My .npmrc looks like this:
registry=http://registry.npmjs.org/
strict-ssl=false
python=python2.7
ca=
It shouldn’t even try to open a SSL connection because I’m using HTTP for the registry.
npm install protractor gives an error when running node-gyp «Error: self signed certificate in certificate chain»:
> utf-8-validate@1.1.0 install .node_modulesprotractornode_modulesselenium-webd
rivernode_moduleswsnode_modulesutf-8-validate
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesutf-8-validate>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\..
..node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesutf-8-validate
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
> bufferutil@1.1.0 install .node_modulesprotractornode_modulesselenium-webdrive
rnode_moduleswsnode_modulesbufferutil
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesbufferutil>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\....
node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesbufferutil
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
npm WARN optional dep failed, continuing utf-8-validate@1.1.0
npm WARN optional dep failed, continuing bufferutil@1.1.0
protractor@2.1.0 node_modulesprotractor
├── jasminewd@1.1.0
├── jasminewd2@0.0.5
├── html-entities@1.1.3
├── saucelabs@0.1.1
├── q@1.0.0
├── minijasminenode@1.1.1
├── optimist@0.6.1 (wordwrap@0.0.3, minimist@0.0.10)
├── adm-zip@0.4.4
├── glob@3.2.11 (inherits@2.0.1, minimatch@0.3.0)
├── jasmine@2.3.1 (exit@0.1.2, jasmine-core@2.3.4)
├── source-map-support@0.2.10 (source-map@0.1.32)
├── accessibility-developer-tools@2.6.0
├── request@2.36.0 (qs@0.6.6, forever-agent@0.5.2, aws-sign2@0.5.0, oauth-sign@0.3.0, tunnel-agent@0.4.1, json-stringify
-safe@5.0.1, mime@1.2.11, node-uuid@1.4.3, form-data@0.1.4, http-signature@0.10.1, tough-cookie@2.0.0, hawk@1.0.0)
├── lodash@2.4.2
└── selenium-webdriver@2.45.1 (tmp@0.0.24, rimraf@2.4.2, xml2js@0.4.4, ws@0.7.2)
. > npm install protractor
-
> bufferutil@1.1.0 install .node_modulesprotractornode_modulesselenium-webdrive
rnode_moduleswsnode_modulesbufferutil
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesbufferutil>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\....
node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesbufferutil
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
> utf-8-validate@1.1.0 install .node_modulesprotractornode_modulesselenium-webd
rivernode_moduleswsnode_modulesutf-8-validate
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesutf-8-validate>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\..
..node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesutf-8-validate
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
npm WARN optional dep failed, continuing bufferutil@1.1.0
npm WARN optional dep failed, continuing utf-8-validate@1.1.0
protractor@2.1.0 node_modulesprotractor
├── jasminewd@1.1.0
├── jasminewd2@0.0.5
├── html-entities@1.1.3
├── saucelabs@0.1.1
├── q@1.0.0
├── minijasminenode@1.1.1
├── optimist@0.6.1 (wordwrap@0.0.3, minimist@0.0.10)
├── adm-zip@0.4.4
├── glob@3.2.11 (inherits@2.0.1, minimatch@0.3.0)
├── jasmine@2.3.1 (exit@0.1.2, jasmine-core@2.3.4)
├── accessibility-developer-tools@2.6.0
├── source-map-support@0.2.10 (source-map@0.1.32)
├── lodash@2.4.2
├── request@2.36.0 (forever-agent@0.5.2, aws-sign2@0.5.0, qs@0.6.6, oauth-sign@0.3.0, tunnel-agent@0.4.1, json-stringify
-safe@5.0.1, mime@1.2.11, node-uuid@1.4.3, form-data@0.1.4, http-signature@0.10.1, tough-cookie@2.0.0, hawk@1.0.0)
└── selenium-webdriver@2.45.1 (tmp@0.0.24, rimraf@2.4.2, xml2js@0.4.4, ws@0.7.2)
. > npm install protractornpm config set ca ""
. > npm config set ca ""
. > npm install protractor
|
> utf-8-validate@1.1.0 install .node_modulesprotractornode_modulesselenium-webd
rivernode_moduleswsnode_modulesutf-8-validate
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesutf-8-validate>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\..
..node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesutf-8-validate
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
> bufferutil@1.1.0 install .node_modulesprotractornode_modulesselenium-webdrive
rnode_moduleswsnode_modulesbufferutil
> node-gyp rebuild
.node_modulesprotractornode_modulesselenium-webdrivernode_moduleswsnode_modu
lesbufferutil>if not defined npm_config_node_gyp (node "C:Program Filesiojsnode_modulesnpmbinnode-gyp-bin\....
node_modulesnode-gypbinnode-gyp.js" rebuild ) else (node rebuild )
gyp WARN install got an error, rolling back install
gyp ERR! configure error
gyp ERR! stack Error: self signed certificate in certificate chain
gyp ERR! stack at Error (native)
gyp ERR! stack at TLSSocket.<anonymous> (_tls_wrap.js:1010:38)
gyp ERR! stack at emitNone (events.js:67:13)
gyp ERR! stack at TLSSocket.emit (events.js:166:7)
gyp ERR! stack at TLSSocket._finishInit (_tls_wrap.js:566:8)
gyp ERR! System Windows_NT 6.3.9600
gyp ERR! command "C:\Program Files\iojs\node.exe" "C:\Program Files\iojs\node_modules\npm\node_modules\node-gyp
\bin\node-gyp.js" "rebuild"
gyp ERR! cwd .node_modulesprotractornode_modulesselenium-webdrivernode_modules
wsnode_modulesbufferutil
gyp ERR! node -v v3.0.0
gyp ERR! node-gyp -v v2.0.2
gyp ERR! not ok
npm WARN optional dep failed, continuing utf-8-validate@1.1.0
npm WARN optional dep failed, continuing bufferutil@1.1.0
protractor@2.1.0 node_modulesprotractor
├── jasminewd@1.1.0
├── jasminewd2@0.0.5
├── saucelabs@0.1.1
├── html-entities@1.1.3
├── q@1.0.0
├── minijasminenode@1.1.1
├── optimist@0.6.1 (wordwrap@0.0.3, minimist@0.0.10)
├── adm-zip@0.4.4
├── jasmine@2.3.1 (exit@0.1.2, jasmine-core@2.3.4)
├── source-map-support@0.2.10 (source-map@0.1.32)
├── accessibility-developer-tools@2.6.0
├── lodash@2.4.2
├── glob@3.2.11 (inherits@2.0.1, minimatch@0.3.0)
├── request@2.36.0 (aws-sign2@0.5.0, qs@0.6.6, forever-agent@0.5.2, oauth-sign@0.3.0, tunnel-agent@0.4.1, json-stringify
-safe@5.0.1, mime@1.2.11, node-uuid@1.4.3, form-data@0.1.4, http-signature@0.10.1, tough-cookie@2.0.0, hawk@1.0.0)
└── selenium-webdriver@2.45.1 (tmp@0.0.24, rimraf@2.4.2, xml2js@0.4.4, ws@0.7.2)
Содержание
- FIX: Self-signed certificate in certificate chain error
- How do I fix self-signed certificate in the certificate chain?
- For Node.js
- For npm
- ERR! self signed certificate in certificate chain #7519
- Comments
- yarn install crashes with the error self signed certificate in certificate chain #892
- Comments
- Bitbucket Support
- Knowledge base
- Products
- Jira Software
- Jira Service Management
- Jira Work Management
- Confluence
- Bitbucket
- Resources
- Documentation
- Community
- Suggestions and bugs
- Marketplace
- Billing and licensing
- Viewport
- Confluence
- Resolving SSL Self-Signed Certificate Errors
- Related content
- Still need help?
- Problem
- Cause
- Workaround
- Resolution
- Step1: Get a self-signed certificate of the remote server
- Get Certificate using OpenSSL
- Get Certificate using the Web browser
- Trust Certificate in your browser
- Export Certificate in .pem format
- Step 2: Configure Git to trust the Certificate
- For MAC/Linux:
- For Windows Client:
FIX: Self-signed certificate in certificate chain error
- Since npm stopped automatically accepting self-signed certificates, users have started to report errors while trying to publish some packages in certain applications.
- The error can be fixed, usually, by upgrading the package manager or use the known registrars.
- If you want to read more about security certificate errors, take a look at our dedicated certificate errors section.
- Feel free to explore our Troubleshooting Hub for more helpful articles.
- Download Restoro PC Repair Tool that comes with Patented Technologies (patent available here) .
- Click Start Scan to find Windows issues that could be causing PC problems.
- Click Repair All to fix issues affecting your computer’s security and performance
- Restoro has been downloaded by 0 readers this month.
For some time now, developers encountered a SELF_SIGNED_CERT_IN_CHAIN error during installing and publishing packages in certain applications and developer tools such as Node.js, npm, or Git.
Until a few years ago, when npm for instance announced that they would no longer support self-signed certificates.
This means that the certificate verification process was no longer automatic. So developers now have to set up their application to see the self-signed certificates.
How do I fix self-signed certificate in the certificate chain?
Depending on the tool you’re using, there are a few recommendations. Some are risky, some are safe. One thing is clear, though: you should not attempt to disable the certification verification process altogether.
For Node.js
You can insert an environment variable to allow untrusted certificates using the following command at the beginning of the code:
This is risky and it’s not recommended to be used in production. Alternatively, use npm config set strict-ssl=false if you have to do this for many applications and you want to save repeating the process.
Users also suggest upgrading your version of Node, to fixes any existing bugs and vulnerabilities.
For npm
The recommended solution is, again, to upgrade your version of npm running one of the following:
npm install npm -g —ca=null
npm update npm — g
Or, tell your current version of npm to use known registrars, and after installing, stop using them:
Some users mentioned that they only switched the registry URL from https to http:
We hope that one of these suggestions helped you fix the problem. Should you have any recommendations, please use the comments section below.
Источник
ERR! self signed certificate in certificate chain #7519
I am brand new to Node and NPM.
I downloaded it today and installed it. (I am trying to get Aurelia up and running.)
The first command I tried was this:
And when that happened I got the following Error:
npm ERR! self signed certificate in certificate chain
I saw that a year ago this error happened a lot, but I don’t see why this would be happening to me now. (NOTE: I tried both to npm install npm -g —ca=null (gave the same error) and npm config set ca=»» (did not do anything))
Any suggestions?
NOTE: It may be related that my company does a «Man in the Middle» attack on almost all SSL traffic. (They have a trusted certificate that they have pushed out to all machines. They use that to intercept all traffic.) I don’t know if this could be the cause or not, but the certificate that they pushed out is not «Self Signed».
I did go to https://registry.npmjs.org/gulp and check the certificate at it is issued by my company (so my system admins are doing the «Man in the Middle» thing on that URL.
Also, the error message that told me to come here with my issue also said to post this, so here it is:
0 info it worked if it ends with ok
1 verbose cli [ ‘C:Program Filesnodejsnode.exe’,
1 verbose cli ‘C:Program Filesnodejsnode_modulesnpmbinnpm-cli.js’,
1 verbose cli ‘install’,
1 verbose cli ‘-g’,
1 verbose cli ‘gulp’ ]
2 info using npm@2.5.1
3 info using node@v0.12.0
4 verbose node symlink C:Program Filesnodejsnode.exe
5 silly cache add args [ ‘gulp’, null ]
6 verbose cache add spec gulp
7 silly cache add parsed spec < raw: ‘gulp’,
7 silly cache add scope: null,
7 silly cache add name: ‘gulp’,
7 silly cache add rawSpec: »,
7 silly cache add spec: ‘‘,
7 silly cache add type: ‘range’ >
8 verbose addNamed gulp@
9 silly addNamed semver.valid null
10 silly addNamed semver.validRange *
11 silly addNameRange < name: ‘gulp’, range: ‘*’, hasData: false >
12 silly mapToRegistry name gulp
13 silly mapToRegistry using default registry
14 silly mapToRegistry registry https://registry.npmjs.org/
15 silly mapToRegistry uri https://registry.npmjs.org/gulp
16 verbose addNameRange registry:https://registry.npmjs.org/gulp not in flight; fetching
17 verbose request uri https://registry.npmjs.org/gulp
18 verbose request no auth needed
19 info attempt registry request try #1 at 5:07:15 PM
20 verbose request id adc0ceb5a3fc1f77
21 http request GET https://registry.npmjs.org/gulp
22 info retry will retry, error on last attempt: Error: self signed certificate in certificate chain
23 info attempt registry request try #2 at 5:07:25 PM
24 http request GET https://registry.npmjs.org/gulp
25 info retry will retry, error on last attempt: Error: self signed certificate in certificate chain
26 info attempt registry request try #3 at 5:08:26 PM
27 http request GET https://registry.npmjs.org/gulp
28 verbose stack Error: self signed certificate in certificate chain
28 verbose stack at Error (native)
28 verbose stack at TLSSocket. (_tls_wrap.js:927:36)
28 verbose stack at TLSSocket.emit (events.js:104:17)
28 verbose stack at TLSSocket._finishInit (_tls_wrap.js:458:8)
29 verbose cwd C:Users18773
30 error Windows_NT 6.1.7601
31 error argv «C:Program Filesnodejsnode.exe» «C:Program Filesnodejsnode_modulesnpmbinnpm-cli.js» «install» «-g» «gulp»
32 error node v0.12.0
33 error npm v2.5.1
34 error code SELF_SIGNED_CERT_IN_CHAIN
35 error self signed certificate in certificate chain
36 error If you need help, you may report this error at:
36 error http://github.com/npm/npm/issues
37 verbose exit [ 1, true ]
The text was updated successfully, but these errors were encountered:
Источник
yarn install crashes with the error self signed certificate in certificate chain #892
Do you want to request a feature or report a bug?
Bug
What is the current behavior?
yarn install crashes with the error self signed certificate in certificate chain
If the current behavior is a bug, please provide the steps to reproduce.
- Create a package.json with a URL that has a self signed certificate. In this case it is a .tgz in our infrastructure.
- Run yarn install
What is the expected behavior?
- yarn install exits without error.
Please mention your node.js, yarn and operating system version.
The text was updated successfully, but these errors were encountered:
This is SSL/TLS working as expected, it’s rejecting invalid certs 😄 . If this validation was not performed, someone could perform a man-in-the-middle attack.
Try running Yarn like this:
or running export NODE_TLS_REJECT_UNAUTHORIZED=0 before yarn install .
This is pretty dangerous though, as it totally turns off TLS validation for every request performed from Node.js while the environment variable is set. A better approach for internal services is to either use a real certificate (which could be a free Let’s Encrypt one) or have an internal CA, install its root cert on developer machines, and then use certificates from that CA for internal services (this is what we do at Facebook)
Potentially we could add a setting to ignore TLS validation errors for particular hostnames (so we’d still validate for the regular npm server and only turn off validation for your internal server) but I don’t know whether that’s worth the maintenance overhead of keeping such a feature.
Источник
Bitbucket Support
Knowledge base
Products
Jira Software
Project and issue tracking
Jira Service Management
Service management and customer support
Jira Work Management
Manage any business project
Confluence
Bitbucket
Git code management
Resources
Documentation
Usage and admin help
Answers, support, and inspiration
Suggestions and bugs
Feature suggestions and bug reports
Marketplace
Billing and licensing
Frequently asked questions
Viewport
Confluence
Resolving SSL Self-Signed Certificate Errors
Related content
Still need help?
The Atlassian Community is here for you.
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the server and data center platforms .
If you’re using a self-signed certificate on your Bitbucket server, you may receive SSL certificate errors when you try to perform certain actions. This page will help you resolve these errors.
Problem
When trying to perform a clone using instructions stated in Debug logging for Git operations on the client the following error is reported:
Cause
This is caused by git not trusting the certificate provided by your server.
Workaround
One possible workaround is to temporary disable SSL check for your git command in case you only need to perform a one time clone:
The workaround is intended to be used for one-time only operations and not to be used frequently. Removing the SSL verification disproves the whole concept of having SSL implemented.
Resolution
Step1: Get a self-signed certificate of the remote server
There is multiple ways of exporting the certificate, Either from the Browser or using the OpenSSL command
Get Certificate using OpenSSL
Get Certificate using the Web browser
Trust Certificate in your browser
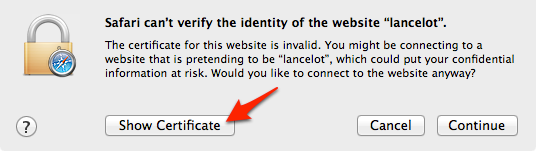
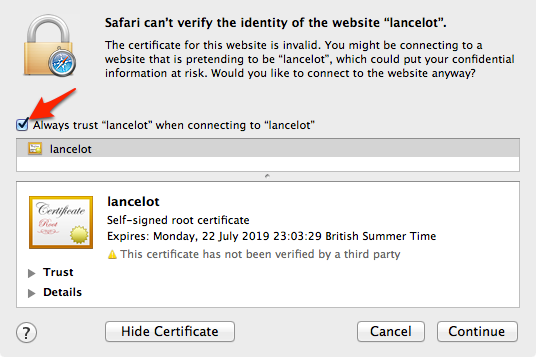
To trust a self-signed certificate, you need to add it to your Keychain.
The easiest way to do that is to open the site in question in Safari, upon which you should get this dialog box:
Click ‘Show Certificate’ to reveal the full details:
Export Certificate in .pem format
Git doesn’t use the Mac OS X keychain to resolve this, so you need to trust the certificate explicitly.
- If you haven’t done so already, follow the steps in ‘Trust certificate in your browser, above
- Open Applications > Keychain Access and select ‘Certificates’ in the lower-left pane
- Type the website into the Search field in the top-right
- Select the certificate entry for the website, then in the menu click File > Export Items
- In the Save dialog, change ‘File Format’ to ‘Privacy Enhanced Mail (.pem)’ and save the file somewhere on your drive
- Access the URL of the remote server
- Click the Open padlock in the address bar.
- Click the arrow beside OpenConnection Secure.
- Click More Information . The OpenPage Info dialog box opens.
- Click View Certificate .
- The Certificate page opens.
- Scroll down to the Miscellaneous section.
- In the Download row, click the PEM (cert) link.
- In the dialog box that opens, click OK to save the certificate file to a known location.
- Navigate to the location for saving the file, and then click Save.
Step 2: Configure Git to trust the Certificate
For MAC/Linux:
Once the certificate is saved on the client you can instruct your git client to use it to trust the remote repository by updating the local git config:
For Windows Client:
Step 1: Import the certificate into the window trust store
- Enter Start | Run | MMC.
- Click File | Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates and click Add.
- Select the Computer account radio button when prompted and click Next
- Select Local computer (selected by default) and click Finish.
- Back in the Add or Remove Snap-ins window, click OK.
- In the MMC main console, click on the plus (+) symbol to expand the Certificate snap-in.
- To import the CA certificate, navigate to Trusted Root Certification Authorities | Certificates pane.
- Right-click within the Certificates panel and click All Tasks | Import to start the Certificate Import wizard.
- On successfully importing the CA certificate the wizard will bring you back to the MMC main console.
Step 2: Configure git to use the certificate in the windows Trust store
When using Windows, the problem resides that git by default uses the «Linux» crypto backend. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
Источник
by Vlad Turiceanu
Passionate about technology, Windows, and everything that has a power button, he spent most of his time developing new skills and learning more about the tech world. Coming… read more
Updated on January 17, 2023
- Since npm stopped automatically accepting self-signed certificates, users have started to report errors while trying to publish some packages in certain applications.
- The error can be fixed, usually, by upgrading the package manager or use the known registrars.
XINSTALL BY CLICKING THE DOWNLOAD FILE
This software will repair common computer errors, protect you from file loss, malware, hardware failure and optimize your PC for maximum performance. Fix PC issues and remove viruses now in 3 easy steps:
- Download Restoro PC Repair Tool that comes with Patented Technologies (patent available here).
- Click Start Scan to find Windows issues that could be causing PC problems.
- Click Repair All to fix issues affecting your computer’s security and performance
- Restoro has been downloaded by 0 readers this month.
For some time now, developers encountered a SELF_SIGNED_CERT_IN_CHAIN error during installing and publishing packages in certain applications and developer tools such as Node.js, npm, or Git.
Until a few years ago, when npm for instance announced that they would no longer support self-signed certificates.
This means that the certificate verification process was no longer automatic. So developers now have to set up their application to see the self-signed certificates.
How do I fix self-signed certificate in the certificate chain?

Depending on the tool you’re using, there are a few recommendations. Some are risky, some are safe. One thing is clear, though: you should not attempt to disable the certification verification process altogether.
For Node.js
You can insert an environment variable to allow untrusted certificates using the following command at the beginning of the code:
process.env['NODE_TLS_REJECT_UNAUTHORIZED'] = 0;This is risky and it’s not recommended to be used in production. Alternatively, use npm config set strict-ssl=false if you have to do this for many applications and you want to save repeating the process.
Users also suggest upgrading your version of Node, to fixes any existing bugs and vulnerabilities.
For npm
The recommended solution is, again, to upgrade your version of npm running one of the following:
npm install npm -g --ca=null
npm update npm -g
Or, tell your current version of npm to use known registrars, and after installing, stop using them:
npm config set ca ""
npm install npm -g
npm config delete caSome users mentioned that they only switched the registry URL from https to http:
npm config set registry="http://registry.npmjs.org/"We hope that one of these suggestions helped you fix the problem. Should you have any recommendations, please use the comments section below.
Newsletter
Overview of the problem
When using Python to connect to z/OSMF, you might see the following errors:
«certificate verify failed: self signed certificate in certificate chain»
OR
«certificate verify failed: unable to get local issuer certificate»
This might be caused either by server configuration or Python configuration. In this article, we assume you use a self-signed CA certificate in z/OSMF. We will guide you step by step to workaround the certification error. You can choose either workaround if you wish.
- Workaround 1: verify = False
- Workaround 2: verify = CAfile (Specify a certificate in the PARM)
- Workaround 3: verify = True (Update key store in Python)
self signed certificate
If your z/OSMF was configured with self signed certificate, the python3 output error is:
certificate verify failed: self signed certificate in certificate chain
- Workaround 1: verify = False
Setting verify = False will skip SSL certificate verification.
- Workaround 2: verify = CAfile (Specify a certificate in the PARM)
The CAfile must be set to the CA certificate Bundle, if you set it as the server certificate, you will get the above error.
- Workaround 3: Verify = True (Update key store in Python)
The default value for parameter verify is True. Python 3.6+ installer has its own default certificate store for verifying SSL connections. The system certificate store will not be used any more. To use default certificate store, python library certifi must be installed in advance, you can use command «pip3 install certifi» to install it. Python default certificate store was in cacert.pem file, you can get it by
>>> import certifi
>>> certifi.where()
‘/Library/Frameworks/Python.framework/Versions/3.9/lib/python3.9/site-packages/certifi/cacert.pem’
If you get the above error, it means that your CA certificate was not included in cacert.pem, please use below command to add it:
For Mac or Linux:
$ cat [full path of your-cacert.pem] >> [full path of cacert.pem]
For Windows:
C:type [full path of your-cacert.pem] >> [full path of cacert.pem]
CA signed certificate
If your z/OSMF was configured with CA signed certificate, the python3 output error is:
certificate verify failed: unable to get local issuer certificate
- Workaround 1: verify = False
Setting verify = False will skip SSL certificate verification.
- Workaround 2: verify = CAfile (Specify a certificate in the PARM)
The CAfile is a CA certificate Bundle, it must be the Root CA certificate. If it is not a Root CA certificate, the above error will be showed.
- Workaround 3: Verify = True (Update key store in Python)
The default value for parameter verify is True. Python 3.6+ installer has its own default certificate store for verifying SSL connections. The system certificate store will not be used any more. To use default certificate store, python library certifi must be installed in advance, you can use command “pip3 install certifi”to install it. Python default certificate store was in cacert.pem file, you can get it by
>>> import certifi
>>> certifi.where()
‘/Library/Frameworks/Python.framework/Versions/3.9/lib/python3.9/site-packages/certifi/cacert.pem’
If you get the above error, it means that your Root CA certificate was not included in cacert.pem, please use below command to add it:
For Mac or Linux:
$ cat [full path of your-Root-cacert.pem] >> [full path of cacert.pem]
For Windows:
C:type [full path of your-Root-cacert.pem] >> [full path of cacert.pem]
How to export z/OSMF CA certificate
- Export CA certificate from z/OS
1. RACDCERT EXPORT(LABEL(‘zOSMFCA’)) DSN(‘IBMUSER.CACERT.IBMUSER.CRT’) FORMAT(CERTDER) CERTAUTH
Where:
- zOSMF is the label of the CA certificate.
- IBMUSER.CACERT.IBMUSER.CRT is the data set that will contain the client certificate. RACF command will auto-create this dataset
- CERTDER indicates that certificate is in DER format
2. Download the CA certificate from z/OS
3. Convert to PEM format
openssl x509 -in zOSMFCA.crt -inform der -outform pem -out zOSMFCA.pem