
OpenSSL can be used to generate it.
Easy-RSA utility simplifies that process, more documentation can be found here:
https://github.com/OpenVPN/easy-rsa/blob/master/README.quickstart.md
CA certificate should have revocation list configured - Burp configured as a proxy with previously generated certificate imported.
- On client machine Root CA certificate has to be installed into Trusted Root Authorities store.
- curl https://google.com -x ProxyServerUrl:ProxyPort
(Got 0x80092012 error)
curl version
curl 7.64.0 (x86_64-pc-win32) libcurl/7.64.0 (OpenSSL/1.1.1a) Schannel zlib/1.2.11 brotli/1.0.7 WinIDN libssh2/1.8.0 nghttp2/1.36.0
Release-Date: 2019-02-06
Protocols: dict file ftp ftps gopher http https imap imaps ldap ldaps pop3 pop3s rtsp scp sftp smb smbs smtp smtps telnet tftp
Features: AsynchDNS IDN IPv6 Largefile SSPI Kerberos SPNEGO NTLM SSL libz brotli TLS-SRP HTTP2 MultiSSL
operating system
Microsoft Windows [Version 10.0.17134.648]
The text was updated successfully, but these errors were encountered:
It’s possible that if a certificate in a chain does not have any revocation point and revocation checks are enabled then the call will fail. The root certificate is checked for revocation as well. Confirm by dumping the chain and inspecting it, and inspect the root certificate. Short of writing our own manual verification process and iterating through each certificate to check revocation I don’t see how we could distinguish certs with no revocation points from certs that have revocation points but aren’t available for whatever reason.
Using —ssl-no-revoke to disable revocation checking by curl schannel of your generated MITM certificates is practical for a case like this. Fiddler does its own schannel revocation check of the actual certificates if you enable it (but I think it’s only interactive). Burp may be similar.
5. curl https://revoked.badssl.com/ —ssl-no-revoke
(Succeeded, but there should be option to not allow this)
That’s exactly how it works and how it should work.
To clarify — are we are talking about «CRL Distribution Points» field in certificate? One from *.google.com:
These are configurations that I know don’t work and produces 0x80092012 error:
Fiddler overrides with certificates without any CRL values. Chain looks like:
DO_NOT_TRUST_FiddlerRoot [No CRL] -> *.service.com [No CRL]
Certificate chain from user (behind proxy):
User-root-CA [No CRL] -> User-CA [CRL] -> *.service.com [No CRL]
Certificate using our test proxy:
TestProxyRoot-CA [CRL] -> *.service.com [No CRL]
These work without any errors with CURL + WinSSL and default revocation checks:
And if connecting CURL to service directly:
DigiCert [No CRL] -> DigiCert CA [CRL] -> *.service.com [CRL]
Also we have our internal testing services like this:
Our-root-CA [No CRL] -> Our CA [CRL] -> *.test-service.com [CRL]
So there is variety of configurations, but both failing ones have no CRL in end-entity (*.service.com) certificates. Can that be what is causing it?
If the schannel backend is used and the user does not specify a bundle of certificates then libcurl uses the default OS certificate store with SCH_CRED_REVOCATION_CHECK_CHAIN which is documented as «When validating a certificate chain, check all certificates for revocation.»
Code for SCH_CRED_REVOCATION_CHECK_CHAIN
Lines 517 to 545 in 521bbbe
| if (conn-> ssl_config . verifypeer ) < |
| # ifdef HAS_MANUAL_VERIFY_API |
| if (BACKEND-> use_manual_cred_validation ) |
| schannel_cred. dwFlags = SCH_CRED_MANUAL_CRED_VALIDATION; |
| else |
| # endif |
| schannel_cred. dwFlags = SCH_CRED_AUTO_CRED_VALIDATION; |
| /* TODO s/data->set.ssl.no_revoke/SSL_SET_OPTION(no_revoke)/g */ |
| if (data-> set . ssl . no_revoke ) < |
| schannel_cred. dwFlags |= SCH_CRED_IGNORE_NO_REVOCATION_CHECK | |
| SCH_CRED_IGNORE_REVOCATION_OFFLINE; |
| DEBUGF ( infof (data, » schannel: disabled server certificate revocation « |
| » checks n » )); |
| > |
| else < |
| schannel_cred. dwFlags |= SCH_CRED_REVOCATION_CHECK_CHAIN; |
| DEBUGF ( infof (data, |
| » schannel: checking server certificate revocation n » )); |
| > |
| > |
| else < |
| schannel_cred. dwFlags = SCH_CRED_MANUAL_CRED_VALIDATION | |
| SCH_CRED_IGNORE_NO_REVOCATION_CHECK | |
| SCH_CRED_IGNORE_REVOCATION_OFFLINE; |
| DEBUGF ( infof (data, |
| » schannel: disabled server cert revocation checks n » )); |
| > |
If the schannel backend is used and the user specifies a bundle of certificates (eg CAINFO) then libcurl ignores the OS certificate store and uses the bundle with CERT_CHAIN_REVOCATION_CHECK_CHAIN which is basically the same thing, documented as «Revocation checking is done on all of the certificates in every chain.»
Code for CERT_CHAIN_REVOCATION_CHECK_CHAIN
Lines 498 to 546 in 521bbbe
| if (result == CURLE_OK) < |
| CERT_CHAIN_PARA ChainPara; |
| memset (&ChainPara, 0 , sizeof (ChainPara)); |
| ChainPara. cbSize = sizeof (ChainPara); |
| if (! CertGetCertificateChain (cert_chain_engine, |
| pCertContextServer, |
| NULL , |
| pCertContextServer-> hCertStore , |
| &ChainPara, |
| (data-> set . ssl . no_revoke ? 0 : |
| CERT_CHAIN_REVOCATION_CHECK_CHAIN), |
| NULL , |
| &pChainContext)) < |
| char buffer[STRERROR_LEN]; |
| failf (data, » schannel: CertGetCertificateChain failed: %s » , |
| Curl_strerror ( GetLastError (), buffer, sizeof (buffer))); |
| pChainContext = NULL ; |
| result = CURLE_PEER_FAILED_VERIFICATION; |
| > |
| if (result == CURLE_OK) < |
| CERT_SIMPLE_CHAIN *pSimpleChain = pChainContext-> rgpChain [ 0 ]; |
| DWORD dwTrustErrorMask = |
(DWORD)(CERT_TRUST_IS_NOT_TIME_NESTED); dwTrustErrorMask &= pSimpleChain-> TrustStatus . dwErrorStatus ; if (dwTrustErrorMask) < if (dwTrustErrorMask & CERT_TRUST_IS_REVOKED) failf (data, » schannel: CertGetCertificateChain trust error « » CERT_TRUST_IS_REVOKED » ); else if (dwTrustErrorMask & CERT_TRUST_IS_PARTIAL_CHAIN) failf (data, » schannel: CertGetCertificateChain trust error « » CERT_TRUST_IS_PARTIAL_CHAIN » ); else if (dwTrustErrorMask & CERT_TRUST_IS_UNTRUSTED_ROOT) failf (data, » schannel: CertGetCertificateChain trust error « » CERT_TRUST_IS_UNTRUSTED_ROOT » ); else if (dwTrustErrorMask & CERT_TRUST_IS_NOT_TIME_VALID) failf (data, » schannel: CertGetCertificateChain trust error « » CERT_TRUST_IS_NOT_TIME_VALID » ); else if (dwTrustErrorMask & CERT_TRUST_REVOCATION_STATUS_UNKNOWN) failf (data, » schannel: CertGetCertificateChain trust error « » CERT_TRUST_REVOCATION_STATUS_UNKNOWN » ); else failf (data, » schannel: CertGetCertificateChain error mask: 0x %08x » , dwTrustErrorMask); result = CURLE_PEER_FAILED_VERIFICATION; > > >
Whether or not certificates without revocation points (any point like AIA or CRL or whatever) are accepted is unclear. Based on what you are describing it’s likely schannel using such a revocation check must allow for root certificates without any revocation point but not leaf certificates without any revocation point, at least in Windows 10.
Also review Can’t connect to Fiddler proxy if using WinSSL backend which is why I added —ssl-no-revoke (I had forgot or I would’ve mentioned it yesterday). You’ll notice in that issue I said:
schannel is returning CRYPT_E_NO_REVOCATION_CHECK likely because we pass SCH_CRED_REVOCATION_CHECK_CHAIN in schannel_connect_step1 and in that case schannel requires all root CAs to have some sort of revocation detail when that flag is passed.
Based on what you describe I guess I’m wrong or it’s not consistent between OS versions.
P.S. I fixed my top issue description to refer to #264 . pasted wrong link before. I was aware about that issue/fix and wanted followup — as it affects more usual proxy configurations, not only Fiddler.
It seems that original issue #264 was not related to root certificate CRLs at all, Fiddler would also make end-entity (leaf) certificates without CRLs as well. Or was there clarification that exactly root certificate checks caused #264 ?
Is there any way to skip end-entity certificate revocation checks if there is none in curl/winssl?
Major reason for this is that all Windows based software works fine with these configurations, but then software that is built on top of CURL + WinSSL is seen as wrong at the end user.
On related note, CRL server offline errors are usually ignored by most of Windows software, but not CURL + WinSSL. While this is much less important, it is inconsistency as well.
It seems that original issue #264 was not related to root certificate CRLs at all, Fiddler would also make end-entity (leaf) certificates without CRLs as well. Or was there clarification that exactly root certificate checks caused #264 ?
The reporter in #264 didn’t respond to the report so I don’t know. It’s not documented what happens when a certificate is missing any revocation point and revocation checks are enabled. It most likely falls under the no revocation check error. We have some empirical results here and in the other issue but that’s about it. It may be different depending on OS version.
Is there any way to skip end-entity certificate revocation checks if there is none in curl/winssl?
Disable revocation checks in curl using —ssl-no-revoke. Whether or not your MITM does actual revocation checks is outside of curl’s control.
Major reason for this is that all Windows based software works fine with these configurations, but then software that is built on top of CURL + WinSSL is seen as wrong at the end user.
Yeah I’d imagine most developers implement soft revocation checking where it tries and if it cannot succeed it continues with the connection anyway. curl does not do that as I discussed in the other issue, you can have it either fully on or fully off when Schannel is used as the backend in Windows.
Источник
Setup cURL in Windows
cURL (client URL) is a command line tool that system admins and developers use to transfer data between server and client in the form of a URL. It supports several different protocols and has a variety of applications. I will not cover the details and applications of cRUL here. If you’re already on this page, I am assuming you know how to use it. Learn how to use curl in Windows if you are just getting started with it.
cURL in Windows 10 version 1803 or higher
Starting with Windows 10 (version 1803) or Server 2019, you will find curl.exe pre-installed in your %systemroot%System32 directory by default. This guide is useful if you are on an older Windows version or you want to use the latest curl version from official website, which supports more protocols than the built-in curl version. I will also cover how to fix some most common errors that you might face while using cURL in Windows.
Most Common Errors with Secure Websites
You will get a whole lot of different errors while using secure URLs with cURL. So if you’re getting any error among the below mentioned errors, you are on the right page.
curl: (35) schannel: next InitializeSecurityContext failed
curl: (35) schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) - The revocation function was unable to check revocation for the certificate.
If you get this error message, it indicates that curl was unable to check revocation for the certificate which is the default behavior when it comes to communication with secure websites. Even though you could easily circumvent this error by using the --ssl-no-revoke argument with curl command but it becomes tedious when you use curl command a lot. The following command shows how to bypass this error:
curl --ssl-no-revoke --head https://www.techtutsonline.com/
To learn how to get around this error once and for all – without having to specify the --ssl-no-revoke argument each time, see the Setup the latest version of cURL in Windows section.
curl: (60) SSL certificate problem
curl: (60) SSL certificate problem: unable to get local issuer certificate
If you get this error, it means there is something wrong with root certificate that curl is using on your local system. To get around this error, you could use the --insecure (or -k for short) argument with curl command as shown in the following command:
curl --insecure https://www.techtutsonline.com/
Again, to learn how to get around this error once and for all, see the Setup the latest version of cURL in Windows section.
curl: (60) schannel: CertGetCertificateChain trust error
curl: (60) schannel: CertGetCertificateChain trust error CERT_TRUST_IS_UNTRUSTED_ROOT
If you see this error, it means the root CA that curl is configured to use is untrusted. It may be using a self-signed certificate or the certificate is no longer valid. This error can also be bypassed by using the --insecure argument with curl command as shown in previous example.
Setup the latest version of cURL in Windows
Depending upon the edition of your Windows, you can download the latest version of cURL from the official website using the following links:
- For 64-bit Windows
- For 32-bit Windows
It will download a zip archive. There is no installer in this file so you will have to manually set the PATH environment for curl.exe binary. Once downloaded, you can extract the zip archive to any folder of your choice. I extracted mine inside D:WORKSOFTWAREcurl-7.81.0-win64 directory. Your directory should look like shown in the following screenshot:
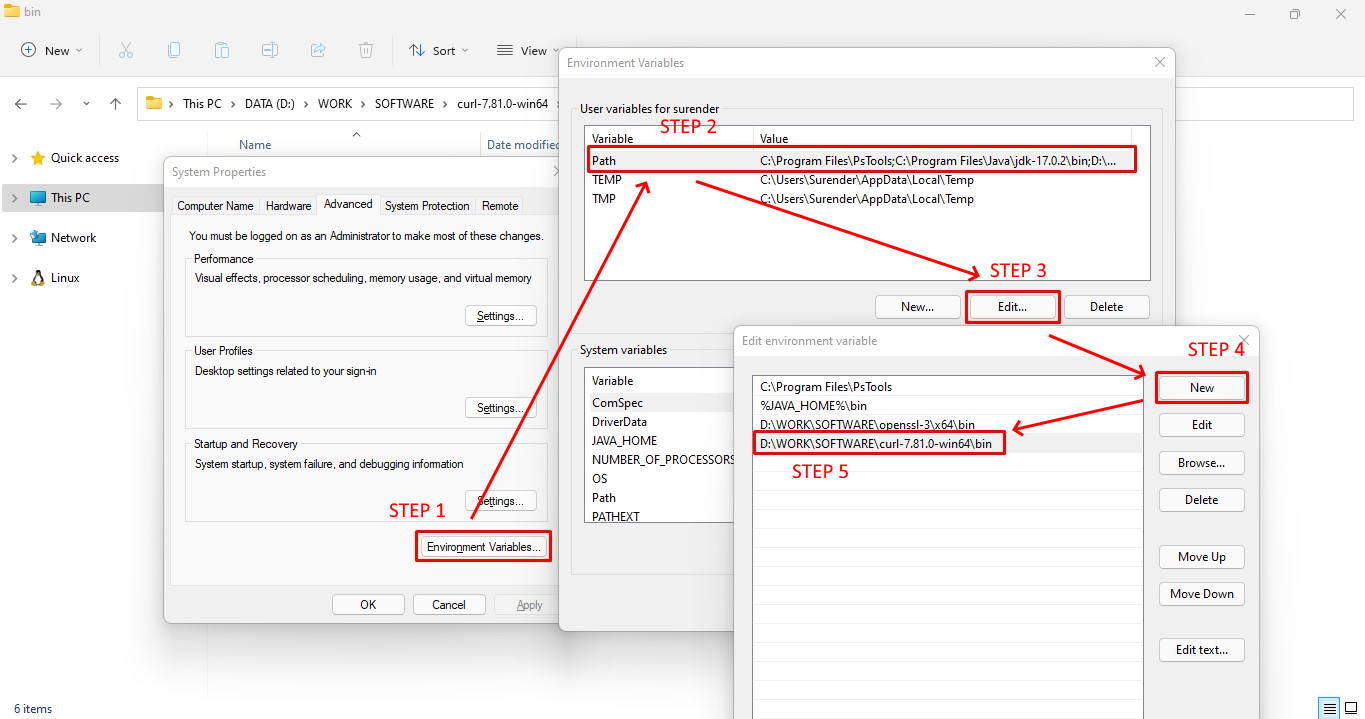
Now to set the PATH environment variable, open RUN dialog (WinLogoKey+R), type “sysdm.cpl ,3” without quotes and press enter. This will open up advanced system properties page. Now follow the steps mentioned in the screenshot and click on OK thrice to save the changes.

When this is done, curl is ready to be used on your system. To confirm, you can open the command prompt and type curl --version command. If you see the curl version as shown in the following image, you’re all set to go to next step:
If you get an error that says ‘curl’ is not recognized as an internal or external command, operable program or batch file, it means something is wrong with the PATH environment variable you created.
If you see this error, please follow the steps mentioned in this video to properly setup your PATH environment variable.
Certificate Setup for cURL
Now comes the most important part. At this point, when you try any secure URL with curl command, you will most probably get an error as we discussed in past sections. To permanently fix those SSL errors, you need to download the CA certificate file from official website and configure the curl on your system to use that certificate file. To do that, follow these steps:
- First of all, download the CA certificate file and copy it into the same directory where curl.exe file is available. To get the location of curl.exe, you could simply type
where curlcommand in your command prompt.
- Now create a new file named .curlrc in the same directory as that of curl.exe. In the end, your curl directory should look like shown in the following image:
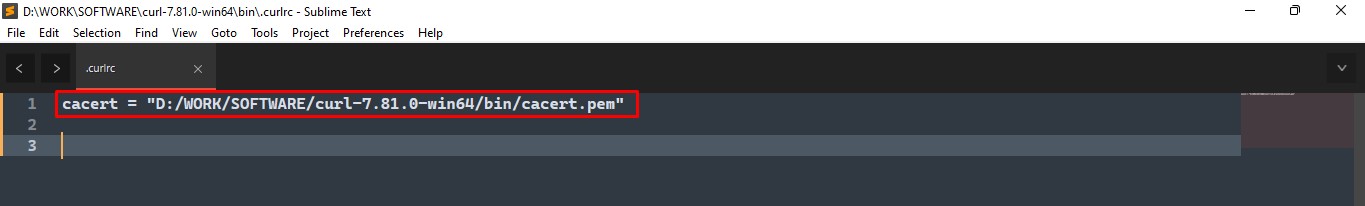
- Now open the .curlrc file in notepad (or any other text editor) and set the complete path of root certificate file that you downloaded in first step. See the screenshot for reference:
Please remember to use the forward slash (/) while specifying directory path as shown below otherwise it won’t work:cacert = "D:/WORK/SOFTWARE/curl-7.81.0-win64/bin/cacert.pem"
- [optional] If you’re using Windows 10 (version 1803) or higher, your system will most likely have curl.exe in %systemroot%System32 directory as well. When you will run curl command without explicitly specifying the complete path to curl.exe executable, your system will use the default executable located in %systemroot%System32. If this is true you will see curl.exe twice when you run
where curlcommand. See the following image for reference:
If you see the same, you need to get rid of default curl.exe that comes with Windows. You can take the ownership of file, set the permissions and then rename the file with the help of following commands:cd C:WindowsSystem32
takeown /a /f curl.exe
icacls curl.exe /grant administrators:F
ren curl.exe curl.exe.bakMake sure you run these commands in an elevated command prompt. See the following screenshot for reference:
- Once you successfully rename the default curl.exe executable, you should see a single instance of curl.exe when running
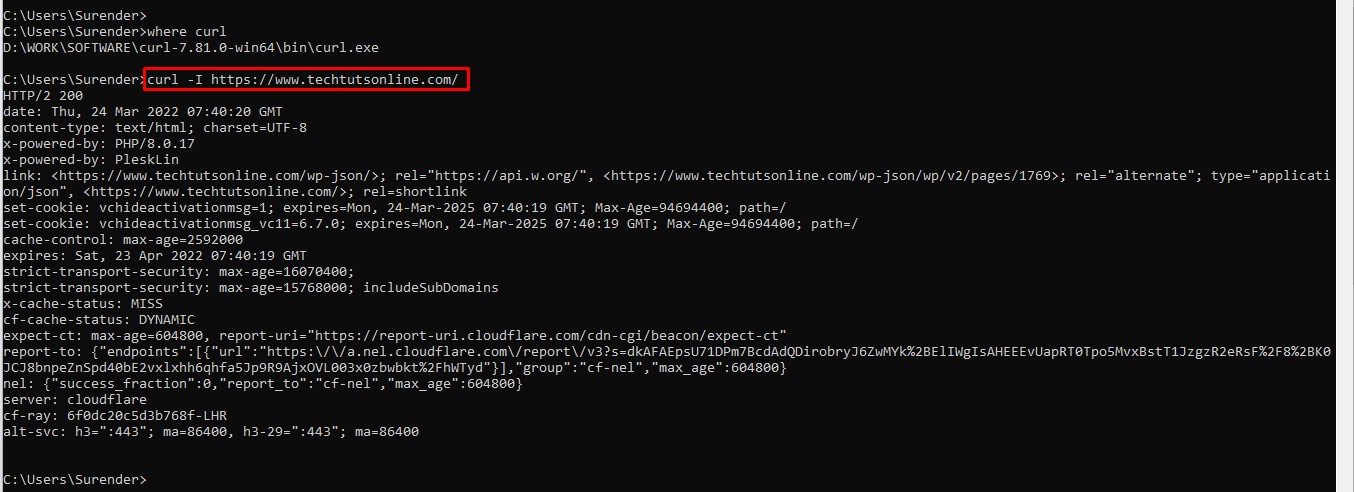
where curlcommand. - Your system is now all set and you can start using curl without any SSL error. The following screenshot shows that I no longer get any SSL error and I don’t have to use the
--insecureor--ssl-no-revokearguments anymore.curl -I https://www.techtutsonline.com/
Open
Issue created May 08, 2017 by
Windows Runner can’t clone repo due to Certificate Revocation problem
Summary
Gitlab CI runner on MS Windows (running on Windows 7 x64) cannot clone repo due to SSL problem (certificate revocation checking).
This is a problem in small / testing environments where Certificate Revocation List infrastructure is not / cannot be set up.
Need to be able to pass the «CURLSSLOPT_NO_REVOKE» option to disable CRL checking with WinSSL (see: https://curl.haxx.se/libcurl/c/CURLOPT_SSL_OPTIONS.html).
Steps to reproduce
-
Have environment where SSL is in use, but there are no entries in the AIA / CDP / OSCP sections of the certificate (e.g no Certificate Revocation List infrastructure exists)
-
Undertake any action that triggers a build using the windows runner, e.g. pushing to a branch with a pipeline or clicking «retry» on a failed build in Gitlab web UI
Actual behavior
Build fails to check out repository, apparently due to being unable to check certificate revocation. Attempted workarounds e.g. specifying tls-ca-file or setting tls-skip-verify to true do not work.
Failure is due to schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) error, see logs section for more.
Expected behavior
Build checking out and building successfully, or at least progressing beyond checkout stage.
Relevant logs and/or screenshots
Running with gitlab-ci-multi-runner 1.11.2 (0489844)
on HOSTNAME (a7e25147)
Using Shell executor...
Running on HOSTNAME...
Cloning repository...
Cloning into 'C:/gitlabrunner/builds/a7e25147/0/USERNAME/PROJECTNAME'...
fatal: unable to access 'https://gitlab-ci-token:xxxxxx@GITLABHOST/USERNAME/PROJECTNAME.git/': schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) - The revocation function was unable to check revocation for the certificate.
ERROR: Job failed: exit status 128Environment description
GitLab Community Edition 8.9.0-pre
Runner running on Windows 7 x64 as workstation admin
Used GitLab Runner version
c:gitlabrunner>gitlab-runner.exe -v
Version: 1.11.2
Git revision: 0489844
Git branch: 1-11-stable
GO version: go1.7.5
Built: Tue, 04 Apr 2017 18:33:28 +0000
OS/Arch: windows/amd64Edited Sep 02, 2020 by 🤖 GitLab Bot 🤖