Connection Reset by peer means the remote side is terminating the session. This error is generated when the OS receives notification of TCP Reset (RST) from the remote peer.
Understanding Connection Reset by peer
Connection reset by peer means the TCP stream was abnormally closed from the other end. A TCP RST was received and the connection is now closed. This occurs when a packet is sent from our end of the connection but the other end does not recognize the connection; it will send back a packet with the RST bit set in order to forcibly close the connection.
“Connection reset by peer” is the TCP/IP equivalent of slamming the phone back on the hook. It’s more polite than merely not replying, leaving one hanging. But it’s not the FIN-ACK expected of the truly polite TCP/IP.
Understanding RST TCP Flag
RST is used to abort connections. It is very useful to troubleshoot a network connection problem.
RST (Reset the connection). Indicates that the connection is being aborted. For active connections, a node sends a TCP segment with the RST flag in response to a TCP segment received on the connection that is incorrect, causing the connection to fail.
The sending of an RST segment for an active connection forcibly terminates the connection, causing data stored in send and receive buffers or in transit to be lost. For TCP connections being established, a node sends an RST segment in response to a connection establishment request to deny the connection attempt. The sender will get Connection Reset by peer error.
Understanding TCP Flags SYN ACK RST FIN URG PSH
Check network connectivity
The “ping” command is a tool used to test the availability of a network resource. The “ping” command sends a series of packets to a network resource and then measures the amount of time it takes for the packets to return.
If you want to ping a remote server, you can use the following command: ping <remote server>
In this example, “<remote server>” is the IP address or hostname of the remote server that you want to ping.
Ping the remote host we were connected to. If it doesn’t respond, it might be offline or there might be a network problem along the way. If it does respond, this problem might have been a transient one (so we can reconnect now)
If you are experiencing packet loss when pinging a remote server, there are a few things that you can do to troubleshoot the issue.
The first thing that you can do is check the network interface on the remote server. To do this, use the “ifconfig” command. The output of the “ifconfig” command will show you the status of all network interfaces on the system. If there is a problem with one of the interfaces, it will be shown in the output.
You can also use the “ip route” command to check routing information. The output of the “ip route” command will show you a list of all routes on the system. If there is a problem with one of the routes, it will be shown in the output.
If you are still experiencing packet loss, you can try to use a different network interface. To do this, use the “ping” command with the “-i” option. For example, the following command will use the eth0 interface:
ping -i eth0 google.com
Check remote service port is open
A port is a logical entity which acts as a endpoint of communication associated with an application or process on an Linux operating system. We can use some Linux commands to check remote port status.
Commands like nc, curl can be used to check if remote ports are open or not. For example, the following command will check if port 80 is open on google.com:
nc -zv google.com 80
The output of the above command should look something like this: Connection to google.com port 80 [tcp/80] succeeded!
This means that the port is open and we can establish a connection to it.
6 ways to Check a remote port is open in Linux
Check application log on remote server
For example, if the error is related with SSH. we can debug this on the remote server from sshd logs. The log entries will be in one of the files in the /var/log directory. SSHD will be logging something every time it drops our session.
Oct 22 12:09:10 server internal-sftp[4929]: session closed for local user fred from [192.0.2.33]
Check related Linux kernel parameters
Kernel parameter is also related to Connection Reset by peer error. The keepalive concept is very simple: when we set up a TCP connection, we associate a set of timers. Some of these timers deal with the keepalive procedure. When the keepalive timer reaches zero, we send our peer a keepalive probe packet with no data in it and the ACK flag turned on.
we can do this because of the TCP/IP specifications, as a sort of duplicate ACK, and the remote endpoint will have no arguments, as TCP is a stream-oriented protocol. On the other hand, we will receive a reply from the remote host (which doesn’t need to support keepalive at all, just TCP/IP), with no data and the ACK set.
If we receive a reply to we keepalive probe, we can assert that the connection is still up and running without worrying about the user-level implementation. In fact, TCP permits us to handle a stream, not packets, and so a zero-length data packet is not dangerous for the user program.
we usually use tcp keepalive for two tasks:
- Checking for dead peers
- Preventing disconnection due to network inactivity
Check Application heartbeat configuration
Connection Reset by peer error is also related to the application. Certain networking tools (HAproxy, AWS ELB) and equipment (hardware load balancers) may terminate “idle” TCP connections when there is no activity on them for a certain period of time. Most of the time it is not desirable.
We will use rabbitmq as an example. When heartbeats are enabled on a connection, it results in periodic light network traffic. Therefore heartbeats have a side effect of guarding client connections that can go idle for periods of time against premature closure by proxies and load balancers.
With a heartbeat timeout of 30 seconds the connection will produce periodic network traffic roughly every 15 seconds. Activity in the 5 to 15 second range is enough to satisfy the defaults of most popular proxies and load balancers. Also see the section on low timeouts and false positives above.
Check OS metric on peer side
Connection Reset by peer can be triggered by a busy system. we can setup a monitoring for our Linux system to the metrics like CPU, memory, network etc. If the system is too busy, the network will be impacted by this.
For example, we can use the “top” command to check the CPU usage. The output of the “top” command will show us the list of processes sorted by CPU usage. If there is a process which is using a lot of CPU, we can investigate this further to see if it is causing the network issues.
We can also use the “netstat” command to check network statistics. The output of the “netstat” command will show us a list of active network connections. If there are too many connections established, this could be causing the network issues.
We can use these commands to troubleshoot network issues on a Linux system. By using these commands, we can narrow down the root cause of the issue and fix it.
Monitoring Linux System with Telegraf Influxdb Grafana
Troubleshoot Network Slow Problems In Linux
Introduction
A remote machine has prevented an SSH connection you were attempting to establish or maintain. The “ssh_exchange_identification: read: Connection reset by peer” message is not specific enough to immediately explain what triggered the error.
To be able to resolve the issue successfully, we first need to identify its cause. This article provides an in-depth analysis of the likely causes and provides the most effective solutions.
By reading this tutorial, you will learn how to fix the “ssh_exchange_identification: read: Connection reset by peer” Error.
Prerequisites
- Necessary permissions to access remote server
- A user account with root or sudo privileges
The “ssh_exchange_identification: read: Connection reset by peer” error indicates that the remote machine abruptly closed the Transition Control Protocol (TCP) stream. In most instances, a quick reboot of a remote server might solve a temporary outage or connectivity issue.
Note: Network-based firewalls or load-balancers can sometimes distort IPs or security permissions. This type of problem can be resolved by contacting your service provider.
Learning how to troubleshoot this issue, and determining the underlying cause, helps you prevent future occurrences on your system. The most common causes of the “ssh_exchange_identification: read: Connection reset by peer” error are:
- The connection is being blocked due to the Host-Based Access Control Lists.
- Intrusion prevention software is blocking your IP by updating firewall rules (Fail2ban, DenyHosts, etc.).
- Changes to the SSH daemon configuration file.
Check the hosts.deny and hosts.allow File
The hosts.deny and hosts.allow files are TCP wrappers. As a security feature, these files are used to limit which IP address or hostname can establish a connection to the remote machine.
Note: Inspect the hosts.deny and hosts.allow files on the remote server, not on the local client.
How to Edit hosts.deny File
Access your remote server and open the hosts.deny file using your preferred text editor. If you are using nano on a Debian based system, enter the following command:
sudo nano /etc/hosts.denyEmpty lines and lines starting with the ‘#’ symbol are comments. Check if you can locate your local IP or host-name in the file. If it is present, it should be removed or commented out, or else it prevents you from establishing a remote connection.
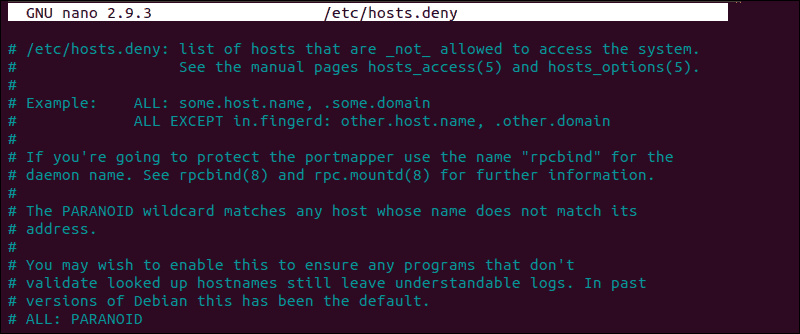
After making the necessary changes, save the file and exit. Attempt to reconnect via SSH.
How to Edit hosts.allow File
As an additional precaution, edit the hosts.allow file. Access rules within the hosts.allow are applied first. They take precedence over rules specified in hosts.deny file. Enter the following command to access the hosts.allow file:
sudo nano /etc/hosts.allowAdding host-names and IPs to the file defines exceptions to the settings in the hosts.deny file.
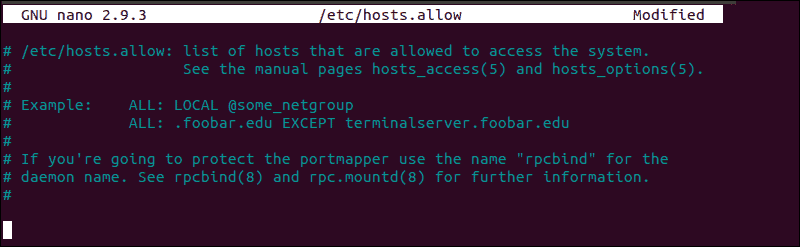
For example, a strict security policy within the etc/hosts.deny file, would deny access to all hosts:
sshd : ALL
ALL : ALLSubsequently, you can add a single IP address, an IP range, or a hostname to the etc/hosts.allow file. By adding the following line, only the following IP would be allowed to establish an SSH connection with your remote server:
sshd : 10.10.0.5, LOCALKeep in mind that such a limiting security setting can affect administering capabilities on your remote servers.
Check if fail2ban Banned Your IP Address
If you’ve tried to connect on multiple occasions, your IP might be blocked by an intrusion prevention software. Fail2ban is a service designed to protect you from brute force attacks, and it can misinterpret your authentication attempts as an attack.
Fail2ban monitors and dynamically alters firewall rules to ban IP addresses that exhibit suspicious behavior. It monitors logs, like the hosts.deny and hosts.allow files we edited previously.
In our example, we used the following command to check if the iptables tool is rejecting your attempted connections:
sudo iptables -L --line-numberThe output in your terminal window is going to list all authentication attempts. If you find that a firewall is indeed preventing your SSH connection, you can white-list your IP with fail2ban. Otherwise, the service is going to block all future attempts continuously. To access the fail2ban configuration file, enter the following command:
sudo nano /etc/fail2ban/jail.confEdit the file by uncommenting the line that contains "ignoreip =" add the IP or IP range you want to white-list.
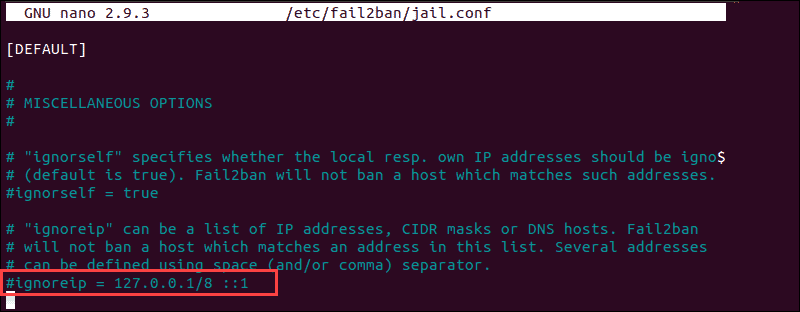
Fail2ban is now going to make an exception and not report suspicious behavior for the IP in question.
Check the sshd_config File
If you are continuing to experience the ‘ssh_exchange_identification: read: Connection reset by peer’ error, examine the authentication log entry. By default, the SSH daemon sends logging information to the system logs. Access the /var/log/auth.log file after your failed attempt to login. To review the latest log entries type:
tail -f /var/log/auth.logThe output presents the results of your authentication attempts, information about your user account, authentication key, or password.
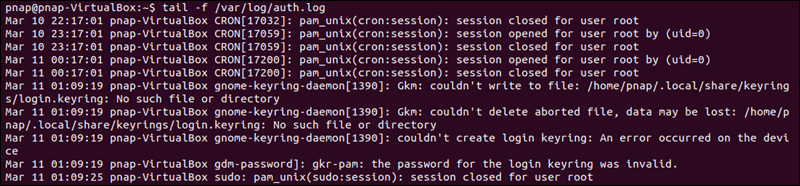
The log provides you with information that can help you find possible issues in the sshd configuration file, sshd_config. Any changes made to the file can affect the terms under which an ssh connection is established and lead the remote server to treat the client as incompatible. To access the sshd_config file type:
sudo nano /etc/ssh/sshd_configThe sshd configuration file enables you to change basic settings, such as the default TCP port or SSH key pairs for authentication, as well as more advanced functions such as port-forwarding.
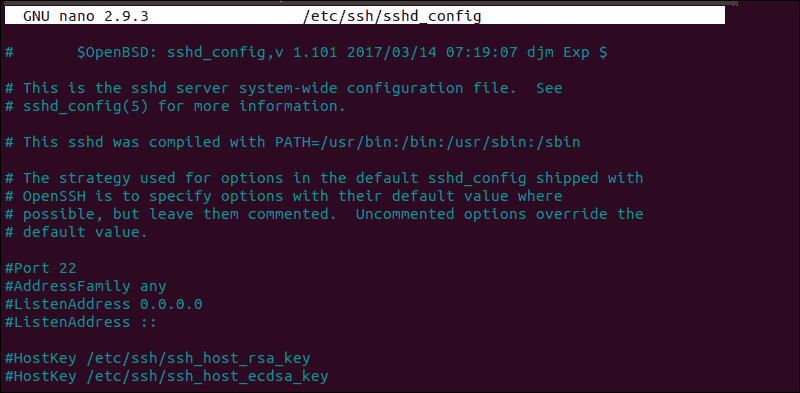
For example, the MaxStartups variable defines how many connections a system accepts in a predefined period. If you have a system that makes a large number of connections in a short timeframe, it might be necessary to increase the default values for this variable. Otherwise, the remote system might refuse additional attempted ssh connections.

Anytime you edit the sshd_config file, restart the sshd service for the changes to take effect:
service sshd restartOnly edit the variables that you are familiar with. A server can become unreachable as a result of a faulty configuration file.
Conclusion
You have thoroughly checked the most common reasons behind the “ssh_exchange_identification: read: Connection reset by peer” error. By looking at each possibility, in turn, you have successfully solved the issue and now know how to deal with similar problems going forward.
The number of potential causes is vast and difficult to troubleshoot in every respect. Ultimately, if the error persists, it might be necessary to contact your host.
What is the meaning of the «connection reset by peer» error on a TCP connection? Is it a fatal error or just a notification or related to the network failure?
amarnath
7853 gold badges20 silver badges23 bronze badges
asked Sep 16, 2009 at 17:38
Franck FreiburgerFranck Freiburger
25.3k20 gold badges69 silver badges95 bronze badges
It’s fatal. The remote server has sent you a RST packet, which indicates an immediate dropping of the connection, rather than the usual handshake. This bypasses the normal half-closed state transition. I like this description:
«Connection reset by peer» is the TCP/IP equivalent of slamming the phone back on the hook. It’s more polite than merely not replying, leaving one hanging. But it’s not the FIN-ACK expected of the truly polite TCP/IP converseur.
answered Sep 16, 2009 at 17:48
ire_and_cursesire_and_curses
67.6k23 gold badges115 silver badges141 bronze badges
10
This means that a TCP RST was received and the connection is now closed. This occurs when a packet is sent from your end of the connection but the other end does not recognize the connection; it will send back a packet with the RST bit set in order to forcibly close the connection.
This can happen if the other side crashes and then comes back up or if it calls close() on the socket while there is data from you in transit, and is an indication to you that some of the data that you previously sent may not have been received.
It is up to you whether that is an error; if the information you were sending was only for the benefit of the remote client then it may not matter that any final data may have been lost. However you should close the socket and free up any other resources associated with the connection.
answered Sep 16, 2009 at 18:07
5
one of the reasons for seeing this error and having trouble connecting to the server is that you enabled the firewall in the UNIX machine and forgot to add a rule to accept ssh connection. search in your WPS provider and you will find a way to connect to you machine and add this rules:
ufw allow ssh && ufw allow 22
answered Jan 19 at 14:18
FarshadFarshad
1751 silver badge9 bronze badges
I am on OS X trying to ssh into a ubuntu 12.04 server. I was able to SSH in — until abruptly stuff stopped working. I’ve read online to use the -v to debug this. Output is shown below. If I ssh into a different box and then ssh from that box to the server I am able to login. I have no idea how to debug this problem but would like to learn.
$ ssh -v me@server
OpenSSH_6.2p2, OSSLShim 0.9.8r 8 Dec 2011
debug1: Reading configuration data /etc/ssh_config
debug1: /etc/ssh_config line 20: Applying options for *
debug1: /etc/ssh_config line 53: Applying options for *
debug1: Connecting to server [IP] port 22.
debug1: Connection established.
debug1: identity file /Users/me/.ssh/id_rsa type 1
debug1: identity file /Users/me/.ssh/id_rsa-cert type -1
debug1: identity file /Users/me/.ssh/id_dsa type -1
debug1: identity file /Users/me/.ssh/id_dsa-cert type -1
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_6.2
ssh_exchange_identification: read: Connection reset by peer
So far (on advice of message boards) I have looked for a hosts deny file — but there is no such file on my machine.
$ cat /etc/hosts.deny
cat: /etc/hosts.deny: No such file or directory
I have admin access on client machine but not on server.
phemmer
69.3k19 gold badges181 silver badges219 bronze badges
asked Aug 24, 2014 at 3:49
7
The abrupt change could be the result of a change in the configuration file on the servers sshd configuration, but you indicate cannot check or alter that without admin right. You can still try the following if the server’s admins cannot be reached (in time).
Your log only indicates the local version string, you should check the versions of sshd running on the server and the intermediate machine.
If these versions differ (especially between the local machine and the server and less between the intermediate machine and the server) there might be some negotiation incompatibility, this has happened before in ssh. The solution used to be to shorten the Ciphers, HostKeyAlgorithms and/or MACs entries, either on the commandline (ssh -c aes256-ctr, etc.) or on in your /etc/ssh/ssh_config.
You should look in the debug information (from connecting via the intermediate to the server) for appropriate values as argument for the -c/Ciphers, -o HostKeyAlgorithms/HostKeyAlgorithms and -m/MACs commandline resp. ssh_config changes.
I haven’t had this problem myself for a while, but IIRC when I did it was enough to manually force the Ciphers and HostKeyAlgorithms setting, after which I could update the server’s sshd version and the problem went away.
answered Aug 24, 2014 at 5:33
AnthonAnthon
77k42 gold badges159 silver badges217 bronze badges
4
You may have been banned by fail2ban or denyhosts. In such a case (and also to check it), if you don’t want to bother with your server provider assistance, you need to log into your server from another IP address : e.g. another server, or a friend’s home connection, or a wifi hot spot, or using SSH with TOR.
Once logged in, check that your IP address indeed appears in /etc/hosts.deny (on the server side). If so, then fail2ban or denyhosts must be the culprit indeed.
See answers to this question for the procedure to prevent denyhosts to block your address continuously. For fail2ban find your ip with iptables -L --line-number and unban you ip with iptables -D <chain> <chain number>, you check details on howtoforge.
You may want to add your IP address to fail2ban and denyhosts whitelists (respectively /etc/fail2ban/jail.conf, line ignoreip, and /var/lib/denyhosts/allowed-hosts, create it if needed (but beware that the path may be different on your distribution)) to prevent the issue to happen again.
answered Feb 3, 2015 at 9:44
0
On the host server, remove the ssh pub.key located here: ~/.ssh/authorized_keysfor your mac. Then tail -f /var/log/auth.log while you open another terminal and try to ssh again ssh -v me@server. If you are prompted for a password then there was a problem with your ssh key. If you are still seeing the ‘ssh_exchange_identification: read: Connection reset by peer’ response, then you should be able to identify what the problem is from the log entry in the ‘/var/log/auth.log’ file after your failed attempt to login.
If you still failed to connect, post the logged entry from the auth file here and I’ll revise my answer.
answered Aug 28, 2014 at 15:22
devnulldevnull
5,23520 silver badges35 bronze badges
1
This can happen if you have multiple machines on the network with the same MAC address (for example, if you make a copy of a virtual machine and forget to change the MAC).
answered Jun 8, 2015 at 16:48
elCapitanoelCapitano
1811 silver badge2 bronze badges
0
Your log means that server-side drops the connection. To find out the reason, you should consult server-side logs, they should show reason for disconnection. You should be almost always be able to find logs in /var/log/messages
I could guess that, as connection dropped just after client sent version number, server somehow threats client as incompatible.
answered Jan 6, 2015 at 12:59
gena2xgena2x
2,34712 silver badges20 bronze badges
I was faced with the same problem. I would open ssh session successfully but it would get reset after some time. When i tried to connect gain immediately i would get the error «Connection refused».
when i debugged the session i got this message at the time when the connection was getting reset
debug1: client_input_channel_req: channel 0 rtype keepalive@openssh.com reply 1
debug1: client_input_channel_req: channel 0 rtype keepalive@openssh.com reply 1
debug1: client_input_channel_req: channel 0 rtype keepalive@openssh.com reply 1
debug1: channel 0: free: client-session, nchannels 1
debug3: channel 0: status: The following connections are open:
#0 client-session (t4 r0 i0/0 o0/0 fd 4/5 cfd -1)
debug3: channel 0: close_fds r 4 w 5 e 6 c -1
Read from remote host 10.x.y.z: Connection reset by peer
Connection to 10.x.y.z closed.
debug1: Transferred: stdin 0, stdout 0, stderr 100 bytes in 1029.9 seconds
debug1: Bytes per second: stdin 0.0, stdout 0.0, stderr 0.1
debug1: Exit status -1
At this point i realized that there was an IP address conflict on the network. I changed to another address and problem was resolved
HalosGhost
4,64410 gold badges32 silver badges40 bronze badges
answered Jan 6, 2015 at 12:26
DavidDavid
811 silver badge3 bronze badges
0
I was getting this due to my ISP’s nameservers in /etc/resolv.conf. These nameservers are often overloaded and if reverse DNS lookup fails sshd will drop the connection. I solved the problem by using more reliable nameservers, e.g. 8.8.8.8.
answered Dec 17, 2014 at 18:38
njahnkenjahnke
1751 silver badge7 bronze badges
I had the same problem but it turned out the cause was different: I was using wrong port.
On newer versions of ssh the error given is Connection refused or Bad port.
On older versions the error given is ssh_exchange_identification: read: Connection reset by peer
So when you get such error check if port is correct.
answered Apr 28, 2017 at 17:31
I know this question is old, but I wanted to share some findings I had. Check if /var/empty/sshd on the server has appropriate ownership and permissions.
We had a chef script that was modified to update some directory permissions, but inadvertently updated the directory below the intended target, changing ownership of /var to an application user/group and changing the permissions to 775.
answered May 20, 2015 at 16:44
0
I ran into this exact error when trying to connect to all my remote hosts via the Wi-Fi bridge option on my Android device (Huawei P30 Pro). When I used the USB tethering option to share the same Internet connection, no problem.
Absolutely nothing else changed in the SSH configuration or options on the client or servers.
TL;DR: sometimes, nothing you can do.
answered Nov 25, 2019 at 17:07
Dan DascalescuDan Dascalescu
7,2314 gold badges18 silver badges24 bronze badges
In my case it was a different IP address prefix length.
The server had set 192.168.0.2/24 while client was 192.168.1.1/23. There was no connectivity issues whatsoever (for example cups printing works) until I tried to ssh.
Check ip addr show on both sides.
answered Dec 15, 2021 at 19:57
mkkotmkkot
1165 bronze badges
Rdesktop connection reset by peer is a common error when connecting to a remote windows server.
Usually, this error happens due to wrong settings in the rdesktop client related to authentication.
At Bobcares, we often get requests to fix rdesktop errors, as a part of our Server Management Services.
Today, let’s see how our Support Engineers fix “rdesktop connection reset by peer”
What is Rdesktop?
Basically, Rdesktop is open-source software that enables us to connect to remote windows server from Linux.
To connect to Windows host from Linux we use the command:
rdesktop -u -p
We can also include a few parameters in the command to change the appearance of the windows host.
Causes for connection reset by peer
Let’s now check on what causes the connection reset error in the rdesktop.
By default, Windows server from and above Windows 2012 allows a connection that supports Network Level Authentication.
Network Level Authentication is a technology that requires a user to authenticate themselves before establishing a connection. As a result, it prevents the initiation of a full rdesktop connection before user authentication. Thus, it helps greatly to mitigate Remote Desktop vulnerabilities.
However, it brings in a lot of restrictions on the rdesktop clients. For instance, to use Network Level Authentication in Remote Desktop Services, the client must be running Windows XP SP3 or later.
So to connect from the Linux machine using rdesktop, the Network level Authentication has to be disabled. Or else, the error message will appear as :
ERROR: send: Connection reset by peer
ERROR: Connection closed
Let’s now move on and see the workarounds to resolve the error.
How we fix it
Recently, we had a customer that was facing problems connecting to his Windows host from his Linux machine.
Let’s discuss how our Support Engineers disabled NLA and made the connection working.
Disable Network Level Authentication
First we login to the windows server from another windows server. Since the RDP supports Network Level Authentication, we disable the setting from :
Search systempropertiesremote.exe from start. A window appears and then click on the Remote tab.
Or Click Start >> Administrative Tools, and then click Server Manager.
In the left pane, expand Roles.
Expand Remote Desktop Services. Then click on Remote Desktop Session Host Configuration.
Deselect “Allow connections only from computers running Remote Desktop with Network Level Authentication”
For servers below Windows Server 2008, we select the option “Allow connections from computers running any version of Remote Desktop (less secure)”
Finally, we apply the changes.
Note: When the option is disabled the Network level authentication is skipped. Allowing connections using NLA is a more secure authentication method. It might even lead to a server attack as well.
Without disabling NLA
However, some customers may not have the option to disable NLA due to security reasons.
Without disabling NLA, the only option is to go for a rdesktop alternative that supports NLA. FreeRDP is a free remote desktop protocol client. Therefore, our Dedicated Engineers recommend the use of FreeRDP as one of the best alternatives for rdesktop that support NLA.
[Still getting a connection reset error in rdesktop? We can fix it for you.]
Conclusion
In short, we have discussed the common causes for the error “rdesktop connection reset by peer”. Also, we saw how our Support Engineers resolve the error by disabling NLA in the windows server.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;
The connection reset by peer is a TCP/IP error that occurs when the other end (peer) has unexpectedly closed the connection. It happens when you send a packet from your end, but the other end crashes and forcibly closes the connection with the RST packet instead of the TCP FIN, which is used to close a connection under normal circumstances. In Go, you can detect the connection reset by peer by checking if the error returned by the peer is equal to syscall.ECONNRESET.
Reproduce the connection reset by peer error
We can reproduce the error by creating a server and client that do the following:
- the server reads a single byte and then closes the connection
- the client sends more than one byte
If the server closes the connection with the remaining bytes in the socket’s receive buffer, then an RST packet is sent to the client. When the client tries to read from such a closed connection, it will get the connection reset by peer error.
See the following example, which simulates this behavior.
package main
import (
"errors"
"log"
"net"
"os"
"syscall"
"time"
)
func server() {
listener, err := net.Listen("tcp", ":8080")
if err != nil {
log.Fatal(err)
}
defer listener.Close()
conn, err := listener.Accept()
if err != nil {
log.Fatal("server", err)
os.Exit(1)
}
data := make([]byte, 1)
if _, err := conn.Read(data); err != nil {
log.Fatal("server", err)
}
conn.Close()
}
func client() {
conn, err := net.Dial("tcp", "localhost:8080")
if err != nil {
log.Fatal("client", err)
}
if _, err := conn.Write([]byte("ab")); err != nil {
log.Printf("client: %v", err)
}
time.Sleep(1 * time.Second) // wait for close on the server side
data := make([]byte, 1)
if _, err := conn.Read(data); err != nil {
log.Printf("client: %v", err)
if errors.Is(err, syscall.ECONNRESET) {
log.Print("This is connection reset by peer error")
}
}
}
func main() {
go server()
time.Sleep(3 * time.Second) // wait for server to run
client()
}
Output:
2021/10/20 19:01:58 client: read tcp [::1]:59897->[::1]:8080: read: connection reset by peer
2021/10/20 19:01:58 This is connection reset by peer error
Handle the connection reset by peer error
Typically, you can see the connection reset by peer error in response to a request being sent from the client to the server. It means that something bad has happened to the server: it has rebooted, the program has crashed, or other problems have occurred that cause the connection to be forcibly closed. Since TCP connections can be broken, there is no need to handle the connection reset by peer in any special way on the client side. You can log the error, ignore it or retry the connection when it occurs. In the example above, we detect the error using the errors.Is() function by checking if the returned error is an instance of syscall.ECONNRESET.
Difference between connection reset by peer and broken pipe
Both connection reset by peer and broken pipe errors occur when a peer (the other end) unexpectedly closes the underlying connection. However, there is a subtle difference between them. Usually, you get the connection reset by peer when you read from the connection after the server sends the RST packet, and when you write to the connection after the RST instead, you get the broken pipe error.
Check how to handle the
broken pipeerror in Go post, where will find another example of generating anRSTpacket and thebroken pipeerror.
Replace the client() function in the example above with the following code to reproduce the broken pipe error.
func client() {
conn, err := net.Dial("tcp", "localhost:8080")
if err != nil {
log.Fatal("client", err)
}
if _, err := conn.Write([]byte("ab")); err != nil {
log.Printf("client: %v", err)
}
time.Sleep(1 * time.Second) // wait for close on the server side
if _, err := conn.Write([]byte("b")); err != nil {
log.Printf("client: %v", err)
}
}
With the new client, you will see the output:
2021/10/20 19:55:40 client: write tcp [::1]:60399->[::1]:8080: write: broken pipe
Note that these simple examples do not cover all cases where connection reset by peer and broken pipe may occur. There are much more situations where you can see these errors, and what error you see in what situation requires a deep understanding of the TCP design.
- Remove From My Forums
-
Question
-
Hi to all,
we have a RDS 2012 R2 farm with 2 gateway, 2 connection broker and 8 session host.
We have a problem when a MAC user try to connect to farm from internet. The Microsoft Remote Desktop client version 8.0.36 (Build 27228) fails the connection with error: Connection reset by peer. The application log contains this entry:[2016-Dec-01 08:55:07] RDP (0): Final rdp configuration used: gatewayhostname:s:xxx.xxx.it
screen mode id:i:2
use multimon:i:0
session bpp:i:32
full address:s:xxx.xxx.IT
audiomode:i:0
username:s:
disable wallpaper:i:0
disable full window drag:i:0
disable menu anims:i:0
disable themes:i:0
alternate shell:s:
shell working directory:s:
authentication level:i:2
connect to console:i:0
gatewayusagemethod:i:1
disable cursor setting:i:0
allow font smoothing:i:1
allow desktop com:1
redirectprinters:i:0
prompt for credentials on client:i:1
autoreconnection enabled:i:1
bookmarktype:i:3
use redirection server name:i:1
loadbalanceinfo:s:tsv://MS Terminal Services Plugin.1.xxxxxxxxx
authoring tool:s:rdmac
[2016-Dec-01 08:55:07] RDP (0): — BEGIN INTERFACE LIST —
[2016-Dec-01 08:55:07] RDP (0): lo0 af=18 addr= netmask=
[2016-Dec-01 08:55:07] RDP (0): lo0 af=30 (AF_INET6) addr=::1 netmask=ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
[2016-Dec-01 08:55:07] RDP (0): lo0 af=2 (AF_INET) addr=127.0.0.1 netmask=255.0.0.0
[2016-Dec-01 08:55:07] RDP (0): lo0 af=30 (AF_INET6) addr=fe80::1%lo0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:07] RDP (0): gif0 af=18 addr= netmask=
[2016-Dec-01 08:55:07] RDP (0): stf0 af=18 addr= netmask=
[2016-Dec-01 08:55:07] RDP (0): en0 af=18 addr= netmask=
[2016-Dec-01 08:55:07] RDP (0): en0 af=30 (AF_INET6) addr=fe80::20c:29ff:feed:53ba%en0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:07] RDP (0): en0 af=2 (AF_INET) addr=192.168.128.138 netmask=255.255.255.0
[2016-Dec-01 08:55:07] RDP (0): — END INTERFACE LIST —
[2016-Dec-01 08:55:07] RDP (0): Protocol state changed to: ProtocolCredentialError(10)
[2016-Dec-01 08:55:07] RDP (0): Showing credentials dialog
[2016-Dec-01 08:55:23] RDP (0): — BEGIN INTERFACE LIST —
[2016-Dec-01 08:55:23] RDP (0): lo0 af=18 addr= netmask=
[2016-Dec-01 08:55:23] RDP (0): lo0 af=30 (AF_INET6) addr=::1 netmask=ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
[2016-Dec-01 08:55:23] RDP (0): lo0 af=2 (AF_INET) addr=127.0.0.1 netmask=255.0.0.0
[2016-Dec-01 08:55:23] RDP (0): lo0 af=30 (AF_INET6) addr=fe80::1%lo0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:23] RDP (0): gif0 af=18 addr= netmask=
[2016-Dec-01 08:55:23] RDP (0): stf0 af=18 addr= netmask=
[2016-Dec-01 08:55:23] RDP (0): en0 af=18 addr= netmask=
[2016-Dec-01 08:55:23] RDP (0): en0 af=30 (AF_INET6) addr=fe80::20c:29ff:feed:53ba%en0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:23] RDP (0): en0 af=2 (AF_INET) addr=192.168.128.138 netmask=255.255.255.0
[2016-Dec-01 08:55:23] RDP (0): — END INTERFACE LIST —
[2016-Dec-01 08:55:23] RDP (0): correlation id: e2051f4c-251f-7cb1-db26-1224d1590000
[2016-Dec-01 08:55:23] RDP (0): Protocol state changed to: ProtocolConnectingNetwork(1)
[2016-Dec-01 08:55:23] RDP (0): Resolved ‘xxx.xxx.IT’ to ‘xxx.xxx.xxx.xxx’ using NameResolveMethod_DNS(1)
[2016-Dec-01 08:55:31] RDP (0): Exception caught: Exception in file ‘../../librdpclient/asiosocketendpoint.cpp’ at line 603
User Message : Unable to connect to remote PC. Please verify Remote Desktop is enabled, the remote PC is turned on and available on the network, and then try again.
[2016-Dec-01 08:55:31] RDP (0): Protocol state changed to: ProtocolDisconnecting(7)
[2016-Dec-01 08:55:31] RDP (0): Protocol state changed to: ProtocolDisconnected(8)
[2016-Dec-01 08:55:31] RDP (0): —— END ACTIVE CONNECTION ——
[2016-Dec-01 08:55:31] RDP (0): — BEGIN INTERFACE LIST —
[2016-Dec-01 08:55:31] RDP (0): lo0 af=18 addr= netmask=
[2016-Dec-01 08:55:31] RDP (0): lo0 af=30 (AF_INET6) addr=::1 netmask=ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
[2016-Dec-01 08:55:31] RDP (0): lo0 af=2 (AF_INET) addr=127.0.0.1 netmask=255.0.0.0
[2016-Dec-01 08:55:31] RDP (0): lo0 af=30 (AF_INET6) addr=fe80::1%lo0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:31] RDP (0): gif0 af=18 addr= netmask=
[2016-Dec-01 08:55:31] RDP (0): stf0 af=18 addr= netmask=
[2016-Dec-01 08:55:31] RDP (0): en0 af=18 addr= netmask=
[2016-Dec-01 08:55:31] RDP (0): en0 af=30 (AF_INET6) addr=fe80::20c:29ff:feed:53ba%en0 netmask=ffff:ffff:ffff:ffff::
[2016-Dec-01 08:55:31] RDP (0): en0 af=2 (AF_INET) addr=192.168.128.138 netmask=255.255.255.0
[2016-Dec-01 08:55:31] RDP (0): — END INTERFACE LIST —
[2016-Dec-01 08:55:31] RDP (0): correlation id: e2051f4c-251f-7cb1-db26-1224d1590100
[2016-Dec-01 08:55:31] RDP (0): Protocol state changed to: ProtocolConnectingNetwork(1)
[2016-Dec-01 08:55:31] RDP (0): Resolved ‘xxx.xxx.it’ to ‘xxx.xxx.xxx.xxx’ using NameResolveMethod_DNS(1)
[2016-Dec-01 08:55:31] RDP (0): Exception caught: Exception in file ‘../../librdpclient/asiosocketendpoint.cpp’ at line 400
User Message : Connection reset by peer
[2016-Dec-01 08:55:31] RDP (0): Resolved ‘xxx.xxx.it’ to ‘xxx.xxx.xxx.102’ using NameResolveMethod_DNS(1)
[2016-Dec-01 08:55:31] RDP (0): Resolved ‘xxx.xxx.it’ to ‘xxx.xxx.xxx.100’ using NameResolveMethod_DNS(1)
[2016-Dec-01 08:55:32] RDP (0): Exception caught: Exception in file ‘../../librdpclient/asiosocketendpoint.cpp’ at line 400
User Message : Connection reset by peer
[2016-Dec-01 08:55:32] RDP (0): Protocol state changed to: ProtocolDisconnecting(7)
[2016-Dec-01 08:55:32] RDP (0): Protocol state changed to: ProtocolDisconnected(8)
[2016-Dec-01 08:55:32] RDP (0): —— END ACTIVE CONNECTION ——-
Edited by
Thursday, December 1, 2016 8:40 AM
-
Edited by
Symptoms
Consider the following scenario:
-
You have a computer that is running Windows 7 or Windows Server 2008 R2.
-
A Transport Driver Interface (TDI) filter driver is installed on the computer. For example, a TDI filter driver is installed when you install McAfee VirusScan.
-
An application opens a TCP listening port to receive connections.
In this scenario, the application may receive the following error message:
WSAECONNRESET (10054) Connection reset by peer.
A existing connection was forcibly closed by the remote host.
This issue occurs because the TCP/IP driver does not close an incomplete TCP connection. Instead, the TCP/IP driver sends a notification that the TCP/IP driver is ready to receive data when the incomplete TCP connection is created. Therefore, the application receives an instance of the 10054 error that indicates that a connection is reset when the application receives data from the connection.
Resolution
To resolve this issue, install this hotfix.
Note This hotfix temporarily resolves this issue for application vendors before they migrate their implementation to Windows Filtering Platform (WFP). These application vendors use the TDI filter driver or the TDI extension driver (TDX) on a computer that is running Windows 7 or Windows Server 2008 R2.
Hotfix information
A supported hotfix is available from Microsoft. However, this hotfix is intended to correct only the problem that is described in this article. Apply this hotfix only to systems that are experiencing the problem described in this article. This hotfix might receive additional testing. Therefore, if you are not severely affected by this problem, we recommend that you wait for the next software update that contains this hotfix.
If the hotfix is available for download, there is a «Hotfix download available» section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix.
Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft Web site:
http://support.microsoft.com/contactus/?ws=supportNote The «Hotfix download available» form displays the languages for which the hotfix is available. If you do not see your language, it is because a hotfix is not available for that language.
Prerequisites
To apply this hotfix, you must be running Windows 7 or Windows Server 2008 R2.
Registry information
Important This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in WindowsTo enable the hotfix in this package, follow these steps:
-
In Registry Editor, locate the following registry subkey:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesTcpipParameters
-
If you are running a 32-bit operating system, perform the following step:
Right-click the Parameters registry subkey, point to New, and then click DWORD Value.If you are running a 64-bit operating system, perform the following step:
Right-click the Parameters registry subkey, point to New, and then click DWORD (32-bit) Value.
-
Rename the new registry entry to TdxPrematureConnectIndDisabled and set the value to 1.
Restart requirement
You may have to restart the computer after you apply this hotfix.
Hotfix replacement information
This hotfix does not replace a previously released hotfix.
File information
The global version of this hotfix installs files that have the attributes that are listed in the following tables. The dates and the times for these files are listed in Coordinated Universal Time (UTC). The dates and the times for these files on your local computer are displayed in your local time together with your current daylight saving time (DST) bias. Additionally, the dates and the times may change when you perform certain operations on the files.
Windows 7 and Windows Server 2008 R2 file information notes
Important Windows 7 hotfixes and Windows Server 2008 R2 hotfixes are included in the same packages. However, hotfixes on the Hotfix Request page are listed under both operating systems. To request the hotfix package that applies to one or both operating systems, select the hotfix that is listed under «Windows 7/Windows Server 2008 R2» on the page. Always refer to the «Applies To» section in articles to determine the actual operating system that each hotfix applies to.
-
The MANIFEST files (.manifest) and the MUM files (.mum) that are installed for each environment are listed separately in the «Additional file information for Windows Server 2008 R2 and for Windows 7» section. MUM and MANIFEST files, and the associated security catalog (.cat) files, are extremely important to maintain the state of the updated components. The security catalog files, for which the attributes are not listed, are signed with a Microsoft digital signature.
For all supported x86-based versions of Windows 7
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Tdx.sys |
6.1.7600.20796 |
74,752 |
09-Sep-2010 |
02:19 |
x86 |
For all supported x64-based versions of Windows 7 and of Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Tdx.sys |
6.1.7600.20796 |
101,376 |
09-Sep-2010 |
02:52 |
x64 |
For all supported IA-64-based versions of Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Tdx.sys |
6.1.7600.20796 |
236,032 |
09-Sep-2010 |
01:47 |
IA-64 |
Status
Microsoft has confirmed that this is a problem in the Microsoft products that are listed in the «Applies to» section.
More Information
For more information about WFP, visit the following Microsoft website:
General information about WFPFor more information about software update terminology, click the following article number to view the article in the Microsoft Knowledge Base:
824684 Description of the standard terminology that is used to describe Microsoft software updates
Additional file information
Additional file information for Windows 7 and for Windows Server 2008 R2
Additional files for all supported x86-based versions of Windows 7
|
File name |
Package_1_for_kb981344~31bf3856ad364e35~x86~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,820 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_2_for_kb981344~31bf3856ad364e35~x86~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,825 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_3_for_kb981344~31bf3856ad364e35~x86~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,805 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_for_kb981344_rtm~31bf3856ad364e35~x86~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
2,421 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
X86_bfb7f2e54887b839240a44ae0de89137_31bf3856ad364e35_6.1.7600.20796_none_3f3df7432361a4c5.manifest |
|
File version |
Not Applicable |
|
File size |
702 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
X86_microsoft-windows-tdi-over-tcpip_31bf3856ad364e35_6.1.7600.20796_none_ea93f14a568e0aaf.manifest |
|
File version |
Not Applicable |
|
File size |
2,924 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
04:58 |
|
Platform |
Not Applicable |
Additional files for all supported x64-based versions of Windows 7 and of Windows Server 2008 R2
|
File name |
Amd64_8e30a6e4951f89c20ce3f8a1c04b9f2a_31bf3856ad364e35_6.1.7600.20796_none_8d28eb4c99ddf2d4.manifest |
|
File version |
Not Applicable |
|
File size |
706 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Amd64_microsoft-windows-tdi-over-tcpip_31bf3856ad364e35_6.1.7600.20796_none_46b28cce0eeb7be5.manifest |
|
File version |
Not Applicable |
|
File size |
2,926 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
06:11 |
|
Platform |
Not Applicable |
|
File name |
Package_1_for_kb981344~31bf3856ad364e35~amd64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,830 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_2_for_kb981344~31bf3856ad364e35~amd64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
2,057 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_3_for_kb981344~31bf3856ad364e35~amd64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,815 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_for_kb981344_rtm~31bf3856ad364e35~amd64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
2,659 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
Additional files for all supported IA-64-based versions of Windows Server 2008 R2
|
File name |
Ia64_0bb425f9d3502a4be9efc4af61147428_31bf3856ad364e35_6.1.7600.20796_none_09467879be47b542.manifest |
|
File version |
Not Applicable |
|
File size |
704 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Ia64_microsoft-windows-tdi-over-tcpip_31bf3856ad364e35_6.1.7600.20796_none_ea959540568c13ab.manifest |
|
File version |
Not Applicable |
|
File size |
2,925 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
05:48 |
|
Platform |
Not Applicable |
|
File name |
Package_1_for_kb981344~31bf3856ad364e35~ia64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
2,051 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
|
File name |
Package_for_kb981344_rtm~31bf3856ad364e35~ia64~~6.1.2.0.mum |
|
File version |
Not Applicable |
|
File size |
1,683 |
|
Date (UTC) |
09-Sep-2010 |
|
Time (UTC) |
18:48 |
|
Platform |
Not Applicable |
Need more help?
предыдущая глава | содержание | следующая глава
- 10.1 «The server’s host key is not cached in the registry»
- 10.2 «WARNING — POTENTIAL SECURITY BREACH!»
- 10.3 «SSH protocol version 2 required by our configuration but remote only provides (old, insecure) SSH-1»
- 10.4 «The first cipher supported by the server is … below the configured warning threshold»
- 10.5 «Remote side sent disconnect message type 2 (protocol error): «Too many authentication failures for root»»
- 10.6 «Out of memory»
- 10.7 «Internal error», «Internal fault», «Assertion failed»
- 10.8 «Unable to use key file», «Couldn’t load private key», «Couldn’t load this key»
- 10.9 «Server refused our key», «Server refused our public key», «Key refused»
- 10.10 «Access denied», «Authentication refused»
- 10.11 «No supported authentication methods available»
- 10.12 «Incorrect MAC received on packet» or «Incorrect CRC received on packet»
- 10.13 «Incoming packet was garbled on decryption»
- 10.14 «PuTTY X11 proxy: various errors»
- 10.15 «Network error: Software caused connection abort»
- 10.16 «Network error: Connection reset by peer»
- 10.17 «Network error: Connection refused»
- 10.18 «Network error: Connection timed out»
- 10.19 «Network error: Cannot assign requested address»
This chapter lists a number of common error messages which PuTTY and its associated tools can produce, and explains what they mean in more detail.
We do not attempt to list all error messages here: there are many which should never occur, and some which should be self-explanatory. If you get an error message which is not listed in this chapter and which you don’t understand, report it to us as a bug (see appendix B) and we will add documentation for it.
10.1 «The server’s host key is not cached in the registry»
This error message occurs when PuTTY connects to a new SSH server. Every server identifies itself by means of a host key; once PuTTY knows the host key for a server, it will be able to detect if a malicious attacker redirects your connection to another machine.
If you see this message, it means that PuTTY has not seen this host key before, and has no way of knowing whether it is correct or not. You should attempt to verify the host key by other means, such as asking the machine’s administrator.
If you see this message and you know that your installation of PuTTY has connected to the same server before, it may have been recently upgraded to SSH protocol version 2. SSH protocols 1 and 2 use separate host keys, so when you first use SSH-2 with a server you have only used SSH-1 with before, you will see this message again. You should verify the correctness of the key as before.
See section 2.2 for more information on host keys.
10.2 «WARNING — POTENTIAL SECURITY BREACH!»
This message, followed by «The server’s host key does not match the one PuTTY has cached in the registry», means that PuTTY has connected to the SSH server before, knows what its host key should be, but has found a different one.
This may mean that a malicious attacker has replaced your server with a different one, or has redirected your network connection to their own machine. On the other hand, it may simply mean that the administrator of your server has accidentally changed the key while upgrading the SSH software; this shouldn’t happen but it is unfortunately possible.
You should contact your server’s administrator and see whether they expect the host key to have changed. If so, verify the new host key in the same way as you would if it was new.
See section 2.2 for more information on host keys.
10.3 «SSH protocol version 2 required by our configuration but remote only provides (old, insecure) SSH-1»
By default, PuTTY only supports connecting to SSH servers that implement SSH protocol version 2. If you see this message, the server you’re trying to connect to only supports the older SSH-1 protocol.
If the server genuinely only supports SSH-1, then you need to either change the «SSH protocol version» setting (see section 4.19.4), or use the -1 command-line option; in any case, you should not treat the resulting connection as secure.
You might start seeing this message with new versions of PuTTY (from 0.68 onwards) where you didn’t before, because it used to be possible to configure PuTTY to automatically fall back from SSH-2 to SSH-1. This is no longer supported, to prevent the possibility of a downgrade attack.
10.4 «The first cipher supported by the server is … below the configured warning threshold»
This occurs when the SSH server does not offer any ciphers which you have configured PuTTY to consider strong enough. By default, PuTTY puts up this warning only for Blowfish, single-DES, and Arcfour encryption.
See section 4.22 for more information on this message.
(There are similar messages for other cryptographic primitives, such as host key algorithms.)
10.5 «Remote side sent disconnect message type 2 (protocol error): «Too many authentication failures for root»»
This message is produced by an OpenSSH (or Sun SSH) server if it receives more failed authentication attempts than it is willing to tolerate.
This can easily happen if you are using Pageant and have a large number of keys loaded into it, since these servers count each offer of a public key as an authentication attempt. This can be worked around by specifying the key that’s required for the authentication in the PuTTY configuration (see section 4.23.8); PuTTY will ignore any other keys Pageant may have, but will ask Pageant to do the authentication, so that you don’t have to type your passphrase.
On the server, this can be worked around by disabling public-key authentication or (for Sun SSH only) by increasing MaxAuthTries in sshd_config.
10.6 «Out of memory»
This occurs when PuTTY tries to allocate more memory than the system can give it. This may happen for genuine reasons: if the computer really has run out of memory, or if you have configured an extremely large number of lines of scrollback in your terminal. PuTTY is not able to recover from running out of memory; it will terminate immediately after giving this error.
However, this error can also occur when memory is not running out at all, because PuTTY receives data in the wrong format. In SSH-2 and also in SFTP, the server sends the length of each message before the message itself; so PuTTY will receive the length, try to allocate space for the message, and then receive the rest of the message. If the length PuTTY receives is garbage, it will try to allocate a ridiculous amount of memory, and will terminate with an «Out of memory» error.
This can happen in SSH-2, if PuTTY and the server have not enabled encryption in the same way (see question A.7.3 in the FAQ).
This can also happen in PSCP or PSFTP, if your login scripts on the server generate output: the client program will be expecting an SFTP message starting with a length, and if it receives some text from your login scripts instead it will try to interpret them as a message length. See question A.7.4 for details of this.
10.7 «Internal error», «Internal fault», «Assertion failed»
Any error beginning with the word «Internal» should never occur. If it does, there is a bug in PuTTY by definition; please see appendix B and report it to us.
Similarly, any error message starting with «Assertion failed» is a bug in PuTTY. Please report it to us, and include the exact text from the error message box.
10.8 «Unable to use key file», «Couldn’t load private key», «Couldn’t load this key»
Various forms of this error are printed in the PuTTY window, or written to the PuTTY Event Log (see section 3.1.3.1) when trying public-key authentication, or given by Pageant when trying to load a private key.
If you see one of these messages, it often indicates that you’ve tried to load a key of an inappropriate type into PuTTY, Plink, PSCP, PSFTP, or Pageant.
You may have tried to load an SSH-2 key in a «foreign» format (OpenSSH or ssh.com) directly into one of the PuTTY tools, in which case you need to import it into PuTTY’s native format (*.PPK) using PuTTYgen – see section 8.2.12.
Alternatively, you may have specified a key that’s inappropriate for the connection you’re making. The SSH-2 and the old SSH-1 protocols require different private key formats, and a SSH-1 key can’t be used for a SSH-2 connection (or vice versa).
10.9 «Server refused our key», «Server refused our public key», «Key refused»
Various forms of this error are printed in the PuTTY window, or written to the PuTTY Event Log (see section 3.1.3.1) when trying public-key authentication.
If you see one of these messages, it means that PuTTY has sent a public key to the server and offered to authenticate with it, and the server has refused to accept authentication. This usually means that the server is not configured to accept this key to authenticate this user.
This is almost certainly not a problem with PuTTY. If you see this type of message, the first thing you should do is check your server configuration carefully. Common errors include having the wrong permissions or ownership set on the public key or the user’s home directory on the server. Also, read the PuTTY Event Log; the server may have sent diagnostic messages explaining exactly what problem it had with your setup.
Section 8.3 has some hints on server-side public key setup.
10.10 «Access denied», «Authentication refused»
Various forms of this error are printed in the PuTTY window, or written to the PuTTY Event Log (see section 3.1.3.1) during authentication.
If you see one of these messages, it means that the server has refused all the forms of authentication PuTTY has tried and it has no further ideas.
It may be worth checking the Event Log for diagnostic messages from the server giving more detail.
This error can be caused by buggy SSH-1 servers that fail to cope with the various strategies we use for camouflaging passwords in transit. Upgrade your server, or use the workarounds described in section 4.28.11 and possibly section 4.28.12.
10.11 «No supported authentication methods available»
This error indicates that PuTTY has run out of ways to authenticate you to an SSH server. This may be because PuTTY has TIS or keyboard-interactive authentication disabled, in which case see section 4.23.4 and section 4.23.5.
10.12 «Incorrect MAC received on packet» or «Incorrect CRC received on packet»
This error occurs when PuTTY decrypts an SSH packet and its checksum is not correct. This probably means something has gone wrong in the encryption or decryption process. It’s difficult to tell from this error message whether the problem is in the client, in the server, or in between.
In particular, if the network is corrupting data at the TCP level, it may only be obvious with cryptographic protocols such as SSH, which explicitly check the integrity of the transferred data and complain loudly if the checks fail. Corruption of protocols without integrity protection (such as HTTP) will manifest in more subtle failures (such as misdisplayed text or images in a web browser) which may not be noticed.
Occasionally this has been caused by server bugs. An example is the bug described at section 4.28.8, although you’re very unlikely to encounter that one these days.
In this context MAC stands for Message Authentication Code. It’s a cryptographic term, and it has nothing at all to do with Ethernet MAC (Media Access Control) addresses, or with the Apple computer.
10.13 «Incoming packet was garbled on decryption»
This error occurs when PuTTY decrypts an SSH packet and the decrypted data makes no sense. This probably means something has gone wrong in the encryption or decryption process. It’s difficult to tell from this error message whether the problem is in the client, in the server, or in between.
If you get this error, one thing you could try would be to fiddle with the setting of «Miscomputes SSH-2 encryption keys» (see section 4.28.10) or «Ignores SSH-2 maximum packet size» (see section 4.28.5) on the Bugs panel.
10.14 «PuTTY X11 proxy: various errors»
This family of errors are reported when PuTTY is doing X forwarding. They are sent back to the X application running on the SSH server, which will usually report the error to the user.
When PuTTY enables X forwarding (see section 3.4) it creates a virtual X display running on the SSH server. This display requires authentication to connect to it (this is how PuTTY prevents other users on your server machine from connecting through the PuTTY proxy to your real X display). PuTTY also sends the server the details it needs to enable clients to connect, and the server should put this mechanism in place automatically, so your X applications should just work.
A common reason why people see one of these messages is because they used SSH to log in as one user (let’s say «fred»), and then used the Unix su command to become another user (typically «root»). The original user, «fred», has access to the X authentication data provided by the SSH server, and can run X applications which are forwarded over the SSH connection. However, the second user («root») does not automatically have the authentication data passed on to it, so attempting to run an X application as that user often fails with this error.
If this happens, it is not a problem with PuTTY. You need to arrange for your X authentication data to be passed from the user you logged in as to the user you used su to become. How you do this depends on your particular system; in fact many modern versions of su do it automatically.
10.15 «Network error: Software caused connection abort»
This is a generic error produced by the Windows network code when it kills an established connection for some reason. For example, it might happen if you pull the network cable out of the back of an Ethernet-connected computer, or if Windows has any other similar reason to believe the entire network has become unreachable.
Windows also generates this error if it has given up on the machine at the other end of the connection ever responding to it. If the network between your client and server goes down and your client then tries to send some data, Windows will make several attempts to send the data and will then give up and kill the connection. In particular, this can occur even if you didn’t type anything, if you are using SSH-2 and PuTTY attempts a key re-exchange. (See section 4.20.2 for more about key re-exchange.)
(It can also occur if you are using keepalives in your connection. Other people have reported that keepalives fix this error for them. See section 4.14.1 for a discussion of the pros and cons of keepalives.)
We are not aware of any reason why this error might occur that would represent a bug in PuTTY. The problem is between you, your Windows system, your network and the remote system.
10.16 «Network error: Connection reset by peer»
This error occurs when the machines at each end of a network connection lose track of the state of the connection between them. For example, you might see it if your SSH server crashes, and manages to reboot fully before you next attempt to send data to it.
However, the most common reason to see this message is if you are connecting through a firewall or a NAT router which has timed the connection out. See question A.7.8 in the FAQ for more details. You may be able to improve the situation by using keepalives; see section 4.14.1 for details on this.
Note that Windows can produce this error in some circumstances without seeing a connection reset from the server, for instance if the connection to the network is lost.
10.17 «Network error: Connection refused»
This error means that the network connection PuTTY tried to make to your server was rejected by the server. Usually this happens because the server does not provide the service which PuTTY is trying to access.
Check that you are connecting with the correct protocol (SSH, Telnet or Rlogin), and check that the port number is correct. If that fails, consult the administrator of your server.
10.18 «Network error: Connection timed out»
This error means that the network connection PuTTY tried to make to your server received no response at all from the server. Usually this happens because the server machine is completely isolated from the network, or because it is turned off.
Check that you have correctly entered the host name or IP address of your server machine. If that fails, consult the administrator of your server.
Unix also generates this error when it tries to send data down a connection and contact with the server has been completely lost during a connection. (There is a delay of minutes before Unix gives up on receiving a reply from the server.) This can occur if you type things into PuTTY while the network is down, but it can also occur if PuTTY decides of its own accord to send data: due to a repeat key exchange in SSH-2 (see section 4.20.2) or due to keepalives (section 4.14.1).
10.19 «Network error: Cannot assign requested address»
This means that the operating system rejected the parameters of the network connection PuTTY tried to make, usually without actually trying to connect to anything, because they were simply invalid.
A common way to provoke this error is to accidentally try to connect to port 0, which is not a valid port number.

