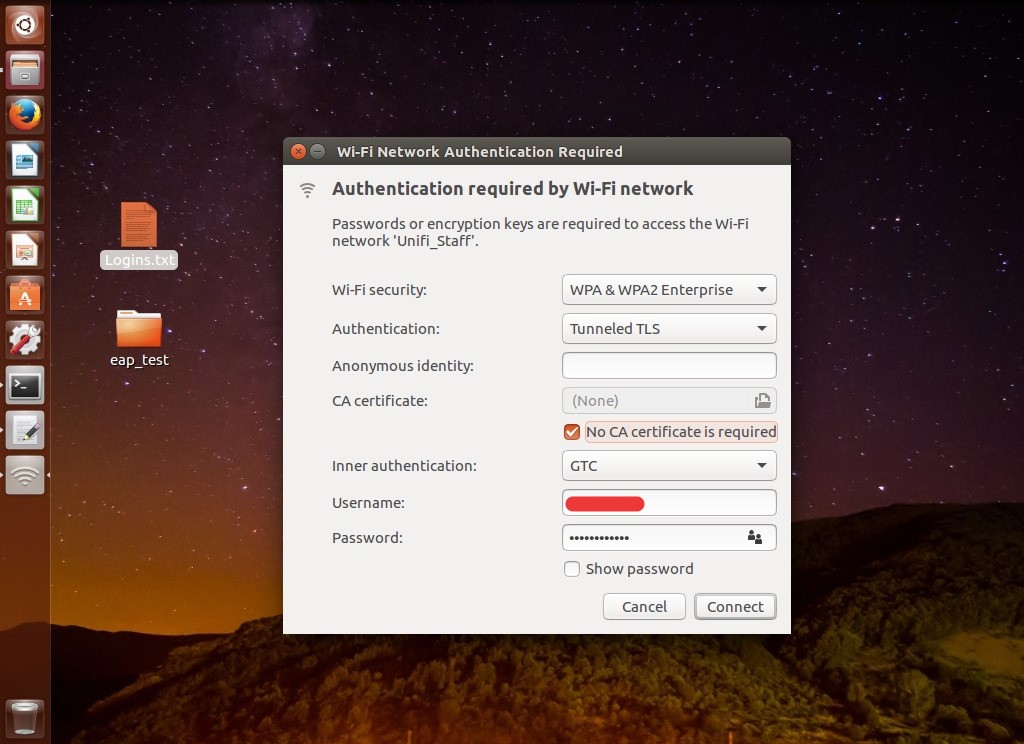
Hi @ALL.
Not sure if we have a bug, but i tried to get an AD authentication about ldap more then 4 days. I read a lot of documentation and testet a lot of stuff.
i have the following:
If i try to login via «radtest -x test testpwd 127.0.0.1:18120 0 testing123» on the linux console, everything is working via ldap. If i try this over the 802.1X AccessPoint, it doesn’t work.
If i try the same with a defined user in users like «bob Cleartext-Password := «hello»» over the accessPoint, it works fine.
Anything goes wrong with the password if we i use peap:
via console with domain User over inner-tunnel:
(1) Received Access-Request Id 7 from 127.0.0.1:48026 to 127.0.0.1:18120 length 74
(1) User-Name = «test»
(1) User-Password = «password»
(1) NAS-IP-Address = 192.168.8.27
(1) NAS-Port = 0
(1) Message-Authenticator = 0xc7c247ef109fb66332c18aab75068b33
(1) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(1) authorize {
(1) [files] = noop
(1) [mschap] = noop
(1) suffix: Checking for suffix after «@»
(1) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(1) suffix: No such realm «NULL»
(1) [suffix] = noop
(1) update control {
(1) Proxy-To-Realm := LOCAL
(1) } # update control = noop
(1) eap: No EAP-Message, not doing EAP
(1) [eap] = noop
(1) [expiration] = noop
(1) [logintime] = noop
rlm_ldap (ldap_domain): Reserved connection (0)
(1) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(1) ldap_domain: —> (sAMAccountName=test)
(1) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=test)», scope «sub»
(1) ldap_domain: Waiting for search result…
(1) ldap_domain: User object found at DN «CN=Test TEST,CN=Users,DC=domain,DC=local»
(1) ldap_domain: Processing user attributes
(1) ldap_domain: WARNING: No «known good» password added. Ensure the admin user has permission to read the password attribute
(1) ldap_domain: WARNING: PAP authentication will NOT work with Active Directory (if that is what you were trying to configure)
rlm_ldap (ldap_domain): Released connection (0)
rlm_ldap (ldap_domain): Need 5 more connections to reach 10 spares
rlm_ldap (ldap_domain): Opening additional connection (5), 1 of 27 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
(1) [ldap_domain] = ok
(1) if ((ok || updated) && User-Password) {
(1) if ((ok || updated) && User-Password) -> TRUE
(1) if ((ok || updated) && User-Password) {
(1) update {
(1) control:Auth-Type := LDAP
(1) } # update = noop
(1) } # if ((ok || updated) && User-Password) = noop
(1) [pap] = noop
(1) if (User-Password) {
(1) if (User-Password) -> TRUE
(1) if (User-Password) {
(1) update control {
(1) Auth-Type := LDAP
(1) } # update control = noop
(1) } # if (User-Password) = noop
(1) } # authorize = ok
(1) Found Auth-Type = LDAP
(1) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(1) Auth-Type LDAP {
rlm_ldap (ldap_domain): Reserved connection (1)
(1) ldap_domain: Login attempt by «test»
(1) ldap_domain: Using user DN from request «CN=Test TEST,CN=Users,DC=domain,DC=local»
(1) ldap_domain: Waiting for bind result…
(1) ldap_domain: Bind successful
(1) ldap_domain: Bind as user «CN=Test TEST,CN=Users,DC=domain,DC=local» was successful
rlm_ldap (ldap_domain): Released connection (1)
(1) [ldap_domain] = ok
(1) } # Auth-Type LDAP = ok
(1) Sent Access-Accept Id 7 from 127.0.0.1:18120 to 127.0.0.1:48026 length 0
(1) Finished request
Waking up in 0.3 seconds.
(0) Cleaning up request packet ID 130 with timestamp +4
Waking up in 4.6 seconds.
(1) Cleaning up request packet ID 7 with timestamp +9
Ready to process requests
via AccessPoint with domain User:
(2) Received Access-Request Id 42 from 192.168.2.250:3072 to 192.168.8.27:1812 length 178
(2) User-Name = «test»
(2) Service-Type = Framed-User
(2) NAS-IP-Address = 192.168.2.250
(2) NAS-Port = 10
(2) NAS-Port-Id = «10»
(2) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(2) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(2) Connect-Info = «CONNECT 54 Mbps 802.11g»
(2) NAS-Identifier = «AP-domain01»
(2) NAS-Port-Type = Wireless-802.11
(2) Framed-MTU = 1500
(2) EAP-Message = 0x020100090174657374
(2) Message-Authenticator = 0x83d8e6487c3977ae8116026c26702525
(2) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(2) authorize {
(2) [files] = noop
(2) [preprocess] = ok
(2) suffix: Checking for suffix after «@»
(2) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(2) suffix: No such realm «NULL»
(2) [suffix] = noop
(2) eap: Peer sent EAP Response (code 2) ID 1 length 9
(2) eap: EAP-Identity reply, returning ‘ok’ so we can short-circuit the rest of authorize
(2) [eap] = ok
(2) } # authorize = ok
(2) Found Auth-Type = EAP
(2) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(2) authenticate {
(2) eap: Peer sent packet with method EAP Identity (1)
(2) eap: Calling submodule eap_peap to process data
(2) eap_peap: Initiating new EAP-TLS session
(2) eap_peap: [eaptls start] = request
(2) eap: Sending EAP Request (code 1) ID 2 length 6
(2) eap: EAP session adding &reply:State = 0x714e61bf714c78fd
(2) [eap] = handled
(2) } # authenticate = handled
(2) Using Post-Auth-Type Challenge
(2) Post-Auth-Type sub-section not found. Ignoring.
(2) Sent Access-Challenge Id 42 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(2) EAP-Message = 0x010200061920
(2) Message-Authenticator = 0x00000000000000000000000000000000
(2) State = 0x714e61bf714c78fd13de40933f3a43c8
(2) Finished request
Waking up in 4.9 seconds.
(3) Received Access-Request Id 58 from 192.168.2.250:3072 to 192.168.8.27:1812 length 339
(3) User-Name = «test»
(3) Service-Type = Framed-User
(3) NAS-IP-Address = 192.168.2.250
(3) NAS-Port = 10
(3) NAS-Port-Id = «10»
(3) State = 0x714e61bf714c78fd13de40933f3a43c8
(3) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(3) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(3) Connect-Info = «CONNECT 54 Mbps 802.11g»
(3) NAS-Identifier = «AP-domain01»
(3) NAS-Port-Type = Wireless-802.11
(3) Framed-MTU = 1500
(3) EAP-Message = 0x0202009819800000008e160301008901000085030156162f87a13e4465c695b7754a35671de87e37f1c9c068c51ee0c258d39cc34f00004a00ffc024c023c00ac009c008c028c027c014c013c012c026c025c005c004c003c02ac029c00fc00ec00d006b0067003900330016003d003c0035002f000ac0
(3) Message-Authenticator = 0x1b3f4a72c416640c87d6f902d0effe2e
(3) session-state: No cached attributes
(3) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(3) authorize {
(3) [files] = noop
(3) [preprocess] = ok
(3) suffix: Checking for suffix after «@»
(3) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(3) suffix: No such realm «NULL»
(3) [suffix] = noop
(3) eap: Peer sent EAP Response (code 2) ID 2 length 152
(3) eap: Continuing tunnel setup
(3) [eap] = ok
(3) } # authorize = ok
(3) Found Auth-Type = EAP
(3) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(3) authenticate {
(3) eap: Expiring EAP session with state 0x714e61bf714c78fd
(3) eap: Finished EAP session with state 0x714e61bf714c78fd
(3) eap: Previous EAP request found for state 0x714e61bf714c78fd, released from the list
(3) eap: Peer sent packet with method EAP PEAP (25)
(3) eap: Calling submodule eap_peap to process data
(3) eap_peap: Continuing EAP-TLS
(3) eap_peap: Peer indicated complete TLS record size will be 142 bytes
(3) eap_peap: Got complete TLS record (142 bytes)
(3) eap_peap: [eaptls verify] = length included
(3) eap_peap: (other): before/accept initialization
(3) eap_peap: TLS_accept: before/accept initialization
(3) eap_peap: <<< TLS 1.0 Handshake [length 0089], ClientHello
(3) eap_peap: TLS_accept: SSLv3 read client hello A
(3) eap_peap: >>> TLS 1.0 Handshake [length 0039], ServerHello
(3) eap_peap: TLS_accept: SSLv3 write server hello A
(3) eap_peap: >>> TLS 1.0 Handshake [length 0964], Certificate
(3) eap_peap: TLS_accept: SSLv3 write certificate A
(3) eap_peap: >>> TLS 1.0 Handshake [length 014b], ServerKeyExchange
(3) eap_peap: TLS_accept: SSLv3 write key exchange A
(3) eap_peap: >>> TLS 1.0 Handshake [length 0004], ServerHelloDone
(3) eap_peap: TLS_accept: SSLv3 write server done A
(3) eap_peap: TLS_accept: SSLv3 flush data
(3) eap_peap: TLS_accept: Need to read more data: SSLv3 read client certificate A
(3) eap_peap: TLS_accept: Need to read more data: SSLv3 read client certificate A
(3) eap_peap: In SSL Handshake Phase
(3) eap_peap: In SSL Accept mode
(3) eap_peap: [eaptls process] = handled
(3) eap: Sending EAP Request (code 1) ID 3 length 1004
(3) eap: EAP session adding &reply:State = 0x714e61bf704d78fd
(3) [eap] = handled
(3) } # authenticate = handled
(3) Using Post-Auth-Type Challenge
(3) Post-Auth-Type sub-section not found. Ignoring.
(3) Sent Access-Challenge Id 58 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(3) EAP-Message = 0x010303ec19c000000b00160301003902000035030194873ddf6cee275a11fcde492d5ae2b8261f83dd50ed9063133a31be2e3d24b500c01400000dff01000100000b00040300010216030109640b00096000095d0005a7308205a33082048ba0030201020213720000003379461d9f383b20c900010000
(3) Message-Authenticator = 0x00000000000000000000000000000000
(3) State = 0x714e61bf704d78fd13de40933f3a43c8
(3) Finished request
Waking up in 4.9 seconds.
(4) Received Access-Request Id 46 from 192.168.2.250:3072 to 192.168.8.27:1812 length 193
(4) User-Name = «test»
(4) Service-Type = Framed-User
(4) NAS-IP-Address = 192.168.2.250
(4) NAS-Port = 10
(4) NAS-Port-Id = «10»
(4) State = 0x714e61bf704d78fd13de40933f3a43c8
(4) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(4) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(4) Connect-Info = «CONNECT 54 Mbps 802.11g»
(4) NAS-Identifier = «AP-domain01»
(4) NAS-Port-Type = Wireless-802.11
(4) Framed-MTU = 1500
(4) EAP-Message = 0x020300061900
(4) Message-Authenticator = 0xe7c2576faeb3228ae2d056b77bc6cce8
(4) session-state: No cached attributes
(4) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(4) authorize {
(4) [files] = noop
(4) [preprocess] = ok
(4) suffix: Checking for suffix after «@»
(4) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(4) suffix: No such realm «NULL»
(4) [suffix] = noop
(4) eap: Peer sent EAP Response (code 2) ID 3 length 6
(4) eap: Continuing tunnel setup
(4) [eap] = ok
(4) } # authorize = ok
(4) Found Auth-Type = EAP
(4) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(4) authenticate {
(4) eap: Expiring EAP session with state 0x714e61bf704d78fd
(4) eap: Finished EAP session with state 0x714e61bf704d78fd
(4) eap: Previous EAP request found for state 0x714e61bf704d78fd, released from the list
(4) eap: Peer sent packet with method EAP PEAP (25)
(4) eap: Calling submodule eap_peap to process data
(4) eap_peap: Continuing EAP-TLS
(4) eap_peap: Peer ACKed our handshake fragment
(4) eap_peap: [eaptls verify] = request
(4) eap_peap: [eaptls process] = handled
(4) eap: Sending EAP Request (code 1) ID 4 length 1000
(4) eap: EAP session adding &reply:State = 0x714e61bf734a78fd
(4) [eap] = handled
(4) } # authenticate = handled
(4) Using Post-Auth-Type Challenge
(4) Post-Auth-Type sub-section not found. Ignoring.
(4) Sent Access-Challenge Id 46 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(4) EAP-Message = 0x010403e81940b53081b206082b060105050730028681a56c6461703a2f2f2f434e3d6e656465636f253230476d624825323043412c434e3d4149412c434e3d5075626c69632532304b657925323053657276696365732c434e3d53657276696365732c434e3d436f6e66696775726174696f6e2c44433d
(4) Message-Authenticator = 0x00000000000000000000000000000000
(4) State = 0x714e61bf734a78fd13de40933f3a43c8
(4) Finished request
Waking up in 4.9 seconds.
(2) Cleaning up request packet ID 42 with timestamp +151
(3) Cleaning up request packet ID 58 with timestamp +151
(4) Cleaning up request packet ID 46 with timestamp +151
Ready to process requests
(5) Received Access-Request Id 216 from 192.168.2.250:3072 to 192.168.8.27:1812 length 193
(5) User-Name = «test»
(5) Service-Type = Framed-User
(5) NAS-IP-Address = 192.168.2.250
(5) NAS-Port = 10
(5) NAS-Port-Id = «10»
(5) State = 0x714e61bf734a78fd13de40933f3a43c8
(5) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(5) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(5) Connect-Info = «CONNECT 54 Mbps 802.11g»
(5) NAS-Identifier = «AP-domain01»
(5) NAS-Port-Type = Wireless-802.11
(5) Framed-MTU = 1500
(5) EAP-Message = 0x020400061900
(5) Message-Authenticator = 0xdf4b4a18dbd046ae4568ed5b900675ca
(5) session-state: No cached attributes
(5) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(5) authorize {
(5) [files] = noop
(5) [preprocess] = ok
(5) suffix: Checking for suffix after «@»
(5) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(5) suffix: No such realm «NULL»
(5) [suffix] = noop
(5) eap: Peer sent EAP Response (code 2) ID 4 length 6
(5) eap: Continuing tunnel setup
(5) [eap] = ok
(5) } # authorize = ok
(5) Found Auth-Type = EAP
(5) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(5) authenticate {
(5) eap: Expiring EAP session with state 0x714e61bf734a78fd
(5) eap: Finished EAP session with state 0x714e61bf734a78fd
(5) eap: Previous EAP request found for state 0x714e61bf734a78fd, released from the list
(5) eap: Peer sent packet with method EAP PEAP (25)
(5) eap: Calling submodule eap_peap to process data
(5) eap_peap: Continuing EAP-TLS
(5) eap_peap: Peer ACKed our handshake fragment
(5) eap_peap: [eaptls verify] = request
(5) eap_peap: [eaptls process] = handled
(5) eap: Sending EAP Request (code 1) ID 5 length 834
(5) eap: EAP session adding &reply:State = 0x714e61bf724b78fd
(5) [eap] = handled
(5) } # authenticate = handled
(5) Using Post-Auth-Type Challenge
(5) Post-Auth-Type sub-section not found. Ignoring.
(5) Sent Access-Challenge Id 216 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(5) EAP-Message = 0x01050342190068d99b627f3ca6561e6c1dcd0e8bb529b85d2515a36c2ba6f906ee9a223e619decfff2f24ef8674307735d591964d50ac988776a55970203010001a3819130818e301306092b060104018237140204061e0400430041300e0603551d0f0101ff040403020186300f0603551d130101ff04
(5) Message-Authenticator = 0x00000000000000000000000000000000
(5) State = 0x714e61bf724b78fd13de40933f3a43c8
(5) Finished request
Waking up in 4.9 seconds.
(6) Received Access-Request Id 228 from 192.168.2.250:3072 to 192.168.8.27:1812 length 331
(6) User-Name = «test»
(6) Service-Type = Framed-User
(6) NAS-IP-Address = 192.168.2.250
(6) NAS-Port = 10
(6) NAS-Port-Id = «10»
(6) State = 0x714e61bf724b78fd13de40933f3a43c8
(6) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(6) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(6) Connect-Info = «CONNECT 54 Mbps 802.11g»
(6) NAS-Identifier = «AP-domain01»
(6) NAS-Port-Type = Wireless-802.11
(6) Framed-MTU = 1500
(6) EAP-Message = 0x0205009019800000008616030100461000004241041ddb75e112e6a51620e1d90e79faf858ba440ee51859f6f36dbb3d61474b8fc891e7a246f576a1aef8372b95f81c96af01b2ba44e938f2dde2e5fa57032812201403010001011603010030680540b7b149e993c9f964d5e0a79cda35934c4c8e292f
(6) Message-Authenticator = 0x96295d1faa87d10973b6fe400102f545
(6) session-state: No cached attributes
(6) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(6) authorize {
(6) [files] = noop
(6) [preprocess] = ok
(6) suffix: Checking for suffix after «@»
(6) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(6) suffix: No such realm «NULL»
(6) [suffix] = noop
(6) eap: Peer sent EAP Response (code 2) ID 5 length 144
(6) eap: Continuing tunnel setup
(6) [eap] = ok
(6) } # authorize = ok
(6) Found Auth-Type = EAP
(6) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(6) authenticate {
(6) eap: Expiring EAP session with state 0x714e61bf724b78fd
(6) eap: Finished EAP session with state 0x714e61bf724b78fd
(6) eap: Previous EAP request found for state 0x714e61bf724b78fd, released from the list
(6) eap: Peer sent packet with method EAP PEAP (25)
(6) eap: Calling submodule eap_peap to process data
(6) eap_peap: Continuing EAP-TLS
(6) eap_peap: Peer indicated complete TLS record size will be 134 bytes
(6) eap_peap: Got complete TLS record (134 bytes)
(6) eap_peap: [eaptls verify] = length included
(6) eap_peap: <<< TLS 1.0 Handshake [length 0046], ClientKeyExchange
(6) eap_peap: TLS_accept: SSLv3 read client key exchange A
(6) eap_peap: <<< TLS 1.0 ChangeCipherSpec length 0001 eap_peap: <<< TLS 1.0 Handshake [length 0010], Finished
(6) eap_peap: TLS_accept: SSLv3 read finished A
(6) eap_peap: >>> TLS 1.0 ChangeCipherSpec length 0001 eap_peap: TLS_accept: SSLv3 write change cipher spec A
(6) eap_peap: >>> TLS 1.0 Handshake [length 0010], Finished
(6) eap_peap: TLS_accept: SSLv3 write finished A
(6) eap_peap: TLS_accept: SSLv3 flush data
(6) eap_peap: (other): SSL negotiation finished successfully
(6) eap_peap: SSL Connection Established
(6) eap_peap: [eaptls process] = handled
(6) eap: Sending EAP Request (code 1) ID 6 length 65
(6) eap: EAP session adding &reply:State = 0x714e61bf754878fd
(6) [eap] = handled
(6) } # authenticate = handled
(6) Using Post-Auth-Type Challenge
(6) Post-Auth-Type sub-section not found. Ignoring.
(6) Sent Access-Challenge Id 228 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(6) EAP-Message = 0x01060041190014030100010116030100301b8a91b9523361e58c472a6f4bedc223a3780b77e80492846d5f574cd2db238cdd236645e7e78ed7e706e2dd3aecd6a2
(6) Message-Authenticator = 0x00000000000000000000000000000000
(6) State = 0x714e61bf754878fd13de40933f3a43c8
(6) Finished request
Waking up in 4.8 seconds.
(7) Received Access-Request Id 77 from 192.168.2.250:3072 to 192.168.8.27:1812 length 193
(7) User-Name = «test»
(7) Service-Type = Framed-User
(7) NAS-IP-Address = 192.168.2.250
(7) NAS-Port = 10
(7) NAS-Port-Id = «10»
(7) State = 0x714e61bf754878fd13de40933f3a43c8
(7) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(7) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(7) Connect-Info = «CONNECT 54 Mbps 802.11g»
(7) NAS-Identifier = «AP-domain01»
(7) NAS-Port-Type = Wireless-802.11
(7) Framed-MTU = 1500
(7) EAP-Message = 0x020600061900
(7) Message-Authenticator = 0xaabe36b47f3a6a409dd2ec806970d983
(7) session-state: No cached attributes
(7) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(7) authorize {
(7) [files] = noop
(7) [preprocess] = ok
(7) suffix: Checking for suffix after «@»
(7) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(7) suffix: No such realm «NULL»
(7) [suffix] = noop
(7) eap: Peer sent EAP Response (code 2) ID 6 length 6
(7) eap: Continuing tunnel setup
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = EAP
(7) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(7) authenticate {
(7) eap: Expiring EAP session with state 0x714e61bf754878fd
(7) eap: Finished EAP session with state 0x714e61bf754878fd
(7) eap: Previous EAP request found for state 0x714e61bf754878fd, released from the list
(7) eap: Peer sent packet with method EAP PEAP (25)
(7) eap: Calling submodule eap_peap to process data
(7) eap_peap: Continuing EAP-TLS
(7) eap_peap: Peer ACKed our handshake fragment. handshake is finished
(7) eap_peap: [eaptls verify] = success
(7) eap_peap: [eaptls process] = success
(7) eap_peap: Session established. Decoding tunneled attributes
(7) eap_peap: PEAP state TUNNEL ESTABLISHED
(7) eap: Sending EAP Request (code 1) ID 7 length 43
(7) eap: EAP session adding &reply:State = 0x714e61bf744978fd
(7) [eap] = handled
(7) } # authenticate = handled
(7) Using Post-Auth-Type Challenge
(7) Post-Auth-Type sub-section not found. Ignoring.
(7) Sent Access-Challenge Id 77 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(7) EAP-Message = 0x0107002b19001703010020a6135f04ae6dffd42c8ef419d75113ac720759219e31f74d4247b6b610e9a071
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) State = 0x714e61bf744978fd13de40933f3a43c8
(7) Finished request
Waking up in 4.8 seconds.
(8) Received Access-Request Id 86 from 192.168.2.250:3072 to 192.168.8.27:1812 length 230
(8) User-Name = «test»
(8) Service-Type = Framed-User
(8) NAS-IP-Address = 192.168.2.250
(8) NAS-Port = 10
(8) NAS-Port-Id = «10»
(8) State = 0x714e61bf744978fd13de40933f3a43c8
(8) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(8) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(8) Connect-Info = «CONNECT 54 Mbps 802.11g»
(8) NAS-Identifier = «AP-domain01»
(8) NAS-Port-Type = Wireless-802.11
(8) Framed-MTU = 1500
(8) EAP-Message = 0x0207002b19001703010020aa7e796b21bdc47f3c2b751c50ffbf8aaaafc3ad47a3a4a6dab850e706bf7227
(8) Message-Authenticator = 0xb0ef481a7beafe09a46383286750ead8
(8) session-state: No cached attributes
(8) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(8) authorize {
(8) [files] = noop
(8) [preprocess] = ok
(8) suffix: Checking for suffix after «@»
(8) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(8) suffix: No such realm «NULL»
(8) [suffix] = noop
(8) eap: Peer sent EAP Response (code 2) ID 7 length 43
(8) eap: Continuing tunnel setup
(8) [eap] = ok
(8) } # authorize = ok
(8) Found Auth-Type = EAP
(8) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(8) authenticate {
(8) eap: Expiring EAP session with state 0x714e61bf744978fd
(8) eap: Finished EAP session with state 0x714e61bf744978fd
(8) eap: Previous EAP request found for state 0x714e61bf744978fd, released from the list
(8) eap: Peer sent packet with method EAP PEAP (25)
(8) eap: Calling submodule eap_peap to process data
(8) eap_peap: Continuing EAP-TLS
(8) eap_peap: [eaptls verify] = ok
(8) eap_peap: Done initial handshake
(8) eap_peap: [eaptls process] = ok
(8) eap_peap: Session established. Decoding tunneled attributes
(8) eap_peap: PEAP state WAITING FOR INNER IDENTITY
(8) eap_peap: Identity — test
(8) eap_peap: Got inner identity ‘test’
(8) eap_peap: Setting default EAP type for tunneled EAP session
(8) eap_peap: Got tunneled request
(8) eap_peap: EAP-Message = 0x020700090174657374
(8) eap_peap: Setting User-Name to test
(8) eap_peap: Sending tunneled request to inner-tunnel
(8) eap_peap: EAP-Message = 0x020700090174657374
(8) eap_peap: FreeRADIUS-Proxied-To = 127.0.0.1
(8) eap_peap: User-Name = «test»
(8) Virtual server inner-tunnel received request
(8) EAP-Message = 0x020700090174657374
(8) FreeRADIUS-Proxied-To = 127.0.0.1
(8) User-Name = «test»
(8) server inner-tunnel {
(8) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(8) authorize {
(8) [files] = noop
(8) [mschap] = noop
(8) suffix: Checking for suffix after «@»
(8) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(8) suffix: No such realm «NULL»
(8) [suffix] = noop
(8) update control {
(8) Proxy-To-Realm := LOCAL
(8) } # update control = noop
(8) eap: Peer sent EAP Response (code 2) ID 7 length 9
(8) eap: EAP-Identity reply, returning ‘ok’ so we can short-circuit the rest of authorize
(8) [eap] = ok
(8) } # authorize = ok
(8) Found Auth-Type = EAP
(8) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(8) authenticate {
(8) eap: Peer sent packet with method EAP Identity (1)
(8) eap: Calling submodule eap_mschapv2 to process data
(8) eap_mschapv2: Issuing Challenge
(8) eap: Sending EAP Request (code 1) ID 8 length 43
(8) eap: EAP session adding &reply:State = 0xbd1845cebd105fc4
(8) [eap] = handled
(8) } # authenticate = handled
(8) } # server inner-tunnel
(8) Virtual server sending reply
(8) EAP-Message = 0x0108002b1a0108002610ba684a0833e561a9e780eedf9829518f667265657261646975732d332e302e3131
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) State = 0xbd1845cebd105fc4a22a1c51082d7ecf
(8) eap_peap: Got tunneled reply code 11
(8) eap_peap: EAP-Message = 0x0108002b1a0108002610ba684a0833e561a9e780eedf9829518f667265657261646975732d332e302e3131
(8) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(8) eap_peap: State = 0xbd1845cebd105fc4a22a1c51082d7ecf
(8) eap_peap: Got tunneled reply RADIUS code 11
(8) eap_peap: EAP-Message = 0x0108002b1a0108002610ba684a0833e561a9e780eedf9829518f667265657261646975732d332e302e3131
(8) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(8) eap_peap: State = 0xbd1845cebd105fc4a22a1c51082d7ecf
(8) eap_peap: Got tunneled Access-Challenge
(8) eap: Sending EAP Request (code 1) ID 8 length 75
(8) eap: EAP session adding &reply:State = 0x714e61bf774678fd
(8) [eap] = handled
(8) } # authenticate = handled
(8) Using Post-Auth-Type Challenge
(8) Post-Auth-Type sub-section not found. Ignoring.
(8) Sent Access-Challenge Id 86 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(8) EAP-Message = 0x0108004b19001703010040c6831d9a1c5c30c64d40563c5fa21ee3cc103adbb4e99517563c9e67d781aefdd941ba0f19bc124976046e7471792eec1d4771c20abf67b78282a152634eed5e
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) State = 0x714e61bf774678fd13de40933f3a43c8
(8) Finished request
Waking up in 4.8 seconds.
(5) Cleaning up request packet ID 216 with timestamp +181
(6) Cleaning up request packet ID 228 with timestamp +181
(7) Cleaning up request packet ID 77 with timestamp +181
(8) Cleaning up request packet ID 86 with timestamp +181
Ready to process requests
(9) Received Access-Request Id 14 from 192.168.2.250:3072 to 192.168.8.27:1812 length 278
(9) User-Name = «test»
(9) Service-Type = Framed-User
(9) NAS-IP-Address = 192.168.2.250
(9) NAS-Port = 10
(9) NAS-Port-Id = «10»
(9) State = 0x714e61bf774678fd13de40933f3a43c8
(9) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(9) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(9) Connect-Info = «CONNECT 54 Mbps 802.11g»
(9) NAS-Identifier = «AP-domain01»
(9) NAS-Port-Type = Wireless-802.11
(9) Framed-MTU = 1500
(9) EAP-Message = 0x0208005b1900170301005041a588e579c1a63e94555d08bea2166f123e059dea3d7f8a17bcbfd8e4f4a54c876ceee7b33a4a101a4afd0dc078e77a3c8163b76b6c9e9567e6954214f5e1ec01cdafcd013db92c58ae136658519d20
(9) Message-Authenticator = 0xac0b3e273dede594c80988c13eaafd54
(9) session-state: No cached attributes
(9) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(9) authorize {
(9) [files] = noop
(9) [preprocess] = ok
(9) suffix: Checking for suffix after «@»
(9) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(9) suffix: No such realm «NULL»
(9) [suffix] = noop
(9) eap: Peer sent EAP Response (code 2) ID 8 length 91
(9) eap: Continuing tunnel setup
(9) [eap] = ok
(9) } # authorize = ok
(9) Found Auth-Type = EAP
(9) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(9) authenticate {
(9) eap: Expiring EAP session with state 0xbd1845cebd105fc4
(9) eap: Finished EAP session with state 0x714e61bf774678fd
(9) eap: Previous EAP request found for state 0x714e61bf774678fd, released from the list
(9) eap: Peer sent packet with method EAP PEAP (25)
(9) eap: Calling submodule eap_peap to process data
(9) eap_peap: Continuing EAP-TLS
(9) eap_peap: [eaptls verify] = ok
(9) eap_peap: Done initial handshake
(9) eap_peap: [eaptls process] = ok
(9) eap_peap: Session established. Decoding tunneled attributes
(9) eap_peap: PEAP state phase2
(9) eap_peap: EAP method MSCHAPv2 (26)
(9) eap_peap: Got tunneled request
(9) eap_peap: EAP-Message = 0x0208003f1a0208003a316670e0343c5cde7c22158c2f3b1e05bd0000000000000000e36cbc3c625721798db23c5fc199979df656a52246010d310074657374
(9) eap_peap: Setting User-Name to test
(9) eap_peap: Sending tunneled request to inner-tunnel
(9) eap_peap: EAP-Message = 0x0208003f1a0208003a316670e0343c5cde7c22158c2f3b1e05bd0000000000000000e36cbc3c625721798db23c5fc199979df656a52246010d310074657374
(9) eap_peap: FreeRADIUS-Proxied-To = 127.0.0.1
(9) eap_peap: User-Name = «test»
(9) eap_peap: State = 0xbd1845cebd105fc4a22a1c51082d7ecf
(9) Virtual server inner-tunnel received request
(9) EAP-Message = 0x0208003f1a0208003a316670e0343c5cde7c22158c2f3b1e05bd0000000000000000e36cbc3c625721798db23c5fc199979df656a52246010d310074657374
(9) FreeRADIUS-Proxied-To = 127.0.0.1
(9) User-Name = «test»
(9) State = 0xbd1845cebd105fc4a22a1c51082d7ecf
(9) server inner-tunnel {
(9) session-state: No cached attributes
(9) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(9) authorize {
(9) [files] = noop
(9) [mschap] = noop
(9) suffix: Checking for suffix after «@»
(9) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(9) suffix: No such realm «NULL»
(9) [suffix] = noop
(9) update control {
(9) Proxy-To-Realm := LOCAL
(9) } # update control = noop
(9) eap: Peer sent EAP Response (code 2) ID 8 length 63
(9) eap: No EAP Start, assuming it’s an on-going EAP conversation
(9) [eap] = updated
(9) [expiration] = noop
(9) [logintime] = noop
rlm_ldap (ldap_domain): Closing connection (2): Hit idle_timeout, was idle for 211 seconds
rlm_ldap (ldap_domain): Closing connection (3): Hit idle_timeout, was idle for 211 seconds
rlm_ldap (ldap_domain): Closing connection (4): Hit idle_timeout, was idle for 211 seconds
rlm_ldap (ldap_domain): Closing connection (0): Hit idle_timeout, was idle for 202 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): Closing connection (5): Hit idle_timeout, was idle for 202 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): Closing connection (1): Hit idle_timeout, was idle for 202 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): 0 of 0 connections in use. You may need to increase «spare»
rlm_ldap (ldap_domain): Opening additional connection (6), 1 of 32 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
rlm_ldap (ldap_domain): Reserved connection (6)
(9) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(9) ldap_domain: —> (sAMAccountName=test)
(9) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=test)», scope «sub»
(9) ldap_domain: Waiting for search result…
(9) ldap_domain: User object found at DN «CN=Test TEST,CN=Users,DC=domain,DC=local»
(9) ldap_domain: Processing user attributes
(9) ldap_domain: WARNING: No «known good» password added. Ensure the admin user has permission to read the password attribute
(9) ldap_domain: WARNING: PAP authentication will NOT work with Active Directory (if that is what you were trying to configure)
rlm_ldap (ldap_domain): Released connection (6)
rlm_ldap (ldap_domain): Need 2 more connections to reach 10 spares
rlm_ldap (ldap_domain): Opening additional connection (7), 1 of 31 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
(9) [ldap_domain] = ok
(9) if ((ok || updated) && User-Password) {
(9) if ((ok || updated) && User-Password) -> FALSE
(9) [pap] = noop
(9) if (User-Password) {
(9) if (User-Password) -> FALSE
(9) } # authorize = updated
(9) Found Auth-Type = EAP
(9) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(9) authenticate {
(9) eap: Expiring EAP session with state 0xbd1845cebd105fc4
(9) eap: Finished EAP session with state 0xbd1845cebd105fc4
(9) eap: Previous EAP request found for state 0xbd1845cebd105fc4, released from the list
(9) eap: Peer sent packet with method EAP MSCHAPv2 (26)
(9) eap: Calling submodule eap_mschapv2 to process data
(9) eap_mschapv2: # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(9) eap_mschapv2: Auth-Type MS-CHAP {
(9) mschap: WARNING: No Cleartext-Password configured. Cannot create NT-Password
(9) mschap: WARNING: No Cleartext-Password configured. Cannot create LM-Password
(9) mschap: Creating challenge hash with username: test
(9) mschap: Client is using MS-CHAPv2
(9) mschap: ERROR: FAILED: No NT/LM-Password. Cannot perform authentication
(9) mschap: ERROR: MS-CHAP2-Response is incorrect
(9) [mschap] = reject
(9) } # Auth-Type MS-CHAP = reject
(9) eap: Sending EAP Failure (code 4) ID 8 length 4
(9) eap: Freeing handler
(9) [eap] = reject
(9) } # authenticate = reject
(9) Failed to authenticate the user
(9) Using Post-Auth-Type Reject
(9) Post-Auth-Type sub-section not found. Ignoring.
(9) } # server inner-tunnel
(9) Virtual server sending reply
(9) MS-CHAP-Error = «10E=691 R=1 C=12a7b91273b8d4ea014f8d6353762c6f V=3 M=Authentication failed»
(9) EAP-Message = 0x04080004
(9) Message-Authenticator = 0x00000000000000000000000000000000
(9) eap_peap: Got tunneled reply code 3
(9) eap_peap: MS-CHAP-Error = «10E=691 R=1 C=12a7b91273b8d4ea014f8d6353762c6f V=3 M=Authentication failed»
(9) eap_peap: EAP-Message = 0x04080004
(9) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(9) eap_peap: Got tunneled reply RADIUS code 3
(9) eap_peap: MS-CHAP-Error = «10E=691 R=1 C=12a7b91273b8d4ea014f8d6353762c6f V=3 M=Authentication failed»
(9) eap_peap: EAP-Message = 0x04080004
(9) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(9) eap_peap: Tunneled authentication was rejected
(9) eap_peap: FAILURE
(9) eap: Sending EAP Request (code 1) ID 9 length 43
(9) eap: EAP session adding &reply:State = 0x714e61bf764778fd
(9) [eap] = handled
(9) } # authenticate = handled
(9) Using Post-Auth-Type Challenge
(9) Post-Auth-Type sub-section not found. Ignoring.
(9) Sent Access-Challenge Id 14 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(9) EAP-Message = 0x0109002b19001703010020b8c28870cb31e457ad24447c2dad4915f836138d395b9e74200fe48a71906242
(9) Message-Authenticator = 0x00000000000000000000000000000000
(9) State = 0x714e61bf764778fd13de40933f3a43c8
(9) Finished request
Waking up in 4.9 seconds.
(10) Received Access-Request Id 10 from 192.168.2.250:3072 to 192.168.8.27:1812 length 230
(10) User-Name = «test»
(10) Service-Type = Framed-User
(10) NAS-IP-Address = 192.168.2.250
(10) NAS-Port = 10
(10) NAS-Port-Id = «10»
(10) State = 0x714e61bf764778fd13de40933f3a43c8
(10) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(10) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(10) Connect-Info = «CONNECT 54 Mbps 802.11g»
(10) NAS-Identifier = «AP-domain01»
(10) NAS-Port-Type = Wireless-802.11
(10) Framed-MTU = 1500
(10) EAP-Message = 0x0209002b190017030100209f64c67a9a32761683b0d21eb6f28bfb8a42fa0a50d6ef3dfbf3815d7511e4a1
(10) Message-Authenticator = 0x26f3267a7372bfa1b0f71a27ccba5c9f
(10) session-state: No cached attributes
(10) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(10) authorize {
(10) [files] = noop
(10) [preprocess] = ok
(10) suffix: Checking for suffix after «@»
(10) suffix: No ‘@’ in User-Name = «test», looking up realm NULL
(10) suffix: No such realm «NULL»
(10) [suffix] = noop
(10) eap: Peer sent EAP Response (code 2) ID 9 length 43
(10) eap: Continuing tunnel setup
(10) [eap] = ok
(10) } # authorize = ok
(10) Found Auth-Type = EAP
(10) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(10) authenticate {
(10) eap: Expiring EAP session with state 0x714e61bf764778fd
(10) eap: Finished EAP session with state 0x714e61bf764778fd
(10) eap: Previous EAP request found for state 0x714e61bf764778fd, released from the list
(10) eap: Peer sent packet with method EAP PEAP (25)
(10) eap: Calling submodule eap_peap to process data
(10) eap_peap: Continuing EAP-TLS
(10) eap_peap: [eaptls verify] = ok
(10) eap_peap: Done initial handshake
(10) eap_peap: [eaptls process] = ok
(10) eap_peap: Session established. Decoding tunneled attributes
(10) eap_peap: PEAP state send tlv failure
(10) eap_peap: Received EAP-TLV response
(10) eap_peap: The users session was previously rejected: returning reject (again.)
(10) eap_peap: This means you need to read the PREVIOUS messages in the debug output
(10) eap_peap: to find out the reason why the user was rejected
(10) eap_peap: Look for «reject» or «fail». Those earlier messages will tell you
(10) eap_peap: what went wrong, and how to fix the problem
(10) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failed
(10) eap: Sending EAP Failure (code 4) ID 9 length 4
(10) eap: Failed in EAP select
(10) [eap] = invalid
(10) } # authenticate = invalid
(10) Failed to authenticate the user
(10) Using Post-Auth-Type Reject
(10) Post-Auth-Type sub-section not found. Ignoring.
(10) Delaying response for 1.000000 seconds
Waking up in 0.3 seconds.
Waking up in 0.6 seconds.
(10) Sending delayed response
(10) Sent Access-Reject Id 10 from 192.168.8.27:1812 to 192.168.2.250:3072 length 44
(10) EAP-Message = 0x04090004
(10) Message-Authenticator = 0x00000000000000000000000000000000
Waking up in 3.9 seconds.
(9) Cleaning up request packet ID 14 with timestamp +211
(10) Cleaning up request packet ID 10 with timestamp +211
Ready to process requests
default site:
server default {
listen {
type = auth
ipaddr = *
port = 0
# clients = per_socket_clients
limit {
max_connections = 0
lifetime = 0
idle_timeout = 30
}
}
listen {
ipaddr = *
port = 0
type = acct
# interface = eth0
# clients = per_socket_clients
limit {
idle_timeout = 0
lifetime = 0
max_connections = 0
}
}
authorize {
files
preprocess
suffix
eap {
ok = return
}
expiration
logintime
}
authenticate {
eap
}
preacct {
}
accounting {
detail
sql_domain
}
session {
radutmp
sql_domain
}
post-auth {
}
pre-proxy {
}
post-proxy {
}
}
inner-tunnel site:
server inner-tunnel {
listen {
ipaddr = 127.0.0.1
port = 18120
type = auth
}
authorize {
files
mschap
suffix
update control {
Proxy-To-Realm := LOCAL
}
eap {
ok = return
}
expiration
logintime
ldap_domain
if ((ok || updated) && User-Password) {
update {
control:Auth-Type := ldap
}
}
pap
if (User-Password) {
update control {
Auth-Type := ldap
}
}
}
authenticate {
Auth-Type PAP {
#ldap_domain
pap
}
Auth-Type CHAP {
chap
}
Auth-Type MS-CHAP {
mschap
}
Auth-Type LDAP {
ldap_domain
}
ldap_domain
eap
}
session {
radutmp
}
post-auth {
}
pre-proxy {
}
post-proxy {
}
}
eap configuration:
eap {
default_eap_type = peap
timer_expire = 60
ignore_unknown_eap_types = no
cisco_accounting_username_bug = no
max_sessions = ${max_requests}
md5 {
}
leap {
}
gtc {
auth_type = PAP
}
tls-config tls-common {
private_key_password = whatever
private_key_file = ${certdir}/nedeco/aaa.nedeco.local.key
certificate_file = ${certdir}/nedeco/aaa.nedeco.local.pem
ca_file = ${cadir}/nedeco/nedeco_CA.pem
dh_file = ${certdir}/dh
random_file = /dev/urandom
ca_path = ${cadir}
cipher_list = "DEFAULT"
ecdh_curve = "prime256v1"
cache {
enable = no
lifetime = 24 # hours
max_entries = 255
}
verify {
}
ocsp {
enable = no
override_cert_url = yes
url = "http://127.0.0.1/ocsp/"
}
}
tls {
tls = tls-common
}
ttls {
}
peap {
tls = tls-common
default_eap_type = mschapv2
copy_request_to_tunnel = no
use_tunneled_reply = no
proxy_tunneled_request_as_eap = no
virtual_server = "inner-tunnel"
}
mschapv2 {
}
}
the chap configuration:
chap {
# no configuration
}
the mschap configuration
mschap {
use_mppe = yes
require_encryption = yes
require_strong = yes
with_ntdomain_hack = yes
pool {
start = ${thread[pool].start_servers}
min = ${thread[pool].min_spare_servers}
max = ${thread[pool].max_servers}
spare = ${thread[pool].max_spare_servers}
uses = 0
retry_delay = 30
lifetime = 86400
cleanup_interval = 300
idle_timeout = 600
}
passchange {
}
retry_msg = "Re-enter (or reset) the password"
}
ldap configuration:
ldap ldap_domain {
server = ‘dc.domain.local’
port = 389
identity = ‘cn=Administrator,cn=Users,dc=domain,dc=local’
password = password
base_dn = ‘cn=Users,dc=domain,dc=local’
sasl {
realm = 'domain.local'
}
update {
control:Password-With-Header += 'userPassword'
control:NT-Password := 'ntPassword'
control: += 'radiusControlAttribute'
request: += 'radiusRequestAttribute'
reply: += 'radiusReplyAttribute'
}
edir_autz = yes
user {
base_dn = "${..base_dn}"
filter = "(sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})"
sasl {
}
scope = 'sub'
}
group {
base_dn = "${..base_dn}"
filter = '(objectClass=posixGroup)'
membership_attribute = 'memberOf'
}
profile {
}
client {
base_dn = "${..base_dn}"
filter = '(objectClass=radiusClient)'
}
attribute {
ipaddr = 'radiusClientIdentifier'
secret = 'radiusClientSecret'
}
}
accounting {
reference = "%{tolower:type.%{Acct-Status-Type}}"
type {
start {
update {
description := "Online at %S"
}
}
interim-update {
update {
description := "Last seen at %S"
}
}
stop {
update {
description := "Offline at %S"
}
}
}
}
post-auth {
update {
description := "Authenticated at %S"
}
}
options {
chase_referrals = yes
rebind = yes
res_timeout = 10
srv_timelimit = 3
net_timeout = 1
idle = 60
probes = 3
interval = 3
ldap_debug = 0x0028
}
tls {
start_tls = yes
require_cert = 'never'
}
pool {
start = ${thread[pool].start_servers}
min = ${thread[pool].min_spare_servers}
max = ${thread[pool].max_servers}
spare = ${thread[pool].max_spare_servers}
uses = 0
retry_delay = 30
lifetime = 0
idle_timeout = 60
}
}
radius Version: radiusd: FreeRADIUS Version 3.0.11 (git #7a659a2), for host x86_64-unknown-linux-gnu, built on Oct 7 2015 at 15:23:07
with user bob over console:
(0) Received Access-Request Id 213 from 127.0.0.1:45282 to 127.0.0.1:18120 length 73
(0) User-Name = «bob»
(0) User-Password = «hello»
(0) NAS-IP-Address = 192.168.8.27
(0) NAS-Port = 0
(0) Message-Authenticator = 0xbed4902174d4f8ff5f36492af1ae51de
(0) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(0) authorize {
(0) files: users: Matched entry bob at line 69
(0) [files] = ok
(0) [mschap] = noop
(0) suffix: Checking for suffix after «@»
(0) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(0) suffix: No such realm «NULL»
(0) [suffix] = noop
(0) update control {
(0) Proxy-To-Realm := LOCAL
(0) } # update control = noop
(0) eap: No EAP-Message, not doing EAP
(0) [eap] = noop
(0) [expiration] = noop
(0) [logintime] = noop
rlm_ldap (ldap_domain): Reserved connection (0)
(0) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(0) ldap_domain: —> (sAMAccountName=bob)
(0) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=bob)», scope «sub»
(0) ldap_domain: Waiting for search result…
(0) ldap_domain: Search returned no results
rlm_ldap (ldap_domain): Released connection (0)
rlm_ldap (ldap_domain): Need 5 more connections to reach 10 spares
rlm_ldap (ldap_domain): Opening additional connection (5), 1 of 27 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
(0) [ldap_domain] = notfound
(0) if ((ok || updated) && User-Password) {
(0) if ((ok || updated) && User-Password) -> FALSE
(0) [pap] = updated
(0) if (User-Password) {
(0) if (User-Password) -> TRUE
(0) if (User-Password) {
(0) update control {
(0) Auth-Type := LDAP
(0) } # update control = noop
(0) } # if (User-Password) = noop
(0) } # authorize = updated
(0) Found Auth-Type = LDAP
(0) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(0) Auth-Type LDAP {
rlm_ldap (ldap_domain): Reserved connection (1)
(0) ldap_domain: Login attempt by «bob»
(0) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(0) ldap_domain: —> (sAMAccountName=bob)
(0) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=bob)», scope «sub»
(0) ldap_domain: Waiting for search result…
(0) ldap_domain: Search returned no results
rlm_ldap (ldap_domain): Released connection (1)
(0) [ldap_domain] = notfound
(0) } # Auth-Type LDAP = notfound
(0) Failed to authenticate the user
(0) Using Post-Auth-Type Reject
(0) Post-Auth-Type sub-section not found. Ignoring.
(0) Delaying response for 1.000000 seconds
Waking up in 0.3 seconds.
Waking up in 0.6 seconds.
(0) Sending delayed response
(0) Sent Access-Reject Id 213 from 127.0.0.1:18120 to 127.0.0.1:45282 length 20
Waking up in 3.9 seconds.
(0) Cleaning up request packet ID 213 with timestamp +5
Ready to process requests
with user bob over AccessPoint:
(1) Received Access-Request Id 155 from 192.168.2.250:3072 to 192.168.8.27:1812 length 176
(1) User-Name = «bob»
(1) Service-Type = Framed-User
(1) NAS-IP-Address = 192.168.2.250
(1) NAS-Port = 10
(1) NAS-Port-Id = «10»
(1) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(1) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(1) Connect-Info = «CONNECT 54 Mbps 802.11g»
(1) NAS-Identifier = «AP-domain01»
(1) NAS-Port-Type = Wireless-802.11
(1) Framed-MTU = 1500
(1) EAP-Message = 0x0201000801626f62
(1) Message-Authenticator = 0x4680895a204b3df7d15d82558ff9e6ea
(1) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(1) authorize {
(1) files: users: Matched entry bob at line 69
(1) [files] = ok
(1) [preprocess] = ok
(1) suffix: Checking for suffix after «@»
(1) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(1) suffix: No such realm «NULL»
(1) [suffix] = noop
(1) eap: Peer sent EAP Response (code 2) ID 1 length 8
(1) eap: EAP-Identity reply, returning ‘ok’ so we can short-circuit the rest of authorize
(1) [eap] = ok
(1) } # authorize = ok
(1) Found Auth-Type = EAP
(1) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(1) authenticate {
(1) eap: Peer sent packet with method EAP Identity (1)
(1) eap: Calling submodule eap_peap to process data
(1) eap_peap: Initiating new EAP-TLS session
(1) eap_peap: [eaptls start] = request
(1) eap: Sending EAP Request (code 1) ID 2 length 6
(1) eap: EAP session adding &reply:State = 0x7322fa167320e364
(1) [eap] = handled
(1) } # authenticate = handled
(1) Using Post-Auth-Type Challenge
(1) Post-Auth-Type sub-section not found. Ignoring.
(1) Sent Access-Challenge Id 155 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(1) EAP-Message = 0x010200061920
(1) Message-Authenticator = 0x00000000000000000000000000000000
(1) State = 0x7322fa167320e3641bb25e163c98a49d
(1) Finished request
Waking up in 4.9 seconds.
(2) Received Access-Request Id 219 from 192.168.2.250:3072 to 192.168.8.27:1812 length 338
(2) User-Name = «bob»
(2) Service-Type = Framed-User
(2) NAS-IP-Address = 192.168.2.250
(2) NAS-Port = 10
(2) NAS-Port-Id = «10»
(2) State = 0x7322fa167320e3641bb25e163c98a49d
(2) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(2) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(2) Connect-Info = «CONNECT 54 Mbps 802.11g»
(2) NAS-Identifier = «AP-domain01»
(2) NAS-Port-Type = Wireless-802.11
(2) Framed-MTU = 1500
(2) EAP-Message = 0x0202009819800000008e1603010089010000850301561634f097408b8f9058fa38f1f34ce4854696e71aebecb3ae3cd9850b14d4cc00004a00ffc024c023c00ac009c008c028c027c014c013c012c026c025c005c004c003c02ac029c00fc00ec00d006b0067003900330016003d003c0035002f000ac0
(2) Message-Authenticator = 0x5309b752e9ed063e669ba97b7c937db8
(2) session-state: No cached attributes
(2) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(2) authorize {
(2) files: users: Matched entry bob at line 69
(2) [files] = ok
(2) [preprocess] = ok
(2) suffix: Checking for suffix after «@»
(2) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(2) suffix: No such realm «NULL»
(2) [suffix] = noop
(2) eap: Peer sent EAP Response (code 2) ID 2 length 152
(2) eap: Continuing tunnel setup
(2) [eap] = ok
(2) } # authorize = ok
(2) Found Auth-Type = EAP
(2) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(2) authenticate {
(2) eap: Expiring EAP session with state 0x7322fa167320e364
(2) eap: Finished EAP session with state 0x7322fa167320e364
(2) eap: Previous EAP request found for state 0x7322fa167320e364, released from the list
(2) eap: Peer sent packet with method EAP PEAP (25)
(2) eap: Calling submodule eap_peap to process data
(2) eap_peap: Continuing EAP-TLS
(2) eap_peap: Peer indicated complete TLS record size will be 142 bytes
(2) eap_peap: Got complete TLS record (142 bytes)
(2) eap_peap: [eaptls verify] = length included
(2) eap_peap: (other): before/accept initialization
(2) eap_peap: TLS_accept: before/accept initialization
(2) eap_peap: <<< TLS 1.0 Handshake [length 0089], ClientHello
(2) eap_peap: TLS_accept: SSLv3 read client hello A
(2) eap_peap: >>> TLS 1.0 Handshake [length 0039], ServerHello
(2) eap_peap: TLS_accept: SSLv3 write server hello A
(2) eap_peap: >>> TLS 1.0 Handshake [length 0964], Certificate
(2) eap_peap: TLS_accept: SSLv3 write certificate A
(2) eap_peap: >>> TLS 1.0 Handshake [length 014b], ServerKeyExchange
(2) eap_peap: TLS_accept: SSLv3 write key exchange A
(2) eap_peap: >>> TLS 1.0 Handshake [length 0004], ServerHelloDone
(2) eap_peap: TLS_accept: SSLv3 write server done A
(2) eap_peap: TLS_accept: SSLv3 flush data
(2) eap_peap: TLS_accept: Need to read more data: SSLv3 read client certificate A
(2) eap_peap: TLS_accept: Need to read more data: SSLv3 read client certificate A
(2) eap_peap: In SSL Handshake Phase
(2) eap_peap: In SSL Accept mode
(2) eap_peap: [eaptls process] = handled
(2) eap: Sending EAP Request (code 1) ID 3 length 1004
(2) eap: EAP session adding &reply:State = 0x7322fa167221e364
(2) [eap] = handled
(2) } # authenticate = handled
(2) Using Post-Auth-Type Challenge
(2) Post-Auth-Type sub-section not found. Ignoring.
(2) Sent Access-Challenge Id 219 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(2) EAP-Message = 0x010303ec19c000000b001603010039020000350301da2dfe903d7c37a7634c8742deb0c9de5ef2b5d7f4c0d4d8d1697deec243cc5600c01400000dff01000100000b00040300010216030109640b00096000095d0005a7308205a33082048ba0030201020213720000003379461d9f383b20c900010000
(2) Message-Authenticator = 0x00000000000000000000000000000000
(2) State = 0x7322fa167221e3641bb25e163c98a49d
(2) Finished request
Waking up in 4.9 seconds.
(1) Cleaning up request packet ID 155 with timestamp +61
(2) Cleaning up request packet ID 219 with timestamp +61
Ready to process requests
(3) Received Access-Request Id 54 from 192.168.2.250:3072 to 192.168.8.27:1812 length 192
(3) User-Name = «bob»
(3) Service-Type = Framed-User
(3) NAS-IP-Address = 192.168.2.250
(3) NAS-Port = 10
(3) NAS-Port-Id = «10»
(3) State = 0x7322fa167221e3641bb25e163c98a49d
(3) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(3) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(3) Connect-Info = «CONNECT 54 Mbps 802.11g»
(3) NAS-Identifier = «AP-domain01»
(3) NAS-Port-Type = Wireless-802.11
(3) Framed-MTU = 1500
(3) EAP-Message = 0x020300061900
(3) Message-Authenticator = 0xa70b8b8371dc21e4a3352e99bad8a487
(3) session-state: No cached attributes
(3) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(3) authorize {
(3) files: users: Matched entry bob at line 69
(3) [files] = ok
(3) [preprocess] = ok
(3) suffix: Checking for suffix after «@»
(3) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(3) suffix: No such realm «NULL»
(3) [suffix] = noop
(3) eap: Peer sent EAP Response (code 2) ID 3 length 6
(3) eap: Continuing tunnel setup
(3) [eap] = ok
(3) } # authorize = ok
(3) Found Auth-Type = EAP
(3) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(3) authenticate {
(3) eap: Expiring EAP session with state 0x7322fa167221e364
(3) eap: Finished EAP session with state 0x7322fa167221e364
(3) eap: Previous EAP request found for state 0x7322fa167221e364, released from the list
(3) eap: Peer sent packet with method EAP PEAP (25)
(3) eap: Calling submodule eap_peap to process data
(3) eap_peap: Continuing EAP-TLS
(3) eap_peap: Peer ACKed our handshake fragment
(3) eap_peap: [eaptls verify] = request
(3) eap_peap: [eaptls process] = handled
(3) eap: Sending EAP Request (code 1) ID 4 length 1000
(3) eap: EAP session adding &reply:State = 0x7322fa167126e364
(3) [eap] = handled
(3) } # authenticate = handled
(3) Using Post-Auth-Type Challenge
(3) Post-Auth-Type sub-section not found. Ignoring.
(3) Sent Access-Challenge Id 54 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(3) EAP-Message = 0x010403e81940b53081b206082b060105050730028681a56c6461703a2f2f2f434e3d6e656465636f253230476d624825323043412c434e3d4149412c434e3d5075626c69632532304b657925323053657276696365732c434e3d53657276696365732c434e3d436f6e66696775726174696f6e2c44433d
(3) Message-Authenticator = 0x00000000000000000000000000000000
(3) State = 0x7322fa167126e3641bb25e163c98a49d
(3) Finished request
Waking up in 4.9 seconds.
(4) Received Access-Request Id 29 from 192.168.2.250:3072 to 192.168.8.27:1812 length 192
(4) User-Name = «bob»
(4) Service-Type = Framed-User
(4) NAS-IP-Address = 192.168.2.250
(4) NAS-Port = 10
(4) NAS-Port-Id = «10»
(4) State = 0x7322fa167126e3641bb25e163c98a49d
(4) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(4) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(4) Connect-Info = «CONNECT 54 Mbps 802.11g»
(4) NAS-Identifier = «AP-domain01»
(4) NAS-Port-Type = Wireless-802.11
(4) Framed-MTU = 1500
(4) EAP-Message = 0x020400061900
(4) Message-Authenticator = 0x841ce2c1c9b797b25c3aff5bba5e059d
(4) session-state: No cached attributes
(4) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(4) authorize {
(4) files: users: Matched entry bob at line 69
(4) [files] = ok
(4) [preprocess] = ok
(4) suffix: Checking for suffix after «@»
(4) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(4) suffix: No such realm «NULL»
(4) [suffix] = noop
(4) eap: Peer sent EAP Response (code 2) ID 4 length 6
(4) eap: Continuing tunnel setup
(4) [eap] = ok
(4) } # authorize = ok
(4) Found Auth-Type = EAP
(4) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(4) authenticate {
(4) eap: Expiring EAP session with state 0x7322fa167126e364
(4) eap: Finished EAP session with state 0x7322fa167126e364
(4) eap: Previous EAP request found for state 0x7322fa167126e364, released from the list
(4) eap: Peer sent packet with method EAP PEAP (25)
(4) eap: Calling submodule eap_peap to process data
(4) eap_peap: Continuing EAP-TLS
(4) eap_peap: Peer ACKed our handshake fragment
(4) eap_peap: [eaptls verify] = request
(4) eap_peap: [eaptls process] = handled
(4) eap: Sending EAP Request (code 1) ID 5 length 834
(4) eap: EAP session adding &reply:State = 0x7322fa167027e364
(4) [eap] = handled
(4) } # authenticate = handled
(4) Using Post-Auth-Type Challenge
(4) Post-Auth-Type sub-section not found. Ignoring.
(4) Sent Access-Challenge Id 29 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(4) EAP-Message = 0x01050342190068d99b627f3ca6561e6c1dcd0e8bb529b85d2515a36c2ba6f906ee9a223e619decfff2f24ef8674307735d591964d50ac988776a55970203010001a3819130818e301306092b060104018237140204061e0400430041300e0603551d0f0101ff040403020186300f0603551d130101ff04
(4) Message-Authenticator = 0x00000000000000000000000000000000
(4) State = 0x7322fa167027e3641bb25e163c98a49d
(4) Finished request
Waking up in 4.9 seconds.
(5) Received Access-Request Id 215 from 192.168.2.250:3072 to 192.168.8.27:1812 length 330
(5) User-Name = «bob»
(5) Service-Type = Framed-User
(5) NAS-IP-Address = 192.168.2.250
(5) NAS-Port = 10
(5) NAS-Port-Id = «10»
(5) State = 0x7322fa167027e3641bb25e163c98a49d
(5) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(5) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(5) Connect-Info = «CONNECT 54 Mbps 802.11g»
(5) NAS-Identifier = «AP-domain01»
(5) NAS-Port-Type = Wireless-802.11
(5) Framed-MTU = 1500
(5) EAP-Message = 0x0205009019800000008616030100461000004241048075a5ca05d012d0fd77b0f9e1664c5ce577eda72a1368e0a8e78fd9072b0a6e04ce9f7f3cb1339ca9fd58bdc40e0afce833807f1c4035e532e91d07e8d45fdb1403010001011603010030bff39ef9cf9a0400269ae5fd8888ba5c4940b72599bca5
(5) Message-Authenticator = 0xfaa49416d762fdf0846428951f176829
(5) session-state: No cached attributes
(5) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(5) authorize {
(5) files: users: Matched entry bob at line 69
(5) [files] = ok
(5) [preprocess] = ok
(5) suffix: Checking for suffix after «@»
(5) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(5) suffix: No such realm «NULL»
(5) [suffix] = noop
(5) eap: Peer sent EAP Response (code 2) ID 5 length 144
(5) eap: Continuing tunnel setup
(5) [eap] = ok
(5) } # authorize = ok
(5) Found Auth-Type = EAP
(5) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(5) authenticate {
(5) eap: Expiring EAP session with state 0x7322fa167027e364
(5) eap: Finished EAP session with state 0x7322fa167027e364
(5) eap: Previous EAP request found for state 0x7322fa167027e364, released from the list
(5) eap: Peer sent packet with method EAP PEAP (25)
(5) eap: Calling submodule eap_peap to process data
(5) eap_peap: Continuing EAP-TLS
(5) eap_peap: Peer indicated complete TLS record size will be 134 bytes
(5) eap_peap: Got complete TLS record (134 bytes)
(5) eap_peap: [eaptls verify] = length included
(5) eap_peap: <<< TLS 1.0 Handshake [length 0046], ClientKeyExchange
(5) eap_peap: TLS_accept: SSLv3 read client key exchange A
(5) eap_peap: <<< TLS 1.0 ChangeCipherSpec length 0001 eap_peap: <<< TLS 1.0 Handshake [length 0010], Finished
(5) eap_peap: TLS_accept: SSLv3 read finished A
(5) eap_peap: >>> TLS 1.0 ChangeCipherSpec length 0001 eap_peap: TLS_accept: SSLv3 write change cipher spec A
(5) eap_peap: >>> TLS 1.0 Handshake [length 0010], Finished
(5) eap_peap: TLS_accept: SSLv3 write finished A
(5) eap_peap: TLS_accept: SSLv3 flush data
(5) eap_peap: (other): SSL negotiation finished successfully
(5) eap_peap: SSL Connection Established
(5) eap_peap: [eaptls process] = handled
(5) eap: Sending EAP Request (code 1) ID 6 length 65
(5) eap: EAP session adding &reply:State = 0x7322fa167724e364
(5) [eap] = handled
(5) } # authenticate = handled
(5) Using Post-Auth-Type Challenge
(5) Post-Auth-Type sub-section not found. Ignoring.
(5) Sent Access-Challenge Id 215 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(5) EAP-Message = 0x010600411900140301000101160301003055bf61e75ec8b42df54cc0a1eab6dd5e274dd8db872c3a18e2616a373eda384dcffbfa8de45423ccb8890ee689f1f4cb
(5) Message-Authenticator = 0x00000000000000000000000000000000
(5) State = 0x7322fa167724e3641bb25e163c98a49d
(5) Finished request
Waking up in 4.8 seconds.
(6) Received Access-Request Id 116 from 192.168.2.250:3072 to 192.168.8.27:1812 length 192
(6) User-Name = «bob»
(6) Service-Type = Framed-User
(6) NAS-IP-Address = 192.168.2.250
(6) NAS-Port = 10
(6) NAS-Port-Id = «10»
(6) State = 0x7322fa167724e3641bb25e163c98a49d
(6) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(6) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(6) Connect-Info = «CONNECT 54 Mbps 802.11g»
(6) NAS-Identifier = «AP-domain01»
(6) NAS-Port-Type = Wireless-802.11
(6) Framed-MTU = 1500
(6) EAP-Message = 0x020600061900
(6) Message-Authenticator = 0xb468a031e9e011addea02301e58313cb
(6) session-state: No cached attributes
(6) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(6) authorize {
(6) files: users: Matched entry bob at line 69
(6) [files] = ok
(6) [preprocess] = ok
(6) suffix: Checking for suffix after «@»
(6) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(6) suffix: No such realm «NULL»
(6) [suffix] = noop
(6) eap: Peer sent EAP Response (code 2) ID 6 length 6
(6) eap: Continuing tunnel setup
(6) [eap] = ok
(6) } # authorize = ok
(6) Found Auth-Type = EAP
(6) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(6) authenticate {
(6) eap: Expiring EAP session with state 0x7322fa167724e364
(6) eap: Finished EAP session with state 0x7322fa167724e364
(6) eap: Previous EAP request found for state 0x7322fa167724e364, released from the list
(6) eap: Peer sent packet with method EAP PEAP (25)
(6) eap: Calling submodule eap_peap to process data
(6) eap_peap: Continuing EAP-TLS
(6) eap_peap: Peer ACKed our handshake fragment. handshake is finished
(6) eap_peap: [eaptls verify] = success
(6) eap_peap: [eaptls process] = success
(6) eap_peap: Session established. Decoding tunneled attributes
(6) eap_peap: PEAP state TUNNEL ESTABLISHED
(6) eap: Sending EAP Request (code 1) ID 7 length 43
(6) eap: EAP session adding &reply:State = 0x7322fa167625e364
(6) [eap] = handled
(6) } # authenticate = handled
(6) Using Post-Auth-Type Challenge
(6) Post-Auth-Type sub-section not found. Ignoring.
(6) Sent Access-Challenge Id 116 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(6) EAP-Message = 0x0107002b19001703010020ba0b3d2b7d949cf1727c708a6c6ac8606201ef325b4408284fbf4115ccf1e60c
(6) Message-Authenticator = 0x00000000000000000000000000000000
(6) State = 0x7322fa167625e3641bb25e163c98a49d
(6) Finished request
Waking up in 4.8 seconds.
(7) Received Access-Request Id 108 from 192.168.2.250:3072 to 192.168.8.27:1812 length 229
(7) User-Name = «bob»
(7) Service-Type = Framed-User
(7) NAS-IP-Address = 192.168.2.250
(7) NAS-Port = 10
(7) NAS-Port-Id = «10»
(7) State = 0x7322fa167625e3641bb25e163c98a49d
(7) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(7) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(7) Connect-Info = «CONNECT 54 Mbps 802.11g»
(7) NAS-Identifier = «AP-domain01»
(7) NAS-Port-Type = Wireless-802.11
(7) Framed-MTU = 1500
(7) EAP-Message = 0x0207002b190017030100205db45e564856f45f7af7cc0f3ec2e54ef3aab9a99f6cb2d9944b2c53980f0bde
(7) Message-Authenticator = 0xd2092e590023b1e9af89a2d5f9927801
(7) session-state: No cached attributes
(7) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(7) authorize {
(7) files: users: Matched entry bob at line 69
(7) [files] = ok
(7) [preprocess] = ok
(7) suffix: Checking for suffix after «@»
(7) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(7) suffix: No such realm «NULL»
(7) [suffix] = noop
(7) eap: Peer sent EAP Response (code 2) ID 7 length 43
(7) eap: Continuing tunnel setup
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = EAP
(7) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(7) authenticate {
(7) eap: Expiring EAP session with state 0x7322fa167625e364
(7) eap: Finished EAP session with state 0x7322fa167625e364
(7) eap: Previous EAP request found for state 0x7322fa167625e364, released from the list
(7) eap: Peer sent packet with method EAP PEAP (25)
(7) eap: Calling submodule eap_peap to process data
(7) eap_peap: Continuing EAP-TLS
(7) eap_peap: [eaptls verify] = ok
(7) eap_peap: Done initial handshake
(7) eap_peap: [eaptls process] = ok
(7) eap_peap: Session established. Decoding tunneled attributes
(7) eap_peap: PEAP state WAITING FOR INNER IDENTITY
(7) eap_peap: Identity — bob
(7) eap_peap: Got inner identity ‘bob’
(7) eap_peap: Setting default EAP type for tunneled EAP session
(7) eap_peap: Got tunneled request
(7) eap_peap: EAP-Message = 0x0207000801626f62
(7) eap_peap: Setting User-Name to bob
(7) eap_peap: Sending tunneled request to inner-tunnel
(7) eap_peap: EAP-Message = 0x0207000801626f62
(7) eap_peap: FreeRADIUS-Proxied-To = 127.0.0.1
(7) eap_peap: User-Name = «bob»
(7) Virtual server inner-tunnel received request
(7) EAP-Message = 0x0207000801626f62
(7) FreeRADIUS-Proxied-To = 127.0.0.1
(7) User-Name = «bob»
(7) server inner-tunnel {
(7) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(7) authorize {
(7) files: users: Matched entry bob at line 69
(7) [files] = ok
(7) [mschap] = noop
(7) suffix: Checking for suffix after «@»
(7) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(7) suffix: No such realm «NULL»
(7) [suffix] = noop
(7) update control {
(7) Proxy-To-Realm := LOCAL
(7) } # update control = noop
(7) eap: Peer sent EAP Response (code 2) ID 7 length 8
(7) eap: EAP-Identity reply, returning ‘ok’ so we can short-circuit the rest of authorize
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = EAP
(7) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(7) authenticate {
(7) eap: Peer sent packet with method EAP Identity (1)
(7) eap: Calling submodule eap_mschapv2 to process data
(7) eap_mschapv2: Issuing Challenge
(7) eap: Sending EAP Request (code 1) ID 8 length 43
(7) eap: EAP session adding &reply:State = 0xa0773c37a07f2697
(7) [eap] = handled
(7) } # authenticate = handled
(7) } # server inner-tunnel
(7) Virtual server sending reply
(7) EAP-Message = 0x0108002b1a0108002610499c5c634fd1c53afcf63e2a20dc0dbd667265657261646975732d332e302e3131
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) State = 0xa0773c37a07f269794c91e639bc0d99c
(7) eap_peap: Got tunneled reply code 11
(7) eap_peap: EAP-Message = 0x0108002b1a0108002610499c5c634fd1c53afcf63e2a20dc0dbd667265657261646975732d332e302e3131
(7) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(7) eap_peap: State = 0xa0773c37a07f269794c91e639bc0d99c
(7) eap_peap: Got tunneled reply RADIUS code 11
(7) eap_peap: EAP-Message = 0x0108002b1a0108002610499c5c634fd1c53afcf63e2a20dc0dbd667265657261646975732d332e302e3131
(7) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(7) eap_peap: State = 0xa0773c37a07f269794c91e639bc0d99c
(7) eap_peap: Got tunneled Access-Challenge
(7) eap: Sending EAP Request (code 1) ID 8 length 75
(7) eap: EAP session adding &reply:State = 0x7322fa16752ae364
(7) [eap] = handled
(7) } # authenticate = handled
(7) Using Post-Auth-Type Challenge
(7) Post-Auth-Type sub-section not found. Ignoring.
(7) Sent Access-Challenge Id 108 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(7) EAP-Message = 0x0108004b19001703010040d8e4f8be725dc18720efdaf547282b5b876c26c5fdbea8c05f380bf87ea452cdf6938d2793528a14f784d70ad64f66ebcb6998cae0cdb2ec340b208caf7adddc
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) State = 0x7322fa16752ae3641bb25e163c98a49d
(7) Finished request
Waking up in 4.8 seconds.
(8) Received Access-Request Id 50 from 192.168.2.250:3072 to 192.168.8.27:1812 length 277
(8) User-Name = «bob»
(8) Service-Type = Framed-User
(8) NAS-IP-Address = 192.168.2.250
(8) NAS-Port = 10
(8) NAS-Port-Id = «10»
(8) State = 0x7322fa16752ae3641bb25e163c98a49d
(8) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(8) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(8) Connect-Info = «CONNECT 54 Mbps 802.11g»
(8) NAS-Identifier = «AP-domain01»
(8) NAS-Port-Type = Wireless-802.11
(8) Framed-MTU = 1500
(8) EAP-Message = 0x0208005b1900170301005035d828d77a9cd3611fc5b79937ff5a2749a2d013a332137a52fe3a206717cde550258b9914956f0b2f88dd7f4491d6d52e7b97a1fd99e59010b7e346d7692d768748d8d8efb3995a7d8d58863b0e3c9f
(8) Message-Authenticator = 0x27a3860baf38d3fd1d0e7f85c85a398e
(8) session-state: No cached attributes
(8) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(8) authorize {
(8) files: users: Matched entry bob at line 69
(8) [files] = ok
(8) [preprocess] = ok
(8) suffix: Checking for suffix after «@»
(8) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(8) suffix: No such realm «NULL»
(8) [suffix] = noop
(8) eap: Peer sent EAP Response (code 2) ID 8 length 91
(8) eap: Continuing tunnel setup
(8) [eap] = ok
(8) } # authorize = ok
(8) Found Auth-Type = EAP
(8) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(8) authenticate {
(8) eap: Expiring EAP session with state 0xa0773c37a07f2697
(8) eap: Finished EAP session with state 0x7322fa16752ae364
(8) eap: Previous EAP request found for state 0x7322fa16752ae364, released from the list
(8) eap: Peer sent packet with method EAP PEAP (25)
(8) eap: Calling submodule eap_peap to process data
(8) eap_peap: Continuing EAP-TLS
(8) eap_peap: [eaptls verify] = ok
(8) eap_peap: Done initial handshake
(8) eap_peap: [eaptls process] = ok
(8) eap_peap: Session established. Decoding tunneled attributes
(8) eap_peap: PEAP state phase2
(8) eap_peap: EAP method MSCHAPv2 (26)
(8) eap_peap: Got tunneled request
(8) eap_peap: EAP-Message = 0x0208003e1a02080039318c4c5187cb6d3acc25374e1a666c6ebd00000000000000005c626c4605277cd81e771f53707290714956dfed703aa31a00626f62
(8) eap_peap: Setting User-Name to bob
(8) eap_peap: Sending tunneled request to inner-tunnel
(8) eap_peap: EAP-Message = 0x0208003e1a02080039318c4c5187cb6d3acc25374e1a666c6ebd00000000000000005c626c4605277cd81e771f53707290714956dfed703aa31a00626f62
(8) eap_peap: FreeRADIUS-Proxied-To = 127.0.0.1
(8) eap_peap: User-Name = «bob»
(8) eap_peap: State = 0xa0773c37a07f269794c91e639bc0d99c
(8) Virtual server inner-tunnel received request
(8) EAP-Message = 0x0208003e1a02080039318c4c5187cb6d3acc25374e1a666c6ebd00000000000000005c626c4605277cd81e771f53707290714956dfed703aa31a00626f62
(8) FreeRADIUS-Proxied-To = 127.0.0.1
(8) User-Name = «bob»
(8) State = 0xa0773c37a07f269794c91e639bc0d99c
(8) server inner-tunnel {
(8) session-state: No cached attributes
(8) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(8) authorize {
(8) files: users: Matched entry bob at line 69
(8) [files] = ok
(8) [mschap] = noop
(8) suffix: Checking for suffix after «@»
(8) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(8) suffix: No such realm «NULL»
(8) [suffix] = noop
(8) update control {
(8) Proxy-To-Realm := LOCAL
(8) } # update control = noop
(8) eap: Peer sent EAP Response (code 2) ID 8 length 62
(8) eap: No EAP Start, assuming it’s an on-going EAP conversation
(8) [eap] = updated
(8) [expiration] = noop
(8) [logintime] = noop
rlm_ldap (ldap_domain): Closing connection (2): Hit idle_timeout, was idle for 90 seconds
rlm_ldap (ldap_domain): Closing connection (3): Hit idle_timeout, was idle for 90 seconds
rlm_ldap (ldap_domain): Closing connection (4): Hit idle_timeout, was idle for 90 seconds
rlm_ldap (ldap_domain): Closing connection (0): Hit idle_timeout, was idle for 85 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): Closing connection (5): Hit idle_timeout, was idle for 85 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): Closing connection (1): Hit idle_timeout, was idle for 85 seconds
rlm_ldap (ldap_domain): You probably need to lower «min»
rlm_ldap (ldap_domain): 0 of 0 connections in use. You may need to increase «spare»
rlm_ldap (ldap_domain): Opening additional connection (6), 1 of 32 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
rlm_ldap (ldap_domain): Reserved connection (6)
(8) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(8) ldap_domain: —> (sAMAccountName=bob)
(8) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=bob)», scope «sub»
(8) ldap_domain: Waiting for search result…
(8) ldap_domain: Search returned no results
rlm_ldap (ldap_domain): Released connection (6)
rlm_ldap (ldap_domain): Need 2 more connections to reach 10 spares
rlm_ldap (ldap_domain): Opening additional connection (7), 1 of 31 pending slots used
rlm_ldap (ldap_domain): Connecting to ldap://dc.domain.local:389
rlm_ldap (ldap_domain): Waiting for bind result…
rlm_ldap (ldap_domain): Bind successful
(8) [ldap_domain] = notfound
(8) if ((ok || updated) && User-Password) {
(8) if ((ok || updated) && User-Password) -> FALSE
(8) pap: WARNING: Auth-Type already set. Not setting to PAP
(8) [pap] = noop
(8) if (User-Password) {
(8) if (User-Password) -> FALSE
(8) } # authorize = updated
(8) Found Auth-Type = EAP
(8) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(8) authenticate {
(8) eap: Expiring EAP session with state 0xa0773c37a07f2697
(8) eap: Finished EAP session with state 0xa0773c37a07f2697
(8) eap: Previous EAP request found for state 0xa0773c37a07f2697, released from the list
(8) eap: Peer sent packet with method EAP MSCHAPv2 (26)
(8) eap: Calling submodule eap_mschapv2 to process data
(8) eap_mschapv2: # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(8) eap_mschapv2: Auth-Type MS-CHAP {
(8) mschap: Found Cleartext-Password, hashing to create NT-Password
(8) mschap: Found Cleartext-Password, hashing to create LM-Password
(8) mschap: Creating challenge hash with username: bob
(8) mschap: Client is using MS-CHAPv2
(8) mschap: Adding MS-CHAPv2 MPPE keys
(8) [mschap] = ok
(8) } # Auth-Type MS-CHAP = ok
(8) MSCHAP Success
(8) eap: Sending EAP Request (code 1) ID 9 length 51
(8) eap: EAP session adding &reply:State = 0xa0773c37a17e2697
(8) [eap] = handled
(8) } # authenticate = handled
(8) } # server inner-tunnel
(8) Virtual server sending reply
(8) EAP-Message = 0x010900331a0308002e533d41303037313532323444323837324439434432334437363345354535313444393146323441424646
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) State = 0xa0773c37a17e269794c91e639bc0d99c
(8) eap_peap: Got tunneled reply code 11
(8) eap_peap: EAP-Message = 0x010900331a0308002e533d41303037313532323444323837324439434432334437363345354535313444393146323441424646
(8) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(8) eap_peap: State = 0xa0773c37a17e269794c91e639bc0d99c
(8) eap_peap: Got tunneled reply RADIUS code 11
(8) eap_peap: EAP-Message = 0x010900331a0308002e533d41303037313532323444323837324439434432334437363345354535313444393146323441424646
(8) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(8) eap_peap: State = 0xa0773c37a17e269794c91e639bc0d99c
(8) eap_peap: Got tunneled Access-Challenge
(8) eap: Sending EAP Request (code 1) ID 9 length 91
(8) eap: EAP session adding &reply:State = 0x7322fa16742be364
(8) [eap] = handled
(8) } # authenticate = handled
(8) Using Post-Auth-Type Challenge
(8) Post-Auth-Type sub-section not found. Ignoring.
(8) Sent Access-Challenge Id 50 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(8) EAP-Message = 0x0109005b19001703010050859ea345fa5ac6b144a9e42ed8bff28f0b2320a237ac8370d029cb70f52d482a0d76da88b813e4df36252cb6397300ec8d8d78b8622e934b5283b40ee5a8abe75b64b6667666fd21f0cac5fcc60f98ed
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) State = 0x7322fa16742be3641bb25e163c98a49d
(8) Finished request
Waking up in 4.7 seconds.
(9) Received Access-Request Id 168 from 192.168.2.250:3072 to 192.168.8.27:1812 length 229
(9) User-Name = «bob»
(9) Service-Type = Framed-User
(9) NAS-IP-Address = 192.168.2.250
(9) NAS-Port = 10
(9) NAS-Port-Id = «10»
(9) State = 0x7322fa16742be3641bb25e163c98a49d
(9) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(9) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(9) Connect-Info = «CONNECT 54 Mbps 802.11g»
(9) NAS-Identifier = «AP-domain01»
(9) NAS-Port-Type = Wireless-802.11
(9) Framed-MTU = 1500
(9) EAP-Message = 0x0209002b19001703010020ef0b01a2e1a2ce59b84fcd3a36f6101ad280a2da6de9e3034ee1142fd2c2d87b
(9) Message-Authenticator = 0xcbef8a5238f2450a86714781617cb91e
(9) session-state: No cached attributes
(9) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(9) authorize {
(9) files: users: Matched entry bob at line 69
(9) [files] = ok
(9) [preprocess] = ok
(9) suffix: Checking for suffix after «@»
(9) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(9) suffix: No such realm «NULL»
(9) [suffix] = noop
(9) eap: Peer sent EAP Response (code 2) ID 9 length 43
(9) eap: Continuing tunnel setup
(9) [eap] = ok
(9) } # authorize = ok
(9) Found Auth-Type = EAP
(9) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(9) authenticate {
(9) eap: Expiring EAP session with state 0xa0773c37a17e2697
(9) eap: Finished EAP session with state 0x7322fa16742be364
(9) eap: Previous EAP request found for state 0x7322fa16742be364, released from the list
(9) eap: Peer sent packet with method EAP PEAP (25)
(9) eap: Calling submodule eap_peap to process data
(9) eap_peap: Continuing EAP-TLS
(9) eap_peap: [eaptls verify] = ok
(9) eap_peap: Done initial handshake
(9) eap_peap: [eaptls process] = ok
(9) eap_peap: Session established. Decoding tunneled attributes
(9) eap_peap: PEAP state phase2
(9) eap_peap: EAP method MSCHAPv2 (26)
(9) eap_peap: Got tunneled request
(9) eap_peap: EAP-Message = 0x020900061a03
(9) eap_peap: Setting User-Name to bob
(9) eap_peap: Sending tunneled request to inner-tunnel
(9) eap_peap: EAP-Message = 0x020900061a03
(9) eap_peap: FreeRADIUS-Proxied-To = 127.0.0.1
(9) eap_peap: User-Name = «bob»
(9) eap_peap: State = 0xa0773c37a17e269794c91e639bc0d99c
(9) Virtual server inner-tunnel received request
(9) EAP-Message = 0x020900061a03
(9) FreeRADIUS-Proxied-To = 127.0.0.1
(9) User-Name = «bob»
(9) State = 0xa0773c37a17e269794c91e639bc0d99c
(9) server inner-tunnel {
(9) session-state: No cached attributes
(9) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(9) authorize {
(9) files: users: Matched entry bob at line 69
(9) [files] = ok
(9) [mschap] = noop
(9) suffix: Checking for suffix after «@»
(9) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(9) suffix: No such realm «NULL»
(9) [suffix] = noop
(9) update control {
(9) Proxy-To-Realm := LOCAL
(9) } # update control = noop
(9) eap: Peer sent EAP Response (code 2) ID 9 length 6
(9) eap: No EAP Start, assuming it’s an on-going EAP conversation
(9) [eap] = updated
(9) [expiration] = noop
(9) [logintime] = noop
rlm_ldap (ldap_domain): Reserved connection (6)
(9) ldap_domain: EXPAND (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})
(9) ldap_domain: —> (sAMAccountName=bob)
(9) ldap_domain: Performing search in «cn=Users,dc=domain,dc=local» with filter «(sAMAccountName=bob)», scope «sub»
(9) ldap_domain: Waiting for search result…
(9) ldap_domain: Search returned no results
rlm_ldap (ldap_domain): Released connection (6)
(9) [ldap_domain] = notfound
(9) if ((ok || updated) && User-Password) {
(9) if ((ok || updated) && User-Password) -> FALSE
(9) pap: WARNING: Auth-Type already set. Not setting to PAP
(9) [pap] = noop
(9) if (User-Password) {
(9) if (User-Password) -> FALSE
(9) } # authorize = updated
(9) Found Auth-Type = EAP
(9) # Executing group from file /usr/local/etc/raddb/sites-enabled/inner-tunnel-domain
(9) authenticate {
(9) eap: Expiring EAP session with state 0xa0773c37a17e2697
(9) eap: Finished EAP session with state 0xa0773c37a17e2697
(9) eap: Previous EAP request found for state 0xa0773c37a17e2697, released from the list
(9) eap: Peer sent packet with method EAP MSCHAPv2 (26)
(9) eap: Calling submodule eap_mschapv2 to process data
(9) eap: Sending EAP Success (code 3) ID 9 length 4
(9) eap: Freeing handler
(9) [eap] = ok
(9) } # authenticate = ok
(9) } # server inner-tunnel
(9) Virtual server sending reply
(9) MS-MPPE-Encryption-Policy = Encryption-Required
(9) MS-MPPE-Encryption-Types = 4
(9) MS-MPPE-Send-Key = 0xc40f7d178a19b383691a863644016790
(9) MS-MPPE-Recv-Key = 0x1f490d8645a1a87f762bc38738f37149
(9) EAP-Message = 0x03090004
(9) Message-Authenticator = 0x00000000000000000000000000000000
(9) User-Name = «bob»
(9) eap_peap: Got tunneled reply code 2
(9) eap_peap: MS-MPPE-Encryption-Policy = Encryption-Required
(9) eap_peap: MS-MPPE-Encryption-Types = 4
(9) eap_peap: MS-MPPE-Send-Key = 0xc40f7d178a19b383691a863644016790
(9) eap_peap: MS-MPPE-Recv-Key = 0x1f490d8645a1a87f762bc38738f37149
(9) eap_peap: EAP-Message = 0x03090004
(9) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(9) eap_peap: User-Name = «bob»
(9) eap_peap: Got tunneled reply RADIUS code 2
(9) eap_peap: MS-MPPE-Encryption-Policy = Encryption-Required
(9) eap_peap: MS-MPPE-Encryption-Types = 4
(9) eap_peap: MS-MPPE-Send-Key = 0xc40f7d178a19b383691a863644016790
(9) eap_peap: MS-MPPE-Recv-Key = 0x1f490d8645a1a87f762bc38738f37149
(9) eap_peap: EAP-Message = 0x03090004
(9) eap_peap: Message-Authenticator = 0x00000000000000000000000000000000
(9) eap_peap: User-Name = «bob»
(9) eap_peap: Tunneled authentication was successful
(9) eap_peap: SUCCESS
(9) eap: Sending EAP Request (code 1) ID 10 length 43
(9) eap: EAP session adding &reply:State = 0x7322fa167b28e364
(9) [eap] = handled
(9) } # authenticate = handled
(9) Using Post-Auth-Type Challenge
(9) Post-Auth-Type sub-section not found. Ignoring.
(9) Sent Access-Challenge Id 168 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(9) EAP-Message = 0x010a002b190017030100209ebe5c178129e763273f16ddd56f3f5e123f6a27587c42e7e480f2874b2985ac
(9) Message-Authenticator = 0x00000000000000000000000000000000
(9) State = 0x7322fa167b28e3641bb25e163c98a49d
(9) Finished request
Waking up in 4.7 seconds.
(10) Received Access-Request Id 89 from 192.168.2.250:3072 to 192.168.8.27:1812 length 229
(10) User-Name = «bob»
(10) Service-Type = Framed-User
(10) NAS-IP-Address = 192.168.2.250
(10) NAS-Port = 10
(10) NAS-Port-Id = «10»
(10) State = 0x7322fa167b28e3641bb25e163c98a49d
(10) Called-Station-Id = «0E-0B-6B-2F-12-67:domain 8021X»
(10) Calling-Station-Id = «B8-E8-56-41-2C-2A»
(10) Connect-Info = «CONNECT 54 Mbps 802.11g»
(10) NAS-Identifier = «AP-domain01»
(10) NAS-Port-Type = Wireless-802.11
(10) Framed-MTU = 1500
(10) EAP-Message = 0x020a002b19001703010020ae6a94676019ad167b393353926209ead29be3185de748899304ff6a50957c1a
(10) Message-Authenticator = 0x64a847e3ae161cf68eccda80a2f11f16
(10) session-state: No cached attributes
(10) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/domain
(10) authorize {
(10) files: users: Matched entry bob at line 69
(10) [files] = ok
(10) [preprocess] = ok
(10) suffix: Checking for suffix after «@»
(10) suffix: No ‘@’ in User-Name = «bob», looking up realm NULL
(10) suffix: No such realm «NULL»
(10) [suffix] = noop
(10) eap: Peer sent EAP Response (code 2) ID 10 length 43
(10) eap: Continuing tunnel setup
(10) [eap] = ok
(10) } # authorize = ok
(10) Found Auth-Type = EAP
(10) # Executing group from file /usr/local/etc/raddb/sites-enabled/domain
(10) authenticate {
(10) eap: Expiring EAP session with state 0x7322fa167b28e364
(10) eap: Finished EAP session with state 0x7322fa167b28e364
(10) eap: Previous EAP request found for state 0x7322fa167b28e364, released from the list
(10) eap: Peer sent packet with method EAP PEAP (25)
(10) eap: Calling submodule eap_peap to process data
(10) eap_peap: Continuing EAP-TLS
(10) eap_peap: [eaptls verify] = ok
(10) eap_peap: Done initial handshake
(10) eap_peap: [eaptls process] = ok
(10) eap_peap: Session established. Decoding tunneled attributes
(10) eap_peap: PEAP state send tlv success
(10) eap_peap: Received EAP-TLV response
(10) eap_peap: Success
(10) eap: Sending EAP Success (code 3) ID 10 length 4
(10) eap: Freeing handler
(10) [eap] = ok
(10) } # authenticate = ok
(10) Sent Access-Accept Id 89 from 192.168.8.27:1812 to 192.168.2.250:3072 length 0
(10) MS-MPPE-Recv-Key = 0xa16bc44cb5331571c4f3d362fd38e1bb11a2670822b415e53eb7ebbc67c2cb93
(10) MS-MPPE-Send-Key = 0xbd2081385181a9a51170b7fa40bfd3b32e396b6e7d46f9b5369a38d64be27cc8
(10) EAP-Message = 0x030a0004
(10) Message-Authenticator = 0x00000000000000000000000000000000
(10) User-Name = «bob»
(10) Finished request
Waking up in 4.7 seconds.
(3) Cleaning up request packet ID 54 with timestamp +90
(4) Cleaning up request packet ID 29 with timestamp +90
Waking up in 0.1 seconds.
(5) Cleaning up request packet ID 215 with timestamp +90
(6) Cleaning up request packet ID 116 with timestamp +90
(7) Cleaning up request packet ID 108 with timestamp +90
(8) Cleaning up request packet ID 50 with timestamp +90
(9) Cleaning up request packet ID 168 with timestamp +90
(10) Cleaning up request packet ID 89 with timestamp +90
Ready to process requests
I think that everything goes wrong with encrypt/decrypt the Domain User password or no User-Password is given after eap or something else. I tried a lot of stuff, but nothing works.
users configuration
bob Cleartext-Password := «hello»
DEFAULT Framed-Protocol == PPP
Framed-Protocol = PPP,
Framed-Compression = Van-Jacobson-TCP-IP
DEFAULT Hint == «CSLIP»
Framed-Protocol = SLIP,
Framed-Compression = Van-Jacobson-TCP-IP
DEFAULT Hint == «SLIP»
Framed-Protocol = SLIP
Messages:
(7) ldap_nedeco: Processing user attributes
(7) ldap_nedeco: WARNING: No «known good» password added. Ensure the admin user has permission to read the password attribute
(7) ldap_nedeco: WARNING: PAP authentication will NOT work with Active Directory (if that is what you were trying to configure)
rlm_ldap (ldap_nedeco): Released connection (0)
..
(7) mschap: WARNING: No Cleartext-Password configured. Cannot create NT-Password
(7) mschap: WARNING: No Cleartext-Password configured. Cannot create LM-Password
(7) mschap: Creating challenge hash with username: test
(7) mschap: Client is using MS-CHAPv2
(7) mschap: ERROR: FAILED: No NT/LM-Password. Cannot perform authentication
(7) mschap: ERROR: MS-CHAP2-Response is incorrect
..
(8) eap_peap: Received EAP-TLV response
(8) eap_peap: The users session was previously rejected: returning reject (again.)
(8) eap_peap: This means you need to read the PREVIOUS messages in the debug output
(8) eap_peap: to find out the reason why the user was rejected
(8) eap_peap: Look for «reject» or «fail». Those earlier messages will tell you
(8) eap_peap: what went wrong, and how to fix the problem
(8) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failed
..
Any Idea?
This topic has been deleted. Only users with topic management privileges can see it.
FreeRADIUS 3.x package NTLM problem since upgrade to PFS 2.4.
Before I used Freeradius 2. Since PFS 2.4 doesn’t have Freeradius 2 package anymore I tried Freeradius 3.
OpenVPN and Captive portal both work with Freeradius 3 but wpa2-eap does not work anymore. I have 2 sites both same problem
The error i’m seeing is:
Oct 13 13:23:27 radiusd 48737 (38) Login incorrect (mschap: FAILED: No NT/LM-Password. Cannot perform authentication): [SomeUsername] (from client AP2 port 0 via TLS tunnel)
Oct 13 13:23:20 radiusd 48737 (30) Login incorrect (eap_peap: The users session was previously rejected: returning reject (again.)): [anonymous] (from client AP3 port 0 cli F0-D7-AA-xx-xx-xx)
The last line has to do with the first one obviously.
I don’t know how to go forward other then turning back to PFS 2.3.4 with Freeradius 2, which I did, and wpa-eap is working again.
Tonight I upgraded to pfS 2.3.5. Again forced to use Freeradius 3 where I before used Freeradius 2 in 2.3.4 and again the same problem as with pfS 2.4:
Login incorrect (mschap: FAILED: No NT/LM-Password. Cannot perform authentication): [Username/<via auth-type=»eap»>] (from client AP2 port 0 via TLS tunnel)
Tomorrow re-install pfS 2.3.4 again :(</via>
I would realy like to upgrade to 2.4.
I’m not the only one with this problem:
https://forum.pfsense.org/index.php?topic=131883.msg737459#msg737459
How can I fix this?
I have no clou what to do other then staying on pfS 2.3.4.
I didn’t use 2.0, so can’t say this is it for sure, but when setting up 3, I ran into that issue. I found I had to store passwords as cleartext for it to work, not MD5. Thats on the 2.4 line though. Hopefully that helps you
I use NT-Password for most users I also have a test user with Cleartext-Password set. No difference they generate the same error message, I don’t use md5. The 2 sites I have are in use I can’t use them to test and/or try things. I have no other choice then to stay on pfSense 2.3 with Freeradius 2 for the time being. At the moment I have no idea how to figure this out.
Thank you for responding.
Since I couldn’t fix the above problem I have setup a external freeradius 2 server so I can uninstall freeradius from pfsense system. To be able to upgrade to the latest pfsense version.
Now I want to uninstall Freeradius 2 from pfSense 2.3.4 but it isn’t showing in the installed packages list. How do I uninstall Freeradius wen it is not showing in the packages manager?
I don’t want any left over packages files etc of freeradius wen i’m going to upgrade pfSense.
@Gé:
….
I don’t want any left over packages files etc of freeradius wen i’m going to upgrade pfSense.
Hi,
Throw out all references to Freeradius in the config.xml
Then, do a clean install using 2.4.x — import your config, and done.
(10 minutes max).
Clean system guaranteed.
Okay great advice, thanks!
Try again on with FreeRADIUS 3.x package version 0.15.5, this should be fixed now.
Today I upgraded to pfSense 2.4.2-1. I didn’t want to install Freeeradius anymore in pfSense since it didn’t work anymore for me. But then you posted the problem should be fixed in the latest version. Today I tested it but sadly it is still the same.
I will keep the Freeradius 3 setup on pfSense for testing new package versions in the future.
Till it is fixed I’m using my other Freeradius 2.
Hi,
today I’ve set up freeradius3 for WPA-EAP, an it is working, but only with «clear text passwords».
If I change it to «MD5 Password», I get error «mschap: FAILED: No NT/LM-Password. Cannot perform authentication»
Is there any way to use non clear text password storage with working WPA-EAP?
Hi Zizi,
I have a freeradius 3 in pfsense and a external freeradius 2 in a vps. The last one works with plain password ánd nthash paswd’s.
I have a test user with a plain passwd this is not working in fact non of my users can login wen i use the pfsense radius 3 server package. If i use the external freeradius 2 server i installed in a virtual debian system all users work 100% nthash and plan text password are no difference then. I have even md5 test users that do work also.
I keep the FR3 package on pfsense on hand so I can test it if and wen there are updates in the hope one day it will work again.
@Zizi:
Hi,
today I’ve set up freeradius3 for WPA-EAP, an it is working, but only with «clear text passwords».
If I change it to «MD5 Password», I get error «mschap: FAILED: No NT/LM-Password. Cannot perform authentication»Is there any way to use non clear text password storage with working WPA-EAP?
Same here.
Модератор: SLEDopit
-
rolano
- Сообщения: 845
- Статус: еще один юзер FreeBSD
- ОС: какая-то
Не проходит проверка пользователя pptp через FreeRADIUS
Взываю к Коллективному разуму, ибо свой уже почти сломался
Имеется:
Debian 5.0 i386 в VMWare. pptp, pppd, FreeRADIUS — из поставок Debian. К системе в VMWare пытаюсь подключиться по ВПН из WindowsXP SP3
Проблема: проверка пользователя из chap-secrets проходит нормально, а через Радиус — нет.
Код: Выделить всё
rad_recv: Access-Request packet from host 127.0.0.1 port 56882, id=53, length=148
Service-Type = Framed-User
Framed-Protocol = PPP
User-Name = "user1"
MS-CHAP-Challenge = 0x70558a5f04f775f367995743de9a2c0d
MS-CHAP2-Response = 0x3900d1e4fe5f18710ab0d39c8b2b9de8a63b000000000000000084455fb01e77df9aca7c602ac9
b0de1b7b2e56c413d7f06c
Calling-Station-Id = "192.168.146.1"
NAS-IP-Address = 127.0.1.1
NAS-Port = 0
+- entering group authorize
++[preprocess] returns ok
rlm_mschap: Found MS-CHAP attributes. Setting 'Auth-Type = mschap'
++[mschap] returns ok
rad_check_password: Found Auth-Type mschap
auth: type "MSCHAP"
+- entering group authenticate
rlm_mschap: No Cleartext-Password configured. Cannot create LM-Password.
rlm_mschap: No Cleartext-Password configured. Cannot create NT-Password.
rlm_mschap: Told to do MS-CHAPv2 for user1 with NT-Password
rlm_mschap: FAILED: No NT/LM-Password. Cannot perform authentication.
rlm_mschap: FAILED: MS-CHAP2-Response is incorrect
++[mschap] returns reject
auth: Failed to validate the user.
Login incorrect: [user1/<via Auth-Type = mschap>] (from client localhost port 0 cli 192.168.146.1)
Delaying reject of request 0 for 1 seconds
Going to the next request
Waking up in 0.9 seconds.
Sending delayed reject for request 0
Sending Access-Reject of id 53 to 127.0.0.1 port 56882
MS-CHAP-Error = "9E=691 R=1"
Waking up in 4.9 seconds.
Cleaning up request 0 ID 53 with timestamp +8
Ready to process requests.Может быть, кто сталкивался с таким поведением?
Я знаю только то, что ничего не знаю … потому и обречен вечно учиться.
-
skor
- Сообщения: 419
- ОС: RTFM-OS v127.0.0.1
Re: Не проходит проверка пользователя pptp через FreeRADIUS
Сообщение
skor » 28.04.2009 17:31
В базе пароли как храните?
Попробуйте пароли хранить в таком виде:
Код: Выделить всё
select * from radcheck;
+-----+----------+----------------------+----+-----------------------+
| id | UserName | Attribute | op | Value |
+-----+----------+----------------------+----+-----------------------+
| 1 | user123 | Password-With-Header | := | {cleartext}secret1234 |
+-----+----------+----------------------+----+-----------------------+Либо Cleartext-Password вместо Password-With-Header, тогда пароль без {cleartext}
This post documents the process of integrating FreeRADIUS with Google G Suite (now Workspace) using Secure LDAP. FreeRADIUS will be used to authenticate Ubiquiti Unifi WPA2 Enterprise WiFi users. The configurations presented here are taken from this wonderful repository. While the repo uses Docker, we will be implementing these settings in FreeRADIUS directly. These settings were tested on Debian 10.
First, follow steps 1-3 given in Google’s support article and also generate access credentials. At the end of these steps, you’ll have a certificate and key along with your access credentials.
Then, install FreeRADIUS and its required packages:
apt update && apt upgrade
apt -y install freeradius freeradius-ldap freeradius-utilsUpload the certificate and key files downloaded from Google G-Suite Admin account into the following directory:
/etc/freeradius/3.0/certs/Rename those files to:
ldap-client.crt
ldap-client.key
Next, use a text editor like nano to edit /etc/freeradius/3.0/clients.conf:
nano /etc/freeradius/3.0/clients.confAdd the following lines at the end (replace 192.168.1.0/24 with your LAN subnet and testing123 with a more secure secret):
client unifi {
ipaddr = 192.168.1.0/24
secret = testing123
}
Use Ctrl + X to save and exit.
Edit the default virtual server:
nano /etc/freeradius/3.0/sites-enabled/defaultIn authorize section after pap add this:
if (User-Password) {
update control {
Auth-Type := ldap
}
}
In authenticate section:
authenticate {
Auth-Type PAP {
ldap
}
Uncomment ldap:
# Auth-Type LDAP {
ldap
# }
Save and exit.
The same changes need to be done in /etc/freeradius/3.0/sites-enabled/inner-tunnel to edit the inner-tunnel virtual server.
After that execute the following commands as root to enable ldap module:
cd /etc/freeradius/3.0/mods-enabled
ln -s ../mods-available/ldap ldap
Now, edit the ldap module:
nano /etc/freeradius/3.0/mods-enabled/ldap
server = 'ldaps://ldap.google.com'
port = 636
Enter your access credentials here:
identity = 'foo'
password = barEnter your domain here:
base_dn = 'dc=example,dc=com'
In tls section:
start_tls = no
certificate_file = /etc/freeradius/3.0/certs/ldap-client.crt
private_key_file = /etc/freeradius/3.0/certs/ldap-client.key
require_cert = 'allow'
Save and exit.
Next, set up the eap module:
nano /etc/freeradius/3.0/mods-enabled/eapIn eap section:
default_eap_type = ttlsIn ttls section:
default_eap_type = gtcSave and exit. Finally, set the proxy settings:
nano /etc/freeradius/3.0/proxy.confEnter your domain at the end of the file:
realm example.com {
}
Save and exit.
Use the following command to restart FreeRADIUS service for new settings to take effect:
systemctl restart freeradius.serviceFreeRADIUS settings are now complete. On the Unifi Controller, go to Settings -> Wireless Networks and either create a new wireless network or edit an existing network. In Security select WPA Enterprise:
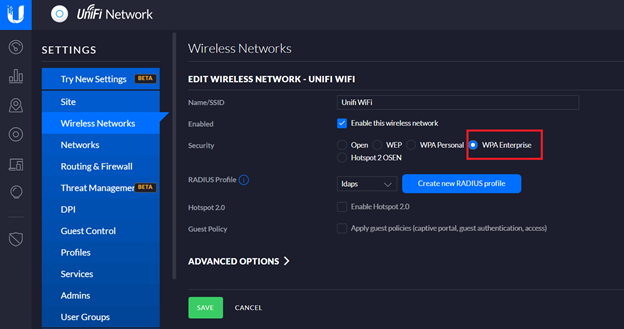
It will require a RADIUS Profile to be specified. Click on “Create new RADIUS profile”. Enter a name for the profile and specify the IP address of your RADIUS server and its shared secret (created earlier).
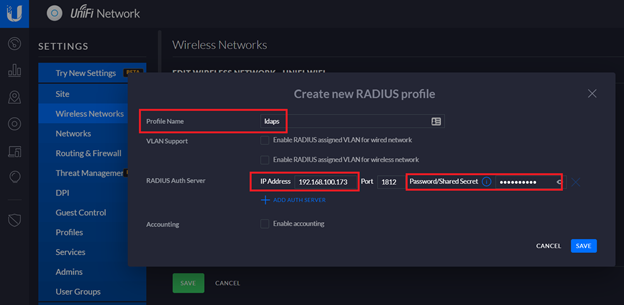
Save the changes made to RADIUS profile and Wireless network.
To setup a mobile client to connect to this network enter your G-Suite Username and password like this:
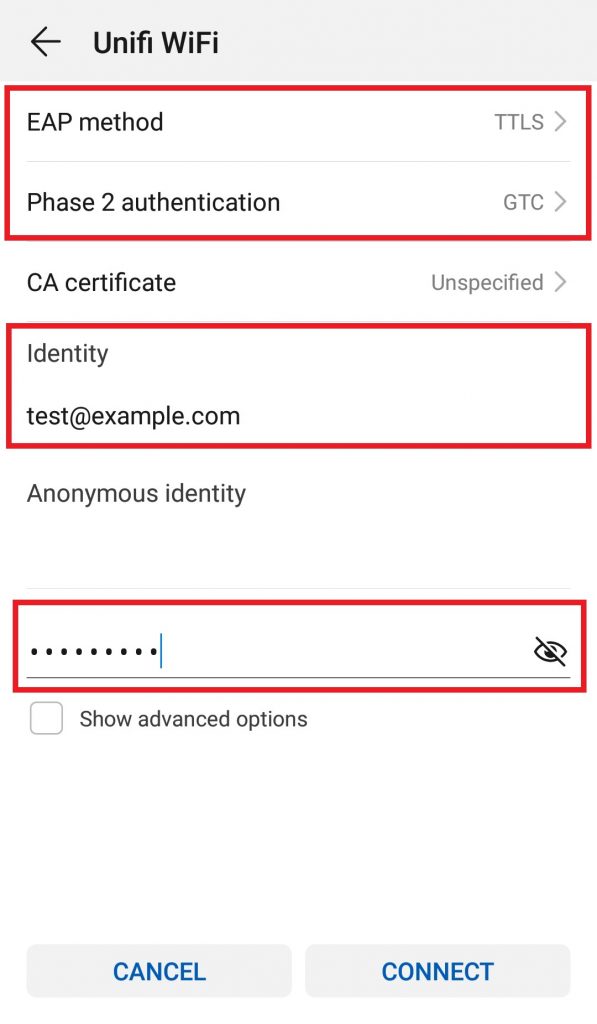
Note: Users are free to enter only their User ID or complete email address in <UserID>@example.com format. It should work either way.
In case of an error, make sure the EAP method is TTLS. For Phase 2 or inner tunnel use either GTC or None. Some devices will auto-detect these settings but on some devices you might need to select them manually.
Generating Certificates for Windows Clients
For authenticating Windows clients we need to generate CA and server certificates on FreeRADIUS and install them on client machines. FreeRADIUS provides helpful scripts for generating certificates.
To generate a self-signed CA certificate (which is what is recommended for RADIUS deployments), open the CA configuration file:
nano /etc/freeradius/3.0/certs/ca.cnfIn CA_default section increase the number of days so that the certificate will be valid for a long time (10 years in this case):
default_days = 3650In req section change the input_password and output_password from their default values:
input_password = tj367tHXVK
output_password = tj367tHXVKIn certificate_authority section enter your organization’s information:
countryName = US
stateOrProvinceName = FL
localityName = Miami
organizationName = NPO Systems
emailAddress = [email protected]
commonName = "NPO Certificate Authority"Save and exit.
Run the following commands to generate CA certificates:
make ca.pem
make ca.derNext generate server certificate by following the same procedure:
nano /etc/freeradius/3.0/certs/server.cnfChange default_days to a large value, input_password and output_password from their default values and enter your organization’s information in server section. Make sure the commonName entered here is different from the one entered in ca.cnf:
default_days = 3650
input_password = tj367tHXVK
output_password = tj367tHXVK
[server]
countryName = US
stateOrProvinceName = FL
localityName = Miami
organizationName = NPO Systems
emailAddress = [email protected]
commonName = "NPO Systems Server Certificate"Save and exit.
Generate server certificate by running this command:
make server.pemEnsure generated files have the right ownership:
chown freerad:freerad /etc/freeradius/3.0/certs/*Add the paths of newly generated certificates in eap configuration file:
nano /etc/freeradius/3.0/mods-enabled/eapIn tls-config tls-common section add the following values:
private_key_password = tj367tHXVK
private_key_file = /etc/freeradius/3.0/certs/server.pem
certificate_file = /etc/freeradius/3.0/certs/server.pem
ca_file = /etc/freeradius/3.0/certs/ca.pem
Save and exit.
Restart FreeRADIUS service:
systemctl restart freeradiusInstalling Certificates on Client Machines
Windows
Download ca.pem and ca.der certificates from /etc/freeradius/3.0/certs/ and distribute to your clients. On a Windows client, ca.der certificate can be installed by double-clicking on it and following the installation wizard:
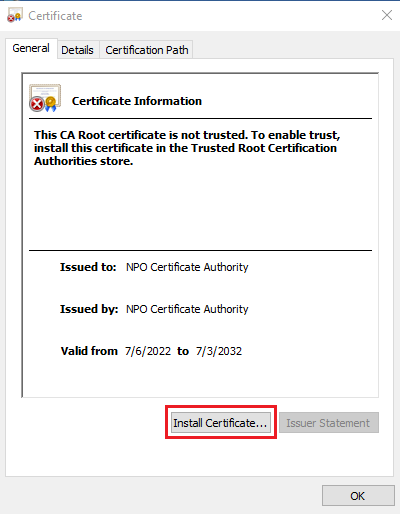
Place the certificate in Trusted Root Certification Authorities store:
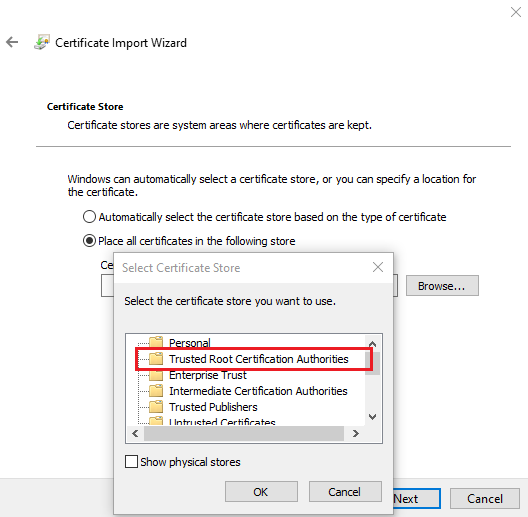
After completing the wizard, accept the security warning:
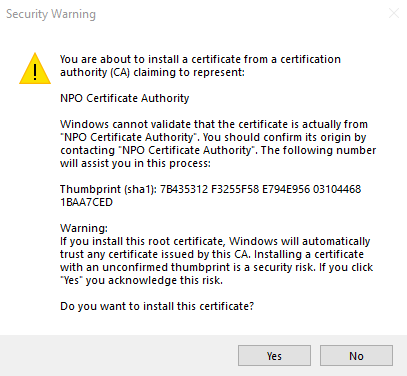
Connect to the WiFi by entering your username and password. If it shows you the certificate information click on Connect to continue:
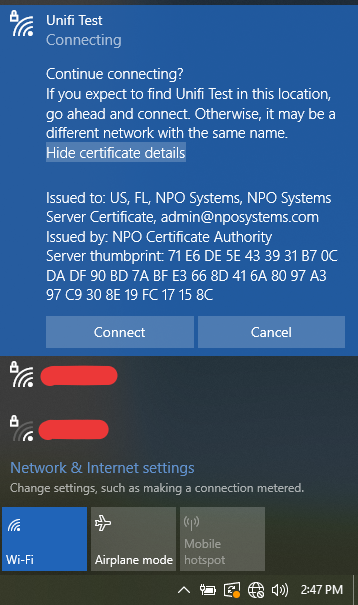
Ubuntu
The CA certificate in pem format needs to be converted to crt format. It can be done by executing this command:
openssl x509 -outform der -in ca.pem -out ca.crtDownload ca.crt file and put it in /usr/local/share/ca-certificates/ directory on the client machine. Then, install the certificate:
sudo update-ca-certificatesConnect to WiFi by selecting Authentication Tunneled TLS, Inner authentication GTC and entering your username and password:
Troubleshooting
In case of any issues troubleshoot FreeRADIUS by first stopping its service:
systemctl stop freeradius.serviceAfter that start it in debug mode:
freeradius -XFollow the debug output to troubleshoot further.
References
Unifi FreeRADIUS on Docker with Google Secure LDAP
FreeRADIUS Production SSL Certificates