4/7/2020] [6:55:06 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [6:55:07 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-2" --agree-tos --email "example@email.com" --preferred-challenges "dns,http" --webroot --domains "unifi.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for unifi.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain unifi.ophiuchus.fr,
http-01 challenge for unifi.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:03:09 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:24 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:32 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:42 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #2: unifi.ophiuchus.fr,
[4/7/2020] [7:03:43 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-2" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-2 (expected /etc/letsencrypt/renewal/npm-2.conf).,
,
[4/7/2020] [7:03:46 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:03:48 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:05:41 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:05:43 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
Connection Error: Error: read ECONNRESET,
[4/7/2020] [7:22:47 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:22:48 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:23:19 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:23:23 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:23:53 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:24:08 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:24:09 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:24:14 PM] [SSL ] › ℹ info Revoking Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:24:22 PM] [SSL ] › ℹ info Revoking Let'sEncrypt certificates for Cert #2: unifi.ophiuchus.fr,
[4/7/2020] [7:25:17 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:51 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:51 PM] [SSL ] › ℹ info Requesting Let'sEncrypt certificates for Cert #3: unifi.ophiuchus.fr,
[4/7/2020] [7:25:56 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:56 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-3" --agree-tos --email "example@email.com" --preferred-challenges "dns,http" --webroot --domains "unifi.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for unifi.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain unifi.ophiuchus.fr,
http-01 challenge for unifi.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:26:25 PM] [Access ] › ℹ info Building Access file #1 for: ophiuchus,
[4/7/2020] [7:26:25 PM] [Access ] › ℹ info Adding: rodolphe,
[4/7/2020] [7:26:26 PM] [Access ] › ✔ success Built Access file #1 for: ophiuchus,
[4/7/2020] [7:33:08 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:08 PM] [SSL ] › ℹ info Requesting Let'sEncrypt certificates for Cert #4: jeedom.ophiuchus.fr,
[4/7/2020] [7:33:13 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:13 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-4" --agree-tos --email "example@email.com" --preferred-challenges "dns,http" --webroot --domains "jeedom.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for jeedom.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain jeedom.ophiuchus.fr,
http-01 challenge for jeedom.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:33:15 PM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[4/7/2020] [7:33:17 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:17 PM] [SSL ] › ℹ info Renew Complete,
[4/7/2020] [7:33:17 PM] [SSL ] › ✖ error Certificate is not valid (Command failed: openssl x509 -in /etc/letsencrypt/live/npm-3/fullchain.pem -subject -noout,
Can't open /etc/letsencrypt/live/npm-3/fullchain.pem for reading, No such file or directory,
140650706484552:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen('/etc/letsencrypt/live/npm-3/fullchain.pem','r'),
140650706484552:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76:,
unable to load certificate,
),
[4/7/2020] [7:33:17 PM] [SSL ] › ✖ error Certificate is not valid (Command failed: openssl x509 -in /etc/letsencrypt/live/npm-4/fullchain.pem -subject -noout,
Can't open /etc/letsencrypt/live/npm-4/fullchain.pem for reading, No such file or directory,
140360297569608:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen('/etc/letsencrypt/live/npm-4/fullchain.pem','r'),
140360297569608:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76:,
unable to load certificate,
),
[4/7/2020] [7:33:41 PM] [Nginx ] › ℹ info Reloading Nginx,
Содержание
- When I add the SSL certificate a «Internal error» occurs. #69
- Comments
- Expected behavior
- Actual behavior
- Steps to reproduce
- Proposed changes
- Problem/Motivation
- Internal error when requesting new certificate #1365
- Comments
- Internal Error on create a new SSL cert #91
- Comments
- Expected behavior
- Real behavior
- Steps to reproduce
- Proposed changes
- Internal Error creating SSL #747
- Comments
When I add the SSL certificate a «Internal error» occurs. #69
Hello.
I am new to programming and a home assistant.
When you add an SSL certificate, an «Internal error» occurs.
I did everything according to the instructions.
Ports 80 and 431 are forwarded to the local IP address on port 8123.
Please help me with this problem.
Sorry for my english, i use google translator.
Expected behavior
Actual behavior
Steps to reproduce
(How can someone else make/see it happen)
Proposed changes
(If you have a proposed change, workaround or fix,
describe the rationale behind it)
The text was updated successfully, but these errors were encountered:
👋 Thanks for opening your first issue here! If you’re reporting a 🐛 bug, please make sure you include steps to reproduce it. Also, logs, error messages and information about your hardware might be useful.
I got the same error when trying to generate a certificate. I realized that even with the error it shows as if the certificate had been generated, however when adding the «newly generated» certificate it starts to indicate offiline system.
I got the same error.
[4/6/2020] [12:21:58 PM] [SSL ] › ✖ error Certificate is not valid (Command failed: openssl x509 -in /etc/letsencrypt/live/npm-4/fullchain.pem -subject -noout Can’t open /etc/letsencrypt/live/npm-4/fullchain.pem for reading, No such file or directory 139660590980424:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen(‘/etc/letsencrypt/live/npm-4/fullchain.pem’,’r’) 139660590980424:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76: unable to load certificate )
Same here @ startup:
I found my internal error when regenerating a new cert was router firewall related.
Problem/Motivation
Ports 80 and 431 are forwarded to the local IP address on port 8123.
The problem is that you are redirecting the external traffic to the port of your home-assistant.
Make sure you route the external traffic from port 80 and 443 to the IP of your home-assistant and to the ports: 80 and 443. The Nginx proxy manager add-on will be running on the ports 443 and 80.
In the Nginx proxy manager, you are able to set up a redirect to your home assistant IP with the port 8123.
@island-automator I have the same error.
I add port forwarding from external to my HA instances at xxx.yyy.zzz.100 and open both 80/443
But I still get same error in addon logs
I add port forwarding from external to my HA instances at xxx.yyy.zzz.100 and open both 80/443
Your port forwarding settings look correct, even though I cannot check the IP Adress of your home assistant but I assume that it correct 😉
@kamontat just to be sure is your add-on HTTPS/HTTP/SSL Entrance set to 443 and 80 in the Network section?
Also, do you have the Letsencrypt add-on installed? just to be sure can you uninstall it and try configuring the Nginx proxy manager again?
I already have a workaround. I think it because the DNS didn’t update the record immediately. I create a new A record on my DNS provider and wait a couple of hours. It works.
Yes, that usually takes sometime before it gets picked up.
Yesterday, after I tried couple way, I thinks create ssl certificates first and proxy later is better. 😉
I had the same issue
1 — Create on my router a port targeting the 80 external to 80 internal and 443 external to 443 internal.
2 — Install the Nginx Proxy Manager Addon and start
3 — Create a host as it says in the manual and I created a creation then SSL, for example, an internal error and the log below
Источник
Internal error when requesting new certificate #1365
Hi,
I get an «internal error» when I try to request a ssl certificate after setting up a proxy host.
It was working fine in july (I’ve created multiple host with working certificate the 16th july 2021), but now it seems to be broken.
I’m running NPM on a raspberry pi, inside Docker (alongside Watchtower, AdGuard Home and Portainer other containers). Being not very good at docker things and ssh command, I manage my container with Portainer GUI.
I’ve try to find a similar issue here, but without succes. Here are the first clues I can provide to you (sorry for my english from France).
My router is ok, 80 and 443 redirected to my Pi.
I can reach some services from outside my network.
So my images :
jc21/nginx-proxy-manager:latest
yobasystems/alpine-mariadb:10.4.17-arm32v7 (I try with :latest, but never get it working. I finally found some advice online saying that on the raspberry pi, you have to use this version. It works for me, but if you have advice, I will take it.
NPM container settings :
When I try to get the certificate, here are the logs inside Portainer :
Inside the console, if I run certbot renew, I get :
Those certificate correspond (I guess) to the working certificate I’ve already set up the 16th july 2021 and which are valid until october.
After that, I’m a bit lost. I don’t know how to reach the Lets’Encrypt log, or other specific log which could be useful.
Thanks for your help.
(edit : clarify syntax, anonymised personnal email and domain)
The text was updated successfully, but these errors were encountered:
Hi, anyone to give me some advice ? In your opinion, is this a known issue, or more likely a misconfiguration (maybe in the database) ?
I’ve seen the post about the v3 developpment : should I understand that this problem won’t be adress and I have to wait for the v3 release ?
Are other people using also the yobasystem databse instead of the jc21 one ? (as already mentionned, I’ve followed a guide online for my Raspberry pi). Do you think that the jc21 databse will fix this ?
Thanks for your advice.
The last console outputs states that your certs are still valid so they are skipped for renewal.
On the database topic: you don’t need it really. npm 3 will switch to an internal sqlite (as far as i unterstand). i used the official mariadb initially but i tossed it and i use the sqlite database. runs fine.
EDIT: I think the jc21 database is only there because he added the aria storage engine. but that is standard in mariadb since 10.4. So i guess that maybe that database might vanish 🙂
I experience a similar issue. An advise from another user was to delete the certificate and request a new one, but it’s not working. For some subdomains renewing worked fine, for some it failed and requesting a new one worked fine. And for some both options didn’t work. Below a part of the logfile for requesting a new certificate after deleting the expired one through the webinterface.
Hi, thanks both of you for your replies.
Today I’ve tried another way, by requesting a wildcart certificate through a DNS Challenge.
My domain name provider is OVH, I’ve correctly generate and copy/paste the key/secrets in NPM fields :
(I’ve of course replaced it by stars 😉
And after a few minutes, here is the error message NPM gives me :
Do you find any clues in this error message ?
Thanks per advance. Eric
@EricGuic Seems like your DNS isn’t working well as you can see in the Temporary failure in name resolution
Are you sure you have pointed your DNS to the correct IP?
Edit: On second reading I noticed that it is the command to install certbot that is failing. This means that your container/npm cannot get an IP address from which to install certbot. Check https://stackoverflow.com/a/46629043/16625037 and see if that solves your problem. Let me know how it goes!
Check https://stackoverflow.com/a/46629043/16625037 and see if that solves your problem. Let me know how it goes!
@thebiblelover7 , thanks to take time to read the log, I will check your link.
@thebiblelover7
I think I’m maybe not good enough to fully understand your link.
But from the first day I installed this raspberry, I was wondering on how to correctly setup the network part.
As I said, this raspberry run Adguard Home in a docker container on bridge network, and the pi has the 192.168.1.10 ip adress. The router is set up with this .10 ip adress as a dns provider.
Nginx PM is in another container, also on bridge network.
Do I have to set somewhere in the NPM container to use the DNS of the host, or another DNS set manually (like 8.8.8.8) ?
Maybe my Adguard Home is blocking some access to certbot or to Let’sEncrypt ? (but I’ve never find online a list of ip or domains used by LE for the certification process).
@thebiblelover7
I think I’m maybe not good enough to fully understand your link.
But from the first day I installed this raspberry, I was wondering on how to correctly setup the network part.
As I said, this raspberry run Adguard Home in a docker container on bridge network, and the pi has the 192.168.1.10 ip adress. The router is set up with this .10 ip adress as a dns provider.
Nginx PM is in another container, also on bridge network.
Do I have to set somewhere in the NPM container to use the DNS of the host, or another DNS set manually (like 8.8.8.8) ?
Maybe my Adguard Home is blocking some access to certbot or to Let’sEncrypt ? (but I’ve never find online a list of ip or domains used by LE for the certification process).
@EricGuic Let me try to simplfy this:
Just watch the video below and afterwards reboot
I hope this makes sense
Hi @thebiblelover7 , thank you very much for taking the time to do this little video.
I’ve followed your guide, and modified the DNS like you show me (primary the raspberry itself with Adguard home, and as a «plan B» the Cloudflare DNS).
I’ve also run this command to change the default settings of the pi :
sudo nano /etc/dhcpcd.conf
I’ve set a fallback to a static ip (192.168.1.10) and I set this two DNS again.
I’ve update+upgrade the pi, reboot it, but I still have the same error in the log of the container :
(I’ve only copied the relevant lines IMHO)
Any idea ? Should I try to completely erase and re-deploy my NPM container ? (with the mariaDB one) ?
(If that can help, I’ve also tried to request a wildcard certificate using the DNS Challenge method, by providing the token from my provider OVH). No way to make it work neither.)
@EricGuic Check this video, hope it helps!
github-docker-portainer-dns.mp4
Hi @thebiblelover7 , thanks again for your tip, it force me to go back to the basics (which I did’nt master apparently).
So I was only getting ping respond for 8.8.8.8 but not from google.com.
After settings the DNS of the host, I’ve search how to force the DNS of the docker container and found that guide online :
https://robinwinslow.uk/fix-docker-networking-dns
You can set the default DNS settings options for the docker daemon by creating a daemon configuration file at /etc/docker/daemon.json.
I’ve choosed to completely «overpassed» my AdGuardHome DNS (running on another container on the same raspberry pi) to see if it could be the problem (so Cloudflare as primary, and Google as secondary DNS)
And with that settings (and maybe in addition with the previous one made on /etc/dhcpcd.conf), everything is now working as expected. Hourra !
I’ve successfully setup a wildcard certificate for my domain (with the DNS challenge).
A’ve also tested LinuxServer SWAG, and it was giving me the same error until I set the daemon.json files.
So thank you again for your help 🙂
(may I try a last thing : what is your advice about the network config : with only AdGuard Home, watchtower (mode notify only) and NPM on the Pi, should I run NPM under the bridge network or under the specific network created by Portainer when I deployed the stack ? (see capture attached of my current config).
Источник
Internal Error on create a new SSL cert #91
Internal error when creating a new SSL certificate
Expected behavior
The creation of the SSL certificate
Real behavior
Internal error when creating a new SSL certificate
Steps to reproduce
1 — Create on my router a port targeting the 80 external to 80 internal and 443 external to 443 internal.
2 — Install the Nginx Proxy Manager Addon and start
3 — Create a host as it says in the manual and I created a creation then SSL, for example, an internal error and the log below
[5/6/2020] [2:50:27 PM] [Nginx ] › ℹ info Reloading Nginx
[5/6/2020] [2:50:27 PM] [SSL ] › ℹ info Requesting Let’sEncrypt certificates for Cert #10: xyz.duckdns.org
[5/6/2020] [2:50:50 PM] [Nginx ] › ℹ info Reloading Nginx
[5/6/2020] [2:50:50 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly —non-interactive —config «/etc/letsencrypt.ini» —cert-name «npm-10» —agree-tos —email «xyz@gmail.com» —preferred-challenges «dns,http» —webroot —domains «xyz.duckdns.org»
Saving debug log to /data/logs/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for xyz.duckdns.org
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.
Waiting for verification.
Challenge failed for domain xyz.duckdns.org
http-01 challenge for xyz.duckdns.org
Cleaning up challenges
Some challenges have failed.
Proposed changes
The text was updated successfully, but these errors were encountered:
Источник
Internal Error creating SSL #747
Checklist
When creating a proxy host, I get an internal error and ssl is not created, new to docker, learning as I go
This pic is when I try to create host proxy with ssl.
This pic is when I try to create ssl on its own without creating a host proxy.
Some of the text is cut out. here is full log.
Error: Command failed: /usr/bin/certbot certonly —non-interactive —config «/etc/letsencrypt.ini» —cert-name «npm-12» —agree-tos —email «magicman32.craig@gmail.com» —preferred-challenges «dns,http» —domains «books.beastunraid.me»
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator webroot, Installer None
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for books.beastunraid.me
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.
Waiting for verification.
Challenge failed for domain books.beastunraid.me
http-01 challenge for books.beastunraid.me
Cleaning up challenges
Some challenges have failed.
The text was updated successfully, but these errors were encountered:
As far as I am aware you must select «Use a DNS challenge» otherwise CertBot tries to use the HTTP-01 challenge which would require NPM to have access to the webroot of the server you are trying to get a cert for and I’m willing to bet that it does not have that access.
Switch on «Use a DNS challenge» then select your DNS provider, if it is on the list, then it will probably need and API token that you will get from your DNS provider. If your DNS provider is not on the list then you may need to switch to one that is. Cloudflare and probably others have free accounts available.

Im with cloudflare, am I putting in my global api key? sorry noob at this stuff
or do I need to create an api token?
You will need to create an API token. Use the «edit zone DNS» template. Make note of the created token as once you close it you will not be able to view the token again.
The global API key no longer works for this. Funny thing is that this is why I was here and saw your post. I was using the global key in some of mine and was getting a similar error when trying to renew. Switching to a created token resolved my issue.
Ok got my edit zone dns api token
What do I need to put in Credentials File content section, im not sure what to add or replace or change there?
I just tried to use Cloudflare DNS Challenge and it seems the Docker Image from JLesage does not have the Cloudflare-DNS module installed, so after running pip3 install certbot-dns-cloudflare==1.8.0
matching the version from the internal error message has now lead me to this Command Failed Error with no obvious reason standing out to me.
`Error: Command failed: /usr/bin/certbot certonly —non-interactive —cert-name «npm-15» —agree-tos —email «» —domains «*.example.com» —authenticator dns-cloudflare —dns-cloudflare-credentials «/etc/letsencrypt/credentials/credentials-15»
Traceback (most recent call last):
File «/usr/bin/certbot», line 11, in
load_entry_point(‘certbot==1.4.0’, ‘console_scripts’, ‘certbot’)()
File «/usr/lib/python3.8/site-packages/certbot/main.py», line 15, in main
return internal_main.main(cli_args)
File «/usr/lib/python3.8/site-packages/certbot/_internal/main.py», line 1315, in main
log.pre_arg_parse_setup()
File «/usr/lib/python3.8/site-packages/certbot/_internal/log.py», line 55, in pre_arg_parse_setup
temp_handler = TempHandler()
File «/usr/lib/python3.8/site-packages/certbot/_internal/log.py», line 243, in init
stream = util.safe_open(self.path, mode=’w’, chmod=0o600)
File «/usr/lib/python3.8/site-packages/certbot/util.py», line 197, in safe_open
fd = filesystem.open(path, os.O_CREAT | os.O_EXCL | os.O_RDWR, *open_args)
File «/usr/lib/python3.8/site-packages/certbot/compat/filesystem.py», line 149, in open
return os.open(file_path, flags, mode)
PermissionError: [Errno 13] Permission denied: ‘/tmp/tmpyp2bcu3c/log’
You will need to create an API token. Use the «edit zone DNS» template. Make note of the created token as once you close it you will not be able to view the token again.
The global API key no longer works for this. Funny thing is that this is why I was here and saw your post. I was using the global key in some of mine and was getting a similar error when trying to renew. Switching to a created token resolved my issue.
Did that, what next?
Ok got my edit zone dns api token
What do I need to put in Credentials File content section, im not sure what to add or replace or change there?
Источник
visitors this year: 10,901
If you need to access Home Assistant remotely away from home, skip this page and instead go to access your Home Assistant remotely using DuckDNS, Letsencrypt and the nginx SSL proxy.
This page is for those who want to access Home Assistant from outside the home, and also want to access other devices, a router, a camera or a server on your home network. If that’s you, you need to install the Home Assistant add-on called nginx Proxy Manager and not install a similar sounding add-on called ‘nginx Home Assistant SSL proxy‘. The procedure to set this up via nginx is tricky but follow along to learn how it’s done.
BTW Sorry to distract you but there’s an alternative way to have secure access to your home network – it uses Wireguard to connect your phone to the network then lets you browse your Home Assistant internal IP, router, IP camera, printer, NAS drive as if you were at your desk. The process of setting up Wireguard in Home Assistant is here.
the nginx proxy manager setup can be summarised:
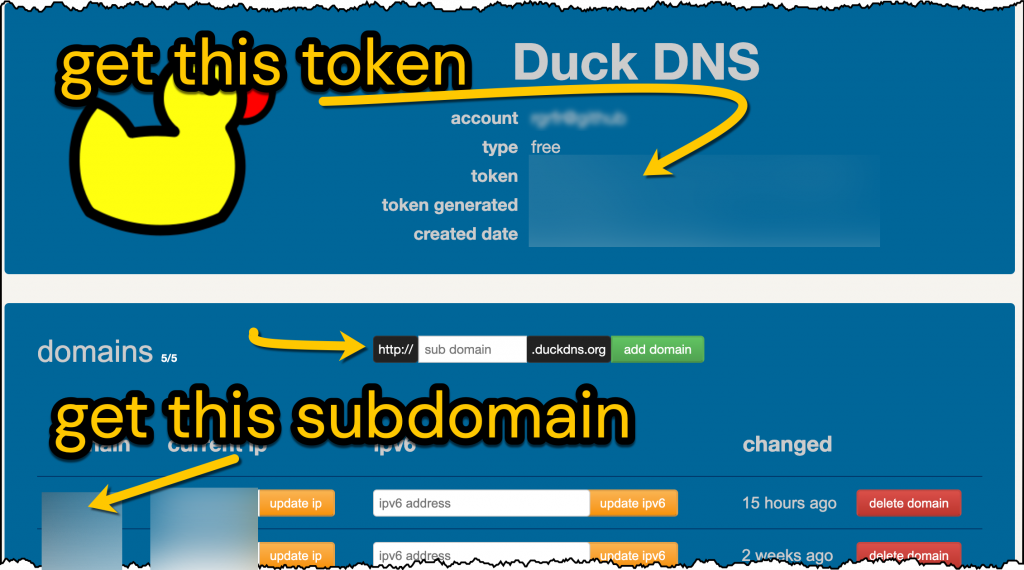
- Create an account and up to 5 subdomains at DuckDNS
- Set up the DuckDNS add-on in Home Assistant
- Temporarily edit configuration.yaml
- Set up the nginx proxy manager add-on in Home Assistant
- Forward some ports in your router.
- Set up the subdomains in nginx proxy manager
- Request certificates via nginx proxy manager
- Re-edit configuration.yaml and restart Home Assistant
- Access your Home Assistant securely using your DuckDNS subdomain without a port number.
connect Home Assistant to a subdomain at duckdns.org
When you’re away from home, the first problem to solve is to be able to find your home network. You can do that by firstly having an easy to remember network name (e.g myhome.duckdns.org). Create an account at duckdns.org, choose a subdomain and get the token (or long password) from your DuckDNS page.
The second problem to solve is that your home IP address can change. If it changes, thankfully the Home Assistant DuckDNS add-on will tell DuckDNS your latest home IP address. Go to Home Assistant > Supervisor > Add-on Store > Install Duck DNS. Then, on the Duck DNS Configuration tab fill in the information shown in bold just below:
When the DuckDNS add-on is running, you’ll be able to use your phone to access your home network from anywhere. However, there’s still more to do if you want this to happen securely.
lets_encrypt: accept_terms: true certfile: fullchain.pem keyfile: privkey.pem token: 8730bbcf-YOUR-TOKEN-FROM-DUCKDNS domains: - YOUR-SUBDOMAIN.duckdns.org - YOUR-OTHER-SUBDOMAIN.duckdns.org aliases: [] seconds: 3000
As you also want to connect to other devices on your home network I suggest that you create additional DuckDNS subdomains now.
use nginx proxy manager to get your domain connected
Go to Home Assistant > Supervisor > Add-on Store > Install nginx Proxy Manager. Then, on the nginx Proxy Manager Configuration tab fill in the information as shown below.
Wait some minutes after you start the nginx add-on. Read the Log tab nearby and hope for only happy messages there. Ideally you want the host entrance port above to be 80 not 8888. You’re welcome to try this – when I try this I get a message saying that port 80 was already in use, hence I changed it to the alt http port 8888.
open up ports for nginx in your router
Go to your home router admin page and find the port forwarding section. Forward the public inward ports to your internal private ports as follows:
- forward public tcp port 443 to private port 443 on the IP address of your Home Assistant computer
- forward public tcp port 8888 to private port 80 on the IP address of your Home Assistant computer
- do not forward public tcp ports 80 or 81 to any other computer.
temporarily edit your configuration.yaml to set up nginx
The Home Assistant docs suggest adding some lines to configuration.yaml. However I had more success setting up nginx when I commented out (#) the entire http block:
# http: # ssl_certificate: /ssl/fullchain.pem # ssl_key: /ssl/privkey.pem # use_x_forwarded_for: true # trusted_proxies: # - 10.0.0.200 # - 172.30.33.0/24
set up the host redirect on nginx proxy manager
Go to the nginx proxy manager add-on page and click Open Web UI of nginx proxy manager. There should be a sign-in page there that lets you log in with admin@example.com and password changeme. When you’re signed in create a login with your own name, email address and password.
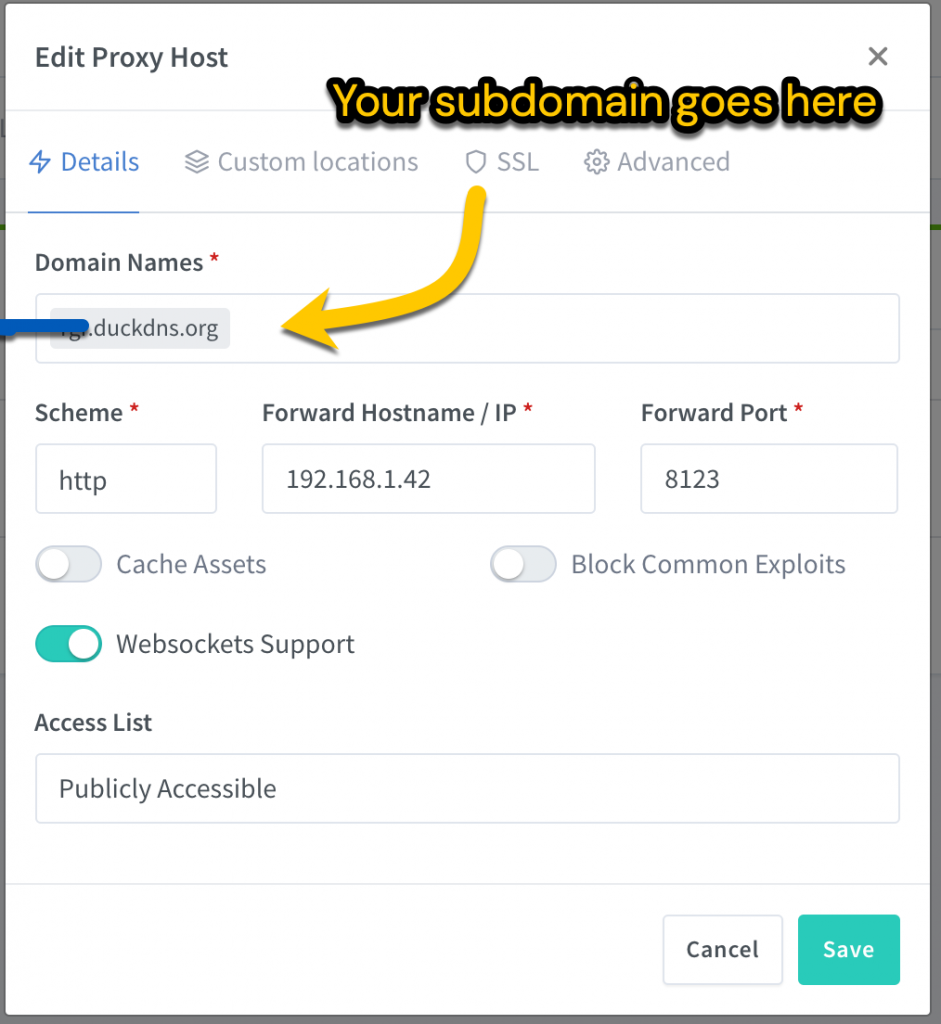
Go to the Hosts tab of nginx proxy manager. Create a new Proxy host. Enter your DuckDNS host name eg YOUR-SUBDOMAIN.duckdns.org. Turn on Websocket support. Add the internal IP address for your Home Assistant device and the port of 8123. Click Save:
Go back to the Hosts tab of nginx proxy manager. Find your DuckDNS host name eg YOUR-SUBDOMAIN.duckdns.org click the three dots to Edit this entry. Click SSL tab. Check Force SSL. Click the drop-down to Request a new SSL certificate. Agree terms and enter your DuckDNS login email address. Click Save and wait a minute for this to complete.
With luck you’ll see that a certificate was granted (by the invisible Letsencrypt). You may see Internal Error or other message in which case try again and check the steps above (which differ from the official procedure).
If you also want to connect to other devices on your home network repeat the above for those devices. In other words, create proxies for your other DuckDNS subdomains and enter the forwarding IP addresses and ports. eg 192.168.1.25:5000 might access a Synology box.
edit your configuration.yaml to get the benefit of nginx
We’re almost done. Use File Editor to change your configuration.yaml as below. It permits Home Assistant to allow access by nginx proxy (as in use_x_forwarded_for: true). The trusted proxies IP addresses are internal addresses and you may add your own to this list. The two certificate lines make my Home Assistant inaccessible so I’ve removed them by adding #. Your configuration.yaml can now read exactly as follows.
http:
# ssl_certificate: /ssl/fullchain.pem
# ssl_key: /ssl/privkey.pem
use_x_forwarded_for: true
trusted_proxies:
- 10.0.0.200
- 172.30.33.0/24
Go to the Server controls page in Home Assistant Configuration. If the configuration check here is good restart Home Assistant. To simulate connecting to your Home Assistant remotely, disconnect your phone from your home wifi and use a browser to try out YOUR-SUBDOMAIN.duckdns.org in the browser. You don’t need to add the port number to the URL because nginx is doing that for you (indeed, it’s acting as a proxy):
- If you see the Home Assistant login page: yay it works!
- If an error appears, go to the nginx proxy manager add-on logs and look for clues.
- You may see a Blank page with Bad request. Likely nginx has blocked access. Other things being equal the http: section above might be absent.
- Do not be running the other Home Assistant nginx proxy add-on.
- You may see a Home Assistant page with retry: first check that you can access Home Assistant using the normal internal address eg 192.168.1.42:8123. Check that you are accessing Home Assistant remotely and not over your wifi (although it may not matter). Check all the steps above after you’ve cleared the cache of your browser or tried another browser. Edit the URL to try access with http:// or https:// and without the port number.
- Remember that the DuckDNS add-on needs to run to refresh your certificates and your IP address. If that fails your certificate or broadband IP address will go out of date.
use nginx proxy manager to protect and allow access to other devices on your network
The point of the above tricky process was that, as well as Home Assistant, you want to access other devices such as a Synology box or a server on your home network. Suppose your other device was Synology on port 5000 with an internal address 192.168.1.20:5000. Do the following:
- Go to DuckDNS and create a subdomain such as mysynology.duckdns.org
- Go to the DuckDNS add-on and add mysynology.duckdns.org to its configuration. The add-on should restart.
- Optional (but required on my system): use Home Assistant File Editor to comment out the http: section of configuration.yaml. In Server Controls check the configuration and restart Home Assistant.
- Optional – check that the router has the open ports as earlier. (You may have changed the ports since you set up the initial Home Assistant proxy.)
- Go to the nginx proxy manager add-on. Open web UI and login again (your previously entered login should be used). Set up a new proxy for that subdomain – enter the forwarding IP address 192.168.1.20 and the port 5000 as used by the Synology box and Save it.
- Edit the proxy and use the SSL tab to Request a new certificate. Enter your email and Agree to terms. Force SSL and click Save.
- If you get an Internal Error rather than a Letsencrypt certificate then you may well need the optional steps 3, 4 and 8 to make progress.
- Optional (but required on my system): use Home Assistant File Editor to restore the http: section of configuration.yaml. In Server Controls check the configuration and restart Home Assistant.
- Use a browser to access your Synology from outside your network with mysynology.duckdns.org
close the unnecessary ports in your router
Go to your home router admin and find the port forwarding / virtual servers section. You can check the ports as follows:
- forward public tcp port 443 to private port 443 on the IP address of your Home Assistant computer
- forward public tcp port 8888 to private port 80 on the IP address of your Home Assistant computer.
- don’t forward public tcp ports 80 or 81 to any computer.
Я обнаружил, что это проверка докеров, похоже, что что-то блокирует завиток, чего не должно быть
[
{
"Id": "5396c4e1207e3486ccb714d7cf9f2027f8be83c35fcbc5c0393d7cb3120a4609",
"Created": "2019-07-26T12:05:10.838857676Z",
"Path": "/init",
"Args": [],
"State": {
"Status": "running",
"Running": true,
"Paused": false,
"Restarting": false,
"OOMKilled": false,
"Dead": false,
"Pid": 15761,
"ExitCode": 0,
"Error": "",
"StartedAt": "2019-07-29T07:06:18.91961627Z",
"FinishedAt": "2019-07-29T07:05:44.533099275Z",
"Health": {
"Status": "unhealthy",
"FailingStreak": 23,
"Log": [
{
"Start": "2019-07-29T07:11:08.475218801Z",
"End": "2019-07-29T07:11:08.698302026Z",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2019-07-29T07:11:23.708785289Z",
"End": "2019-07-29T07:11:23.931405635Z",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2019-07-29T07:11:38.941957592Z",
"End": "2019-07-29T07:11:39.161505674Z",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2019-07-29T07:11:54.171975308Z",
"End": "2019-07-29T07:11:54.424361521Z",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
При попытке проверить связь с моим собственным IP-адресом на порту 9876 (докер-прокси я получаю это)
(основан там https://github.com/EOSIO/eosio-project-demux-example/issues/25)
Хорошо, я ничего не сказал, он сделал это снова, и я понял, в чем проблема. Итак, просто создайте новый прокси-хост «Запросить новый сертификат SSL». Затем подтвердите, как только вы это сделаете, измените хост и добавьте еще несколько доменов, поддоменов и вернитесь в сертификаты ssl и «Запросите новый сертификат SSL» сохраните его, и это внутренняя ошибка.
После этого уже невозможно использовать давайте снова зашифровать
Я столкнулся с этой проблемой только сегодня. Я исходил из предположения, что это ошибка.
Изучая журналы докеров, я заметил, что он искал «npm-4» и «npm-5», но не смог их найти. В конце концов я решил удалить ошибку SSL и переделать прокси-сервер, снова запросив SSL.
Когда вы просматриваете журналы докеров, что они содержат?
У меня такая же проблема.
Определенно есть ошибка с сертификатами Let’s Encrypt.
В настоящее время мой прокси-менеджер Enginx работает только на порту 81 (поэтому у меня есть доступ к панели). Что бы я ни пытался изменить — у меня внутренняя ошибка (но после обновления веб-страницы изменения выглядят как сохраненные). К сожалению, весь мой веб-трафик по этой проблеме мертв 
Мне удалось запустить его, просто скопировав любой другой сертификат в место, где ищет скрипт, и все начинает работать:
Мне удалось запустить его, просто скопировав любой другой сертификат в место, где ищет скрипт, и все начинает работать:
Вы можете мне объяснить, что именно вы сделали, и теперь это работает? (Также я новичок в докере, поэтому, если бы вы могли предоставить команду для доступа к оболочке докера, было бы очень приятно от вас c:!)
Я использовал Portainer (графический интерфейс Docker), но вы можете сделать это, выполнив следующую команду на своем сервере узла:
Чтобы перечислить все контейнеры докеров:
$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3xamp13id my_image X hours ago Up X hours my_container
Ввести в контейнер:
$ docker exec -it 3xamp13id bash
Затем внутри просто зайдите в каталоги /etc/letsencrypt/live и скопируйте любой другой сертификат на место, где он отсутствует.
Вы также можете сделать это на уровне тома, поскольку каталоги letsencrypt должны находиться вне контейнера dicker.
В конфигурации по умолчанию:
volumes:
# Make sure this config.json file exists as per instructions above:
- ./config.json:/app/config/production.json
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
Большое спасибо! Надеюсь, @ jc21 это увидит, так что, возможно, он найдет исправление для этого
Ага, такая же проблема.
Кто-нибудь еще нашел исправление, которое не связано с возиться с самим контейнером? Я совсем не знаком с Докером, я рад, что он у меня как-то работает, ха-ха 
Давайте еще раз
Тоже самое. Также работает на докере.
То же самое, но у меня проблемы с NAT Loopback (из-за моего роутера). Может ли это быть проблемой?
Я не проверял глубоко свои журналы, когда это происходит, но это может быть случай (я использую его в домашней конфигурации и за домашним маршрутизатором).
Те же проблемы, что и выше. Не знаю, Docker — настройка друга для меня. Работал вечно, но мне пришлось заново создать образ диска ОС (все виртуальные вещи через HyperV, и ничего из этого не было даже на диске ОС). После этого ничего не работает. Я пытаюсь удалить все хосты и сертификаты SSL и получаю «Внутреннюю ошибку» для всего. Надеюсь, что кто-то опубликует кое-что, чтобы попытаться / команда исправить
Я думаю, что нашел проблему. Когда указанный вами URL-адрес недоступен, он будет действовать так, как будто все работает, вместо того, чтобы сообщать вам, что пошло не так. Я случайно дал ему URL-адрес, который еще не был настроен должным образом.
У меня возникла такая же проблема вчера после обновления до 2.1.0. Откат на 2.0.14 вроде бы исправил.
@ lachlan334 было бы неплохо узнать, почему это не удалось, в журналах
Ребят, у меня тоже нездоровый статус npm-container, но работает … какие будут рекомендации?
@ lachlan334 было бы неплохо узнать, почему это не удалось, в журналах
Результат проверки работоспособности: % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 curl: (7) Failed to connect to localhost port 9876: Connection refused
Журналы бывают следующие:
[s6-init] making user provided files available at /var/run/s6/etc...exited 0.,
[s6-init] ensuring user provided files have correct perms...exited 0.,
[fix-attrs.d] applying ownership & permissions fixes...,
[fix-attrs.d] done.,
[cont-init.d] executing container initialization scripts...,
[cont-init.d] done.,
[services.d] starting services,
[services.d] done.,
[2/21/2020] [2:53:12 AM] [Migrate ] › ℹ info Current database version: 20190227065017,
[2/21/2020] [2:53:12 AM] [IP Ranges] › ℹ info Fetching IP Ranges from online services...,
[2/21/2020] [2:53:12 AM] [IP Ranges] › ℹ info Fetching https://ip-ranges.amazonaws.com/ip-ranges.json,
[2/21/2020] [2:53:15 AM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v4,
[2/21/2020] [2:53:15 AM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v6,
[2/21/2020] [2:53:15 AM] [SSL ] › ℹ info Let's Encrypt Renewal Timer initialized,
[2/21/2020] [2:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [2:53:15 AM] [IP Ranges] › ℹ info IP Ranges Renewal Timer initialized,
[2/21/2020] [2:53:15 AM] [Global ] › ℹ info Backend PID 206 listening on port 3000 ...,
[2/21/2020] [2:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [2:53:16 AM] [SSL ] › ℹ info Renew Complete,
`QueryBuilder#allowEager` method is deprecated. You should use `allowGraph` instead. `allowEager` method will be removed in 3.0,
`QueryBuilder#eager` method is deprecated. You should use the `withGraphFetched` method instead. `eager` method will be removed in 3.0,
QueryBuilder#omit is deprecated. This method will be removed in version 3.0,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [3:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [3:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [3:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
Connection Error: Error: Packets out of order. Got: 1 Expected: 16,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [4:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [4:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [4:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [5:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [5:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [5:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [6:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [6:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [6:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [7:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [7:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [7:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [8:53:15 AM] [IP Ranges] › ℹ info Fetching IP Ranges from online services...,
[2/21/2020] [8:53:15 AM] [IP Ranges] › ℹ info Fetching https://ip-ranges.amazonaws.com/ip-ranges.json,
[2/21/2020] [8:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [8:53:15 AM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v4,
[2/21/2020] [8:53:15 AM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v6,
[2/21/2020] [8:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [8:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [8:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [9:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [9:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [9:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
[2/21/2020] [10:53:15 AM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[2/21/2020] [10:53:16 AM] [Nginx ] › ℹ info Reloading Nginx,
[2/21/2020] [10:53:16 AM] [SSL ] › ℹ info Renew Complete,
Connection Error: Error: read ECONNRESET,
@ lachlan334 привет, приятель, у меня такой же .. но npm работает нормально.
Last output | % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 curl: (7) Failed to connect to localhost port 9876: Connection refused
-- | --
Если это что-то значит, я получаю эту ошибку с версией 2.0.14 при запуске образа докера jlesage / nginx-proxy-manager
@GregHilston Ага, это очень много значит. Я не обслуживаю изображения jlesage . Сейчас у нас версия 2.1.1, и порт 9876 больше не используется внутри компании.
@ lachlan334 Похоже, вы использовали этот образ 2.1.1, но не имеет смысла, почему Healthcheck все еще использует настройку из предыдущего образа докера. При правильной проверке работоспособности в конечном итоге будет запущена команда curl: curl --silent http://127.0.0.1:81/api/ из контейнера NPM.
Возможно, попробуйте полностью опустить стек и вернуть его обратно, предполагая, что у вас есть тома, смонтированные в каталоге: docker-compose down && docker-compose up -d
У меня похожая проблема. Запрос нового сертификата SSL вызывает внутреннюю ошибку.
Проверка контейнера докеров показывает, что он неработоспособен и выдает некоторые ошибки:
`
[
{
"Id": "9d2d526acb3512e60ca4db020b9ef86b93e859735267d224223ca40f5054b3d4",
"Created": "2020-02-21T02:30:55.239750232Z",
"Path": "/init",
"Args": [],
"State": {
"Status": "running",
"Running": true,
"Paused": false,
"Restarting": false,
"OOMKilled": false,
"Dead": false,
"Pid": 3473,
"ExitCode": 0,
"Error": "",
"StartedAt": "2020-02-21T02:30:58.116917696Z",
"FinishedAt": "0001-01-01T00:00:00Z",
"Health": {
"Status": "unhealthy",
"FailingStreak": 20095,
"Log": [
{
"Start": "2020-02-24T16:56:39.096936098+01:00",
"End": "2020-02-24T16:56:39.294612731+01:00",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0r 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0ncurl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2020-02-24T16:56:54.409165629+01:00",
"End": "2020-02-24T16:56:54.726601709+01:00",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0r 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0ncurl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2020-02-24T16:57:09.810871898+01:00",
"End": "2020-02-24T16:57:10.019143483+01:00",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0r 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0ncurl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2020-02-24T16:57:25.125134859+01:00",
"End": "2020-02-24T16:57:25.335763382+01:00",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0r 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0ncurl: (7) Failed to connect to localhost port 9876: Connection refusedn"
},
{
"Start": "2020-02-24T16:57:40.435902211+01:00",
"End": "2020-02-24T16:57:40.643842955+01:00",
"ExitCode": 1,
"Output": " % Total % Received % Xferd Average Speed Time Time Time Currentn Dload Upload Total Spent Left Speednr 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0r 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0ncurl: (7) Failed to connect to localhost port 9876: Connection refusedn"
}
]
}
`
Здесь я увидел отказ в соединении на 9876, не зная, чем это вызвано.
Я использую образ jc21, работающий под управлением версии 2.1.1.
Я не хочу угонять, но, возможно, это та же проблема, с которой столкнулся OP.
РЕДАКТИРОВАТЬ: форматирование кода
Здесь я увидел отказ в соединении на 9876, не зная, чем это вызвано.
Я использую образ jc21, работающий под управлением версии 2.1.1.
Тоже самое ! Использование образа jc21 версии 2.1.1 на мосту докеров.
РЕДАКТИРОВАТЬ: удаление контейнера и создание нового с нуля все же исправили.
Не уверен, что это ошибка докера или ожидаемое поведение, но похоже, что обновление образа докера в уже созданном контейнере не обновляет проверку работоспособности. Между 2.0. * И 2.1. * NPM произошло довольно много изменений, поэтому я рекомендую полностью отключить стек и воссоздать его.
Однако можно использовать существующие монтирования data и letsencrypt .
Тем не менее, проверка работоспособности не должна влиять на возможность продления сертификата.
Спасибо за ответ jc21.
Не знаю, как другие пользователи, но в моем случае это чистый контейнер / образ версии 2.1.1.
Я воссоздал его один раз, повторно используя данные, и давайте зашифруем папку. Но получение сертификатов SSL так и не помогло.
В конце концов я отказался от этого и использовал свои Synology nas для получения сертификатов и ручного импорта их в Nginx, который работал нормально.
Но было бы неплохо узнать, почему возникает внутренняя ошибка и почему журнал спамит отказ в соединении на порт 9876.
Могу ли я представить что-нибудь, что могло бы помочь вам понять ситуацию?
С уважением.
У меня такая же ошибка и нездоровый статус в Docker. Раньше у меня появлялось сообщение об ошибке, но в настоящее время я все еще могу создавать новые сертификаты. Я попытался удалить старые сертификаты и воссоздать их, но у меня всегда один и тот же нездоровый контейнер 
Вывод из моего контейнера ниже, если это помогает
Докер:
% Всего% Получено% Xferd Средняя скорость Время Время Время Текущая загрузка загрузки Общая затраченная оставшаяся скорость 0 0 0 0 0 0 0 0 -: -: — -: -: — -: -: — 0 0 0 0 0 0 0 0 0 -: -: — -: -: — -: -: — 0 curl: (7) Не удалось подключиться к порту localhost 9876: В соединении отказано
Журналы:
Traceback (последний вызов последний):,
Файл «/usr/lib/python3.8/site-packages/certbot/_internal/renewal.py», строка 64, в _reconstitute,
возобновление_кандидате = хранилище.RenewableCert (полный_путь, конфигурация),
Файл «/usr/lib/python3.8/site-packages/certbot/_internal/storage.py», строка 465, в __init__,
self._check_symlinks (),
Файл «/usr/lib/python3.8/site-packages/certbot/_internal/storage.py», строка 531, в _check_symlinks,
вызывать ошибки. CertStorageError (,
certbot.errors.CertStorageError: ожидается, что /etc/letsencrypt/live/npm-2/cert.pem будет символической ссылкой,
Файл конфигурации обновления /etc/letsencrypt/renewal/npm-2.conf поврежден. Пропуская.,
,
… [Повторяется до npm-7] …
,
в ChildProcess.exithandler (child_process.js: 295: 12),
в ChildProcess.emit (events.js: 210: 5),
в mightClose (internal / child_process.js: 1028: 16),
в Process.ChildProcess._handle.onexit (internal / child_process.js: 283: 5),
Существует образ github-develop docker, который удалил 9876 из Dockerfile EXPOSE. Это был последний след этого порта во всей кодовой базе, и хотя изображения 2.1. * Не должны использовать этот порт вообще, по некоторым причинам, относящимся к конкретным людям, это может иметь значение.
Итак, используйте тег github-develop image, убедитесь, что предыдущий контейнер полностью удален, прежде чем создавать новый. Я упомяну шаги здесь для тех, кто не знает:
docker rm -f name_of_nginx_proxy_manager_container
или же
docker-compose down
Если после этого в ваших проверках состояния будут какие-либо следы этого порта 9876, я буквально переверну свой стол и в ярости выйду из этого проекта.
Удаление контейнера и установка нового с использованием изображения github-develop решило внутреннюю ошибку при запросе сертификатов SSL для меня.
Я вижу, что порт 9876 больше не используется этим образом.
Мне только что удалось получить сертификаты Let’s Encrypt для всех моих прокси-хостов напрямую через Nginx, какое счастье!
В настоящее время я не могу подключиться к своему устройству по SSH (разрешено только из локальной сети, и я сейчас нахожусь в офисе), поэтому, вернувшись домой, я проверю состояние работоспособности контейнера докеров. Вернусь к вам!
Могу подтвердить!
Используется github-develop image, и контейнер снова становится работоспособным, порт 9876 больше не используется! Я пробовал это на 3 разных хостах, и контейнеры больше не вредны.
Существует образ
github-developdocker, который удалил 9876 из Dockerfile EXPOSE. Это был последний след этого порта во всей кодовой базе, и хотя изображения 2.1. * Не должны использовать этот порт вообще, по некоторым причинам, относящимся к конкретным людям, это может иметь значение.Итак, используйте тег
github-developimage, убедитесь, что предыдущий контейнер полностью удален, прежде чем создавать новый. Я упомяну шаги здесь для тех, кто не знает:
docker rm -f name_of_nginx_proxy_manager_container
или же
docker-compose downЕсли после этого в ваших проверках состояния будут какие-либо следы этого порта 9876, я буквально переверну свой стол и в ярости выйду из этого проекта.
Я только что пришел домой и проверил через SSH состояние работоспособности контейнера докеров. Выглядит прекрасно!
Здоровье «: {
«Статус»: «здоров»,
«FailingStreak»: 0,
Не нужно переворачивать стол и в ярости бросить проект @ jc21 
Я сбросил ядерную бомбу на свой контейнер и перестроил с помощью github-develop, и мой теперь тоже счастлив и здоров. Благодаря!
Также можно подтвердить, что использование изображения github-develop устранило проблему.
Да, после удаления контейнера и использования изображения github-docker сертификаты обновляются автоматически.
Хорошо, сладко, я объединю и перевыпущу сегодня. Фух 
Итак, ребята, что мне нужно делать? Использовать проявку контейнера? «Потому что я все еще нездоров. Заранее спасибо.
@SAOPP unhealthy обычно означает, что контейнеру потребовалось более 5 секунд, чтобы вернуть статус ОК. Если вы можете создавать новые сертификаты SSL, все будет в порядке. Нездоровый статус не имеет большого значения.
Да, я понял это, просто интересно, и да, я могу создать новые сертификаты, но я вижу, что ребята говорили о невозможности автоматического продления сертификатов, или я неправильно понял?
Пожалуйста, простите меня за то, что я не информирован о Docker, но когда это будет распространено в такие места, как Dockerhub? Я использую среду Unraid.
Можно ли пока что загрузить и использовать свой собственный сертификат, например сертификат Cloudflare?
Ах я вижу! Мой был извлечен из jlesage / nginx-proxy-manager /, который устарел на 5 месяцев.
Это должен быть какой-то другой образ Docker, который не так хорошо поддерживается. Я, наверное, должен использовать это вместо этого. Спасибо.
jlesage придется обновлять свои собственные образы докеров каждый раз, когда я выпускаю свои. У меня нет настройки без страха, поэтому я не знаю, какие изменения необходимы, чтобы она работала
Здравствуйте,
Я только что установил последнюю версию npm.
docker-compose.yml
version: "3"
services:
app:
image: jc21/nginx-proxy-manager:latest
restart: always
ports:
- 80:80
- 81:81
- 443:443
volumes:
- ./config.json:/app/config/production.json
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
depends_on:
- db
environment:
# if you want pretty colors in your docker logs:
- FORCE_COLOR=1
db:
image: mariadb:latest
restart: always
environment:
MYSQL_ROOT_PASSWORD: "npm"
MYSQL_DATABASE: "npm"
MYSQL_USER: "npm"
MYSQL_PASSWORD: "npm"
volumes:
- ./data/mysql:/var/lib/mysql
config.json
{
"database": {
"engine": "mysql",
"host": "db",
"name": "npm",
"user": "npm",
"password": "npm",
"port": 3306
}
}
Я попытался добавить новые сертификаты SSL, и у меня возникает эта проблема, когда я пытаюсь его сгенерировать:
я имею
Спасибо за все
@ rto54 без логов самих докер-контейнеров, отлаживать можно не так много. Вы можете их предоставить?
@nldoty , Вы можете мне в этом помочь.
Я новичок с докером 
Спасибо
[
4/7/2020] [6:55:06 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [6:55:07 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-2" --agree-tos --email "[email protected]" --preferred-challenges "dns,http" --webroot --domains "unifi.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for unifi.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain unifi.ophiuchus.fr,
http-01 challenge for unifi.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:03:09 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:24 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:32 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:03:42 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #2: unifi.ophiuchus.fr,
[4/7/2020] [7:03:43 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-2" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-2 (expected /etc/letsencrypt/renewal/npm-2.conf).,
,
[4/7/2020] [7:03:46 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:03:48 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:05:41 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:05:43 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
Connection Error: Error: read ECONNRESET,
[4/7/2020] [7:22:47 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:22:48 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:23:19 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:23:23 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:23:53 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:24:08 PM] [SSL ] › ℹ info Renewing Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:24:09 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot renew --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-1" --preferred-challenges "dns,http" --disable-hook-validation ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
No certificate found with name npm-1 (expected /etc/letsencrypt/renewal/npm-1.conf).,
,
[4/7/2020] [7:24:14 PM] [SSL ] › ℹ info Revoking Let'sEncrypt certificates for Cert #1: jeedom.ophiuchus.fr,
[4/7/2020] [7:24:22 PM] [SSL ] › ℹ info Revoking Let'sEncrypt certificates for Cert #2: unifi.ophiuchus.fr,
[4/7/2020] [7:25:17 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:51 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:51 PM] [SSL ] › ℹ info Requesting Let'sEncrypt certificates for Cert #3: unifi.ophiuchus.fr,
[4/7/2020] [7:25:56 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:25:56 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-3" --agree-tos --email "[email protected]" --preferred-challenges "dns,http" --webroot --domains "unifi.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for unifi.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain unifi.ophiuchus.fr,
http-01 challenge for unifi.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:26:25 PM] [Access ] › ℹ info Building Access file #1 for: ophiuchus,
[4/7/2020] [7:26:25 PM] [Access ] › ℹ info Adding: rodolphe,
[4/7/2020] [7:26:26 PM] [Access ] › ✔ success Built Access file #1 for: ophiuchus,
[4/7/2020] [7:33:08 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:08 PM] [SSL ] › ℹ info Requesting Let'sEncrypt certificates for Cert #4: jeedom.ophiuchus.fr,
[4/7/2020] [7:33:13 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:13 PM] [Express ] › ⚠ warning Command failed: /usr/bin/certbot certonly --non-interactive --config "/etc/letsencrypt.ini" --cert-name "npm-4" --agree-tos --email "[email protected]" --preferred-challenges "dns,http" --webroot --domains "jeedom.ophiuchus.fr" ,
Saving debug log to /var/log/letsencrypt/letsencrypt.log,
Plugins selected: Authenticator webroot, Installer None,
Obtaining a new certificate,
Performing the following challenges:,
http-01 challenge for jeedom.ophiuchus.fr,
Using the webroot path /data/letsencrypt-acme-challenge for all unmatched domains.,
Waiting for verification...,
Challenge failed for domain jeedom.ophiuchus.fr,
http-01 challenge for jeedom.ophiuchus.fr,
Cleaning up challenges,
Some challenges have failed.,
,
[4/7/2020] [7:33:15 PM] [SSL ] › ℹ info Renewing SSL certs close to expiry...,
[4/7/2020] [7:33:17 PM] [Nginx ] › ℹ info Reloading Nginx,
[4/7/2020] [7:33:17 PM] [SSL ] › ℹ info Renew Complete,
[4/7/2020] [7:33:17 PM] [SSL ] › ✖ error Certificate is not valid (Command failed: openssl x509 -in /etc/letsencrypt/live/npm-3/fullchain.pem -subject -noout,
Can't open /etc/letsencrypt/live/npm-3/fullchain.pem for reading, No such file or directory,
140650706484552:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen('/etc/letsencrypt/live/npm-3/fullchain.pem','r'),
140650706484552:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76:,
unable to load certificate,
),
[4/7/2020] [7:33:17 PM] [SSL ] › ✖ error Certificate is not valid (Command failed: openssl x509 -in /etc/letsencrypt/live/npm-4/fullchain.pem -subject -noout,
Can't open /etc/letsencrypt/live/npm-4/fullchain.pem for reading, No such file or directory,
140360297569608:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen('/etc/letsencrypt/live/npm-4/fullchain.pem','r'),
140360297569608:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76:,
unable to load certificate,
),
[4/7/2020] [7:33:41 PM] [Nginx ] › ℹ info Reloading Nginx,
Журналы letsencrypt
[[email protected]:/var/log/letsencrypt]# vi letsencrypt.log
2020-04-07 20:01:27,880:DEBUG:certbot._internal.main:certbot version: 1.0.0
2020-04-07 20:01:27,881:DEBUG:certbot._internal.main:Arguments: ['--non-interactive', '--config', '/etc/letsencrypt.ini', '--cert-name', 'npm-3', '--preferred-challenges', 'dns,http', '--disable-hook
2020-04-07 20:01:27,881:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2020-04-07 20:01:27,919:DEBUG:certbot._internal.log:Root logging level set at 20
2020-04-07 20:01:27,919:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2020-04-07 20:01:27,920:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 11, in <module>
load_entry_point('certbot==1.0.0', 'console_scripts', 'certbot')()
File "/usr/lib/python3.8/site-packages/certbot/main.py", line 14, in main
return internal_main.main(cli_args)
File "/usr/lib/python3.8/site-packages/certbot/_internal/main.py", line 1350, in main
return config.func(config, plugins)
File "/usr/lib/python3.8/site-packages/certbot/_internal/main.py", line 1259, in renew
renewal.handle_renewal_request(config)
File "/usr/lib/python3.8/site-packages/certbot/_internal/renewal.py", line 391, in handle_renewal_request
conf_files = [storage.renewal_file_for_certname(config, config.certname)]
File "/usr/lib/python3.8/site-packages/certbot/_internal/storage.py", line 52, in renewal_file_for_certname
raise errors.CertStorageError("No certificate found with name {0} (expected "
certbot.errors.CertStorageError: No certificate found with name npm-3 (expected /etc/letsencrypt/renewal/npm-3.conf).
Кажется, у меня очень похожая проблема …
У меня тоже была проблема до получения последнего изображения
журналы докеров nginx_proxy
[4/16/2020] [3:17:52 PM] [Migrate ] › ℹ info Current database version: 20200410143839
[4/16/2020] [3:17:52 PM] [IP Ranges] › ℹ info Fetching IP Ranges from online services...
[4/16/2020] [3:17:52 PM] [IP Ranges] › ℹ info Fetching https://ip-ranges.amazonaws.com/ip-ranges.json
[4/16/2020] [3:17:52 PM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v4
[4/16/2020] [3:17:53 PM] [IP Ranges] › ℹ info Fetching https://www.cloudflare.com/ips-v6
[4/16/2020] [3:17:53 PM] [SSL ] › ℹ info Let's Encrypt Renewal Timer initialized
[4/16/2020] [3:17:53 PM] [SSL ] › ℹ info Renewing SSL certs close to expiry...
[4/16/2020] [3:17:53 PM] [IP Ranges] › ℹ info IP Ranges Renewal Timer initialized
[4/16/2020] [3:17:53 PM] [Global ] › ℹ info Backend PID 203 listening on port 3000 ...
`QueryBuilder#allowEager` method is deprecated. You should use `allowGraph` instead. `allowEager` method will be removed in 3.0
`QueryBuilder#eager` method is deprecated. You should use the `withGraphFetched` method instead. `eager` method will be removed in 3.0
QueryBuilder#omit is deprecated. This method will be removed in version 3.0
[4/16/2020] [3:18:46 PM] [SSL ] › ✖ error Error: Command failed: /usr/bin/certbot renew --non-interactive --quiet --config "/etc/letsencrypt.ini" --preferred-challenges "dns,http" --disable-hook-validation
Challenge failed for domain cloud.domain.net
Challenge failed for domain www.domain.net
Attempting to renew cert (npm-3) from /etc/letsencrypt/renewal/npm-3.conf produced an unexpected error: Some challenges have failed.. Skipping.
All renewal attempts failed. The following certs could not be renewed:
/etc/letsencrypt/live/npm-3/fullchain.pem (failure)
1 renew failure(s), 0 parse failure(s)
at ChildProcess.exithandler (child_process.js:295:12)
at ChildProcess.emit (events.js:210:5)
at maybeClose (internal/child_process.js:1028:16)
at Process.ChildProcess._handle.onexit (internal/child_process.js:283:5)
container-start.sh
docker create
--name $name
-p 80:80
-p 443:443
-p 81:81
-v /mnt/z.raid1/software.docker/A-dockerStartFiles/nginx-proxy/config.json:/app/config/production.json
-v /mnt/z.raid1/software.docker/nginx_proxy/data:/data
-v /mnt/z.raid1/software.docker/nginx_proxy/letsencrypt:/etc/letsencrypt
-e TZ=Europe/Helsinki
-e FORCE_COLOR=1
--restart unless-stopped
--log-opt max-size=1m
jc21/nginx-proxy-manager:latest
образ докера проверить jc21 / nginx-proxy- manager: последний
[
{
"Id": "sha256:ed18ab76b851f62ab3672b5a35b19f43671a4380c4bb8d95b4209a08c6de36e5",
"RepoTags": [
"jc21/nginx-proxy-manager:latest"
],
"RepoDigests": [
"jc21/nginx-proxy-manager<strong i="11">@sha256</strong>:940681f8439604c9a5a2b88d2036adbcdd23675908bf915806a3289fa8c6b226"
],
"Parent": "",
"Comment": "buildkit.dockerfile.v0",
"Created": "2020-04-15T06:02:31.803807951Z",
журналы в контейнере:
(/var/log/letsencrypt/letsencrypt.log)
2020-04-17 08:21:32,578:INFO:certbot._internal.renewal:Cert not yet due for renewal
2020-04-17 08:21:32,580:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2020-04-17 08:21:32,583:DEBUG:certbot._internal.cli:Var pref_challs=dns,http (set by user).
2020-04-17 08:21:32,583:DEBUG:certbot._internal.cli:Var authenticator=webroot (set by user).
2020-04-17 08:21:32,584:DEBUG:certbot._internal.cli:Var webroot_path=/data/letsencrypt-acme-challenge (set by user).
2020-04-17 08:21:32,584:DEBUG:certbot._internal.cli:Var webroot_map={'webroot_path'} (set by user).
2020-04-17 08:21:32,584:DEBUG:certbot._internal.cli:Var webroot_path=/data/letsencrypt-acme-challenge (set by user).
2020-04-17 08:21:32,609:INFO:certbot._internal.renewal:Cert not yet due for renewal
2020-04-17 08:21:32,612:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2020-04-17 08:21:32,612:ERROR:certbot._internal.renewal:All renewal attempts failed. The following certs could not be renewed:
2020-04-17 08:21:32,613:ERROR:certbot._internal.renewal: /etc/letsencrypt/live/npm-3/fullchain.pem (failure)
2020-04-17 08:21:32,613:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 11, in <module>
load_entry_point('certbot==1.0.0', 'console_scripts', 'certbot')()
File "/usr/lib/python3.8/site-packages/certbot/main.py", line 14, in main
return internal_main.main(cli_args)
File "/usr/lib/python3.8/site-packages/certbot/_internal/main.py", line 1350, in main
return config.func(config, plugins)
File "/usr/lib/python3.8/site-packages/certbot/_internal/main.py", line 1259, in renew
renewal.handle_renewal_request(config)
File "/usr/lib/python3.8/site-packages/certbot/_internal/renewal.py", line 473, in handle_renewal_request
raise errors.Error("{0} renew failure(s), {1} parse failure(s)".format(
certbot.errors.Error: 1 renew failure(s), 0 parse failure(s)
Сообщите мне, если выше отсутствует какая-либо другая информация.
Не уверен, что кто-то еще сталкивался с этим. Я запускаю прокси-контейнер на виртуальной машине внутри корпоративной сети, и когда я пытаюсь создать прокси в Nginx Proxy Manager, я тоже получаю «Внутреннюю ошибку», и в журнале я вижу, что позволяет шифрованию не проверять мой домен. В разделе «Сертификаты SSL» есть запись, но срок ее действия немедленно истек. В используемом нами диспетчере DNS мой домен сопоставлен с IP-адресом хоста машины, на которой я запускаю прокси-контейнер в зоне прямого просмотра. Прав ли я, думая, что letsencrypt просто не может связаться с моим доменом, чтобы подтвердить, что «он принадлежит мне»?
2020-05-04 17: 10: 39,713: ОТЛАДКА: urllib3.connectionpool : https://acme-v02.api.letsencrypt.org : 443 «POST / acme / authz-v3 / 4362994539 HTTP / 1.1» 200625
2020-05-04 17: 10: 39 714: DEBUG: acme.client : Получен ответ:
HTTP 200
Сервер: nginx
Дата: пн, 04 мая 2020 17:11:21 GMT
Тип содержимого: приложение / json
Длина содержимого: 625
Подключение: keep-alive
Запрашивающий валун: 85028888
Cache-Control: общедоступный, max-age = 0, no-cache
Ссылка: https://acme-v02.api.letsencrypt.org/directory ; rel = «index»
Replay-Nonce: 0002Z8epRT7DdbUiCHQ6gsOQuvNlarPnL7KRDGYsEg7qoCM
Параметры X-Frame: ОТКАЗАТЬ
Строгая безопасность транспорта: max-age = 604800
{
«идентификатор»: {
«тип»: «днс»,
«значение»: «»
},
«статус»: «недействительный»,
«истекает»: «2020-05-11T17: 11: 19Z»,
«вызовы»: [
{
«тип»: «http-01»,
«статус»: «недействительный»,
«ошибка»: {
«тип»: » urn: ietf : params: acme : error: dns «,
«detail»: «Проблема с DNS: NXDOMAIN ищет A для- убедитесь, что для этого домена существует DNS-запись »,
«статус»: 400
},
«url»: » https://acme-v02.api.letsencrypt.org/acme/chall-v3/4362994539/zHEy1w «,
«токен»: «PCdm1kOKDDqyzF4LX6-gAt0omNYuV0iwRNBtQ0NLR5Q»
}
]
}
@ jmford775 Да, вы правы. Letsencrypt требует, чтобы вы подтвердили право собственности на домен перед выдачей сертификата. Он делает это, сначала ища действительный ответ домена, а затем обращаясь к домену, чтобы убедиться, что сервер сидит там. Для этого вам нужно будет указать домен на IP-адрес, который вы планируете использовать, и открыть порт 80 на этом IP-адресе, чтобы он указывал на ваш прокси-контейнер.
Судя по звуку вашего поста, вы планируете использовать это для внутренних целей. Обратите внимание, что настройки внутреннего DNS для указания на ваш компьютер будет недостаточно. Должен быть действующий общедоступный IP-адрес с соответствующим DNS, указывающим на ваш контейнер. Точно так же сертификат будет действителен ТОЛЬКО для этого внешнего адреса и не будет работать внутри (если вы не используете ту же схему именования).
Например:
Внешний публичный IP-адрес: 1.1.1.x
Внутренний публичный IP-адрес: 10.0.10.x
Публичный DNS: public.com
Внутренний DNS: internal.com
Ваш контейнер находится на 10.0.10.y и запрашивает сертификат для container.internal.com. Letsencrypt не знает, где находится ваш контейнер, потому что он использует внутреннюю схему DNS. Если вы запросите container.public.com, letsencrypt сможет увидеть, что вы указали container.public.com на свой внешний IP-адрес (1.1.1.x), и подключится к этому IP-адресу (порт 80 [переадресован на брандмауэре]) чтобы убедиться, что контейнер действительно находится там.
@ s4b3rt0oth У меня та же проблема, что и у @ jmford775, но у меня подключение извне. Мои порты 80 и 443 открыты и указывают на сервер NPM, но все еще показывает внутреннюю ошибку. То же самое произошло со мной, когда при попытке добавить сертификат SSL он показывает «Внутреннюю ошибку» и показывает, что срок действия сертификата истек в ту же дату и время, когда я пытался добавить.
Тоже самое. Запуск сборки github-develop.
отправлено из моего Айфона
5 мая 2020 года в 14:38 AnonJervis [email protected] написал:
Взаимодействие с другими людьми
@ s4b3rt0oth У меня та же проблема, что и у @ jmford775, но у меня подключение извне. Мои порты 80 и 443 открыты и указывают на сервер NPM, но все еще показывает внутреннюю ошибку. То же самое произошло со мной, когда при попытке добавить сертификат SSL он показывает «Внутреннюю ошибку» и показывает, что срок действия сертификата истек в ту же дату и время, когда я пытался добавить.—
Вы получаете это, потому что подписаны на эту ветку.
Ответьте на это письмо напрямую, просмотрите его на GitHub или откажитесь от подписки.
@ s4b3rt0oth Да, я понял, что в нашей корпоративной сети не получится, и спасибо за ответ. Я решил, что, поскольку мы уже находимся за сверхстрогими брандмауэрами, я бы просто запустил реестр без авторизации и joxit ui
То же самое и здесь. Использование надстройки Nginx Proxy Manager для Home Assistant
Была ли эта страница полезной?
0 / 5 — 0 рейтинги
It’s not the full, but it contains the proof that it failed to access the file needed todo the verification.
2021-12-02 15:54:39,525:DEBUG:urllib3.connectionpool:https://acme-v02.api.letsencrypt.org:443 "POST /acme/authz-v3/<**masked**> HTTP/1.1" 200 1353
2021-12-02 15:54:39,526:DEBUG:acme.client:Received response:
HTTP 200
Server: nginx
Date: Thu, 02 Dec 2021 15:54:39 GMT
Content-Type: application/json
Content-Length: 1353
Connection: keep-alive
Boulder-Requester: 122098528
Cache-Control: public, max-age=0, no-cache
Link: <https://acme-v02.api.letsencrypt.org/directory>;rel="index"
Replay-Nonce: 0101KB-iImdk_v4_E8qeaJBpzYY_-RvkALfB9wFV7ilE8Gc
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
{
"identifier": {
"type": "dns",
"value": "<**masked**>"
},
"status": "invalid",
"expires": "2021-12-09T15:54:37Z",
"challenges": [
{
"type": "http-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:connection",
"detail": "Fetching https://<**masked**>/.well-known/acme-challenge/lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY: Error getting validation data",
"status": 400
},
"url": "https://acme-v02.api.letsencrypt.org/acme/chall-v3/<**masked**>/<**masked**>",
"token": "lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY",
"validationRecord": [
{
"url": "http://<**masked**>/.well-known/acme-challenge/lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY",
"hostname": "<**masked**>",
"port": "80",
"addressesResolved": [
"<**masked**>"
],
"addressUsed": "<**masked**>"
},
{
"url": "https://<**masked**>/.well-known/acme-challenge/lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY",
"hostname": "<**masked**>",
"port": "443",
"addressesResolved": [
"<**masked**>"
],
"addressUsed": "<**masked**>"
}
],
"validated": "2021-12-02T15:54:38Z"
}
]
}
2021-12-02 15:54:39,526:DEBUG:acme.client:Storing nonce: <**masked**>
2021-12-02 15:54:39,526:INFO:certbot._internal.auth_handler:Challenge failed for domain <**masked**>
2021-12-02 15:54:39,526:INFO:certbot._internal.auth_handler:http-01 challenge for <**masked**>
2021-12-02 15:54:39,526:DEBUG:certbot._internal.display.obj:Notifying user:
Certbot failed to authenticate some domains (authenticator: webroot). The Certificate Authority reported these problems:
Domain: <**masked**>
Type: connection
Detail: Fetching https://<**masked**>/.well-known/acme-challenge/lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY: Error getting validation data
Hint: The Certificate Authority failed to download the temporary challenge files created by Certbot. Ensure that the listed domains serve their content from the provided --webroot-path/-w and that files created there can be downloaded from the internet.
2021-12-02 15:54:39,527:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/auth_handler.py", line 90, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/auth_handler.py", line 178, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2021-12-02 15:54:39,527:DEBUG:certbot._internal.error_handler:Calling registered functions
2021-12-02 15:54:39,527:INFO:certbot._internal.auth_handler:Cleaning up challenges
2021-12-02 15:54:39,527:DEBUG:certbot._internal.plugins.webroot:Removing /data/letsencrypt-acme-challenge/.well-known/acme-challenge/lKn4ocQjD6nyrS2_SZbE-Gw32s6uedE-jAo4mTYAcdY
2021-12-02 15:54:39,527:DEBUG:certbot._internal.plugins.webroot:All challenges cleaned up
2021-12-02 15:54:39,528:ERROR:certbot._internal.renewal:Failed to renew certificate npm-3 with error: Some challenges have failed.
2021-12-02 15:54:39,529:DEBUG:certbot._internal.renewal:Traceback was:
Traceback (most recent call last):
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/renewal.py", line 475, in handle_renewal_request
main.renew_cert(lineage_config, plugins, renewal_candidate)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/main.py", line 1386, in renew_cert
renewed_lineage = _get_and_save_cert(le_client, config, lineage=lineage)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/main.py", line 122, in _get_and_save_cert
renewal.renew_cert(config, domains, le_client, lineage)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/renewal.py", line 335, in renew_cert
new_cert, new_chain, new_key, _ = le_client.obtain_certificate(domains, new_key)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/client.py", line 389, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/client.py", line 439, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, self.config, best_effort)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/auth_handler.py", line 90, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/auth_handler.py", line 178, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
certbot.errors.AuthorizationError: Some challenges have failed.
2021-12-02 15:54:39,529:DEBUG:certbot._internal.display.obj:Notifying user:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2021-12-02 15:54:39,529:ERROR:certbot._internal.renewal:All renewals failed. The following certificates could not be renewed:
2021-12-02 15:54:39,529:ERROR:certbot._internal.renewal: /etc/letsencrypt/live/npm-3/fullchain.pem (failure)
2021-12-02 15:54:39,529:DEBUG:certbot._internal.display.obj:Notifying user: - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2021-12-02 15:54:39,529:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/opt/certbot/bin/certbot", line 8, in <module>
sys.exit(main())
File "/opt/certbot/lib/python3.7/site-packages/certbot/main.py", line 15, in main
return internal_main.main(cli_args)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/main.py", line 1574, in main
return config.func(config, plugins)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/main.py", line 1460, in renew
renewal.handle_renewal_request(config)
File "/opt/certbot/lib/python3.7/site-packages/certbot/_internal/renewal.py", line 501, in handle_renewal_request
len(renew_failures), len(parse_failures)))
certbot.errors.Error: 1 renew failure(s), 0 parse failure(s)
2021-12-02 15:54:39,530:ERROR:certbot._internal.log:1 renew failure(s), 0 parse failure(s)
Recommend Projects
-
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.