- Remove From My Forums
-
Question
-
Emails from Office 365 are being rejected by yahoo.com
When Office 365 tried to send your message, the receiving email server outside Office 365 reported an error.
sarah
Office 365
vreken
Sender
Action Required
[if gte mso 15]> <![endif]
[if gte mso 15]> <![endif]
[if gte mso 15]> <![endif]
[if gte mso 15]> <![endif]
[if gte mso 15]> <![endif]
Policy violation or system error
How to Fix It
Check the «Reported Error» from the «Error Details» section shown below for more information about the problem. The error might tell you what went wrong and how to fix it. For example, if the error states that the message was blocked
due to a potential virus or because the message was too large, try sending the message again without attachments.If you’re not able to fix the problem, it’s likely that only the recipient’s email admin can fix it. Contact the recipient by some other means (by phone, for example) and ask them to tell their email admin about the problem. Give them the «Reported
Error» from the «Error Details» section below.
Answers
-
Hi,
There are many reasons an email can be returned. The «How to Fix It» section already provides the general troubleshooting steps for this kind of issue.
As mentioned, you will first need to check the «Reported Error» from the «Error Details» section in the bounce-back message for more information about the problem.
If you can’t fix the problem, contact the responsible party’s email admin for further action.
Please feel free to post back with any findings.
Regards,
Ethan Hua
Please remember to mark the replies as answers if they help, and unmark the answers if they provide no help. If you have feedback for TechNet Support, contact
tnmff@microsoft.com-
Edited by
Wednesday, July 6, 2016 8:40 AM
-
Proposed as answer by
Ethan HuaMicrosoft contingent staff
Thursday, July 14, 2016 9:09 AM -
Marked as answer by
Ethan HuaMicrosoft contingent staff
Monday, August 8, 2016 1:43 AM
-
Edited by
I am thinking the receiver is the issue what do you guys think ?
I can;t see my domain name which is not boats.com.au on any blacklists.
Your
message to couldn’t be delivered.
When
Office 365 tried to riette@palplans.com.au send your message, the receiving email server outside
Office 365 reported an error.
|
maria |
Office |
henriette |
|||
|
Sender |
Action |
||||
|
|
|||||
|
Policy |
|
How |
|
Check |
|
If |
Was this helpful? Send feedback to
Microsoft.
More Info for Email Admins
Status code: 550
5.0.350
The error reported by the receiving server wasn’t specific enough to
determine the exact nature of the problem. These errors often indicate the
message violates a security or policy setting configured on the recipient’s
email servers.
If the sender is unable to fix the problem by modifying their message, then
it’s likely a problem that only the recipient’s email admin can fix. Try the
following:
Check the error for information about the problem — The «Reported
Error» returned by the external email server can be found in the
«Error Details» section below. This error might tell you what went
wrong and provide clues for how to fix it. For example, if the error states
the message was rejected due a Sender Policy Framework (SPF) issue, then
you’ll have to work with your domain registrar to correctly configure your
domain’s SPF records.
Check the error for information about where the problem is happening —
For example, look for a domain name like contoso.com. A domain name in the
error might suggest who is responsible for the error. It could be the
recipient’s email server, or it could be a third-party service that your
organization or the recipient’s organization is using to process or filter
email messages.
If you can’t fix the problem, contact the responsible party’s email admin
— Give them the error code and error message from this non-delivery
report (NDR) to help them troubleshoot the issue. For security or policy
violation issues, it might be sufficient for them to just add your sending IP
addresses or domain to their allowed senders list.
It’s likely that only the recipient’s email admin can fix the problem.
Unfortunately, it’s unlikely Office 365 Support will be able to help with
these kinds of externally reported errors.
Original Message Details
Error Details
|
Reported |
550 |
|
DSN |
SYXPR01MB1264.ausprd01.prod.outlook.com |
|
Remote |
vmse04.mailcluster.com.au |
From: Microsoft Outlook
Sent: Monday, 20 February 2017 6:14 PM
To: Søren Sørensen
Subject: Undeliverable: RE: Major stock blowout
Your message couldn’t be delivered to the recipients shown below.
When Office 365 tried to send your message, the receiving email server outside Office 365 reported an error.
sjs Office 365 Multiple recipients
Sender Action Required
Policy violation or system error
Couldn’t deliver the message to the following recipients:
Dhruv.Pandya@axieo.com, Dominic.Happe@Axieo.com, Roberto.Pita@Axieo.com
How to Fix It
Check the «Reported Error» from the «Error Details» section shown below for more information about the problem. The error might tell you what went wrong and how to fix it. For example, if the error states that the message was blocked due to a potential virus or because the message was too large, try sending the message again without attachments.
If you’re not able to fix the problem, it’s likely that only the recipient’s email admin can fix it. Contact the recipient by some other means (by phone, for example) and ask them to tell their email admin about the problem. Give them the «Reported Error» from the «Error Details» section below.
Was this helpful? Send feedback to Microsoft.
________________________________________
More Info for Email Admins
Status code: 550 5.0.350
The error reported by the receiving server wasn’t specific enough to determine the exact nature of the problem. These errors often indicate the message violates a security or policy setting configured on the recipient’s email servers.
If the sender is unable to fix the problem by modifying their message, then it’s likely a problem that only the recipient’s email admin can fix. Try the following:
Check the error for information about the problem — The «Reported Error» returned by the external email server can be found in the «Error Details» section below. This error might tell you what went wrong and provide clues for how to fix it. For example, if the error states the message was rejected due a Sender Policy Framework (SPF) issue, then you’ll have to work with your domain registrar to correctly configure your domain’s SPF records.
Check the error for information about where the problem is happening — For example, look for a domain name like contoso.com. A domain name in the error might suggest who is responsible for the error. It could be the recipient’s email server, or it could be a third-party service that your organization or the recipient’s organization is using to process or filter email messages.
If you can’t fix the problem, contact the responsible party’s email admin — Give them the error code and error message from this non-delivery report (NDR) to help them troubleshoot the issue. For security or policy violation issues, it might be sufficient for them to just add your sending IP addresses or domain to their allowed senders list.
It’s likely that only the recipient’s email admin can fix the problem. Unfortunately, it’s unlikely Office 365 Support will be able to help with these kinds of externally reported errors.
Original Message Details
Created Date: 20/02/2017 7:13:44 AM
Sender Address: sjs@targit.com.au
Recipient Address: Dhruv.Pandya@axieo.com, Dominic.Happe@Axieo.com, . . .
Subject: RE: Major stock blowout
Error Details
Reported error: 550 5.0.350 Remote server returned an error -> 553 Message filtered. Refer to the Troubleshooting page at;http://www.symanteccloud.com/troubleshooting for more;information. (#5.7.1)
DSN generated by: SY3PR01MB1148.ausprd01.prod.outlook.com
Remote server: server-7.tower-192.messagelabs.com
Message Hops
HOP TIME (UTC) FROM TO WITH RELAY TIME
1 20/02/2017
7:13:44 AM SY3PR01MB1148.ausprd01.prod.outlook.com SY3PR01MB1148.ausprd01.prod.outlook.com mapi *
2 20/02/2017
7:13:44 AM SY3PR01MB1148.ausprd01.prod.outlook.com SY3PR01MB1148.ausprd01.prod.outlook.com Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) *
Original Message Headers
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=TARGITAustralia.onmicrosoft.com; s=selector1-targit-com-au;
h=From:Date:Subject:Message-ID:Content-Type:MIME-Version;
bh=leyBuaUI0BHf9cMAyuiMr4aTGersAHGyHtD3vpmL9Zs=;
b=TH+dbpr2IIu/sSKeNPUG8N0rptYss0szkqyTfdpAg7ndbJUVTLk813UAKfGl2h32vfx20xywrtI2ASRqgtfTzUKRjfL8+EBFF1kggFfqqfda0zAYtsSXJVHt9i7aWaJYZBOPKFyjtVaficGPywkaNUhESU3wEwP5bXCwE47ZWo8=
Received: from SY3PR01MB1148.ausprd01.prod.outlook.com (10.171.0.14) by
SY3PR01MB1148.ausprd01.prod.outlook.com (10.171.0.14) with Microsoft SMTP
Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) id
15.1.919.13; Mon, 20 Feb 2017 07:13:44 +0000
Received: from SY3PR01MB1148.ausprd01.prod.outlook.com ([10.171.0.14]) by
SY3PR01MB1148.ausprd01.prod.outlook.com ([10.171.0.14]) with mapi id
15.01.0919.015; Mon, 20 Feb 2017 07:13:44 +0000
From: =?iso-8859-1?Q?S=F8ren_S=F8rensen?= <sjs@targit.com.au>
To: Dhruv Pandya <Dhruv.Pandya@axieo.com>, Dominic Happe
<Dominic.Happe@Axieo.com>
CC: Roberto Pita Rodriguez <Roberto.Pita@Axieo.com>
Subject: RE: Major stock blowout
Thread-Topic: Major stock blowout
Thread-Index: AdKLNow/7QrTNl/ITJybU7mco4tTFwAAW6mwAAQgAZA=
Date: Mon, 20 Feb 2017 07:13:44 +0000
Message-ID: <SY3PR01MB11488D34BC68D5B4E10DB27DF85E0@SY3PR01MB1148.ausprd01.prod.outlook.com>
References: <MEXPR01MB0629418D8690FD0EB64C1688965E0@MEXPR01MB0629.ausprd01.prod.outlook.com>
<SYXPR01MB1087BCD4EC634C0C6083172D9F5E0@SYXPR01MB1087.ausprd01.prod.outlook.com>
In-Reply-To: <SYXPR01MB1087BCD4EC634C0C6083172D9F5E0@SYXPR01MB1087.ausprd01.prod.outlook.com>
Accept-Language: en-AU, en-US
Content-Language: en-US
X-MS-Has-Attach: yes
X-MS-TNEF-Correlator:
authentication-results: spf=none (sender IP is )
smtp.mailfrom=sjs@targit.com.au;
x-originating-ip: [122.108.150.207]
x-ms-office365-filtering-correlation-id: e6f0b6d4-8642-4591-537e-08d4596001b7
x-microsoft-antispam: UriScan:;BCL:0;PCL:0;RULEID:(22001);SRVR:SY3PR01MB1148;
x-microsoft-exchange-diagnostics: 1;SY3PR01MB1148;7:0r9IN0mROTtLo1WX8fsqk+aPU1XYIj5VR3froq1PUcpvUz7QV89ZOwKT6a+l9dcAgBHIfJQviuNgQyAIZ6GNn1Nlp1uuSoBHWjToXRY9Uzr1MoUxgZ5pl+mUAUvEEX4VXxpAMKm7tcfmVBROXVFxPPmgXGYfzaTBKsMEDJNHanaYjMu9hY70NDWfWRTZiXlm12MFAztYP/ary36c2zUfGbLJaCaHmx2chZMXQHS0hUpoQmzoSSjZXcLETycEYk6iOOiLYC0TZc8E7CfuEh+quCs2t4OVncb1wqNpBTVmuCt63uHCRZAFgqmU0Q8E/ErP3Sib2S5wp0mtffZZTYebcw==
x-microsoft-antispam-prvs: <SY3PR01MB114896ED6EAE1307542CACD2F85E0@SY3PR01MB1148.ausprd01.prod.outlook.com>
x-exchange-antispam-report-test: UriScan:(20558992708506)(278049740866173)(46150409022019)(21748063052155);
x-exchange-antispam-report-cfa-test: BCL:0;PCL:0;RULEID:(102415395)(6040375)(2401047)(8121501046)(5005006)(3002001)(10201501046)(6041248)(20161123555025)(2016111802025)(20161123564025)(20161123562025)(20161123560025)(20161123558025)(6072148)(6043046);SRVR:SY3PR01MB1148;BCL:0;PCL:0;RULEID:;SRVR:SY3PR01MB1148;
x-forefront-prvs: 02243C58C6
x-forefront-antispam-report: SFV:NSPM;SFS:(10009020)(7916002)(39830400002)(39450400003)(39410400002)(377454003)(51914003)(55674003)(53754006)(199003)(189002)(106356001)(97736004)(54556002)(54896002)(55016002)(7906003)(229853002)(189998001)(3660700001)(33656002)(92566002)(6506006)(9686003)(53946003)(6306002)(99286003)(74482002)(7736002)(66066001)(3280700002)(86362001)(4326007)(77096006)(105586002)(2906002)(2900100001)(38730400002)(8676002)(53936002)(81156014)(81166006)(101416001)(50986999)(6246003)(102836003)(6116002)(790700001)(3846002)(99936001)(3480700004)(8936002)(733005)(606005)(236005)(54356999)(7696004)(5660300001)(6436002)(7116003)(74316002)(25786008)(5890100001)(76176999)(53546006)(42882006)(2950100002)(68736007)(450100001)(122556002)(7099028)(321804003)(11873001)(579004);DIR:OUT;SFP:1101;SCL:1;SRVR:SY3PR01MB1148;H:SY3PR01MB1148.ausprd01.prod.outlook.com;FPR:;SPF:None;PTR:InfoNoRecords;A:1;MX:1;LANG:en;
received-spf: None (protection.outlook.com: targit.com.au does not designate
permitted sender hosts)
spamdiagnosticoutput: 1:99
spamdiagnosticmetadata: NSPM
Content-Type: multipart/related;
boundary=»_012_SY3PR01MB11488D34BC68D5B4E10DB27DF85E0SY3PR01MB1148ausp_»;
type=»multipart/alternative»
MIME-Version: 1.0
X-OriginatorOrg: targit.com.au
X-MS-Exchange-CrossTenant-originalarrivaltime: 20 Feb 2017 07:13:44.5025
(UTC)
X-MS-Exchange-CrossTenant-fromentityheader: Hosted
X-MS-Exchange-CrossTenant-id: 5f5e9046-2250-4c8e-aa26-206f1df0678c
X-MS-Exchange-Transport-CrossTenantHeadersStamped: SY3PR01MB1148
Нарушение системной лицензии – одна из сотен ошибок, вызывающая синий экран в Windows 8, 8.1 и 10. Большинство из них решаются простой перезагрузкой системы, однако некоторые появляются постоянно, и могут препятствовать доступу пользователей к Windows. Нарушение лицензии является одной из таких ошибок, поэтому она требует срочного решения.
Причины появления данной неполадки могут быть в несовместимости системы с некоторыми сторонними приложениями. В редких случаях ошибка возникает после обновления драйверов, хотя проблема здесь также в конфликте программ. Помимо прочего, SYSTEM_LICENSE_VIOLATION сигнализирует о нарушении лицензионного соглашения на обеспечение, возможно, из-за неправильного размещения или повреждения реестра. Ниже рассмотрим все варианты решения данной неисправности.
Содержание
- Запустите Windows в безопасном режиме
- Решение 1. Запустите средство проверки системных файлов
- Решение 2. Проверьте диск на наличие ошибок
- Решение 3. Удалить проблемный драйвер
- Решение 4. Выполните восстановление системы
- Решение 5. Используйте Windows Media Creation Tool
Запустите Windows в безопасном режиме
Очень часто данная проблема не позволяет запустить компьютер в обычном режиме, и у пользователя нет возможности зайти на рабочий стол, чтобы внести какие-либо поправки. Поэтому необходимо загрузить систему в безопасном режиме.
- Перезагрузите компьютер.
- Как только Windows начнёт загрузку, нажмите три раза кнопку питания, прервав процесс.
- После этого Windows автоматически перейдёт в режим расширенного запуска.
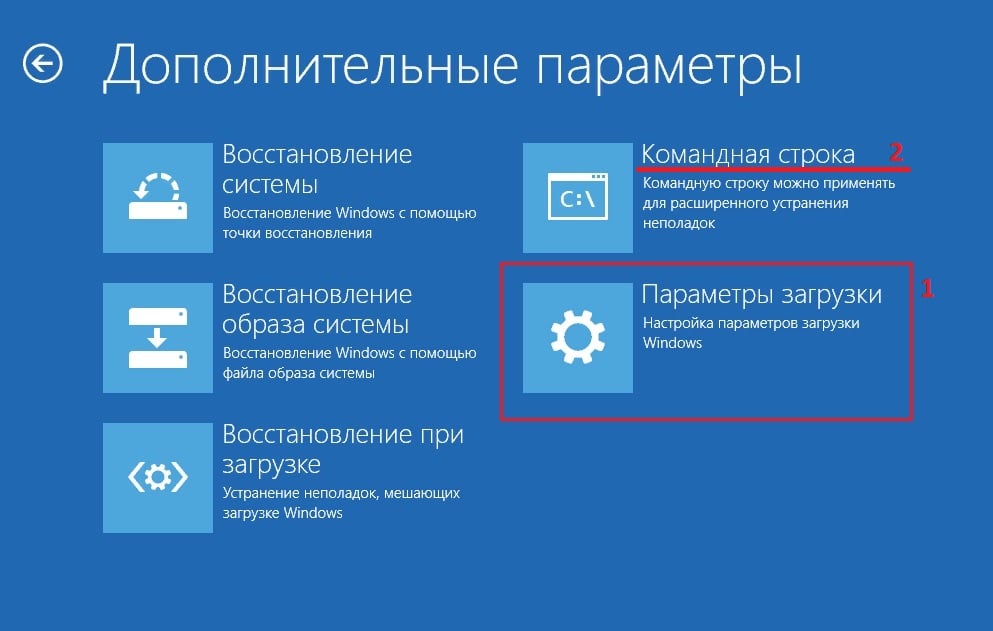
- Выберите Устранение неполадок> Дополнительные параметры> Параметры загрузки.
- После перезагрузки нажмите 4/F4 для безопасного режима или 5/F5 для безопасного режима с загрузкой сетевых драйверов (1).
- Если вам не удалось получить доступ к этому параметру, можно использовать командную строку (2): Устранения неполадок> Дополнительные параметры> Командная строка.
Решение 1. Запустите средство проверки системных файлов
После того, как удалось попасть на рабочий стол можно приступать к непосредственному решению проблемы.
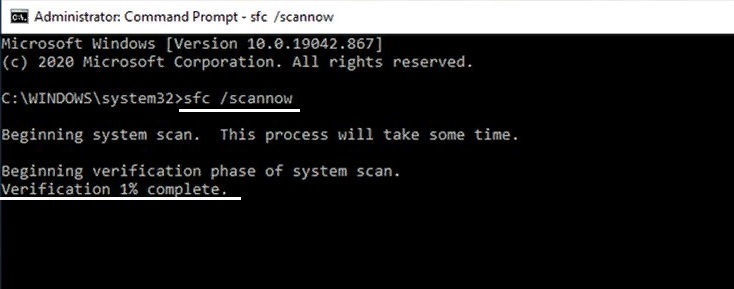
- Нажмите ПКМ по значку Windows, и выберите Командная строка (Администратор).
- В новом окне введите команду sfc/scannow и кликните Enter.
- Дождитесь окончания проверки системных файлов.
- Если неполадки были исправлены, перезагрузите систему.
- В обратном случае переходите к следующему пункту.
Решение 2. Проверьте диск на наличие ошибок
Для этого можно использовать встроенную функцию:
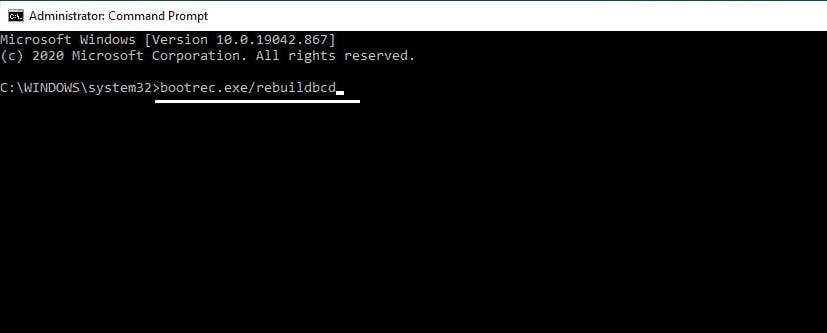
- Скопируйте и вставьте в командную строку следующие строки, нажимая Enter после каждой:
- bootrec.exe/rebuildbcd
bootrec.exe/fixmbr
bootrec.exe/fixboot
chkdsk C: /f/r - После завершения перезагрузите компьютер.
Решение 3. Удалить проблемный драйвер
Если проблема возникла после того, как вы установили определённый драйвер, следует удалить его.
- Нажмите комбинацию Win + X, и выберите Диспетчер устройств.
- В новом окне разверните раздел с установленным приложением, и удалите проблемный файл, нажав по нему ПКМ.
- Далее подтвердите выбор, а затем перезагрузите систему.
Решение 4. Выполните восстановление системы
Данный метод является универсальным решением для многих проблем, так как этот процесс откатывает систему до одного из предыдущих состояний, когда всё работало стабильно.
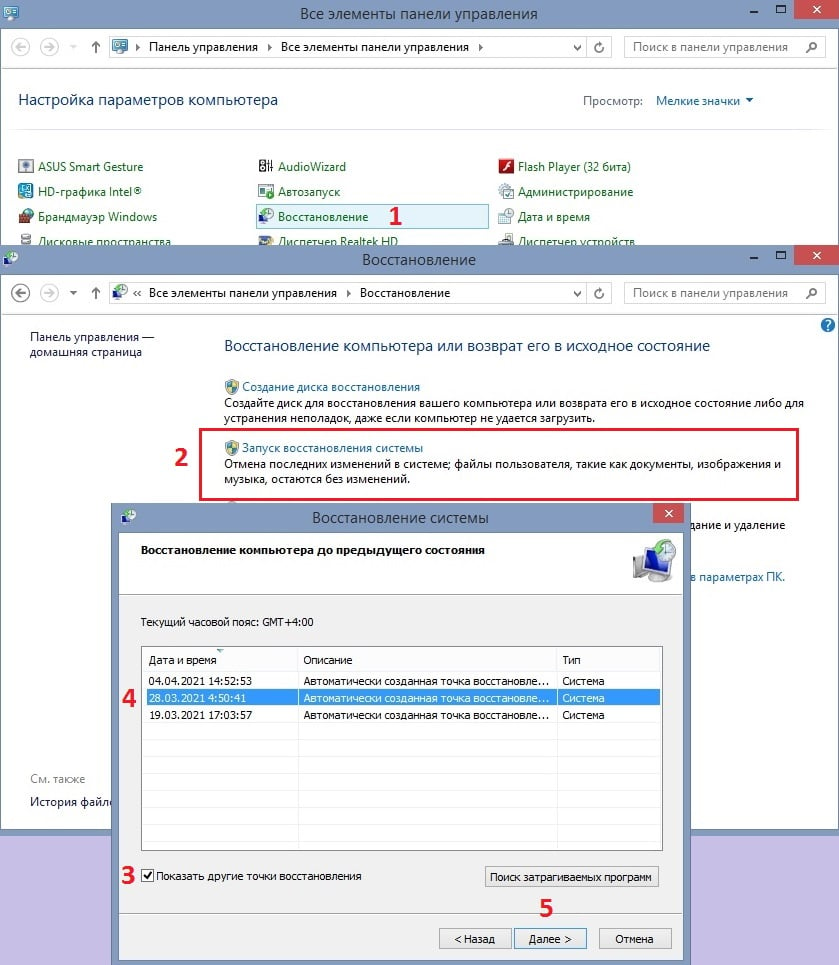
- Нажмите ПКМ по значку Windows, и выберите Панель управления.
- Перейдите в раздел Восстановление, а затем в подраздел Запуск восстановления системы.
- В следующем окне будет предложено выбрать одну из доступных дат, когда был создан бэкап.
- Если точек для отката недостаточно, установите флажок: Показать другие точки восстановления.
- После выбора предпочтительной даты запустите процесс, нажав Далее.
Решение 5. Используйте Windows Media Creation Tool
В редких случаях, при самых критических ситуациях необходимо загрузить с официального сайта Microsoft установочный файл Windows Media Creation Tool, который автоматически внесёт необходимые исправления в систему. Стоит отметить, что для этого метода нужен другой рабочий компьютер.
- Посетите официальный сайт Microsoft.
- Загрузите установочный носитель Windows 10.
- Запустите установщик, согласитесь с Условиями и нажмите Далее.
- Выберите Создать установочный носитель (USB-накопитель, DVD или файл ISO) для другого ПК.
- Нажмите Далее и выберите USB-накопитель (убедитесь, что USB подключён к ПК).
- Теперь следуйте инструкциям на экране, и как только появится возможность выбрать раздел, выберите UEFI.
- После того как процесс завершится, подключите USB-носитель к проблемному ПК.
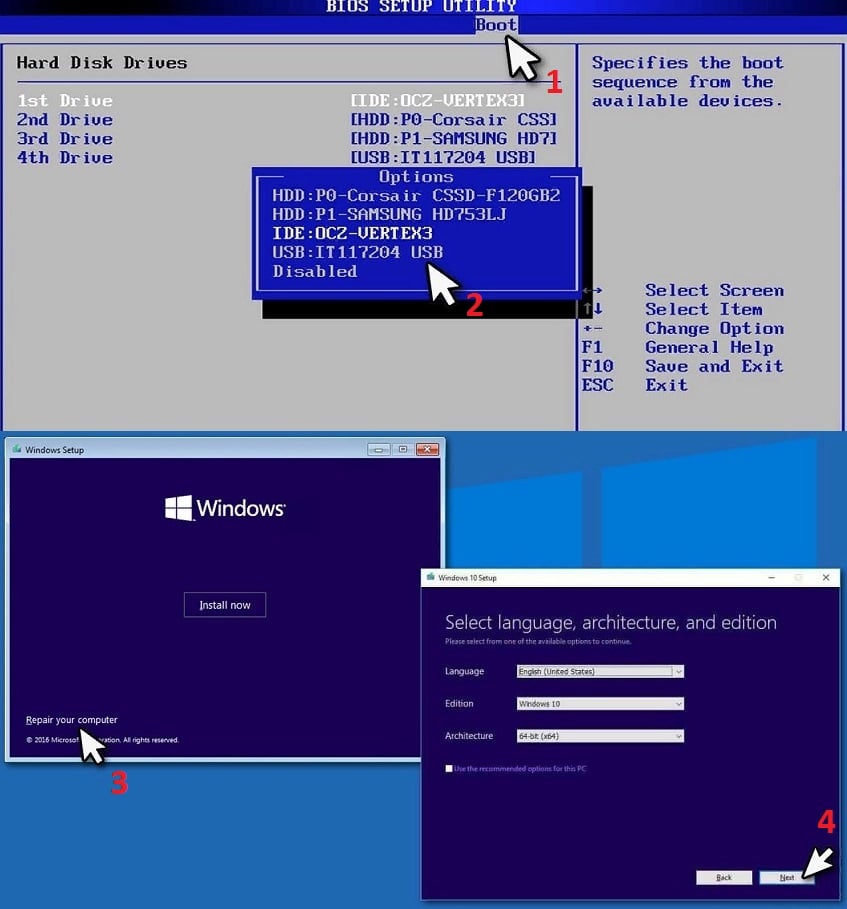
- Загрузитесь в BIOS, нажимая во время загрузки компьютера несколько раз F2, F8, F12, Del (в зависимости от вашего устройства) и перейдите в меню загрузки.
- Здесь выберите параметр «Приоритет загрузки» и установите для него значение «Приоритет загрузки USB».
- Перезагрузите компьютер.
- Затем нажмите Восстановить компьютер в нижнем левом углу.
- В дополнительных параметрах выберите: Использовать Windows Media Creation Tool.
- Нажмите Устранение неполадок> Автоматический ремонт.
Cloud management gateway (CMG) is a new chapter in Microsoft Endpoint Manager Configuration Manager (MEMCM). It is getting improved better and better in each version that gets released. If you look at the technical preview build that was released recently (version 2009), it has a remote control feature for CMG connected devices which is very much needed to support the internet-connected devices and there are many other good features in the technical preview build that might ship in the next production build. But that’s a whole other topic. In this blog post, I will describe the SCCM CMG Policy Violation error that I recently come across at a customer while deploying the SCCM Cloud Management Gateway service.
Due to the COVID-19, lot of workforce is working from home and managing the endpoints over internet or VPN is at most important and meet the compliance.
You can refer to our guide for a complete Cloud Management Gateway installation.
Refer to this TechNet blog if you need more information about managing remote machines with cloud management gateway.
Every time I set up a CMG service, there is always something to learn from it and this time, I have learnt something new about the resource group and region.
Just to brief about the customer infra, SCCM 2006, self-signed certificate, e-HTTP enabled, wild card certificate from public CA for server authentication.
With SCCM 2002+, clients can use token-based authentication if you don’t have PKI, hybrid Azure AD join or Azure AD join. These are different authentication methods for the client to authenticate with CMG service.
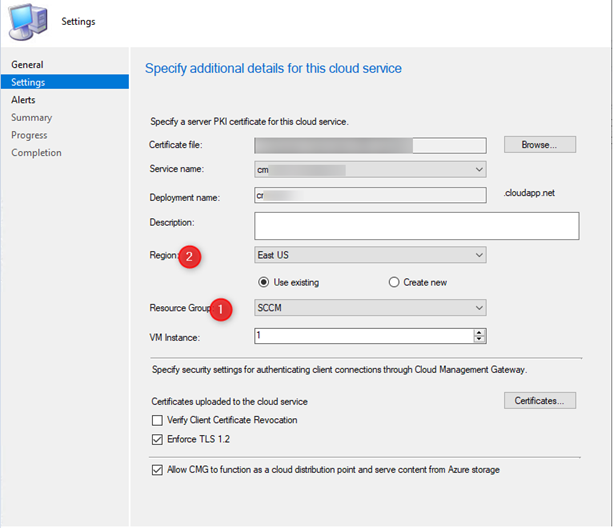
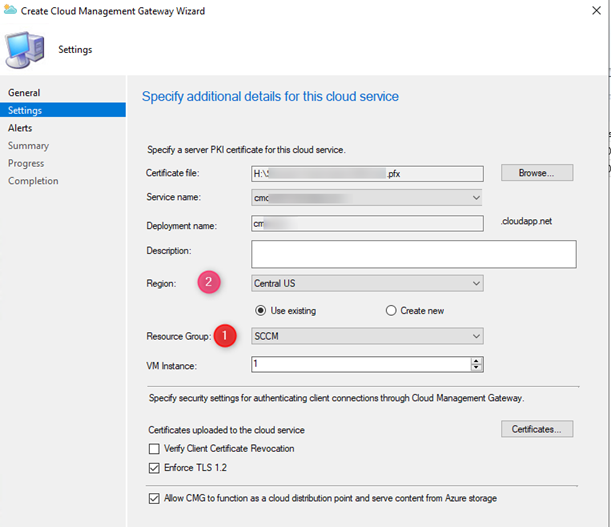
We used the wild card certificate for the CMG server authentication and started the CMG setup.
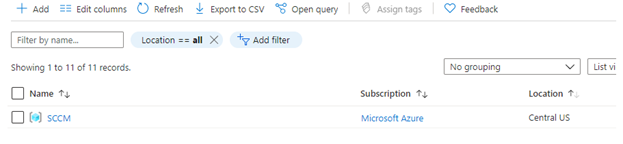
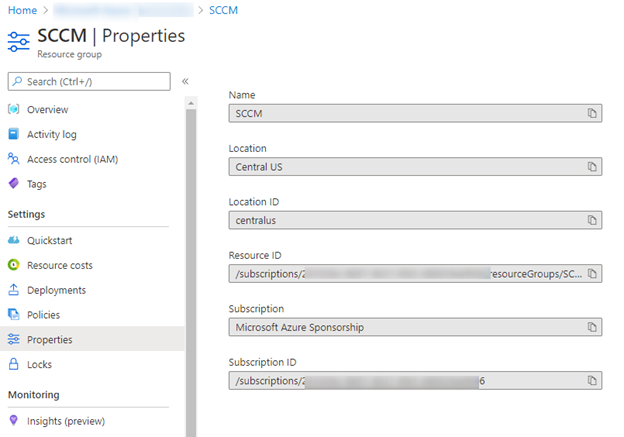
We had selected the existing resource group called SCCM and the region as East US.
After the completion of the setup, I had looked the console for the status and status shows provisioning service failed error.
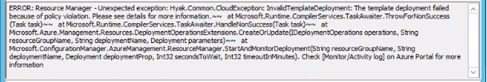
So I have looked at the CMGsetup log on the primary site server log files and found the following error several times.
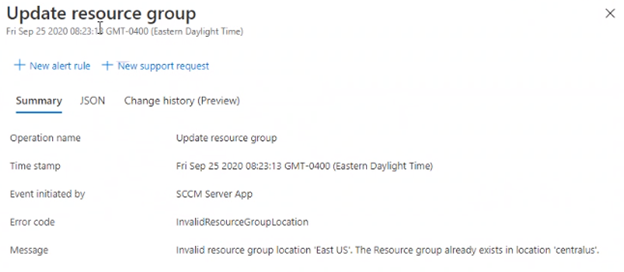
Error: Resource Manager – Unexpected exception: Hyak.Common.CloudExeception: InvalidTemplatedeployment: The template deployment failed because of the policy violation. Please see the details for more information. Check monitor/activity log on Azure portal for more information.
SCCM CMG Policy Violation Solution
To find the actual reason for this failure (the policy violation) :
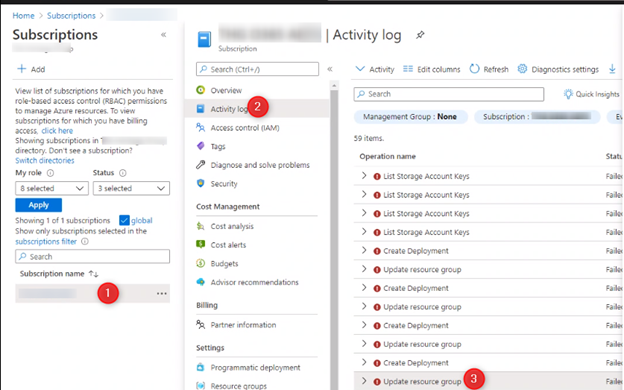
- I have logged into the Azure portal
- go the Subscription where the CMG service was targeted for the deployment
- Click Activity log
- In the activity log, you will see several alerts
- Click on any one of the activity log, you will see more information about the error.
- We had the following message: Invalid resource group location ‘East US’. The Resource group already exists in location ‘CentralUS’.
If you remember the region that was selected for the resource group (SCCM) in the CMG setup, it was East US and this resource group SCCM already created with region CentralUS hence a mismatch.
So now, we have couple of options to fix the issue:
- Change the region for the existing resource group in the subscription from CentralUS to East US
- Select Central US in the CMG setup wizard for the existing resource group SCCM
- Create a new resource group and choose the wanted location
- We tried option #1… but we can’t change the location of a resource group once it is created… let’s try #2
- We will now go with either option #2 or #3. We decided to try option 2 by simply changing the region that matches the resource group region Central US in the CMG setup wizard.
This time, the CMG setup wizard successfully executed, and the services were in place in no time. The SCCM CMG Policy Violation error didn’t happen this time
Conclusion
If you want to use the existing resource group for the CMG setup, make sure, you select the same region that was used in the Azure subscription else you will run into this SCCM CMG Policy Violation error.
На чтение 9 мин. Просмотров 1.6k. Опубликовано 03.09.2019
Компьютерные ошибки относительно распространены и их легко исправить, но иногда вы можете получить ошибку «Синего экрана смерти», такую как SYSTEM_LICENSE_VIOLATION. Эти типы ошибок довольно серьезны, так как они приводят к сбою Windows 10 и перезагружают ваш компьютер, чтобы предотвратить повреждение, поэтому сегодня мы собираемся показать вам, как исправить вышеупомянутую ошибку.
Как исправить ошибку SYSTEM_LICENSE_VIOLATION BSoD
Содержание .
- Обновите Windows 10 и все ваши драйверы
- Запустите средство устранения неполадок BSOD
- Запустите сканирование SFC
- Запустить DISM
- Проверьте жесткий диск
- Найти и удалить проблемные приложения
- Войдите в безопасный режим
- Выполнить восстановление системы/сброс Windows 10
- Проверьте на неисправное оборудование
Исправлено – SYSTEM_LICENSE_VIOLATION Windows 10 ошибка
Решение 1. Обновите Windows 10 и все ваши драйверы
Ошибки Blue Screen of Death часто бывают вызваны аппаратными и программными проблемами, и во избежание этих ошибок настоятельно рекомендуется обновлять Windows 10 как можно чаще. Microsoft постоянно выпускает обновления для Windows 10 через Центр обновления Windows, поэтому обязательно загрузите их. Многие из этих обновлений устраняют определенные аппаратные и программные проблемы, поэтому, если вы хотите избежать ошибок Blue Screen of Death, мы настоятельно рекомендуем вам поддерживать Windows 10 в актуальном состоянии.
Помимо загрузки обновлений для Windows 10, также важно обновлять драйверы. Windows 10 использует ваши драйверы для связи с вашим оборудованием, и если определенный драйвер устарел или просто не совместим с Windows 10, вы, вероятно, получите ошибку BSoD, такую как SYSTEM_LICENSE_VIOLATION. Поэтому, чтобы исправить эти типы ошибок, вы должны обновить все ваши драйверы. Обновление драйверов является относительно простым, и вы можете сделать это, просто посетив веб-сайт производителя оборудования и загрузив последние версии драйверов для вашего устройства. При загрузке драйверов обязательно загружайте драйверы для всех основных компонентов оборудования.
Обновлять драйверы автоматически
Поиск драйверов самостоятельно может занять много времени. Поэтому мы советуем вам использовать инструмент, который сделает это автоматически. Использование автоматического средства обновления драйверов, безусловно, избавит вас от необходимости поиска драйверов вручную и всегда будет поддерживать вашу систему в курсе последних версий драйверов.
Модуль обновления драйверов Tweakbit (одобрен Microsoft и Norton Antivirus) поможет вам автоматически обновлять драйверы и предотвращать повреждение ПК, вызванное установкой неправильных версий драйверов. После нескольких тестов наша команда пришла к выводу, что это наиболее автоматизированный решение.
Вот краткое руководство о том, как его использовать:
-
Загрузите и установите средство обновления драйверов TweakBit
-
После установки программа начнет сканирование вашего компьютера на наличие устаревших драйверов автоматически. Driver Updater проверит установленные вами версии драйверов по своей облачной базе данных последних версий и порекомендует правильные обновления. Все, что вам нужно сделать, это дождаться завершения сканирования.
-
По завершении сканирования вы получите отчет обо всех проблемных драйверах, найденных на вашем ПК. Просмотрите список и посмотрите, хотите ли вы обновить каждый драйвер по отдельности или все сразу. Чтобы обновить один драйвер за раз, нажмите ссылку «Обновить драйвер» рядом с именем драйвера. Или просто нажмите кнопку «Обновить все» внизу, чтобы автоматически установить все рекомендуемые обновления.
Примечание. Некоторые драйверы необходимо установить в несколько этапов, поэтому вам придется нажмите кнопку «Обновить» несколько раз, пока все его компоненты не будут установлены.
Решение 2. Запустите средство устранения неполадок BSOD .
Если обновление драйверов не помогло, мы можем попробовать встроенный инструмент устранения неполадок Microsoft для ошибок BSOD. Это, вероятно, самое простое решение практически для любой проблемы BSOD, потому что оно в основном решает проблему для вас.
Вот как запустить встроенное средство устранения неполадок Windows 10:
- Откройте приложение Настройки и перейдите в раздел Обновление и безопасность .
- Выберите «Устранение неполадок» в меню слева.
-
Выберите BSOD на правой панели и нажмите Запустить средство устранения неполадок .
- Следуйте инструкциям на экране для устранения неполадок.
Решение 3. Запустите сканирование SFC
Следующее, что мы собираемся попробовать, – это сканирование SFC. Это инструмент командной строки, который сканирует ваш компьютер на наличие потенциальных проблем и решает их.Таким образом, это может быть полезно при работе с ошибкой SYSTEM_LICENSE_VIOLATION.
Вот как запустить сканирование SFC в Windows 10:
- Щелкните правой кнопкой мыши кнопку «Пуск» и откройте Командную строку (Admin).
-
Введите следующую строку и нажмите Enter: SFC/SCANNOW
- Подождите, пока процесс не будет завершен (это может занять некоторое время).
- Если решение найдено, оно будет применено автоматически.
- Теперь закройте командную строку и перезагрузите компьютер.
Решение 4. Запустите DISM .
Третий инструмент для устранения неполадок, который мы собираемся попробовать, это DISM. Как следует из названия, служба обслуживания образов развертывания и управления ими (DISM) перезагружает образ системы, разрешая на пути некоторые потенциальные проблемы.
Мы рассмотрим как стандартные, так и процедуры, которые используют установочный носитель ниже:
- Стандартный способ
- Щелкните правой кнопкой мыши Пуск и откройте командную строку (администратор).
-
Вставьте следующую команду и нажмите Enter:
-
-
DISM/Online/Cleanup-Image/RestoreHealth
-
DISM/Online/Cleanup-Image/RestoreHealth
-
- Подождите, пока сканирование не закончится.
- Перезагрузите компьютер и попробуйте обновить снова.
- С установочного носителя Windows
- Вставьте установочный носитель Windows.
- Щелкните правой кнопкой мыши меню «Пуск» и выберите в меню «Командная строка» («Администратор»).
-
В командной строке введите следующие команды и нажмите Enter после каждого:
- dism/online/cleanup-image/scanhealth
- dism/online/cleanup-image/restorehealth
-
Теперь введите следующую команду и нажмите Enter:
- DISM/Online/Cleanup-Image/RestoreHealth /source:WIM:X:SourcesInstall.wim:1/LimitAccess
- Обязательно измените значение X с буквой подключенного диска при установке Windows 10.
- После завершения процедуры перезагрузите компьютер.
Решение 5. Проверьте жесткий диск
Поврежденные сектора диска или некоторые другие проблемы, связанные с жестким диском, могут легко вызвать различные проблемы BSOD. Включая ошибку SYSTEM_LICENSE_VIOLATION. Таким образом, проверка состояния вашего жесткого диска, безусловно, не повредит.
Вот как запустить команду chkdsk для проверки состояния жесткого диска в Windows 10:
- Введите Расширенный запуск (перезагрузите компьютер, удерживая клавишу Shift ).
- Выберите Устранение неполадок> Дополнительные параметры .
- Выберите Командная строка в списке параметров.
-
Когда появится командная строка, введите следующие строки и нажмите Enter после каждой строки, чтобы запустить ее:
-
bootrec.exe/rebuildbcd
- bootrec.exe/fixmbr
- bootrec.exe/fixboot
-
bootrec.exe/rebuildbcd
-
Некоторые пользователи также рекомендуют запускать дополнительные команды chkdsk . Для выполнения этих команд вам необходимо знать буквы дисков для всех разделов жесткого диска. В командной строке вы должны ввести следующее (но не забудьте использовать буквы, которые соответствуют разделам вашего жесткого диска на вашем ПК):
-
chkdsk/r c:
- c hkdsk/r d:
Это только наш пример, так что имейте в виду, что вы должны выполнять команду chkdsk для каждого раздела жесткого диска, который у вас есть.
-
chkdsk/r c:
- Перезагрузите компьютер и проверьте, решена ли проблема.
Решение 6 – Найти и удалить проблемные приложения
Иногда определенные приложения могут вызвать появление этой ошибки, поэтому крайне важно найти и удалить это приложение. Стоит отметить, что почти любое приложение может вызвать ошибку SYSTEM_LICENSE_VIOLATION, поэтому вам может потребоваться провести некоторое исследование, прежде чем вы найдете проблемное приложение. Вы также должны знать, что недавно установленные или недавно обновленные приложения могут также вызывать эту ошибку, поэтому, если вы обновили или установили какое-либо новое приложение за последние несколько дней до появления ошибки BSoD, обязательно удалите ее.
- ЧИТАЙТЕ ТАКЖЕ: исправьте код ошибки 0x803f7000 в Магазине Windows 10
Одной из распространенных причин ошибок Blue Screen of Death является антивирусное программное обеспечение. Почти любое антивирусное программное обеспечение может вызвать ошибку BSoD, поэтому обязательно удалите все сторонние антивирусные программы, которые вы установили. Чтобы полностью удалить антивирусную программу, вы должны использовать специальный инструмент для удаления. Многие охранные компании предлагают эти инструменты для своего программного обеспечения, поэтому обязательно загрузите один из них для своей антивирусной программы.
Решение 7 – войдите в безопасный режим
Если проблема вызвана определенным программным обеспечением, вы сможете узнать это, войдя в безопасный режим. Для входа в безопасный режим выполните следующие действия:
-
Запустите автоматическое восстановление при перезагрузке компьютера во время загрузки. В качестве альтернативы вы можете удерживать клавишу Shift и нажать кнопку Перезагрузить .
- Выберите Устранение неполадок> Дополнительные параметры> Параметры запуска . Нажмите кнопку Перезагрузить .
- Когда ваш компьютер загружается, выберите Безопасный режим с сетевым подключением или любую другую версию безопасного режима.
Безопасный режим запускается только с основными драйверами и программным обеспечением, поэтому, если ваша проблема вызвана определенным приложением или проблемным драйвером, ваша система должна работать без проблем в безопасном режиме.
Решение 8. Выполните восстановление системы/сброс Windows 10
По словам пользователей, им удалось исправить ошибку SYSTEM_LICENSE_VIOLATION путем восстановления системы. Для восстановления системы необходимо выполнить следующие действия:
- Запустите автоматическое восстановление, перезагрузив компьютер несколько раз во время загрузки.
- Выберите Устранение неполадок> Дополнительные параметры> Восстановление системы .
- Выберите свое имя пользователя, введите пароль и нажмите Продолжить .
- Выберите Выбрать другую точку восстановления и выберите точку восстановления, к которой вы хотите вернуться.
- Нажмите Далее и дождитесь окончания процесса.
- ЧИТАЙТЕ ТАКЖЕ: исправьте ошибку NTFS_File_System в Windows 10
Если восстановление системы не устранило проблему, попробуйте выполнить сброс Windows 10. Эта процедура похожа на чистую установку, поэтому обязательно сделайте резервную копию всех важных файлов из вашего раздела C. Также стоит упомянуть, что вам может потребоваться установочный носитель Windows 10 для выполнения этого шага, поэтому вы должны использовать Media Creation Tool для создания загрузочного USB-накопителя. Чтобы выполнить сброс Windows 10, выполните следующие действия:
- Запустите автоматическое восстановление.
- Выберите Устранение неполадок> Сбросить этот компьютер> Удалить все . Если вас попросят вставить установочный носитель Windows 10, обязательно сделайте это.
- Выберите Только диск, на котором установлена Windows> Просто удалите мои файлы и нажмите Сбросить .
- Следуйте инструкциям и дождитесь завершения процесса сброса.
После сброса все ваши установленные приложения и файлы будут удалены, включая любые программные причины для BSoD. Если ошибка появляется снова, скорее всего, у вас неисправное оборудование.
Решение 9. Проверьте наличие неисправного оборудования
Ваша ОЗУ может быть частой причиной ошибок BSoD, таких как SYSTEM_LICENSE_VIOLATION, поэтому сначала обязательно проверьте свою ОЗУ. Такие инструменты, как MemTest86 +, могут использоваться для детального тестирования вашей оперативной памяти, поэтому обязательно загрузите ее. Если проблема не в оперативной памяти, проверьте, правильно ли работают другие основные аппаратные компоненты.
Стоит также отметить, что любое недавно установленное оборудование может вызывать проблемы такого типа, особенно если оно не полностью совместимо с вашим ПК. Если вы недавно установили какое-либо новое оборудование, обязательно удалите его или замените и проверьте, исправляет ли это ошибку.
Ошибка SYSTEM_LICENSE_VIOLATION BSoD может вызывать проблемы, но мы надеемся, что вам удалось исправить ее с помощью одного из наших решений.
Примечание редактора . Этот пост был первоначально опубликован в июне 2016 года и с тех пор был полностью переработан и обновлен для обеспечения свежести, точности и полноты.
The Computer Investigation Process
Littlejohn Shinder, Michael Cross, in Scene of the Cybercrime (Second Edition), 2008
Policy Violations
When policies are violated, it doesn’t necessarily mean that a full police investigation is required. In many situations, the violation may require disciplinary actions against the employee, whether it is a reprimand, fine, demotion, or termination. The severity of the actions will often depend on the past performance and current conduct of the person. Despite the end result, computer forensics may still be incorporated. Using forensic procedures to investigate the incident creates a tighter case against the employee, thereby making it difficult for the employee to argue the facts.
In any investigation, it is important to treat the case as though it were going to court, as you never know what you’ll find. For example, an employee may have violated a company’s acceptable use policy by viewing questionable Web sites during work hours. However, if it was found that the person was downloading child pornography, the internal investigation becomes a criminal one. Any actions taken in the investigation would be scrutinized, and anything found could be evidence in a criminal trial.
Policy violations can also extend beyond the machines owned by a company. Many people have their own blogs or personal Web sites, or enjoy social networks such as Facebook (http://www.facebook.com), Friendster ((http://www.friendster.com), and others. On such sites, people can publish text and pictures to the Internet. If the person mentions where he or she works, and makes derogatory comments about coworkers or portrays the company in a negative manner, it may seem that little can be done. After all, the information isn’t on a corporate computer, but on another server entirely. However, depending on policies implemented in the organization, this may not always be the case. In 2007, an eleventh grade student in Abbotsford, BC, named Amanda Bunn created a page on Facebook titled “If 200 people sign this, I’ll kick (teacher Pat Mullaney) in the box.” Because the threat was made to her teacher, the student was suspended for three weeks before ultimately being expelled from the school. Other schools have taken similar actions against students in cases of cyberbullying. Because school policies exist in many schools that prohibit threatening teachers and students, the students are held accountable for their actions, even though the incidents never occurred on school property.
In the same way that schools are realizing that cyberbullying can escalate into more violent actions, fewer and fewer organizations are tolerating hostile working environments. Hostile working environments are workplaces where a person fears intimidation, harassment, physical threats, humiliation, or other experiences that create an offensive or oppressive atmosphere. One common example of a hostile working environment is sexual harassment. If a person had to view sexual images displayed on a computer, or received messages sent through e-mail, Short Message Service (SMS) or IM that had undertones or blatant sexual remarks, he or she could feel objectified and humiliated by the atmosphere. In such cases, internal disciplinary tribunals, criminal charges, or civil suits may be the only way to stop such actions. When these activities are received, transmitted, or displayed using technologies issued by the company, it is simple to acquire evidence by looking at information stored on the devices or on hard disks.
One of the most devastating types of policy violation is industrial espionage, which is also a criminal act. Industrial espionage is the selling of trade secrets, intellectual property, or other classified information to competitors. If the wrong person has access to such information, it could be detrimental to the organization, as releasing it to the public or competitors could undermine confidence in the organization, and even jeopardize its ability to remain solvent. Source code for programs, secret recipes, and other knowledge that is often limited to the most trusted insiders could be devastating if released. Information must be kept secure, and any suspected leaks must be dealt with swiftly.
On the Scene
The Cola Wars and Industrial Espionage
When you think of Coca-Cola and Pepsi, you probably think of staunch competitors in the Cola Wars, with each trying to get an advantage over the other in the marketplace. The last thing you’d imagine is the two of them working together to stop a Coke employee from selling secrets to Pepsi. However, because such companies rely on secret recipes and other trade secrets to remain in business, the threat of industrial espionage is one that can’t be tolerated and is considered one of their greatest risks to security.
In May 2006, PepsiCo Inc. received a letter offering to sell them trade secrets of the Coca-Cola Co. Pepsi immediately contacted Coke, who in turn contacted the FBI. The FBI worked with both companies to create a sting operation that led to the arrest of Joya Williams, a secretary who worked at Coca-Cola, and two others working with her to sell the secrets. Williams had stolen not only confidential information, but also a sample of a new soft drink the company was developing, which she, Ibrahim Dimson, and Edmund Duhaney tried to sell to Pepsi for $1.5 million.
In 2007, Williams was convicted and received a prison sentence of eight years; Dimson entered a guilty plea and was sentenced to five years in prison. Both were also sentenced to an additional three years of supervised release, and each was ordered to pay $40,000 in restitution. Duhaney also entered a guilty plea, thereby closing the cap on this case.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597492768000054
Central Alarm Stations and Dispatch Operations
Sean Smith, … Rich Abrams, in The Professional Protection Officer, 2010
Communications
Communications equipment plays a huge role in the successful resolution of alarms, criminal and policy violations, emergency situations, and, of course, customer service. In a modern central monitoring and dispatch station, communication takes many forms. However, the vast majority of communication is performed verbally, through telephone lines and radio channels.
A modern telephone system in a central station will incorporate many technological advances available to the general public, such as caller ID, preset number dialers, and the ability to place callers on hold or transfer them to other lines. However, the system should also be tailored for use by emergency service personnel.
The system’s interface may be a series of physical keys on what looks like a very large telephone base, or it may be integrated with touchscreen software, to allow the operator to switch between functions quickly and easily. Typically, the operator will be equipped with a headset, in order to move about the station and keep both hands free while communicating with a caller. The system may incorporate several incoming emergency lines and several incoming nonemergency lines, which would likely be shared by all telephone consoles at the station. Each console would also have access to its own line for outgoing calls. Alternatively, all emergency calls may be routed to a dedicated “red phone” in the station, eliminating the need to place an emergency caller on hold while briefing police, fire, or emergency medical services (Thibodeau, 2003). It is common for all telephone calls, incoming and outgoing, emergency and nonemergency, to be automatically recorded and archived for supervisors to refer to later.
In agencies with very advanced technology, telephone systems may be integrated with a variety of other systems in the central station. For example, it is possible to connect certain telephone software with certain computer-aided dispatch software and geographic mapping software. In these situations, the central station may receive an emergency call, and the location provided by the caller ID may be automatically highlighted on a computerized map. The location might then be automatically imported into the computer-aided dispatch software when a new event is created by the operator.
Organizational policy varies with regard to the usage of cellular phones by protection officers in the field. When they are permitted, they can be very useful tools for relaying information back and forth that is sensitive but nonemergency in nature. At the very least, it is common for a patrol supervisor to be equipped with an organization-issued cellular phone for this purpose.
Radio systems are equally as important as telephone systems in both emergency and non-emergency situations. They are the most frequently used method by which field officers communicate with their dispatchers and with each other. A modern radio system interface, like that of a modern telephone system, may consist of a set of keys or may incorporate a touch screen for ease of use. The same headset used by the operator for telephone communication will often be integrated with the station’s radio system as well. Additionally, the central station should be equipped with software enabling an operator to see the name or ID of a handheld or mobile unit; to page, activate, or deactivate an individual unit; to acknowledge emergency signals received; and to perform maintenance functions.
The radio system will typically be capable of monitoring and transmitting on a large number of channels simultaneously. These may consist of the primary channel, an emergency channel, a tactical channel, maintenance and custodial staff channels, and many more. Direct monitoring and transmitting on local police, fire, and emergency medical channels is also possible.
A two-way radio operates in either simplex or duplex mode. In simplex mode, a radio transmits and receives messages on the same frequency and communicates directly with other radios. In duplex mode, a radio transmits and receives messages on two different frequencies. This mode also incorporates a repeater. A repeater is simply a stationary device, attached to an antenna, which receives a radio message, amplifies it to increase its range, then retransmits the message to its destination. Duplex mode is far more common than simplex mode in this day and age.
Radio equipment can be either analog or digital. Analog equipment has been in use for many years. It tends to be less complicated than digital, and is therefore less expensive to purchase and maintain. It also tends to be more compatible with existing radio systems. Digital equipment allows for a larger number of officers to talk at once on the same channel. It also allows for different types of data—for example, text messages—to be sent and received. Certain digital radio systems can even be integrated with certain computer-aided dispatch software, which can communicate via text with individual radio units.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781856177467000080
What’s First?
Christian B. Lahti, Roderick Peterson, in Sarbanes-Oxley IT Compliance Using Open Source Tools (Second Edition), 2007
Server Room Access Policy
This policy is another example of the indirect relationship between operational responsibilities versus the operational consequences of a policy violation. You should look to other areas where IT may not own the process but might be adversely affected by violations to stated business policies. This policy is an example of one that was required by the AS2 standard, but as a result of the new AS5 standard it may be possible to negotiate with your auditor. Please keep in mind that we are not suggesting that operationally this policy should not be in place and/or implemented. But rather that as a result of the new AS5 standard your auditor may view it differently as it applies to Sarbanes-Oxley compliance.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597492164000069
Understanding Digital Forensics
Jason Sachowski, in Implementing Digital Forensic Readiness, 2016
Legal Aspects
Even if legal prosecution is not the end-goal of the investigation, such as a corporate policy violation, there may be some form of legal action, such as employee termination. It is important that the forensic science principles, methodologies, and techniques are consistently followed because the investigation may wind up in a court of law at some point. Regardless of criminal proceedings, every digital forensic investigation must ensure that:
- •
-
an exact copy of digital data is created to ensure no information is lost or overlooked
- •
-
the authenticity of digital data is preserved through the use of cryptographic algorithms
- •
-
a chain of custody is established to maintain integrity through the evidence’s life cycle
- •
-
actions taken by people through the different investigative phases are recorded
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9780128044544000010
Policies and Privacy
Michael Cross, in Social Media Security, 2014
How not to report a violation
Social media may be a great way of sharing information, but it’s not the way to report a policy violation. An example of using social media to register a complaint was seen in March 2013 at PyCon, an annual Python developer conference in Santa Clara, California. During the conference, Adria Richards overheard two developers sitting behind her, who were making jokes about dongles and forking. The jokes were sexual innuendo, and while the tech terms sound like dirty words, they’re actually not. Finding it inappropriate, she decided not to tell them she was offended. Instead, she took a photo of the developers (and others surrounding them), and as seen in Figure 9.1, tweeted a complaint to the PyCon hashtag
Figure 9.1. Adria Richard’s tweet about inappropriate behavior.
PyCon approached Richards, who pointed out the developers who made the remarks. The pair was taken out of the conference, the matter was discussed privately, and the developers apologized. As a result of the incident, PyCon updated their code of conduct. It provides information on how to properly report harassment or inappropriate behavior by contacting a member of the conference or hotel staff. PlayHaven, the employer of one developer, also took action by later firing their employee.
Richards was also fired from SendGrid, where she worked as a developer evangelist. While SendGrid stated they respect her right to report inappropriate behavior, however, they did not agree with how she did it. CEO Jim Franklin wrote in a blog that “Publicly shaming the offenders—and bystanders—was not the appropriate way to handle the situation.”
The incident became a point of controversy. The situation and related firings were debated on social media sites and became heated. After firing Richards, SendGrid experienced a Distributed Denial of Service (DDoS) attack. People also noted that while Richards claimed she was taking a stand against the sexist comments and jokes with sexual overtones, as seen in Figure 9.2, she had made them herself during the week of the conference, prior to the incident.
Figure 9.2. Inappropriate tweet by Adria Richards.
As is the way of the Internet, additional information about Richards appeared on sites. Her previous history at conferences was reported by tech conference organizer Amanda Blum, who wrote on a blog (http://amandablumwords.wordpress.com/2013/03/21/3/) about Richards’ past conduct. During a New York conference, there had been a session by Danielle Morrill (www.daniellemorrill.com) called “Getting the Money Shot,” which jokingly made reference to thinking like a porn director while creating a screencast. Richards took offense, but didn’t say anything to the speaker or conference organizers. Instead, in a podcast, she threatened to boycott the conference for promoting porn, and when speaking at a session, spent her time talking about how porn had no place at the conference.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597499866000096
Collecting the Volatile Data from a Router
Dale Liu, in Cisco Router and Switch Forensics, 2009
Analyzing What Happened
In collecting volatile evidence from a Cisco router, you are attempting to analyze network activity to discover the source of security policy violations or a data or system breach. The forensic analysis of a Cisco router is straightforward in theory, but complicated in practice due to the volatility of the evidence. Much of the data that you collect will not be of use to the analysis, but without it, you cannot demonstrate a systematic process.
Routers are not a goal in themselves, but act as platforms for other attacks. Routers are used to drill into networks, bypassing firewalls and intrusion detection systems (IDSs), and to attack other organizations or systems.
Your goal is to be able to use the evidence you have collected to analyze behavior and pinpoint any anomalous or harmful behavior. This can aid in reconstructing what occurred. This process adds evidence as to which activities occurred and how these have led to a breach or other incident.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597494182000090
Securing the Smart Grid
Eric D. Knapp, Raj Samani, in Applied Cyber Security and the Smart Grid, 2013
Where to monitor
Based on the advice given so far, the trite answer is, “everywhere!” However, there’s a broader concept of “where” that applies to the grid. For example, what domains should be monitored? What zones? Well, the answer is still trite, and it’s still “everywhere!” However, the concept of domains and zones by definition means that the systems will be separated from each other, and often there will be (or at least should be) hard cyber security perimeters between them.
Therefore, in many cases the information will need to be collected locally within a domain or within a specific zone within a domain. In some cases, there will be no network path at all to a centralized facility (i.e. the mythical “air gap”), and in many cases, there will be hard security restrictions in place. For example, in nuclear generation facilities, there is a clear one-way communication requirement between secure zones and unsecure zones: if a network connection is used at all, it must only support outbound communication, so that information can be obtained from a reactor for use by business systems, but malware or malicious control cannot be sent from the insecure location back to the reactor. Local information can therefore be collected by a local SIEM that is deployed within the secure facility. The collected data can then be sent, one-way over a data diode or unidirectional network gateway, to a SIEM located centrally.
In most areas, however, establishing a secure connection for the bi-directional communication of collected data is enough. Fortunately, most SIEM tools on the market today support encrypted transfer of data when deployed in a distributed manner—many of which are actually certified “secure” under standards such as common criteria (which certifies system security) and FIPS 140-2 (which certifies secure and cryptographic boundaries).
Once information is being collected from within and between zones, simple correlation rules within the SIEM can be used to detect policy violations, for example, controllers communicating with IEDs in a separate zone, or administrators authenticating to servers in a separate domain. These types of deviations are clear indicators of risk—someone or something is behaving in a way that may seem normal but has not been explicitly allowed—but also of threats. This is because most methods used by attackers will violate these strict policy definitions. The trick is to “teach” these policies to the SIEM so that it can detect the violation. This requires configuring the SIEM with domain and zone knowledge, as well as user roles and responsibilities, and any other relevant policy information. This can be done by the following:
- •
-
Establishing lists of IP addresses or IP ranges (subnets) that are authorized within a defined zone, typically by defining and populating variables within the SIEM.
- •
-
Defining access rules (this controller is only allowed to communicate with these field devices) within the SIEM, typically via correlation rules assessing network flow data.
- •
-
Establishing users, groups, and roles as actionable variables within the SIEM, typically done automatically through integration with LDAP or Active Directory, but sometimes requiring manual variable definitions.
- •
-
Defining allowed user/asset interactions, again using correlation rules to assess established user knowledge against defined zones.
Note
Segmented monitoring and situational awareness
Just as monitoring can be distributed within and between different systems, zones and domains, security analysis can also be distributed. The security management tools that provide situational awareness—SIEM, log management systems, etc.—typically consist of separate components for the collection of data (“visibility”) and the analysis of data (“awareness”). Most commercial solutions allow either component to be distributed, feeding back into one or more centralized location. For example, a collector appliance might be deployed across several plants to feed data back to a centralized analysis appliance.
But what about areas that require a first-line defense capability? In these areas, the “analysis” portion of the solution can be distributed as well, providing the critical facility with the ability to collect and analyze local data. At the same time, those data can still be fed back to a central location for further analysis;—however, now there is localized situational awareness as well, to support incident detection, investigation and remediation inside of the secure facility. This type of distributed situational awareness is widely adopted in high-security facilities such as nuclear generation plants, but is also applicable within the Smart Grid, providing localized situational awareness to crews within substations, dispatch facilitates, etc.
This methodology can also be extended in the other direction: feeding data up even further, to provide remote situational awareness to a trusted third party who provides managed security services.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597499989000062
Pervasive Sensing and Monitoring for Situational Awareness
Sharad Mehrotra, … Carolyn Talcott, in Handbook on Securing Cyber-Physical Critical Infrastructure, 2012
20.6.3 Privacy Policy Enforcement through “Privacy as a Constraint”
Given that we can specify privacy policies, the next challenge is to develop mechanisms to enforce such policies. Given a sensor data produced that may result in a policy violation, the system will obfuscate the data to the degree such that the data shared does not result in the policy violation. This is, however, a complex task given that the policy violation might not be caused directly by the sensor data under consideration but rather through an inference made using the sensor data. One of the approaches to obfuscate the resulting sensor data is to add controlled amount of noise in the released data to prevent direct or indirect violation of policy. Such an approach is adopted, for instance, in PoolView [120] in the context of participatory sensing. In PoolView, clients (subjects) independently perturb their data using an application-specific noise model. The noise model is robust to reconstruction attacks and yet allows computation of aggregate property of the data by appropriately cancelling the noise. A similar technique is also used in PreSense [121] to support computation of certain aggregation functions. Although the approach to controlled noise addition has worked in certain situations, a more general system based on such a technique that may work for diverse sensor data-sharing applications has yet to be devised. One can possibly argue that such a general solution that provides privacy guarantees irrespective of the types and nature of inferences possible in the pervasive space will necessarily be very pessimistic. A system built under the worst case assumption of adversarial knowledge will possibly have too low utility for practical purposes.
An alternate approach to designing privacy-preserving data sharing for pervasive spaces is to first explicitly model and represent domain knowledge that capture all the laws of inference in the system. Such domain knowledge may be a result of a combination of developing a formal model of the pervasive space that allows for reasoning and/or rules inducted from past sensor logs generated. Given such a knowledge representation, one can use a policy reasoning algorithm as part of the enforcement mechanism, to filter information being gathered. Given a formal model of information and general inference rules, one can carry out analyses such as whether a given privacy policy can be enforced, and using model-checking and other formal analysis tools, one can detect cases where given set of policies allows information to leak. Reference [40] proposes such a model-driven policy enforcement approach. This paper proposes an interactive model wherein the system starts with some generic knowledge (either explicitly specified or gained through mining using logs of the pervasive space). In addition, the knowledge can be refined through interaction with users if a privacy violation occurs. If the outcome of the formal analysis establishes possible violations of privacy policies through inference, different information hiding techniques are used to prevent such information leakage. These techniques use a range of data modification approaches such as coarsening, perturbation, and transformation or clustering. Coarsening, for instance, refers to changing the resolution at which an attribute value is revealed. Typically, for categorical attributes, taxonomies or some form of partial order defined on the domain is used to coarsen the value. For instance, if the location information is captured at the room level, and “room<floor<building” denotes the partial order, then coarsening may result in Bob’s location being revealed only at the building level. The goal in such an approach is minimal modification of the data such that no policy violations occur or number of such violations are limited. An alternate mechanism that could be used is clustering which will group a set of events to make them indistinguishable from each other. For instance, “Bob entered smoking lounge” may be clubbed together with “Alice entered the elevator” and “Tom exited the building.” In effect, the observer only knows that one of these three events occurred. Notice that such an approach is based on the assumption that it is possible to perform data modifications, associate a measure of disclosure with the modified representation, and choose the least modification that meets the disclosure control requirements. Although sometimes this is not difficult – for instance, in the case when events are location updates, in general, this is a significant challenge. Indeed, the space of possible data modifications may be exponential (or perhaps even unbounded), disclosure depends on the model of adversarial knowledge (inference rules) and might not be easily quantifiable, and identification of the optimal solution is a combinatorial challenge.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9780124158153000200
Technical Investigations
Brett Shavers, in Placing the Suspect Behind the Keyboard, 2013
Summary
Attributing computer use to a specific person or persons is just as important as a forensic analysis of the computer device to uncover the criminal activity, civil violations, or internal policy violations. The ongoing process of creating a timeline does not have a beginning or end, as it is constantly changing with new information added as it is discovered.
Although there are few, if any, evidentiary items which can place a suspect behind a keyboard with absolute certainty, the culmination of a forensic analysis of activity combined with traditional investigative methods can result in substantial circumstantial evidence. Circumstantial evidence that eliminates persons of interest integrated with corroborating sources of evidence contributes to conclusions that no other person but the suspect could have been behind the keyboard.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9781597499859000046
SDN Futures
Paul Göransson, … Timothy Culver, in Software Defined Networks (Second Edition), 2017
Flowguard
In [39] authors propose Flowguard, an SDN firewall capable of filtering not only at the packet level but also at the flow level. An entire flow may violate policy and should thus be rejected. A key theme of the authors is that flow policy changes may be in conflict with firewall policy and resolving these conflicts is the responsibility of an SDN firewall. Thus the authors assert that an SDN firewall is both a packet filter and also a policy checker. In Flowguard, flow packet violations are distinguished from a broader class of flow policy violations. Flow policy violations may occur when a new flow is installed or when policy is changed. The simpler of the two cases is when a new flow is installed. This may violate existing policy and may thus be rejected. It is more complicated when flow policy is changed as this change can cause a violation of firewall policy. The authors illustrate this via a simple example of an OpenFlow-based load balancer which may alter packet header fields in order to change flow paths. When flows are modified by this load balancer, it is imperative that the packet header fields modified by the OpenFlow rules do not result in a firewall rule being circumvented. In order to prevent this, an SDN firewall must check that flow policy does not conflict with firewall policy. Flowguard decomposes this policy conflict problem into entire violations and partial violations. Outcomes may include rejection of the policy update, removal of affected flows or, in the case of a partial violation, specific packet blocking. The authors contrast Flowguard with Veriflow which, as described in Section 15.3.2 does not do its flow analysis in real time. Flowguard, however, does work in real time. The authors provide data that shows that Flowguard performs favorably as compared with Floodlight’s built-in firewall.
Read full chapter
URL:
https://www.sciencedirect.com/science/article/pii/B9780128045558000156
Posted by Jorge on 2015-03-12
You may be testing SSPR or a user may actually be using it to reset its own password and the following error is presented.
Figure 1: The Password Does Not Comply With Your Organization’s Password Policies
–
When you look in the Forefront Identity Manager Event Log you will see the following event ID 3
Figure 2: The Password Reset Activity In The Password Reset Action Workflow Failed Due To A Policy Violation
–
PWReset Activity’s MIIS Password Set call failed because of a policy violation.
–
…And you will also see the following error, which does not tell you anything
Figure 3: Service Fault Exception – DataRequiredFaultReason
–
The web portal received a fault error from the FIM service.
Details:
Microsoft.ResourceManagement.WebServices.Faults.ServiceFaultException: DataRequiredFaultReason
at Microsoft.ResourceManagement.WebServices.ResourceFactoryClient.Create(Message request)
at Microsoft.IdentityManagement.CredentialManagement.Portal.Common.ResetProxy.InteractWithPasswordResetActivity(SecureString newPassword, String activityEndpoint, String workflowInstanceId, ContextualSecurityToken sessionSecurityToken)
Web Portal: FIM Password Reset Portal
Session Id: xlei5mqvkukke145sjxbu355
IP Address: 10.1.1.32
–
A password policy consists of the following policy settings:
- Enforce password history X passwords remembered
- Maximum password age X days
- Minimum password age X days
- Minimum password length X characters
- Password must meet complexity requirements Disabled
- Store passwords using reversible encryption
–
A password change will always enforce all policy settings, except policy setting [2] (The maximum password age is what actually triggers the password change)
–
A regular password reset or a password reset through FIM SSPR while policy enforcement is disabled will by default enforce all policy settings, except the policy settings [2], [1] and [3]. When policy enforcement is enabled as specified in «FIM 2010 Self Service Password Reset now supports Enforcement of all domain password policies«, it will also enforce policy setting [1] and [3], and therefore the password reset will behave like a password change. Be aware of that!
–
Cheers,
Jorge
———————————————————————————————
* This posting is provided «AS IS» with no warranties and confers no rights!
* Always evaluate/test yourself before using/implementing this!
* DISCLAIMER: https://jorgequestforknowledge.wordpress.com/disclaimer/
———————————————————————————————
############### Jorge’s Quest For Knowledge #############
######### http://JorgeQuestForKnowledge.wordpress.com/ ########
———————————————————————————————
This entry was posted on 2015-03-12 at 23:00 and is filed under Forefront Identity Manager (FIM) Portal, Self Service Password Reset.
You can follow any responses to this entry through the RSS 2.0 feed.
You can leave a response, or trackback from your own site.