Содержание
- 2035 MQRC_NOT_AUTHORIZED Connecting to WebSphere MQ from WebSphere Application Server via CLIENT Bindings
- Troubleshooting
- Problem
- Symptom
- Cause
- Diagnosing The Problem
- Resolving The Problem
- 2035 MQRC_NOT_AUTHORIZED in WMQ
- Troubleshooting
- Problem
- Cause
- Resolving The Problem
- (JMS) WebSphere MQ failed: 2035 MQRC_NOT_AUTHORIZED
- Troubleshooting
- Problem
- Symptom
- Cause
- Diagnosing The Problem
- Resolving The Problem
2035 MQRC_NOT_AUTHORIZED Connecting to WebSphere MQ from WebSphere Application Server via CLIENT Bindings
Troubleshooting
Problem
Symptom
Cause
Diagnosing The Problem
Please note that WebSphere MQ V7.5 and earlier does not provide any out-of-the box password authentication system for client connections.
Password authentication is provided out of the box in IBM MQ V8.0. More details on the new IBM MQ V8.0 security features are available in this presentation.
For WebSphere MQ V7.5 and earlier, this means that while the understanding provided in this technote over how usernames and passwords are passed from the application server to MQ is helpful for development environments, solving the security requirements of production environments usually also requires one of the following approaches:
- Mutual SSL/TLS authentication.
MQ provides out-of-the-box features toauthenticate a remotely attaching client using the digital certificate they provide for SSL/TLS transport security. For example by configuring an SSLPEER rule on the SVRCONN channel to match the Distinguished Name in the certificate of the WebSphere Application Server, and establishing trust in the issuer of that certificate. - A custom, or 3rd party supplied, WebSphere MQ Security Exit
A security exit can be written for MQ that performs username and password authentication against a repository, such as the local operating system on the MQ server, or an LDAP repository.
When using a security exit for authentication it is important that SSL/TLS transport security is still configured, to ensure passwords are not sent in plain text.
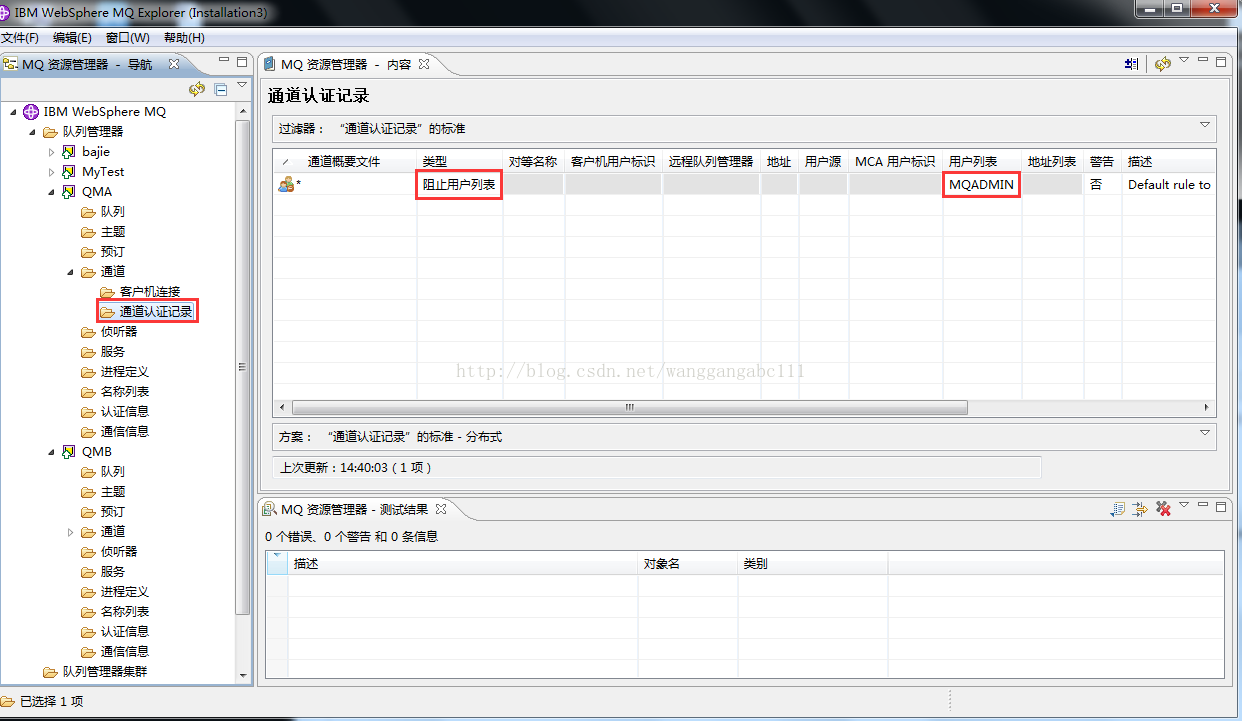
MCA user ID (MCAUSER) configured on the Server Connection (SVRCONN) channel
If an MCAUSER is configured on the SVRCONN channel that the application server is using to connect, and no security exit or mapping Channel Authentication Record is installed, then this overrides the username provided by the application server.
It is common practice for many customers to set an MCAUSER on every SVRCONN channel, and use mutual SSL/TLS authentication exclusively for authentication.
Default behavior when no credentials are supplied in the application server
If no credentials are supplied by the application on the createConnection call, and neither of the component managed or container-managed security systems described below are configured, then WebSphere Application Server provides a blank username to MQ. This causes MQ to authorize the client based on the user id that the listener is running under. In the majority of cases this is ‘mqm’ on UNIX/Linux systems and ‘MUSR_MQADMIN’ on Windows.
As these are administrative users, they will be blocked by default in WebSphere MQ V7.1 and higher, with an AMQ9777 error logged in the error logs of the queue manager.
Container-managed security for outbound connections
The recommended way to configure the username and password passed to MQ by the application server for outbound connections, is to use container-managed security. Outbound connections are those created using a Connection Factory, rather than a Listener Port or Activation Specification.
Usernames of 12 characters or less are passed to MQ by the application server. Usernames longer than 12 characters in length will be truncated, either during authorization (on UNIX), or in the MQMD of messages that are sent.
Container-managed security means that the deployment descriptor, or EJB 3.0 annotations, of the application declare a resource reference with authentication type set to Container.
Then when the application looks up the Connection Factory in JNDI, it does so indirectly via the resource reference. For example an EJB 2.1 application would perform a JNDI lookup as follows, where «jms/MyResourceRef» has been declared as a resource reference in the deployment descriptor:
ConnectionFactory myCF = (ConnectionFactory)ctx.lookup(«java:comp/env/ jms/MyResourceRef»)
An EJB 3.0 application might declare an annotated object property on the bean as follows:
When the application is deployed by an administrator, they bind this authentication alias to an actual Connection Factory that has been created in JNDI, and assign it a J2C authentication alias on deployment.
It is the username and password contained in this authentication alias that is then passed to MQ/JMS by the application server when the application connects. This approach puts the administrator in control of which username and password is used by each application, and prevents a different application from looking up the connection factory in JNDI directly to connect with the same username and password.
A default container-managed authentication alias can be supplied on the configuration panels in the administrative console for MQ connection factories. This default will only be used in the case that an application uses a resource reference configured for container-managed security, but the administrator has not bound it to an authentication alias during deployment. A screen shot is provided below:
Default component-managed authentication alias for outbound connections
For cases where it is impractical to change the application to use container-managed security, or to change it to supply a username and password directly on the createConnection call, it is possible to supply a default.
This default is called the «component-managed authentication alias» and cannot be configured via the administrative console (since WebSphere Application Server Version 7.0 when it was removed from the panels connection factories). The below scripting samples show how to configure it using wsadmin:
- JACL:
wsadmin>set cell [ $AdminConfig getid «/Cell:mycell» ]
wsadmin>$AdminTask listWMQConnectionFactories $cell
wsadmin>$AdminTask modifyWMQConnectionFactory MyCF(cells/mycell|resources.xml#MQConnectionFactory_1247500675104)
MyCF(cells/mycell|resources.xml#MQConnectionFactory_1247500675104)
Jython:
wsadmin>cell = AdminConfig.getid(«/Cell:mycell»)
wsadmin>AdminTask.modifyWMQConnectionFactory(‘MyCF(cells/mycell|resos urces.xml#MQConnectionFactory_1247500675104)’, «-componentAuthAlias myalias»)
‘MyCF(cells/mycell|resources.xml#MQConnectionFactory_1247500675104)’
Authentication alias for inbound MDB connections using an activation specification
For inbound connections using an activation specification an authentication alias can be specified by the administrator when deploying the application, or a default authentication alias can be specified on the activation specification via the administrative console.
Authentication alias for inbound MDB connections using a listener port
For inbound connections using a listener port, the value specified in the «Container-managed authentication alias» setting of the connection factory (seen in the above screen shot) is used.
On zOS, first the «Container-managed authentication alias» is checked and used if set, then the «Component-managed authentication alias» is checked and used it set.
Resolving The Problem
For all production environments where transport security is required, SSL/TLS security must be configured between the application server and MQ.
In order to configure SSL/TLS transport security, you must establish the appropriate trust between the queue manager and WebSphere Application Server. The application server, who initiates the SSL/TLS handshake, must always be configured to trust the certificate provided by the queue manager . If the application server is configured to send a certificate to the queue manager, then the queue manager must also be configured to trust it.
If trust is not correctly configured on both sides, you will encounter 2393 MQRC_SSL_INITIALIZATION_ERROR reason codes after enabling SSL/TLS on the connection.
If you do not have a security exit that performs username and password authentication, then you should configure mutual SSL/TLS authentication on your Server Connection channel to cause the queue manager to require a trusted certificate is provided by the application server. To do this you set «SSL Authentication» to «Required» in the MQ Explorer or SSLCAUTH(REQUIRED) via MQSC.
If you do have a security exit that performs username and password authentication installed in your MQ server, then configure your application to supply a username and password for validation by that security exit. The details of how to configure the username and password passed to MQ by the application server are described above in the «Diagnosing the problem» section.
All Server Connection channels that do not have SSL/TLS security applied should be disabled. Example MQSC commands to disable the SYSTEM.DEF.SVRCONN channel are provided as follows (these assume no user exists on the server called ‘NOAUTH’):
ALTER CHL(SYSTEM.DEF.SVRCONN) CHLTYPE(SVRCONN) MCAUSER(‘NOAUTH’)
STOP CHL(SYSTEM.DEF.SVRCONN)
Details of how to configure the private certificate and trust of a queue manager, and to enable SSL security on a Server Connection channel, see the following locations in the Information Center:
- To configure the certificates and trust of the queue manager see the following topic:
Configuring SSL on queue managers - To configure the Server Connection channel, used by applications running in the application server to connect to MQ, see the following topic:
Configuring SSL channels
Details of how you configure trust within WebSphere Application Server, and whether the application server sends a certificate to MQ for authentication, are in the following locations in the WebSphere Application Server information center:
- To create or modify an SSL Configuration containing the appropriate SSL/TLS configuration for connecting to MQ, see the following topic:
SSL configurations
Note that MQ requires you specify a matching Cipher Suite / Cipher Spec on both sides of the connection, as it checks the negotiated Cipher Suite matches the SSLCIPH setting on the channel after the handshake is complete. As a result the WebSphere Application Server SSL Configuration should be configured to containonlythe Cipher Suite that matches the SSLCIPH setting on the Server Connection channel. See the following topic in the information center for details of matching pairs:
CipherSuite and CipherSpec name mappings for connections to a WebSphere® MQ queue manager - To enable SSL/TLS on a client connection, and choose which SSL Configuration to use, see the «Use SSL to secure communication with Websphere MQ», «Centrally managed» and «Specific configuration» sections of the following topics on Connection Factories and Activation Specifications
WebSphere MQ messaging provider connection factory settings
WebSphere MQ messaging provider activation specification settings
Источник
Troubleshooting
Problem
You are getting MQRC 2035, Not Authorized in your WebSphere MQ application or channel. You need to understand what causes this failure. 2035 0x000007f3 MQRC_NOT_AUTHORIZED
Cause
MQRC 2035 (MQRC_NOT_AUTHORIZED) is returned when a user is not authorized to perform the function that is attempted.
Resolving The Problem
MQRC 2035 (MQRC_NOT_AUTHORIZED) is returned when a user is not authorized to perform the function. Determine which object the user cannot access and provide the user access to the object.
Debugging techniques:
Use the dspmqaut (display authority command), to determine if the user has the authorization to access the intended object.
For more difficult problems a trace of the failure may be necessary. See «Additional information» for trace debugging pointers.
Corrective action:
Use the setmqaut (set or reset authority) command, to grant access to WebSphere MQ objects.
You will then need to restart the queue manager to refresh the security cache, or via runmqsc run «REFRESH SECURITY(*)» to do the same.
In some cases you may want to make the user a member of the «mqm» group. That will give the user full access to WebSphere MQ.
For further details regarding the WebSphere MQ authority commands, refer to:
- dspmqaut (display authority)
setmqaut (set or reset authority)
Additional information
Here’s a quick overview of WMQ security:
Users in the ‘mqm’ group and the ‘mqm’ userid (on UNIX) have full authority. Other users and groups need to be given limited authority through the OAM using ‘setmqaut’.
Imagine that a WMQ application issues a MQOPEN. Here is the sequence of events as that MQOPEN is handled by the application and its agent (note: this is a general flow. The internal routine names or the specific interactions between routines could change without any notification.)
Источник
(JMS) WebSphere MQ failed: 2035 MQRC_NOT_AUTHORIZED
Troubleshooting
Problem
User setting up JMS logging using WebSphere MQ embedded client in SSPcm configuration.
Symptom
[Thread-41] ERROR JmsPublisherProxy$PublisherRunnable — Failed to send message to JMS
com.ibm.msg.client.jms.DetailedJMSSecurityException: JMSWMQ2006: Failed to open MQ topic ‘SSPcm.Topic’.
at com.ibm.msg.client.wmq.common.internal.Reason.reasonToException(Reason.java:521)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.common.internal.Reason.createException(Reason.java:221)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQMessageProducer.checkJmqiCallSuccess(WMQMessageProducer.java:1061)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQMessageProducer.checkJmqiCallSuccess(WMQMessageProducer.java:1019)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQMessageProducer.access$800(WMQMessageProducer.java:68)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQMessageProducer$SpiIdentifiedProducerShadow.initialise(WMQMessageProducer.java:765)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQMessageProducer. (WMQMessageProducer.java:995)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.wmq.internal.WMQSession.createProducer(WMQSession.java:886)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.jms.internal.JmsSessionImpl.createProducer(JmsSessionImpl.java:1232)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.msg.client.jms.internal.JmsTopicSessionImpl.createPublisher(JmsTopicSessionImpl.java:87)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.ibm.mq.jms.MQTopicSession.createPublisher(MQTopicSession.java:99)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
at com.sterlingcommerce.hadrian.jms.AbstractJmsPublisher.connect(AbstractJmsPublisher.java:80)
[sspconfig.jar:?]
at com.sterlingcommerce.hadrian.jms.JmsPublisherProxy$PublisherRunnable.run(JmsPublisherProxy.java:270) [sspconfig.jar:?]
at java.lang.Thread.run(Thread.java:785) [. ]
Caused by: com.ibm.mq.MQException: JMSCMQ0001: WebSphere MQ call failed with compcode ‘2’ (‘MQCC_FAILED’) reason ‘2035’ (‘MQRC_NOT_AUTHORIZED’).
at com.ibm.msg.client.wmq.common.internal.Reason.createException(Reason.java:209)
[com.ibm.mqjms.jar:7.5.0.2 — p750-002-131001_DE]
. 12 more
Cause
The error can be cause by one of the following reasons:
1.) The Topic string in WebSphere MQ must must match the JSM Topic configuration.
2.) Putting the wrong password for the user in the SSP JMS configuration.
3.) The user does not have privileges to publish to the «Topic string» in WebSphere MQ.
Diagnosing The Problem
Process(7823.48287) User(mqm) Program(amqzlaa0)
AMQ8009: Entity ‘userID’ has insufficient authority to access topic string ‘SSPcm.TOPIC’.
EXPLANATION: The specified entity is not authorized to access the required topic. The following permissions were requested: pub
ACTION: Ensure that the correct level of authority has been set for this entity against appropriate topic objects, or ensure that the entity is a member of a privileged group.
Resolving The Problem
Set the «Topic string» in WebSphere MQ to be the same value as the JMS
Источник
Problem: If we create a new queue manager in WebSphere MQ 7.1, 7.5, 8.0 or 9.0 or later and try to use a user id(commonly mqm for UNIX and MUSR_MQADMIN on Windows) that is an MQ Administrator to access the queue manager via a server-connection channel (remotely from another host, or locally from the same host and not using bindings mode). You get an error with reason code 2035:
2035 MQRC_NOT_AUTHORIZED
Related error codes:
MQ Explorer => AMQ4036
MQ classes for JMS => JMSWMQ2013
org.springframework.jms.JmsSecurityException: JMSWMQ2013: The security authentication was not valid that was supplied for QueueManager » with connection mode ‘Client’ and host name ‘localhost(1417)’.; nested exception is com.ibm.msg.client.jms.DetailedJMSSecurityException: JMSWMQ2013: The security authentication was not valid that was supplied for QueueManager » with connection mode ‘Client’ and host name ‘localhost(1417)’.
Please check if the supplied username and password are correct on the QueueManager to which you are connecting.; nested exception is com.ibm.mq.MQException: JMSCMQ0001: WebSphere MQ call failed with compcode ‘2’ (‘MQCC_FAILED’) reason ‘2035’ (‘MQRC_NOT_AUTHORIZED’).
Note: The MQ Administrator can remotely access (via a server-connection channel) without problems other MQ queue managers at version 6 or 7.0.x.
Solution : If we want the MQ Administrator to be able to access the queue manager via client channels, we have different approach to achieve:
1a. We can add the following two Channel Authentication Records:
The first rule blocks administrative users and the MCAUSER «nobody» (which prevents someone from creating a user ID «nobody» and putting it into an authorized group).
$ runmqsc QmgrName
SET CHLAUTH(*) TYPE(BLOCKUSER) USERLIST(‘nobody’,’*MQADMIN’)
The second rule provides a reduced blacklist for SYSTEM.ADMIN channels that allows administrators to use these. It is assumed here that some other CHLAUTH rule such as an SSLPEERMAP has validated the administrator’s connection or that an exit has done so.
SET CHLAUTH(SYSTEM.ADMIN.*) TYPE(BLOCKUSER) USERLIST(‘nobody’)
The above rules apply to SYSTEM.ADMIN.SVRCONN which is used by the MQ Explorer.
If you are using another user-defined channel, such as MY.ADMIN.SVRCONN, then you need to add the following two records:
SET CHLAUTH(MY.ADMIN.SVRCONN) TYPE(ADDRESSMAP) ADDRESS(*) USERSRC(CHANNEL)
SET CHLAUTH(MY.ADMIN.SVRCONN) TYPE(BLOCKUSER) USERLIST(‘nobody’)
Note: it is not advisable to use SYSTEM.DEF.* channels for active connections. The system default channels are the objects from which all user-defined channels inherit properties. The recommended practice is that SYSTEM.DEF.* and SYSTEM.AUTO.* channels should NOT be configured to be usable.
1b. This is a variation of (1a) but allowing the MQ Administrator to only use a particular host.
The first rule blocks MCAUSER «nobody».
SET CHLAUTH(SYSTEM.ADMIN.SVRCONN) TYPE(BLOCKUSER) USERLIST(‘nobody’)
The second rule removes all access to SYSTEM.ADMIN.SVRCONN …
SET CHLAUTH(SYSTEM.ADMIN.SVRCONN) TYPE(ADDRESSMAP) ADDRESS(*) ACTION(REMOVE)
And the third rule adds an entry for the server that needs access.
SET CHLAUTH(SYSTEM.ADMIN.SVRCONN) TYPE(ADDRESSMAP) ADDRESS(9.xx.xx.8y) USERSRC(CHANNEL)
1c. Disable the Channel Authentication Records feature:
$ runmqsc QmgrName
DISPLAY QMGR CHLAUTH
AMQ8408: Display Queue Manager details.
QMNAME(TEST01) CHLAUTH(ENABLED)
ALTER QMGR CHLAUTH(DISABLED)
WARNING: Disabling this new feature is not recommended for MQ 7.1 production queue managers due to security implications.
Note that disabling CHLAUTH results in a policy that accepts administrative connections by default. The administrative effort to lock down administrative access with CHLAUTH(DISABLED) is much greater than to do so with CHLAUTH(ENABLED). It is therefore recommended to leave CHLAUTH(ENABLED) and use the other security features of WebSphere MQ V7.1 to authenticate administrator connections.
Spring jms code with ibm websphere mq example
How to use hermes jms in soapui for IBM MQ
IBM MQ reason code 2087 (AMQ4048)com.ibm.msg.client.jms.DetailedIllegalStateException: JMSWMQ2007
With some development experience with IBM MQ, you should realize when you look at 2035 that it was a permissions issue. The following figure
MQJE001: Completion code is '2', reason is '2035'.
Exception in thread "main" com.ibm.mq.MQException: MQJE001: Completion code is '2', reason is '2035'.
at com.ibm.mq.MQManagedConnectionJ11.<init>(MQManagedConnectionJ11.java:247)
at com.ibm.mq.MQClientManagedConnectionFactoryJ11._createManagedConnection(MQClientManagedConnectionFactoryJ11.java:588)
at com.ibm.mq.MQClientManagedConnectionFactoryJ11.createManagedConnection(MQClientManagedConnectionFactoryJ11.java:630)
at com.ibm.mq.StoredManagedConnection.<init>(StoredManagedConnection.java:107)
at com.ibm.mq.MQSimpleConnectionManager.allocateConnection(MQSimpleConnectionManager.java:205)
at com.ibm.mq.MQQueueManagerFactory.obtainBaseMQQueueManager(MQQueueManagerFactory.java:911)
at com.ibm.mq.MQQueueManagerFactory.procure(MQQueueManagerFactory.java:799)
at com.ibm.mq.MQQueueManagerFactory.constructQueueManager(MQQueueManagerFactory.java:750)
at com.ibm.mq.MQQueueManagerFactory.createQueueManager(MQQueueManagerFactory.java:157)
at com.ibm.mq.MQQueueManager.<init>(MQQueueManager.java:681)
at com.yusys.SendMsg.connect(SendMsg.java:30)
at com.yusys.SendMsg.main(SendMsg.java:76)Of course, you can also view the log file under the error folder of MQ, which has detailed error instructions.
Here is the test code:
package com.yusys;
import java.io.IOException;
import com.ibm.mq.MQEnvironment;
import com.ibm.mq.MQException;
import com.ibm.mq.MQMessage;
import com.ibm.mq.MQPutMessageOptions;
import com.ibm.mq.MQQueue;
import com.ibm.mq.MQQueueManager;
import com.ibm.msg.client.wmq.v6.base.internal.MQC;
public class SendMsg {
static MQQueueManager qMgr;
static int CCSID = 1381;
static String queueName = "RQ_0000";
static String message;
public static void connect() throws MQException{
MQEnvironment.hostname = "172.20.35.98";
MQEnvironment.channel = "JMS_RECEIVE";
MQEnvironment.port = 1416;
MQEnvironment.CCSID = CCSID;
//User name with privileges in MQ
MQEnvironment.userID = "MUSR_MQADMIN";
// the password corresponding to the user name
MQEnvironment.password = "123456";
qMgr = new MQQueueManager("QMA");
}
public static void sendMsg(String msgStr){
int openOptions = MQC.MQOO_OUTPUT|MQC.MQOO_FAIL_IF_QUIESCING;
MQQueue queue = null;
try {
//Open the queue
queue = qMgr.accessQueue(queueName, openOptions);
// Create message buffer
MQMessage msg = new MQMessage();
//set the options for placing messages
MQPutMessageOptions pmo = new MQPutMessageOptions();
//the message data to be sent
msg.format = MQC.MQFMT_STRING;
msg.characterSet = CCSID;
msg.encoding = CCSID;
msg.writeString(msgStr);
msg.expiry = -1;//Set messages to never expire
queue.put(msg,pmo);
qMgr.commit();
} catch (MQException e) {
e.printStackTrace();
} catch (IOException e){
e.printStackTrace();
} catch (Exception e){
e.printStackTrace();
} finally {
if(queue!=null){
try {
queue.close();
} catch (MQException e) {
e.printStackTrace();
} finally{
try {
qMgr.disconnect();
} catch (MQException e) {
e.printStackTrace();
}
}
}
}
}
public static void main(String[] args) throws MQException{
connect();
// String msg = HttpClientUtil.doGet("http://localhost:8080/user/all");
// sendMsg(msg);
sendMsg("Zhuang Sheng dawned a butterfly and wished the emperor a cuckoo in spring");
System.out.println("End of insertion");
}
}
Usually, MQ client and MQ server communication, using the MQ server connection channel service in the MCAUSER attribute specified by the user as the MQ client even come up with the user, if the MCAUSER attribute value is empty, use the MQ client in the operating system used by the user as the MQ client even come up with the user, communication, reported a 2035 error, is due to the client and server communication used by the user without permission, there are two solutions.
Method one:
If you set the MCAUSER property to MUSR_MQADMIN(CHANNEL definition name JMS_RECEIVE) in the server’s service connection CHANNEL definition: ALTER CHANNEL(JMS_RECEIVE) CHLTYPE(SVRCONN); MCAUSER(MUSR_MQADMIN) must ensure that the MUSR_MQADMIN user is a member of the MQM group as follows:
Usermod-g GroupName Username (change the group of the existing user)
Useradd-g GroupName Username (create new user and group)
Method 2:
If MQ channel definition on the server MCAUSER attribute values for vacant province, namely is empty, the MQ client can be used by the users to add to the MQ server’s operating system, for example, if the MQ client USES for the ADMIN user, the user is added to the MQ server ADMIN, and ensure the users in the MQM group MQ the server, and how to perform the necessary permissions on the queue manager operation.
Special note: When claiming MCA authentication under Windows and finding 2035, it may be because the channel authentication record Settings are blocked. You just need to change the list of users.
Read More:
IBM MQ — Resolve «MQCC_FAILED MQRC_NOT_AUTHORIZED»
The following error occurs when a request is submitted to IBM MQ, such as a request to connect to an IBM MQ channel, or to GET or PUT messages on an IBM MQ queue.
IBM MQ call failed with compcode '2' ('MQCC_FAILED') reason '2035' ('MQRC_NOT_AUTHORIZED').Following are the most probable reasons this exception is being returned:
- An invalid username and/or password is being used in the connection request
- The user has not been granted permission to the object (queue manager, topic, queue, et cetera)
- The channel is blocked
- MQConstants.USE_MQCSP_AUTHENTICATION_PROPERTY is set to false or JmsConstants.USER_AUTHENTICATION_MQCSP is set to false or system property com.ibm.mq.cfg.jmqi.useMQCSPauthentication is set to false
Get the principal (username)
Often, you will know the username being used to connect to IBM MQ. However, if you only know the channel or queue or topic, the dmpmqaut command can be used to potentially find the username. In this scenario, the username will be known as the principal.
dmpmqaut -m MANAGER01 > dump.txt 2>&1Something like this should be in dump.txt.
profile: QUEUE001
object type: queue
entity: john.doe
entity type: principal
authority: get browse put inqQueue Manager
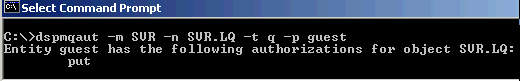
If you are able to determine the username that should have been granted permission to the object, use the dspmqaut command to determine if the user has the inq and connect permission to the queue manager.
dspmqaut -m MANAGER01 -t qmgr -p JohnDoe
Entity JohnDoe has the following authorizations for object MANAGER01:
connect
inqChannel
Let’s say your IBM MQ — Error Logs contains AMQ9777E Channel was blocked. In this example, the channel named CHANNEL01 was blocked. This means that a connection could not be made to the channel.
mm/dd/yyyy hh:mm:ss - Process(18271.9654) User(mqm) Program(amqrmppa)
Host(mq.example.com) Installation(Installation1)
VRMF(9.1.0.3) QMgr(MANAGER01)
Time(yyyy-mm-ddThh:mm:ss.sss)
RemoteHost(10.1.2.3)
CommentInsert1(CHANNEL01)
CommentInsert2(SERVER01 (10.4.5.6))
CommentInsert3(CLNTUSER(john.doe) ADDRESS(client.example.com))
AMQ9777E: Channel was blocked
EXPLANATION:
The inbound channel 'CHANNEL01' was blocked from address 'client.example.com
(10.4.5.6)' because the active values of the channel matched a record
configured with USERSRC(NOACCESS). The active values of the channel were
'CLNTUSER(john.doe) ADDRESS(client.example.com)'.
The display chlauth (channel authority) command can be used. Notice in this example that the channel is configured to allow connections from «client01.example.com». If the connection is NOT being made from the system with hostname client01.example.com, the connection will be refused and the IBM MQ log should have «AMQ9777E Channel was blocked».
The set chlauth command can be used to add authority to the channel.
~]# echo "display chlauth (CHANNEL01)" | runmqsc MANAGER01
CHLAUTH(CHANNEL01) TYPE(ADDRESSMAP)
DESCR(Allow access and use ID from channel)
CUSTOM( ) ADDRESS(client01.example.com)
USERSRC(CHANNEL) CHCKCLNT(ASQMGR)
ALTDATE(2019-08-20) ALTTIME(07.09.01)Queue or Topic
Use the dspmqaut command to determine if the user has the pub and sub permission to the Topic . . .
dspmqaut -m MANAGER01 -n TOPIC01 -t topic -p JohnDoe
Entity JohnDoe has the following authorizations for object TOPIC01:
pub
sub. . . or the inq, browse, put and get permissions to the queue.
dspmqaut -m MANAGER01 -n QUEUE01 -t queue -p JohnDoe
Entity JohnDoe has the following authorizations for object QUEUE01:
inq
browse
get
putNote that some Java applications will include the name of the Queue Manager, Queue or Topic, username and password being used in the request.
private static final String QMGR = "MANAGER01";
private static final String QUEUE = "QUEUE01";
private static final String USER = "JohnDoe";
private static final String PASSWORD = "itsasecret";Check the MQ Error Logs
Refer to IBM MQ — Error Logs for details on the MQ Error Logs. Here is an example of one possible exception in the Error Log, which identifies that channel «MANAGER01.CHANNEL01.SVR» was blocked. In this scenario, you would use the display chlauth command to confirm that «client.example.com» does indeed not have access to channel «MANAGER01.CHANNEL01.SVR».
The set chlauth command can be used to add authority to the channel.
If the log has «AMQ9557E Queue Manager User ID initialization failed», check out my article Resolve «AMQ9557E Queue Manager User ID initialization failed»
mm/dd/yyyy hh:mm:ss - Process(18271.9654) User(mqm) Program(amqrmppa)
Host(mq.example.com) Installation(Installation1)
VRMF(9.1.0.3) QMgr(MANAGER01)
Time(yyyy-mm-ddThh:mm:ss.sss)
RemoteHost(10.1.2.3)
CommentInsert1(MANAGER01.CHANNEL01.SVR)
CommentInsert2(SERVER01 (10.4.5.6))
CommentInsert3(CLNTUSER(john.doe) ADDRESS(client.example.com))
AMQ9777E: Channel was blocked
EXPLANATION:
The inbound channel 'MANAGER01.CHANNEL01.SVR' was blocked from address 'client.example.com
(10.4.5.6)' because the active values of the channel matched a record
configured with USERSRC(NOACCESS). The active values of the channel were
'CLNTUSER(john.doe) ADDRESS(client.example.com)'.
Did you find this article helpful?
If so, consider buying me a coffee over at