Если вы из Windows 10 или 11 не можете открыть сетевые папки на других сетевых устройствах (NAS, Samba сервера Linux) или на компьютерах со старыми версиями Windows (Windows 7/ XP /2003), скорее всего проблема связана с тем, что в вашей версии Windows отключена поддержка устаревших и небезопасных версий протокола SMB (используется в Windows для доступа к общим сетевым папкам и файлам). В современных версиях Windows 10 и в Windows 11 по-умолчанию отключен протокол SMBv1 и анонимный (гостевой) доступ к сетевым папкам по протоколу SMBv2 и SMBv3.
Microsoft планомерно отключает старые и небезопасные версии протокола SMB во всех последний версиях Windows. Начиная с Windows 10 1709 и Windows Server 2019 (как в Datacenter так и в Standard редакциях) в операционной системе по умолчанию отключен протокол SMBv1 (помните атаку шифровальщика WannaCry, которая как раз и реализовалась через дыру в SMBv1).
Конкретные действия, которые нужно предпринять зависят от ошибки, которая появляется в Windows при доступе к общей сетевой папке и от настроек удаленного SMB сервера, на котором хранятся общие папки.
Содержание:
- Вы не можете получить гостевой доступ к общей папке без проверки подлинности
- Вашей системе необходимо использовать SMB2 или более позднюю
- Нет доступа к сетевой папке, у вас нет прав доступа
- Дополнительные способы проверки доступа к сетевой папке в Windows
Вы не можете получить гостевой доступ к общей папке без проверки подлинности
Начиная с версии Windows 10 1709 (Fall Creators Update) Enterprise и Education пользователи стали жаловаться, что при попытке открыть сетевую папку на соседнем компьютере стала появляться ошибка:
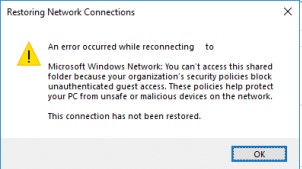
Вы не можете получить доступ к этой общей папке, так как политики безопасности вашей организации блокируют гостевой доступ без проверки подлинности. Эти политики помогают защитить ваш компьютер от небезопасных или вредоносных устройств в сети.
An error occurred while reconnecting Y: to \nas1share Microsoft Windows Network: You can’t access this shared folder because your organization’s security policies block unauthenticated guest access. These policies help protect your PC from unsafe or malicious devices on the network.
При этом на других компьютерах со старыми версиями Windows 8.1/7 или на Windows 10 с билдом до 1709, эти же сетевые каталоги открываются нормально. Причина в том, что в современных билдах Windows 10 (начиная с 1709) по умолчанию запрещен сетевой доступ к сетевым папкам под гостевой учетной записью по протоколу SMBv2 (и ниже). Гостевой (анонимный) доступ подразумевают доступ к сетевой папке без аутентификации. При доступе под гостевым аккаунтом по протоколу SMBv1/v2 не применяются такие методы защиты трафика, как SMB подписывание и шифрование, что делает вашу сессию уязвимой против MiTM (man-in-the-middle) атак.
При попытке открыть сетевую папку под гостем по протоколу SMB2, в журнале клиента SMB (Microsoft-Windows-SMBClient) фиксируется ошибка:
Log Name: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Event ID: 31017 Rejected an insecure guest logon.
Данная ошибка говорит о том, что ваш компьютер (клиент) блокирует не аутентифицированный доступ под аккаунтом guest.
Чаще всего с этой проблемой можно столкнуться при использовании старых версий NAS (обычно для простоты настройки на них включают гостевой доступ) или при доступе к сетевым папкам на старых версиях Windows 7/2008 R2 или Windows XP /2003 с настроенным анонимным (гостевым) доступом (см. таблицу поддерживаемых версий SMB в разных версиях Windows).
Microsoft рекомендует изменить настройки на удаленном компьютере или NAS устройстве, который раздает сетевые папки. Желательно переключить сетевой ресурс в режим SMBv3. А если поддерживается только протокол SMBv2, тогда нужно настроить доступ с аутентификацией. Это самый правильный и безопасный способ исправить проблему.
В зависимости от устройства, на котором хранятся сетевые папки, вы должны отключить на них гостевой доступ.
- NAS устройство – отключите гостевой доступ в настройках вашего NAS устройства (зависит от модели);
- Samba сервер на Linux — если вы раздаете SMB папку с Linux, добавьте в в секции [global] конфигурационного файла smb.conf строку:
map to guest = never
А в секции с описанием сетевой папки запретить анонимный доступ:
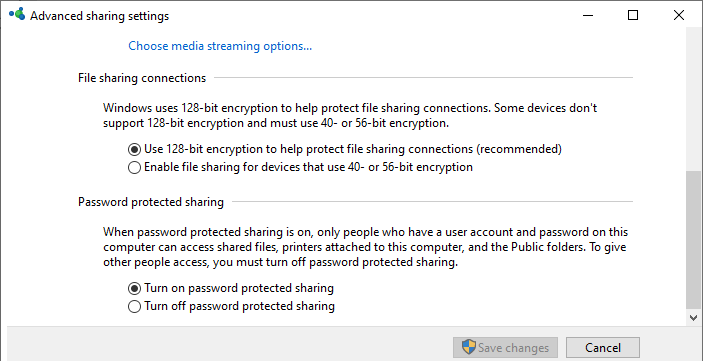
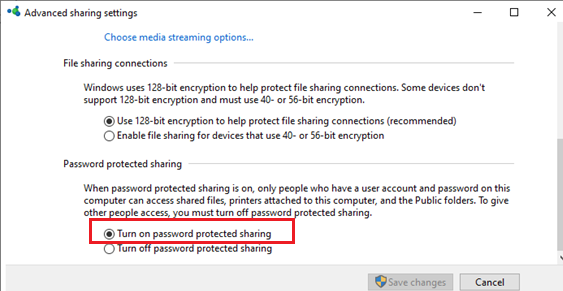
guest ok = no - В Windows вы можете включить общий доступ к сетевым папкам и принтерам с парольной защитой в разделе Control PanelAll Control Panel ItemsNetwork and Sharing CenterAdvanced sharing settings. Для All Networks (Все сети) в секции “Общий доступ с парольной защитой” (Password Protected Sharing) измените значение на “Включить общий доступ с парольной защитой” (Turn on password protected sharing). В этом случае анонимный (гостевой) доступ к папкам будет отключен и вам придется создать локальных пользователей, предоставить им доступ к сетевым папкам и принтерам и использовать эти аккаунты для сетевого доступа к общим папкам на этом компьютере..
Есть другой способ – изменить настройки вашего SMB клиента и разрешить доступ с него на сетевые папки под гостевой учетной записью.
Этот способ нужно использовать только как временный (!!!), т.к. доступ к папкам без проверки подлинности существенно снижает уровень безопасности ваших данных.
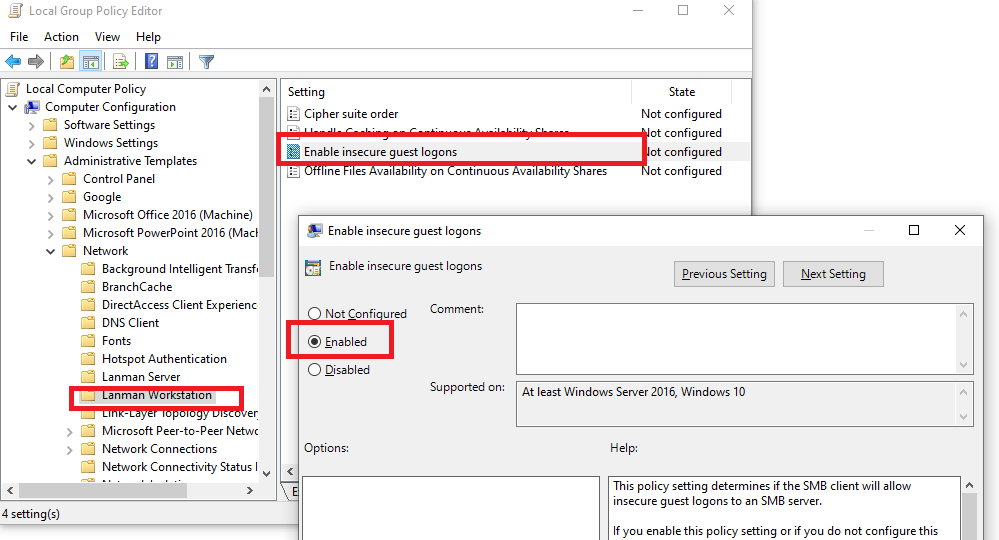
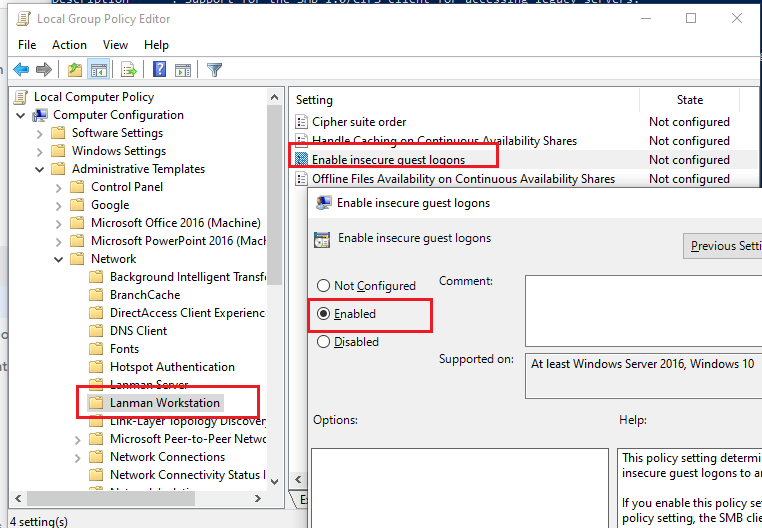
Чтобы разрешить гостевой доступ с вашего компьютера, откройте редактор локальных групповых политик (gpedit.msc) и перейдите в раздел: Конфигурация компьютера -> Административные шаблоны -> Сеть -> Рабочая станция Lanman (Computer Configuration ->Administrative templates -> Network (Сеть) -> Lanman Workstation). Включите политику Enable insecure guest logons (Включить небезопасные гостевые входы).
Обновите настройки групповых политик в Windows с помощью команды:
gpupdate /force
В Windows 10 Home, в которой нет редактора локальной GPO,вы можете внести аналогичное изменение через редактор реестра вручную::
HKLMSYSTEMCurrentControlSetServicesLanmanWorkstationParameters “AllowInsecureGuestAuth”=dword:1
Или такими командами:
reg add HKLMSYSTEMCurrentControlSetServicesLanmanWorkstationParameters /v AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
reg add HKLMSoftwarePoliciesMicrosoftWindowsLanmanWorkstation /v AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
Вашей системе необходимо использовать SMB2 или более позднюю
Другая возможная проблема при доступе к сетевой папке из Windows 10 – поддержка на стороне сервера только протокола SMBv1. Т.к. клиент SMBv1 по умолчанию отключен в Windows 10, то при попытке открыть шару или подключить сетевой диск вы можете получить ошибку:
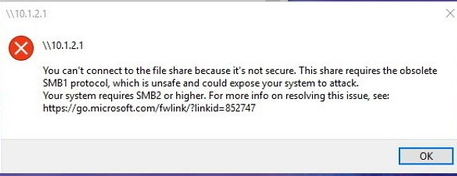
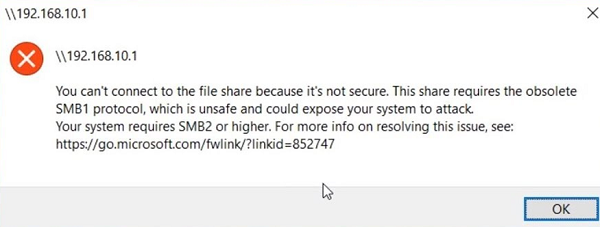
Не удалось выполнить сопоставление сетевого диска из-за следующей ошибки. Вы не можете подключиться к общей папке, так как она небезопасна. Эта общая папка работает по устаревшему протоколу SMB1, который небезопасен и может подвергнуть вашу систему риску атаки. Вашей системе необходимо использовать SMB2 или более позднюю версию.
You can’t connect to the file share because it’s not secure. This share requires the obsolete SMB1 protocol, which is unsafe and could expose your system to attack. Your system requires SMB2 or higher.
При этом соседние устройства SMB могут не отображаться в сетевом окружении и при открытии сетевых папок по UNC пути может появляться ошибка 0x80070035.
Сообщение об ошибки явно указывает, что сетевая папка поддерживает только SMBv1 для доступа к файлам. В этом случае нужно попытаться перенастроить удаленное SMB устройство для поддержки как минимум SMBv2 (правильный и безопасный путь).
Если сетевые папки раздает Samba сервер на Linux, вы можете указать минимально поддерживаемую версию SMB в файле smb.conf так:
[global] server min protocol = SMB2_10 client max protocol = SMB3 client min protocol = SMB2_10 encrypt passwords = true restrict anonymous = 2
В Windows 7/Windows Server 2008 R2 вы можете отключить SMBv1 и разрешить SMBv2 так через реестр:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 0 –Force
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 1 –Force
В Windows 8.1 отключите SMBv1, разрешите SMBv2 и SMBv3 и проверьте что для вашего сетевого подключения используется частный или доменный профиль:
Disable-WindowsOptionalFeature -Online -FeatureName "SMB1Protocol"
Set-SmbServerConfiguration –EnableSMB2Protocol $true
Если ваше сетевое устройство (NAS, Windows XP, Windows Server 2003), поддерживает только протокол SMB1, в Windows 10 вы можете включить отдельный компонент SMB1Protocol-Client. Но это не рекомендуется!!!
Если удаленное устройство требует использовать SMBv1 для подключения, и этот протокол отключен в вашем устройстве Windows, в Event Viewer появляется ошибка:
Log Name: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Event ID: 32000 Description: SMB1 negotiate response received from remote device when SMB1 cannot be negotiated by the local computer.
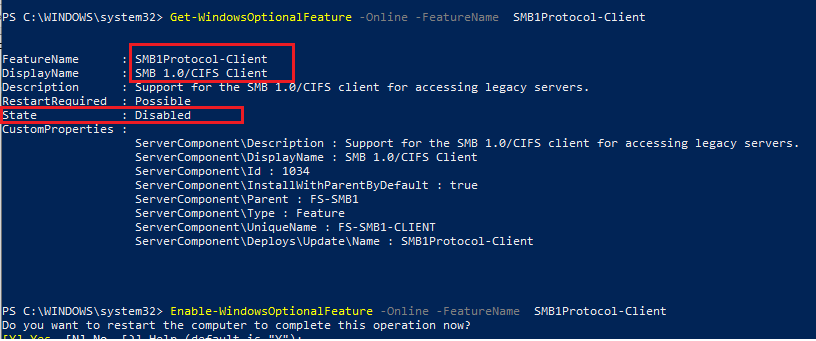
Запустите консоль PowerShell и проверьте, что SMB1Protocol-Client отключен (
State: Disabled
):
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
Включите поддержку протокола SMBv1 (потребуется перезагрузка):
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
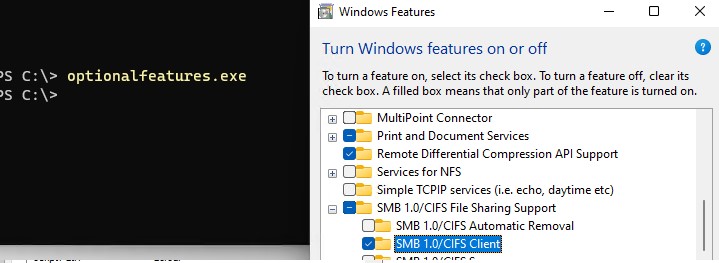
Также вы можете включить/отключить SMBv1 в Windows 10 и 11 из меню
optionalfeatures.exe
-> SMB 1.0/CIFS File Sharing Support –> SMB 1.0/CIFS Client.
В Windows 10 1709 и выше клиент SMBv1 автоматически удаляется, если он не использовался более 15 дней (за это отвечает компонент SMB 1.0/CIFS Automatic Removal).
В этом примере я включил только SMBv1 клиент. Не включайте компонент SMB1Protocol-Server, если ваш компьютер не используется устаревшими клиентами в качестве сервера для хранения общих папок.
После установке клиента SMBv1, вы должны без проблем подключиться к общей сетевой папке или принтеру. Однако, нужно понимать, что использование данного обходного решения не рекомендовано, т.к. подвергает снижает уровень безопасности.
Нет доступа к сетевой папке, у вас нет прав доступа
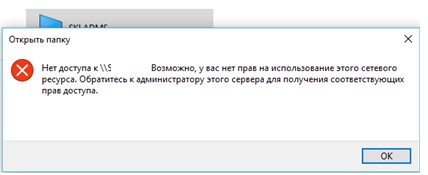
При подключении к сетевой папке на другом компьютере может появится ошибка:
Нет доступа к \ComputerNameShare. Возможно у вас нет прав на использование этого сетевого ресурса. Обратитесь к системному администратору этого сервера для получения соответствующих прав доступа.
Network Error Windows cannot access \PC12Share You do not have permissions to access \PC12Share. Contact your network administrator to request access.
При появлении это ошибки нужно:
- Убедиться, что пользователю, под которым вы подключаетесь к сетевой папке, предоставлены права доступа на сервере. Откройте свойства общей папке на сервере и убедитесь что у вашего пользователя есть права доступа.
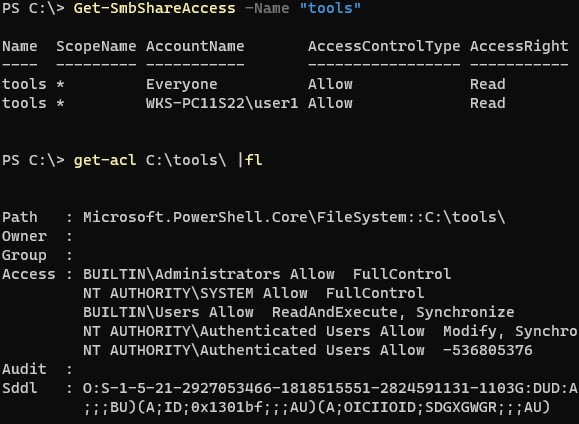
Проверьте разрешения сетевой шары на сервере с помощью PowerShell:
Get-SmbShareAccess -Name "tools"
Затем проверьте NTFS разрешения:
get-acl C:tools |fl
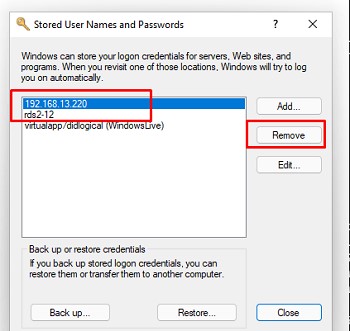
Если нужно, отредактируйте разрешения в свойствах папки. - Проверьте, что вы используете правильные имя пользователя и пароль для доступа к сетевой папки. Если имя и пароль не запрашиваются, попробуйте удалить сохраненные пароли для доступа к сетевой папке в диспетчере учетных записей Windows. Выполните команду
rundll32.exe keymgr.dll, KRShowKeyMgr
и удалите сохраненные учетные данные для доступа к сетевой папке.
При следующем подключении к сетевой папки появится запрос имени и пароля. Укажите имя пользователя для доступа к папке. Можете сохранить его в Credential Manager или добавить вручную.
Дополнительные способы проверки доступа к сетевой папке в Windows
В этом разделе указаны дополнительные способы диагностики при проблема с открытием сетевые папок в Windows:
When trying to access existing remote network shares from a Windows machine, you may see some errors that prevent you from accessing the share. This blog is about some of those errors and how to fix them.
Problem 1: User account has insufficient permissions
This is the most obvious issue but is often overlooked.
If you log into Windows and are unable to access a remote network share, then make sure your account has sufficient access permissions for the share.
If a Windows service such as Apache web server is unable to access the network share, then make sure that the Windows service is run using an account that has sufficient permissions to access the share. When the service is run by a user account without proper access permissions, the service will not be able to read the share.
Solution:
To fix problems with share access for a service, follow these steps:
- Open the services window and double-click on the service that is facing the issue (for example, Apache Web Service). On the resulting properties dialog, switch to the Logon tab and enter the username and password of an account that has sufficient access to the network share.
- Restart the service.
- Now the service should be able to access the network shares.
Problem 2: The computer does not have a domain trust relationship
Solution
By default, domains are unable to communicate with other domains. For the communication to be established, a trust relationship between these domains should be configured.
After a trust relationship is defined between Domain A and Domain B, users of Domain B can log on to their own domain through a workstation in Domain A. Here Domain B is the trusted domain and Domain A is the trusting domain.
There are different types of trust relationships. Explaining all of them is out of the scope of this document. But some information is provided below:
| Trust Type | Transitive | Non-Transitive | Direction | Authentication Mechanism |
Notes |
| Parent-Child | Yes | No | Two-way | Kerberos V5 or NTLM |
Created automatically when a child domain is added. |
| Tree-Root | Yes | No | Two-way | Kerberos V5 or NTLM |
Created automatically when a new Tree is added to a forest. |
| Shortcut | Yes | No | One-way or Two-way |
Kerberos V5 or NTLM |
Created Manually. Used to improve logon times between two domains |
| Forest | Yes | No | One-way or Two-way |
Kerberos V5 or NTLM |
The trust allows all domains in one forest to trust all domains in another forest. Used to share resources between forests |
| External | No | Yes | One-way | NTLM Only | Created Manually between domains in two separate Forests |
| Realm | Yes | Yes | One-way or Two-way |
Kerberos V5 Only | Created Manually. Used to access resources between a non-Windows Kerberos V5 realm and an AD DS domain. |
Used to access resources between a non-Windows Kerberos V5 realm and an AD DS domain.
Steps to Create External Trusts
- Open Active Directory Domains and Trusts.
- Click Start, click Administrative Tools, and then click Active Directory Domains and Trusts.
- Right-click the domain node for the domain that you want to establish a trust with, and then click Properties.
- On the Trusts tab, click the New Trust, and then click Next.
- On the Trust Name page, type the Domain Name System (DNS) name (or NetBIOS name) of the domain, and then click Next.
- On the Trust Type page, click External trust, and then click Next.
- On the Direction of Trust page, do one of the following:
- To create a two-way, external trust, click Two-way. Otherwise, click one-way which create an incoming trust
Problem 3: Share protected by an authentication firewall
Even when the trust relationship is established successfully, access to network shares might fail. This could be due to authentication firewall rules preventing access for the user account.
To confirm what the actual error is:
- Log in to the server from which you want to access the shares.
- Open a CMD prompt.
- If you need to check for a different user, then right-click the CMD option and select Run as a different user. Give the credentials of the Apache logon user
- Then try to list the content of that network path location
eg : DIR \test.localFilecloud
If the listing is successful, then the user account should have access permissions to the path. But if an error like the following appears below it, although the group or the user has been granted rights to access the share Then the share is in another domain and the trust was set up with ‘selective authentication.’
“The computer you are signing into is protected by an authentication firewall. The specified account is not allowed to authenticate the computer. “
Solution:
Navigate to the domain which has the share:
- Open the domain controller and open the folder Active Directory Users and Computers.
- Go to View > Advanced Features > Computers and select the computer that needs to be authenticated.
- Click the Security tab, then add the user or group that requires access. >
- Tick the Allowed to authenticate box, and click Apply
This will fix the issue, and you will be able to access the shares and list.
Share Protected By Authentication Firewall
Problem 4: Path too long
By default, Windows has a limit of 255 characters for the path. Trying to access files/folders from a Windows share longer than this limit might result in access issues.
Solution:
One option to fix this issue is to restructure the folder on the Windows share such that the path length does not exceed 255 characters.
Another option is to enable long path support for Windows (this support only is available on Windows 10 and server versions).
Steps
- Type regedit in the Search tab in windows. This will open the registry window.
- Navigate to the below location.
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlFileSystem
- On the right window, find the value LongPathsEnabled. Double-click it. Change the value from 0 to 1, and click OK.
- If you don’t see the value listed, create it by right-clicking the FileSystem key, and choosing New > DWORD (32-bit) Value. Give it the name LongPathsEnabled and set value 1
“Windows Cannot Access \ Computer Name” is mainly a network-related problem of your Local Area Connection and generally this error occurs due to the lack of network permissions, improper installed Network Drivers, and sometimes a single corrupted Windows Registry can be the reason too.
Most of the time people have this problem right after creating a new LAN Connection in their network and mainly the error popup message appears when every time you try to open the shared folder located on the other computer.
The bad thing which I really hate about this network error is, not only on the folder you can also get this error message on any network file or even on the network shared drive too. And believe it or not but sometimes it gets really hard to find where the actual fault is, and what do we really need to do to fix the problem.
Network error
Windows cannot access \ Computer Name
You do not have permission to access \ Computer Name contact your network administrator to request access.
If you’re having this problem on your Local Area Network, then I don’t think you should really need to worry about it;
Because with the help of this tutorial I’ll definitely going to help you out by showing you, how you can change the permissions configuration of your computer to read and write the files or folder on the shared network drive through your Windows Network Place.
So, Let’s See How to Troubleshoot This Error;
This problem can occur on any version of windows, even if you are using the latest Windows 10 or running an old Windows 7 Computer. Normally, Access Denied Network Error comes because of some kind of network-related permission problem. But sometimes there are some other reasons for this error to shows up on your computer’s screen and here’s the list of those reasons which can be possibly happening on your computer:
- Improper LAN Connection
- Improper LAN Sharing Setting
- Improper Drive or Folder Security Setting
- TCP/IP NetBIOS Setting is Unconfigured
- Windows Registry got Corrupted
- Network Driver got Corrupted
1# Solution – Improper LAN Connection and Sharing Setting
If you have recently created a LAN connection by yourself, or maybe tried to start the file sharing, or changed the LAN Wire or Modem, or just made any changes in your LAN configuration, then this is the time where you’ll need to rectify it all.
Let’s start with the connections and wires;
To make a connection between two different network devices like a Modem and Computer, we actually need to use a Straight cable. On the other hand, the same network devices like ‘PC to PC’ or ‘Modem to Modem’ need a Cross-over cable to interact properly.

Both of the cables look exactly the same but the internal wiring is completely different and that’s why people usually get confused while creating their PC to PC LAN connection.
The next configuration is the ‘Sharing Setting’. Check for the proper IP configuration on every connected device in your network. If all the PC’s have an IP address configured in it, then make sure it won’t conflict. Confliction mainly happens when two different PC has the same IP configuration.
You’ll also need to assign the IP address to all of your Share PCs if you found the setting is pre-set on “Obtain the IP Address Automatically”.
To change or check your saved setting, you can go to the ‘Network and Sharing Center‘ and then on the left sidebar, click on “Change Adapter Settings” option. Now right-click on your network adapter and select “Properties“. After that, select “Internet Protocol Version 4 (TCP/IPv4)” and then click on its “Properties” button.

- Turn on network discovery.
- Turn on file and printer sharing.
- Allow windows to manage homegroup connection (recommended).
- Turn on sharing so anyone with network access can read and write files in the public folders.
- Use 128-bit encryption to help protect files sharing connections (recommended).
- Turn off password protected sharing.
Note: Make these changes on your current selected network profile.


2# Solution – Improper Drive or Folder Security Setting
80% of you will be going to fix your problem by following this particular solution because generally, people do forget to change the security setting while making any drive/file/folder shared in their network place.
So now I’m going to show you how you can easily configure the permission setting to connect with all devices in your network just to read and write the files or folder.
If you’re having this problem with all of your network drives and folder and wanted to grant permission to all of those shared folders or drives at once, then it’s not possible and you’ll need to repeat all these steps for all of your shared drives and even for a single file and folder.
If the list of sharable File/folder contains in a single drive, then granting permission for that single drive can make all the internal File/Folder read and writeable for the other network computer.
Step 1 – Give Sharing Permission to Everyone
To configure the sharing permission, First, you’ll need to right click on that drive, file or folder which you wanted to share and then select ‘Properties’.
In the properties window, select the “Sharing” tab and then click on “Advanced Sharing …” button. Now make sure you have ticked on the “Share this folder” button.
After that, click on the “Permission” button and give “Everyone” user the Full Control.

This step allows you to add a new username into the security tab of your file/folder/drive’s properties, just to make it accessible to all users which is connected to your LAN.
To grant the access to everyone, we actually need a username called “Everyone” under the security tab, so your OS can permit other connted PC’s to cross the security. But still, there is no username called ‘Everyone’ is mentioned under the security tab of your shared drive, file or folder.
So now again in the properties windows, click on the Security Tab and then select the “Edit” button which will lead you to another pop-up window, where you can add the username by clicking on another “Add…” button.
Now in the third pop-up window, you’ll have to click on the “Advanced …” button which will help to find all of the linked usernames connected to your PC.
On the fourth pop-up, click on the “Find Now” button to make your computer to show you the list of all available users;
And in between all those usernames, you’ll find the username called “Everyone” in the list, which you need to select and then click on “OK”.
After that, you’ll again need to click on the “Ok” and at this moment you will be seeing the username “Everyone” is showing under the users and groups setting.

When you have done with adding the username, then it’s the time when you need to grant the full permission to the username “Everyone” in the security tab, just to make it accessible from any LAN connected computer.
Now, click on the username “Everyone” and then tick on the Full control option and then click on “Apply”.

So, at this moment you’ll just need to sit back and watch the whole process until it gets completed and make sure you don’t click on the cancel button or otherwise you’ll get the same problem while accessing some files in the future.
After that, you can actually able to read and write the files on that drive right after when this whole security configuration gets done. If not, then just continue.
3# Solution – Configure TCP/IP NetBIOS
‘TCP/IP NetBIOS’ also known by its another name “NetBT” and it’s a network protocol based on session layer of the OSI model, allowing applications on separate computers to communicate over a local area network.
Using the NetBIOS over TCP/IP (NetBT) service on the network allows users to share files, printers, and log on to the network. If the NetBT service is unconfigured, some of these functions might not be available to the user. If this service is disabled, any services that explicitly depend on it will fail to start.
So, make sure on every shared computer of your network the ‘NetBIOS over TCP/IP’ is enabled and to confirm that, here is the procedure given below:
- To change the configuration, first, you’ll need to search the “services.msc” on the Windows Starts Menu to open the ‘Windows Servies’ (where you can easily start, stops, and configures any Windows services).
- Now on the Services window, search for a service named “TCP/IP NetBIOS Helper” and double-click on it. Then on the pop-up general tab, change the ”Startup type setting” to the ‘Automatic’.
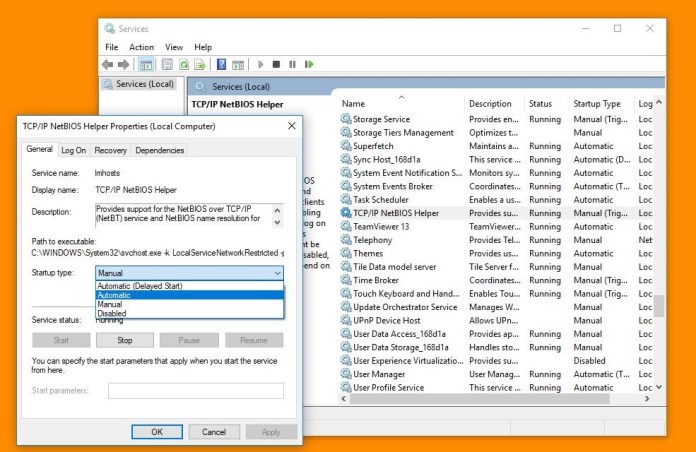
To do that, you’ll have to again open the “Internet Protocol Version 4 (TCP/IPv4)” properties. Then on the pop-up, click on the “Advanced…” button, select “WINS” tab and pick “Enable NetBIOS over TCP/IP” as your main preference. And that’s it.
 4# Solution – Corrupted Windows Registry
4# Solution – Corrupted Windows Registry
The Windows Registry is a hierarchical configuration storage database that stores settings for the Microsoft Windows Operating System and other installed software in your Windows.
The registry is the main target when a virus or malware starts to corrupt your windows and a single changed value in your Windows Registry can cause this network related problem. You can fix your Windows Registry by using some best in class Registry Cleaner and that will fix your problem by just doing some simple steps.
But before using that, I have some couple of manual registry settings which you can try to fix the issue;
First, open your Windows Registry Database by using the run command “regedit”. You can press Windows + R Key to instantly show the Run Commander. Or you can just search the “regedit” on Starts Menu.
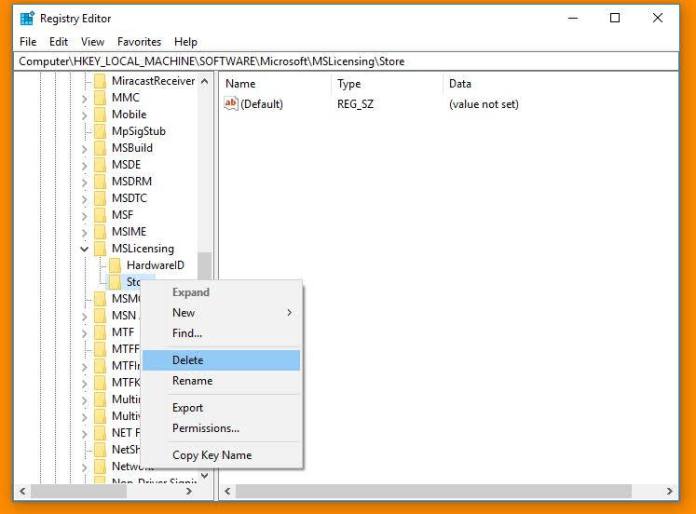
When it gets open, go to this location “HKEY_LOCAL_MACHINESOFTWAREMicrosoftMSLicensing” into the database.
Now expand the ‘MSLicensing’ folder and then delete both of the “HardwareID” and “Store” sub-folders listed under the expansion. Make sure you only delete sub-folders and not the whole MSLicensing.
This can fix the connection licensing problems in case, your connection is having any.

How to Fix Registry Related Issues using a Registry Cleaner?
The Registry is a very important database that resides within your Operating System. It contains vital information on all the settings, preferences, etc. on hardware and software installed in your rig. When it comes to programs, the Registry also maintains data like the location of the program, what is required to launch the program, what sort of resources it needs from the computer, and so on and so forth… Read More
5# Solution – Corrupted Windows Drivers
Computer operating systems are able to support network adapters via software known as Network driver. Network drivers are actually that you needed in order to connect your computer to any network. If something bad happens to your network drivers then it’s quite possible that you get some constant errors on your screen while working in the network area.
Now updating the drivers is the best thing what you can do to fix all the drivers related issue and make everything back to normal.
What Is a Network Driver, And How To Install It?
As a PC user at some point, you have heard of Network Drivers. Have you ever wondered what network drivers is all about? Prior to figuring out what a network driver is, let us get to know few things about something called Network Adapter… Read More
“That’s all for now, thanks for sticking with the article, and you know it will always good to let me know about the article, in the comments below.” 🙂
Still Finding Solution or Need Some Help ?
If you still can’t find your solution then maybe you’ll need to contact us and we will definitely gonna help you out by our technical support.
Click Here For The Technical Support
Windows OS Hub / Windows 10 / Can’t Access Shared Folders or Map Network Drives from Windows 10 and 11
If you cannot open or map network shared folders on your NAS, Samba Linux server, computers with legacy Windows versions (Windows 7/XP/Server 2003) from Windows 10 or 11, most likely the problem is that legacy and insecure versions of the SMB protocol are disabled in the current Windows builds (SMB protocol is used in Windows to access shared network folders and files).
Microsoft is systematically disabling legacy and insecure versions of the SMB protocol in all recent versions of Windows. Starting with Windows 10 1709 and Windows Server 2019 (both in Datacenter and Standard editions), the unsafe SMBv1 protocol is disabled by default as well as anonymous (guest) access to network shared folders.
The specific steps to take depend on the error that appears in Windows when accessing a shared folder, and on the settings of the remote SMB server that hosts the network shares.
Contents:
- Can’t Access Shared Folder Because Security Policies Block Unauthenticated Guest Access
- Can’t Connect to the File Share Because It’s Not Secure and Requires the Obsolete SMB1 Protocol
- Windows Cannot Access Shared Folder: You Don’t Have Permissions
- Other Fixes: Windows Cannot Access Shared Folders
Can’t Access Shared Folder Because Security Policies Block Unauthenticated Guest Access
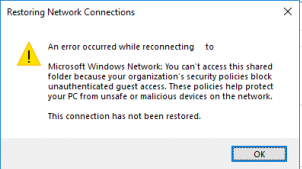
Starting with Windows 10 build 1709 Fall Creators Update (Enterprise and Education editions), users began to complain that when they tried to open a network shared folder on a neighboring computer, an error appeared:
Restoring Network Connections An error occurs when you try to open a network folder: An error occurred while reconnecting Y: to \nas1share Microsoft Windows Network: You can’t access this shared folder because your organization’s security policies block unauthenticated guest access. These policies help protect your PC from unsafe or malicious devices on the network.
Moreover, on other computers with Windows 8.1, Windows 7, or Windows 10 with a build of up to 1709, the same shared network folders open normally. The point is that in modern versions of Windows 10 (build 1709+), the guest access to the shared folders using the SMBv2 protocol is disabled by default. Guest (anonymous) means access to a shared network folder without authentication. When accessing a network folder under a guest account over the SMBv1/v2 protocol, such methods of traffic protection as SMB signing and encryption are not used, which makes your session vulnerable to the MiTM (man-in-the-middle) attacks.
These changes are not applied on Windows 10 Home editions and the network access under the guest account is working fine.
If you try to open a shared network folder using the SMB v2 protocol under the guest account, the following error will appear in the Event Viewer of your computer (SMB client):
Log Name: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Event ID: 31017 Rejected an insecure guest logon.
This error says that your computer (client) blocks non-authenticated access under the Guest account.
In most cases, you can face this problem when accessing old NAS devices (usually guest access is enabled on them for ease of setup) or when opening shared folders on legacy Windows 7/2008 R2/Windows XP/2003 devices with anonymous (guest) access enabled (see the table of supported SMB protocol versions in different Windows editions).
Microsoft recommends changing the settings on a remote computer or NAS device that hosts the shared network folders. It is advisable to switch the network share to the SMBv3 mode. Or configure access with authentication if only the SMBv2 protocol is supported by the device. This is the most correct and safest way to fix the problem.
Disable guest access on the device where your shared folders are stored:
- NAS devices – disable guest access in the settings of your NAS device (depending on vendor and model);
- Samba server on Linux — if you are sharing a network folder with Samba on Linux, add the following string to the smb.conf configuration file under the section [global]:
map to guest = never
And restrict anonymous access in the shared folder configuration section:guest ok = no - In Windows, you can enable sharing of network folders and printers with password protection via the Control Panel -> Network and Sharing Center -> Advanced sharing settings. For All Networks in the “Password Protected Sharing” section, change the value to the “Turn on password protected sharing”. In this case, anonymous (guest) access to the network shared folders will be disabled and you will have to create local users, grant them access permissions to the shared folders and printers and use these accounts to connect to the shared folders on a remote computer.
There is another way – you can change the settings on your Windows device to allow access to shared network folders under the guest account. This method should be used only as a temporary workaround (!!!), because access to folders without authentication significantly reduces your computer security.
To enable guest access from your computer, you need to use the Group Policy Editor (gpedit.msc). Go to the section: Computer Configuration -> Administrative templates -> Network -> Lanman Workstation. Find and enable the policy Enable insecure guest logons. This policy option determines whether the SMB client will allow an unsafe guest logon to the SMB server.
Update the Group Policy settings in Windows with the command:
gpupdate /force
In Windows 10 Home, which does not have a local GPO editor, you can make a similar change through the Registry Editor manually:
HKLMSYSTEMCurrentControlSetServicesLanmanWorkstationParameters “AllowInsecureGuestAuth”=dword:1
Or with these commands:
reg add HKLMSYSTEMCurrentControlSetServicesLanmanWorkstationParameters /v AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
reg add HKLMSoftwarePoliciesMicrosoftWindowsLanmanWorkstation /v AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
Can’t Connect to the File Share Because It’s Not Secure and Requires the Obsolete SMB1 Protocol
Another possible problem when accessing a network folder from Windows 10 is that only the SMBv1 protocol version is supported on the server-side. Since the SMBv1 client is disabled by default in Windows 10 1709+ when you try to open the shared folder or map a network drive, you may get an error:
You can’t connect to the file share because it’s not secure. This share requires the obsolete SMB1 protocol, which is unsafe and could expose your system to attack. Your system requires SMB2 or higher.
The error message clearly shows that the network shared folder only supports the SMBv1 client access protocol. In this case, you should try to reconfigure the remote SMB device to use at least SMBv2 (the correct and safe way).
If you use Samba server on Linux to share files, you can specify the minimum supported version of SMB protocol in the smb.conf file like this:
[global] server min protocol = SMB2_10 client max protocol = SMB3 client min protocol = SMB2_10 encrypt passwords = true restrict anonymous = 2
On Windows 7/Windows Server 2008 R2, you can disable the SMB 1 protocol and enable SMBv2 through the registry with the following PowerShell commands:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 0 –Force
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 1 –Force
On Windows 8.1/Windows Server 2012 R2, you can disable SMBv1, allow SMBv2 and SMBv3 with the following command (verify that a private or domain profile is used for your network connection):
Disable-WindowsOptionalFeature -Online -FeatureName "SMB1Protocol"
Set-SmbServerConfiguration –EnableSMB2Protocol $true
If your network device (NAS, Windows XP, Windows Server 2003) supports only the SMB1 protocol, you can enable a separate SMB1Protocol-Client feature on Windows 10/11 or Windows Server. But this is not recommended!!!
If the remote device requires SMBv1 to connect, and this protocol is disabled on your Windows device, an error appears in the Event Viewer:
Log Name: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Event ID: 32000 Description: SMB1 negotiate response received from a remote device when SMB1 cannot be negotiated by the local computer.
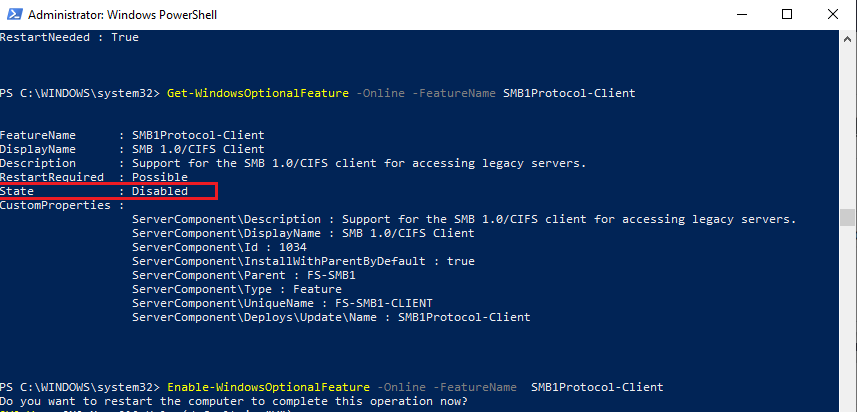
Run the elevated PowerShell prompt and verify that the SMB1Protocol-Client is disabled (State: Disabled):
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
Enable the SMBv1 client protocol (a reboot is required):
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
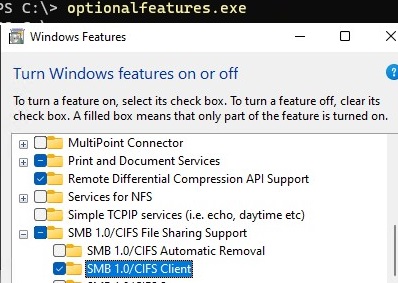
You can also enable/disable additional features in Windows 10 and 11 from the optionalfeatures.exe. Expand SMB 1.0/CIFS File Sharing Support and enable the SMB 1.0/CIFS Client.
On Windows 10 1809 and newer, the SMBv1 client is automatically removed if it has not been used for more than 15 days (the SMB 1.0/CIFS Automatic Removal component is responsible for this).
In this example, I enabled only the SMBv1 client. Do not enable the SMB1Protocol-Server feature if your computer is not used by legacy clients as an SMB server to host shared folders.
After installing the SMBv1 client, you should be able to connect to a shared folder or printer without any problems. However, you should understand this workaround is not recommended, because it reduces the security of your computer.
Windows Cannot Access Shared Folder: You Don’t Have Permissions
When connecting to a shared network folder on a remote computer, an error may appear:
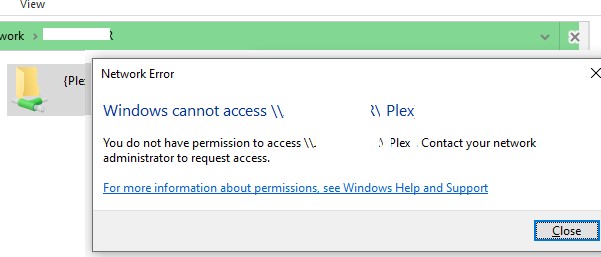
Network Error Windows cannot access \PC12Share You do not have permission to access \PC12Share. Contact your network administrator to request access.
When this error occurs, you need to:
- Make sure that the user you are using to access the shared folder is granted access permissions on the remote share. Open the properties of the shared folder on the server and make sure your user has at least read permissions. Also, you can check the SMB file share permissions on the remote host using PowerShell:
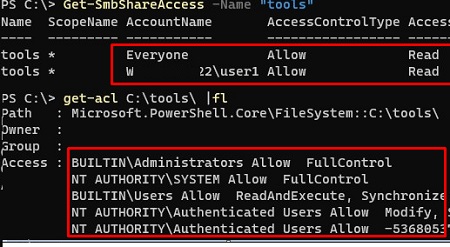
Get-SmbShareAccess -Name "tools"
Then check the NTFS folder permissions:
get-acl C:tools |flIf necessary, edit the permissions in the folder and/or share properties;
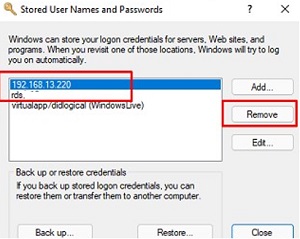
- Make sure you are using the correct username and password to access the network folder. If you’re not prompted for a username and password, try removing saved (cached) credentials for remote shares in Windows Credential Manager. Run the command
rundll32.exe keymgr.dll, KRShowKeyMgrand delete cached credentials for the remote computer you are trying to access.
The next time you connect to the shared folder, you will be prompted for a username and password. Specify the credentials to access the network shared folder on the remote computer. You can save it in Credential Manager or add it manually.
Other Fixes: Windows Cannot Access Shared Folders
This section provides additional ways to troubleshoot a problem opening network folders in Windows:










 4# Solution
4# Solution 




 If necessary, edit the permissions in the folder and/or share properties;
If necessary, edit the permissions in the folder and/or share properties;