Introduction
This document describes various types of IP Access Control Lists (ACLs) and how they can filter network traffic.
Prerequisites
Requirements
There are no specific prerequisites for this document. The concepts discussed are present in Cisco IOS®Software Releases 8.3 or later. This is noted under each access list feature.
Components Used
This document discusses various types of ACLs. Some of these are present since Cisco IOS Software Releases 8.3 and others were introduced in later software releases. This is noted in the discussion of each type.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
Refer toCisco Technical Tips Conventionsfor more information on document conventions.
Background Information
This document describes how IP access control lists (ACLs) can filter network traffic. It also contains brief descriptions of the IP ACL types, feature availability, and an example of use in a network.
Note: RFC 1700 contains assigned numbers of well-known ports.RFC 1918 contains address allocation for private Internets, IP addresses which must not normally be seen on the Internet.
Note: Only registered Cisco users can access internal information.
Note: ACLs can also be used to define traffic to Network Address Translate (NAT), encrypt or filter non-IP protocols such as AppleTalk or IPX. A discussion of these functions is outside the scope of this document.
ACL Concepts
Masks
Masks are used with IP addresses in IP ACLs to specify what must be permitted and denied. Masks in order to configure IP addresses on interfaces start with 255 and have the large values on the left side, for example, IP address 10.165.202.129 with a 255.255.255.224 mask. Masks for IP ACLs are the reverse, for example, mask 0.0.0.255. This is sometimes called an inverse mask or a wildcard mask. When the value of the mask is broken down into binary (0s and 1s), the results determine which address bits to consider when traffic is processed. A 0 indicates that the address bits must be considered (exact match); a 1 in the mask is a do not care. This table further explains the concept.
| Mask Example | |
|---|---|
| network address (traffic that is to be processed) | 10.1.1.0 |
| mask | 0.0.0.255 |
| network address (binary) | 00001010.00000001.00000001.00000000 |
| mask (binary) | 00000000.00000000.00000000.11111111 |
Based on the binary mask, you can see that the first three sets (octets) must match the given binary network address exactly (00001010.00000001.00000001). The last set of numbers are do not cares (.11111111). Therefore, all traffic that begins with 10.1.1. matches since the last octet is do not care. Therefore, with this mask, network addresses 10.1.1.1 through 10.1.1.255 (10.1.1.x) are processed.
Subtract the normal mask from 255.255.255.255 in order to determine the ACL inverse mask. In this example, the inverse mask is determined for network address 172.16.1.0 with a normal mask of 255.255.255.0.
-
255.255.255.255 — 255.255.255.0 (normal mask) = 0.0.0.255 (inverse mask)
Notice the ACL equivalents.
-
The source/wildcard of 0.0.0.0/255.255.255.255 means any.
-
The source/wildcard of 10.1.1.2/0.0.0.0 is the same as host 10.1.1.2.
ACL Summarization
Note: Subnet masks can also be represented as a fixed length notation. For example, 192.168.10.0/24 represents 192.168.10.0 255.255.255.0.
This list describes how to summarize a range of networks into a single network for ACL optimization. Consider these networks.
192.168.32.0/24 192.168.33.0/24 192.168.34.0/24 192.168.35.0/24 192.168.36.0/24 192.168.37.0/24 192.168.38.0/24 192.168.39.0/24
The first two octets and the last octet are the same for each network. This table is an explanation of how to summarize these into a single network.
The third octet for the previous networks can be written as seen in this table, correspondent to the octet bit position and address value for each bit.
| Decimal | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| 32 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 |
| 33 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 1 |
| 34 | 0 | 0 | 1 | 0 | 0 | 0 | 1 | 0 |
| 35 | 0 | 0 | 1 | 0 | 0 | 0 | 1 | 1 |
| 36 | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 |
| 37 | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 1 |
| 38 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 0 |
| 39 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 1 |
| M | M | M | M | M | D | D | D |
Since the first five bits match, the previous eight networks can be summarized into one network (192.168.32.0/21 or 192.168.32.0 255.255.248.0). All eight possible combinations of the three low-order bits are relevant for the network ranges in question. This command defines an ACL that permits this network. If you subtract 255.255.248.0 (normal mask) from 255.255.255.255, it yields 0.0.7.255.
access-list acl_permit permit ip 192.168.32.00.0.7.255
Consider this set of networks for further explanation.
192.168.146.0/24 192.168.147.0/24 192.168.148.0/24 192.168.149.0/24
The first two octets and the last octet are the same for each network. This table is an explanation of how to summarize these.
The third octet for the previous networks can be written as seen in this table, correspondent to the octet bit position and address value for each bit.
| Decimal | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| 146 | 1 | 0 | 0 | 1 | 0 | 0 | 1 | 0 |
| 147 | 1 | 0 | 0 | 1 | 0 | 0 | 1 | 1 |
| 148 | 1 | 0 | 0 | 1 | 0 | 1 | 0 | 0 |
| 149 | 1 | 0 | 0 | 1 | 0 | 1 | 0 | 1 |
| M | M | M | M | M | ? | ? | ? |
Unlike the previous example, you cannot summarize these networks into a single network. If they are summarized to a single network, they become 192.168.144.0/21 because there are five bits similar in the third octet. This summarized network 192.168.144.0/21 covers a range of networks from 192.168.144.0 to 192.168.151.0. Among these, 192.168.144.0, 192.168.145.0, 192.168.150.0, and 192.168.151.0 networks are not in the given list of four networks. In order to cover the specific networks in question, you need a minimum of two summarized networks. The given four networks can be summarized into these two networks:
-
For networks 192.168.146.x and 192.168.147.x, all bits match except for the last one, which is a do not care. This can be written as 192.168.146.0/23 (or 192.168.146.0 255.255.254.0).
-
For networks 192.168.148.x and 192.168.149.x, all bits match except for the last one, which is a do not care. This can be written as 192.168.148.0/23 (or 192.168.148.0 255.255.254.0).
This output defines a summarized ACL for the previously networks.
!--- This command is used to allow access access for devices with IP
!--- addresses in the range from 192.168.146.0 to 192.168.147.254. access-list 10 permit 192.168.146.00.0.1.255
!--- This command is used to allow access access for devices with IP
!--- addresses in the range from 192.168.148.0 to 192.168.149.254 access-list 10 permit 192.168.148.00.0.1.255
Process ACLs
Traffic that comes into the router is compared to ACL entries based on the order that the entries occur in the router. New statements are added to the end of the list. The router continues to look until it has a match. If no matches are found when the router reaches the end of the list, the traffic is denied. For this reason, you must have the frequently hit entries at the top of the list. There is an implied deny for traffic that is not permitted. A single-entry ACL with only one deny entry can deny all traffic. You must have at least one permit statement in an ACL or all traffic is blocked. These two ACLs (101 and 102) have the same effect.
!--- This command is used to permit IP traffic from 10.1.1.0
!--- network to 172.16.1.0 network. All packets with a source
!--- address not in this range will be rejected. access-list 101 permit ip 10.1.1.0 0.0.0.255 172.16.1.00.0.0.255
!--- This command is used to permit IP traffic from 10.1.1.0
!--- network to 172.16.1.0 network. All packets with a source
!--- address not in this range will be rejected. access-list 102 permit ip 10.1.1.0 0.0.0.255 172.16.1.00.0.0.255
access-list 102 deny ip any any
In the next example, the last entry is sufficient. You do not need the first three entries because IP includes TCP, User Datagram Protocol (UDP), and Internet Control Message Protocol (ICMP).
!--- This command is used to permit Telnet traffic
!--- from machine 10.1.1.2 to machine 172.16.1.1. access-list 101 permit tcp host 10.1.1.2 host 172.16.1.1 eq telnet
!--- This command is used to permit tcp traffic from
!--- 10.1.1.2 host machine to 172.16.1.1 host machine. access-list 101 permit tcp host 10.1.1.2 host 172.16.1.1
!--- This command is used to permit udp traffic from
!--- 10.1.1.2 host machine to 172.16.1.1 host machine. access-list 101 permit udp host 10.1.1.2 host 172.16.1.1
!--- This command is used to permit ip traffic from
!--- 10.1.1.0 network to 172.16.1.10 network. access-list 101 permit ip 10.1.1.0 0.0.0.255 172.16.1.00.0.0.255
Define Ports and Message Types
Not only can you define ACL source and destination, but you can also define ports, ICMP message types, and other parameters. A good source of information for well-known ports is RFC 1700 . ICMP message types are explained in RFC 792 .
The router can display descriptive text on some of the well-known ports. Use a?for help.
access-list 102 permit tcp host 10.1.1.1 host 172.16.1.1 eq ? bgp Border Gateway Protocol (179) chargen Character generator (19) cmd Remote commands (rcmd, 514)
During configuration, the router also converts numeric values to more user-friendly values. This is an example where you type the ICMP message type number, and it causes the router to convert the number to a name.
access-list 102 permit icmp host 10.1.1.1 host 172.16.1.1 14
becomes
access-list 102 permit icmp host 10.1.1.1 host 172.16.1.1 timestamp-reply
Apply ACLs
You can define ACLs and still not apply them. But, the ACLs have no effect until they are applied to the interface of the router. It is a good practice to apply the ACL on the interface closest to the source of the traffic. As shown in this example, when you try to block traffic from source to destination, you can apply an inbound ACL to E0 on router A instead of an outbound list to E1 on router C. An access-list has adeny ip any anyimplicitly at the end of any access-list. If traffic is related to a DHCP request and if it is not explicitly permitted, the traffic is dropped because when you look at DHCP request in IP, the source address is s=0.0.0.0 (Ethernet1/0), d=255.255.255.255, len 604, rcvd 2 UDP src=68, dst=67. Notice that the source IP address is 0.0.0.0 and destination address is 255.255.255.255. Source port is 68 and destination 67. Therefore, you must permit this kind of traffic in your access-list or else the traffic is dropped due to implicit deny at the end of the statement.
Note: For UDP traffic to pass through, UDP traffic must also be permitted explicitly by the ACL.
Define In, Out, Inbound, Outbound, Source, and Destination
The router uses the terms in, out, source, and destination as references. Traffic on the router can be compared to traffic on the highway. If you were a law enforcement officer in Pennsylvania and wanted to stop a truck that travels from Maryland to New York, the source of the truck is Maryland, and the destination of the truck is New York. The roadblock could be applied at the Pennsylvania–New York border (out) or the Maryland–Pennsylvania border (in).
When you refer to a router, these terms have these meanings.
-
Out—Traffic that has already been through the router and leaves the interface. The source is where it has been, on the other side of the router, and the destination is where it goes.
-
In—Traffic that arrives on the interface and then goes through the router. The source is where it has been and the destination is where it goes, on the other side of the router.
-
Inbound—If the access list is inbound, when the router receives a packet, the Cisco IOS software checks the criteria statements of the access list for a match. If the packet is permitted, the software continues to process the packet. If the packet is denied, the software discards the packet.
-
Outbound—If the access list is outbound, after the software receives and routes a packet to the outbound interface, the software checks the criteria statements of the access list for a match. If the packet is permitted, the software transmits the packet. If the packet is denied, the software discards the packet.
The in ACL has a source on a segment of the interface to which it is applied and a destination off of any other interface. The out ACL has a source on a segment of any interface other than the interface to which it is applied and a destination off of the interface to which it is applied.
Edit ACLs
When you edit an ACL, it requires special attention. For example, if you intend to delete a specific line from a numbered ACL that exists as shown here, the entire ACL is deleted.
!--- The access-list 101 denies icmp from any to any network
!--- but permits IP traffic from any to any network. router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. router(config)#access-list 101 deny icmp any any router(config)#access-list 101 permit ip any any router(config)#^Z router#show access-list Extended IP access list 101 deny icmp any any permit ip any any router# *Mar 9 00:43:12.784: %SYS-5-CONFIG_I: Configured from console by console router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. router(config)#no access-list 101 deny icmp any any router(config)#^Z router#show access-list router# *Mar 9 00:43:29.832: %SYS-5-CONFIG_I: Configured from console by console
Copy the configuration of the router to a TFTP server or a text editor such as Notepad in order to edit numbered ACLs. Then make any changes and copy the configuration back to the router.
You can also do this.
router#configure terminal Enter configuration commands, one per line. router(config)#ip access-list extended test !--- Permits IP traffic from 10.2.2.2 host machine to 10.3.3.3 host machine. router(config-ext-nacl)#permit ip host 10.2.2.2 host 10.3.3.3 !--- Permits www traffic from 10.1.1.1 host machine to 10.5.5.5 host machine. router(config-ext-nacl)#permit tcp host 10.1.1.1 host 10.5.5.5 eq www !--- Permits icmp traffic from any to any network. router(config-ext-nacl)#permit icmp any any !--- Permits dns traffic from 10.6.6.6 host machine to 10.10.10.0 network. router(config-ext-nacl)#permit udp host 10.6.6.6 10.10.10.0 0.0.0.255 eq domain router(config-ext-nacl)#^Z 1d00h: %SYS-5-CONFIG_I: Configured from console by consoles-l router#show access-list Extended IP access list test permit ip host 10.2.2.2 host 10.3.3.3 permit tcp host 10.1.1.1 host 10.5.5.5 eq www permit icmp any any permit udp host 10.6.6.6 10.10.10.0 0.0.0.255 eq domain
Any deletions are removed from the ACL and any additions are made to the end of the ACL.
router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
router(config)#ip access-list extended test
!--- ACL entry deleted.
router(config-ext-nacl)#no permit icmp any any
!--- ACL entry added.
router(config-ext-nacl)#permit gre host 10.4.4.4 host 10.8.8.8
router(config-ext-nacl)#^Z
1d00h: %SYS-5-CONFIG_I: Configured from console by consoles-l
router#show access-list
Extended IP access list test
permit ip host 10.2.2.2 host 10.3.3.3
permit tcp host 10.1.1.1 host 10.5.5.5 eq www
permit udp host 10.6.6.6 10.10.10.0 0.0.0.255 eq domain
permit gre host 10.4.4.4 host 10.8.8.8
You can also add ACL lines to numbered standard or numbered extended ACLs by sequence number in Cisco IOS. This is a sample of the configuration:
Configure the extended ACL in this way:
Router(config)#access-list 101 permit tcp any any Router(config)#access-list 101 permit udp any any Router(config)#access-list 101 permit icmp any any Router(config)#exit Router#
Issue theshow access-listcommand in order to view the ACL entries. The sequence numbers such as 10, 20, and 30 also appear here.
Router#show access-list
Extended IP access list 101
10 permit tcp any any
20 permit udp any any
30 permit icmp any any
Add the entry for the access list 101 with the sequence number 5.
Example 1:
Router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)#ip access-list extended 101 Router(config-ext-nacl)#5 deny tcp any any eq telnet Router(config-ext-nacl)#exit Router(config)#exit Router#
In theshow access-listcommand output, the sequence number 5 ACL is added as the first entry to the access-list 101.
Router#show access-list
Extended IP access list 101
5 deny tcp any any eq telnet
10 permit tcp any any
20 permit udp any any
30 permit icmp any any
Router#
Example 2:
internetrouter#show access-lists
Extended IP access list 101
10 permit tcp any any
15 permit tcp any host 172.16.2.9
20 permit udp host 172.16.1.21 any
30 permit udp host 172.16.1.22 any
internetrouter#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
internetrouter(config)#ip access-list extended 101
internetrouter(config-ext-nacl)#18 per tcp any host 172.16.2.11
internetrouter(config-ext-nacl)#^Z
internetrouter#show access-lists
Extended IP access list 101
10 permit tcp any any
15 permit tcp any host 172.16.2.9
18 permit tcp any host 172.16.2.11
20 permit udp host 172.16.1.21 any
30 permit udp host 172.16.1.22 any
internetrouter#
Similarly, you can configure the standard access list in this way:
internetrouter(config)#access-list 2 permit 172.16.1.2
internetrouter(config)#access-list 2 permit 172.16.1.10
internetrouter(config)#access-list 2 permit 172.16.1.11
internetrouter#show access-lists
Standard IP access list 2
30 permit 172.16.1.11
20 permit 172.16.1.10
10 permit 172.16.1.2
internetrouter(config)#ip access-list standard 2
internetrouter(config-std-nacl)#25 per 172.16.1.7
internetrouter(config-std-nacl)#15 per 172.16.1.16
internetrouter#show access-lists
Standard IP access list 2
15 permit 172.16.1.16
30 permit 172.16.1.11
20 permit 172.16.1.10
25 permit 172.16.1.7
10 permit 172.16.1.2
The major difference in a standard access list is that the Cisco IOS adds an entry in descendant order of the IP address, not on a sequence number.
This example shows the different entries, for example, how to permit an IP address (192.168.100.0) or the networks (10.10.10.0).
internetrouter#show access-lists
Standard IP access list 19
10 permit 192.168.100.0
15 permit 10.10.10.0, wildcard bits 0.0.0.255
19 permit 10.101.110.0, wildcard bits 0.0.0.255
25 deny any
Add the entry in access list 2 in order to permit the IP Address 172.22.1.1:
internetrouter(config)#ip access-list standard 2 internetrouter(config-std-nacl)#18 permit 172.22.1.1
This entry is added in the top of the list in order to give priority to the specific IP address rather than network.
internetrouter#show access-lists
Standard IP access list 19
10 permit 192.168.100.0
18 permit 172.22.1.1
15 permit 10.10.10.0, wildcard bits 0.0.0.255
19 permit 10.101.110.0, wildcard bits 0.0.0.255
25 deny any
Note: The previous ACLs are not supported in Security Appliance such as the ASA/PIX Firewall.
Guidelines to change access-lists when they are applied to crypto maps
-
If you add to a current access-list configuration, there is no need to remove the crypto map. If you add to them directly without the removal of the crypto map, then that is supported and acceptable.
-
If you need to modify or delete access-list entry from a current access-lists, then you must remove the crypto map from the interface. After you remove crypto map, make all changes to the access-list and re-add the crypto map. If you make changes such as the deletion of the access-list without the removal of the crypto map, this is not supported and can result in unpredictable behavior.
Troubleshoot
How do I remove an ACL from an interface?
Go into configuration mode and enter no in front of the access-group command, as shown in this example, in order to remove an ACL from an interface.
interface <interface-name> no ip access-group <acl-number> {in|out}
What do I do when too much traffic is denied?
If too much traffic is denied, study the logic of your list or try to define and apply an additional broader list. The show ip access-lists command provides a packet count that shows which ACL entry is hit. The log keyword at the end of the individual ACL entries shows the ACL number and whether the packet was permitted or denied, in addition to port-specific information.
Note: The log-input keyword exists in Cisco IOS Software Release 11.2 and later, and in certain Cisco IOS Software Release 11.1 based software created specifically for the service provider market. Older software does not support this keyword. Use of this keyword includes the input interface and source MAC address where applicable.
How do I debug at the packet level that uses a Cisco router?
This procedure explains the debug process. Before you begin, be certain that there are no currently applied ACLs, that there is an ACL, and that fast switching is not disabled.
Note: Use extreme caution when you debug a system with heavy traffic. Use an ACL in order to debug specific traffic. But ensure the process and the traffic flow.
-
Use theaccess-listcommand in order to capture the desired data.
In this example, the data capture is set for the destination address of 10.2.6.6 or the source address of 10.2.6.6.
access-list 101 permit ip any host 10.2.6.6 access-list 101 permit ip host 10.2.6.6 any
-
Disable fast switching on the interfaces involved. You only see the first packet if fast switching is not disabled.
configure terminal
interface <interface-name> no ip route-cache -
Use the terminal monitor command in enable mode in order to display debug command output and system error messages for the current terminal and session.
-
Use the debug ip packet 101 or debug ip packet 101 detail command in order to begin the debug process.
-
Execute the no debug all command in enable mode and the interface configuration command in order to stop the debug process.
-
Restart caching.
configure terminal
interface <interface-name> ip route-cache
Types of IP ACLs
This section of the document describes ACL types.
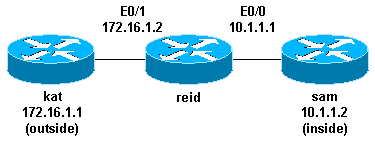
Network Diagram
Standard ACLs
Standard ACLs are the oldest type of ACL. They date back to as early as Cisco IOS Software Release 8.3. Standard ACLs control traffic by the comparison of the source address of the IP packets to the addresses configured in the ACL.
This is the command syntax format of a standard ACL.
access-list <access-list-number> {permit|deny} {host|source source-wildcard|any}
In all software releases, the access-list-number can be anything from 1 to 99. In Cisco IOS Software Release 12.0.1, standard ACLs begin to use additional numbers (1300 to 1999). These additional numbers are referred to as expanded IP ACLs. Cisco IOS Software Release 11.2 added the ability to use list name in standard ACLs.
A s ource/source-wildcard setting of 0.0.0.0/255.255.255.255 can be specified as any . The wildcard can be omitted if it is all zeros. Therefore, host 10.1.1.2 0.0.0.0 is the same as host 10.1.1.2.
After the ACL is defined, it must be applied to the interface (inbound or outbound). In early software releases, out was the default when a keyword out or in was not specified. The direction must be specified in later software releases.
interface <interface-name>
ip access-group number {in|out}
This is an example of the use of a standard ACL in order to block all traffic except that from source 10.1.1.x.
interface Ethernet0/0 ip address 10.1.1.1 255.255.255.0 ip access-group 1 in !
access-list 1 permit 10.1.1.0 0.0.0.255
Extended ACLs
Extended ACLs were introduced in Cisco IOS Software Release 8.3. Extended ACLs control traffic by the comparison of the source and destination addresses of the IP packets to the addresses configured in the ACL.
This is the command syntax format of extended ACLs. Lines are wrapped here for space considerations.
IP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} protocol source source-wildcard destination destination-wildcard [precedence precedence]
[tos tos] [log|log-input] [time-range time-range-name]
ICMP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} icmp source source-wildcard destination destination-wildcard
[icmp-type [icmp-code] |icmp-message]
[precedence precedence] [tos tos] [log|log-input]
[time-range time-range-name]
TCP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} tcp source source-wildcard [operator [port]]
destination destination-wildcard [operator [port]]
[established] [precedence precedence] [tos tos]
[log|log-input] [time-range time-range-name]
UDP
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} udp source source-wildcard [operator [port]]
destination destination-wildcard [operator [port]]
[precedence precedence] [tos tos] [log|log-input]
[time-range time-range-name]
In all software releases, the access-list-number can be 100 to 199. In Cisco IOS Software Release 12.0.1, extended ACLs begin to use additional numbers (2000 to 2699). These additional numbers are referred to as expanded IP ACLs. Cisco IOS Software Release 11.2 added the ability to use list name in extended ACLs.
The value of 0.0.0.0/255.255.255.255 can be specified as any . After the ACL is defined, it must be applied to the interface (inbound or outbound). In early software releases, out was the default when a keyword out or in was not specified. The direction must be specified in later software releases.
interface <interface-name>
ip access-group {number|name} {in|out}
This extended ACL is used to permit traffic on the 10.1.1.x network (inside) and to receive ping responses from the outside while it prevents unsolicited pings from people outside, which permits all other traffic.
interface Ethernet0/1 ip address 172.16.1.2 255.255.255.0 ip access-group 101 in !
access-list 101 deny icmp any 10.1.1.0 0.0.0.255 echo access-list 101 permit ip any 10.1.1.0 0.0.0.255
Note: Some applications such as network management require pings for a keepalive function. If this is the case, you can limit the inbound pings that are blocked or be more granular in permitted/denied IPs.
Lock and Key (Dynamic ACLs)
Lock and key, also known as dynamic ACLs, was introduced in Cisco IOS Software Release 11.1. This feature is dependent on Telnet, authentication (local or remote), and extended ACLs.
Lock and key configuration starts with the application of an extended ACL to block traffic through the router. Users that want to traverse the router are blocked by the extended ACL until they Telnet to the router and are authenticated. The Telnet connection then drops, and a single-entry dynamic ACL is added to the extended ACL that exists. This permits traffic for a particular time period; idle and absolute timeouts are possible.
This is the command syntax format for lock and key configuration with local authentication.
username <user-name> password <password> !
interface <interface-name> ip access-group {number|name} {in|out}
The single-entry ACL in this command is dynamically added to the ACL that exists after authentication.
access-list access-list-number dynamic name {permit|deny} [protocol]
{source source-wildcard|any} {destination destination-wildcard|any}
[precedence precedence][tos tos][established] [log|log-input]
[operator destination-port|destination port]
line vty <line_range>
login local
This is a basic example of lock and key.
username test password 0 test !--- Ten (minutes) is the idle timeout. username test autocommand access-enable host timeout 10 ! interface Ethernet0/0 ip address 10.1.1.1 255.255.255.0 ip access-group 101 in ! access-list 101 permit tcp any host 10.1.1.1 eq telnet !--- 15 (minutes) is the absolute timeout. access-list 101 dynamic testlist timeout 15 permit ip 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255 ! line vty 0 4 login local
After the user at 10.1.1.2 makes a Telnet connection to 10.1.1.1, the dynamic ACL is applied. The connection is then dropped, and the user can go to the 172.16.1.x network.
IP Named ACLs
IP named ACLs were introduced in Cisco IOS Software Release 11.2. This allows standard and extended ACLs to be given names instead of numbers.
This is the command syntax format for IP named ACLs.
ip access-list {extended|standard} name
This is a TCP example:
{permit|deny} tcp source source-wildcard [operator [port]]
destination destination-wildcard [operator [port]] [established]
[precedence precedence] [tos tos] [log] [time-range time-range-name]
This is an example of the use of a named ACL in order to block all traffic except the Telnet connection from host 10.1.1.2 to host 172.16.1.1.
interface Ethernet0/0 ip address 10.1.1.1 255.255.255.0 ip access-group in_to_out in ! ip access-list extended in_to_out permit tcp host 10.1.1.2 host 172.16.1.1 eq telnet
Reflexive ACLs
Reflexive ACLs were introduced in Cisco IOS Software Release 11.3. Reflexive ACLs allow IP packets to be filtered based on upper-layer session information. They are generally used to allow outbound traffic and to limit inbound traffic in response to sessions that originate inside the router.
Reflexive ACLs can be defined only with extended named IP ACLs. They cannot be defined with numbered or standard named IP ACLs, or with other protocol ACLs. Reflexive ACLs can be used in conjunction with other standard and static extended ACLs.
This is the syntax for various reflexive ACL commands.
interface <interface-name>
ip access-group {number|name} {in|out}
!
ip access-list extended <name>
permit protocol any any reflect name [timeoutseconds]
!
ip access-list extended <name>
evaluate <name>
This is an example of the permit of ICMP outbound and inbound traffic, while it permits only TCP traffic that has initiated from inside, other traffic is denied.
ip reflexive-list timeout 120 ! interface Ethernet0/1 ip address 172.16.1.2 255.255.255.0 ip access-group inboundfilters in ip access-group outboundfilters out ! ip access-list extended inboundfilters permit icmp 172.16.1.0 0.0.0.255 10.1.1.0 0.0.0.255 evaluate tcptraffic !--- This ties the reflexive ACL part of the outboundfilters ACL,
!--- called tcptraffic, to the inboundfilters ACL. ip access-list extended outboundfilters permit icmp 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255 permit tcp 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255 reflect tcptraffic
Time-Based ACLs Using Time Ranges
Time-based ACLs were introduced in Cisco IOS Software Release 12.0.1.T. While similar to extended ACLs in function, they allow for access control based on time. A time range is created that defines specific times of the day and week in order to implement time-based ACLs. The time range is identified by a name and then referenced by a function. Therefore, the time restrictions are imposed on the function itself. The time range relies on the router system clock. The router clock can be used, but the feature works best with Network Time Protocol (NTP) synchronization.
These are time-based ACL commands.
!--- Defines a named time range. time-range time-range-name !--- Defines the periodic times. periodic days-of-the-week hh:mm to [days-of-the-week] hh:mm !--- Or, defines the absolute times. absolute [start time date] [end time date] !--- The time range used in the actual ACL. ip access-list name|number <extended_definition>time-rangename_of_time-range
In this example, a Telnet connection is permitted from the inside to outside network on Monday, Wednesday, and Friday during business hours:
interface Ethernet0/0 ip address 10.1.1.1 255.255.255.0 ip access-group 101 in ! access-list 101 permit tcp 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255 eq telnet time-range EVERYOTHERDAY ! time-range EVERYOTHERDAY periodic Monday Wednesday Friday 8:00 to 17:00
Commented IP ACL Entries
Commented IP ACL entries were introduced in Cisco IOS Software Release 12.0.2.T. Comments make ACLs easier to understand and can be used for standard or extended IP ACLs.
This is the commented name IP ACL command syntax.
ip access-list {standard|extended} <access-list-name>
remark remark
This is the commented numbered IP ACL command syntax.
access-list <access-list-number> remark remark
This is an example of comments within a numbered ACL.
interface Ethernet0/0 ip address 10.1.1.1 255.255.255.0 ip access-group 101 in ! access-list 101 remark permit_telnet access-list 101 permit tcp host 10.1.1.2 host 172.16.1.1 eq telnet
Context-Based Access Control
Context-based access control (CBAC) was introduced in Cisco IOS Software Release 12.0.5.T and requires the Cisco IOS Firewall feature set. CBAC inspects traffic that travels through the firewall in order to discover and manage state information for TCP and UDP sessions. This state information is used in order to create temporary openings in the access lists of the firewall. Configureip inspectlists in the direction of the flow of traffic initiation in order to allow return traffic and additional data connections for permissible session, sessions that originated from within the protected internal network, in order to do this.
This is the syntax for CBAC.
ip inspect name inspection-name protocol [timeoutseconds]
This is an example of the use of CBAC in order to inspect outbound traffic. Extended ACL 111 normally block the return traffic other than ICMP without CBAC opening holes for the return traffic.
ip inspect name myfw ftp timeout 3600 ip inspect name myfw http timeout 3600 ip inspect name myfw tcp timeout 3600 ip inspect name myfw udp timeout 3600 ip inspect name myfw tftp timeout 3600
! interface Ethernet0/1 ip address 172.16.1.2 255.255.255.0 ip access-group 111 in ip inspect myfw out !
access-list 111 deny icmp any 10.1.1.0 0.0.0.255 echo access-list 111 permit icmp any 10.1.1.0 0.0.0.255
Authentication Proxy
Authentication proxy was introduced in Cisco IOS Software Release 12.0.5.T. This requires that you have the Cisco IOS Firewall feature set. Authentication proxy is used to authenticate inbound or outbound users, or both. Users who are normally blocked by an ACL can bring up a browser to go through the firewall and authenticate on a TACACS+ or RADIUS server. The server passes additional ACL entries down to the router in order to allow the users through after authentication.
Authentication proxy is similar to lock and key (dynamic ACLs). These are the differences:
-
Lock and key is turned on by a Telnet connection to the router. Authentication proxy is turned on by HTTP through the router.
-
Authentication proxy must use an external server.
-
Authentication proxy can handle the addition of multiple dynamic lists. Lock and key can only add one.
-
Authentication proxy has an absolute timeout but no idle timeout. Lock and key has both.
Refer to the Cisco Secure Integrated Software Configuration Cookbook for examples of authentication proxy.
Turbo ACLs
Turbo ACLs were introduced in Cisco IOS Software Release 12.1.5.T and are found only on the 7200, 7500, and other high-end platforms. The turbo ACL feature is designed in order to process ACLs more efficiently in order to improve router performance.
Use the access-list compiled command for turbo ACLs. This is an example of a compiled ACL.
access-list 101 permit tcp host 10.1.1.2 host 172.16.1.1 eq telnet access-list 101 permit tcp host 10.1.1.2 host 172.16.1.1 eq ftp access-list 101 permit udp host 10.1.1.2 host 172.16.1.1 eq syslog access-list 101 permit udp host 10.1.1.2 host 172.16.1.1 eq tftp access-list 101 permit udp host 10.1.1.2 host 172.16.1.1 eq ntp
After the standard or extended ACL is defined, use the global configuration command in order to compile.
!--- Tells the router to compile. access-list compiled ! interface Ethernet0/1 ip address 172.16.1.2 255.255.255.0 !--- Applies to the interface. ip access-group 101 in
The show access-list compiled command shows statistics about the ACL.
Distributed Time-Based ACLs
Distributed time-based ACLs were introduced in Cisco IOS Software Release 12.2.2.T in order to implement time-based ACLs on VPN-enabled 7500 series routers. Before the introduction of the distributed time-based ACL feature, time-based ACLs were not supported on line cards for the Cisco 7500 series routers. If time-based ACLs were configured, they behaved as normal ACLs. If an interface on a line card was configured with time-based ACLs, the packets switched into the interface were not distributed switched through the line card but forwarded to the route processor in order to process.
The syntax for distributed time-based ACLs is the same as for time-based ACLs with the addition of the commands in regard to the status of the Inter Processor Communication (IPC) messages between the route processor and line card.
debug time-range ipc show time-range ipc clear time-range ipc
Receive ACLs
Receive ACLs are used in order to increase security on Cisco 12000 routers by the protection of the gigabit route processor (GRP) of the router from unnecessary and potentially nefarious traffic. Receive ACLs were added as a special waiver to the maintenance throttle for Cisco IOS Software Release 12.0.21S2 and integrated into 12.0(22)S. Refer toGSR: Receive Access Control Listsfor further information.
Infrastructure Protection ACLs
Infrastructure ACLs are used in order to minimize the risk and effectiveness of direct infrastructure attack by the explicit permission of only authorized traffic to the infrastructure equipment while it permits all other transit traffic. Refer to Protecting Your Core: Infrastructure Protection Access Control Lists for further information.
Transit ACLs
Transit ACLs are used in order to increase network security since they explicitly permit only required traffic into your network or networks. Refer to Transit Access Control Lists: Filtering at Your Edge for further information.
Related Information
- Configure Commonly Used IP ACLs
- RFC 1700
- RFC 1918
- Access Lists Support Page
- Cisco IOS Firewall
- Technical Support & Documentation — Cisco Systems
The reason your router hangs is because you’re editing the ACL through the same interface that it’s applied to. Usually what happens is you wind up blocking yourself accidentally.
Note that I make a suggestion for reorganizing your ACLs at the bottom of this answer, although most people will be interested in this first section (the easiest way to change ACLs).
The easiest way to change Cisco IOS ACLs
Newer Cisco IOS images (such as the image on your Cisco 1941) support IP access-list line numbering, which means you can modify your ACL without removing it…
I will use the example of your original ACL 110, although as I mentioned you should really consider reorganizing your ACLs into two different ACLs.
Step 1, ACL 110 already on the router:
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
50 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
60 permit udp any any
70 permit ip any any
Take note of the line numbers that Cisco automatically added to ACL 110. Remember that you need to add your ACL entries before line 50, due to the deny statement.
Step 2, Modify ACL 110 in place with new entries, starting after line 40:
LAB_RTR#conf t
Enter configuration commands, one per line. End with CNTL/Z.
LAB_RTR(config)#ip access-list extended 110
LAB_RTR(config-ext-nacl)#41 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
LAB_RTR(config-ext-nacl)#42 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
LAB_RTR(config-ext-nacl)#43 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
LAB_RTR(config-ext-nacl)#44 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
LAB_RTR(config-ext-nacl)#end
LAB_RTR#
LAB_RTR#
LAB_RTR#
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
41 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
42 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
43 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
44 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
50 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
60 permit udp any any
70 permit ip any any
LAB_RTR#
Step 3, Renumber the ACL, automatically:
The automatic line numbers are nice, because Cisco also gives you a way to renumber the config…
LAB_RTR#conf t
LAB_RTR(config)#! Renumber ACL 110, from line 10... increment in steps of 10
LAB_RTR(config)#ip access-list resequence 110 10 10
LAB_RTR(config)#end
LAB_RTR#
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
50 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
60 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
70 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
80 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
90 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
100 permit udp any any
110 permit ip any any
LAB_RTR#
Original way to change Cisco IOS ACLs
Originally, the safest way to change your ACL was by removing it from the interfaces in question (this prevented problems if you were changing the ACL via the same interface it was applied to).
Use this technique if your IOS doesn’t support IP access-list line numbering:
interface GigabitEthernet0/1.1
no ip access-group 110 in
!
interface GigabitEthernet0/1.2
no ip access-group 110 in
Now you can add the new ACL lines, but do it before the other permit any entries…
! Reset the ACL
no access-list 110
!
access-list 110 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
access-list 110 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
access-list 110 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
!! New ACL lines before the deny statement
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
access-list 110 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
access-list 110 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
!! Deny statement
access-list 110 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 110 permit udp any any
access-list 110 permit ip any any
Finally, reapply the ACL to the switch…
interface GigabitEthernet0/1.1
ip access-group 110 in
!
interface GigabitEthernet0/1.2
ip access-group 110 in
ACL Reorganization
You should really consider using two different ACLs for Gigabit0/1.1 and GigabitEthernet0/1.2… this is a guess at what you’re trying to do, but it’s unclear that I’m interpreting things correctly…
access-list 111 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
access-list 111 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
access-list 111 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
access-list 111 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
access-list 111 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 111 permit udp any any
access-list 111 permit ip any any
!
interface GigabitEthernet0/1.1
no ip access-group 110 in
ip access-group 111 in
!
interface GigabitEthernet0/1.2
no ip access-group 110 in
The reason your router hangs is because you’re editing the ACL through the same interface that it’s applied to. Usually what happens is you wind up blocking yourself accidentally.
Note that I make a suggestion for reorganizing your ACLs at the bottom of this answer, although most people will be interested in this first section (the easiest way to change ACLs).
The easiest way to change Cisco IOS ACLs
Newer Cisco IOS images (such as the image on your Cisco 1941) support IP access-list line numbering, which means you can modify your ACL without removing it…
I will use the example of your original ACL 110, although as I mentioned you should really consider reorganizing your ACLs into two different ACLs.
Step 1, ACL 110 already on the router:
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
50 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
60 permit udp any any
70 permit ip any any
Take note of the line numbers that Cisco automatically added to ACL 110. Remember that you need to add your ACL entries before line 50, due to the deny statement.
Step 2, Modify ACL 110 in place with new entries, starting after line 40:
LAB_RTR#conf t
Enter configuration commands, one per line. End with CNTL/Z.
LAB_RTR(config)#ip access-list extended 110
LAB_RTR(config-ext-nacl)#41 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
LAB_RTR(config-ext-nacl)#42 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
LAB_RTR(config-ext-nacl)#43 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
LAB_RTR(config-ext-nacl)#44 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
LAB_RTR(config-ext-nacl)#end
LAB_RTR#
LAB_RTR#
LAB_RTR#
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
41 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
42 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
43 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
44 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
50 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
60 permit udp any any
70 permit ip any any
LAB_RTR#
Step 3, Renumber the ACL, automatically:
The automatic line numbers are nice, because Cisco also gives you a way to renumber the config…
LAB_RTR#conf t
LAB_RTR(config)#! Renumber ACL 110, from line 10... increment in steps of 10
LAB_RTR(config)#ip access-list resequence 110 10 10
LAB_RTR(config)#end
LAB_RTR#
LAB_RTR#sh access-list 110
Extended IP access list 110
10 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
20 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
30 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
40 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
50 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
60 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
70 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
80 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
90 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
100 permit udp any any
110 permit ip any any
LAB_RTR#
Original way to change Cisco IOS ACLs
Originally, the safest way to change your ACL was by removing it from the interfaces in question (this prevented problems if you were changing the ACL via the same interface it was applied to).
Use this technique if your IOS doesn’t support IP access-list line numbering:
interface GigabitEthernet0/1.1
no ip access-group 110 in
!
interface GigabitEthernet0/1.2
no ip access-group 110 in
Now you can add the new ACL lines, but do it before the other permit any entries…
! Reset the ACL
no access-list 110
!
access-list 110 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
access-list 110 permit ip host 192.168.2.44 192.168.1.0 0.0.0.255
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.18
access-list 110 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
!! New ACL lines before the deny statement
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.120
access-list 110 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
access-list 110 permit ip 192.168.2.0 0.0.0.255 host 192.168.1.222
access-list 110 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
!! Deny statement
access-list 110 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 110 permit udp any any
access-list 110 permit ip any any
Finally, reapply the ACL to the switch…
interface GigabitEthernet0/1.1
ip access-group 110 in
!
interface GigabitEthernet0/1.2
ip access-group 110 in
ACL Reorganization
You should really consider using two different ACLs for Gigabit0/1.1 and GigabitEthernet0/1.2… this is a guess at what you’re trying to do, but it’s unclear that I’m interpreting things correctly…
access-list 111 permit ip 192.168.1.0 0.0.0.255 host 192.168.2.44
access-list 111 permit ip host 192.168.1.18 192.168.2.0 0.0.0.255
access-list 111 permit ip host 192.168.1.120 192.168.2.0 0.0.0.255
access-list 111 permit ip host 192.168.1.222 192.168.2.0 0.0.0.255
access-list 111 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 111 permit udp any any
access-list 111 permit ip any any
!
interface GigabitEthernet0/1.1
no ip access-group 110 in
ip access-group 111 in
!
interface GigabitEthernet0/1.2
no ip access-group 110 in
06 Dec 2011 — Lab-Rat
One of the things that took me a while to get was how to edit an ACL after I had configured it. I used to just copy/paste the ACL from the running config into notepad, make my edits, then delete it out of the router, then paste it back in. Sometimes that’s still the fastest way if you have lots of changes- but for the little stuff knowing how to edit and resequence is helpful. Here’s a quick guide:
Create a Simple Standard Access List:
Router(config)#access-list 10 permit host 192.168.1.2
Router(config)#access-list 10 deny any log
Router(config)#exit
Verify the Access List:
Router#show access-lists
Standard IP access list 10
10 permit 192.168.1.2
20 deny any log
Add a Line in Between Existing Entries:
To insert a line in between entries, you just need to find a number in between, then add the line starting with that number. So if we have lines 10 and 20, we can use 15 (or 11, or 17, you get the idea) and just add it directly.
Router(config)#ip access-list standard 10
Router(config-std-nacl)#15 permit host 192.168.1.5
Router(config-std-nacl)#do show access-lists
Standard IP access list 10
10 permit 192.168.1.2
15 permit 192.168.1.5
20 deny any log
Delete an Existing Entry:
Killing a line is easy, just put “no” in front of the line number.
Router(config)#ip access-list standard 10
Router(config-std-nacl)#no 15
Router(config-std-nacl)#do show access-lists
Standard IP access list 10
10 permit 192.168.1.2
20 deny any log
Renumber an Access List:
If you happen to have a list with many edits, you may actually run out of room to insert additional entries. If you do, just renumber the list. You specify the access list number, starting number, and increment. Here’s how that works:
Router#show access-lists
Standard IP access list 10
10 permit 192.168.1.2
15 permit 192.168.1.5
20 deny any log
Router(config)#ip access-list resequence 10 100 10
Router(config)#do show access-list
Standard IP access list 10
100 permit 192.168.1.2
110 permit 192.168.1.5
120 deny any log
Additional Reading:
Cisco Command Reference
Read this article in English
Рассмотрим создание и использование списков доступа (access lists) на примере схемы подключения малого офиса к сети Интернет с помощью маршрутизатора Cisco 881. Команды для настройки маршрутизаторов других серий (1841, 2800, 3825…) или коммутаторов 3 уровня (серии 3500, 4800…) будут аналогичными. Различия могут быть лишь в настройках интерфейсов.
В распоряжении имеем:
- несколько компьютеров и серверов в локальной сети офиса
- маршрутизатор Cisco 881
- коммутатор (используется для организации локальной сети офиса, без дополнительных настроек)
Задача: ограничить соединения, проходящие через маршрутизатор.
Списки доступа (access lists) сами по себе не являются какими-то правилами, ограничивающими доступ. Эти строки лишь указывают определенный трафик. Эффект от них появляется тогда, когда в настройках определенной функции маршрутизатора указывается ссылка на соответствующий список доступа.
Логика устройства такова, что сначала мы показываем маршрутизатору трафик, который нам интересен, а затем указываем что маршрутизатор должен с ним сделать. Например, в одном случае список доступа будет указывать адрес, с которого возможен удаленный доступ к маршрутизатору по протоколу SSH, а в другом будет указывать маршрут, который будет распространен с помощью протокола динамической маршрутизации.
Ограничение удаленного доступа к маршрутизатору
Пример access list, который используется для ограничения удаленного доступа к консоли маршрутизатора только с определенных ip адресов. В нашем случае – адрес рабочей станции администратора.
Создаем список доступа ACL_REMOTE_ACCESS
R-DELTACONFIG(config)#
ip access-list standard ACL_REMOTE_ACCESS
permit ip host 192.168.0.100
Привязываем access list для ограничения доступа к удаленному управлению маршрутизатором только с адреса 192.168.0.100
R-DELTACONFIG(config)#
line vty 0 4
access-class ACL_REMOTE_ACCESS in
Важно!
Будьте осторожны и внимательно все проверьте перед применением. Ошибку можно будет исправить только подключившись консольным кабелем или сбросив настройки маршрутизатора до заводских.
Ограничение доступа в Интернет
Для ограничения доступа из локальной сети офиса в Интернет необходим соответствующий список доступа, а также привязка его к одному из интерфейсов маршрутизатора.
Допустим, что нужно ограничить выход пользователей в сеть Интернет следующим образом:
- разрешить доступ прокси серверу (http и https)
- разрешить доступ DNS серверу (TCP 53 и UDP 53)
- полный доступ администратору сети
- разрешить протокол ICMP для всех рабочих станций для работы команды Ping.
Создаем следующий список доступа ACL_INSIDE_IN и последовательно вводим правила доступа:
R-DELTACONFIG(config)#
ip access-list extended ACL_INSIDE_IN
доступ DNS сервера в Интернет
permit udp host 192.168.0.201 any eq 53
permit tcp host 192.168.0.201 any eq 53
доступ Прокси сервера в Интернет
permit tcp host 192.168.0.202 any eq 80
permit tcp host 192.168.0.202 any eq 443
полный доступ администратора
permit ip host 192.168.0.100 any
разрешение Ping для всей локальной сети
permit icmp 192.168.0.0 0.0.0.255 any
запрет иных подключений
deny ip any any log
Важно!
Обратите внимание на то, как записана строчка правила для протокола ICMP (Ping). В списках доступа на маршрутизаторах Cisco маска подсети пишется в обратном виде: не 255.255.255.0, а 0.0.0.255
После привязываем список доступа ко внутреннему интерфейсу Vlan 1 в направлении «внутрь маршрутизатора» (параметр in). Собственно, направление привязки всегда считается относительно устройства Cisco. Для удобства интерфейс и направление трафика указано в названии самого списка доступа: ACL_INSIDE_IN — фильтр трафика, входящего во внутренний интерфейс.
R-DELTACONFIG(config)#
interface Vlan 1
ip access-group ACL_INSIDE_IN in
С этого момента доступ наружу будет осуществляться в соответствии с примененным access list при условии, что корректно настроена трансляция адресов (NAT). Как это делается описано в статье про настройку доступа в интернет с помощью маршрутизатора Cisco.
Проверка работы access list
Проверить работу списка доступа можно посмотрев статистику срабатываний правил. После привязки списка доступа ACL_INSIDE_IN к интерфейсу Vlan 1 запустите Ping с любой из рабочих станций сети до любого адреса в Интернет (например до www.yandex.ru), а затем выполните из привилегированного режима (знак # рядом с названием устройства) команду show access-lists. Результат должен показывать количество срабатываний каждой из строк списка доступа:
R-DELTACONFIG#sh access-lists
Extended IP access list ACL_INSIDE_IN
…
60 permit icmp any any (4 estimate matches)
70 deny ip any any log
Важные аспекты использования списков доступа (access list)
- Список доступа состоит из строк – правил, показывающих определенный трафик
- Список доступа, привязанный к интерфейсу, ограничивает проходящие через этот интерфейс пакеты.
- Список доступа может быть привязан к интерфейсу в одном из направлений: входящем или исходящем.
- В списках доступа может быть указан или только источник соединения (standard, пример ограничения доступа по SSH) или источник и назначение соединения(extended, пример ограничения доступа в Интернет).
- Не может быть привязано более одного списка доступа к одному интерфейсу в одном направлении. Все необходимые правила должны быть указаны только в одном привязанном списке доступа.
Ограничение доступа из сети Интернет
Создаем список доступа ACL_OUTSIDE_IN для внешнего интерфейса. В нем указываем лишь то, что внешний интерфейс должен отвечать на ping, а все остальные запросы отклонять.
R-DELTACONFIG(config)#
ip access-list extended ACL_OUTSIDE_IN
permit icmp any interface //разрешение Ping
deny ip any any log //запрет иных подключений
Привязываем список доступа ко внешнему интерфейсу.
R-DELTACONFIG(config)#
interface FastEthernet 4
ip access-group ACL_OUTSIDE_IN in
Важно!
Все новые правила, которые потребуются для доступа изнутри или снаружи, следует добавлять в соответствующие списки доступа ДО строчки
deny ip any any log
Если какая-то строчка с разрешением окажется в списке после запрещающей, то она не будет хоть как-то влиять на трафик, так как маршрутизатор обрабатывает строки access list последовательно до первого совпадения.
Для изменения access list удобно зайти в сам список доступа, добавить все нужные разрешения, а после этого удалить последнюю строку (deny ip any any log) и тут же ее добавить. Выполняя это нехитрое правило запрещающая строка всегда будет в самом конце списка, а все правила будут идти в порядке добавления снизу вверх. Для наглядности разрешим доступ к маршрутизатору извне по протоколу http (TCP порт 80)
R-DELTACONFIG(config)#
ip access-list extended ACL_OUTSIDE_IN
permit tcp any interface eq 80
no deny ip any any log
deny ip any any log
Разрешение ответного трафика
После привязки списка доступа ACL_OUTSIDE_IN пропадает весь доступ из локальной сети ко всем ресурсам по любым протоколам кроме Ping. Это происходит из-за того, что фильтрующие трафик правила применяются и на внутреннем (ACL_INSIDE_IN) и на внешнем (ACL_OUTSIDE_IN) интерфейсах.
Для того, чтобы проходили все обратные пакеты на запросы из локальной сети указываем протоколы для функции Inspect.
R-DELTACONFIG(config)#
ip inspect name Internet http
ip inspect name Internet https
ip inspect name Internet dns
ip inspect name Internet icmp
Привязываем правило инспектирования ко внешнему интерфейсу.
R-DELTACONFIG(config)#
interface FastEthernet 4
ip inspect Internet out
Список разрешенных для инспекции служб можно расширить в будущем.
Надеюсь, что статья поможет Вам лучше понять принцип работы списков доступа. К сожалению эту достаточно простую тему очень сложно описать простым языком. Если у Вас возникли вопросы или какой-то момент остался неясным, напишите мне на адрес smogdelta@gmail.com или оставьте свой вопрос в комментариях.
Важно!
Не забудьте сохранить конфигурацию на всех устройствах командой write или copy run start. Иначе после перезагрузки все изменения будут потеряны.
R-DELTACONFIG-1#write
Building configuration...
[OK]
Перейти к оглавлению
Содержание
- 1 Что такое Access Control List?
- 2 Какие бывают ACL?
- 2.1 Стандартные списки ACL
- 2.2 Расширенные списки ACL
- 2.3 Синтаксис расширенных списков ACL.
- 2.4 Примеры расширенных ACL
- 2.4.1 Настраиваем роутер.
- 2.5 Приступим к настройке ACL-ов.
- 2.5.1 Запрещаем FTP трафик.
Пришло время поговорить об ACL подробней. Как взрослые люди, начнём делать серьёзные вещи. Да и я, наконец, собрался с мыслями и поковырял эту тему.
В данной статье мы рассмотрим простые типовые конфигурации для списков управления доступом на базе Cisco ACL, которые фильтруют IP-пакеты в зависимости от следующих данных:
- адрес источника (source address);
- адрес назначения (destination address);
- тип пакета (протокол верхнего уровня);
Маршрутизатор проверяет каждый пакет и на основании вышеперечисленных критериев, указанных в ACL определяет, что нужно сделать с пакетом, пропустить или отбросить.
Что такое Access Control List?
IP ACL – последовательный набор правил разрешающих или запрещающих прохождение пакета. Маршрутизатор последовательно проверяет каждый пакет на соответствие правилам. После первого же совпадения принимается решение и дальше правила не обрабатываются.
Если ни одно из правил не подошло, то пакет отбрасывается из-за неявного последнего правила deny all.
Можно выделить следующие виды списков контроля доступа:
- стандартные ACL;
- расширенные ACL (об этом речь пойдёт ниже);
- динамические ACL (ключ и замок);
- именованные IP-списки ACL;
- рефлексивные ACL;
- синхронизируемые списки ACL, использующие временные диапазоны;
- прокси-аутентификации;
- Turbo ACL;
- контекстно-ориентированные ACL;
- откомментированные записи IP ACL;
- распределённые синхронизируемые ACL;
Всему своё время, а мы рассмотрим самое распространённое – стандартные и расширенные списки контроля доступа.
Стандартные списки ACL
Формат синтаксиса команды стандартного ACL выглядит так:
# access-list number {permit|deny} {host|source source-wildcard|any}
- permit – пропускаем пакет.
- deny – отбрасываем пакет.
- host – конкретный IP-адрес узла
- source source-wildcard – IP и его обратная маска. Надо несколько слов сказать про обратную маску. Здесь применяется инвертированная маска сети, которая показывает, какие биты изменяются.
- any – любой хост.
Стандартные ACL управляют трафиком, сравнивая адрес источника пакетов с адресами, заданными в списке.
Ну и чтобы лучше понять параметры, приведу несколько примеров:
- Задача: разрешаем прохождение трафика от узла 10.0.0.10
Правило:
# access-list 1 permit host 10.0.0.10
равнозначно
# access-list 1 permit 10.0.0.10 0.0.0.0
- Задача: запрещаем прохождение пакетов из подсети 10.0.1.0/24
Правило:
# access-list 2 deny 10.0.1.0 0.0.0.255
- Задача: разрешить доступ только админу (10.0.0.9), остальным запретить.
Правило:
# access-list 3 permit 10.0.0.9 0.0.0.0
# access-list 3 deny any
И здесь очень важно написать правила именно в таком порядке. Я не зря сказал, что правила проверяются последовательно, до первого совпадения.
Здесь, если пакет принадлежит IP 10.0.0.9, то первая строчка соответствует и пакет пропустится.
А если написать правила в обратном порядке, то первой же строкой будет deny any, что отбросит любой пакет (даже 10.0.0.9) и дальше правила применяься не будут. Поэтому нужно быть очень внимательным в этом.
Расширенные списки ACL
Расширенные списки управляют трафиком, сравнивая адреса источника и назначения пакетов с адресами, заданными в списке. Это более тонкая фильтрация трафика по следующим критериям:
- протокол;
- номер порта;
- значение DSCP;
- приоритет;
- состояние бита SYN;
Синтаксис расширенных списков ACL.
# access-list number [dynamic dynamic-name [timeout minutes]] {deny|permit} {protocol|protocol-keyword} {source source-wildcard|any} [source-port] {destination destination-wildcard|any} [precedence precedence] [tos tos] [log | log-input] [time-range time-range-name] [fragments]
Уже представляю ваши глаза “О_О”. Да, вот такой расширенный список, действительно, параметров немного больше.
Примеры расширенных ACL
Я составил типовую конфигурацию в Cisco Packet Tracer, две подсети 10.0.1.0/24 и 192.168.1.0/24.
Узлы подсети 10.0.1.0/24 имеют шлюз по умолчанию 10.0.1.1, а 192.168.1.0/24 соответственно 192.168.1.1.
Настраиваем роутер.
router> en
router# conf t
router(config)# int fast 0/0
router(config-if)# ip address 10.0.1.1 255.255.255.0
router(config-if)# no shut
Аналогично настраиваем и второй инерфейс (fast 0/1), только в качестве адреса указываем не 10.0.1.1, а 192.168.1.1.
Приступим к настройке ACL-ов.
Сначала убедимся, что сеть коммутируется и все узлы доступны друг для друга:
PC>ping 10.0.1.3
Pinging 10.0.1.3 with 32 bytes of data:
Reply from 10.0.1.3: bytes=32 time=125ms TTL=127
Reply from 10.0.1.3: bytes=32 time=107ms TTL=127
Reply from 10.0.1.3: bytes=32 time=125ms TTL=127
Reply from 10.0.1.3: bytes=32 time=109ms TTL=127
Ping statistics for 10.0.1.3:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 107ms, Maximum = 125ms, Average = 116ms
Запрещаем FTP трафик.
Задача: разрешить доступ к FTP для узла 192.168.1.2 и запретить для узла 192.168.1.3.
На сервере 10.0.1.3 поднят FTP сервис (дефолтные cisco:cisco). Убедимся, что узел доступен и FTP работает.
PC>ipconfig
IP Address………………….: 192.168.1.2
Subnet Mask…………………: 255.255.255.0
Default Gateway……………..: 192.168.1.1
PC>ftp 10.0.1.3
Trying to connect…10.0.1.3
Connected to 10.0.1.3
220- Welcome to PT Ftp server
Username:cisco
331- Username ok, need password
Password:
230- Logged in
(passive mode On)
ftp>dir
Listing /ftp directory from 10.0.1.3:
0 : c1841-advipservicesk9-mz.124-15.T1.bin 33591768
1 : c1841-ipbase-mz.123-14.T7.bin 13832032
2 : c1841-ipbasek9-mz.124-12.bin 16599160
3 : c2600-advipservicesk9-mz.124-15.T1.bin 33591768
4 : c2600-i-mz.122-28.bin 5571584
5 : c2600-ipbasek9-mz.124-8.bin 13169700
6 : c2800nm-advipservicesk9-mz.124-15.T1.bin 50938004
7 : c2800nm-ipbase-mz.123-14.T7.bin 5571584
8 : c2800nm-ipbasek9-mz.124-8.bin 15522644
9 : c2950-i6q4l2-mz.121-22.EA4.bin 3058048
10 : c2950-i6q4l2-mz.121-22.EA8.bin 3117390
11 : c2960-lanbase-mz.122-25.FX.bin 4414921
12 : c2960-lanbase-mz.122-25.SEE1.bin 4670455
13 : c3560-advipservicesk9-mz.122-37.SE1.bin 8662192
14 : pt1000-i-mz.122-28.bin 5571584
15 : pt3000-i6q4l2-mz.121-22.EA4.bin 3117390
ftp>quit
Packet Tracer PC Command Line 1.0
PC>221- Service closing control connection.
Команды и настройка FTP-сервера есть на нашем сайте тут.
Убедимся, что доступ есть как с узла 192.168.1.2, так и с 192.168.1.3. У меня всё по плану. Если у вас вдруг нет доступа, убедитесь, что каждому узлу назначен IP и маска, а так же прописан шлюз по-умолчанию. И не перепутали ли вы интерфейсы?
Идём дальше.
Router(config)#ip access-list extended 101
Router(config-ext-nacl)#permit tcp 192.168.1.2 0.0.0.0 10.0.1.3 0.0.0.0 eq 21
Router(config-ext-nacl)#permit tcp 192.168.1.2 0.0.0.0 10.0.1.3 0.0.0.0 eq 20
Router(config-ext-nacl)#deny tcp 192.168.1.3 0.0.0.0 10.0.1.3 0.0.0.0 eq 21
Router(config-ext-nacl)#deny tcp 192.168.1.3 0.0.0.0 10.0.1.3 0.0.0.0 eq 20
Здесь мы видми по 2 разрешающих и по 2 запрещающих правила для указанных направлений и портов 21 и 20. Это служба FTP, передача команд и данных.
А теперь применяем наш список к интерфейсу со стороны сети 192.168.1.0/24 на вход (потому что трафик ВХОДИТ на роутер со стороны интерфейса 192.168.1.1):
Router(config)#int fa 0/1
Router(config-if)#ip access-group 101 in
Как видите, мы просто применили наше правило с номером 101.
Проверяем коннект. С узла 192.168.1.3 видим следующее:
PC>ftp 10.0.1.3
Trying to connect…10.0.1.3
и всё.
А с узла 192.168.1.2 по прежнему коннект!
Содержание
- 1 IP списки доступа Cisco IOS
- 1.1 Стандартный Access-list
- 1.2 Расширенный Access-list
- 1.3 Применение к интерфейсу
- 1.4 Применение к линиям доступа telnet
- 1.5 Именованный расширенный Access-list
- 1.6 Расширенные параметры ACE
- 1.7 Классификация трафика с помощью ACL
- 1.8 Отладка IP ACL
- 1.9 Vlan-ACL (VACL)
- 1.10 Порядок обработки пакетов
- 1.11 Подробная инструкция по работе с IP ACL от cisco
- 1.12 Примеры типичных применений IP ACL
IP списки доступа Cisco IOS
Access-lists, Access-control-lists (ACL) – списки контроля доступа.
Существует несколько разновидностей аксесс-листов, применяемых на маршрутизаторах и коммутаторах Cisco. Аксесс-листы используются для фильтрации трафика или для определения классов трафика при применении политик. Список доступа представляет собой набор строк вида условие-действие. Строка аксесс-листа называется access-control-entry (ACE).
Условием может быть соответствие пакета определенному протоколу или набору параметров. Действием может быть разрешение пакета (permit), либо запрещение (deny). Для списков доступа справедливы следующие правила:
- Созданный список доступа не действует, пока он не применен к конкретному интерфейсу.
- Список доступа применяется на интерфейсе в конкретном направлении – для исходящего, либо входящего трафика (inbound/outbound).
- К интерфейсу можно применить только по одному аксесс-листу на протокол (ip), на направление (in/out).
- Список доступа проверяется строка за строкой до первого совпадения. Оставшиеся строки игнорируются.
- В конце любого IP аксесс-листа подразумевается запрещающее правило (implicit deny). Пакет, не попавший ни под одно условие в списке, отбрасывается, в соответствии с правилом implicit deny.
- Рекомендуется более специфические правила указывать в начале аксесс-листа, а более общие – в конце.
- Новые строки по умолчанию дописываются в конец списка.
- Отдельную строку можно удалить из именованного аксесс-листа, другие ACL удаляются лишь целиком.
- Список доступа должен иметь по крайней мере один permit, иначе он будет блокировать весь трафик.
- Интерфейс, которому назначен несуществующий аксесс-лист не фильтрует трафик.
- IP Extended Access-lists применяются как можно ближе к источнику трафика.
По способу создания списки доступа делятся на стандартные, расширенные, и именованные. Удобнее всего работать с именованными.
Стандартный Access-list
Фильтрует только по ip адресу источника. Должен иметь номер в диапазоне 1-99. Пример:
access-list 10 deny host 172.16.30.2 – запретить ip источника access-list 10 permit any - разрешить всё
Расширенный Access-list
Фильтрует по адресам источника и получателя, по протоколам 3, 4 уровня. Должен иметь номер в диапазоне 100-199. Пример:
acсess-list 110 deny tcp any host 172.16.30.2 eq 22 - запретить tcp от всех на хост с портом 22 access-list 110 deny ip 192.168.160.0 0.0.31.255 any - запретить ip от сети по шаблону на всех access-list 110 permit ip any any - разрешить всё
Применение к интерфейсу
conf t - переход в режим конфигурирования int fa 0/0 - переход к интерфейсу FastEthernet0/0 ip access-group 110 in - применить ACL 110 на вход ip access-group 120 out - применить ACL 120 на выход
Применение к линиям доступа telnet
conf t - переход в режим конфигурирования line vty 0 4 - переход к линиям vty с 0 по 4 access-class 10 in - применить ACL 10 на вход
Именованный расширенный Access-list
Фильтрует по адресам источника и получателя, по протоколам 3, 4 уровня. Должен иметь имя. Возможно удалять отдельные строки. Пример:
ip access-list extended INET - создать список с именем INET deny tcp any host 172.16.30.2 eq 22 - запретить tcp от всех на хост с портом 22 deny ip 192.168.160.0 0.0.31.255 any - запретить ip от сети по шаблону на всех permit ip any any - разрешить всё
Строки доступа нумеруются с шагом 10 по-умолчанию. Можно перенумеровать аксесс-лист с другим шагом. Можно добавить строку пронумеровав – она попадет в указанное место, по нумерации.
Просмотр расширенного аксесс-листа:
router# sh access-list INET Extended IP access list INET 10 deny tcp any host 172.16.30.2 eq 22 (150 matches) 20 deny ip 192.168.160.0 0.0.31.255 any (4 matches) 30 permit ip any any (1556 matches)
Как видим — строки пронумерованы с шагом 10. Можно вставить новую строку в произвольное место листа, используя номер:
router(conf)# ip access-list extended INET router(config-ext-nacl)# 5 permit ip host 10.10.10.10 any router(config-ext-nacl)# 223 deny ip host 1.1.1.1 any router(config-ext-nacl)# end router# sh access-list INET Extended IP access list INET 5 permit ip host 10.10.10.10 any 10 deny tcp any host 172.16.30.2 eq 22 (150 matches) 20 deny ip 192.168.160.0 0.0.31.255 any (4 matches) 30 permit ip any any (1556 matches) 223 deny ip host 1.1.1.1 any
Удалить отдельную строчку из листа можно по номеру, или по полному указанию строки с префиксом «no».
Например так:
router(conf)# ip access-list extended INET router(config-ext-nacl)# no permit ip host 10.10.10.10 any
Или так:
router(config-ext-nacl)# no 223
Полностью удалить список доступа можно указав соответствующую команду и «no»:
router(conf)# no ip access-list extended INET
Расширенные параметры ACE
log
log-input
established
time-range
reflexive
permit icmp vs. permit ip
Deny ACEs that check Layer 4 information never match a fragment unless the fragment contains Layer 4 information.
Классификация трафика с помощью ACL
Отладка IP ACL
Vlan-ACL (VACL)
VLAN map применяется для всех отбриджованных пакетов. Router ACL только для маршрутизированных.
Если
1. VLAN map for input VLAN10
2. Input router ACL / int VLAN10
3. routing VLAN10 to VLAN 20
4. Output router ACL / int VLAN20
5. VLAN map for output VLAN20
ip access-list extended WIFIHOSTEL
permit ip 10.12.0.0 0.0.255.255 host 212.192.64.2
permit ip host 212.192.64.2 10.12.0.0 0.0.255.255
deny ip any any
!
vlan access-map WIFIHOSTEL 10
match ip address WIFIHOSTEL
action forward
!
vlan filter WIFIHOSTEL vlan-list 534
Порядок обработки пакетов
Подробная инструкция по работе с IP ACL от cisco
http://www.cisco.com/en/US/products/sw/secursw/ps1018/products_tech_note09186a00800a5b9a.shtml
Примеры типичных применений IP ACL
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_configuration_example09186a0080100548.shtml