# HERE IS MY server.ovpn FILE
#################################################
# Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients <-> one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine <-> single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, e.g.: #
# «C:\Program Files\OpenVPN\config\foo.key» #
# #
# Comments are preceded with ‘#’ or ‘;’ #
#################################################
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# «dev tun» will create a routed IP tunnel,
# «dev tap» will create an ethernet tunnel.
# Use «dev tap0» if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use «dev-node» for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don’t need this.
;dev-node MyTap
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the «easy-rsa» directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see «pkcs12» directive in man page).
ca «C:\OpenVPN\config\ca.crt»
cert «C:\OpenVPN\config\server.crt»
key «C:\OpenVPN\config\server.key» # This file should be kept secret
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh «C:\OpenVPN\config\dh4096.pem»
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, i.e. a /30 per client)
# Defaults to net30 (not recommended)
;topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
server 10.8.0.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS’s bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 10.8.0.4/255.255.255.0. Finally we
# must set aside an IP range in this subnet
# (start=10.8.0.50 end=10.8.0.100) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS’s bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push «route 192.168.10.0 255.255.255.0»
;push «route 192.168.20.0 255.255.255.0»
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory «ccd» for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name «Thelonious»
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
;client-config-dir ccd
;route 192.168.40.128 255.255.255.248
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious’ private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, i.e. you are
# using «dev tun» and «server» directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Suppose that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push «redirect-gateway def1 bypass-dhcp»
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
;push «dhcp-option DNS 208.67.222.222»
;push «dhcp-option DNS 208.67.220.220»
# Uncomment this directive to allow different
# clients to be able to «see» each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server’s TUN/TAP interface.
;client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE «COMMON NAME»,
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an «HMAC firewall»
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn —genkey —secret ca.key
#
# The server and each client must have
# a copy of this key.
# The second parameter should be ‘0’
# on the server and ‘1’ on the clients.
tls-auth «C:\OpenVPN\config\ca.key» 0 # This file is secret
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that v2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-256-CBC
# Enable compression on the VPN link and push the
# option to the client (v2.4+ only, for earlier
# versions see below)
;compress lz4-v2
;push «compress lz4-v2»
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It’s a good idea to reduce the OpenVPN
# daemon’s privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
;user nobody
;group nobody
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status «C:\OpenVPN\log\openvpn-status.log»
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the «Program FilesOpenVPNlog» directory).
# Use log or log-append to override this default.
# «log» will truncate the log file on OpenVPN startup,
# while «log-append» will append to it. Use one
# or the other (but not both).
;log openvpn.log
;log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
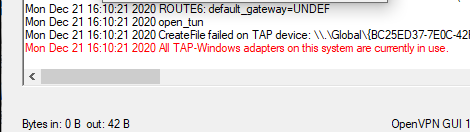
При запуске OpenVPN сервера или подключения из клиента OpenVPN вы можете столкнуться с ошибкой:
All TAP-Windows adapters on this system are currently in use Exiting due to fatal error
Или
All wintun adapters on this system are currently in use or disabled
Или
No TAP Adapter Available
Вы можете увидеть эту ошибку логе OpenVPN сервера (файл C:Program FilesOpenVPNlogopenvpn.log) или в клиенте OpenVPN GUI/
Это известная ошибка, связанная с тем что в Windows не установлены или некорректно работают виртуальные сетевые адаптеры TAP или wintun.
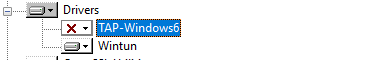
В OpenVPN 2.5+ вместо сетевых адаптеров TAP можно использовать WinTun от разработчиков WireGuard. По словам разработчиков, wintun драйвер работает быстрее чем классический OpenVPN драйвер TAP. Вы можете выбрать какой сетевой драйвер использовать при установке OpenVPN (TAP-Windows6 или Wintun).
Чтобы исправить эту ошибку нужно выполнить один из следующих шагов (расположены в порядке от самого простого к самому сложному):
- Перезапустить TAP-Windows/WinTun через панель управления.
- Переустановить драйвер TAP-Windows/Wintun;
- Создать новый сетевой адаптер для OpenVPN (или другого VPN клиента)
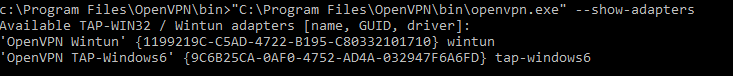
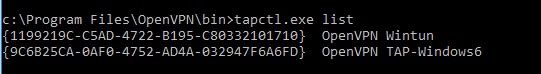
Выведите список всех TAP адаптеров, доступных клиенту OpenVPN:
cd "c:Program FilesOpenVPNbin"
“C:Program FilesOpenVPNbinopenvpn.exe” --show-adapters
В нашем случае установлен как Wintun, так и TAP адаптер:
'OpenVPN Wintun' {1199219C-C5AD-4722-B195-C80332101710} wintun
'OpenVPN TAP-Windows6' {9C6B25CA-0AF0-4752-AD4A-032947F6A6FD} tap-windows6
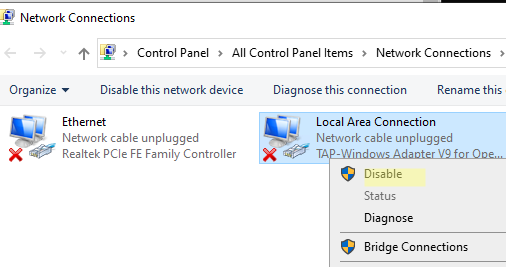
Для устранения ошибки обычно достаточно включить и отключить TAP адаптер в панели управления Windows, перезагрузить компьютер или переустановить клиент OpenVPN.
Вы можете включить и отключить сетевой адаптер WinTap из панели управления ncpa.cpl. Щелкните в панели управления по нужному адаптеру (TAP-Windows или Wintun Userspace Tunnel) и выберите Disable. Затем включите его (Enable.)
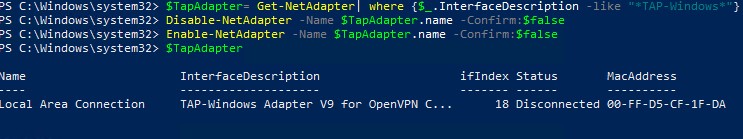
Также вы можете перезапустить все сетевые интерфейсе OpenVPN TAP с помощью PowerShell:
$TapAdapter= Get-NetAdapter| where {$_.InterfaceDescription -like "*TAP-Windows*"}
Disable-NetAdapter -Name $TapAdapter -Confirm:$false
Enable-NetAdapter -Name $TapAdapter -Confirm:$false
Если предыдущий способ не помог, попробуйте переустановить драйвера для вашего виртуального TAP адаптера вручную
- Скачайте последнюю версию TAP драйвера для Windows здесь (http://build.openvpn.net/downloads/releases/). Например, tap-windows-9.24.7.zip или wintun-amd64-0.8.1.
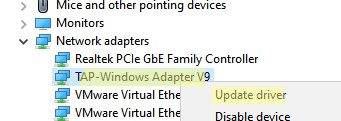
- Распакуйте архив, запустите Device Manager (
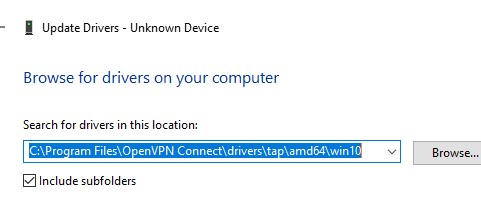
devmgmt.msc), щелкните правой кнопкой по сетевому адаптеру TAP-Windows Adapter v9 в секции Network Adapters и выберите Update driver; - Укажите путь к каталогу с драйвером TAP.
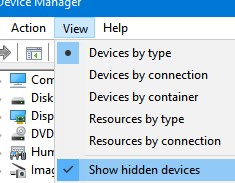
Если вы не видите в панели управления TAP-Windows Adapter V9, откройте консоль Device Manager и включите опцию View-> Show hidden device.
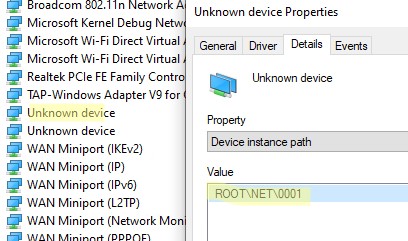
Если в секции Network adapters есть устройства типа unknown device, откройте его свойства, перейдите на вкладку Details и проверьте значение свойства Device instance path.
Если здесь указано ROOTNET000, значит попробуйте выполнить авматотический поиск дрвйвера или вручную укажите путь к INF файлу (например C:Program FilesOpenVPN Connectdriverstapamd64win10OemVista.inf). После этого в панели управления появится ваш TAP адаптер.
В Windows 7 драйвер TAP, подписанный с помощью SHA256, не будет работать корректно, пока вы вручную не установите обновление KB4474419.
В самых редких случаях может помочь полное пересоздание TAP/Wintun адаптера.
Перед установкой нужно удалить существующий сетевой адаптер TAP и его драйвер. Для этого запустите программу C:Program FilesTAP-WindowsUninstall.exe или просто удалите устройство из Device Manager (Uninstall device).
Для установки TAP драйвера используется утилита tapinstall.exe.
Распакуйте архив и запустите установочный файл с правами администратора.
В новых версиях OpenVPN для управления виртуальными сетевыми адаптерами используется утилита c:Program FilesOpenVPNbintapctl.exe.
Вывести список сетевых адаптеров OpenVPN:
tapctl.exe list
Удалить адаптер:
tapctl.exe delete "OpenVPN TAP-Windows6"
Создать новый адаптер TAP:
tapctl.exe create
Создать новый wintun адаптер:
tapctl.exe create --hwid wintun
Обязательно проверьте, что новый сетевой адаптер TAP-Windows Adapter появился в списке сетевых подключения в панели управления Windows (консоль ncpa.cpl).
Также ошибка “ All TAP-Windows adapters on the system are currently in use” может возникнуть, если вы пытаетесь установить несколько OpenVPN подключений с одного компьютера. Для каждого VPN подключения нужно создать свой адаптер.
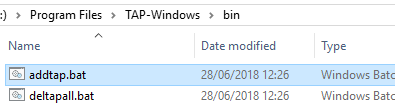
Вы можете создать дополнительный WinTap сетевой адаптер с помощью скрипта (bat файл) %ProgramFiles%TAP-Windowsbinaddtap.bat.
Или с помощью команды (в современных версиях клиента OpenVPN):
c:Program FilesOpenVPNbintapctl.exe.tapctl.exe create
В результате в панели управления появится два (или более) сетевых адаптеров TAP-Windows Adapter V9, и вы сможете одновременно установить несколько одновременных OpenVPN сессий с разными серверами.
Теперь вы можете использовать ваше OpenVPN подключение в Windows и настроить автоматическое подключение к VPN. [/alert]
Содержание
- OpenVPN Support Forum
- OpenVPN GUI client on Win7 complains about missing TAP
- OpenVPN GUI client on Win7 complains about missing TAP
- Re: OpenVPN GUI client on Win7 complains about missing TAP
- Re: OpenVPN GUI client on Win7 complains about missing TAP
- Re: OpenVPN GUI client on Win7 complains about missing TAP
- Re: OpenVPN GUI client on Win7 complains about missing TAP
- Re: OpenVPN GUI client on Win7 complains about missing TAP
- Ошибка OpenVPN: All TAP-Windows adapters are currently in use
- OpenVPN Support Forum
- Exiting due to fatal error
- Exiting due to fatal error
- Re: Exiting due to fatal error
- Re: Exiting due to fatal error
OpenVPN Support Forum
Community Support Forum
OpenVPN GUI client on Win7 complains about missing TAP
OpenVPN GUI client on Win7 complains about missing TAP
Post by BobAGI » Tue Oct 30, 2018 5:41 pm
I have a colleague in Spain who has gotten a login to the OpenVPN company server I am managing.
He is using a Windows7 Pro X64 PC
The server runs this version: OpenVPN 2.4.6 x86_64-pc-linux-gnu
Today he installed OpenVPN from the installer «openvpn-install-2.4.6-I602.exe» found on the OpenVPN website.
It seemed to go OK so next he tried to connect using the OVPN file I had made for him.
But he gets a fatal error which says:
Re: OpenVPN GUI client on Win7 complains about missing TAP
Post by TinCanTech » Tue Oct 30, 2018 5:58 pm
I would hope by now that you understand the details we need in order to help ..
But it looks like the TAP adaptor installation failed .. try re-installing openvpn.
Re: OpenVPN GUI client on Win7 complains about missing TAP
Post by BobAGI » Tue Oct 30, 2018 6:10 pm
Re: OpenVPN GUI client on Win7 complains about missing TAP
Post by BobAGI » Wed Oct 31, 2018 5:10 pm
Re: OpenVPN GUI client on Win7 complains about missing TAP
Post by TinCanTech » Wed Oct 31, 2018 8:27 pm
Re: OpenVPN GUI client on Win7 complains about missing TAP
Post by BobAGI » Wed Oct 31, 2018 10:22 pm
As you can see the last two lines constitute a report of the fatal error concerning the TAP device.
The next step was to try the advice in the logfile, but it failed with an error.
Then he uninstalled/reinstalled OpenVPN and tried again.
At this point he claims that it was again unsuccessful, but I am no longer sure what he actually meant since later on I discovered that his «not working» meant that he could not access a specific server on the network using the //computername syntax, whereas I assumed he meant that what we had been working on did not succeed (connecting to VPN).
Anyway I assumed there was no TAP adapter still and asked him to run the command «as administrator» and report back.
Now after another back-and-forth I got a screenshot showing that he now had in fact no less than 3 TAP adapters !!
And I could verify through the logfile on the server that he was in fact connected.
In his case he was having a DNS issue once he finally got connected since using the IP address of the server worked.
So I told him how to add the two servers to his local hosts file and then his system worked as he expected.
This means that I cannot truly claim that the reinstall of OpenVPN did not in fact solve the problem, even though creating new TAP devices finally seemed to work. The needed TAP may well have been created during re-install.
Sorry for this confusion, I am an engineer now in Sweden and he is a marketing guy in the Madrid office and the home office LAN with VPN server is in the USA.
Concerning the DNS issue I just opened a new ticket here.
Источник
Ошибка OpenVPN: All TAP-Windows adapters are currently in use
При запуске OpenVPN сервера или подключения из клиента OpenVPN вы можете столкнуться с ошибкой:
Вы можете увидеть эту ошибку логе OpenVPN сервера (файл C:Program FilesOpenVPNlogopenvpn.log) или в клиенте OpenVPN GUI/
Это известная ошибка, связанная с тем что в Windows не установлены или некорректно работают виртуальные сетевые адаптеры TAP или wintun.
Для устранения ошибки обычно достаточно включить и отключить TAP адаптер в панели управления Windows, перезагрузить компьютер или переустановить клиент OpenVPN.
Вы можете включить и отключить сетевой адаптер WinTap из панели управления ncpa.cpl или с помощью такого скрипта PowerShell:
$TapAdapter= Get-NetAdapter| where <$_.InterfaceDescription -like «*TAP-Windows*»>
Disable-NetAdapter -Name $TapAdapter -Confirm:$false
Enable-NetAdapter -Name $TapAdapter -Confirm:$false
В редких случаях нужно переустановить виртуальный адаптер TAP вручную. Последнюю версию TAP драйвера для Windows можно скачать здесь (http://build.openvpn.net/downloads/releases/) . Например, tap-windows-9.24.5.zip.
Перед установкой нужно удалить существующий сетевой адаптер TAP и его драйвер. Для этого запустите программу C:Program FilesTAP-WindowsUninstall.exe.
Для установки TAP драйвера используется утилита tapinstall.exe.
Распакуйте архив и запустите установочный файл с правами администратора.
Обязательно проверьте, что новый сетевой адаптер TAP-Windows Adapter появился в списке сетевых подключения в панели управления Windows (консоль ncpa.cpl ).
Вы этом случае можно создать дополнительный WinTap сетевой адаптер с помощью скрипта (bat файл) %ProgramFiles%TAP-Windowsbinaddtap.bat.
В результате в панели управления появится два (или более) сетевых адаптеров TAP-Windows Adapter V9, и вы сможете одновременно установить несколько одновременных OpenVPN сессий с разными серверами.
Источник
OpenVPN Support Forum
Community Support Forum
Exiting due to fatal error
Exiting due to fatal error
Post by jameelb » Mon Nov 20, 2017 7:28 am
I do have a problem setting OpenVPN in my vps.
I did create cert and key, but I do have problem with editing server.ovpn file
#################################################
# Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, e.g.: #
# «C:\Program Files\OpenVPN\config\foo.key» #
# #
# Comments are preceded with ‘#’ or ‘;’ #
#################################################
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# «dev tun» will create a routed IP tunnel,
# «dev tap» will create an ethernet tunnel.
# Use «dev tap0» if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use «dev-node» for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don’t need this.
;dev-node MyTap
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the «easy-rsa» directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see «pkcs12» directive in man page).
ca ca.crt
cert jarat.crt ((((((((((this is my crt name that I did)))))))))
key jarat.key # This file should be kept secret ((((((((((this is my key name that I did)))))))))
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh4096.pem 4096 (((((( I did replace 2048 to 4096 which I have ))))))
dh dh4096.pem
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, i.e. a /30 per client)
# Defaults to net30 (not recommended)
;topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
server 10.8.0.0 255.255.255.0
# Maintain a record of client virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS’s bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 10.8.0.4/255.255.255.0. Finally we
# must set aside an IP range in this subnet
# (start=10.8.0.50 end=10.8.0.100) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS’s bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push «route 213.32.x.xxx 255.255.255.255»
;push «route 213.32.x.xxx 255.255.255.255»
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory «ccd» for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name «Thelonious»
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
;client-config-dir ccd
;route 213.32.x.xxx 255.255.255.255
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious’ private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, i.e. you are
# using «dev tun» and «server» directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 176.31.2xx.xxx 255.255.255.255
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Suppose that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push «redirect-gateway def1 bypass-dhcp»
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
;push «dhcp-option DNS 208.67.222.222»
;push «dhcp-option DNS 208.67.220.220»
# Uncomment this directive to allow different
# clients to be able to «see» each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server’s TUN/TAP interface.
;client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE «COMMON NAME»,
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an «HMAC firewall»
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn —genkey —secret ta.key
#
# The server and each client must have
# a copy of this key.
# The second parameter should be ‘0’
# on the server and ‘1’ on the clients.
tls-auth jarat.key 0 # This file is secret
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that v2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-256-CBC
# Enable compression on the VPN link and push the
# option to the client (v2.4+ only, for earlier
# versions see below)
;compress lz4-v2
;push «compress lz4-v2»
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It’s a good idea to reduce the OpenVPN
# daemon’s privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
;user nobody
;group nobody
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status openvpn-status.log
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the «Program FilesOpenVPNlog» directory).
# Use log or log-append to override this default.
# «log» will truncate the log file on OpenVPN startup,
# while «log-append» will append to it. Use one
# or the other (but not both).
;log openvpn.log
;log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
since I use vps here’s when I write ipconfig in the CMD
- hernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fexx::x919:xxxx:363f:66ac%11
IPv4 Address. . . . . . . . . . . : 213.32.x.xxx
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . : 176.31.2xx.xxx
Can you guys help me with it
Re: Exiting due to fatal error
Post by TinCanTech » Mon Nov 20, 2017 12:44 pm
What is the «Fatal Error» ? (Post your log please)
Re: Exiting due to fatal error
Post by jameelb » Tue Nov 21, 2017 5:09 am
I think I do have errors with the # Configure server mode for ethernet bridging. Also with subnet mask and default gateway.
because I work in VPS so I don’t have local IP like 192.168.0.1 I do have like this when I write command ipconfig
ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fexx::x919:xxxx:363f:66ac%11
IPv4 Address. . . . . . . . . . . : 213.32.x.xxx
Subnet Mask . . . . . . . . . . . : 255.255.255.255
Default Gateway . . . . . . . . . : 176.31.2xx.xxx
and here’s the error when I run server.ovpn
Mon Nov 20 21:08:20 2017 OpenVPN 2.4.4 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO]
[LZ4] [PKCS11] [AEAD] built on Sep 26 2017
Mon Nov 20 21:08:20 2017 Windows version 6.1 (Windows 7) 64bit
Mon Nov 20 21:08:20 2017 library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.10
Источник
Skip to forum content
Форум проекта FreeOpenVPN.Org
Бесплатный VPN-доступ без ограничений
You are not logged in. Please login or register.
Active topics Unanswered topics
Проблема подключения
Pages 1
You must login or register to post a reply
1 23.08.2016 18:36:51
- IMPACT-TWO
- Новичок
- Offline
- Registered: 23.08.2016
- Posts: 4
Topic: Проблема подключения
Tue Aug 23 17:30:27 2016 OpenVPN 2.3.11 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on May 10 2016
Tue Aug 23 17:30:27 2016 Windows version 6.2 (Windows 8 or greater) 64bit
Tue Aug 23 17:30:27 2016 library versions: OpenSSL 1.0.1t 3 May 2016, LZO 2.09
Enter Management Password:
Tue Aug 23 17:30:51 2016 Control Channel Authentication: tls-auth using INLINE static key file
Tue Aug 23 17:30:51 2016 Outgoing Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Tue Aug 23 17:30:51 2016 Incoming Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Tue Aug 23 17:30:51 2016 UDPv4 link local: [undef]
Tue Aug 23 17:30:51 2016 UDPv4 link remote: [AF_INET]46.30.45.178:18930
Tue Aug 23 17:30:51 2016 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Tue Aug 23 17:30:52 2016 VERIFY OK: depth=1, O=57ab796c6b4f9b07af6e5a1a, CN=57ab796c6b4f9b07af6e5a1b
Tue Aug 23 17:30:52 2016 Validating certificate key usage
Tue Aug 23 17:30:52 2016 ++ Certificate has key usage 00a0, expects 00a0
Tue Aug 23 17:30:52 2016 NOTE: —mute triggered…
Tue Aug 23 17:30:53 2016 10 variation(s) on previous 3 message(s) suppressed by —mute
Tue Aug 23 17:30:53 2016 [57ab796c6b4f9b07af6e5a23] Peer Connection Initiated with [AF_INET]46.30.45.178:18930
Tue Aug 23 17:30:55 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue Aug 23 17:30:55 2016 open_tun, tt->ipv6=0
Tue Aug 23 17:30:55 2016 All TAP-Windows adapters on this system are currently in use.
Tue Aug 23 17:30:55 2016 Exiting due to fatal error
Здравствуйте, я вчера начал пользоваться вашим сервисом. (Ну или как его правильно назвать)
Суть проблемы в том, что я не могу подключиться ни к Российскому, ни к Нидерландскому серверу.
Почитал на форуме решение, ни одно не помогло и заметил, что вы владеете магией исправлять ошибки с «не стыковками с сервером и компьютером» помогите, пожалуйста.
2 Reply by Rino 23.08.2016 18:58:55
- Rino
- Moderator
- Offline
- Registered: 20.05.2016
- Posts: 518
Re: Проблема подключения
Здравствуйте.
Ваш провайдер не блокирует порты?
3 Reply by IMPACT-TWO 23.08.2016 19:05:08
- IMPACT-TWO
- Новичок
- Offline
- Registered: 23.08.2016
- Posts: 4
Re: Проблема подключения
Я вчера пользовался без проблем, из этого выходит, что нет.
4 Reply by Rino 23.08.2016 19:06:58
- Rino
- Moderator
- Offline
- Registered: 20.05.2016
- Posts: 518
Re: Проблема подключения
IMPACT-TWO wrote:
Я вчера пользовался без проблем, из этого выходит, что нет.
Попробуйте подключиться через протокол TCP. После отпишитесь здесь, пожалуйста.
Если не подключится, приложите лог.
5 Reply by IMPACT-TWO 23.08.2016 19:10:17
- IMPACT-TWO
- Новичок
- Offline
- Registered: 23.08.2016
- Posts: 4
Re: Проблема подключения
Tue Aug 23 18:08:16 2016 OpenVPN 2.3.11 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on May 10 2016
Tue Aug 23 18:08:16 2016 Windows version 6.2 (Windows 8 or greater) 64bit
Tue Aug 23 18:08:16 2016 library versions: OpenSSL 1.0.1t 3 May 2016, LZO 2.09
Enter Management Password:
Tue Aug 23 18:09:10 2016 Control Channel Authentication: tls-auth using INLINE static key file
Tue Aug 23 18:09:10 2016 Outgoing Control Channel Authentication: Using 256 bit message hash ‘SHA256’ for HMAC authentication
Tue Aug 23 18:09:10 2016 Incoming Control Channel Authentication: Using 256 bit message hash ‘SHA256’ for HMAC authentication
Tue Aug 23 18:09:10 2016 Attempting to establish TCP connection with [AF_INET]46.30.45.178:443 [nonblock]
Tue Aug 23 18:09:11 2016 TCP connection established with [AF_INET]46.30.45.178:443
Tue Aug 23 18:09:11 2016 TCPv4_CLIENT link local: [undef]
Tue Aug 23 18:09:11 2016 TCPv4_CLIENT link remote: [AF_INET]46.30.45.178:443
Tue Aug 23 18:09:11 2016 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Tue Aug 23 18:09:14 2016 VERIFY OK: depth=1, O=57ab796c6b4f9b07af6e5a1a, CN=57ab796c6b4f9b07af6e5a1b
Tue Aug 23 18:09:14 2016 Validating certificate key usage
Tue Aug 23 18:09:14 2016 ++ Certificate has key usage 00a0, expects 00a0
Tue Aug 23 18:09:14 2016 NOTE: —mute triggered…
Tue Aug 23 18:09:15 2016 10 variation(s) on previous 3 message(s) suppressed by —mute
Tue Aug 23 18:09:15 2016 [57ab796c6b4f9b07af6e5a29] Peer Connection Initiated with [AF_INET]46.30.45.178:443
Tue Aug 23 18:09:17 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue Aug 23 18:09:17 2016 open_tun, tt->ipv6=0
Tue Aug 23 18:09:17 2016 All TAP-Windows adapters on this system are currently in use.
Tue Aug 23 18:09:17 2016 Exiting due to fatal error
Я и с TPC и с UPD пытался, но увы и ах.
6 Reply by Rino 23.08.2016 19:22:51
- Rino
- Moderator
- Offline
- Registered: 20.05.2016
- Posts: 518
Re: Проблема подключения
All TAP-Windows adapters on this system are currently in use — т.е. адаптер для соединения уже используется.
Каким образом, неясно.
Перегрузите компьютер, попробуйте подключиться.
Если не поможет, переустановите OpenVPN клиент.
7 Reply by IMPACT-TWO 23.08.2016 20:25:06
- IMPACT-TWO
- Новичок
- Offline
- Registered: 23.08.2016
- Posts: 4
Re: Проблема подключения
Я нашёл решение, я в настройках «Изменение параметров адаптера» периодически выключаю/включаю Hamachi (при включённом Hamachi некоторые локальные игры не играют по настоящей локальной игре) и выключил адаптер, который появился вместе с OpenVPN. Я его включил и всё работает. Извините за мою глупость и за то, что потревожил.
8 Reply by Rino 23.08.2016 20:29:05
- Rino
- Moderator
- Offline
- Registered: 20.05.2016
- Posts: 518
Re: Проблема подключения
Нет проблем! Пользуйтесь.
Posts: 8
Pages 1
You must login or register to post a reply
Hi there, very new to all of this so please try to excuse my lack of knowledge. So, to start off, I just wanted to run OpenVPN for transmission which I got fully working with haugene/transmission-openvpn. Then I heard it is better to just have a single VPN container and run all your other containers through that one, as I wanted to have more containers in the future.
But for the life of me I couldn’t get it to work. The OpenVPN section always exits with a fatal error and just goes into a re-boot loop with the same error every time. So I hope there is somebody that will be able to help me with this issue.
Below are all the files that I think you need to work out whatever I am doing wrong.
Error Log — shortened to just one boot of OpenVPN as they were all the same
vpn_1 | mknod: /dev/net/tun: File exists
vpn_1 | + exec sg vpn -c 'openvpn --cd /vpn --config /vpn/Windscribe-United-Kingdom.ovpn --script-security 2 --redirect-gateway def1 --auth-user-pass /vpn/vpn.auth '
vpn_1 | Tue Jun 2 11:29:47 2020 WARNING: file '/vpn/vpn.auth' is group or others accessible
vpn_1 | Tue Jun 2 11:29:47 2020 OpenVPN 2.4.8 x86_64-alpine-linux-musl [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Feb 7 2020
vpn_1 | Tue Jun 2 11:29:47 2020 library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.10
vpn_1 | Tue Jun 2 11:29:47 2020 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
vpn_1 | Tue Jun 2 11:29:47 2020 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
vpn_1 | Tue Jun 2 11:29:47 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]212.102.63.62:54783
vpn_1 | Tue Jun 2 11:29:47 2020 UDP link local: (not bound)
vpn_1 | Tue Jun 2 11:29:47 2020 UDP link remote: [AF_INET]212.102.63.62:54783
vpn_1 | Tue Jun 2 11:29:47 2020 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
vpn_1 | Tue Jun 2 11:29:47 2020 VERIFY OK: depth=1, C=CA, ST=ON, L=Toronto, O=Windscribe Limited, OU=Operations, CN=Windscribe Node CA
vpn_1 | Tue Jun 2 11:29:47 2020 VERIFY KU OK
vpn_1 | Tue Jun 2 11:29:47 2020 Validating certificate extended key usage
vpn_1 | Tue Jun 2 11:29:47 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
vpn_1 | Tue Jun 2 11:29:47 2020 VERIFY EKU OK
vpn_1 | Tue Jun 2 11:29:47 2020 VERIFY OK: depth=0, C=CA, ST=ON, O=Windscribe Limited, OU=Operations, CN=Windscribe Node Server 4096
vpn_1 | Tue Jun 2 11:29:47 2020 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1602', remote='link-mtu 1550'
vpn_1 | Tue Jun 2 11:29:47 2020 WARNING: 'cipher' is used inconsistently, local='cipher AES-256-CBC', remote='cipher AES-256-GCM'
vpn_1 | Tue Jun 2 11:29:47 2020 WARNING: 'auth' is used inconsistently, local='auth SHA512', remote='auth [null-digest]'
vpn_1 | Tue Jun 2 11:29:47 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
vpn_1 | Tue Jun 2 11:29:47 2020 [Windscribe Node Server 4096] Peer Connection Initiated with [AF_INET]212.102.63.62:54783
vpn_1 | Tue Jun 2 11:29:48 2020 Data Channel: using negotiated cipher 'AES-256-GCM'
vpn_1 | Tue Jun 2 11:29:48 2020 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
vpn_1 | Tue Jun 2 11:29:48 2020 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
vpn_1 | Tue Jun 2 11:29:48 2020 ERROR: Cannot ioctl TUNSETIFF tun: Function not implemented (errno=38)
vpn_1 | Tue Jun 2 11:29:48 2020 Exiting due to fatal error
docker-compose.yml
version: '3.4'
services:
vpn:
image: dperson/openvpn-client
# cap_add, security_opt, and volume required for the image to function
cap_add:
- net_admin
environment:
- TZ='Europe/London'
networks:
- default
# if using '-d' or 'DNS' you can't enable the `read_only: true` option
read_only: true
tmpfs:
- /run
- /tmp
restart: unless-stopped
security_opt:
- label:disable
stdin_open: true
tty: true
volumes:
- 'D:DockerVPNdevnet:/dev/net:z'
- 'D:DockerVPNvpn:/vpn'
organizr:
image: linuxserver/organizr
container_name: organizr
depends_on:
- vpn
network_mode: "service:vpn"
environment:
- PUID=1000
- PGID=1000
- TZ=Europe/London
volumes:
- 'D:DockerOrganizr:/config'
stdin_open: true
tty: true
restart: unless-stopped
web:
image: dperson/nginx
depends_on:
- organizr
environment:
- TZ='Europe/London'
links:
- vpn:organizr
networks:
- default
ports:
- "9936:80"
- "443:443"
read_only: true
tmpfs:
- /run
- /tmp
- /var/cache/nginx
restart: unless-stopped
stdin_open: true
tty: true
command: -w "http://organizr:8888;/organizr"
# service1 shares the network stack of vpn. The service can by reached using
# the name of the service as a hostname.
networks:
default:
I’d also like to note that all the other containers in this stack run without any errors.
Thanks for any help
When starting an OpenVPN server or establishing a new connection using the OpenVPN client, you may encounter an error:
All TAP-Windows adapters on this system are currently in use
Exiting due to fatal error
Or:
All wintun adapters on this system are currently in use or disabled
Or:
No TAP Adapter Available
The error can be displayed in the OpenVPN server log (file C:Program FilesOpenVPNlogopenvpn.log).
Or in the OpenVPN GUI client:
This is a known bug related to the fact that TAP or Wintun virtual network adapters are not installed or do not work correctly in Windows.
In OpenVPN 2.5+, you can use Wintun network adapter (from the developers of WireGuard) instead of the TAP adapter. According to the developers, the Wintun driver is faster than the classic OpenVPN TAP driver. You can choose which network driver to use when installing OpenVPN (TAP-Windows6 or Wintun).
To fix this error, you need to do one of the following (in order from easiest to hardest):
- Restart TAP-Windows/Wintun via the Control Panel;
- Reinstall the TAP-Windows/Wintun driver;
- Create a new virtual network adapter for OpenVPN (or another VPN client).
List all network adapters available to the OpenVPN client:
cd "c:Program FilesOpenVPNbin"
"C:Program FilesOpenVPNbinopenvpn.exe" --show-adaptersIn this case, both Wintun and TAP adapters are installed:
'OpenVPN Wintun' {1199219C-C5AD-4722-B195-C80332101710} wintun
'OpenVPN TAP-Windows6' {9C6B25CA-0AF0-4752-AD4A-032947F6A6FD} tap-windows6<c/ode>
To fix the error, it is usually enough to enable and disable the TAP adapter in the Windows control panel, restart the computer, or reinstall the OpenVPN client.
You can enable and disable the WinTap adapter from the Network Connections (ncpa.cpl). Right-click on the network adapter (TAP-Windows or Wintun Userspace Tunnel) and select Disable. Then re-enable it (Enable.)
You can also restart all OpenVPN TAP network interfaces using PowerShell:
$TapAdapter= Get-NetAdapter| where {$_.InterfaceDescription -like "*TAP-Windows*"}
Disable-NetAdapter -Name $TapAdapter -Confirm:$false
Enable-NetAdapter -Name "$TapAdapter -Confirm:$falseIn rare cases, you need to manually reinstall the TAP virtual adapter. The latest TAP driver for Windows can be downloaded here (http://build.openvpn.net/downloads/releases/). For example, download the file tap-windows-9.24.5.zip.
- Download the latest TAP/Wintun driver for Windows here (http://build.openvpn.net/downloads/releases/). For example, tap-windows-9.24.7.zip or wintun-amd64-0.8.1;
- Extract the archive, open the Device Manager (
devmgmt.msc), right-click on the TAP-Windows Adapter v9 device in the Network Adapters section and select Update driver; - Specify the path to the directory with the TAP driver
If you don’t see TAP-Windows Adapter V9 in the Control Panel, open the Device Manager console and enable the View-> Show hidden device option. If there is an Unknown Device in the Network adapters section, then try opening its properties, go to the Details tab. and check the value of the Device instance path property.
If ROOTNET000 is listed here, then try to automatically search for the driver or manually specify the path to the INF file (for example C:Program FilesOpenVPN Connectdriverstapamd64win10OemVista.inf). After that, your TAP adapter will appear in the network connections.
On Windows 7, a TAP driver signed with SHA256 will not work correctly until you manually install update KB4474419.
In rare cases, a complete re-creation of the OpenVPN TAP/Wintun adapter may help.
First, you need to remove the existing TAP network adapter and its driver. To do this, run C:Program FilesTAP-WindowsUninstall.exe or just uninstall the network adapter from Device Manager (Uninstall device).
The tapinstall.exe utility is used to add the TAP adapter and install driver.
Extract the archive and run the installation file as an administrator.
In modern versions of OpenVPN, the C:Program FilesOpenVPNbintapctl.exe tool should be used to manage virtual network adapters.
List OpenVPN network adapters:
tapctl.exe listRemove OpenVPN virtual network adapter:
tapctl.exe delete "OpenVPN TAP-Windows6"Create a new TAP adapter:
tapctl.exe createCreate a new Wintun adapter:
tapctl.exe create --hwid wintunBe sure to check that the new TAP-Windows Adapter has appeared in the list of network connections in the Windows Control Panel (ncpa.cpl console).
Also, the problem “wintun adapters on this system are currently in use” may occur if you are trying to establish multiple OpenVPN connections from your device. You must create a separate adapter for each VPN connection.
In this case, you can create an additional WinTap network adapter using the batch file %ProgramFiles%TAP-Windowsbinaddtap.bat.
Or using the following command (in current versions of the OpenVPN client):
c:Program FilesOpenVPNbintapctl.exe.tapctl.exe createAs a result, two (or more) TAP-Windows Adapter V9 will appear in the network connections and will be able to establish two simultaneous OpenVPN sessions to different VPN servers.
You can now enable the OpenVPN connection on Windows and configure it to start on startup.
OpenVPN WindowsСтроитьРезюме вопроса
1, в исполнении файла конфигурации, Build-ca.bat и build-dh.bat, следующая ошибка
unable to write ‘random state’
Проверьте это, говорится, что это разрешение, он должен изменить «OpenSSL-1.0.0.cnf» будет изменяться «$ env :: home / .rnd», например, на xx.rnd, например, к «$ env: : Главная / А.rnd. Согласно личной фактической операции, OpenVPN вызван путем установки под Windows, например, не установленным в пути по умолчанию, пространство в пути установки и т. Д. Мое решение выглядит следующим образом:
【Решение】
1) Сначала откройте файл сценариев конфигурации «OpenVPN Easy-RSA vars.bat.sample», и измените его «Установить Home =% Programfiles% OpenVPN Easy-RSA» на ваш сайт APPORVPN, например, Настройка: «Установить Home = D: App OpenVPN Easy-RSA»
2) После завершения модификации запустите CMD в качестве администратора, а затем выполните сценарий конфигурации Шаг на шаг за шагом.
2, после успешной конфигурации, будь то сервер OpenVPN GUI или Client OpenVPN GUI для подключения к следующей ошибке:
Insufficient key material or header text not found in file ‘ta.key’ (0/128/256 bytes found/min/max)
Exiting due to fatal error
【Решение】
Метод 1: Изменить «D: app openvpn config server.ovpn» Примечание «tls-auth ta.key 0 # This file is secret”Писание. следующее:
Прежде чем изменить:
tls-auth ta.key 0 # This file is secret
После изменения:
# tls-auth ta.key 0 # This file is secret
Способ 2: Создайте файл TA.Key. Выполните следующее утверждение:
D:appOpenVPNbinopenvpn —genkey —secret keysta.key
Скопируйте генерируемый TA.Key к каталогу конфигурации на основе сервера.
3, Клиентские газеты: Маршрут: Дополнение маршрута Неудачная продажа CreateiPForwordentry: хотя бы один параметр неверный
【Причина анализ】
Такая ситуация, в основном из-за комментария“tls-auth ta.key 0 # This file is secret”Функция.
【Решение】
Метод 1: Создайте файл TA. KKE. Выполните следующее утверждение:
OpenVPNbinopenvpn —genkey —secret keysta.key
Скопируйте генерируемый TA.Key к каталогу конфигурации на основе сервера.
Метод 2: Во-первых, убедитесь, что «TLS-Auth Ta.Key 0 # этот файл является секретом», прокомментирован в файле конфигурации Client.ovpn, затем измените профиль Client.ovpn и добавьте следующие две операторы строки в файл :
route-method exe
route-delay 2
4. После того, как сервер успешно запущен, он может быть подключен нормально, но отчет неверно:
Could not determine IPv4/IPv6 protocol. Using AF_INET6
Я не знаю почему.
5, отчет промокол не удалось по ошибке интерфейса
【Решение】
Запустить openvpn как администратор
6, Предупреждение о докладах: Шлюз маршрута не достижима в любой ошибке активных сетевых адаптеров
【Решение】
Запустите CMD в качестве администратора, выполните:
netsh int ip reset logfile.txt
netsh winsock reset catalog
Затем перезагрузите машину