try {
//code
} catch (ParseException e) {
e.printStackTrace();
} catch (MalformedURLException e) {
LOG.error("Error in finding Resource Bundle", e);
}
I wrote like that, but when I am using Checkmarx code analysis tool I am getting «Information Exposure Through an Error Message». How to resolve and when this we get.
Alex Gyoshev
11.9k4 gold badges48 silver badges74 bronze badges
asked Dec 26, 2016 at 9:57
1
What is Information Exposure Through an Error Message?
The software generates an error message that includes sensitive information about its environment, users, or associated data.
The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack.
(Quote taken from CWE-209: Information Exposure Through an Error Message
)
You did not specify, but I’m assuming that the Checkmarx tool pointed to printStackTrace() as the problematic end point of the flow.
By using this method, an exception (including its entire stack trace) will be printed to the standard error stream. This might include information that may be sensitive by itself (like usernames or passwords) or at least disclose some environment data. If this data is exposed to a user, it can be abused or used maliciously for more effective attacks.
There are many others reasons not to use printStackTrace() that way, as can be seen here: Why is exception.printStackTrace() considered bad practice?
answered Dec 26, 2016 at 11:03
5
First of all remove e.printStackTrace();.
Now, As its compulsory to log errors so, you can;t remove LOG.error("Error in finding Resource Bundle", e);.
So, just provide the closure for this .. that Logs are being generated. As this is LOW critical their is no big issue.
This happens every-time with our project too 
answered Dec 26, 2016 at 12:06
Atul SharmaAtul Sharma
8,89610 gold badges37 silver badges63 bronze badges
Содержание
- Information Exposure Through an Error Message #462
- Comments
- Issue Description and Impact:-
- Recommendation:-
- Information Exposure Through Externally-Generated Error Message [CWE-211]
- Table of Content
- 1. Description
- 2. Potential impact
- 3. Exploitation Examples
- 4. Severity and CVSS Scoring
- 5. Mitigations
- Information Exposure [CWE-200]
- Table of Content
- 1. Description
- 2. Potential impact
- 3. Attack patterns
- 4. Affected software
- 5. Exploitation Examples
- 6. Severity and CVSS Scoring
- 7. Mitigations
- 8. References
- 9. Information Exposure Vulnerabilities, Exploits and Examples
Information Exposure Through an Error Message #462
Location in Source Code:-
/com/netflix/zuul/context/RequestContext.java (Line 730)
/com/netflix/zuul/FilterFileManager.java (Line 110)
/com/netflix/zuul/FilterProcessor.java (Line 323, 501, 311, 344, 299, 269, 414, 462)
/com/netflix/zuul/ZuulFilter.java (Line 195, 239)
/com/netflix/zuul/ZuulRunner.java (Line 167)
/com/netflix/zuul/filters/ZuulServletFilter.java (Line 195, 168, 250, 223)
/com/netflix/zuul/http/ZuulServlet.java (Line 196)
/com/netflix/zuul/util/DeepCopy.java (Line 52, 54)
Issue Description and Impact:-
The application generates an error message including raw exceptions, either by not being handled, by explicit returning of the object, or by configuration. Exception details may include sensitive information that could leak out of the exception to the users.
Exposed details about the application’s environment, users, or associated data (for example, stack trace) could enable an attacker to find another flaw and help the attacker to mount an attack.
Recommendation:-
It is recommended that any method that could cause an exception should be wrapped in a try-catch block that: 1. Explicitly handles expected exceptions. 2. Includes a default solution to explicitly handle unexpected exceptions. Further, it is recommended to configure a global handler to prevent unhandled errors from leaving the application.
The text was updated successfully, but these errors were encountered:
Источник
Information Exposure Through Externally-Generated Error Message [CWE-211]
Information Exposure Through Externally-Generated Error Message describes information exposure case where software generates a message with potentially sensitive data and outputs it.
Created: December 10, 2013
Latest Update: December 28, 2020
Table of Content
Want to have an in-depth understanding of all modern aspects of Information Exposure Through Externally-Generated Error Message [CWE-211]? Read carefully this article and bookmark it to get back later, we regularly update this page.
1. Description
This weakness describes information disclosure case where software performs an operation that triggers an error or diagnostic message in an external component. It is a child element of Information Exposure weakness and should be treated as such.
An example of this weakness is an error generated by the programming language interpreter used by software. The provided error message may contain potentially sensitive information and can be used to advance the attack surface.
This weakness can be introduced on design, implementation or operation stages of software development process and is not restricted to certain programming languages; PHP however is the most common and popular example.
The exposed information can be divided into two groups:
- Exposure of system information
e.g. file system structure, installation directory, installed software and its versions, etc. - Exposure of sensitive data
e.g. database structure, memory dump, login credentials, etc.
Exposure of error messages is often used to determine vulnerabilities that exist within the application, such as PHP File Inclusion, or SQL injection, and is helpful for performing advanced attacks against the application. Knowledge of web application document root is extremely valuable when exploiting PHP local file inclusions, since it is possible to determine possible log file location to include and execute PHP code stored in webserver log files.
2. Potential impact
An attacker might be able to gain access to restricted information and use it to widen the attack surface. Depending on the disclosed information, it might be possible to escalate privileges within the application or, in rare cases, to gain complete control over the system.
- GDPR & PCI DSS Test
- Website CMS Security Test
- CSP & HTTP Headers Check
- WordPress & Drupal Scanning
Try For Free
3. Exploitation Examples
Let’s have a look at certain common cases of this weakness.
Example 1
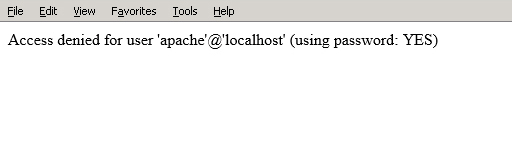
The application uses incorrect credentials to connect to database. The error message generated by PHP exposes database user and database host:
Example 2
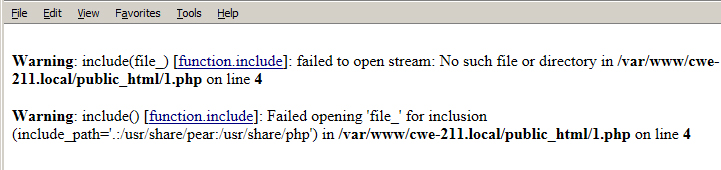
The application uses the PHP » include() » function to include non-existent file. As a result, PHP generates an error message that includes full path to the application and certain system configuration.
As we can see from examples above, the application outputs data that can be useful for an attacker to e.g. perform a brute-force attack or gain knowledge of file system structure.
4. Severity and CVSS Scoring
Here is a scoring example of installation path disclosure.
3.7 [CVSS:3.0/AV: N /AC: H /PR: N /UI: N /S: U /C: L /I: N /A: N ] — Low severity.
5. Mitigations
The best way to protect your system against this weakness is to disable any output of error messages. Here are basic rules that should be followed when creating and implementing the application. Be sure that the application:
- does not generate errors accessible to others
- does not output debugging information
- handles errors internally and does not display errors that may contain potentially sensitive data
- sanitizes all input and does not send unverified data to external components that might trigger unhandled exceptions (e.g. division by zero, fatal errors).
The environment should be also configured not to output additional information.
Источник
Information Exposure [CWE-200]
Information disclosure weakness describes intentional or unintentional disclosure of information that is considered sensitive.
Created: September 11, 2012
Latest Update: December 28, 2020
Table of Content
Want to have an in-depth understanding of all modern aspects of Information Exposure [CWE-200]? Read carefully this article and bookmark it to get back later, we regularly update this page.
1. Description
This weakness could be result of numerous types of problems that involve exposure of sensitive information. The information is considered sensitive when:
- It is sensitive within the product functionality (e.g. information with restricted access, private messages, etc.)
- It contains data about the product itself, its environment or the related system that is not intended be disclosed by the application.
CWE-200 is a parent for the following weaknesses:
- CWE-201: Information Exposure Through Sent Data
- CWE-202: Exposure of Sensitive Data Through Data Queries
- CWE-203: Information Exposure Through Discrepancy
- CWE-209: Information Exposure Through an Error Message
- CWE-211: Information Exposure Through Externally-Generated Error Message
- CWE-212: Improper Cross-boundary Removal of Sensitive Data
- CWE-213: Intentional Information Exposure
- CWE-214: Information Exposure Through Process Environment
- CWE-215: Information Exposure Through Debug Information
- CWE-226: Sensitive Information Uncleared Before Release
- CWE-497: Exposure of System Data to an Unauthorized Control Sphere
- CWE-524: Information Exposure Through Caching
- CWE-526: Information Exposure Through Environmental Variables
- CWE-538: File and Directory Information Exposure
- CWE-598: Information Exposure Through Query Strings in GET Request
- CWE-612: Information Exposure Through Indexing of Private Data
2. Potential impact
Potential impact can vary depending on application, environment and other circumstances. There are many different problems that involve information leaks and their severity can be widely ranged based on information that is disclosed.
- GDPR & PCI DSS Test
- Website CMS Security Test
- CSP & HTTP Headers Check
- WordPress & Drupal Scanning
Try For Free
3. Attack patterns
The following CAPEC vectors are related to information disclosure weakness:
In WASC Threat Classification this weakness is described as an attack and weakness under WASC-45 (Fingerprinting) and WASC-13 (Information Leakage) respectively.
4. Affected software
Basically all types of software can be vulnerable to this issue.
5. Exploitation Examples
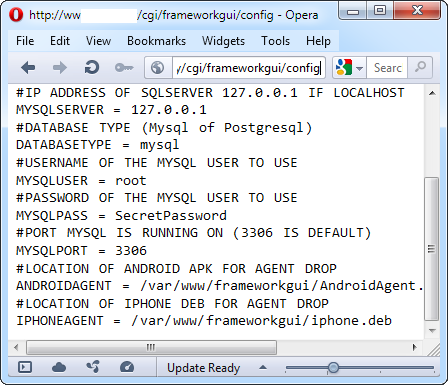
Let’s have a look at the HTB23123 security advisory (CVE-2012-5696). The vulnerability allows a malicious user to access configuration file via HTTP request by accessing the file directly. We will use the following URL to access the configuration file:
http://[host]/frameworkgui/config
The output is shown on the image below:
As we can see, it is possible to view contents of the file that contains credentials for accessing the database along with other configuration options.
6. Severity and CVSS Scoring
When scoring information disclosure weaknesses security specialists must consider the maximum possible impact. If an attacker can gain access to certain parts of information or he does not have control over what is obtained the weakness should be scored as C: P . If an attacker is able to read all system data (e.g. files, memory) it should be scored as C: C . Usually, when information exposure is the only weakness presented in application it is scored as C: P .
For a web application disclosure of files should be scored as:
7.5 [CVSS:3.0/AV: N /AC: L /PR: N /UI: N /S: U /C: H /I: N /A: N ] – High severity.
7. Mitigations
For CWE-211 [Information Exposure Through Externally-Generated Error Message] mitigation techniques please refer to this article.
The main approach in defending sensitive data is to use safe mechanisms to store and access information. But first, information assets should be identified in order to determine what exactly should be protected and how. There are certain certifications, standards and compliance requirements when dealing with classified information, which are far beyond the scope of this article. Here, however, we will try to provide basic understanding of information types and give general advices to developers. We suggest dividing information into two categories:
System information
It should be obvious from the category name that here we are talking about system related data, such as file system structure, system users, installed software, system log files, etc. This is basically any information that reveals environment of the application or asset. To prevent system information exposure follow these recommendations:
- General recommendations
- Never run applications in debug mode on production servers,
- Use least privilege approach and proper file system permissions,
- Run remotely accessible applications in chroot/sandbox environments,
- Never store log files with world-readable permissions;
- Web site environment
- Disable directory listing to prevent exposure of web site structure and potentially sensitive files,
- Use custom error pages that prevent from displaying excessive system information,
- Disable error reporting output into the client’s browser,
- Use IP-based approach to access sensitive directories or restrict access to directories otherwise.
You can use the following Cheat Sheet when configuring your webserver:
| Action needed | Examples |
|---|---|
| Disable debugging output PHP |
Change the value for «display_errors» to «off» in PHP configuration file php.ini: display_errors=0 |
| Disable debugging output IIS |
Edit the Web.config file file and set «debug» attribute to «false»: |
| Disable debugging output ColdFusion |
Use the cfsetting tag showDebugOutput attribute to turn off debugging output for a specific page: |
| Disable debugging output NodeJS |
Set the NODE_ENV to production to disable stack traces being returned upon error conditions: set NODE_ENV=production |
| Custom error pages IIS |
To add custom error pages follow instructions below: To add a custom error, use the following syntax: appcmd set config /section:httpErrors /+»[statusCode=’ int ‘,subStatusCode=’ int ‘, prefixLanguageFilePath=’ string ‘,path=’ string ‘, responseMode = ‘File|ExecuteURL|Redirect’]» For more information on custom error pages refer to TechNet web site: http://technet.microsoft.com/en-us/library/cc753103(v=ws.10).aspx |
| Custom error pages in Apache |
To change the default error pages use the «ErrorDocument» directive in your webserver configuration. These pages can be changed globally for every web site hosted by Apache HTTP server using httpd.conf file or for each site via .htaccess files. For example: ErrorDocument 500 «Sorry, our script crashed. Oh dear» For more information on custom error pages refer to official documentation: http://httpd.apache.org/docs/current/custom-error.html |
| Custom error pages Nginx |
Use the following configuration to change the default error page: error_page / .html; location /.html < internal; > where ErrNo is number of HTTP Error. For example: error_page 403 /403.html; location = /403.html < root html; allow all; > For more information refer to official documentation: http://nginx.org/en/docs/http/ngx_http_core_module.html#error_page |
| Custom error pages NodeJS |
You can create custom classes in NodeJS that handle error conditions, by extending the Error class: class CustomError extends Error < |
| Restrict access Nginx |
You can restrict access to sensitive script «/admin.php» using the following configuration: location = /admin.php < deny all; > |
| Restrict access IIS |
You can restrict access to sensitive script «admin.aspx» using the following configuration: |
| Restrict access Apache |
You can restrict access to sensitive script «admin.php» using the following configuration: Order allow,deny Deny from all |
Sensitive information
This category contains the actual information we want to protect, such as passwords, valuable data etc. Developers should always pay attention to privileges within the application and information that can be accessed by application itself. All sensitive data should be encrypted and stored in safe places. This particularly applies to:
- Passwords,
- Backup copies,
- Any other information that might have a value for potential intruder (e.g. sensitive documents, sensitive configuration data, etc.).
When deploying the application, pay attention to files that may contain sensitive data as well as access control lists applied to these files. When dealing with web applications, place all sensitive content outside the webroot directory or make sure that access to these files is restricted to application itself (e.g. the file cannot be directly accessed using a web browser). Never output debug information to user’s browser, use log files outside the webroot directory instead.
8. References
- CWE-200: Information Exposure [cwe.mitre.org]
- Information Leakage [projects.webappsec.org]
9. Information Exposure Vulnerabilities, Exploits and Examples
Copyright Disclaimer: Any above-mentioned content can be copied and used for non-commercial purposes only if proper credit to ImmuniWeb is given.
Источник
try {
//code
} catch (ParseException e) {
e.printStackTrace();
} catch (MalformedURLException e) {
LOG.error("Error in finding Resource Bundle", e);
}
Я написал так, но когда я использую инструмент анализа кода Checkmarx, я получаю «раскрытие информации через сообщение об ошибке». Как решить и когда это у нас получится.
2 ответа
Что такое раскрытие информации через сообщение об ошибке ?
Программное обеспечение выдает сообщение об ошибке, которое включает конфиденциальную информацию о своей среде, пользователях или связанных данных.
Конфиденциальная информация может быть ценной информацией сама по себе (например, пароль) или может быть полезна для запуска других, более смертоносных атак. Если атака не удалась, злоумышленник может использовать информацию об ошибке, предоставленную сервером, для запуска другой, более целенаправленной атаки.
(Цитата из CWE-209: раскрытие информации через сообщение об ошибке)
Вы не указали, но я предполагаю, что инструмент Checkmarx указал на printStackTrace() как на проблемную конечную точку потока.
При использовании этого метода исключение (включая всю трассировку стека) будет распечатано в стандартный поток ошибок. Это может включать информацию, которая может быть конфиденциальной сама по себе (например, имена пользователей или пароли) или, по крайней мере, раскрывать некоторые данные среды. Если эти данные будут доступны пользователю, они могут быть использованы злонамеренно или злонамеренно для более эффективных атак.
Есть много других причин не использовать printStackTrace() таким образом, как можно увидеть здесь: Почему exception.printStackTrace () считается плохой практикой?
2
Community
20 Июн 2020 в 12:12
Прежде всего удалите e.printStackTrace();.
Теперь, поскольку это обязательное занятие для регистрации ошибок, вы не можете удалить LOG.error("Error in finding Resource Bundle", e);.
Так что просто закройте это .. это Logs are being generated. Поскольку это LOW критично, для них нет большой проблемы.
Это происходит каждый раз и с нашим проектом: P.
0
Atul Sharma
26 Дек 2016 в 15:06