I have installed the ssl certificate and key in my git server. But am getting error when i try to clone via https from my mysysgit. Earlier it was working fine with http. Unable to identify where it is failing
$ git clone https://server.name/git/testing.git
Cloning into 'testing'...
* Couldn't find host server.name in the _netrc file; using defaults
* About to connect() to server.name port 443 (#0)
* Trying server.name...
* Adding handle: conn: 0x274fd60
* Adding handle: send: 0
* Adding handle: recv: 0
* Curl_addHandleToPipeline: length: 1
* - Conn 0 (0x274fd60) send_pipe: 1, recv_pipe: 0
* Connected to server.name(server.name) port 443 (#0)
* successfully set certificate verify locations:
* CAfile: C:Usersuser1AppDataLocalProgramsGit/bin/curl-ca-bundle.crt
CApath: none
* SSL certificate problem: self signed certificate
* Closing connection 0
fatal: unable to access 'https://server.name/git/testing.git/': SSL certificate problem: self signed certificate
asked Sep 27, 2013 at 7:52
1
If you are getting an error while doing a git clone, then above needs to be changed to:
git config --global http.sslVerify false
BuZZ-dEE
5,49410 gold badges65 silver badges94 bronze badges
answered Dec 20, 2013 at 10:36
Pradeep SPradeep S
2,2792 gold badges15 silver badges6 bronze badges
4
You might have to disable the certificate verification in your case:
cd /path/to/repo
git config http.sslVerify false
(as in «Git: ignore a self signed certificate»)
The other option, similar to «Unable to clone Git repository due to self signed certificate» would be to import that certificate into git.
That is: copied it at the end of the file /path/to/git/bin/curl-ca-bundle.crt.
I would not advise git config --global http.sslVerify false, as that would disable certificate verification for all local repositories.
answered Oct 1, 2013 at 11:15
VonCVonC
1.2m508 gold badges4248 silver badges5069 bronze badges
3
Check your .gitconfig file.
If you’ve found the following line, Remove it!
[http]
sslCAinfo = /bin/curl-ca-bundle.crt
It worked for me.
answered Oct 27, 2014 at 9:05
If you’re using a self-signed certificate on your Bitbucket server, you may receive SSL certificate errors when you try to perform certain actions. This page will help you resolve these errors.
Problem
When trying to perform a clone using instructions stated in Debug logging for Git operations on the client the following error is reported:
$ export GIT_CURL_VERBOSE=1
$ git clone https://username@git.example.com/scm/repository.git
Cloning into 'repository'...
* Couldn't find host git.example.com in the _netrc file; using defaults
* Adding handle: conn: 0x22a7568
* Adding handle: send: 0
* Adding handle: recv: 0
* Curl_addHandleToPipeline: length: 1
* - Conn 0 (0x22a7568) send_pipe: 1, recv_pipe: 0
* About to connect() to git.example.com port 443 (#0)
* Trying 10.253.136.142...
* Connected to git.example.com (10.253.136.142) port 443 (#0)
* successfully set certificate verify locations:
* CAfile: C:Program Files (x86)Git/bin/curl-ca-bundle.crt
CApath: c:/Users/username/Downloads
* SSL certificate problem: self signed certificate in certificate chain
* Closing connection 0
fatal: unable to access 'https://username@git.example.com/scm/repository.git': SSL certificate problem: self signed certificate in certificate chain
Cause
This is caused by git not trusting the certificate provided by your server.
Workaround
One possible workaround is to temporary disable SSL check for your git command in case you only need to perform a one time clone:
GIT_SSL_NO_VERIFY=true git clone https://username@git.example.com/scm/repository.git
or
git remote add origin <gitrepo>
git config --global http.sslVerify falseThe workaround is intended to be used for one-time only operations and not to be used frequently. Removing the SSL verification disproves the whole concept of having SSL implemented.
Resolution
Step1: Get a self-signed certificate of the remote server
There is multiple ways of exporting the certificate, Either from the Browser or using the OpenSSL command
Get Certificate using OpenSSL
Get Certificate using OpenSSL
$ echo | openssl s_client -servername NAME -connect HOST:PORT |
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > certificate.pemGet Certificate using the Web browser
Export Certificate in MAC
Trust Certificate in your browser
To trust a self-signed certificate, you need to add it to your Keychain.
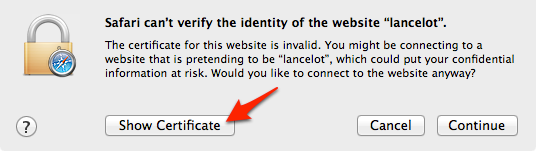
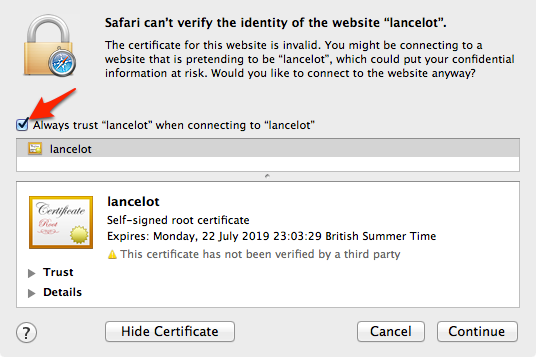
The easiest way to do that is to open the site in question in Safari, upon which you should get this dialog box:
Click ‘Show Certificate’ to reveal the full details:
Export Certificate in .pem format
Git doesn’t use the Mac OS X keychain to resolve this, so you need to trust the certificate explicitly.
- If you haven’t done so already, follow the steps in ‘Trust certificate in your browser, above
- Open Applications > Keychain Access and select ‘Certificates’ in the lower-left pane
- Type the website into the Search field in the top-right
- Select the certificate entry for the website, then in the menu click File > Export Items
- In the Save dialog, change ‘File Format’ to ‘Privacy Enhanced Mail (.pem)’ and save the file somewhere on your drive
Export Certificate From Firefox
- Access the URL of the remote server
- Click the Open padlock in the address bar.
- Click the arrow beside OpenConnection Secure.
- Click More Information. The OpenPage Info dialog box opens.
- Click View Certificate.
- The Certificate page opens.
- Scroll down to the Miscellaneous section.
- In the Download row, click the PEM (cert) link.
- In the dialog box that opens, click OK to save the certificate file to a known location.
- Navigate to the location for saving the file, and then click Save.
Step 2: Configure Git to trust the Certificate
For MAC/Linux:
Once the certificate is saved on the client you can instruct your git client to use it to trust the remote repository by updating the local git config:
# Initial clone
GIT_SSL_CAINFO=/path/to/certificate.pem
git clone https://username@git.example.com/scm/repository.git
# Ensure all future interactions with origin remote also work
cd repository
git config http.sslCAInfo /path/to/certificate.pemFor Windows Client:
Step 1: Import the certificate into the window trust store
Import a signed certificate into the local machine certificate store
- Enter Start | Run | MMC.
- Click File | Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates and click Add.
- Select the Computer account radio button when prompted and click Next
- Select Local computer (selected by default) and click Finish.
- Back in the Add or Remove Snap-ins window, click OK.
- In the MMC main console, click on the plus (+) symbol to expand the Certificate snap-in.
- To import the CA certificate, navigate to Trusted Root Certification Authorities | Certificates pane.
- Right-click within the Certificates panel and click All Tasks | Import to start the Certificate Import wizard.
- On successfully importing the CA certificate the wizard will bring you back to the MMC main console.
- Close the MMC console.
Step 2: Configure git to use the certificate in the windows Trust store
When using Windows, the problem resides that git by default uses the «Linux» crypto backend. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
git config --global http.sslbackend schannelThis means that it will use the Windows certificate storage mechanism and you don’t need to explicitly configure the curl CA storage (http.sslCAInfo) mechanism. Once you have updated the git config, Git will use the Certificate in the Windows certificate store and should not require http.sslCAInfo setting.
HTTPS cloning errors
There are a few common errors when using HTTPS with Git. These errors usually indicate you have an old version of Git, or you don’t have access to the repository.
Here’s an example of an HTTPS error you might receive:
> error: The requested URL returned error: 401 while accessing
> https://github.com/USER/REPO.git/info/refs?service=git-receive-pack
> fatal: HTTP request failed> Error: The requested URL returned error: 403 while accessing
> https://github.com/USER/REPO.git/info/refs
> fatal: HTTP request failed> Error: https://github.com/USER/REPO.git/info/refs not found: did you run git
> update-server-info on the server?Check your Git version
There’s no minimum Git version necessary to interact with GitHub, but we’ve found version 1.7.10 to be a comfortable stable version that’s available on many platforms. You can always download the latest version on the Git website.
Ensure the remote is correct
The repository you’re trying to fetch must exist on GitHub.com, and the URL is case-sensitive.
You can find the URL of the local repository by opening the command line and
typing git remote -v:
$ git remote -v
# View existing remotes
> origin https://github.com/ghost/reactivecocoa.git (fetch)
> origin https://github.com/ghost/reactivecocoa.git (push)
$ git remote set-url origin https://github.com/ghost/ReactiveCocoa.git
# Change the 'origin' remote's URL
$ git remote -v
# Verify new remote URL
> origin https://github.com/ghost/ReactiveCocoa.git (fetch)
> origin https://github.com/ghost/ReactiveCocoa.git (push)Alternatively, you can change the URL through our
GitHub Desktop application.
Provide an access token
To access GitHub, you must authenticate with a personal access token instead of your password. For more information, see «Creating a personal access token.»
If you are accessing an organization that uses SAML SSO and you are using a personal access token (classic), you must also authorize your personal access token to access the organization before you authenticate. For more information, see «About authentication with SAML single sign-on» and «Authorizing a personal access token for use with SAML single sign-on.»
Check your permissions
When prompted for a username and password, make sure you use an account that has access to the repository.
Tip: If you don’t want to enter your credentials every time you interact with the remote repository, you can turn on credential caching. If you are already using credential caching, please make sure that your computer has the correct credentials cached. Incorrect or out of date credentials will cause authentication to fail.
Use SSH instead
If you’ve previously set up SSH keys, you can use the SSH clone URL instead of HTTPS. For more information, see «About remote repositories.»
Error: Repository not found
If you see this error when cloning a repository, it means that the repository does not exist or you do not have permission to access it. There are a few solutions to this error, depending on the cause.
Check your spelling
Typos happen, and repository names are case-sensitive. If you try to clone git@github.com:user/repo.git, but the repository is really named User/Repo you will receive this error.
To avoid this error, when cloning, always copy and paste the clone URL from the repository’s page. For more information, see «Cloning a repository.»
To update the remote on an existing repository, see «Managing remote repositories».
Checking your permissions
If you are trying to clone a private repository but do not have permission to view the repository, you will receive this error.
Make sure that you have access to the repository in one of these ways:
- The owner of the repository
- A collaborator on the repository
- A member of a team that has access to the repository (if the repository belongs to an organization)
Check your SSH access
In rare circumstances, you may not have the proper SSH access to a repository.
You should ensure that the SSH key you are using is attached to your personal account on GitHub. You can check this by typing
the following into the command line:
$ ssh -T git@github.com
> Hi USERNAME! You've successfully authenticated, but GitHub does not
> provide shell access.If the repository belongs to an organization and you’re using an SSH key generated by an OAuth App, OAuth App access may have been restricted by an organization owner. For more information, see «About OAuth App access restrictions.»
For more information, see Adding a new SSH key to your GitHub account.
Check that the repository really exists
If all else fails, make sure that the repository really exists on GitHub.com!
If you’re trying to push to a repository that doesn’t exist, you’ll get this error.
Error: Remote HEAD refers to nonexistent ref, unable to checkout
This error occurs if the default branch of a repository has been deleted on GitHub.com.
Detecting this error is simple; Git will warn you when you try to clone the repository:
$ git clone https://github.com/USER/REPO.git
# Clone a repo
> Cloning into 'repo'...
> remote: Counting objects: 66179, done.
> remote: Compressing objects: 100% (15587/15587), done.
> remote: Total 66179 (delta 46985), reused 65596 (delta 46402)
> Receiving objects: 100% (66179/66179), 51.66 MiB | 667 KiB/s, done.
> Resolving deltas: 100% (46985/46985), done.
> warning: remote HEAD refers to nonexistent ref, unable to checkout.To fix the error, you’ll need to be an administrator of the repository on GitHub.com.
You’ll want to change the default branch of the repository.
After that, you can get a list of all the available branches from the command line:
$ git branch -a
# Lists ALL the branches
> remotes/origin/awesome
> remotes/origin/more-work
> remotes/origin/new-mainThen, you can just switch to your new branch:
$ git checkout new-main
# Create and checkout a tracking branch
> Branch new-main set up to track remote branch new-main from origin.
> Switched to a new branch 'new-main'- 28-Jul-2015

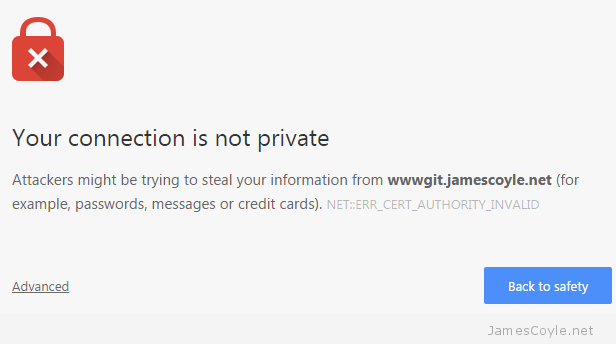
If you host something like this yourself, you’ll probably have entered the world called self signed certificates. These are SSL certificates that have not been signed by a known and trusted certificate authority. There is no security concern using a self signed certificate, the level of security will be similar to a paid for certificate, the problem is that your commuter won’t know that it can trust the certificate. You may have seen this error in a Web Browser, such as Chrome:
With Git, however, you’ll get an error from the git command line tool similar to the below:
$ git clone https://wwwgit.jamescoyle.net/test/test-project.git Cloning into 'test-project'... fatal: unable to access 'https://[email protected]/test/test-project.git/': SSL certificate problem: unable to get local issuer certificate
The preferred method of dealing with this error is to add the Certificate Authority’s signing certificate as a trusted Certificate Authority on your computer.The way to do this differs depending on your OS and is out of scope for this post.
There are two Git specific methods of forcing Git to accept the self signed certificates, which don’t require you to import the CA certificate to your computers Trusted CA store:
Turn off Git SSL Verification
You can stop the Git client from verifying your servers certificate and to trust all SSL certificates you use with the Git client. This has it’s own security risks as you would not be warned if there was a valid problem with the server you are trying to connect to.
That said, it’s the quickest and easiest fix for a non trusted server certificate. Simply run the below git command on your Git client.
git config --global http.sslVerify false
Tell Git Where Your Certificate Authority Certificates Are
Another option is to point your Git client towards a folder that contains the Certificate Authority certificate that was used to sign your Git server’s SSL certificate. You may not have one of these if you’re using Self Signed certificates.
Save the CA certificate to a folder on your Git client and run the following git command to tell your Git client to use it when connecting t the server:
git config --system http.sslCAPath /git/certificates
Содержание
- Bitbucket Support
- Knowledge base
- Products
- Jira Software
- Jira Service Management
- Jira Work Management
- Confluence
- Bitbucket
- Resources
- Documentation
- Community
- Suggestions and bugs
- Marketplace
- Billing and licensing
- Viewport
- Confluence
- Resolving SSL Self-Signed Certificate Errors
- Related content
- Still need help?
- Problem
- Cause
- Workaround
- Resolution
- Step1: Get a self-signed certificate of the remote server
- Get Certificate using OpenSSL
- Get Certificate using the Web browser
- Trust Certificate in your browser
- Export Certificate in .pem format
- Step 2: Configure Git to trust the Certificate
- For MAC/Linux:
- For Windows Client:
- How to fix ‘ssl certificate problem unable to get local issuer certificate’ Git error
- Learning objective
- What is the ‘ssl certificate problem unable to get local issuer certificate’ error
- What causes ‘ssl certificate problem unable to get local issuer certificate’
- Detect and fix errors 5x faster
- How can you fix ‘ssl certificate problem unable to get local issuer certificate errors’
- How to prevent ‘ssl certificate problem unable to get local issuer certificate’ errors
- Kubernetes Troubleshooting With Komodor
- Cant clone from GitHub : SSL certificate problem: unable to get local issuer certificate #9293
- Comments
- Describe the feature or problem you’d like to solve
- Proposed solution
- Additional context
Bitbucket Support
Knowledge base
Products
Jira Software
Project and issue tracking
Jira Service Management
Service management and customer support
Jira Work Management
Manage any business project
Confluence
Bitbucket
Git code management
Resources
Documentation
Usage and admin help
Answers, support, and inspiration
Suggestions and bugs
Feature suggestions and bug reports
Marketplace
Billing and licensing
Frequently asked questions
Viewport
Confluence
Resolving SSL Self-Signed Certificate Errors
Related content
Still need help?
The Atlassian Community is here for you.
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the server and data center platforms .
If you’re using a self-signed certificate on your Bitbucket server, you may receive SSL certificate errors when you try to perform certain actions. This page will help you resolve these errors.
Problem
When trying to perform a clone using instructions stated in Debug logging for Git operations on the client the following error is reported:
Cause
This is caused by git not trusting the certificate provided by your server.
Workaround
One possible workaround is to temporary disable SSL check for your git command in case you only need to perform a one time clone:
The workaround is intended to be used for one-time only operations and not to be used frequently. Removing the SSL verification disproves the whole concept of having SSL implemented.
Resolution
Step1: Get a self-signed certificate of the remote server
There is multiple ways of exporting the certificate, Either from the Browser or using the OpenSSL command
Get Certificate using OpenSSL
Get Certificate using the Web browser
Trust Certificate in your browser
To trust a self-signed certificate, you need to add it to your Keychain.
The easiest way to do that is to open the site in question in Safari, upon which you should get this dialog box:
Click ‘Show Certificate’ to reveal the full details:
Export Certificate in .pem format
Git doesn’t use the Mac OS X keychain to resolve this, so you need to trust the certificate explicitly.
- If you haven’t done so already, follow the steps in ‘Trust certificate in your browser, above
- Open Applications > Keychain Access and select ‘Certificates’ in the lower-left pane
- Type the website into the Search field in the top-right
- Select the certificate entry for the website, then in the menu click File > Export Items
- In the Save dialog, change ‘File Format’ to ‘Privacy Enhanced Mail (.pem)’ and save the file somewhere on your drive
- Access the URL of the remote server
- Click the Open padlock in the address bar.
- Click the arrow beside OpenConnection Secure.
- Click More Information . The OpenPage Info dialog box opens.
- Click View Certificate .
- The Certificate page opens.
- Scroll down to the Miscellaneous section.
- In the Download row, click the PEM (cert) link.
- In the dialog box that opens, click OK to save the certificate file to a known location.
- Navigate to the location for saving the file, and then click Save.
Step 2: Configure Git to trust the Certificate
For MAC/Linux:
Once the certificate is saved on the client you can instruct your git client to use it to trust the remote repository by updating the local git config:
For Windows Client:
Step 1: Import the certificate into the window trust store
- Enter Start | Run | MMC.
- Click File | Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates and click Add.
- Select the Computer account radio button when prompted and click Next
- Select Local computer (selected by default) and click Finish.
- Back in the Add or Remove Snap-ins window, click OK.
- In the MMC main console, click on the plus (+) symbol to expand the Certificate snap-in.
- To import the CA certificate, navigate to Trusted Root Certification Authorities | Certificates pane.
- Right-click within the Certificates panel and click All Tasks | Import to start the Certificate Import wizard.
- On successfully importing the CA certificate the wizard will bring you back to the MMC main console.
Step 2: Configure git to use the certificate in the windows Trust store
When using Windows, the problem resides that git by default uses the «Linux» crypto backend. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
Источник
How to fix ‘ssl certificate problem unable to get local issuer certificate’ Git error
Learning objective
What is the ‘ssl certificate problem unable to get local issuer certificate’ error
The unable to get local issuer certificate is a common issue faced by developers when trying to push, pull, or clone a git repository using Git Bash, a command-line tool specific to Windows.
The unable to get local issuer certificate error often occurs when the Git server’s SSL certificate is self-signed. The issue with self-signed certificates is that the private key associated with them cannot be revoked, making it a security vulnerability.
Alternatively, it can be due to incorrect configuration for Git on your system or when using git inside Visual Studio Code (VS Code) terminal.
What causes ‘ssl certificate problem unable to get local issuer certificate’
The unable to get local issuer certificate error is caused by the misconfiguration of the SSL certificate on your local machine. When pushing, pulling, or cloning, Git cannot verify your SSL certification, which leads to the error.
A valid HTTPS handshake requires both the client and the server to create a secure connection, allowing for safe communication between your local machine and where the source code is hosted. When the SSL certificate cannot be verified, Git cannot complete the HTTPS handshake with the server that hosts the repository.
When the unable to get local issuer certificate error occurs in VS Code, it is often because Visual Studio cannot locate the SSL certificate. This may be due to the path being misconfigured on the local machine.
Detect and fix errors 5x faster
Komodor monitors your entire K8s stack, identifies issues, and uncovers their root cause.
How can you fix ‘ssl certificate problem unable to get local issuer certificate errors’
When ssl certificate problem unable to get local issuer certificate error is caused by a self-signed certificate, the fix is to add the certificate to the trusted certificate store.
By default, the trusted certificate store is located in the following directory for Git Bash:
Open the file ca-bundle.crt located in the directory above, then copy and paste the Git SSL certificate to the end of the file. Once completed, save the file and run your git pull, push, or clone command.
Disabling SSL certificate validation is not recommended for security purposes. However, it is an option for fixing the ssl certificate problem unable to get local issuer certificate error.
You can disable SSL certificate validation locally in Git using the following command:
You can also disable SSL certificate validation at a global level using the following command:
To re-enable SSL certificate validation, use the following command:
Another method for fixing the ssl certificate problem unable to get local issuer certificate error is to reinstall Git and choose the SSL transport backend option during the installation process.
If the unable to get local issuer certificate error occurs inside Visual Studio Code, you need to grant your repository access to the SSL certificates. To do this, git can be reconfigured with the —global flag on your SSL certificate configuration. This will give the Git server accessibility to the required SSL certificate.
To do this, run the following command in the Terminal:
Accessibility to SSL certificate verification can also be set at the system level. To do this, you must be running in administrator mode before executing the following command:
If the unable to get local issuer certificate error in Visual Studio Code is not due to accessibility but a location misconfiguration, this can be fixed by reassigning the path. This can be done through the following command:
How to prevent ‘ssl certificate problem unable to get local issuer certificate’ errors
The main purpose of a SSL certificate is to confirm authentication so that the information passed between client and server is secure. When an unable to get local issuer certificate error occurs, a secure connection cannot be established, and the git client rejects your attempt to push, pull, or clone a repository for security reasons.
While disabling SSL certificates altogether is an option and common fix, it is not recommended. It opens up a security vulnerability for your repository and your local machine. Nevertheless, you can negate the unable to get local issuer certificate error by disabling SSL certificates at a local and global level. If SSL certificates are disabled at a global level, it is good to always enable them again so that other projects are not impacted by the intentional security disablement.
To prevent the error, ensure that you have a valid SSL certificate in your certificate store. Alternatively, you can reinstall your Git Bash with SSL Transport backend selected during the installation process.
If you are using Git via Visual Studio Code and have a valid SSL certificate in your certificate store but still encounter the certificate problem error, use the —global flag on your SSL certificate configuration to grant the Git server accessibility.
Kubernetes Troubleshooting With Komodor
We hope that the guide above helps you better understand the troubleshooting steps you need to take in order to fix the unable to get local issuer certificate error.
Keep in mind that this is just one of many Git errors that can pop up in your k8s logs and cause the system to fail. Due to the complex and distributed nature of k8s, the search for the root cause of each such failure can be stressful, disorienting, and time-consuming.
Komodor is a Kubernetes troubleshooting platform that turns hours of guesswork into actionable answers in just a few clicks. Using Komodor, you can monitor, alert and troubleshoot incidents in your entire K8s cluster.
For each K8s resource, Komodor automatically constructs a coherent view, including the relevant deploys, config changes, dependencies, metrics, and past incidents. Komodor seamlessly integrates and utilizes data from cloud providers, source controls, CI/CD pipelines, monitoring tools, and incident response platforms.
- Discover the root cause automatically with a timeline that tracks all changes made in your application and infrastructure.
- Quickly tackle the issue, with easy-to-follow remediation instructions.
- Give your entire team a way to troubleshoot independently, without having to escalate.
Источник
Cant clone from GitHub : SSL certificate problem: unable to get local issuer certificate #9293
Describe the feature or problem you’d like to solve
DINESH.DIXIT@LP-B1NY0Z2 MINGW64 /c/code/GitHub2
$ git clone https://github.com/dineshdixitgit/meta-api.git
Cloning into ‘meta-api’.
fatal: unable to access ‘https://github.com/dineshdixitgit/meta-api.git/’: SSL certificate problem: unable to get local issuer certificate
A clear and concise description of what the feature or problem is.
Proposed solution
How will it benefit Desktop and its users?
Additional context
Add any other context like screenshots or mockups are helpful, if applicable.
The text was updated successfully, but these errors were encountered:
@dineshdixitgit this error can be caused by a few things — are you running any security software on your machine that could be interfering with your connection to GitHub? Some security software will man-in-the-middle your connection.
You can also check out this issue thread #3684 for some specific steps to debug this issue. To check if there are any configuration issues on your machine it would be helpful if you could open up Git for Windows and run the following command:
git config -l —show-origin
Let me know the output of that.
@dineshdixitgit it looks like you have http.sslbackend set to openssl , which means GitHub Desktop isn’t using the Windows certificate store. Running the command git config —global http.sslBackend schannel should resolve this issue and allow your stored certificate to be picked up. Let me know if that doesn’t get things working.
Hi Steve,
Both openchannel and schannel gave me errors as below. Please suggest-
$ git config —global http.sslBackend «openssl»
$ git clone https://github.com/wmgdsp/gcdm-api.git gcdm-api-test
Cloning into ‘gcdm-api-test’.
fatal: unable to access ‘https://github.com/wmgdsp/gcdm-api.git/’: SSL certificate problem: unable to get local issuer certificate
$ git config —global http.sslBackend «schannel»
$ git clone https://github.com/wmgdsp/gcdm-api.git gcdm-api-test
Cloning into ‘gcdm-api-test’.
fatal: unable to access ‘https://github.com/wmgdsp/gcdm-api.git/’: schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) — The revocation function was unable to check revocation for the certificate.
The ‘revocation’ error is usually caused by your network blocking the attempt by Windows to check the revocation status of a certificate, which then causes the whole operation to error. You can find a workaround for this issue here:
Let me know if that doesn’t get things working for you.
D:Rajivmicroservice>git config -l —show-origin
file:»C:ProgramData/Git/config» core.symlinks=false
file:»C:ProgramData/Git/config» core.autocrlf=true
file:»C:ProgramData/Git/config» core.fscache=true
file:»C:ProgramData/Git/config» color.diff=auto
file:»C:ProgramData/Git/config» color.status=auto
file:»C:ProgramData/Git/config» color.branch=auto
file:»C:ProgramData/Git/config» color.interactive=true
file:»C:ProgramData/Git/config» help.format=html
file:»C:ProgramData/Git/config» http.sslcainfo=C:/Program Files/Git/mingw64/ssl/certs/ca-bundle.crt
file:»C:ProgramData/Git/config» diff.astextplain.textconv=astextplain
file:»C:ProgramData/Git/config» rebase.autosquash=true
file:»C:Program FilesGitmingw64/etc/gitconfig» credential.helper=manager
file:C:/Users/RA346186/.gitconfig user.name=Rajiv
file:C:/Users/RA346186/.gitconfig user.email=rajiv.sharma8@wipro.com
I have the above settings and not able to clone too
@rajivsharma2022 are you encountering the unable to get local issuer certificate error? It’d be helpful if you could open a new issue and upload your log file from GitHub Desktop.
HI @steveward,
I tried : git config —global http.sslBackend schannel
after this I tried cloning, and got this error
fatal: unable to access ‘https://github.com/KDS717/Python.git/’: schannel: next InitializeSecurityContext failed: Unknown error (0x80092012) — The revocation function was unable to check revocation for the certificate.
@KDS717 are you running any antivirus software on your system that could be causing this? We’ve seen specific antivirus software like Kaspersky cause this as well.
You can also skip the revocation check by running this command:
git config —global http.schannelCheckRevoke false
See this section of our known issues doc for reference.
My issues resolved by applying git config —global http.sslBackend schannel
@KDS717 are you running any antivirus software on your system that could be causing this? We’ve seen specific antivirus software like Kaspersky cause this as well.
You can also skip the revocation check by running this command:
git config —global http.schannelCheckRevoke false
See this section of our known issues doc for reference.
This worked for me on my corporate machine — I was cloning from my own GitHub repo. I made sure to revert it to git config —global http.schannelCheckRevoke true once I was done, however 🙂
Edit: I would instead now recommend adding the -c http.sslVerify=false argument to your git command, e.g. git -c http.sslVerify=false pull or git -c http.sslVerify=false clone as the SSL permissions are only overridden temporarily, therefore eliminating the possibility of forgetting to re-enable http.schannelCheckRevoke true .
@dineshdixitgit it looks like you have http.sslbackend set to openssl , which means GitHub Desktop isn’t using the Windows certificate store. Running the command git config —global http.sslBackend schannel should resolve this issue and allow your stored certificate to be picked up. Let me know if that doesn’t get things working.
Hi. Thanks to this, worked for me. My setup is: I have a VPN running which serves as a middleware ( company requirement ) and it blocks any access that’s not listed on my policy.
My issues resolved by applying git config —global http.sslBackend schannel
Yes.. Even my issue got resolved, after setting that one
excellent .. My Issue also resolved after settig git config —global http.sslBackend schannel
Having same issue but using a MAC. Any thoughts as I dont get the same info when running
git config -l —show-origin
@ashleyjamesbrown the best fix I found only yesterday — add a -c http.sslVerify=false argument to your git clone command.
e.g. git -c http.sslVerify=false clone https://github.com/AzureADQuickStarts/AppModelv2-NativeClient-DotNet.git
That way git knows to temporarily set the sslVerify property to false for the duration of the command. The same also works for git pull and git push (and any other git commands).
remote: Password authentication is not available for Git operations.
remote: You must use a personal access token or SSH key.
I think tis the enterprise (work) account so ill see if its that
Источник
What is the ‘ssl certificate problem unable to get local issuer certificate’ error
The unable to get local issuer certificate is a common issue faced by developers when trying to push, pull, or clone a git repository using Git Bash, a command-line tool specific to Windows.
The unable to get local issuer certificate error often occurs when the Git server’s SSL certificate is self-signed. The issue with self-signed certificates is that the private key associated with them cannot be revoked, making it a security vulnerability.
Alternatively, it can be due to incorrect configuration for Git on your system or when using git inside Visual Studio Code (VS Code) terminal.
What causes ‘ssl certificate problem unable to get local issuer certificate’
The unable to get local issuer certificate error is caused by the misconfiguration of the SSL certificate on your local machine. When pushing, pulling, or cloning, Git cannot verify your SSL certification, which leads to the error.
A valid HTTPS handshake requires both the client and the server to create a secure connection, allowing for safe communication between your local machine and where the source code is hosted. When the SSL certificate cannot be verified, Git cannot complete the HTTPS handshake with the server that hosts the repository.
When the unable to get local issuer certificate error occurs in VS Code, it is often because Visual Studio cannot locate the SSL certificate. This may be due to the path being misconfigured on the local machine.
How can you fix ‘ssl certificate problem unable to get local issuer certificate errors’
When ssl certificate problem unable to get local issuer certificate error is caused by a self-signed certificate, the fix is to add the certificate to the trusted certificate store.
By default, the trusted certificate store is located in the following directory for Git Bash:
C:Program FilesGitmingw64sslcerts
Open the file ca-bundle.crt located in the directory above, then copy and paste the Git SSL certificate to the end of the file. Once completed, save the file and run your git pull, push, or clone command.
Disabling SSL certificate validation is not recommended for security purposes. However, it is an option for fixing the ssl certificate problem unable to get local issuer certificate error.
You can disable SSL certificate validation locally in Git using the following command:
$ git -c http.sslVerify=false clone [URL]
You can also disable SSL certificate validation at a global level using the following command:
$ git config --global http.sslVerify false
To re-enable SSL certificate validation, use the following command:
$ git config --global http.sslVerify true
Another method for fixing the ssl certificate problem unable to get local issuer certificate error is to reinstall Git and choose the SSL transport backend option during the installation process.
If the unable to get local issuer certificate error occurs inside Visual Studio Code, you need to grant your repository access to the SSL certificates. To do this, git can be reconfigured with the --global flag on your SSL certificate configuration. This will give the Git server accessibility to the required SSL certificate.
To do this, run the following command in the Terminal:
git config --global http.sslBackend schannel
Accessibility to SSL certificate verification can also be set at the system level. To do this, you must be running in administrator mode before executing the following command:
git config --system http.sslBackend schannel
If the unable to get local issuer certificate error in Visual Studio Code is not due to accessibility but a location misconfiguration, this can be fixed by reassigning the path. This can be done through the following command:
git config --global http.sslcainfo "Path"
How to prevent ‘ssl certificate problem unable to get local issuer certificate’ errors
The main purpose of a SSL certificate is to confirm authentication so that the information passed between client and server is secure. When an unable to get local issuer certificate error occurs, a secure connection cannot be established, and the git client rejects your attempt to push, pull, or clone a repository for security reasons.
While disabling SSL certificates altogether is an option and common fix, it is not recommended. It opens up a security vulnerability for your repository and your local machine. Nevertheless, you can negate the unable to get local issuer certificate error by disabling SSL certificates at a local and global level. If SSL certificates are disabled at a global level, it is good to always enable them again so that other projects are not impacted by the intentional security disablement.
To prevent the error, ensure that you have a valid SSL certificate in your certificate store. Alternatively, you can reinstall your Git Bash with SSL Transport backend selected during the installation process.
If you are using Git via Visual Studio Code and have a valid SSL certificate in your certificate store but still encounter the certificate problem error, use the --global flag on your SSL certificate configuration to grant the Git server accessibility.
Kubernetes Troubleshooting With Komodor
We hope that the guide above helps you better understand the troubleshooting steps you need to take in order to fix the unable to get local issuer certificate error.
Keep in mind that this is just one of many Git errors that can pop up in your k8s logs and cause the system to fail. Due to the complex and distributed nature of k8s, the search for the root cause of each such failure can be stressful, disorienting, and time-consuming.
Komodor is a Kubernetes troubleshooting platform that turns hours of guesswork into actionable answers in just a few clicks. Using Komodor, you can monitor, alert and troubleshoot incidents in your entire K8s cluster.
For each K8s resource, Komodor automatically constructs a coherent view, including the relevant deploys, config changes, dependencies, metrics, and past incidents. Komodor seamlessly integrates and utilizes data from cloud providers, source controls, CI/CD pipelines, monitoring tools, and incident response platforms.
- Discover the root cause automatically with a timeline that tracks all changes made in your application and infrastructure.
- Quickly tackle the issue, with easy-to-follow remediation instructions.
- Give your entire team a way to troubleshoot independently, without having to escalate.