Hello I am very new to ubuntu, I installed wireguard almost 6 months ago, and it was working fine, untill yesterday when my ubuntu was updated, the wirguard does not want to come up, and gives the below status:
May 31 08:41:03 lenovo systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
May 31 08:41:03 lenovo wg-quick[5463]: [#] ip link add wg0 type wireguard
May 31 08:41:03 lenovo wg-quick[5463]: Error: Unknown device type.
May 31 08:41:03 lenovo wg-quick[5463]: Unable to access interface: Protocol not supported
May 31 08:41:03 lenovo wg-quick[5463]: [#] ip link delete dev wg0
May 31 08:41:03 lenovo wg-quick[5463]: Cannot find device "wg0"
May 31 08:41:03 lenovo systemd[1]: wg-quick@wg0.service: Main process exited, code=exited,
status=1/FAILURE
May 31 08:41:03 lenovo systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
May 31 08:41:03 lenovo systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
here is my ubuntu version: Ubuntu 18.04.4 LTS
FedKad
7,7185 gold badges36 silver badges69 bronze badges
asked May 31, 2020 at 12:59
Try reinstalling package wireguard-dkms (remove and install again). Probably afterwards a reboot will be needed.
answered Jun 5, 2020 at 14:19
1
Run the Following commands :
sudo apt-get update
sudo apt-get upgrade
sudo systemctl enable --now systemd-resolved
and reboot the system
It has worked in my case, I hope it will be helpful to you!
answered Sep 21, 2020 at 11:08
for me the dkms way proposed by @Błotosmętek worked in the beginning, but after doing an experimental systemctl restart ... it never recovered, with errors such as:
Sep 10 10:46:46 ryzen wg-quick[6005]: RTNETLINK answers: File exists
Sep 10 10:46:46 ryzen wg-quick[5915]: [#] resolvconf -d tun.wg0 -f
Sep 10 10:46:46 ryzen wg-quick[5915]: [#] ip link delete dev wg0
Sep 10 10:46:46 ryzen systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=2/INVALIDARGUMENT
Sep 10 10:46:46 ryzen systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
Sep 10 10:46:46 ryzen systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
Thus resorted to the networkmanager way described here: https://www.xmodulo.com/wireguard-vpn-network-manager-gui.html
answered Sep 10, 2022 at 9:30
dimisjimdimisjim
2632 silver badges11 bronze badges
Hello I am very new to ubuntu, I installed wireguard almost 6 months ago, and it was working fine, untill yesterday when my ubuntu was updated, the wirguard does not want to come up, and gives the below status:
May 31 08:41:03 lenovo systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
May 31 08:41:03 lenovo wg-quick[5463]: [#] ip link add wg0 type wireguard
May 31 08:41:03 lenovo wg-quick[5463]: Error: Unknown device type.
May 31 08:41:03 lenovo wg-quick[5463]: Unable to access interface: Protocol not supported
May 31 08:41:03 lenovo wg-quick[5463]: [#] ip link delete dev wg0
May 31 08:41:03 lenovo wg-quick[5463]: Cannot find device "wg0"
May 31 08:41:03 lenovo systemd[1]: wg-quick@wg0.service: Main process exited, code=exited,
status=1/FAILURE
May 31 08:41:03 lenovo systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
May 31 08:41:03 lenovo systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
here is my ubuntu version: Ubuntu 18.04.4 LTS
FedKad
7,7185 gold badges36 silver badges69 bronze badges
asked May 31, 2020 at 12:59
Try reinstalling package wireguard-dkms (remove and install again). Probably afterwards a reboot will be needed.
answered Jun 5, 2020 at 14:19
1
Run the Following commands :
sudo apt-get update
sudo apt-get upgrade
sudo systemctl enable --now systemd-resolved
and reboot the system
It has worked in my case, I hope it will be helpful to you!
answered Sep 21, 2020 at 11:08
for me the dkms way proposed by @Błotosmętek worked in the beginning, but after doing an experimental systemctl restart ... it never recovered, with errors such as:
Sep 10 10:46:46 ryzen wg-quick[6005]: RTNETLINK answers: File exists
Sep 10 10:46:46 ryzen wg-quick[5915]: [#] resolvconf -d tun.wg0 -f
Sep 10 10:46:46 ryzen wg-quick[5915]: [#] ip link delete dev wg0
Sep 10 10:46:46 ryzen systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=2/INVALIDARGUMENT
Sep 10 10:46:46 ryzen systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
Sep 10 10:46:46 ryzen systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
Thus resorted to the networkmanager way described here: https://www.xmodulo.com/wireguard-vpn-network-manager-gui.html
answered Sep 10, 2022 at 9:30
dimisjimdimisjim
2632 silver badges11 bronze badges
I recently installed Raspberry Pi OS on my Pi 3b. After some basic configuration and running raspi-config, I installed wireguard using apt and the debian backport repos, according to a tutorial.
I wasn’t able to start the service though:
# systemctl start wg-quick@wg0
Job for wg-quick@wg0.service failed because the control process exited with error code.
See "systemctl status wg-quick@wg0.service" and "journalctl -xe" for details.
# journalctl -u wg-quick@wg0
raspberrypi systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
raspberrypi wg-quick[1773]: [#] ip link add wg0 type wireguard
raspberrypi wg-quick[1773]: Error: Unknown device type.
raspberrypi wg-quick[1773]: Unable to access interface: Protocol not supported
raspberrypi wg-quick[1773]: [#] ip link delete dev wg0
raspberrypi wg-quick[1773]: Cannot find device "wg0"
raspberrypi systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=1/FAILURE
raspberrypi systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
raspberrypi systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
The key lines are Unknown device type and Unable to access interface: Protocol not supported. It seems like wireguard isn’t able to create a new wireguard interface, as if the kernel module didn’t exist…
asked Jul 24, 2020 at 3:14
According to a comment on r/Wireguard, this error is caused by having the wrong kernel headers:
dkms packages (wireguard-dkms this time) need kernel headers for
current kernel you have loaded (uname -a). As long as kernel is
updated through apt or aptitude you should not run into problems, but
if you update kernel with rpi-update you’ll likely get newer kernel
than what is available through package repository and there will be no
headers available for it
The Foundation now offers headers for the rpi kernel, they just have to be installed. From the official online documentation on kernel headers:
If you are compiling a kernel module or similar, you will need the
Linux Kernel headers. These provide the various function and structure
definitions required when compiling code that interfaces with the
kernel.sudo apt install raspberrypi-kernel-headersNote that it can take quite a while for this command to complete, as
it installs a lot of small files. There is no progress indicator.
After installing raspberrypi-kernel-headers, and rebooting, Wireguard started normally.
answered Jul 24, 2020 at 3:14
ki9ki9
2961 gold badge2 silver badges11 bronze badges
2
I haven’t followed the tutorial you used but wireguard is heavy under development and there are some outdated installation tutorials on the web. Try this Wireguard installation that uses an official backport from Debian Bullseye. I have just tested it again with success.
answered Jul 27, 2020 at 18:41
IngoIngo
41k15 gold badges79 silver badges191 bronze badges
For those that have the same issue but had a working wireguard set-up, (Linux headers were installed in the past) a bad kernel update may provoke a Linux headers mismatch.
I tried the following command:
sudo dpkg-reconfigure raspberrypi-kernel-headers
and that solved my issue.
answered Oct 14, 2020 at 19:47
1
On recent distributions there is no tinkering with the headers necessary. However, the Pi needs a reboot after installing wireguard.
answered Aug 17, 2022 at 13:32
bombenbomben
2993 silver badges12 bronze badges
- Index
- » Networking, Server, and Protection
- » [SOLVED] Wireguard connection error, can’t connect
Pages: 1
#1 2021-02-09 14:42:58
- Celsiuss
- Member
- Registered: 2020-11-05
- Posts: 15
[SOLVED] Wireguard connection error, can’t connect
When I try to connect with wg-quick, I get these errors:
$ sudo wg-quick up wg0
[#] ip link add wg0 type wireguard
Error: Unknown device type.
Unable to access interface: Protocol not supported
[#] ip link delete dev wg0
Cannot find device "wg0"Then I checked if the module is loaded
$ sudo modprobe wireguard && lsmod | grep -i wireguard
modprobe: FATAL: Module wireguard not found in directory /lib/modules/5.10.11-arch1-1Shouldn’t wireguard be included in the newest kernels?
Last edited by Celsiuss (2021-02-09 14:58:21)
#2 2021-02-09 14:47:04
- frostschutz
- Member
- Registered: 2013-11-15
- Posts: 1,243
Re: [SOLVED] Wireguard connection error, can’t connect
Did you update kernel and not reboot? pacman unfortunately removes modules of the still running kernel … leaving you unable to load any module, forcing you to reboot.
# find /lib/modules -iname "*wireguard*"
/lib/modules/5.10.13-arch1-2/kernel/drivers/net/wireguard
/lib/modules/5.10.13-arch1-2/kernel/drivers/net/wireguard/wireguard.ko.xz
# pacman -Syu
[...]
# find /lib/modules -iname "*wireguard*"
/lib/modules/5.10.14-arch1-1/kernel/drivers/net/wireguard
/lib/modules/5.10.14-arch1-1/kernel/drivers/net/wireguard/wireguard.ko.xz
# uname -a
Linux ALU 5.10.13-arch1-1 #1 SMP PREEMPT Wed, 03 Feb 2021 23:44:07 +0000 x86_64 GNU/Linux
# modprobe / insmod will fail at this point until you rebootLast edited by frostschutz (2021-02-09 14:51:19)
#3 2021-02-09 14:57:59
- Celsiuss
- Member
- Registered: 2020-11-05
- Posts: 15
Re: [SOLVED] Wireguard connection error, can’t connect
Thanks, that seems to be my problem
This script is not working in Iran.
Everything is successfully installed and configuration file in generated, but there is no internet connection after connecting to wireguard. However i see people using wireguard and i don’t know which script they are using. I think something should be changed in this script in case of successful connection.
Thanks!
+1 this issue. this script is broken; when a connection is established (with default settings) nothing works.
No I’m in the US.
Spun up a new digital ocean instance and ran this script, but I couldn’t connect.
Which OS did you use?
Android and Windows.
I spun up a digital ocean droplet to run this script. That droplet was running Linux.
DO supports a variety of Linux distributions:
Sorry, forgot to specify. Ubuntu 18.04.
created centos server updated run this script and this is the systemctl status
[root@centos-s-1vcpu-1gb-fra1-01 ~]# systemctl status wg-quick@wg0
wg-quick@wg0.service - WireGuard via wg-quick(8) for wg0
Loaded: loaded (/usr/lib/systemd/system/wg-quick@.service; enabled; vendor preset: disabled)
Active: failed (Result: exit-code) since Sun 2020-06-21 17:40:34 UTC; 2min 46s ago
Docs: man:wg-quick(8)
man:wg(8)
https://www.wireguard.com/
https://www.wireguard.com/quickstart/
https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8
https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8
Process: 925 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=1/FAILURE)
Main PID: 925 (code=exited, status=1/FAILURE)
Jun 21 17:40:33 centos-s-1vcpu-1gb-fra1-01 systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 wg-quick[925]: [#] ip link add wg0 type wireguard
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 wg-quick[925]: Error: Unknown device type.
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 wg-quick[925]: Unable to access interface: Protocol not supported
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 wg-quick[925]: [#] ip link delete dev wg0
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 wg-quick[925]: Cannot find device "wg0"
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=1/FAILURE
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 systemd[1]: wg-quick@wg0.service: Failed with result 'exit-code'.
Jun 21 17:40:34 centos-s-1vcpu-1gb-fra1-01 systemd[1]: Failed to start WireGuard via wg-quick(8) for wg0.
[root@centos-s-1vcpu-1gb-fra1-01 ~]#
Created Config files
[root@centos-s-1vcpu-1gb-fra1-01` wireguard]# [root@centos-s-1vcpu-1gb-fra1-01 wireguard]# cat params
SERVER_PUB_IP=[actualIP]
SERVER_PUB_NIC=eth0
SERVER_WG_NIC=wg0
SERVER_WG_IPV4=10.66.66.1
SERVER_WG_IPV6=fd42:42:42::1
SERVER_PORT=50396
SERVER_PRIV_KEY=[privKey]
SERVER_PUB_KEY=[pubKey]
[root@centos-s-1vcpu-1gb-fra1-01 wireguard]# cat wg0.conf
[Interface]
Address = 10.66.66.1/24,fd42:42:42::1/64
ListenPort = 50396
PrivateKey = [privKey]
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE; ip6tables -A FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE; ip6tables -D FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = [pubKey]
PresharedKey = [presharedKey]
AllowedIPs = 10.66.66.2/32,fd42:42:42::2/128
[root@centos-s-1vcpu-1gb-fra1-01 wireguard]#
trying to load conf
[root@centos-s-1vcpu-1gb-fra1-01 ~]# wg-quick up /etc/wireguard/wg0.conf
[#] ip link add wg0 type wireguard
Error: Unknown device type.
Unable to access interface: Protocol not supported
[#] ip link delete dev wg0
Cannot find device "wg0"
Trying Debian same result. I update and upgrade first then start the script.
Following lines are intresting
dpkg: dependency problems prevent configuration of wireguard:
wireguard depends on wireguard-modules (>= 0.0.20191219) | wireguard-dkms (>= 0.0.20200121-2); however:
Package wireguard-modules is not installed.
Package wireguard-dkms is not configured yet.
dpkg: error processing package wireguard (--configure):
dependency problems - leaving unconfigured
Processing triggers for systemd (241-7~deb10u4) ...
Processing triggers for libc-bin (2.28-10) ...
Processing triggers for resolvconf (1.79) ...
Errors were encountered while processing:
wireguard-dkms
wireguard
Done.
Loading new wireguard-1.0.20200520 DKMS files...
Building for 4.19.0-8-cloud-amd64
Building initial module for 4.19.0-8-cloud-amd64
Error! Bad return status for module build on kernel: 4.19.0-8-cloud-amd64 (x86_64)
Consult /var/lib/dkms/wireguard/1.0.20200520/build/make.log for more information.
dpkg: error processing package wireguard-dkms (--configure):
installed wireguard-dkms package post-installation script subprocess returned error exit status 10
dpkg: dependency problems prevent configuration of wireguard:
wireguard depends on wireguard-modules (>= 0.0.20191219) | wireguard-dkms (>= 0.0.20200121-2); however:
Package wireguard-modules is not installed.
Package wireguard-dkms is not configured yet.
dpkg: error processing package wireguard (--configure):
dependency problems - leaving unconfigured
Errors were encountered while processing:
wireguard-dkms
wireguard
Yes, the wireguard-dkms package has been broken for days now…
I just tried again on Debian 10 and it seems to be working fine:
root@scw-hungry-wu:~# systemctl status wg-quick@wg0
● wg-quick@wg0.service - WireGuard via wg-quick(8) for wg0
Loaded: loaded (/lib/systemd/system/wg-quick@.service; enabled; vendor preset: enabled)
Active: active (exited) since Mon 2020-06-22 09:45:25 UTC; 1min 16s ago
Docs: man:wg-quick(8)
man:wg(8)
https://www.wireguard.com/
https://www.wireguard.com/quickstart/
https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8
https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8
Process: 10102 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=0/SUCCESS)
Main PID: 10102 (code=exited, status=0/SUCCESS)
Jun 22 09:45:25 scw-hungry-wu systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] ip link add wg0 type wireguard
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] wg setconf wg0 /dev/fd/63
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] ip -4 address add 10.66.66.1/24 dev wg0
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] ip -6 address add fd42:42:42::1/64 dev wg0
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] ip link set mtu 1420 up dev wg0
Jun 22 09:45:25 scw-hungry-wu wg-quick[10102]: [#] iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o ens2 -j MASQUERADE; ip6tables -A FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -A POSTROUTING -o ens2 -j MASQUERADE
Jun 22 09:45:25 scw-hungry-wu systemd[1]: Started WireGuard via wg-quick(8) for wg0.
root@scw-hungry-wu:~# dpkg -l | grep wireguard
ii wireguard 1.0.20200513-1~bpo10+1 all fast, modern, secure kernel VPN tunnel (metapackage)
ii wireguard-dkms 1.0.20200611-1~bpo10+1 all fast, modern, secure kernel VPN tunnel (DKMS version)
ii wireguard-tools 1.0.20200513-1~bpo10+1 amd64 fast, modern, secure kernel VPN tunnel (userland utilities)
Maybe it has something to do with the packages on digital ocean
I tried on DO:
- Debian: it’s broken, idk why
- Ubuntu: works after a reboot
- CentOS: need an update + reboot (hence the warning at the end of the script)
Worked after reboot for me as well.
I also have problems on a pulseheberg vps with debian 10, install works, status doesn’t specify any errors and I can connect but after that nothing happens.
Can confirm that wireguard works on Ubuntu 18.04 after a reboot.
Yes, It was the same issue for me using ubuntu 18.04 then It works after i reboot the server. Thanks
i tried it on centos7 fresh install and ubuntu18.04 fresh install, on centos7 handshake was not successful and i tried everything to fix it but no luck, on the ubuntu i got it work after reboot but honestly its kinda weird, connection seems to be very faulty, no stability at all and when its connected its very slow around 0.05 Mb/ps on 40Mb/ps network, i dont know what to do, any help would be much appreciated.
weird enough i also live in iran, dont see any correlation with the problem but…
and vps servers are from HETZNER
@angristan
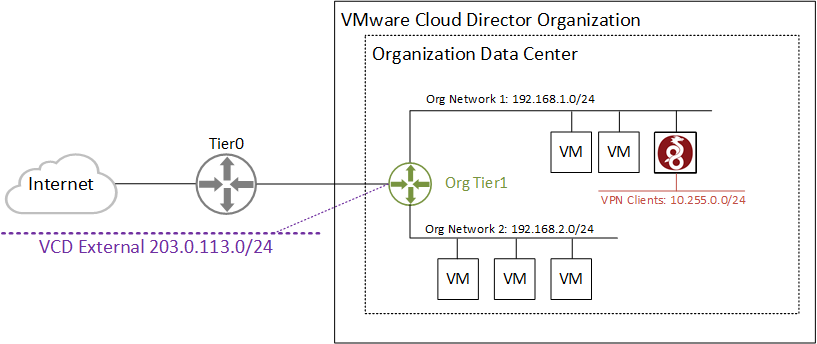
When you are running an NSX-T backed VMware Cloud Director, your customers might have the requirement to implement a remote access VPN solution. While Client VPN was possible with NSX-v, it is completely missing in NSX-T. This article explains how a customer can implement a Client VPN solution based on WireGuard. The implementation is fully in the hand of the customer and does not need any VCD modification or Service Provider interaction.
Wireguard is not part of VMware Cloud Director but can be installed easily on a Virtual Machine in the tenant’s network. The following diagram shows the environment that is used throughout the article.
When implementing a Client VPN solution in VCD, you should make yourself aware that you can’t add static routes on the Tier 1 Gateway. To make the VPN Client network (10.255.0.0/24) reachable for all Organization networks, you need to add a static route to either the default gateway (not possible with NSX-T) or on each VM (very impractical). To solve this limitation, you have to use masquerading/NAT on the VPN Server. This will hide the VPN Client Network from the organization and use the VPN Servers IP address instead. Of course, with masquerading, you can’t access VPN Clients from Org Networks, but this usually isn’t a requirement in remote access VPN.
WireGuard Installation on CentOS 8
WireGuard is available for all common Linux distributions. In this example, I’m using a CentOS 8 Virtual Machine. Refer to the official documentation for installation instructions on other distributions. A CentOS 8 Virtual Machine is already prepared and available in the Org Network 1 using the IP address 192.168.1.250.
# yum install elrepo-release epel-release -y # yum install kmod-wireguard wireguard-tools -y
WireGuard Server Configuration
Create Public and Private Keys
First, you have to create a private and public key using the wg tool. In WireGuard, you can always derive the public key from the private key. You don’t create a «keypair» like in SSL, you just generate a private key and derive the public key from the private key using wg pubkey.
# wg genkey | tee /etc/wireguard/privatekey | wg pubkey | tee /etc/wireguard/publickey # cat /etc/wireguard/privatekey 8AqJCXhEjvR6F6yglZ96LULpeK31MmL2VuV3oBMSXXQ= # cat /etc/wireguard/publickey c+xGx+Xu0lVeJUI9ZrCIhZOAPUgIqm5qlP32WKAR1hQ=
Create the Tunnel Configuration
The tunnel is configured in a simple configuration file. Create the configuration file /etc/wireguard/wg0.conf with the following content:
[Interface] # IP Address of the VPN Server in the VPN Client Network Address = 10.255.0.1/24 # Automatically save the configuration when a new client is added SaveConfig = true # UDP port number the VPN Server is listening to ListenPort = 51820 # Private Key from the /etc/wireguard/privatekey file PrivateKey = 8AqJCXhEjvR6F6yglZ96LULpeK31MmL2VuV3oBMSXXQ= # Open the firewall port and enable masquerading after starting the VPN Service. PostUp = firewall-cmd --zone=public --add-port 51820/udp && firewall-cmd --zone=public --add-masquerade # Close the firewall port and disable masquerading after stopping the VPN Service. PostDown = firewall-cmd --zone=public --remove-port 51820/udp && firewall-cmd --zone=public --remove-masquerade
To prevent users from accessing the private key or VPN configuration, set the permission to 600.
# chmod 600 /etc/wireguard/*
Start the Interface
Bring the interface up by running the following command:
# wg-quick up wg0 [#] ip link add wg0 type wireguard [#] wg setconf wg0 /dev/fd/63 [#] ip -4 address add 10.255.0.1/24 dev wg0 [#] ip link set mtu 1420 up dev wg0 [#] firewall-cmd --zone=public --add-port 51820/udp && firewall-cmd --zone=public --add-masquerade success success
When everything was successful, set the service to persist after reboots.
# systemctl enable wg-quick@wg0
Make the VPN Server available to the Internet
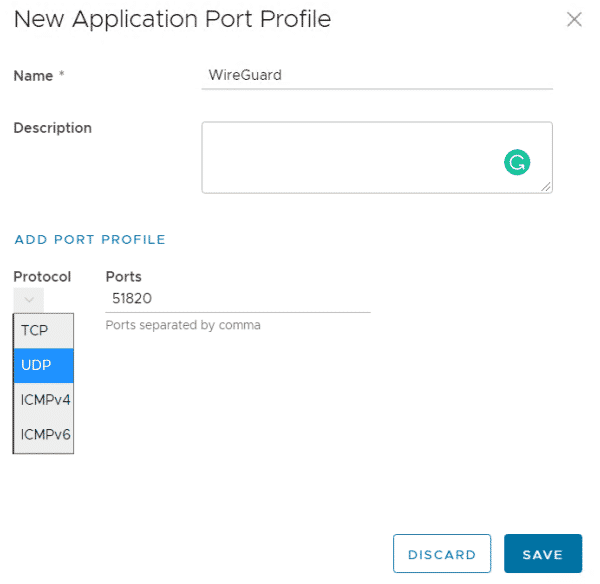
To make the VPN Server available to the Internet, create a Port Forwarding (NAT) in VMware Cloud Director. As the WireGuard port is not part of the default set of applications, you have to use a custom application port profile.
- Open Cloud Director as Tenant
- Navigate to Networking > Edge Gateways and open the Gateway configuration
- Within Security > Application Port Profiles press NEW
- Create a profile WireGuard including the port UDP/51820
- Press SAVE
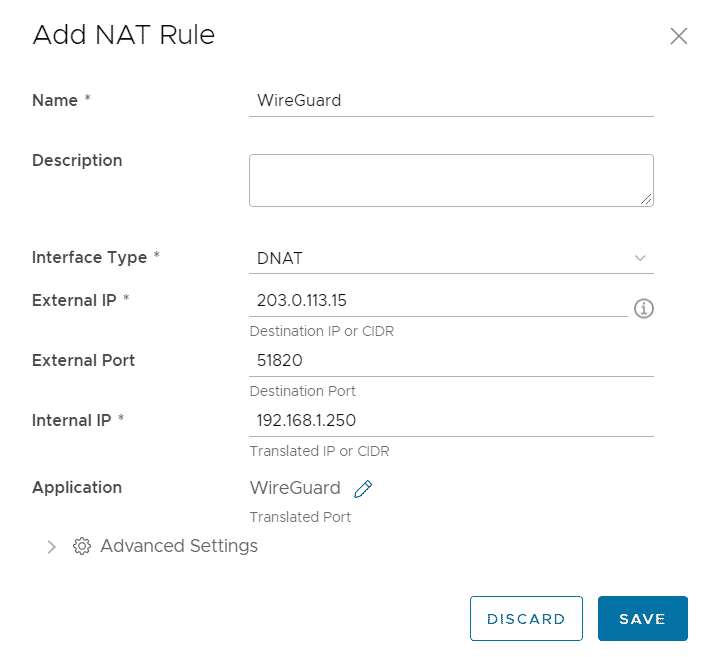
- In the Edge Gateway Configuration, open the NAT page
- Create a DNAT rule to forward a public IP to the WireGuard Server.
- Press SAVE
Add a WireGuard VPN Client
To add clients, the process is as follows:
- The Client generates private and public keys
- The Client sends its public key to the VPN Server maintainer
- The VPN Server maintainer adds the key to the VPN Server and assigns an IP address
- The VPN Server maintainer sends a configuration file to the Client
- The Client adds the configuration file to its WireGuard client
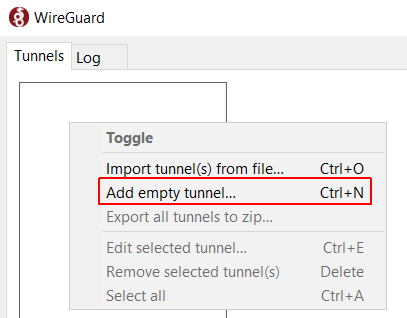
In this example, I’m using the Windows Client. You can get the Client from the official website.
- After installing the Client, right-click in the Tunnel Configuration and select Add empty tunnel…
- Give the tunnel a Name and copy the Public Key.
- Use the public key to add a peer in the WireGuard Server configuration. At this step, an IP address from the VPN Client Network is assigned to the Client.
# wg set wg0 peer vev5WHsYM/+HzbF8x6KtVC4Iy43TOegIgMwKC5scrDk= allowed-ips 10.255.0.10/32
- Edit the tunnel in the client and add the following configuration
[Interface] PrivateKey = SN0JI0Tm8Wy/eGpJQboi7DMgM2X1F+7QCBQa4pPZnXs= Address = 10.255.0.10/32 [Peer] PublicKey = B2S2OVZpDbekItMzn5ylGdM2aCosYs9W905FlqXaNXM= AllowedIPs = 192.168.1.0/24, 192.168.2.0/24 Endpoint = 203.0.113.15:51820
- Press Activate to start the tunnel
You should now have full access to all Org Networks connected to the Edge Gateway.
Troubleshooting
When your Virtual Machine has Secure Boot enabled, the WireGuard kernel module might fail to load, resulting in the following error message when trying to bring up an interface:
# ip link add dev wg0 type wireguard Error: Unknown device type # modprobe wireguard modprobe: ERROR: could not insert 'wireguard': Required key not available
Workaround: Disable Secure Boot, or use an Image with Secure Boot disabled.