|
«ICMP error does not match an existing connection» log in SmartView Tracker |
Technical Level
|
| Solution ID | sk119312 |
Technical Level  |
|
| Product | Quantum Security Gateways |
| Version | All |
| OS | Gaia |
| Platform / Model | All |
| Date Created |
2017-08-03 00:00:00.0 |
| Last Modified | 2019-01-24 00:00:19.0 |
Symptoms
-
SmartView Tracker log shows:
ICMP: Port Unreachable; ICMP Type 3; ICMP Code 3 message_info: ICMP error does not match an existing connection -
Kernel debug (
fw ctl debug -m fw + conn drop vm) shows:;FW-1: fw_log_bad_conn_ex: reason ICMP error does not match an existing connection; ;fw_log_drop_ex: Packet proto=1 ... dropped by fw_first_packet_state_checks Reason: ICMP error does not match an existing connection; ;fw_handle_first_packet: first packet state violation (action=VANISH); ;fw_filter_chain: handle_first_packet returned action VANISH for new conn;
Cause
ICMP Error packet arrives through the firewall while the original connection (For which the ICMP error was generated) did not go through the firewall. (For example, asymmetric routing).
Solution
|
Note: To view this solution you need to Sign In |
- Products
- Learn
- CheckFlix
- CheckMates Go Cyber Security Podcast
- Check Point for Beginners 2.0
- Check Point Trivia
- Cyber Talk
- Incident Response
- LGPD
- Tip Of The Week
- Training and Certification
- Check Point Security Masters
- CheckMates Labs
- TechTalks
- Local User Groups
- Partners
- Welcome Partners!
-
More
- Products
- Quantum (Secure the Network)
- IoT Protect
- Maestro
- Management
- Scalable Chassis
- SD-WAN
- Security Gateways
- SmartMove
- Smart-1 Cloud
- SMB Gateways (Spark)
- Threat Prevention
- Telemetry
- CloudGuard CloudMates
- Application Security
- Cloud Intelligence And Threat Hunting
- Cloud Network Security
- Cloud Security Posture Management
- Container Security
- Serverless Security
- Talking Cloud Podcast
- CloudMates General
- Harmony (Secure Users and Access)
- Browse
- Connect
- Email and Collaboration
- Endpoint
- Mobile
- Remote Access VPN
- Horizon (Unified Management and Security Operations)
- Horizon MDR
- Horizon NDR
- Horizon XDR
- Horizon Events
- Horizon Policy
- Horizon SOC
- Developers
- Ansible
- API / CLI Discussion
- DevSecOps
- SmartConsole Extensions
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Quantum (Secure the Network)
- Learn
- CheckFlix
- CheckMates Go Cyber Security Podcast
- Check Point for Beginners 2.0
- Check Point Trivia
- Cyber Talk
- Incident Response
- LGPD
- Tip Of The Week
- Training and Certification
- Check Point Security Masters
- CheckMates Labs
- TechTalks
- Local User Groups
- Upcoming Events
- Americas
- Brazil
- Canada
- The Caribbean
- Central US
- Eastern US
- Latin America
- Mid-Atlantic US
- Pacific Northwest
- South Central US
- Southeast US
- US Federal
- Western US
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH — Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Korea
- Mongolia
- Bangalore
- Greater China
- Australia/New Zealand
- Philippines
- Japan
- Singapore
- India
- Thailand
- Taiwan
- Hong Kong
- Partners
- Welcome Partners!
- More
- Non-English Discussions
- Español
- Français
- Português
- Russian
- Chinese 中文
- Japanese 日本語
- More
- Exclusive Content
- CPX 360 2021 Content
- R8x Training Videos
- Message Views
- Recent Messages
- Recent Threads
- Contests
- How-To Video Contest
- CheckMates Everywhere 5th Birthday
- Blogs
- Careers at Check Point
- The CheckMates Blog
- Threat Intelligence Reports
- Cyber Talk Cyber Security Insights
- Off-Topic Discussions
- ABOUT CHECKMATES & FAQ
- About CheckMates & FAQ
- Community Guidelines
- Sign In
- Leaderboard
- Events
CPX 360 2023
The Industry’s Premier Cyber Security Summit and Expo
LEARN MORE
QUANTUM SD-WAN IS HERE
Security & Connectivity in a Single Appliance
LEARN MORE
CHECK POINT is #1
in Miercom NGFW Security Benchmark 2023
GET THE REPORT
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Search instead for
Did you mean:
- CheckMates
- Products
- General Topics
- Firewall drop icmp error type 3 code 4 «ICMP error…
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Search instead for
Did you mean:
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don’t have an account, create one now for free!
Now I can fixed by follow sk119312.
But not sure this traffic should be allow by «Accept stateful ICMP Errors» or uncheck «drop out of state ICMP packet» on global properties or not ?
Thank you
-
All forum topics -
Previous Topic -
Next Topic
1 Reply
Not related. the log is about out of state ICMP for asymmetric routing.

YOU DESERVE THE BEST SECURITY
We’re Social. Follow Us
|
|
Страница 1 из 1 | [ Сообщений: 7 ] |
| Автор | Сообщение |
|---|---|
|
Зарегистрирован: 18 май 2009, 12:34 |
есть аса 5520, софт 8.05 переодически в логах возникает Цитата: %ASA-4-313005: No matching connection for ICMP error message: icmp src dmz:192.168.123.10 dst vpn:192.168.25.60 (type 3, code 3) on dmz interface. Original IP payload: udp src 192.168.25.60/53 dst 192.168.123.10/53974. но при этом в акцес листе разрешено Цитата: access-list acl_dmz extended permit icmp 192.168.123.0 255.255.255.0 any unreachable sh service-policy global | inc icmp |
| 13 янв 2010, 11:54 |
|
|
Motylek Зарегистрирован: 18 май 2009, 12:34 |
думаю что проблема это inspect icmp дропает, но почему тогда в счетчиках дропа нули… |
| 13 янв 2010, 12:29 |
|
|
Fedia Супермодератор Зарегистрирован: 01 окт 2008, 12:24 |
цитата: Error Message %ASA-4-313005: No matching connection for ICMP error message: Explanation ICMP error packets were dropped by the adaptive security appliance because the ICMP error messages are not related to any session already established in the adaptive security appliance. Recommended Action If the cause is an attack, you can deny the host by using ACLs. Из этого я делаю вывод, что почему то не отрабатывает ACL. Или даже вернее так, ACL наверно отрабатывает, но инспект раньше сообщает, что такой сессии нет. В ACL есть совпадения с этой строкой? А сессий нет, потому что ДНС запрос имеет очень коротенькое время жизни и быстро из таблицы удаляется. Unreachable идет позже. |
| 13 янв 2010, 12:49 |
|
|
Motylek Зарегистрирован: 18 май 2009, 12:34 |
Цитата: Из этого я делаю вывод, что почему то не отрабатывает ACL. Или даже вернее так, ACL наверно отрабатывает, но инспект раньше сообщает, что такой сессии нет. В ACL есть совпадения с этой строкой? ну я тоже так думаю, но мне не понятно другое, почему счетчики дропов не увеличиваются по sh service-policy global | inc icmp и еще вопрос, если у меня включен inspect icmp error то между внутренними интерфейсами (между ними нет ната. только nat 0) почему то не работает трэйс (точнее отвечает только последний хоп) |
| 13 янв 2010, 12:57 |
|
|
Fedia Супермодератор Зарегистрирован: 01 окт 2008, 12:24 |
Ха, так это и есть фишка icmp error! Она и придумана для того, чтобы трейс снаружи случайно не выдал внутренние адреса! Как раз и получается: есть nat 0 , значит с т.з. циски трейс выдает «наружу» секурную инфу! АСА говорит «не пущать!» и подменяет эти адреса своим. ЗЫ А дропов не увеличивается, видимо потому, что сам инспект ничего и не дропает. Дропает правило на интерфейсе, которое в данном случае разрешает. |
| 13 янв 2010, 14:44 |
|
|
Motylek Зарегистрирован: 18 май 2009, 12:34 |
Цитата: Ха, так это и есть фишка icmp error! ага, теперь понятно |
| 14 янв 2010, 10:21 |
|
|
Fedia Супермодератор Зарегистрирован: 01 окт 2008, 12:24 |
Все, чем АСА может дропать и счетчики дропов по этим технологиям можно поглядеть командой |
| 14 янв 2010, 13:40 |
|
| Показать сообщения за: Поле сортировки |
|
|
Страница 1 из 1 | [ Сообщений: 7 ] |
Introduction
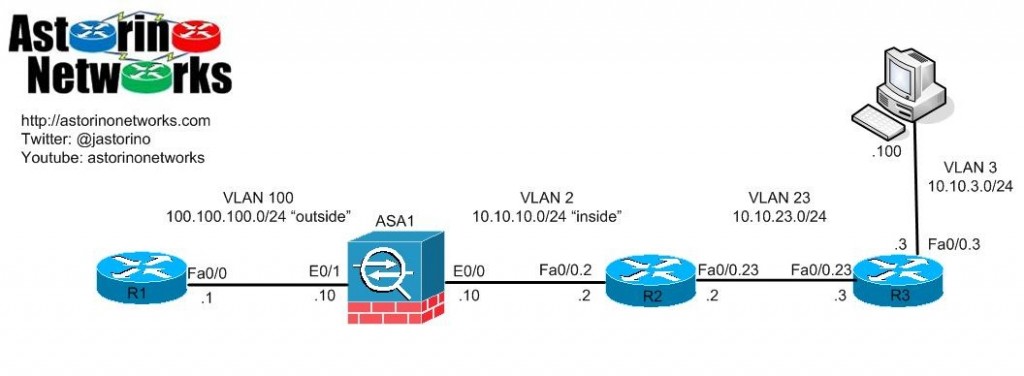
I have been labbing up this particular technology in an effort to understand it better. It is my personal opinion that the documentation is rather “lacking” in this particular area. The topic of interest is ASA ICMP error inspection. Note, we are NOT talking about standard ICMP inspection, but the inspection of ICMP error messages. Let’s look at our test bed for today:
What we have here is a pretty simple setup. To test our ICMP error inspection, we need to make it mildly more complicated. We will add a static NAT on the ASA such that the test PC at 10.10.3.100 is seen on the outside as 100.100.100.100. Note, OSPF has been configured on R2, R3 and the ASA for end to end IP connectivity. The ASA redistributes the outside 100.100.100.0/24 subnet into OSPF. NAT control is NOT being enforced. Let’s also make a simple outside ACL to permit our UNIX style traceroute. While we are at it we will allow ICMP echo-reply from the outside as well so we can ping R1 from the inside if need be for testing
static (inside,outside) 100.100.100.100 10.10.3.100 netmask 255.255.255.255 ! access-list OUTSIDE_IN extended permit udp host 100.100.100.1 any range 33434 33464 access-list OUTSIDE_IN extended permit icmp host 100.100.100.1 any echo-reply access-group OUTSIDE_IN in interface outside
Default Behavior (no inspect icmp error)
Let’s give this a try and see what happens by default.
R1#trace 100.100.100.100 Type escape sequence to abort. Tracing the route to 100.100.100.100 1 100.100.100.100 232 msec 252 msec 140 msec 2 100.100.100.100 532 msec 480 msec 612 msec 3 100.100.100.100 744 msec 584 msec 628 msec
Uhhhhh, OK…that is interesting. We have not enabled any kind of fancy inspection of any kind, yet we have some fairly strange output for our trace. All three hops show as 100.100.100.100, the global IP address of our server. Why? Well, we have to understand how traceroute normally works before we can understand how the ASA modifies it. Normally, the process would look something like this assuming no ASA is in the middle.
- R1 sends three UDP packets to 10.10.3.100 with a TTL of 1. These UDP packets are destined for ports 33434,33435 and 33436.
- As the next hop router R2 receives these packets, it decrements the TTL to 0 and thus has to send an ICMP time-exceeded message back to the source. R2 sends an ICMP time-exceeded sourced from 10.10.10.2 back to 100.100.100.1, one for each packet.
- R1 receives these three ICMP time-exceeded messages and now we now that R2 is the first “hop” towards the server. The first “hop” of our traceroute is complete
- The process repeats, but R1 sends three packets this time with a TTL of 2. Once the packets get to R3, R3 decrements the TTL to 0 and the same thing happens again.
- Eventually, we trace the entire path to the server and the server sends back an ICMP unreachable message. With no firewall in the middle, our trace looks like this assuming we had a route to 10.10.3.0/24 from R1
R1#trace 10.10.3.100 Type escape sequence to abort. Tracing the route to 10.10.3.100 1 10.10.10.2 232 msec 252 msec 140 msec 2 10.10.23.3 532 msec 480 msec 612 msec 3 10.10.3.100 744 msec 584 msec 628 msec
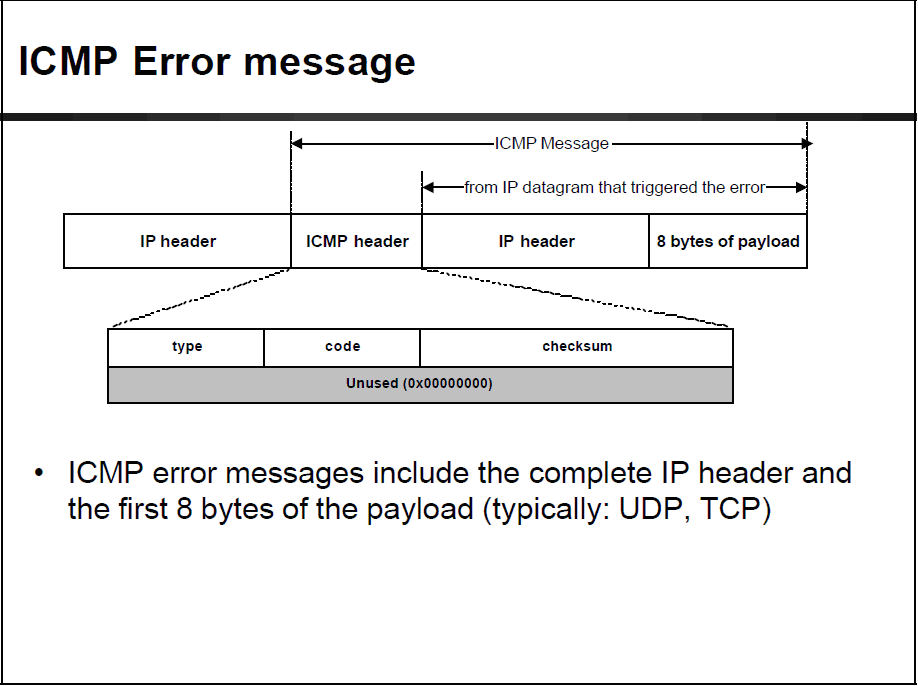
So, what happened? By default, the ASA doesn’t like to reveal any more than it has to. It does some crafty packet manipulation to hide the real IP address of the end destination we are tracing to AS WELL AS any intermediate hop routers between the firewall and the end destination. To fully understand what happens, we need to look at what an ICMP error packet looks like
The most interesting thing about this packet is that in the ICMP error payload, there is a record of the packet that caused the error in the first place. As you can see, the ICMP error payload carries the IP header of the original packet that triggered the error. This makes life a little more difficult when you have NAT involved in the process.
When R1 sends that first UDP packet in the traceroute, by the time the packet hits R2, the destination IP address has already been altered by the ASA due to the static NAT. When it hits R2 the packet is destined to 10.10.3.100. That means when R2 sends back the ICMP time-exceeded error message, in the payload of that ICMP message, the source and destination of the original message will be 100.100.100.1 –> 10.10.3.100.
What the ASA does by default is a couple of things. First, when R2 sends the ICMP time-exceeded back to R1, the ASA actually looks into that packet. It looks specifically at the ICMP payload, and it looks at the original IP packet source and destination as well as the original UDP source and destination port numbers. If those source/destination pairs match an existing connection flow that was setup through the ASA, a few different things happen. What do I mean by if it matches an existing connection? When R1 sent that first UDP packet, a connection was created in the ASA for 100.100.100.1/abcde going to 10.10.3.100 port 33434. When the ICMP error message coming back is looked into and the ASA sees that the original source/destination was 100.100.100.1/abcde –> 10.10.3.100/33434 it knows inherently that this is “return” traffic and it makes some changes to account for the NAT process. What happens if there is no match or there is a mismatch? The traffic is dropped. What happens if we were using Microsoft tracert instead, which does not use UDP, but ICMP? The same concept, but instead of tracking UDP ports it can look at ICMP sequence number pairs. So, what exactly happens?
The ASA changes the source IP address of that message to 100.100.100.100. This “hides” R2 as being an intermediate hop. We still have a problem with our secrecy though, because in the ICMP payload, the true IP address of our server, 10.10.3.100 is revealed in the “Original IP destination” field. To mask this behavior, the ASA also rewrites the ICMP payload such that the original IP destination address is changed back to 100.100.100.100. That way, from the perspective of R1 on the outside, it has no idea that there was a NAT in the process. The same thing happens as each other hop behind the ASA sends back the time-exceeded messages. That is why every hop comes back the same by default
Enabling ICMP error inspection
We have seen that by default, the ASA “hides” the real IP address of the host you are tracing to, and it also hides the IP addresses of any intermediate hops. It does this by manipulating information in the IP and ICMP header as the ICMP error messages pass through it back to the source. What if we don’t want that? What if we actually want to see intermediate hop routers along the way to our destination? That is where ICMP error inspection comes into play. We can enable this using the legacy command fixup protocol icmp error or by enabling it in the MPF like so:
policy-map global_policy class inspection_default inspect icmp error
Let’s enable that on our ASA and see what happens.
ASA(config)# policy-map global_policy ASA(config-pmap)# class inspection_default ASA(config-pmap-c)# inspect icmp error ASA(config-pmap-c)#
R1#trace 100.100.100.100 Type escape sequence to abort. Tracing the route to 100.100.100.100 1 10.10.10.2 464 msec 372 msec 308 msec 2 10.10.23.3 484 msec 324 msec 372 msec 3 100.100.100.100 728 msec 724 msec 404 msec
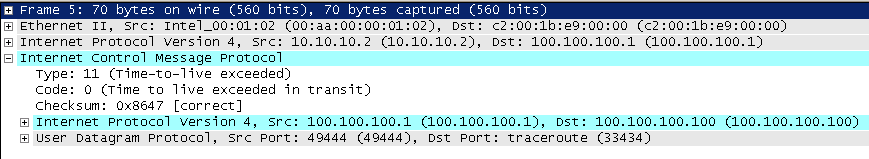
OK, we see all the hops! Keep in mind the ASA still does not show up as a hop itself. This is normal, as the ASA does NOT decrement the TTL when it routes packets through itself (clever!). Now, what happened? Well, for starters we no longer are changing the source IP address in the IP header to 100.100.100.100. That is the key that makes the “real” hops show up. In our case we do not have any other NAT going on, but if we had NAT translations for those intermediate hops, the translated addresses would show up in our traceroute instead of the real addresses. For example, if we translated 10.10.10.2 on the inside to 100.100.100.2 on the outside, our first hop here would have been 100.100.100.2. However, if we examine the actual ICMP payload we will see that the original IP destination field is STILL set to 100.100.100.100. The ASA still changes this field. The net result is that the intermediate hop routers are now visible to our trace, but ultimately the REAL IP address of our server remains a mystery to R1 and anybody else on the outside of our network. Here is a wireshark capture of the first ICMP time-exceeded message from R2 to R1 arriving at R1 AFTER the ASA has had it’s way with it.
Let’s step through a few things. We have enabled ICMP error inspection, so the source IP address is the REAL IP address of R2, 10.10.10.2. Good. Recall that when we have the feature disabled, the source IP was actually changed to the global IP of the server. The next important thing is the ICMP payload. As you see, it contains the IP header of the “original” packet that triggered the ICMP time-exceeded message. Notice that the DST field is set to 100.100.100.100. When the ASA received this packet from R2 that field was naturally set to 10.10.3.100, but the ASA altered it, thus hiding the real IP address of the server.
That about does it for ICMP error inspection on the ASA
The problem
I’ve been recently working for a customer which needed consultancy because of some unexplained Netfilter behaviors related to ICMP error messages. He authorizes me to share the result of my study and I thank him for making this blog entry possible.
His problem was that one of his firewalls is using a private interconnexion with their border router and the customer did not manage to NAT all outgoing ICMP error messages.
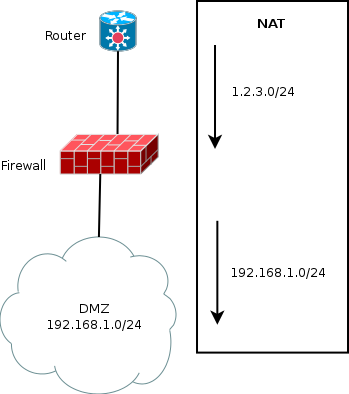
The simplified network diagram is the following:
The DMZ is in a private network. The router has a route to the public network via the firewall and the public network address do not exists.
The firewall has set of DNAT rules to redirect a public IP to the matching private IP:
iptables -A PREROUTING -t nat -d 1.2.3.X -j DNAT --to 192.168.1.X
The interconnection between the router and firewall is made using a private network. Let’s say 192.168.42.0/24 and 192.168.42.1 for the firewall. The interface eth0 is the one used as interconnection interface.
On the firewall, some filtering rules reject some FORWARD traffic:
iptables -A FORWARD -d 192.168.1.X -j REJECT iptables -A FORWARD -d 192.168.1.Y -j REJECT
The issue is related with the ICMP unreachable messages. When someone from internet (behind the router) is sending a packet to 192.168.1.X or 192.168.1.Y then:
- If 192.168.1.X is NATed then the ICMP unreachable message is emitted and seen as coming from 1.2.3.X on eth0.
- If 192.168.1.Y is not NATed then the ICMP unreachable message is emitted and seen as coming from 192.168.42.1 on eth0.
So, a packet going to 192.168.1.Y results in a ICMP message which is not routed by the router due to the private IP.
To fix the issue, the customer has added a Source NAT rules to translate all packet coming from 192.168.42.1 to 1.2.3.1:
iptables -A POSTROUTING -t nat -p icmp -s 192.168.42.1 -o eth0 -j SNAT --to 1.2.3.1
But this rules has no effect on the ICMP unreachable message.
Explanations
In the case of packets going to X or Y, an ICMP message is sent. Internally the same function (called icmp_send) is used for to send the icmp error message. This is a standard function and
as such, it uses the best local source address possible. In our case the best address is 192.168.42.1 because the packet has to get back through eth0.
At current stage, there is no difference between the two ICMP packets and the result should be the same.
But if nothing is done, the packet to X will result in a packet going to the original source and containing the internal IP information: the packet has been NATed so we have 192.168.1.X and not the public IP in the original packet data contained in the ICMP message. This is a real problem as this will leak private information to the outside.
Hopefully, the packets are handled differently due to the ICMP error connection tracking module. It searches in the payload part of the ICMP error message if it belongs to existing connection. If a connection is found, the IMCP packet is marked as RELATED to the original connection. Once this is done, the ICMP nat helper makes the reverse transformation to send to the network a packet containing only public information. For packet to X, the source addresses of the ICMP messages and payload are modified to the public IP address. This explains the difference between the ICMP error message sent because of packet sent to X or sent to Y.
But this does not explain why the NAT rules inserted by the customer did not work. In fact, the response was already made: the ICMP packet is marked as belonging to a connection related to the original one. Being in a RELATED state, it will not cross the NAT in POSTROUTING as only packet with a connection in state NEW are sent to the nat tables.
The validation of this study can be done by using marking and logging. If we log a packet which belong to a RELATED connection and if we are sure that the original connection is the one we are tracing then our hypothesis is validated. Getting a RELATED connection is easy with the filter: “-m conntrack –ctstate RELATED”. To prove that the packet is RELATED to the original connection, we have to use the fact that RELATED connection inherit of the connection mark of the originating connection. Thus, if we set a connection mark with the CONNMARK target, we will be able to match it in the ICMP error message. The following rules implement this:
iptables -t mangle -A PREROUTING -d 1.2.3.4 -j CONNMARK --set-mark 1 iptables -A OUTPUT -t mangle -m state --state RELATED -m connmark --mark 1 -j LOG
And it logs an ICMP error message when we try to reach 1.2.3.4.
Other debug methods
Using conntrack
The conntrack utils can be used to display connection tracking events by using the -E flag:
# conntrack -E
[NEW] tcp 6 120 SYN_SENT src=192.168.1.12 dst=91.121.96.152 sport=53398 dport=22 [UNREPLIED] src=91.121.96.152 dst=192.168.1.12 sport=22 dport=53398
[UPDATE] tcp 6 60 SYN_RECV src=192.168.1.12 dst=91.121.96.152 sport=53398 dport=22 src=91.121.96.152 dst=192.168.1.12 sport=22 dport=53398
[UPDATE] tcp 6 432000 ESTABLISHED src=192.168.1.12 dst=91.121.96.152 sport=53398 dport=22 src=91.121.96.152 dst=192.168.1.12 sport=22 dport=53398 [ASSURED]
This can be really useful to see what transformation are made by the connection tracking system. But this does not work in your case because the icmp message does not trigger any connection creation and so no event.
Using TRACE target
The TRACE target is a really useful tool. It allows you to see which rules are matched by a packet. It’s usage is really simple. For example, if we want to trace all ICMP traffic coming to the box:
iptables -A PREROUTING -t raw -p icmp -j TRACE
In our test system, the result was the following:
[ 5281.733217] TRACE: raw:PREROUTING:policy:2 IN=eth0 OUT= MAC=08:00:27:a9:f5:30:0a:00:27:00:00:00:08:00 SRC=192.168.56.1 DST=1.2.3.4 LEN=84 TOS=0x00 PREC=0x00 TTL=64 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=12114 SEQ=1 [ 5281.737057] TRACE: nat:PREROUTING:rule:1 IN=eth0 OUT= MAC=08:00:27:a9:f5:30:0a:00:27:00:00:00:08:00 SRC=192.168.56.1 DST=1.2.3.4 LEN=84 TOS=0x00 PREC=0x00 TTL=64 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=12114 SEQ=1 [ 5281.737057] TRACE: nat:PREROUTING:rule:2 IN=eth0 OUT= MAC=08:00:27:a9:f5:30:0a:00:27:00:00:00:08:00 SRC=192.168.56.1 DST=1.2.3.4 LEN=84 TOS=0x00 PREC=0x00 TTL=64 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=12114 SEQ=1 [ 5281.737057] TRACE: filter:FORWARD:rule:1 IN=eth0 OUT=eth1 MAC=08:00:27:a9:f5:30:0a:00:27:00:00:00:08:00 SRC=192.168.56.1 DST=192.168.42.4 LEN=84 TOS=0x00 PREC=0x00 TTL=63 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=12114 SEQ=1
In the raw TABLE, in PREROUTING the policy is applied (here ACCEPT). In nat PREROUTING the first rule is matching (a mark rule) and the second one is matching too. Finally in FORWARD, the first rule is matching (here the REJECT rule). TRACE is only following the initial packet and thus does not display any information about the ICMP error message.
Conclusion
So Netfilter’s behavior is correct when it translate back the elements initially transformed by NAT. The surprising part comes from the fact that the NAT rules in POSTROUTING are not reach. But this is needed to avoid any complicated issue by doing multiple transformation. Regarding interconnexion with router, you should really use a public network if you want your ICMP error messages to be seen on Internet.