Well, it is very weird. I’m using Github protection rules to enforce to make pull requests and to trigger TravisCI for every push. However, because of continuous translation, I need a user who should be able to push without making a pull request and avoiding TravisCI status check (for that I use [ci skip]). This user is included in the white list that Github provides in branch protection rules. It worked perfect since last week, suddenly when I try to push with this user I receive this:
remote: Resolving deltas: 100% (5/5), completed with 5 local objects.
remote: error: GH006: Protected branch update failed for refs/heads/master.
remote: error: Required status check "Travis CI - Pull Request" is expected. At least 1 approving review is required by reviewers with write access.
To https://github.com/*****
! [remote rejected] master -> master (protected branch hook declined)
error: failed to push some refs to 'https://*****'
It is very weird since it always worked till now. And, the user has permissions to push without making a pull request and it is skipping Travis with through the commit message so I do not understand why Github is asking me about status check and approvals.
7_R3X
3,4764 gold badges24 silver badges43 bronze badges
asked Oct 1, 2018 at 10:35
2
The latest issue I had :
remote: error: GH006: Protected branch update failed for refs/heads/master.
remote: error: Cannot force-push to this protected branch
To https://github.com/org/project.git
! [remote rejected] master -> master (protected branch hook declined)
error: failed to push some refs to 'https://github.com/org/project.git
Because I’m admin/owner I was able to go and do the following and that helped me to resolve the push problem.
Steps :
—> Settings
—>Branches
—> Tick Allow force pushes
Permit force pushes for all users with push access.
That will do the work.
answered Apr 2, 2020 at 10:36
JohnBegoodJohnBegood
5725 silver badges8 bronze badges
0
I solved it finally giving admin access to the user instead of just write access. Now it is able to push avoiding approvals and status check. But I don’t understand why does not work just being in the white list of protection branch rules… It worked before, looks like GitHub made some changes…
answered Oct 1, 2018 at 13:16
David EscaleraDavid Escalera
3891 gold badge3 silver badges8 bronze badges
1
Master [now Main] is a protected branch. You need to make a new branch and push that instead.
Seen in branch protection rules:
answered Apr 20, 2021 at 21:08
KermitKermit
4,4984 gold badges39 silver badges70 bronze badges
In my case a Branch Protection Rule was misfiring. Deleting the rule, then recreating it in GitHub fixed the issue.
answered Oct 23, 2020 at 11:37
O WigleyO Wigley
1291 silver badge4 bronze badges
In my case a security rule was somehow created for the repo. This rule allowed only admins to push. I deleted that rule and things started working as expected.
Repo > Settings > Branches > Branch protection rules [Delete]
answered Apr 20, 2021 at 14:07
singh2005singh2005
1,20312 silver badges19 bronze badges
In my case, I made a Pull (Rebase) first, and then I made Push
answered Jun 26, 2020 at 16:57
JotaPardoJotaPardo
7377 silver badges24 bronze badges
In my case git push origin HEAD fixed the problem.
answered Jun 23, 2022 at 18:31
TheodoryTheodory
1811 gold badge2 silver badges11 bronze badges
0
Содержание
- push to protected master branch without admin permissions #205
- Comments
- Footer
- Requiring Pull Requests and Reviews in Your Git Workflow
- Outline What is a pull request? If you’ve been using Git for any substantial amount of time then you have probably at least heard of pull requests. However, pull requests are not necessarily an integral part of everybody’s Git workflow. You could use Git/GitHub for years and never once have to create/merge a pull request. A pull request isn’t really anything special. If I have been working on a branch in the repository, and I push that back up to the remote branch on GitHub (or wherever), a pull request is basically a formal method to say: «Hey, I’ve got some changes over in this branch I want to merge into the main branch» Creating a pull request will allow you to review the changes that will be included and make comments about the pull request for the person(s) who will be reviewing that pull request. This then creates a more formal environment where the changes can be reviewed/discussed, and if necessary you (or others) can push further changes to that branch which will also be included in the pull request. A pull request can then be merged into the main branch either directly through Github (just by clicking a button), or by checking out the pull request locally and merging it using the command line (this will be required if there are merge conflicts that need to be resolved). NOTE: We are talking about a shared repository model in this tutorial where multiple contributors all have push access to the same shared repository. Pull requests are also heavily used in open source software where you might typically fork a repository you don’t have push access to, make some changes in your own fork, and then create a pull request to request changes from your fork be included in the original repository. Why do we want to use pull requests? As I mentioned at the beginning, there is nothing stopping any contributor in our repository from just pulling down the main branch and pushing right back to it. This violates the task branching model we are trying to follow, and we just have to hope that people follow the rules. Even if people do make a good faith effort to follow the rules in general, there will almost certainly be times where these rules are violated. Although this will be our main motivation for enforcing that pull requests are used, using pull requests and reviews is also just a good idea from a collaboration and code review perspective. Enforcing pull requests Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now. Go to Settings > Branches Click Add rule on Branch protection rules Add main as the Branch name pattern Now you can set whatever rules you want. We are going to add the following rules: Once you have enabled the rules you need, you just need to click Create . NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place. An example of the workflow with pull requests Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it: git checkout main git commit -m «pushing straight to main» NOTE: If you have not set the Include Administrators option mentioned above the push to main will work. Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating: NOTE: Creating an issue isn’t actually enforced. Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series): BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
- What is a pull request? If you’ve been using Git for any substantial amount of time then you have probably at least heard of pull requests. However, pull requests are not necessarily an integral part of everybody’s Git workflow. You could use Git/GitHub for years and never once have to create/merge a pull request. A pull request isn’t really anything special. If I have been working on a branch in the repository, and I push that back up to the remote branch on GitHub (or wherever), a pull request is basically a formal method to say: «Hey, I’ve got some changes over in this branch I want to merge into the main branch» Creating a pull request will allow you to review the changes that will be included and make comments about the pull request for the person(s) who will be reviewing that pull request. This then creates a more formal environment where the changes can be reviewed/discussed, and if necessary you (or others) can push further changes to that branch which will also be included in the pull request. A pull request can then be merged into the main branch either directly through Github (just by clicking a button), or by checking out the pull request locally and merging it using the command line (this will be required if there are merge conflicts that need to be resolved). NOTE: We are talking about a shared repository model in this tutorial where multiple contributors all have push access to the same shared repository. Pull requests are also heavily used in open source software where you might typically fork a repository you don’t have push access to, make some changes in your own fork, and then create a pull request to request changes from your fork be included in the original repository. Why do we want to use pull requests? As I mentioned at the beginning, there is nothing stopping any contributor in our repository from just pulling down the main branch and pushing right back to it. This violates the task branching model we are trying to follow, and we just have to hope that people follow the rules. Even if people do make a good faith effort to follow the rules in general, there will almost certainly be times where these rules are violated. Although this will be our main motivation for enforcing that pull requests are used, using pull requests and reviews is also just a good idea from a collaboration and code review perspective. Enforcing pull requests Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now. Go to Settings > Branches Click Add rule on Branch protection rules Add main as the Branch name pattern Now you can set whatever rules you want. We are going to add the following rules: Once you have enabled the rules you need, you just need to click Create . NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place. An example of the workflow with pull requests Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it: git checkout main git commit -m «pushing straight to main» NOTE: If you have not set the Include Administrators option mentioned above the push to main will work. Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating: NOTE: Creating an issue isn’t actually enforced. Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series): BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
- Why do we want to use pull requests? As I mentioned at the beginning, there is nothing stopping any contributor in our repository from just pulling down the main branch and pushing right back to it. This violates the task branching model we are trying to follow, and we just have to hope that people follow the rules. Even if people do make a good faith effort to follow the rules in general, there will almost certainly be times where these rules are violated. Although this will be our main motivation for enforcing that pull requests are used, using pull requests and reviews is also just a good idea from a collaboration and code review perspective. Enforcing pull requests Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now. Go to Settings > Branches Click Add rule on Branch protection rules Add main as the Branch name pattern Now you can set whatever rules you want. We are going to add the following rules: Once you have enabled the rules you need, you just need to click Create . NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place. An example of the workflow with pull requests Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it: git checkout main git commit -m «pushing straight to main» NOTE: If you have not set the Include Administrators option mentioned above the push to main will work. Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating: NOTE: Creating an issue isn’t actually enforced. Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series): BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
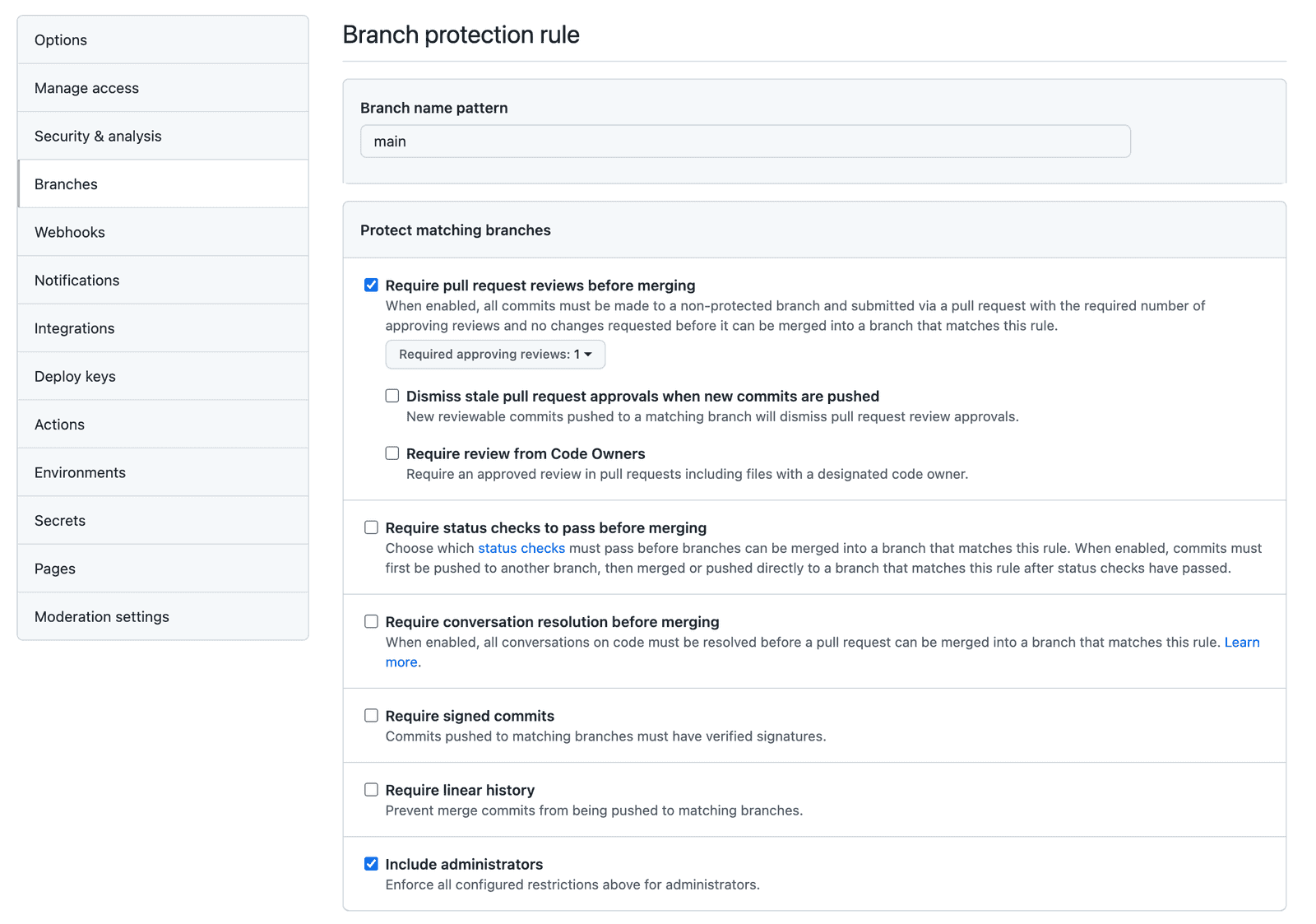
- Enforcing pull requests Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now. Go to Settings > Branches Click Add rule on Branch protection rules Add main as the Branch name pattern Now you can set whatever rules you want. We are going to add the following rules: Once you have enabled the rules you need, you just need to click Create . NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place. An example of the workflow with pull requests Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it: git checkout main git commit -m «pushing straight to main» NOTE: If you have not set the Include Administrators option mentioned above the push to main will work. Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating: NOTE: Creating an issue isn’t actually enforced. Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series): BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
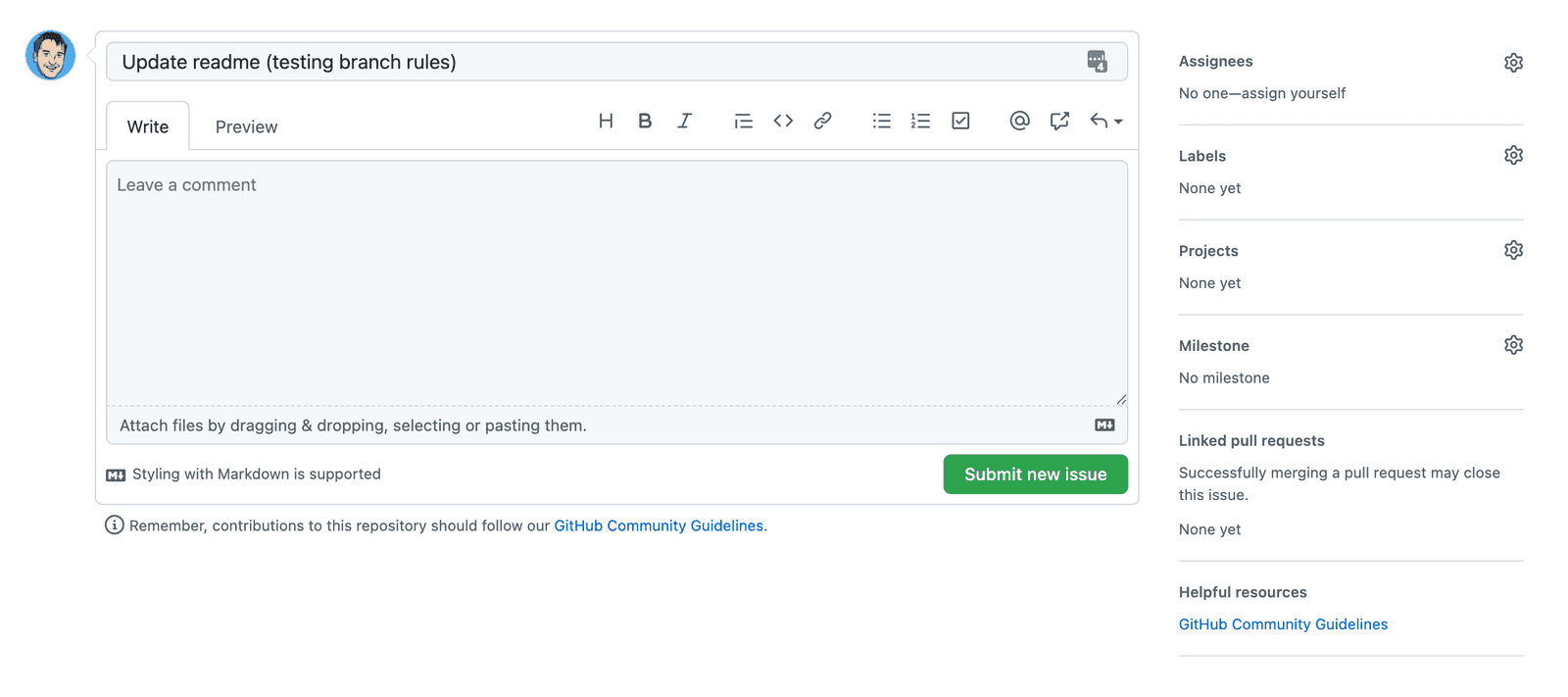
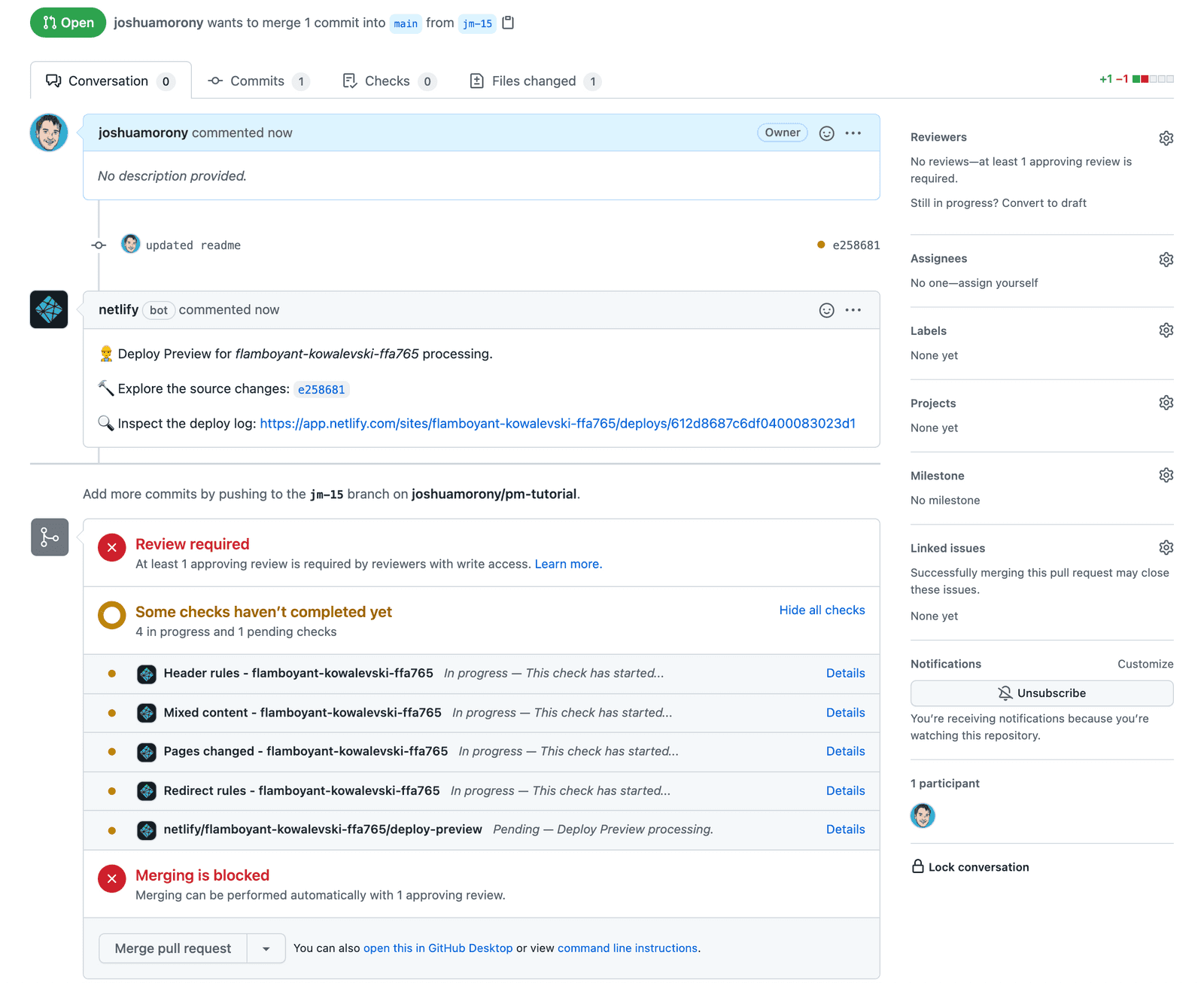
- An example of the workflow with pull requests Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it: git checkout main git commit -m «pushing straight to main» NOTE: If you have not set the Include Administrators option mentioned above the push to main will work. Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating: NOTE: Creating an issue isn’t actually enforced. Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series): BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
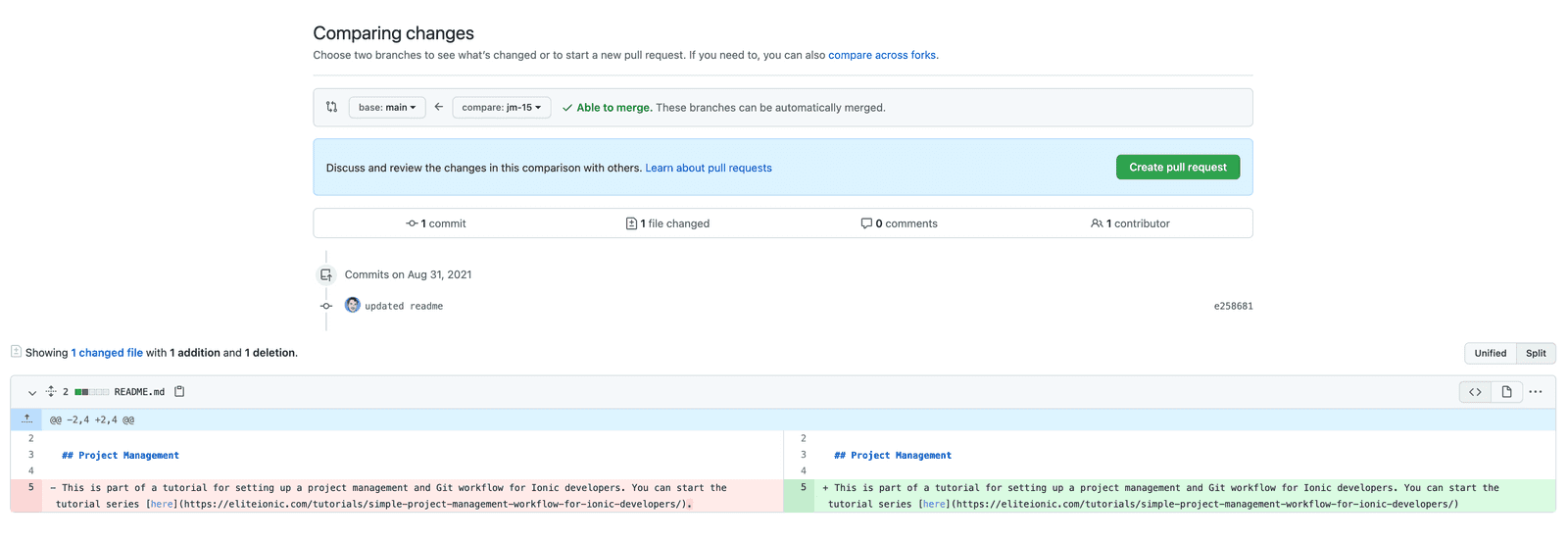
- BONUS TIP: Moving work committed onto the main branch to a feature branch Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run: To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g: NOTE: Type :q to exit the editor Then you can change back to your existing feature branch: and pull those commits into the feature branch using cherry-pick for each commit that you want to keep: To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run: This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially. Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
- Creating and merging a pull request Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main . First, we will need to push our changes up to the remote repository: NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet) If you go to Github now you will see a notice like this: You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request. You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes: Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this: The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review: To review a pull request you will need someone (who is not the person who created the pull request) to: Open the pull request and click on the Files changed tab Click Review changes Leave a comment, check Approve , and then Submit review Back on the main pull request page, click Merge pull request NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this. And we are done! Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
- Summary We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place. Источник When using protected branches (1 peer review) auto fails #1491 Comments Describe the bug We have protected branches branches turned on to ensure To Reproduce Add «Require pull request reviews before merging» Expected behavior Auto should deploy, bypassing the branch protections. Screenshots Environment information: Additional context Settings: The text was updated successfully, but these errors were encountered: Another option is to use a PAT instead of the gh action’s token. We are using a PAT. We were using the wrong token 😅 I 🙏 it works lol This isn’t really an Auto issue but rather a thought-out limitation of Github Actions: Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered. I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR. If protected branches is enabled then create a release PR rather than pushing to master. Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need: to move that behavior into core make a new hook for pushing the release make a plugin that uses that hook to do what you described I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin: Turn off branch protection during the afterVersion hook Turn on branch protection during the afterPublish hook Just gotta find the right octokit API It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection. I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can. Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection And if it the publish were to fail the branch protection rules would be lost 😢 The work to move the tag pushing into core looks like: Move all git push —tags calls from publish hooks to after this line Examples of git push —tags calls: Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described. Create a new hook called something like push that’s a bail hook Set up the default behavior to just do the push Create a plugin (as a package or internally) that overrides the default behavior and makes the PR So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917 Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements. feel free to discuss this here! I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now. So the only way this wouldn’t work now is if: you don’t have permission to change this setting you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness) As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with. What’s weird is that this works fine for me on GitHub enterprise. On enterprise we use a dummy «bot» account with admin permissions to do this. Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all. That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin. I need to look at how our Buildkite jobs do this. Maybe they found a trick that works. I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support. All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI I’m in contact with someone who works at github and there might be a fix to this coming out at some point Источник
- When using protected branches (1 peer review) auto fails #1491
- Comments
push to protected master branch without admin permissions #205
Our master branch is protected with At least 1 approving review is required by reviewers with write access. . and we do not want our bot user to have admin permission.
On using the ‘@semantic-release/git’ plugin to update version # in package.json, we get the error:
remote: error: Required status check «Travis CI — Branch» is expected. At least 1 approving review is required by reviewers with write access. 436
Is there a best practice recommendation. This was also discussed here semantic-release/github#175 , but don’t see a workaround. Any pointers will help.
The text was updated successfully, but these errors were encountered:
Keep in mind that semantic-release interacts with GitHub as one of the users that your have granted permission to interact with you repos. semantic-release does not have any ability to work around the permissions that are enforced by GitHub.
The only exception that GitHub allows to the branch protection that you describe is to not enforce for users with admin level permissions.
If you desire more flexibility than GitHub currently enables, your best bet is contacting GitHub support and describing the enhancements that you would want.
© 2023 GitHub, Inc.
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
Requiring Pull Requests and Reviews in Your Git Workflow
August 31, 2021
Originally published August 31, 2021
Earlier in this series we covered how to use branch-per-issue or task branching to isolate work into short lived feature branches in Git that are then merged back into the main branch. I would recommend reading that tutorial for more information on the philosophy of this process, but the basic idea is this:
- An issue is created for each bit of work to be performed (these are generally small units of work)
- A new branch is created for the issue
- Work is performed/completed in that branch
- That branch is then merged back into the main branch once work is complete (or perhaps an integration branch if you prefer)
One thing that has been lacking from anything we have covered so far is governance features. We have been operating under the assumption that anybody who is working on our repository will have full access to everything and will act according to the rules/processes we have set forth. In practice, not everyone is always going to follow these rules (especially in larger teams).
With the set up we have now, there is nothing stopping ourselves or one of our developers from just pulling down the main branch and pushing straight back to it. As silly as it might sound, you might even want to set up governance features if it is just you and only you working on the repository. This won’t actually add any extra protection in this case because you will be able to bypass restrictions with administrator privileges, but it will help you develop good Git/Github workflow hygiene. Setting up and following governance features for yourself can help improve and enforce your own software development process, and it will also help a great deal if you ever do need to transition to a more team oriented environment.
We are now going to start exploring how to add governance features to more strictly control what can and can not be done in our repositories, starting with: pull requests.
Outline
What is a pull request?
If you’ve been using Git for any substantial amount of time then you have probably at least heard of pull requests. However, pull requests are not necessarily an integral part of everybody’s Git workflow. You could use Git/GitHub for years and never once have to create/merge a pull request.
A pull request isn’t really anything special. If I have been working on a branch in the repository, and I push that back up to the remote branch on GitHub (or wherever), a pull request is basically a formal method to say:
«Hey, I’ve got some changes over in this branch I want to merge into the main branch»
Creating a pull request will allow you to review the changes that will be included and make comments about the pull request for the person(s) who will be reviewing that pull request.
This then creates a more formal environment where the changes can be reviewed/discussed, and if necessary you (or others) can push further changes to that branch which will also be included in the pull request.
A pull request can then be merged into the main branch either directly through Github (just by clicking a button), or by checking out the pull request locally and merging it using the command line (this will be required if there are merge conflicts that need to be resolved).
NOTE: We are talking about a shared repository model in this tutorial where multiple contributors all have push access to the same shared repository. Pull requests are also heavily used in open source software where you might typically fork a repository you don’t have push access to, make some changes in your own fork, and then create a pull request to request changes from your fork be included in the original repository.
Why do we want to use pull requests?
As I mentioned at the beginning, there is nothing stopping any contributor in our repository from just pulling down the main branch and pushing right back to it. This violates the task branching model we are trying to follow, and we just have to hope that people follow the rules. Even if people do make a good faith effort to follow the rules in general, there will almost certainly be times where these rules are violated.
Although this will be our main motivation for enforcing that pull requests are used, using pull requests and reviews is also just a good idea from a collaboration and code review perspective.
Enforcing pull requests
Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now.
- Go to Settings > Branches
- Click Add rule on Branch protection rules
- Add main as the Branch name pattern
Now you can set whatever rules you want. We are going to add the following rules:
Once you have enabled the rules you need, you just need to click Create .
NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place.
An example of the workflow with pull requests
Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it:
git checkout main
git commit -m «pushing straight to main»
NOTE: If you have not set the Include Administrators option mentioned above the push to main will work.
Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating:
NOTE: Creating an issue isn’t actually enforced.
Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series):
BONUS TIP: Moving work committed onto the main branch to a feature branch
Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run:
To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g:
NOTE: Type :q to exit the editor
Then you can change back to your existing feature branch:
and pull those commits into the feature branch using cherry-pick for each commit that you want to keep:
To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run:
This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially.
Creating and merging a pull request
Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main .
First, we will need to push our changes up to the remote repository:
NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet)
If you go to Github now you will see a notice like this:
You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request.
You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes:
Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this:
The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review:
To review a pull request you will need someone (who is not the person who created the pull request) to:
- Open the pull request and click on the Files changed tab
- Click Review changes
- Leave a comment, check Approve , and then Submit review
- Back on the main pull request page, click Merge pull request
NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this.
And we are done!
Summary
We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place.
Источник
When using protected branches (1 peer review) auto fails #1491
Describe the bug
We have protected branches branches turned on to ensure
To Reproduce
Add «Require pull request reviews before merging»
Expected behavior
Auto should deploy, bypassing the branch protections.
Screenshots
Environment information:
Additional context
Settings:
The text was updated successfully, but these errors were encountered:
Another option is to use a PAT instead of the gh action’s token.
We are using a PAT. We were using the wrong token 😅
I 🙏 it works lol
This isn’t really an Auto issue but rather a thought-out limitation of Github Actions:
Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered.
I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR.
If protected branches is enabled then create a release PR rather than pushing to master.
Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need:
- to move that behavior into core
- make a new hook for pushing the release
- make a plugin that uses that hook to do what you described
I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin:
- Turn off branch protection during the afterVersion hook
- Turn on branch protection during the afterPublish hook
Just gotta find the right octokit API
It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection.
I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can.
Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements.
It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection
And if it the publish were to fail the branch protection rules would be lost 😢
The work to move the tag pushing into core looks like:
Move all git push —tags calls from publish hooks to after this line
Examples of git push —tags calls:
Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described.
Create a new hook called something like push that’s a bail hook
Set up the default behavior to just do the push
Create a plugin (as a package or internally) that overrides the default behavior and makes the PR
So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917
Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements.
feel free to discuss this here!
I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now.
So the only way this wouldn’t work now is if:
- you don’t have permission to change this setting
- you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness)
As for the PR method you are describing. It goes pretty far out of the way of auto ‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with.
What’s weird is that this works fine for me on GitHub enterprise.
On enterprise we use a dummy «bot» account with admin permissions to do this.
Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all.
That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin.
I need to look at how our Buildkite jobs do this. Maybe they found a trick that works.
I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support.
All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI
I’m in contact with someone who works at github and there might be a fix to this coming out at some point
Источник
push to protected master branch without admin permissions #205
Comments
pheenomenon commented May 21, 2020
Our master branch is protected with At least 1 approving review is required by reviewers with write access. . and we do not want our bot user to have admin permission.
On using the ‘@semantic-release/git’ plugin to update version # in package.json, we get the error:
remote: error: Required status check «Travis CI — Branch» is expected. At least 1 approving review is required by reviewers with write access. 436
Is there a best practice recommendation. This was also discussed here semantic-release/github#175 , but don’t see a workaround. Any pointers will help.
The text was updated successfully, but these errors were encountered:
travi commented May 24, 2020
Keep in mind that semantic-release interacts with GitHub as one of the users that your have granted permission to interact with you repos. semantic-release does not have any ability to work around the permissions that are enforced by GitHub.
The only exception that GitHub allows to the branch protection that you describe is to not enforce for users with admin level permissions.
If you desire more flexibility than GitHub currently enables, your best bet is contacting GitHub support and describing the enhancements that you would want.
Footer
© 2023 GitHub, Inc.
You can’t perform that action at this time.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session.
Источник
Requiring Pull Requests and Reviews in Your Git Workflow
August 31, 2021
Originally published August 31, 2021
Earlier in this series we covered how to use branch-per-issue or task branching to isolate work into short lived feature branches in Git that are then merged back into the main branch. I would recommend reading that tutorial for more information on the philosophy of this process, but the basic idea is this:
- An issue is created for each bit of work to be performed (these are generally small units of work)
- A new branch is created for the issue
- Work is performed/completed in that branch
- That branch is then merged back into the main branch once work is complete (or perhaps an integration branch if you prefer)
One thing that has been lacking from anything we have covered so far is governance features. We have been operating under the assumption that anybody who is working on our repository will have full access to everything and will act according to the rules/processes we have set forth. In practice, not everyone is always going to follow these rules (especially in larger teams).
With the set up we have now, there is nothing stopping ourselves or one of our developers from just pulling down the main branch and pushing straight back to it. As silly as it might sound, you might even want to set up governance features if it is just you and only you working on the repository. This won’t actually add any extra protection in this case because you will be able to bypass restrictions with administrator privileges, but it will help you develop good Git/Github workflow hygiene. Setting up and following governance features for yourself can help improve and enforce your own software development process, and it will also help a great deal if you ever do need to transition to a more team oriented environment.
We are now going to start exploring how to add governance features to more strictly control what can and can not be done in our repositories, starting with: pull requests.
Outline
What is a pull request?
If you’ve been using Git for any substantial amount of time then you have probably at least heard of pull requests. However, pull requests are not necessarily an integral part of everybody’s Git workflow. You could use Git/GitHub for years and never once have to create/merge a pull request.
A pull request isn’t really anything special. If I have been working on a branch in the repository, and I push that back up to the remote branch on GitHub (or wherever), a pull request is basically a formal method to say:
«Hey, I’ve got some changes over in this branch I want to merge into the main branch»
Creating a pull request will allow you to review the changes that will be included and make comments about the pull request for the person(s) who will be reviewing that pull request.
This then creates a more formal environment where the changes can be reviewed/discussed, and if necessary you (or others) can push further changes to that branch which will also be included in the pull request.
A pull request can then be merged into the main branch either directly through Github (just by clicking a button), or by checking out the pull request locally and merging it using the command line (this will be required if there are merge conflicts that need to be resolved).
NOTE: We are talking about a shared repository model in this tutorial where multiple contributors all have push access to the same shared repository. Pull requests are also heavily used in open source software where you might typically fork a repository you don’t have push access to, make some changes in your own fork, and then create a pull request to request changes from your fork be included in the original repository.
Why do we want to use pull requests?
As I mentioned at the beginning, there is nothing stopping any contributor in our repository from just pulling down the main branch and pushing right back to it. This violates the task branching model we are trying to follow, and we just have to hope that people follow the rules. Even if people do make a good faith effort to follow the rules in general, there will almost certainly be times where these rules are violated.
Although this will be our main motivation for enforcing that pull requests are used, using pull requests and reviews is also just a good idea from a collaboration and code review perspective.
Enforcing pull requests
Making a pull request required for merging into the main branch (or any branch) is quite easy with Github. Let’s do it now.
- Go to Settings > Branches
- Click Add rule on Branch protection rules
- Add main as the Branch name pattern
Now you can set whatever rules you want. We are going to add the following rules:
Once you have enabled the rules you need, you just need to click Create .
NOTE: If you are the only person working on this repository you should not check the Include Administrators option. You can not review your own pull requests, so you will need the ability to bypass the review requirement. Unfortunately, this will also allow you to push directly to the main branch so it defeats the purpose of doing this in the first place. As I mentioned, I still think it is a good idea to set up and follow this process as if it were required, but just know that your admin privileges remove the protections we are putting in place.
An example of the workflow with pull requests
Let’s see what our workflow looks like now. One of our main goals here was to stop people from pushing changes directly to the main branch. Let’s see what happens if we accidentally worked on the main branch and tries to push it:
git checkout main
git commit -m «pushing straight to main»
NOTE: If you have not set the Include Administrators option mentioned above the push to main will work.
Perfect, our push was rejected. Realising our error we might now want to move our commits onto a new branch. First, we will create an issue for the branch we are creating:
NOTE: Creating an issue isn’t actually enforced.
Then we will create a new branch that references that issue (using the branch name format we discussed in the first tutorial in this series):
BONUS TIP: Moving work committed onto the main branch to a feature branch
Since this branch was just created from our local main branch it will include the changes that we committed to the main branch. This allows us to carry our work over to this new branch. However, if this branch already existed then this would not work. If we already had a branch called jm-15 , and we wanted to move commits from main to our feature branch, then what we could do instead is on the main branch run:
To view the most recent commits. Make a note of the hash of each commit that you want to move over to the existing branch, e.g:
NOTE: Type :q to exit the editor
Then you can change back to your existing feature branch:
and pull those commits into the feature branch using cherry-pick for each commit that you want to keep:
To remove the commits from the main branch and get that back into a fresh state from the origin, you can just run:
This will remove any staged commits and destroy your local work. If you switch between main and jm-15 now, you should see that main does not contain any changes and jm-15 does, which is what we should have done initially.
Creating and merging a pull request
Ok, we have our new work in its own branch now, which we were forced to do by the branch protection rules that we created. Now let’s see how we actually go about getting our changes merged into main .
First, we will need to push our changes up to the remote repository:
NOTE: —set-upstream origin jm-15 is only required if this is the first time you are pushing the branch to the remote repository (i.e. the branch does not exist in the remote repository yet)
If you go to Github now you will see a notice like this:
You can just click Compare & pull request here but that notice won’t be displayed forever. You can also create a pull request by going to the Pull requests tab and then clicking New pull request.
You will want to set the base to main (or whatever your main branch is called) and the compare to jm-15 (or whatever the branch you are merging is called). You will then be able to review the changes:
Once you are satisfied, click Create pull request. You will then be given the chance to add a comment, and then you can click Create pull request again to actually create the pull request. Then you will see a rather intimidating screen like this:
The status checks aren’t actually of any concern to us here as we haven’t enabled status checks in our branch protection rules (we will likely cover that in another tutorial). What is blocking us at the moment though is the need for a review:
To review a pull request you will need someone (who is not the person who created the pull request) to:
- Open the pull request and click on the Files changed tab
- Click Review changes
- Leave a comment, check Approve , and then Submit review
- Back on the main pull request page, click Merge pull request
NOTE: You can not not approve your own pull requests, so if you are working on the repository by yourself you will need to bypass the review restrictions by just clicking Merge pull request without submitting a review. The Include administrators option under the branch protection rules must be disabled in order to allow this.
And we are done!
Summary
We all make mistakes, and wherever possible we shouldn’t rely on people manually following processes and following the rules. If mistakes from developers end up negatively affecting our codebase or product, then we should see it as a failure of our processes not of that developer. If we can use tools to help enforce the software development process we want to create, and protect/guide our developers in the process, then we should absolutely do that. It creates a much less stressful work environment for all stakeholders if you know there are safeguards in place.
Источник
Releasing on protected branch #1957
Comments
lukasjuhas commented Mar 5, 2019 •
Hello, thanks for a great tool.
We have a protected master branch becase we want to enforce pull requests reviewes before merging as well as prevent accidental merging to master directly.
Expected Behavior
I would like to be able publish packages no matter if primary branch is protected
Current Behavior
Currently, if user is not administrator, and error is thrown.
Possible Solution
No idea if there is any way around this, but I would appreciate suggestions on how to go around this and keep the primary branch protected.
Context
I would like to be able publish packages no matter if primary branch is protected or even if user is not an Administrator of the org or repo.
Your Environment
| Executable | Version |
|---|---|
| lerna —version | 3.10.7 |
| npm —version | 6.4.1 |
| yarn —version | 1.13.0 |
| node —version | v10.15.1 |
| OS | Version |
|---|---|
| macOS | 10.14.3 |
Thank you very much for any suggestions.
The text was updated successfully, but these errors were encountered:
kachkaev commented Mar 25, 2019
Hey @lukasjuhas have you found a decent workaround? I’m trying to wrap my head around this problem too.
lukasjuhas commented Mar 25, 2019
Hi @kachkaev. Unfortunatelly no workaround. I tried several suggestions I found across Github but none of them are sufficient.. hoping to get some input, suggestion or possible feature here.
kachkaev commented Mar 25, 2019
Thanks for your reply! What’s your current approach to releasing and having branch policies? Which trade-offs did you choose in the end?
lukasjuhas commented Mar 25, 2019
Bascally, because the team is quite small for now.. one of administrators of the org account publishes packages when PRs are merged to master (that’s the only branch we release from).
We have tried something along the lines of creating a «release» branch and release packages through there but then, after the branch is merge to master, lerna thinks it’s a change that has not been released yet and it wants to release it again so that doesn’t really work. The only way around really, is to just disable the protection.. if you can’t / don’t want to do that (like we do), you just get administrators of the org to release if it’s possible. Hopefully someone will come up with sufficient workaround. I would love to find time and dig into this and possibly find a solution that I could submit but I cannot see this any time soon..
The main problem of protected branch is that unless you are administrator, you cannot push to master directly. That becomes a problem, when you publish packages, lerna on your behalf is trying to push to master changes in version in package.json .
However, there might be actually possiblity of maintaininig version manually.. I believe there are some lerna options that allow you to do this.. e.g. you bumb version yourself.. so when releasing you are not asked to enter version.. but I can imagine this gets quite hard to maintain.. But I’m not quite sure about this 👀
evocateur commented Mar 26, 2019
I would question the necessity of locking master first, frankly. It’s not going to magically protect you from all mistakes.
In any event, as long as you’re willing to sacrifice the specificity that Lerna achieves through git tags, you can run lerna version —no-git-tag-version to prepare a PR (which will bump everything, as you’ve mangled the previous tags through merging), merge that PR into master, and then run lerna publish from-package —yes (maybe in CI? up to you), which does not make a commit or tag and publishes any local packages whose version does not exist in the configured registry.
But again, I would recommend reconsidering what you’re really gaining by locking master , given the tradeoff of losing all relevant git tags and partially-applied publishes.
lukasjuhas commented Mar 27, 2019
Hi @evocateur, thank you for your input and suggestions. And of course thanks for lerna!
I do get your point. The main reason for locking master is to add rules such as :
Require pull request reviews before merging When enabled, all commits must be made to a non-protected branch and submitted via a pull request with the required number of approving reviews and no changes requested before it can be merged into a branch that matches this rule.
Require status checks to pass before merging Choose which status checks must pass before branches can be merged into a branch that matches this rule. When enabled, commits must first be pushed to another branch, then merged or pushed directly to a branch that matches this rule after status checks have passed.
The problem is, in our repo, various member of team are contributing to it, including junior staff members that are more likely to make a mistake and e.g. merge PR without a review etc. Although this would be managable, and we could always revert.. at scale this might get difficult to keep track of.
I do understand that this is not really problem of lerna but more rules and politics in our team, I was just wondering if there is a way how to keep branch protected and publish packages which I get is not possible at the moment. Now the question is, if someone would take this challenge on, is it possible to achieve this at all?
So I do think being able to lock master does make sense and is common practice, and being to publish via lerna would be a really good feature and would help other people that have been having the same issue.
Источник
When using protected branches (1 peer review) auto fails
Describe the bug
We have protected branches branches turned on to ensure
To Reproduce
Add «Require pull request reviews before merging»
Expected behavior
Auto should deploy, bypassing the branch protections.
Screenshots
https://github.com/virtru/virtuoso-design-system/runs/1023167159?check_suite_focus=true#step:6:181
Error: Running command 'git' with args [push, --follow-tags, --set-upstream, ***github.com/virtru/virtuoso-design-system, master] failed
remote: error: GH006: Protected branch update failed for refs/heads/master.
remote: error: At least 1 approving review is required by reviewers with write access.
To https://github.com/virtru/virtuoso-design-system
* [new tag] v1.6.2 -> v1.6.2
! [remote rejected] master -> master (protected branch hook declined)
Environment information:
https://github.com/virtru/virtuoso-design-system/blob/master/package.json#L78
Additional context
Settings:
Another option is to use a PAT instead of the gh action’s token.
We are using a PAT. We were using the wrong token 😅
Yes I agree that it isn’t autos issue, but given auto have a deep relationship with Github it should be considered.
I like the automated merge PR. Seems like it’s something that an auto plugin could support? If protected branches is enabled then create a release PR rather than pushing to master. Additionally, it could utilize the API to use the associated admin permissions granted through the PAT to merge the release PR.
If protected branches is enabled then create a release PR rather than pushing to master.
Currently this would be a little more work than that. Each plugin is responsible for pushing the changlog/version commits. To make this pluggable we would need:
- to move that behavior into core
- make a new hook for pushing the release
- make a plugin that uses that hook to do what you described
I kind of like what https://github.com/benjefferies/branch-protection-bot does. this would be easier to do via a plugin:
- Turn off branch protection during the
afterVersionhook - Turn on branch protection during the
afterPublishhook
Just gotta find the right octokit API
It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection.
I scanned through the plugins and I see what you mean. Instead of moving the changelog / version to core what if there were different types of plugins. For instance if the conventional-commit plugin was broken into two plugin types: conventional-commit-changelog and conventional-commit-version. If I want to use conventional-commit changelogs, but use github labels for my versioning I can.
Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements.
It surely will work, but it seems precarious and potentially problematic for orgs that have strict controls around branch protection
And if it the publish were to fail the branch protection rules would be lost 😢
The work to move the tag pushing into core looks like:
-
Move all
git push --tagscalls frompublishhooks to after this lineExamples of
git push --tagscalls:https://github.com/intuit/auto/blob/master/plugins/npm/src/index.ts#L1172-L1179
https://github.com/intuit/auto/blob/master/plugins/cocoapods/src/index.ts#L163-L169
https://github.com/intuit/auto/blob/master/plugins/gradle/src/index.ts#L221-L227Looking at this more it might be tricky finding all the places where we would push a commit to the baseBranch to switch to the PR flow you described.
-
Create a new hook called something like
pushthat’s a bail hook -
Set up the default behavior to just do the
push -
Create a plugin (as a package or internally) that overrides the default behavior and makes the PR
So I’m gonna close the PR I made to do this in a plugin as it seems to brittle. I’d be willing to accept a PR for this but it also seems like a pretty big lift. Although I had planned on moving the tag pushing into core at some point to facilitate #917
Possibly, a much larger conversation, but I’d be interested in assisting in developing a more robust solution which would satisfy various org requirements.
feel free to discuss this here!
I’ve made changes to my PR that will re-enable the Peer Reviews even when something in auto throws an error. So this should be a little less brittle now.
So the only way this wouldn’t work now is if:
- you don’t have permission to change this setting
- you hit the «merge quickly» window perfectly (low chance and i’m pretty sure the first one would abort before any weirdness)
As for the PR method you are describing. It goes pretty far out of the way of auto‘s normal workflow. The biggest pain point I can imagine is that since you would be pushing tags to branches there would be a possibility of multiple PR merges creating branches with conflicting tags. We could write code that makes sure we only have 1 of those PRs up at a time but I feel like there would be some edge case weirdness to deal with.
What’s weird is that this works fine for me on GitHub enterprise…
On enterprise we use a dummy «bot» account with admin permissions to do this.
Locally on my test project i’ve made a key with all permissons and it still doesn’t work at all.
That is strange. We don’t use Enterprise at my org, but I have experienced the same issue on our (teams?) account despite being an Admin or using our dummy account which is also an admin.
I need to look at how our Buildkite jobs do this. Maybe they found a trick that works.
I’m going to formalize my thoughts and post about it tomorrow. Thanks for your attentiveness and support.
All sources point to a token from an admin with the right permissions should fix this. I’m trying this on this repo to no avail. what’s weird is everything works fine locally using the same exact token. I can push directly to master but the same token doesn’t work in CI
I’m in contact with someone who works at github and there might be a fix to this coming out at some point
I’ve just stumbled upon this problem and am wondering if there has been any progress. If not, I’d be happy to extend the troubleshooting section.
@hipstersmoothie you were half way there:
- have to be on enterprise org, because there you can now…
- describe which groups/users can skip branch protection rules
- use a seat license to create a service account
- on that service account create a PAT that has all required scopes to make changes
repo:write,packages,workflows(if your bot is rewriting workflows), etc etc.
for us peasants on anything less than enterprise we have to forage for clams and fabricobble our paper towels into the eternal diaper.