Содержание
- Клиенты не подключаются к OpenVPN на микротике.
- OpenVPN Support Forum
- TLS handshake failed
- TLS handshake failed
- Re: TLS handshake failed
- Re: TLS handshake failed
- Re: TLS handshake failed
- Re: TLS handshake failed
- Re: TLS handshake failed
- OpenVPN Support Forum
- TLS handshake failed
- TLS handshake failed
Клиенты не подключаются к OpenVPN на микротике.
Не подключаются клиенты (linux) к OpenVPN серверу на микротике.
Сертификаты для сервера и клиентов созданы? Сертификат сервера в микротык импортирован? Клиентские сертификаты клиентам розданы? ca.crt и серверу, и клиентам роздан?
Да. Все сертификаты на местах.
А кроме этого ворнинга какая-нибудь еще ругань есть? Микротык в log print что-нибудь говорит?
Если я все правильно понимаю, то клиенту недоступен либо чем-то не нравится ca.crt.
понять бы, чем не нравится..
Может все-таки конфиги покажем?
Микротик настраивался по статье на хабре.
1. Про серверный мы видимо должны догадаться.
2. смотрите что у вас в /etc/openvpn/ca.crt и сравните с серверным
3. Микротик настраивался по статье на хабре. — про которую мы видимо тоже должны догадаться.
ЗЫ Даты на клиенте и сервере все-таки тоже проверьте.
Буквально на днях цеплял еще одного клиента к рабочему ovpn’у. Один момент — клиент на windows. Была точно такая же ошибка, хотя конфиг и все остальное было взято с рабочего клиента. Вопрос решился установкой другой версии openvpn. Скачивал с сайта текущий 2.3.11 — с ним не шло. Поставил 2.3.10 — сразу все подключилось. Что-то они там с SSL в клиенте сделали.
Клиентский конфиг и примеры рабочих корневого и клиентского сертификатов можете скинуть?
Вообще они немного разные, но как минимум ns-cert-type server пробовали раскоментировать?
Клиентский конфиг и примеры рабочих корневого и клиентского сертификатов можете скинуть?
И ключи от квартиры где деньги лежат?
да. результат тот же.
Посмотрите от кого запускается openvpn может ему /etc/openvpn/ca.crt не доступен.
Я и имел ввиду сгенерировать новые, но с теми же параметрами (nsCertType, keyUsage,keyCertSign, authorityKeyIdentifier, и.т.д) как у рабочих.
запускал и от рута и от обычного пользователя.
btw не нулевая вероятность. Сам не сталкивался, но читал про такое.
Хотя больше предполагаю, что проблема была как обычно в самом конфиге (устаревшие/изменившие поведение/добавленные параметры). Вы лог клиента не пробовали читать?
Возможно в самом openvpn (мы же только догадываемся) захаркоден конкретный юзвер:группа, например openvpn:openvpn.
Вообще микротик насколько я слышал, та еще пакость во многих частях. Попробуйте все-таки полностью хотя по одной из инструкций сделать (они реально разные) а у вас если смотреть наискосок вроде как помесь уже.
Как уже выше писал dexpl проблема явно в одном:
Fri Jun 10 21:46:52 2016 TLS_ERROR: BIO read tls_read_plaintext error: error:14094418:SSL routines:SSL3_READ_BYTES:tlsv1 alert unknown ca: error:140940E5:SSL routines:SSL3_READ_BYTES:ssl handshake failure
Что вы сделали не так, честно говоря я хз. Сливаюсь. Может знатоки микротика подтянуться, не нулевая вероятность что вы совсем не ca.crt выложили или не в том формате.
У меня эта проблема вылезла, после того как обновился openvpn-клиент в федоре. Теперь не могу к серверам на микротиках подключаться. А вот к старому серверу на линуксе вполне ок. Буду разбираться.
Источник
OpenVPN Support Forum
Community Support Forum
TLS handshake failed
TLS handshake failed
Post by tadrim » Mon Aug 24, 2015 4:04 pm
I’m getting TLS errors in windows when I run the configuration on Linux it works fine so unsure what’s occurring!
The error I’m getting:
Mon Aug 24 16:48:35 2015 VERIFY OK:
Mon Aug 24 16:48:35 2015 VERIFY OK: nsCertType=SERVER
Mon Aug 24 16:48:35 2015 TLS_ERROR: BIO read tls_read_plaintext error: error:14082174:SSL routines:SSL3_CHECK_CERT_AND_ALGORITHM:dh key too small
Mon Aug 24 16:48:35 2015 TLS Error: TLS object -> incoming plaintext read error
Mon Aug 24 16:48:35 2015 TLS Error: TLS handshake failed
Mon Aug 24 16:48:35 2015 Fatal TLS error (check_tls_errors_co), restarting
It connects fine with a Linux OS but when you try to connect via Windows it just keeps repeating the error
client
dev tun
proto tcp
remote (obscured) 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert tadrim.crt
key tadrim.key
auth-nocache
ns-cert-type server
comp-lzo
verb 3
I have tried putting in the full path for the certs etc and still get the same error
Re: TLS handshake failed
Post by maikcat » Tue Aug 25, 2015 8:26 am
are you using the SAME configs/certs/openvpn ver?
Re: TLS handshake failed
Post by tadrim » Tue Aug 25, 2015 8:35 am
Yes I have also generated new configs/certs to see if that is the issue but still get the same error on windows — works okay on Linux, the client is using the latest openvpn ver.
Re: TLS handshake failed
Post by tadrim » Tue Aug 25, 2015 10:21 am
Yes I am using the same configs/certs and openvpn version — apart from changing the directory of the cert files.
Re: TLS handshake failed
Post by maikcat » Tue Aug 25, 2015 11:02 am
which windows version do you have?
which openvpn version do you use on win?
please post complete server/client logs.
Re: TLS handshake failed
Post by tadrim » Thu Aug 27, 2015 12:16 pm
the version is:
OpenVPN 2.3.7 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on Jul 9 2015
Thu Aug 27 12:58:02 2015 library versions: OpenSSL 1.0.1p 9 Jul 2015, LZO 2.08
Here is the server log:
TLS: Initial packet from xxxx
VERIFY OK: details
VERIFY OK: nsCertType=SERVER
VERIFY OK: details
TLS_ERROR: BIO read tls_read_plaintext error: error:14082174:SSL routines:SSL3_CHECK_CERT_AND_ALGORITHM:dh key too small
TLS Error: TLS object -> incoming plaintext read error
TLS Error: TLS handshake failed
Fatal TLS error (check_tls_errors_co), restarting
SIGUSR1[soft,tls-error] received, process restarting
MANAGEMENT: >STATE:1440677050,RECONNECTING,tls-error,,
Restart pause, 5 second(s)
and here is the client log:
MULTI: multi_create_instance called
Re-using SSL/TLS context
LZO compression initialized
Control Channel MTU parms [ L:1544 D:140 EF:40 EB:0 ET:0 EL:0 ]
Data Channel MTU parms [ L:1544 D:1450 EF:44 EB:135 ET:0 EL:0 AF:3/1 ]
Local Options hash (VER=V4): ‘c0103fa8’
Expected Remote Options hash (VER=V4): ‘69109d17’
TCP connection established with (ipaddress):64448
TCPv4_SERVER link local: [undef]
TCPv4_SERVER link remote: (ipaddress):64448
(ipaddress):64448 TLS: Initial packet from (ipaddress):64448, sid=b991999d 259a72c5
(ipaddress):64448 Connection reset, restarting [0]
(ipaddress):64448 SIGUSR1[soft,connection-reset] received, client-instance restarting
TCP/UDP: Closing socket
Источник
OpenVPN Support Forum
Community Support Forum
TLS handshake failed
TLS handshake failed
Post by Bransonb3 » Sat Jan 06, 2018 4:57 pm
When I try to connect to my openvpn server I get TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) and TLS Error: TLS handshake failed. It looks like the server sees the client try to connect (TLS: Initial packet from. ) but doesn’t respond.
I’m running openvpn 2.4.4 on Windows Server 2016 1607. I am trying to connect my Mac running OSX 10.13.2, using Tunnelblick 3.7.4b but have also tried connecting using the openvpn connect android app. I have port forwarded 1194 udp to my server, made an inbound and outbound windows firewall rule allowing openvpn.exe, allowed tunnelblick incoming connections on the mac firewall. I have also tried to run the server as admin.
#################################################
# Sample OpenVPN 2.0 config file for #
# multi-client server. #
# #
# This file is for the server side #
# of a many-clients one-server #
# OpenVPN configuration. #
# #
# OpenVPN also supports #
# single-machine single-machine #
# configurations (See the Examples page #
# on the web site for more info). #
# #
# This config should work on Windows #
# or Linux/BSD systems. Remember on #
# Windows to quote pathnames and use #
# double backslashes, e.g.: #
# «C:\Program Files\OpenVPN\config\foo.key» #
# #
# Comments are preceded with ‘#’ or ‘;’ #
#################################################
# Which local IP address should OpenVPN
# listen on? (optional)
;local a.b.c.d
# Which TCP/UDP port should OpenVPN listen on?
# If you want to run multiple OpenVPN instances
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
port 1194
# TCP or UDP server?
;proto tcp
proto udp
# «dev tun» will create a routed IP tunnel,
# «dev tap» will create an ethernet tunnel.
# Use «dev tap0» if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use «dev-node» for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tun
dev tap
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel if you
# have more than one. On XP SP2 or higher,
# you may need to selectively disable the
# Windows firewall for the TAP adapter.
# Non-Windows systems usually don’t need this.
dev-node Ethernet_7
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key). Each client
# and the server must have their own cert and
# key file. The server and all clients will
# use the same ca file.
#
# See the «easy-rsa» directory for a series
# of scripts for generating RSA certificates
# and private keys. Remember to use
# a unique Common Name for the server
# and each of the client certificates.
#
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS #12 formatted key file
# (see «pkcs12» directive in man page).
ca «C:\Program Files\OpenVPN\config\ca.crt»
cert «C:\Program Files\OpenVPN\config\server.crt»
key «C:\Program Files\OpenVPN\config\server.key» # This file should be kept secret
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh «C:\Program Files\OpenVPN\config\dh4096.pem»
# Network topology
# Should be subnet (addressing via IP)
# unless Windows clients v2.0.9 and lower have to
# be supported (then net30, i.e. a /30 per client)
# Defaults to net30 (not recommended)
topology subnet
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
;server 192.168.1.225 255.255.0.0
# Maintain a record of client virtual IP address
# associations in this file. If OpenVPN goes down or
# is restarted, reconnecting clients can be assigned
# the same virtual IP address from the pool that was
# previously assigned.
ifconfig-pool-persist ipp.txt
# Configure server mode for ethernet bridging.
# You must first use your OS’s bridging capability
# to bridge the TAP interface with the ethernet
# NIC interface. Then you must manually set the
# IP/netmask on the bridge interface, here we
# assume 192.168.1.227/255.255.0.0. Finally we
# must set aside an IP range in this subnet
# (start=192.168.3.1 end=192.168.3.254) to allocate
# to connecting clients. Leave this line commented
# out unless you are ethernet bridging.
server-bridge 192.168.1.227 255.255.0.0 192.168.3.1 192.168.3.254
# Configure server mode for ethernet bridging
# using a DHCP-proxy, where clients talk
# to the OpenVPN server-side DHCP server
# to receive their IP address allocation
# and DNS server addresses. You must first use
# your OS’s bridging capability to bridge the TAP
# interface with the ethernet NIC interface.
# Note: this mode only works on clients (such as
# Windows), where the client-side TAP adapter is
# bound to a DHCP client.
;server-bridge
# Push routes to the client to allow it
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push «route 192.168.10.0 255.255.255.0»
;push «route 192.168.20.0 255.255.255.0»
# To assign specific IP addresses to specific
# clients or if a connecting client has a private
# subnet behind it that should also have VPN access,
# use the subdirectory «ccd» for client-specific
# configuration files (see man page for more info).
# EXAMPLE: Suppose the client
# having the certificate common name «Thelonious»
# also has a small subnet behind his connecting
# machine, such as 192.168.40.128/255.255.255.248.
# First, uncomment out these lines:
;client-config-dir ccd
;route 192.168.40.128 255.255.255.248
# Then create a file ccd/Thelonious with this line:
# iroute 192.168.40.128 255.255.255.248
# This will allow Thelonious’ private subnet to
# access the VPN. This example will only work
# if you are routing, not bridging, i.e. you are
# using «dev tun» and «server» directives.
# EXAMPLE: Suppose you want to give
# Thelonious a fixed VPN IP address of 10.9.0.1.
# First uncomment out these lines:
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
# Then add this line to ccd/Thelonious:
# ifconfig-push 10.9.0.1 10.9.0.2
# Suppose that you want to enable different
# firewall access policies for different groups
# of clients. There are two methods:
# (1) Run multiple OpenVPN daemons, one for each
# group, and firewall the TUN/TAP interface
# for each group/daemon appropriately.
# (2) (Advanced) Create a script to dynamically
# modify the firewall in response to access
# from different clients. See man
# page for more info on learn-address script.
;learn-address ./script
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push «redirect-gateway def1 bypass-dhcp»
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
# The addresses below refer to the public
# DNS servers provided by opendns.com.
;push «dhcp-option DNS 208.67.222.222»
;push «dhcp-option DNS 208.67.220.220»
# Uncomment this directive to allow different
# clients to be able to «see» each other.
# By default, clients will only see the server.
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server’s TUN/TAP interface.
client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
# files or common names. This is recommended
# only for testing purposes. For production use,
# each client should have its own certificate/key
# pair.
#
# IF YOU HAVE NOT GENERATED INDIVIDUAL
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE «COMMON NAME»,
# UNCOMMENT THIS LINE OUT.
;duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
# the link so that each side knows when
# the other side has gone down.
# Ping every 10 seconds, assume that remote
# peer is down if no ping received during
# a 120 second time period.
keepalive 10 120
# For extra security beyond that provided
# by SSL/TLS, create an «HMAC firewall»
# to help block DoS attacks and UDP port flooding.
#
# Generate with:
# openvpn —genkey —secret ta.key
#
# The server and each client must have
# a copy of this key.
# The second parameter should be ‘0’
# on the server and ‘1’ on the clients.
;tls-auth «C:\Program Files\OpenVPN\config\ta.key» 0 # This file is secret
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
# Note that v2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-256-CBC
# Enable compression on the VPN link and push the
# option to the client (v2.4+ only, for earlier
# versions see below)
;compress lz4-v2
;push «compress lz4-v2»
# For compression compatible with older clients use comp-lzo
# If you enable it here, you must also
# enable it in the client config file.
;comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# It’s a good idea to reduce the OpenVPN
# daemon’s privileges after initialization.
#
# You can uncomment this out on
# non-Windows systems.
;user nobody
;group nobody
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status openvpn-status.log
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the «Program FilesOpenVPNlog» directory).
# Use log or log-append to override this default.
# «log» will truncate the log file on OpenVPN startup,
# while «log-append» will append to it. Use one
# or the other (but not both).
;log openvpn.log
;log-append openvpn.log
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
# Notify the client that when the server restarts so it
# can automatically reconnect.
explicit-exit-notify 1
##############################################
# Sample client-side OpenVPN 2.0 config file #
# for connecting to multi-client server. #
# #
# This configuration can be used by multiple #
# clients, however each client should have #
# its own cert and key files. #
# #
# On Windows, you might want to rename this #
# file so it has a .ovpn extension #
##############################################
# Specify that we are a client and that we
# will be pulling certain config file directives
# from the server.
client
# Use the same setting as you are using on
# the server.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
;dev tap
dev tun
# Windows needs the TAP-Win32 adapter name
# from the Network Connections panel
# if you have more than one. On XP SP2,
# you may need to disable the firewall
# for the TAP adapter.
;dev-node MyTap
# Are we connecting to a TCP or
# UDP server? Use the same setting as
# on the server.
;proto tcp
proto udp
# The hostname/IP and port of the server.
# You can have multiple remote entries
# to load balance between the servers.
remote [Public IP] 1194
# Choose a random host from the remote
# list for load-balancing. Otherwise
# try hosts in the order specified.
;remote-random
# Keep trying indefinitely to resolve the
# host name of the OpenVPN server. Very useful
# on machines which are not permanently connected
# to the internet such as laptops.
resolv-retry infinite
# Most clients don’t need to bind to
# a specific local port number.
nobind
# Downgrade privileges after initialization (non-Windows only)
;user nobody
;group nobody
# Try to preserve some state across restarts.
persist-key
persist-tun
# If you are connecting through an
# HTTP proxy to reach the actual OpenVPN
# server, put the proxy server/IP and
# port number here. See the man page
# if your proxy server requires
# authentication.
;http-proxy-retry # retry on connection failures
;http-proxy [proxy server] [proxy port #]
# Wireless networks often produce a lot
# of duplicate packets. Set this flag
# to silence duplicate packet warnings.
;mute-replay-warnings
# SSL/TLS parms.
# See the server config file for more
# description. It’s best to use
# a separate .crt/.key file pair
# for each client. A single ca
# file can be used for all clients.
——BEGIN CERTIFICATE——
Redacted
——END CERTIFICATE——
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 5 (0x5)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, ST=NC, L=High Point, O= Redacted, OU= Redacted, CN=BT-MonCon-SRV/name=Certificate Authority/emailAddress= Redacted
Validity
Not Before: Jan 5 04:57:55 2018 GMT
Not After : Jan 3 04:57:55 2028 GMT
Subject: C=US, ST=NC, L=High Point, O= Redacted, OU= Redacted, CN=BransonMac/name=BransonMac/emailAddress= Redacted
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
Redacted
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
Easy-RSA Generated Certificate
X509v3 Subject Key Identifier:
Redacted
X509v3 Authority Key Identifier:
keyid: Redacted
DirName:/C=US/ST=NC/L=High Point/O= Redacted/OU= Redacted/CN=BT-MonCon-SRV/name=Certificate Authority/emailAddress= Redacted
serial: Redacted
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
Redacted
——BEGIN CERTIFICATE——
Redacted
——END CERTIFICATE——
——BEGIN PRIVATE KEY——
Redacted
——END PRIVATE KEY——
# Verify server certificate by checking that the
# certicate has the correct key usage set.
# This is an important precaution to protect against
# a potential attack discussed here:
# http://openvpn.net/howto.html#mitm
#
# To use this feature, you will need to generate
# your server certificates with the keyUsage set to
# digitalSignature, keyEncipherment
# and the extendedKeyUsage to
# serverAuth
# EasyRSA can do this for you.
;remote-cert-tls BT-MonCon-SRV
# If a tls-auth key is used on the server
# then every client must also have the key.
;tls-auth ta.key 1
# Select a cryptographic cipher.
# If the cipher option is used on the server
# then you must also specify it here.
# Note that v2.4 client/server will automatically
# negotiate AES-256-GCM in TLS mode.
# See also the ncp-cipher option in the manpage
cipher AES-256-CBC
# Enable compression on the VPN link.
# Don’t enable this unless it is also
# enabled in the server config file.
#comp-lzo
# Set log file verbosity.
verb 4
# Silence repeating messages
;mute 20
Источник
OVPN сервер — микротик, OVPN клиент — венда
конфиг сервера:
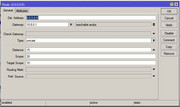
[ziptar@MikroTik] > interface ovpn-server server print
enabled: yes
port: 1194
mode: ip
netmask: 24
mac-address: FE:9F:0B:F7:CB:D9
max-mtu: 1500
keepalive-timeout: 60
default-profile: PPP_Server
certificate: cert4
require-client-certificate: yes
auth: sha1
cipher: blowfish128конфиг клиента:
client
dev tun
proto tcp
remote ovpn.ml.ziptar.net 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
remote-cert-tls server
verb 4
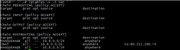
--connect-retry 60Sun Oct 11 23:39:31 2015 us=376834 Current Parameter Settings:
список текущих параметров вырезан - больше 10000 букаф тостер ниасилил
Sun Oct 11 23:39:32 2015 us=17340 OpenVPN 2.3.8 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on Aug 4 2015
Sun Oct 11 23:39:32 2015 us=19342 library versions: OpenSSL 1.0.1p 9 Jul 2015, LZO 2.08
Enter Private Key Password:
Sun Oct 11 23:39:38 2015 us=627780 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sun Oct 11 23:39:38 2015 us=633773 Control Channel MTU parms [ L:1543 D:140 EF:40 EB:0 ET:0 EL:3 ]
Sun Oct 11 23:39:38 2015 us=633773 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Oct 11 23:39:38 2015 us=637778 Data Channel MTU parms [ L:1543 D:1450 EF:43 EB:12 ET:0 EL:3 ]
Sun Oct 11 23:39:38 2015 us=637778 Local Options String: 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_CLIENT,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Sun Oct 11 23:39:38 2015 us=638782 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_SERVER,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Sun Oct 11 23:39:38 2015 us=655792 Local Options hash (VER=V4): 'db02a8f8'
Sun Oct 11 23:39:38 2015 us=656788 Expected Remote Options hash (VER=V4): '7e068940'
Sun Oct 11 23:39:38 2015 us=656788 Attempting to establish TCP connection with [AF_INET]95.31.27.23:1194 [nonblock]
Sun Oct 11 23:39:39 2015 us=663222 TCP connection established with [AF_INET]95.31.27.23:1194
Sun Oct 11 23:39:39 2015 us=663222 TCPv4_CLIENT link local: [undef]
Sun Oct 11 23:39:39 2015 us=663222 TCPv4_CLIENT link remote: [AF_INET]95.31.27.23:1194
Sun Oct 11 23:39:39 2015 us=666219 TLS: Initial packet from [AF_INET]95.31.27.23:1194, sid=0fc9eb4e dea8cee0
Sun Oct 11 23:39:39 2015 us=751116 VERIFY OK: depth=1, C=RU, O=Ziptar.Net, OU=Ziptar.Net Main Lair CA, CN=Ziptar.Net Main Lair Certification Authority
Sun Oct 11 23:39:39 2015 us=752117 Validating certificate key usage
Sun Oct 11 23:39:39 2015 us=752117 ++ Certificate has key usage 00a0, expects 00a0
Sun Oct 11 23:39:39 2015 us=755119 VERIFY KU OK
Sun Oct 11 23:39:39 2015 us=757282 Validating certificate extended key usage
Sun Oct 11 23:39:39 2015 us=759447 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sun Oct 11 23:39:39 2015 us=762598 VERIFY EKU OK
Sun Oct 11 23:39:39 2015 us=764603 VERIFY OK: depth=0, C=RU, O=Ziptar.Net, OU=Ziptar.Net Main Lair, CN=Ziptar.Net Main Lair OVPN Server Certificate
Sun Oct 11 23:40:40 2015 us=242140 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun Oct 11 23:40:40 2015 us=242140 TLS Error: TLS handshake failed
Sun Oct 11 23:40:40 2015 us=243132 Fatal TLS error (check_tls_errors_co), restarting
Sun Oct 11 23:40:40 2015 us=247138 TCP/UDP: Closing socket
Sun Oct 11 23:40:40 2015 us=250137 SIGUSR1[soft,tls-error] received, process restarting
Sun Oct 11 23:40:40 2015 us=252138 Restart pause, 60 second(s)
на микротике-сервере коннект client-ip(внешний):1194->server-ip:1194 в состоянии established
на роутере, за которым находится венда — аналогично
netstat на венде кажет:
TCP 172.16.12.13:51360 95-31-27-23:1194 ESTABLISHED
единственно не понимаю почему через дефисы
в логе сервера идёт обмен пакетами, и оканчивается строчкой::using encoding BF-128-CBC/SHA1
Key usage сертификата сервера
KU 0xa0: Digital Signature, Key Encipherment
EKU TLS Web Server Authentication
то есть ровнёхонько то, что желает сам ovpn
сертификата клиента
KU Digital Signature, Key Encipherment, Data Encipherment
EKU TLS Web Client Authentication
так что же он от меня желает? 
Mikrotik noob here,
I’ve adquired an Mikrotik Hap AC3 this week and I’m currently trying to set it up as OpenVPN Server. I’ve followed plenty of online guides to do it, even though most of them were using TCP instead of UDP, but I can’t seem to go past a TLS Error. I’ve checked the OpenVPN related posts on this sub and haven’t found the solution yet, so here I go.
This is the OpenVPN client connection log:
Thu May 12 12:09:05 2022 MANAGEMENT: >STATE:1652350145,RESOLVE,,,,,,
Thu May 12 12:09:05 2022 TCP/UDP: Preserving recently used remote address: [AF_INET] <PUB_IP>:1194
Thu May 12 12:09:05 2022 Socket Buffers: R=[65536->65536] S=[65536->65536]
Thu May 12 12:09:05 2022 UDP link local: (not bound)
Thu May 12 12:09:05 2022 UDP link remote: [AF_INET]<PUB_IP>:1194
Thu May 12 12:09:05 2022 MANAGEMENT: >STATE:1652350145,WAIT,,,,,,
Thu May 12 12:10:05 2022 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu May 12 12:10:05 2022 TLS Error: TLS handshake failed
Thu May 12 12:10:05 2022 SIGUSR1[soft,tls-error] received, process restarting
Here’s the relevant export:
/ip pool
add comment=DHCP name=dhcp ranges=192.168.1.150-192.168.1.250
add comment=OpenVPN name=openvpn ranges=172.16.1.150-172.16.1.200
/ppp profile
add bridge=bridge local-address=172.166.1.1 name=openvpn remote-address=openvpn use-ipv6=no
/interface ovpn-server server
set auth=sha1,md5 certificate=openvpn-server default-profile=openvpn enabled=yes protocol=udp require-client-certificate=no
/ip address
add address=192.168.1.1/24 comment=defconf interface=bridge network=192.168.1.0
add address=192.168.10.1/24 comment=DMZ_VLAN10 interface=VLAN10 network=192.168.10.0
/ip firewall filter
add action=accept chain=input comment="Allow OpenVPN UDP" dst-port=1194 protocol=udp
/ppp secret
add name=user profile=openvpn service=ovpn
/certificate
0 KLAT ca ca
1 KLAT openvpn-server server
2 KLA client client
I’ve been stuck with this issue for a bit and tried checking and unchecking the «require client cert» but the result is the same. OpenVPN Client error points to Network Issue, but I moved the firewall rule to position nº1 so it is priorized to allow the traffic on that port.
Here’s the ovpn content:
client
dev tun
proto udp
remote PUBLIC_IP 1194
resolv-retry infinite
nobind
persist-key
persist-tun
tls-client
remote-cert-tls server
ca cert_export_ca.crt
cert cert_export_client.crt
key cert_export_client.key
cipher AES-128-CBC
auth SHA1
pull
auth-user-pass
verb 3
route 192.168.1.0 255.255.255.0
route 192.168.10.0 255.255.255.0
Not sure what I’m missing but it’s probably something really dumb just like everytime I get stuck looking at something for hours xD. If you guys could throw me a bone here I’d really appreciate it!
Cheers!
Здравствуйте.
Можно с разрешения ТС подобный вопрос задать, чтоб темы не плодить.
Подскажите пожалуйста. Поднял сервер openvpn на ubuntu server 18.04, на микрот установил сертификат и ключ. Пробую соединиться — не получается.
Лог сервера:
Код: Выделить всё
Thu Nov 14 01:32:07 2019 TCP connection established with [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS: Initial packet from [AF_INET]***.***.***.***:53340, sid=53ffafd8 2edccd19
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 Fatal TLS error (check_tls_errors_co), restarting
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 SIGUSR1[soft,tls-error] received, client-instance restartingконфигурация сервера:
Код: Выделить всё
port 1194
# Протокол может быть UDP или TCP, я выбрал 1-й вариант.
proto tcp
# Если вы выберите протокол TCP, здесь должно быть устройство tap. Однако, это вариант я не проверял, поэтому ищите информацию отдельно. FIXME
dev tun
# Указываем где искать ключи
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
# Для 12.04 dh1024.pem
# Задаем IP и маску виртуальной сети. Произвольно, но если не уверены лучше делайте как показано здесь
server 10.8.0.0 255.255.255.0
# Указыем, где хранятся файлы с настройками IP-адресов клиентов (создадим ниже)
client-config-dir ccd
# Запоминать динамически выданные адреса для VPN-клиентов и при последующих подключениях назначать те же значения.
ifconfig-pool-persist ipp.txt
# Указываем сети, в которые нужно идти через туннель (сеть-клиента).
route 192.168.0.0 255.255.255.0
# Включаем TLS
tls-server
tls-auth /etc/openvpn/keys/ta.key 0
tls-timeout 120
auth SHA1
cipher AES-256-CBC
# Если нужно, чтобы клиенты видели друг друга раскомментируйте
;client-to-client
keepalive 10 120
# Сжатие трафика
;comp-lzo
# Максимум клиентов
max-clients 10
user nobody
group nogroup
# Не перечитывать ключи, не закрывать и переоткрывать TUNTAP устройство, после получения SIGUSR1 или ping-restart
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
# Детальность логирования
verb 3
# Защита от повторов (максимум 20 одинаковых сообщений подряд)
mute 20
# Файл отозванных сертификатов. Разремить, когда такие сертификаты появятся.
;crl-verify /etc/openvpn/crl.pemлог с микрота:
Настраивал по мануалу с вики ubuntu.ru
Где может быть ошибка?
благодарю
Mikrotik OpenVPN Client и OpenVPN Server
5
Посты
3
Пользователи
1
Likes
5,860
Просмотры
(@uj2062)
New Member
Присоединился: 3 года назад
Сообщения: 2
Topic starter
09.09.2019 09:51
Добрый день. Прошу прощения за оффтоп, вопрос скорее про настройку ovpn-сервера для подключения mikrotik-клиента.
Есть mikrotik в качестве граничного устройства небольшой сети с несколькими сегментами.
Есть VPS (Debian 9) с установленным OpenVPN сервером.
Есть несколько клиентов в интернете, которым необходимо обеспечить доступ к одному из сегментов за микротиком.
Возникла проблема при настройке сервера, не могу отключить TLS, который mikrotik не понимает, и получаю ошибку сервера «TLS Error: cannot locate HMAC in incoming packet from «
Буду признателен за помощь.
server.conf :
port 1194
proto tcp
dev tun
sndbuf 0
rcvbuf 0
ca ca.crt
cert server.crt
key server.key
dh dh.pem
auth SHA1
#tls-auth ta.key 0
#tls-server
#tls-auth none
key-direction 0
topology subnet
server 192.168.8.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push «redirect-gateway def1 bypass-dhcp»
push «dhcp-option DNS 217.12.200.200»
push «route 192.168.8.0 255.255.255.0»
keepalive 10 120
cipher BF-CBC
user nobody
group nogroup
persist-key
persist-tun
;status openvpn-status.log
client-config-dir ccd
verb 5
crl-verify crl.pem
client-to-client
push «route 0.0.0.0 0.0.0.0 vpn_gateway 512»
status openvpn-status.log
log openvpn.log
(@zerox)
Prominent Member Admin
Присоединился: 9 лет назад
Сообщения: 806
09.09.2019 12:46
Я для микротиков поднимаю отдельный туннель. Вот пример конфига с работающего сервера vpn.
port 1195
proto tcp
dev tun2ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/router.crt
key /etc/openvpn/keys/router.key
dh /etc/openvpn/keys/dh1024.pem
crl-verify /etc/openvpn/crl.pemserver 10.10.110.0 255.255.255.0
push "dhcp-option DNS 10.1.3.21"
push "route 10.1.3.0 255.255.255.0"
push "route 10.1.4.0 255.255.255.0"
push "route 10.1.5.0 255.255.255.0"
push "route 10.10.100.0 255.255.255.0"
push "route 10.10.101.0 255.255.255.0"
push "route 10.10.102.0 255.255.255.0"
push "route 10.10.103.0 255.255.255.0"
push "route 10.10.104.0 255.255.255.0"
push "route 10.10.110.0 255.255.255.0"client-config-dir ccd-mikrotik-tcp
ifconfig-pool-persist mikrotik-tcp.txt
route 10.1.5.0 255.255.255.0
route 10.10.110.0 255.255.255.0
client-to-client
auth SHA1
cipher BF-CBC
keepalive 10 30
max-clients 100
user nobody
group nobody
persist-key
persist-tun
status /var/log/openvpn/status-mikrotik-tcp.log
log /var/log/openvpn/log-mikrotik-tcp.log
verb 3
push "ping 10"
push "ping-restart 20"
(@uj2062)
New Member
Присоединился: 3 года назад
Сообщения: 2
Topic starter
12.09.2019 10:15
@zerox
Спасибо, помогло. Смущает скорость соединения, пинги между клиентами прыгают иногда до 800 мс. Средние 150-200 мс. Говорят в микротике гораздо удачней реализован sstp-client. Не было опыта установки связки softether — mikrotik sstp client ?
(@zerox)
Prominent Member Admin
Присоединился: 9 лет назад
Сообщения: 806
12.09.2019 11:48
@uj2062
В общем случае, у меня проблем на каналах до 50-ти мегабит с микротиком и openvpn нет. Пинги не скачат, скорости нормальные. Обращаю только внимание на cipher BF-CBC Сейчас это считается не безопасным. Нужно использовать другие алгоритмы, если нужна 100% защита. Мне это чаще всего не нужно, поэтому я жертвую защитой в пользу быстродействия.
(@farrukhg84)
Estimable Member
Присоединился: 4 года назад
Сообщения: 105
21.04.2020 08:13
А как прописать в настройках клиента ip address DNS серверов ( у нас их две). VPN-server настроен на микротике
I want to connect my OpenVPN server (Ubuntu 16.4) in my office to my Mikrotik at home as client.
I already have OpenVPN server set based on this tutorial (link). If I try to connect it connects with OpenVPN client Windows app (no errors), and asks for username and password, with Client.ovpn added in Program Files/OpenVPN/config.
Here is my server.conf in OpenVPN server:
port 51333
proto tcp
dev tun5
ca ca.crt
cert server.crt
key server.key
dh dh2048.pem
server 10.8.101.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "route 192.168.20.10 255.255.255.255" #This is my server that I want to connect in Office
keepalive 10 120
tls-auth /etc/openvpn/ta.key
key-direction 0
cipher AES-256-CBC
auth SHA1
max-clients 10
user nobody
group nogroup
persist-key
persist-tun
username-as-common-name
plugin /usr/lib/openvpn/openvpn-plugin-auth-pam.so /etc/pam.d/openvpn
status /etc/openvpn/mikrotik.log
verb 5
mute-replay-warnings
client-config-dir ccd
management localhost 7505
Here is my configuration of base.conf in OpenVPN server (Ubuntu) for creating client.ovpn files:
client
dev tun
proto tcp
remote mydomain.com 51333 #in my DNS I redirect this domain to my public static domain in office there in firewall I am portforwarding this port to my server in office
resolv-retry infinite
nobind
user nobody
group nogroup
auth-user-pass
#ca ca.crt
#cert client.crt
#key client.key
remote-cert-tls server
tls-auth ta.key
cipher AES-256-CBC
auth SHA1
# More reliable detection when a system loses its connection.
ping 15
ping-restart 45
ping-timer-rem
persist-tun
persist-key
verb 5
key-direction 1
Now in Mikrotik (OS is: v6.42.12 in hAP lite (simps) I have:
- Import my Client.ovpn in Files
- Import Certificate Client.ovpn and set for T (name: ca.crt_0) and for KT (name: client.crt_0).
- Create new PPP Profile: ppp profile add name=OVPN-client change-tcp-mss=yes only-one=yes use-encryption=required use-mpls=no
- Create new interface: interface ovpn-client add connect-to=mydomain.com port 51333 add-default-route=no auth=sha1 certificate=client.crt_0 disabled=no user=vpnuser password=vpnpass name=myvpn profile=OVPN-client
But with this configuration, I cannot establish a connection. I cannot get «R — status» on OVPN-client, I only get this error:
* ovpn-out1: connecting
* ovpn-out1: terminating - peer disconnected
* ovpn-out1: disconnected
If I check logs in server I get this:
openVPN1 ovpn-server[2050]: MULTI: multi_create_instance called
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Re-using SSL/TLS context
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Control Channel MTU parms
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Data Channel MTU parms
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Local Options String: 'V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_SERVER,keydir 0,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-server'
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Expected Remote Options String: 'V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_CLIENT,keydir 1,cipher AES-256-CBC,auth SHA1,keysize 256,tls-auth,key-method 2,tls-client'
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Local Options hash (VER=V4): '7ac8f09f'
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: Expected Remote Options hash (VER=V4): '53276059'
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: TCP connection established with [AF_INET]XX.XXX.XXX.XX:60345
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: TCPv4_SERVER link local: [undef]
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: TCPv4_SERVER link remote: [AF_INET]XX.XXX.XXX.XX:60345
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: XX.XXX.XXX.XX:60345 TLS: Initial packet from [AF_INET]XX.XXX.XXX.XX:60345
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: XX.XXX.XXX.XX:60345 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]XX.XXX.XXX.XX:60345
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: XX.XXX.XXX.XX:60345 Fatal TLS error (check_tls_errors_co), restarting
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: XX.XXX.XXX.XX:60345 SIGUSR1[soft,tls-error] received, client-instance restarting
Oct 26 09:33:03 openVPN1 ovpn-server[2050]: TCP/UDP: Closing socket
- Печать
Страницы: [1] Вниз
Тема: openvpn + mikrotik (Прочитано 1062 раз)
0 Пользователей и 1 Гость просматривают эту тему.

YDenis
Здравствуйте.
Подскажите пожалуйста. Поднял сервер openvpn на ubuntu server 18.04, на микрот установил сертификат и ключ. Пробую соединиться — не получается.
Лог сервера:
Thu Nov 14 01:32:07 2019 TCP connection established with [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS: Initial packet from [AF_INET]***.***.***.***:53340, sid=53ffafd8 2edccd19
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]***.***.***.***:53340
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 Fatal TLS error (check_tls_errors_co), restarting
Thu Nov 14 01:32:07 2019 185.184.233.160:53340 SIGUSR1[soft,tls-error] received, client-instance restarting
конфигурация сервера:
port 1194
# Протокол может быть UDP или TCP, я выбрал 1-й вариант.
proto tcp
# Если вы выберите протокол TCP, здесь должно быть устройство tap. Однако, это вариант я не проверял, поэтому ищите информацию отдельно. FIXME
dev tun
# Указываем где искать ключи
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
# Для 12.04 dh1024.pem
# Задаем IP и маску виртуальной сети. Произвольно, но если не уверены лучше делайте как показано здесь
server 10.8.0.0 255.255.255.0
# Указыем, где хранятся файлы с настройками IP-адресов клиентов (создадим ниже)
client-config-dir ccd
# Запоминать динамически выданные адреса для VPN-клиентов и при последующих подключениях назначать те же значения.
ifconfig-pool-persist ipp.txt
# Указываем сети, в которые нужно идти через туннель (сеть-клиента).
route 192.168.0.0 255.255.255.0
# Включаем TLS
tls-server
tls-auth /etc/openvpn/keys/ta.key 0
tls-timeout 120
auth SHA1
cipher AES-256-CBC
# Если нужно, чтобы клиенты видели друг друга раскомментируйте
;client-to-client
keepalive 10 120
# Сжатие трафика
comp-lzo
# Максимум клиентов
max-clients 10
user nobody
group nogroup
# Не перечитывать ключи, не закрывать и переоткрывать TUNTAP устройство, после получения SIGUSR1 или ping-restart
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
# Детальность логирования
verb 3
# Защита от повторов (максимум 20 одинаковых сообщений подряд)
mute 20
# Файл отозванных сертификатов. Разремить, когда такие сертификаты появятся.
;crl-verify /etc/openvpn/crl.pem
Настраивал по мануалу с вики ubuntu.ru
Где может быть ошибка?
благодарю
Пользователь добавил сообщение 14 Ноября 2019, 08:43:09:
Нашел ошибку.
Закоментировать
;tls-server
;tls-auth /etc/openvpn/keys/ta.key 0
;tls-timeout 120
« Последнее редактирование: 14 Ноября 2019, 08:43:09 от YDenis »

YDenis
Ребята, на клиентских машинах за миктротом не могу добиться выхода в инет через openvpn туннель.
Здравствуйте.
Подскажите пожалуйста. На арубе на ubuntu server 18.04 поднял opevpn сервер.
Конфигурация:
port 443ccd:
proto tcp
dev tun
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key
dh /etc/openvpn/keys/dh2048.pem
server 10.8.0.0 255.255.255.0
push "dhcp-option DNS 8.8.8.8"
client-config-dir /etc/openvpn/ccd
auth SHA1
cipher AES-256-CBC
client-to-client
keepalive 10 120
max-clients 10
user nobody
group nogroup
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
verb 3
mute 20
ifconfig-push 10.8.0.50 10.8.0.1Ip сервера openvpn — 10.8.0.1/24
Ip клиента на микроте — 10.8.0.50
Микрот соединение поднял, но в статусе соединения поле с remote и local ip пустые. Но в роутинге появились динамические маршруты с верными адресами:
С микрота трансроут на ya.ru:
Пинг с ubuntu на микрот:
Включаю маршрут на микроте — все пакеты завернуть на openvpn:
Пинг с клиенткой машины за микротом (192.168.1.200) при включенном выше маршруте:
iptables:
Плиз, где я неверно сделал?
Благодарю
« Последнее редактирование: 17 Ноября 2019, 16:51:12 от YDenis »
- Печать
Страницы: [1] Вверх