- Remove From My Forums
-
Question
-
I just noticed we have a couple of windows 2008 SP2 32 bits servers (some of them are upgraded from Windows 2003 server) it shows «Compliant» in the Compliance report. But actually since sept 2016, no any new updates were installed on these servers.
In the client servers, you won’t see any patches regarding windows 2008 sp2 in software center. Same, software update group, other Windows 2008 sp2 can see lots of patches and installed successfully every month.I have tried uninstall and reinstall the SCCM client on the servers, but doesn’t work.
Here is the part of the «UpdatesDeployment log»
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_3e2fd768-3492-48a2-aba5-601f1daf34a6) added to the targeted list of deployment ({ab8111c7-e303-4b51-b8c7-3149be6ac909}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
3080 (0x0C08)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_022f043b-57fb-4017-9239-629e82367a70) added to the targeted list of deployment ({ab8111c7-e303-4b51-b8c7-3149be6ac909}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
3080 (0x0C08)
Failed to attach update to the automation wrapper, error = 0x87d00215 UpdatesDeploymentAgent 7/18/2017 10:52:46 AM 3644 (0x0E3C)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_88718960-31fb-4bd9-9f3c-c005eef1eb27″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent 7/18/2017 10:52:46 AM 3080 (0x0C08)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_88718960-31fb-4bd9-9f3c-c005eef1eb27) added to the targeted list of deployment ({ab8111c7-e303-4b51-b8c7-3149be6ac909}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
3080 (0x0C08)
Failed to attach update to the automation wrapper, error = 0x87d00215 UpdatesDeploymentAgent 7/18/2017 10:52:46 AM 5504 (0x1580)
DetectJob completion received for assignment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM 5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_7499212f-5d2d-4def-8d3b-7dfb8a3dcbe4) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_5222bcce-90fb-4605-9a30-d49b557d2a0e) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_c0549aab-ff1d-45d2-8913-3bafda7662e3) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_69d1f69a-7b06-45a7-b83f-318efcc45d52) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_6b94cdc3-27fa-4e92-baf2-3a14029ad51c) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_e98eeb00-1c94-4a8f-9bdb-ac502b755ee1) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_bfc74d76-3a8f-403a-a4d5-b94d2eac5d7f) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_fba8f906-dfe7-4210-94bc-b9cbd74a613a) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
DetectJob completion received for assignment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM 2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_32e5af4b-fb9f-44f8-b18a-33863ffecd7f) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_b27cf4b3-0b7d-475d-9129-883e6ded6182) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_bfb5d776-d17b-4cc2-8afb-3fe1d004eb3f) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_4809ef80-5f6e-4ef0-a4c3-da892c1e2361) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_b61029f3-d259-40f0-808b-877e00f3e0a9) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_ad5a9460-ad28-4abb-bf5d-177885033c64) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_c0cf4783-03fc-41ca-bf26-bc79546b6330) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_98a9cd9b-7bec-4b80-802d-68acb26d6b81) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_e38966e9-be66-474f-8754-db30468ffeff) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_6b65e1ac-474e-4258-b8b0-e52e4dd4d8dd) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_9cd3d6a0-2474-4577-b7a7-d1ba5234c128) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_4028e69f-9d24-4062-9075-9bbe4df0538e) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_ad5a9460-ad28-4abb-bf5d-177885033c64) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_30abe6e7-12e8-4b96-91be-1b6869602aee) added to the targeted list of deployment ({C2A51A37-0B4F-4DA3-B219-411BFEDE341A}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
2184 (0x0888)
Update (Site_579FA4E9-7164-4F0F-8005-7AD0A23777D3/SUM_98a9cd9b-7bec-4b80-802d-68acb26d6b81) added to the targeted list of deployment ({2c394de0-f80e-4f21-9704-92f9b16998f1}) UpdatesDeploymentAgent 7/18/2017 10:52:46 AM
5384 (0x1508)The only err I can find is «Failed to attach update to the automation wrapper, error = 0x87d00215».
Hi I am also getting error. Extract from log with offending lines:
Message received: ‘<?xml version=’1.0’ ?>
<CIAssignmentMessage MessageType=’Activation’>
<AssignmentID>{433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5}</AssignmentID>
</CIAssignmentMessage>’
UpdatesDeploymentAgent 28/07/2016 11:22:08 PM
10856 (0x2A68)
Assignment {433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5} has total CI = 16
UpdatesDeploymentAgent 28/07/2016 11:22:08 PM
10856 (0x2A68)
Assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5}) received activation trigger
UpdatesDeploymentAgent 28/07/2016 11:22:08 PM
10856 (0x2A68)
Detection job ({B0C9440E-CD4D-48C3-95A9-7A4E65B26D0F}) started for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:08 PM
10856 (0x2A68)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
14556 (0x38DC)
DetectJob completion received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_d88607ab-1a9a-4f09-b920-3fd39d4db172″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_d88607ab-1a9a-4f09-b920-3fd39d4db172) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_e832d18c-6f2c-466b-bb83-57d19bb5ef54) Name (Update for Windows 10 for x64-based Systems (KB3125217)) ArticleID (3125217) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_488f5069-60cf-4fa9-b97b-c3cb378ade49″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_488f5069-60cf-4fa9-b97b-c3cb378ade49) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_8412426c-6bb2-4d5b-af8e-df6744a0ea70″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_8412426c-6bb2-4d5b-af8e-df6744a0ea70) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_f227a554-3fe1-4e74-af64-0bd89596ca41″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_f227a554-3fe1-4e74-af64-0bd89596ca41) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_7f722a3c-887f-41db-ae8a-a0fee28b4ae5) Name (Cumulative Update for Windows 10 for x64-based Systems (KB3163912)) ArticleID (3163912) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_22658655-0e69-4d2c-ace5-64d42eeb0e6f», actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_22658655-0e69-4d2c-ace5-64d42eeb0e6f) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_ac8d2656-7f38-4645-9b76-b43bc0f125bd», actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_ac8d2656-7f38-4645-9b76-b43bc0f125bd) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_4ca2bada-86c7-482c-952d-b775af564d4b», actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
13668 (0x3564)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_4ca2bada-86c7-482c-952d-b775af564d4b) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_7f415d14-9086-441a-8e1a-08cf818a3082″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_7f415d14-9086-441a-8e1a-08cf818a3082) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_fa87a527-dc20-48c7-88f7-8afded1cc667) Name (Security Update for Adobe Flash Player for Windows 10 for x64-based Systems (KB3174060)) ArticleID (3174060) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_5a3a209a-4cab-4094-ac31-f7f774b7a7e7″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_5a3a209a-4cab-4094-ac31-f7f774b7a7e7) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_75528011-1e8a-4a3e-9543-030c7d5074d7″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_75528011-1e8a-4a3e-9543-030c7d5074d7) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_4a357632-0a3c-42f3-8f03-f46fb7647ddd», actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_4a357632-0a3c-42f3-8f03-f46fb7647ddd) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_e37fe62f-f4e3-491d-81b7-f21c0f1a1d6c) Name (Update for Windows 10 for x64-based Systems (KB3173427)) ArticleID (3173427) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID=»Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_fdec3740-d6b2-4856-bb33-f936626811a7″, actionType 12l, value NULL, user NULL, session 4294967295l, level 0l,
verbosity 30l UpdatesDeploymentAgent
28/07/2016 11:22:13 PM 12052 (0x2F14)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_fdec3740-d6b2-4856-bb33-f936626811a7) added to the targeted list of deployment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
18164 (0x46F4)
DownloadCIContents Job ({F9B89F70-1897-447A-8CF1-FB9C6FC69DE2}) started for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
12052 (0x2F14)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
8440 (0x20F8)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
8440 (0x20F8)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
5960 (0x1748)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:13 PM
14556 (0x38DC)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_e832d18c-6f2c-466b-bb83-57d19bb5ef54) Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_7f722a3c-887f-41db-ae8a-a0fee28b4ae5) Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_fa87a527-dc20-48c7-88f7-8afded1cc667) Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_e37fe62f-f4e3-491d-81b7-f21c0f1a1d6c) Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
8440 (0x20F8)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
7192 (0x1C18)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
14556 (0x38DC)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
5960 (0x1748)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
7532 (0x1D6C)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
7532 (0x1D6C)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
8440 (0x20F8)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
5960 (0x1748)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
8440 (0x20F8)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
8440 (0x20F8)
Failed to attach update to the automation wrapper, error = 0x87d00215
UpdatesDeploymentAgent 28/07/2016 11:22:14 PM
18164 (0x46F4)
Progress received for assignment ({433F4DFF-62EC-4B7B-BCB8-C2D4D8BFDDA5})
UpdatesDeploymentAgent 28/07/2016 11:23:36 PM
4240 (0x1090)
Update (Site_C16F4129-6AA8-43D3-BCAA-A455A1D1E130/SUM_e832d18c-6f2c-466b-bb83-57d19bb5ef54) Progress: Status = ciStateDownloading, PercentComplete = 50, Result = 0x0
UpdatesDeploymentAgent 28/07/2016 11:23:36 PM
4240 (0x1090)
- Status
- Not open for further replies.
-
#1
Hi,
We have a newly setup MECM server and planning to update it with the latest july 20h2 update. However, the deployment status keeps UNKNOWN -greyed status and failed to install to all pilot pcs. Wsyncmgr n wuahandler logs shows no issues as the updates are able to be sync successfully.
The software updatese did not delivered to ccmcache as it should but it has advertise in the software compliance .
Boundaries were set directly to primary server.
add info : http://mecmserver: 8530/ 403 — Forbidden: Access is denied.
any suggestion where should I look into to start remediating. Thank you
updatesdeployment.logs error below :
-
#2
Failed to get targeted update error = 0x87d00215. 0x87d00215, it means «Item not found». Do you have enough disk space on the remote DP? No Maintenance Windows on the device collection?
-
Thread Starter
-
#3
Thanks guys. found the issue was due to access previlages
-
#4
Glad to hear that issue is fixed. Marking this thread as Solved.
- Status
- Not open for further replies.
Содержание
- Getupdateinfo failed to get targeted update error 0x87d00215
- Answered by:
- Question
- Getupdateinfo failed to get targeted update error 0x87d00215
- Answered by:
- Question
- Answers
- All replies
- Getupdateinfo failed to get targeted update error 0x87d00215
- Answered by:
- Question
- Answers
- All replies
- Updates Deployment 0x87d00215 error
- 6 answers
Getupdateinfo failed to get targeted update error 0x87d00215
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
I have just installed SCCM 2012 on VM running Server 2012.
I am trying to deploy it on this local machine and keep getting this error (snippet)
I checked my MP setup and it looks fine:
====================================================================
SMSMP Setup Started.
Parameters: C:Program FilesMicrosoft Configuration Managerbinx64rolesetup.exe /install /siteserver:ARV-VM01 SMSMP 0
Installing Pre Reqs for SMSMP
======== Installing Pre Reqs for Role SMSMP ========
Found 2 Pre Reqs for Role SMSMP
Pre Req MSXML60 found.
No versions of MSXML60 are installed. Would install new MSXML60.
Enabling MSI logging. msxml6_x64.msi will log to C:Program FilesMicrosoft Configuration Managerlogsmsxml6_x64MSI.log
Installing C:Program FilesMicrosoft Configuration Managerbinx640000409msxml6_x64.msi
msxml6_x64.msi exited with return code: 0
msxml6_x64.msi Installation was successful.
Pre Req SqlNativeClient found.
SqlNativeClient already installed (Product Code: <49d665a2-4c2a-476e-9ab8-fcc425f526fc>). Would not install again.
Pre Req SqlNativeClient is already installed. Skipping it.
======== Completed Installation of Pre Reqs for Role SMSMP ========
Installing the SMSMP
Passed OS version check.
IIS Service is installed.
SMSMP already installed (Product Code: ). Upgrading/Reinstalling SMSMP
New SMSMP is the same product code. This is a minor upgrade.
Enabling MSI logging. mp.msi will log to C:Program FilesMicrosoft Configuration ManagerlogsmpMSI.log
Installing C:Program FilesMicrosoft Configuration Managerbinx64mp.msi REINSTALL=ALL REINSTALLMODE=vmaus CCMINSTALLDIR=»C:Program FilesSMS_CCM» CCMSERVERDATAROOT=»C:Program FilesMicrosoft Configuration Manager» USESMSPORTS=TRUE SMSPORTS=80 USESMSSSLPORTS=TRUE SMSSSLPORTS=443 USESMSSSL=TRUE SMSSSLSTATE=0 CCMENABLELOGGING=TRUE CCMLOGLEVEL=1 CCMLOGMAXSIZE=1000000 CCMLOGMAXHISTORY=1
mp.msi exited with return code: 0
Installation was successful.
I have tried removing Distribution Point and putting it back, same error.
Источник
Getupdateinfo failed to get targeted update error 0x87d00215
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
I have a server that is not getting any patches or antivirus updates. All other servers work fine. Only error I see is the following:
failed to get targeted update, error = 0x87d00215.
I already recreated the software distribution folder and reinstalled the SCCM client. Any ideas on what else to check or try? TIA
Answers
Has the Windowsupdate.log scan completed successfully on the machine now ?
Kamala kannan.c| Please remember to click “Mark as Answer” or Vote as Helpful if its helpful for you. |Disclaimer: This posting is provided with no warranties and confers no rights
Actually not that I see. I have the following errors in the windows update log:
WARNING: IsSessionRemote: WinStationQueryInformationW(WTSIsRemoteSession) failed for session 4, GetLastError=2250
WARNING: Failed to get Wu Exemption info from NLM, assuming not exempt, error = 0x80240037
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037.
Currently AUX is enabled — so not show any WU Upgrade notifications.
Источник
Getupdateinfo failed to get targeted update error 0x87d00215
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Answered by:
Question
On two distribution points which have been working fine for six months I am getting now an error: 0x87d00215
Failed to get DP locations as the expected version from MP ‘HTTPS://VRPSCCMPR01.ad’. Error 0x87d00215 ccmsetup 1/3/2018 1:54:40 PM 5948 (0x173C)
MP ‘HTTPS://VRPSCCMPR01.ad’ didn’t return DP locations for client package with the expected version. Retrying in 30 minutes. ccmsetup 1/3/2018 1:54:40 PM 5948 (0x173C)
Next retry in 30 minute(s). ccmsetup 1/3/2018 1:54:40 PM 5948 (0x173C)>
Any idea how to correct this error
Security / System Center Operations Manager 2012 / System Center Configuration Manager 2012 / SQL System Center Operations Manager 2007 / System Center Configuration Manager 2007 R2 / Forefront Client Security / Forefront Identity Manager
Answers
If you have checked the boundary/boundary groups, Please check your package, make sure the client package is available on your DPs.
I suggest you to follow the below link and check:
https://social.technet.microsoft.com/Forums/en-US/c60242ff-4a1a-43ce-9da3-fbc47b82eee5/getdplocations-failed-with-error-0x87d00215?forum=configmanagerapps
I hope this helps you.
Please remember to mark the replies as answers if they help. If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
If you have checked the boundary/boundary groups, Please check your package, make sure the client package is available on your DPs.
I suggest you to follow the below link and check:
https://social.technet.microsoft.com/Forums/en-US/c60242ff-4a1a-43ce-9da3-fbc47b82eee5/getdplocations-failed-with-error-0x87d00215?forum=configmanagerapps
I hope this helps you.
Please remember to mark the replies as answers if they help. If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
Have you distributed the client package to a distribution point, and does the machine fall into a boundary/boundary group associated with the distribution point?
Yes the Client package has already been upgraded automatically on 22,000+ machines.
Yes the machines are Distribution Points Servers used for the past six months they are in the boundaries.
Security / System Center Operations Manager 2012 / System Center Configuration Manager 2012 / SQL System Center Operations Manager 2007 / System Center Configuration Manager 2007 R2 / Forefront Client Security / Forefront Identity Manager
If you have checked the boundary/boundary groups, Please check your package, make sure the client package is available on your DPs.
I suggest you to follow the below link and check:
https://social.technet.microsoft.com/Forums/en-US/c60242ff-4a1a-43ce-9da3-fbc47b82eee5/getdplocations-failed-with-error-0x87d00215?forum=configmanagerapps
I hope this helps you.
Please remember to mark the replies as answers if they help. If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
Thanks still in progress..
Security / System Center Operations Manager 2012 / System Center Configuration Manager 2012 / SQL System Center Operations Manager 2007 / System Center Configuration Manager 2007 R2 / Forefront Client Security / Forefront Identity Manager
If you have checked the boundary/boundary groups, Please check your package, make sure the client package is available on your DPs.
I suggest you to follow the below link and check:
https://social.technet.microsoft.com/Forums/en-US/c60242ff-4a1a-43ce-9da3-fbc47b82eee5/getdplocations-failed-with-error-0x87d00215?forum=configmanagerapps
I hope this helps you.
Please remember to mark the replies as answers if they help. If you have feedback for TechNet Subscriber Support, contact tnmff@microsoft.com.
Thanks still in progress..
Security / System Center Operations Manager 2012 / System Center Configuration Manager 2012 / SQL System Center Operations Manager 2007 / System Center Configuration Manager 2007 R2 / Forefront Client Security / Forefront Identity Manager
Good Catch the boundary group was missing, adding one it works and the client is properly upgraded now
Security / System Center Operations Manager 2012 / System Center Configuration Manager 2012 / SQL System Center Operations Manager 2007 / System Center Configuration Manager 2007 R2 / Forefront Client Security / Forefront Identity Manager
Источник
Updates Deployment 0x87d00215 error
I am trying to install Updates on my machines, but no luck.
I created a new Update for Win 10 machines: created a SW Update Group, created a new package, downloaded this updates to this new package and distribute de package to my Distribution Point.
My DP status show success to package deployment.
Now I deploy the SW Update Group to my desktop Collections with Win 10.
I update my client using actions in SCCM Client.
But, my Software Center is show empty for Updates and my client UpdatesDeployment.log is showing this:
More info from the desktop machine:
- Local WSUS policy in pointing to my SUP, it is right
- My SCCM Client is green and inventory is working fine
More info from my DP:
- Package content is there, I validade that
- Other packages, lipe APP packages are there too
- IIS is working fine
Please, any ideias what is happening?
@Patrick Mor
Thanks for your posting on Q&A.
What is the version of your MECM? How many clients in the collection encountered this issue? What are the KB numbers of the software updates you are tried to deploy? Please make sure the updates are required for the clients before moving on.
Please to try to review the scanagent.log and PolicyEvaluator.log on the client to get more error information.
Best regards,
Rita
6 answers
Thanks for the sharing for the logs. I don’t see any obvious errors or issues. There is an error in updatesdeployment log, but more on that later. Do you have maintenance windows configured by any chance? Can you check servicewindow log?
Updates will not download and install unless there is a service window available. You didn’t confirm if a service window is available or not.
Are you sure this is accurate 100% of the time? If the deployment was configured with ‘User Experience’ menu option ‘Deadline Behavior’ with a value of ‘Software updates installation’, would this skip evaluating maintenance windows altogether?
Is the update applicable? Maybe look under wuahandler, scanagent logs as well.
*****WSUSLocationUpdate received for location request guid= <780253aa-2a5c-4666-abeb-ce20e2e56806>ScanAgent 3/17/2022 10:49:19 PM 11720 (0x2DC8)
CScanJobMgr::UpdateSUPLocationList- Original WUA location count is 0, new location count is 1, WUA locations updated. ScanAgent 3/17/2022 10:49:19 PM 11720 (0x2DC8)
Sources are current and valid. TTLs are however, invalid. ScanAgent 3/17/2022 10:49:19 PM 11720 (0x2DC8)
ScanJob(<9761a3d1-f372-4513-9545-1b36b834dbc3>): Performing Full Scan. ScanAgent 3/17/2022 10:49:19 PM 11720 (0x2DC8)
*****ScanByUpdates request received with ForceReScan=0, ScanOptions=0x00000008, WSUSLocationTimeout = 604800 ScanAgent 3/17/2022 10:49:21 PM 5152 (0x1420)
- — -Evaluating Update Status. ScanAgent 3/17/2022 10:49:22 PM 5152 (0x1420)
Found CategoryID of :b3c75dc1-155f-4be4-b015-3f1a91758e52 for Update:5a0aea9e-a1aa-43c7-99a7-e0ee07340d50 ScanAgent 3/17/2022 10:50:59 PM 5152 (0x1420)
CScanAgent::ScanByUpdates — Found UpdateClassification 3689bdc8-b205-4af4-8d4a-a63924c5e9d5 for Update:5a0aea9e-a1aa-43c7-99a7-e0ee07340d50 ScanAgent 3/17/2022 10:50:59 PM 5152 (0x1420)
ScanJob(<9761a3d1-f372-4513-9545-1b36b834dbc3>): Scan Succeeded, Resetting Source to Current and TTLs to Valid ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4)
ScanJob(<9761a3d1-f372-4513-9545-1b36b834dbc3>): CScanJob::OnScanComplete — Scan completed successfully, ScanType=1 ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4)
ScanJob(<9761a3d1-f372-4513-9545-1b36b834dbc3>): CScanJobManager::OnScanComplete -ScanJob is completed. ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4)
ScanJob(<9761a3d1-f372-4513-9545-1b36b834dbc3>): CScanJobManager::OnScanComplete — Reporting Scan request complete to clients. ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4) - — Calling back to client on Scan request complete. ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4)
CScanAgent::ScanComplete- Scan completion received. ScanAgent 3/17/2022 10:51:00 PM 10948 (0x2AC4)
Sources are current and valid. TTLs are also valid. ScanAgent 3/17/2022 10:51:00 PM 5152 (0x1420)
CScanJobManager::Scan — SKIPPING SCAN and using cached results. ScanAgent 3/17/2022 10:51:00 PM 5152 (0x1420)
CScanJobManager::Scan — Reporting Scan request complete to clients. ScanAgent 3/17/2022 10:51:01 PM 5152 (0x1420) - — -Evaluating Update Status. ScanAgent 3/17/2022 10:51:01 PM 10948 (0x2AC4)
- — Calling back to client on Scan request complete. ScanAgent 3/17/2022 10:51:01 PM 10948 (0x2AC4)
*****Policy Change notification received for ToolUniqueID= ScanAgent 3/18/2022 12:34:15 AM 208 (0x00D0)
Источник
Доброго времени суток!
Подскажите куда копать, уже вторую неделю ни каких подвижек.
Ситуация в следующем: Потребовалось перенести SCCM 2012 R2 SP1 CU2 на платформу 2012 сервера. Имя и код сайта сохранились. Что и было сделано. Но так как 2012 сервер работает только с WSUS 4, роль SUP пришлось переделывать.
Порядок действий:
1. Поднял WSUS без конфигурирования
2. Включил роль SUP.
3. Провел синхронизацию, выполнил задачи авто развертывания обновлений.
На сервере SCCM обновления синхронизированы, нужные выкачаны, развернуты на коллекции, статус на точках распространения — ОК.
Переходим к проблеме собственно. На клиентах ссм обновления после сканирования не доступны.
В UpdateStore.log — например :
Querying update status of 64 updates. UpdatesStore
27.11.2015 10:18:23 2696 (0x0A88)
Queried Update (00584797-4409-4bfe-b89e-53acb5b79618): Status=Installed, Title=Обновление для Windows Server 2012 R2 (KB3078676), BulletinID=, QNumbers=3078676, LocaleID=, ProductID=cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, UpdateClassification = cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, ExcludeForStateReporting=FALSE. UpdatesStore
27.11.2015 10:18:23 2696 (0x0A88)
Queried Update (04f04253-f803-43b8-8b37-6841c614dd9f): Status=Installed, Title=Обновление для системы безопасности Windows Server 2012 R2 (KB3084135), BulletinID=MS15-102, QNumbers=3084135, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Queried Update (096b9d81-332f-4748-a023-7d37a5ea7ecf): Status=Installed, Title=Обновление для Windows Server 2012 R2 (KB3101183), BulletinID=, QNumbers=3101183, LocaleID=, ProductID=cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, UpdateClassification = cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, ExcludeForStateReporting=FALSE. UpdatesStore
27.11.2015 10:18:23 2696 (0x0A88)
Queried Update (13412e0c-7eec-4c31-b03b-876c5fa4a54a): Status=Installed, Title=Обновление для системы безопасности Microsoft .NET Framework 3.5.1 в Windows 8.1 и Windows Server 2012 R2 для 64-разрядных систем (KB3074232), BulletinID=MS15-101, QNumbers=3074232, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Queried Update (150d47ae-3196-4afc-a37e-95d7a2228f15): Status=Installed, Title=Обновление для Windows Server 2012 R2 (KB3096433), BulletinID=, QNumbers=3096433, LocaleID=, ProductID=cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, UpdateClassification = cd5ffd1e-e932-4e3a-bf74-18bf0b1bbd83, ExcludeForStateReporting=FALSE. UpdatesStore
27.11.2015 10:18:23 2696 (0x0A88)
Queried Update (15453dab-ae77-42e0-b752-8c7cc91f280c): Status=Installed, Title=Обновление для системы безопасности Windows Server 2012 R2 (KB3083992), BulletinID=, QNumbers=3083992, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Queried Update (16306add-e04d-4b8d-bf0b-4d14f62ef250): Status=Installed, Title=Обновление для системы безопасности Windows Server 2012 R2 (KB3088195), BulletinID=MS15-111, QNumbers=3088195, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Queried Update (1e495e58-8a3b-404a-9502-cf6dbd7e27a5): Status=Installed, Title=Обновление для системы безопасности Windows Server 2012 R2 (KB3080446), BulletinID=MS15-109, QNumbers=3080446, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Queried Update (1eed8026-af28-49fd-9082-8b6946d6a115): Status=Missing, Title=Обновление для системы безопасности Windows Server 2012 R2 (KB3101246), BulletinID=MS15-122, QNumbers=3101246, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE.
UpdatesStore 27.11.2015 10:18:23
2696 (0x0A88)
Т.е. видно что из 64 развернутых обновлений некоторые требуются для установки.
В UpdatesDeployment.log
Total Updates = 64 UpdatesDeploymentAgent
27.11.2015 11:24:59 5968 (0x1750)
EnumerateUpdates for action (UpdateActionInstall) — Total actionable updates = 13
UpdatesDeploymentAgent 27.11.2015 11:24:59
5968 (0x1750)
CUpdatesJobManager::AnyActiveInstallJobs — Returning false
UpdatesDeploymentAgent 27.11.2015 11:24:59
5968 (0x1750)
Enumerate targeted updates for action = UpdateActionInstall
UpdatesDeploymentAgent 27.11.2015 11:36:32
4168 (0x1048)
А в UpdatesHandler.log
Initiating updates scan for checking applicability.
UpdatesHandler 27.11.2015 10:18:10
2696 (0x0A88)
Successfully initiated scan. UpdatesHandler
27.11.2015 10:18:10 2696 (0x0A88)
Updates scan completion received, result = 0x0. UpdatesHandler 27.11.2015 10:18:16
6020 (0x1784)
Updates scan completion received, result = 0x0. UpdatesHandler 27.11.2015 10:18:23
2696 (0x0A88)
Method (Discover) called from SDM. UpdatesHandler
27.11.2015 10:18:23 6020 (0x1784)
Starting job with id = {5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}
UpdatesHandler 27.11.2015 10:18:23
6020 (0x1784)
Initiating Scan. Forced = (0) UpdatesHandler
27.11.2015 10:18:23 6020 (0x1784)
Successfully initiated scan for job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}).
UpdatesHandler 27.11.2015 10:18:23
6020 (0x1784)
Scan completion received for job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}).
UpdatesHandler 27.11.2015 10:18:24
2696 (0x0A88)
Evaluating status of the updates for the job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}).
UpdatesHandler 27.11.2015 10:18:24
2696 (0x0A88)
Successfully sent job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}) success completion to the SdmAgent
UpdatesHandler 27.11.2015 10:18:24
6880 (0x1AE0)
CompleteJob received from SDM. UpdatesHandler
27.11.2015 10:18:24 2696 (0x0A88)
Complete — Job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}) Cleanup.
UpdatesHandler 27.11.2015 10:18:24
2696 (0x0A88)
CompleteJob — Job ({5BCC9F20-2ADB-483F-A0FB-E1DE5852EAFF}) removed from job manager list.
UpdatesHandler 27.11.2015 10:18:24
2696 (0x0A88)
CUpdatesAgent::FinalConstruct entered UpdatesHandler
27.11.2015 11:28:53 6196 (0x1834)
Куда копать не понятно, обновления как бы есть, развернуты, доступны но не выкачиваются на клиенты.
Пробовал скинуть регистрацию машины в базе WSUS через команду wuauclt.exe /resetauthorization /detectnow, но не помогло)
We are trying to deploy updates via WSUS/SCCM through to some test windows 10 machines. I noticed that we were not patched a high enough level so have gone through and installed the hotfixes that were required to decrypt the files.
I’ve then run through the steps here to remove the files:
https://support.microsoft.com/en-us/help/3194588/-0xc1800118-error-when-you-push-windows-10-version-… Opens a new window
I’ve then recreated our Windows 10 service plan and can see the new 1709 download come through and deploy to the distribution points but it will not deploy. It just sits installing in software center.
In the event log I can see the folllowing immediately after the install starts:
In the SCCM logs on the client machine… I get these:
Text
Update 1 (debf641f-97e2-49d1-ad82-26d421804f6b) finished installing (0x80070652), Reboot Required? No WUAHandler 25/10/2017 14:53:46 8880 (0x22B0) Async install completed. WUAHandler 25/10/2017 14:53:46 8880 (0x22B0) Upgrade installation result indicates that commit cannot be done. WUAHandler 25/10/2017 14:53:46 15764 (0x3D94) Installation job encountered some failures. Error = 0x80240022. Commit Result = 0x00000001. WUAHandler 25/10/2017 14:53:46 15764 (0x3D94)
And this:
Text
GetUpdate - failed to get targeted update, error = 0x87d00215. UpdatesDeploymentAgent 24/10/2017 09:17:43 9016 (0x2338) GetUpdate failed, error 87d00215 UpdatesDeploymentAgent 24/10/2017 09:17:43 9016 (0x2338) CCCMUpdatesDeployment::GetUpdate failed, error = 0x87d00215 UpdatesDeploymentAgent 24/10/2017 09:17:43 13636 (0x3544) GetUpdate - failed to get targeted update, error = 0x87d00215. UpdatesDeploymentAgent 24/10/2017 09:17:43 780 (0x030C) GetUpdate failed, error 87d00215 UpdatesDeploymentAgent 24/10/2017 09:17:43 780 (0x030C) CCCMUpdatesDeployment::GetUpdate failed, error = 0x87d00215 UpdatesDeploymentAgent 24/10/2017 09:17:43 10056 (0x2748)
Normal windows updates are working, its just Windows 10. Has anyone else run into these problems?
In this post, we see how to Fix SCCM Client-Side Patching or Software Updates Issues and troubleshooting tips. Let’s go through ConfigMgr Software Updates Troubleshooting Tips, Fix Installation Issues, & Backend Process via the Update Deployment Agent component (UpdateDeployment.log).
I tried to give you an overview of the SCCM patching process using the Update Deployment Agent component. ConfigMgr also provides a solution to third-party application patching as well.
Software updates in SCCM provide a set of tools and resources along with WSUS that can help to manage the task of installing Microsoft patches on Windows 10 devices.
The main topic that I’m going to cover is Servicing Stack Update (SSU) software update deployment mechanism for Windows 10. You can look into other ConfigMgr logs to get a similar kind of flow for each feature.
You need to configure Software Update Point (SUP) and infra setup before starting using the software update feature from ConfigMgr.
➡️SCCM Patch Software Update Deployment Process Guide.
Introduction – Troubleshoot SCCM Patching
In this post, I assume that you already have knowledge of how to configure and deploy software updates to Windows 10 devices. You can learn more about this here -> How to Create Deploy New Software Update Patch Package Using SCCM | ConfigMgr
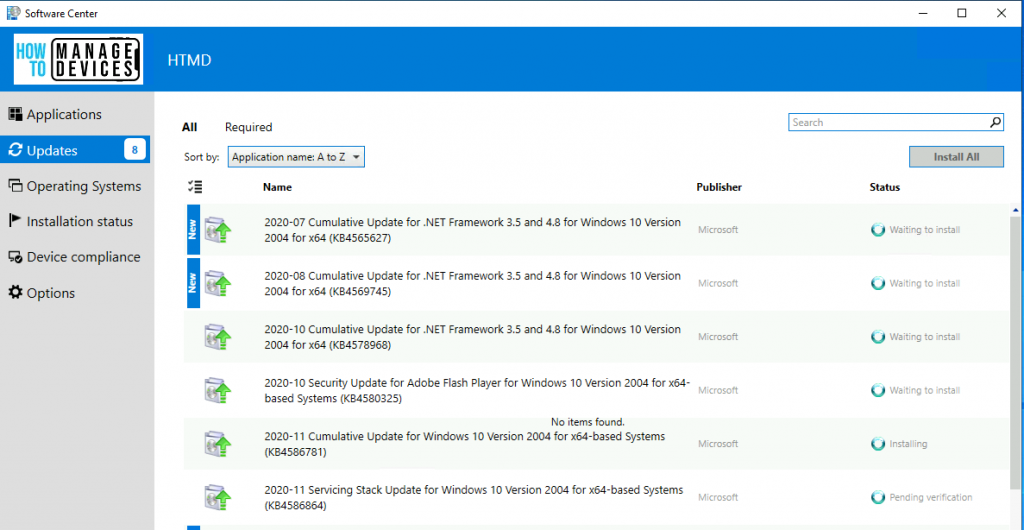
I have already deployed the following software updates to Windows 10 device and now the client is trying to install the updates.
The following process of going through UpdateDeployment.log will help you to understand the background process. Also, this will help you to troubleshoot SCCM patching-related issues.
The flows which you need to check things from SCCM client-side – to Fix SCCM Client-Side Patching or Software Updates Issues.
- UpdateStore.log to know the status of the updates?
- Updatedeployment.log – % of Download completed? Status = ciStateInstalling, PercentComplete = 16,
- added to the targeted list of deployment
- Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
- Progress: Status = ciStateWaitInstall, PercentComplete = 0, DownloadSize = 0, Result = 0x0
- Progress: Status = ciStateInstalling, PercentComplete = 89, DownloadSize = 0, Result = 0x0
- Progress: Status = ciStateInstalling, PercentComplete = 100, DownloadSize = 0, Result = 0x0
- Progress: Status = ciStatePendingSoftReboot, PercentComplete = 0, DownloadSize = 0, Result = 0x0
- Progress: Status = ciStateInstallComplete, PercentComplete = 0, DownloadSize = 0, Result = 0x0
- Job completion received.
- CCMSDKProvider.log – Get client agent settings…Getting reboot setting whether to show dialog instead of notification
More Granular way of SCCM Client-Side Patching Issue Troubleshooting Options
Let’s seen the more granular way of troubleshooting SCCM Client-Side Patching Issue Troubleshooting Options. The SCCM client side log files are located at C:WindowsCCMLogs on Windows 11 or Windows 10 PCs.
1. Locationservices.log – Check whether it’s able to find WSUS Path= and Distribution Point with patches
2. WUAHandler.log to check whether the scan is completed or not
3. Updatedeployment.log – Check for the deadline of the assignment and Software Updates client configuration policy, DetectJob completion received for assignment, Added update (Site_, PercentComplete, etc…
4. Execmgr.log – Execution is complete for program Software Updates Program
5. RebootCoordinator.log – Reboot related things
Added to Targeted List of Deployment
This is the first step handled by the Update Deployment Agent component. You can find these details in the UpdateDeployment.log.
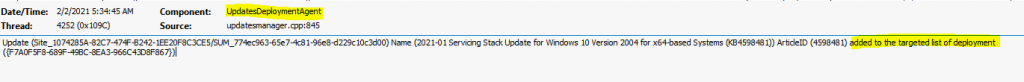
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Name (2021-01 Servicing Stack Update for Windows 10 Version 2004 for x64-based Systems (KB4598481)) ArticleID (4598481) added to the targeted list of deployment ({F7A0F5F8-689F-49BC-8EA3-966C43D8F867})
Start Downloading – Fix SCCM Client-Side Patching or Software Updates Issues
The SCCM Software Update (patching) is going into Downloading state as you can UpdateDeployment.log.
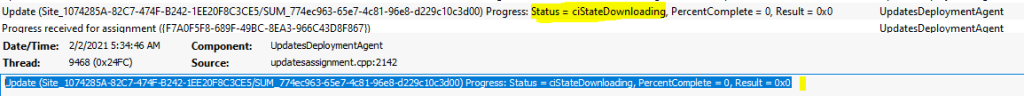
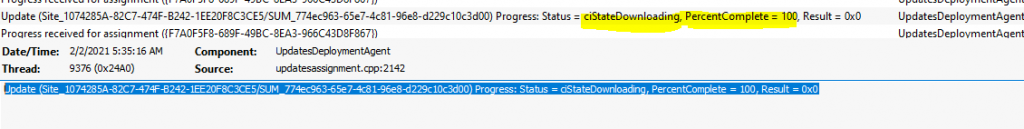
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateDownloading, PercentComplete = 0, Result = 0x0
Download Completed
The Configuration Manager Software Update (patching) is going into Download completed state as you can UpdateDeployment.log. The download percentage completed is 100% as per the log file.
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateDownloading, PercentComplete = 100, Result = 0x0
Waiting to Install
This is the next stage for patch installation using ConfigMgr (a.k.a) and WSUS. The update goes into the waiting to install stage or in the queue to get installed.
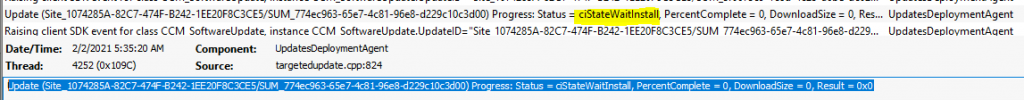
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateWaitInstall, PercentComplete = 0, DownloadSize = 0, Result = 0x0
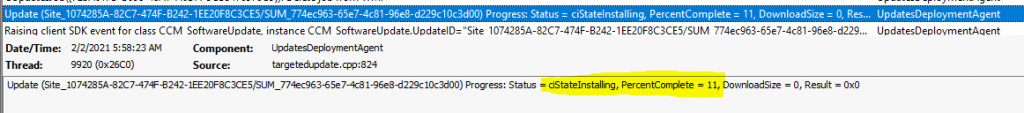
Installing
Now, the patch/software update is getting into installing stage. It also gives the indication of the Percentage completed (11%) as you can in the UpdateDeployment.log.
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateInstalling, PercentComplete = 11, DownloadSize = 0, Result = 0x0
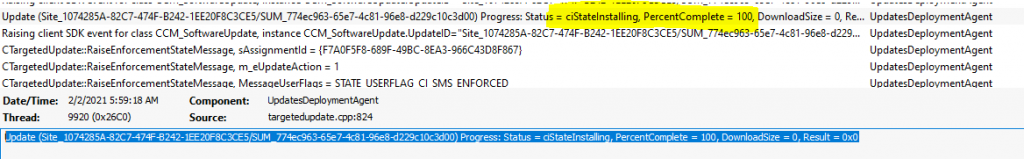
Installation Completed
Let’s check how to confirm whether one patch/software update got installed successfully or installation is completed successfully. You can refer to UpdateDeployment.log and check for the key word – Progress: Status = ciStateInstalling, PercentComplete = 100, DownloadSize = 0, Result = 0x0.
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateInstalling, PercentComplete = 100, DownloadSize = 0, Result = 0x0
Enforcement Message – Fix SCCM Client-Side Patching or Software Updates Issues
This message in the Update Deployment log file is important. The installation (enforcement state message for installation state) was successful and a Reboot is pending.
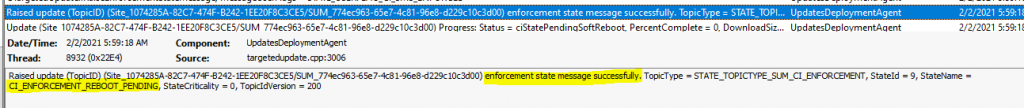
Raised update (TopicID) (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) enforcement state message successfully. TopicType = STATE_TOPICTYPE_SUM_CI_ENFORCEMENT, StateId = 9, StateName = CI_ENFORCEMENT_REBOOT_PENDING, StateCriticality = 0, TopicIdVersion = 200
Soft Reboot Pending
This is the message you can see in the updatedeployment.log file to confirm whether there is any reboot pending for the patch deployment using SCCM. The keyword that you can look for is Status = ciStatePendingSoftReboot.
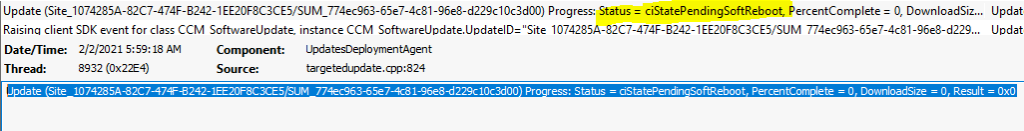
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStatePendingSoftReboot, PercentComplete = 0, DownloadSize = 0, Result = 0x0
Get Assignment Priority
You can also check the assignment priority for a patch or software update from UpdateDeployment.log when you are using SCCM/WSUS for the installation of patches. The keyword that you have to look into is GetAssignmentPriority. The assignment priority for SSU is #1.
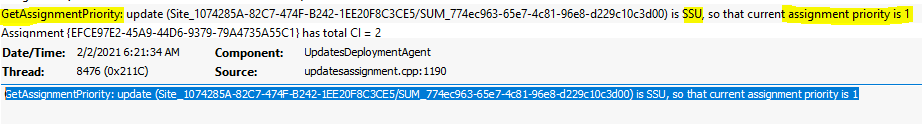
GetAssignmentPriority: update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) is SSU, so that current assignment priority is 1
Successful Installation SCCM Software Update Client-Side Troubleshooting
This is the step after the restart of the Windows 10 device. The ConfigMgr patch installation got completed. The keywords are CI_ENFORCEMENT_SUCCESSFULL & Progress: Status = ciStateInstallComplete.
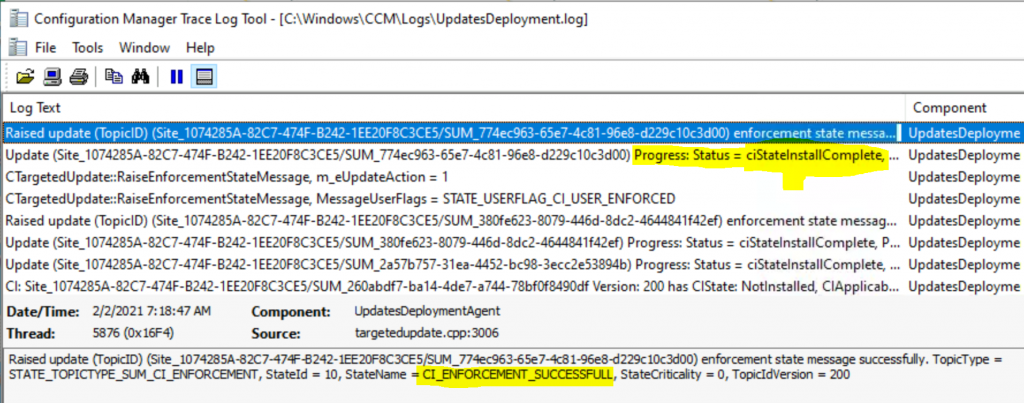
Raised update (TopicID) (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) enforcement state message successfully. TopicType = STATE_TOPICTYPE_SUM_CI_ENFORCEMENT, StateId = 10, StateName = CI_ENFORCEMENT_SUCCESSFULL, StateCriticality = 0, TopicIdVersion = 200
Update (Site_1074285A-82C7-474F-B242-1EE20F8C3CE5/SUM_774ec963-65e7-4c81-96e8-d229c10c3d00) Progress: Status = ciStateInstallComplete, PercentComplete = 0, DownloadSize = 0, Result = 0x0
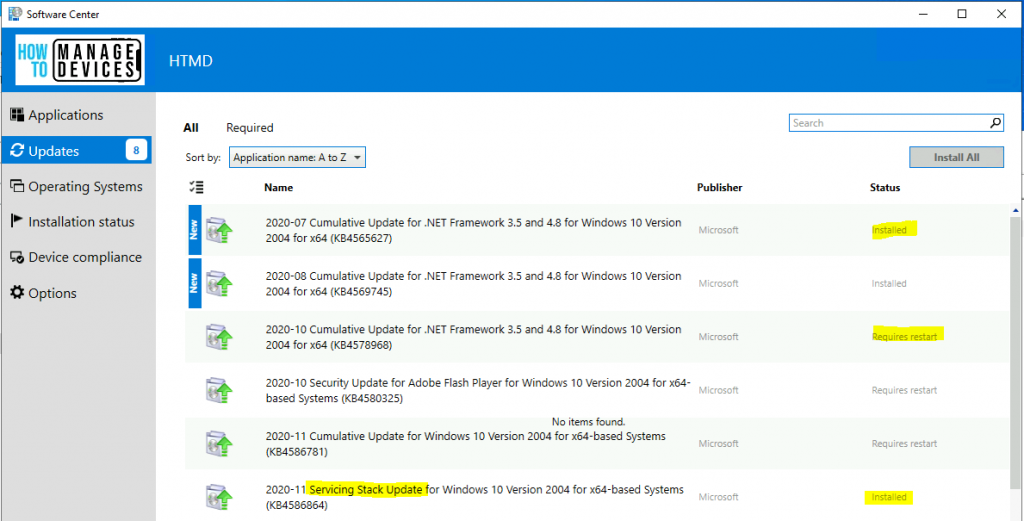
Results – SCCM Client-Side Patching Troubleshooting
All the updates/patches will get disappeared from the software center after the restart and successful installation of patches/updates.
Bonus Tip – Error 0x87d00215
There is a strange issue with SCCM (2107) and the devices are showing scanned for patches means missing patch information. The following thread in the HTMD Forum helped to resolve the error 0x87d00215.
Error 0x87d00215 means – Item not found. It ended up being an expired cert on the server. After renewing it started working again.
- Reference – SCCM – SUG Not Reporting Back Correctly – HTMD Forum (howtomanagedevices.com)
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.