Exit codes indicates a failure condition when ending a program and they fall between 0 and 255. The shell and its builtins may use especially the values above 125 to indicate specific failure modes, so list of codes can vary between shells and operating systems (e.g. Bash uses the value 128+N as the exit status). See: Bash — 3.7.5 Exit Status or man bash.
In general a zero exit status indicates that a command succeeded, a non-zero exit status indicates failure.
To check which error code is returned by the command, you can print $? for the last exit code or ${PIPESTATUS[@]} which gives a list of exit status values from pipeline (in Bash) after a shell script exits.
There is no full list of all exit codes which can be found, however there has been an attempt to systematize exit status numbers in kernel source, but this is main intended for C/C++ programmers and similar standard for scripting might be appropriate.
Some list of sysexits on both Linux and BSD/OS X with preferable exit codes for programs (64-78) can be found in /usr/include/sysexits.h (or: man sysexits on BSD):
0 /* successful termination */
64 /* base value for error messages */
64 /* command line usage error */
65 /* data format error */
66 /* cannot open input */
67 /* addressee unknown */
68 /* host name unknown */
69 /* service unavailable */
70 /* internal software error */
71 /* system error (e.g., can't fork) */
72 /* critical OS file missing */
73 /* can't create (user) output file */
74 /* input/output error */
75 /* temp failure; user is invited to retry */
76 /* remote error in protocol */
77 /* permission denied */
78 /* configuration error */
/* maximum listed value */
The above list allocates previously unused exit codes from 64-78. The range of unallotted exit codes will be further restricted in the future.
However above values are mainly used in sendmail and used by pretty much nobody else, so they aren’t anything remotely close to a standard (as pointed by @Gilles).
In shell the exit status are as follow (based on Bash):
-
1—125— Command did not complete successfully. Check the command’s man page for the meaning of the status, few examples below: -
1— Catchall for general errorsMiscellaneous errors, such as «divide by zero» and other impermissible operations.
Example:
$ let "var1 = 1/0"; echo $? -bash: let: var1 = 1/0: division by 0 (error token is "0") 1 -
2— Misuse of shell builtins (according to Bash documentation)Missing keyword or command, or permission problem (and diff return code on a failed binary file comparison).
Example:
empty_function() {} -
6— No such device or addressExample:
$ curl foo; echo $? curl: (6) Could not resolve host: foo 6 -
124— command times out 125— if a command itself failssee: coreutils-
126— if command is found but cannot be invoked (e.g. is not executable)Permission problem or command is not an executable.
Example:
$ /dev/null $ /etc/hosts; echo $? -bash: /etc/hosts: Permission denied 126 -
127— if a command cannot be found, the child process created to execute it returns that statusPossible problem with
$PATHor a typo.Example:
$ foo; echo $? -bash: foo: command not found 127 -
128— Invalid argument toexitexit takes only integer args in the range 0 — 255.
Example:
$ exit 3.14159 -bash: exit: 3.14159: numeric argument required -
128—254— fatal error signal «n» — command died due to receiving a signal. The signal code is added to 128 (128 + SIGNAL) to get the status (Linux:man 7 signal, BSD:man signal), few examples below: -
130— command terminated due to Ctrl-C being pressed, 130-128=2 (SIGINT)Example:
$ cat ^C $ echo $? 130 -
137— if command is sent theKILL(9)signal (128+9), the exit status of command otherwisekill -9 $PPIDof script. -
141—SIGPIPE— write on a pipe with no readerExample:
$ hexdump -n100000 /dev/urandom | tee &>/dev/null >(cat > file1.txt) >(cat > file2.txt) >(cat > file3.txt) >(cat > file4.txt) >(cat > file5.txt) $ find . -name '*.txt' -print0 | xargs -r0 cat | tee &>/dev/null >(head /dev/stdin > head.out) >(tail /dev/stdin > tail.out) xargs: cat: terminated by signal 13 $ echo ${PIPESTATUS[@]} 0 125 141 -
143— command terminated by signal code 15 (128+15=143)Example:
$ sleep 5 && killall sleep & [1] 19891 $ sleep 100; echo $? Terminated: 15 143 -
255* — exit status out of range.exit takes only integer args in the range 0 — 255.
Example:
$ sh -c 'exit 3.14159'; echo $? sh: line 0: exit: 3.14159: numeric argument required 255
According to the above table, exit codes 1 — 2, 126 — 165, and 255 have special meanings, and should therefore be avoided for user-specified exit parameters.
Please note that out of range exit values can result in unexpected exit codes (e.g. exit 3809 gives an exit code of 225, 3809 % 256 = 225).
See:
- Appendix E. Exit Codes With Special Meanings at Advanced Bash-Scripting Guide
- Writing Better Shell Scripts – Part 2 at Innovationsts
Exit codes indicates a failure condition when ending a program and they fall between 0 and 255. The shell and its builtins may use especially the values above 125 to indicate specific failure modes, so list of codes can vary between shells and operating systems (e.g. Bash uses the value 128+N as the exit status). See: Bash — 3.7.5 Exit Status or man bash.
In general a zero exit status indicates that a command succeeded, a non-zero exit status indicates failure.
To check which error code is returned by the command, you can print $? for the last exit code or ${PIPESTATUS[@]} which gives a list of exit status values from pipeline (in Bash) after a shell script exits.
There is no full list of all exit codes which can be found, however there has been an attempt to systematize exit status numbers in kernel source, but this is main intended for C/C++ programmers and similar standard for scripting might be appropriate.
Some list of sysexits on both Linux and BSD/OS X with preferable exit codes for programs (64-78) can be found in /usr/include/sysexits.h (or: man sysexits on BSD):
0 /* successful termination */
64 /* base value for error messages */
64 /* command line usage error */
65 /* data format error */
66 /* cannot open input */
67 /* addressee unknown */
68 /* host name unknown */
69 /* service unavailable */
70 /* internal software error */
71 /* system error (e.g., can't fork) */
72 /* critical OS file missing */
73 /* can't create (user) output file */
74 /* input/output error */
75 /* temp failure; user is invited to retry */
76 /* remote error in protocol */
77 /* permission denied */
78 /* configuration error */
/* maximum listed value */
The above list allocates previously unused exit codes from 64-78. The range of unallotted exit codes will be further restricted in the future.
However above values are mainly used in sendmail and used by pretty much nobody else, so they aren’t anything remotely close to a standard (as pointed by @Gilles).
In shell the exit status are as follow (based on Bash):
-
1—125— Command did not complete successfully. Check the command’s man page for the meaning of the status, few examples below: -
1— Catchall for general errorsMiscellaneous errors, such as «divide by zero» and other impermissible operations.
Example:
$ let "var1 = 1/0"; echo $? -bash: let: var1 = 1/0: division by 0 (error token is "0") 1 -
2— Misuse of shell builtins (according to Bash documentation)Missing keyword or command, or permission problem (and diff return code on a failed binary file comparison).
Example:
empty_function() {} -
6— No such device or addressExample:
$ curl foo; echo $? curl: (6) Could not resolve host: foo 6 -
124— command times out 125— if a command itself failssee: coreutils-
126— if command is found but cannot be invoked (e.g. is not executable)Permission problem or command is not an executable.
Example:
$ /dev/null $ /etc/hosts; echo $? -bash: /etc/hosts: Permission denied 126 -
127— if a command cannot be found, the child process created to execute it returns that statusPossible problem with
$PATHor a typo.Example:
$ foo; echo $? -bash: foo: command not found 127 -
128— Invalid argument toexitexit takes only integer args in the range 0 — 255.
Example:
$ exit 3.14159 -bash: exit: 3.14159: numeric argument required -
128—254— fatal error signal «n» — command died due to receiving a signal. The signal code is added to 128 (128 + SIGNAL) to get the status (Linux:man 7 signal, BSD:man signal), few examples below: -
130— command terminated due to Ctrl-C being pressed, 130-128=2 (SIGINT)Example:
$ cat ^C $ echo $? 130 -
137— if command is sent theKILL(9)signal (128+9), the exit status of command otherwisekill -9 $PPIDof script. -
141—SIGPIPE— write on a pipe with no readerExample:
$ hexdump -n100000 /dev/urandom | tee &>/dev/null >(cat > file1.txt) >(cat > file2.txt) >(cat > file3.txt) >(cat > file4.txt) >(cat > file5.txt) $ find . -name '*.txt' -print0 | xargs -r0 cat | tee &>/dev/null >(head /dev/stdin > head.out) >(tail /dev/stdin > tail.out) xargs: cat: terminated by signal 13 $ echo ${PIPESTATUS[@]} 0 125 141 -
143— command terminated by signal code 15 (128+15=143)Example:
$ sleep 5 && killall sleep & [1] 19891 $ sleep 100; echo $? Terminated: 15 143 -
255* — exit status out of range.exit takes only integer args in the range 0 — 255.
Example:
$ sh -c 'exit 3.14159'; echo $? sh: line 0: exit: 3.14159: numeric argument required 255
According to the above table, exit codes 1 — 2, 126 — 165, and 255 have special meanings, and should therefore be avoided for user-specified exit parameters.
Please note that out of range exit values can result in unexpected exit codes (e.g. exit 3809 gives an exit code of 225, 3809 % 256 = 225).
See:
- Appendix E. Exit Codes With Special Meanings at Advanced Bash-Scripting Guide
- Writing Better Shell Scripts – Part 2 at Innovationsts
Содержание
- find(1) — Linux man page
- Synopsis
- Description
- Options
- Expressions
find(1) — Linux man page
find — search for files in a directory hierarchy
Synopsis
find [-H] [-L] [-P] [-D debugopts] [-Olevel] [path. ] [expression]
Description
This manual page documents the GNU version of find. GNU find searches the directory tree rooted at each given file name by evaluating the given expression from left to right, according to the rules of precedence (see section OPERATORS), until the outcome is known (the left hand side is false for and operations, true for or), at which point find moves on to the next file name.
If you are using find in an environment where security is important (for example if you are using it to search directories that are writable by other users), you should read the «Security Considerations» chapter of the findutils documentation, which is called Finding Files and comes with findutils. That document also includes a lot more detail and discussion than this manual page, so you may find it a more useful source of information.
Options
The -H, -L and -P options control the treatment of symbolic links. Command-line arguments following these are taken to be names of files or directories to be examined, up to the first argument that begins with ‘-‘, or the argument ‘(‘ or ‘!’. That argument and any following arguments are taken to be the expression describing what is to be searched for. If no paths are given, the current directory is used. If no expression is given, the expression -print is used (but you should probably consider using -print0 instead, anyway).
This manual page talks about ‘options’ within the expression list. These options control the behaviour of find but are specified immediately after the last path name. The five ‘real’ options -H, -L, -P, -D and -O must appear before the first path name, if at all. A double dash — can also be used to signal that any remaining arguments are not options (though ensuring that all start points begin with either ‘./’ or ‘/’ is generally safer if you use wildcards in the list of start points). -P
Never follow symbolic links. This is the default behaviour. When find examines or prints information a file, and the file is a symbolic link, the information used shall be taken from the properties of the symbolic link itself.
Follow symbolic links. When find examines or prints information about files, the information used shall be taken from the properties of the file to which the link points, not from the link itself (unless it is a broken symbolic link or find is unable to examine the file to which the link points). Use of this option implies -noleaf. If you later use the -P option, -noleaf will still be in effect. If -L is in effect and find discovers a symbolic link to a subdirectory during its search, the subdirectory pointed to by the symbolic link will be searched. When the -L option is in effect, the -type predicate will always match against the type of the file that a symbolic link points to rather than the link itself (unless the symbolic link is broken). Using -L causes the -lname and -ilname predicates always to return false. -H
Do not follow symbolic links, except while processing the command line arguments. When find examines or prints information about files, the information used shall be taken from the properties of the symbolic link itself. The only exception to this behaviour is when a file specified on the command line is a symbolic link, and the link can be resolved. For that situation, the information used is taken from whatever the link points to (that is, the link is followed). The information about the link itself is used as a fallback if the file pointed to by the symbolic link cannot be examined. If -H is in effect and one of the paths specified on the command line is a symbolic link to a directory, the contents of that directory will be examined (though of course -maxdepth 0 would prevent this). If more than one of -H, -L and -P is specified, each overrides the others; the last one appearing on the command line takes effect. Since it is the default, the -P option should be considered to be in effect unless either -H or -L is specified.
GNU find frequently stats files during the processing of the command line itself, before any searching has begun. These options also affect how those arguments are processed. Specifically, there are a number of tests that compare files listed on the command line against a file we are currently considering. In each case, the file specified on the command line will have been examined and some of its properties will have been saved. If the named file is in fact a symbolic link, and the -P option is in effect (or if neither -H nor -L were specified), the information used for the comparison will be taken from the properties of the symbolic link. Otherwise, it will be taken from the properties of the file the link points to. If find cannot follow the link (for example because it has insufficient privileges or the link points to a nonexistent file) the properties of the link itself will be used.
When the -H or -L options are in effect, any symbolic links listed as the argument of -newer will be dereferenced, and the timestamp will be taken from the file to which the symbolic link points. The same consideration applies to -newerXY, -anewer and -cnewer.
The -follow option has a similar effect to -L, though it takes effect at the point where it appears (that is, if -L is not used but -follow is, any symbolic links appearing after -follow on the command line will be dereferenced, and those before it will not). -D debugoptions Print diagnostic information; this can be helpful to diagnose problems with why find is not doing what you want. The list of debug options should be comma separated. Compatibility of the debug options is not guaranteed between releases of findutils. For a complete list of valid debug options, see the output of find -D help. Valid debug options include help
Explain the debugging options
Show the expression tree in its original and optimised form.
Print messages as files are examined with the stat and lstat system calls. The find program tries to minimise such calls.
Prints diagnostic information relating to the optimisation of the expression tree; see the -O option.
Prints a summary indicating how often each predicate succeeded or failed. -Olevel Enables query optimisation. The find program reorders tests to speed up execution while preserving the overall effect; that is, predicates with side effects are not reordered relative to each other. The optimisations performed at each optimisation level are as follows. 0
Equivalent to optimisation level 1.
This is the default optimisation level and corresponds to the traditional behaviour. Expressions are reordered so that tests based only on the names of files (for example -name and -regex) are performed first.
Any -type or -xtype tests are performed after any tests based only on the names of files, but before any tests that require information from the inode. On many modern versions of Unix, file types are returned by readdir() and so these predicates are faster to evaluate than predicates which need to stat the file first.
At this optimisation level, the full cost-based query optimiser is enabled. The order of tests is modified so that cheap (i.e. fast) tests are performed first and more expensive ones are performed later, if necessary. Within each cost band, predicates are evaluated earlier or later according to whether they are likely to succeed or not. For -o, predicates which are likely to succeed are evaluated earlier, and for -a, predicates which are likely to fail are evaluated earlier. The cost-based optimiser has a fixed idea of how likely any given test is to succeed. In some cases the probability takes account of the specific nature of the test (for example, -type f is assumed to be more likely to succeed than -type c). The cost-based optimiser is currently being evaluated. If it does not actually improve the performance of find, it will be removed again. Conversely, optimisations that prove to be reliable, robust and effective may be enabled at lower optimisation levels over time. However, the default behaviour (i.e. optimisation level 1) will not be changed in the 4.3.x release series. The findutils test suite runs all the tests on find at each optimisation level and ensures that the result is the same.
Expressions
The expression is made up of options (which affect overall operation rather than the processing of a specific file, and always return true), tests (which return a true or false value), and actions (which have side effects and return a true or false value), all separated by operators. -and is assumed where the operator is omitted.
If the expression contains no actions other than -prune, -print is performed on all files for which the expression is true.
OPTIONS All options always return true. Except for -daystart, -follow and -regextype, the options affect all tests, including tests specified before the option. This is because the options are processed when the command line is parsed, while the tests don’t do anything until files are examined. The -daystart, -follow and -regextype options are different in this respect, and have an effect only on tests which appear later in the command line. Therefore, for clarity, it is best to place them at the beginning of the expression. A warning is issued if you don’t do this. -d
A synonym for -depth, for compatibility with FreeBSD, NetBSD, MacOS X and OpenBSD. -daystart Measure times (for -amin, -atime, -cmin, -ctime, -mmin, and -mtime) from the beginning of today rather than from 24 hours ago. This option only affects tests which appear later on the command line. -depth
Process each directory’s contents before the directory itself. The -delete action also implies -depth. -follow Deprecated; use the -L option instead. Dereference symbolic links. Implies -noleaf. The -follow option affects only those tests which appear after it on the command line. Unless the -H or -L option has been specified, the position of the -follow option changes the behaviour of the -newer predicate; any files listed as the argument of -newer will be dereferenced if they are symbolic links. The same consideration applies to -newerXY, -anewer and -cnewer. Similarly, the -type predicate will always match against the type of the file that a symbolic link points to rather than the link itself. Using -follow causes the -lname and -ilname predicates always to return false. -help, —help Print a summary of the command-line usage of find and exit. -ignore_readdir_race Normally, find will emit an error message when it fails to stat a file. If you give this option and a file is deleted between the time find reads the name of the file from the directory and the time it tries to stat the file, no error message will be issued. This also applies to files or directories whose names are given on the command line. This option takes effect at the time the command line is read, which means that you cannot search one part of the filesystem with this option on and part of it with this option off (if you need to do that, you will need to issue two find commands instead, one with the option and one without it). -maxdepth levels Descend at most levels (a non-negative integer) levels of directories below the command line arguments. -maxdepth 0 means only apply the tests and actions to the command line arguments. -mindepth levels Do not apply any tests or actions at levels less than levels (a non-negative integer). -mindepth 1 means process all files except the command line arguments. -mount
Don’t descend directories on other filesystems. An alternate name for -xdev, for compatibility with some other versions of find. -noignore_readdir_race Turns off the effect of -ignore_readdir_race. -noleaf Do not optimize by assuming that directories contain 2 fewer subdirectories than their hard link count. This option is needed when searching filesystems that do not follow the Unix directory-link convention, such as CD-ROM or MS-DOS filesystems or AFS volume mount points. Each directory on a normal Unix filesystem has at least 2 hard links: its name and its ‘.’ entry. Additionally, its subdirectories (if any) each have a ‘..’ entry linked to that directory. When find is examining a directory, after it has statted 2 fewer subdirectories than the directory’s link count, it knows that the rest of the entries in the directory are non-directories (‘leaf’ files in the directory tree). If only the files’ names need to be examined, there is no need to stat them; this gives a significant increase in search speed. -regextype type Changes the regular expression syntax understood by -regex and -iregex tests which occur later on the command line. Currently-implemented types are emacs (this is the default), posix-awk, posix-basic, posix-egrep and posix-extended. -version, —version Print the find version number and exit. -warn, -nowarn Turn warning messages on or off. These warnings apply only to the command line usage, not to any conditions that find might encounter when it searches directories. The default behaviour corresponds to -warn if standard input is a tty, and to -nowarn otherwise. -xautofs Don’t descend directories on autofs filesystems. -xdev
Don’t descend directories on other filesystems.
TESTS Some tests, for example -newerXY and -samefile, allow comparison between the file currently being examined and some reference file specified on the command line. When these tests are used, the interpretation of the reference file is determined by the options -H, -L and -P and any previous -follow, but the reference file is only examined once, at the time the command line is parsed. If the reference file cannot be examined (for example, the stat(2) system call fails for it), an error message is issued, and find exits with a nonzero status.
Numeric arguments can be specified as +n
for greater than n,
for less than n,
for exactly n. -amin n File was last accessed n minutes ago. -anewer file File was last accessed more recently than file was modified. If file is a symbolic link and the -H option or the -L option is in effect, the access time of the file it points to is always used. -atime n File was last accessed n*24 hours ago. When find figures out how many 24-hour periods ago the file was last accessed, any fractional part is ignored, so to match -atime +1, a file has to have been accessed at least two days ago. -cmin n File’s status was last changed n minutes ago. -cnewer file File’s status was last changed more recently than file was modified. If file is a symbolic link and the -H option or the -L option is in effect, the status-change time of the file it points to is always used. -ctime n File’s status was last changed n*24 hours ago. See the comments for -atime to understand how rounding affects the interpretation of file status change times. -empty
File is empty and is either a regular file or a directory. -executable Matches files which are executable and directories which are searchable (in a file name resolution sense). This takes into account access control lists and other permissions artefacts which the -perm test ignores. This test makes use of the access(2) system call, and so can be fooled by NFS servers which do UID mapping (or root-squashing), since many systems implement access(2) in the client’s kernel and so cannot make use of the UID mapping information held on the server. Because this test is based only on the result of the access(2) system call, there is no guarantee that a file for which this test succeeds can actually be executed. -false
Always false. -fstype type File is on a filesystem of type type. The valid filesystem types vary among different versions of Unix; an incomplete list of filesystem types that are accepted on some version of Unix or another is: ufs, 4.2, 4.3, nfs, tmp, mfs, S51K, S52K. You can use -printf with the %F directive to see the types of your filesystems. -gid n
File’s numeric group ID is n. -group gname File belongs to group gname (numeric group ID allowed). -ilname pattern Like -lname, but the match is case insensitive. If the -L option or the -follow option is in effect, this test returns false unless the symbolic link is broken. -iname pattern Like -name, but the match is case insensitive. For example, the patterns ‘fo*’ and ‘F??’ match the file names ‘Foo’, ‘FOO’, ‘foo’, ‘fOo’, etc. In these patterns, unlike filename expansion by the shell, an initial ‘.’ can be matched by ‘*’. That is, find -name *bar will match the file ‘.foobar’. Please note that you should quote patterns as a matter of course, otherwise the shell will expand any wildcard characters in them. -inum n File has inode number n. It is normally easier to use the -samefile test instead. -ipath pattern Behaves in the same way as -iwholename. This option is deprecated, so please do not use it. -iregex pattern Like -regex, but the match is case insensitive. -iwholename pattern Like -wholename, but the match is case insensitive. -links n File has n links. -lname pattern File is a symbolic link whose contents match shell pattern pattern. The metacharacters do not treat ‘/’ or ‘.’ specially. If the -L option or the -follow option is in effect, this test returns false unless the symbolic link is broken. -mmin n File’s data was last modified n minutes ago. -mtime n File’s data was last modified n*24 hours ago. See the comments for -atime to understand how rounding affects the interpretation of file modification times. -name pattern Base of file name (the path with the leading directories removed) matches shell pattern pattern. The metacharacters (‘*’, ‘?’, and ‘[]’) match a ‘.’ at the start of the base name (this is a change in findutils-4.2.2; see section STANDARDS CONFORMANCE below). To ignore a directory and the files under it, use -prune; see an example in the description of -path. Braces are not recognised as being special, despite the fact that some shells including Bash imbue braces with a special meaning in shell patterns. The filename matching is performed with the use of the fnmatch(3) library function. Don’t forget to enclose the pattern in quotes in order to protect it from expansion by the shell. -newer file File was modified more recently than file. If file is a symbolic link and the -H option or the -L option is in effect, the modification time of the file it points to is always used. -newerXY reference Compares the timestamp of the current file with reference. The reference argument is normally the name of a file (and one of its timestamps is used for the comparison) but it may also be a string describing an absolute time. X and Y are placeholders for other letters, and these letters select which time belonging to how reference is used for the comparison. Some combinations are invalid; for example, it is invalid for X to be t. Some combinations are not implemented on all systems; for example B is not supported on all systems. If an invalid or unsupported combination of XY is specified, a fatal error results. Time specifications are interpreted as for the argument to the -d option of GNU date. If you try to use the birth time of a reference file, and the birth time cannot be determined, a fatal error message results. If you specify a test which refers to the birth time of files being examined, this test will fail for any files where the birth time is unknown. -nogroup
No group corresponds to file’s numeric group ID. -nouser No user corresponds to file’s numeric user ID. -path pattern File name matches shell pattern pattern. The metacharacters do not treat ‘/’ or ‘.’ specially; so, for example,
find . -path «./sr*sc» will print an entry for a directory called ‘./src/misc’ (if one exists). To ignore a whole directory tree, use -prune rather than checking every file in the tree. For example, to skip the directory ‘src/emacs’ and all files and directories under it, and print the names of the other files found, do something like this:
find . -path ./src/emacs -prune -o -print Note that the pattern match test applies to the whole file name, starting from one of the start points named on the command line. It would only make sense to use an absolute path name here if the relevant start point is also an absolute path. This means that this command will never match anything:
find bar -path /foo/bar/myfile -print The predicate -path is also supported by HP-UX find and will be in a forthcoming version of the POSIX standard. -perm mode File’s permission bits are exactly mode (octal or symbolic). Since an exact match is required, if you want to use this form for symbolic modes, you may have to specify a rather complex mode string. For example -perm g=w will only match files which have mode 0020 (that is, ones for which group write permission is the only permission set). It is more likely that you will want to use the ‘/’ or ‘-‘ forms, for example -perm -g=w, which matches any file with group write permission. See the EXAMPLES section for some illustrative examples. -perm —mode All of the permission bits mode are set for the file. Symbolic modes are accepted in this form, and this is usually the way in which would want to use them. You must specify ‘u’, ‘g’ or ‘o’ if you use a symbolic mode. See the EXAMPLES section for some illustrative examples. -perm /mode Any of the permission bits mode are set for the file. Symbolic modes are accepted in this form. You must specify ‘u’, ‘g’ or ‘o’ if you use a symbolic mode. See the EXAMPLES section for some illustrative examples. If no permission bits in mode are set, this test matches any file (the idea here is to be consistent with the behaviour of -perm -000). -perm +mode Deprecated, old way of searching for files with any of the permission bits in mode set. You should use -perm /mode instead. Trying to use the ‘+’ syntax with symbolic modes will yield surprising results. For example, ‘+u+x’ is a valid symbolic mode (equivalent to +u,+x, i.e. 0111) and will therefore not be evaluated as -perm +mode but instead as the exact mode specifier -perm mode and so it matches files with exact permissions 0111 instead of files with any execute bit set. If you found this paragraph confusing, you’re not alone — just use -perm /mode. This form of the -perm test is deprecated because the POSIX specification requires the interpretation of a leading ‘+’ as being part of a symbolic mode, and so we switched to using ‘/’ instead. -readable Matches files which are readable. This takes into account access control lists and other permissions artefacts which the -perm test ignores. This test makes use of the access(2) system call, and so can be fooled by NFS servers which do UID mapping (or root-squashing), since many systems implement access(2) in the client’s kernel and so cannot make use of the UID mapping information held on the server. -regex pattern File name matches regular expression pattern. This is a match on the whole path, not a search. For example, to match a file named ‘./fubar3’, you can use the regular expression ‘.*bar.’ or ‘.*b.*3’, but not ‘f.*r3’. The regular expressions understood by find are by default Emacs Regular Expressions, but this can be changed with the -regextype option. -samefile name File refers to the same inode as name. When -L is in effect, this can include symbolic links. -size n[cwbkMG] File uses n units of space. The following suffixes can be used: ‘b’
for 512-byte blocks (this is the default if no suffix is used)
for two-byte words
for Kilobytes (units of 1024 bytes)
for Megabytes (units of 1048576 bytes)
for Gigabytes (units of 1073741824 bytes) The size does not count indirect blocks, but it does count blocks in sparse files that are not actually allocated. Bear in mind that the ‘%k’ and ‘%b’ format specifiers of -printf handle sparse files differently. The ‘b’ suffix always denotes 512-byte blocks and never 1 Kilobyte blocks, which is different to the behaviour of -ls. -true
Always true. -type c File is of type c: b
block (buffered) special
character (unbuffered) special
named pipe (FIFO)
symbolic link; this is never true if the -L option or the -follow option is in effect, unless the symbolic link is broken. If you want to search for symbolic links when -L is in effect, use -xtype.
File’s numeric user ID is n. -used n File was last accessed n days after its status was last changed. -user uname File is owned by user uname (numeric user ID allowed). -wholename pattern See -path. This alternative is less portable than -path. -writable Matches files which are writable. This takes into account access control lists and other permissions artefacts which the -perm test ignores. This test makes use of the access(2) system call, and so can be fooled by NFS servers which do UID mapping (or root-squashing), since many systems implement access(2) in the client’s kernel and so cannot make use of the UID mapping information held on the server. -xtype c The same as -type unless the file is a symbolic link. For symbolic links: if the -H or -P option was specified, true if the file is a link to a file of type c; if the -L option has been given, true if c is ‘l’. In other words, for symbolic links, -xtype checks the type of the file that -type does not check. -context pattern (SELinux only) Security context of the file matches glob pattern.
ACTIONS -delete Delete files; true if removal succeeded. If the removal failed, an error message is issued. If -delete fails, find‘s exit status will be nonzero (when it eventually exits). Use of -delete automatically turns on the -depth option.
Warnings: Don’t forget that the find command line is evaluated as an expression, so putting -delete first will make find try to delete everything below the starting points you specified. When testing a find command line that you later intend to use with -delete, you should explicitly specify -depth in order to avoid later surprises. Because -delete implies -depth, you cannot usefully use -prune and -delete together. -exec command ; Execute command; true if 0 status is returned. All following arguments to find are taken to be arguments to the command until an argument consisting of ‘;’ is encountered. The string ‘<>‘ is replaced by the current file name being processed everywhere it occurs in the arguments to the command, not just in arguments where it is alone, as in some versions of find. Both of these constructions might need to be escaped (with a ‘’) or quoted to protect them from expansion by the shell. See the EXAMPLES section for examples of the use of the -exec option. The specified command is run once for each matched file. The command is executed in the starting directory. There are unavoidable security problems surrounding use of the -exec action; you should use the -execdir option instead. -exec command <> + This variant of the -exec action runs the specified command on the selected files, but the command line is built by appending each selected file name at the end; the total number of invocations of the command will be much less than the number of matched files. The command line is built in much the same way that xargs builds its command lines. Only one instance of ‘<>‘ is allowed within the command. The command is executed in the starting directory. -execdir command ; -execdir command <> + Like -exec, but the specified command is run from the subdirectory containing the matched file, which is not normally the directory in which you started find. This a much more secure method for invoking commands, as it avoids race conditions during resolution of the paths to the matched files. As with the -exec action, the ‘+’ form of -execdir will build a command line to process more than one matched file, but any given invocation of command will only list files that exist in the same subdirectory. If you use this option, you must ensure that your $PATH environment variable does not reference ‘.’; otherwise, an attacker can run any commands they like by leaving an appropriately-named file in a directory in which you will run -execdir. The same applies to having entries in $PATH which are empty or which are not absolute directory names. -fls file True; like -ls but write to file like -fprint. The output file is always created, even if the predicate is never matched. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -fprint file True; print the full file name into file file. If file does not exist when find is run, it is created; if it does exist, it is truncated. The file names »/dev/stdout» and »/dev/stderr» are handled specially; they refer to the standard output and standard error output, respectively. The output file is always created, even if the predicate is never matched. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -fprint0 file True; like -print0 but write to file like -fprint. The output file is always created, even if the predicate is never matched. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -fprintf file format True; like -printf but write to file like -fprint. The output file is always created, even if the predicate is never matched. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -ls
True; list current file in ls -dils format on standard output. The block counts are of 1K blocks, unless the environment variable POSIXLY_CORRECT is set, in which case 512-byte blocks are used. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -ok command ; Like -exec but ask the user first. If the user agrees, run the command. Otherwise just return false. If the command is run, its standard input is redirected from /dev/null. The response to the prompt is matched against a pair of regular expressions to determine if it is an affirmative or negative response. This regular expression is obtained from the system if the ‘POSIXLY_CORRECT’ environment variable is set, or otherwise from find‘s message translations. If the system has no suitable definition, find‘s own definition will be used. In either case, the interpretation of the regular expression itself will be affected by the environment variables ‘LC_CTYPE’ (character classes) and ‘LC_COLLATE’ (character ranges and equivalence classes). -okdir command ; Like -execdir but ask the user first in the same way as for -ok. If the user does not agree, just return false. If the command is run, its standard input is redirected from /dev/null. -print
True; print the full file name on the standard output, followed by a newline. If you are piping the output of find into another program and there is the faintest possibility that the files which you are searching for might contain a newline, then you should seriously consider using the -print0 option instead of -print. See the UNUSUAL FILENAMES section for information about how unusual characters in filenames are handled. -print0 True; print the full file name on the standard output, followed by a null character (instead of the newline character that -print uses). This allows file names that contain newlines or other types of white space to be correctly interpreted by programs that process the find output. This option corresponds to the -0 option of xargs. -printf format True; print format on the standard output, interpreting ‘’ escapes and ‘%’ directives. Field widths and precisions can be specified as with the ‘printf’ C function. Please note that many of the fields are printed as %s rather than %d, and this may mean that flags don’t work as you might expect. This also means that the ‘-‘ flag does work (it forces fields to be left-aligned). Unlike -print, -printf does not add a newline at the end of the string. The escapes and directives are: a
Stop printing from this format immediately and flush the output.
Источник
Below is a partial list of more common Linux and Windows operating system error codes.
The perror tool can be used to find the error message which is associated with a given error code.
| Number | Error Code | Description |
|---|---|---|
| 1 | EPERM | Operation not permitted |
| 2 | ENOENT | No such file or directory |
| 3 | ESRCH | No such process |
| 4 | EINTR | Interrupted system call |
| 5 | EIO | I/O error |
| 6 | ENXIO | No such device or address |
| 7 | E2BIG | Argument list too long |
| 8 | ENOEXEC | Exec format error |
| 9 | EBADF | Bad file number |
| 10 | ECHILD | No child processes |
| 11 | EAGAIN | Try again |
| 12 | ENOMEM | Out of memory |
| 13 | EACCES | Permission denied |
| 14 | EFAULT | Bad address |
| 15 | ENOTBLK | Block device required |
| 16 | EBUSY | Device or resource busy |
| 17 | EEXIST | File exists |
| 18 | EXDEV | Cross-device link |
| 19 | ENODEV | No such device |
| 20 | ENOTDIR | Not a directory |
| 21 | EISDIR | Is a directory |
| 22 | EINVAL | Invalid argument |
| 23 | ENFILE | File table overflow |
| 24 | EMFILE | Too many open files |
| 25 | ENOTTY | Not a typewriter |
| 26 | ETXTBSY | Text file busy |
| 27 | EFBIG | File too large |
| 28 | ENOSPC | No space left on device |
| 29 | ESPIPE | Illegal seek |
| 30 | EROFS | Read-only file system |
| 31 | EMLINK | Too many links |
| 32 | EPIPE | Broken pipe |
| 33 | EDOM | Math argument out of domain of func |
| 34 | ERANGE | Math result not representable |
| 35 | EDEADLK | Resource deadlock would occur |
| 36 | ENAMETOOLONG | File name too long |
| 37 | ENOLCK | No record locks available |
| 38 | ENOSYS | Function not implemented |
| 39 | ENOTEMPTY | Directory not empty |
| 40 | ELOOP | Too many symbolic links encountered |
| 42 | ENOMSG | No message of desired type |
| 43 | EIDRM | Identifier removed |
| 44 | ECHRNG | Channel number out of range |
| 45 | EL2NSYNC | Level 2 not synchronized |
| 46 | EL3HLT | Level 3 halted |
| 47 | EL3RST | Level 3 reset |
| 48 | ELNRNG | Link number out of range |
| 49 | EUNATCH | Protocol driver not attached |
| 50 | ENOCSI | No CSI structure available |
| 51 | EL2HLT | Level 2 halted |
| 52 | EBADE | Invalid exchange |
| 53 | EBADR | Invalid request descriptor |
| 54 | EXFULL | Exchange full |
| 55 | ENOANO | No anode |
| 56 | EBADRQC | Invalid request code |
| 57 | EBADSLT | Invalid slot |
| 59 | EBFONT | Bad font file format |
| 60 | ENOSTR | Device not a stream |
| 61 | ENODATA | No data available |
| 62 | ETIME | Timer expired |
| 63 | ENOSR | Out of streams resources |
| 64 | ENONET | Machine is not on the network |
| 65 | ENOPKG | Package not installed |
| 66 | EREMOTE | Object is remote |
| 67 | ENOLINK | Link has been severed |
| 68 | EADV | Advertise error |
| 69 | ESRMNT | Srmount error |
| 70 | ECOMM | Communication error on send |
| 71 | EPROTO | Protocol error |
| 72 | EMULTIHOP | Multihop attempted |
| 73 | EDOTDOT | RFS specific error |
| 74 | EBADMSG | Not a data message |
| 75 | EOVERFLOW | Value too large for defined data type |
| 76 | ENOTUNIQ | Name not unique on network |
| 77 | EBADFD | File descriptor in bad state |
| 78 | EREMCHG | Remote address changed |
| 79 | ELIBACC | Can not access a needed shared library |
| 80 | ELIBBAD | Accessing a corrupted shared library |
| 81 | ELIBSCN | .lib section in a.out corrupted |
| 82 | ELIBMAX | Attempting to link in too many shared libraries |
| 83 | ELIBEXEC | Cannot exec a shared library directly |
| 84 | EILSEQ | Illegal byte sequence |
| 85 | ERESTART | Interrupted system call should be restarted |
| 86 | ESTRPIPE | Streams pipe error |
| 87 | EUSERS | Too many users |
| 88 | ENOTSOCK | Socket operation on non-socket |
| 89 | EDESTADDRREQ | Destination address required |
| 90 | EMSGSIZE | Message too long |
| 91 | EPROTOTYPE | Protocol wrong type for socket |
| 92 | ENOPROTOOPT | Protocol not available |
| 93 | EPROTONOSUPPORT | Protocol not supported |
| 94 | ESOCKTNOSUPPORT | Socket type not supported |
| 95 | EOPNOTSUPP | Operation not supported on transport endpoint |
| 96 | EPFNOSUPPORT | Protocol family not supported |
| 97 | EAFNOSUPPORT | Address family not supported by protocol |
| 98 | EADDRINUSE | Address already in use |
| 99 | EADDRNOTAVAIL | Cannot assign requested address |
| 100 | ENETDOWN | Network is down |
| 101 | ENETUNREACH | Network is unreachable |
| 102 | ENETRESET | Network dropped connection because of reset |
| 103 | ECONNABORTED | Software caused connection abort |
| 104 | ECONNRESET | Connection reset by peer |
| 105 | ENOBUFS | No buffer space available |
| 106 | EISCONN | Transport endpoint is already connected |
| 107 | ENOTCONN | Transport endpoint is not connected |
| 108 | ESHUTDOWN | Cannot send after transport endpoint shutdown |
| 109 | ETOOMANYREFS | Too many references: cannot splice |
| 110 | ETIMEDOUT | Connection timed out |
| 111 | ECONNREFUSED | Connection refused |
| 112 | EHOSTDOWN | Host is down |
| 113 | EHOSTUNREACH | No route to host |
| 114 | EALREADY | Operation already in progress |
| 115 | EINPROGRESS | Operation now in progress |
| 116 | ESTALE | Stale NFS file handle |
| 117 | EUCLEAN | Structure needs cleaning |
| 118 | ENOTNAM | Not a XENIX named type file |
| 119 | ENAVAIL | No XENIX semaphores available |
| 120 | EISNAM | Is a named type file |
| 121 | EREMOTEIO | Remote I/O error |
| 122 | EDQUOT | Quota exceeded |
| 123 | ENOMEDIUM | No medium found |
| 124 | EMEDIUMTYPE | Wrong medium type |
| 125 | ECANCELED | Operation Canceled |
| 126 | ENOKEY | Required key not available |
| 127 | EKEYEXPIRED | Key has expired |
| 128 | EKEYREVOKED | Key has been revoked |
| 129 | EKEYREJECTED | Key was rejected by service |
| 130 | EOWNERDEAD | Owner died |
| 131 | ENOTRECOVERABLE | State not recoverable |
| Number | Error Code | Description |
|---|---|---|
| 1 | ERROR_INVALID_FUNCTION | Incorrect function. |
| 2 | ERROR_FILE_NOT_FOUND | The system cannot find the file specified. |
| 3 | ERROR_PATH_NOT_FOUND | The system cannot find the path specified. |
| 4 | ERROR_TOO_MANY_OPEN_FILES | The system cannot open the file. |
| 5 | ERROR_ACCESS_DENIED | Access is denied. |
| 6 | ERROR_INVALID_HANDLE | The handle is invalid. |
| 7 | ERROR_ARENA_TRASHED | The storage control blocks were destroyed. |
| 8 | ERROR_NOT_ENOUGH_MEMORY | Not enough storage is available to process this command. |
| 9 | ERROR_INVALID_BLOCK | The storage control block address is invalid. |
| 10 | ERROR_BAD_ENVIRONMENT | The environment is incorrect. |
| 11 | ERROR_BAD_FORMAT | An attempt was made to load a program with an incorrect format. |
| 12 | ERROR_INVALID_ACCESS | The access code is invalid. |
| 13 | ERROR_INVALID_DATA | The data is invalid. |
| 14 | ERROR_OUTOFMEMORY | Not enough storage is available to complete this operation. |
| 15 | ERROR_INVALID_DRIVE | The system cannot find the drive specified. |
| 16 | ERROR_CURRENT_DIRECTORY | The directory cannot be removed. |
| 17 | ERROR_NOT_SAME_DEVICE | The system cannot move the file to a different disk drive. |
| 18 | ERROR_NO_MORE_FILES | There are no more files. |
| 19 | ERROR_WRITE_PROTECT | The media is write protected. |
| 20 | ERROR_BAD_UNIT | The system cannot find the device specified. |
| 21 | ERROR_NOT_READY | The device is not ready. |
| 22 | ERROR_BAD_COMMAND | The device does not recognize the command. |
| 23 | ERROR_CRC | Data error (cyclic redundancy check). |
| 24 | ERROR_BAD_LENGTH | The program issued a command but the command length is incorrect. |
| 25 | ERROR_SEEK | The drive cannot locate a specific area or track on the disk. |
| 26 | ERROR_NOT_DOS_DISK | The specified disk or diskette cannot be accessed. |
| 27 | ERROR_SECTOR_NOT_FOUND | The drive cannot find the sector requested. |
| 28 | ERROR_OUT_OF_PAPER | The printer is out of paper. |
| 29 | ERROR_WRITE_FAULT | The system cannot write to the specified device. |
| 30 | ERROR_READ_FAULT | The system cannot read from the specified device. |
| 31 | ERROR_GEN_FAILURE | A device attached to the system is not functioning. |
| 32 | ERROR_SHARING_VIOLATION | The process cannot access the file because it is being used by another process. |
| 33 | ERROR_LOCK_VIOLATION | The process cannot access the file because another process has locked a portion of the file. |
| 34 | ERROR_WRONG_DISK | The wrong diskette is in the drive. Insert %2 (Volume Serial Number: %3) into drive %1. |
| 36 | ERROR_SHARING_BUFFER_EXCEEDED | Too many files opened for sharing. |
| 38 | ERROR_HANDLE_EOF | Reached the end of the file. |
| 39 | ERROR_HANDLE_DISK_FULL | The disk is full. |
| 87 | ERROR_INVALID_PARAMETER | The parameter is incorrect. |
| 112 | ERROR_DISK_FULL | The disk is full. |
| 123 | ERROR_INVALID_NAME | The file name, directory name, or volume label syntax is incorrect. |
| 1450 | ERROR_NO_SYSTEM_RESOURCES | Insufficient system resources exist to complete the requested service. |
Introduction to Linux Error codes
In the Linux operating system, we are working on many components. While working, we are getting lots of errors. The same errors can be acknowledged by the Linux error codes. There are different error codes available as per the execution error. We can capture the error code with the help of the “echo” command also.
To fix the error message in the Linux level jobs/query or application-level job, it is mandatory that we need to understand the nature of the error, the error description, and the error code. Accordingly, we can fix the application or job on the Linux level.
The error code utility i.e., “errno” is written by the Lars Wirzenius.
Syntax of Error Codes
errno [ OPTION ] [ STRING ]
echo $?
- errno: We can use the “errno” keyword in the syntax or command. It will take the two arguments as access OPTION and the string. As per the provided arguments, it will provide the error information as per the string or the error code.
- OPTION: We can provide the different flags as options that are compatible with the “errno” command.
- STRING: We can provide the short string as per the “error” define. It will provide the error information concerning the provided string.
- echo $?: The echo command will also provide the error code. We need to use the “?” symbol with the echo command.
How Linux Error Codes Works?
In Linux, we are having a total of 134 error codes. Every error message or the failure in the Linux environment, it will have their error code. With the help of error code, we can fetch the error description and help to fix the issue or error message. If we will keep the same error message as it is then it will be a big impact on the server level.
When we are executing any command or job on the Linux level without any error then it will be fine. But if the Linux command will not be executed properly then the Linux compiler will notify with the relevant error message to the login user.
Below are the lists of error code information available,
| Sr No | Error Code | Error Number | Error Description |
| 1 | EPERM | 1 | It will print the error message if the operation is not permitted. |
| 2 | ENOENT | 2 | It will print the error message if there are no such files or directory exists. |
| 3 | ESRCH | 3 | It will print the error message if there is no such process exists. |
| 4 | EINTR | 4 | It will print the error message if any interrupted system calls. |
| 5 | EIO | 5 | It will print the error message if it is any input/output error. |
| 6 | ENXIO | 6 | It will print the error message if there is no such device or address exists. |
| 7 | E2BIG | 7 | It will print the error message if the argument list is too long. |
| 8 | ENOEXEC | 8 | It will print the error message if there is an exec format error. |
| 9 | EBADF | 9 | It will print the error message in it is a bad file descriptor. |
| 10 | ECHILD | 10 | It will print the error message if there are no child process exits. |
Examples to implement Linux Error codes
Here are the following examples mention below
Examples #1 – Print the List
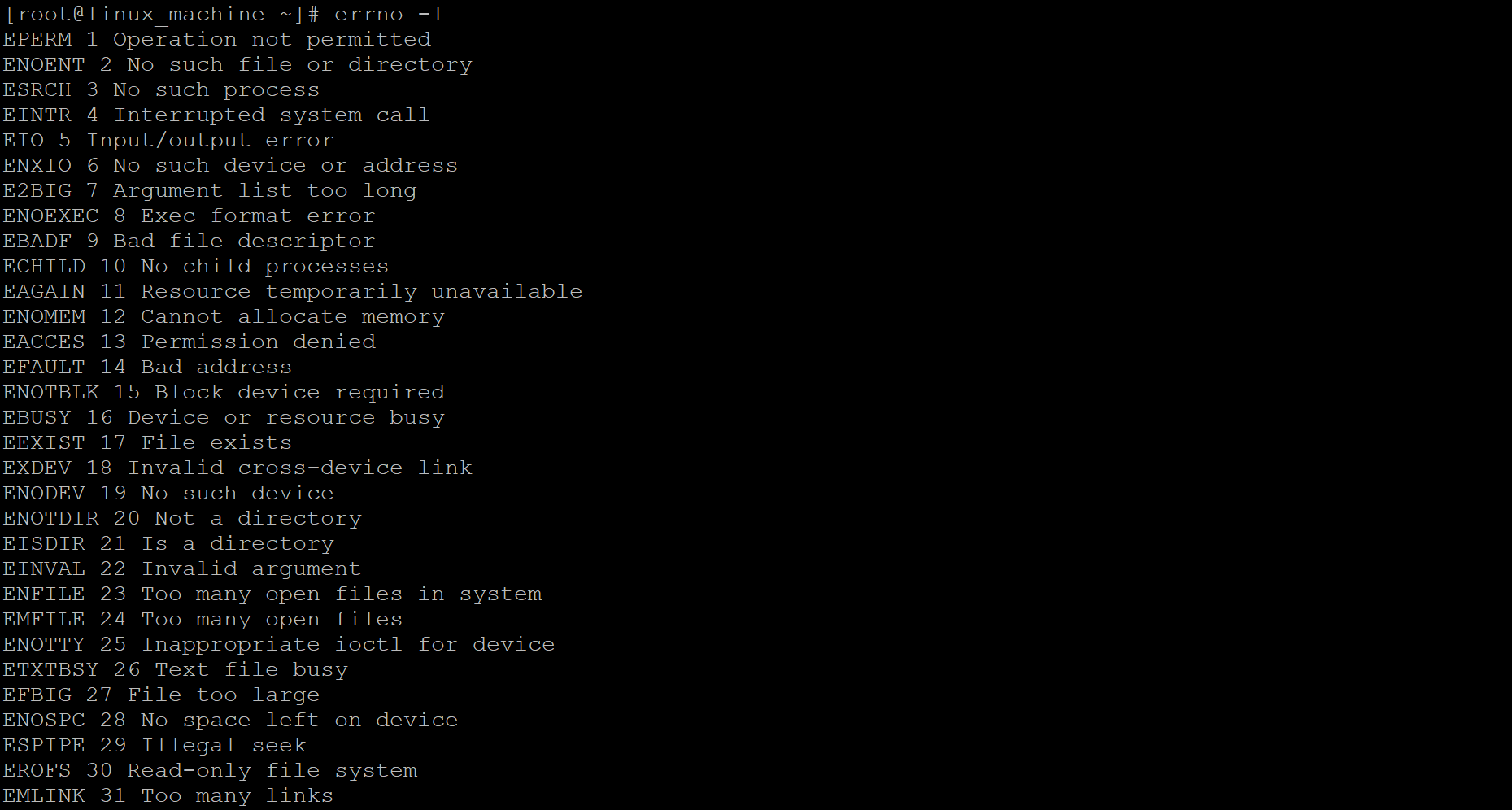
The “errno” utility is a very simple and common way to check the list of error codes in a Linux environment. It will print all the list of error codes with the error number and error description.
Command :
errno -l
Explanation :
As per the above command, we can print all the list of error codes available in the Linux environment. It will print the details information of error code like an error code name, error code number, and the description of the error code.
Output :
Example #2 – Information of Individual Error Number
By default, we are getting all the list of error code information. But we can also get the individual error number information as well.
Command:
errno 9
Explanation :
In the “errno” utility, we can get the specific information error information with the help of an error number. We have used the error no “9” and get the information of “error number 9” only.
Output :
Example #3 – Information of Individual Error Name
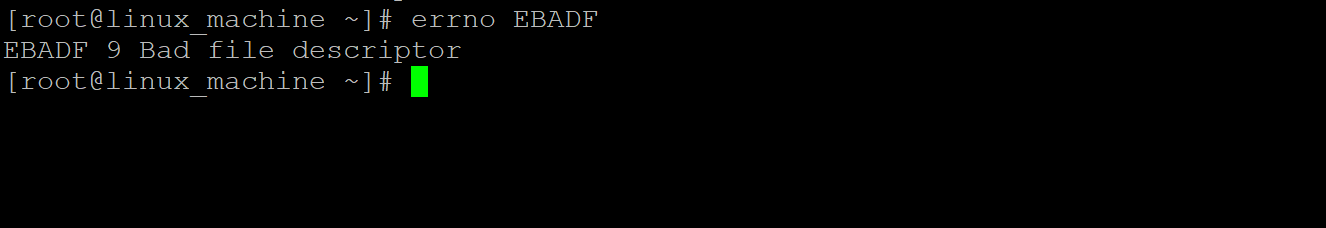
In the error codes, we can get the individual error number information. Similarly, we are having the functionality to print the individual error name information.
Command :
errno EBADF
Explanation :
As per the above command, we can get the specific information error information with the help of the error name. We have used the error name “EBADF” and get the information of “error name (EBADF)” only.
Output :
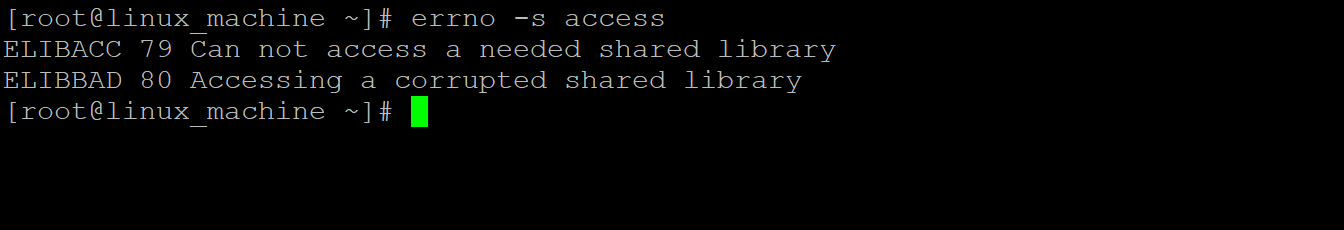
Example #4 – Error Code Information from the Input String
In the Linux environment, we are having the functionality to get the error code and error number information from the input string. We need to use the “-s” option with the “errno” utility.
Note: we need to provide the relevant input string as an input to the “errno” command.
Command :
errno -s access
Explanation :
When we don’t know the exact error number or name then we can use the relevant string to identify the error code and description of it. We have used the “access” string and get the related information of access.
Output :
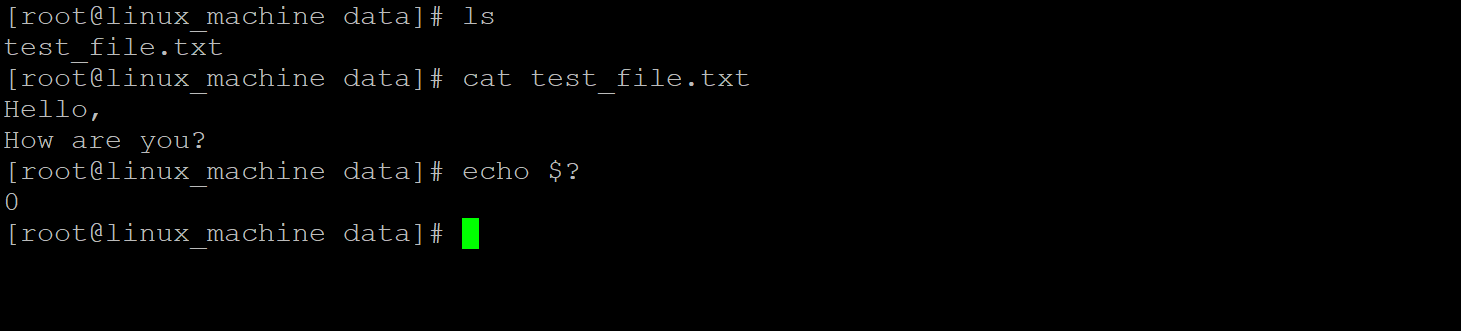
Example #5 – Get the Error Code Information with “echo” Command
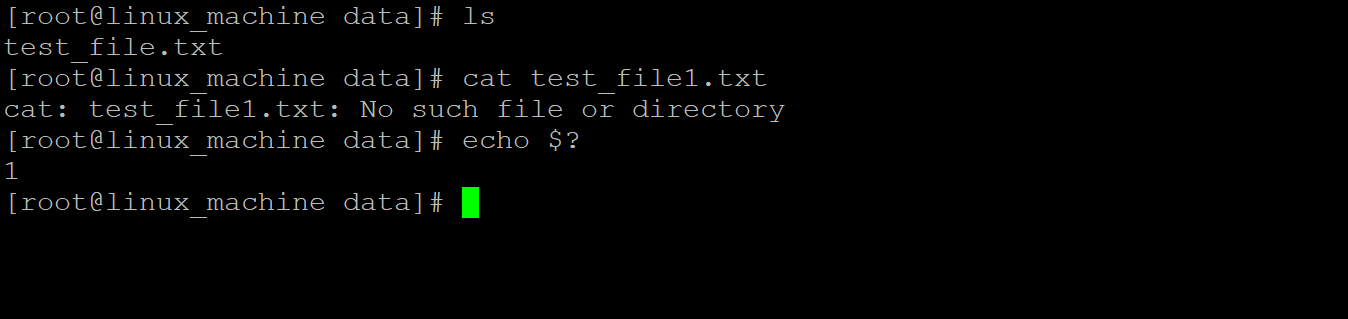
In the Linux ecosystem, we are having the functionality to check the quick error code information via the “echo” command. If it will return the “0” output then the command was executed fine. If it will return the output value except “0” then there are some issues in the command or job.
Command :
cat test_file.txt
echo $?
Explanation :
In screenshot 1 (a), we are getting the echo command output as “0”. Hence, it is an indication of the proper execution of the command. In screenshot 1 (b), we are getting the echo command output as “1”. Because the previous command was not executed successfully.
Output :
Screenshot 1 (a)
Screenshot 1 (b)
Conclusion
We have seen the uncut concept of “Linux Error Codes” with the proper example, explanation, and command with different outputs. Every error code is having its unique error name and the error number. The error codes are very important in terms of fixing the issues on command or job level.
Recommended Articles
This is a guide to Linux Error Codes. Here we discuss How Linux Error Codes Works and Examples along with the commands and outputs. You may also have a look at the following articles to learn more –
- Linux Mount Command
- Linux Inode
- Linux tac
- Linux Free Command