In this article, we’ll describe how to get and audit the RDP connection logs in Windows. The RDP connection logs allow RDS terminal servers administrators to get information about which users logged on to the server when a specific RDP user logged on and ended up the session, and from which device (DNS name or IP address) the user logged on.
Contents:
- RDP Connection Events in Windows Event Viewer
- Getting Remote Desktop Login History with PowerShell
- Outgoing RDP Connection Logs in Windows
The article is applicable when analyzing RDP logs for both Windows Server 2022/2019/2016/2012R2 and to desktop editions (Windows 11, 10, and 8.1).
RDP Connection Events in Windows Event Viewer
When a user connects to a Remote Desktop-enabled or RDS host, information about these events is stored in the Event Viewer logs (eventvwr.msc). Consider the main stages of RDP connection and related events in the Event Viewer, which may be of interest to the administrator
- Network Connection;
- Authentication;
- Logon;
- Session Disconnect/Reconnect;
- Logoff.
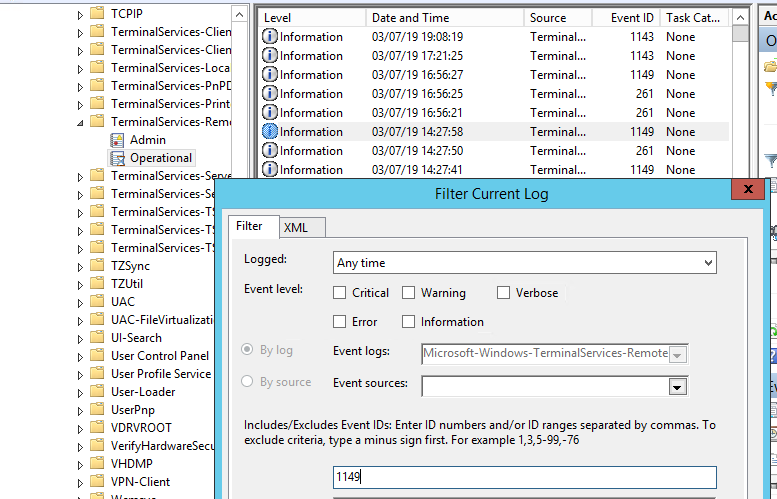
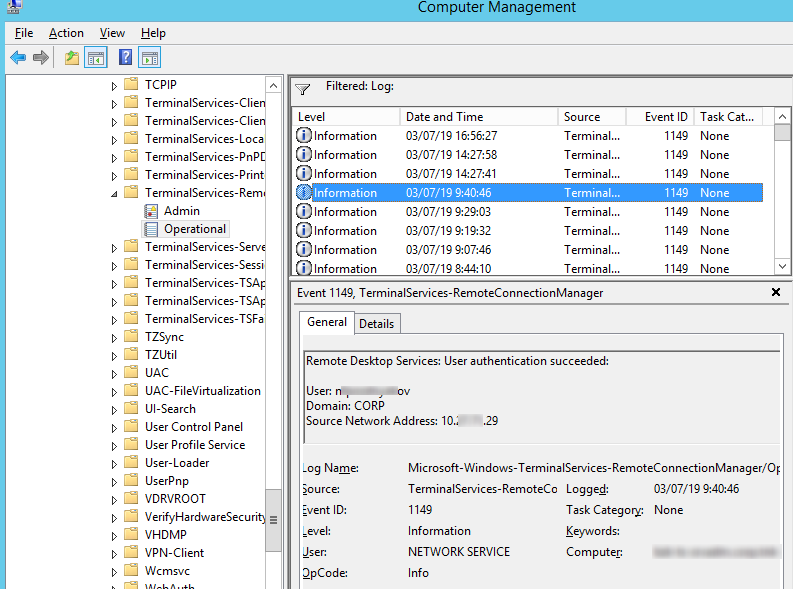
Network Connection – establishing a network connection to a server from the user’s RDP client. It is the event with the EventID 1149 (Remote Desktop Services: User authentication succeeded). If this event is found, it doesn’t mean that user authentication has been successful. This log is located in “Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational”. Enable the log filter for this event (right-click the log -> Filter Current Log -> EventId 1149).
You can list all RDP connection attempts with PowerShell:
$RDPAuths = Get-WinEvent -LogName 'Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational' -FilterXPath '<QueryList><Query Id="0"><Select>*[System[EventID=1149]]</Select></Query></QueryList>'
[xml[]]$xml=$RDPAuths|Foreach{$_.ToXml()}
$EventData = Foreach ($event in $xml.Event)
{ New-Object PSObject -Property @{
TimeCreated = (Get-Date ($event.System.TimeCreated.SystemTime) -Format 'yyyy-MM-dd hh:mm:ss K')
User = $event.UserData.EventXML.Param1
Domain = $event.UserData.EventXML.Param2
Client = $event.UserData.EventXML.Param3
}
} $EventData | FT
Then you will get an event list with the history of all RDP connections to this server. The logs provide a username, a domain (in this case the Network Level Authentication is used; if NLA is disabled, the event description looks differently), and the IP address of the user’s computer.
Authentication shows whether an RDP user has been successfully authenticated on the server or not. The log is located under Windows -> Security. So, you may be interested in the events with the EventID 4624 (An account was successfully logged on) or 4625 (An account failed to log on).
Please, pay attention to the LogonType value in the event description.
- LogonType = 10 or 3 — if the Remote Desktop service has been used to create a new session during log on;
- LogonType = 7, means that a user has reconnected to the existing RDP session;
- LogonType = 5 – RDP connection to the server console (in the mstsc.exe /admin mode).
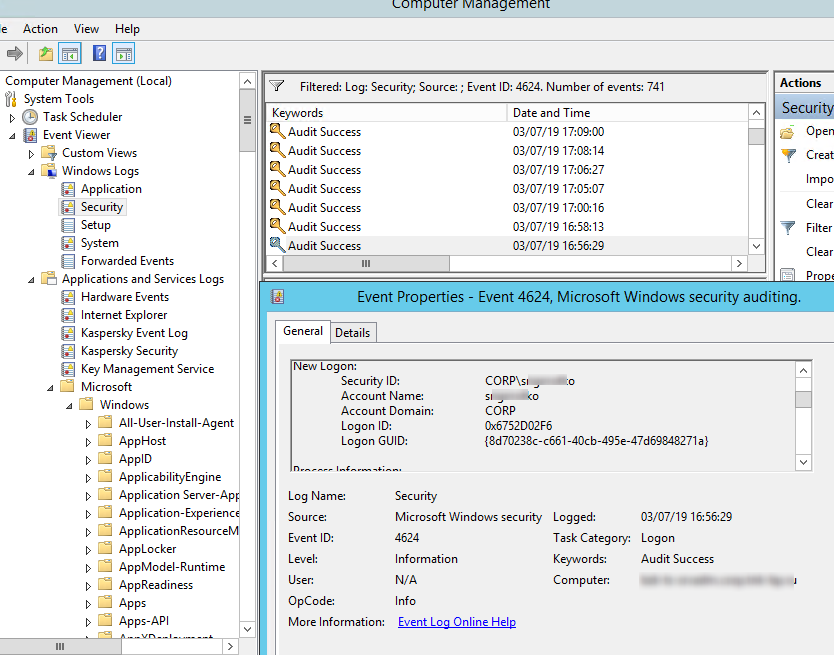
In this case, the user name is contained in the event description in the Account Name field, the computer name in the Workstation Name, and the user IP in the Source Network Address.
Please, note the value of the LogonID field. This is a unique user RDP session identifier that helps track the user’s further activity. However, if an RDP session is disconnected and a user reconnects to it, the user will be assigned a new LogonID (although the RDP session remains the same).
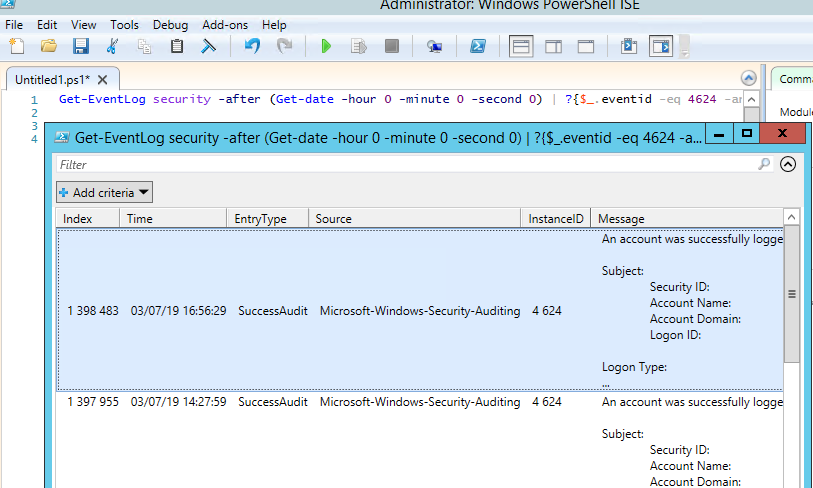
You can get a list of successful RDP authentication events (EventID 4624) using this PowerShell command:
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ?{$_.eventid -eq 4624 -and $_.Message -match 'logon type:s+(10)s'} | Out-GridView
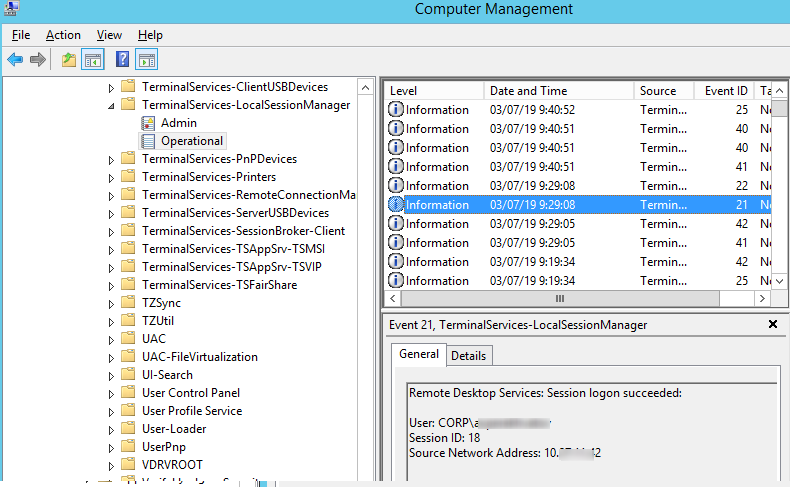
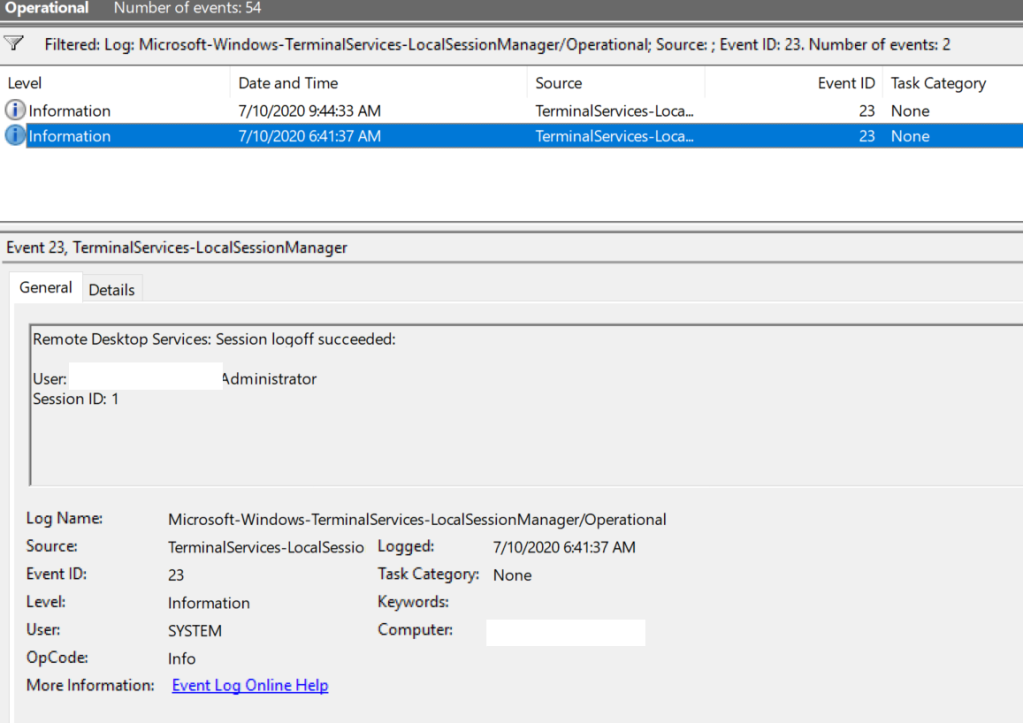
Logon refers to an RDP login to Windows. EventID 21 – this event appears after a user has been successfully authenticated (Remote Desktop Services: Session logon succeeded). This events are located in the “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. As you can see, here you can find the ID of a user RDP session — Session ID.
EventID – 21 (Remote Desktop Services: Shell start notification received) indicates that the Explorer shell has been successfully started (the Windows desktop appears in the user’s RDP session).
Session Disconnect/Reconnect – session disconnection and reconnection events have different IDs depending on what caused the user disconnection (disconnection due to inactivity set in timeouts for RDP sessions, Disconnect option has been selected by the user in the session, RDP session ended by another user or an administrator, etc.). You can find these events in the Event Viewer under “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”. Let’s consider the RDP Event IDs that might be useful:
- EventID – 24 (
Remote Desktop Services: Session has been disconnected) –a user has disconnected from the RDP session; - EventID – 25 (
Remote Desktop Services: Session reconnection succeeded) – a user has reconnected to the existing RDP session on the server; - EventID – 39 (
Session <A> has been disconnected by session <B>) – a user has disconnected from the RDP session by selecting the corresponding menu option (instead of just closing the RDP client window). If the session IDs are different, a user has been disconnected by another user (or administrator); - EventID – 40 (
Session <A> has been disconnected, reason code <B>). Here you must check the disconnection reason code in the event description. For example:- reason code 0 (
No additional information is available) means that a user has just closed the RDP client window; - reason code 5 (
The client’s connection was replaced by another connection) means that a user has reconnected to the previous RDP session; - reason code 11 (
User activity has initiated the disconnect) a user has clicked the Disconnect button in the start menu.
- reason code 0 (
EventID 4778 in Windows -> Security log (A session was reconnected to a Window Station). A user has reconnected to an RDP session (a user is assigned a new LogonID).
EventID 4779 in “Windows -> Security” log (A session was disconnected from a Window Station). A user has been disconnected from an RDP session.
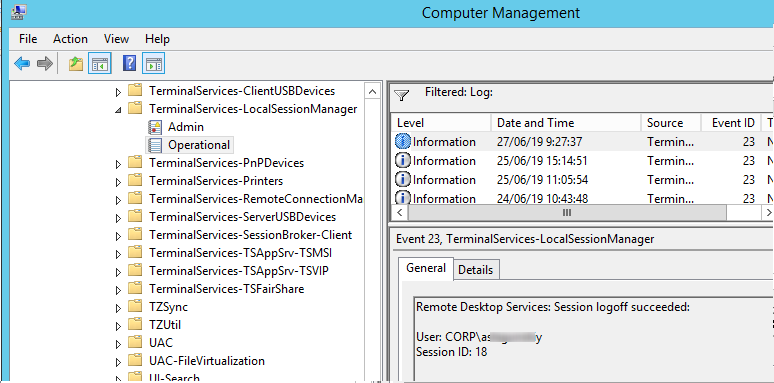
Logoff refers to the end of a user session. It is logged as the event with the EventID 23 (Remote Desktop Services: Session logoff succeeded) under “Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-LocalSessionManager -> Operational”.
At the same time the EventID 4634 (An account was logged off) appears in the Security log.
The EventID 9009 (The Desktop Window Manager has exited with code <X>) in the System log means that a user has initiated logoff from the RDP session with both the window and the graphic shell of the user have been terminated.
EventID 4647 — User-initiated logoff
Getting Remote Desktop Login History with PowerShell
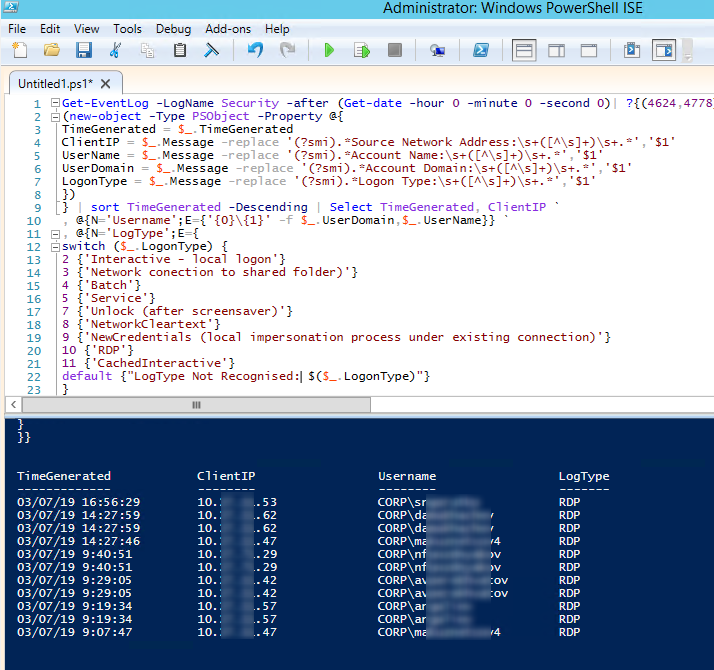
Here is a short PowerShell script that lists the history of all RDP connections for the current day from the terminal RDS server event logs. The resulting table shows the connection time, the client’s IP address (DNS computername), and the remote user name (if necessary, you can include other LogonTypes in the report).
Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ?{(4624,4778) -contains $_.EventID -and $_.Message -match 'logon type:s+(10)s'}| %{
(new-object -Type PSObject -Property @{
TimeGenerated = $_.TimeGenerated
ClientIP = $_.Message -replace '(?smi).*Source Network Address:s+([^s]+)s+.*','$1'
UserName = $_.Message -replace '(?smi).*ssAccount Name:s+([^s]+)s+.*','$1'
UserDomain = $_.Message -replace '(?smi).*ssAccount Domain:s+([^s]+)s+.*','$1'
LogonType = $_.Message -replace '(?smi).*Logon Type:s+([^s]+)s+.*','$1'
})
} | sort TimeGenerated -Descending | Select TimeGenerated, ClientIP `
, @{N='Username';E={'{0}{1}' -f $_.UserDomain,$_.UserName}} `
, @{N='LogType';E={
switch ($_.LogonType) {
2 {'Interactive - local logon'}
3 {'Network connection to shared folder)'}
4 {'Batch'}
5 {'Service'}
7 {'Unlock (after screensaver)'}
8 {'NetworkCleartext'}
9 {'NewCredentials (local impersonation process under existing connection)'}
10 {'RDP'}
11 {'CachedInteractive'}
default {"LogType Not Recognised: $($_.LogonType)"}
}
}}
This method allows you to collect and parse RDP connection logs on a standalone RDSH server. If you have multiple servers in the RDS farm, you can query each of them with this script, or get logs from a management server with the Remote Desktop Connection Broker role.
You can export RDP connection logs from the Event Viewer to a CSV file (for further analysis in an Excel spreadsheet). You can export the log from the Event Viewer GUI (assuming Event Viewer logs are not cleared) or via the command prompt:
WEVTUtil query-events Security > c:psrdp_security_log.txt
Or with PowerShell:
get-winevent -logname "Microsoft-Windows-TerminalServices-LocalSessionManager/Operational" | Export-Csv c:psrdp_connection_log.txt -Encoding UTF8
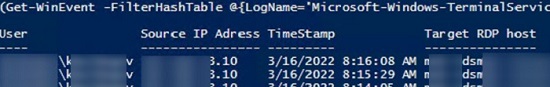
If your users connect to corporate RDS hosts through the Remote Desktop Gateway, you can check the user connection logs in the Microsoft-Windows-TerminalServices-Gateway log by the EventID 302. For example, the following PowerShell script will display the specified user’s connection history through RD Gateway:
$rdpusername="b.smith"
$properties = @(
@{n='User';e={$_.Properties[0].Value}},
@{n='Source IP Adress';e={$_.Properties[1].Value}},
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='Target RDP host';e={$_.Properties[3].Value}}
)
(Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-Gateway/Operational';ID='302'} | Select-Object $properties) -match $rdpusername
You can check the following RD Gateway user connection events in the Microsoft-Windows-TerminalServices-Gateway event log:
- 300 — The user NAME, on client computer DEVICE, met resource authorization policy requirements and was therefore authorized to connect to resource RDPHOST;
- 302 — The user NAME, on client computer DEVICE, connected to resource RDPHOST;
- 303 — The user NAME, on client computer DEVICE, disconnected from the following network resource: RDPHOST. Before the user disconnected, the client transferred X bytes and received X bytes. The client session duration was X seconds.
You can display the list of current remote sessions on your RDS host with the command:
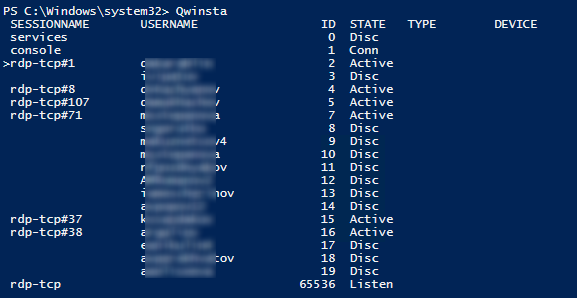
qwinsta
The command returns the session ID, the USERNAME, and the session state (Active/Disconnect). This command is useful when you need to get the user’s RDP session ID when using shadow Remote Desktop connections.
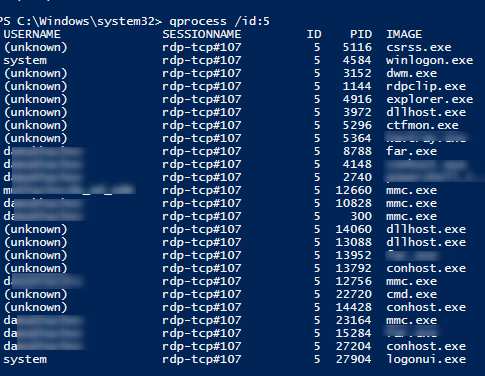
You can display the list of the running processes in the specific RDP session (the session ID is specified):
qprocess /id:5
Outgoing RDP Connection Logs in Windows
You can also view outgoing RDP connection logs on the client side. They are available in the following event log: Application and Services Logs -> Microsoft -> Windows -> TerminalServices-ClientActiveXCore -> Microsoft-Windows-TerminalServices-RDPClient -> Operational.
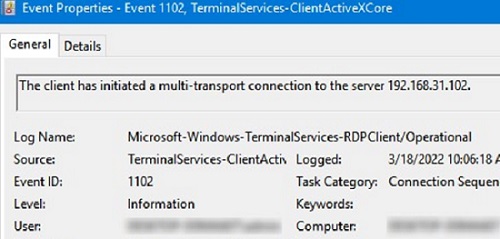
For example, EventID 1102 occurs when a user connects to a remote Windows Server RDS host or a Windows 10/11 computer with RDP enabled (desktop Windows editions also support multiple simultaneous RDP connections).
The client has initiated a multi-transport connection to the server 192.168.13.201.
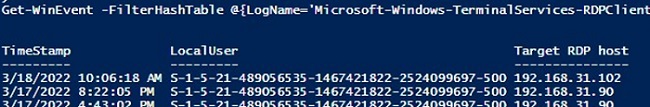
The following RDP script will display the history of RDP client connections on the current computer:
$properties = @(
@{n='TimeStamp';e={$_.TimeCreated}}
@{n='LocalUser';e={$_.UserID}}
@{n='Target RDP host';e={$_.Properties[1].Value}}
)
Get-WinEvent -FilterHashTable @{LogName='Microsoft-Windows-TerminalServices-RDPClient/Operational';ID='1102'} | Select-Object $properties
The script returns the SIDs of the users who initiated RDP connections on this computer, as well as the DNS names/IP addresses of the Remote Desktop hosts that the users connected to. You can convert SIDs to usernames as follows.
Table of Contents
- Overview:
- Covered in this Article:
- Environment Configuration:
- RDP connection scenario sequences:
- Items to Collect for Troubleshooting:
- Tracing and Logging:
- Event Viewer:
- To show Analytic and Debug Logs:
- Network:
- Capturing a network trace:
- Event Viewer:
- Troubleshooting:
- Client:
- Common items to check:
- Network:
- Windows Event Logs:
- Common RDP client errors:
- RDSH Server:
- Common items to check:
- Network:
- Windows Event Logs:
- Common RDSH Server errors:
- RDS License Server:
- Common items to check:
- Network:
- Windows Event Logs:
- Common RDS License errors:
- Client:
- Tools:
- Logman
- Message Analyzer
- Network Monitor
- NetSH
- Process Explorer
- Process Monitor
- Reference
Overview:
In supporting RDS, the two most common issues are the connection / reconnection process and licensing. This article is to document the RDP connection and licensing sequence that takes place for the most common RDP connection scenarios. All information provided
is available through event logs and network tracing. Understanding the connection and licensing process should make troubleshooting a connection issue easier.
Covered in this Article:
- An overview of the connection sequence when you establish a direct RDP connection using NLA which is default.
- Network ports used in the RDP connection process.
- Details on what tracing and logging you can gather to troubleshoot RDP connection problems.
- Links to detailed trace and log information broken out by the type of tracing and by component.
Environment Configuration:
The environment that was used for testing unless noted differently in the specific scenarios sections is as follows:
- Azure RDS IaaS cloud only deployment
- All machines are Windows 2012 r2 with latest fixes at time of testing including the ‘client’
- All machines are on the same network and in same domain
- One forest and domain at 2012 functional level with one domain controller using Kerberos authentication
- All tests are using Remote Desktop Services role and not Remote Administration
- All tests use a single Windows 2012 RDS License server in per user mode
RDP connection scenario sequences:
- RDP Direct Connection Process with NLA Enabled
Items to Collect for Troubleshooting:
- Has anything changed?
- Is this a new configuration?
- Has this connection ever worked?
- Does this connection always fail?
- Time of issue if intermittent.
- If intermittent, is connection a new connection or a reconnect?
- Name of:
- user account
- client machine name and IP
- server machine name and IP
- session ID
- Client disconnect codes / reasons given on screen and in event logs.
- OS version and hotfix levels.
- Isolate issue as much as possible. Some examples:
- Specific user or user profile
- Specific client or server machine
- Specific OS or build
- Specific network
- Specific connection process (internal vs external)
Tracing and Logging:
There are multiple Windows Event Logs that are valuable for troubleshooting RDS connectivity issues. This along with network tracing and sometimes process monitor can solve most of the common issues. Enabling ‘Show Analytic and Debug Logs’ will display the
debug logs which will often provide better detail into an issue from the View menu option in Event Viewer. The debug logs can trace a lot of information and should only be used when actively troubleshooting an issue. All of the Event Logs being discussed are
under the ‘Applications and Services Logs/Microsoft/Windows’ node in Event Viewer.
Event Viewer:
To show Analytic and Debug Logs:
Once the Additional logs are displayed, the will most likely need to be enabled by right-clicking and selecting ‘Enable log’.
These logs are not the typical .evtx event logs and real-time .etl logs that can capture more information. Though they are not typically associated with additional overhead, it is best to disable these logs when finished troubleshooting by selecting ‘Disable
Log’
Network:
For network tracing, Microsoft Network Monitor, Wireshark are often used, however, if just gathering a trace for later analysis, the easiest method is netsh. Netsh is built into the OS and therefore requires no download or install except the first time it runs
it will add the packet driver to the network stack if it is not there.
Capturing a network trace:
Netsh has many switches to capture network traces and more. Here are example commands to start and stop a network trace using netsh from an Administrator command prompt that will capture a basic network trace. The trace max size will be 1 GB and will be
circular. The output location is c:net.etl:
To start a network capture:
netsh trace start capture=yes overwrite=yes maxsize=1024 tracefile=c:net.etl filemode=circular
To stop a network capture:
After trace has successfully stopped which can sometimes take a while, use Network Monitor or Message Analyzer to view the trace. In the example above the file is c:net.etl.
Most of the time all that is necessary from a network perspective is to check for general connectivity issues and SSL/TLS handshake issues. Common ports used by RDS such as 3389 -rdp, 443 -ssl/tls, 53 -dns, 389-ldap, 88 -kerberos,135 and ephemeral rpc. Connectivity
errors due to authentication can be seen as well as a non-response.
In example below, notice there are many predefined filters built into Network Monitor (as well as Message Analyzer). Using the predefined ‘TCPRetransmits’ and or TCPSynAndResets filters are useful for looking for connectivity problems.
NOTE: To view network traces from netsh, you will need to set the ‘Parser Profiles’ active selection to ‘Windows’ from the ‘Options’ menu item in top right of window:
Troubleshooting:
Client:
Common items to check:
- Client version — more important if Windows 7 / 2008 r2. No widespread issues with any RDP client version 8.x or above.
- Local user / admin account — if domain account is failing, trying a local account is a good test and can rule out domain issues.
- Disabling NLA (Network Level Authentication) — by default this is enabled. If there are issues authenticating (client or server having issue communicating with a domain controller), disabling NLA as a requirement on the server AND setting enablecredsspsupport:i:0
in a test.rdp file. - Mstsc /admin — mstsc /admin /v %ip address of ‘server’% is a simple test. It will bypass brokering if environment is configured with a broker and will also bypass licensing. These are two big components that can be easily ruled out with this test.
- Network — checking basic network connectivity from client to server with ping, tracert, nslookup, telnet 3389 or powershell test-netconnection
- Firewall — At minimum TCP 3389 has to be open from client to server for a direct connection. If using an RD Gateway, additional ports such as TCP 443 are needed for connectivity as well.
- Event logs — see below
- Certificates — if using a trusted certificate for the RDP listener on the server, or if using a gateway, certificates can be a cause of connection issues.
- Hotfixes / rollups — It is best practice to apply current rollups as well as staying up to date with RDS specific hotfixes. see Reference below.
Network:
- TCP outbound port 3389
- UDP outbound port 3389 (optional depending on configuration)
- SSL / TLS TCP 443
- DNS port 53
- DS port 445
- LDAP port 389
- Kerberos port 88
Windows Event Logs:
- Microsoft-Windows-TerminalServices-ClientActiveXCore
- Microsoft-Windows-TerminalServices-RDPClient/Analytic
- Microsoft-Windows-TerminalServices-RDPClient/Debug
- Microsoft-Windows-TerminalServices-RDPClient/Operational
Common RDP client errors:
There are many client errors that can be displayed and logged into the event logs that are useful for troubleshooting.
RDS Remote Desktop Client Disconnect Codes and Reasons
RDSH Server:
Common items to check:
- Licensing
- Netstat
- mstsc /v localhost
- RDP Listener
- Services
- Firewall
- Hotfixes / rollups
Network:
- TCP RDP inbound port 3389
- UDP RDP inbound port 3389
- RPC ephemeral outbound for RDS License Server
- TCP outbound port 135
- DNS port 53
- LDAP port 389
- DS port 445
- Kerberos port 88
Windows Event Logs:
- RemoteDesktopServices-RdpCoreTS/Operational
- RemoteDesktopServices-SessionServices/Operational
- TerminalServices-LocalSessionManager
- Analytic
- Debug
- Operational
- TerminalServices-RemoteConnectionManager
- Analytic
- Debug
- Operational
Common RDSH Server errors:
- Authentication
- Certificates
- Schannel encryptions and ciphers
- Domain controller connectivity
- Licensing
RDS Session Host Server Disconnect Codes
RDS License Server:
Common items to check:
- Client Access Licenses (CAL’s) available
- Services
- Firewall
- Trusts
- Group Membership
- Hotfixes / rollups
Network:
- TCP inbound rpc ephemeral
- TCP inbound port 135
- DNS port 53
- LDAP port 389
- DS port 445
- Kerberos port 88
Windows Event Logs:
- System
- Security
Common RDS License errors:
- TerminalServices-Licensing 4105 – The Terminal Services license server cannot update the license attributes for user “<UserName>” in Active Directory Domain “<DomainName>”
- https://support.microsoft.com/en-us/kb/2030310
- RPC connection failures can be seen in the Security Event Log of the License server. The RDS Server authenticates to the License server as itself. In multiple domain / forest setups there can be configuration issues that cause this authentication to fail.
Tools:
Logman
Built into OS. Gives the ability to enable / disable Debug and Analytic Event logs from command line.
Message Analyzer
Microsoft Message Analyzer is an ETW /ETL file viewer that can be used to view netmon/netsh network traces.
http://www.microsoft.com/en-us/download/details.aspx?id=44226
Network Monitor
Microsoft Network Monitor 3.4 (archive) Network trace file viewer that can be used to view netmon/netsh network traces.
http://www.microsoft.com/en-us/download/details.aspx?id=4865
NetSH
Netsh is built into the OS and therefore requires no install but is only command-line based.
To capture a network trace: netsh trace start capture=yes overwrite=yes maxsize=1024 tracefile=c:net.etl filemode=circular
To stop a network trace: netsh trace stop
To view a network trace: Use Network Monitor or Message Analyzer
Process Explorer
Used to view process information, such as utilization, thread utilization, handles, dlls.
http://live.sysinternals.com/procexp.exe
Process Monitor
Used to trace out certain events such as registry read / writes, file read / writes, network connectivity, and system events like thread start.
http://live.sysinternals.com/procmon.exe
Reference
Welcome to Remote Desktop Services (MSDN Remote Desktop Services Overview)
Downloadable PDF
Azure desktop hosting — Reference architecture and deployment guides
Windows 2012 Capacity planning guide
RDS 2012: Which ports are used during deployment?
Available Updates for Remote Desktop Services in Windows Server 2012 R2
Remote Desktop Services Blog
Remote Desktop Services Forums
RDS 2012 Session Host deployment scenarios
RDS 2012 session deployment scenarios
Standard Deployment
RDS 2012 session deployment scenarios
Server Role Deployment
RDS 2012 session deployment scenarios Quick Start
Guidelines for installing the Remote Desktop Session Host role service on a computer running Windows Server 2012 without the Remote Desktop Connection Broker role service
Best practices for setting up Remote Desktop Licensing (Terminal Server Licensing) across Active Directory Domains/Forests or Workgroup
RD Licensing Configuration on Windows Server 2012
Specify a License Server for an RD Session Host Server to Use
Troubleshooting Remote Desktop Licensing Issues
Remote Desktop Licensing Demystified
In this article we will take a look at the features of Remote Desktop Protocol (RDP) connection auditing and log analysis in Windows. Typically, it is useful when investigating various incidents on Windows servers when a system administrator is required to provide information about what users logged on to the server, when he logged on and off, and from which device (name or IP address) the RDP user was connecting.
Remote Desktop Connection Events
Like other events, the Windows RDP connection logs are stored in the event logs. The Windows logs contain a lot of information, but it can be difficult to find the right event quickly. When a user remotely connects to a Windows server, many events are generated in the Windows logs. We will take a look at the following:
- Network Connection
- Authentication
- Logon
- Session Disconnect/Reconnect
- Logoff
Network Connection Events
Network Connection connects user’s RDP client with the Windows server. That logs EventID – 1149 (Remote Desktop Services: User authentication succeeded). The presence of this event does not indicate successful user authentication. This log can be found at Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ Terminal-Services-RemoteConnectionManager ⇒ Operational. You can filter this log by right clicking on Operational log ⇒ Selecting “Filter Current Log” and type in EventID 1149.
The result is a list with the history of all network RDP connections to this server. As you can see, the log file contains the username, domain (When Network Level Authentication (NLA) authentication is used), and IP address of the computer from which the RDP connection is made.
Authentication Events
User authentication can be successful or unsuccessful on the server. Navigate to Windows logs ⇒ Security. We are interested in logs with EventID – 4624 (An account was successfully logged on) or 4625 (An account failed to log on). Pay attention to the LogonType value in the event. LogonType – 10 or 3 indicates a new logon to the system. If LogonType is 7, it indicates re-connection to an existing RDP session.
The username of the connecting account is written in the Account Name field, his computer name is written in Workstation Name, and the IP address in Source Network Address.
Take a look at TargetLogonID field, which is a unique user session identifier that can be used to track further activity of this user. However, if a user disconnects from the RDP session and reconnects to the session again, the user will be issued a new TargetLogonID (although the RDP session remains the same).
You can get a list of successful authentication events over RDP (EventID 4624) using the following PowerShell command:
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ?{$_.eventid -eq 4624 -and $_.Message -match 'logon type:s+(10)s'} | Out-GridView
Logon Events
RDP logon is the event that appears after successful user authentication. Log entry with EventID – 21 (Remote Desktop Services: Session logon succeeded). This log can be found in Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational. As you can see here you can see the RDP Session ID for the user.
“Remote Desktop Services: Shell start received” details in EventID 21 means that the Explorer shell has been successfully launched in the RDP session.
Session Disconnect and Reconnect Events
Session Disconnect/Reconnect events have different codes depending on what caused the user to end the session, for example disable by inactivity, selecting “Disconnect” in Start menu, RDP session drop by another user or administrator, etc. These events can be found in Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational. Let’s take a look at the RDP events that may be of interest:
- EventID – 24 (Remote Desktop Services: Session has been disconnected) – the user has disconnected from the RDP session.
- EventID – 25 (Remote Desktop Services: Session reconnection succeeded) – The user has reconnected to his existing RDP session on the server.
- EventID – 39 (Session A has been disconnected by session B) – user disconnected from his RDP session by selecting the appropriate menu item (not just closed the RDP client window by clicking on “x” in the top right corner). If the session IDs are different, then the user has been disconnected by another user or administrator.
- EventID – 40 (Session A has been disconnected, reason code B). Here you should look at the reason code for the disconnection in the event. For example:
- Reason code 0 (No additional information is available) – usually indicates that the user just closed the RDP client window.
- Reason code 5 (The client’s connection was replaced by another connection) – the user re-connected to his old session.
- Reason code 11 (User activity has the disconnect) – the user clicked the Disconnect button on the menu.
- EventID – 4778 in Windows log ⇒ Security (A session was reconnected to a Window Station). The user re-connected to an RDP session (the user is given a new LogonID).
- EventID 4799 in Windows Logon ⇒ Security (A session was reconnected to a Window Station). Disconnection from an RDP session.
Logoff Events
Logoff logs track the user disconnection from the system. In the Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational logs we can find EventID 23. In this case in Security log we need to search for EventID 4634 (An account was logged off).
Event 9009 (The Desktop Window Manager has exited with code (x)) in the System log shows that the user initiated the end of the RDP session and the user’s window and graphical shell were terminated. Below is a small PowerShell that uploads the history of all RDP connections for the current day from the Remote Desktop Service server. The table below shows the connection time, client IP address, and RDP username (you can include other logon types in the report if necessary).
Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ?{(4624,4778) -contains $_.EventID -and $_.Message -match 'logon type:s+(10)s'}| %{
(new-object -Type PSObject -Property @{
TimeGenerated = $_.TimeGenerated
ClientIP = $_.Message -replace '(?smi).*Source Network Address:s+([^s]+)s+.*','$1'
UserName = $_.Message -replace '(?smi).*Account Name:s+([^s]+)s+.*','$1'
UserDomain = $_.Message -replace '(?smi).*Account Domain:s+([^s]+)s+.*','$1'
LogonType = $_.Message -replace '(?smi).*Logon Type:s+([^s]+)s+.*','$1'
})
} | sort TimeGenerated -Descending | Select TimeGenerated, ClientIP `
, @{N='Username';E={'{0}{1}' -f $_.UserDomain,$_.UserName}} `
, @{N='LogType';E={
switch ($_.LogonType) {
2 {'Interactive - local logon'}
3 {'Network conection to shared folder)'}
4 {'Batch'}
5 {'Service'}
7 {'Unlock (after screensaver)'}
8 {'NetworkCleartext'}
9 {'NewCredentials (local impersonation process under existing connection)'}
10 {'RDP'}
11 {'CachedInteractive'}
default {"LogType Not Recognised: $($_.LogonType)"}
}
}}
Exporting RDP logs
Sometimes it is needed to export RDP logs into Excel table, in this case you can upload any Windows log to a text file and afterwards import it into Excel. You can export the log from the Event Viewer console or from the command line:
WEVTUtil query-events Security > c:pssecurity_log.txt
Or:
get-winevent -logname "Microsoft-Windows-TerminalServices-LocalSessionManager/Operational" | Export-Csv c:psrdp-log.txt -Encoding UTF8
A list of the current RDP sessions on the server can be displayed as a command “Qwinsta”
The command returns as session identifier, username and status (Active/Disconnect). This command is useful when you need to determine the RDP session ID of a user during a shadow connection.
After defining a Session ID you can list running processes in a particular RDP session:
So here are the most common ways to view RDP connection logs in Windows.