This article relies on the following:
The OpenWrt system logging facility is an important debugging/monitoring capability.
The standard logging facility is implemented using logd, the ubox log daemon.
This is implemented as a ring buffer with fixed sized records stored in RAM.
The ring buffer records can be read using logread on the router, streamed to a file or sent to a remote system through a TCP/UDP socket.
# List syslog logread # Write a message with a tag to syslog logger -t TAG MESSAGE # List syslog filtered by tag logread -e TAG
Usage: logger [OPTIONS] [MESSAGE]
Write MESSAGE (or stdin) to syslog
-s Log to stderr as well as the system log
-t TAG Log using the specified tag (defaults to user name)
-p PRIO Priority (numeric or facility.level pair)
Examples of using priority and tag values:
logger "example" logger -p notice -t example_tag "example notice" logger -p err -t example_tag "example error" # Fri May 8 00:23:26 2020 user.notice root: example # Fri May 8 00:23:31 2020 user.notice example_tag: example notice # Fri May 8 00:23:40 2020 user.err example_tag: example error
The message format differs based on the destination (local logread, local file, remote socket).
Roughly it can be viewed as:
<time stamp> <router name> <subsystem name/pid> <log_prefix>: <message body>
The logging message facility and priority are roughly equivalent to syslog implementations (see linux /usr/include/sys/syslog.h).
The local ‘logread’ executable puts the facility.priority after the time stamp.
Logging to a remote socket puts a numeric value before the time stamp.
For some common OpenWrt messages see log.messages.

logd is configured in /etc/config/system. After changing the file, run
/etc/init.d/log restart /etc/init.d/system restart
to read in the new configuration and restart the service.
There are three basic destinations for log messages: the RAM ring buffer (the default), a local persistent file, a remote destination listening for messages on a TCP or UDP port.
The full set of log_* options for /etc/config/system are defined in
System Configuration
This is the default interface and the simplest.
It is a local executable that will read the ring buffer records and display them chronologically.
In order to log to a local file on the router, one needs to set the following options:
config system ... option log_file '/var/log/mylog' option log_remote '0'
In order to log remotely one needs to set the following options in /etc/config/system
config system ... option log_ip <destination IP> option log_port <destination port> option log_proto <tcp or udp>
For the destination port, if you’ll be manually reading the logs on the remote system as an unprivileged user (such as via the netcat command given below), then specify a high port (e.g. 5555). If you’re sending to a syslog server, use whatever port the syslog server is listening on (typically 514).
Additionally, the firewall3 default is to ACCEPT all LAN traffic. If the router blocks LAN-side access, add the following firewall3 rule to /etc/config/firewall to ACCEPT tcp/udp traffic from the router to the LAN-side.
config rule
option target 'ACCEPT'
option dest 'lan'
option proto 'tcp udp'
option dest_port '5555'
option name 'ACCEPT-LOG-DEVICE-LAN'
and then reload the rules using /etc/init.d/firewall restart.
For the LAN-side station/client, there are a large number of mechanisms to listen for log messages.
One of the simplest is ncat:
# TCP ncat -4 -l 5555 # Read UDP logs with ncat or python3 ncat -u -4 -l 5555 python3 -c "import socket s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) s.bind(('0.0.0.0', 5141)) while True: print(s.recvfrom(4096)[0].decode('utf-8'))"
Log messages are in traditional syslog format (RFC 3164 / 5424), beginning with a priority number in angle brackets (e.g., <30>) and lacking a terminating newline.
The above netcat method will therefore yield somewhat messy output. The python log reader above will most of the time get the line breaks into the right spots. A cleaner solution is to send messages to a remote machine’s syslog daemon, in which case they will appear in the remote system’s logs.
See Receiving Messages from a Remote System for server configuration instructions for rsyslog.
The advantage to using TCP is reliability — it logs every event.
The disadvantage is it can cause some performance degradation on the router if the logging level is high.
There is a section on iptable event logging which can cause a noticable latency in traffic throughput using TCP socket logging.
If you want to test the logging out, just run a command like
logger testLog “Blah1”
and it should be written to the configured destination.
If an event is not logged, check:
* /sbin/logd is running; it should have an argument of -S <log_size> indicating the size of the ring buffer,
* logd is configured correctly in /etc/config/system,
* restart it using /etc/init.d/log restart and check for warnings/errors
See rsyslog — to e.g. rout all or specific logs to a (central) rsyslog receiver
opkg install rsyslog
With the config file: /etc/rsyslog.conf
*.info;mail.none;authpriv.none;cron.none;kern.none /var/log/messages .. kern.* @192.168.1.119:514
rsyslog and Logz.io
You can support logging direct to a cloud ELK provider like Logz.io by adding a few lines to your rsyslog.conf.
Replace codecodecode with your unique Logz.io identifier, it’s 32 characters.
And will appear in help manuals when you’re logged in, reference the guide here.
$template logzFormatFileTagName,"[codecodecodecode] <%pri%>%protocol-version% %timestamp:::date-rfc3339% %HOSTNAME% %app-name% %procid% %msgid% [type=TYPE] %msg%n" *.* @@listener.logz.io:5000;logzFormatFileTagName
Confirm you have the right config with:
rsyslogd -N1
The logging mechanism discussed here uses logd. There are other packages that
provide the same functionality.
See syslog-ng (log.syslog-ng3).

syslog-ng page appears very out-of-date.
In 12.09 The content of the membuffer that syslogd writes to, by default, consists of up to 16 KB utf-8/ASCII encoded characters. Remember this if/when you use logger. To read the content of the membuffer that syslogd writes to, use the logread utility (for kernel messages use dmesg). Let’s have a look at the MESSAGES different program produces: on OpenWrt they all start with the name of the program that send the message plus his PID.
It would be foolish to even try to display and explain all the Log messages the programs used with OpenWrt generate. We need external links.
Feb 4 21:45:43 openwrt user.info dropbear[9815]: Child connection from 192.168.1.1:46247 Feb 4 21:45:43 openwrt user.notice dropbear[9815]: password auth succeeded for 'username' from 192.168.1.1:46247 Feb 5 00:03:34 openwrt user.info dropbear[9815]: exit after auth (username): Exited normally Feb 5 03:13:39 openwrt user.warn dropbear[10221]: bad password attempt for 'root' from 192.168.1.1:51570 Feb 5 03:13:40 openwrt user.warn dropbear[10221]: bad password attempt for 'root' from 192.168.1.1:51570 Feb 5 03:13:42 openwrt user.warn dropbear[10221]: bad password attempt for 'root' from 192.168.1.1:51570 Feb 5 03:13:43 openwrt user.warn dropbear[10221]: bad password attempt for 'root' from 192.168.1.1:51570 Feb 5 03:13:45 openwrt user.warn dropbear[10221]: bad password attempt for 'root' from 192.168.1.1:51570 Feb 5 03:13:48 openwrt user.info dropbear[10221]: exit before auth (user 'root', 5 fails): Disconnect received
As you see, it is possible to try many many passwords. You can put an end to this by configuring dropbear or with netfilter.
You can (and should) read your logs regularly, but of course you can also initiate thing with logs.
Yes, when you have any service running 24/7, you are responsible for it. “I didn’t know” doesn’t really count in court. It is your responsibility to keep yourself informed!
Feb 3 16:04:14 openwrt user.warn kernel: IPT_dsl-Rej IN=pppoe-dsl OUT= MAC= SRC=119.121.32.2 DST=141.70.120.8 LEN=79 TOS=0x00 PREC=0x00 TTL=53 ID=22415 PROTO=UDP SPT=15758 DPT=38565 LEN=59 |
kernel: IPT_dsl-Rej IN=pppoe-dsl OUT= MAC= SRC=222.155.169.237 DST=79.128.154.27 LEN=60 TOS=0x00 PREC=0x40 TTL=46 ID=7247 DF PROTO=TCP SPT=4709 DPT=23 WINDOW=5808 RES=0x00 SYN URGP=0 |
| Part of Message | Meaning |
|---|---|
| kernel: | The kernel send this message. (because netfilter is part of the kernel) remember iptables/ip6tables are only the user space programs to configure netfilter. |
| IPT_dsl-Rej | the string you set with --log-prefix, see configuration |
| IN= | Incoming interface |
| OUT= | Outgoing Interface |
| MAC= | dst and src MACs and something else |
| SRC= | Source IP address |
| DST= | Destination IP address |
| LEN= | Overall length of IP packet in bytes |
| TOS= | the ToS-Flag |
| PREC= | belongs to ToS |
| TTL= | Time-to-live in ms or in hops |
| ID= | |
| DF | Don’t Fragment Flag set |
| PROTO= | transport protocol used TCP UDP etc. |
| SPT= | source port |
| DPT= | destination port |
| LEN= | payload size in bytes |
| WINDOW= | |
| RES= | |
| SYN | SYN flag, see Three-way handshake |
| URGP= |
http://logi.cc/en/2010/07/netfilter-log-format/
Feb 22 14:20:13 openwrt daemon.info pppd[18505]: Plugin rp-pppoe.so loaded. Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: pppd 2.4.4 started by root, uid 0 Feb 22 14:20:13 openwrt daemon.info pppd[18505]: PPP session is 1561 Feb 22 14:20:13 openwrt daemon.info pppd[18505]: Using interface pppoe-dsl Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: Connect: pppoe-dsl <--> eth0.2 Feb 22 14:20:13 openwrt daemon.info pppd[18505]: CHAP authentication succeeded: access accepted : xxxxxxx Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: CHAP authentication succeeded Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: peer from calling number xx:xx:xx:xx:xx:xx authorized Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: local IP address 123.123.123.99 Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: remote IP address 123.123.123.1 Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: primary DNS address 100.150.100.200 Feb 22 14:20:13 openwrt daemon.notice pppd[18505]: secondary DNS address 100.150.100.100 Feb 22 14:20:13 openwrt user.notice ifup: Enabling Router Solicitations on dsl (pppoe-dsl) Feb 22 14:20:15 openwrt user.notice rdate: Synced with ntp0.fau.de --- Feb 22 23:20:11 openwrt daemon.info pppd[18196]: Terminating on signal 15 Feb 22 23:20:11 openwrt daemon.info pppd[18196]: Connect time 1268.2 minutes. Feb 22 23:20:11 openwrt daemon.info pppd[18196]: Sent 62343675 bytes, received 1094463306 bytes. Feb 22 23:20:11 openwrt daemon.notice pppd[18196]: Connection terminated. Feb 22 23:20:12 openwrt daemon.info pppd[18196]: Exit.
NOTE: You can make pppd verbose with setting option pppd_options debug in your /etc/config/network, see network. With uci commit network and then restart pppd (ifdown pppoe-dsl does NOT restart the daemon, you can achieve that with ???)
Feb 4 20:07:59 openwrt daemon.info dnsmasq-dhcp[1026]: DHCPREQUEST(eth0.1) 192.168.1.1 xx:xx:xx:xx:xx:xx Feb 4 20:07:59 openwrt daemon.info dnsmasq-dhcp[1026]: DHCPACK(eth0.1) 192.168.1.1 xx:xx:xx:xx:xx:xx wonderwoman Feb 4 21:16:20 openwrt daemon.info dnsmasq-dhcp[1026]: DHCPREQUEST(eth0.1) 192.168.1.1 xx:xx:xx:xx:xx:xx Feb 4 21:16:20 openwrt daemon.info dnsmasq-dhcp[1026]: DHCPACK(eth0.1) 192.168.3.1 xx:xx:xx:xx:xx:xx superman
Отправка логов с OpenWRT/LEDE в syslog и обработка событий
2019-01-13 02:31:22 —
Evgeniy Shumilov

Настройка роутера
Есть два пути настройки — через веб интерфейс и через консоль. Первый прост как угол дома. Авторизуемся на роутере, переходим в раздел System -> System и прописываем путь к нашему syslog серверу во вкладке Logging. В принципе, этого достаточно, но тут возникает одна проблема — нам необходимо некое ключевое слово, по которому мы будем фильтровать логи, приходящие именно с OpenWRT таким же образом, как было сделано ранее для докер контейнеров с опцией логирования tag, но в веб интерфейсе такой опции нет, поэтому придётся настраивать через консоль, благо, это не намного сложнее. Заходим на роутер по ssh и редактируем конфигурационный файл system:
vim /etc/config/system
В раздел system нам нужно добавить следующие параметры:
option log_proto 'udp'
option log_ip '10.11.11.4'
option log_prefix 'OpenWRT-Routers'
option conloglevel '7'
option cronloglevel '7'
Если вы не сильны в vi/vim (выход c записью через Esc, затем ввод :wq), есть и другой способ:
uci set system.@system[0].log_proto='udp' uci set system.@system[0].log_ip='10.11.11.4' uci set system.@system[0].log_prefix='OpenWRT-Routers' uci set system.@system[0].conloglevel='7' uci set system.@system[0].cronloglevel='7'
После изменения настроек, чтобы они вступили в силу, нужно выполнить
/etc/init.d/log restart
В официальной документации так же было написано о необходимости затем выплонить
/etc/init.d/system restart
Но у меня прекрасно заработало и без этого. Для сохранения настроек во флешпамять, выполняем
uci commit
В описанных выше настройках log_prefix как раз отвечает за то, что будет приходить на наш syslog в поле PROGRAM, что очень удобно для фильтрации. 10.11.11.4 — это адрес моего syslog-ng сервера, у вас он скорее всего будет другим. conloglevel и cronloglevel — это уровни фильтрации для ядра и тех процессов, которые запускаются из cron. Самый низкий — нулевой, самый высокий — восьмой.
Настройка syslog-ng
Теперь можно заглянуть в логи контейнера syslog-ng. Мы должны увидеть примерно такую запись:
[2019-01-05T10:04:20.894114] Incoming log entry; line='Jan 5 15:04:20 gw01 OpenWRT-Routers: logread[32051]: Logread connected to 10.11.11.4:514' [2019-01-05T10:04:20.894234] Setting value; msg='0x55e2eb847c00', name='HOST_FROM', value='gw01.lan' [2019-01-05T10:04:20.894270] Setting value; msg='0x55e2eb847c00', name='SOURCE', value='src_net'
Как мы видим, logd на роутере успешно подключился к нашему syslog-ng. Теперь напишем конфигурационный файл. Для удобства Будем складывать логи в директорию logs/network/%hostname%.
filter f_openwrt {
match("OpenWRT-Routers" value("PROGRAM"));
};
destination dst_openwrt {
file( "/logs/network/${HOST}/$YEAR-$MONTH-$DAY.log" template("$ISODATE $LEVEL $MSGn") );
};
log {
source(src_net);
filter(f_openwrt);
destination(dst_openwrt);
};
И перезагрузим специально предназначенным для этого скриптом
scripts/reload
В консоли роутера можем проверить отправку логов при помощи команды
logger test123
Можем убедиться, что всё работает.
$ tail -n 1 logs/network/gw01/2019-01-05.log 2019-01-05T20:56:52+00:00 notice root: test123
Реакция на события
А теперь сделаем кое-что поинтереснее — заставим syslog-ng реагировать на какой-нибудь скрипт. Скрипт в свою очередь должен постоянно слушать stdin, иначе вас завалит сообщениями вида
syslog-ng[2673]: POLLERR occurred while idle; fd='12'
В качестве примера будем дёргать http запросы в момент, когда в логах приходит нужная запись. К url будем добавлять последнее слово из входящей записи. Содержимое scripts/testscripts:
#!/bin/sh
while read line; do
echo "$line" | sed 's#^.* #wget -q -O - http://10.11.11.224:8000/#' | sh
done < /dev/stdinНа хосте 10.11.11.224:8000 я подниму тестовый веб сервер. И пусть он отдаёт 404-ю ошибку, но в логах мы будем видеть обращения — это именно то, что нам нужно.
$ python -m SimpleHTTPServer Serving HTTP on 0.0.0.0 port 8000 ...
Далее нам нужен конфигурационный файл для syslog-ng:
filter f_openwrttest {
match("test123" value("MESSAGE")) and match("OpenWRT-Routers" value("PROGRAM"));
};
destination dst_openwrttest {
program("/scripts/testscript");
};
log {
source(src_net);
filter(f_openwrttest);
destination(dst_openwrttest);
};
Теперь возвращаемся к консоли любого из роутеров и выполняем:
$ logger test12345 $ logger test123456
И в логах веб сервера видим следующее:
[06/Jan/2019 00:48:04] code 404, message File not found 10.11.11.4 - - [06/Jan/2019 00:48:04] "GET /test12345 HTTP/1.1" 404 - 10.11.11.4 - - [06/Jan/2019 00:48:06] code 404, message File not found 10.11.11.4 - - [06/Jan/2019 00:48:06] "GET /test123456 HTTP/1.1" 404 -
Таким образом мы можем вызывать внешние апи. Например, я могу по наступлению какого-нибудь события, (скажем, разрыва VPN соединения) отправить на ближайшую свою управляемую розетку мелодию главной темы из «Семейства Аддамс» в формате RTTTL, или отправить событие в систему мониторинга, но об этом я напишу как-нибудь в другой раз.
Ещё я только что добавил к образу две полезных фичи — сжатие и очистку старых логов. Так как ротацией syslog-ng замечательно занимается сам, то очистка и компрессия никакой сложности для реализации не представляют. Я сделал следующим образом — entrypoint при старте запускает в фоновом режиме скрипт scripts/cleaner, который в свою очередь ищет в директории с логами файлы с именем .clean со следующим содержимым:
archive=7 clean=60
Для данного примера все файлы (кроме самого файла .clean конечно) старше 60-ти дней будут удалены в той же директории и всех поддиректориях. Оставшиеся файлы (кроме того же .clean и файлов с расширением bz2 будут сжаты с помощью bzip2. Скрипт по умолчанию запускается каждые 2 часа.
Репозиторий лежит всё там же: https://github.com/alive-corpse/es-syslog-ng
Теги: админское, docker, logging
Update 2020-07-09: With the latest 19.07.3, syslog-ng is no longer the preferred option. Instead, read my other article on using rsyslog with OpenWRT.
Update 2014-10-08: If you upgraded to the stable Barrier Breaker 14.07, and Syslog-NG is not available, or if don’t want to use Syslog-NG for any other reason, please check our other article on using the built in logging feature of OpenWRT to write the log to a file.
We wrote earlier on OpenWRT on D-Link DIR-835. Now, we need to expand the functionality a bit more.
On OpenWRT, the default logging mechanism is an in-memory circular buffer. The user interface for it is the logread command. The log buffer default size is 16 kB. There are a couple of directives that can be set in the system configuration for OpenWRT, but because of the limited size of flash and the non-permanence of RAM, you need another solution if you want to store logs for anything longer than a day or two.
Syslog-NG
Syslog-NG is a good system logging program that is available for OpenWRT.
To install syslog-ng, enter the following command from ssh:
Install the packages:
opkg update
opkg install syslog-ng3Make syslog start automatically on boot:
/etc/init.d/syslog-ng enableConfiguration for Syslog-NG
The configuration for syslog-ng goes in to the file /etc/syslog-ng.conf.
The following configuration logs a monthly file to the USB drive, and also excludes a couple of repetitive messages. It also avoid the annoying «—MARK—» entries that just eat up space.
Adjust the configuration to your needs:
@version:3.0options {
chain_hostnames(no);
create_dirs(yes);
flush_lines(0);
keep_hostname(yes);
log_fifo_size(256);
log_msg_size(8192);
stats_freq(0);
flush_lines(0);
use_fqdn(no);
# Do not add "--MARK--" entries to the log
mark_freq(0);
};
source local {
internal();
unix-stream("/dev/log");
};
source net {
udp(ip(0.0.0.0) port(514));
};
source kernel {
file("/proc/kmsg" program_override("kernel"));
};
destination logfile {
# Log to a file on the USB filesystem, and a new file every month
file("/mnt/usb/logs/syslog-$YEAR-$MONTH.log");
};
# This filter is used to exclude excessive noise in the logs
filter f_not_noise {
# This is a warning from odhcpd about routing
not message("there is no public prefix")
and
# This is cron executing the bandwidth monitor script every minute,
# so we just exclude them too
not message("cmd /mnt/usb/wrtbwmon/wrtbwmon ")
;
};
log {
source(local);
source(net);
source(kernel);
filter(f_not_noise);
destination(logfile);
};
Start syslog-ng
Finally, start the syslog-ng program
/etc/init.d/syslog-ng enableNote that any changes you make to syslog-ng’s configuration followed by the command:
/etc/init.d/syslog-ng restartwill not take effect immediately. To solve this, use the following command instead:
killall syslog-ng
/etc/init.d/syslog-ng startAdjust the startup order
By default, Sylog-NG takes a startup number of 50, that is the init.d script is linked to /etc/rc.d/S50syslog-ng. This can cause some processes that start before syslog-ng to log to the old logging mechanism rather than syslog-ng.
To solve this, check the startup order using the following command:
Then change the startup order of syslog-ng to be just after the original logging mechanism.
mv /etc/rc.d/S50syslog-ng /etc/rc.d/S12syslog-ngThen check the order again:
You should see syslog-ng right after S12log.
... /etc/rc.d/S12log -> ../init.d/log
... /etc/rc.d/S12syslog-ng -> ../init.d/syslog-ngA typical day’s worth of logs is around 750 kB, so even a 1GB USB drive should last for a very long time. You can check intrusion attempts or unauthorized connections to WiFi months after they happen.
Further Reading
- Logging on OpenWRT
- OpenWRT Basic Log Support
- Syslog-NG on OpenWRT
When debugging OpenWRT network components and user software, the system problems need to be solved through the analysis of log information; Product online quality tracking also requires log information to analyze product bugs, so the use of system logs is very important. This article records the process of OpenWRT-19.07 log opening and log automatic reporting to the server.
1. Operating environment description
- The server side adopts the rsyslog component automatically installed by ubuntu-16.04 system;
- Porting syslog components to openwrt-19.07 system;
- The client uses mtk7621 router.
2. Server ubuntu16 system rsyslog parameter configuration
2.1 parameter configuration file of rsyslog, etc / rsyslog conf
# /etc/rsyslog.conf Configuration file for rsyslog. # # For more information see # /usr/share/doc/rsyslog-doc/html/rsyslog_conf.html # # Default logging rules can be found in /etc/rsyslog.d/50-default.conf module(load="imuxsock") # provides support for local system logging module(load="imklog") # provides kernel logging support #module(load="immark") # provides --MARK-- message capability # provides UDP syslog reception module(load="imudp") input(type="imudp" port="514") # Open the udp listening port on the server # provides TCP syslog reception module(load="imtcp") input(type="imtcp" port="514") # Open the server tcp listening port # Enable non-kernel facility klog messages $KLogPermitNonKernelFacility on ########################### #### GLOBAL DIRECTIVES #### ########################### # # Use traditional timestamp format. # To enable high precision timestamps, comment out the following line. # $ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat # Filter duplicated messages $RepeatedMsgReduction on # # Set the default permissions for all log files. # $FileOwner syslog $FileGroup adm $FileCreateMode 0640 $DirCreateMode 0755 $Umask 0022 $PrivDropToUser syslog $PrivDropToGroup syslog # # Where to place spool and state files # $WorkDirectory /var/spool/rsyslog # Storage path of log content received by the server # # Include all config files in /etc/rsyslog.d/ # $IncludeConfig /etc/rsyslog.d/*.conf # The path of rsyslog configuration file set. Users can supplement custom log storage, packaging and deletion rules
2.2 configuring log file storage rules
In / etc / rsyslog D / new router Conf configuration file, which configures the file name of the receiving log file, as follows:
root@ubuntu:/# cat /etc/rsyslog.d/router.conf # :FROMHOST-IP,startswith, "192.168.90." /var/spool/rsyslog/%fromhost-ip%-%HOSTNAME%-%$YEAR%-%$MONTH%-%$DAY%.log :fromhost-ip,isequal,"192.168.1.1" /var/spool/rsyslog/%fromhost-ip%-%HOSTNAME%-%$YEAR%-%$MONTH%-%$DAY%.log &~ #Indicates that the receiving log does not need to be written to the local log file
2.3 restart rsyslog service and detect the service startup status
sudo service rsyslog restart
sudo netstat -tulpn | grep rsyslog
root@ubuntu:/# netstat -tulpn|grep rsyslog tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 8778/rsyslogd tcp6 0 0 :::514 :::* LISTEN 8778/rsyslogd udp 0 0 0.0.0.0:514 0.0.0.0:* 8778/rsyslogd udp6 0 0 :::514 :::* 8778/rsyslogd
3. syslog migration and parameter configuration of client OpenWRT system
3.1 configuring syslog components
make menuconfig select the syslog component, as shown in
Base system
busybox… Core utilities for embedded Linux
System Logging Utilities
Select content
[*] syslogd (13 kb) │ │ [*] Rotate message files │ │ [*] Remote Log support │ │ [*] Support -D (drop dups) option │ │ [*] Support syslog.conf │ │ (256) Read buffer size in bytes │ │ [*] Circular Buffer support │ │ (4) Circular buffer size in Kbytes (minimum 4KB) │ │ [*] Linux kernel printk buffer support
Compile and write to mtk7621 router.
3.2 enable router log
- The first method is to configure the parameters of syslog through uci set command. The contents are as follows:
Example: uci set system.system.log_file=/tmp/syslog
The configured contents are as follows:
config system option hostname 'OpenWrt' option ttylogin '0' option log_size '64' option urandom_seed '0' # The following are syslog configuration parameters option log_ip '192.168.90.180' #Server side address of log reporting option log_file '/tmp/syslog' #Local log file storage location option conloglevel '7' option cronloglevel '8' option log_proto 'udp' #udp communication is adopted for reporting # The following time zone configuration information option zonename 'Asia/Shanghai' option timezone 'CST-8'
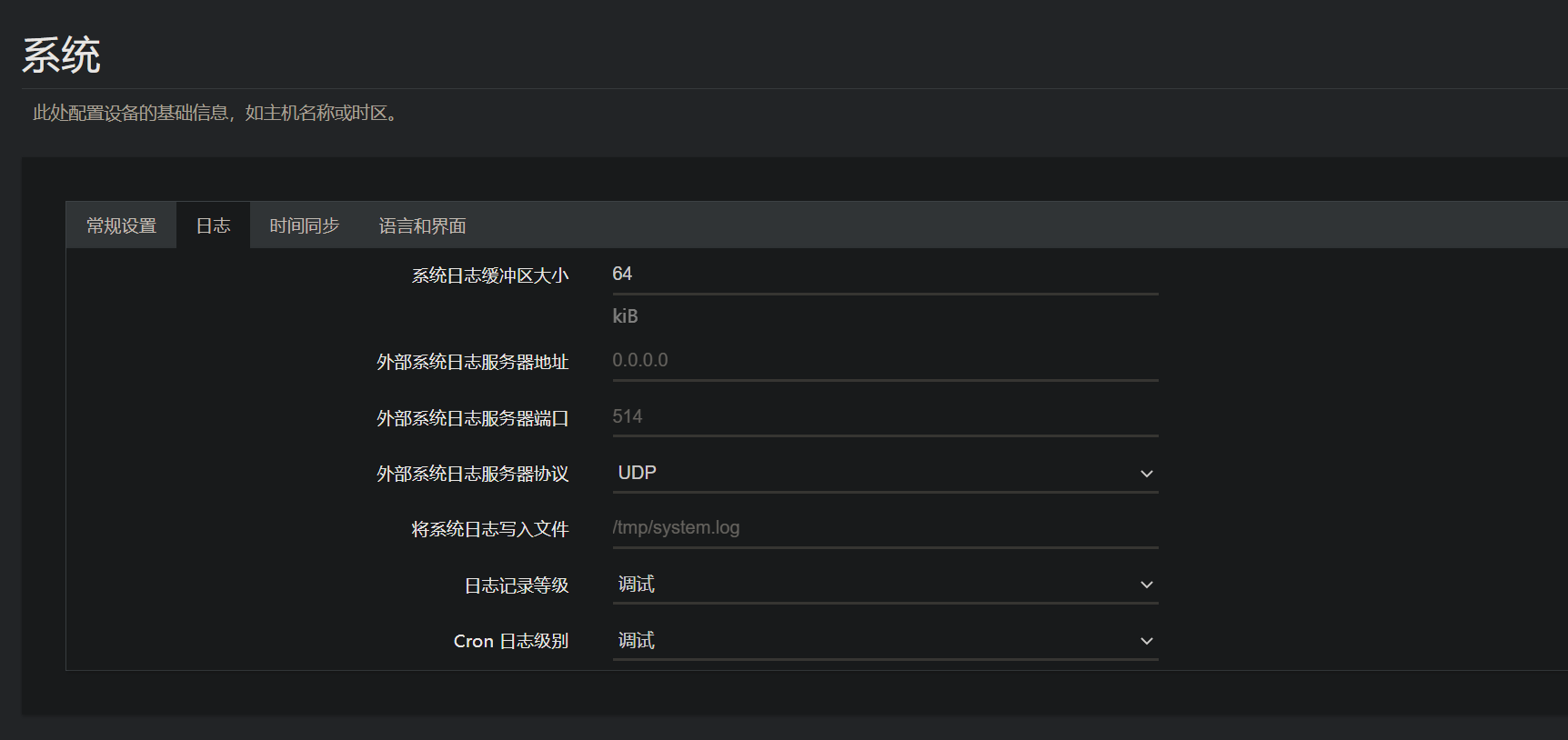
- The second method: configure through the WEB management interface of openWRT
After logging into the configuration interface, the configuration page path is: System — > System — > log.
4. Verify the client syslog local log
View local log files root@eCloud:~# cat /tmp/syslog, as follows:
Thu Jun 17 08:10:47 2021 daemon.info logread[10237]: Logread connected to 192.168.90.180:514 Thu Jun 17 08:12:27 2021 daemon.warn zabbix_agentd[17566]: active check configuration update from [172.16.29.171:10051] started to fail (ZBX_TCP_READ() timed out) Thu Jun 17 08:13:14 2021 daemon.err uhttpd[4723]: luci: accepted login on / for root from 192.168.90.29 Thu Jun 17 08:13:27 2021 daemon.warn zabbix_agentd[17566]: active check configuration update from [172.16.29.171:10051] is working again Thu Jun 17 08:16:00 2021 daemon.err netdata[6426]: PROCFILE: Cannot open file '/proc/sysvipc/shm' Thu Jun 17 08:16:42 2021 daemon.info dnsmasq[3711]: read /etc/hosts - 4 addresses Thu Jun 17 08:16:42 2021 daemon.info dnsmasq[3711]: read /tmp/hosts/odhcpd - 0 addresses Thu Jun 17 08:16:42 2021 daemon.info dnsmasq[3711]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses Thu Jun 17 08:16:42 2021 daemon.err netdata[6426]: PROCFILE: Cannot open file '/proc/sysvipc/shm'
This log is the local log content of OpenWRT virtual machine. The log shows that the ZABBIX client failed to start because the file cannot open ‘/ proc/sysvipc/shm’.
5. Verify the contents of the server-side rsyslog remote log
View the remote report log on the server side, root@ubuntu:/# cat var/spool/rsyslog/r-network.log |head -n 80
The contents are as follows:
Jun 17 06:33:22 ixe pppd[23653]: sent [LCP EchoRep id=0x83 magic=0xffaaa8e9] Jun 17 06:33:31 ixe dnsmasq[4030]: read /etc/hosts - 4 addresses Jun 17 06:33:31 ixe dnsmasq[4030]: read /tmp/hosts/odhcpd - 1 addresses Jun 17 06:33:31 ixe dnsmasq[4030]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses Jun 17 06:33:31 ixe dnsmasq-dhcp[4030]: read /etc/ethers - 0 addresses Jun 17 14:33:52 ixe pppd[23653]: rcvd [LCP EchoReq id=0x84 magic=0x6cf92d34] Jun 17 14:33:52 ixe pppd[23653]: sent [LCP EchoRep id=0x84 magic=0xffaaa8e9] Jun 17 14:34:09 ixe pppd[23653]: Terminating on signal 15 Jun 17 14:34:09 ixe pppd[23653]: Connect time 194.1 minutes. Jun 17 14:34:09 ixe pppd[23653]: Sent 152 bytes, received 0 bytes. Jun 17 14:34:09 ixe pppd[23653]: MPPE disabled Jun 17 14:34:09 ixe pppd[23653]: Overriding mtu 1500 to 1400 Jun 17 14:34:09 ixe pppd[23653]: PPPoL2TP options: debugmask 0 Jun 17 14:34:09 ixe pppd[23653]: Overriding mru 1500 to mtu value 1400 Jun 17 14:34:09 ixe pppd[23653]: sent [LCP TermReq id=0x4 "MPPE disabled"] Jun 17 14:34:09 ixe pppd[23653]: Overriding mtu 1500 to 1400 Jun 17 14:34:09 ixe pppd[23653]: PPPoL2TP options: debugmask 0 Jun 17 14:34:09 ixe pppd[23653]: Overriding mru 1500 to mtu value 1400 Jun 17 14:34:09 ixe pppd[23653]: sent [LCP TermReq id=0x5 "MPPE disabled"] Jun 17 14:34:12 ixe pppd[23653]: sent [LCP TermReq id=0x6 "MPPE disabled"] Jun 17 14:34:12 ixe pppd[23653]: Connection terminated. Jun 17 14:34:12 ixe pppd[23653]: Modem hangup Jun 17 14:34:12 ixe pppd[23653]: Exit. Jun 17 14:34:33 ixe pppd[27050]: Plugin pppol2tp.so loaded. Jun 17 14:34:33 ixe pppd[27050]: pppd 2.4.7 started by root, uid 0 Jun 17 14:34:33 ixe pppd[27050]: using channel 3 Jun 17 14:34:33 ixe pppd[27050]: Using interface ppp0 Jun 17 14:34:33 ixe pppd[27050]: Connect: ppp0 <--> Jun 17 14:34:33 ixe pppd[27050]: Overriding mtu 1500 to 1400 Jun 17 14:34:33 ixe pppd[27050]: PPPoL2TP options: debugmask 0 Jun 17 14:34:33 ixe pppd[27050]: Overriding mru 1500 to mtu value 1400 Jun 17 14:34:33 ixe pppd[27050]: sent [LCP ConfReq id=0x1 <mru 1400> <asyncmap 0x0> <magic 0x7d73ba8d>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [LCP ConfReq id=0x1 <auth chap MS-v2> <mru 1450> <magic 0xfb92c32>] Jun 17 14:34:33 ixe pppd[27050]: sent [LCP ConfAck id=0x1 <auth chap MS-v2> <mru 1450> <magic 0xfb92c32>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [LCP ConfRej id=0x1 <asyncmap 0x0>] Jun 17 14:34:33 ixe pppd[27050]: sent [LCP ConfReq id=0x2 <mru 1400> <magic 0x7d73ba8d>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [LCP ConfAck id=0x2 <mru 1400> <magic 0x7d73ba8d>] Jun 17 14:34:33 ixe pppd[27050]: PPPoL2TP options: debugmask 0 Jun 17 14:34:33 ixe pppd[27050]: rcvd [CHAP Challenge id=0x1 <5570fcc24838fe7fa186d6a7f2688529>, name = "CHR-GZ-DY-Router003-MGT-1"] Jun 17 14:34:33 ixe pppd[27050]: added response cache entry 0 Jun 17 14:34:33 ixe pppd[27050]: sent [CHAP Response id=0x1 <ea6f73fb3f10a92293b903f0b9ad13d40000000000000000f31a83726597822671b76789c9079504f9d054bf654db79b00>, name = "test02"] Jun 17 14:34:33 ixe pppd[27050]: rcvd [CHAP Success id=0x1 "S=9DCD53371E49AE8C63FEF51C461FCD90329C8978"] Jun 17 14:34:33 ixe pppd[27050]: response found in cache (entry 0) Jun 17 14:34:33 ixe pppd[27050]: CHAP authentication succeeded Jun 17 14:34:33 ixe pppd[27050]: sent [IPCP ConfReq id=0x1 <addr 0.0.0.0>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [CCP ConfReq id=0x1 <mppe +H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: sent [CCP ConfReq id=0x1 <mppe -H -M -S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: sent [CCP ConfNak id=0x1 <mppe -H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [proto=0x8281] 01 01 00 04 Jun 17 14:34:33 ixe pppd[27050]: Unsupported protocol 0x8281 received #There are unsupported protocols here Jun 17 14:34:33 ixe pppd[27050]: sent [LCP ProtRej id=0x3 82 81 01 01 00 04] Jun 17 14:34:33 ixe pppd[27050]: rcvd [IPCP ConfReq id=0x1 <addr 172.20.156.1>] Jun 17 14:34:33 ixe pppd[27050]: sent [IPCP ConfAck id=0x1 <addr 172.20.156.1>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [IPCP ConfNak id=0x1 <addr 172.20.156.3>] Jun 17 14:34:33 ixe pppd[27050]: sent [IPCP ConfReq id=0x2 <addr 172.20.156.3>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [CCP ConfNak id=0x1 <mppe +H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: sent [CCP ConfReq id=0x2 <mppe +H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [CCP ConfReq id=0x2 <mppe -H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: sent [CCP ConfAck id=0x2 <mppe -H -M +S -L -D -C>] Jun 17 14:34:33 ixe pppd[27050]: rcvd [IPCP ConfAck id=0x2 <addr 172.20.156.3>] Jun 17 14:34:33 ixe pppd[27050]: local IP address 172.20.156.3 Jun 17 14:34:33 ixe pppd[27050]: remote IP address 172.20.156.1
Log information includes l2tp link and heartbeat message; And have unsupported protocols.
Improve the remote reporting of logs after Internet NAT
Through the log file, we can quickly find the problems existing in the system operation and improve the efficiency of finding problems. At present, there are still some problems in the system operation in the rsyslog configuration.
Question 1 The configuration log file name generation rule is incorrect
As follows:
root@ubuntu:/# ls var/spool/rsyslog/ %fromhost-ip%-%HOSTNAME%-%$YEAR%-%$MONTH%-%$DAY%.log r-network.log
The file name here does not get the client ip address and date information.
Problem 2: the device reports via the Internet, and the naming rules of log files
If the device is connected to the cloud server through the Internet, the device address passes through the NAT address, and the factory settings of the host name are the same; How to distinguish the log information of different devices? This problem will be solved later.
If you have any good methods, please leave a message, thank you.
LUCI native debug interface is not very comfortable, searching for the following debugging method online.
Save the following LUA code as log.lua, then placed in / usr / lib / lua / luci, you can call any directory of LuCI
local M = {}
local tconcat = table.concat
local tinsert = table.insert
local srep = string.rep
local function local_print(str)
local dbg = io.open("/tmp/luci.output", "a+")
local str = str or ""
if dbg then
dbg:write(str..'n')
dbg:close()
end
end
function M.print(...)
local dbg = io.open("/tmp/luci.output", "a+")
if dbg then
dbg:write(os.date("[%H:%M:%S]: "))
for _, o in ipairs({...}) do
dbg:write(tostring(o)..' ')
end
dbg:write("n")
dbg:close()
end
end
function M.print_r(data, depth)
local depth = depth or 3
local cstring = "";
local top_flag = true
local function table_len(t)
local i = 0
for k, v in pairs(t) do
i = i + 1
end
return i
end
local function tableprint(data,cstring, local_depth)
if data == nil then
local_print("core.print data is nil");
end
local cs = cstring .. " ";
if top_flag then
local_print(cstring .."{");
top_flag = false
end
if(type(data)=="table") then
for k, v in pairs(data) do
if type(v) ~= "table" then
if type(v) == "string" then
local_print(cs..tostring(k).." = ".."'"..tostring(v).."'");
else
local_print(cs..tostring(k).." = "..tostring(v));
end
elseif table_len(v) == 0 then
local_print(cs..tostring(k).." = ".."{}")
elseif local_depth < depth then
local_print(cs..tostring(k).." = {");
tableprint(v,cs,local_depth+1);
else
local_print(cs..tostring(k).." = ".."{*}")
end
end
else
local_print(cs..tostring(data));
end
local_print(cstring .."}");
end
tableprint(data,cstring,0);
end
return M
Call method:
- as an example of just code block
local password
- Import log module
local log = require "luci.log"
- Get incoming data
password = luci.http.formvalue('password')
- Print log
log.print(password)
log.print_r(password)
Use TAIL -F trace log output file with tail -f/tmp/luci.output
tail -f /tmp/luci.output
Transferred fromhttps://blog.csdn.net/bailyzheng/article/details/48663369