Содержание
- Doh server connection error connection refused mikrotik
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Re: DoH server connection error, idle time out connecting
- Doh server connection error connection refused mikrotik
- Re: DoH server connection error
- Re: DoH server connection error
- Re: DoH server connection error
- Re: DoH server connection error
- MikroTik поддерживает DNS over HTTPS (DoH)
- MikroTik поддерживает DNS over HTTPS (DoH) : 36 комментариев
- Добавить комментарий Отменить ответ
- Doh server connection error connection refused mikrotik
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
- Re: Add DNS over HTTPS (DoH) support
Doh server connection error connection refused mikrotik
Wed Jun 10, 2020 1:15 pm
Re: DoH server connection error, idle time out connecting
Wed Jun 10, 2020 2:28 pm
Probaly problem with your connection, but likely these short time errors you will not notice for normal use.
You can also do DoH verification:
Re: DoH server connection error, idle time out connecting
Wed Jun 10, 2020 9:17 pm
Re: DoH server connection error, idle time out connecting
Wed Jun 10, 2020 9:29 pm
Re: DoH server connection error, idle time out connecting
Wed Jun 10, 2020 11:55 pm
how about this error
dns,error DoH server connection error: remote disconnected while in HTTP exchange
Re: DoH server connection error, idle time out connecting
Wed Jun 10, 2020 11:57 pm
Re: DoH server connection error, idle time out connecting
Fri Nov 13, 2020 10:43 pm
After trying to setup DOH on 6.47 (stable) and testing firlware on hex, using opendns, clouflare and google dns i always experience the same behavior. (settings up proper static DNS for the doh server, then ensuring SSL root cert is added)
Setup works very well for 45 minutes to 1h30 and then no more resolution is done. I can reboot the hex and it works again, but after 45 min to 1h30 again it don’t work again.
Log show server time out, while I can access it via IP adress. flushing the DNS cache doesn’t help.
Re: DoH server connection error, idle time out connecting
Mon Dec 14, 2020 11:25 am
Re: DoH server connection error, idle time out connecting
Wed Jan 06, 2021 5:06 am
Re: DoH server connection error, idle time out connecting
Tue Feb 16, 2021 10:23 am
Same issue here. Not any fix yet?
DoH server connection error, idle time out connecting.
Re: DoH server connection error, idle time out connecting
Sat Feb 27, 2021 5:34 pm
Re: DoH server connection error, idle time out connecting
Thu Mar 11, 2021 6:35 pm
I’ve recently tried DoH feature and this error message appears from time to time depending on load.
If you enable logs for dns you can see something like that:
612 Mar/11/2021 18:18:42 memory dns, error DoH server connection error: Idle timeout — connecting
613 Mar/11/2021 18:18:42 memory dns done query: #16331 dns server failure
.
520 Mar/11/2021 18:18:37 memory dns query from 10.10.100.32: #16331 www.google.com. A
Just part of the queries fails. It stay so in any configuration: with google or cloudflare, with or w/o «Verify DoH Certificate», w/ and w/o static records for DoH servers etc.
After removing DoH server error logs disappear.
my fw is 6.48.1
Re: DoH server connection error, idle time out connecting
Mon Jun 21, 2021 7:41 pm
Same issue. HEX S stable 6.48.3, or longterm 6.47.10. Reboot router resolve issue for a time about few hours, maybe less winbox stuck on «Logining. «. Only reboot with power cycle can resolve.
RouterOS developers, please pay attention to this bug (stable and longterm branches). It’s kind of memory leak or something.
In log a lot of:
DoH server connection error: SSL: handshake timed out (6)
DoH server connection error: resolving error
l2tp connections with ipsec stop working and can’t reconnect without reboot with messages in log:
initiator can’t find identity for peer:
Источник
Doh server connection error connection refused mikrotik
Sat Oct 16, 2021 4:32 pm
Re: DoH server connection error
Sun Oct 17, 2021 2:25 am
Re: DoH server connection error
Thu Oct 28, 2021 2:33 pm
Re: DoH server connection error
Mon Nov 08, 2021 12:31 pm
Re: DoH server connection error
Mon Aug 01, 2022 6:23 pm
I’m having the same issue
Lots of entries in the log
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:15:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:16:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
19:17:48 dns,error DoH server connection error: resolving error
DNS seems to work, and there are cached entries, but not sure what this error relates too. Every now and then I get a failed page load and a refresh solved that so I do think there is an issue
Источник
MikroTik поддерживает DNS over HTTPS (DoH)
Начиная со стабильной версии 6.47 MikroTik поддерживает DNS over HTTPS (DoH).
Далее краткая инструкция по настройке с проверкой сертификата сервера на примере Cloudflare.
1) Импортируем сертификат DigiCert Global Root CA в хранилище сертификатов роутера:
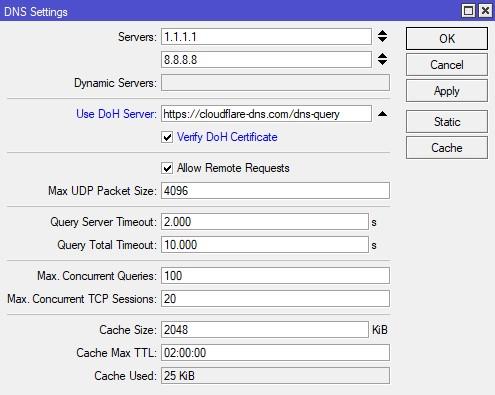
2) В поле Use DoH Server пишем https://1.1.1.1/dns-query и ставим галку Verify DoH Certificate:
3) Убираем все существующие DNS-сервера, чтобы поля Servers и Dynamic Servers (из DHCP Client) были пустыми и все запросы шли через DNS over HTTPS (не обязательно для 6.47.1+).
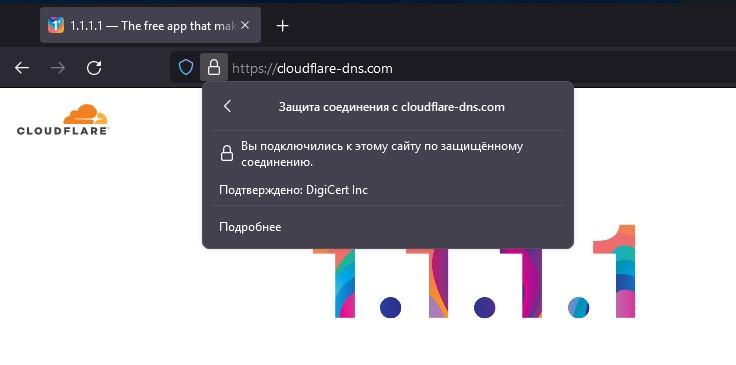
Проверить корректность настройки можно на странице https://www.cloudflare.com/ssl/encrypted-sni
MikroTik поддерживает DNS over HTTPS (DoH) : 36 комментариев
DoH server connection error: SSL: handshake failed: unable to get local issuer certificate (6)
в логах такая ошибка
Видимо вы не добавили сертификат из первого шага.
CF сломал https://1.1.1.1/dns-query , а так всё хорошо начиналось…
Нет, всё работает, видимо вы не настоящий админ.
Возвращение 400 это работает называется?
400 = 200 уже?
Его нужно не в браузере открывать, а в микротике прописывать, у меня до сих пор работает.
Он лишь в Curl’е иногда проскакивает что работает.
В микротике тоже отказывается.
У них в DoH мане теперь написано что нужно указывать домен, т.е. что бы юзать DoH, нужно юзать чей то DNS.
У гугла та же история теперь, по этому DoH в той самой изначальной идее уже больше мёртв, чем жив, т.к. остальную мелочь из поставщиков DoH не рассматриваем.
Укажите домен статикой будет вам счастье.
И искать потом приключения на удалённых узлах, когда он вдруг сменится?
Хороший такой совет.
перестало сегодня работать
DoH server connection error: SSL: handshake failed: certificate is not yet valid (6)
DoH server connection error: Connection refused
не смог заставить работать
и серт перекачал
Как вариант, снимите галку с пункта verify-doh-cert=
Спасибо за инструкцию.
Всё работает как надо.
После я усложнил схему. Я ещё и WARP Cloudflare подключил через WireGuard (в RouterOS 7.1) и смаршрутизировал запросы на 1.1.1.1 в тоннель.
класс. Поделитесь конфигом?)
Там его нужно генерировать через неофициальный cli клиент, вот инструкция: https://moonback.ru/page/keenetic-warp
Вот клиент: https://github.com/ViRb3/wgcf
Добавить комментарий Отменить ответ
Источник
Doh server connection error connection refused mikrotik
Mon Apr 02, 2018 4:57 pm
Add DNS over HTTPS (DoH) client to RouterOS. This will significantly improve the privacy of network users and devices (especially when RouterOS device serves as DNS cache/recursive resolver).
While experimental protocol, the infrastructure is already provided by 2 of the biggest 4 recursive DNS providers and provides significant benefits in practice.
Re: Add DNS over HTTPS (DoH) support
Mon Apr 02, 2018 6:18 pm
Re: Add DNS over HTTPS (DoH) support
Mon Apr 02, 2018 6:47 pm
There’s also DNS over TLS (RFC7858).
But when you look how much attention MikroTik gave to DNS in the past (there’s nothing over basic functionality and one could argue that even some basics are missing), I don’t see any of this happening anytime soon.
Re: Add DNS over HTTPS (DoH) support
Mon Apr 02, 2018 9:24 pm
Add DNS over HTTPS (DoH) client to RouterOS. This will significantly improve the privacy of network users and devices (especially when RouterOS device serves as DNS cache/recursive resolver).
While experimental protocol, the infrastructure is already provided by 2 of the biggest 4 recursive DNS providers and provides significant benefits in practice.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Wed Feb 13, 2019 11:09 am
Can anybody from MikroTik reply on this thread?
Re: Add DNS over HTTPS (DoH) support
Sun Apr 07, 2019 12:32 am
Re: Add DNS over HTTPS (DoH) support
Sun Apr 07, 2019 4:45 pm
Re: Add DNS over HTTPS (DoH) support
Tue Jul 16, 2019 11:11 am
Re: Add DNS over HTTPS (DoH) support
Mon Sep 09, 2019 4:26 pm
Re: Add DNS over HTTPS (DoH) support
Mon Sep 09, 2019 5:06 pm
Re: Add DNS over HTTPS (DoH) support
Mon Sep 09, 2019 9:16 pm
«Funny» thing is that implementation in browser (as Mozilla is pushing now; or generally per-application) makes the least sense of all. Either I want to protect whole network, so I need it on router. Or I want to protect computer (better for mobile devices, because with them I don’t always have control over network) and then I need system-wide solution there. Not only browsers use DNS.
And the idea with canary domain and ability to tell browser this way to not use DoH, it’s not hard to predict how it will go, is it? If I’m the bad guy who wants to mess with users’ DNS, of course I will use that.
Re: Add DNS over HTTPS (DoH) support
Thu Sep 12, 2019 1:10 pm
Re: Add DNS over HTTPS (DoH) support
Thu Sep 12, 2019 4:26 pm
Yes that is why there is some discussion about this.
However, be warned that this «canary domain», as Sob already writes too, is likely to go away in the future once hackers who want to play man-in-the-middle on DNS see this, implement the canary domain, Mozilla finds out about that, and decides to disable that feature (at least by default).
You should prepare for the situation that you get less and less control over what happens on your network!
All wellknown ways of peeking in traffic to implement policies (like website blocking, or QoS implementations that e.g. try to set a lower priority for some traffic) are going to be taken away from you by those browser developers.
It is not only DNS over HTTPS. Firefox will also start to do all web browsing traffic over a «VPN» between the browser and some Cloudflare service, running over HTTPS.
So no way to block sites by IP address anymore! (or to put lower priority on some websites)
You will only see a lot of sessions to a single HTTPS service and no more way to get insight in what is happening over those sessions.
Re: Add DNS over HTTPS (DoH) support
Tue Nov 19, 2019 4:03 pm
Re: Add DNS over HTTPS (DoH) support
Tue Nov 19, 2019 4:15 pm
Re: Add DNS over HTTPS (DoH) support
Wed Nov 20, 2019 3:58 pm
Re: Add DNS over HTTPS (DoH) support
Wed Nov 20, 2019 5:08 pm
Re: Add DNS over HTTPS (DoH) support
Wed Nov 20, 2019 5:37 pm
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 3:47 pm
I’d like to append my request for RoS DoH support as well.
We should not have to trade security for usability when the need arises.
To elaborate:
I am currently intercepting all DNS server requests, redirecting them to the router itself (RB4011), using static DNS at router level to block many social sites as well as redirect some domains to internal servers, while all allowed requests are forwarded to 1.1.1.1 or 8.8.8.8.
If I use DoH at browser level — I get security but I can no longer redirect the domains.
When Windows 10 starts recognizing DoH enabled DNS servers, the manual rules won’t apply either.
The only way I see is for RoS to intoduce DoH support and transparently resolve using DoH enabled DNS servers.
Default case: DoH is enabled in neither browser or OS.
- DNS requests are not secure .
- Router DNS cache is used .
- Router static DNS entries are honored .
Case 1: No DoH support at router level. Browser uses DoH:
- Browser DNS requests are secure .
- OS DNS requests are not secure .
- Router DNS cache is not used for browser requests.
- Router static DNS entries are ignored for browser requests.
Case 2: No DoH support at router level. OS supports DoH.
(Windows 10 DNS client is said to support DoH natively for DoH enabled DNS servers in the next major update)
- Windows uses DoH.
- All DNS requests are secure .
- Router DNS cache is not used .
- Router static DNS entries are ignored .
Ideal case: If Mikrotik adds native DoH support to RoS:
- Home network (Browser, OS, IOT devices) > DNS req. > RouterOS > DoH req. > Cloudflare / Google
- All DNS requests are secure .
- Router DNS cache is used .
- Router static DNS entries are honored .
- Devices do not need to support DoH directly to benefit from it.
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 5:48 pm
DoH uses HTTPS as a transport, so transparent redirects are not gonna be possible.
DoH has nothing to do with security. Really nothing. Some believe it has something to do with confidentiality (which is not the same as security), though this statement is also arguable.
And. Yes, I would also like to ask for a builtin way (like the ability to return NXDOMAIN for a given domain) to tell clients to NOT use DoH.
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 7:34 pm
Using a pi-hole here and have just, put a small doh-proxy in front. Wotk great and I have TLS 1.3 secure connection.
The router blocks on IP basis DoH addresses that I know of, so that is cut off. Normal DNS requests are delivered at Pi-hole by the router. DoT is next as proxy ior Pi-hole.
The DNS server of RouterOS limited and if you want more, get other solution.
Pi-hole is also a development version that tackles the CNAME cloaking of third party tracking and cookies behaving as first party to avoid detection.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 8:21 pm
It would be transparent to the client devices which are still using vanilla DNS requests — not the router.
Upon client request — the router does the resolve via DOH, caches it and serves it back as a «vanilla» dns response to the client.
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 9:30 pm
You transfer the possibility for your ISP (a party you selected yourself and probably know well, and who you pay for your internet service) to sniff the DNS traffic to another party who you do not know, you do not know where they are located, and you do not pay them money for the service directly (so they have to earn money from your requests in a different way).
You choose what you prefer.
it is similar to using a VPN (in the newfangled sense of the word). It may prevent your ISP from sniffing, but you transfer that possibility to the VPN company.
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 11:27 pm
It would be up to you what DOH resolver you’d use, it could be something public, some trusted commercial service, your own server somewhere else, anything. So this part is fine, but what you’ll achieve is different matter.
If you want to keep DNS queries secret, there’s currently no point, because you’ll most likely use them to connect to some website and SNI will tell anyone on the way to which one.
It will prevent tampering, so ISP will no longer be able to block something simply by blocking relevant DNS queries. That seems good at first sight. Problem is, they probably don’t do that just for fun, but often because they have to. So the result will be that they will have to find some other, much worse method.
Re: Add DNS over HTTPS (DoH) support
Wed Nov 27, 2019 11:43 pm
Server Name Indication (SNI) can be used by the client to select one of several sites on the same host, and so a different X.509 certificate can be sent depending on the hostname that was sent in the SNI extension. If the SNI extension is not sent the server’s options are to either disconnect or select a default hostname and matching certificate. The default would typically be the main site.
SNI has been made mandatory to implement in TLS 1.3 but not mandatory to use. Some sites want to encourage the use of SNI and configure a default certificate that fails WebPKI authentication when the client supports TLS 1.3. This is under the assumption that if a hostname is not sent, then it means that the client does not verify the server certificate (unauthenticated opportunistic TLS). For implementation that actually don’t send the SNI extension, but do verify the server certificate this can cause connection failures.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 1:29 am
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 3:24 pm
That the web would not work without is partially true if you look at only IPv4. With IPv6 you don’t need SNI anymore because you have huge numbers of unique IPv6 address available. I read about ESNI and it badly supported or even not supported.
If you then put your DoH sever on a IPv6 address then you could omit the SNI in your «Client Hello» to the DoH server (proxy) when using TLS 1.3.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 3:38 pm
So developing ESNI (encrypted SNI) does not make sense because usual DNS leaks the information anyway?
Your argument is nonsense and would stop any technical improvement. Let’s start to use/implement DoH now, so ESNI is the last piece of the puzzle still missing.
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 4:20 pm
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 4:47 pm
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 5:13 pm
Of course when these techniques become universally implemented, we need to make a sticky topic for the many users that come here with requests like:
— I need to block some specific website (Youtube/Facebook/whatever)
— I need to allow access to only one specific website (externally hosted company site)
— I need to limit the use of bandwidth by this or that service, e.g. operating system updates
etc. There can be a simple cooked reply stating that these things are no longer possible, and that all recipes those people find that claim to solve it do no longer work.
And also that despite information they have read elsewhere, other manufacturer’s equipment cannot do it either.
At first sight it may seem that this privacy is a good thing, but of course it will cause some things to collapse, like free Wifi for visitors and limited-bandwidth wireless internet connectivity with purposely limited usage.
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 7:28 pm
Why use a webserver. I don’t want DoH go through a webserver then a proxy and finally arrive at the DNS server and the has to the way back.
I don’t know a DNS server that offers DoH or DoT any thr proxies or loadbalancers are used.
Do away, with we have to use SNI and just have a single certificate and one addres (IPv6). leak three IPv6 address.
I suggested it earlier with Xs4all (ISP) that don’t need a fixed address to browse on the internet.
So spread traffic from costumers over many adresses and only Xs4all knows wo have that traffic back. For every visited domain the client gets a diiferent source IP on the border of inner and outer. Needs two gateways and/or VPN so that services and have a fixed adress available.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 7:33 pm
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 7:39 pm
Webservers that also hosts sites, are not needed to provide DoH.
That is born from not having good proxies.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Nov 28, 2019 9:23 pm
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 11:24 am
A DoH proxy or loadbalancers for DNS do not serve websites so have don’t a requirement to be using a SNI.
That the webservers crops up each time, is due that many used a webserver in between the client and the DNS server. This is not needed anymore now proxies can handle DoH natively.
If later we get esni makes not much difference if one block on IP addresses of yhe DoH servers.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 11:39 am
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 12:20 pm
DoH is using SNI after «Hello Client». Secondly, your ISP can’t see which domain you are requesting for an IP address in you DoH traffic. Thirdly using a VPN, the VPN provider and every device between them and destination, knows where you are going on IP address and then SNI.
SNI is used to run many services after one IP address. Running only one service behind an IP makes SNI obsolete but makes it easier to block by IP address.
We are in the Adding HTTPS DoH topic after all.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 12:45 pm
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 8:33 pm
@msatter: Let’s try once more. You want to visit https://forum.mikrotik.com. There are two steps:
1) resolve forum.mikrotik.com to numeric IP address
2) establish tcp connection to IP address from 1), negotiate encryption with server and send http request
To do 1), you have several choices. You can send traditional DNS query to port 53 and ask ISP’s server or some public one (ISP can see both). You can tunnel these queries through VPN (ISP can no longer see them, but now VPN provider can). You can be sneaky, write down the correct IP address and put it in local hosts file, this way there won’t be any DNS query leaving your computer and nobody will see it. Or you can use DoH and neither ISP nor VPN provider will see the query, because it will be encrypted. Whoever runs the DoH server will see it, obviously, but you probably trust them.
Now let’s focus on DoH. It’s DNS over HTTPS, so there’s the HTTPS part and HTTPS can use SNI to indicate target hostname. Honestly, I have no idea if DoH client uses SNI or not. But it doesn’t matter, because even if it does, it will contain the name of DoH server, parhaps something like dns01.someprovider.tld. So now ISP or VPN provider would know that you’re using DoH resolver. But hey, good news, they can’t know that you’re asking about forum.mikrotik.com.
And now the problematic part. Browser already knows the correct IP address (which forum.mikrotik.com uses). Browser opens tcp connection to this address and port 443. You’re still good, nobody knows anything about forum.mikrotik.com (not counting that they may already know that this IP address belongs to it, but the name is not mentioned anywhere). Now browser needs to get certificate from server, in order to verify that it’s really the correct one and there’s no man-in-the-middle attack going on. And bam, here comes the «bad SNI».
Browser doesn’t know what websites are hosted on target address. It can be just forum.mikrotik.com, it can be other MikroTik’s websites, or perhaps some employee can also host a personal blog about kittens there, blog.routersandkittens.com. And each of these sites can have different certificate. If you want to visit forum.mikrotik.com, it would be useless if server sends certificate for blog.routersandkittens.com. Technically, there could be one certificate valid for both, but it probably won’t be this case. Perhaps server could send both and client could choose. It would work for two hosted websites. But it could also be more than two, thousands, no problem. Server can keep sending thousands of certificates to each client.
And that’s what SNI does, as part of negotiation, client (in this case web browser) tells server «hello, I want to visit forum.mikrotik.com, would you please send me correct certificate?» And the problem is, currently used unencrypted SNI sends this greeting in readable plaintext form. So all the effort to get forum.mikrotik.com resolved secretly was for nothing, because now anyone on the way (either ISP or VPN provider) can see that you’re visiting forum.mikrotik.com.
You see the problem now, right?
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 8:55 pm
I got a little carried away and it’s too long, but two more points, just to be sure that there’s no misundertanding:
— Yes, MikroTik should add DoH client to their TODO list, because router is the right place for it.
— Users should not see DoH as magic solution for privacy, because by itself it’s not. Widespread use of encrypted SNI will help, but it’s something that will happen in future (maybe). But too many servers have unique and static IP addresses and much can still be gathered from that, so if «they» (evil hackers, government, . take your pick) are trying to get you, they probably will, even with DoH and ESNI.
Re: Add DNS over HTTPS (DoH) support
Fri Nov 29, 2019 9:39 pm
To me DoH is something that belong browers or any client software that could use it. It is there, to hide traffic between other encrypted traffic. SNI still gives away, where that encrypted traffic is heading. besides the destination IP address. You can’t change te destination address but you can change the source address to avoid trace back to the user source address.
DoT should be at home on routers as a replacement for current DNS.
If you make the source IP address variable as with CGNAT but then every different destination IP address has a different source IP addres and different return port. Kind of VPN with double NAT.
Governments won’t like it because they can only track it in the CGNAT self and ofcourse in the devices of the users.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Sat Nov 30, 2019 1:24 am
It’s slightly OT, but you’re underestimating governments. They have special powers, they can cheat, they are the ones who make rules for ISPs. Your plan to use random source addresses? It would require cooperation from ISP. Or from VPN provider, but that’s just different kind of ISP. If government doesn’t like it, they will simply say «no, that’s not allowed». There are foreign VPN providers who they can’t reach, but what stops government from making a law that would make using them illegal? It would look bad if the country claims to value freedom and such, and it’s not really needed (yet). That’s it.
The last part is very important. For example, where I live, our enlightened government decided to protect citizens from gambling, or at least that was one story. The actual implementation of that idea is a law that forces ISPs to block access to few websites. The list currently contains a little over hundered of them and most is taken by 1xbet1.com to 1xbet110.com, which I’d say tells a lot about the whole thing. And if it wasn’t absurd enough already, it’s allowed to «block» access only on DNS level and only on own resolvers (or whatever is default config given to clients). Any user is free to set some other resolver like 8.8.8.8 to bypass blocking and ISP is not responsible for that. Anyone with the slightest amount of technical knowledge can immediatelly see how the whole thing is useless. But government is happy. I don’t know, maybe it even works on average idiot who needs to be protected from gambling. But what will be next? Maybe the secret art of resolver changing will become too known and updated law will require to really block «bad» DNS queries, no matter what resolver is used? No problem, there’s already DoH. So maybe in next version, ISPs will have to block access to few well-known DoH resolvers? Block connections to gambling sites based on SNI? There’s no limit how far it can go (well, they can’t probably outlaw internet completely. at least we can’t imagine something like that now). And of course at some point, they will find other things to block, because once you start with something.
And about encrypted SNI, it has one major problem, at least current version of it. It’s optional extension and it requires extra work (to put key in DNS). Who will bother with that? It could be enough if some big players like Cloudflare do it. And if it annoys some governments, they can’t really block «half of internet» by blocking their whole network, can they? Hooray, the technology will win the fight! Erm. but for some reason my mind still brings up the famous https://xkcd.com/538/.
Re: Add DNS over HTTPS (DoH) support
Sat Nov 30, 2019 11:56 am
I get 1208925819614629174706177 IP addresses from my ISP (1208925819614629174706176 of them are IPv6 and 1 is IPv4) but of course it is completely useless to vary between them because the 1208925819614629174706176 IPv6 addresses are all in a single block that is easily traceable to me.
And as I have already written: using multiple IPv6 addresses to separate websites running on the same server: not going to happen. It would have to be done by EVERY webserver in the world before SNI can be omitted on IPv6 requests, and even then the webbrowser may not even know if the request is over IPv6.
For example, on our company network the LAN is only IPv4, there is no routing to internet, there is a proxy server for web access, and it has IPv4 and IPv6 externally.
The browsers connect the proxy using IPv4, they send their «CONNECT www.example.com:443» request to the proxy, which resolves the domain name and connects it (IPv6 preferred), then the browser starts its TLS handshake over this tunnel. The browser has no way of knowing whether the connection to the website is IPv4 or IPv6, so it can only assume it has to send the SNI. Which could then be picked out by an external observer on the internet (the proxy log of course already contains de requested domainname, it does not require SNI for that).
And as Sob writes, there sometimes are «legitimate» reasons to block some site, either by law (because the visited site performs illegal activities) or by local policy (e.g. because some workplace does not want the employees to spend their time on certain activities, or because parents want to hide some content from their children).
We should understand that the ever progressing move towards privacy on the internet does not have only advantages. There sometimes are reasons to block certain things and there sometimes is a requirement to research some (past) activities that have happened on a network or user, and taking away that possibility will certainly lead to more abuse and crime. Which in turn may lead to more drastic action by frustrated governments.
Re: Add DNS over HTTPS (DoH) support
Sat Nov 30, 2019 3:43 pm
1208925819614629174706177 Is not important you need only on at your home or firm if you don’t offer services.
Example you connect to example.com and your IPv6 or IPv4 is converted to source address 1.2.3.4 port 1000. At same time sob connects out and he receives source address 1.2.3.4 port 1010 and I connect also out and get source address 1.2.3.4 and port 1020. Traffic is separated and the ISP knows which client address belongs to which source address and port.
If you have spare IP addresses then you can also vary with that.
The ISP still can still block destination addresses. You can’t offer services unless your ISP gives you a virtual IP or dedicated IP on IPv4. On IPv6 you are free to offer any IP in your block.
I would prefer also secure connection proxy in front of many services and SAN (alternative name) allows that with only one certificate. A webserver does only have to do what it is designed for, serving pages.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Sat Nov 30, 2019 6:58 pm
So in a way, you must like current IPv4 shortage and ISPs who use NAT to hide multiple customers behind common public address. Hundered customers, one address, and evil website tracing users doesn’t know who is who (it probably does anyway because of cookies or browser fingerprinting, but not just from IP address). But nosy government is still fine, because it can simply require ISPs to keep records about who was connecting where.
And the proxy, it’s what e.g. Cloudflare does. You as client are connecting to their servers and they are forwarding traffic to real servers with content. I do believe that they can make a difference, for a while at least. The local government of random country has no power over them and if you successfully hide DNS queries and they have ESNI, you’re safe. Blocking their whole network would be too extreme. But it won’t be one annoyed government, it will be many of them. They will eventually come together and figure something out. A global regulation, marketed as a noble cause, some variation of «we can’t let criminals be anonymous». It won’t be easy, but nobody really believes that they would just give up.
Re: Add DNS over HTTPS (DoH) support
Sun Jan 12, 2020 5:02 am
Almost 12 months are passed and no information. no plans, no progress.
I need to make DNS queries outside local network via secured channel to improve confidentiality.
In my scenario Mikrotik router is used as DNS cache.
So all local DNS queries are made using that Mikrotik server.
Why is it not possible to make external DNS calls using DoH?
All clients connected to local network will give encrypted DNS communication without need to setup each client (or even software).
Hey Mikrotik guys, please tell us why not?
Re: Add DNS over HTTPS (DoH) support
Sun Jan 12, 2020 9:52 am
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 12:24 pm
Agreed, DOH is BULL.
The only things it archieves are:
1- completely breaks local caching, therefore causing problems in networks with high latency. (basically everyone on radio.)
2- ensures no one besides google will have visibility on DNS-query statistics (google collects its data chrome, that’s why they pledge no data collection server-side. they already have all the data they want from chrome.).
this is mostly a powerplay by google, at the cost of performance in the whole internet infrastructure.
disguised off course, as the latest and greatest privacy thing.
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 1:36 pm
DOT is blockable by blocking UDP/TCP port 853 and so controlable in a network. DOT in the router, using and offering, is not a bad thing and even wished for.
In ROS I can enforce which DNS server is used except when I use IKEv2 to a provider.
DOH is there to avoid control and that should only be used where is no free internet. It is like working with a host file with all the IP-addresses you need in there.
You could send dummy requests to local DNS server to keep up appearances but if is looked at the traffic it will still show you are looking a different site.
VPN is a possible solution which also provides DNS. But you have be allowed reach the IP addres of the VPN server.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 1:39 pm
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 3:47 pm
Agreed, DOH is BULL.
The only things it archieves are:
1- completely breaks local caching, therefore causing problems in networks with high latency. (basically everyone on radio.)
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 4:10 pm
I would tend to disagree. The case you mention is only one possible application of DNS over HTTPS.
There are many places in the world where the Internet is restricted and tools like this help users in those regions to browse privately. There are other use cases as well but increased privacy and encryption for the end user is a trend that will continue IMO.
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 4:17 pm
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 4:28 pm
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 4:37 pm
This entire thread is way over my head, but smatter. I tried DNS over pihole and all it got me was grief from the family as the internet would work intermittently or not at all.
There is no clean implementation path I could discern using pihole (how to set it up without effing up my router configuration or creating a monster mess). Obviously beyond my capabilities so I ditched the effort.
Just trying to keep it real, in terms of supporting extra capabilities when deemed, by the angry red bird, to be of sufficient practicality and purpose by adding said functionality to the router.
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 5:44 pm
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 6:01 pm
I prefer 9.9.9.9 / 2620:fe::fe
It has malware protection and is very transparent about not storing or tracking user data.
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 7:03 pm
This entire thread is way over my head, but smatter. I tried DNS over pihole and all it got me was grief from the family as the internet would work intermittently or not at all.
There is no clean implementation path I could discern using pihole (how to set it up without effing up my router configuration or creating a monster mess). Obviously beyond my capabilities so I ditched the effort.
Just trying to keep it real, in terms of supporting extra capabilities when deemed, by the angry red bird, to be of sufficient practicality and purpose by adding said functionality to the router.
Sorry to read that and I think you had problems with DHCP. First I setup it without being it also a DHCP server and just get it resolving DNS locally. Then look if a client can resolve by using dig miktotik.com @192.168.88.X and the IP is from the pi-hole.
Then can tell the DHCP in the router that there is new DNS server and it takes time till the clients are informed about it. It could take more than a day in which all keep working.
After the clients are using the pi-hole now you could also force the router to use pi-hole.
Pi-hole DHCP is something you could use but don’t have to.
The soon to be released Pi-hole 5.0 has become database driven and CNAME aware. I think that it is ready to come out the Beta period in a few weeks. In the works a control webclient wich does not need a separate webserver anymore.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Mon Feb 03, 2020 9:42 pm
Google is going to enable DOH by default in future versions of chrome, firefox is going to use Cloudflare by default.
Re: Add DNS over HTTPS (DoH) support
Tue Feb 04, 2020 5:00 pm
Re: Add DNS over HTTPS (DoH) support
Mon Feb 10, 2020 10:19 am
Privacy up down, data collected here there.
Can we expect support for this?
Than users themselves can decide who or what thew want to use, DNS DoH DoT.
Re: Add DNS over HTTPS (DoH) support
Mon Feb 10, 2020 4:23 pm
Of course when these techniques become universally implemented, we need to make a sticky topic for the many users that come here with requests like:
— I need to block some specific website (Youtube/Facebook/whatever)
— I need to allow access to only one specific website (externally hosted company site)
— I need to limit the use of bandwidth by this or that service, e.g. operating system updates
etc. There can be a simple cooked reply stating that these things are no longer possible, and that all recipes those people find that claim to solve it do no longer work.
And also that despite information they have read elsewhere, other manufacturer’s equipment cannot do it either.
At first sight it may seem that this privacy is a good thing, but of course it will cause some things to collapse, like free Wifi for visitors and limited-bandwidth wireless internet connectivity with purposely limited usage.
Or just limit the whole connection and stop trying to get fancy. If you can’t serve 20mbps then dont try to for some things and not others. I really don’t care if my Gmail runs at full speed but u can’t watch a YouTube video on your WiFi, the end result is the feeling that it’s broken.
Here in the US you’re not responsible for what people do on a free WiFi connection. Funny enough captive portals aren’t required either.
The one exception I’ll give you is schools. They have some rules that say Internet access has to be restricted. How they will cope with these regulations will be interesting. The only feasible solution I see is malware (read: security software) on all network connected devices and no connectivity otherwise.
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 10:32 am
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 10:40 am
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 11:56 am
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 12:31 pm
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 1:28 pm
I already use a DoH/DoT server in front of Pihole so the browsers/devices I use. The settings have to changed if an other server is going to be used.
Malware software can build their own connection over DoH but that has first have pass Netguard or the HIPS to have access to the network.
DoH is a way to hide and not to be used in normal situations. If your ISP is selling your DNS data then DoT is also possible. If that is blocked then then are rightfully going to use the way of hacking yourself out with DoH.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 1:33 pm
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 2:42 pm
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 4:58 pm
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 5:03 pm
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 6:11 pm
In our country, news websites are not blocked. Some Movie/Music sharing websites are. But they are blocked both on ISP DNS and on IP address.
However, DNS queries are not captured and redirected so there is no difference between using ISP DNS or one’s own DNS resolver or even big player DNS resolvers operating on port 53.
But, when you send your traffic (either only DNS or all traffic) via encrypted tunnel (DoH/DoT) to some hoster in another country, you essentially expose yourself to the monitoring and blocking mandated in that other country. When Trump does not like what our local paper writes about him, he may require Google/Cloudflare/etc to block that website or he may require them to log my visits to that site to use it against me should I want to visit the USA.
Not really an improvement over using local DNS.
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 7:58 pm
Re: Add DNS over HTTPS (DoH) support
Wed Feb 12, 2020 9:21 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 9:40 am
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 12:38 pm
Well, in some countries people trust their local government more than they trust the USA where there can be a president like Trump.
But of course this decision depends on the trust you can have in the local government as well.
Here, these blocks are not made by the government but by the court of justice, who receive requests from institutions protecting e.g. artists who want to sell music and find it freely downloadable on internet. They request that certain sites be blocked, and sometimes this request is granted (of course it makes no difference at all for the downloading of music).
They have mostly focussed on the Bittorrent system.
As I have no interest in using Bittorrent to download music or videos, I am not affected by that silly battle, and I have no problem using plain DNS.
In other countries it may be different, e.g. because news sites or other sites with opinions against the government are blocked. That does not happen here.
But I see no reason to hand over even more data to Mozilla, Google and Cloudflare than already happens by default. We do not know what happens with the data.
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 9:27 pm
Normis reacted many times in this thread. Can you more specific what you are looking for or want to contribute.
Just asking to write something is mostly a shot in the dark.
Have you read the pages I linked to in the other thread? That was about dns leaking and this is about the way traffic that goes between you and the dnsserver.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 10:47 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 11:07 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 13, 2020 11:30 pm
If you use a validating, recursive, caching DNS resolver you don’t need any ISP or any other resolver that is providing a DNS service.
You are then asking the authorative servers themselves and so cutting out all the collectors/providers in between. Those big firms will only know of that resolve when they are the authorative server for that domain. You request goes plain over the internet but then you csn alway put that traffic in a VPN tunnel.
I am using it now for several years and it as fast or faster then using the DNS of my ISP. Unbound is very flexible and full of features you can only dream of and give you full control of what you need. It has DoT serving to clients and if you want to use a DoT server to resolve, it works great.
No DoH supported, I don’t expect that ever happening. Knot resolver is also such a kind of server that has similar or more features.
If you want be indepented then run you own DNS recursive server. Running great on just a RaspberryPI board.
[IN READ-ONLY MODE]
Loving my freedom and so, no PayPal, no TikTok, no Meta/Facebook/Instagram/WhatsApp, no Apple and no Alphabet/Google, no Amazon/Cloudfront/AWS.
Running: RouterOS 7.6beta8 and 7.2.1 / Winbox 3.37 64bits
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 3:28 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 3:30 pm
Like said many times before, it depends on your country and your ISP.
Some people have strong censorship, some are afraid of their governments.
So in the end, information will flow somewhere, this feature allows you to control who you trust more.
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:00 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:14 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:29 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:37 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:40 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 4:54 pm
Re: Add DNS over HTTPS (DoH) support
Thu Feb 27, 2020 11:25 pm
Re: Add DNS over HTTPS (DoH) support
Wed Mar 04, 2020 4:45 pm
Re: Add DNS over HTTPS (DoH) support
Fri Mar 06, 2020 6:14 pm
Re: Add DNS over HTTPS (DoH) support
Mon Mar 09, 2020 9:15 am
Re: Add DNS over HTTPS (DoH) support
Fri Mar 13, 2020 7:23 pm
I didn’t go through every post, but I noticed that at some point normis asked for a use case.
Example 1:
There are companies that have on-prem systems, that are used both from the Internet and from the corp LAN.
Let’s say company has an email server, located on domain «email.company.net». The server lives inside the company network. People have laptops, mobile phones, etc. All of that connects to hostname «email.company.net». When accessing that hostname from inside corp LAN, you have to resolve «email.company.net» hostname to some internal IP address. So it can point local users to a local IP. You don’t access a local server via a public IP, from inside a NAT routed network (maybe with some magic you could, but it’s far less dirty to just give out the local IP to the client). So, in your local DNS you add a record (static entry in Mikrotik) for the hostname. The client receives a local IP address of the server, available inside the LAN and problem is solved. Clients only need to use that DNS server (and DHCP gives then the proper one) and that’s it. Everything works from the Internet and also when you’re inside the corp network where the servers actually live.
This approach solves availability of resources from both corp LAN and Internet, where this is needed.
Example two:
Another example are systems that are not at all available from the Internet directly, but only from through a VPN. Many companies employ this. So, the client (or the entire client network) first has to connect to VPN, then access resources. If this VPN is resolved with Mikrotik (many RB devices, even the cheap ones, have nice hardware offloading for IPSEC, so it’s a very good solution for site-to-site VPN) it’s all good. We just use static entries in DNS in ROS and point clients to use DNS from ROS. And everything works. No need for additional DNS server.
And this all works well for IMAP, SMTP etc, because normally everything on the machine uses DNS server as set up on the system. So email clients and custom applications all work. But what about browsers. All is well until a browser decides not to honor system DNS settings. Then, anything in the corp LAN that you try to access through a browser, doesn’t work anymore. Same is you’re accessing through a VPN. Stuff like CRM, webmail — well, most apps today are web apps anyway, used through a browser.
And now it starting to happen, browsers are trying to reinvent how Internet works. Because. DNS, in it’s standard and widely used implementation, is no longer deemed safe enough. Ok, fine. Someone has to lift the standards. Browsers are trying to do it, other apps will probably follow after that. But if Mikrotik doesn’t follow this change, and MT is used to provide DNS queries, then setups like the ones described in above examples will stop working.
Yeah, we can use a separate DNS server that would solve this, of course, and maybe we should. But why not have it in ROS, as an option at least. Network-wise we have (almost) everything you can imagine in ROS — even stuff you wouldn’t expect to have. But none of the more recent DNS stuff. Why ? Why would Mikrotik not provide a solution that solves this issue, like any other network related issue it already solves, in the same box ?
I understand that many proposals exists to solve DNS problem and it’s not yet clear which one is going to be used in future. It’s hard to know what to implement. One way is to implement just the ones that browsers are going for -> because those are the ones we’re going to need to have in our network for above setups to continue working. And that’s probably the ones that everyone is going to switch to in the end.
I believe these setups (like the ones mentioned above) are not at all uncommon. Well, maybe people don’t use ROS for DNS in such cases, but you get the point. So, again, yes, we can solve this by installing a compatible DNS inside our network, but. ROS was always able to handle this stuff for us, without the need for additional equipment. Why would we need to change that. Is it too heavy load for a Mikrotik device (TLS handshakes and all that) ? But recent RB-s are not at all slow, I guess this won’t be a problem. Or would it be ? Normis, could you provide any insight regarding this ?
Источник
-
nifyecusp
- Сообщения: 3
- Зарегистрирован: 12 фев 2021, 13:31
У кого-то работает DoH с включенными опциями Verify DoH Certificate И (это важно!) с включенными опциями CRL Download и Use CRL в System -> Certificates? Пробовал сервера Cloudflare и Google. В логах ошибка «DoH server connection error: SSL: handshake failed: unable to get certificate CRL (6)» Если у вас все работает без ошибок — можете подсказать какие сертификаты вы ставили и что у вас в списке System -> Certificates -> CRL?
Код: Выделить всё
certificate print detail
1 L T name="cloudf.pem_0" issuer=C=US,O=DigiCert Inc,OU=www.digicert.com,CN=DigiCert Global Root CA digest-algorithm=sha384 key-type=ec country="US"
organization="DigiCert Inc" common-name="DigiCert TLS Hybrid ECC SHA384 2020 CA1" key-size=secp384r1 subject-alt-name="" days-valid=3651 trusted=yes
key-usage=digital-signature,key-cert-sign,crl-sign,tls-server,tls-client serial-number="0A275FE704D6EECB23D5CD5B4B1A4E04"
fingerprint="d79a2d5e03295c0e9feae36d021ebd5209700ab1a9e817a43f30fa3c66f78d21" akid=03de503556d14cbb66f0a3e21b1bc397b23dd155
skid=0abc0829178ca5396d7a0ece33c72eb3edfbc37a invalid-before=sep/23/2020 06:00:00 invalid-after=sep/23/2030 05:59:59 expires-after=501w2d13h22m2s
2 T name="cloudf.pem_1" issuer=C=US,O=DigiCert Inc,OU=www.digicert.com,CN=DigiCert Global Root CA digest-algorithm=sha1 key-type=rsa country="US"
organization="DigiCert Inc" unit="www.digicert.com" common-name="DigiCert Global Root CA" key-size=2048 subject-alt-name="" days-valid=9131
trusted=yes key-usage=digital-signature,key-cert-sign,crl-sign serial-number="083BE056904246B1A1756AC95991C74A"
fingerprint="4348a0e9444c78cb265e058d5e8944b4d84f9662bd26db257f8934a443c70161" akid=03de503556d14cbb66f0a3e21b1bc397b23dd155
skid=03de503556d14cbb66f0a3e21b1bc397b23dd155 invalid-before=nov/10/2006 06:00:00 invalid-after=nov/10/2031 06:00:00 expires-after=560w2d13h22m3s
3 L T name="GSR2.crt_0" issuer=OU=GlobalSign Root CA - R2,O=GlobalSign,CN=GlobalSign digest-algorithm=sha1 key-type=rsa organization="GlobalSign"
unit="GlobalSign Root CA - R2" common-name="GlobalSign" key-size=2048 subject-alt-name="" days-valid=5479 trusted=yes
key-usage=key-cert-sign,crl-sign serial-number="0400000000010F8626E60D"
fingerprint="ca42dd41745fd0b81eb902362cf9d8bf719da1bd1b1efc946f5b4c99f42c1b9e" akid=9be20757671c1ec06a06de59b49a2ddfdc19862e
skid=9be20757671c1ec06a06de59b49a2ddfdc19862e invalid-before=dec/15/2006 14:00:00 invalid-after=dec/15/2021 14:00:00 expires-after=43w4d21h22m3s
ROS 6.47.9
-
KaNelam
- Сообщения: 589
- Зарегистрирован: 11 июл 2017, 13:03
-
nifyecusp
- Сообщения: 3
- Зарегистрирован: 12 фев 2021, 13:31
12 фев 2021, 15:16
DoH server connection error: SSL: handshake failed: unable to get certificate CRL (6)
-
gmx
- Модератор
- Сообщения: 3054
- Зарегистрирован: 01 окт 2012, 14:48
12 фев 2021, 15:50
Попробовал.
С включенными CRL Download и Use CRL в System -> Certificates не работает.
Пишет ошибку DoH server connection error: SSL: handshake failed: unable to get certificate CRL (6)
Если опции отключить, то все работает.
Наверное, лучше в техподдержку микротика написать…
-
nifyecusp
- Сообщения: 3
- Зарегистрирован: 12 фев 2021, 13:31
12 фев 2021, 16:17
В поддержке говорят
The server certificate has additional CRL in itself which is not installed in RouterOS CRL list. Currently you can disable the CRL usage as stated before or try to figure out what CRL’s are required for the specific server and add them manually.
Как и где искать не говорят.
-
Igor.Govor
- Сообщения: 2
- Зарегистрирован: 11 мар 2021, 16:59
11 мар 2021, 17:34
В общем у меня по сути та же проблема где-то с февраля 2020(в апреле вообще жесткий DDos на мои системы был(воевал по этому поводу очень серьезно с обращением в МВД и Роскомнадзор) Билайн тогда меня вообще отфутболил как не своего клиента(до сих пор тишина, что наводит на мысль о том, что это чудят мвдшные железки которые на анализе трафика висят), поставил в апреле 2020 https://1.1.1.1/dns-query с проверкой сертификата (но параметры CLR не отмечал!), сертификат брал отсюда https://cacerts.digicert.com/DigiCertGl … CA.crt.pem и всё работало отлично примерно до сентября 2020 (пошли небольшие провалы при подключении к Cloudflare) а с 06.03.2021 вообще трэш начался, звоню провайдеру, уверяют что все в порядке(на скринах видно что потери идут на шлюзе у провайдера, а они пытаются меня уверить что это мое железо глючит). ИМХО: В общем попробую сейчас включить CLR, но дело тут явно в том что очень многим не нравится что они больше не видят что, откуда и в каком объеме проходит через сеть пользователя интернет.
P.S. Были жалобы на Акадо(соседка ко мне обращалась за помощью, у неё сайт не открывался (реально было ошибочное присвоение имя адрес со стороны Акадовских DNS) по поводу работы их DNS, но там вообще можно даже не звонить а самостоятельно DNS в настройках поменять и забыть про них как про страшный сон. А вот с использованием DoH, DoT, DoQ(DNS over QUIC(еще более прикольная штука)) полагаю кто-то явно борется(Посмотрите публикации по поводу законопроекта запрещающего использование данных протоколов передачи и попытка внесения изменения в 149-ФЗ с сентября 2020 года!!!). С показателями производительности крупнейших DNS серверов можно ознакомиться на этом сайте: https://www.dnsperf.com/#!dns-resolvers,Europe,uptime В общем всем удачи и хорошего коннекта.
-
gmx
- Модератор
- Сообщения: 3054
- Зарегистрирован: 01 окт 2012, 14:48
12 мар 2021, 09:23
По поводу борьбы, кстати, светлая мысль. Очень даже может быть. Тоже начались проблемы и именно с 1.1.1.1 Но….
попробуйте настроить DoH на Гугол. Мне помогло, работает, почти как часы. Есть подозрение, что именно к 1.1.1.1 запросы пытаются банить.
-
denis1978
- Сообщения: 56
- Зарегистрирован: 06 июн 2020, 09:52
12 мар 2021, 09:36
gmx писал(а): ↑
12 мар 2021, 09:23
По поводу борьбы, кстати, светлая мысль. Очень даже может быть. Тоже начались проблемы и именно с 1.1.1.1 Но….попробуйте настроить DoH на Гугол. Мне помогло, работает, почти как часы. Есть подозрение, что именно к 1.1.1.1 запросы пытаются банить.
А ещё лучше заведите в сети малинку, а на нее поставьте PiHole, будет Вам и DOH и резалка мусора и ещё много плюшек в одном флаконе.
Работает на самом деле как часы, не напрягая микрот.
Сегодня рассмотрим интересное решение — это настройку DoH на роутере Mikrotik (другими словами DNS over HTTPS). В одной из предыдущих статей, мы вам рассказывали, как настроить DNS сервер возьмём ее за основу и немного докрутим.
DoH – это технология которая позволяет шифровать ваши запросы с помощью TLS. Был придуман для защиты запросов от анализа или вскрытия, а также подмены результатов запроса. Обычный DNS ничем не защищён и передаёт данные в открытом виде. Запросы отправляются по UDP на 53 порт. В DoH немного по-другому, т.к. тут есть TLS и HTTP, то по сути своей это TCP на 443 порт, т.к. тут есть TCP, то работы данного протокола, в разы медленно чем у прародителя. Конечно, его тоже можно вскрыть при желании, но для этого нужна прокся со вскрытием TLS, что накладывает определённые технические нюансы и ресурсы.
Если вы хотите углубить свои знания по работе с роутерами MikroTik, то наша команда рекомендует пройти курсы которые сделаны на основе MikroTik Certified Network Associate и расширены автором на основе опыта . Подробно читайте ниже.
В использовании данной технологии есть клиент и сервер. Так вот, клиентская часть реализована в RouterOS с версии 6.47. Mikrotik не может быть DoH сервером.
Настройка DoH
Перед включением необходимо определиться, какой сервис вы будите использовать. На сегодняшний день их достаточно и выбрать есть из чего, так же вы может быть захотите свой сервер поднять. Из общедоступных есть следующие:
- OpenDNS — https://doh.opendns.com/dns-query
- Quad9 — https://dns.quad9.net/dns-query
- Cloudflare — https://cloudflare-dns.com/dns-query
- Google Public — https://dns.google/dns-query
В примере я буду использовать проверенный временем Cloudflare. Они обещают не передавать аналитику третьим лица.
Открываем IP – DNS и вставляем строку резолвера в Use DoH Server
Обязательно ставим галочку Verify DoH Certificate.
Обратите внимание на адреса в Servers. Это классические вышестоящие резолверы имен. Их убирать не нужно. Потому что Mikrotik не будет знать, какой IP соответствует cloudflare-dns.com. Да, это нюанс, про который нельзя забывать.
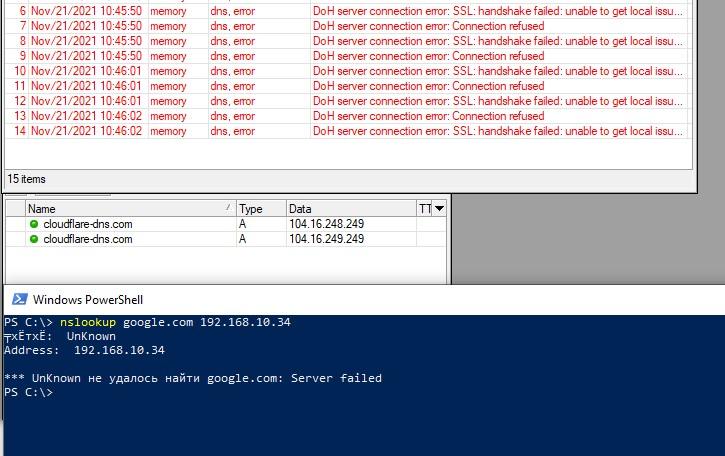
Попробуем проверить работу по новой технологии через nslookup.
В примере выше, я попытался разрешить имя google.com через Mikrotik. Как мы видим, ничего не вышло и в логах ошибка: DoH server connection error: SSL : handshake failed….
Так же видно, что в кэше тоже ничего нет. В чем может быть причина? Правильно в сертификате!
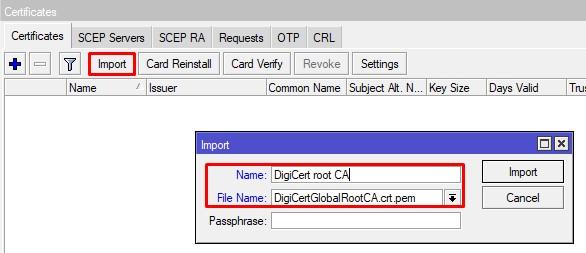
Импорт сертификатов
RouterOS ничего не знает о сертификате Cloudflare и о других, т.к. в него не импортированы корневые публичные ключи глобальных CA и по этому он не может выстроить доверие. Допустим в ОС Windows они уже идут в составе и добавляются / удаляются с обновлениями.
Прежде чем импортировать корневой CA вам нужно понять, кем был выпущен сертификат для одного из сервис-провайдеров. Допустим, для моего примера выпустил DigiCert.
Качаем его публичную часть по этой ссылке. Делаем его Upload на девайс, после в System – Certificates импортируем.
Проверим снова разрешение имён
Теперь все отлично. Как вы видите, ничего сложного нет, выбираем сервис, который вам больше нравится, прописываем его в настройках и импортируем CA того, кто выпустил вашему сервису сертификат, и все на этом настройка DoH на MikroTik завершена.
89 вопросов по настройке MikroTik
Вы хорошо разбираетесь в Микротиках? Или впервые недавно столкнулись с этим оборудованием и не знаете, с какой стороны к нему подступиться? В обоих случаях вы найдете для себя полезную информацию в курсе «Настройка оборудования MikroTik». 162 видеоурока, большая лабораторная работа и 89 вопросов, на каждый из которых вы будете знать ответ. Подробности и доступ к началу курса бесплатно тут.