This link options section covers options related to the connection between
the local and the remote host.
| --bind keywords | |
|
Bind to local address and port. This is the default unless any of If the optional |
|
| --float |
Allow remote peer to change its IP address and/or port number, such as Essentially, |
| --fragment args | |
|
Valid syntax: fragment max fragment max mtu Enable internal datagram fragmentation so that no UDP datagrams are sent If the If the The
See the It should also be noted that this option is not meant to replace UDP Having said that, there are circumstances where using OpenVPN’s internal |
|
| --keepalive args | |
|
A helper directive designed to simplify the expression of Valid syntax: keepalive interval timeout Send ping once every This option can be used on both client and server side, but it is enough The For example, if mode server:
ping 10 # Argument: interval
ping-restart 120 # Argument: timeout*2
push "ping 10" # Argument: interval
push "ping-restart 60" # Argument: timeout
else
ping 10 # Argument: interval
ping-restart 60 # Argument: timeout
|
|
| --link-mtu n |
DEPRECATED Sets an upper bound on the size of UDP packets which are sent between Due to variable header size of IP header (20 bytes for IPv4 and 40 bytes |
| --local host | Local host name or IP address for bind. If specified, OpenVPN will bind to this address only. If unspecified, OpenVPN will bind to all interfaces. |
| --lport port | Set local TCP/UDP port number or name. Cannot be used together with--nobind option. |
| --mark value | Mark encrypted packets being sent with value. The mark value can bematched in policy routing and packetfilter rules. This option is only supported in Linux and does nothing on other operating systems. |
| --mode m | Set OpenVPN major mode. By default, OpenVPN runs in point-to-point mode ( p2p). OpenVPN 2.0 introduces a new mode (server) whichimplements a multi-client server capability. |
| --mssfix args |
Valid syntax: mssfix max [mtu] mssfix max [fixed] mssfix Announce to TCP sessions running over the tunnel that they should limit If the If the If the if The
The usual symptom of such a breakdown is an OpenVPN connection which If Therefore, one could lower the maximum UDP packet size to 1300 (a good --tun-mtu 1500 --fragment 1300 --mssfix If the |
| --mtu-disc type | |
|
Should we do Path MTU discovery on TCP/UDP channel? Only supported on Valid types:
|
|
| --mtu-test | To empirically measure MTU on connection startup, add the --mtu-testoption to your configuration. OpenVPN will send ping packets of various sizes to the remote peer and measure the largest packets which were successfully received. The --mtu-test process normally takes about 3minutes to complete. |
| --nobind | Do not bind to local address and port. The IP stack will allocate a dynamic port for returning packets. Since the value of the dynamic port could not be known in advance by a peer, this option is only suitable for peers which will be initiating connections by using the --remoteoption. |
| --passtos | Set the TOS field of the tunnel packet to what the payload’s TOS is. |
| --ping n |
Ping remote over the TCP/UDP control channel if no packets have been This option has two intended uses:
When using OpenVPN in server mode see also |
| --ping-exit n |
Causes OpenVPN to exit after For example, openvpn [options...] --inactive 3600 --ping 10 --ping-exit 60 when used on both peers will cause OpenVPN to exit within 60 seconds if |
| --ping-restart n | |
|
Similar to This option is useful in cases where the remote peer has a dynamic IP If the peer cannot be reached, a restart will be triggered, causing the In server mode, In client mode, the See the signals section below for more information on Note that the behavior of Also note that |
|
| --ping-timer-rem | |
Run the --ping-exit / --ping-restart timer only if we have aremote address. Use this option if you are starting the daemon in listen mode (i.e. without an explicit --remote peer), and you don’t want tostart clocking timeouts until a remote peer connects. |
|
| --proto p |
Use protocol The default protocol is For UDP operation, For TCP operation, one peer must use OpenVPN is designed to operate optimally over UDP, but TCP capability is This article outlines some of problems with tunneling IP over TCP: There are certain cases, however, where using TCP may be advantageous |
| --port port | TCP/UDP port number or port name for both local and remote (sets both--lport and --rport options to given port). The current defaultof 1194 represents the official IANA port number assignment for OpenVPN and has been used since version 2.0-beta17. Previous versions used port 5000 as the default. |
| --rport port | Set TCP/UDP port number or name used by the --remote option. Theport can also be set directly using the --remote option. |
| --replay-window args | |
|
Modify the replay protection sliding-window size and time window. Valid syntaxes: replay-window n replay-window n t Use a replay protection sliding-window of size By default This option is only relevant in UDP mode, i.e. when either When OpenVPN tunnels IP packets over UDP, there is the possibility that
If you are using a network link with a large pipeline (meaning that the If you run OpenVPN at There is some controversy on the appropriate method of handling packet Namely, to what extent should the security layer protect the The IPSec and OpenVPN approach is to allow packet reordering within a OpenVPN adds to the IPSec model by limiting the window size in time as OpenVPN also adds TCP transport as an option (not offered by IPSec) in In this sense, it could be argued that TCP tunnel transport is preferred So I would make the statement that one should never tunnel a non-IP |
|
| --replay-persist file | |
|
Persist replay-protection state across sessions using This option will keep a disk copy of the current replay protection state This option only makes sense when replay protection is enabled (the |
|
| --session-timeout n | |
|
Raises This option can also be specified in a client instance config file |
|
| --socket-flags flags | |
|
Apply the given flags to the OpenVPN transport socket. Currently, only The This option is pushable from server to client, and should be used on |
|
| --tcp-nodelay |
This macro sets the The macro expands as follows: if mode server:
socket-flags TCP_NODELAY
push "socket-flags TCP_NODELAY"
|
| --max-packet-size size | |
|
This option will instruct OpenVPN to try to limit the maximum on-write packet OpenVPN will try to keep its control channel messages below this size but In terms of mssfix size mtu If you need to set In general the default size of 1250 should work almost universally apart |
Introduction
For some time now I’ve systematically used an OpenVPN-connection whenever I was using an untrusted WLAN (at hotels, restaurants, etc.). And so should you: Whether or not a hotel’s WLAN is WPA-encrypted has no influence on its trustworthyness. After all, are you really sure that among all of the connected users there’s not a single bored teen that’s having fun sniffing your passwords or doing a man-in-the-middle-attack through a few taps on his smartphone? (Yes, it’s that easy!)
And here’s the problem: You’ve set up your own OpenVPN-Server following one of the many detailed Howto guides available online and now that you’re actually abroad your VPN is failing miserably: The VPN-client connects just fine, but even the simplest webbrowsing has weird issues or doesn’t work at all. The most frequent cause (besides an overly restrictive firewall) is a problematic MTU-setting.
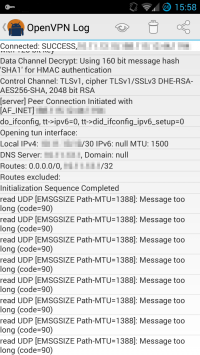
Here’s what it may look like in the logs:
If you just want a quick’n’dirty solution that works perfectly fine (at least in my limited experience), simply change your OpenVPN’s transport protocol from the default UDP to TCP. (i.e. change «proto udp» to «proto tcp» on client and server. Better yet, have two server instances running, one for UDP and one for TCP.)
For various technical reasons (page referenced by the official manual!), such a setup is not recommended (TCP-over-TCP, reduced bandwidth), but in practice it works remarkably well “due to all kinds of magic related to mssfix” (as it’s “explained” on the OpenVPN-bugtracker, issue 375)
MTU you say?
MTU stands for Maximum Transmission Unit and represents the maximum size an IP packet can have before it must be fragmented, i.e. split up. And IP-fragmentation, even though it’s part of the IP specifications, is a feature you’ll want to avoid whenever possible. (And that’s completely independent of your using OpenVPN or not. It applies generally to any kind of IP-based traffic.) Fragmentation entails security issues, performance penalities and transmission issues. It’s obvious that on the path a given IP packet travels to its destination, it’s the smallest encountered MTU that determines whether the packet has to be fragmented. This is the so-called Path-MTU. (The expected value is 1500; this corresponds to the MTU of regular ethernet or wifi connections. Problems arise when Path-MTU is less than 1500.)
In order to detect Path-MTU most IP packets are actually transmitted with the «Don’t Fragment»-bit set. This leaves an intermediate router with an MTU less than the packet’s length no choice but to drop it. It notifies the sender by means of a special ICMP message (Destination unreachable: fragmentation needed and DF set). The sender can then progressively scale down the size of the packets it emits. (This reduces throughput, since the headers are of a fixed size and the actual payload decreases.) In essence, this process is known as Path-MTU Discovery (PMTUD).
Unfortunately, PMTUD often fails due to a misconfigured firewall dropping those precious ICMP messages. Another reason is the possibly suboptimal handling of PMTUD by OpenVPN itself. But I’m not entirely sure of that. (See this bug report or read up about the Linux-only —mtu-disc setting. Feel free to comment.)
And that’s when the OpenVPN’s various MTU-related configuration directives come into play. I won’t go in all the gory details (I’m no networking expert either…), but I’ll try my best to sum up the sometimes contradicting or incorrect information I could find.
All of the following is strictly for the case you’re using the recommended UDP as transport protocol. (link-mtu and tun-mtu are also valid for TCP as transport protocol, but normally they’re not needed in this case.)
My objective is to derive a setup that’s (hopefully) compatible with a wide range of clients (at least Linux, Windows and the two major Android clients).
On to the first step:
RTFM
Actually I read the fine manual for you and here’s the summary:
—link-mtu n
Sets an upper bound on the size of UDP packets which are sent between OpenVPN peers. It’s best not to set this parameter unless you know what you’re doing.
—tun-mtu n
Take the TUN device MTU to be n and derive the link MTU from it (default=1500). In most cases, you will probably want to leave this parameter set to its default value.
The MTU (Maximum Transmission Units) is the maximum datagram size in bytes that can be sent unfragmented over a particular network path. OpenVPN requires that packets on the control or data channels be sent unfragmented.
MTU problems often manifest themselves as connections which hang during periods of active usage. It’s best to use the
--fragmentand/or--mssfixoptions to deal with MTU sizing issues.
—fragment max
Enable internal datagram fragmentation so that no UDP datagrams are sent which are larger than max bytes.
The max parameter is interpreted in the same way as the —link-mtu parameter, i.e. the UDP packet size after encapsulation overhead has been added in, but not including the UDP header itself. […]
It should also be noted that this option is not meant to replace UDP fragmentation at the IP stack level. It is only meant as a last resort when path MTU discovery is broken. Using this option is less efficient than fixing path MTU discovery for your IP link and using native IP fragmentation instead. Having said that, there are circumstances where using OpenVPN’s internal fragmentation capability may be your only option, such as tunneling a UDP multicast stream which requires fragmentation.
—mssfix max
Announce to TCP sessions running over the tunnel that they should limit their send packet sizes such that after OpenVPN has encapsulated them, the resulting UDP packet size that OpenVPN sends to its peer will not exceed max bytes. The default value is 1450.
The max parameter is interpreted in the same way as the
--link-mtu parameter, i.e. the UDP packet size after encapsulation overhead has been added in, but not including the UDP header itself. […]
--mssfixand--fragmentcan be ideally used together, where--mssfixwill try to keep TCP from needing packet fragmentation in the first place, and if big packets come through anyhow (from protocols other than TCP),--fragmentwill internally fragment them. […] If--fragmentand--mssfixare used together,--mssfixwill take its default max parameter from the--fragmentmax option.Therefore, one could lower the maximum UDP packet size to 1300 (a good first try for solving MTU-related connection problems) with the following options:
--tun-mtu 1500 --fragment 1300 --mssfix
So, it’s not THAT complicated after all? In order to adapt to a smaller MTU, I’ll just set --tun-mtu to some smaller value, e.g. 1300?
Unfortunately, it’s not that simple. What I haven’t told you about are the various restrictions.
Caveats, restrictions, limitations, compatibility issues…
OpenVPN can’t set or modify the MTU on Windows
Quoting the official documentation:
Currently on Windows, the only way to change the TAP-Windows MTU is to go to the adapter advanced properties and do it manually. Because of this, the easiest choice is to leave the TAP-Windows MTU setting at “1500” and tell OpenVPN on both sides of the connection to use an MTU of “1500” with the config option:
tun-mtu 1500If you then need to lower the MTU because of fragmentation or router problems, use something like
fragment 1400 mssfixto lower OpenVPN’s tunnel carrier UDP packet size to “1400”.
That’s the reason why older versions of OpenVPN (before the Windows-port) simply used --link-mtu 1300, but newer ones no longer take this route… If you want the broadest possible compatibility, you’ll always manually specify --tun-mtu 1500 even if it’s a fictitious value.
Limitations of the official Android client
Ok, then I’ll set mssfix and fragment on client and server and be done with it?
Not quite.
Neither configuration directive is supported by the official OpenVPN client for Android, “OpenVPN Connect”!
fragment — The fragment directive is not supported due to the complexity it adds to the OpenVPN implementation and the fact that it is usually better to leave fragmentation up to the lower-level transport protocols. Note as well that the client does not support connecting to a server that uses the fragment directive.
mssfix — This directive will be added in a future release. Since the functionality of mssfix can be achieved on either the client or server side, specifying it on the server side will enable it even if the client doesn’t support the directive.
(Source)
Do note that the mssfix limitation is not applicable to the excellent “OpenVPN for Android” by Arne Schwabe. (I’m not sure about fragment support, but mssfix definitely works!)
Server limitations
All of the clients connecting to the same server instance must share the same tun-mtu and fragment settings.
Recommendations
Considering all of the above, I see only one possibility that comes close to a one-size-fits-all approach and that’s setting mssfix 1300 and leaving all of the other settings at their default values: tun-mtu 1500, no fragmentation. Do note that mssfix can’t be pushed to clients (or at least it fails on OpenVPN for Android). The following snippet is included in both the client and server config files:
proto udp
dev tun
tun-mtu 1500
mssfix 1300
# no fragment setting :-/Even though these settings should be compatible with a wide array of clients, they’re not perfect: only TCP-traffic (through the UDP-tunnel) is taken care of. As soon as the client device emits UDP packets that are too large (once encrypted and encapsulated), packet loss is still a possibility. This is entirely dependent of the traffic you generate. The good news is that most «stuff» is TCP-based (web browsing, e-mail, streaming audio/video, etc.), whereas UDP is mainly used for some «management protocols» such as DNS, DHCP and similar. Usually these UDP packets are rather small, hence unproblematic. It’s the exceptions that might prove problematic: realtime video applications (think Skype or Facetime), NFS, some types of online games. In these cases, there’s probably no way around enabling OpenVPN’s internal fragmentation routines and avoiding incompatible clients.
Conclusion
Getting OpenVPN right when confronted with non-standard networks can be cumbersome… At the same time it’s a very powerful tool that can be adapted to suit almost any secure tunneling needs.
Finding correct OpenVPN MTU and MSSFIX settings can really drive you batty. No really. It’s ridiculous how much trouble MTU settings can cause and how often people don’t realize that MTU is actually what’s causing the problem!
My Experience with OpenVPN MTU Problems
As many of you are aware, I run a ton of VPNs. I use a combination of OpenVPN and/or WireGuard depending on what I am doing with it. Generally I use pfSense as my firewall (although sometimes a Ubiquiti Dream Machine Pro).
Mostly, I run a VPN Between Friends and Family and I run a VPN to our new building, and all of these locations have AXIS security cameras that are recording to a combination of an onsite and remote Synology for video surveillance. This means there is a lot of UDP IP camera traffic traversing the VPN.
In the beginning with only one or two cameras I noticed that there were frame drops, but it wasn’t really enough to matter or cause a significant degradation in the video feed. But after I started to get 5, 6, or 7 cameras up I noticed things would degrade very quickly. UDP packets would get dropped like crazy, but TCP traffic would work perfectly.
So what gives?
TCP vs. UDP for OpenVPN
Before we get to fixing our OpenVPN MTU issues, let’s first take a minute to understand the difference between UDP and TCP. Trust me, this is worth understanding and it can have major impacts on your VPN’s overall performance.
TCP is an acronym for Transmission Control Protocol. UDP is an acronym for User Datagram Protocol. While we’re not going to go into all of the gory detail of differences between these protocols there are a few things that are very important to understand.
First, TCP creates a session between two devices and checks to make sure the packet was delivered. If the a reply is not received within the limits of the defined TTL (time-to-live) the data will be retransmitted. This guarantees delivery even over unstable connections.
UDP on the other hand is session-less. It simply fires a packet down the wire and hopes for the best. If the other end never receives the data nothing happens, it is simply lost.
In the case of transmitting a file such as a word document, if a some of the data doesn’t arrive, the document will be corrupted and unreadable. In the case of streaming music, you’ll just get some degraded sound quality for a second. This is why most file transfers used TCP and most streaming uses UDP.
OpenVPN Defaults to UDP for the Tunnel
Now it might come as a huge shocker to learn that OpenVPN (and most VPNs) use UDP for their tunnel! That’s crazy talk right? What do you mean my VPN can lose data? Madness I say!
Well it actually makes perfect sense. If an application needs TCP, that TCP session will be tunneled inside the OpenVPN UDP transmission. And if the application detects a packet didn’t make it… it will retransmit just like normal. The VPN doesn’t need to do it There is no reason to tunnel TCP over a TCP tunnel! In fact doing so adds lots of overhead, can cause jitter and latency problems and a lot of other undesirable behavior.
In the case of UDP, if it was going to get lost outside the tunnel it will still get lost inside the tunnel. If you’re having problems with lost packets, maybe the application should be using TCP. Or maybe you have an OpenVPN MTU problem (we’re getting there).
You should never use TCP for the OpenVPN tunnel itself unless you have a specific technical challenge to overcome and you understand the greater impacts.
Understanding MTU
MTU is an acronym for Maximum Transmission Unit. Simply put, it defines the maximum size of a packet traversing the network. Anything bigger than this number must be broken into multiple packets. The default MTU for Ethernet is 1500 bytes. For two devices to properly communicate they need to know this number. If they transmit packets larger than 1500 bytes the packets will be discarded by one of the network devices.
In the case of OpenVPN MTU settings, its important to realize that we’re tunneling data and that the VPN overhead is going to take away some of our MTU!
So here’s the problem I here all of the time: “My OpenVPN works fine for TCP traffic, but UDP traffic is very buggy and only works sometimes.” Why is this? Because TCP has many mechanisms to deal with networks and it will lower its Maximum Segment Size (MSS) and try again (retransmit). UDP being fire and forget will never know there was a problem and just keep firing those oversize packets into oblivion to be dropped by the VPN tunnel!
In my case this translated to SSH and web sessions working perfectly, but video streams and VoIP running over the tunnel would fail miserably, resulting is stuttering and choppy video and audio.
Fixing OpenVPN MTU Issues
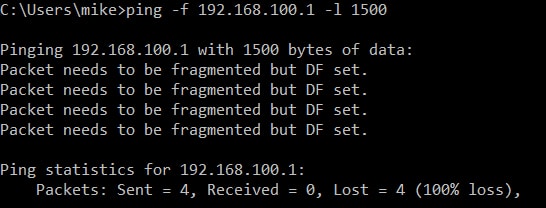
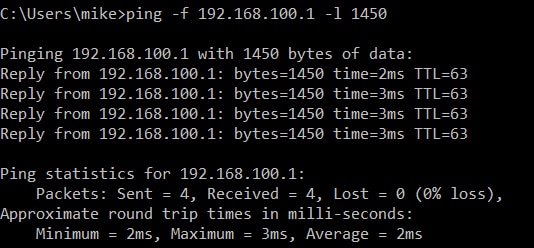
The first thing you need to do to fix your OpenVPN MTU problem is to figure out what your largest MTU actually is. You can do this using the ping command. “ping -f” tells ping not to fragment the packet under any circumstances. “ping -l” tells ping the packet size to use.
ping -f <IP of Device on other end of VPN> -l <MTU to test> ping -f 192.168.100.1 -l 1500
And you can see in our case the pings failed because they were too large to pass through our VPN tunnel. Keep trying the command over and over. Each time lower the packet size (-l) by 10 until the pings work.
You can see that in our case, we had to drop down to a 1450 byte packet to get data to cross the tunnel.
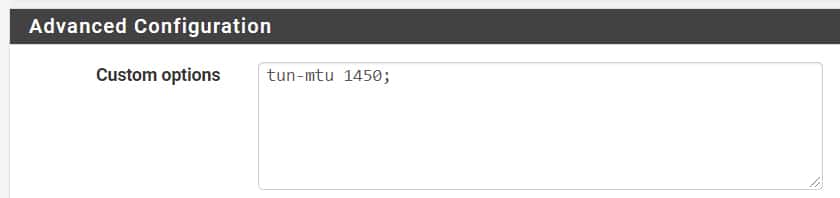
On both our client and server and server size I made the following Open VPN MTU change: –tun-mtu 1450;
You can make this change in pfSense’s OpenVPN in the Advanced Configuration portion as follows:
What about MSSFIX for OpenVPN?
A lot of people will suggest setting MSSFIX to 40 bytes smaller and also including it in your statement, as some devices don’t properly learn MTU settings. MSSFIX is a workaround used when MTU path discovery is broken for some reason.
My advice, try the tun-mtu 1450 (or whatever your tunnel needs to be set to) without MSSFIX first and see if it resolves your issue first. Only add MSSFIX if absolutely necessary. Keep it simple.
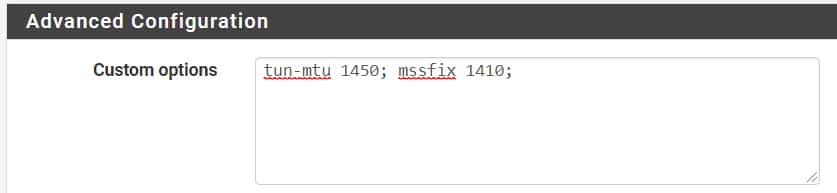
If you do need MSSFIX, you can add it as follows: –tun-mtu 1450; –mssfix 1410; or in pfSense as follows:
Finding correct Setting correct MTU for OpenVPN and MSSFIX settings can really drive you batty. No really. It’s ridiculous how much trouble MTU settings can cause and how often people don’t realize that MTU is actually what’s causing the problem!
VPN connections can be sensitive to incorrect or low MTU set within your network, or on networks between you and your server. It is important that the correct MTU is set, to ensure fast and error-free VPN performance.
Symptoms of mistaken MTU
- Incomplete page load of resources via HTTP over VPN
- Slow VPN performance
TCP vs UDP for OpenVPN
Before we get to fixing our OpenVPN MTU issues, let’s first take a minute to recognize the difference between UDP and TCP. Trust me, this is really worth appreciation and it can have major impacts on your VPN’s average performance.
TCP is an acronym for Transmission Control Protocol. UDP is an acronym for User Datagram Protocol. While we’re no longer going to go into all of the gory element of variations between these protocols there are a few matters that are very vital to understand.
First, TCP creates a session between two gadgets and tests to make certain the packet used to be delivered. If the a reply is now not obtained inside the limits of the described TTL (time-to-live) the information will be retransmitted. This ensures shipping even over unstable connections.
UDP on the different hand is session-less. It sincerely fires a packet down the wire and hopes for the best. If the different give up by no means receives the information nothing happens, it is truly lost.
In the case of transmitting a file such as a phrase document, if a some of the data doesn’t arrive, the report will be corrupted and unreadable. In the case of streaming music, you’ll simply get some degraded sound best for a second. This is why most file transfers used TCP and most streaming makes use of UDP.
Understanding MTU
MTU is an acronym for Maximum Transmission Unit. Simply put, it defines the maximum size of a packet traversing the network. Anything better than this quantity have to be damaged into more than one packets. The default MTU for Ethernet is 1500 bytes. For two gadgets to communicate they want to recognize this number. If they transmit packets large than 1500 bytes the packets will be discarded with the aid of one of the community devices.
In the case of OpenVPN MTU settings, its necessary to comprehend that we’re tunneling records and that the VPN overhead is going to take away some of our MTU!
So here’s the trouble I right here all of the time: “My OpenVPN works pleasant for TCP traffic, however UDP site visitors is very buggy and solely works sometimes.” Why is this? Because TCP has many mechanisms to deal with networks and it will decrease its Maximum Segment Size (MSS) and attempt once more (retransmit). UDP being furnace and forget will in no way recognize there was once a trouble and simply hold firing these oversize packets into oblivion to be dropped via the VPN tunnel!
In my case this translated to SSH and web sessions working perfectly, however video streams and VoIP jogging over the tunnel would fail miserably, ensuing is stuttering and uneven video and audio.
Finding correct MTU
Discovering the correct MTU is very straightforward and can be achieved using ping, use the respective following commands (change www.devninja.net to suit)
for windows
ping -n 1 -l 1500 -f www.devninja.net
for Linux
ping -M do -s 1500 -c 1 www.devninja.net
for Mac OSX
ping -D -v -s 1500 -c 1 www.devninja.net
Once you have test and get time out. try decrease the 1500 value by 10 each time, until the ping succeeds. Once the ping succeeds, the value used is the MTU you should use.
Setting the MTU
OpenVPN requires a value called the MSS to be set. The MSS is the value for the MTU minus 40.
Eg. If your MTU is 1460, your MSS is 1420
MSS = MTU - 40 MSS = 1460 - 40 MSS = 1420
To set the MSS for OpenVPN, in your OpenVPN configuration file (the file originally sent ending in .ovpn), add the following configuration line (replacing 1420 with the appropriate value).
mssfix 1420
DevNinja
System & Network Administrator Ninja
OpenVPN, Wireguard, L2TP/IPSec, SSTP, IKEv2, PPTP, or others. If you had the luxury of choosing, which VPN protocols would you use? Therein lies my problem. In my current use case, I must find a way to improve OpenVPN performance and throughput.
You may have been following my Linux home lab build. One of the most important decisions when building your home lab is selecting the proper router/firewall for your network. After many hours of research, online comparisons, reading reviews, and watching Youtube videos, I went with the Edgerouter 10x (ER-10x). Note: this article includes my affiliate links; however, I only link to hardware and services I’ve paid for and tested myself.
Last week, I figured out that it does not support Wireguard, at least not officially, as I recently discovered (my next to-do). This isn’t a knock on the ER-10x; it’s a remarkably capable router with many business-class features and, most important rock-solid stability.
That said, my VPN service provider of choice is ovpn.com. They have many locations, excellent performance, and offer dedicated IPs with open ports at $3/month. On routers, they support Wireguard or OpenVPN.
OpenVPN 2.4 internet speed test results using Google+M-Lab and wifiman.com.
The Edgerouter 10x is built on Debian Linux. This makes it a pleasure to work with because a lot of the functionality feels familiar. Over the past year, I’ve spent more time in the command line and less time using the GUI.
Setting up OpenVPN is one of those command-line-only features. However, after downloading the .ovpn file and setting it up on the router, I soon hit a crippling OpenVPN limitation. The CPU! The ER-10x features 880 MHz CPU cores, which is often overkill. However, in this case, OpenVPN performance is not very efficient as throughput largely depends on the CPU’s core speed.
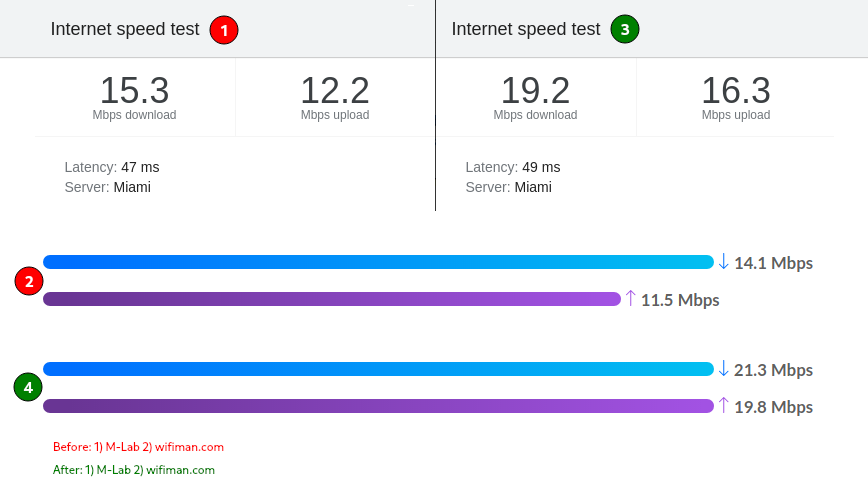
On my first speed test, download speeds were around 15 Mbps download and 12 Mbps upload. I needed a solid 20 Mbps down for the IoT devices connected to a VLAN that uses that VPN connection.
My basic setup at home currently is: dual WAN with backup 4G LTE ISP auto-failover, VLANs for isolated Guest WiFI network, and IoT devices, both wired and wireless. For now, I’ll run with what I have; it works!
Improving OpenVPN Performance
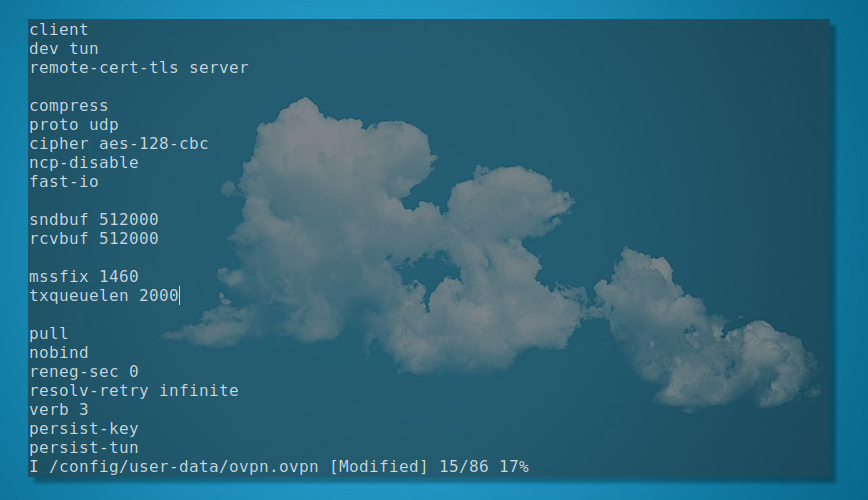
OpenVPN config Screenshot from my Manjaro i3 SSH session with the router.
Note: I’ve already verified results when I initially set up everything a week ago using my Ubuntu server over higher LAN throughput with iperf. As the hardware/CPU limits are so low on the Edgerouter, the ISP tests were very much representative of those tests. If you are using OpenVPN in a hardware-restricted setup, try the following config tweaks. I’ll try to take the time and revisit this article with some redone iperf test results. If you have the time, you can share your test results in the comments section below or by email using the “contact” link.
My ISP download speed is just over 100 Mbps. In this part of the world, this is as good as it gets for under $200 per month. That said, even before this OpenVPN setup, the IoT devices on my home network were restricted to a maximum download of 20 Mbps. I am using an EdgeSwitch to limit wired connections’ bandwidth and the Unifi controller via Unifi APs to limit wireless bandwidth. These network restrictions ensure that one or more devices don’t gobble bandwidth.
My plan? Improve OpenVPN performance as much as possible to at least hit 20 Mbps download speeds, as you can see from the above before vs. after internet speed tests. (I’ve since disabled bandwidth restrictions on the OpenVPN VLAN).
After optimizing OpenVPN’s performance, the max up/down speed is just about what the previous limits were. Let’s look at how you can go from 15 Mbps to 20 Mbps internet download speed on an 880 MHz CPU core router.
OpenVPN server Location
Whether you are using NordVPN (awesome 24/7 customer support), OVPN (best dedicated IP VPN, in my opinion), or another VPN service, the first step should be selecting the VPN servers closest to you. In my case, its servers are located in South Miami. Not much to elaborate on here… Closer is generally faster. Still, you should test locations for yourself because not all servers perform equally. Some are under more load than others. Thankfully, OVPN shows load levels for VPN server locations.
Disable compression
If the CPU isn’t a bottleneck, then feel free to enable compression. On the Edgerouter, compression will use CPU resources leading to higher CPU usage. You can disable it with:
comp-lzo no ;deprecated - remove or use 'compress' without an algorithm
or recommended for OpenVPN version 2.4+:
compress
Providing just compress without an algorithm is the equivalent of comp-lzo no which disables compression but enables the packet framing for compression.
Use UDP for better OpenVPN performance.
With OpenVPN, in most cases, UDP is faster than TCP. TCP packets are heavier, adding overhead. TCP also numbers packets in a sequence while UDP doesn’t. UDP uses very minimal headers making it less resource-intensive. Here’s the config line:
proto udp
Choosing the right Cipher
By default, OpenVPN uses Blowfish, a 128-bit cipher. Regarding the level of security you require, you will have to decide between better encryption vs. faster throughput with respect to CPU load. Again, especially with this 880 MHz CPU. If there’s no CPU bottleneck, I would recommend using AES-256-GCM. In my case, I’m using AES-128-CBC as it resulted in faster OpenVPN throughput.
cipher AES-128-CBC
Disable cipher negotiation
You can set ncp-disable (disable “negotiable crypto parameters”). This completely disables cipher negotiation and instead uses what’s specified by the cipher option discussed previously. As of OpenVPN 2.4, this is now deprecated. Also, read OpenVPN Cipher Negotiation (Quick reference).
ncp-disable
Optimize TUN/TAP/UDP I/O writes
Set fast-io to optimize TUN/TAP/UDP I/O writes by avoiding a call to poll/epoll/select before the write operation.
“The purpose of such a call would normally be to block until the device or socket is ready to accept the write. Such blocking is unnecessary on some platforms which don’t support write blocking on UDP sockets or TUN/TAP devices. In such cases, one can optimize the event loop by avoiding the poll/epoll/select call, improving CPU efficiency by 5% to 10%. This option can only be used on non-Windows systems, when proto udp is specified, and when shaper is NOT specified.” – Source.
Set send/receive buffers
You can set the UDP socket send and receive buffer sizes. On OpenVPN 2.3.9+, this defaults to the operating system’s default (usually 64K).
Add to client config (bytes):
sndbuf 512000 rcvbuf 512000
Or, if you have access, set buffers in the server config:
sndbuf 512000 rcvbuf 512000 push "sndbuf 512000" push "rcvbuf 512000"
Read more about fine-tuning these buffers here. These make a noticeable difference when tuned correctly.
Adjust client MTUs to match the OpenVPN server
You can use the following command to grep connection logs for ‘MTU’ mismatches. Use the warnings about size mismatch to adjust tun-mtu if necessary. My router defaults to 1500, which is also OpenVPN’s default, so there is no need to mess with it. Also, see warnings about adjusting tun-mtu and be sure to read about mssfix.
sudo cat /path/to/openvpn.log | grep WARNING
Which will display any warning like this:
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1500', remote='link-mtu 3000'
Set the transmit queue length
Set the TX queue length on the TUN/TAP interface. This defaults to the system OS, which in my case is 1000.
txqueuelen 2000
Default ovpn.com config (before)
client dev tun remote-cert-tls server cipher aes-256-cbc pull nobind reneg-sec 0 resolv-retry infinite verb 3 persist-key persist-tun remote-random proto udp mute-replay-warnings comp-lzo route-delay 10
My improved OpenVPN performance config file. (After)
client dev tun remote-cert-tls server compress proto udp cipher aes-128-cbc ncp-disable fast-io sndbuf 512000 rcvbuf 512000 txqueuelen 2000 pull nobind reneg-sec 0 resolv-retry infinite verb 3 persist-key persist-tun remote-random mute-replay-warnings route-delay 10
OpenVPN Performance – Conclusion
Often, even more so in work environments than at home, we are obliged to use technology, devices, software, and other tools we wouldn’t typically support. In these cases, we are still tasked with making things work, finding a workaround, and patching things up. Using OpenVPN on an Edgerouter feels a lot like that right now.
My next article should be the top five home and small business routers; what do you think? I would still include the Edgerouter 12, but I do have at least three others off the top of my head that I’m looking at next. For one, I’m interested in the Firewalla Gold, but at 2x the cost of the ER-12, it probably won’t make the list. Let’s discuss this later, yea? Please send me some suggestions to look into as well.
Published: Mar 24, 2021 | Last updated: July 18, 2022
Tags: performance, security, sysadmins
Есть сервер OpenVPN на убунте и клиенты на платформах Linux, Android и Win разных версий.
На nix и android проблем никаких, на большинстве win-машин тоже. Но есть несколько win-машин с такой проблемой: при подключении к vpn по началу все норм, но рандомно через какое-то время сайты (не все) перестают открываться. При этом на пинги продолжают отвечать. Бегло погуглив, пришел таки к выводу, что дело в MTU на конкретных машинах, но как я с ним не экспериментировал, рабочего результата так и не достиг.
MTU провайдера у этих машин 1492 (ADSL).
Конфиг сервера:
local aaa.bbb.xxx.yyy
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
client-to-client
tls-auth ta.key 0
crl-verify crl.pem
port 9852
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
verb 3
Конфиг проблемного клиента:
remote aaa.bbb.xxx.yyy 9852
comp-lzo yes
client
dev tun
ping 10
proto udp
tls-client
remote-cert-tls server
pkcs12 "c:\Program Files\OpenVPN\config\vpn.work1.p12"
tls-auth "c:\Program Files\OpenVPN\config\ta.key" 1
verb 3
pullЛог подключения с клиента (ip было лень уже замазывать):
C:Windowssystem32>"C:Program FilesOpenVPNbinopenvpn.exe" --config "c:Prog
ram FilesOpenVPNconfigmyvpnconfig.ovpn"
Wed Jul 29 09:23:16 2015 OpenVPN 2.3.7 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO]
[PKCS11] [IPv6] built on Jul 9 2015
Wed Jul 29 09:23:16 2015 library versions: OpenSSL 1.0.1p 9 Jul 2015, LZO 2.08
Enter Private Key Password:
Wed Jul 29 09:23:20 2015 WARNING: this configuration may cache passwords in memo
ry -- use the auth-nocache option to prevent this
Wed Jul 29 09:23:20 2015 Control Channel Authentication: using 'c:Program Files
OpenVPNconfigta.key' as a OpenVPN static key file
Wed Jul 29 09:23:20 2015 Outgoing Control Channel Authentication: Using 160 bit
message hash 'SHA1' for HMAC authentication
Wed Jul 29 09:23:20 2015 Incoming Control Channel Authentication: Using 160 bit
message hash 'SHA1' for HMAC authentication
Wed Jul 29 09:23:20 2015 Socket Buffers: R=[8192->8192] S=[8192->8192]
Wed Jul 29 09:23:20 2015 UDPv4 link local (bound): [undef]
Wed Jul 29 09:23:20 2015 UDPv4 link remote: [AF_INET]109.234.38.113:9852
Wed Jul 29 09:23:20 2015 TLS: Initial packet from [AF_INET]109.234.38.113:9852,
sid=981eb7c4 1766a3de
Wed Jul 29 09:23:21 2015 VERIFY OK: depth=1, C=RU, ST=59, L=Orda, O=vpnorda.tk,
OU=OrdaVpnServer, CN=vpnorda.tk, name=EasyRSA, emailAddress=root@vpnorda.tk
Wed Jul 29 09:23:21 2015 Validating certificate key usage
Wed Jul 29 09:23:21 2015 ++ Certificate has key usage 00a0, expects 00a0
Wed Jul 29 09:23:21 2015 VERIFY KU OK
Wed Jul 29 09:23:21 2015 Validating certificate extended key usage
Wed Jul 29 09:23:21 2015 ++ Certificate has EKU (str) TLS Web Server Authenticat
ion, expects TLS Web Server Authentication
Wed Jul 29 09:23:21 2015 VERIFY EKU OK
Wed Jul 29 09:23:21 2015 VERIFY OK: depth=0, C=RU, ST=59, L=Orda, O=vpnorda.tk,
OU=OrdaVpnServer, CN=vpnorda.tk, name=EasyRSA, emailAddress=root@vpnorda.tk
Wed Jul 29 09:23:23 2015 Data Channel Encrypt: Cipher 'BF-CBC' initialized with
128 bit key
Wed Jul 29 09:23:23 2015 Data Channel Encrypt: Using 160 bit message hash 'SHA1'
for HMAC authentication
Wed Jul 29 09:23:23 2015 Data Channel Decrypt: Cipher 'BF-CBC' initialized with
128 bit key
Wed Jul 29 09:23:23 2015 Data Channel Decrypt: Using 160 bit message hash 'SHA1'
for HMAC authentication
Wed Jul 29 09:23:23 2015 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES2
56-SHA, 2048 bit RSA
Wed Jul 29 09:23:23 2015 [vpnorda.tk] Peer Connection Initiated with [AF_INET]10
9.234.38.113:9852
Wed Jul 29 09:23:26 2015 SENT CONTROL [vpnorda.tk]: 'PUSH_REQUEST' (status=1)
Wed Jul 29 09:23:26 2015 PUSH: Received control message: 'PUSH_REPLY,redirect-ga
teway def1 bypass-dhcp,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,route 10.
8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.18 1
0.8.0.17'
Wed Jul 29 09:23:26 2015 OPTIONS IMPORT: timers and/or timeouts modified
Wed Jul 29 09:23:26 2015 OPTIONS IMPORT: --ifconfig/up options modified
Wed Jul 29 09:23:26 2015 OPTIONS IMPORT: route options modified
Wed Jul 29 09:23:26 2015 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options
modified
Wed Jul 29 09:23:26 2015 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Wed Jul 29 09:23:26 2015 open_tun, tt->ipv6=0
Wed Jul 29 09:23:26 2015 TAP-WIN32 device [Подключение по локаÐ
»ÑŒÐ½Ð¾Ð¹ Ñети 2] opened: \.Global{125CBAA8-B6E0-400C-A292-C8FEDA657477}.
tap
Wed Jul 29 09:23:26 2015 TAP-Windows Driver Version 9.21
Wed Jul 29 09:23:26 2015 Notified TAP-Windows driver to set a DHCP IP/netmask of
10.8.0.18/255.255.255.252 on interface {125CBAA8-B6E0-400C-A292-C8FEDA657477} [
DHCP-serv: 10.8.0.17, lease-time: 31536000]
Wed Jul 29 09:23:26 2015 Successful ARP Flush on interface [16] {125CBAA8-B6E0-4
00C-A292-C8FEDA657477}
Wed Jul 29 09:23:31 2015 TEST ROUTES: 2/2 succeeded len=1 ret=1 a=0 u/d=up
Wed Jul 29 09:23:31 2015 C:Windowssystem32route.exe ADD 109.234.38.113 MASK 2
55.255.255.255 192.168.0.13
Wed Jul 29 09:23:31 2015 ROUTE: CreateIpForwardEntry succeeded with dwForwardMet
ric1=20 and dwForwardType=4
Wed Jul 29 09:23:31 2015 Route addition via IPAPI succeeded [adaptive]
Wed Jul 29 09:23:31 2015 C:Windowssystem32route.exe ADD 0.0.0.0 MASK 128.0.0.
0 10.8.0.17
Wed Jul 29 09:23:31 2015 ROUTE: CreateIpForwardEntry succeeded with dwForwardMet
ric1=20 and dwForwardType=4
Wed Jul 29 09:23:31 2015 Route addition via IPAPI succeeded [adaptive]
Wed Jul 29 09:23:31 2015 C:Windowssystem32route.exe ADD 128.0.0.0 MASK 128.0.
0.0 10.8.0.17
Wed Jul 29 09:23:31 2015 ROUTE: CreateIpForwardEntry succeeded with dwForwardMet
ric1=20 and dwForwardType=4
Wed Jul 29 09:23:31 2015 Route addition via IPAPI succeeded [adaptive]
Wed Jul 29 09:23:31 2015 C:Windowssystem32route.exe ADD 10.8.0.0 MASK 255.255
.255.0 10.8.0.17
Wed Jul 29 09:23:31 2015 ROUTE: CreateIpForwardEntry succeeded with dwForwardMet
ric1=20 and dwForwardType=4
Wed Jul 29 09:23:31 2015 Route addition via IPAPI succeeded [adaptive]
Wed Jul 29 09:23:31 2015 Initialization Sequence CompletedКакие есть соображения?