Содержание
- Ipa error не получены учетные данные kerberos
- Репликация домена IPA в ОС RELS и «КОБАЛЬТ»
- Содержание
- Применимость
- Назначение
- Список поддерживаемых ОС
- Настройки серверов
- Установка FreeIPA
- Настройка DNS и hostname
- Установка оснастки
- Настройка репликации
- Подготовка
- Добавление резервного сервера в DNS
- Подготовка к репликации на основном сервере
- Запуск сервера репликации
- Troubleshooting/Kerberos
- Contents
- kinit does not work
- Service does not start
- Cannot authenticate on client
- Failed auth increments failed login count by 2
- Cannot authenticate user with OTP with Google Authenticator
- Smart Card authentication
- Trusts
- Cannot create trust with trust-add
- Portal:FreeIPA/Troubleshoot
- Contents
- General Information
- Troubleshoot Certificate Authority
- YaST fails to create CA with error «According to ‘basicConstraints’, this is not a CA.»
- YaST fails to create server certificate with error «Signing certificate failed.»
- Troubleshoot Common CA and LDAP configuration
- Command update-ca-certificates does not produce any output
- File /etc/openldap/ldap.conf does not exist
- Troubleshoot FreeIPA Server/Replica Installation
- Access installation log file
- Clean up after a failed run of ipa-server-install
- Clean up after a failed run of ipa-replica-install
- «>The server certificate is not valid: invalid for server
- hostname: Name or service not known
- Troubleshoot FreeIPA Administration Tools
- Access web service log files
- Command line tool «ipa» gives error «did not receive Kerberos credentials»
- Troubleshoot FreeIPA Client
- Access authentication daemon log
- SSSD complains «Key table entry not found»
- Desktop or remote login using IPA credentials fails on the client
Ipa error не получены учетные данные kerberos
В первый раз пытаюсь сделать SSL сертификат с помощью FreeIPA CA (dogtag). Пытаюсь отправить CSR через certmonger. На клиенте сделал:
На нём же смотрю, что получилось:
Пробую пихнуть ещё раз:
Не верю, пробую другую команду:
Проверяю кэш Kerberos на клиенте:
Пробую вручную пробиться:
В логах у клиента и у сервера — только сообщения о старте-стопе.
Никто не видел такого зверя, что я делаю неправильно?
Ответить | Правка | Cообщить модератору
- Проблема с FreeIPA, ACCA (ok), 05:50 , 05-Окт-18, (1)
| Сообщения по теме | [Сортировка по времени | RSS] |
Сам уже разобрался. Там наслоилось три проблемы:
1. RFC-6125 — почти весь SSL-софт перестал заглядывать в CN совсем
2. для каждого servernameX в ipa-getcert request -D servername1 -D servername2 должен быть свой service principal вида HTTP/servernameX
3. конкретная версия ipa-getcert имела баг — брала только первый -D
Источник
Репликация домена IPA в ОС RELS и «КОБАЛЬТ»
Содержание
Применимость
Назначение
В этой инструкции описан процесс развёртывания резервного сервера IPA (Identification, Policy and Audit) при наличии основного. Предполагается, что у вас уже работает основной сервер домена, настроенный по инструкции.
Список поддерживаемых ОС
- ROSA Enterprise Linux Server (RELS) версии 6.6 и выше
- РОСА «КОБАЛЬТ»
Если основной сервер домена развёрнут на ОС РОСА «КОБАЛЬТ», то репликация возможна на любую из поддерживаемых ОС, т. е как непосредственно на сам «КОБАЛЬТ», так и на RELS.
Настройки серверов
Предполагается, что на момент настройки репликации у вас есть сервер с установленной ОС RELS или РОСА «КОБАЛЬТ» в варианте «Минимальная». Все команды выполняются от имени администратора (root).
В примерах, приводимых в данной инструкции, предполагается, что серверы имеют следующие сетевые параметры:
Установка FreeIPA
Настройка DNS и hostname
- Убедитесь, что в качестве первого DNS-сервера используется будущий сервер домена IPA. Если в сети планируется использовать короткие имена машин, также должна быть прописана корректная опция domain или search . В файле /etc/resolv.conf должны содержаться записи следующего вида:
Убедитесь, что имя сервера (hostname) записано строчными буквами. Имя сервера задаётся в файле /etc/sysconfig/network.
Установка оснастки
- Установите оснастку для сервера IPA:
- Проверьте корректность сетевых параметров в файле /etc/hosts:
Содержимое файла должно иметь следующий вид:
Последняя строка должна указывать на сервер.
Настройка репликации
Подготовка
Выполните подготовительные команды:
Добавление резервного сервера в DNS
Добавить запись о резервном сервере в DNS можно двумя способами.
- Способ 1. Подключитесь с серверу домена с помощью браузера и воспользуйтесь графической утилитой управления доменом «Identity Managment»:
- Способ 2. На основном сервере IPA выполните следующую команду:
Возможно, на этом этапе вы получите сообщение вида:
В этом случае нужно получить билет Kerberos:
Подготовка к репликации на основном сервере
- Создайте ключи и сертификаты для резервного сервера:
- Скопируйте их на резервный сервер:
Если второй сервер работает под управлением ОС РОСА «КОБАЛЬТ», выполните downgrade nss:
Запуск сервера репликации
Инициализируйте сервер репликации, выполнив на резервном сервере следующую команду:
Сначала будет выполнена проверка доступности портов на основном сервере. Если какие-либо порты не доступны, проверьте настройки межсетевого экрана, если таковой существует между серверами, а также сервиса блокировки портов iptables на обоих серверах.
Источник
Troubleshooting/Kerberos
This page contains Kerberos troubleshooting advice, including trusts. For other issues, refer to the index at Troubleshooting.
Contents
kinit does not work
- On client, see the debug messages from the kinit process itself:
- Make sure that there are no DNS Issues and that forward (A and/or AAAA) records of the client are OK.
- Make sure that krb5kdc and dirsrv services on the FreeIPA server are running
- Check for errors in /var/log/krb5kdc.log
Service does not start
- See service log of the respective service for the exact error text. For example, the Directory Server stores the log in /var/log/dirsrv/slapd-REALM-NAME/errors
- Make sure that the server the service is running on has a fully qualified domain name
- Make sure that if /etc/hosts contains an entry for this server, the fully qualified domain name comes first, e.g.:
- See what keys are in the keytab used for authentication of the service, e.g.:
- Make sure that the stored principals match the system FQDN system name
- Make sure that the version of the keys (KVNO) stored in the keytab and in the FreeIPA server match:
- Make sure that there are no DNS Issues and both forward and reverse DNS records of the are OK and match the system name and the stored principal keys
- Make sure that the system time difference on the host and FreeIPA server is not greater than 5 minutes
Cannot authenticate on client
- If FreeIPA was re-enrolled against different FreeIPA server, try removing SSSD caches (/var/lib/sss/db/*) and restarting the SSSD service (freeipa-users thread)
For further advise, see SSSD guide for troubleshooting problems on clients, including tips for gathering SSSD log files.
Failed auth increments failed login count by 2
- This happens when migration mode is enabled. After normal auth attempt SSSD performs LDAP bind to generate Kerberos keys. This failure raises the counter for second time.
- Resolution: disable migration mode when all users are migrated by
Cannot authenticate user with OTP with Google Authenticator
- This happens when hash function other that SHA-1 is used and OTP code is generated using Google Authenticator (encountered with 4.74). Google Authenticator ignores the hash function and uses SHA-1 anyway making the generated codes unusable. Use FreeOTP application or OTP tokens with SHA-1 hash function. related freeipa-users thread.
Smart Card authentication
For Kerberos PKINIT authentication both client and server (KDC) side must have support for PKINIT enabled. On Fedora/RHEL/CentOS systems this means an RPM package krb5-pkinit or similar should be installed. If a client system lacks krb5-pkinit package, a client will not be able to use a smartcard to obtain an initial Kerberos ticket (TGT). This is hard to notice as Kerberos client will simply have no way to respond to the pre-authentication scheme for PKINIT. Thus, a first step in resolving issues with PKINIT would be to check that krb5-pkinit package is installed.
Trusts
Ubuntu distributions at this time don’t support Trust feature of FreeIPA. See https://bugs.launchpad.net/ubuntu/+source/samba/+bug/1552249 for more details.
Cannot create trust with trust-add
See separate page with instructions how to debug trust creating issues.
Источник
Portal:FreeIPA/Troubleshoot
Contents
General Information
FreeIPA is a complicated system and requires the cooperation of directory, name resolution, authentication and web services. Please carefully read the Installation Guide before attempting server/replica/client installation.
YaST fails to create CA with error «According to ‘basicConstraints’, this is not a CA.»
There is currently a bug in the YaST CA Management module, when you create a new CA, the default constraints are not properly configured and CA creation fails. To resolve the issue, visit «Advanced Options» when prompted for new CA password, and set CA «CA:true» under «Basic Constraints».
YaST fails to create server certificate with error «Signing certificate failed.»
Click «Details» button to learn the error details. Most commonly the valid period of the server certificate is incorrectly set to exceed the valid period of CA; if this is the case, decrease the valid period of the certificate and try again.
Troubleshoot Common CA and LDAP configuration
Command update-ca-certificates does not produce any output
This is normal. The command only produces output when an error is encountered.
File /etc/openldap/ldap.conf does not exist
Please install OpenLDAP client package:
Troubleshoot FreeIPA Server/Replica Installation
Access installation log file
ipa-server-install command writes logging information into file /var/log/ipaserver-install.log. To inspect the log file while IPA server is being installed, run:
ipa-replica-install command writes logging information into file /var/log/ipareplica-install.log. To inspect the log file while IPA replica is being installed, run:
Occasionally binary-only content is written into the log files during the installation process (a known issue), therefore it is necessary to use «cat -v» to turn the binary content into readable characters.
Clean up after a failed run of ipa-server-install
If ipa-server-install installation has started but fails to complete successfully, the next installation attempt will fail with message «IPA server is already configured on this system.». It is necessary to clean up the incomplete installation by running:
before making another installation attempt.
Clean up after a failed run of ipa-replica-install
If ipa-replica-install installation has started but fails to complete successfully, the next installation attempt will fail. It is necessary to clean up the incomplete installation by running on the replica:
And run on replica Target machine (not the replica machine itself):
Then you may re-try replica installation.
«>The server certificate is not valid: invalid for server
Make sure that the certificate file used for FreeIPA service satisfies all of these conditions:
- It is in PKCS12 format.
- It is a Server certificate (not a Client certificate).
- It contains both certificate and key.
- It does not contain CA or sub-CA certificate.
- The certificate common name matches server fully-qualified-domain-name exactly.
hostname: Name or service not known
Sometimes NetworkManager can cause hostname-unknown issue, please disable NetworkManager and use Wicked Service for network setup. Consult YaST Network Settings manual for more details.
If NetworkManager is determined not to be the cause of host name trouble, correct host name and FQDN manually via «hostnamectl» command and manually enter the FQDN and short host name into /etc/hosts, then proceed with FreeIPA server/replica installation.
Access web service log files
FreeIPA web application runs on Apache web server.
Apache web server daemon logs critical and startup errors in system journal, accessible via:
Web access log and FreeIPA web application errors are logged in conventional log files, located by default under «/var/log/apache2».
Command line tool «ipa» gives error «did not receive Kerberos credentials»
Before using the command line tool «ipa», your current system user must have already obtained a Kerberos ticket with IPA administrative privilege. Use command «klist» to determine whether a Kerberos ticket has been obtained, and if not, obtain a new ticket via:
and then retry the ipa command.
Troubleshoot FreeIPA Client
Access authentication daemon log
FreeIPA client runs SSSD (System Security Services Daemon), whose logs are accessible via:
SSSD complains «Key table entry not found»
(Or alternatively «Failed to initialize credentials using keytab», «Client . not found in Kerberos database.»)
The error indicates SSSD was looking for your client host’s Kerberos key but it is not found in Kerberos keytab file (/etc/krb5.keytab).
There are several possible causes:
- Keytab file is empty.
- Keytab file does not belong to this client machine (incorrect placement).
- Client machine’s FQDN does not match the principal name in keytab file due to name resolution error.
- Client machine’s host name does not reflect the FQDN used by IPA database to identify the host.
In any case, inspect the keytab file content by running command:
The result should show more than one entries belonging to principal «host/ .domain@DOMAIN_REALM», e.g.:
If the keytab file appears empty or the principal name does not match with the client’s fully-qualified-domain-name, it is necessary to re-retrieve the client’s keytab file via «ipa-getkeytab» command. Refer to Installation Guide for detailed procedure.
If the keytab file content looks correct, then there is a possibility of name resolution error on the client side. Re-visit YaST Authentication Client module and enter the expected FQDN from client (e.g. «pulautin.linuxdom.net») into domain parameter «ipa_hostname», and see if the problem is eliminated. If the problem is eliminated, then check the private network’s domain name and DNS server settings on DHCP server.
Desktop or remote login using IPA credentials fails on the client
Inspect all system journal:
While re-attempting a login, to determine the failure reason.
Please note that it is sometimes necessary to reboot the client machine after it is configured as IPA client for the very first time.
Источник
Adblock
detector
| 1. «Проблема с FreeIPA» | + / – | |
| Сообщение от ACCA (ok), 05-Окт-18, 05:50 | ||
Содержание
- 1 Применимость
- 1.1 Назначение
- 1.2 Список поддерживаемых ОС
- 1.3 Настройки серверов
- 2 Установка FreeIPA
- 2.1 Настройка DNS и hostname
- 2.2 Установка оснастки
- 3 Настройка репликации
- 3.1 Подготовка
- 3.2 Добавление резервного сервера в DNS
- 3.3 Подготовка к репликации на основном сервере
- 3.4 Запуск сервера репликации
Применимость
Назначение
В этой инструкции описан процесс развёртывания резервного сервера IPA (Identification, Policy and Audit) при наличии основного. Предполагается, что у вас уже работает основной сервер домена, настроенный по инструкции.
Список поддерживаемых ОС
- ROSA Enterprise Linux Server (RELS) версии 6.6 и выше
- РОСА «КОБАЛЬТ»
Если основной сервер домена развёрнут на ОС РОСА «КОБАЛЬТ», то репликация возможна на любую из поддерживаемых ОС, т. е как непосредственно на сам «КОБАЛЬТ», так и на RELS.
Настройки серверов
Предполагается, что на момент настройки репликации у вас есть сервер с установленной ОС RELS или РОСА «КОБАЛЬТ» в варианте «Минимальная». Все команды выполняются от имени администратора (root).
В примерах, приводимых в данной инструкции, предполагается, что серверы имеют следующие сетевые параметры:
Основной сервер:
Имя: dc1.test.dom IP: 192.168.76.47/24
Резервный сервер:
Имя: dc2.test.dom IP: 192.168.76.82/24
Установка FreeIPA
Настройка DNS и hostname
- Убедитесь, что в качестве первого DNS-сервера используется будущий сервер домена IPA. Если в сети планируется использовать короткие имена машин, также должна быть прописана корректная опция
domainилиsearch. В файле /etc/resolv.conf должны содержаться записи следующего вида:
search test.dom nameserver 192.168.76.47
Убедитесь, что имя сервера (hostname) записано строчными буквами. Имя сервера задаётся в файле /etc/sysconfig/network.
cat /etc/sysconfig/network
HOSTNAME=dc2.test.dom NETWORKING=yes NISDOMAIN=test.dom
Установка оснастки
- Установите оснастку для сервера IPA:
yum install bind-dyndb-ldap bind ipa-server
- Проверьте корректность сетевых параметров в файле /etc/hosts:
cat /etc/hosts
Содержимое файла должно иметь следующий вид:
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.76.82 dc2.test.dom dc2
Последняя строка должна указывать на сервер.
Настройка репликации
Подготовка
Выполните подготовительные команды:
rm -f /etc/portreserve/slapd service portreserve restart yum remove firefox thunderbird yum downgrade nss nss-tools nss-sysinit nss-util
Добавление резервного сервера в DNS
Добавить запись о резервном сервере в DNS можно двумя способами.
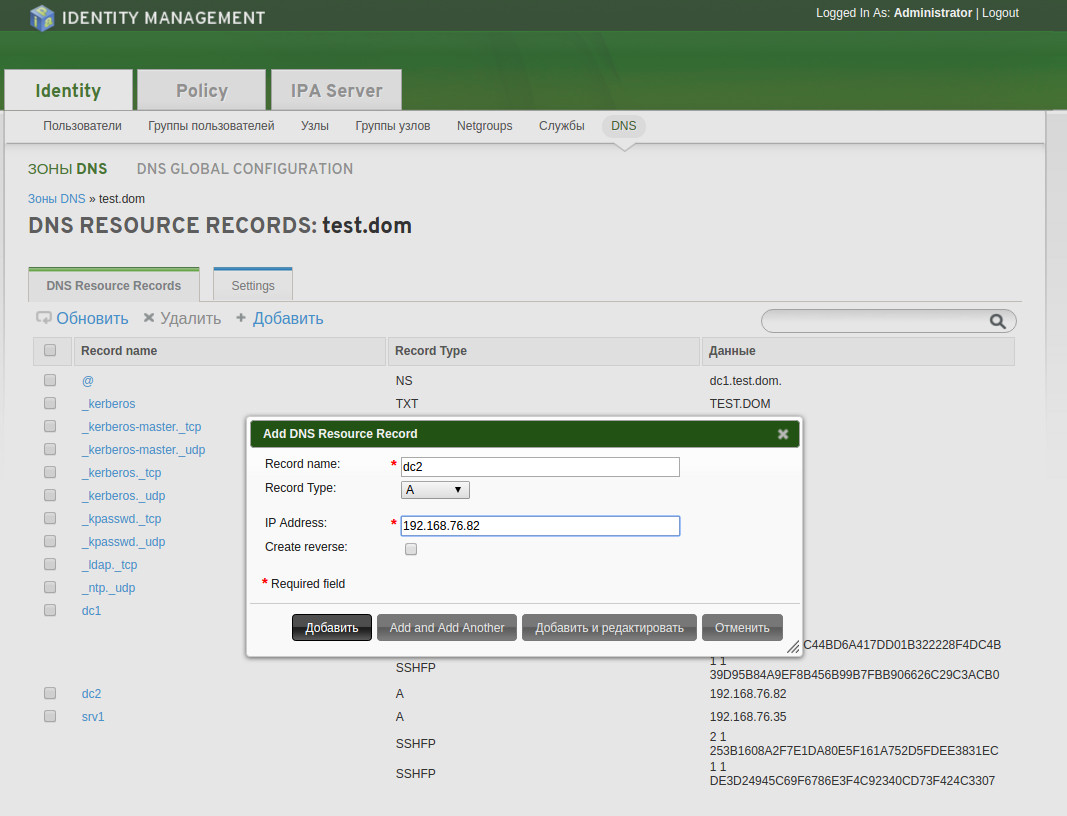
- Способ 1. Подключитесь с серверу домена с помощью браузера и воспользуйтесь графической утилитой управления доменом «Identity Managment»:

- Способ 2. На основном сервере IPA выполните следующую команду:
ipa dnsrecord-add test.dom dc2 --a-rec 192.168.76.82
Возможно, на этом этапе вы получите сообщение вида:
ipa: ERROR: не получены регистрационные данные Kerberos
В этом случае нужно получить билет Kerberos:
kinit admin
Подготовка к репликации на основном сервере
- Создайте ключи и сертификаты для резервного сервера:
ipa-replica-prepare dc2.test.dom --ip-address 192.168.76.82
Directory Manager (existing master) password: Preparing replica for dc2.test.dom from dc1.test.dom Creating SSL certificate for the Directory Server Creating SSL certificate for the dogtag Directory Server Creating SSL certificate for the Web Server Exporting RA certificate Copying additional files Finalizing configuration Packaging replica information into /var/lib/ipa/replica-info-dc2.test.dom.gpg Adding DNS records for dc2.test.dom Using reverse zone 76.168.192.in-addr.arpa.
- Скопируйте их на резервный сервер:
scp /var/lib/ipa/replica-info-dc2.test.dom.gpg root@dc2.test.dom:/var/lib/ipa/
Если второй сервер работает под управлением ОС РОСА «КОБАЛЬТ», выполните downgrade nss:
yum remove firefox thunderbird yum downgrade nss nss-tools nss-sysinit nss-util
Запуск сервера репликации
Инициализируйте сервер репликации, выполнив на резервном сервере следующую команду:
ipa-replica-install --setup-ca --setup-dns --no-forwarders /var/lib/ipa/replica-info-dc2.test.dom.gpg
Сначала будет выполнена проверка доступности портов на основном сервере. Если какие-либо порты не доступны, проверьте настройки межсетевого экрана, если таковой существует между серверами, а также сервиса блокировки портов iptables на обоих серверах.
This wiki was updated to MediaWiki 1.37. If you notice any issues, please report them to admin[at]opensuse.org
Jump to: navigation,
search
General Information
FreeIPA is a complicated system and requires the cooperation of directory, name resolution, authentication and web services. Please carefully read the Installation Guide before attempting server/replica/client installation.
YaST fails to create CA with error «According to ‘basicConstraints’, this is not a CA.»
There is currently a bug in the YaST CA Management module, when you create a new CA, the default constraints are not properly configured and CA creation fails. To resolve the issue, visit «Advanced Options» when prompted for new CA password, and set CA «CA:true» under «Basic Constraints».
YaST fails to create server certificate with error «Signing certificate failed.»
Click «Details» button to learn the error details. Most commonly the valid period of the server certificate is incorrectly set to exceed the valid period of CA; if this is the case, decrease the valid period of the certificate and try again.
Troubleshoot Common CA and LDAP configuration
Command update-ca-certificates does not produce any output
This is normal. The command only produces output when an error is encountered.
File /etc/openldap/ldap.conf does not exist
Please install OpenLDAP client package:
# zypper install openldap2-client
And try again.
Troubleshoot FreeIPA Server/Replica Installation
Access installation log file
ipa-server-install command writes logging information into file /var/log/ipaserver-install.log. To inspect the log file while IPA server is being installed, run:
# tail -F /var/log/ipaserver-install.log | cat -v
ipa-replica-install command writes logging information into file /var/log/ipareplica-install.log. To inspect the log file while IPA replica is being installed, run:
# tail -F /var/log/ipaserver-install.log | cat -v
Occasionally binary-only content is written into the log files during the installation process (a known issue), therefore it is necessary to use «cat -v» to turn the binary content into readable characters.
Clean up after a failed run of ipa-server-install
If ipa-server-install installation has started but fails to complete successfully, the next installation attempt will fail with message «IPA server is already configured on this system.». It is necessary to clean up the incomplete installation by running:
# ipa-server-install —uninstall
before making another installation attempt.
Clean up after a failed run of ipa-replica-install
If ipa-replica-install installation has started but fails to complete successfully, the next installation attempt will fail. It is necessary to clean up the incomplete installation by running on the replica:
# ipa-server-install —uninstall
And run on replica Target machine (not the replica machine itself):
# ipa-replica-manage del <failed_replica_FQDN> —force
Then you may re-try replica installation.
The server certificate is not valid: invalid for server <host name>
Make sure that the certificate file used for FreeIPA service satisfies all of these conditions:
- It is in PKCS12 format.
- It is a Server certificate (not a Client certificate).
- It contains both certificate and key.
- It does not contain CA or sub-CA certificate.
- The certificate common name matches server fully-qualified-domain-name exactly.
hostname: Name or service not known
Sometimes NetworkManager can cause hostname-unknown issue, please disable NetworkManager and use Wicked Service for network setup. Consult YaST Network Settings manual for more details.
If NetworkManager is determined not to be the cause of host name trouble, correct host name and FQDN manually via «hostnamectl» command and manually enter the FQDN and short host name into /etc/hosts, then proceed with FreeIPA server/replica installation.
Troubleshoot FreeIPA Administration Tools
Access web service log files
FreeIPA web application runs on Apache web server.
Apache web server daemon logs critical and startup errors in system journal, accessible via:
# journalctl -u apache2.service -f
Web access log and FreeIPA web application errors are logged in conventional log files, located by default under «/var/log/apache2».
Command line tool «ipa» gives error «did not receive Kerberos credentials»
Before using the command line tool «ipa», your current system user must have already obtained a Kerberos ticket with IPA administrative privilege. Use command «klist» to determine whether a Kerberos ticket has been obtained, and if not, obtain a new ticket via:
# kinit admin Password for admin@LINUXDOM.NET: <enter IPA admin password>
and then retry the ipa command.
Troubleshoot FreeIPA Client
Access authentication daemon log
FreeIPA client runs SSSD (System Security Services Daemon), whose logs are accessible via:
# journalctl -u sssd.service -f
SSSD complains «Key table entry not found»
(Or alternatively «Failed to initialize credentials using keytab», «Client … not found in Kerberos database.»)
The error indicates SSSD was looking for your client host’s Kerberos key but it is not found in Kerberos keytab file (/etc/krb5.keytab).
There are several possible causes:
- Keytab file is empty.
- Keytab file does not belong to this client machine (incorrect placement).
- Client machine’s FQDN does not match the principal name in keytab file due to name resolution error.
- Client machine’s host name does not reflect the FQDN used by IPA database to identify the host.
In any case, inspect the keytab file content by running command:
# klist -ke
The result should show more than one entries belonging to principal «host/<client_FQDN>.domain@DOMAIN_REALM», e.g.:
host/pulautin.linuxdom.net@LINUXDOM.NET (aes256-cts-hmac-sha1-96) host/pulautin.linuxdom.net@LINUXDOM.NET (des3-cbc-sha1) ... (and more)
If the keytab file appears empty or the principal name does not match with the client’s fully-qualified-domain-name, it is necessary to re-retrieve the client’s keytab file via «ipa-getkeytab» command. Refer to Installation Guide for detailed procedure.
If the keytab file content looks correct, then there is a possibility of name resolution error on the client side. Re-visit YaST Authentication Client module and enter the expected FQDN from client (e.g. «pulautin.linuxdom.net») into domain parameter «ipa_hostname», and see if the problem is eliminated. If the problem is eliminated, then check the private network’s domain name and DNS server settings on DHCP server.
Desktop or remote login using IPA credentials fails on the client
Inspect all system journal:
# journalctl -f
While re-attempting a login, to determine the failure reason.
Please note that it is sometimes necessary to reboot the client machine after it is configured as IPA client for the very first time.
We have a working FreeIPA installation, it’s in production since February. Almost everything works as expected but when we try to run command-line FreeIPA-related tools none of them work:
[admin@ipa ~]$ kinit admin
Password for admin@EXAMPLE.COM:
[admin@ipa ~]$ klist
Ticket cache: KEYRING:persistent:8800000
Default principal: admin@EXAMPLE.COM
Valid starting Expires Service principal
06/30/2014 21:19:30 07/01/2014 21:19:12 krbtgt/EXAMPLE.COM@EXAMPLE.COM
[admin@ipa ~]$ ipa pwpolicy-show global_policy
ipa: ERROR: Kerberos error: ('Unspecified GSS failure. Minor code may provide more information', 851968)/('No Kerberos credentials available', -1765328243)
[admin@ipa ~]$
I’m not a Kerberos expert and don’t really know what to check. How can we debug and resolve this?
Update: when I add -vv I get the following:
[admin@ipa ~]$ ipa -vv pwpolicy-show global_policy
ipa: INFO: trying https://ipa.example.com/ipa/xml
ipa: INFO: Forwarding 'pwpolicy_show' to server 'https://ipa.example.com/ipa/xml'
ipa: ERROR: Kerberos error: ('Unspecified GSS failure. Minor code may provide more information', 851968)/('No Kerberos credentials available', -1765328243)
[admin@ipa ~]$
Update 2: the content of /etc/krb5.conf follows:
includedir /var/lib/sss/pubconf/krb5.include.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = EXAMPLE.COM
dns_lookup_realm = false
dns_lookup_kdc = true
rdns = false
ticket_lifetime = 24h
forwardable = yes
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
EXAMPLE.COM = {
kdc = ipa.example.com:88
master_kdc = ipa.example.com:88
admin_server = ipa.example.com:749
default_domain = example.com
pkinit_anchors = FILE:/etc/ipa/ca.crt
}
[domain_realm]
.example.com = EXAMPLE.COM
example.com = EXAMPLE.COM
[dbmodules]
EXAMPLE.COM = {
db_library = ipadb.so
}
Update 3: This is a single-server installation, the distro is Fedora 19 and FreeIPA version is 3.3.5
ipa-server-4.6.6-11.el7.centos.x86_64
freeipa collection version 0.1.12
The playbook works with some users, and not working for other users!
This is a task I have:
- name: add host to hostgroup
freeipa.ansible_freeipa.ipahostgroup:
ipaadmin_password: "{{ipaadmin_password}}"
name: "{{host_location}}"
action: member
host: "{{host_fqdn}}"
```-------
The full traceback is:
WARNING: The below traceback may *not* be related to the actual failure.
File "/tmp/ansible_freeipa.ansible_freeipa.ipahostgroup_payload_5z8Agp/ansible_freeipa.ansible_freeipa.ipahostgroup_payload.zip/ansible_collections/freeipa/ansible_freeipa/plugins/modules/ipahostgroup.py", line 240, in main
File "/tmp/ansible_freeipa.ansible_freeipa.ipahostgroup_payload_5z8Agp/ansible_freeipa.ansible_freeipa.ipahostgroup_payload.zip/ansible_collections/freeipa/ansible_freeipa/plugins/module_utils/ansible_freeipa_module.py", line 156, in api_connect
backend.connect()
File "/usr/lib/python2.7/site-packages/ipalib/backend.py", line 69, in connect
conn = self.create_connection(*args, **kw)
File "/usr/lib/python2.7/site-packages/ipaserver/plugins/ldap2.py", line 196, in create_connection
principal = krb_utils.get_principal(ccache_name=ccache)
File "/usr/lib/python2.7/site-packages/ipalib/krb_utils.py", line 171, in get_principal
raise errors.CCacheError(message=unicode(e))
fatal: [lab-01.ipa.example.com]: FAILED! => {
"changed": false,
"invocation": {
"module_args": {
"action": "member",
"description": null,
"host": [
"rqtest-01.lab.example.com"
],
"hostgroup": null,
"ipaadmin_password": "VALUE_SPECIFIED_IN_NO_LOG_PARAMETER",
"ipaadmin_principal": "admin",
"name": [
"mel_lab"
],
"nomembers": null,
"state": "present"
}
},
"msg": "Major (851968): Unspecified GSS failure. Minor code may provide more information, Minor (2529639053): No Kerberos credentials available (default cache: KEYRING:persistent:1604100503)"
}
This page contains Kerberos troubleshooting advice, including trusts. For other issues, refer to the index at Troubleshooting.
Contents
- 1 kinit does not work
- 2 Service does not start
- 3 Cannot authenticate on client
- 4 Failed auth increments failed login count by 2
- 5 Cannot authenticate user with OTP with Google Authenticator
- 6 Smart Card authentication
- 7 Trusts
- 7.1 Cannot create trust with trust-add
kinit does not work
- On client, see the debug messages from the kinit process itself:
-
KRB5_TRACE=/dev/stdout kinit admin
-
- Make sure that there are no DNS Issues and that forward (A and/or AAAA) records of the client are OK.
- Make sure that krb5kdc and dirsrv services on the FreeIPA server are running
- Check for errors in /var/log/krb5kdc.log
Service does not start
- See service log of the respective service for the exact error text. For example, the Directory Server stores the log in /var/log/dirsrv/slapd-REALM-NAME/errors
- Make sure that the server the service is running on has a fully qualified domain name
- Make sure that if /etc/hosts contains an entry for this server, the fully qualified domain name comes first, e.g.:
-
192.168.1.1 ipa.example.com ipa
-
- See what keys are in the keytab used for authentication of the service, e.g.:
-
# klist -kt /etc/dirsrv/ds.keytab
-
- Make sure that the stored principals match the system FQDN system name
- Make sure that the version of the keys (KVNO) stored in the keytab and in the FreeIPA server match:
-
$ kvno ldap/ipa.example.com@EXAMPLE.COM
-
- Make sure that there are no DNS Issues and both forward and reverse DNS records of the are OK and match the system name and the stored principal keys
- Make sure that the system time difference on the host and FreeIPA server is not greater than 5 minutes
Cannot authenticate on client
- If FreeIPA was re-enrolled against different FreeIPA server, try removing SSSD caches (/var/lib/sss/db/*) and restarting the SSSD service (freeipa-users thread)
For further advise, see SSSD guide for troubleshooting problems on clients, including tips for gathering SSSD log files.
Failed auth increments failed login count by 2
- This happens when migration mode is enabled. After normal auth attempt SSSD performs LDAP bind to generate Kerberos keys. This failure raises the counter for second time.
- Resolution: disable migration mode when all users are migrated by
-
ipa config-mod --enable-migration=False
-
Cannot authenticate user with OTP with Google Authenticator
- This happens when hash function other that SHA-1 is used and OTP code is generated using Google Authenticator (encountered with 4.74). Google Authenticator ignores the hash function and uses SHA-1 anyway making the generated codes unusable. Use FreeOTP application or OTP tokens with SHA-1 hash function. related freeipa-users thread.
Smart Card authentication
See Troubleshooting SmartCard authentication for SmartCard authentication issues.
For Kerberos PKINIT authentication both client and server (KDC) side must have support for PKINIT enabled. On Fedora/RHEL/CentOS systems this means an RPM package krb5-pkinit or similar should be installed. If a client system lacks krb5-pkinit package, a client will not be able to use a smartcard to obtain an initial Kerberos ticket (TGT). This is hard to notice as Kerberos client will simply have no way to respond to the pre-authentication scheme for PKINIT. Thus, a first step in resolving issues with PKINIT would be to check that krb5-pkinit package is installed.
Trusts
Ubuntu distributions at this time don’t support Trust feature of FreeIPA. See https://bugs.launchpad.net/ubuntu/+source/samba/+bug/1552249 for more details.
Cannot create trust with trust-add
See separate page with instructions how to debug trust creating issues.
Installation[edit | edit source]
Here are my notes as I fumble my way setting up FreeIPA.
Docker[edit | edit source]
There is an official Docker container that has a complete FreeIPA installation. This container uses systemd to start up FreeIPA along with the other related services such as OpenLDAP, Bind, and Kerberos. See more at: https://github.com/freeipa/freeipa-container
Use the following docker-compose.yml stack to quickly get started with FreeIPA:
version: '3.3' services: freeipa: image: freeipa/freeipa-server:rocky-8 restart: unless-stopped tty: true stdin_open: true hostname: ipa domainname: home.steamr.com extra_hosts: - "ipa.home.steamr.com:10.1.2.12" environment: - IPA_SERVER_HOSTNAME=ipa.home.steamr.com - IPA_SERVER_IP=10.1.2.12 - DNS=10.1.0.8 - TZ=America/Edmonton command: - ipa-server-install - --realm=home.steamr.com - --domain=home.steamr.com - --ds-password=xxxxxxxxxx - --admin-password=xxxxxxxxxx - --no-host-dns - --setup-dns - --auto-forwarders - --allow-zone-overlap - --no-dnssec-validation - --unattended sysctls: - net.ipv6.conf.all.disable_ipv6=0 volumes: - ./data:/data - ./logs:/var/logs - /sys/fs/cgroup:/sys/fs/cgroup:ro tmpfs: - /run - /var/cache - /tmp cap_add: - SYS_TIME ports: - "10.1.2.12:80:80/tcp" - "10.1.2.12:443:443/tcp" # DNS - "10.1.2.12:53:53/tcp" - "10.1.2.12:53:53/udp" # LDAP(S) - "10.1.2.12:389:389/tcp" - "10.1.2.12:636:636/tcp" # Kerberos - "10.1.2.12:88:88/tcp" - "10.1.2.12:464:464/tcp" - "10.1.2.12:88:88/udp" - "10.1.2.12:464:464/udp"
Samba integration[edit | edit source]
There are 3 methods to using FreeIPA with Samba. I eventually settled on method #2.
- Configure Samba to use FreeIPA as a simple LDAP server, using ldapsam as the passdb backend. This requires a schema change to include the sambaSAMAccount and sambaGroupMapping, and sambaSID object classes. There is a DNA (distributed numeric assignment) plugin that can be used to update these fields.
- Configure Samba to use FreeIPA using ipasam as the passdb backend. This requires the
ipasam.somodule installed on the samba servers. - Configure Samba to use Kerberos. Does not seem to allow users to use password authentication.
Method 1: ldapsam[edit | edit source]
I didn’t get this to work
I wasn’t able to fully get this method to work. If you are using OpenLDAP only, this way of integrating Samba does work. The issue I had was getting the DNA plugin to work as advertised.
I eventually settled on the ipasam method in the section below.
To use ldapsam, we need to make some changes to the FreeIPA LDAP server by adding sambaSAMAccount and sambaGroupMapping as a default user object class and group object class.
You can either set this in the FreeIPA web interface under configuration, or run:
# ldapmodify <<EOF dn: cn=ipaConfig,cn=etc,dc=home,dc=steamr,dc=com changetype: modify add: ipaUserObjectClasses ipaUserObjectClasses: sambaSAMAccount - add: ipaGroupObjectClasses ipaGroupObjectClasses: sambaGroupMapping EOF
We will then need to make a custom DNA (distributed numeric assignment) plugin to update these attributes whenever something related to the object (such as the password) is changed. This can be done by adding a DNA object into LDAP.
ldapadd <<EOF dn: cn=SambaSid,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config objectClass: top objectClass: extensibleObject dnatype: sambaSID dnaprefix: S-1-5-21-2049073866-1371207509-1214748462 dnainterval: 1 dnamagicregen: assign dnafilter: (|(objectclass=sambasamaccount)(objectclass=sambagroupmapping)) dnascope: dc=home,dc=steamr,dc=com cn: SambaSid dnanextvalue: 2 dn: cn=sambaGroupType,cn=Distributed Numeric Assignment Plugin,cn=plugins,cn=config objectClass: top objectClass: extensibleObject cn: sambaGroupType dnatype: sambaGroupType dnainterval: 1 dnamagicregen: assign dnafilter: (objectClass=sambagroupmapping) dnascope: dc=home,dc=steamr,dc=com dnanextvalue: 2 EOF
A ldapsam user entry should have these fields. I don’t see these though.
dn: uid=guest2, ou=People,dc=quenya,dc=org sambaLMPassword: 878D8014606CDA29677A44EFA1353FC7 sambaPwdMustChange: 2147483647 sambaPrimaryGroupSID: S-1-5-21-2447931902-1787058256-3961074038-513 sambaNTPassword: 552902031BEDE9EFAAD3B435B51404EE sambaPwdLastSet: 1010179124 sambaLogonTime: 0 objectClass: sambaSamAccount uid: guest2 sambaKickoffTime: 2147483647 sambaAcctFlags: [UX ] sambaLogoffTime: 2147483647 sambaSID: S-1-5-21-2447931902-1787058256-3961074038-5006 sambaPwdCanChange: 0
Configure the Samba server[edit | edit source]
You can either use a specific binding credential that’s shared across all your samba servers, or use the machine’s cifs service account to authenticate to the LDAP server.
I tried to do the following using the admin account as the bind DN: (using the admin account like this is probably a bad idea, I’m just testing)
[global] # freeipa configurations passdb backend = ipasam:ldap://home.steamr.com ldap admin dn = uid=admin,cn=users,cn=accounts,dc=home,dc=steamr,dc=com ldapsam:trusted = yes ldap suffix = cn=accounts,dc=home,dc=steamr,dc=com ldap user suffix = cn=users,cn=accounts ldap machine suffix = cn=computers,cn=accounts ldap group suffix = cn=groups,cn=accounts ldap passwd sync = only ldap ssl = no
Run smbpasswd -w password to set your bind credential passwords.
Method 2: ipasam[edit | edit source]
See: https://bgstack15.wordpress.com/2017/05/10/samba-share-with-freeipa-auth/
Install the adtrust components on the FreeIPA server. Install ipa-server-trust-ad and run ipa-adtrust-install --add-sids. This will add the additional IPASAM attributes such as ipaNtPassword in user objects.
# ipa-adtrust-install --add-sids ## Answer yes to overwrite smb.conf ## Answer yes to install slapi-nis
Ensure that your hostname is set to the FQDN of the hostname otherwise this process will fail. If you are using an external DNS server, ensure that the additional service records are present. If you are using a Docker container, set the hostname to the full FQDN (eg. ipa.example.com, rather than just ‘ipa’).
Next, create a new user and then change the user’s password. This should populate the ipaNTPassword attribute.
# ipa user-add leo --first=Leo --last=Leung # ipa group-add-member smbgrp --users=leo
When modifying smb.conf, the service account or bind DN must have access to these new ipasam attributes. You need to create a new set of privilege and role and grant the account access. Create the role and permissions in the web interface or run:
# ipa permission-add "CIFS server can read user passwords" --attrs={ipaNTHash,ipaNTSecurityIdentifier} --type=user --right={read,search,compare} --bindtype=permission # ipa privilege-add "CIFS server privilege" # ipa privilege-add-permission "CIFS server privilege" --permission="CIFS server can read user passwords" # ipa role-add "CIFS server" # ipa role-add-privilege "CIFS server" --privilege="CIFS server privilege"
Then, add your service account or bind DN to the ‘CIFS server’ role. For example:
# ipa service-add cifs/dnas.home.steamr.com # ipa role-add-member "CIFS server" --services=cifs/dnas.home.steamr.com
Configure the Samba server[edit | edit source]
Generate a keytab file for samba.
# kinit -kt /etc/krb5.keytab ## Note: we ran this in the previous step. ## ipa service-add cifs/dnas.home.steamr.com # ipa-getkeytab -s ipa.home.steamr.com -p cifs/dnas.home.steamr.com -k /etc/samba/samba.keytab
Then, tweak smb.conf.
[global] passdb backend = ipasam:ldap://ipa.home.steamr.com ldapsam:trusted = yes ldap suffix = dc=home,dc=steamr,dc=com ldap user suffix = cn=users,cn=accounts ldap machine suffix = cn=computers,cn=accounts ldap group suffix = cn=groups,cn=accounts ldap ssl = no idmap config * : backend = tdb create krb5 conf = No dedicated keytab file = FILE:/etc/samba/samba.keytab kerberos method = dedicated keytab
If you get: NT_STATUS_BAD_TOKEN_TYPE, you need to disable MS-POC in the FreeIPA settings or disable it specifically for this cifs service account.
The ipasam passdb provider is available from the ipa-server-trust-ad package. However, this package also pulls in a ton of other IPA dependencies which aren’t needed. If you just want the provider to work on a bare minimal samba server, you can simply just copy (or extract from the ipa-server-trust-ad package) the ipasam.so file to /usr/lib64/samba/pdb/ipasam.so.
Method 3: Kerberos[edit | edit source]
This method is similar to the ipasam method above and you will need to set up the server in the same way. However, the way you configure Samba is different.
On the Samba server[edit | edit source]
## Join the samba server to FreeIPA # ipa-client-install ## Then add the client to samba. # ipa-client-samba
Note that when you try adding the samba client, the IPA server has to be able to resolve the A record for the Samba server you’re adding or else it will fail.
This should automatically set up the cifs service accounts for this particular samba server, get the samba keytab file in /etc/samba/samba.keytab, and then tweak the smb.conf file to use this keytab file.
The smb.conf file now looks like:
[global]
# Limit number of forked processes to avoid SMBLoris attack
max smbd processes = 1000
# Use dedicated Samba keytab. The key there must be synchronized
# with Samba tdb databases or nothing will work
dedicated keytab file = FILE:/etc/samba/samba.keytab
kerberos method = dedicated keytab
# Set up logging per machine and Samba process
log file = /var/log/samba/log.%m
log level = 1
# We force 'member server' role to allow winbind automatically
# discover what is supported by the domain controller side
server role = member server
realm = HOME.STEAMR.COM
netbios name = DNAS
workgroup = HOME
# Local writable range for IDs not coming from IPA or trusted domains
idmap config * : range = 0 - 0
idmap config * : backend = tdb
idmap config HOME : range = 100000 - 299999
idmap config HOME : backend = sss
# Default homes share
[homes]
read only = no
You need to then start winbind and smb. For some reason, this method doesn’t seem to work as winbind is stuck with «wb_parent_idmap_setup_lookupname_done: Lookup domain name 'home' failed 'NT_STATUS_DOMAIN_CONTROLLER_NOT_FOUND'»
Debug samba issues[edit | edit source]
Use smbclient to help debug issues. This utility is provided by the samba-client package. You can then test authentication by running: smbclient -d 10 -U leo //dnas/home
Tasks[edit | edit source]
Join a computer to a FreeIPA[edit | edit source]
Use the ipa-client-install command to add a computer to a FreeIPA server. This should also automatically add a computer account, generate a keytab file, and tweak sssd to use FreeIPA as an authentication mechanism.
# ipa-client-install -U -p admin -w $Password --server ipa.home.steamr.com --domain home.steamr.com --force-join --no-ntp --fixed-primary
Troubleshooting[edit | edit source]
Error: did not receive Kerberos credentials[edit | edit source]
Tools such as ‘ipa’ uses your session’s Kerberos tickets for authentication. If you don’t have any tickets or if your tickets expired, you may get an ipa: ERROR: did not receive Kerberos credentials error. Fix this by running:
## Renew/obtain Kerberos tickets for 'admin' # kinit admin Password for admin@HOME.STEAMR.COM: ****
Verify if your tickets are available with klist:
# klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: admin@STEAMR.COM Valid starting Expires Service principal 03/06/22 14:44:35 03/07/22 14:39:47 krbtgt/STEAMR.COM@STEAMR.COM
Container issues[edit | edit source]
- Don’t mount /var/log because the container image symlinks everything into /data. If you do mount /var/log, make sure you make the expected directories or else the installer will fail.
- Error with
AssertionError: Another instance named 'HOME-STEAMR-COM' may already exist. I can’t figure out what’s causing lib389 to think there’s another instance. I built a container image on top of this image with the assertion patched out. This seemed to have fixed the issue. -
FROM freeipa/freeipa-server:rocky-8 RUN sed 's/assert_c(len(insts)/# assert_c(len(insts)/' -i /usr/lib/python3.6/site-packages/lib389/instance/setup.py
Can’t find the ipa-adtrust-install package[edit | edit source]
The FreeIPA packages are under a different app stream repo. Enable it by running dnf -y module enable idm:DL1.
sssd: Decrypt integrity check failed[edit | edit source]
After recreating the FreeIPA server, I uninstalled and reinstalled the FreeIPA client on a machine. Kinit works as expected, but sssd authentication fails with the following error in /var/log/sssd/.
[krb5_child[29691]] [get_and_save_tgt] (0x0020): [RID#6] 1725: [-1765328353][Decrypt integrity check failed]
The fix here is to wipe out all the caches. sss_cache -E isn’t sufficient. You have to stop sssd and delete all the databases:
# systemctl stop sssd # rm -rf /var/lib/sss/db/* # systemctl start sssd
File permission issues[edit | edit source]
I ran into issues starting FreeIPA in a Docker container. Symptoms include the following issues in the subsections below.
Bind / named doesn’t start:[edit | edit source]
ipa named-pkcs11[5407]: LDAP error: Invalid credentials: bind to LDAP server failed ipa named-pkcs11[5407]: couldn't establish connection in LDAP connection pool: permission denied ipa named-pkcs11[5407]: dynamic database 'ipa' configuration failed: permission denied ipa named-pkcs11[5407]: loading configuration: permission denied ipa named-pkcs11[5407]: exiting (due to fatal error)
Ignore this for now. You have other issues, likely.
Samba doesn’t start: Error: Invalid credentials[edit | edit source]
When trying to start smb, I get the following:
[2023/01/24 05:17:46.170883, 0, pid=5124] ipa_sam.c:4945(bind_callback) bind_callback: cannot perform interactive SASL bind with GSSAPI. LDAP security error is 49 [2023/01/24 05:17:46.171155, 0, pid=5124] ../../source3/lib/smbldap.c:1059(smbldap_connect_system) failed to bind to server ldapi://%2fvar%2frun%2fslapd-HOME-STEAMR-COM.socket with dn="[Anonymous bind]" Error: Invalid credentials (unknown) [2023/01/24 05:17:46.171419, 1, pid=5124] ../../source3/lib/smbldap.c:1272(get_cached_ldap_connect) Connection to LDAP server failed for the 1 try!
The fix was to stop FreeIPA with ipactl stop, then rm /run/samba/krb5cc_samba, and restarting FreeIPA with ipactl start. If the error recurrs after restarting FreeIPA, then you have other issues that’s preventing Samba from starting.
Tomcat doesn’t start: status=5/NOTINSTALLED[edit | edit source]
When trying to start Tomcat, you get a 5 exit code, as reported by systemd:
pki-tomcatd@pki-tomcat.service: Control process exited, code=exited, status=5/NOTINSTALLED pki-tomcatd@pki-tomcat.service: Failed with result 'exit-code'. Failed to start PKI Tomcat Server pki-tomcat.
The exit code 5 being ‘NOTINSTALLED’ is a red herring. You likely have permission issues that’s preventing the user running tomcat (pkiuser) from accessing some certs or configs. Go through your Docker volumes and chown anything directory called ‘pki’ to the pkiuser.
# chown -R 17:17 etc/pki etc/sysconfig/pki var/lib/pki var/lib/ipa/pki-ca
Tomcat still doesn’t start: start-post operation timed out. Terminating.[edit | edit source]
Tomcat doesn’t start as it times out.
pki-tomcatd@pki-tomcat.service: start-post operation timed out. Terminating. pki-tomcatd@pki-tomcat.service: Control process exited, code=killed, status=15/TERM pki-tomcatd@pki-tomcat.service: Failed with result 'timeout'.
There’s likely still something tomcat can’t write to.
It seemed to get better when made the ownerships for /data/var/lib/pki/pki-tomcat/logs/ and /var/log/pki/pki-tomcat to pkiuser.
To help troubleshoot, su as pkiuser and try running tomcat as per the service file and see if you get any stack traces.
IPA Web GUI reports «Your session has expired. Please re-login»[edit | edit source]
Review the logs for dirsrv and see if there are any errors.
# tail -f /var/log/dirsrv/slapd-*/access
For this instance, this was caused when I accidentally removed /etc/dirsrv/ds.keytab.
Configuring Samba issues[edit | edit source]
When running # ipa-adtrust-install —add-sids, you get:
# ipa-adtrust-install --add-sids ... Configuring CIFS [1/25]: validate server hostname [error] ValueError: Host reports different name than configured: 'ipa' versus 'ipa.home.steamr.com'. Samba requires to have the same hostname or Kerberos principal 'cifs/ipa.home.steamr.com' will not be found in Samba keytab. Unexpected error - see /var/log/ipaserver-adtrust-install.log for details: ValueError: Host reports different name than configured: 'ipa' versus 'ipa.home.steamr.com'. Samba requires to have the same hostname or Kerberos principal 'cifs/ipa.home.steamr.com' will not be found in Samba keytab.
Ensure that your hostname is the full FQDN.
# hostname ipa # hostname -f ipa.home.steamr.com ## You need to fix the hostname so that this is what you get: # hostname ipa.home.steamr.com # hostname ipa.home.steamr.com
Once the hostname is fixed, try the command again.
DNS is missing A/AAAA entries for hosts[edit | edit source]
When trying to add a new host, the DNS silently gets ignored. Possible issues:
- I think this is related to this error when running ipa-client-install:
Could not update DNS SSHFP records.. - Possibly bad DNS entries during install was detected and it skipped the DNS tasks?
Hostname (fc37.home.steamr.com) does not have A/AAAA record. Failed to update DNS records. Missing A/AAAA record(s) for host fc37.home.steamr.com: 10.1.2.32. Incorrect reverse record(s): 10.1.2.32 is pointing to fc35.home.steamr.com. instead of fc37.home.steamr.com.
Without this DNS entry set, other issues will crop up later on:
[root@ipa /]# ipa service-add cifs/dnas.home.steamr.com ipa: ERROR: Host 'dnas.home.steamr.com' does not have corresponding DNS A/AAAA record
The quick work-around would be to add the DNS entry manually and try again.
See also[edit | edit source]
- https://bgstack15.wordpress.com/2017/05/10/samba-share-with-freeipa-auth/ — Older guide walking how to set up FreeIPA and Samba
- https://blog.cubieserver.de/2018/synology-nas-samba-nfs-and-kerberos-with-freeipa-ldap/
- https://www.freeipa.org/page/Howto/Integrating_a_Samba_File_Server_With_IPA — Samba integration using kerberos (not ipasam)
- https://freeipa-users.redhat.narkive.com/ez2uKpFS/authenticate-samba-3-or-4-with-freeipa
Linux |
|
|---|---|
| Various Linux Notes |
|
| Linux Tools and Utilites |
|
| Package Management |
|
| Linux Distributions |
|
| Networking |
|
| Containers |
|
