Содержание
- AndroidSigning@3 fails to sign — java.io.IOException: Keystore was tampered with, or password was incorrect #11624
- Comments
- Environment
- Issue Description
- java.io.IOException: Keystore was tampered with, or password was incorrect #4
- Comments
AndroidSigning@3 fails to sign — java.io.IOException: Keystore was tampered with, or password was incorrect #11624
Question, Bug, or Feature?
Type: Bug
Enter Task Name: AndroidSigning@3 fails to sign
MicrosoftDocs/azure-devops-docs#6097
Environment
- Server — Azure Pipelines
- Agent — Hosted
Issue Description
Is AndroidSigning@3 using a different keystore format and if so, how do you generate it?
I’m receiving a DevOps YAML task signing error using AndroidSigning@3
VS2019 16.3.5 generated the keystore, using Ad-Hoc
The keystore is uploaded as a secure file.
The passwords are set as secure
Using the same pipeline, but different android signing tasks:
This works:
task: AndroidSigning@2
displayName: «align and sign»
inputs:
apkFiles: ‘$(outputDirectory)/*.apk’
jarsign: true
jarsignerKeystoreFile: ‘myapp-keystore.keystore’
jarsignerKeystorePassword: ‘$(keystorePassword)’
jarsignerKeystoreAlias: ‘myapp-keystore’
jarsignerKeyPassword: ‘$(keyPassword)’
zipalign: true
This fails (see error details below)
task: AndroidSigning@3
displayName: ‘align and sign’
inputs:
apkFiles: ‘$(outputDirectory)/*.apk’
apksignerKeystoreFile: ‘myapp-keystore.keystore’
apksignerKeystorePassword: ‘$(keystorePassword)’
apksignerKeystoreAlias: ‘myapp-keystore’
apksignerKeyPassword: ‘$(keyPassword)’
zipalign: true
C:windowssystem32cmd.exe /D /S /C «»C:Program Files (x86)Androidandroid-sdkbuild-tools24.0.3apksigner.bat» sign —ks d:a_tempmyapp-keystore.keystore —ks-pass «pass:» —ks-key-alias myapp-keystore —key-pass «pass:» —verbose
d:a1bReleaseandroidcom.aiworldwide.myapp.apk»
Failed to load signer «signer #1»
java.io.IOException: Keystore was tampered with, or password was incorrect
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:785)
at sun.security.provider.JavaKeyStore$JKS.engineLoad(JavaKeyStore.java:56)
at sun.security.provider.KeyStoreDelegator.engineLoad(KeyStoreDelegator.java:224)
at sun.security.provider.JavaKeyStore$DualFormatJKS.engineLoad(JavaKeyStore.java:70)
at java.security.KeyStore.load(KeyStore.java:1445)
at com.android.apksigner.ApkSignerTool$SignerParams.loadPrivateKeyAndCertsFromKeyStore(ApkSignerTool.java:604)
at com.android.apksigner.ApkSignerTool$SignerParams.loadPrivateKeyAndCerts(ApkSignerTool.java:546) at com.android.apksigner.ApkSignerTool$SignerParams.access$200(ApkSignerTool.java:500)
at com.android.apksigner.ApkSignerTool.sign(ApkSignerTool.java:236)
at com.android.apksigner.ApkSignerTool.main(ApkSignerTool.java:93)
Caused by: java.security.UnrecoverableKeyException: Password verification failed
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:783)
. 9 more
##[error]Error: The process ‘C:Program Files (x86)Androidandroid-sdkbuild-tools24.0.3apksigner.bat’ failed with exit code 2
The text was updated successfully, but these errors were encountered:
Источник
java.io.IOException: Keystore was tampered with, or password was incorrect #4
java InstallCert github.com 443
Loading KeyStore C:Program FilesJavajre1.8.0_101libsecuritycacerts.
Exception in thread «main» java.io.IOException: Keystore was tampered with, or password was incorrect
at sun.security.provider.JavaKeyStore.engineLoad(Unknown Source)
at sun.security.provider.JavaKeyStore$JKS.engineLoad(Unknown Source)
at sun.security.provider.KeyStoreDelegator.engineLoad(Unknown Source)
at sun.security.provider.JavaKeyStore$DualFormatJKS.engineLoad(Unknown Source)
at java.security.KeyStore.load(Unknown Source)
at InstallCert.main(InstallCert.java:81)
Caused by: java.security.UnrecoverableKeyException: Password verification failed
. 6 more
The text was updated successfully, but these errors were encountered:
Password verification failed. The examples use the default keystore password. The password for the keystore you are trying to use must have been changed.
Isn’t the default keystore password «changeit»?
If I run keytool, when i’m asked for the password I use «changeit» and it works:
C:Usersmirandaru>keytool -list -keystore «C:Program FilesJavajre1.8.0_101libsecurity
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 104 entries
digicertassuredidrootca, 16.4.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 05:63:B8:63:0D:62:D7:5A:BB:C8:AB:1E:4B:DF:B5:A8:99:B2:4D:43
comodorsaca, 11.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): AF:E5:D2:44:A8:D1:19:42:30:FF:47:9F:E2:F8:97:BB:CD:7A:8C:B4
thawtepremiumserverca, 20.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): E0:AB:05:94:20:72:54:93:05:60:62:02:36:70:F7:CD:2E:FC:66:66
swisssignsilverg2ca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 9B:AA:E5:9F:56:EE:21:CB:43:5A:BE:25:93:DF:A7:F0:40:D1:1D:CB
swisssignplatinumg2ca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 56:E0:FA:C0:3B:8F:18:23:55:18:E5:D3:11:CA:E8:C2:43:31:AB:66
identrustdstx3, 5.5.2016, trustedCertEntry,
Certificate fingerprint (SHA1): DA:C9:02:4F:54:D8:F6:DF:94:93:5F:B1:73:26:38:CA:6A:D7:7C:13
equifaxsecureebusinessca1, 21.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): AE:E6:3D:70:E3:76:FB:C7:3A:EB:B0:A1:C1:D4:C4:7A:A7:40:B3:F4
securetrustca, 5.3.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 87:82:C6:C3:04:35:3B:CF:D2:96:92:D2:59:3E:7D:44:D9:34:FF:11
digicertassuredidg3, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): F5:17:A2:4F:9A:48:C6:C9:F8:A2:00:26:9F:DC:0F:48:2C:AB:30:89
digicertassuredidg2, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): A1:4B:48:D9:43:EE:0A:0E:40:90:4F:3C:E0:A4:C0:91:93:51:5D:3F
utnuserfirstclientauthemailca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): B1:72:B1:A5:6D:95:F9:1F:E5:02:87:E1:4D:37:EA:6A:44:63:76:8A
identrustpublicca, 5.5.2016, trustedCertEntry,
Certificate fingerprint (SHA1): BA:29:41:60:77:98:3F:F4:F3:EF:F2:31:05:3B:2E:EA:6D:4D:45:FD
affirmtrustnetworkingca, 15.4.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 29:36:21:02:8B:20:ED:02:F5:66:C5:32:D1:D6:ED:90:9F:45:00:2F
utnuserfirsthardwareca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): 04:83:ED:33:99:AC:36:08:05:87:22:ED:BC:5E:46:00:E3:BE:F9:D7
entrustevca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): B3:1E:B1:B7:40:E3:6C:84:02:DA:DC:37:D4:4D:F5:D4:67:49:52:F9
globalsigneccrootcar5, 23.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 1F:24:C6:30:CD:A4:18:EF:20:69:FF:AD:4F:DD:5F:46:3A:1B:69:AA
globalsigneccrootcar4, 23.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 69:69:56:2E:40:80:F4:24:A1:E7:19:9F:14:BA:F3:EE:58:AB:6A:BB
certumca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 62:52:DC:40:F7:11:43:A2:2F:DE:9E:F7:34:8E:06:42:51:B1:81:18
entrustrootcag2, 22.6.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 8C:F4:27:FD:79:0C:3A:D1:66:06:8D:E8:1E:57:EF:BB:93:22:72:D4
addtrustclass1ca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): CC:AB:0E:A0:4C:23:01:D6:69:7B:DD:37:9F:CD:12:EB:24:E3:94:9D
equifaxsecureca, 20.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): D2:32:09:AD:23:D3:14:23:21:74:E4:0D:7F:9D:62:13:97:86:63:3A
quovadisrootca3, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 1F:49:14:F7:D8:74:95:1D:DD:AE:02:C0:BE:FD:3A:2D:82:75:51:85
quovadisrootca2, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): CA:3A:FB:CF:12:40:36:4B:44:B2:16:20:88:80:48:39:19:93:7C:F7
swisscomrootca2, 15.1.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 77:47:4F:C6:30:E4:0F:4C:47:64:3F:84:BA:B8:C6:95:4A:8A:41:EC
digicertglobalrootg3, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 7E:04:DE:89:6A:3E:66:6D:00:E6:87:D3:3F:FA:D9:3B:E8:3D:34:9E
digicertglobalrootg2, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): DF:3C:24:F9:BF:D6:66:76:1B:26:80:73:FE:06:D1:CC:8D:4F:82:A4
digicerthighassuranceevrootca, 16.4.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 5F:B7:EE:06:33:E2:59:DB:AD:0C:4C:9A:E6:D3:8F:1A:61:C7:DC:25
equifaxsecureglobalebusinessca1, 21.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 3A:74:CB:7A:47:DB:70:DE:89:1F:24:35:98:64:B8:2D:82:BD:1A:36
geotrustuniversalca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): E6:21:F3:35:43:79:05:9A:4B:68:30:9D:8A:2F:74:22:15:87:EC:79
thawteprimaryrootcag3, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): F1:8B:53:8D:1B:E9:03:B6:A6:F0:56:43:5B:17:15:89:CA:F3:6B:F2
verisignclass3ca, 11.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): A1:DB:63:93:91:6F:17:E4:18:55:09:40:04:15:C7:02:40:B0:AE:6B
thawteprimaryrootcag2, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): AA:DB:BC:22:23:8F:C4:01:A1:27:BB:38:DD:F4:1D:DB:08:9E:F0:12
deutschetelekomrootca2, 14.11.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 85:A4:08:C0:9C:19:3E:5D:51:58:7D:CD:D6:13:30:FD:8C:DE:37:BF
buypassclass3ca, 13.1.2014, trustedCertEntry,
Certificate fingerprint (SHA1): DA:FA:F7:FA:66:84:EC:06:8F:14:50:BD:C7:C2:81:A5:BC:A9:64:57
utnuserfirstobjectca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): E1:2D:FB:4B:41:D7:D9:C3:2B:30:51:4B:AC:1D:81:D8:38:5E:2D:46
dtrustclass3ca2, 4.5.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 58:E8:AB:B0:36:15:33:FB:80:F7:9B:1B:6D:29:D3:FF:8D:5F:00:F0
geotrustprimaryca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 32:3C:11:8E:1B:F7:B8:B6:52:54:E2:E2:10:0D:D6:02:90:37:F0:96
buypassclass2ca, 13.1.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 49:0A:75:74:DE:87:0A:47:FE:58:EE:F6:C7:6B:EB:C6:0B:12:40:99
verisignclass1ca, 11.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): CE:6A:64:A3:09:E4:2F:BB:D9:85:1C:45:3E:64:09:EA:E8:7D:60:F1
baltimorecodesigningca, 10.5.2002, trustedCertEntry,
Certificate fingerprint (SHA1): 30:46:D8:C8:88:FF:69:30:C3:4A:FC:CD:49:27:08:7C:60:56:7B:0D
baltimorecybertrustca, 10.5.2002, trustedCertEntry,
Certificate fingerprint (SHA1): D4:DE:20:D0:5E:66:FC:53:FE:1A:50:88:2C:78:DB:28:52:CA:E4:74
starfieldclass2ca, 20.1.2005, trustedCertEntry,
Certificate fingerprint (SHA1): AD:7E:1C:28:B0:64:EF:8F:60:03:40:20:14:C3:D0:E3:37:0E:B5:8A
actalisauthenticationrootca, 15.4.2015, trustedCertEntry,
Certificate fingerprint (SHA1): F3:73:B3:87:06:5A:28:84:8A:F2:F3:4A:CE:19:2B:DD:C7:8E:9C:AC
camerfirmachamberscommerceca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 6E:3A:55:A4:19:0C:19:5C:93:84:3C:C0:DB:72:2E:31:30:61:F0:B1
ttelesecglobalrootclass3ca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 55:A6:72:3E:CB:F2:EC:CD:C3:23:74:70:19:9D:2A:BE:11:E3:81:D1
digicerttrustedrootg4, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): DD:FB:16:CD:49:31:C9:73:A2:03:7D:3F:C8:3A:4D:7D:77:5D:05:E4
verisignclass3g5ca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 4E:B6:D5:78:49:9B:1C:CF:5F:58:1E:AD:56:BE:3D:9B:67:44:A5:E5
ttelesecglobalrootclass2ca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 59:0D:2D:7D:88:4F:40:2E:61:7E:A5:62:32:17:65:CF:17:D8:94:E9
verisignclass3g4ca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 22:D5:D8:DF:8F:02:31:D1:8D:F7:9D:B7:CF:8A:2D:64:C9:3F:6C:3A
verisignclass3g3ca, 25.3.2004, trustedCertEntry,
Certificate fingerprint (SHA1): 13:2D:0D:45:53:4B:69:97:CD:B2:D5:C3:39:E2:55:76:60:9B:5C:C6
xrampglobalca, 5.3.2014, trustedCertEntry,
Certificate fingerprint (SHA1): B8:01:86:D1:EB:9C:86:A5:41:04:CF:30:54:F3:4C:52:B7:E5:58:C6
entrustrootcaec1, 16.2.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 20:D8:06:40:DF:9B:25:F5:12:25:3A:11:EA:F7:59:8A:EB:14:B5:47
certumtrustednetworkca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 07:E0:32:E0:20:B7:2C:3F:19:2F:06:28:A2:59:3A:19:A7:0F:06:9E
certplusclass3pprimaryca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 21:6B:2A:29:E6:2A:00:CE:82:01:46:D8:24:41:41:B9:25:11:B2:79
verisignclass3g2ca, 20.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 85:37:1C:A6:E5:50:14:3D:CE:28:03:47:1B:DE:3A:09:E8:F8:77:0F
globalsignr3ca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): D6:9B:56:11:48:F0:1C:77:C5:45:78:C1:09:26:DF:5B:85:69:76:AD
secomscrootca2, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 5F:3B:8C:F2:F8:10:B3:7D:78:B4:CE:EC:19:19:C3:73:34:B9:C7:74
secomscrootca1, 2.6.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 36:B1:2B:49:F9:81:9E:D7:4C:9E:BC:38:0F:C6:56:8F:5D:AC:B2:F7
gtecybertrustglobalca, 10.5.2002, trustedCertEntry,
Certificate fingerprint (SHA1): 97:81:79:50:D8:1C:96:70:CC:34:D8:09:CF:79:44:31:36:7E:F4:74
affirmtrustcommercialca, 15.4.2014, trustedCertEntry,
Certificate fingerprint (SHA1): F9:B5:B6:32:45:5F:9C:BE:EC:57:5F:80:DC:E9:6E:2C:C7:B2:78:B7
verisignuniversalrootca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 36:79:CA:35:66:87:72:30:4D:30:A5:FB:87:3B:0F:A7:7B:B7:0D:54
globalsignr2ca, 2.8.2007, trustedCertEntry,
Certificate fingerprint (SHA1): 75:E0:AB:B6:13:85:12:27:1C:04:F8:5F:DD:DE:38:E4:B7:24:2E:FE
certplusclass2primaryca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 74:20:74:41:72:9C:DD:92:EC:79:31:D8:23:10:8D:C2:81:92:E2:BB
digicertglobalrootca, 16.4.2008, trustedCertEntry,
Certificate fingerprint (SHA1): A8:98:5D:3A:65:E5:E5:C4:B2:D7:D6:6D:40:C6:DD:2F:B1:9C:54:36
globalsignca, 19.3.2008, trustedCertEntry,
Certificate fingerprint (SHA1): B1:BC:96:8B:D4:F4:9D:62:2A:A8:9A:81:F2:15:01:52:A4:1D:82:9C
thawteprimaryrootca, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 91:C6:D6:EE:3E:8A:C8:63:84:E5:48:C2:99:29:5C:75:6C:81:7B:81
starfieldrootg2ca, 19.7.2014, trustedCertEntry,
Certificate fingerprint (SHA1): B5:1C:06:7C:EE:2B:0C:3D:F8:55:AB:2D:92:F4:FE:39:D4:E7:0F:0E
geotrustglobalca, 18.7.2003, trustedCertEntry,
Certificate fingerprint (SHA1): DE:28:F4:A4:FF:E5:B9:2F:A3:C5:03:D1:A3:49:A7:F9:96:2A:82:12
swisscomrootevca2, 15.1.2015, trustedCertEntry,
Certificate fingerprint (SHA1): E7:A1:90:29:D3:D5:52:DC:0D:0F:C6:92:D3:EA:88:0D:15:2E:1A:6B
soneraclass2ca, 29.3.2006, trustedCertEntry,
Certificate fingerprint (SHA1): 37:F7:6D:E6:07:7C:90:C5:B1:3E:93:1A:B7:41:10:B4:F2:E4:9A:27
verisigntsaca, 11.11.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 20:CE:B1:F0:F5:1C:0E:19:A9:F3:8D:B1:AA:8E:03:8C:AA:7A:C7:01
quovadisrootca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): DE:3F:40:BD:50:93:D3:9B:6C:60:F6:DA:BC:07:62:01:00:89:76:C9
starfieldservicesrootg2ca, 19.7.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 92:5A:8F:8D:2C:6D:04:E0:66:5F:59:6A:FF:22:D8:63:E8:25:6F:3F
affirmtrustpremiumeccca, 15.4.2014, trustedCertEntry,
Certificate fingerprint (SHA1): B8:23:6B:00:2F:1D:16:86:53:01:55:6C:11:A4:37:CA:EB:FF:C3:BB
comodoaaaca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): D1:EB:23:A4:6D:17:D6:8F:D9:25:64:C2:F1:F1:60:17:64:D8:E3:49
keynectisrootca, 23.4.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 9C:61:5C:4D:4D:85:10:3A:53:26:C2:4D:BA:EA:E4:A2:D2:D5:CC:97
addtrustqualifiedca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): 4D:23:78:EC:91:95:39:B5:00:7F:75:8F:03:3B:21:1E:C5:4D:8B:CF
aolrootca2, 19.3.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 85:B5:FF:67:9B:0C:79:96:1F:C8:6E:44:22:00:46:13:DB:17:92:84
aolrootca1, 19.3.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 39:21:C1:15:C1:5D:0E:CA:5C:CB:5B:C4:F0:7D:21:D8:05:0B:56:6A
addtrustexternalca, 2.5.2006, trustedCertEntry,
Certificate fingerprint (SHA1): 02:FA:F3:E2:91:43:54:68:60:78:57:69:4D:F5:E4:5B:68:85:18:68
verisignclass2g3ca, 25.3.2004, trustedCertEntry,
Certificate fingerprint (SHA1): 61:EF:43:D7:7F:CA:D4:61:51:BC:98:E0:C3:59:12:AF:9F:EB:63:11
luxtrustglobalrootca, 17.12.2014, trustedCertEntry,
Certificate fingerprint (SHA1): C9:3C:34:EA:90:D9:13:0C:0F:03:00:4B:98:BD:8B:35:70:91:56:11
verisignclass2g2ca, 25.3.2004, trustedCertEntry,
Certificate fingerprint (SHA1): B3:EA:C4:47:76:C9:C8:1C:EA:F2:9D:95:B6:CC:A0:08:1B:67:EC:9D
quovadisrootca3g3, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 48:12:BD:92:3C:A8:C4:39:06:E7:30:6D:27:96:E6:A4:CF:22:2E:7D
geotrustprimarycag3, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 03:9E:ED:B8:0B:E7:A0:3C:69:53:89:3B:20:D2:D9:32:3A:4C:2A:FD
geotrustprimarycag2, 10.12.2009, trustedCertEntry,
Certificate fingerprint (SHA1): 8D:17:84:D5:37:F3:03:7D:EC:70:FE:57:8B:51:9A:99:E6:10:D7:B0
swisssigngoldg2ca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): D8:C5:38:8A:B7:30:1B:1B:6E:D4:7A:E6:45:25:3A:6F:9F:1A:27:61
entrust2048ca, 22.6.2010, trustedCertEntry,
Certificate fingerprint (SHA1): 50:30:06:09:1D:97:D4:F5:AE:39:F7:CB:E7:92:7D:7D:65:2D:34:31
chunghwaepkirootca, 14.1.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 67:65:0D:F1:7E:8E:7E:5B:82:40:A4:F4:56:4B:CF:E2:3D:69:C6:F0
quovadisrootca2g3, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 09:3C:61:F3:8B:8B:DC:7D:55:DF:75:38:02:05:00:E1:25:F5:C8:36
camerfirmachambersignca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 4A:BD:EE:EC:95:0D:35:9C:89:AE:C7:52:A1:2C:5B:29:F6:D6:AA:0C
quovadisrootca1g3, 2.2.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 1B:8E:EA:57:96:29:1A:C9:39:EA:B8:0A:81:1A:73:73:C0:93:79:67
camerfirmachambersca, 31.10.2008, trustedCertEntry,
Certificate fingerprint (SHA1): 78:6A:74:AC:76:AB:14:7F:9C:6A:30:50:BA:9E:A8:7E:FE:9A:CE:3C
usertrusteccca, 11.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): D1:CB:CA:5D:B2:D5:2A:7F:69:3B:67:4D:E5:F0:5A:1D:0C:95:7D:F0
godaddyclass2ca, 20.1.2005, trustedCertEntry,
Certificate fingerprint (SHA1): 27:96:BA:E6:3F:18:01:E2:77:26:1B:A0:D7:77:70:02:8F:20:EE:E4
identrustcommercial, 5.5.2016, trustedCertEntry,
Certificate fingerprint (SHA1): DF:71:7E:AA:4A:D9:4E:C9:55:84:99:60:2D:48:DE:5F:BC:F0:3A:25
affirmtrustpremiumca, 15.4.2014, trustedCertEntry,
Certificate fingerprint (SHA1): D8:A6:33:2C:E0:03:6F:B1:85:F6:63:4F:7D:6A:06:65:26:32:28:27
usertrustrsaca, 11.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 2B:8F:1B:57:33:0D:BB:A2:D0:7A:6C:51:F7:0E:E9:0D:DA:B9:AD:8E
verisignclass1g3ca, 25.3.2004, trustedCertEntry,
Certificate fingerprint (SHA1): 20:42:85:DC:F7:EB:76:41:95:57:8E:13:6B:D4:B7:D1:E9:8E:46:A5
secomevrootca1, 2.6.2008, trustedCertEntry,
Certificate fingerprint (SHA1): FE:B8:C4:32:DC:F9:76:9A:CE:AE:3D:D8:90:8F:FD:28:86:65:64:7D
dtrustclass3ca2ev, 4.5.2016, trustedCertEntry,
Certificate fingerprint (SHA1): 96:C9:1B:0B:95:B4:10:98:42:FA:D0:D8:22:79:FE:60:FA:B9:16:83
verisignclass1g2ca, 25.3.2004, trustedCertEntry,
Certificate fingerprint (SHA1): 27:3E:E1:24:57:FD:C4:F9:0C:55:E8:2B:56:16:7F:62:F5:32:E5:47
comodoeccca, 11.5.2015, trustedCertEntry,
Certificate fingerprint (SHA1): 9F:74:4E:9F:2B:4D:BA:EC:0F:31:2C:50:B6:56:3B:8E:2D:93:C3:11
godaddyrootg2ca, 19.7.2014, trustedCertEntry,
Certificate fingerprint (SHA1): 47:BE:AB:C9:22:EA:E8:0E:78:78:34:62:A7:9F:45:C2:54:FD:E6:8B
I see what the problem is. The 2nd argument to InstallCert is the keystore password you want to use. In your example, it’s trying to use 443 as the keystore password. You can leave port 443 off, since it’s the default, but if you did want to use a port, your command would be (using the default keystore password of ‘changeit’):
java InstallCert GitHub.com:443
ouh my bad, thank you!
On trying to install certificates using the company internal network driven by Cisco Anyconnect Secure Mobility Client, I am not able to proceed further. Kindly find the below issue copy pasted from the console. If there is a possible solution to this problem, kindly let me know.
D:>java InstallCert localhost:8090
Loading KeyStore D:Javalibsecuritycacerts.
Opening connection to localhost:8090.
Starting SSL handshake.
Источник
AppGallery supports two kinds of signing certificates: one that is totally generated by AppGallery Connect and the other one that is generated by developers. Here I will share some solutions with you for the common errors reported during the signing certificate generation.
The command in the official document is as follows:
Error 1 — «No value provided for flag: include-cer»
Cause: It is not the correct pepk.jar file. Normally, its file size is around 2 MB. Check whether it is the file that was provided by Android Studio.
Solution: Use the correct pepk.jar file that you can get from Google.
Error 2: «java.io.IOException: Keystore was tampered with, or password was incorrect»
Cause: The keystore password is most likely not correct.
Solution: Enter the correct password.
Error 3: «Unable to export or encrypt the private key»
Cause: Incorrect password. The keystore password is entered correctly, but the key file password is entered incorrectly when entered for the second time.
Solution: Enter the correct key file password.
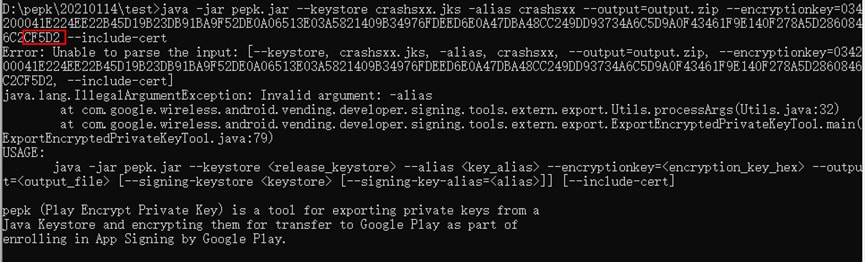
Error 4: «Unable to parse the input:»
Cause: The length of the encryption key is incorrect. Check whether you have copied the complete encryption key.
Solution: Use the complete encryption key.
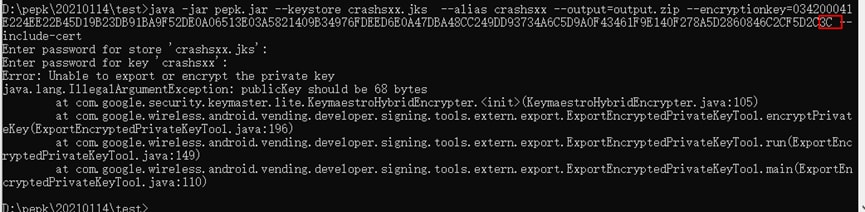
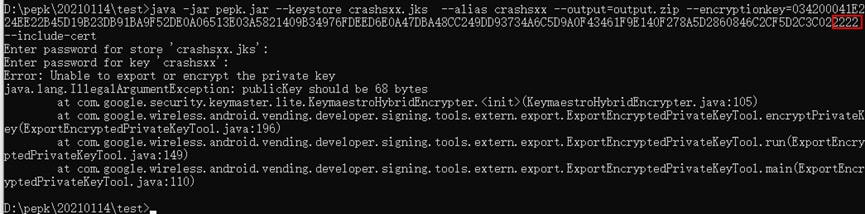
Error 5: «java.lang.IllegalArgumentException: publicKey should be 68 bytes»
Cause: The length of the encryption key is incorrect. Check whether you have copied the complete encryption key.
Solution: Use the complete encryption key.
Error 6: «java.lang.IllegalArgumentException: Hex encoded byte array must have even length but instead has length: 143.»
Cause: The encryption key is too long.
Solution: Use the correct encryption key
Error 7: «java.security.GeneralSecurityException: point is not on the curve»
Cause: The encryption key is incorrect.
Solution: Use the correct encryption key.
After upgrade to VS 16.4, I was unable to sign again my application for Google Play with my keystore. Tought it was a bug so I waited for for an update to see if it was fixed, but no (16.4.1)
I tried so sign my APK with jarsigner from Android JDK and it worked, so I confirm that I don’t lost the password or alias.
Steps to Reproduce
- Keystore password and alias the same (generated by VS old version). Password have the next symbols: @ ^ ] $
- Distribute project with AdHoc/Google Play
- Get error
Expected Behavior
Sign the APK
Actual Behavior
Failed to load signer «signer 1»
java.io.IOException: Keystore was tampered with, or password was incorrect.
Version Information
Microsoft Visual Studio Enterprise 2019
Version 16.4.1
VisualStudio.16.Release/16.4.1+29609.76
Microsoft .NET Framework
Version 4.8.03752
Installed Version: Enterprise
Azure App Service Tools v3.0.0 16.4.457.38025
Azure App Service Tools v3.0.0
C# Tools 3.4.1-beta4-19607-02+52d275c4f82f329a9732b078c7f7fa0e45cd3e84
C# components used in the IDE. Depending on your project type and settings, a different version of the compiler may be used.
Common Azure Tools 1.10
Provides common services for use by Azure Mobile Services and Microsoft Azure Tools.
Extensibility Message Bus 1.2.0 (d16-2@8b56e20)
Provides common messaging-based MEF services for loosely coupled Visual Studio extension components communication and integration.
IntelliCode Extension 1.0
IntelliCode Visual Studio Extension Detailed Info
Microsoft JVM Debugger 1.0
Provides support for connecting the Visual Studio debugger to JDWP compatible Java Virtual Machines
Microsoft MI-Based Debugger 1.0
Provides support for connecting Visual Studio to MI compatible debuggers
Mono Debugging for Visual Studio 16.5.23 (1b51e8c)
Support for debugging Mono processes with Visual Studio.
NuGet Package Manager 5.4.0
NuGet Package Manager in Visual Studio. For more information about NuGet, visit https://docs.nuget.org/
ProjectServicesPackage Extension 1.0
ProjectServicesPackage Visual Studio Extension Detailed Info
Visual Basic Tools 3.4.1-beta4-19607-02+52d275c4f82f329a9732b078c7f7fa0e45cd3e84
Visual Basic components used in the IDE. Depending on your project type and settings, a different version of the compiler may be used.
Visual F# Tools 10.4 for F# 4.6 16.4.0-beta.19556.5+e7597deb7042710a7142bdccabd6f92b0840d354
Microsoft Visual F# Tools 10.4 for F# 4.6
Visual Studio Code Debug Adapter Host Package 1.0
Interop layer for hosting Visual Studio Code debug adapters in Visual Studio
VisualStudio.DeviceLog 1.0
Information about my package
VisualStudio.Foo 1.0
Information about my package
VisualStudio.Mac 1.0
Mac Extension for Visual Studio
Xamarin 16.4.000.306 (d16-4@564b8d0)
Visual Studio extension to enable development for Xamarin.iOS and Xamarin.Android.
Xamarin Designer 16.4.0.464 (remotes/origin/d16-4@4abf337c3)
Visual Studio extension to enable Xamarin Designer tools in Visual Studio.
Xamarin Templates 16.4.25 (579ee62)
Templates for building iOS, Android, and Windows apps with Xamarin and Xamarin.Forms.
Xamarin.Android SDK 10.1.1.0 (d16-4/f2c9364)
Xamarin.Android Reference Assemblies and MSBuild support.
Mono: bef1e63
Java.Interop: xamarin/java.interop@c4e569f
ProGuard: xamarin/proguard@905836d
SQLite: xamarin/sqlite@46204c4
Xamarin.Android Tools: xamarin/xamarin-android-tools@9f4ed4b
Xamarin.iOS and Xamarin.Mac SDK 13.8.3.0 (0d8fe21)
Xamarin.iOS and Xamarin.Mac Reference Assemblies and MSBuild support.
Я получаю следующую ошибку при создании сертификатов на своей локальной машине.
C:Usersabc>keytool -genkey -alias tomcat -keyalg RSA
Enter keystore password:
keytool error: java.io.IOException: Keystore was tampered with, or password was incorrect
Я думаю, что есть некоторые проблемы в jdk version.I запускал ту же самую команду на моей машине collegues, и она работает нормально.
Пожалуйста, поделитесь своими входом.
Ответ 1
Из вашего описания я предполагаю, что вы на машине с Windows, а ваш дом abc
Итак: Причина
При запуске этой команды
keytool -genkey -alias tomcat -keyalg RSA
потому что вы не указываете явное хранилище ключей, оно попытается сгенерировать (и в вашем случае, когда вы получаете исключение, чтобы обновить) keystore C:usersabc>.keystore, и, конечно же, вам нужно предоставить старый пароль для .keystore, пока я считаю, что вы предоставляют вашу версию (новую).
Решение
-
Удалите
.keystoreизC:usersabc>и попробуйте выполнить команду -
или попробуйте выполнить следующую команду, которая создаст новый xyzkeystore:
keytool -genkey -keystore xyzkeystore -alias tomcat -keyalg RSA
Примечание: -genkey теперь старое, вместо этого используйте -genkeypair, хотя обе работают одинаково.
Ответ 2
Я решил это, используя пароль по умолчанию для хранилища cacerts: 'changeit'
Ответ 3
Этот ответ будет полезен для нового пользователя Mac (Works for Linux, Window 7 64 бит).
Пустой пароль работал в моем mac. (вставьте нижнюю строку в терминал)
keytool -list -v -keystore ~/.android/debug.keystore
когда он запрашивает
Enter keystore password:
просто нажмите кнопку ввода (не вводите ничего). Он должен работать.
Пожалуйста, убедитесь, что это файл по умолчанию debug.keystore, а не файл хранилища ключей на основе проекта (для этого может измениться пароль).
Хорошо работает и для MacOS Sierra 10.10+.
Я слышал, он работает и в среде linux. Я еще не тестировал это в Linux.
Ответ 4
В Tomcat 8.5 обратите внимание, чтобы написать правильное имя атрибутов. Это мой код на server.xml:
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true">
<SSLHostConfig>
<Certificate certificateKeystoreFile="conf/keystore" certificateKeystorePassword="mypassword" type="RSA"/>
</SSLHostConfig>
</Connector>
Вы можете посетить https://tomcat.apache.org/tomcat-8.5-doc/config/http.html, чтобы увидеть все атрибуты.
Ответ 5
Использование changeit для пароля также важно.
Эта команда, наконец, работала для меня (с причалом):
keytool -genkey -keyalg RSA -alias selfsigned -keystore keystore.jks -storepass changeit -validity 360 -keysize 2048
Ответ 6
Работает на Windows
откройте командную строку (нажмите клавишу Windows + R, затем введите «cmd» без кавычек в появившемся диалоговом окне и нажмите клавишу ввода).
затем введите код сниффа ниже:
- cd C:Program FilesJavajdk1.7.0_25bin
затем введите следующую команду
- keytool -list — хранилище ключей «C: /Documents and Settings/Ваше имя /.android/debug.keystore»
Затем он запросит пароль Keystore. Пароль по умолчанию — это тип «android», введите или просто нажмите «DONT TYPE ANY PASSWORD».
Ответ 7
Проверьте свою домашнюю папку ~/.gradle/gradle.properties. Иногда, если у вас есть gradle.properties в домашнем каталоге, он получает данные от него. Либо вы можете изменить это, либо удалить файлы. Затем он берет необходимые данные из вашей локальной папки.
Ответ 8
Я решил эту проблему, используя пароль по умолчанию «changeit«.
Ответ 9
Обобщая советы на этой странице, я закончил со следующим:
keytool -genkeypair -keystore ~/.android/release.keystore -alias <my_alias> -storepass <my_cert_pass> -keyalg RSA
Затем у меня появился набор вопросов относительно имени, организации, местоположения и пароля для моего псевдонима.
Ответ 10
ошибка keytool: java.io.IOException: был поврежден Keystore или неверный пароль
Я решил проблему, когда изменил путь хранилища ключей C:MyWorksmykeystore на C:MyWorksmykeystore.keystore.
Ответ 11
Поймал эту вещь сегодня. Пробовал менять пароли — это не помогло.
В моем случае это помогло обновить Android Studio с 1.5 до 2.0. Не знаю почему, но теперь все работает.
Ответ 12
В моем случае мне нужно было иметь root доступ.
Ответ 13
Я исправил эту проблему, удалив выходной файл и снова выполнив команду. Оказывается, он НЕ перезаписывает предыдущий файл. У меня была эта проблема при обновлении сертификата let encrypt с помощью tomcat
Ответ 14
[[email protected] Certificate]# openssl pkcs12 -export -in
/opt/Certificate/115c99f4c5aa98f5.crt -inkey /opt/Certificate/ravi.in.key -certfile
/opt/Certificate/gd_bundle-g2-g1.crt -out RaviNew.p12
Enter Export Password: <Password>
Verifying - Enter Export Password: <Password>
Примечание: — Над Экспортом Pasworrd запишите куда угодно, потому что это необходимо для создания файла JKS (это зависит от вашего выбора, какой пароль вы хотите сделать)
keytool -importkeystore -srckeystore DigiEduNew.p12 -srcstoretype pkcs12 -destkeystore finaldigiEdu.jks -deststoretype JKS
Importing keystore DigiEduNew.p12 to finaldigiEdu.jks...
Enter destination keystore password: <Any Password >
Re-enter new password: <Any Password >
Enter source keystore password: <.P12 Password >
Entry for alias 1 successfully imported.
Import command completed: 1 entries successfully imported, 0 entries failed or
cancelled
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12
which is an industry standard format using "keytool -importkeystore -srckeystore
finaldigiEdu.jks -destkeystore finaldigiEdu.jks -deststoretype pkcs12".
Ответ 15
Это случилось со мной в самый первый раз при создании файла keystone. Я думал, что у него есть пароль по умолчанию. но в конце концов я ввел пароль своей учетной записи, и он работал в Mac.
Ответ 16
Для меня я решил это, изменив пароли с арабской буквы на английскую букву, но сначала я пошел в папку и удалил сгенерированный ключ, затем он работает.
Ответ 17
Пароль по умолчанию для хранилища ключей отладки — android.
Ответ 18
Ваш пароль неверный. Проверьте номерку !
Hi All,
i am facing this error in the SOA composite created for approval. I think it is the either the access of the keystore file or the keystore file itself is corrupted. Any pointers on this would be great!
Also, can someone let me know how do we create the new keystore for this and map the new keystore to the composite?
FYI — The same composite is working in an other environment.
[2014-01-01T05:31:05.011-07:00] [soa_server1] [ERROR] [WSM-00055] [oracle.wsm.resources.security] [tid: orabpel.invoke.pool-4.thread-1] [userId: weblogic] [ecid: 004viVPMDD9Fw000jzwkno0005E5000QKe,1:31579] [WSM_POLICY_NAME: oracle/wss11_saml_token_with_message_protection_client_policy] [APP: soa-infra] [composite_name: MgrApproval] [component_name: ApprovalProcess] [component_instance_id: 120001] [URI: /identity/faces/home] The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException: Keystore was tampered with, or password was incorrect. Ensure that valid keystore type and password are configured.
[2014-01-01T05:31:05.037-07:00] [soa_server1] [ERROR] [WSM-07501] [oracle.wsm.resources.enforcement] [tid: orabpel.invoke.pool-4.thread-1] [userId: weblogic] [ecid: 004viVPMDD9Fw000jzwkno0005E5000QKe,1:31579] [WSM_POLICY_NAME: oracle/wss11_saml_token_with_message_protection_client_policy] [APP: soa-infra] [composite_name: MgrApproval] [component_name: ApprovalProcess] [component_instance_id: 120001] [URI: /identity/faces/home] Failure in Oracle WSM Agent processRequest, category=security, function=agent.function.client, application=default, composite=MgrApproval, modelObj=CallbackService_2, policy=null, policyVersion=null, assertionName=null.[[
oracle.wsm.common.sdk.WSMException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.initialize(SecurityScenarioExecutor.java:463)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.init(SecurityScenarioExecutor.java:336)
at oracle.wsm.security.policy.scenario.executor.Wss11SamlWithCertsScenarioExecutor.init(Wss11SamlWithCertsScenarioExecutor.java:72)
at oracle.wsm.policyengine.impl.runtime.WSPolicyRuntimeExecutor.populateAssertionExecutors(WSPolicyRuntimeExecutor.java:262)
…………………………….
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1110)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:603)
at com.collaxa.cube.engine.dispatch.Dispatcher$ContextCapturingThreadFactory$2.run(Dispatcher.java:850)
at java.lang.Thread.run(Thread.java:722)
Caused by: oracle.wsm.security.SecurityException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.wsm.security.jps.WsmLegacyKeyStore.<init>(WsmLegacyKeyStore.java:270)
at oracle.wsm.security.jps.WsmKeyStoreFactory.getKeyStore(WsmKeyStoreFactory.java:63)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.updateWsmKeyStore(SecurityScenarioExecutor.java:1293)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.initialize(SecurityScenarioExecutor.java:437)
… 120 more
Caused by: java.io.IOException: Keystore was tampered with, or password was incorrect
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:772)
at sun.security.provider.JavaKeyStore$JKS.engineLoad(JavaKeyStore.java:55)
at java.security.KeyStore.load(KeyStore.java:1214)
at oracle.wsm.security.jps.WsmLegacyKeyStore.createInstanceOfKeyStoreWrapper(WsmLegacyKeyStore.java:604)
at oracle.wsm.security.jps.WsmLegacyKeyStore.<init>(WsmLegacyKeyStore.java:249)
… 123 more
Caused by: java.security.UnrecoverableKeyException: Password verification failed
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:770)
… 127 more
]]
[2014-01-01T05:31:05.076-07:00] [soa_server1] [ERROR] [] [oracle.integration.platform.blocks.soap] [tid: orabpel.invoke.pool-4.thread-1] [userId: weblogic] [ecid: 004viVPMDD9Fw000jzwkno0005E5000QKe,1:31579] [APP: soa-infra] [composite_name: MgrApproval] [component_name: ApprovalProcess] [component_instance_id: 120001] [URI: /identity/faces/home] Unable to dispatch request to http://iam.secureoracle.com:80/workflowservice/CallbackService due to exception[[
javax.xml.ws.WebServiceException: oracle.fabric.common.PolicyEnforcementException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.j2ee.ws.client.jaxws.DispatchImpl.invoke(DispatchImpl.java:867)
at oracle.j2ee.ws.client.jaxws.OracleDispatchImpl.synchronousInvocationWithRetry(OracleDispatchImpl.java:235)
at oracle.j2ee.ws.client.jaxws.OracleDispatchImpl.invoke(OracleDispatchImpl.java:106)
at oracle.integration.platform.blocks.soap.AbstractWebServiceBindingComponent.dispatchRequest(AbstractWebServiceBindingComponent.java:553)
at oracle.integration.platform.blocks.soap.WebServiceExternalBindingComponent.processOutboundMessage(WebServiceExternalBindingComponent.java:248)
…………………………..
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:603)
at com.collaxa.cube.engine.dispatch.Dispatcher$ContextCapturingThreadFactory$2.run(Dispatcher.java:850)
at java.lang.Thread.run(Thread.java:722)
Caused by: oracle.fabric.common.PolicyEnforcementException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.fabric.common.AbstractSecurityInterceptor.processResult(AbstractSecurityInterceptor.java:184)
at oracle.fabric.common.BindingSecurityInterceptor.processRequest(BindingSecurityInterceptor.java:95)
at oracle.integration.platform.common.InterceptorChainImpl$1.run(InterceptorChainImpl.java:210)
at java.security.AccessController.doPrivileged(Native Method)
at javax.security.auth.Subject.doAsPrivileged(Subject.java:536)
at oracle.integration.platform.common.InterceptorChainImpl.processRequestAsSubject(InterceptorChainImpl.java:208)
… 100 more
Caused by: oracle.wsm.common.sdk.WSMException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.initialize(SecurityScenarioExecutor.java:463)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.init(SecurityScenarioExecutor.java:336)
at oracle.wsm.security.policy.scenario.executor.Wss11SamlWithCertsScenarioExecutor.init(Wss11SamlWithCertsScenarioExecutor.java:72)
at oracle.wsm.policyengine.impl.runtime.WSPolicyRuntimeExecutor.populateAssertionExecutors(WSPolicyRuntimeExecutor.java:262)
at oracle.wsm.policyengine.impl.runtime.WSPolicyRuntimeExecutor.populateAssertionExecutors(WSPolicyRuntimeExecutor.java:285)
at oracle.wsm.policyengine.impl.runtime.WSPolicyRuntimeExecutor.init(WSPolicyRuntimeExecutor.java:168)
at oracle.wsm.policyengine.impl.PolicyExecutionEngine.getPolicyExecutor(PolicyExecutionEngine.java:137)
at oracle.wsm.policyengine.impl.PolicyExecutionEngine.execute(PolicyExecutionEngine.java:101)
at oracle.wsm.agent.WSMAgent.processCommon(WSMAgent.java:1039)
at oracle.wsm.agent.WSMAgent.processRequest(WSMAgent.java:485)
at oracle.fabric.common.BindingSecurityInterceptor.processRequest(BindingSecurityInterceptor.java:94)
… 110 more
Caused by: oracle.wsm.security.SecurityException: WSM-00055 : The keystore located at /app/oracle/product/ofm/user_projects/domains/IAM_domain/config/fmwconfig/default-keystore.jks cannot be loaded due to java.io.IOException. Ensure that valid keystore type and password are configured.
at oracle.wsm.security.jps.WsmLegacyKeyStore.<init>(WsmLegacyKeyStore.java:270)
at oracle.wsm.security.jps.WsmKeyStoreFactory.getKeyStore(WsmKeyStoreFactory.java:63)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.updateWsmKeyStore(SecurityScenarioExecutor.java:1293)
at oracle.wsm.security.policy.scenario.executor.SecurityScenarioExecutor.initialize(SecurityScenarioExecutor.java:437)
… 120 more
Caused by: java.io.IOException: Keystore was tampered with, or password was incorrect
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:772)
at sun.security.provider.JavaKeyStore$JKS.engineLoad(JavaKeyStore.java:55)
at java.security.KeyStore.load(KeyStore.java:1214)
at oracle.wsm.security.jps.WsmLegacyKeyStore.createInstanceOfKeyStoreWrapper(WsmLegacyKeyStore.java:604)
at oracle.wsm.security.jps.WsmLegacyKeyStore.<init>(WsmLegacyKeyStore.java:249)
… 123 more
Caused by: java.security.UnrecoverableKeyException: Password verification failed
at sun.security.provider.JavaKeyStore.engineLoad(JavaKeyStore.java:770)
… 127 more
]]
[2014-01-01T05:31:05.097-07:00] [soa_server1] [ERROR] [] [oracle.integration.platform.blocks.soap] [tid: orabpel.invoke.pool-4.thread-1] [userId: weblogic] [ecid: 004viVPMDD9Fw000jzwkno0005E5000QKe,1:31579] [APP: soa-infra] [composite_name: MgrApproval] [component_name: ApprovalProcess] [component_instance_id: 120001] [URI: /identity/faces/home] Unable to dispatch request to http://iam.secureoracle.com:80/workflowservice/CallbackService due to exception[[
oracle.fabric.common.FabricInvocationException: Unable to access the following endpoint(s): http://iam.secureoracle.com:80/workflowservice/CallbackService
at oracle.integration.platform.blocks.soap.AbstractWebServiceBindingComponent.dispatchRequest(AbstractWebServiceBindingComponent.java:581)
at oracle.integration.platform.blocks.soap.WebServiceExternalBindingComponent.processOutboundMessage(WebServiceExternalBindingComponent.java:248)
at oracle.integration.platform.blocks.soap.WebServiceExternalBindingComponent.sendSOAPMessage(WebServiceExternalBindingComponent.java:1026)
at oracle.integration.platform.blocks.soap.WebServiceExternalBindingComponent.request(WebServiceExternalBindingComponent.java:745)
I have used the Windows certificate store quite a lot over the years, including fixing a really gnarly issue caused by a minor change in Windows Server 2003, but I haven’t used the Java Keystore at all until recently. One thing I learned very quickly is that the error messages are utterly terrible most of the time and you can lose hours of your life labouring under the misguided belief that the error relates to the actual problem.
To help the next person who fires up command prompt to use the Java keytool for the first time, here are the problems I encountered on my first visit.
The first one is reasonably obvious. If the path to the keytool isn’t in your system paths, you’ll need to use the full path to use the keytool, which is c:Program FilesJavajre6bin> or something similar (if you have multiple versions of JRE, see Additional Problems below!).
Once you are in the right place, you are likely to come across these errors:
keytool error: java.io.IOException: Keystore was tampered with, or password was incorrect
The default password is changeit. You should probably follow that advice, but you’ll need to know this default password to get started.
keytool error: java.lang.Exception: Input not an X.509 certificate
Sometimes this means you have forgotten to specify the alias when adding a certificate. Most of the time though, it is because it doesn’t like any content before the -----BEGIN CERTIFICATE----- or after the -----END CERTIFICATE-----. It is worth taking a back-up copy and then delete all the extra rubbish in the file other than these tags and the content in between – even white-space before and after.
keytool error: java.io.FileNotFoundException: C:Program FilesJavajre6libsecuritycacerts (Access is denied)
Browse the the file specified in the error message and give yourself permission to modify it – by default on Windows 7, SYSTEM has full access, but you will be read only.
Additional Problems
As if that wasn’t enough, here are other pit-falls I found.
- If you are running 64 bit windows, you need to add to the “Program Files” flavour of the certificate store, not the “Program Files (x86)” flavour, unless you are specifically running your Java app in x86 mode.
- If you have multiple versions of JRE installed, you need to install to the one being used, i.e. “jre6” rather than “jre7”.
I hope this information helps you to have a smoother first encounter with the Keystore!
Written by
Wednesday, September 12, 2012
Steve Fenton is an Octonaut at Octopus Deploy and five-time Microsoft MVP for developer technologies. He’s a Software Punk and writer.
-
Calling Azure Open AI with RestSharp
Written by
Steve FentonSaturday, January 28, 2023
-
JavaScript remote error logging
Written by
Steve FentonThursday, September 6, 2012