I’m trying to use OpenVPN to connect two TrueNAS servers together and configure one as the offsite backup. So, I was able to create the necessary CAs and certificates and configure the OpenVPN Server service parameters on my main server (truenas.local). Then, I was able to download the .ovpn file, load it into OpenVPN Connect on my PC and remotely access my main TrueNAS server. So, I think the server configuration should be correct.
.ovpn File:
client
dev tun
proto udp4
port 1194
remote «openvpn.mydomain.com»
user nobody
group nobody
persist-key
persist-tun
<ca>
——BEGIN CERTIFICATE————END CERTIFICATE——
</ca>
<cert>
——BEGIN CERTIFICATE————END CERTIFICATE——
</cert>
<key>
——BEGIN PRIVATE KEY————END PRIVATE KEY——
</key>
verb 3
remote-cert-tls server
auth SHA1
cipher AES-256-CBC
<tls-crypt>
#
# 2048 bit OpenVPN static key
#
——BEGIN OpenVPN Static key V1——
3991c23449a0b7da8c09499038b46075——END OpenVPN Static key V1——
</tls-crypt>
Now, I want to enable the OpenVPN Client service on my offsite TrueNAS server (truenas-backup.local). So, I followed these directions [https://www.truenas.com/community/resources/truenas-and-openvpn-client-configuration.158/] which were helpful in setting up the CAs, certificates, and other parameters. However, I still can’t get it to work. I keep getting these TLS errors and that the CN could not be verified.
truenas-backup.local Console report:
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000380-07:00 truenas-backup.local openvpn_client 2161 — — VERIFY ERROR: could not extract CN from X509 subject string (‘C=US, ST=NC, L=WS, O=myname, emailAddress=myemail@email.com’) — note that the username length is limited to 64 characters
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000404-07:00 truenas-backup.local openvpn_client 2161 — — OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000408-07:00 truenas-backup.local openvpn_client 2161 — — TLS_ERROR: BIO read tls_read_plaintext error
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000412-07:00 truenas-backup.local openvpn_client 2161 — — TLS Error: TLS object -> incoming plaintext read error
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000415-07:00 truenas-backup.local openvpn_client 2161 — — TLS Error: TLS handshake failed
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000461-07:00 truenas-backup.local openvpn_client 2161 — — SIGUSR1[soft,tls-error] received, process restarting
Jul 2 15:49:42 truenas-backup 1 2022-07-02T15:49:42.000476-07:00 truenas-backup.local openvpn_client 2161 — — Restart pause, 160 second(s)
I have yet to find a straightforward answer on why you can’t just import the .ovpn file especially when it was generated on another TrueNAS server.
Anyways, how do it fix these TLS and CN errors?
Thanks
-
Summary
-
Reviews
-
Support
-
Git ▾
- easy-rsa
- openvpn
- openvpn-historical-cvs
- tap-windows
-
Mailing Lists
-
News
-
Donate
Menu
▾
▴
|
From: Jorge Luiz Silva Peixoto <jorge…@gm…> — 2015-01-19 22:48:14 |
Hello OpenVPN community!
Line below was extract from my openvpn server log.
Jan 8 17:44:25 myserver openvpn[28644]: a.b.178.157:22853 VERIFY
ERROR: could not extract CN from X509 subject string (' ***user
certificate dn here*** ') -- note that the username length is limited
to 64 characters
Initially I thought such user certificate DN had more than 64
characters on CN field, actually CN has *exactly* 64 ASCII characters.
Looking at ssl_verify.c and ssl_verify_openssl.c, I found that
backend_x509_get_username returns FAILURE. In turn,
extract_x509_field_ssl returns FAILURE as well. At the end of
extract_x509_field_ssl, I found something suspicious. Look at the line
bellow:
const result_t ret = (strlen ((char *)buf) < size) ? SUCCESS: FAILURE;
Is the comparison between strlen ((char *)buf) and size correct?
Shouldn't be less equal?
I'll do some tests, e.g. changing TLS_USERNAME_LEN from 64 to 65.
PS: According to rfc5280, common name maximum length is 64.
Regards,
Jorge Peixoto
|
|
From: Steffan Karger <st…@ka…> — 2015-01-19 23:43:31 |
Hi Jorge, On 19-01-15 23:47, Jorge Luiz Silva Peixoto wrote: > Is the comparison between strlen ((char *)buf) and size correct? > Shouldn't be less equal? That check is correct, since strlen() excludes the NULL-character, and we rely on the string begin NULL-terminated. > I'll do some tests, e.g. changing TLS_USERNAME_LEN from 64 to 65. At first glance this seems to be the right fix, but keep in mind that you'll have to change the warning messages using the value too, to keep them displaying '64'. > PS: According to rfc5280, common name maximum length is 64. Yes, and that is where this errors stems from. The strings used by rfc5280 are not NULL-terminated, whereas C strings are. Please feel free to send your patch to openv...@li... if you decide to do a patch for this. (and please use git format-patch to create such a patch). -Steffan |
Hi.
I am trying to connect my Linux client to my Mikrotik OVPN server.
To setup the certificates on the Mikrotik i followed this guide (http://wiki.mikrotik.com/wiki/Manual:Cr … rtificates)
/certificate
add name=ca-template common-name=myCa key-usage=key-cert-sign,crl-sign
add name=server-template common-name=server
add name=client1-template common-name=client1
add name=client2-template common-name=client2/certificate
sign ca-template ca-crl-host=10.5.101.16 name=myCa
sign server-template ca=myCa name=server
sign client1-template ca=myCa name=client1
sign client2-template ca=myCa name=client2/certificate
set myCa trusted=yes
set server trusted=yes/certificate export-certificate myCa
/certificate export-certificate client1 export-passphrase=xxxxxxxx
/certificate export-certificate client2 export-passphrase=xxxxxxxxThen on the Mikrotik OVPN configuration it asks for a certificate and I put in myCa
Once that has been done. I take the exported client.crt from the Mikrotik, to the linux client. Setup the OpenVPN connection using Network Manager, it asked for certificate, username & password which is all supplied.
The VPN does not connect, Mikrotik has no relevant logs but Linux does, I have attached a section below, its obviouslly a problem with the certificate but I cannot figure out what to do, any help?
Feb 10 08:14:48 cspace nm-openvpn[59389]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Feb 10 08:14:48 cspace nm-openvpn[59389]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 10 08:14:48 cspace nm-openvpn[59389]: Attempting to establish TCP connection with [AF_INET]41.164.32.77:1194 [nonblock]
Feb 10 08:14:48 cspace pptp[124817]: anon log[decaps_gre:pptp_gre.c:414]: buffering packet 557277 (expecting 557276, lost or reordered)
Feb 10 08:14:49 cspace nm-openvpn[59389]: TCP connection established with [AF_INET]41.164.32.77:1194
Feb 10 08:14:49 cspace nm-openvpn[59389]: TCPv4_CLIENT link local: [undef]
Feb 10 08:14:49 cspace nm-openvpn[59389]: TCPv4_CLIENT link remote: [AF_INET]41.164.32.77:1194
Feb 10 08:14:49 cspace nm-openvpn[59389]: VERIFY ERROR: depth=0, error=self signed certificate: CN=myCa
Feb 10 08:14:49 cspace nm-openvpn[59389]: TLS_ERROR: BIO read tls_read_plaintext error: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
Feb 10 08:14:49 cspace nm-openvpn[59389]: TLS Error: TLS object -> incoming plaintext read error
Feb 10 08:14:49 cspace nm-openvpn[59389]: TLS Error: TLS handshake failed
Feb 10 08:14:49 cspace nm-openvpn[59389]: Fatal TLS error (check_tls_errors_co), restarting
Feb 10 08:14:49 cspace nm-openvpn[59389]: SIGUSR1[soft,tls-error] received, process restarting
Feb 10 08:14:49 cspace pptp[124817]: anon log[decaps_gre:pptp_gre.c:414]: buffering packet 558283 (expecting 558282, lost or reordered)
- Печать
Страницы: [1] Вниз
Тема: Конфиги openvpn (Прочитано 4134 раз)
0 Пользователей и 1 Гость просматривают эту тему.

sheffv
Уважаемые, чем отличаются клиентские конфиги openvpn 2.1 и 2.0.9? А ситуация такова, 2.0.9 поднимает впн, но почему то скорость доступа никакая(в винде нормально), 2.1rc11 не может подняться ругается на Common Name и неверный сертификат в итоге. Вопрос — как ковертировать конфиги из более старой версии?
« Последнее редактирование: 12 Октября 2009, 09:35:46 от sheffv »

Frank
По-моему, там ясно написано, что
WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info
и
VERIFY ERROR: could not extract Common Name from X509 subject string

sheffv
оно то ясно, как выяснилось на сервере стоит openvpn 2.0.9 — ну не совместимы эти серты с 2.1, ну что ж такие простые вещи в Винде так сложно решаются в Линуксе? Неужто нельзя нормальный клиент опенвпн написать..

Frank
Неужто нельзя прописать конкретный метод проверки сертификата (не выбран ни один) и сгенерировать нормальный сертификат, содержащий Common name?

Tokh
ну что ж такие простые вещи в Винде так сложно решаются в Линуксе?
В Вин эти «простые вещи не решаются» вообще, как просто, так и сложно. 
Неужто нельзя нормальный клиент опенвпн написать..
Да нормальный он, очень. Тема сложная. Относительно сложная. О сложностях см. оффтопик тут https://forum.ubuntu.ru/index.php?topic=43824.0 Это профессиональные компоненты из которых можно гибко конструировать систему. В Вин — жёсткое решение, ориентированное на возможность обслуживания дёшево и слабо обученным человеком.
Изменения между версиями должны быть описаны в документации или специальных описаниях. Эти изменения касаются не только удобств, но и безопасности. По всей видимости ссылка из лога теперь выглядит вот так http://openvpn.net/index.php/open-source/documentation/howto.html#mitm
Если таки действительно «ну не совместимы эти серты с 2.1«, то это вопрос не столько к OpenVPN, сколько к OpenSSL и формату x.509 сертификатов. Есть линк на то, где сказано «ну не совместимы эти серты с 2.1«?
StarDict и Mueller помогут против английского мануала.

sheffv
Собственно сделал я такой вывод подключившись к впн на сертификате pk12, все прошло гуд. Но тут возникла другая проблема — очень медленный коннект через wlan0. Проблема в ipv6, потому как через 3Г модем пошло все боле менее нормально. Вопрос — как избавится от ipv6 в wlan0, попробовал разные советы, не помогло. Какое генерик ядро можете посоветовать без этих проблем? Или надо перекомпилировать ядро и убирать поддержку ipv6?

Frank
При чём тут ipv6? Где конфиг сервера? Разве там прописано ему слушать на ipv6 интерфейсе?
Какой прототип используется, tcp или udp?

sheffv
tcp и dev tap используется. Конфиг сервера не знаю, впн покупной.
« Последнее редактирование: 13 Октября 2009, 11:08:33 от sheffv »

Frank
На интерфейсе, создаваемом OpenVPN, уменьши MTU — из-за dev tap пакет в 1500 байт+заголовки не влезает в окно размером в те же 1500 байт. Сделай MTU=1400 для tapX
« Последнее редактирование: 13 Октября 2009, 11:17:09 от Frank »

sheffv
Спасибо огромное , MTU 1400 очень помогло
- Печать
Страницы: [1] Вверх
Добавил:
Upload
Опубликованный материал нарушает ваши авторские права? Сообщите нам.
Вуз:
Предмет:
Файл:
Jan Just Keijser. OpenVPN 2 Cookbook (2011).pdf
Скачиваний:
163
Добавлен:
18.03.2016
Размер:
10.98 Mб
Скачать
Chapter 12
The client-connect and client-disconnect scripts are very similar to the ones used in the Proxy-ARP recipe from Chapter 2, Client-server IP-only Networks. By using a handy feature of the Linux arp command, we can make the remote clients appear to be part
of the local network.
There’s more…
The topology subnet feature was introduced in OpenVPN 2.1. Without this feature, each client would be handed out a miniature /30 network, which means that each client would use up to four public IP addresses. This made the deployment of handing out public IP addresses to VPN clients very expensive.
See also
Chapter 2‘s recipe Proxy-ARP, which explains in more detail how the Linux/UNIX Proxy-ARP feature works.
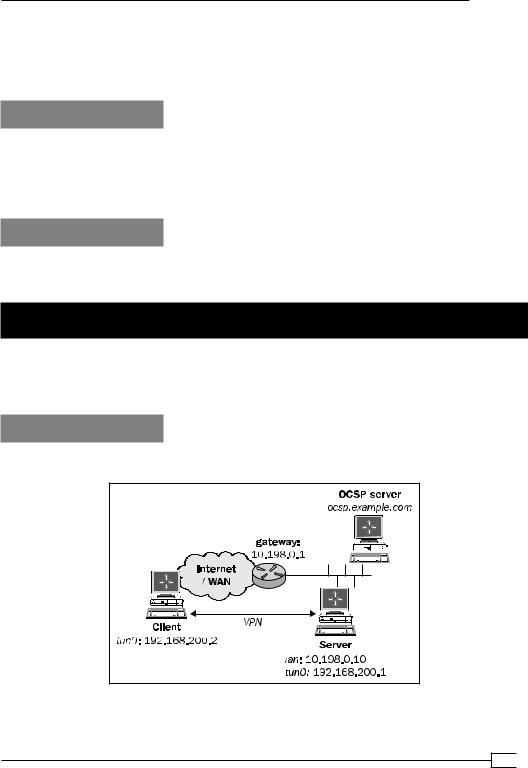
A little known fact—the client certificate’s serial number is present as an environment variable in scripts—allows OpenVPN to support the Online Certificate Status Protocol (OCSP). This recipe will show how OCSP can be set up and be supported by an OpenVPN server.
Getting ready
We use the following network layout:
325

New Features of OpenVPN 2.1 and 2.2
Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. For this recipe, the machine on which the CA certificate and private key are stored is ocsp.example.com. The server computer was running CentOS 5 Linux and OpenVPN 2.1.3. The client was running Windows XP SP3 and OpenVPN 2.1.3. Keep the
configuration file basic-udp-server.conf from the Chapter 2 recipe Server-side routing at hand, as well as the client configuration file, basic-udp-client.ovpn, from the Chapter 2 recipe Using an ‘ifconfig-pool’ block.
How to do it…
1.First, start an OCSP server by re-using the PKI created in Chapter 2, Client-server IP-only Networks. On the machine ocsp.example.com run:
[ocsp]$ cd /etc/openvpn/cookbook
[ocsp]$ openssl ocsp -index keys/index.txt -port 4444
-CA keys/ca.crt -rsigner keys/ca.crt -rkey keys/ca.key -resp_text
2.Then, create the server configuration file by adding a line to the basic-udp-server.conf file:
script-security 2
tls-verify /etc/openvpn/cookbook/example12-6-ocsp.sh
Save it as example12-6-server.conf.
3.Create the tls-verify script:
#!/bin/bash
# if the depth is non-zero , continue processing [ «$1» -ne 0 ] && exit 0
cd /etc/openvpn/cookbook oscp_url=»http://ocsp.example.com:4444″ if [ -n «${tls_serial_0}» ]
then
status=$(openssl ocsp -issuer ca.crt -CAfile ca.crt -url «$ocsp_url»
-serial «0x${tls_serial_0}» 2>/dev/null)
if [ $? -eq 0 ] then
# debug:
echo «OCSP status: $status»

Chapter 12
if echo «$status» | grep -Fq «0x${tls_serial_0}: good» then
exit 0
fi else
# debug:
echo «openssl ocsp command failed!»
fi
fi exit 1
This script is based on the OCSP_verify.sh script that is found in the OpenVPN 2.2 contrib directory. Save it as example12-6-ocsp.sh.
4.Make sure the script is executable, then start the server:
[root@server]# chmod 755 example12-6-ocsp.sh [root@server]# openvpn —config example12-6-server.conf
5.Start the OpenVPN client using the basic-udp-client.ovpn configuration file.
6.Check the log file /var/log/openvpn.log on the OpenVPN server to see the following output:
OCSP status: 0x02: good
And the VPN connection will have been established successfully.
How it works…
Because the client’s certificate serial number is now present as the environment variable tls_serial_0, it becomes possible to support OCSP. By requesting verification with the OCSP server if a certificate is valid (that is, known and neither revoked nor expired) the server can verify that the client has been issued a valid certificate. This could also have been achieved using a Certificate Revocation List (CRL), but in some cases, an OCSP is more convenient to use, as CRLs need to be periodically updated.
See also
Chapter 4‘s recipe The use of CRLs, which explains Certificate Revocation
Lists (CRLs). Using CRLs is the most standard method for verifying the validity of certificates.
327
New Features of OpenVPN 2.1 and 2.2
New for 2.2: the ‘x509_user_name’ parameter
OpenVPN 2.2 is primarily a bug fix release, but there are a few new features added to version
2.2. In this recipe, we will focus on one of these features. The purpose of the x509_user_name parameter is to allow the usage of X509 certificates where the certificate name is not specified by the /CN= element. This can be especially useful when using certificates from a third-party source or when integrating certificates into other authorization systems.
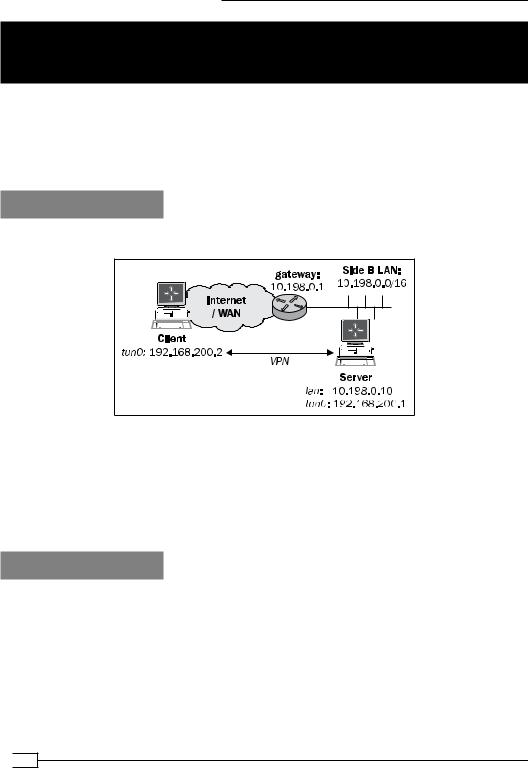
Getting ready
We use the following network layout:
Set up the client and server certificates using the first recipe from Chapter 2, Client-server IP-only Networks. In this recipe, the server computer was running CentOS 5 Linux and OpenVPN 2.2-beta3. The client was running Windows XP SP3 and OpenVPN 2.1.3. Keep the configuration file basic-udp-server.conf from the Chapter 2 recipe Server-side routing at hand, as well as the client configuration file, basic-udp-client.ovpn, from the Chapter 2 recipe Using an ifconfig-pool block.
How to do it…
First, we generate a new certificate using low-level OpenSSL commands. This is because the OpenVPN-supplied easy-rsa scripts do not easily allow us to create a script without a /CN= part.
1.Generate a new certificate request with a special subject name:
[server]$ cd /etc/openvpn/cookbook
[server]$ openssl req -new -nodes -keyout client6.key -out client6.csr -newkey rsa:2048
-subj «/C=NL/O=Cookbook/UID=cookbook»


Chapter 12
2.Create an empty OpenSSL extensions file to ensure that the resulting certificate is an X.509 v3 certificate:
[server]$ touch openssl-ext.conf
3.And finally, sign the certificate request using the CA key:
[server]$ openssl x509 -req -CA keys/ca.crt -CAkey keys/ca.key -in client6.csr -set_serial 0xAA -sha1 -days 1000
-extfile openssl-ext.conf -out client6.crt
4.Create the server configuration file by adding the followings line to the basic-udp-server.conf file:
script-security 2
client-connect /etc/openvpn/cookbook/example12-7-client-connect.sh
x509-username-field «UID»
Save it as example12-7-server.conf.
5.Create the client-connect script:
#!/bin/bash
echo «common_name = [$common_name]»
And, save it as example12-7-client-connect.sh.
6.Make sure the script is executable, then start the server:
[root@server]# chmod 755 example12-7-client-connect.sh [root@server]# openvpn —config example12-7-server.conf
7.Copy the client6.crt and client6.key files to the Windows client using a secure channel; for example, using PuTTY’s pscp command.
8.Modify the client configuration file basic-udp-client.ovpn by changing the lines:
cert /etc/openvpn/cookbook/client2.crt key /etc/openvpn/cookbook/client2.key
to:
cert /etc/openvpn/cookbook/client6.crt key /etc/openvpn/cookbook/client6.key
Save it as example12-7.ovpn.
329
New Features of OpenVPN 2.1 and 2.2
9. Start the OpenVPN client:
10.Check the log file /var/log/openvpn.log on the OpenVPN server to see the following output:
common_name = [cookbook]
How it works…
With the new x509_user_name directive, OpenVPN can extract the connecting client name from a field other than the default /CN= field. In this recipe, the section /UID= was used. When a client connects with a certificate that has a subject section /UID=, the OpenVPN server extracts the client name from this field. This client name is set as the environment variable common_name for most server-side scripts and plugins, such as the client-connect, client-disconnect, and learn-address scripts, as well as the
ifconfig pool persist file.
Note that it is not possible to use just any /<field>=<name> section as part of an X509 certificate. The <field> must be all uppercase and it must be recognized by OpenSSL itself, as otherwise it is not easily possible to generate a certificate.
There’s more…
OpenVPN 2.1 behaviour
If the above certificate was used when connecting to an OpenVPN 2.1 server, the client would not have been able to connect. Instead, the following log message would appear in the server log file:
VERIFY ERROR: could not extract Common Name from X509 subject string (‘/C=NL/O=Cookbook/UID=cookbook’) — note that the Common Name length is limited to 64 characters







