Starting today (or within the last few days) I’ve hit an SSL error when trying to connect to github.com (e.g. to clone a repository).
This is a legacy server running Red Hat 4.1.2-33.
Here’s what it looks like when I try to connect:
$ curl https://www.github.com --verbose
* About to connect() to www.github.com port 443 (#0)
* Trying 192.30.252.130... connected
* Connected to www.github.com (192.30.252.130) port 443 (#0)
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* NSS error -12286
* Closing connection #0
* SSL connect error
curl: (35) SSL connect error
I can see from this page that the NSS error code is:
«Cannot communicate securely with peer: no common encryption
algorithm(s).»The local and remote systems share no cipher suites in common. This
can be due to a misconfiguration at either end. It can be due to a
server being misconfigured to use a non-RSA certificate with the RSA
key exchange algorithm.
If I’m putting this altogether right, it appears that github.com has a recently updated SSL certificate and my server doesn’t have a cipher suite compatible with it. This is a legacy server so I’m not that surprised.
I’ve tried yum update nss (since that what curl seems to be using) as well as yum update openssl but none of those packages have updated.
I’ve also tried following the procedure outline here but to no avail.
I’m sort of hitting a wall with my knowledge of how TLS handshakes work to even troubleshoot this much deeper. Does anyone have any good ideas on how to start digging deeper and figuring out what’s going wrong and where I need to update things? Upgrading the OS is for the time being not an option.
Update
Digging further, it appears to be an issue with libcurl and the cipher it is using when connecting to github.com via git. I can get curl to work if I specify a compatible cipher explicitly:
$ curl https://github.com --cipher rsa_aes_128_sha
And I can even add the --cipher rsa_aes_128_sha parameter to a .curlrc file and have curl use that cipher by default. Unfortunately, this doesn’t seem to get picked up by the git command so it got me nowhere…nor could I find an alternate way to specify the cipher. This is what the result of a verbose git pull looks like on a github.com repository:
$ GIT_CURL_VERBOSE=1 git pull
* Couldn't find host github.com in the .netrc file, using defaults
* About to connect() to github.com port 443 (#0)
* Trying 192.30.252.129... * Connected to github.com (192.30.252.129) port 443 (#0)
* CAfile: /root/certs/cacert.pem
CApath: none
* NSS error -12286
* Expire cleared
* Closing connection #0
* Couldn't find host github.com in the .netrc file, using defaults
* About to connect() to github.com port 443 (#0)
* Trying 192.30.252.129... * Connected to github.com (192.30.252.129) port 443 (#0)
* CAfile: /root/certs/cacert.pem
CApath: none
* NSS error -12286
* Expire cleared
* Closing connection #0
error: SSL connect error while accessing https://github.com/twbs/bootstrap.git/info/refs
fatal: HTTP request failed
This might be a dead-end…looks like this guy on StackOverflow ran into the exact same issue.
Curl — View SSL certificate using CURL on Linux
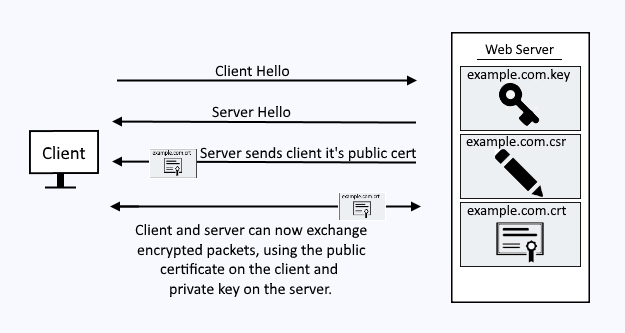
When a server is configured to use SSL/TLS so that packets exchanged between the client and server are encrypted, the client will need to obtain the certificate from the server. For example, the following diagram illustrates how a client would obtain the certificate from an HTTPS web server.
The CURL command can be used to identify the certificate that the server presents to the client.
curl --verbose https://www.example.comIf a certificate is being presented, basic information about the certificate should be displayed.
* Server certificate:
* subject: CN=example.com,OU=foo,O=bar
* start date: Jan 01 2019
* expire date: Jan 01 2021
* common name: example.com
* issuer: CN=VeriSign Certification AuthorityNSS error -12286
If you get NSS error 12286 when attempting to connect to a site, try updating curl and nss.
yum update curl
yum update nssTarget URL
You only need to use the hostname of the web server, such as www.example.com or www.google.com or www.freekb.net. In other words, there is no need to use a sub directory, such as www.example.com/foo/bar, since the certificate would be provided by just www.example.com.
curl --verbose https://www.example.comgrep the output
Curl writes output to stderr, not stdout, you’ll need to use 2>&1 if you want to pipe the output to grep.
curl --verbose https://www.example.com 2>&1 | grep expire
* expire date: Jan 01 2021define timeout to prevent hangs
Issues can cause cURL to hang sometimes. To prevent cURL from hanging for to long, you can use the -m or —max-time option followed by the number of seconds that cURL should hold tight before closing the connection to the remove server. In this second, cURL will timeout after 10 seconds.
curl --max-time 10 https://www.example.com—insecure (certificate authority not recognized)
If the -k or —insecure option are not used, cURL will only get certificates that have been issued by a trusted certificate authority (CA). If you want to get certificates from both a trusted and untrusted certificate authority, use the -k or —insecure option.
curl --verbose --insecure https://www.example.comCertificate chain
Let’s say there is a certificate chain, like this. cURL will only get the server certificate. If you need to determine each certificate used in the certificate chain, you are much better off using openSSL.
- example.com (root certificate)
-- example.com (intermediate certificate)
--- *.example.com (server certificate)
Did you find this article helpful?
If so, consider buying me a coffee over at
-
AlexDark
- Posts: 2
- Joined: 2015/05/27 22:06:07
Error performing cURL to HTTPS (Handshake error)
Hi all,
I’m having an issue when doing cURL to HTTPS url. Below the error:
Code: Select all
curl -v https://repo.thinkofdeath.co.uk/content/groups/public/
* About to connect() to repo.thinkofdeath.co.uk port 443 (#0)
* Trying 104.28.17.59...
* Connected to repo.thinkofdeath.co.uk (104.28.17.59) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* NSS error -12286 (SSL_ERROR_NO_CYPHER_OVERLAP)
* Cannot communicate securely with peer: no common encryption algorithm(s).
* Error in TLS handshake, trying SSLv3...
> GET /content/groups/public/ HTTP/1.1
> User-Agent: curl/7.29.0
> Host: repo.thinkofdeath.co.uk
> Accept: */*
>
* Connection died, retrying a fresh connect
* Closing connection 0
* Issue another request to this URL: 'https://repo.thinkofdeath.co.uk/content/groups/public/'
* About to connect() to repo.thinkofdeath.co.uk port 443 (#1)
* Trying 104.28.17.59...
* Connected to repo.thinkofdeath.co.uk (104.28.17.59) port 443 (#1)
* TLS disabled due to previous handshake failure
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* NSS error -12286 (SSL_ERROR_NO_CYPHER_OVERLAP)
* Cannot communicate securely with peer: no common encryption algorithm(s).
* Closing connection 1
curl: (35) Cannot communicate securely with peer: no common encryption algorithm(s).I’m running CentOS Linux release 7.1.1503 (Core) and my libcurl and curl versions are:
libcurl-7.29.0-19.el7.x86_64
curl-7.29.0-19.el7.x86_64
It looks like it’s trying to perform SSLv3 connection, but since almost all servers have this protocol disabled because of the known poodle vulnerability, it fails..
I need this to work for a Java application which checks for data over HTTPS using the same method.
Any solution to get this forced to use TLS or maybe i’m totally wrong and it’s completely related to some other setting?
-
avij
- Retired Moderator
- Posts: 3046
- Joined: 2010/12/01 19:25:52
- Location: Helsinki, Finland
-
Contact:
Re: Error performing cURL to HTTPS (Handshare error)
Post
by avij » 2015/05/27 23:20:14
You can force curl to use TLS v1.2 with the —tlsv1.2 option, but looks like that does not help. The problem is probably related to the web server only supporting cipher suites TLS_ECDHE_ECDSA_WITH_something, and looks like curl does not support those ciphers. I don’t immediately know of a workaround for this problem, sorry. Perhaps others are smarter.
The Qualys SSL Labs test is usually quite informative when diagnosing HTTPS problems.
— edit #1:
Oh, this seems to work:
curl —ciphers ecdhe_ecdsa_aes_256_sha https://repo.thinkofdeath.co.uk/content/groups/public/
— edit #2:
https://bugzilla.redhat.com/show_bug.cgi?id=1185708 and the linked bugs are related to this problem.
Я получаю сообщение об ошибке NSS -12286 при попытке загрузить страницу https с использованием сертификата ca, используя код cacertinpem.c curl c. я использую файл cacert.pem в коде alog с путем. но то же самое работает, когда я пытаюсь использовать curl -v «https://sampleserve.com:443», в этом случае ssl использует путь CA по умолчанию как «/etc/tls/certs/ca.budle.crt»
Но этот код c не работает как для расположения ca по умолчанию, так и для выбора внешнего пути ca.
В чем причина этой ошибки (NSS -12286).
Error:
* About to connect() to fiservices.sterlingbankng.com port 443 (#0)
* Trying 1.1.1.1... * Connection timed out
* Trying 1.1.1.2... * connected
* Connected to fiservices.sterlingbankng.com (1.1.1.2) port 443 (#0)
* Initializing NSS with certpath: /etc/pki/nssdb
* CAfile: ./cacert.pem CApath: ./cacert.pem
* NSS error -12286
* Error in TLS handshake, trying SSLv3...
GET /CanFI/ HTTP/1.1
Host: sampleserver.com
Accept: */*
* Connection died, retrying a fresh connect
* Closing connection #0
* Issue another request to this URL: 'https://sampleserver.com'
* About to connect() to sampleserver.com port 443 (#0)
* Trying 1.1.1.1... * Connection timed out
* Trying 1.1.1.2... * connected
* Connected to sampleserver.com (1.1.1.2) port 443 (#0)
* TLS disabled due to previous handshake failure
* CAfile: ./cacert.pem
CApath: ./cacert.pem
* NSS error -12286
* Closing connection #0
* SSL connect error
Образец кода:
size_t writefunction( void *ptr, size_t size, size_t nmemb, void *stream)
{
fwrite(ptr,size,nmemb,stream);
return(nmemb*size);
}
static CURLcode sslctx_function(CURL * curl, void * sslctx, void * parm)
{
X509_STORE * store;
X509 * cert=NULL;
BIO * bio;
char * mypem = "-----BEGIN CERTIFICATE-----n" "-----END CERTIFICATE-----n"; //public certificate
}
int main(void)
{
CURL * ch;
CURLcode rv;
rv=curl_global_init(CURL_GLOBAL_ALL);
ch=curl_easy_init();
rv=curl_easy_setopt(ch,CURLOPT_VERBOSE, 1L);
rv=curl_easy_setopt(ch,CURLOPT_HEADER, 0L);
rv=curl_easy_setopt(ch,CURLOPT_NOPROGRESS, 1L);
rv=curl_easy_setopt(ch,CURLOPT_NOSIGNAL, 1L);
rv=curl_easy_setopt(ch,CURLOPT_WRITEFUNCTION, *writefunction);
rv=curl_easy_setopt(ch,CURLOPT_WRITEDATA, stdout);
rv=curl_easy_setopt(ch,CURLOPT_HEADERFUNCTION, *writefunction);
rv=curl_easy_setopt(ch,CURLOPT_WRITEHEADER, stderr);
rv=curl_easy_setopt(ch,CURLOPT_SSLCERTTYPE,"PEM");
rv=curl_easy_setopt (ch, CURLOPT_CAPATH, "./cacert.pem" );
rv=curl_easy_setopt (ch, CURLOPT_CAINFO, "./cacert.pem" );
rv=curl_easy_setopt(ch,CURLOPT_SSL_VERIFYPEER,1L);
rv=curl_easy_setopt(ch, CURLOPT_URL, "https://");
rv=curl_easy_perform(ch);
if (rv==CURLE_OK)
printf("*** transfer succeeded ***n");
else
printf("*** transfer failed ***n");
rv=curl_easy_setopt(ch,CURLOPT_SSL_CTX_FUNCTION, *sslctx_function);
rv=curl_easy_perform(ch);
if (rv==CURLE_OK)
printf("*** transfer succeeded ***n");
else
printf("*** transfer failed ***n");
curl_easy_cleanup(ch);
curl_global_cleanup();
return rv;
}
Спасибо
Hello
I am stumped. I am trying to us the kraxel qemu repository, it appears the repository moved to secure server since then I have not been able to configure this properly. https://www.kraxel.org/repos/jenkins/
I receive the following error when I try to use the repository curl: (35) Cannot communicate securely with peer: no common encryption algorithm(s).
I have discovered this problem on my fedora 20 computer, the fedora mailing list will not accept my email, I am experiencing this problem with curl on both my CentOS and fedora systems.
I receive the same error with CentOS 7 minimal installation and fedora
20. What am I doing wrong, I have recently switch to the Fedora platform, I have not read all the manuals but trying.
I have imported the gpg keys that Kraxel has posted on his blog using rpm –import. I can only download file through my web browser. I was going to clone his git repository and set up a local repository, bit git report the same error. Which leads me to believe the problem is with my certificates.
I have even tried the firefox-db2pem.sh, I am not sure it did anything.
Does curl need to be recompiled with nss support? Is there a package I
need to compile? nss 3.17.2 is installed, non of the man page work.
Looking deeper into the nss,
# certutil -L
certutil: function failed: SEC_ERROR_LEGACY_DATABASE: The certificate/key database is in an old, unsupported format.
I think there is something wrong with my nss certificates, but I have run out of time. Any suggestions.
This is on a brand new installation Fedora 20 and CentOS 7, I have not had time to break anything.
The openssl command connect with the server, is
$ openssl s_client -connect www.kraxel.org:443
The curl output is posted below in fedora system the output for the CentOS is the same with the exception of the curl and nss versions:
$ curl -v https://www.kraxel.org/repos/jenkins/repodata/repomd.xml
* Adding handle: conn: 0x6bea60
* Adding handle: send: 0
* Adding handle: recv: 0
* Curl_addHandleToPipeline: length: 1
* – Conn 0 (0x6bea60) send_pipe: 1, recv_pipe: 0
* About to connect() to www.kraxel.org port 443 (#0)
* Trying 217.197.83.6…
* Connected to www.kraxel.org (217.197.83.6) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* NSS error -12286 (SSL_ERROR_NO_CYPHER_OVERLAP)
* Cannot communicate securely with peer: no common encryption algorithm(s).
* Error in TLS handshake, trying SSLv3…
* Connection died, retrying a fresh connect
* Closing connection 0
* Issue another request to this URL:
‘https://www.kraxel.org/repos/jenkins/repodata/repomd.xml’
* About to connect() to www.kraxel.org port 443 (#1)
* Trying 217.197.83.6…
* Adding handle: conn: 0x6bea60
* Adding handle: send: 0
* Adding handle: recv: 0
* Curl_addHandleToPipeline: length: 1
* – Conn 1 (0x6bea60) send_pipe: 1, recv_pipe: 0
* Connected to www.kraxel.org (217.197.83.6) port 443 (#1)
* TLS disabled due to previous handshake failure
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* NSS error -12286 (SSL_ERROR_NO_CYPHER_OVERLAP)
* Cannot communicate securely with peer: no common encryption algorithm(s).
* Closing connection 1
curl: (35) Cannot communicate securely with peer: no common encryption algorithm(s).