-
phikev
- OpenVpn Newbie
- Posts: 3
- Joined: Sun Nov 29, 2020 7:28 pm
Failed to Parse .OVPN File, TAP Mode Not Supported
Hello,
I just installed OpenVPN Client version 3.2.2 (1455) and am trying to import a .OVPN file created by my routers VPN setup instructions (NETGEAR R6400). When I attempt to import the file I get the following error, «Failed to import file Failed to parse profile: option_error, proto_option_error. TAP mode is not supported.» I read another post that sounded similar, the fix on that was that the version of OpenVPN was not the most current. I double checked that I have the most up to date from the website. Any ideas?
Thanks!
-
TinCanTech
- OpenVPN Protagonist
- Posts: 11142
- Joined: Fri Jun 03, 2016 1:17 pm
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by TinCanTech » Sun Nov 29, 2020 7:44 pm
phikev wrote: ↑
Sun Nov 29, 2020 7:33 pm
«Failed to import file Failed to parse profile: option_error, proto_option_error. TAP mode is not supported.»
-
phikev
- OpenVpn Newbie
- Posts: 3
- Joined: Sun Nov 29, 2020 7:28 pm
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by phikev » Mon Nov 30, 2020 6:59 pm
I’m guessing based on TinCanTech’s eyeroll that I’m missing something obvious…mind letting me know what that is?
-
Pippin
- Forum Team
- Posts: 1189
- Joined: Wed Jul 01, 2015 8:03 am
- Location: irc://irc.libera.chat:6697/openvpn
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by Pippin » Mon Nov 30, 2020 7:10 pm
The error message says «TAP mode is not supported» …
Android, iPhone…?
If Windows, download:
https://openvpn.net/community-downloads
I gloomily came to the ironic conclusion that if you take a highly intelligent person and give them the best possible, elite education, then you will most likely wind up with an academic who is completely impervious to reality.
Halton Arp
-
phikev
- OpenVpn Newbie
- Posts: 3
- Joined: Sun Nov 29, 2020 7:28 pm
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by phikev » Wed Dec 02, 2020 3:57 pm
Yep, easy fix. I appreciate the time, thank you!
-
kwende
- OpenVpn Newbie
- Posts: 1
- Joined: Tue Jul 13, 2021 3:18 am
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by kwende » Tue Jul 13, 2021 3:21 am
I’m sorry. I’m sure TinCanTech has been helpful to many people, but if you can take the time to respond with an eyeroll, you can take the time to respond with something a _bit_ more useful. The time it takes to make a snarky rolling-eye emoticon it can take to https://en.wikipedia.org/wiki/TUN/TAP. C’mon. With all due respect, I think one can do better.
-
TinCanTech
- OpenVPN Protagonist
- Posts: 11142
- Joined: Fri Jun 03, 2016 1:17 pm
Re: Failed to Parse .OVPN File, TAP Mode Not Supported
Post
by TinCanTech » Tue Jul 13, 2021 3:57 am
@ kwende — If people refuse to read the error which they are presented with then they cannot be helped
an eye-roll is exactly what they deserve.
And you should not be so quick to judge … lest you be judged also ..
Looks like you’re using OpenVPN Connect on Windows and I assume it’s version 3.In that version TAP is no longer supported. You should use TUN mode.
I believe OpenVPN Community Edition 2.5 (https://openvpn.net/community-downloads/ Opens a new window) still supports TAP.
Better option is to just turn off TAP altogether if you can in the Netgear. The screenshot above does not seem to suggest a way to only configure TUN. Perhaps in Advanced settings you can do such a thing?
You can look at modifying the generated openvpn configuration file and see about removing the TAP portions. The ovpn file is usually just a text file you can edit in Notepad.
Was this post helpful?
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
Looks like you’re using OpenVPN Connect on Windows and I assume it’s version 3.In that version TAP is no longer supported. You should use TUN mode.
I believe OpenVPN Community Edition 2.5 (https://openvpn.net/community-downloads/ Opens a new window) still supports TAP.
Better option is to just turn off TAP altogether if you can in the Netgear. The screenshot above does not seem to suggest a way to only configure TUN. Perhaps in Advanced settings you can do such a thing?
You can look at modifying the generated openvpn configuration file and see about removing the TAP portions. The ovpn file is usually just a text file you can edit in Notepad.
It looks like the TAP can not be disabled through the interface. I will attempt to download version 2.5 to see if I can get this to work. If that doesn’t work, what steps would need to be taken to remove the openvpn configuration files?
Was this post helpful?
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
Here is the error I am receiving when using version 2.5:
2021-02-23 09:35:59 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless «allow-compression yes» is also set.
2021-02-23 09:35:59 us=883743 DEPRECATED OPTION: —cipher set to ‘AES-128-CBC’ but missing in —data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore —cipher for cipher negotiations. Add ‘AES-128-CBC’ to —data-ciphers or change —cipher ‘AES-128-CBC’ to —data-ciphers-fallback ‘AES-128-CBC’ to silence this warning.
Options error: —ca fails with ‘ca.crt’: No such file or directory (errno=2)
Options error: —cert fails with ‘client.crt’: No such file or directory (errno=2)
2021-02-23 09:35:59 us=884706 WARNING: cannot stat file ‘client.key’: No such file or directory (errno=2)
Options error: —key fails with ‘client.key’: No such file or directory (errno=2)
Options error: Please correct these errors.
Use —help for more information.
Was this post helpful?
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
Additionally,
The config files are in the directory of:
C:Program filesOpenVPNconfig
Was this post helpful?
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
Which in turns gives this result:
Was this post helpful?
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
The client.opvn extension file:
client
dev tap
proto udp
dev-node NETGEAR-VPN
remote x.x.x.x (MY IP) 12974
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
cipher AES-128-CBC
comp-lzo
verb 5
Was this post helpful?
thumb_up
thumb_down
Try just changing «tap» to «tun» and update the port number in the «remote» line from 12974 to the TUN port shown in your Netgear config.
The other errors about missing files are curious because you are showing those files exist in the same folder. Or did you move the files into there after you showed the error log? The last screenshot tells you to check the client.log file — what does that contain?
1 found this helpful
thumb_up
thumb_down
Have you opened the appropriate ports in the client firewall?
Also, try entering the appropriate path to the certs in the config. Examples (notice the double slashes):
ca «C:\Program Files\OpenVPN\config\ca.crt»
cert «C:\Program Files\OpenVPN\config\MRdesktop.crt»
key «C:\Program Files\OpenVPN\config\MRdesktop.key»
1 found this helpful
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
GerardBeekmans wrote:
Try just changing «tap» to «tun» and update the port number in the «remote» line from 12974 to the TUN port shown in your Netgear config.
The other errors about missing files are curious because you are showing those files exist in the same folder. Or did you move the files into there after you showed the error log? The last screenshot tells you to check the client.log file — what does that contain?
Okay I replaced tap with tun and changed the port to 12973 and I am getting a bit further but am running into a TLS handshake issue.
2021-02-23 11:15:58 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless «allow-compression yes» is also set.
2021-02-23 11:15:58 us=108749 DEPRECATED OPTION: —cipher set to ‘AES-128-CBC’ but missing in —data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore —cipher for cipher negotiations. Add ‘AES-128-CBC’ to —data-ciphers or change —cipher ‘AES-128-CBC’ to —data-ciphers-fallback ‘AES-128-CBC’ to silence this warning.
2021-02-23 11:15:58 us=109744 Current Parameter Settings:
2021-02-23 11:15:58 us=109744 config = ‘client.ovpn’
2021-02-23 11:15:58 us=109744 mode = 0
2021-02-23 11:15:58 us=109744 show_ciphers = DISABLED
2021-02-23 11:15:58 us=109744 show_digests = DISABLED
2021-02-23 11:15:58 us=109744 show_engines = DISABLED
2021-02-23 11:15:58 us=109744 genkey = DISABLED
2021-02-23 11:15:58 us=109744 genkey_filename = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 key_pass_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 show_tls_ciphers = DISABLED
2021-02-23 11:15:58 us=109744 connect_retry_max = 0
2021-02-23 11:15:58 us=109744 Connection profiles [0]:
2021-02-23 11:15:58 us=109744 proto = udp
2021-02-23 11:15:58 us=109744 local = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 local_port = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 remote = ‘MYIP’
2021-02-23 11:15:58 us=109744 remote_port = ‘12973’
2021-02-23 11:15:58 us=109744 remote_float = DISABLED
2021-02-23 11:15:58 us=109744 bind_defined = DISABLED
2021-02-23 11:15:58 us=109744 bind_local = DISABLED
2021-02-23 11:15:58 us=109744 bind_ipv6_only = DISABLED
2021-02-23 11:15:58 us=109744 connect_retry_seconds = 5
2021-02-23 11:15:58 us=109744 connect_timeout = 120
2021-02-23 11:15:58 us=109744 socks_proxy_server = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 socks_proxy_port = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 tun_mtu = 1500
2021-02-23 11:15:58 us=109744 tun_mtu_defined = ENABLED
2021-02-23 11:15:58 us=109744 link_mtu = 1500
2021-02-23 11:15:58 us=109744 link_mtu_defined = DISABLED
2021-02-23 11:15:58 us=109744 tun_mtu_extra = 0
2021-02-23 11:15:58 us=109744 tun_mtu_extra_defined = DISABLED
2021-02-23 11:15:58 us=109744 mtu_discover_type = -1
2021-02-23 11:15:58 us=109744 fragment = 0
2021-02-23 11:15:58 us=109744 mssfix = 1450
2021-02-23 11:15:58 us=109744 explicit_exit_notification = 0
2021-02-23 11:15:58 us=109744 tls_auth_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 key_direction = not set
2021-02-23 11:15:58 us=109744 tls_crypt_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 tls_crypt_v2_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 Connection profiles END
2021-02-23 11:15:58 us=109744 remote_random = DISABLED
2021-02-23 11:15:58 us=109744 ipchange = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 dev = ‘tun’
2021-02-23 11:15:58 us=109744 dev_type = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 dev_node = ‘NETGEAR-VPN’
2021-02-23 11:15:58 us=109744 lladdr = ‘[UNDEF]’
2021-02-23 11:15:58 us=109744 topology = 1
2021-02-23 11:15:58 us=109744 ifconfig_local = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 ifconfig_remote_netmask = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 ifconfig_noexec = DISABLED
2021-02-23 11:15:58 us=110741 ifconfig_nowarn = DISABLED
2021-02-23 11:15:58 us=110741 ifconfig_ipv6_local = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 ifconfig_ipv6_netbits = 0
2021-02-23 11:15:58 us=110741 ifconfig_ipv6_remote = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 shaper = 0
2021-02-23 11:15:58 us=110741 mtu_test = 0
2021-02-23 11:15:58 us=110741 mlock = DISABLED
2021-02-23 11:15:58 us=110741 keepalive_ping = 0
2021-02-23 11:15:58 us=110741 keepalive_timeout = 0
2021-02-23 11:15:58 us=110741 inactivity_timeout = 0
2021-02-23 11:15:58 us=110741 ping_send_timeout = 0
2021-02-23 11:15:58 us=110741 ping_rec_timeout = 0
2021-02-23 11:15:58 us=110741 ping_rec_timeout_action = 0
2021-02-23 11:15:58 us=110741 ping_timer_remote = DISABLED
2021-02-23 11:15:58 us=110741 remap_sigusr1 = 0
2021-02-23 11:15:58 us=110741 persist_tun = ENABLED
2021-02-23 11:15:58 us=110741 persist_local_ip = DISABLED
2021-02-23 11:15:58 us=110741 persist_remote_ip = DISABLED
2021-02-23 11:15:58 us=110741 persist_key = ENABLED
2021-02-23 11:15:58 us=110741 passtos = DISABLED
2021-02-23 11:15:58 us=110741 resolve_retry_seconds = 1000000000
2021-02-23 11:15:58 us=110741 resolve_in_advance = DISABLED
2021-02-23 11:15:58 us=110741 username = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 groupname = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 chroot_dir = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 cd_dir = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 writepid = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 up_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 down_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 down_pre = DISABLED
2021-02-23 11:15:58 us=110741 up_restart = DISABLED
2021-02-23 11:15:58 us=110741 up_delay = DISABLED
2021-02-23 11:15:58 us=110741 daemon = DISABLED
2021-02-23 11:15:58 us=110741 inetd = 0
2021-02-23 11:15:58 us=110741 log = ENABLED
2021-02-23 11:15:58 us=110741 suppress_timestamps = DISABLED
2021-02-23 11:15:58 us=110741 machine_readable_output = DISABLED
2021-02-23 11:15:58 us=110741 nice = 0
2021-02-23 11:15:58 us=110741 verbosity = 5
2021-02-23 11:15:58 us=110741 mute = 0
2021-02-23 11:15:58 us=110741 gremlin = 0
2021-02-23 11:15:58 us=110741 status_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 status_file_version = 1
2021-02-23 11:15:58 us=110741 status_file_update_freq = 60
2021-02-23 11:15:58 us=110741 occ = ENABLED
2021-02-23 11:15:58 us=110741 rcvbuf = 0
2021-02-23 11:15:58 us=110741 sndbuf = 0
2021-02-23 11:15:58 us=110741 sockflags = 0
2021-02-23 11:15:58 us=110741 fast_io = DISABLED
2021-02-23 11:15:58 us=110741 comp.alg = 2
2021-02-23 11:15:58 us=110741 comp.flags = 1
2021-02-23 11:15:58 us=110741 route_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 route_default_gateway = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 route_default_metric = 0
2021-02-23 11:15:58 us=110741 route_noexec = DISABLED
2021-02-23 11:15:58 us=110741 route_delay = 5
2021-02-23 11:15:58 us=110741 route_delay_window = 30
2021-02-23 11:15:58 us=110741 route_delay_defined = ENABLED
2021-02-23 11:15:58 us=110741 route_nopull = DISABLED
2021-02-23 11:15:58 us=110741 route_gateway_via_dhcp = DISABLED
2021-02-23 11:15:58 us=110741 allow_pull_fqdn = DISABLED
2021-02-23 11:15:58 us=110741 Pull filters:
2021-02-23 11:15:58 us=110741 ignore «route-method»
2021-02-23 11:15:58 us=110741 management_addr = ‘127.0.0.1’
2021-02-23 11:15:58 us=110741 management_port = ‘25340’
2021-02-23 11:15:58 us=110741 management_user_pass = ‘stdin’
2021-02-23 11:15:58 us=110741 management_log_history_cache = 250
2021-02-23 11:15:58 us=110741 management_echo_buffer_size = 100
2021-02-23 11:15:58 us=110741 management_write_peer_info_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 management_client_user = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 management_client_group = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 management_flags = 6
2021-02-23 11:15:58 us=110741 shared_secret_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 key_direction = not set
2021-02-23 11:15:58 us=110741 ciphername = ‘AES-128-CBC’
2021-02-23 11:15:58 us=110741 ncp_enabled = ENABLED
2021-02-23 11:15:58 us=110741 ncp_ciphers = ‘AES-256-GCM:AES-128-GCM:AES-128-CBC’
2021-02-23 11:15:58 us=110741 authname = ‘SHA1’
2021-02-23 11:15:58 us=110741 prng_hash = ‘SHA1’
2021-02-23 11:15:58 us=110741 prng_nonce_secret_len = 16
2021-02-23 11:15:58 us=110741 keysize = 0
2021-02-23 11:15:58 us=110741 engine = DISABLED
2021-02-23 11:15:58 us=110741 replay = ENABLED
2021-02-23 11:15:58 us=110741 mute_replay_warnings = DISABLED
2021-02-23 11:15:58 us=110741 replay_window = 64
2021-02-23 11:15:58 us=110741 replay_time = 15
2021-02-23 11:15:58 us=110741 packet_id_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 test_crypto = DISABLED
2021-02-23 11:15:58 us=110741 tls_server = DISABLED
2021-02-23 11:15:58 us=110741 tls_client = ENABLED
2021-02-23 11:15:58 us=110741 ca_file = ‘ca.crt’
2021-02-23 11:15:58 us=110741 ca_path = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 dh_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 cert_file = ‘client.crt’
2021-02-23 11:15:58 us=110741 extra_certs_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=110741 priv_key_file = ‘client.key’
2021-02-23 11:15:58 us=110741 pkcs12_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 cryptoapi_cert = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 cipher_list = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 cipher_list_tls13 = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 tls_cert_profile = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 tls_verify = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 tls_export_cert = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 verify_x509_type = 0
2021-02-23 11:15:58 us=111738 verify_x509_name = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 crl_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 ns_cert_type = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_ku[i] = 0
2021-02-23 11:15:58 us=111738 remote_cert_eku = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 ssl_flags = 0
2021-02-23 11:15:58 us=111738 tls_timeout = 2
2021-02-23 11:15:58 us=111738 renegotiate_bytes = -1
2021-02-23 11:15:58 us=111738 renegotiate_packets = 0
2021-02-23 11:15:58 us=111738 renegotiate_seconds = 3600
2021-02-23 11:15:58 us=111738 handshake_window = 60
2021-02-23 11:15:58 us=111738 transition_window = 3600
2021-02-23 11:15:58 us=111738 single_session = DISABLED
2021-02-23 11:15:58 us=111738 push_peer_info = DISABLED
2021-02-23 11:15:58 us=111738 tls_exit = DISABLED
2021-02-23 11:15:58 us=111738 tls_crypt_v2_metadata = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_protected_authentication = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_private_mode = 00000000
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_cert_private = DISABLED
2021-02-23 11:15:58 us=111738 pkcs11_pin_cache_period = -1
2021-02-23 11:15:58 us=111738 pkcs11_id = ‘[UNDEF]’
2021-02-23 11:15:58 us=111738 pkcs11_id_management = DISABLED
2021-02-23 11:15:58 us=111738 server_network = 0.0.0.0
2021-02-23 11:15:58 us=111738 server_netmask = 0.0.0.0
2021-02-23 11:15:58 us=111738 server_network_ipv6 = ::
2021-02-23 11:15:58 us=111738 server_netbits_ipv6 = 0
2021-02-23 11:15:58 us=111738 server_bridge_ip = 0.0.0.0
2021-02-23 11:15:58 us=111738 server_bridge_netmask = 0.0.0.0
2021-02-23 11:15:58 us=111738 server_bridge_pool_start = 0.0.0.0
2021-02-23 11:15:58 us=111738 server_bridge_pool_end = 0.0.0.0
2021-02-23 11:15:58 us=111738 ifconfig_pool_defined = DISABLED
2021-02-23 11:15:58 us=111738 ifconfig_pool_start = 0.0.0.0
2021-02-23 11:15:58 us=111738 ifconfig_pool_end = 0.0.0.0
2021-02-23 11:15:58 us=112736 ifconfig_pool_netmask = 0.0.0.0
2021-02-23 11:15:58 us=112736 ifconfig_pool_persist_filename = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 ifconfig_pool_persist_refresh_freq = 600
2021-02-23 11:15:58 us=112736 ifconfig_ipv6_pool_defined = DISABLED
2021-02-23 11:15:58 us=112736 ifconfig_ipv6_pool_base = ::
2021-02-23 11:15:58 us=112736 ifconfig_ipv6_pool_netbits = 0
2021-02-23 11:15:58 us=112736 n_bcast_buf = 256
2021-02-23 11:15:58 us=112736 tcp_queue_limit = 64
2021-02-23 11:15:58 us=112736 real_hash_size = 256
2021-02-23 11:15:58 us=112736 virtual_hash_size = 256
2021-02-23 11:15:58 us=112736 client_connect_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 learn_address_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 client_disconnect_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 client_config_dir = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 ccd_exclusive = DISABLED
2021-02-23 11:15:58 us=112736 tmp_dir = ‘C:UsersitAppDataLocalTemp’
2021-02-23 11:15:58 us=112736 push_ifconfig_defined = DISABLED
2021-02-23 11:15:58 us=112736 push_ifconfig_local = 0.0.0.0
2021-02-23 11:15:58 us=112736 push_ifconfig_remote_netmask = 0.0.0.0
2021-02-23 11:15:58 us=112736 push_ifconfig_ipv6_defined = DISABLED
2021-02-23 11:15:58 us=112736 push_ifconfig_ipv6_local = ::/0
2021-02-23 11:15:58 us=112736 push_ifconfig_ipv6_remote = ::
2021-02-23 11:15:58 us=112736 enable_c2c = DISABLED
2021-02-23 11:15:58 us=112736 duplicate_cn = DISABLED
2021-02-23 11:15:58 us=112736 cf_max = 0
2021-02-23 11:15:58 us=112736 cf_per = 0
2021-02-23 11:15:58 us=112736 max_clients = 1024
2021-02-23 11:15:58 us=112736 max_routes_per_client = 256
2021-02-23 11:15:58 us=112736 auth_user_pass_verify_script = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 auth_user_pass_verify_script_via_file = DISABLED
2021-02-23 11:15:58 us=112736 auth_token_generate = DISABLED
2021-02-23 11:15:58 us=112736 auth_token_lifetime = 0
2021-02-23 11:15:58 us=112736 auth_token_secret_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 vlan_tagging = DISABLED
2021-02-23 11:15:58 us=112736 vlan_accept = all
2021-02-23 11:15:58 us=112736 vlan_pvid = 1
2021-02-23 11:15:58 us=112736 client = ENABLED
2021-02-23 11:15:58 us=112736 pull = ENABLED
2021-02-23 11:15:58 us=112736 auth_user_pass_file = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 show_net_up = DISABLED
2021-02-23 11:15:58 us=112736 route_method = 3
2021-02-23 11:15:58 us=112736 block_outside_dns = DISABLED
2021-02-23 11:15:58 us=112736 ip_win32_defined = DISABLED
2021-02-23 11:15:58 us=112736 ip_win32_type = 3
2021-02-23 11:15:58 us=112736 dhcp_masq_offset = 0
2021-02-23 11:15:58 us=112736 dhcp_lease_time = 31536000
2021-02-23 11:15:58 us=112736 tap_sleep = 0
2021-02-23 11:15:58 us=112736 dhcp_options = DISABLED
2021-02-23 11:15:58 us=112736 dhcp_renew = DISABLED
2021-02-23 11:15:58 us=112736 dhcp_pre_release = DISABLED
2021-02-23 11:15:58 us=112736 domain = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 netbios_scope = ‘[UNDEF]’
2021-02-23 11:15:58 us=112736 netbios_node_type = 0
2021-02-23 11:15:58 us=112736 disable_nbt = DISABLED
2021-02-23 11:15:58 us=112736 OpenVPN 2.5.0 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 28 2020
2021-02-23 11:15:58 us=112736 Windows version 10.0 (Windows 10 or greater) 64bit
2021-02-23 11:15:58 us=112736 library versions: OpenSSL 1.1.1h 22 Sep 2020, LZO 2.10
Enter Management Password:
2021-02-23 11:15:58 us=113734 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
2021-02-23 11:15:58 us=113734 Need hold release from management interface, waiting…
2021-02-23 11:15:58 us=585474 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
2021-02-23 11:15:58 us=696210 MANAGEMENT: CMD ‘state on’
2021-02-23 11:15:58 us=696210 MANAGEMENT: CMD ‘log all on’
2021-02-23 11:15:58 us=875747 MANAGEMENT: CMD ‘echo all on’
2021-02-23 11:15:58 us=877747 MANAGEMENT: CMD ‘bytecount 5’
2021-02-23 11:15:58 us=879737 MANAGEMENT: CMD ‘hold off’
2021-02-23 11:15:58 us=881731 MANAGEMENT: CMD ‘hold release’
2021-02-23 11:15:58 us=881731 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm Opens a new window for more info.
2021-02-23 11:15:58 us=884676 LZO compression initializing
2021-02-23 11:15:58 us=884676 Control Channel MTU parms [ L:1622 D:1212 EF:38 EB:0 ET:0 EL:3 ]
2021-02-23 11:15:58 us=884676 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
2021-02-23 11:15:58 us=884676 Local Options String (VER=V4): ‘V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-client’
2021-02-23 11:15:58 us=884676 Expected Remote Options String (VER=V4): ‘V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-128-CBC,auth SHA1,keysize 128,key-method 2,tls-server’
2021-02-23 11:15:58 us=884676 TCP/UDP: Preserving recently used remote address: [AF_INET]MYIP:12973
2021-02-23 11:15:58 us=884676 Socket Buffers: R=[65536->65536] S=[65536->65536]
2021-02-23 11:15:58 us=884676 UDP link local: (not bound)
2021-02-23 11:15:58 us=884676 UDP link remote: [AF_INET]MYIP:12973
2021-02-23 11:15:58 us=884676 MANAGEMENT: >STATE:1614100558,WAIT,,,,,,
Was this post helpful?
thumb_up
thumb_down
I see some warnings in that log but no showstoppers. Last line shows your openvpn client is in a waiting state. Does the Netgear show you anything useful like an incoming connection?
1 found this helpful
thumb_up
thumb_down
Check this link that’s embedded in the log: http://openvpn.net/howto.html#mitm Opens a new window . The How To can answer a lot of questions.
1 found this helpful
thumb_up
thumb_down
OP
RDB001
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.
jalapeno
It now works in V 3.3. Changing the tap to tun and the port number resolved this issue.
Was this post helpful?
thumb_up
thumb_down
Содержание
- Настройка OpenVPN в macOS
- Настройка для Tunelblick
- Настройка для Viscosity
- Настройка для OpenVPN Connect 3
- OpenVPN Connect for Mac OS
- The Interface
- Frequently Asked Questions
- Can the new and old client co-exist?
- Can i connect to multiple servers at the same time?
- Is the old client still available?
- Where can I get this for other OS?
- Should I use this client or the client from my instance of Access Server?
- How do I install the Mac client?
- How do I install the client directly from my Access Server?
- How do I import a profile from a server?
- How do I import a profile from my computer?
- Why did I receive an error message that TAP mode is not supported when importing a profile?
- Why am I getting a certificate error? How can I fix using a self-signed certificate?
- Where do I find my Access Server Hostname and credentials?
- What do I enter for “Title”?
- What does “import autologin profile” mean?
- Why did I get this message: “In this version compression was disabled by default. If you need it, please re-enable this setting.”
- 12 Replies
- Connecting to Access Server with macOS
- Installing a client application
- OpenVPN Connect with your Access Server
- Steps: Access your client UI
- OpenVPN Connect v3
- OpenVPN Connect v2
- Alternative OpenVPN open source client: Tunnelblick
- Alternative OpenVPN client: Viscosity
- Other client GUI projects
- Helpful Resources
- Installation guide for OpenVPN Connect Client on macOS
- Introduction
- Requirements
- Downloading and installing the OpenVPN Connect Client for macOS
Настройка OpenVPN в macOS
Настройка для Tunelblick
Если ваша версия macOS старшее MacOS X Leopard, вы можете воспользоваться клиентом OpenVPN Tunnelblick.
Tunnelblick также работает и на современных версиях macOS. Для настройки работы Tunellblick выполните следующие действия:
1. Скачайте инсталятор Tunelblick Tunnelblick и установите его.
2. Распакуйте конфигурационные файлы, выданные техподдержкой. Вы также можете их скачать в личном кабинете.
3. Откройте файл с конфигурационного файла ovpn в программе Tunnelblick.
4. Выберите в меню Tunelblick пункт Connect config. При запросе логина и пароля, ввести их, взяв из файла pass.txt,
который также был в архиве с конфигурационными файлами.
5. Для проверки работы сервиса, можете обратитесь к странице https://whoer.net/ru. В отчете Вы можете увидеть текущий IP-адрес.
После окончания работы с VPN, кликните в меню Tunelblick выберите Disconnect config.
Настройка для Viscosity
Если у Вас Mac OS X Leopard или новее, наиболее удобной в использовании является клиент OpenVPN Viscosity.
В этом случае настройка VPN-сервиса сводится к следующим действиям:
1. Скачайте последнюю версию программы Viscosity и установите.
2. Распакуйте конфигурационные файлы, доступные в ваших заказах, в любой каталог.
3. Откройте конфигурационный файл ovpn в программе Viscosity.

4. Далее в верхнем меню рядом с часами кликаем на икноку Viscosity и в выпадающем меню программы выбираем Connect,
в диалоговом окне вводим имя пользователя и пароль (находятся в файле pass.txt в архиве в Ваших заказах).
5. Для проверки работы сервиса, можете обратитесь к странице https://whoer.net/ru. В отчете Вы можете увидеть текущий IP-адрес.
После окончания работы с VPN, кликните в меню Viscosity выберите Disconnect.
Настройка для OpenVPN Connect 3
1. Скачайте дистрибутив OpenVPN Connect 3 с официального сайта openvpn.net и установите его.
2. Скачайте конфигурационные файлы из личного кабинете и распакуйте их
3. Чтобы добавить конфигурационный файл в OpenVPN Connect просто переместите файл на приложение.
6. Вы можете избежать появления данной ошибки в будущем, добавив в конфигурационый файл ovpn строчку
после этого, изменённый конфигурационный файл нужно снова передобавить в OpenVPN Connect.
7. Впн подключение активируется, вы сможете управлять им в OpenVPN Connect.
Источник
OpenVPN Connect for Mac OS
This is the official OpenVPN Connect client software for Mac OS developed and maintained by OpenVPN Inc. This is the recommended client program for the OpenVPN Access Server. The latest version of OpenVPN Connect client for Mac is available on our website.
If you have an OpenVPN Access Server, it is recommended to download the OpenVPN Connect client software directly from your own Access Server, as it will then come preconfigured for use. The version available here contains no configuration to make a connection, although it can be used to update an existing installation and retain settings.
sha256 signature: 221fe99f9eaa998a2f39f02ffdb16005eb5fae890dce1c1474bbd4b5fa691171
For mac OS versions titled Yosemite, El Capitan, Sierra, High Sierra, Mojave, Catalina, Big Sur, and Monterey.
Previous generation OpenVPN Connect V2 is available here:
sha256 signature: 2b49e35d0c1b8ee83d1b7067e07f382beacb626e8f5bb7d75fe92debeda42dbc
The Interface
Our latest line of OpenVPN Connect software available for the major platforms features a new and improved user interface, making the experience of installing and using the OpenVPN software a snap. With an easy to use import feature you can import profiles straight from your OpenVPN Access Server or just import a saved profile from disk.
Frequently Asked Questions
Can the new and old client co-exist?
Yes, you may continue to use both v2 and v3 on the same connect device and import the profiles desired into each. If you like, you can run either one or both.
Can i connect to multiple servers at the same time?
No, the client cannot connect to multiple servers at once. It does support multiple connection profiles, giving you the option to switch easily from one server to the next, but you can only be connected to one at a time. This is by design, to prevent unexpected traffic paths when connecting to multiple VPN servers at the same time. If you are a system administrator and you require a complex setup where multiple connections are active at the same time, there is the option to use the open source community OpenVPN client software available from our website.
Is the old client still available?
The OpenVPN client v1 was called “OpenVPN Desktop Client” and is no longer available. It is also not safe to use this anymore as it hasn’t been maintained for many years. It was replaced with the OpenVPN client v2. The OpenVPN client v2 is called “OpenVPN Connect Client” and has been in use for many years. It is still available from our website and offered in the OpenVPN Access Server client web interface itself. The OpenVPN client v3 is called “OpenVPN Connect” and is the latest generation of our software. It is available on our website as a beta version, and will be included soon in Access Server releases.
Where can I get this for other OS?
Should I use this client or the client from my instance of Access Server?
This is the official OpenVPN Connect software for Windows workstation platforms developed and maintained by OpenVPN Inc. This is the recommended client program for the OpenVPN Access Server. The latest versions are available on our website. If you have an OpenVPN Access Server, you can download the OpenVPN Connect client software directly from your own Access Server, and it will then come pre-configured for use. The version available here contains no configuration to make a connection, although it can be used to update an existing installation and retain settings.
How do I install the Mac client?
How do I install the client directly from my Access Server?
Directions found here for installing the client directly from Access Server for your macOS computer. This install is preconfigured with your connection settings from your server.
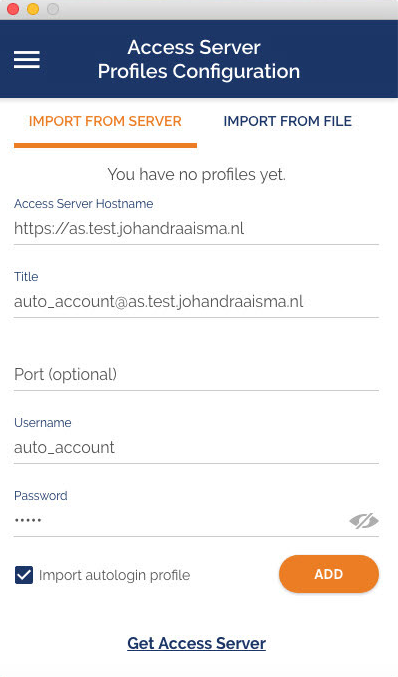
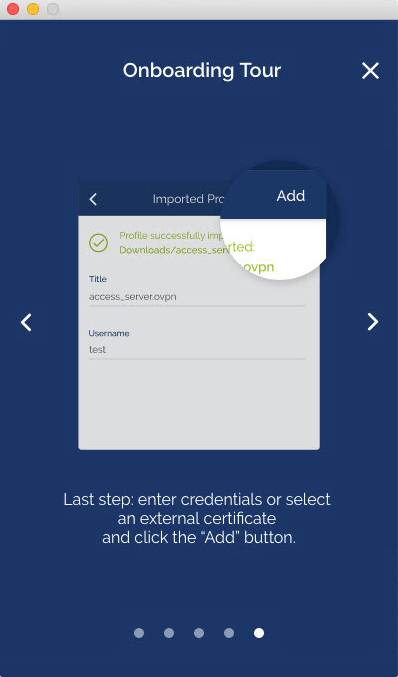
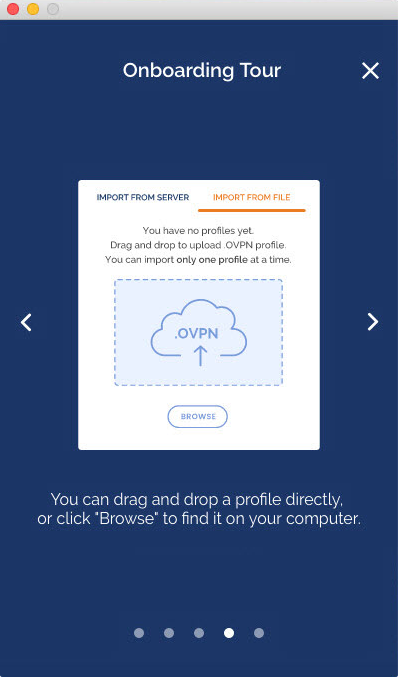
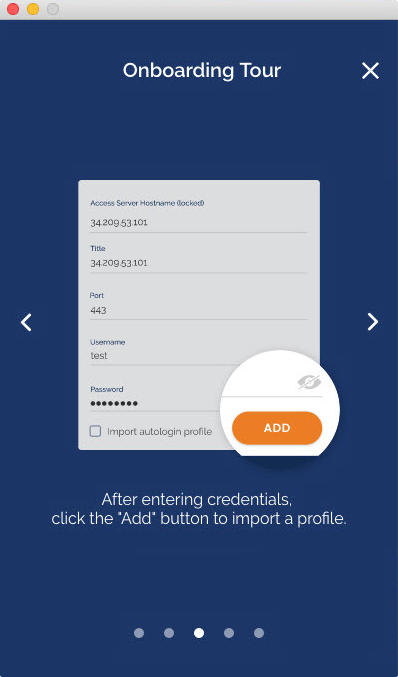
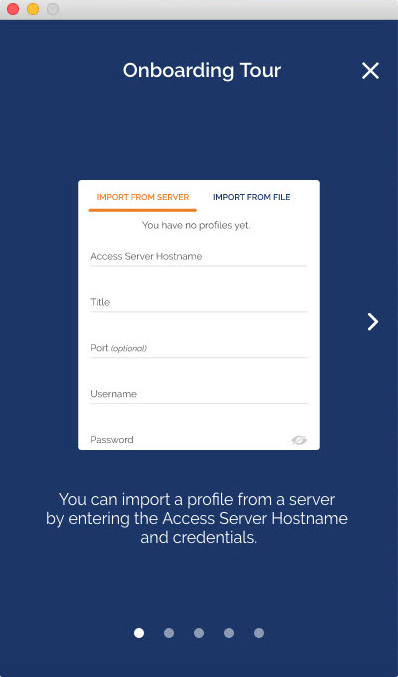
How do I import a profile from a server?
How do I import a profile from my computer?
Why did I receive an error message that TAP mode is not supported when importing a profile?
Layer 2 bridging (TAP) is no longer supported. Switch over to TUN Mode to resolve this issue.
Why am I getting a certificate error? How can I fix using a self-signed certificate?
OpenVPN Access Server starts with a self-signed certificate. With this, you will receive warnings from your web browser about the site not being secure as well as a certificate error when importing a profile with the Connect Client. You can simply override the warnings or add an exception for your web browser. To resolve this, you can set up a DNS host name that resolves to the public address of your Access Server and install a valid SSL certificate that corresponds to that DNS host name. Going forward, you would use that hostname to access your server instead of the IP address. This is also the recommended method as validated SSL certificates can only ever function with a valid public DNS hostname.
Where do I find my Access Server Hostname and credentials?
Your Access Server Hostname is the address at which your Access Server can be reached. For example it could be https://vpn.yourcompany.com/. If a DNS hostname is not set up, it is also possible to specify the IP address where your Access Server. For example:https://55.193.55.55 Your credentials are your username and password. You may need to get that information from your Access Server administrator if you don’t know it.
What do I enter for “Title”?
Title is the name for the profile. It is automatically defined as the username with the hostname or IP address(example: user1@hostname). It differentiates between multiple profiles. You can define it manually as well. The title can be anything you want is just so you can see which profile is which.
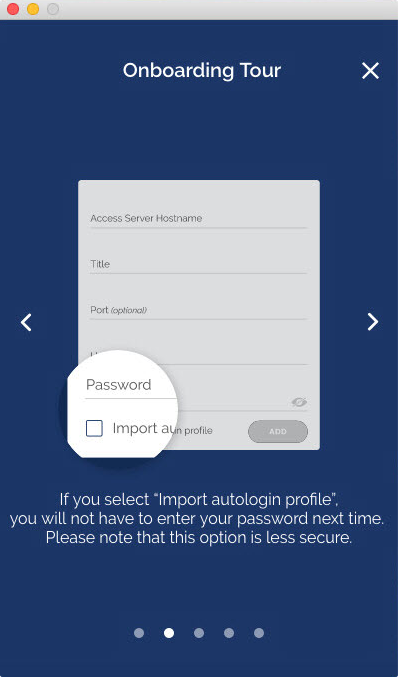
What does “import autologin profile” mean?
Choosing this option allows you to import an autologin profile with the address and credentials for your Access Server, then simply start the connection with the tap of a button. You would not need to re-enter credentials each time you connect. The autoprofile itself contains an embedded secure certificate that identifies and authorizes your connection automatically. It is an optional setting on the OpenVPN Access Server that the administrator of the server can choose to make available to you. If you find you cannot import the autologin profile, your administrator may not have allowed autologin through user permissions.
Why did I get this message: “In this version compression was disabled by default. If you need it, please re-enable this setting.”
During investigation of a vulnerability called VORACLE, it was found that using compression to make the data that goes through the VPN tunnel smaller, and thus faster, has an adverse effect on security. To learn more about this see our security notification on our website regarding the VORACLE attack vulnerability. In order to protect our customers, we are disabling compression by default. Some servers of the open source variety can be configured in such a way that the client must do compression, or else the client may not connect successfully. In such a case, you should get the server updated to disable compression. But we understand that this is not always possible, and you may need to be able to connect to such a server. In that event you can go into the settings and re-enable compression.
Источник
I am running a NETGEAR R7450 and the VPN profile works fine on my android device but doesn’t work on a Windows 10 device using the «Windows» configuration files. I get the error: «Failed to import Profile». Failed to parse profile: option_error: proto_option_error: TAP mode is not supported. How can this be fixed?
Try just changing «tap» to «tun» and update the port number in the «remote» line from 12974 to the TUN port shown in your Netgear config.
Looks like you’re using OpenVPN Connect on Windows and I assume it’s version 3.In that version TAP is no longer supported. You should use TUN mode.
I believe OpenVPN Community Edition 2.5 (https://openvpn.net/community-downloads/) still supports TAP.
Better option is to just turn off TAP altogether if you can in the Netgear. The screenshot above does not seem to suggest a way to only configure TUN. Perhaps in Advanced settings you can do such a thing?
You can look at modifying the generated openvpn configuration file and see about removing the TAP portions. The ovpn file is usually just a text file you can edit in Notepad.
Looks like you’re using OpenVPN Connect on Windows and I assume it’s version 3.In that version TAP is no longer supported. You should use TUN mode.
I believe OpenVPN Community Edition 2.5 (https://openvpn.net/community-downloads/) still supports TAP.
Better option is to just turn off TAP altogether if you can in the Netgear. The screenshot above does not seem to suggest a way to only configure TUN. Perhaps in Advanced settings you can do such a thing?
You can look at modifying the generated openvpn configuration file and see about removing the TAP portions. The ovpn file is usually just a text file you can edit in Notepad.
It looks like the TAP can not be disabled through the interface. I will attempt to download version 2.5 to see if I can get this to work. If that doesn’t work, what steps would need to be taken to remove the openvpn configuration files?
Here is the error I am receiving when using version 2.5:
The config files are in the directory of: C:Program filesOpenVPNconfig
Which in turns gives this result:
The client.opvn extension file:
client
dev tap
proto udp
dev-node NETGEAR-VPN
remote x.x.x.x (MY IP) 12974
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
cipher AES-128-CBC
comp-lzo
verb 5
Try just changing «tap» to «tun» and update the port number in the «remote» line from 12974 to the TUN port shown in your Netgear config.
Have you opened the appropriate ports in the client firewall?
Also, try entering the appropriate path to the certs in the config. Examples (notice the double slashes):
ca «C:\Program Files\OpenVPN\config\ca.crt»
cert «C:\Program Files\OpenVPN\config\MRdesktop.crt»
key «C:\Program Files\OpenVPN\config\MRdesktop.key»
Try just changing «tap» to «tun» and update the port number in the «remote» line from 12974 to the TUN port shown in your Netgear config.
Okay I replaced tap with tun and changed the port to 12973 and I am getting a bit further but am running into a TLS handshake issue.
Источник
Connecting to Access Server with macOS
Each macOS device needs a client application to connect with your OpenVPN Access Server. We recommend using OpenVPN Connect, which is pre-configured to connect with your Access Server. This document provides information on using OpenVPN Connect as well as alternative solutions.
Installing a client application
The OpenVPN protocol is not built into macOS. Therefore, you must install a client app to handle communication with Access Server. A client app is required to capture the traffic you want to send through the OpenVPN tunnel, encrypt it, pass it on to the server, and decrypt the return traffic.
OpenVPN Connect with your Access Server
Your installation of OpenVPN Access Server includes a copy of OpenVPN Connect, which is a separate package called openvpn-as-bundled-clients that is updated when new versions of OpenVPN Connect are released. OpenVPN Connect is our official client app and your users can download it directly from your client UI, pre-configured to connect with your server, or download it separately from our website and import a connection profile.
Steps: Access your client UI
OpenVPN Connect only supports one active VPN tunnel at a time. It was purposely designed to not support connections to two or more servers simultaneously. Connecting to two servers at the same time requires two different adjustments to the routing table on the client computer. Therefore, it is very easy to make a mistake and break connectivity or cause traffic to flow to the wrong destination. Limiting connections to one server ensures connectivity and traffic flow. OpenVPN Connect can store many profiles for different servers, but you can only actively connect to one at a time.
OpenVPN Connect also supports client-side scripting, importing connection profiles directly from Access Server, and connecting with a server-locked profile. A server-locked profile enables you to authenticate any valid user on your Access Server without installing unique connection profiles for each user.
OpenVPN Connect v3
We recommend and support OpenVPN Connect v3 as the official app for OpenVPN Access Server and OpenVPN Cloud. The client software offers client connectivity across four major platforms: Windows, macOS, Android, and iOS. For Linux, we recommend the open source OpenVPN client.
We recommend downloading OpenVPN Connect v3 directly from your Access Server web client UI. You can also download the installation file for OpenVPN Connect v3 from the download page on our site or with the link below. The app installation from our site does not contain any connection settings, so you’ll need to take additional steps to configure the connection to your Access Server. If you are installing the below file on a computer that already has OpenVPN Connect v3 installed and configured, it simply updates it to the latest version and retains all settings.
OpenVPN Connect v2
This is the previous generation of OpenVPN Connect client software for OpenVPN Access Server. It is still supported but we recommend people to use OpenVPN Connect v3 instead.
Alternative OpenVPN open source client: Tunnelblick
The open source project also has a client for macOS called Tunnelblick. Tunnelblick supports the option to connect to multiple OpenVPN servers simultaneously, which can cause connection issues if not configured correctly. You must not implement conflicting routes and subnets. Unlike on Windows platform, however, you don’t need to add multiple virtual network adapters because they are provisioned automatically.
Alternative OpenVPN client: Viscosity
Viscosity is a third-party OpenVPN client that is created by SparkLabs. Viscosity is available for Windows and macOS and is compatible with OpenVPN Access Server.
Other client GUI projects
There are many VPN clients built for the OpenVPN protocol that will also work with OpenVPN Access Server. Refer to the community website for the current list.
Helpful Resources
For further information on VPN configuration details, refer to this documentation:
Источник
Installation guide for OpenVPN Connect Client on macOS
Introduction
This guide is meant for users of the OpenVPN Access Server product that wish to connect their macOS computer using the official OpenVPN Connect Client software. In the steps outlined below we’ll take you through the process of obtaining the OpenVPN Connect Client from your Access Server’s web interface, and installing and using it on the macOS operating system. Aside from some minor differences due to different versions of software used this guide should be accurate and easy to follow. Each step can be clicked to show a screenshot for that particular step in the installation process. Each screenshot can be clicked to reveal an image gallery you can follow to go through all the steps.
Requirements
You will need to have a valid set of credentials, like user name and password, and of course the address of your OpenVPN Access Server. If you are not the administrator of the Access Server you are going to connect to, then you should contact the administrator of this server to obtain this information. We here at OpenVPN Inc. cannot provide this information, since we do not manage servers run by our customers. If you are the administrator of your Access Server, you can create new user accounts using the admin web interface of the Access Server or the external authentication backend you have configured, and then use those credentials to obtain and install the OpenVPN Connect Client on macOS.
The OpenVPN Connect Client for macOS, latest version, currently supports these operating systems:
Downloading and installing the OpenVPN Connect Client for macOS
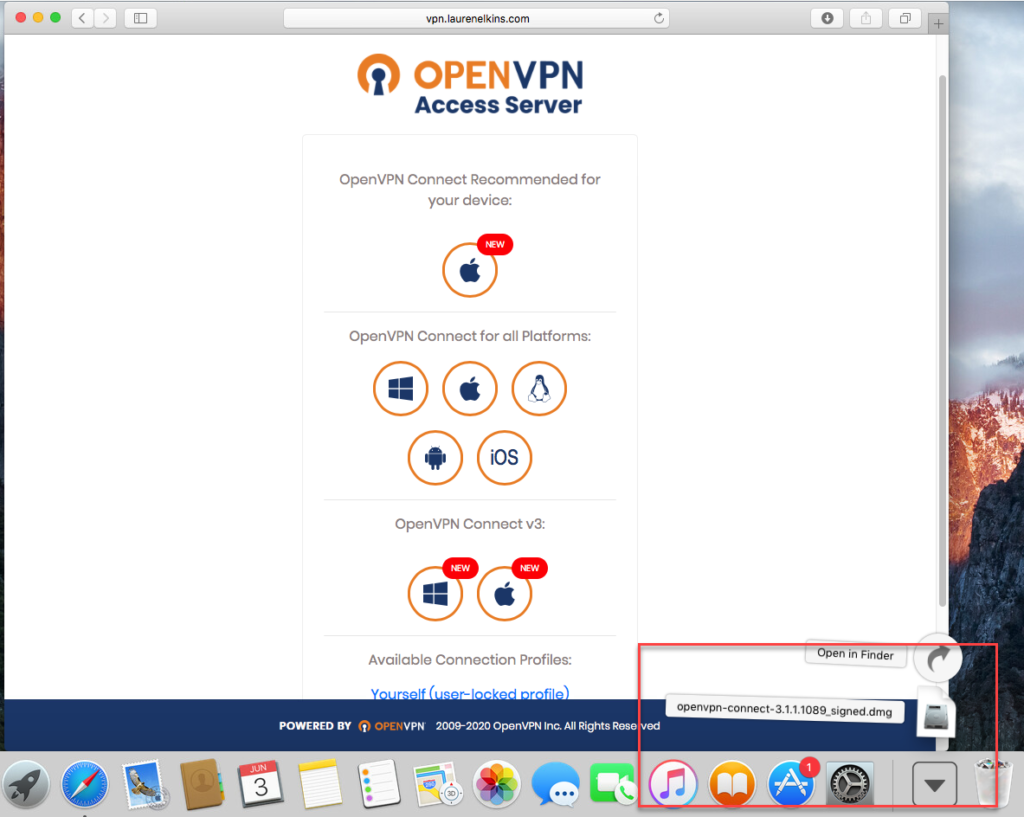
Navigate to the OpenVPN Access Server client web interface.
Login with your credentials.
Click on the Mac icon to begin download.
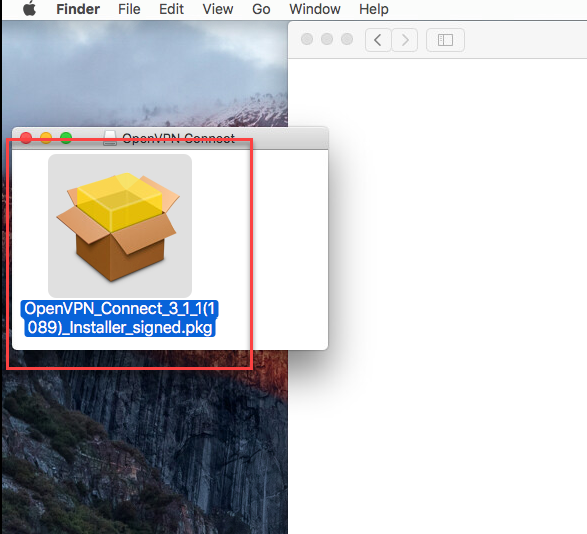
Wait until the download completes, and then open it (the exact procedure varies a bit per browser).
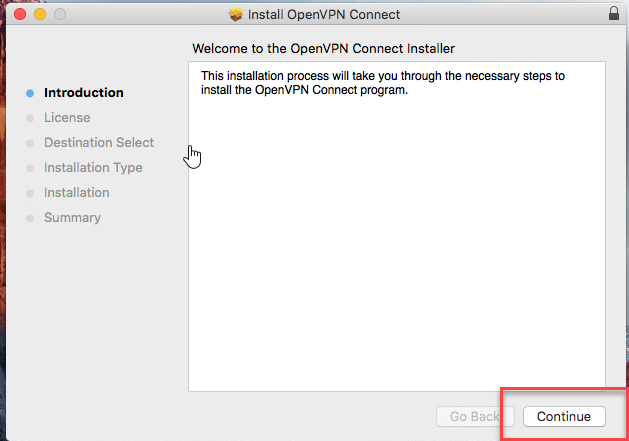
Open the ‘OpenVPN Connect installer’ to start the installation.
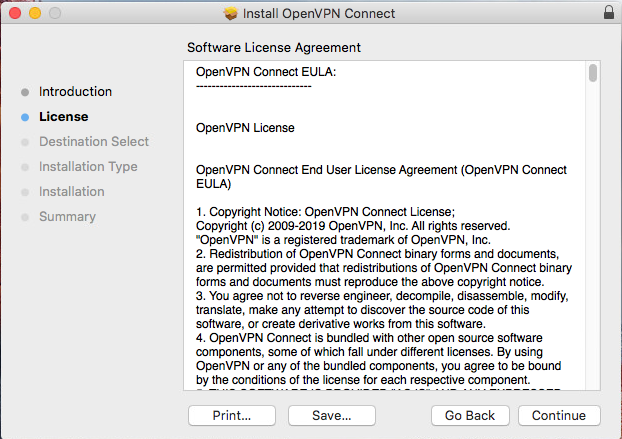
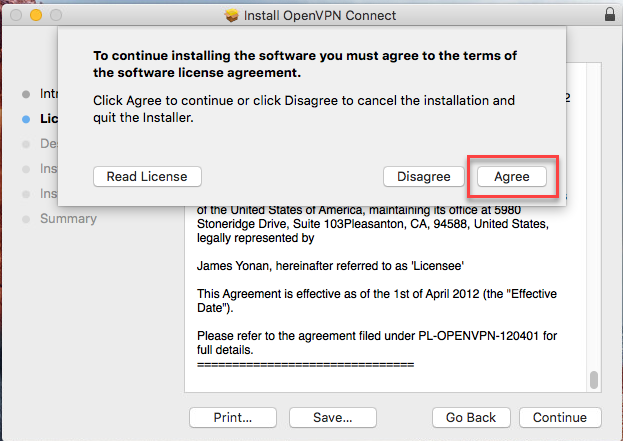
Please read the licensing terms. Then click ‘Continue’.
Click ‘Agree’ to accept the licensing terms.
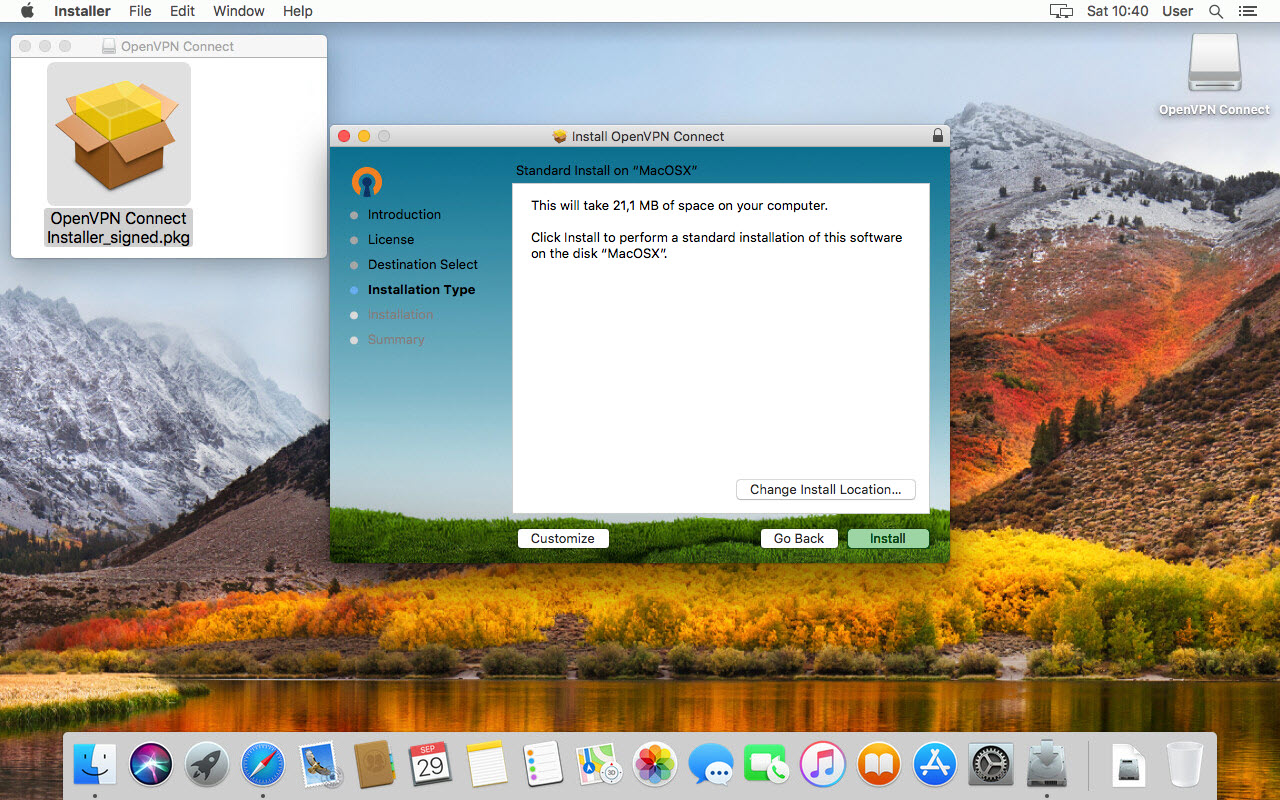
Click ‘Install’ to proceed.
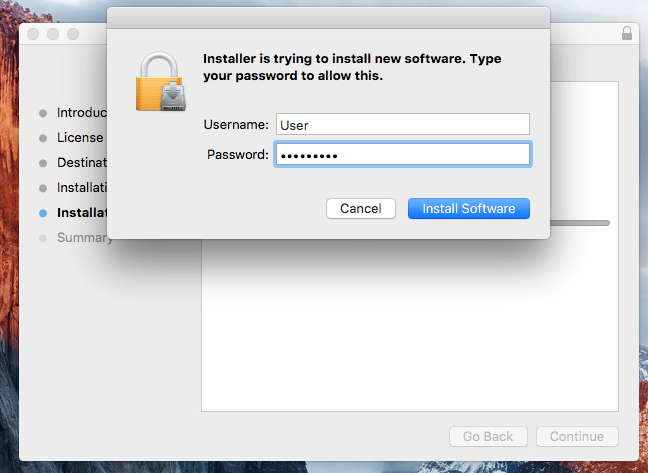
Enter your device password, if you have one configured, and click ‘Install Software’.
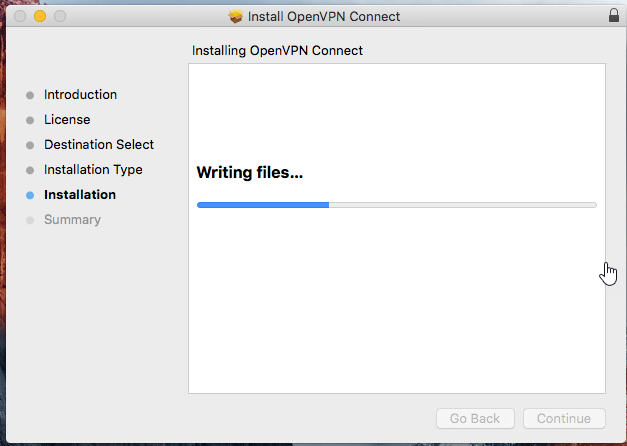
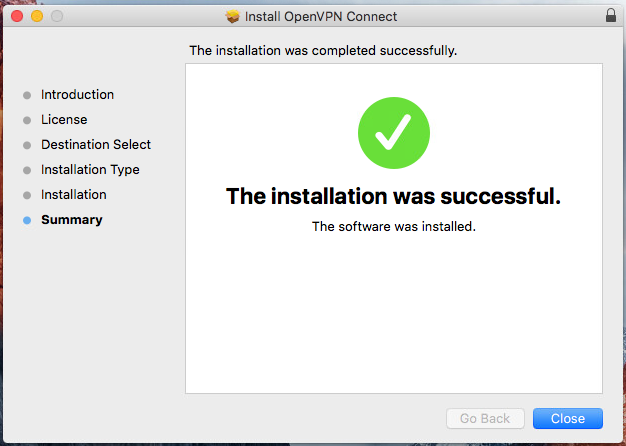
Wait for the installation process to complete.
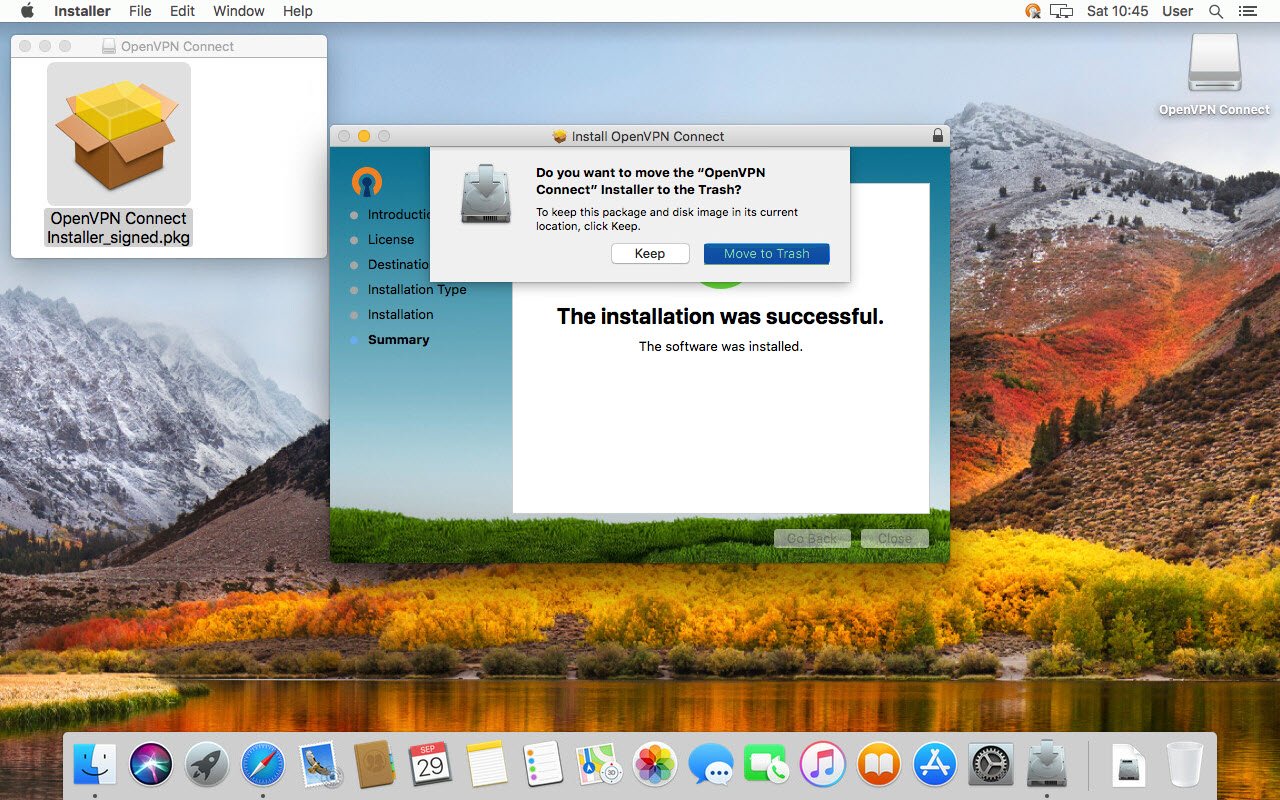
Click ‘Close’ to end the installation process.
If your device asks, click ‘Move to Trash’ to clean up the installer file.
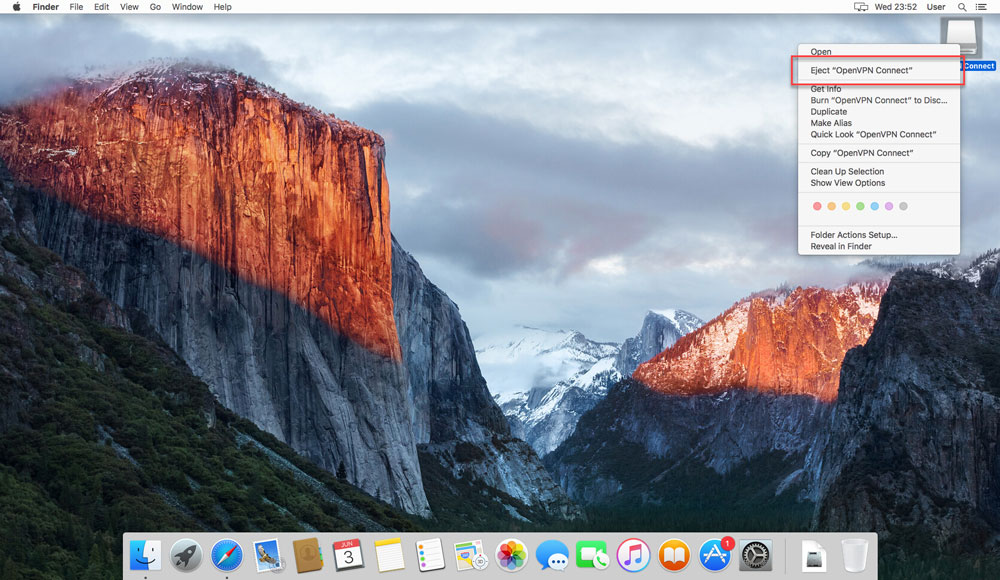
Rightclick (ctrl+click) ‘OpenVPN Connect’ and eject it.
In Applications, OpenVPN Connect is now ready for use.
Источник
Хорошо, с первим понятно. Редагую конфиг на клиенте.
А что с конфигом на сервере. Где нужно вставить ету строчку: push «topology subnet» …..?
Вот конфиг:
####Server######
# EBox OpenVPN 2.0 config file for server sachemplace1
# Which local IP address should OpenVPN
# listen on? (optional)
# Which TCP/UDP port should OpenVPN listen on?
port ***
# TCP or UDP server?
proto ***
# virtual device
dev tap1
# SSL/TLS root certificate (ca), certificate
# (cert), and private key (key).
ca ‘/var/lib/ebox/CA/cacert.pem’
cert ‘/var/lib/ebox/CA/certs/34F288873BF03F59.pem’
key ‘/var/lib/ebox/CA/private/vpn-sachemplace1.pem’
# This file should be kept secret
# check peer certificate against certificate revokation list
crl-verify /var/lib/ebox/CA/crl/latest.pem
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh1024.pem 1024
# Substitute 2048 for 1024 if you are using
# 2048 bit keys.
#dh /etc/openvpn/dh1024.pem
dh /etc/openvpn/ebox-dh1024.pem
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
server 192.168.160.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file.
ifconfig-pool-persist ‘/etc/openvpn/sachemplace1-ipp.txt’
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN
;push «redirect-gateway»
# Uncomment this directive to allow different
# clients to be able to «see» each other.
client-to-client
# The keepalive directive causes ping-like
# messages to be sent back and forth over
keepalive 10 120
# client certificate common name authentication
# For extra security beyond that provided
# by SSL/TLS, create an «HMAC firewall»
# to help block DoS attacks and UDP port flooding.
;tls-auth ta.key 0 # This file is secret
# Select a cryptographic cipher.
# This config item must be copied to
# the client config file as well.
;cipher BF-CBC # Blowfish (default)
;cipher AES-128-CBC # AES
;cipher DES-EDE3-CBC # Triple-DES
# Enable compression on the VPN link.
# If you enable it here, you must also
# enable it in the client config file.
comp-lzo
# The maximum number of concurrently connected
# clients we want to allow.
;max-clients 100
# group and user for the OpenVPN
# daemon’s privileges after initialization.
user nobody
group nogroup
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
# of the privilege downgrade.
persist-key
persist-tun
# Output a short status file showing
# current connections, truncated
# and rewritten every minute.
status ‘/var/log/ebox/openvpn/status-sachemplace1.log’
# By default, log messages will go to the syslog (or
# on Windows, if running as a service, they will go to
# the «Program FilesOpenVPNlog» directory).
# Use log or log-append to override this default.
# «log» will truncate the log file on OpenVPN startup,
# while «log-append» will append to it. Use one
# or the other (but not both).
log-append ‘/var/log/ebox/openvpn/sachemplace1.log’
# Set the appropriate level of log
# file verbosity.
#
# 0 is silent, except for fatal errors
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# Silence repeating messages. At most 20
# sequential messages of the same message
# category will be output to the log.
;mute 20
push «route 192.168.4.0 255.255.255.0»