— ОШИБКА:
Не удалось отправить широковещательное сообщение ‘bc-check-dc:.domena.net’:Сеть недоступна
—
Сеть не настроена или настроена не полностью:
Настройка сети через interfaces:
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address i.i.i.i
netmask 255.255.m.m
gateway g.g.g.g
Если во время настройки и перезагрузки сети появляются ошибки, например «Failed to bring up eth0», то можно «очистить» интерфейс командой:
ip addr flush eth0
ald-client join
— ОШИБКА:
Не удалось отправить широковещательное сообщение ‘bc-check-dc:.da’: Сеть недоступна
—
— ОШИБКА:
Astra Linux Directory не сконфигурирована.
Заполните конфигурационный файл ‘/etc/ald/ald.conf’.
Не указан gateway в настройках сети клиента.
Не заполнен /etc/ald/ald.conf
ald-client join
— ОШИБКА:
Не удалось отправить широковещательное сообщение ‘bc-check-dc:.da’: Сеть недоступна
—
— ПРЕДУПРЕЖДЕНИЕ:
ALD сервер домена ‘.da’ не обнаружен.
—
— ОШИБКА:
Не удалось отправить широковещательное сообщение ‘bc-check-dc:.da’: Сеть недоступна
—
Не указан gateway в настройках сети клиента.
ald-client status
— ОШИБКА:
Не удалось отправить широковещательное сообщение ‘bc-check-dc:.da’: Сеть недоступна
—
— ПРЕДУПРЕЖДЕНИЕ:
ALD сервер домена ‘.da’ не обнаружен.
—
Не указан gateway в настройках сети клиента.
ald-client join server.da
— ПРЕДУПРЕЖДЕНИЕ:
Ошибка разрешения имени компьютера ‘server.da’.
—
Некорректно настроены имя и ip адрес, например в /etc/hosts отсутствует длинное имя машин:
127.0.0.1 localhost 192.168.1.1 myserver 192.168.1.2 client
ald-init init
— ОШИБКА:
Триггер ‘ald-cfg-nfs:DoNFSInitFS’ вызвал исключение!
Ошибка RPC: Ошибка Krb5 сервера ALD: Ошибка проверки сообщения KRB-PRIV. в ADKrb5Server.cpp:248(decode)
:> Incorrect net address
:> (rpc-creds)
—
Ошибка может быть вызвана применением антивируса или изменением правил iptables.
ald-init init или ald-client join
— ОШИБКА: Ошибка аутентификации пользователя ‘admin/admin’: Ошибка MIT Kerberos V5:
Ошибка инициализации интерфейса администрирования kadm5. в ALDKadm5Connection.cpp:345(ConnectPassword)
:> GSS-API (or Kerberos) error
—
Некорректно настроены имя и ip адрес, например в /etc/hosts (разрешение имен может быть настроено и с помощью сервера DNS) следует указать ip, длинное и короткое имя и исключить запись «127.0.1.1 myserver»:
127.0.0.1 localhost 192.168.1.1 myserver.example.ru myserver 192.168.1.2 client.example.ru client
В /etc/ald/ald.conf не указаны длинное имя машины и домен:
DOMAIN=.example.ru SERVER=myserver.example.ru
Недостаточно энтропии во время инициализации домена.
- При вводе клиента (ald-client join), ошибка(345) возникает из-за несовпадения времени на машинах.
Утилита hostname должна выдавать короткое имя. После внесения изменений в файл /etc/hostname необходимо перезагрузить машину.
ald-init init или ald-client join
— ОШИБКА:
Ошибка OpenLDAP при GSSAPI соединения — Local error в ALDLDapConnection.cpp:734(Connect)
:> SASL(1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server ldap/dc.test.test not found in Kerberos database)
—
Разрешение имен настроено не верно, перепутаны местами длинное и короткое имя, пример:
127.0.0.1 localhost 192.168.1.1 myserver myserver.example.ru 192.168.1.2 client client.example.ru
ald-admin test-integrity —admin=ald-admin
Вход от имени пользователя ‘ald-admin’…
Введите пароль администратора ALD ‘ald-admin’: *
Проверка конфигурации домена…………………………….ok
Проверка модулей LDAP…………………………………..ok
Проверка индексов LDAP………………………………….ok
Проверка ограничений уникальности LDAP……………………ok
Проверка системных принципалов…………………………..— ОШИБКА:
Ошибка RPC: Ошибка MIT Kerberos V5: Не удалось получить список принципалов Kerberos. в ALDKadm5Connection.cpp:924(Principals)
:> Operation requires «list» privilege
:> (rpc-princ-list)
—
После добавления astra-admin в ALLOWED_LOCAL_GROUPS и выполнения ald-init commit-config снять права администратора домена, применить, установить права администратора домена, применить.
- При выполнении: ald-client commit-config
— ОШИБКА:
Ошибка OpenLDAP при запросе ‘cn=client.ru,ou=hosts,dc=ru (objectClass=x-ald-host-object)’ — Can’tcontact LDAP server в ALDLdapConnection.cpp:213(Search)
—
На клиенте в файле /etc/hosts не внесены данные о резервном сервере.
I’m setting up openLDAP with SASL authentification with kerberos.
I got problem with this auth.
First, I get the kerberos ticket with kinit. When I make a klist, the ticket is displayed. So, no problem.
But when I try to make ldapwhoami. I got an error :
[hue@sandbox ~]$ kdestroy
[hue@sandbox ~]$ kinit vishnu
Password for vishnu@MORTO.COM:
[hue@sandbox ~]$ klist
Ticket cache: _FILE:/tmp/krb5cc_1007
Default principal: vishnu@MORTO.COM
Valid starting Expires Service principal
05/29/14 06:42:52 05/29/14 16:42:52 krbtgt/MORTO.COM@MORTO.COM
renew until 06/05/14 06:42:48
05/29/14 06:42:57 05/29/14 16:42:52 ldap/morto.com@MORTO.COM
renew until 06/05/14 06:42:48
[hue@sandbox ~]$ ldapwhoami
SASL/GSSAPI authentication started
ldap_sasl_interactive_bind_s: Other (e.g., implementation specific) error (80)
additional info: SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information ()
I don’t know where to search anymore.
Please, help me.
asked May 29, 2014 at 14:43
VoulzyVoulzy
1,1073 gold badges10 silver badges11 bronze badges
I had the same error message with the missing minor code. While searching for people with similar problems I noticed that this usually has something to do with an inaccessible keytab file.
In my case the problem was the group of the /etc/openldap/ldap.keytab file was root instead of ldap. Other possible problems can be a wrong or missing KRB5_KTNAME path in your slapd options file (/etc/sysconfig/ldap on red hat 6)
answered Jun 3, 2014 at 12:16
3
Hi all,
I’m trying to set up a kickstart that includes registering in the local AD.
I have managed to get it working with my trialruns using CentOS7.
Including using a dedicated KeyTab to register the machine.
/sbin/realm join --verbose --computer-ou="...." example.com
But when I started with a RHEL7 server intended for live use the KeyTab does not work for joining the realm and when I join it manually (with -U ) I can’t log in to the new server using my AD user.
/sbin/realm join -U sysUser@EXAMPLE.COM --verbose --computer-ou="...." example.com
I have verified that the sssd.conf and krb5.conf have the same settings.
Actually every setting I can think of is the same between the two Machines.
I tried setting SELinux to permissive mode but it did not help either.
I can use kinit to authenticate from the cli:
]$ kinit -V myUser@EXAMPLE.COM
Using default cache: /tmp/krb5cc_1000
Using principal: myUser@EXAMPLE.COM
Password for myUser@EXAMPLE.COM:
Authenticated to Kerberos v5
]$
but the sssd service says:
]$ sudo systemctl status sssd -l
● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; vendor preset: disabled)
Drop-In: /etc/systemd/system/sssd.service.d
└─journal.conf
Active: active (running) since Mon 2018-03-05 18:22:42 CET; 1min 33s ago
Main PID: 682 (sssd)
CGroup: /system.slice/sssd.service
├─682 /usr/sbin/sssd -i -f
├─771 /usr/libexec/sssd/sssd_be --domain example.com --uid 0 --gid 0 --debug-to-files
├─924 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --debug-to-files
└─925 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --debug-to-files
Mar 05 18:23:57 my-host@example.com sssd[be[example.com ]][771]: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
Mar 05 18:23:57 my-host@example.com sssd_be[771]: GSSAPI client step 1
Mar 05 18:23:57 my-host@example.com sssd_be[771]: GSSAPI client step 1
/var/log/sssd/sssd_example.com.log is huge even on log-level 3 but this part stands out:
(Mon Mar 5 18:22:44 2018) [sssd[be[example.com]]] [be_run_online_cb] (0x0080): Going online. Running callbacks.
(Mon Mar 5 18:22:44 2018) [sssd[be[example.com]]] [ad_sasl_log] (0x0040): SASL: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)
(Mon Mar 5 18:22:44 2018) [sssd[be[example.com]]] [sasl_bind_send] (0x0020): ldap_sasl_bind failed (-2)[Local error]
(Mon Mar 5 18:22:44 2018) [sssd[be[example.com]]] [sasl_bind_send] (0x0080): Extended failure message: [SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Server not found in Kerberos database)]
(Mon Mar 5 18:22:44 2018) [sssd[be[example.com]]] [sdap_cli_connect_recv] (0x0040): Unable to establish connection [1432158226]: Authentication Failed
Can anyone give me some idea of where I should continue searching?
Thanks.
Regards,
//Samuel
Содержание
- sssd: tkey query failed (dyndns_update) #5383
- Comments
- Footer
- Samba4 DNS bugs
- Stuck joining Ubuntu Studio 22.04.1 to Active Directory
- 1 Answer 1
- Samba4 DNS bugs
- Record of the UNIX Wars
- Monday, March 17, 2014
- generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information ()
- Solution
sssd: tkey query failed (dyndns_update) #5383
On a running NethServer 7.4 with local AD accounts provider an error message is logged to the journal every day at the same hour.
Steps to reproduce
Expected behavior
No error in the journal
Actual behavior
The query matches the same error line in the same hour every day and when sssd is restarted
Components
See also
Thanks to @fasttech and André Wismer
The text was updated successfully, but these errors were encountered:
krb5_realm = DPNET.NETHESIS.IT
default_domain_suffix = dpnet.nethesis.it
The DynDNS update query fails. In journalctl -u sssd :
Samba DC log (increased log level)
tcpdump output, tcpdump -i br0 -s 65535 -w capture.pcap ‘host 192.168.122.55 and port 53’ :
The same issue is reproducible on a plain CentOS7 too.
The «tkey query failed» lines correspond to failed PTR updates. They can be disabled by setting dyndns_update_ptr = false in sssd.conf
However «tsig verify failure» lines still remain. It seems not to be a real issue though:
Unfortunately also TSIG failure is reported as an error, even if server reported success and nsupdate understands it. — https://bugzilla.redhat.com/show_bug.cgi?id=1394320#c9
© 2023 GitHub, Inc.
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
Samba4 DNS bugs
Перодически раз где-то в три дня приходится рестартить самбу, поскольку доменные ПК не могут получить имена других ПК.
DNS_backend=SAMBA_INTERNAL, на всех ПК static ip.
Значение allow dns updates какое стоит? На днях была похожая проблема, правда без потери Kerberos, временно решилось выставлением данного параметра значения nonsecure
Спасибо, попробуем. У меня стояло:
Сосбтвенно, я к тому что данный DC перенесенный с Win2008. И при вывовде samba-tool drs showrepl у меня был некоторый геморой ))
Вот здесь написано, что нужно создать:
Все, разобрался с GUID. По вашему совету выставил nonsecure и пока что-то вроде все ок. Погоняю несколько дней — посмотрю.
Теперь вот такой ВОПРОС: при использовании DNS-бэкенда SAMBA_INTERNAL приходится все компы добавлять в остнастке DNS вручную. Как сделать чтобы сами регистрировались?
Насчет добавления вручную не подскажу, при добавление в домен автоматически добавляются, а без домена, присутствие хоста в записях днс в моем случае не обязательно, поэтому не вникал почему так.
А вообще пришел к выводу что лучше использовать bind.
еще переодически встречал в поисковиках что какая то проблема с зоной local, но о чем конкретно речь там не смотрел.
Источник
Stuck joining Ubuntu Studio 22.04.1 to Active Directory
I am trying to join my freshly installed Ubuntu Studio 22.04.1 to an AD domain hosted on my Synology NAS, by following the instructions in this white paper, starting on page 11 («Joining After Installation via SSSD»).
When I perform the recommended checks on pages 19-20 everything looks fine, but when I run:
as suggested on page 21, I get the expected output as shown in the whitepaper, followed by 5 error messages like this:
The remaining tests on pages 21-24 using sssctl and samba-tool produce the expected results, but when I try to login (from an existing terminal session), I get:
Since the login command is shown entered at what looks like a shell prompt rather than a terminal session prompt, I may have misunderstood the context.
IAC, what can/must I do about the Kerberos errors? Presumably no AD login will be possible without a Kerberos server.
1 Answer 1
I noticed that DNSHostName in the domain contained only the server name of my Ubuntu Studio desktop and not the FQDN. As it proved difficult to change this, I used «realm leave» to remove the client machine from the domain, removed the Computer entry from the Doman Controller (DC) and rejoined the domain. The only thing I am aware of doing differently is that I have left «use_fully_qualified_names = True» in «/etc/sssd/sssd.conf» instead of changing it to «False», an option mentioned at the bottom of page 16 in the whitepaper Now things appear to work as expected. The only peculiarities I have observed are as follows:
- Due to setting the FQDN in «/etc/hostname» as described on page 10 of the whitepaper, both «hostname» and «hostname -f» return the FQDN.
- «dig», «host». «nslookup» and «resolvectl query» all return an address of «127.0.1.1» (from 127.0.0.53#53) regardless of whether they are queried with the simple server name or the FQDN.
- However, reverse lookup works as expected with «dig», «host», «nslookup» and «resolvectl query». All of these return , and .local
None of this seems to cause any problems (so far 😉
Источник
Samba4 DNS bugs
Перодически раз где-то в три дня приходится рестартить самбу, поскольку доменные ПК не могут получить имена других ПК.
DNS_backend=SAMBA_INTERNAL, на всех ПК static ip.
Значение allow dns updates какое стоит? На днях была похожая проблема, правда без потери Kerberos, временно решилось выставлением данного параметра значения nonsecure
Спасибо, попробуем. У меня стояло:
Сосбтвенно, я к тому что данный DC перенесенный с Win2008. И при вывовде samba-tool drs showrepl у меня был некоторый геморой ))
Вот здесь написано, что нужно создать:
Все, разобрался с GUID. По вашему совету выставил nonsecure и пока что-то вроде все ок. Погоняю несколько дней — посмотрю.
Теперь вот такой ВОПРОС: при использовании DNS-бэкенда SAMBA_INTERNAL приходится все компы добавлять в остнастке DNS вручную. Как сделать чтобы сами регистрировались?
Насчет добавления вручную не подскажу, при добавление в домен автоматически добавляются, а без домена, присутствие хоста в записях днс в моем случае не обязательно, поэтому не вникал почему так.
А вообще пришел к выводу что лучше использовать bind.
еще переодически встречал в поисковиках что какая то проблема с зоной local, но о чем конкретно речь там не смотрел.
Источник
Record of the UNIX Wars
It began as a personal voyage through the strange world of systems, network, and storage administration. Original stops were in the usual (Linux/Windows/Unix/OSX/Cisco/Brocade/Juniper) stations, but later on more were added. Please don’t tip the delivery boy. This was never planned to be the ultimate authoritative source of knowledge, but more like quick notes and thoughts to help me remember how to do something. If you learn something by reading this, don’t blame me!
Monday, March 17, 2014
generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information ()
This will be a quick post about something that was biting my ass these last few days and what was the real cause. After you read it, you are welcome to laugh at my expense. Go ahead! I deserve it!
I was working in a kerberos/ldap (linux) server and needed to debug the connection to a given client. The ldap connection uses TLS, GnuTLS specifically since the two machines were ubuntu servers, which means we also had to worry about certs. And since kerberos is in the picture, we need to configure for that. To help in solving other issues, which I should comment about later (at least those were clever problems not like this one), I was running slapd in debug mode,
and that did help solve the other issue I had. Some of you will notice I am also running ldaps (port 636), which I really do not need since TLS should take care of the encryption thingie. But, I digress for this post, so let’s go back on topic. What I then noticed was some very problems with ldap. For instance, if I created a kerberos ticket and then tried to run ldapsearch, I would then get the following error:
Here is what the server sees:
Since I do not have many clever things to talk about and fill the space until the solution, how about if we talk about what some of those lines mean?
- IP=192.168.1.181:44610 (IP=0.0.0.0:389) : Client 192.168.1.181 is connecting from its port 44610 to my port 389.
- oid=1.3.6.1.4.1.1466.20037: Start TLS extended request (per rfc2830).
- BIND : anonymous if we are doing a SIMPLE bind. If we are however doing SASL bind, it is not used.
- tag=97: result from a client bind operation.
As you noticed, at least from reading the title of this post, the error line is this generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information () thingie. Here is where it annoyed me to no end: what minor code? It is supposed to put some kind of message between the parenthesis, like «No principal in keytab matches desired name» or «Ticket expired». Then I would be able to search online for something. Instead, zilch. I could not find a single entry where the minor code parenthesis thingie was empty. Not very helpful today are we?
Solution
So, what was wrong? Me. User error. Do you remember how I was running slapd? Do you also remember the part about kerberos? Well, in the /etc/default/slapd (that’ll be /etc/sysconfig/ldap for you RedHat/CentOS/Fedora folks) I have defined
which means ldap knows then where the keytab containing the ldap service principal hides. Can you see where this is going? No? Let’s look again at how I am running slapd, shall we?
As you can see, I did not pass a KRB5_KTNAME to slapd. As soon as I fed that to slapd, all was once again well in the Land of Ooo.
Источник
Issue
User is able to run a workflow on the local machine and through Designer on the Gallery machine, but the following error is thrown when attempting to load the workflow to the gallery or run it through the gallery:
SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (Internal credentials cache error)
Environment Details
- Alteryx Server
- All versions
- Alteryx Designer with Scheduler
- All versions
- Windows Server OS
- MIT Kerberos with transitive trust with Active Directory
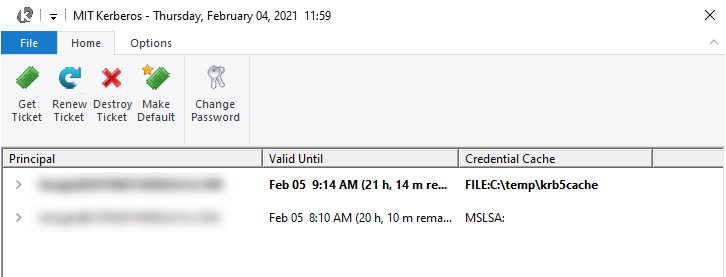
- Ask your Kerberos admin or IT if you have a transitive trust. You likely have this setup if you see two tickets in the MIT Kerberos ticket manager with one pointing to the MSLSA cache:
Cause
Alteryx cannot use the ticket stored in the ticket cache on the server because it cannot access the ticket from the session that the Alteryx service creates to run the Alteryx engine.
Solution A: Use the API ticket cache
The ticket needs to be created in the same session the engine is running in. To do so, use the API cache for the ticket instead of the default ticket location. The API cache holds the credentials in memory for the user rather than writing them to disk.
See the MIT Kerberos documentation for more detail on the different cache types.
1. You will need a keytab file in order to be able to do this. If you don’t have one, work with your Hadoop admin to obtain one.
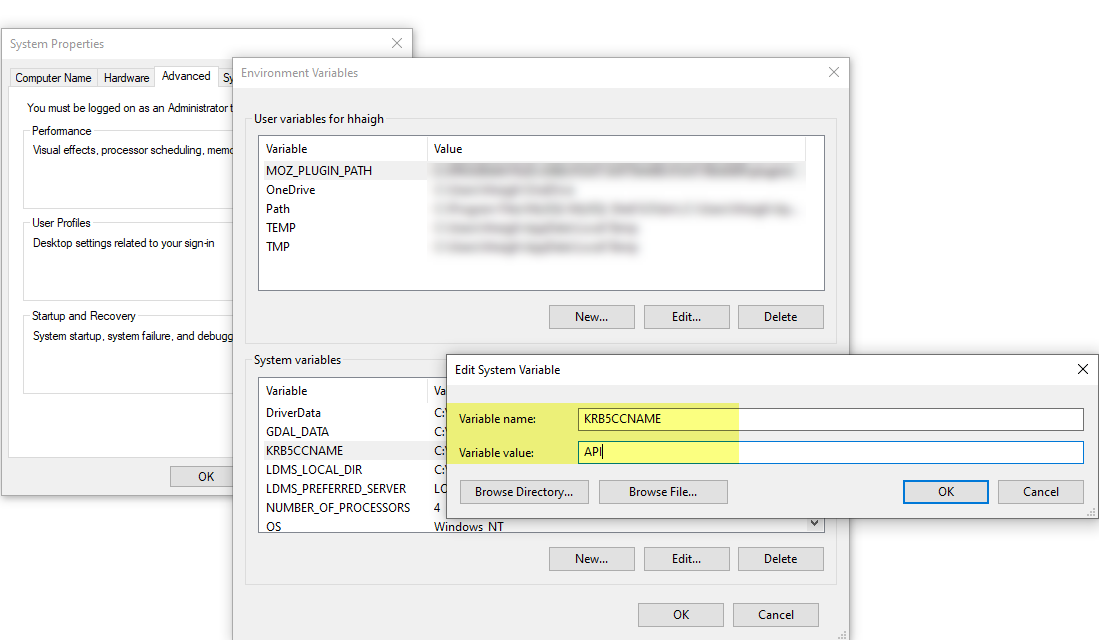
2. Change the KRB5CCNAME environmental variable to point to the API cache rather than a location on disk:
3. Add an event to the workflow to run before the workflow executes to create a ticket.
The command is the kinit command for Kerberos, the command arguments are options for the kinit command.
Command: C:Program FilesMITKerberosbinkinit.exe Command Arguments: -c API -k -t <keytab_file> <kerberos principal>
- -c is the cache name, in this case, we specify API as the cache.
- -k requests a ticket, obtained from a key in the local host’s keytab.
- -t points to the keytab file.
4. If you want to destroy the ticket after running the workflow, you can add a kdestroy event after the workflow finishes running.
Solution B: Change the Kerberos configuration to use Active Directory Kerberos
***NOTE: This option can only be implemented with the Kerberos/Hadoop admin’s help and requires an overall change of the Kerberos configuration and infrastructure. This solution is beyond the scope of Alteryx Support to help implement. The solution is provided to strictly aid with potential solution ideas for your organization to implement along with your organization’s IT support.
Using Active Directory Kerberos (Kerberos SSPI) means that no ticket needs to be created on the server machine because it uses Active Directory as the KDC and no local KDC is required. When used together with workflow credentials, this provides the most seamless option for using Kerberos authentication to Hadoop clusters on a Gallery install.
Once Kerberos has been configured, make sure that the ODBC DSN is configured correctly and works to connect. There is no need for additional configurations in Alteryx.
Additional Information
- SSPI/Kerberos Interoperability with GSSAPI
- MIT Kerberos Site
I’m trying search my company’s AD with ldapsearch. However I always get the error:
ldap_bind: Strong(er) authentication required (8)
additional info: BindSimple: Transport encryption required.
I tried to use LDAPS in every combination possible, but I can’t seem to be able to connect to the server in any other way than just LDAP on the default port.
Weirdly enough I have no issues whatsoever using Active Directory Explorer.
I was thinking that it could be that the firewall isn’t configured correctly and blocking the LDAPS (636) Port, but that wouldn’t explain Active Directory Explorer working…
Also GitLab seems to be able to connect to it just fine too. Except that it won’t authenticate. But that’s what I’m trying to debug with ldapsearch too.
That’s the command I’m using:
ldapsearch -D "cn=myuser,cn=Users,dc=company,dc=local" -w "<password>"
-p 389 -h 10.128.1.254
-b "cn=Users,dc=company,dc=local"
The server is correct, so is the bind_dn (according to Active Directory Explorer) and the corresponding password, I tried using upper an lowercase for the stuff like cn, I tried all possible configurations of using LDAPS (like -H ldaps://10.128.1.254, -H ldaps://10.128.1.254:389, -H ldaps://10.128.1.254:636) and the flag -x, so I’m really running out of ideas.
If it’s relevant, the AD server is the Active Directory Server on Synology/DSM, which is a linux SAMBA server under the hood.
Any help is greatly apprechiated.
UPDATE:
Looks like adding -Y NTLM gets me further.
Now I get:
SASL/NTLM authentication started
ldap_sasl_interactive_bind_s: Invalid credentials (49)
additional info: SASL:[NTLM]: NT_STATUS_OBJECT_NAME_NOT_FOUND
which is weird, as I know the password is correct.
UPDATE 2:
Now using -Y GSSAPI creates this rather nothing saying error:
SASL/GSSAPI authentication started
ldap_sasl_interactive_bind_s: Local error (-2)
additional info: SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_0))
UPDATE 3:
The parameter -ZZ (-Z too) ends with this error:
ldap_start_tls: Connect error (-11)
additional info: The TLS connection was non-properly terminated.