Finally, this post helped me to do away with the crumb problem, but still securing Jenkins from a CSRF attack.
Solution for no-valid crumb included in the request issue
Basically, we need to first request for a crumb with authentication and then issue a POST API calls with a crumb as a header along with authentication again.
This is how I did it,
curl -v -X GET http://jenkins-url:8080/crumbIssuer/api/json --user <username>:<password>
The response was,
{
"_class":"hudson.security.csrf.DefaultCrumbIssuer",
"crumb":"0db38413bd7ec9e98974f5213f7ead8b",
"crumbRequestField":"Jenkins-Crumb"
}
Then the POST API call with the above crumb information in it.
curl -X POST http://jenkins-url:8080/job/<job-name>/build --user <username>:<password> -H 'Jenkins-Crumb: 0db38413bd7ec9e98974f5213f7ead8b'
answered Feb 18, 2019 at 15:30
6
This solution is safe to use
We came along this issue when we changed Jenkins to be accessible via a reverse proxy.
There is an option in the «Configure Global Security» that «Enable proxy compatibility«
This helped with my issue.
Another solution
In the GitHub payload URL, make your URL look like this:
https://jenkins:8080/github-webhook/
Don’t forget to mention / at the end.
answered May 16, 2019 at 11:19
sachin_ursachin_ur
2,19713 silver badges27 bronze badges
3
To resolve this issue I unchecked «Prevent Cross Site Request Forgery exploits» in jenkins.com/configureSecurity section and it started working.
answered Jun 24, 2017 at 4:19
BalkrishnaBalkrishna
2,8493 gold badges22 silver badges31 bronze badges
5
I solved this by using an API token as a basic authentication password. Here is how:
curl -v -X POST http://jenkins-url:8080/job/<job-name>/buildWithParameters?param=value --user <username>:<token>
Note: To create the API token under the accounts icon → Configure → API Token → Add New token.
answered Jul 31, 2020 at 12:03
Aravinthan KAravinthan K
1,7052 gold badges19 silver badges22 bronze badges
3
A crumb is nothing but an access token. Below is the API to get the crumb:
https://jenkins.xxx.xxx.xxx/crumbIssuer/api/json
// Replace it with your Jenkins URL and make a GET call in your Postman or REST API caller.
This will generate output like:
{
"_class": "hudson.security.csrf.DefaultCrumbIssuer",
"crumb": "ba4742b9d92606f4236456568a",
"crumbRequestField": "Jenkins-Crumb"
}
Below are more details and link related to same:
How to request for the crumb issuer for Jenkins
Jenkins wiki page.
If you are calling the same via REST API call, checkout the below link where it is explained how to do a REST call using jenkins-crumb.
How to update a Jenkins job posting config.xml
Example:
curl -X POST http://anthony:anthony@localhost:8080/jenkins/job/pof/config.xml --data-binary "@config.xml" -data ".crumb=6bbabc426436b72ec35e5ad4a4344687"
answered Jun 23, 2017 at 6:47
anshul Guptaanshul Gupta
1,1727 silver badges17 bronze badges
5
For the new release of Jenkins you should follow the solution below:
From Upgrading to Jenkins 2.176.3:
Upgrading to Jenkins 2.176.2 Improved CSRF protection
SECURITY-626
CSRF tokens (crumbs) are now only valid for the web session they were
created in to limit the impact of attackers obtaining them. Scripts
that obtain a crumb using the /crumbIssuer/api URL will now fail to
perform actions protected from CSRF unless the scripts retain the web
session ID in subsequent requests. Scripts could instead use an API
token, which has not required a CSRF token (crumb) since Jenkins 2.96.To disable this improvement you can set the system property
hudson.security.csrf.DefaultCrumbIssuer.EXCLUDE_SESSION_ID to true.
Alternatively, you can install the Strict Crumb Issuer Plugin which
provides more options to customize the crumb validation. It allows
excluding the web session ID from the validation criteria, and instead
e.g. replacing it with time-based expiration for similar (or even
better) protection from CSRF
In my case, it helped for the installation of the Strict Crumb Issuer Plugin, rebooting Jenkins and applying a less strict policy for the web interface of Jenkins as it is suggested on the vendor’s site.
answered Mar 11, 2020 at 10:20
Alex KonkinAlex Konkin
5391 gold badge5 silver badges14 bronze badges
3
According to Jenkins Directive
First you have to check your Jenkins version if the version is < 2.176.2 then per Jenkins guideline CSRF tokens (crumbs) are now only valid for the web session they were created in to limit the impact of attackers obtaining them. Scripts that obtain a crumb using the /crumbIssuer/api URL will now fail to perform actions protected from CSRF unless the scripts retain the web session ID in subsequent requests.
Alternatively, you can install the Strict Crumb Issuer Plugin which provides more options to customize the crumb validation. It allows excluding the web session ID from the validation criteria, and instead e.g. replacing it with time-based expiration for similar (or even better) protection from CSRF.
Steps :
- you have to installed the plugin called «Strict Crumb Issuer»
- Once installed restart the jenkins service
- got to «Manage Jenkins» —> «Configure Global Security» —> Under CSRF Protection, select «Strict Crumb Issue» from the drop down list —> Click on Advance and uncheck everything but select «Prevent Breach Attack» option. —> Apply and save.
- Now run you crumb script.
It should work now.
Check this image for your reference
answered Jul 17, 2020 at 16:03
mht.haquemht.haque
1552 silver badges6 bronze badges
1
You need a two-step procedure to first get a crumb from the server and then use it.
I am using this Bash script and cURL for that:
#!/bin/bash
# buildme.sh Runs a build Jenkins build job that requires a crumb
# e.g.
# $ ./buildme.sh 'builderdude:monkey123' 'awesomebuildjob' 'http://paton.example.com:8080'
# Replace with your admin credentials, build job name and Jenkins URL
#
# More background:
# https://support.cloudbees.com/hc/en-us/articles/219257077-CSRF-Protection-Explained
USERPASSWORD=$1
JOB=$2
SERVER=$3
# File where web session cookie is saved
COOKIEJAR="$(mktemp)"
CRUMB=$(curl -f -u "$USERPASSWORD" --cookie-jar "$COOKIEJAR" "$SERVER/crumbIssuer/api/xml?xpath=concat(//crumbRequestField,%22:%22,//crumb)")
status=$?
if [[ $status -eq 0 ]] ; then
curl -f -X POST -u "$USERPASSWORD" --cookie "$COOKIEJAR" -H "$CRUMB" "$SERVER"/job/"$JOB"/build
status=$?
fi
rm "$COOKIEJAR"
exit $status
Here is an example of executing this script with the parameters you need:
./buildme.sh 'builderdude:monkey123' 'awesomebuildjob'
Output:
'http://paton.example.com:8080'
This script will return an error code if one of the cURL command fails for any reason.
More details can be found from cloudbees.
answered Mar 9, 2021 at 18:13
GaryGary
6,2275 gold badges29 silver badges36 bronze badges
I did get the same «403 No valid crumb was included in request» error when I created a Jenkins job from a Java program using jenkins-client library, i.e., com.offbytwo.jenkins. Then I used the Jenkins API token instead of password in the following code. Now, the issue is fixed.
JenkinsServer jServer = new JenkinsServer(new URI(jenkins_url), jnkn_username, jnkn_password);
We can generate an API token from the Jenkins console. Profile → Configure → API Token (Add new token).
The same API token can also be used instead of a password with curl.
curl -v -X POST http://jenkins-url:port/job/<job-name>/buildWithParameters?param=value --user <jen_username>:<jenkins_api_token>
answered Feb 14, 2020 at 6:16
SanthoshSanthosh
4,95612 gold badges60 silver badges88 bronze badges
2
I lost a bunch of time trying to figure this out. At the end, I just installed the plugin Build Authorization Token Root and enabled build permissions to anonymous users.
At the end doesn’t really matter, because the Jenkins instance is behind a VPN and I’m using https://smee.io to forward the webhook to the Jenkins instance.
Also the Jenkins instance is behind a reverse proxy, so the «Enable proxy compatibility» option is checked as well, and the «ignore_invalid_headers» setting set to off in the Nginx configuration at the server level. I am sharing my solution just in case someone else is struggling as well. I’m sure there are better ways to do it, but this is one option.
Note that with this plugin the build URL is set to buildByToken/build?job=JobName&token=TokenValue and the token is generated in the job settings.
This is in Jenkins 2.235.2 which doesn’t have an option to disable CSRF.
answered Jul 30, 2020 at 21:09
RafalfaroRafalfaro
2114 silver badges3 bronze badges
1
Since this question is the first SO link when searching for «No valid crumb was included in the request» in Google, I think it’s worth mentioning that the same error is generated if you omit/forget the Authorization HTTP header or use a blank username/password:
Relevant error messages related to the Authorization header are only generated when a value is passed:
And, yes, the crumb passed in the first screenshots is actually valid; everything works with the correct username/password:
So, not sure if that’s a bug or not, but «No valid crumb was included in the request» could also mean you accidentally forgot the Authorization header.
Jenkins 2.222.3, Ubuntu Server 20.04, Java Runtime 1.8.0_252-8u252-b09-1ubuntu1-b09
answered May 22, 2020 at 7:25
ChrisChris
765 bronze badges
For me, the below solutions work in Bitbucket:
I updated the URL to:
http://jenkinsurl:8080/bitbucket-hook/
Bitbucket Webhook:
answered Mar 14, 2022 at 14:04
Visiting Jenkins with https://... instead of http://... solved the problem for me.
answered Sep 2, 2021 at 8:54
1
For me the solution was to pass the X-Forwarded-Host and X-Forwarded-Port headers
as suggested in the reverse-proxy-configuration-troubleshooting chapter of the Handbook.
HaProxy config, inside the frontend section:
http-request set-header X-Forwarded-Host %[hdr(host)]
http-request set-header X-Forwarded-Port %[dst_port]
answered Apr 22, 2021 at 9:59
I followed this comment: In Dashboard → Manage Jenkins → Configure Global Security. Under CSRF Protection, choose option Enable proxy compatibility. It works for me.
answered Nov 18, 2022 at 9:10
When I was trying to build a job in Jenkins by following options like build steps, accessing Git code, whatever the options, etc., I
faced the error
jenkins-403-no-valid-crumb-was-included-in-the-request
Seriously, I tried a number of ways to resolve it… But there wasn’t any luck…!
Surprisingly, I changed my Wi-Fi network, and then it worked.
answered Oct 13, 2022 at 19:25
In my case, I was able to bypass the error by using Remote Desktop into the Jenkins server directly and using
a localhost-based URL instead of trying to go through the corporate proxy from my computer.
answered May 5, 2022 at 16:59
MenashehMenasheh
3,4513 gold badges31 silver badges47 bronze badges
I also faced a similar problem. I was using a password instead of a token.
When updated, it solved my problem. There isn’t any need to uncheck anything and make it insecure. Below are the complete steps that I followed to have Jenkins CLI working:
Step 1: Prepare environment variables
export JENKINS_URL=http://localhost:8080/
export JENKINS_USER=admin
export JENKINS_PASSWORD=b7f04f4efe5ee117912a1.....
export JENKINS_CRUMB=f360....
export FOLDER=test
Obtain a token as:
How to get the API token for Jenkins
Get the crumb as:
http://localhost:8080/crumbIssuer/api/json
Step 2: Prepare the XML file, file name creds.xml
<com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
<scope>GLOBAL</scope>
<id>TEST-CLI</id>
<username>test</username>
<password>test123</password>
<description>this secret if created confirms that jenkins-cli is working</description>
</com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
Step 3: POST using cURL
curl -X POST -u $JENKINS_USER:$JENKINS_PASSWORD -H "Jenkins-Crumb:${JENKINS_CRUMB}" -H 'content-type:application/xml' -d @creds.xml "$JENKINS_URL/job/$FOLDER/credentials/store/folder/domain/_/createCredentials"
answered May 19, 2021 at 11:38
Yogesh JilhawarYogesh Jilhawar
5,2877 gold badges41 silver badges56 bronze badges
Here is my solution to this issue (Git hooks to launch a Jenkins job behind a reverse proxy).
-
Get the crumb from a first call and store the sessionid in a cookie jar:
CRUMB=$(/usr/bin/curl --cookie-jar ./cookie -sX GET https://******.net/crumbIssuer/api/json|cut -d'"' -f8) -
Launch the job:
/usr/bin/curl --cookie ./cookie -X POST https://******.net/job/PROJECTNAME/build -H "Jenkins-Crumb: $CRUMB"
answered Feb 4, 2021 at 11:09
The guide CSRF Protection Explained explains how to generate a Jenkins crumb, save the cookies and use both the crumb and the saved cookies in the subsequent requests that require authentication. This is a must for Jenkins after version 2.176.2.
answered Nov 2, 2020 at 13:07
EslamEslam
1,5832 gold badges11 silver badges18 bronze badges
For Java code to access the Jenkins API I will let my advise out.
The answer of Santhosh does resolve the problem. That consists in changing the password for a token, but as far as I know, the token is now a legacy manner to do it.
So I tried other way, and find out a solution inside Java code.
Here how I did it.
In my Java code I use the com.offbytwo.jenkins package and the class that I use is JenkinsServer.
My problem was to create a job in Jenkins because I was getting an error: «403 No valid crumb was included in request«
Then I found a Boolean parameter called crumbFlag and passed true on it and everything worked.
My code was like this:
jenkins.createJob(job.getName(), config);
Then, I changed for this, and it worked like a charm:
jenkins.createJob(job.getName(), config, true);
This parameter is inside almost all methods of this package, by example:
- createJob(String jobName, String jobXml, Boolean crumbFlag)
- updateJob(String jobName, String jobXml, boolean crumbFlag)
- renameJob(String oldJobName, String newJobName, Boolean crumbFlag)
- Others.
The technical documentation inside the code is:
@param crumbFlag
trueto add crumbIssuer
*falseotherwise.
I understood if you pass true for this parameter it will issue a crumb automatically.
Well, the official documentation has this information in detail. If you wish, take a look here:
Class JenkinsServer
answered Oct 7, 2020 at 13:44
I had the same issue when trying to set up a GitHub project with the GitHub Pull Request Builder plugin.
-
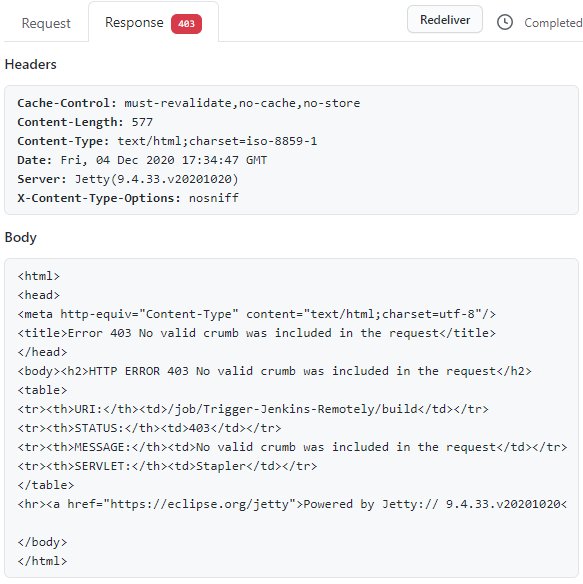
Here is an example of the response I was getting from my Jenkins server
-
Response content
-
The problem was happening because my payload URL was missing a forward slash at the end,
/. -
adding a forward slash at the end of the URL solves the problem
-
your payload URL should look like this: https://jenkins.host.com/ghprbhook/
-
Examples after adding the forward slash
answered Jan 26, 2021 at 9:17
lotfiolotfio
1,8862 gold badges18 silver badges33 bronze badges
I am running with a reverse proxy with nignx. I changed a Jenkins option in the «Configure Global Security», that «Enable proxy compatibility».
This fixed with my issue.
answered Aug 9, 2020 at 17:38
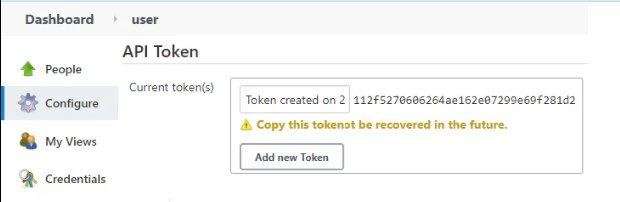
First create a user API token by going to user → API Token → Add new token.
Then use the below script for triggering.
import jenkins,requests
job_name='sleep_job'
jenkins_url = "http://10.10.10.294:8080"
auth = ("jenkins","1143e7efc9371dde2e4f312345bec")
request_url = "{0:s}/job/{1:s}/buildWithParameters".format(jenkins_url,
job_name, )
crumb_data = requests.get("{0:s}/crumbIssuer/api/json".format(jenkins_url),
auth=auth, ).json()
headers = {'Jenkins-Crumb': crumb_data['crumb']}
jenkins_job_params={}
jenkins_job_params['NODE_NAME']='10_10_1_29'
jenkins_job_params['SLEEP_TIME']='1h'
response = requests.post(request_url, data=jenkins_job_params, auth=auth, )
response.raise_for_status()
answered Oct 26, 2020 at 10:26
1
Head over to Manage Jenkins => Configure global security.
Then uncheck «Prevent Cross Site Request Forgery exploits«
answered Aug 30, 2019 at 21:03
I have run into the same issue. I have only refreshed my browser, logged back in to Jenkins, did the same process and everything worked.
answered Mar 5, 2020 at 16:58
Fix Jenkins GitHub ‘valid crumb’ errors
A common problem DevOps professionals hit when trying to configure a GitHub webhook to remotely invoke a Jenkins build job is the dreaded 403: No valid crumb was included in the request error. Thankfully, there’s a pretty straight forward fix to the problem.
This error is typically caused by using the Jenkins remote build trigger URL on the Jenkins webhook, rather than using the github-webhook URI that is configured as part of the Jenkins GitHub plugin.
If you want a GitHub webhook to trigger a Jenkins build without a 403 no valid crumb error, the Jenkins plugin must be used.
There’s an easy fix to the GitHub to Jenkins 403: no valid crumb error
403: No valid crumb fix
To avoid a 403 error when integrating Jenkins and GitHub, follow these three steps when you create the build job and configure the webhook:
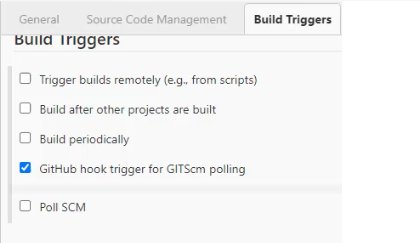
- Make sure the Jenkins GitHub plugin is installed in Jenkins
- In your Jenkins build job click the GitHub hook trigger for GITScm polling checkbox
- Do not choose the Trigger builds remotely option
- Create a Jenkins API for the user with rights to run the build job
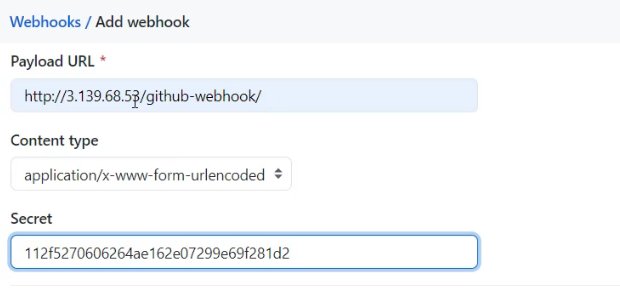
- In GitHub, create a webhook to trigger the Jenkins GitHub plugin
- Set the GitHub payload as <JENKINS_URL> /github-webhook/
- Set the Jenkins API Token as the webhook’s secret token
- Save the GitHub webhook configuration and watch Jenkins builds run without 403 no crumb errors
The GitHub hook trigger must be used to avoid 403 no crumb in request errors from Jenkins.
Jenkins tokens and Webhook secrets
The Webhook secret used by GitHub is created as an API token in Jenkins for a user who has rights to invoke the build job.
The Jenkins API token is used as the GitHub webhook secret.
Do not use the remote URL Jenkins provides for invoking builds remotely from scripts or external programs. Instead, use the Jenkins server’s IP address or domain name with /github-webhook/ appended to it.
| Your intro to GitHub Actions training course |
|---|
|
Here’s how to get started with GitHub Actions:
Follow these tutorials and you’ll learn GitHub Actions fast. |
GitHub webhook configuration in GitHub.
With the GitHub webhook to Jenkins configured as a trigger, push commits to your GitHub repository at will. The GitHub server will then invoke our Jenkins instance and your continuous integration build jobs will run.
If you follow these steps, your Jenkins GitHub webhook will run successfully without any 403 no crumb in the request errors slowing you down.
If you are working with the Python based JenkinsAPI library you might run into the No valid crumb was included in the request error. The error below will probably look familiar if you’ve run into this issue.
Traceback (most recent call last):
File "myscript.py", line 47, in <module>
deploy()
File "myscript.py", line 24, in deploy
jenkins.build_job('test')
File "/usr/local/lib/python3.6/site-packages/jenkinsapi/jenkins.py", line 165, in build_job
self[jobname].invoke(build_params=params or {})
File "/usr/local/lib/python3.6/site-packages/jenkinsapi/job.py", line 209, in invoke
allow_redirects=False
File "/usr/local/lib/python3.6/site-packages/jenkinsapi/utils/requester.py", line 143, in post_and_confirm_status
response.text.encode('UTF-8')
jenkinsapi.custom_exceptions.JenkinsAPIException: Operation failed. url=https://jenkins.example.com/job/test/build, data={'json': '{"parameter": [], "statusCode": "303", "redirectTo": "."}'}, headers={'Content-Type': 'application/x-www-form-urlencoded'}, status=403, text=b'<html>n<head>n<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/>n<title>Error 403 No valid crumb was included in the request</title>n</head>n<body><h2>HTTP ERROR 403</h2>n<p>Problem accessing /job/test/build. Reason:n<pre> No valid crumb was included in the request</pre></p><hr><a href="http://eclipse.org/jetty">Powered by Jetty:// 9.4.z-SNAPSHOT</a><hr/>nn</body>n</html>n'
It is good practice to enable additional security in Jenkins by turning on the “Prevent Cross Site Forgery exploits” option in the security settings, so if you see this error it is a good thing. The below example shows this security feature in Jenkins.
The Fix
This error threw me off at first, but it didn’t take long to find a quick fix. There is a crumb_requester class in the jenkinsapi that you can use to create the crumbed auth token. You can use the following example as a guideline in your own code.
from jenkinsapi.jenkins import Jenkins from jenkinsapi.utils.crumb_requester import CrumbRequester JENKINS_USER = 'user' JENKINS_PASS = 'pass' JENKINS_URL = 'https://jenkins.example.com' # We need to create a crumb for the request first crumb=CrumbRequester(username=JENKINS_USER, password=JENKINS_PASS, baseurl=JENKINS_URL) # Now use the crumb to authenticate against Jenkins jenkins = Jenkins(JENKINS_URL, username=JENKINS_USER, password=JENKINS_PASS, requester=crumb) ...
The code looks very similar to creating a normal Jenkins authentication object, the only difference being that we create and then pass in a crumb for the request, rather than just a username/password combination. Once the crumbed authentication object has been created, you can continue writing your Python code as you would normally. If you’re interested in learning more about crumbs and CSRF you can find more here, or just Google for CSRF for more info.
This issue was slightly confusing/annoying, but I’d rather deal with an extra few lines of code and know that my Jenkins server is secure.
Josh is the creator of this blog, a system administrator and a contributor to other technology communities such as /r/sysadmin and Ops School. You can also find him on Twitter and Facebook.